Key-dependent pyramidal wavelet domains for secure watermark embedding
|
|
|
- Gordon Webster
- 5 years ago
- Views:
Transcription
1 Key-dependent pyramidal wavelet domains for secure watermark embedding Werner M. Dietl, Peter Meerwald and Andreas Uhl Department of Scientific Computing, University of Salzburg, Austria ABSTRACT Wavelet filters can be parametrized to create an entire family of different wavelet filters. We discuss wavelet filter parametrization as a means to add security to wavelet based watermarking schemes. We analyze the influence of the number of filter parameters and use non-stationary multi-resolution decomposition where different wavelet filters are used at different levels of the decomposition. Using JPEG and JPEG2 compression we assess the normalized correlation and Peak Signal to Noise Ratio (PSNR) behavior of the watermarks. The security against unauthorized detection is also investigated. We conclude that the proposed systems show good robustness against compression and depending on the resolution we choose for the parameters we get between 2 99 and 2 85 possible keys. Keywords: parametrized wavelet filters, watermarking, security, robustness. INTRODUCTION Fast and easy distribution of content over the Internet is a serious threat to the revenue stream of content owners. Watermarking has gained high popularity as a method to protect intellectual property rights on the Internet. For introductions to this topic see. 5 Over the last several years wavelet analysis was developed as a new method to analyze signals. 6 8 Wavelet analysis is also used in image compression, where better energy compaction, the multi-resolution analysis and many other features make it superior to the existing discrete-cosine based systems like JPEG. The new JPEG2 compression standard 9, uses the wavelet transformation and achieves higher compression rates with less perceptible artifacts and other advanced features. With the rising interest in wavelets also the watermarking community started to use them. Many watermarking algorithms have been developed that embed the watermark in the wavelet transform domain Meerwald compiled an overview. The resilience of a watermarking system can be separated into robustness and security. In the following we will use the terminology suggested by Cox. 4 Robustness means the resistance against common signal distortions that are known beforehand. For example, a system that includes a transmission over a noisy communication channel needs to be robust against the noise. It is known in advance that the channel is noisy and without robustness against the noise the watermarking system is useless. Security means the resistance against malicious, intentional modifications of the watermarked signal. Depending on the application scenario we can distinguish four types of attacks. Unauthorized detection allows the attacker to detect the existence of a watermark or extract the watermark information. Unauthorized removal tries to remove the embedded watermark information. Unauthorized embedding attempts to embed a watermark without the correct authorization. Finally a system attack tries to exploit weaknesses in the overall system. 4 In previous work the following techniques to enhance the security of watermarks have been proposed. Pseudorandom skipping of coefficients has been proposed by Wang 2 or Kundur, 3 but skipping significant coefficients reduces the capacity of the systems. Fridrich 4 introduced the concept of key-dependent basis functions in order to protect a watermark from hostile attacks. By embedding the watermark information in a secret transform Further author information: {wdietl,pmeerw,uhl}@cosy.sbg.ac.at Address: Jakob-Haringerstrasse 2, 52 Salzburg, Austria / Europe
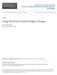
2 Host Image Wavelet Decomposition Watermarked Image Daubechies-6 parametric Forward DWT Inverse DWT Filter Parameters Watermark Embedding Filter Parameters (a) Proposed System (b) Wavelet Filters Figure. Overview of watermark embedding procedure using parametrized wavelet filters (a) and a comparison of the standard Daubechies 6 and a parametrized wavelet filter using α =.485 and α = (b) domain, Fridrich s algorithm can better withstand attacks such as those described by Kalker 5 employing a public watermark detector device. However, Fridrich s approach suffers from the computational complexity and the storage requirements for generating numerous orthogonal patterns of the size of the host image. In a later paper Fridrich reduced the computational complexity of the system. 