Don't Cares in Multi-Level Network Optimization. Hamid Savoj. Abstract
|
|
|
- Hillary Wiggins
- 6 years ago
- Views:
Transcription
1 Don't Cares in Multi-Level Network Optimization Hamid Savoj University of California Berkeley, California Department of Electrical Engineering and Computer Sciences Abstract An important factor in the optimization of a multi-level circuit, modeled as a Boolean network, is to compute the exibility for implementing each node of the network and to exploit this exibility to get a better functional implementation at that node. The most general form for describing input-output behavior of a Boolean network is to use a Boolean relation. This relation or a subset of it, is then used to compute the exibility for implementing each node in the network. The nodes in the network can be either single or multiple output. In the case of a network composed of single-output nodes, this exibility is captured by don't cares. Techniques for computing both maximum and compatible don't care sets for each node are presented. In the case of multi-output nodes, don't cares are not sucient to express input-output behavior of the node. Thus, we present techniques to compute maximal and compatible exibility at multi-output nodes using Boolean relations. The current model for representing a Boolean circuit uses single output nodes. We present ecient techniques for single-output node simplication that use don't cares in terms of the fanins of node being simplied. The don't care set in terms of fanins of a node is called the local don't care set for that node; it usually has a small size and can be used to remove all the redundancies within that node. Practical issues for computing local don't cares and simplifying nodes are discussed in detail and experimental results are presented that show the eectiveness of the approach. New scripts are designed for technology independent optimization of Boolean circuits which use these new techniques. Finally, a new Boolean matching algorithm is presented that can match two functions with given don't care sets. To prove the eectiveness of the approach, this algorithm is used within a technology mapper where matches are sought between subfunctions in the network and sets of gates in the library. The symmetries of the gates in the library are used to speed up the matching process. Prof. Robert K. Brayton Thesis Committee Chairman
2 Don't Cares in Multi-Level Network Optimization Copyright c 1992 Hamid Savoj
3 Contents Table of Contents List of Figures List of Tables i v vii 1 Introduction CAD for VLSI : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Logic Synthesis : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Transformations : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Flexibility in Node Implementation : : : : : : : : : : : : : : : : : : : Overview : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : 5 2 Terminology and Background Boolean Functions and Boolean Networks : : : : : : : : : : : : : : : : : : : Boolean Functions : : : : : : : : : : : : : : : : : : : : : : : : : : : : Boolean Network : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Set Operations and BDD's : : : : : : : : : : : : : : : : : : : : : : : : : : : : Binary Decision Diagrams : : : : : : : : : : : : : : : : : : : : : : : : Consensus Operator : : : : : : : : : : : : : : : : : : : : : : : : : : : Smoothing Operator : : : : : : : : : : : : : : : : : : : : : : : : : : : Boolean Dierence : : : : : : : : : : : : : : : : : : : : : : : : : : : : Image and Inverse Image Computations : : : : : : : : : : : : : : : : : : : : The Generalized Cofactor : : : : : : : : : : : : : : : : : : : : : : : : The Transition Relation Method : : : : : : : : : : : : : : : : : : : : The Recursive Image Computation Method : : : : : : : : : : : : : : Observability Relations : : : : : : : : : : : : : : : : : : : : : : : : : : : : : 21 3 Don't Care Conditions for Single-Output Nodes Introduction : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Don't Cares in a Boolean Network : : : : : : : : : : : : : : : : : : : : : : : Satisability Don't Cares : : : : : : : : : : : : : : : : : : : : : : : : Observability Don't Cares : : : : : : : : : : : : : : : : : : : : : : : : External Don't Cares : : : : : : : : : : : : : : : : : : : : : : : : : : 28 i
4 ii CONTENTS Terminology : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Observability Network : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Computing ODC's : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : A New Approach : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Deriving Damiani's Formula : : : : : : : : : : : : : : : : : : : : : : : Using the Observability Relation : : : : : : : : : : : : : : : : : : : : Observability Don't Care Subsets : : : : : : : : : : : : : : : : : : : : : : : : Compatible Observability and External Don't Cares : : : : : : : : : CODC's for Trees : : : : : : : : : : : : : : : : : : : : : : : : : : : : CODC's for a General Network : : : : : : : : : : : : : : : : : : : : : ODC's and Equivalence Classes of a Cut : : : : : : : : : : : : : : : : : : : : 51 4 Observability Relations for Multi-Output Nodes Previous Work : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Two-Way Partitioning of a Boolean Relation : : : : : : : : : : : : : : : : : Serial Decomposition : : : : : : : : : : : : : : : : : : : : : : : : : : : Parallel Decomposition : : : : : : : : : : : : : : : : : : : : : : : : : Compatible and Maximal Observability Relations : : : : : : : : : : : : : : : Node Optimization Using Maximal Observability Relations : : : : : Node Optimization Using Compatible Observability Relations : : : : Conclusion : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : 71 5 Node Simplication: Practical Issues Introduction : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Node Simplication : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Using Don't Cares : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Computing Local Don't Cares : : : : : : : : : : : : : : : : : : : : : : : : : : Implementation : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : External Don't Cares : : : : : : : : : : : : : : : : : : : : : : : : : : Inverse of Boolean Dierence : : : : : : : : : : : : : : : : : : : : : : Computing Observability and External Don't Cares at Each Node : Filtering : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Computing the Image : : : : : : : : : : : : : : : : : : : : : : : : : : Conclusion : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : 91 6 Scripts for Technology Independent Optimization Introduction : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Scripts Used for Logic Minimization : : : : : : : : : : : : : : : : : : : : : : Kernel and Cube Extraction : : : : : : : : : : : : : : : : : : : : : : Simplication : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Elimination : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Scripts : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Experimental Results : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Area Optimization : : : : : : : : : : : : : : : : : : : : : : : : : : : : Sequential Optimization : : : : : : : : : : : : : : : : : : : : : : : : : 108
5 CONTENTS iii Testability : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Conclusion : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Boolean Matching in Logic Synthesis Introduction : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Boolean Matching : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Boolean Matching for Technology Mapping : : : : : : : : : : : : : : : : : : Generating all Supports : : : : : : : : : : : : : : : : : : : : : : : : : Boolean Matching Algorithm : : : : : : : : : : : : : : : : : : : : : : Symmetries : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Heuristic : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Don't Care Computation : : : : : : : : : : : : : : : : : : : : : : : : : : : : Library Organization : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Results : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Conclusion : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Conclusions 131 Bibliography 133
6 iv CONTENTS
7 List of Figures 2.1 Binary Decision Diagram : : : : : : : : : : : : : : : : : : : : : : : : : : : : Generalized Cofactor : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Example : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Example : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : A Separating Set of Nodes : : : : : : : : : : : : : : : : : : : : : : : : : : : : Example : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Example : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : A Directed Tree : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Example : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Example : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Decomposition of Observability Relation : : : : : : : : : : : : : : : : : : : : Observability Relation for a Cut : : : : : : : : : : : : : : : : : : : : : : : : Example : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Example : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Observability Network for a Network of Multi-Output Nodes : : : : : : : : Maximal Observability Relation Computation and Node Simplication : : : Compatible Observability Relation Computation and Node Simplication : Node Simplication : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Input to Two-Level Minimizer : : : : : : : : : : : : : : : : : : : : : : : : : : Input to Two-Level Minimizer : : : : : : : : : : : : : : : : : : : : : : : : : : don't care computation and node simplication : : : : : : : : : : : : : : : : Berkeley Logic Interchange Format : : : : : : : : : : : : : : : : : : : : : : : don't care computation and node simplication : : : : : : : : : : : : : : : : An Intermediate Node : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Range Computation Algorithm : : : : : : : : : : : : : : : : : : : : : : : : : Partition into Groups with Disjoint Support : : : : : : : : : : : : : : : : : : Simplication Script Using fast extract : : : : : : : : : : : : : : : : : : : : : Simplication Script Using Kernel Extraction : : : : : : : : : : : : : : : : : Generating Supports : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : 122 v
8 vi LIST OF FIGURES 7.2 Boolean Matching : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : Cluster Functions : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : 126
9 List of Tables 6.1 Performance of Scripts Starting from Multi-Level Circuits : : : : : : : : : : Performance of Scripts Starting from PLA's : : : : : : : : : : : : : : : : : : Comparison of Algebraic Extraction Techniques : : : : : : : : : : : : : : : : Performance of the Scripts on Sequential Circuits : : : : : : : : : : : : : : : Performance on Testability : : : : : : : : : : : : : : : : : : : : : : : : : : : Boolean Matching for Technology Mapping : : : : : : : : : : : : : : : : : : 130 vii
10 viii LIST OF TABLES
11 Chapter 1 Introduction Computer Aided Design (CAD) tools are used in many elds of science to cope with the complexity in the analysis or synthesis of systems. CAD tools have been developed to help chemists and biologist to study the structure of molecules, nd common sub-structures among them, and predict their activities. CAD tools have also been used to analyze and predict the behavior of nancial markets based on statistical models. Finally, CAD tools have been employed to automate the design of VLSI circuits. This dissertation focuses on new techniques for automated synthesis of logic circuits, which is a major division of CAD for VLSI circuits. 1.1 CAD for VLSI The objective of VLSI CAD is to automate the design of VLSI systems. The starting point is usually a description of a system in a high-level language like ELLA [56] or VHDL [64]. The result of the design process is a layout description of that system which can be implemented as a set of integrated circuits in one or more technologies. This process is usually divided into four steps because the problem is too complex to be handled all at once. These steps are high-level synthesis, logic synthesis, physical design, and fabrication and test. A design may have to go through many iterations in one or more of the above steps before it meets the required specication. In some applications, CAD tools are employed starting at logic or physical design level. This is the case when a design in an old technology is converted into a new technology. We discuss the steps in VLSI design using the order in which they are applied. 1
12 2 CHAPTER 1. INTRODUCTION High-level synthesis generates a register-transfer level structure from a behavioral description which realizes the given behavior. The temporal scheduling of operations and allocation of hardware are among the issues considered at this stage. Behavioral synthesis tools [38, 62, 83, 85, 87] can be used to reduce the amount hardware while meeting the required performance constraints. The next step is logic synthesis, where the register transfer structure is transformed into a netlist of gates in a given technology. Optimization techniques are applied to improve the area, performance, and testability of the circuit at this stage. Our focus is on new sets of optimization techniques that can be applied during logic synthesis. The third step, physical design provides the physical realization of a net-list on a chip and includes placement, routing, and geometric artwork [16, 75, 65, 88]. As in logic synthesis, the objective is to nd a layout with the best area and/or performance. The nal step is fabrication and test where mask-making, fabrication, and performance test is done. Some manufactured circuits are defective because manufacturing processes cannot guarantee 100% yield. It is important to separate defective circuits from the proper ones. To detect defective circuits, test patterns are applied to the circuit and the response is compared with the expected response. Test pattern generation has been investigated for many years [2, 33, 36, 45, 49, 35, 74]. While synthesizing a given specication at higher level of the design, one may estimate some information from the lower levels of the design to produce a better design. For example, one may use placement and routing information during logic synthesis [63, 1]. Partitioning of a VLSI system and handling hierarchies are hard problems that need to be dealt with at all levels [29, 30, 8]. Formal verication is another area of interest where a given high-level specication of a circuit is checked for some desired behavior before any implementation is done [20, 44, 79]. This area has received considerable attention lately. 1.2 Logic Synthesis Logic synthesis is the process of transforming a set of Boolean functions, obtained from the register transfer level structure, into a network of gates in a particular technology, while optimizing the network for performance, area, and/or testability. The best implementation of a functional specication is usually in multi-level logic. The model used for representing multiple levels of logic is a directed acyclic graph with single-output nodes, called a Boolean network, where each node of the network is a logic function itself. A set
