Multi-Way Search Trees
|
|
|
- Gervais Henry
- 6 years ago
- Views:
Transcription
1 Multi-Way Search Trees Manolis Koubarakis 1
2 Multi-Way Search Trees Multi-way trees are trees such that each internal node can have many children. Let us assume that the entries we store in a search tree are pairs of the form (k, x) where k is the key and x the value associated with the key. Example: Assume we store information about students. The key can be the student ID while the value can be information such as name, year of study etc. 2
3 Definitions A tree is ordered if there is a linear ordering defined for the children of each node; that is, we can identify children of a node as being the first, the second, third and so on. Let v be a node of an ordered tree. We say that v is a d-node if v has d children. 3
4 Definitions (cont d) A multi-way search tree is an ordered tree T that has the following properties: Each internal node of T has at least 2 children. That is, each internal node is a d-node such that d 2. Each internal d-node of T with children v 1,, v d stores an ordered set of d 1 key-value entries k 1, x 1,, k d 1, x d 1, where k 1 k d 1. Let us conveniently define k 0 = and k d = +. For each entry (k, x) stored at a node in the subtree of v rooted at v i, i = 1,, d, we have that k i 1 k k i. 4
5 Definitions (cont d) By the above definition, the external nodes of a multi-way search tree do not store any entries and serve only as place holders. A binary search tree is a special case of a multi-way search tree, where each internal node stores one entry and has two children. Note: in this way binary search trees are viewed as non-empty proper binary trees. 5
6 Example Multi-Way Search Tree (m = 3)
7 Proposition Let T be an m-way search tree with height h, n entries and n E external nodes. Then, the following inequalities hold: 1. h n m h 1 2. log m (n + 1) h n 3. n E = n + 1 Proof? 7
8 Proof We will prove (1) first. The lower bound can be seen by considering an m-way search tree like the one given on the next slide where we have one internal node in each level and one entry in each node for levels 0, 1, 2,, h 1 (level h contains only external nodes). 8
9 Proof (cont d) h 1 h 9
10 Proof (cont d) For the upper bound, consider an m-way search tree of height h where each internal node in the levels 0 to h 1 has exactly m children (the external nodes are at level h ). h 1 i=0 These internal nodes are total. Since each of these nodes has m 1 entries, the total number of entries in the internal nodes is m h 1. m i = mh 1 m 1 in 10
11 Proof (cont d) To prove the lower bound of (2), rewrite (1) and take logarithms in base m. The upper bound in (2) is the same as the lower bound in (1). The proof of (3) is left as an exercise. 11
12 Searching in a Multi-Way Search Tree Let T be a multi-way search tree and k be a key. The algorithm for searching for an entry with key k is simple. We trace a path in T starting at the root. When we are at a d-node v during the search, we compare the key k with the keys k 1,, k d 1 stored at v. If k = k i, for some i, the search is successfully completed. Otherwise, we continue the search in the child v i of v such that k i 1 < k < k i. If we reach an external node, then we know that there is no entry with key k in T. 12
13 Example Multi-Way Search Tree
14 Search for Key Unsuccessful search 14
15 Search for Key Successful search 15
16 Insertion in a Multi-Way Search Tree If we want to insert a new pair (k, x) into a multi-way search tree, then we start by searching for this entry. If we find the entry, then we do not need to reinsert it. If we end up in an external node, then the entry is not in the tree. In this case, we return to the parent v of the external node and attempt to insert the key there. If v has space for one more key then we insert the entry there. If not, we create a new node, we insert the entry in this node and make this node a child of v in the appropriate position. 16
17 Insert Key Unsuccessful search 17
18 Key 28 Inserted
19 Insert Key Unsuccessful search 19
20 Key 32 Inserted
21 Insert Key Unsuccessful Search 21
22 Key 12 Inserted
23 Deletion from a Multi-Way Search Tree The algorithm for deletion from a multi-way search tree is left as an exercise. 23
24 Complexity of Operations Let us consider the time to search a m-way search tree for a given key. The time spent at a d-node depends on the implementation of the node. If we use a sorted array then, using binary search, we can search a node in O(log d) time. Thus the time for a search operation in the tree is O h log m. The complexity of insertion and deletion is also O h log m. 24
25 Efficiency Considerations We know that maintaining perfect balance in binary search trees yields shortest average search paths, but the attempts to maintain perfect balance when we insert or delete nodes can incur costly rebalancing in which every node of the tree needs to be rearranged. AVL trees showed us one way to solve this problem by abandoning the goal of perfect balance and adopt the goal of keeping the trees almost balanced. 25
26 Efficiency Considerations (cont d) Multi-way search trees give us another way to solve this problem. The primary efficiency goal for a multi-way search tree is to keep the height as small as possible but permit the number of keys at each node to vary. We want the height of the tree h to be a logarithmic function of n, the total number of entries stored in the tree. A search tree with logarithmic height is called a balanced search tree. 26
27 Balanced Multi-way Search Trees We will study two kinds of balanced multi-way search trees: 2-3 trees trees or (2,4) trees. 27
28 2-3 Trees A 2-3 tree is a multi-way search tree which has the following properties: Size property: Each internal node contains one or two entries, and has either two or three children. Depth property: All leaves of the tree are empty trees that have the same depth (lie on a single bottom level). 28
29 Example of 2-3 Tree H D J N A E F I K L O P 29
30 Searching in 2-3 Trees To search for the key L, for example, we start at the root and since L > H, we follow the pointer to the right subtree of the root node. Now we note that L lies between J and N, so we follow the middle pointer between the nodes J and N to the node containing the keys K and L. L is found and the search terminates. 30
31 Search for Key L H D J N A E F I K L O P 31
32 Insertion of New Keys Suppose we want to insert the new key B into the tree. Since B<H, we follow the left pointer from the root node to the node containing D in the second row. Then we follow the left pointer of D s node to the node containing A. Since B>A, we follow the right pointer of A s node which lead us to an empty tree (an external node). Then we go back to the parent of the external node and try to store the new key there. The node containing A has room for one more key so we store key B there. We also add a new empty child to this node. 32
33 Example: Insert B H D J N A E F I K L O P 33
34 Example: Insert B H D J N A E F I K L O P 34
35 Example: Result H D J N A B E F I K L O P 35
36 Insertion of New Keys (cont d) Let us now insert key M. This leads to the attempt to add M to the node containing K and L which now overflows with keys K, L and M. The strategy for such cases is to split the overflowed node into two nodes and pass the middle key to the parent. Hence we split the overflowed node into two new nodes containing K and M respectively. We also pass the middle key L to the parent node containing J and N. 36
37 Insertion of New Keys (cont d) The attempt to add L to this parent node results in a new overflowed node in which the key L lies between keys J and N. So we split this parent node into new nodes containing J and N respectively, and we pass the middle key L up to the root. The root has room for L so we store it there. 37
38 Example: Insert M H D J N A B E F I K L O P 38
39 Example: Insert M (cont d) H D J N A B E F I K L O P M overflows this node 39
40 Example: Insert M (cont d) H D J N L A B E F I M O P K The node is split in two and L is passed to the parent node 40
41 Example: Insert M (cont d) H D J N L overflows this node L A B E F I M O P K 41
42 Example: Insert M (cont d) H L The node is split in two and L is passed up to the parent D J N A B E F I K M O P 42
43 Example: Result H L L is inserted in the root node D J N A B E F I K M O P 43
44 Insertion of New Keys (cont d) Let us now insert key Q. Q should be entered in the node containing O and P which now overflows. Thus, this node is split up to two nodes one containing O and the other containing R, and the middle key is passed up towards the parent node. The parent node has only key N so there is space for P and it is inserted there. 44
45 Example: Insert Q H L D J N A B E F I K M O P Q overflows this node 45
46 Example: Insert Q (cont d) H L D J N P A B E F I K M O Q P This node is split up and P is passed up 46