6 In this paper we propose the use of parametrized wavelet filters as a method to protect wavelet-based watermarks against unauthorized detection. We demonstrate this approach with the algorithms by Kim 7 and Wang. 2 Both use spread-spectrum techniques and need the original image to extract the watermark. In section 2 we introduce wavelet filter parametrization and then use it in a six parameter system in section 3 and in a system with different numbers of parameters in section 4. We present a combined system that uses a total of 2 filter parameters in section 5 and close with the conlusions in section WAVELET FILTER PARAMETRIZATION In order to construct compactly supported orthonormal wavelets, solutions for the dilation equation φ(t) = k c k φ(2t k), with c k, have to be derived, satisfying two conditions on the coefficients c k. 6 Schneid 8 describes a parametrization for suitable coefficients c k based on the work of Zou 9 to facilitate construction of such wavelets. Given N parameter values π α i < π, i < N, the recursion c = 2 and c = 2 c n k = 2 ( (c n k 2 + cn k ) ( + cos α n ) + (c n 2(n+) k cn 2(n+) k 3 )( )k sin α n ) can be used to determine the filter coefficients c N k, k < 2N + 2. We set c k = for k < and k 2N + 2. We propose to decompose the host image using wavelet filters constructed with the above parametrization. The parameter values α i used for construction and the resulting wavelet filter coefficients are kept secret. Hence, the watermark information can be embedded in a secret multi-resolution transform domain, making it difficult to mount a hostile attack that seeks to destroy or remove watermark information at specific locations. Our concept is illustrated in figure (a) and in figure (b) a standard Daubechies 6 filter is compared with a parametrized filter with N = 2 that was generated using α =.485 and α = , resulting in a 6-tap filter. Our approach to generating key-dependent wavelet filters is, in principle, applicable to all wavelet-based watermarking systems and can also be integrated with the JPEG2, Part 2, standard for image compression.
3 kim on lena with 4 db PSNR kim on lena with 4 db PSNR (a) One filter with six parameters (b) Six filters each with one parameter Figure 2. Security assessment of the Kim algorithm Overview 3. NON-STATIONARY DECOMPOSITION WITH SIX PARAMETERS In previous work 2, 2 we analyzed the security and quality aspects of using two filter parameters as watermarking key. We have seen that with two parameters we have a keyspace from a few hundred-thousands to a few millions, depending on the selected resolution. We have two options if we are interested in a larger possible keyspace. We could use more than two parameters to create a filter or use different filters for the different wavelet decomposition levels, which is also called Non- Stationary Multi-Resolution Analysis (NSMRA). 22 Of course we can also combine those two possibilities. Non-stationary MRA can be used for improving image compression. 23 Here we use non-stationary MRA as a method to increase security. To get a larger parameter space we use different parametrized filters for the decomposition levels. We hope that the number of parameters for the different levels add up and produce a system with a large number of parameters. In this section we are going to look at different possibilities to distribute six parameters over the decomposition levels. We analyze different parameter numbers in detail in section 4 and look at a combined system in section 5. We experimented with different distributions of the six parameters over the decomposition levels. Because of space restrictions we can only present a subset of the available results. For the security assessment we only present the two extreme cases. We either use all six parameters to generate one filter and use that filter for all decomposition levels or we use every single parameter to create a filter that is used for one of the six decomposition levels. For the robustness assessment against JPEG2 and JPEG compression we present the results for the four systems that use an equal number of parameters for every level. This includes the two extreme cases, plus using two or three parameters per filter. We do not present the results for the systems that use a different number of parameters for the different decomposition levels. 3.. Protection Against Unauthorized Detection To test the security of the system we embed a fixed watermark with one key parametrization and then try to detect the watermark with other parametrizations. The optimal system would have a normalized correlation between the embedded and the extracted mark of. only with the correct parameters and would be zero everywhere else. We embed the watermark into the well-known Lena image with an embedding strength that results in 4dB PSNR. We use the parameters to embed the watermark. The overview diagrams vary all the parameters with ±. around the correct value and use a step size =.5. This results in 5 possibilities for every parameter and a total of 5 6 = 5625 analyzed filter parametrizations. Using =.5 over the complete parameter space results in more than 2 4 possible filter parametrizations.