13 1.2. LOGIC SYNTHESIS 3 of transformations are applied to the logic network to nd the best set of nodes which give the desired input-output behavior Transformations The synthesis process is usually divided into technology independent and technology dependent phases [10, 7]. The objective of the technology independent phase is to simplify the logic as much as possible, while the main role of the technology dependent phase is to implement the logic network using a set of well characterized gates. In [47], it was shown experimentally that the layout area of a Boolean network implementation in standard cells correlates well with the number of literals used for representing that network in factored form (dened in [10]). This measure is used in the technology independent stage because it helps to reduce the size of the nodes in the network and therefore, the amount of logic used. After a circuit is optimized for literals in factored form, additional transformations can be applied to optimize performance, or to tune the circuit for eventual implementation in a particular technology such as, Field Programmable Gate Arrays [40, 4]. A network optimized for literals in factored form is a good starting point for these other manipulations. When the amount of logic used is reduced, there are less gates to be placed on a chip and fewer nets to be routed. As a result, performance is also improved in most cases. In the same way, a circuit can be implemented on an FPGA chip using fewer blocks, if the amount of logic is reduced. An important transformation to reduce the number of levels in factored form is to apply a two-level logic minimizer to each node of the multi-level network to optimize the two-level function associated with the node. The input supplied to a two-level minimizer is the onset and the don't care set of the node. The onset gives the function of the node in terms of its fanins. The don't care set gives the exibility in implementing the node, and is a combination of structural don't cares and external don't cares supplied by the user. In the technology dependent stage, transformations are applied to implement and optimize logic for a particular technology. For standard cells, the most common approach decomposes the circuit into a set of trees and then maps each tree into a set of library gates [43, 66]. For the Xilinx FPGA architecture, the Boolean network is decomposed into a set of nodes where each node has less than 5 inputs; therefore, it can be directly mapped into a logic block [58, 59]. Don't care conditions can be used to improve the quality of the mapped
14 4 CHAPTER 1. INTRODUCTION circuits Flexibility in Node Implementation This thesis contributes to the understanding and ability to use don't care sets and Boolean relations to manipulate Boolean networks. Don't cares are used to nd the maximum exibility for implementing nodes of a network decomposed into single-output nodes. The don't care set at each node is a combination of external, observability, and satisability don't cares. The external don't care set for a network is a restricted form for expressing the freedom in input-output behavior of that network. These are input conditions under which the value of a particular output is not important. The observability and satisability don't cares are related to the structure of the network. The observability don't cares are conditions under which the value of a node is not observable at any of the outputs. Satisability don't cares are related to the functions at the nodes of the network. Each intermediate node of a Boolean network gets a value of 1 or 0 for a particular input. Some combinations are impossible in the Boolean space of intermediate nodes and primary inputs of the network; satisability don't cares capture all such impossible combinations. A Boolean network can be also decomposed into a set of multi-output nodes. This is very useful for data path synthesis where the circuit has many multi-output blocks like multipliers and adders. These blocks must be recognized and mapped into corresponding multi-output gates in the library. The maximum exibility for implementing a multi-output node is captured by a Boolean relation which gives the set of outputs possible for any particular input pattern to the node. A Boolean network is a multi-output node itself, and external don't cares are not sucient to express the maximum exibility for implementing it. Thus Boolean relations must be used to express the input-output behavior of a Boolean network. Such a relation is called an observability relation. The use of the observability relation allows the denition and computation of maximum exibility in implementing multi-output nodes in a Boolean network. An interesting concept which applies to both don't cares and Boolean relations is the concept of compatibility. In general, the exibility in implementing a node in the network aects the exibility in implementing other nodes in the network; therefore, if the function at a node is changed, don't care sets or Boolean relations at other nodes in the network have to be updated. The updating process can be costly. It is possible to order all
15 1.3. OVERVIEW 5 the nodes in the network and compute compatible exibilities according to the ordering. In this manner, all the nodes in the network can be optimized simultaneously. Furthermore, once the function at a node is changed, the exibility for implementing other nodes in the network need not be recomputed. 1.3 Overview Chapter 2 presents some basic denitions used throughout this thesis. It also contains the denition of generalized cofactor and its properties. Finally, it discusses different methods for image computation and explains shortcomings and advantages of each approach. Chapter 3 discusses maximum exibility for implementing nodes of a Boolean network decomposed into single-output nodes. The exibility for a single-output node can be computed in the form of don't cares. We discuss dierent kinds of don't cares and techniques for computing a full don't care set and approximate don't care sets at a particular node. The input-output behavior of the network itself is expressed by a Boolean relation because it can be viewed as a multi-output node. This relation is represented by a node attached to the top of the original network. This new network is called the observability network. We develop techniques for computing full and compatible don't cares from the observability network. Techniques for computing compatible and maximal Boolean relations for a network decomposed into multi-output nodes are developed in Chapter 4. We rst discuss the parallel and serial decomposition of Boolean relations and then expand this to a general decomposition into multi-output nodes. Chapter 5 discusses the practical issues in using local don't cares for the simplication of single-output nodes in a multi-level network. The algorithms used for local don't care computation are discussed in detail. The extensions to BLIF for representing external don't cares are discussed in this chapter. Chapter 6 discusses scripts used for technology independent optimization. The algorithms used within these scripts are discussed and improvements are provided which enable the application of these algorithms to larger circuits. Experiments are run on a large set of benchmark circuits to show the eectiveness of these improved scripts for reducing the amount of logic used and removing redundancies in each circuit.
16 6 CHAPTER 1. INTRODUCTION Finally, we discuss Boolean matching in Chapter 7 and show how this can be used for technology mapping. The tree matching algorithm used to match a subfunction in the network with a gate in the library, is replaced by Boolean matching. The symmetries of the gates in the library are found and used to speed up the matching process. Gates in the library are grouped into sets using the same Boolean matching algorithm, where it is enough to check the existence of a match of a subfunction in the network with a set representative.
17 Chapter 2 Terminology and Background The purpose of this chapter is to introduce some basic denitions and concepts that are essential for describing the work presented in this thesis. 2.1 Boolean Functions and Boolean Networks Boolean Functions Denition A completely specied Boolean function f with n inputs and l outputs is a mapping f : B n 0! B l where B = f0; 1g. In particular, if l = 1 the onset and oset of f are onset = fm 2 B n j f(m) = 1g oset = fm 2 B n j f(m) = 0g Denition Any vertex in B n is also called a minterm. A minterm of a function f is a vertex m such that f(m) = 1. Denition An incompletely specied Boolean function F with n inputs and l outputs is a mapping F : B n 0! Y l 7
18 8 CHAPTER 2. TERMINOLOGY AND BACKGROUND where Y = f0; 1; 3g. The onset, oset, and don't care set (dcset) of F : B n 0! Y are, onset = fm 2 B n j F(m) = 1g oset = fm 2 B n j F(m) = 0g dcset = fm 2 B n j F(m) = 3g: The symbol 3 implies that the function can be either 0 or 1. Denition A cover for the incompletely specied function F : B n 0! Y is any completely specied function f such that f(m) = 1 if F(m) = 1, f(m) = 0 if F(m) = 0, and f(m) = 0 or 1 if F(m) = 3. F : B n 0! Y is usually described by two completely specied functions f and d where f is a cover for F and d(m) = 1 if F(m) = 3, and 0 otherwise. Alternately, F can be described as F = (f; d; r) where f; d; r are respectively the onset, don't care set, and oset. Let x 1 ; x 2 ; : : :; x n be the variables of the space B n. We use x to represent a vertex or a vector of variables in B n. Denition Let A B n. The characteristic function of A is the function f : B n! B dened by f(x) = 1 if x 2 A, f(x) = 0 otherwise. Characteristic functions are nothing but a functional representation of a subset of a set. Any completely specied function f : B n 0! B is a characteristic function for its onset. Denition A literal is a variable in its true or complement form (e.g.x i, or x i ). A product term or cube is the conjunction of some set of literals (e.g. x 1 x 2 x 3 ). Denition A cube c is called a prime cube of F if c f [ d and there is no cube c 0 such that c c 0 f [ d. Denition The distance between two cubes denoted as dist(c 1 ; c 2 ) is the number of literals in which c 1 contains the complement literal of c 2. Two cubes c 1 and c 2 are called orthogonal if dist(c 1 ; c 2 ) 1 (e.g. x 1 x 2 x 3 is orthogonal to x 1 x 2 and of distance 1). The onset, don't care set, and oset of an incompletely specied function F : B n 0! Y can each be represented by the union of some set of cubes. This representation is called a sum-of-products form.
19 2.1. BOOLEAN FUNCTIONS AND BOOLEAN NETWORKS 9 Denition Let f : B n! B be a Boolean function, and x i an input variable of f. The cofactor of f with respect to a literal x i (x i ), shown as f xi (f xi ), is a new function obtained by substituting 1(0) for x i (x i ) in every cube in f which contains x i (x i ). Denition Let f : B n! B be a Boolean function, and x i an input variable of f. f is monotone increasing in a variable x i if f xi f xi. A function f is monotone decreasing in a variable x i if f xi f xi. f is unate in variable x i if it is monotone increasing or decreasing in that variable. f is a unate function if it is unate in all its input variables. A function is independent of x i if f xi = f xi. Denition Let f : B n! B be a Boolean function, and x i an input variable of f. The Shannon's expansion of a Boolean function f with respect to a variable x i is x i f xi + x i f xi : Lemma f = x i f xi + x i f xi. The iterated Shannon decomposition of a Boolean function is a Binary tree representing the function obtained by applying Shannon's expansion with respect to all the variables. The leaves are either 0 or 1. Each path of the tree represents a minterm of the function Boolean Network Denition A Boolean network N, is a directed acyclic graph (DAG) such that for each node in N there is an associated representation of a Boolean function f i, and a Boolean variable y i, where y i = f i. There is a directed edge (i; j) from y i to y j if f j depends explicitly on y i or y i. A node y i is a fanin of a node y j if there is a directed edge (i; j) and a fanout if there is a directed edge (j; i). A node y i is a transitive fanin of a node y j if there is a directed path from y i to y j and a transitive fanout if there is a directed path from y j to y i. Primary inputs x = (x 1 ; : : :; x n ) are inputs of the Boolean network and primary outputs z = (z 1 ; : : :; z m ) are its outputs. Intermediate nodes of the Boolean network have at least one fanin and one fanout. The global function f g i in terms of primary inputs. at y i is the function at the node expressed We sometimes represent the local function at y i by f l i global function f g i. to make a clear distinction with the
20 10 CHAPTER 2. TERMINOLOGY AND BACKGROUND Denition The cofactor of N with respect to y i denoted by z yi is a new network obtained from N by disconnecting the output edges of y i from y i and forcing each output edge equal to 1. The cofactor of N with respect to y i denoted by z yi is a new network obtained from N by disconnecting the output edges of y i from y i and forcing each output edge equal to 0. Example: If N has only one output z, z yi z yi is a new network representing the function obtained by ANDing outputs of z yi and z yi. z yi z yi gives conditions under which the value of y i can be changed from 0 to 1 or vice versa but output z remains equal to 1. This computation is important while computing observability don't cares discussed in Chapter 3. Denition The support of a function f is the set of variables that f explicitly depends on. Example: The support of f = x 1 x 2 + x 2 x 3 is fx 1 ; x 2 ; x 3 g. Denition Nodes of a network are topologically ordered from outputs if each node appears somewhere after all its fanouts in the ordering. They are topologically ordered from inputs if each node appears somewhere after all its fanins in the ordering. 2.2 Set Operations and BDD's Binary Decision Diagrams Binary Decision Diagrams [14] are compact representations of recursive Shannon decompositions. The decomposition is done with the same order along every path from the root to the leaves as shown in Figure 2.1. BDD's are unique for a given variable ordering and hence are canonical forms for representing Boolean functions. They can be constructed from the Shannon's expansion of a Boolean function by 1) deleting a node whose two child edges point to the same node, and 2) sharing isomorphic subgraphs. Technically the result is a reduced ordered BDD, (ROBDD), which we shall just call BDD. Example: Figure 2.1 shows the Shannon decomposition of f = x 1 x 3 + x 1 x 3 with the ordering x 1
21 2.2. SET OPERATIONS AND BDD'S 11 x f = x x + x x2 x x 2 x x 3 x 3 x 3 x x 2 x Figure 2.1: Binary Decision Diagram x 2 x 3 and the corresponding BDD. The unreduced one is on the left, the reduced one on the right. An example of reduction is the merging of the two right most nodes which represent the same function, namely x 3. Then the x 2 node above them has both of its children with the same node and thus can be eliminated Consensus Operator Denition Let f : B n! B be a Boolean function, and x = (x i1 ; : : : ; x ik ) a set of input variables of f. The consensus of f by x is C x f = C xi1 : : :C xik f C xij f = f xij f xij This is also the largest Boolean function contained in f which is independent of x i1 ; : : :; x ik Smoothing Operator Denition Let f : B n! B be a Boolean function, and x = (x i1 ; : : : ; x ik ) a set of input variables of f. The smoothing of f by x is S x f = S xi1 : : :S xik f S xij f = f xij + f xij If f is interpreted as the characteristic function of a set, the smoothing operator computes the projection of f to the subspace of B n orthogonal to the domain of the x variables. This is also the smallest Boolean function independent of x i1 ; : : :; x ik which contains f.