47 Example: Result H L D J N P A B E F I K M O Q P 47
48 Insertion of New Keys (cont d) Let us now insert key R. R is inserted in the node with Q where there is space. 48
49 Example: Insert R H L D J N P A B E F I K M O Q P R 49
50 Inserting New Keys (cont d) Let us now insert key S. S should be inserted in the node with Q and R. This node overflows. Thus, it is split into two nodes one containing Q and the other containing S and R is passed up to the parent node. R now oveflows this node where N and P are also stored. Thus, this node is split into two nodes one containing N and the other containing R and the middle key P is sent up to the parent (the root). 50
51 Inserting New Keys (cont d) The root now overflows with the addition of P so it is split into two nodes one containing H and the other containing P and the middle key L is used to create a new root. Thus, we have added one more level to the tree. 51
52 Example: Insert S H L D J N P A B E F I K M O Q P R S overflows this node 52
53 Example: Insert S (cont d) H L D J N P R A B E F I K M O Q S This node is split and R is sent up 53
54 Example: Insert S (cont d) H L D J N P R overflows this node R A B E F I K M O Q S 54
55 Example: Insert S (cont d) H L P This node is split up and P is sent up D J N R A B E F I K M O Q S 55
56 Example: Insert S (cont d) P overflows the root H L P D J N R A B E F I K M O Q S 56
57 Example: Result L The root splits and L becomes the new root H P D J N R A B E F I K M O Q S 57
58 Complexity of Insertion in 2-3 Trees When we insert a key at level k, in the worst case we need to split k + 1 nodes (one at each of the k levels plus the root). A 2-3 tree containing n keys with the maximum number of levels takes the form of a binary tree where each internal node has one key and two children. In such a tree n = 2 k+1 1 where k is the number of the lowest level. This implies that k + 1 = log(n + 1) from which we see that the splits are in the worst case O log n. So insertion in a 2-3 tree takes at worst O lll n time. Similarly we can prove that searches and deletions take O lll n time. 58
59 (2,4) Trees A (2,4) tree or tree is a multi-way search tree which has the following two properties: Size property: Every internal node contains at least one and at most three keys, and has at least two and at most four children. Depth property: All the external nodes are empty trees that have the same depth (lie on a single bottom level). 59
60 Result Proposition. The height of a (2,4) tree storing n entries is O log n. Proof: Let h be the height of a (2,4) tree T storing n entries. We justify the proposition by showing that and 1 2 log(n + 1) h h log(n + 1). 60
61 Result (cont d) Note that by the size property, we have at most 4 nodes at depth 1, at most 4 2 nodes at depth 2, and so on. Thus, the number of external nodes of T is at most 4 h. Similarly, by the size property, we have at least 2 nodes at depth 1, at least 2 2 nodes at depth 2, and so on. Thus, the number of external nodes in T is at least 2 h. We also know that the number of external nodes is n
62 Result (cont d) Therefore, we obtain 2 h n + 1 and n h. Taking the logarithm in base 2 of each of the above terms, we get that h log(n + 1) and log(n + 1) 2h. These inequalities prove our claims. 62
63 Insertion in (2,4) Trees To insert a new entry (k, x), with key k, into a (2,4) tree T, we first perform a search for k. Assuming that T has no entry with key k, this search terminates unsuccessfully at an external node z. Let v be the parent of z. We insert the new entry into node v and add a new child (an external node) to v on the left of z. 63
64 Insertion (cont d) Our insertion method preserves the depth property, since we add a new external node at the same level as existing external nodes. But it might violate the size property. If a node v was previously a 4-node, then it may become a 5- node after the insertion which causes the tree to longer be a (2,4) tree. This type of violation of the size property is called an overflow node at node v, and it must be resolved in order to restore the properties of a (2,4) tree. 64
65 Dealing with Overflow Nodes Let v 1,, v 5 be the children of v, and let k 1,, k 4 be the keys stored at v. To remedy the overflow at node v, we perform a split operation on v as follows. Replace v with two nodes vv and vvv, where vv is a 3-node with children v 1, v 2, v 3 storing keys k 1 and k 2 vvv is a 2-node with children v 4, v 5, storing key k 4. If v was the root of T, create a new root node u. Else, let u be the parent of v. Insert key k 3 into u and make vv and vvv children of u, so that if v was child i of u, then vv and vvv become children i and i + 1 of u, respectively. 65
66 Overflow at a 5-node h 1 h 2 u u 1 v = u 2 k 1 k 2 k 3 k 4 u 3 v 1 v 2 v 3 v 4 v 5 66
67 The third key of v inserted into the parent node u h 1 h 2 u k 3 v = u u 2 1 u 3 k 1 k 2 k 4 v 1 v 2 v 3 v 4 v 5 67
68 Node v replaced with a 3-node vv and a 2-node vvv h 1 k 3 h 2 u u 1 v = u 2 v = u 3 u 4 k 1 k 2 k 4 v 1 v 2 v 3 v 4 v 5 68
69 Example Let us now see an example of few insertions into an initially empty (2,4) tree. 69
70 Insert
71 Insert
72 Insert
73 Insert 15 - Overflow
74 Creation of New Root Node
75 Split
76 Insert
77 Insert 5 - Overflow
78 5 is Sent to the Parent Node
79 Split
80 Insert
81 Insert
82 Insertion (cont d) Let us now see a more complicated example of insertion in a (2,4) tree. 82
83 Initial Tree
84 Insert 17 - Overflow
85 15 is Sent to the Parent Node
86 Split
87 Overflow at the Root
88 Creation of New Root
89 Split
90 Final Tree
91 Complexity Analysis of Insertion A split operation affects a constant number of nodes of the tree and a constant number of entries stored at such nodes. Thus, it can be implemented in O(1) time. As a consequence of a split operation on node v, a new overflow may arise at the parent u of v. A split operation either eliminates the overflow or it propagates it into the parent of the current node. Hence, the number of split operations is bounded by the height of the tree, which is O log n. Therefore, the total time to perform an insertion is O log n. 91
92 Removal in (2,4) Trees Let us now consider the removal of an entry with key k from a (2,4) tree T. Removing such an entry can always be reduced to the case where the entry to be removed is stored at a node v whose children are external nodes. Suppose that the entry we wish to remove is stored in the i-th entry (k i, x i ) at a node z that has only internal nodes as children. In this case, we swap the entry (k i, x i ) with an appropriate entry that is stored at a node v with external-node children as follows: We find the right-most internal node v in the subtree rooted at the ith child of z, noting that the children of node v are all external nodes. We swap the entry (k i, x i ) at z with the last entry of v. The key of this entry is the predecessor of k i in the natural ordering of the keys of the tree. 92
93 Removal (cont d) Once we ensure that the entry to be removed is stored at a node v with only external-node children, we simply remove the entry from v and remove the i-th external node of v. Removing an entry from a node v preserves the depth property, because we always remove an external node child from a node v with only external-node children. However, we might violate the size property at v. 93
94 Removal (cont d) If v was previously a 2-node, then, after the removal, it becomes a 1-node with no entries. This type of violation of the size property is called an underflow node at v. To remedy an underflow, we check whether an immediate sibling of v is a 3-node or a 4-node. If we find such a sibling w, then we perform a transfer operation, in which we move a child of w to v, a key of w to the parent u of v and w, and a key of u to v. If v has only one sibling, or if both immediate siblings of v are 2-nodes, then we perform a fusion operation, in which we merge v with a sibling, creating a new node v, and move a key from the parent u of v to v. 94
95 Removal (cont d) A fusion operation at a node v may cause a new underflow to occur at the parent u of v, which in turn triggers a transfer or fusion at u. Hence, the number of fusion operations is bounded by the height of the tree which is O log n. Therefore, a removal operation can take O lll n time in the worst case. If an underflow propagates all the way up to the root, then the root is simply deleted. 95
96 Examples Let us now see some examples of removal from a (2,4) tree. 96
97 Initial Tree
98 Remove v
99 Transfer 12 v 5 u w
100 After the Transfer 12 u v 5 w
101 Remove v 5 8 w
102 Fusion of w and v 11 u 6 15 v 5 10 w v
103 After the Fusion
104 Remove
105 After the Removal of
106 Remove 14 - Underflow
107 Fusion 11 6 u 5 v
108 Underflow at u 11 6 u
109 Fusion 6 11 u
110 Remove the Root
111 Final Tree