4 kim on lena with 4 db PSNR kim on lena with 4 db PSNR kim on lena with 4 db PSNR (a) Detail A (b) Detail B (c) Detail F Figure 3. Security assessment of the Kim algorithm One filter with six parameters kim on lena with 4 db PSNR kim on lena with 4 db PSNR kim on lena with 4 db PSNR (a) Detail A (b) Detail B (c) Detail F Figure 4. Security assessment of the Kim algorithm Six filters each with one parameter The detail diagrams vary only one parameter with ±.2 and =.2; all the other parameters are set to the correct key position. This results in.4/.2 + = 2 analyzed filters. Detail A means that only the first of the six parameters is varied, Detail B that only the second parameter is varied and so on. We only present the detailed results for parameters, 2 and 6. Figure 2(a) shows the behavior when the Kim algorithm is used and all six parameters are used to generate one filter. The response when just one parameter is modified is shown in figure 3. There is one clear peak at the embedding position and all other correlation values are below.4. All detail diagrams show just a very small area of high correlation and an impact from all parameters. The other extreme case is that every parameter is used for a different filter, generating six filters for six decomposition levels. Figure 2(b) gives the overview and figure 4 the single parameter behavior. We can already see from the overview that there is a security problem. There is a range from roughly parametrization 6 to 9 that has a correlation of more than.7. This means that even if you are only close to the correct embedding parameters you already get a very high correlation value. By looking at figure 4 we see what the problem is. Figure (a) shows good behavior and we only have one peak in the correlation. But as soon as the first parameter has the correct value we have an increase in correlation to more than.7. Figure (b) has a correlation of nearly.8 over the complete parameter range. The other parameters look even worse. In figure (c) there is no significant difference in correlation if you vary the parameter for the sixth decomposition level. Clearly the security of this system is not what we expect. From all six parameters only the first one has real significance. The other five parameters do not influence the correlation in the expected way. When the Wang algorithm is used and we let all six parameters produce one filter, then we get the results shown in figures 5(a) and 6. As expected there is one clear peak and generally very low correlation everywhere
5 wang on lena with 4 db PSNR wang on lena with 4 db PSNR (a) One filter with six parameters (b) Six filters each with one parameter Figure 5. Security assessment of the Wang algorithm Overview wang on lena with 4 db PSNR wang on lena with 4 db PSNR wang on lena with 4 db PSNR (a) Detail A (b) Detail B (c) Detail F Figure 6. Security assessment of the Wang algorithm One filter with six parameters else. Also the influence from each of the six parameters looks similar and each one has a very small area of high correlation. Figures 5(b) and 7 show the six parameters distributed over six filters. With the Wang embedding scheme we see very good results. Figures 7(a) and (b) look very good and only have one clear peak. Figure 7(c) has a larger area of high correlation, but still shows that even the last parameter has an effect on the correlation. We see that using the Wang watermarking method with non-stationary MRA shows higher security than wang on lena with 4 db PSNR wang on lena with 4 db PSNR wang on lena with 4 db PSNR (a) Detail A (b) Detail B (c) Detail F Figure 7. Security assessment of the Wang algorithm Six filters each with one parameter
6 Six Filters Three Filters Two Filters One Filter Six Filters Three Filters Two Filters One Filter JPEG2 Rate JPEG Quality (a) JPEG2 (b) JPEG Figure 8. Quality assessment of the Kim algorithm under JPEG2 and JPEG compression using the Kim method. All parameters from all decomposition levels have an influence on the correlation result. NSMRA can be used to increase the parameter-space and enhance the security of the system only if the Wang method is used. The different sequence of levels selected by the Wang algorithm is a clear advantage over the top-down approach used by Kim Quality Assessment and Robustness To analyze the influence of the parametrized filters on the image quality and correlation under compression we embed a watermark with different filters. Each filter parameter α i is chosen from {.5,.5, 2.5}, therefore we assess 3 6 = 729 different parametrizations. Again we choose an embedding strength that results in 4dB PSNR with the Lena image. Then we compress the watermarked images using JPEG and JPEG2 with different quality levels. We measure the PSNR of the compressed image to see the effect of the parameterized filters on the image quality. We also try to detect the watermark in the compressed image with the known parameters and measure the resulting correlation between the embedded and the extracted watermarks. Then the minimum, maximum and average of all parametrized filters are calculated and used for comparing the different parameter distributions. The average results for the Kim algorithm are presented in figure 8. In both figures you can see that the correlation after strong compression is better when the filter was generated from fewer parameters. For a JPEG2 compression rate of.5 the system that uses all six parameters to create the filters has a correlation of around. below the correlation for the system that uses each parameter to create six different filters. The behavior of the Wang systems is shown in figure 9. It is again clear to see that for compression rates between.5 and.25 the shorter filters show better resistance to the compression. For a JPEG2 rate of.5 the correlation for the single-parameter filters is around. higher than the correlation for the six-parameter filter. For JPEG compression the filters that were generated by one or two parameters are clearly above the filters generated by six parameters. The difference at a quality factor of is.8 in advantage of the shorter filters. 4. DIFFERENT NUMBERS OF PARAMETERS In the last section we looked at the distribution of six parameters over the different decomposition levels. For the quality assessment we varied the α i {.5,.5, 2.5}, which results in 729 different parametrizations. Now if the six parameters are used for one long filter we have 3 6 = 729 different filters that are used for the decompositions. But if we use each single parameter to create a filter, then we only have 3 distinct filters that are distributed in different combinations over the six decomposition levels.