22 12 CHAPTER 2. TERMINOLOGY AND BACKGROUND Lemma Let f : B n 2 B m! B and g : B m! B be two Boolean functions. Then: Boolean Dierence S x (f(x; y)g(y)) = S x (f(x; y))g(y) (2.1) Let f : B n! B be a Boolean function, and x i an input variable of f. The Boolean dierence of a function f with respect to a variable x i is i f xi f xi + f xi f xi This function gives all the conditions under which the value of f is inuenced by the value of x i. Its complement therefore is all the conditions under which f is insensitive to x i. The concept of Boolean dierence of a Boolean function with respect to a variable is very similar to the concept of partial derivative of a real function with respect to a variable. Example: Let f = x 1 x 3 + x 2 x 3. Then, a 3 = x 1 x 2 + x 1 x 2. Notice that if x 1 = 0 and x 2 = 1, 3, f = x 3. As a result, the value of f is sensitive to x 3. In the same way, if x 1 = 1 and x 2 = 0, f = x 3 and the vlaue of f changes with the value of x Image and Inverse Image Computations Denition Let f : B n! B m be a Boolean function and A a subset of B n. The image of A by f is the set f(a) = fy 2 B m j y = f(x); x 2 Ag. If A = B n, the image of A by f is also called the range of f. Denition Let f : B n! B m be a Boolean function and A a subset of B m. The inverse image of A by f is the set f 01 (A) = fx 2 B n j f(x) = y; y 2 Ag. Example: Let f(x; i) : B n 2 B k! B n be the next state function of a nite state machine, where n is the number of state variables and k the number of input variables. Let c 1 be the set of states reachable from a set of initial states c 0. c 1 can be obtained by repeated computation of an image as follows c i+1 = c i [ f(c i 2 B k ) c 1 = c i if c i+1 = c i
23 2.3. IMAGE AND INVERSE IMAGE COMPUTATIONS 13 The sequence is guaranteed to converge after a nite number of iterations because fc i g is monotone increasing and the number of states is nite The Generalized Cofactor The generalized cofactor is an important operator that can be used to reduce an image computation to a range computation. This operator was initially proposed by Coudert et al. in [21] and called the constraint operator. Given a Boolean function: f = (f 1 ; : : :; f m ) : B n! B m and a subset of B n represented by its characteristic function h, the generalized cofactor f h = ((f 1 ) h ; : : :; (f m ) h ) is one of many functions from B n to B m whose range is equal to the image of h by f. An important property of this function is that f h (x) = f(x) if h(x) = 1. In addition, in most cases, the BDD representation of f h is smaller than the BDD representation of f. Given a cover f : B n! B for the onset and don't care set d : B n! B of an incompletely specied function F, the function f d has the property that f 0 d f d f + d; therefore f d is also a cover of F = (f d; d; f d). This is beacsue f d gives the same values as f for any minterm in d. In practice the size of the BDD for f d is usually smaller than that of f [81]. As a result, this is an eective way to get a cover with smaller BDD size. The generalized cofactor f h depends in general on the variable ordering used in the BDD representation. Denition Let h : B n! B be a non-null Boolean function and x 1 x 2 : : : x n an ordering of its input variables. We dene the mapping h : B n! B n as follows: h (x) = x if h(x) = 1 h (x) = arg min h(y)=1 d(x; y) if h(x) = 0 where d(x; y) = X 1in jx i 0 y i j2 n0i Lemma h is the projection that maps a minterm x to the minterm y in the onset of h which has the closest distance to x according to the metric d. The particular form of the distance metric guarantees the uniqueness of y in this denition, for any given variable ordering. Proof Let y and y 0 be two minterms in the onset of h such that d(x; y) = d(x; y 0 ). Each of the expressions d(x; y) and d(x; y 0 ) can be interpreted as the binary representation of
24 14 CHAPTER 2. TERMINOLOGY AND BACKGROUND some integer. Since the binary representation is unique, jx i 0 y i j = jx i 0 y 0 ij for 1 i n and thus y = y 0. Lemma Let h have the support x (h does not depend on y variables). There is a vertex x 0 such that h (x; y) = (x 0 ; y) for any ordering of variables x and y. Proof Any vertex (x; y) must be mapped to the closest vertex (x 0 ; y 0 ) to it according to metric d such that h(x 0 ; y 0 ) = 1. y 0 6= y is not possible because (x 0 ; y) is closer to (x; y) than (x 0 ; y 0 ) and h(x 0 ; y) = 1. Denition Let f : B n! B and h : B n! B, with h 6= 0. The generalized cofactor of f with respect to h, denoted by f h, is the function f h = f h, i.e. f h (x) = f( h (x)). If f : B n! B m, then f h : B n! B m is the function whose components are the cofactors by h of the components of f. If c is a cube the generalized cofactor f c is equal to the usual cofactor of a Boolean function, and is, in that case, independent of the variable ordering. Lemma If h is a cube (i.e. c = c 1 c 2 : : :c n where c i = f0; 1; 3g), c is independent of the variable ordering. More precisely, y = c (x) satises y i = 0 if c i = 0 y i = 1 if c i = 1 y i = x i if c i = 3 and f c = f c is the usual cofactor of a Boolean function by a cube. Proof Any minterm y 0 in B n such that c(y 0 ) = 1 is orthogonal to x in at least the same variables as y. Thus y minimizes d(x; y) over c. In addition, the generalized cofactor preserves the following important properties of cofactors: Lemma Let g : B m! B and f : B n! B m. Then (g f) h = g f h. In particular the cofactor of a sum of functions is the sum of the cofactors, and the cofactor of an inverse is the inverse of the cofactor (e.g. f = [f 1 ; f 2 ] and g = f 1 + f 2, then g h = f 1h + f 2h ).
25 2.3. IMAGE AND INVERSE IMAGE COMPUTATIONS 15 Proof (g f) h = (g f) h and g f h = g (f h ). Lemma Let f : B n 2 B m! B and h : B n! B be two Boolean functions, with h 6= 0. Then: S x (f(x; y) 1 h(x)) = S x (f h (x; y)) (2.2) Proof For every vertex x 2 B n if h(x) = 1, then f h (x; y) = f(x; y). This is from the denition of generalized cofactor. If h(x) = 0, then f(x; y)h(x) = 0. Therefore, f(x; y)h(x) f h (x; y) and S x (f(x; y)h(x)) S x (f h (x; y)). Conversely, if vertex y 2 B m is such that S x (f h (x; y)) = 1, there exists an x for which f h (x; y) = 1 and therefore there exists an x 0 such that f(x 0 ; y) = 1 and h(x 0 ) = 1. This is because f h (x; y) = f h (x; y) and h is dependent only on x variables; therefore for each vertex (x; y), f h (x; y) = f(x 0 ; y) and h(x 0 ) = 1 from Lemma This gives S x (f h (x; y)) S x (f(x; y)h(x)) and the statement of the Lemma follows. Lemma Let f be a Boolean function, and h a non-null Boolean function. Then h is contained in f if and only if f h is a tautology. Proof Suppose that h is contained in f. Let x be an arbitrary minterm. y = h (x) implies h(y) = 1. Since h ) f, f h (x) = f(y) = 1. Thus f h is a tautology. Conversely, suppose that f h is a tautology. Let x be such that h(x) = 1. Then h (x) = x and f(x) = f( h (x)) = f h (x) = 1, which proves that h is contained in f. Lemma If h is the characteristic function of a set A then f h (B n ) = f(a); that is the image of A by f is equal to the range of the cofactor f h. Proof h (B n ) is equal to the onset of h, which is A. Thus f h (B n ) = f h (B n ) = f(a). The generalized cofactor can be computed very eciently in a single bottom-up traversal of the BDD representations of f and h by the algorithm given in Figure 2.2. Theorem f h gcofactor(f; h).