112 Readings T. A. Standish. Data Structures, Algorithms and Software Principles in C. Section 9.9 M. T. Goodrich, R. Tamassia and D. Mount. Data Structures and Algorithms in C++. Section 10.4 R. Sedgewick. Αλγόριθμοι σε C. 3 η Αμερικανική Έκδοση. Εκδόσεις Κλειδάριθμος. Section
Multi-Way Search Trees
 Multi-Way Search Trees Manolis Koubarakis 1 Multi-Way Search Trees Multi-way trees are trees such that each internal node can have many children. Let us assume that the entries we store in a search tree
Multi-Way Search Trees Manolis Koubarakis 1 Multi-Way Search Trees Multi-way trees are trees such that each internal node can have many children. Let us assume that the entries we store in a search tree
(2,4) Trees Goodrich, Tamassia (2,4) Trees 1
 (2,4) Trees 9 2 5 7 10 14 2004 Goodrich, Tamassia (2,4) Trees 1 Multi-Way Search Tree A multi-way search tree is an ordered tree such that Each internal node has at least two children and stores d -1 key-element
(2,4) Trees 9 2 5 7 10 14 2004 Goodrich, Tamassia (2,4) Trees 1 Multi-Way Search Tree A multi-way search tree is an ordered tree such that Each internal node has at least two children and stores d -1 key-element
Multiway Search Trees. Multiway-Search Trees (cont d)
 Multiway Search Trees Each internal node v of a multi-way search tree T has at least two children contains d-1 items, where d is the number of children of v an item is of the form (k i,x i ) for 1 i d-1,
Multiway Search Trees Each internal node v of a multi-way search tree T has at least two children contains d-1 items, where d is the number of children of v an item is of the form (k i,x i ) for 1 i d-1,
Multi-way Search Trees. (Multi-way Search Trees) Data Structures and Programming Spring / 25
 Multi-way Search Trees (Multi-way Search Trees) Data Structures and Programming Spring 2017 1 / 25 Multi-way Search Trees Each internal node of a multi-way search tree T: has at least two children contains
Multi-way Search Trees (Multi-way Search Trees) Data Structures and Programming Spring 2017 1 / 25 Multi-way Search Trees Each internal node of a multi-way search tree T: has at least two children contains
Lecture 11: Multiway and (2,4) Trees. Courtesy to Goodrich, Tamassia and Olga Veksler
 Lecture 11: Multiway and (2,4) Trees 9 2 5 7 10 14 Courtesy to Goodrich, Tamassia and Olga Veksler Instructor: Yuzhen Xie Outline Multiway Seach Tree: a new type of search trees: for ordered d dictionary
Lecture 11: Multiway and (2,4) Trees 9 2 5 7 10 14 Courtesy to Goodrich, Tamassia and Olga Veksler Instructor: Yuzhen Xie Outline Multiway Seach Tree: a new type of search trees: for ordered d dictionary
(2,4) Trees. 2/22/2006 (2,4) Trees 1
 (2,4) Trees 9 2 5 7 10 14 2/22/2006 (2,4) Trees 1 Outline and Reading Multi-way search tree ( 10.4.1) Definition Search (2,4) tree ( 10.4.2) Definition Search Insertion Deletion Comparison of dictionary
(2,4) Trees 9 2 5 7 10 14 2/22/2006 (2,4) Trees 1 Outline and Reading Multi-way search tree ( 10.4.1) Definition Search (2,4) tree ( 10.4.2) Definition Search Insertion Deletion Comparison of dictionary
Search Trees - 1 Venkatanatha Sarma Y
 Search Trees - 1 Lecture delivered by: Venkatanatha Sarma Y Assistant Professor MSRSAS-Bangalore 11 Objectives To introduce, discuss and analyse the different ways to realise balanced Binary Search Trees
Search Trees - 1 Lecture delivered by: Venkatanatha Sarma Y Assistant Professor MSRSAS-Bangalore 11 Objectives To introduce, discuss and analyse the different ways to realise balanced Binary Search Trees
Trees. Courtesy to Goodrich, Tamassia and Olga Veksler
 Lecture 12: BT Trees Courtesy to Goodrich, Tamassia and Olga Veksler Instructor: Yuzhen Xie Outline B-tree Special case of multiway search trees used when data must be stored on the disk, i.e. too large
Lecture 12: BT Trees Courtesy to Goodrich, Tamassia and Olga Veksler Instructor: Yuzhen Xie Outline B-tree Special case of multiway search trees used when data must be stored on the disk, i.e. too large
Multiway Search Trees
 Multiway Search Trees Intuitive Definition A multiway search tree is one with nodes that have two or more children. Within each node is stored a given key, which is associated to an item we wish to access
Multiway Search Trees Intuitive Definition A multiway search tree is one with nodes that have two or more children. Within each node is stored a given key, which is associated to an item we wish to access
B-Trees. Disk Storage. What is a multiway tree? What is a B-tree? Why B-trees? Insertion in a B-tree. Deletion in a B-tree
 B-Trees Disk Storage What is a multiway tree? What is a B-tree? Why B-trees? Insertion in a B-tree Deletion in a B-tree Disk Storage Data is stored on disk (i.e., secondary memory) in blocks. A block is
B-Trees Disk Storage What is a multiway tree? What is a B-tree? Why B-trees? Insertion in a B-tree Deletion in a B-tree Disk Storage Data is stored on disk (i.e., secondary memory) in blocks. A block is
Algorithms. AVL Tree
 Algorithms AVL Tree Balanced binary tree The disadvantage of a binary search tree is that its height can be as large as N-1 This means that the time needed to perform insertion and deletion and many other
Algorithms AVL Tree Balanced binary tree The disadvantage of a binary search tree is that its height can be as large as N-1 This means that the time needed to perform insertion and deletion and many other
B-Trees and External Memory
 Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 B-Trees and External Memory 1 (2, 4) Trees: Generalization of BSTs Each internal
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 B-Trees and External Memory 1 (2, 4) Trees: Generalization of BSTs Each internal
B-Trees and External Memory
 Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 and External Memory 1 1 (2, 4) Trees: Generalization of BSTs Each internal node
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 and External Memory 1 1 (2, 4) Trees: Generalization of BSTs Each internal node
Properties of red-black trees
 Red-Black Trees Introduction We have seen that a binary search tree is a useful tool. I.e., if its height is h, then we can implement any basic operation on it in O(h) units of time. The problem: given
Red-Black Trees Introduction We have seen that a binary search tree is a useful tool. I.e., if its height is h, then we can implement any basic operation on it in O(h) units of time. The problem: given
CHAPTER 10 AVL TREES. 3 8 z 4
 CHAPTER 10 AVL TREES v 6 3 8 z 4 ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY
CHAPTER 10 AVL TREES v 6 3 8 z 4 ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY
M-ary Search Tree. B-Trees. Solution: B-Trees. B-Tree: Example. B-Tree Properties. B-Trees (4.7 in Weiss)
 M-ary Search Tree B-Trees (4.7 in Weiss) Maximum branching factor of M Tree with N values has height = # disk accesses for find: Runtime of find: 1/21/2011 1 1/21/2011 2 Solution: B-Trees specialized M-ary
M-ary Search Tree B-Trees (4.7 in Weiss) Maximum branching factor of M Tree with N values has height = # disk accesses for find: Runtime of find: 1/21/2011 1 1/21/2011 2 Solution: B-Trees specialized M-ary
Self-Balancing Search Trees. Chapter 11
 Self-Balancing Search Trees Chapter 11 Chapter Objectives To understand the impact that balance has on the performance of binary search trees To learn about the AVL tree for storing and maintaining a binary
Self-Balancing Search Trees Chapter 11 Chapter Objectives To understand the impact that balance has on the performance of binary search trees To learn about the AVL tree for storing and maintaining a binary
M-ary Search Tree. B-Trees. B-Trees. Solution: B-Trees. B-Tree: Example. B-Tree Properties. Maximum branching factor of M Complete tree has height =
 M-ary Search Tree B-Trees Section 4.7 in Weiss Maximum branching factor of M Complete tree has height = # disk accesses for find: Runtime of find: 2 Solution: B-Trees specialized M-ary search trees Each
M-ary Search Tree B-Trees Section 4.7 in Weiss Maximum branching factor of M Complete tree has height = # disk accesses for find: Runtime of find: 2 Solution: B-Trees specialized M-ary search trees Each
Algorithms. Deleting from Red-Black Trees B-Trees
 Algorithms Deleting from Red-Black Trees B-Trees Recall the rules for BST deletion 1. If vertex to be deleted is a leaf, just delete it. 2. If vertex to be deleted has just one child, replace it with that
Algorithms Deleting from Red-Black Trees B-Trees Recall the rules for BST deletion 1. If vertex to be deleted is a leaf, just delete it. 2. If vertex to be deleted has just one child, replace it with that
(2,4) Trees Goodrich, Tamassia. (2,4) Trees 1
 (2,4) Trees 9 2 5 7 10 14 (2,4) Trees 1 Multi-Way Search Tree ( 9.4.1) A multi-way search tree is an ordered tree such that Each internal node has at least two children and stores d 1 key-element items
(2,4) Trees 9 2 5 7 10 14 (2,4) Trees 1 Multi-Way Search Tree ( 9.4.1) A multi-way search tree is an ordered tree such that Each internal node has at least two children and stores d 1 key-element items
What is a Multi-way tree?