7 Six Filters Three Filters Two Filters One Filter Six Filters Three Filters Two Filters One Filter JPEG2 Rate JPEG Quality (a) JPEG2 (b) JPEG Figure 9. Quality assessment of the Wang algorithm and PSNR under JPEG2 and JPEG compression Corrrelation.4 PSNR Length Length 2 Length 3 Length 5 Length 6 Length Length Length 2 Length 3 Length 5 Length 6 Length JPEG2 Rate JPEG2 Rate (a) JPEG2 (b) JPEG2 PSNR Figure. Systems with a different number of parameters under JPEG2 compression The different number of parametrizations used for the different filter lengths could produce skewed results. To make sure the different filter lengths produce comparable results we now look at filters with, 2, 3, 5, 6 and 9 parameters. For each length we choose parameters to get between 52 and 24 different filter parametrizations. The same filter is used for all decomposition levels. We present the average results for the Wang algorithm alone, because we have already seen that using the Kim algorithm results in inferior security. Figure (a) shows the average correlation under JPEG2 compression. As expected the longer filters show worse behavior under compression. What needs to be noted is the behavior of the nine parameter filters. They show an average correlation of around.2 below the other filters. A look at the minimum correlation revealed that there are filters with which no correlation could be detected. Close inspection showed that for more than % of the 9 parameter filters the wavelet decomposition and composition could not be performed with 4dB PSNR. Even without modification from the watermarking algorithms these filters created distorted images with a quality below 4dB PSNR. The influence of the different number of filter parameters on the image quality (as measured by the PSNR) is minimal. Figure (b) shows the average PSNR under JPEG2 compression. The longer filters show only a slight advantage for compression rates between.5 and.25. The same behavior can be seen under JPEG compression, shown in figure. Figure (a) shows the average correlation under JPEG compression. Filters with, 2 and 3 parameters are very close together, but are clearly
8 Corrrelation.6.4 PSNR Length Length 2 Length 3 Length 5 Length 6 Length Length Length 2 Length 3 Length 5 Length 6 Length JPEG Quality JPEG Quality (a) JPEG (b) JPEG PSNR Figure. Systems with a different number of parameters under JPEG compression separated from the 5 and 6 parameter filters. We again see that the average value for the 9 parameter case is around.2 below the other values. The average PSNR under JPEG compression is shown in figure (b). From a compression quality of 9 down to the longer filters have a higher PSNR than the shorter filters. But again the difference is rather small. From these results we see that the shorter filters do show better correlation behavior under compression. A comparable number of different filters was used for the different filter lengths to make sure that the results are not skewed. We also repeated the experiments with 52 random parameter selections for every filter length and got the same results. 5. MULTI-LEVEL SYSTEM Now we present a combined system that only uses the Wang algorithm. We use filters that are generated by five parameters and use four different filters for the first four decomposition levels. This results in a combined system with 2 parameters as embedding key. 5.. Protection Against Unauthorized Detection For 2 parameters examining every parameter variation is not easily possible. Therefore we decided to look at the system and try to attack it. The attacker knows the basic design of the system, but does not know the key that was used for embedding. He in turn looks at the different decomposition levels and tries to independently guess the value of the 5 parameters used for that level. The parameters for the lower levels are set to zero. The watermark was embedded using the parameter values: Parameter Level Level Level Level 4 + higher In the following tests we vary all five parameters for each level at the same time. We take the starting value.6 below the correct value for each of the five parameters. Then we increment the parameters by.2 until all parameters are.6 above the correct value. We therefore have 7 5 = 687 measurements for every level.