26 16 CHAPTER 2. TERMINOLOGY AND BACKGROUND function gcofactor(f, h) f assert (h 6= 0) ; if (h = 1 or is constant(f)) return f; else if (h x1 = 0) return gcofactor(f x1 ; h x1 ); else if (h x1 = 0) return gcofactor(f x1 ; h x1 ); else return x 1 gcofactor(f x1 ; h x1 ) + x 1 gcofactor(f x1 ; h x1 ); g Figure 2.2: Generalized Cofactor Proof Let the variable ordering be x 1 : : : x n, and x = x 1 : : :x n 2 B n be a particular vertex. We compute the value of the function gcofactor(f; h) for the particular x (shown as [gcofactor(f; h)](x) ) and show that it is equal to f h (x) irrespective of the choice of x. Assume h and f are not constants. The proof in such cases is trivial. If h(x) = 1, it follows from Figure 2.2 that gcofactor(f; h) = x 1 gcofactor(f x1 ; h x1 ) because h x1 6= 0. We are not interested in the x 1 gcofactor(f x1 ; h x1 ) becuase it gives 0 for the vertex x. In the ith step, if neither f x1 :::x i nor h x1 :::x i is a constant, x 1 : : :x i gcofactor(f x1 :::x i ; h x1 :::x i ) = x 1 : : : x i+1 gcofactor(f x1 :::x i+1 ; h x1 :::x i+1 ) because h x1 :::x i+1 6= 0. Eventually either f x1 :::x j becomes constant or h x1 :::x j = 1. In either case, the returned function is x 1 : : : x j f x1 :::x j which is equal to x 1 : : : x j f. As a result, [gcofactor(f; h)](x) = x 1 : : : x j f(x) = f(x). The same reasoning holds for any x such that c(x) = 1; therefore, f h (x) [gcofactor(f; h)](x), if h(x) = 1. If h(x) = 0, the computation is as before as long as h x1 :::x i01 6= 0. If h x1 :::x i = 0, it follows from Figure 2.2 that x 1 : : : x i01 gcofactor(f x1 :::x i01 ; h x1 :::x i01 ) = x 1 : : : x i01 gcofactor(f x1 :::x i ; h x1 :::x i ): Eventually, either f x1 :::x i :::x j becomes constant or h x1 :::x i :::x j = 1 in the jth iteration. In either case, the part of the returned function which is of interest is x 1 : : :x i01 x i+1 : : : x j f x1 :::x i :::x j. If c = x 1 : : : x i01 x i+1 : : :x j, then the returned expression can be written as cf c. The value of [gcofactor(f; h)](x) = [x 1 : : : x i01 x i+1 : : :x j f x1 :::x i :::x j ] x which is f x1 :::x i :::x j x j+1 :::x n. We
27 2.3. IMAGE AND INVERSE IMAGE COMPUTATIONS 17 prove that the closest vertex x 0 to x such that h(x 0 ) = 1 is in the cube c = x 1 : : : x i : : : x j. Because h x1 :::x i01 6= 0, the closest vertex x 0 to x (distance is dened by Denition 2.3.3) such that h(x 0 ) = 1 must have literals x 1 ; : : :; x i01. Because h x1 :::x i = 0, the closest vertex x 0 to x such that h(x 0 ) = 1 must have literals x 1 ; : : :; x i01 ; x i. This same reasoning holds for any other literal in c, therefore x 0 must have all the literals in c. If c = 1, x 1 : : : x i : : : x j x j+1 : : :x n is the closest vertex to x and f h (x) [gcofactor(f; h)](x). If c 6= 1, f c must be constant to terminate the algorithm in Figure 2.2. f c has the same value for all the vertices in c and again f h (x) [gcofactor(f; h)](x). This same reasoning holds for any x such that h(x) = 0. The next example shows that the BDD size of f h is not always smaller than the BDD size of f. Example: Let f = x 2 + x 3, h = x 1 + x 2, and the ordering used for computing generalized cofactor be x 1 x 2 x 3. gcofactor(f; h) = x 1 gcofactor(x 2 + x 3 ; 1) + x 1 gcofactor(x 2 + x 3 ; x 2 ). This gives f h = gcofactor(f; h) = x 1 x 2 + x 3. The BDD for f h with the given ordering has 3 nodes while the BDD for f has 2 nodes The Transition Relation Method Denition Let f : B n! B m be a Boolean function. The transition relation associated with f, F : B n 2 B m! B, is dened as F (x; y) = f(x; y) 2 B n 2 B m j y = f(x)g. Equivalently, in terms of Boolean operations: F (x; y) = Y 1im (y i 8f i (x)) (2.3) We can use F to obtain the image by f of a subset A of B n, by computing the projection on B m of the set F \ (A 2 B m ). In terms of BDD operations, this is achieved by a Boolean and and a smooth. The smoothing and the Boolean and can be done in one pass on the BDD's to further reduce the need for intermediate storage [15]: f(a)(y) = S x (F (x; y) 1 A(x)) (2.4) The inverse image by f of a subset A of B m can be computed as easily: f 01 (A)(x) = S y (F (x; y) 1 A(y)) (2.5)
28 18 CHAPTER 2. TERMINOLOGY AND BACKGROUND The transition relation method allows both image and inverse image computation for a function f. However, computing the transition relation may require too much memory to be feasible in some examples. We do not need to compute the transition relation explicitly to perform an image computation as in equation 2.4. Using propositions and 2.3.5, we can rewrite equation 2.4 as follows: S x (F (x; y) 1 A(x)) = S x ( Y 1im y i 8f ia(x) ) One ecient way to compute the product is to decompose the Boolean AND of the m functions (g i (x; y) = y i 8f ia(x) ) into a balanced binary tree of Boolean AND's. Moreover, after computing every binary and p of two partial products p 1 and p 2, we can smooth the x variables that only appear in p. As for equation 2.4, the smoothing and the AND computations can be done in one pass on the BDD's to reduce storage requirements The Recursive Image Computation Method Coudert et al. [21, 22] introduced an alternate procedure to compute the image of a set by a Boolean function that does not require building the BDD for the transition relation. This procedure relies on lemma to reduce the image computation to a range computation, and proceeds recursively by cofactoring by a variable of the input space or the output space. We use range(f) to denote the range of a multiple output function f = [f 1 ; : : :; f m ]. There are two techniques for doing this range computation. The rst is input cofactoring where output functions are cofactored with respect to inputs only. range(f)(y) = range([f 1 ; : : :; f m ] x1 ) + range([f 1 ; : : :; f m ] x1 ) The second technique is output cofactoring where output functions are cofactored with respect to other functions. range(f)(y) = range([f 1 ; f 2 ; : : :; f m ] f1 ) + range([f 1 ; f 2 ; : : : ; f m ] f1 ) = range([1; f 2 ; : : : ; f m ] f1 ) + range([0; f 2 ; : : :; f m ] f1 ) = y 1 range([f 2 ; : : :; f m ] f1 ) + y 1 range([f 2 ; : : :; f m ] f1 ) If a particular component f i becomes constant, the corresponding y i in positive or complement form depending on the value of f i replaces f i in the range computation. The image
29 2.3. IMAGE AND INVERSE IMAGE COMPUTATIONS 19 of f for a set A(x) is obtained by rst nding f A(x) and then applying one of the input or output cofactoring techniques. One can also apply a combination of input and output cofactoring. The ordering in which cofactoring is done is very important. The procedure can be sped up dramatically by caching intermediate range computations, and detecting the case where, at any step in the recursion, the functions [f 1 ; : : :; f m ] can be grouped into two or more sets with disjoint support. In this case, the range computation can proceed independently on each group with disjoint support. This reduces the worst case complexity from 2 m to 2 s 1 + : : : + 2 s k, where (s 1 ; : : : ; s k ) are the sizes of the groups with disjoint support (s 1 + : : : + s k = m). Example: We nd the range of the function f = [f 1 ; : : :; f 5 ] using the transition relation method, input cofactoring method, and output cofactoring method. three techniques. f 1 = x 1 x 2 x 3 f 2 = x 1 + x 2 + x 3 f 3 = x 1 x 2 x 3 f 4 = x 4 x 5 f 5 = x 4 x 5 The characteristic function for f is F (x; y) = (y 1 8x 1 x 2 x 3 )(y 2 8(x 1 + x 2 + x 3 ))(y 3 8x 1 x 2 x 3 )(y 4 8x 4 x 5 )(y 5 8x 4 x 5 ): Using the transition relation method the range of f is f(y) = S x F (x; y) = S x1 x 2 x 3 (y 1 8x 1 x 2 x 3 )(y 2 8(x 1 + x 2 + x 3 ))(y 3 8x 1 x 2 x 3 ) S x4 x 5 (y 4 8x 4 x 5 )(y 5 8x 4 x 5 ) = (y 2 y 3 + y 1 y 2 y 3 )(y 4 + y 5 ): We use the fact that the components of f can be separated into groups of disjoint support and Lemma to speed up the range computation. The range can be also computed by cofactoring output functions with respect to each input. The components ff 1 ; f 2 ; f 3 g are grouped together because they are dependent on fx 1 ; x 2 ; x 3 g and the components ff 4 ; f 5 g are grouped together because they are dependent
30 20 CHAPTER 2. TERMINOLOGY AND BACKGROUND on fx 4 ; x 5 g. range([f 1 ; f 2 ; f 3 ; f 4 ; f 5 ]) = range([f 1 ; f 2 ; f 3 ]) range([f 4 ; f 5 ]) We use the ordering x 1 x 2 x 3 to nd range([f 1 ; f 2 ; f 3 ]) = range([f 1x1 ; f 2x1 ; f 3x1 ]) + range([f 1x1 ; f 2x1 ; f 3x1 ]) = range([x 2 x 3 ; 1; 0]) + range([0; x 2 + x 3 ; x 2 x 3 ]) = y 2 y 3 range([x 2 x 3 ]) + y 1 range([x 2 + x 3 ; x 2 x 3 ]) = y 2 y 3 + y 1 (range([x 2 + x 3 ; x 2 x 3 ] x2 ) + range([x 2 + x 3 ; x 2 x 3 ] x2 )) = y 2 y 3 + y 1 range([1; 0]) + y 1 range([x 3 ; x 3 ]) = y 2 y 3 + y 1 range([x 3 ; x 3 ]) = y 2 y 3 + y 1 (range([x 3 ; x 3 ] x3 ) + range([x 3 ; x 3 ] x3 )) = y 2 y 3 + y 1 range([1; 0]) + y 1 range([0; 1]) = y 2 y 3 + y 1 y 2 y 3 : The ordering x 4 x 5 is used to nd range([f 4 ; f 5 ]) = range([x 4 x 5 ; x 4 x 5 ]) = range([x 4 x 5 ; x 4 x 5 ] x4 ) + range([x 4 x 5 ; x 4 x 5 ] x4 ) = range([x 5 ; 0]) + range([0; x 5 ]) = y 5 + y 4 Finally, we show how this can be done using output cofactoring. The ordering x 1 x 2 x 3 x 4 x 5 is used for the generalized cofactor. As before range([f 1 ; f 2 ; f 3 ; f 4 ; f 5 ]) = range([f 1 ; f 2 ; f 3 ]) range([f 4 ; f 5 ]) For output cofactoring, we use f 1 f 2 f 3 to nd range([f 1 ; f 2 ; f 3 ]) = range([f 1f1 ; f 2f1 ; f 3f1 ]) + range([f 1 ; f f 2 ; f 1 f 3 ]) 1 f 1 = range([1; 1; 0]) + range([0; x 1 + x 2 + x 3 ; x 1 x 2 x 3 ]) = y 1 y 2 y 3 + y 1 range([x 1 + x 2 + x 3 ; x 1 x 2 x 3 ])
Unit 4: Formal Verification
 Course contents Unit 4: Formal Verification Logic synthesis basics Binary-decision diagram (BDD) Verification Logic optimization Technology mapping Readings Chapter 11 Unit 4 1 Logic Synthesis & Verification
Course contents Unit 4: Formal Verification Logic synthesis basics Binary-decision diagram (BDD) Verification Logic optimization Technology mapping Readings Chapter 11 Unit 4 1 Logic Synthesis & Verification
LOGIC SYNTHESIS AND VERIFICATION ALGORITHMS. Gary D. Hachtel University of Colorado. Fabio Somenzi University of Colorado.