 B-Tree Motivation for studying Multi-way and B-trees A disk access is very expensive compared to a typical computer instruction (mechanical limitations) -One disk access is worth about 200,000 instructions.
B-Tree Motivation for studying Multi-way and B-trees A disk access is very expensive compared to a typical computer instruction (mechanical limitations) -One disk access is worth about 200,000 instructions.
Red-Black Trees Goodrich, Tamassia. Red-Black Trees 1
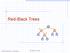 Red-Black Trees 3 8 00 Goodrich, Tamassia Red-Black Trees 1 From (,) to Red-Black Trees A red-black tree is a representation of a (,) tree by means of a binary tree hose nodes are colored red or black
Red-Black Trees 3 8 00 Goodrich, Tamassia Red-Black Trees 1 From (,) to Red-Black Trees A red-black tree is a representation of a (,) tree by means of a binary tree hose nodes are colored red or black
Data Structure: Search Trees 2. Instructor: Prof. Young-guk Ha Dept. of Computer Science & Engineering
 Data Structure: Search Trees 2 2017 Instructor: Prof. Young-guk Ha Dept. of Computer Science & Engineering Search Trees Tree data structures that can be used to implement a dictionary, especially an ordered
Data Structure: Search Trees 2 2017 Instructor: Prof. Young-guk Ha Dept. of Computer Science & Engineering Search Trees Tree data structures that can be used to implement a dictionary, especially an ordered
Multi-way Search Trees! M-Way Search! M-Way Search Trees Representation!
 Lecture 10: Multi-way Search Trees: intro to B-trees 2-3 trees 2-3-4 trees Multi-way Search Trees A node on an M-way search tree with M 1 distinct and ordered keys: k 1 < k 2 < k 3
Lecture 10: Multi-way Search Trees: intro to B-trees 2-3 trees 2-3-4 trees Multi-way Search Trees A node on an M-way search tree with M 1 distinct and ordered keys: k 1 < k 2 < k 3
Chapter 10: Search Trees
 < 6 > 1 4 = 8 9 Chapter 10: Search Trees Nancy Amato Parasol Lab, Dept. CSE, Texas A&M University Acknowledgement: These slides are adapted from slides provided with Data Structures and Algorithms in C++,
< 6 > 1 4 = 8 9 Chapter 10: Search Trees Nancy Amato Parasol Lab, Dept. CSE, Texas A&M University Acknowledgement: These slides are adapted from slides provided with Data Structures and Algorithms in C++,
AVL Trees Goodrich, Tamassia, Goldwasser AVL Trees 1
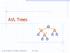 AVL Trees v 6 3 8 z 20 Goodrich, Tamassia, Goldwasser AVL Trees AVL Tree Definition Adelson-Velsky and Landis binary search tree balanced each internal node v the heights of the children of v can 2 3 7
AVL Trees v 6 3 8 z 20 Goodrich, Tamassia, Goldwasser AVL Trees AVL Tree Definition Adelson-Velsky and Landis binary search tree balanced each internal node v the heights of the children of v can 2 3 7
Binary Search Trees. Analysis of Algorithms
 Binary Search Trees Analysis of Algorithms Binary Search Trees A BST is a binary tree in symmetric order 31 Each node has a key and every node s key is: 19 23 25 35 38 40 larger than all keys in its left
Binary Search Trees Analysis of Algorithms Binary Search Trees A BST is a binary tree in symmetric order 31 Each node has a key and every node s key is: 19 23 25 35 38 40 larger than all keys in its left
CSE100. Advanced Data Structures. Lecture 8. (Based on Paul Kube course materials)
 CSE100 Advanced Data Structures Lecture 8 (Based on Paul Kube course materials) CSE 100 Treaps Find, insert, delete, split, and join in treaps Randomized search trees Randomized search tree time costs
CSE100 Advanced Data Structures Lecture 8 (Based on Paul Kube course materials) CSE 100 Treaps Find, insert, delete, split, and join in treaps Randomized search trees Randomized search tree time costs
Outline. Definition. 2 Height-Balance. 3 Searches. 4 Rotations. 5 Insertion. 6 Deletions. 7 Reference. 1 Every node is either red or black.