9 -.2 wang on lena with 4 db PSNR wang on lena with 4 db PSNR wang on lena with 4 db PSNR wang on lena with 4 db PSNR (a) First Level (b) Second Level (c) Third Level (d) Fourth Level Figure 2. Guessing all four levels of the multi-level system wang on lena with 4 db PSNR wang on lena with 4 db PSNR wang on lena with 4 db PSNR wang on lena with 4 db PSNR (a) First Level (b) Second Level (c) Third Level (d) Fourth Level Figure 3. Variations of all levels of the multi-level system In figure 2(a) we try to attack the first level. We vary the five parameters for the first decomposition level and keep the other parameters set to zero. From the correlation response to the different parametrizations there is no way for the attacker to guess the correct values. If for some reason the attacker knows the correct parameter values for the first decomposition level, then he only needs to search for the remaining 5 parameters. Again we focus on the next set of five parameters used for the second decomposition level. The first decomposition is performed with the correct filter and the third and higher filter parametrizations are unknown to the attacker. In figure 2(b) we see that the attacker did not get any additional knowledge from knowing the first decomposition filter. The correlation is low over the complete range of guessed parametrizations, although the correct parametrization for the second decomposition level was tested. The same is true for the third level. If we already have the first and second decomposition level parameters and only need to find the third and fourth level, then we will again first try to find the five parameters for the third decomposition. Figure 2(c) shows the correlation when the first two levels are set to the correct keys, the fourth level is set to zero and the five parameters for the third level are varied over a set of parametrizations that contain the correct parameter values. Again there is no sign which of the tested parametrizations is the correct one and the attacker has no way of knowing that he has tested the correct parameters for the third level. Only in case the attacker already knows the decomposition parameters for the first three levels is he able to determine the correct parameters for the fourth level. In figure 2(d) the attacker already knows the first 5 keys and only varies the last five parameters for the fourth decomposition level. There is a clear peak at the location of the correct embedding parametrization and low correlation everywhere else. So only after having all 2 parameters right does the attacker get a high correlation. Next we look at the sensitivity of the different levels to parameter changes. We set all levels to the correct embedding parameters and only vary the five parameters for one level and measure the correlation. In figure 3(a) we vary the parameters for the first level and have the correct values for the other three levels. There is one peak at the embedding position and low correlation everywhere else. For levels two and three we see the
10 -.2 kim on lena with 4 db PSNR kim on lena with 4 db PSNR kim on lena with 4 db PSNR (a) First Level (b) Second Level (c) Third Level Figure 4. Multi-level system with Kim embedding Guessing the first three levels PSNR Multi-Level 2 Average Multi-Level 2 Minimum Multi-Level 2 Maximum Daubechies-6 Biorthogonal 7, Multi-Level 2 Average Multi-Level 2 Minimum Multi-Level 2 Maximum Daubechies-6 Biorthogonal 7, JPEG2 Rate JPEG2 Rate (a) JPEG2 (b) JPEG2 PSNR Figure 5. and PSNR of multi-level system under JPEG2 compression respective results in figures 3(b) and 3(c). For the fourth level this attack is the same as the previous attack on the fourth level. The results are shown again in figure 3(d). We see that the first level has higher correlation for wrong parameter values. Overall the behavior of the system is very good and there is always one clear peak. To give a clear view of the security advantage of using the Wang embedding scheme we show the attacks on the first three levels for the Kim method in figure 4. For figure 4(a) we varied the five parameters for the first levels and set all remaining 5 parameters to zero. There is one clear peak with a correlation of around.3. So although we do not get a. correlation by only guessing the first level we still see a significantly higher correlation for the correct parameters for this level. Now by using the correct filters for the first level, setting the third and higher levels to zero and only varying the