 LOGIC SYNTHESIS AND VERIFICATION ALGORITHMS by Gary D. Hachtel University of Colorado Fabio Somenzi University of Colorado Springer Contents I Introduction 1 1 Introduction 5 1.1 VLSI: Opportunity and
LOGIC SYNTHESIS AND VERIFICATION ALGORITHMS by Gary D. Hachtel University of Colorado Fabio Somenzi University of Colorado Springer Contents I Introduction 1 1 Introduction 5 1.1 VLSI: Opportunity and
VLSI System Design Part II : Logic Synthesis (1) Oct Feb.2007
 VLSI System Design Part II : Logic Synthesis (1) Oct.2006 - Feb.2007 Lecturer : Tsuyoshi Isshiki Dept. Communications and Integrated Systems, Tokyo Institute of Technology isshiki@vlsi.ss.titech.ac.jp
VLSI System Design Part II : Logic Synthesis (1) Oct.2006 - Feb.2007 Lecturer : Tsuyoshi Isshiki Dept. Communications and Integrated Systems, Tokyo Institute of Technology isshiki@vlsi.ss.titech.ac.jp
ABC basics (compilation from different articles)
 1. AIG construction 2. AIG optimization 3. Technology mapping ABC basics (compilation from different articles) 1. BACKGROUND An And-Inverter Graph (AIG) is a directed acyclic graph (DAG), in which a node
1. AIG construction 2. AIG optimization 3. Technology mapping ABC basics (compilation from different articles) 1. BACKGROUND An And-Inverter Graph (AIG) is a directed acyclic graph (DAG), in which a node
1/28/2013. Synthesis. The Y-diagram Revisited. Structural Behavioral. More abstract designs Physical. CAD for VLSI 2
 Synthesis The Y-diagram Revisited Structural Behavioral More abstract designs Physical CAD for VLSI 2 1 Structural Synthesis Behavioral Physical CAD for VLSI 3 Structural Processor Memory Bus Behavioral
Synthesis The Y-diagram Revisited Structural Behavioral More abstract designs Physical CAD for VLSI 2 1 Structural Synthesis Behavioral Physical CAD for VLSI 3 Structural Processor Memory Bus Behavioral
Assign auniquecodeto each state to produce a. Given jsj states, needed at least dlog jsje state bits. (minimum width encoding), at most jsj state bits
 State Assignment The problem: Assign auniquecodeto each state to produce a logic level description. Given jsj states, needed at least dlog jsje state bits (minimum width encoding), at most jsj state bits
State Assignment The problem: Assign auniquecodeto each state to produce a logic level description. Given jsj states, needed at least dlog jsje state bits (minimum width encoding), at most jsj state bits
CSE241 VLSI Digital Circuits UC San Diego
 CSE241 VLSI Digital Circuits UC San Diego Winter 2003 Lecture 05: Logic Synthesis Cho Moon Cadence Design Systems January 21, 2003 CSE241 L5 Synthesis.1 Kahng & Cichy, UCSD 2003 Outline Introduction Two-level
CSE241 VLSI Digital Circuits UC San Diego Winter 2003 Lecture 05: Logic Synthesis Cho Moon Cadence Design Systems January 21, 2003 CSE241 L5 Synthesis.1 Kahng & Cichy, UCSD 2003 Outline Introduction Two-level
Logic Synthesis & Optimization Lectures 4, 5 Boolean Algebra - Basics
 Logic Synthesis & Optimization Lectures 4, 5 Boolean Algebra - Basics 1 Instructor: Priyank Kalla Department of Electrical and Computer Engineering University of Utah, Salt Lake City, UT 84112 Email: kalla@ece.utah.edu
Logic Synthesis & Optimization Lectures 4, 5 Boolean Algebra - Basics 1 Instructor: Priyank Kalla Department of Electrical and Computer Engineering University of Utah, Salt Lake City, UT 84112 Email: kalla@ece.utah.edu
Logic Synthesis and Verification
 Logic Synthesis and Verification Jie-Hong Roland Jiang 江介宏 Department of Electrical Engineering National Taiwan University Fall 2012 1 SOPs and Incompletely Specified Functions Reading: Logic Synthesis
Logic Synthesis and Verification Jie-Hong Roland Jiang 江介宏 Department of Electrical Engineering National Taiwan University Fall 2012 1 SOPs and Incompletely Specified Functions Reading: Logic Synthesis
Boolean Representations and Combinatorial Equivalence
 Chapter 2 Boolean Representations and Combinatorial Equivalence This chapter introduces different representations of Boolean functions. It then discusses the applications of these representations for proving
Chapter 2 Boolean Representations and Combinatorial Equivalence This chapter introduces different representations of Boolean functions. It then discusses the applications of these representations for proving
Beyond the Combinatorial Limit in Depth Minimization for LUT-Based FPGA Designs
 Beyond the Combinatorial Limit in Depth Minimization for LUT-Based FPGA Designs Jason Cong and Yuzheng Ding Department of Computer Science University of California, Los Angeles, CA 90024 Abstract In this
Beyond the Combinatorial Limit in Depth Minimization for LUT-Based FPGA Designs Jason Cong and Yuzheng Ding Department of Computer Science University of California, Los Angeles, CA 90024 Abstract In this
Synthesis 1. 1 Figures in this chapter taken from S. H. Gerez, Algorithms for VLSI Design Automation, Wiley, Typeset by FoilTEX 1
 Synthesis 1 1 Figures in this chapter taken from S. H. Gerez, Algorithms for VLSI Design Automation, Wiley, 1998. Typeset by FoilTEX 1 Introduction Logic synthesis is automatic generation of circuitry
Synthesis 1 1 Figures in this chapter taken from S. H. Gerez, Algorithms for VLSI Design Automation, Wiley, 1998. Typeset by FoilTEX 1 Introduction Logic synthesis is automatic generation of circuitry
ECE260B CSE241A Winter Logic Synthesis
 ECE260B CSE241A Winter 2007 Logic Synthesis Website: /courses/ece260b-w07 ECE 260B CSE 241A Static Timing Analysis 1 Slides courtesy of Dr. Cho Moon Introduction Why logic synthesis? Ubiquitous used almost
ECE260B CSE241A Winter 2007 Logic Synthesis Website: /courses/ece260b-w07 ECE 260B CSE 241A Static Timing Analysis 1 Slides courtesy of Dr. Cho Moon Introduction Why logic synthesis? Ubiquitous used almost
Lecture 9 - Matrix Multiplication Equivalences and Spectral Graph Theory 1
 CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanfordedu) February 6, 2018 Lecture 9 - Matrix Multiplication Equivalences and Spectral Graph Theory 1 In the
CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanfordedu) February 6, 2018 Lecture 9 - Matrix Multiplication Equivalences and Spectral Graph Theory 1 In the
Disjoint Support Decompositions
 Chapter 4 Disjoint Support Decompositions We introduce now a new property of logic functions which will be useful to further improve the quality of parameterizations in symbolic simulation. In informal
Chapter 4 Disjoint Support Decompositions We introduce now a new property of logic functions which will be useful to further improve the quality of parameterizations in symbolic simulation. In informal
A New Algorithm to Create Prime Irredundant Boolean Expressions
 A New Algorithm to Create Prime Irredundant Boolean Expressions Michel R.C.M. Berkelaar Eindhoven University of technology, P.O. Box 513, NL 5600 MB Eindhoven, The Netherlands Email: michel@es.ele.tue.nl
A New Algorithm to Create Prime Irredundant Boolean Expressions Michel R.C.M. Berkelaar Eindhoven University of technology, P.O. Box 513, NL 5600 MB Eindhoven, The Netherlands Email: michel@es.ele.tue.nl
A Toolbox for Counter-Example Analysis and Optimization
 A Toolbox for Counter-Example Analysis and Optimization Alan Mishchenko Niklas Een Robert Brayton Department of EECS, University of California, Berkeley {alanmi, een, brayton}@eecs.berkeley.edu Abstract
A Toolbox for Counter-Example Analysis and Optimization Alan Mishchenko Niklas Een Robert Brayton Department of EECS, University of California, Berkeley {alanmi, een, brayton}@eecs.berkeley.edu Abstract
Motivation. CS389L: Automated Logical Reasoning. Lecture 5: Binary Decision Diagrams. Historical Context. Binary Decision Trees
 Motivation CS389L: Automated Logical Reasoning Lecture 5: Binary Decision Diagrams Işıl Dillig Previous lectures: How to determine satisfiability of propositional formulas Sometimes need to efficiently
Motivation CS389L: Automated Logical Reasoning Lecture 5: Binary Decision Diagrams Işıl Dillig Previous lectures: How to determine satisfiability of propositional formulas Sometimes need to efficiently
L3: Representations of functions
 L3: Representations of functions Representations of Boolean functions Boolean expression Two level sum of product form, factorized form Truth tables Karnaugh maps Cubes (MIN,MAX) notation positional cube
L3: Representations of functions Representations of Boolean functions Boolean expression Two level sum of product form, factorized form Truth tables Karnaugh maps Cubes (MIN,MAX) notation positional cube
Advanced Digital Logic Design EECS 303
 Advanced Digital Logic Design EECS 303 http://ziyang.eecs.northwestern.edu/eecs303/ Teacher: Robert Dick Office: L477 Tech Email: dickrp@northwestern.edu Phone: 847 467 2298 Outline 1. 2. 2 Robert Dick
Advanced Digital Logic Design EECS 303 http://ziyang.eecs.northwestern.edu/eecs303/ Teacher: Robert Dick Office: L477 Tech Email: dickrp@northwestern.edu Phone: 847 467 2298 Outline 1. 2. 2 Robert Dick
Don t Cares and Multi-Valued Logic Network Minimization
 Don t Cares and Multi-Valued Logic Network Minimization Yunian Jiang Robert K. Brayton Department of Electrical Engineering and Computer Sciences University of California, Berkeley wiang,brayton @eecs.berkeley.edu
Don t Cares and Multi-Valued Logic Network Minimization Yunian Jiang Robert K. Brayton Department of Electrical Engineering and Computer Sciences University of California, Berkeley wiang,brayton @eecs.berkeley.edu
COE 561 Digital System Design & Synthesis Introduction
 1 COE 561 Digital System Design & Synthesis Introduction Dr. Aiman H. El-Maleh Computer Engineering Department King Fahd University of Petroleum & Minerals Outline Course Topics Microelectronics Design
1 COE 561 Digital System Design & Synthesis Introduction Dr. Aiman H. El-Maleh Computer Engineering Department King Fahd University of Petroleum & Minerals Outline Course Topics Microelectronics Design
ICS 252 Introduction to Computer Design
 ICS 252 Introduction to Computer Design Logic Optimization Eli Bozorgzadeh Computer Science Department-UCI Hardware compilation flow HDL RTL Synthesis netlist Logic synthesis library netlist Physical design
ICS 252 Introduction to Computer Design Logic Optimization Eli Bozorgzadeh Computer Science Department-UCI Hardware compilation flow HDL RTL Synthesis netlist Logic synthesis library netlist Physical design
Localization in Graphs. Richardson, TX Azriel Rosenfeld. Center for Automation Research. College Park, MD
 CAR-TR-728 CS-TR-3326 UMIACS-TR-94-92 Samir Khuller Department of Computer Science Institute for Advanced Computer Studies University of Maryland College Park, MD 20742-3255 Localization in Graphs Azriel
CAR-TR-728 CS-TR-3326 UMIACS-TR-94-92 Samir Khuller Department of Computer Science Institute for Advanced Computer Studies University of Maryland College Park, MD 20742-3255 Localization in Graphs Azriel
Binary Decision Diagrams
 Logic and roof Hilary 2016 James Worrell Binary Decision Diagrams A propositional formula is determined up to logical equivalence by its truth table. If the formula has n variables then its truth table
Logic and roof Hilary 2016 James Worrell Binary Decision Diagrams A propositional formula is determined up to logical equivalence by its truth table. If the formula has n variables then its truth table
Multi-valued Logic Synthesis. Robert K Brayton Sunil P Khatri University of California Berkeley, CA brayton,
 Multi-valued Logic Synthesis Robert K Brayton Sunil P Khatri University of California Berkeley, CA 9470 brayton, linus @iceecsberkeleyedu Abstract We survey some of the methods used for manipulating, representing,
Multi-valued Logic Synthesis Robert K Brayton Sunil P Khatri University of California Berkeley, CA 9470 brayton, linus @iceecsberkeleyedu Abstract We survey some of the methods used for manipulating, representing,
22 Elementary Graph Algorithms. There are two standard ways to represent a
 VI Graph Algorithms Elementary Graph Algorithms Minimum Spanning Trees Single-Source Shortest Paths All-Pairs Shortest Paths 22 Elementary Graph Algorithms There are two standard ways to represent a graph
VI Graph Algorithms Elementary Graph Algorithms Minimum Spanning Trees Single-Source Shortest Paths All-Pairs Shortest Paths 22 Elementary Graph Algorithms There are two standard ways to represent a graph
Multi-Level Logic Synthesis for Low Power
 Examples Before Mapping After Mapping Area Power Area Delay Power 5xp1 0.93 0.98 0.86 0.82 0.90 Z5xp1 0.97 0.91 0.95 0.78 0.84 9sym 0.89 1.01 0.83 0.86 0.87 9symml 1.24 1.02 1.15 1.12 0.84 apex5 0.99 0.96
Examples Before Mapping After Mapping Area Power Area Delay Power 5xp1 0.93 0.98 0.86 0.82 0.90 Z5xp1 0.97 0.91 0.95 0.78 0.84 9sym 0.89 1.01 0.83 0.86 0.87 9symml 1.24 1.02 1.15 1.12 0.84 apex5 0.99 0.96
Synthesis of 2-level Logic Heuristic Method. Two Approaches
 Synthesis of 2-level Logic Heuristic Method Lecture 8 Exact Two Approaches Find all primes Find a complete sum Find a minimum cover (covering problem) Heuristic Take an initial cover of cubes Repeat Expand
Synthesis of 2-level Logic Heuristic Method Lecture 8 Exact Two Approaches Find all primes Find a complete sum Find a minimum cover (covering problem) Heuristic Take an initial cover of cubes Repeat Expand
State Machine Specification. State Minimization. State Assignment. Logic Synthesis. Tech Mapping. Test Generation
 Synthesis for Logical Initializability of Synchronous Finite State Machines Montek Singh Steven M. Nowick Department of Computer Science Columbia University 24 Amsterdam Ave: Mailcode 4 New York, NY 27
Synthesis for Logical Initializability of Synchronous Finite State Machines Montek Singh Steven M. Nowick Department of Computer Science Columbia University 24 Amsterdam Ave: Mailcode 4 New York, NY 27
Trees. 3. (Minimally Connected) G is connected and deleting any of its edges gives rise to a disconnected graph.