 Outline 1 Definition Computer Science 331 Red-Black rees Mike Jacobson Department of Computer Science University of Calgary Lectures #20-22 2 Height-Balance 3 Searches 4 Rotations 5 s: Main Case 6 Partial
Outline 1 Definition Computer Science 331 Red-Black rees Mike Jacobson Department of Computer Science University of Calgary Lectures #20-22 2 Height-Balance 3 Searches 4 Rotations 5 s: Main Case 6 Partial
Motivation for B-Trees
 1 Motivation for Assume that we use an AVL tree to store about 20 million records We end up with a very deep binary tree with lots of different disk accesses; log2 20,000,000 is about 24, so this takes
1 Motivation for Assume that we use an AVL tree to store about 20 million records We end up with a very deep binary tree with lots of different disk accesses; log2 20,000,000 is about 24, so this takes
Comp 335 File Structures. B - Trees
 Comp 335 File Structures B - Trees Introduction Simple indexes provided a way to directly access a record in an entry sequenced file thereby decreasing the number of seeks to disk. WE ASSUMED THE INDEX
Comp 335 File Structures B - Trees Introduction Simple indexes provided a way to directly access a record in an entry sequenced file thereby decreasing the number of seeks to disk. WE ASSUMED THE INDEX
Lecture 5. Treaps Find, insert, delete, split, and join in treaps Randomized search trees Randomized search tree time costs
 Lecture 5 Treaps Find, insert, delete, split, and join in treaps Randomized search trees Randomized search tree time costs Reading: Randomized Search Trees by Aragon & Seidel, Algorithmica 1996, http://sims.berkeley.edu/~aragon/pubs/rst96.pdf;
Lecture 5 Treaps Find, insert, delete, split, and join in treaps Randomized search trees Randomized search tree time costs Reading: Randomized Search Trees by Aragon & Seidel, Algorithmica 1996, http://sims.berkeley.edu/~aragon/pubs/rst96.pdf;
AVL Tree Definition. An example of an AVL tree where the heights are shown next to the nodes. Adelson-Velsky and Landis
 Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 0 AVL Trees v 6 3 8 z 0 Goodrich, Tamassia, Goldwasser
Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 0 AVL Trees v 6 3 8 z 0 Goodrich, Tamassia, Goldwasser
CSE 326: Data Structures B-Trees and B+ Trees
 Announcements (2/4/09) CSE 26: Data Structures B-Trees and B+ Trees Midterm on Friday Special office hour: 4:00-5:00 Thursday in Jaech Gallery (6 th floor of CSE building) This is in addition to my usual
Announcements (2/4/09) CSE 26: Data Structures B-Trees and B+ Trees Midterm on Friday Special office hour: 4:00-5:00 Thursday in Jaech Gallery (6 th floor of CSE building) This is in addition to my usual
Data Structures in Java
 Data Structures in Java Lecture 10: AVL Trees. 10/1/015 Daniel Bauer Balanced BSTs Balance condition: Guarantee that the BST is always close to a complete binary tree (every node has exactly two or zero
Data Structures in Java Lecture 10: AVL Trees. 10/1/015 Daniel Bauer Balanced BSTs Balance condition: Guarantee that the BST is always close to a complete binary tree (every node has exactly two or zero
Algorithms. Red-Black Trees
 Algorithms Red-Black Trees Red-Black Trees Balanced binary search trees guarantee an O(log n) running time Red-black-tree Binary search tree with an additional attribute for its nodes: color which can
Algorithms Red-Black Trees Red-Black Trees Balanced binary search trees guarantee an O(log n) running time Red-black-tree Binary search tree with an additional attribute for its nodes: color which can
From (2,4) to Red-Black Trees
 Red-Black Trees 3/0/1 Presentation for use ith the textbook Data Structures and Algorithms in Jaa, th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldasser, Wiley, 01 Red-Black Trees 3 8 01 Goodrich,
Red-Black Trees 3/0/1 Presentation for use ith the textbook Data Structures and Algorithms in Jaa, th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldasser, Wiley, 01 Red-Black Trees 3 8 01 Goodrich,
Search Trees - 2. Venkatanatha Sarma Y. Lecture delivered by: Assistant Professor MSRSAS-Bangalore. M.S Ramaiah School of Advanced Studies - Bangalore
 Search Trees - 2 Lecture delivered by: Venkatanatha Sarma Y Assistant Professor MSRSAS-Bangalore 11 Objectives To introduce, discuss and analyse the different ways to realise balanced Binary Search Trees
Search Trees - 2 Lecture delivered by: Venkatanatha Sarma Y Assistant Professor MSRSAS-Bangalore 11 Objectives To introduce, discuss and analyse the different ways to realise balanced Binary Search Trees
Advanced Algorithms. Class Notes for Thursday, September 18, 2014 Bernard Moret
 Advanced Algorithms Class Notes for Thursday, September 18, 2014 Bernard Moret 1 Amortized Analysis (cont d) 1.1 Side note: regarding meldable heaps When we saw how to meld two leftist trees, we did not
Advanced Algorithms Class Notes for Thursday, September 18, 2014 Bernard Moret 1 Amortized Analysis (cont d) 1.1 Side note: regarding meldable heaps When we saw how to meld two leftist trees, we did not
CS 234. Module 6. October 16, CS 234 Module 6 ADT Dictionary 1 / 33
 CS 234 Module 6 October 16, 2018 CS 234 Module 6 ADT Dictionary 1 / 33 Idea for an ADT Te ADT Dictionary stores pairs (key, element), were keys are distinct and elements can be any data. Notes: Tis is
CS 234 Module 6 October 16, 2018 CS 234 Module 6 ADT Dictionary 1 / 33 Idea for an ADT Te ADT Dictionary stores pairs (key, element), were keys are distinct and elements can be any data. Notes: Tis is
Chapter 12 Advanced Data Structures
 Chapter 12 Advanced Data Structures 2 Red-Black Trees add the attribute of (red or black) to links/nodes red-black trees used in C++ Standard Template Library (STL) Java to implement maps (or, as in Python)
Chapter 12 Advanced Data Structures 2 Red-Black Trees add the attribute of (red or black) to links/nodes red-black trees used in C++ Standard Template Library (STL) Java to implement maps (or, as in Python)
An AVL tree with N nodes is an excellent data. The Big-Oh analysis shows that most operations finish within O(log N) time
 B + -TREES MOTIVATION An AVL tree with N nodes is an excellent data structure for searching, indexing, etc. The Big-Oh analysis shows that most operations finish within O(log N) time The theoretical conclusion
B + -TREES MOTIVATION An AVL tree with N nodes is an excellent data structure for searching, indexing, etc. The Big-Oh analysis shows that most operations finish within O(log N) time The theoretical conclusion
Algorithms in Systems Engineering ISE 172. Lecture 16. Dr. Ted Ralphs
 Algorithms in Systems Engineering ISE 172 Lecture 16 Dr. Ted Ralphs ISE 172 Lecture 16 1 References for Today s Lecture Required reading Sections 6.5-6.7 References CLRS Chapter 22 R. Sedgewick, Algorithms
Algorithms in Systems Engineering ISE 172 Lecture 16 Dr. Ted Ralphs ISE 172 Lecture 16 1 References for Today s Lecture Required reading Sections 6.5-6.7 References CLRS Chapter 22 R. Sedgewick, Algorithms
Hashing. Manolis Koubarakis. Data Structures and Programming Techniques
 Hashing Manolis Koubarakis 1 The Symbol Table ADT A symbol table T is an abstract storage that contains table entries that are either empty or are pairs of the form (K, I) where K is a key and I is some
Hashing Manolis Koubarakis 1 The Symbol Table ADT A symbol table T is an abstract storage that contains table entries that are either empty or are pairs of the form (K, I) where K is a key and I is some
Balanced Search Trees
 Balanced Search Trees Computer Science E-22 Harvard Extension School David G. Sullivan, Ph.D. Review: Balanced Trees A tree is balanced if, for each node, the node s subtrees have the same height or have
Balanced Search Trees Computer Science E-22 Harvard Extension School David G. Sullivan, Ph.D. Review: Balanced Trees A tree is balanced if, for each node, the node s subtrees have the same height or have
CSE 530A. B+ Trees. Washington University Fall 2013
 CSE 530A B+ Trees Washington University Fall 2013 B Trees A B tree is an ordered (non-binary) tree where the internal nodes can have a varying number of child nodes (within some range) B Trees When a key
CSE 530A B+ Trees Washington University Fall 2013 B Trees A B tree is an ordered (non-binary) tree where the internal nodes can have a varying number of child nodes (within some range) B Trees When a key
COMP Analysis of Algorithms & Data Structures
 COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Lecture 9 - Jan. 22, 2018 CLRS 12.2, 12.3, 13.2, read problem 13-3 University of Manitoba COMP 3170 - Analysis of Algorithms & Data Structures
COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Lecture 9 - Jan. 22, 2018 CLRS 12.2, 12.3, 13.2, read problem 13-3 University of Manitoba COMP 3170 - Analysis of Algorithms & Data Structures
Sorting and Selection
 Sorting and Selection Introduction Divide and Conquer Merge-Sort Quick-Sort Radix-Sort Bucket-Sort 10-1 Introduction Assuming we have a sequence S storing a list of keyelement entries. The key of the element
Sorting and Selection Introduction Divide and Conquer Merge-Sort Quick-Sort Radix-Sort Bucket-Sort 10-1 Introduction Assuming we have a sequence S storing a list of keyelement entries. The key of the element
10/23/2013. AVL Trees. Height of an AVL Tree. Height of an AVL Tree. AVL Trees
 // AVL Trees AVL Trees An AVL tree is a binary search tree with a balance condition. AVL is named for its inventors: Adel son-vel skii and Landis AVL tree approximates the ideal tree (completely balanced
// AVL Trees AVL Trees An AVL tree is a binary search tree with a balance condition. AVL is named for its inventors: Adel son-vel skii and Landis AVL tree approximates the ideal tree (completely balanced
HEAPS: IMPLEMENTING EFFICIENT PRIORITY QUEUES
 HEAPS: IMPLEMENTING EFFICIENT PRIORITY QUEUES 2 5 6 9 7 Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H., Wiley, 2014
HEAPS: IMPLEMENTING EFFICIENT PRIORITY QUEUES 2 5 6 9 7 Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H., Wiley, 2014
Computational Optimization ISE 407. Lecture 16. Dr. Ted Ralphs
 Computational Optimization ISE 407 Lecture 16 Dr. Ted Ralphs ISE 407 Lecture 16 1 References for Today s Lecture Required reading Sections 6.5-6.7 References CLRS Chapter 22 R. Sedgewick, Algorithms in
Computational Optimization ISE 407 Lecture 16 Dr. Ted Ralphs ISE 407 Lecture 16 1 References for Today s Lecture Required reading Sections 6.5-6.7 References CLRS Chapter 22 R. Sedgewick, Algorithms in
Multiway searching. In the worst case of searching a complete binary search tree, we can make log(n) page faults Everyone knows what a page fault is?