second level parameters we get figure 4(b). The first thing to notice is that the correlation is above.2 for all tested parametrizations. But again there is a significantly higher correlation for the correct filter parametrization. We see the same behavior for the third and fourth levels, only that the overall correlation gets higher and higher. From this last experiment we conclude that only by using the Wang embedding algorithm we get the real security of all 2 parameters. Using 2 filter parameters we get a vast key space. If we use a resolution of.2 we have around (2 π/.2) possible filter parametrizations. For a finer resolution of. we get (2 π/.) filters. If we choose a parameter resolution between.2 and. we have a very large key space and have very good separation between the correct key and incorrect embedding parametrizations Quality Assessment and Robustness In this investigation we look at the correlation and PSNR behavior of the combined system under JPEG and JPEG2 compression. We create 768 different filter parametrizations by randomly choosing values for the 2
11 PSNR Multi-Level 2 Average Multi-Level 2 Minimum Multi-Level 2 Maximum Daubechies-6 Biorthogonal 7, Multi-Level 2 Average Multi-Level 2 Minimum Multi-Level 2 Maximum Daubechies-6 Biorthogonal 7, JPEG Quality JPEG Quality (a) JPEG (b) JPEG PSNR Figure 6. and PSNR of multi-level system under JPEG compression parameters between -3.4 and 3.4. For each parametrization we embed a given watermark with an embedding strength that results in 4dB PSNR into the Lena image. Then we compress the watermarked image with JPEG and JPEG2 at different compression rates. We try to detect the watermark in the compressed images and measure the correlation between the extracted watermark and the embedded one. Also the PSNR is measured to determine how strongly distorted the compressed image is. We calculate the average, minimum and maximum values from all 768 different parametrizations and compare the results for the combined system to the results for the two standard systems using the Daubechies 6 and the Biorthogonal 7/9 filters. Figure 5(a) shows the correlation behavior under JPEG2 compression, figure (b) shows the PSNR. The corresponding values for JPEG compression are shown in figure 6(a) and (b). The average behavior of the combined system is very close to the two standard systems. The range of possible behavior includes filters that are above the standard systems and even the worst behaving filters produce acceptable results for medium compression rates. 6. CONCLUSIONS In this work we analyzed the effect of non-stationary decomposition where different filters are used for different decomposition levels. We concluded that the Wang method of selecting significant coefficients is best suited. For the Kim algorithm non-stationary decomposition is not improving the security as much as expected. We also investigated the influence of the number of parameters on the robustness against JPEG and JPEG2 compression. We have seen that more parameters lead to less resistance against compression. The use of 5 parameters to generate a filter seems to be a good compromise between possible key-space and robustness against compression. Finally we presented a combined system that uses a total of 2 parameters. We use 5 parameters per filter and use four different filters for the non-stationary decomposition. This combination of filter parametrization and non-stationary wavelet decomposition achieves a keyspace of cryptographically reasonable size, with between 2 99 and 2 85 possible filters. Also, robustness against JPEG and JPEG2 compression is on an equal level as compared to the use of standard wavelet filters. ACKNOWLEDGMENTS Part of this work was funded by the Austrian Science Fund FWF project P57 Sicherheit für Bilddaten in Waveletdarstellung.