 Trees 1 Introduction Trees are very special kind of (undirected) graphs. Formally speaking, a tree is a connected graph that is acyclic. 1 This definition has some drawbacks: given a graph it is not trivial
Trees 1 Introduction Trees are very special kind of (undirected) graphs. Formally speaking, a tree is a connected graph that is acyclic. 1 This definition has some drawbacks: given a graph it is not trivial
History: Combinational Logic! single FSM! Hierarchy. Facilities for managing networks of FSMs MISII. Facilities for handling latches
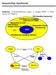 Sequential Synthesis History: Combinational Logic! single FSM! Hierarchy of FSM's. Sequential Circuit Optimization (single machine) SIS Facilities for managing networks of FSMs MISII Facilities for handling
Sequential Synthesis History: Combinational Logic! single FSM! Hierarchy of FSM's. Sequential Circuit Optimization (single machine) SIS Facilities for managing networks of FSMs MISII Facilities for handling
Set Manipulation with Boolean Functional Vectors for Symbolic Reachability Analysis
 Set Manipulation with Boolean Functional Vectors for Symbolic Reachability Analysis Amit Goel Department of ECE, Carnegie Mellon University, PA. 15213. USA. agoel@ece.cmu.edu Randal E. Bryant Computer
Set Manipulation with Boolean Functional Vectors for Symbolic Reachability Analysis Amit Goel Department of ECE, Carnegie Mellon University, PA. 15213. USA. agoel@ece.cmu.edu Randal E. Bryant Computer
Boolean Algebra and Logic Gates
 Boolean Algebra and Logic Gates Binary logic is used in all of today's digital computers and devices Cost of the circuits is an important factor Finding simpler and cheaper but equivalent circuits can
Boolean Algebra and Logic Gates Binary logic is used in all of today's digital computers and devices Cost of the circuits is an important factor Finding simpler and cheaper but equivalent circuits can
PARALLEL PERFORMANCE DIRECTED TECHNOLOGY MAPPING FOR FPGA. Laurent Lemarchand. Informatique. ea 2215, D pt. ubo University{ bp 809
 PARALLEL PERFORMANCE DIRECTED TECHNOLOGY MAPPING FOR FPGA Laurent Lemarchand Informatique ubo University{ bp 809 f-29285, Brest { France lemarch@univ-brest.fr ea 2215, D pt ABSTRACT An ecient distributed
PARALLEL PERFORMANCE DIRECTED TECHNOLOGY MAPPING FOR FPGA Laurent Lemarchand Informatique ubo University{ bp 809 f-29285, Brest { France lemarch@univ-brest.fr ea 2215, D pt ABSTRACT An ecient distributed
SIS: A System for Sequential Circuit Synthesis
 SIS: A System for Sequential Circuit Synthesis Electronics Research Laboratory Memorandum No. UCB/ERL M92/41 Ellen M. Sentovich Kanwar Jit Singh Luciano Lavagno Cho Moon Rajeev Murgai Alexander Saldanha
SIS: A System for Sequential Circuit Synthesis Electronics Research Laboratory Memorandum No. UCB/ERL M92/41 Ellen M. Sentovich Kanwar Jit Singh Luciano Lavagno Cho Moon Rajeev Murgai Alexander Saldanha
Introduction. Sungho Kang. Yonsei University
 Introduction Sungho Kang Yonsei University Outline VLSI Design Styles Overview of Optimal Logic Synthesis Model Graph Algorithm and Complexity Asymptotic Complexity Brief Summary of MOS Device Behavior
Introduction Sungho Kang Yonsei University Outline VLSI Design Styles Overview of Optimal Logic Synthesis Model Graph Algorithm and Complexity Asymptotic Complexity Brief Summary of MOS Device Behavior
Math 443/543 Graph Theory Notes
 Math 443/543 Graph Theory Notes David Glickenstein September 3, 2008 1 Introduction We will begin by considering several problems which may be solved using graphs, directed graphs (digraphs), and networks.
Math 443/543 Graph Theory Notes David Glickenstein September 3, 2008 1 Introduction We will begin by considering several problems which may be solved using graphs, directed graphs (digraphs), and networks.
EECS 219C: Formal Methods Binary Decision Diagrams (BDDs) Sanjit A. Seshia EECS, UC Berkeley
 EECS 219C: Formal Methods Binary Decision Diagrams (BDDs) Sanjit A. Seshia EECS, UC Berkeley Boolean Function Representations Syntactic: e.g.: CNF, DNF (SOP), Circuit Semantic: e.g.: Truth table, Binary
EECS 219C: Formal Methods Binary Decision Diagrams (BDDs) Sanjit A. Seshia EECS, UC Berkeley Boolean Function Representations Syntactic: e.g.: CNF, DNF (SOP), Circuit Semantic: e.g.: Truth table, Binary
Advanced VLSI Design Prof. Virendra K. Singh Department of Electrical Engineering Indian Institute of Technology Bombay
 Advanced VLSI Design Prof. Virendra K. Singh Department of Electrical Engineering Indian Institute of Technology Bombay Lecture 40 VLSI Design Verification: An Introduction Hello. Welcome to the advance
Advanced VLSI Design Prof. Virendra K. Singh Department of Electrical Engineering Indian Institute of Technology Bombay Lecture 40 VLSI Design Verification: An Introduction Hello. Welcome to the advance
Additional Slides to De Micheli Book
 Additional Slides to De Micheli Book Sungho Kang Yonsei University Design Style - Decomposition 08 3$9 0 Behavioral Synthesis Resource allocation; Pipelining; Control flow parallelization; Communicating
Additional Slides to De Micheli Book Sungho Kang Yonsei University Design Style - Decomposition 08 3$9 0 Behavioral Synthesis Resource allocation; Pipelining; Control flow parallelization; Communicating
Quick Look under the Hood of ABC
 Quick Look under the Hood of ABC A Programmer s Manual December 25, 2006 Network ABC is similar to SIS/MVSIS in that it processes the design by applying a sequence of transformations to the current network,
Quick Look under the Hood of ABC A Programmer s Manual December 25, 2006 Network ABC is similar to SIS/MVSIS in that it processes the design by applying a sequence of transformations to the current network,
Optimized Implementation of Logic Functions
 June 25, 22 9:7 vra235_ch4 Sheet number Page number 49 black chapter 4 Optimized Implementation of Logic Functions 4. Nc3xe4, Nb8 d7 49 June 25, 22 9:7 vra235_ch4 Sheet number 2 Page number 5 black 5 CHAPTER
June 25, 22 9:7 vra235_ch4 Sheet number Page number 49 black chapter 4 Optimized Implementation of Logic Functions 4. Nc3xe4, Nb8 d7 49 June 25, 22 9:7 vra235_ch4 Sheet number 2 Page number 5 black 5 CHAPTER
Math 443/543 Graph Theory Notes
 Math 443/543 Graph Theory Notes David Glickenstein September 8, 2014 1 Introduction We will begin by considering several problems which may be solved using graphs, directed graphs (digraphs), and networks.
Math 443/543 Graph Theory Notes David Glickenstein September 8, 2014 1 Introduction We will begin by considering several problems which may be solved using graphs, directed graphs (digraphs), and networks.
22 Elementary Graph Algorithms. There are two standard ways to represent a
 VI Graph Algorithms Elementary Graph Algorithms Minimum Spanning Trees Single-Source Shortest Paths All-Pairs Shortest Paths 22 Elementary Graph Algorithms There are two standard ways to represent a graph
VI Graph Algorithms Elementary Graph Algorithms Minimum Spanning Trees Single-Source Shortest Paths All-Pairs Shortest Paths 22 Elementary Graph Algorithms There are two standard ways to represent a graph
Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1
 CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) January 11, 2018 Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1 In this lecture
CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) January 11, 2018 Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1 In this lecture
Binary Decision Diagrams (BDD)
 Binary Decision Diagrams (BDD) Contents Motivation for Decision diagrams Binary Decision Diagrams ROBDD Effect of Variable Ordering on BDD size BDD operations Encoding state machines Reachability Analysis
Binary Decision Diagrams (BDD) Contents Motivation for Decision diagrams Binary Decision Diagrams ROBDD Effect of Variable Ordering on BDD size BDD operations Encoding state machines Reachability Analysis
Binary recursion. Unate functions. If a cover C(f) is unate in xj, x, then f is unate in xj. x
 Binary recursion Unate unctions! Theorem I a cover C() is unate in,, then is unate in.! Theorem I is unate in,, then every prime implicant o is unate in. Why are unate unctions so special?! Special Boolean
Binary recursion Unate unctions! Theorem I a cover C() is unate in,, then is unate in.! Theorem I is unate in,, then every prime implicant o is unate in. Why are unate unctions so special?! Special Boolean
An Efficient Framework of Using Various Decomposition Methods to Synthesize LUT Networks and Its Evaluation
 An Efficient Framework of Using Various Decomposition Methods to Synthesize LUT Networks and Its Evaluation Shigeru Yamashita Hiroshi Sawada Akira Nagoya NTT Communication Science Laboratories 2-4, Hikaridai,
An Efficient Framework of Using Various Decomposition Methods to Synthesize LUT Networks and Its Evaluation Shigeru Yamashita Hiroshi Sawada Akira Nagoya NTT Communication Science Laboratories 2-4, Hikaridai,
would be included in is small: to be exact. Thus with probability1, the same partition n+1 n+1 would be produced regardless of whether p is in the inp
 1 Introduction 1.1 Parallel Randomized Algorihtms Using Sampling A fundamental strategy used in designing ecient algorithms is divide-and-conquer, where that input data is partitioned into several subproblems
1 Introduction 1.1 Parallel Randomized Algorihtms Using Sampling A fundamental strategy used in designing ecient algorithms is divide-and-conquer, where that input data is partitioned into several subproblems
Homework 3 Handout 19 February 18, 2016
 CSEE E6861y Prof. Steven Nowick Homework 3 Handout 19 February 18, 2016 This homework is due at the beginning of class on Thursday, March 3. NOTE: A correct answer without adequate explanation or derivation
CSEE E6861y Prof. Steven Nowick Homework 3 Handout 19 February 18, 2016 This homework is due at the beginning of class on Thursday, March 3. NOTE: A correct answer without adequate explanation or derivation
IEEE Transactions on computers
 215 IEEE. Personal use of this material is permitted. Permission from IEEE must be obtained for all other uses, in any current or future media, including reprinting/republishing this material for advertising
215 IEEE. Personal use of this material is permitted. Permission from IEEE must be obtained for all other uses, in any current or future media, including reprinting/republishing this material for advertising
Enumeration of Full Graphs: Onset of the Asymptotic Region. Department of Mathematics. Massachusetts Institute of Technology. Cambridge, MA 02139
 Enumeration of Full Graphs: Onset of the Asymptotic Region L. J. Cowen D. J. Kleitman y F. Lasaga D. E. Sussman Department of Mathematics Massachusetts Institute of Technology Cambridge, MA 02139 Abstract
Enumeration of Full Graphs: Onset of the Asymptotic Region L. J. Cowen D. J. Kleitman y F. Lasaga D. E. Sussman Department of Mathematics Massachusetts Institute of Technology Cambridge, MA 02139 Abstract
Rigidity, connectivity and graph decompositions
 First Prev Next Last Rigidity, connectivity and graph decompositions Brigitte Servatius Herman Servatius Worcester Polytechnic Institute Page 1 of 100 First Prev Next Last Page 2 of 100 We say that a framework
First Prev Next Last Rigidity, connectivity and graph decompositions Brigitte Servatius Herman Servatius Worcester Polytechnic Institute Page 1 of 100 First Prev Next Last Page 2 of 100 We say that a framework
Review. EECS Components and Design Techniques for Digital Systems. Lec 05 Boolean Logic 9/4-04. Seq. Circuit Behavior. Outline.