 Multiway searching What do we do if the volume of data to be searched is too large to fit into main memory Search tree is stored on disk pages, and the pages required as comparisons proceed may not be
Multiway searching What do we do if the volume of data to be searched is too large to fit into main memory Search tree is stored on disk pages, and the pages required as comparisons proceed may not be
Binary search trees. Binary search trees are data structures based on binary trees that support operations on dynamic sets.
 COMP3600/6466 Algorithms 2018 Lecture 12 1 Binary search trees Reading: Cormen et al, Sections 12.1 to 12.3 Binary search trees are data structures based on binary trees that support operations on dynamic
COMP3600/6466 Algorithms 2018 Lecture 12 1 Binary search trees Reading: Cormen et al, Sections 12.1 to 12.3 Binary search trees are data structures based on binary trees that support operations on dynamic
We assume uniform hashing (UH):
 We assume uniform hashing (UH): the probe sequence of each key is equally likely to be any of the! permutations of 0,1,, 1 UH generalizes the notion of SUH that produces not just a single number, but a
We assume uniform hashing (UH): the probe sequence of each key is equally likely to be any of the! permutations of 0,1,, 1 UH generalizes the notion of SUH that produces not just a single number, but a
Red-Black Trees. 2/24/2006 Red-Black Trees 1
 Red-Black Trees 3 8 //00 Red-Black Trees 1 Outline and Reading From (,) trees to red-black trees ( 10.5) Red-black tree ( 10.5.1) Definition Height Insertion restructuring recoloring Deletion restructuring
Red-Black Trees 3 8 //00 Red-Black Trees 1 Outline and Reading From (,) trees to red-black trees ( 10.5) Red-black tree ( 10.5.1) Definition Height Insertion restructuring recoloring Deletion restructuring
Binary search trees 3. Binary search trees. Binary search trees 2. Reading: Cormen et al, Sections 12.1 to 12.3
 Binary search trees Reading: Cormen et al, Sections 12.1 to 12.3 Binary search trees 3 Binary search trees are data structures based on binary trees that support operations on dynamic sets. Each element
Binary search trees Reading: Cormen et al, Sections 12.1 to 12.3 Binary search trees 3 Binary search trees are data structures based on binary trees that support operations on dynamic sets. Each element
Organizing Spatial Data
 Organizing Spatial Data Spatial data records include a sense of location as an attribute. Typically location is represented by coordinate data (in 2D or 3D). 1 If we are to search spatial data using the
Organizing Spatial Data Spatial data records include a sense of location as an attribute. Typically location is represented by coordinate data (in 2D or 3D). 1 If we are to search spatial data using the
Lecture 6: Analysis of Algorithms (CS )
 Lecture 6: Analysis of Algorithms (CS583-002) Amarda Shehu October 08, 2014 1 Outline of Today s Class 2 Traversals Querying Insertion and Deletion Sorting with BSTs 3 Red-black Trees Height of a Red-black
Lecture 6: Analysis of Algorithms (CS583-002) Amarda Shehu October 08, 2014 1 Outline of Today s Class 2 Traversals Querying Insertion and Deletion Sorting with BSTs 3 Red-black Trees Height of a Red-black
Introduction. for large input, even access time may be prohibitive we need data structures that exhibit times closer to O(log N) binary search tree
 Chapter 4 Trees 2 Introduction for large input, even access time may be prohibitive we need data structures that exhibit running times closer to O(log N) binary search tree 3 Terminology recursive definition
Chapter 4 Trees 2 Introduction for large input, even access time may be prohibitive we need data structures that exhibit running times closer to O(log N) binary search tree 3 Terminology recursive definition
COMP Analysis of Algorithms & Data Structures
 COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Lecture 9 - Jan. 22, 2018 CLRS 12.2, 12.3, 13.2, read problem 13-3 University of Manitoba 1 / 12 Binary Search Trees (review) Structure
COMP 3170 - Analysis of Algorithms & Data Structures Shahin Kamali Lecture 9 - Jan. 22, 2018 CLRS 12.2, 12.3, 13.2, read problem 13-3 University of Manitoba 1 / 12 Binary Search Trees (review) Structure
2-3 Tree. Outline B-TREE. catch(...){ printf( "Assignment::SolveProblem() AAAA!"); } ADD SLIDES ON DISJOINT SETS
 Outline catch(...){ printf( "Assignment::SolveProblem() AAAA!"); } Balanced Search Trees 2-3 Trees 2-3-4 Trees Slide 4 Why care about advanced implementations? Same entries, different insertion sequence:
Outline catch(...){ printf( "Assignment::SolveProblem() AAAA!"); } Balanced Search Trees 2-3 Trees 2-3-4 Trees Slide 4 Why care about advanced implementations? Same entries, different insertion sequence:
Laboratory Module X B TREES
 Purpose: Purpose 1... Purpose 2 Purpose 3. Laboratory Module X B TREES 1. Preparation Before Lab When working with large sets of data, it is often not possible or desirable to maintain the entire structure
Purpose: Purpose 1... Purpose 2 Purpose 3. Laboratory Module X B TREES 1. Preparation Before Lab When working with large sets of data, it is often not possible or desirable to maintain the entire structure
Splay Trees. (Splay Trees) Data Structures and Programming Spring / 27
 Splay Trees (Splay Trees) Data Structures and Programming Spring 2017 1 / 27 Basic Idea Invented by Sleator and Tarjan (1985) Blind rebalancing no height info kept! Worst-case time per operation is O(n)
Splay Trees (Splay Trees) Data Structures and Programming Spring 2017 1 / 27 Basic Idea Invented by Sleator and Tarjan (1985) Blind rebalancing no height info kept! Worst-case time per operation is O(n)
Priority Queues. 1 Introduction. 2 Naïve Implementations. CSci 335 Software Design and Analysis III Chapter 6 Priority Queues. Prof.
 Priority Queues 1 Introduction Many applications require a special type of queuing in which items are pushed onto the queue by order of arrival, but removed from the queue based on some other priority
Priority Queues 1 Introduction Many applications require a special type of queuing in which items are pushed onto the queue by order of arrival, but removed from the queue based on some other priority
Chapter 2: Basic Data Structures
 Chapter 2: Basic Data Structures Basic Data Structures Stacks Queues Vectors, Linked Lists Trees (Including Balanced Trees) Priority Queues and Heaps Dictionaries and Hash Tables Spring 2014 CS 315 2 Two
Chapter 2: Basic Data Structures Basic Data Structures Stacks Queues Vectors, Linked Lists Trees (Including Balanced Trees) Priority Queues and Heaps Dictionaries and Hash Tables Spring 2014 CS 315 2 Two
9/29/2016. Chapter 4 Trees. Introduction. Terminology. Terminology. Terminology. Terminology
 Introduction Chapter 4 Trees for large input, even linear access time may be prohibitive we need data structures that exhibit average running times closer to O(log N) binary search tree 2 Terminology recursive
Introduction Chapter 4 Trees for large input, even linear access time may be prohibitive we need data structures that exhibit average running times closer to O(log N) binary search tree 2 Terminology recursive
Balanced search trees
 Balanced search trees Ordinary binary search trees have expected height Θ(log n) if items are inserted and deleted in random order, but for other orders the height can be Θ(n). This is undesirable, since
Balanced search trees Ordinary binary search trees have expected height Θ(log n) if items are inserted and deleted in random order, but for other orders the height can be Θ(n). This is undesirable, since
CISC 235: Topic 4. Balanced Binary Search Trees
 CISC 235: Topic 4 Balanced Binary Search Trees Outline Rationale and definitions Rotations AVL Trees, Red-Black, and AA-Trees Algorithms for searching, insertion, and deletion Analysis of complexity CISC
CISC 235: Topic 4 Balanced Binary Search Trees Outline Rationale and definitions Rotations AVL Trees, Red-Black, and AA-Trees Algorithms for searching, insertion, and deletion Analysis of complexity CISC
CSCI Trees. Mark Redekopp David Kempe
 CSCI 104 2-3 Trees Mark Redekopp David Kempe Trees & Maps/Sets C++ STL "maps" and "sets" use binary search trees internally to store their keys (and values) that can grow or contract as needed This allows
CSCI 104 2-3 Trees Mark Redekopp David Kempe Trees & Maps/Sets C++ STL "maps" and "sets" use binary search trees internally to store their keys (and values) that can grow or contract as needed This allows
Advanced Set Representation Methods
 Advanced Set Representation Methods AVL trees. 2-3(-4) Trees. Union-Find Set ADT DSA - lecture 4 - T.U.Cluj-Napoca - M. Joldos 1 Advanced Set Representation. AVL Trees Problem with BSTs: worst case operation
Advanced Set Representation Methods AVL trees. 2-3(-4) Trees. Union-Find Set ADT DSA - lecture 4 - T.U.Cluj-Napoca - M. Joldos 1 Advanced Set Representation. AVL Trees Problem with BSTs: worst case operation
Ch04 Balanced Search Trees
 Presentation for use with the textbook Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 05 Ch0 Balanced Search Trees v 3 8 z Why care about advanced implementations? Same entries,
Presentation for use with the textbook Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 05 Ch0 Balanced Search Trees v 3 8 z Why care about advanced implementations? Same entries,
CSCI2100B Data Structures Heaps
 CSCI2100B Data Structures Heaps Irwin King king@cse.cuhk.edu.hk http://www.cse.cuhk.edu.hk/~king Department of Computer Science & Engineering The Chinese University of Hong Kong Introduction In some applications,
CSCI2100B Data Structures Heaps Irwin King king@cse.cuhk.edu.hk http://www.cse.cuhk.edu.hk/~king Department of Computer Science & Engineering The Chinese University of Hong Kong Introduction In some applications,
CS 310 B-trees, Page 1. Motives. Large-scale databases are stored in disks/hard drives.
 CS 310 B-trees, Page 1 Motives Large-scale databases are stored in disks/hard drives. Disks are quite different from main memory. Data in a disk are accessed through a read-write head. To read a piece
CS 310 B-trees, Page 1 Motives Large-scale databases are stored in disks/hard drives. Disks are quite different from main memory. Data in a disk are accessed through a read-write head. To read a piece
Lecture 3: B-Trees. October Lecture 3: B-Trees
 October 2017 Remarks Search trees The dynamic set operations search, minimum, maximum, successor, predecessor, insert and del can be performed efficiently (in O(log n) time) if the search tree is balanced.
October 2017 Remarks Search trees The dynamic set operations search, minimum, maximum, successor, predecessor, insert and del can be performed efficiently (in O(log n) time) if the search tree is balanced.
CH 8. HEAPS AND PRIORITY QUEUES
 CH 8. HEAPS AND PRIORITY QUEUES ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY
CH 8. HEAPS AND PRIORITY QUEUES ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY
Physical Level of Databases: B+-Trees
 Physical Level of Databases: B+-Trees Adnan YAZICI Computer Engineering Department METU (Fall 2005) 1 B + -Tree Index Files l Disadvantage of indexed-sequential files: performance degrades as file grows,
Physical Level of Databases: B+-Trees Adnan YAZICI Computer Engineering Department METU (Fall 2005) 1 B + -Tree Index Files l Disadvantage of indexed-sequential files: performance degrades as file grows,
CH. 8 PRIORITY QUEUES AND HEAPS
 CH. 8 PRIORITY QUEUES AND HEAPS ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY
CH. 8 PRIORITY QUEUES AND HEAPS ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY
Heaps Outline and Required Reading: Heaps ( 7.3) COSC 2011, Fall 2003, Section A Instructor: N. Vlajic
 1 Heaps Outline and Required Reading: Heaps (.3) COSC 2011, Fall 2003, Section A Instructor: N. Vlajic Heap ADT 2 Heap binary tree (T) that stores a collection of keys at its internal nodes and satisfies
1 Heaps Outline and Required Reading: Heaps (.3) COSC 2011, Fall 2003, Section A Instructor: N. Vlajic Heap ADT 2 Heap binary tree (T) that stores a collection of keys at its internal nodes and satisfies
Operations on Heap Tree The major operations required to be performed on a heap tree are Insertion, Deletion, and Merging.
 Priority Queue, Heap and Heap Sort In this time, we will study Priority queue, heap and heap sort. Heap is a data structure, which permits one to insert elements into a set and also to find the largest
Priority Queue, Heap and Heap Sort In this time, we will study Priority queue, heap and heap sort. Heap is a data structure, which permits one to insert elements into a set and also to find the largest
Note that this is a rep invariant! The type system doesn t enforce this but you need it to be true. Should use repok to check in debug version.
 Announcements: Prelim tonight! 7:30-9:00 in Thurston 203/205 o Handed back in section tomorrow o If you have a conflict you can take the exam at 5:45 but can t leave early. Please email me so we have a
Announcements: Prelim tonight! 7:30-9:00 in Thurston 203/205 o Handed back in section tomorrow o If you have a conflict you can take the exam at 5:45 but can t leave early. Please email me so we have a
Trees. Manolis Koubarakis. Data Structures and Programming Techniques
 Trees Manolis Koubarakis 1 Trees Trees (δένδρα) are one of the most important data structures in Computer Science. Examples of trees: Directory structure Search trees (for stored information associated
Trees Manolis Koubarakis 1 Trees Trees (δένδρα) are one of the most important data structures in Computer Science. Examples of trees: Directory structure Search trees (for stored information associated
13.4 Deletion in red-black trees
 Deletion in a red-black tree is similar to insertion. Apply the deletion algorithm for binary search trees. Apply node color changes and left/right rotations to fix the violations of RBT tree properties.
Deletion in a red-black tree is similar to insertion. Apply the deletion algorithm for binary search trees. Apply node color changes and left/right rotations to fix the violations of RBT tree properties.