 Review EECS 150 - Components and Design Techniques for Digital Systems Lec 05 Boolean Logic 94-04 David Culler Electrical Engineering and Computer Sciences University of California, Berkeley Design flow
Review EECS 150 - Components and Design Techniques for Digital Systems Lec 05 Boolean Logic 94-04 David Culler Electrical Engineering and Computer Sciences University of California, Berkeley Design flow
CS8803: Advanced Digital Design for Embedded Hardware
 CS883: Advanced Digital Design for Embedded Hardware Lecture 2: Boolean Algebra, Gate Network, and Combinational Blocks Instructor: Sung Kyu Lim (limsk@ece.gatech.edu) Website: http://users.ece.gatech.edu/limsk/course/cs883
CS883: Advanced Digital Design for Embedded Hardware Lecture 2: Boolean Algebra, Gate Network, and Combinational Blocks Instructor: Sung Kyu Lim (limsk@ece.gatech.edu) Website: http://users.ece.gatech.edu/limsk/course/cs883
Computer-Aided Design (CAD) Logic Synthesis Tutorial. Prepared by Ray Cheung
 Computer-Aided Design (CAD) Logic Synthesis Tutorial Prepared by Ray Cheung What is Logic Synthesis? Logic Synthesis - Takes the circuit description at the RTL level and generates an optimal implementation
Computer-Aided Design (CAD) Logic Synthesis Tutorial Prepared by Ray Cheung What is Logic Synthesis? Logic Synthesis - Takes the circuit description at the RTL level and generates an optimal implementation
to automatically generate parallel code for many applications that periodically update shared data structures using commuting operations and/or manipu
 Semantic Foundations of Commutativity Analysis Martin C. Rinard y and Pedro C. Diniz z Department of Computer Science University of California, Santa Barbara Santa Barbara, CA 93106 fmartin,pedrog@cs.ucsb.edu
Semantic Foundations of Commutativity Analysis Martin C. Rinard y and Pedro C. Diniz z Department of Computer Science University of California, Santa Barbara Santa Barbara, CA 93106 fmartin,pedrog@cs.ucsb.edu
Delay Estimation for Technology Independent Synthesis
 Delay Estimation for Technology Independent Synthesis Yutaka TAMIYA FUJITSU LABORATORIES LTD. 4-1-1 Kamikodanaka, Nakahara-ku, Kawasaki, JAPAN, 211-88 Tel: +81-44-754-2663 Fax: +81-44-754-2664 E-mail:
Delay Estimation for Technology Independent Synthesis Yutaka TAMIYA FUJITSU LABORATORIES LTD. 4-1-1 Kamikodanaka, Nakahara-ku, Kawasaki, JAPAN, 211-88 Tel: +81-44-754-2663 Fax: +81-44-754-2664 E-mail:
2 ATTILA FAZEKAS The tracking model of the robot car The schematic picture of the robot car can be seen on Fig.1. Figure 1. The main controlling task
 NEW OPTICAL TRACKING METHODS FOR ROBOT CARS Attila Fazekas Debrecen Abstract. In this paper new methods are proposed for intelligent optical tracking of robot cars the important tools of CIM (Computer
NEW OPTICAL TRACKING METHODS FOR ROBOT CARS Attila Fazekas Debrecen Abstract. In this paper new methods are proposed for intelligent optical tracking of robot cars the important tools of CIM (Computer
TECHNOLOGY MAPPING FOR THE ATMEL FPGA CIRCUITS
 TECHNOLOGY MAPPING FOR THE ATMEL FPGA CIRCUITS Zoltan Baruch E-mail: Zoltan.Baruch@cs.utcluj.ro Octavian Creţ E-mail: Octavian.Cret@cs.utcluj.ro Kalman Pusztai E-mail: Kalman.Pusztai@cs.utcluj.ro Computer
TECHNOLOGY MAPPING FOR THE ATMEL FPGA CIRCUITS Zoltan Baruch E-mail: Zoltan.Baruch@cs.utcluj.ro Octavian Creţ E-mail: Octavian.Cret@cs.utcluj.ro Kalman Pusztai E-mail: Kalman.Pusztai@cs.utcluj.ro Computer
Eulerian disjoint paths problem in grid graphs is NP-complete
 Discrete Applied Mathematics 143 (2004) 336 341 Notes Eulerian disjoint paths problem in grid graphs is NP-complete Daniel Marx www.elsevier.com/locate/dam Department of Computer Science and Information
Discrete Applied Mathematics 143 (2004) 336 341 Notes Eulerian disjoint paths problem in grid graphs is NP-complete Daniel Marx www.elsevier.com/locate/dam Department of Computer Science and Information
ACKNOWLEDGEMENTS. my thesis committee and for their input on this document. effort. This research was funded under NSF contract MIP
 ACKNOWLEDGEMENTS I would like to think my thesis advisor, Dr. Thornton, for the opportunity to work on this project, for his many insights into this research, and for the numerous times that he reviewed
ACKNOWLEDGEMENTS I would like to think my thesis advisor, Dr. Thornton, for the opportunity to work on this project, for his many insights into this research, and for the numerous times that he reviewed
ECE260B CSE241A Winter Logic Synthesis
 ECE260B CSE241A Winter 2005 Logic Synthesis Website: / courses/ ece260bw05 ECE 260B CSE 241A Static Timing Analysis 1 Slides courtesy of Dr. Cho Moon Introduction Why logic synthesis? Ubiquitous used almost
ECE260B CSE241A Winter 2005 Logic Synthesis Website: / courses/ ece260bw05 ECE 260B CSE 241A Static Timing Analysis 1 Slides courtesy of Dr. Cho Moon Introduction Why logic synthesis? Ubiquitous used almost
History: Combinational Logic! single FSM! Hierarchy. Facilities for managing networks of FSMs MISII. Facilities for handling latches
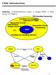 FSM Introduction History: Combinational Logic! single FSM! Hierarchy of FSM's. Sequential Circuit Optimization (single machine) SIS Facilities for managing networks of FSMs MISII Facilities for handling
FSM Introduction History: Combinational Logic! single FSM! Hierarchy of FSM's. Sequential Circuit Optimization (single machine) SIS Facilities for managing networks of FSMs MISII Facilities for handling
Hardware Design Environments. Dr. Mahdi Abbasi Computer Engineering Department Bu-Ali Sina University
 Hardware Design Environments Dr. Mahdi Abbasi Computer Engineering Department Bu-Ali Sina University Outline Welcome to COE 405 Digital System Design Design Domains and Levels of Abstractions Synthesis
Hardware Design Environments Dr. Mahdi Abbasi Computer Engineering Department Bu-Ali Sina University Outline Welcome to COE 405 Digital System Design Design Domains and Levels of Abstractions Synthesis
Design of Framework for Logic Synthesis Engine
 Design of Framework for Logic Synthesis Engine Tribikram Pradhan 1, Pramod Kumar 2, Anil N S 3, Amit Bakshi 4 1 School of Information technology and Engineering, VIT University, Vellore 632014, Tamilnadu,
Design of Framework for Logic Synthesis Engine Tribikram Pradhan 1, Pramod Kumar 2, Anil N S 3, Amit Bakshi 4 1 School of Information technology and Engineering, VIT University, Vellore 632014, Tamilnadu,
The Encoding Complexity of Network Coding
 The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
Model Checking I Binary Decision Diagrams
 /42 Model Checking I Binary Decision Diagrams Edmund M. Clarke, Jr. School of Computer Science Carnegie Mellon University Pittsburgh, PA 523 2/42 Binary Decision Diagrams Ordered binary decision diagrams
/42 Model Checking I Binary Decision Diagrams Edmund M. Clarke, Jr. School of Computer Science Carnegie Mellon University Pittsburgh, PA 523 2/42 Binary Decision Diagrams Ordered binary decision diagrams
Overview. Discrete Event Systems - Verification of Finite Automata. What can finite automata be used for? What can finite automata be used for?
 Computer Engineering and Networks Overview Discrete Event Systems - Verification of Finite Automata Lothar Thiele Introduction Binary Decision Diagrams Representation of Boolean Functions Comparing two
Computer Engineering and Networks Overview Discrete Event Systems - Verification of Finite Automata Lothar Thiele Introduction Binary Decision Diagrams Representation of Boolean Functions Comparing two
Read-Once Functions (Revisited) and the Readability Number of a Boolean Function. Martin Charles Golumbic
 Read-Once Functions (Revisited) and the Readability Number of a Boolean Function Martin Charles Golumbic Caesarea Rothschild Institute University of Haifa Joint work with Aviad Mintz and Udi Rotics Outline
Read-Once Functions (Revisited) and the Readability Number of a Boolean Function Martin Charles Golumbic Caesarea Rothschild Institute University of Haifa Joint work with Aviad Mintz and Udi Rotics Outline
Software Engineering 2DA4. Slides 2: Introduction to Logic Circuits
 Software Engineering 2DA4 Slides 2: Introduction to Logic Circuits Dr. Ryan Leduc Department of Computing and Software McMaster University Material based on S. Brown and Z. Vranesic, Fundamentals of Digital
Software Engineering 2DA4 Slides 2: Introduction to Logic Circuits Dr. Ryan Leduc Department of Computing and Software McMaster University Material based on S. Brown and Z. Vranesic, Fundamentals of Digital
Fast Boolean Matching for Small Practical Functions
 Fast Boolean Matching for Small Practical Functions Zheng Huang Lingli Wang Yakov Nasikovskiy Alan Mishchenko State Key Lab of ASIC and System Computer Science Department Department of EECS Fudan University,
Fast Boolean Matching for Small Practical Functions Zheng Huang Lingli Wang Yakov Nasikovskiy Alan Mishchenko State Key Lab of ASIC and System Computer Science Department Department of EECS Fudan University,
MA651 Topology. Lecture 4. Topological spaces 2
 MA651 Topology. Lecture 4. Topological spaces 2 This text is based on the following books: Linear Algebra and Analysis by Marc Zamansky Topology by James Dugundgji Fundamental concepts of topology by Peter
MA651 Topology. Lecture 4. Topological spaces 2 This text is based on the following books: Linear Algebra and Analysis by Marc Zamansky Topology by James Dugundgji Fundamental concepts of topology by Peter
Treewidth and graph minors
 Treewidth and graph minors Lectures 9 and 10, December 29, 2011, January 5, 2012 We shall touch upon the theory of Graph Minors by Robertson and Seymour. This theory gives a very general condition under
Treewidth and graph minors Lectures 9 and 10, December 29, 2011, January 5, 2012 We shall touch upon the theory of Graph Minors by Robertson and Seymour. This theory gives a very general condition under
Topology - I. Michael Shulman WOMP 2004
 Topology - I Michael Shulman WOMP 2004 1 Topological Spaces There are many different ways to define a topological space; the most common one is as follows: Definition 1.1 A topological space (often just
Topology - I Michael Shulman WOMP 2004 1 Topological Spaces There are many different ways to define a topological space; the most common one is as follows: Definition 1.1 A topological space (often just
COPYRIGHTED MATERIAL INDEX
 INDEX Absorption law, 31, 38 Acyclic graph, 35 tree, 36 Addition operators, in VHDL (VHSIC hardware description language), 192 Algebraic division, 105 AND gate, 48 49 Antisymmetric, 34 Applicable input
INDEX Absorption law, 31, 38 Acyclic graph, 35 tree, 36 Addition operators, in VHDL (VHSIC hardware description language), 192 Algebraic division, 105 AND gate, 48 49 Antisymmetric, 34 Applicable input
ECE 5775 (Fall 17) High-Level Digital Design Automation. Binary Decision Diagrams Static Timing Analysis
 ECE 5775 (Fall 17) High-Level Digital Design Automation Binary Decision Diagrams Static Timing Analysis Announcements Start early on Lab 1 (CORDIC design) Fixed-point design should not have usage of DSP48s
ECE 5775 (Fall 17) High-Level Digital Design Automation Binary Decision Diagrams Static Timing Analysis Announcements Start early on Lab 1 (CORDIC design) Fixed-point design should not have usage of DSP48s
CS6702 GRAPH THEORY AND APPLICATIONS 2 MARKS QUESTIONS AND ANSWERS
 CS6702 GRAPH THEORY AND APPLICATIONS 2 MARKS QUESTIONS AND ANSWERS 1 UNIT I INTRODUCTION CS6702 GRAPH THEORY AND APPLICATIONS 2 MARKS QUESTIONS AND ANSWERS 1. Define Graph. A graph G = (V, E) consists
CS6702 GRAPH THEORY AND APPLICATIONS 2 MARKS QUESTIONS AND ANSWERS 1 UNIT I INTRODUCTION CS6702 GRAPH THEORY AND APPLICATIONS 2 MARKS QUESTIONS AND ANSWERS 1. Define Graph. A graph G = (V, E) consists
Giovanni De Micheli. Integrated Systems Centre EPF Lausanne
 Two-level Logic Synthesis and Optimization Giovanni De Micheli Integrated Systems Centre EPF Lausanne This presentation can be used for non-commercial purposes as long as this note and the copyright footers
Two-level Logic Synthesis and Optimization Giovanni De Micheli Integrated Systems Centre EPF Lausanne This presentation can be used for non-commercial purposes as long as this note and the copyright footers
SEPP: a New Compact Three-Level Logic Form
 SEPP: a New Compact Three-Level Logic Form Valentina Ciriani Department of Information Technologies Università degli Studi di Milano, Italy valentina.ciriani@unimi.it Anna Bernasconi Department of Computer
SEPP: a New Compact Three-Level Logic Form Valentina Ciriani Department of Information Technologies Università degli Studi di Milano, Italy valentina.ciriani@unimi.it Anna Bernasconi Department of Computer
Versatile SAT-based Remapping for Standard Cells
 Versatile SAT-based Remapping for Standard Cells Alan Mishchenko Robert Brayton Department of EECS, UC Berkeley {alanmi, brayton@berkeley.edu Thierry Besson Sriram Govindarajan Harm Arts Paul van Besouw
Versatile SAT-based Remapping for Standard Cells Alan Mishchenko Robert Brayton Department of EECS, UC Berkeley {alanmi, brayton@berkeley.edu Thierry Besson Sriram Govindarajan Harm Arts Paul van Besouw
DISCRETE MATHEMATICS
 DISCRETE MATHEMATICS WITH APPLICATIONS THIRD EDITION SUSANNA S. EPP DePaul University THOIVISON * BROOKS/COLE Australia Canada Mexico Singapore Spain United Kingdom United States CONTENTS Chapter 1 The
DISCRETE MATHEMATICS WITH APPLICATIONS THIRD EDITION SUSANNA S. EPP DePaul University THOIVISON * BROOKS/COLE Australia Canada Mexico Singapore Spain United Kingdom United States CONTENTS Chapter 1 The
On the Relationships between Zero Forcing Numbers and Certain Graph Coverings
 On the Relationships between Zero Forcing Numbers and Certain Graph Coverings Fatemeh Alinaghipour Taklimi, Shaun Fallat 1,, Karen Meagher 2 Department of Mathematics and Statistics, University of Regina,
On the Relationships between Zero Forcing Numbers and Certain Graph Coverings Fatemeh Alinaghipour Taklimi, Shaun Fallat 1,, Karen Meagher 2 Department of Mathematics and Statistics, University of Regina,
16 Greedy Algorithms
 16 Greedy Algorithms Optimization algorithms typically go through a sequence of steps, with a set of choices at each For many optimization problems, using dynamic programming to determine the best choices
16 Greedy Algorithms Optimization algorithms typically go through a sequence of steps, with a set of choices at each For many optimization problems, using dynamic programming to determine the best choices
CHAPTER 9 MULTIPLEXERS, DECODERS, AND PROGRAMMABLE LOGIC DEVICES
 CHAPTER 9 MULTIPLEXERS, DECODERS, AND PROGRAMMABLE LOGIC DEVICES This chapter in the book includes: Objectives Study Guide 9.1 Introduction 9.2 Multiplexers 9.3 Three-State Buffers 9.4 Decoders and Encoders
CHAPTER 9 MULTIPLEXERS, DECODERS, AND PROGRAMMABLE LOGIC DEVICES This chapter in the book includes: Objectives Study Guide 9.1 Introduction 9.2 Multiplexers 9.3 Three-State Buffers 9.4 Decoders and Encoders
Application of Binary Decision Diagram in digital circuit analysis.
 Application of Binary Decision Diagram in digital circuit analysis. Jyoti Kukreja University of Southern California For Dr. James Ellison Abstract: Binary Decision Diagrams (BDDs) are one of the biggest
Application of Binary Decision Diagram in digital circuit analysis. Jyoti Kukreja University of Southern California For Dr. James Ellison Abstract: Binary Decision Diagrams (BDDs) are one of the biggest
Chapter 8. NP-complete problems
 Chapter 8. NP-complete problems Search problems E cient algorithms We have developed algorithms for I I I I I finding shortest paths in graphs, minimum spanning trees in graphs, matchings in bipartite
Chapter 8. NP-complete problems Search problems E cient algorithms We have developed algorithms for I I I I I finding shortest paths in graphs, minimum spanning trees in graphs, matchings in bipartite
CS357 Lecture: BDD basics. David Dill
 CS357 Lecture: BDD basics David Dill BDDs (Boolean/binary decision diagrams) BDDs are a very successful representation for Boolean functions. A BDD represents a Boolean function on variables x, x 2,...
CS357 Lecture: BDD basics David Dill BDDs (Boolean/binary decision diagrams) BDDs are a very successful representation for Boolean functions. A BDD represents a Boolean function on variables x, x 2,...
6. Lecture notes on matroid intersection
 Massachusetts Institute of Technology 18.453: Combinatorial Optimization Michel X. Goemans May 2, 2017 6. Lecture notes on matroid intersection One nice feature about matroids is that a simple greedy algorithm
Massachusetts Institute of Technology 18.453: Combinatorial Optimization Michel X. Goemans May 2, 2017 6. Lecture notes on matroid intersection One nice feature about matroids is that a simple greedy algorithm
Local Two-Level And-Inverter Graph Minimization without Blowup
 Local Two-Level And-Inverter Graph Minimization without Blowup Robert Brummayer and Armin Biere Institute for Formal Models and Verification Johannes Kepler University Linz, Austria {robert.brummayer,
Local Two-Level And-Inverter Graph Minimization without Blowup Robert Brummayer and Armin Biere Institute for Formal Models and Verification Johannes Kepler University Linz, Austria {robert.brummayer,
v V Question: How many edges are there in a graph with 10 vertices each of degree 6?
 ECS20 Handout Graphs and Trees March 4, 2015 (updated 3/9) Notion of a graph 1. A graph G = (V,E) consists of V, a nonempty set of vertices (or nodes) and E, a set of pairs of elements of V called edges.
ECS20 Handout Graphs and Trees March 4, 2015 (updated 3/9) Notion of a graph 1. A graph G = (V,E) consists of V, a nonempty set of vertices (or nodes) and E, a set of pairs of elements of V called edges.
Submitted for TAU97 Abstract Many attempts have been made to combine some form of retiming with combinational
 Experiments in the Iterative Application of Resynthesis and Retiming Soha Hassoun and Carl Ebeling Department of Computer Science and Engineering University ofwashington, Seattle, WA fsoha,ebelingg@cs.washington.edu
Experiments in the Iterative Application of Resynthesis and Retiming Soha Hassoun and Carl Ebeling Department of Computer Science and Engineering University ofwashington, Seattle, WA fsoha,ebelingg@cs.washington.edu
Algorithms for an FPGA Switch Module Routing Problem with. Application to Global Routing. Abstract
 Algorithms for an FPGA Switch Module Routing Problem with Application to Global Routing Shashidhar Thakur y Yao-Wen Chang y D. F. Wong y S. Muthukrishnan z Abstract We consider a switch-module-routing
Algorithms for an FPGA Switch Module Routing Problem with Application to Global Routing Shashidhar Thakur y Yao-Wen Chang y D. F. Wong y S. Muthukrishnan z Abstract We consider a switch-module-routing
On Universal Cycles of Labeled Graphs
 On Universal Cycles of Labeled Graphs Greg Brockman Harvard University Cambridge, MA 02138 United States brockman@hcs.harvard.edu Bill Kay University of South Carolina Columbia, SC 29208 United States
On Universal Cycles of Labeled Graphs Greg Brockman Harvard University Cambridge, MA 02138 United States brockman@hcs.harvard.edu Bill Kay University of South Carolina Columbia, SC 29208 United States
Decreasing a key FIB-HEAP-DECREASE-KEY(,, ) 3.. NIL. 2. error new key is greater than current key 6. CASCADING-CUT(, )
 Decreasing a key FIB-HEAP-DECREASE-KEY(,, ) 1. if >. 2. error new key is greater than current key 3.. 4.. 5. if NIL and.
Decreasing a key FIB-HEAP-DECREASE-KEY(,, ) 1. if >. 2. error new key is greater than current key 3.. 4.. 5. if NIL and.
II (Sorting and) Order Statistics
 II (Sorting and) Order Statistics Heapsort Quicksort Sorting in Linear Time Medians and Order Statistics 8 Sorting in Linear Time The sorting algorithms introduced thus far are comparison sorts Any comparison
II (Sorting and) Order Statistics Heapsort Quicksort Sorting in Linear Time Medians and Order Statistics 8 Sorting in Linear Time The sorting algorithms introduced thus far are comparison sorts Any comparison
On the Verification of Sequential Equivalence
 686 IEEE TRANSACTIONS ON COMPUTER-AIDED DESIGN OF INTEGRATED CIRCUITS AND SYSTEMS, VOL 22, NO 6, JUNE 2003 On the Verification of Sequential Equivalence Jie-Hong R Jiang and Robert K Brayton, Fellow, IEEE
686 IEEE TRANSACTIONS ON COMPUTER-AIDED DESIGN OF INTEGRATED CIRCUITS AND SYSTEMS, VOL 22, NO 6, JUNE 2003 On the Verification of Sequential Equivalence Jie-Hong R Jiang and Robert K Brayton, Fellow, IEEE
Behavior models and verification Lecture 6
 Behavior models and verification Lecture 6 http://d3s.mff.cuni.cz Jan Kofroň, František Plášil Model checking For a Kripke structure M = (S, I, R, L) over AP and a (state based) temporal logic formula
Behavior models and verification Lecture 6 http://d3s.mff.cuni.cz Jan Kofroň, František Plášil Model checking For a Kripke structure M = (S, I, R, L) over AP and a (state based) temporal logic formula
A Relational View of Subgraph Isomorphism
 A Relational View of Subgraph Isomorphism J. Cortadella and G. Valiente Department of Software, Technical University of Catalonia, Barcelona, Spain Abstract. This paper presents a novel approach to the
A Relational View of Subgraph Isomorphism J. Cortadella and G. Valiente Department of Software, Technical University of Catalonia, Barcelona, Spain Abstract. This paper presents a novel approach to the