B-Trees. Version of October 2, B-Trees Version of October 2, / 22
 B-Trees Version of October 2, 2014 B-Trees Version of October 2, 2014 1 / 22 Motivation An AVL tree can be an excellent data structure for implementing dictionary search, insertion and deletion Each operation
B-Trees Version of October 2, 2014 B-Trees Version of October 2, 2014 1 / 22 Motivation An AVL tree can be an excellent data structure for implementing dictionary search, insertion and deletion Each operation
Chapter 11: Indexing and Hashing
 Chapter 11: Indexing and Hashing Basic Concepts Ordered Indices B + -Tree Index Files B-Tree Index Files Static Hashing Dynamic Hashing Comparison of Ordered Indexing and Hashing Index Definition in SQL
Chapter 11: Indexing and Hashing Basic Concepts Ordered Indices B + -Tree Index Files B-Tree Index Files Static Hashing Dynamic Hashing Comparison of Ordered Indexing and Hashing Index Definition in SQL
Lower Bound on Comparison-based Sorting
 Lower Bound on Comparison-based Sorting Different sorting algorithms may have different time complexity, how to know whether the running time of an algorithm is best possible? We know of several sorting
Lower Bound on Comparison-based Sorting Different sorting algorithms may have different time complexity, how to know whether the running time of an algorithm is best possible? We know of several sorting
Design and Analysis of Algorithms Lecture- 9: B- Trees
 Design and Analysis of Algorithms Lecture- 9: B- Trees Dr. Chung- Wen Albert Tsao atsao@svuca.edu www.408codingschool.com/cs502_algorithm 1/12/16 Slide Source: http://www.slideshare.net/anujmodi555/b-trees-in-data-structure
Design and Analysis of Algorithms Lecture- 9: B- Trees Dr. Chung- Wen Albert Tsao atsao@svuca.edu www.408codingschool.com/cs502_algorithm 1/12/16 Slide Source: http://www.slideshare.net/anujmodi555/b-trees-in-data-structure
Heaps. 2/13/2006 Heaps 1
 Heaps /13/00 Heaps 1 Outline and Reading What is a heap ( 8.3.1) Height of a heap ( 8.3.) Insertion ( 8.3.3) Removal ( 8.3.3) Heap-sort ( 8.3.) Arraylist-based implementation ( 8.3.) Bottom-up construction
Heaps /13/00 Heaps 1 Outline and Reading What is a heap ( 8.3.1) Height of a heap ( 8.3.) Insertion ( 8.3.3) Removal ( 8.3.3) Heap-sort ( 8.3.) Arraylist-based implementation ( 8.3.) Bottom-up construction
Part 2: Balanced Trees
 Part 2: Balanced Trees 1 AVL Trees We could dene a perfectly balanced binary search tree with N nodes to be a complete binary search tree, one in which every level except the last is completely full. A
Part 2: Balanced Trees 1 AVL Trees We could dene a perfectly balanced binary search tree with N nodes to be a complete binary search tree, one in which every level except the last is completely full. A
Search Trees (Ch. 9) > = Binary Search Trees 1
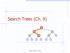 Search Trees (Ch. 9) < 6 > = 1 4 8 9 Binary Search Trees 1 Ordered Dictionaries Keys are assumed to come from a total order. New operations: closestbefore(k) closestafter(k) Binary Search Trees Binary
Search Trees (Ch. 9) < 6 > = 1 4 8 9 Binary Search Trees 1 Ordered Dictionaries Keys are assumed to come from a total order. New operations: closestbefore(k) closestafter(k) Binary Search Trees Binary
COSC160: Data Structures Balanced Trees. Jeremy Bolton, PhD Assistant Teaching Professor
 COSC160: Data Structures Balanced Trees Jeremy Bolton, PhD Assistant Teaching Professor Outline I. Balanced Trees I. AVL Trees I. Balance Constraint II. Examples III. Searching IV. Insertions V. Removals
COSC160: Data Structures Balanced Trees Jeremy Bolton, PhD Assistant Teaching Professor Outline I. Balanced Trees I. AVL Trees I. Balance Constraint II. Examples III. Searching IV. Insertions V. Removals
Red-black trees (19.5), B-trees (19.8), trees
 Red-black trees (19.5), B-trees (19.8), 2-3-4 trees Red-black trees A red-black tree is a balanced BST It has a more complicated invariant than an AVL tree: Each node is coloured red or black A red node
Red-black trees (19.5), B-trees (19.8), 2-3-4 trees Red-black trees A red-black tree is a balanced BST It has a more complicated invariant than an AVL tree: Each node is coloured red or black A red node
CS Fall 2010 B-trees Carola Wenk
 CS 3343 -- Fall 2010 B-trees Carola Wenk 10/19/10 CS 3343 Analysis of Algorithms 1 External memory dictionary Task: Given a large amount of data that does not fit into main memory, process it into a dictionary
CS 3343 -- Fall 2010 B-trees Carola Wenk 10/19/10 CS 3343 Analysis of Algorithms 1 External memory dictionary Task: Given a large amount of data that does not fit into main memory, process it into a dictionary
TREES. Trees - Introduction
 TREES Chapter 6 Trees - Introduction All previous data organizations we've studied are linear each element can have only one predecessor and successor Accessing all elements in a linear sequence is O(n)
TREES Chapter 6 Trees - Introduction All previous data organizations we've studied are linear each element can have only one predecessor and successor Accessing all elements in a linear sequence is O(n)
10.2 AVL Trees. Definition of an AVL Tree. 438 Chapter 10. Search Trees
 438 Chapter 10. Search Trees 10. AVL Trees In theprevioussection,wediscussedwhatshouldbeanefficientmapdatastructure, but the worst-case performance it achieves for the various operations is linear time,
438 Chapter 10. Search Trees 10. AVL Trees In theprevioussection,wediscussedwhatshouldbeanefficientmapdatastructure, but the worst-case performance it achieves for the various operations is linear time,
Section 1: True / False (1 point each, 15 pts total)
 Section : True / False ( point each, pts total) Circle the word TRUE or the word FALSE. If neither is circled, both are circled, or it impossible to tell which is circled, your answer will be considered
Section : True / False ( point each, pts total) Circle the word TRUE or the word FALSE. If neither is circled, both are circled, or it impossible to tell which is circled, your answer will be considered
2-3 and Trees. COL 106 Shweta Agrawal, Amit Kumar, Dr. Ilyas Cicekli
 2-3 and 2-3-4 Trees COL 106 Shweta Agrawal, Amit Kumar, Dr. Ilyas Cicekli Multi-Way Trees A binary search tree: One value in each node At most 2 children An M-way search tree: Between 1 to (M-1) values
2-3 and 2-3-4 Trees COL 106 Shweta Agrawal, Amit Kumar, Dr. Ilyas Cicekli Multi-Way Trees A binary search tree: One value in each node At most 2 children An M-way search tree: Between 1 to (M-1) values
Search Trees. Chapter 11
 Search Trees Chapter 6 4 8 9 Outline Binar Search Trees AVL Trees Spla Trees Outline Binar Search Trees AVL Trees Spla Trees Binar Search Trees A binar search tree is a proper binar tree storing ke-value
Search Trees Chapter 6 4 8 9 Outline Binar Search Trees AVL Trees Spla Trees Outline Binar Search Trees AVL Trees Spla Trees Binar Search Trees A binar search tree is a proper binar tree storing ke-value
Sorting and Searching
 Sorting and Searching Lecture 2: Priority Queues, Heaps, and Heapsort Lecture 2: Priority Queues, Heaps, and Heapsort Sorting and Searching 1 / 24 Priority Queue: Motivating Example 3 jobs have been submitted
Sorting and Searching Lecture 2: Priority Queues, Heaps, and Heapsort Lecture 2: Priority Queues, Heaps, and Heapsort Sorting and Searching 1 / 24 Priority Queue: Motivating Example 3 jobs have been submitted
CS301 - Data Structures Glossary By
 CS301 - Data Structures Glossary By Abstract Data Type : A set of data values and associated operations that are precisely specified independent of any particular implementation. Also known as ADT Algorithm
CS301 - Data Structures Glossary By Abstract Data Type : A set of data values and associated operations that are precisely specified independent of any particular implementation. Also known as ADT Algorithm
DATA STRUCTURES AND ALGORITHMS. Hierarchical data structures: AVL tree, Bayer tree, Heap
 DATA STRUCTURES AND ALGORITHMS Hierarchical data structures: AVL tree, Bayer tree, Heap Summary of the previous lecture TREE is hierarchical (non linear) data structure Binary trees Definitions Full tree,
DATA STRUCTURES AND ALGORITHMS Hierarchical data structures: AVL tree, Bayer tree, Heap Summary of the previous lecture TREE is hierarchical (non linear) data structure Binary trees Definitions Full tree,