12 REFERENCES. S. Katzenbeisser and F. A. P. Petitcolas, Information Hiding Techniques for Steganography and Digital Watermarking, Artech House, Dec J. Dittmann, ed., Digitale Wasserzeichen: Grundlagen, Verfahren, Anwendungsgebiete, Springer Verlag, N. F. Johnson, Z. Duric, and S. Jajodia, Information Hiding: Steganography and Watermarking - Attacks and Countermeasures, Kluwer Academic Publishers, I. J. Cox, M. L. Miller, and J. A. Bloom, Digital Watermarking, Morgan Kaufmann, J. J. Eggers and B. Girod, Informed Watermarking, Kluwer Academic Publishers, I. Daubechies, Ten Lectures on Wavelets, no. 6 in CBMS-NSF Series in Applied Mathematics, SIAM Press, Philadelphia, PA, USA, M. Wickerhauser, Adapted wavelet analysis from theory to software, A.K. Peters, Wellesley, Mass., S. Mallat, A wavelet tour of signal processing, Academic Press, ISO/IEC JPEG committee, JPEG 2 image coding system ISO/IEC 5444-:2, Dec. 2.. D. Taubman and M. Marcellin, JPEG2 Image Compression Fundamentals, Standards and Practice, Kluwer Academic Publishers, 22.. P. Meerwald and A. Uhl, A survey of wavelet-domain watermarking algorithms, in Proceedings of SPIE, Electronic Imaging, Security and Watermarking of Multimedia Contents III, P. W. Wong and E. J. Delp, eds., 434, SPIE, (San Jose, CA, USA), Jan H.-J. Wang and C.-C. J. Kuo, Watermark design for embedded wavelet image codec, in Proceedings of the SPIE s 43rd Annual Meeting, Applications of Digital Image Processing, 346, pp , (San Diego, CA, USA), July D. Kundur, Improved digital watermarking through diversity and attack characterization, in Proceedings of the ACM Workshop on Multimedia Security 99, pp , (Orlando, FL, USA), Oct J. Fridrich, A. C. Baldoza, and R. J. Simard, Robust digital watermarking based on key-dependent basis functions, in Information hiding: second international workshop, D. Aucsmith, ed., Lecture notes in computer science 525, pp , Springer Verlag, Berlin, Germany, (Portland, OR, USA), Apr T. Kalker, J.-P. Linnartz, G. Depovere, and M. Maes, On the reliability of detecting electronic watermarks in digital images, in Proceedings of the 9th European Signal Processing Conference, EUSIPCO 98, pp. 3 6, (Island of Rhodes, Greece), Sept J. Fridrich, Key-dependent random image transforms and their applications in image watermarking, in Proceedings of the 999 International Conference on Imaging Science, Systems, and Technology, CISST 99, pp , (Las Vegas, NV, USA), June J. R. Kim and Y. S. Moon, A robust wavelet-based digital watermark using level-adaptive thresholding, in Proceedings of the 6th IEEE International Conference on Image Processing, ICIP 99, p. 22, (Kobe, Japan), Oct J. Schneid and S. Pittner, On the parametrization of the coefficients of dilation equations for compactly supported wavelets, Computing 5, pp , May H. Zou and A. H. Tewfik, Parametrization of compactly supported orthonormal wavelets, IEEE Transactions on Signal Processing 4, pp , Mar P. Meerwald and A. Uhl, Watermark security via wavelet filter parametrization, in Proceedings of the IEEE International Conference on Image Processing (ICIP ), 3, pp. 27 3, IEEE Signal Processing Society, (Thessaloniki, Greece), Oct W. Dietl, P. Meerwald, and A. Uhl, Watermark security via high-resolution wavelet filter parametrization, in Proceedings of 7th International Scientific Conference, Section : Applied Mathematics, K. Stanislav and P. Miron, eds., pp. 2 28, (Košice, Slovakia), May A. Cohen, Non-stationary multiscale analysis, in 24, pp. 3 2, Academic Press, A. Uhl, Image compression using non-stationary and inhomogeneous multiresolution analyses, Image and Vision Computing 4(5), pp , C. Chui, L. Montefusco, and L. Puccio, Wavelets: Theory, Algorithms and Applications, Academic Press, San Diego, 994.
PROTECTION OF WAVELET-BASED WATERMARKING SYSTEMS USING FILTER PARAMETRIZATION
 PROTECTION OF WAVELET-BASED WATERMARKING SYSTEMS USING FILTER PARAMETRIZATION Werner Dietl, Peter Meerwald, Andreas Uhl Department of Scientific Computing, University of Salzburg Jakob-Haringerstrasse
PROTECTION OF WAVELET-BASED WATERMARKING SYSTEMS USING FILTER PARAMETRIZATION Werner Dietl, Peter Meerwald, Andreas Uhl Department of Scientific Computing, University of Salzburg Jakob-Haringerstrasse
A Robust Wavelet-Based Watermarking Algorithm Using Edge Detection
 A Robust Wavelet-Based Watermarking Algorithm Using Edge Detection John N. Ellinas Abstract In this paper, a robust watermarking algorithm using the wavelet transform and edge detection is presented. The
A Robust Wavelet-Based Watermarking Algorithm Using Edge Detection John N. Ellinas Abstract In this paper, a robust watermarking algorithm using the wavelet transform and edge detection is presented. The
Experimental Study on Watermark Interference in Multiple Re-Watermarking
 Experimental Study on Watermark Interference in Multiple Re-Watermarking Daniel Mark 1, Andreas Uhl 1,2, and Hartmut Wernisch 2 1 School of Telematics & Network Engineering, Carinthia Tech Institute (CTI),
Experimental Study on Watermark Interference in Multiple Re-Watermarking Daniel Mark 1, Andreas Uhl 1,2, and Hartmut Wernisch 2 1 School of Telematics & Network Engineering, Carinthia Tech Institute (CTI),
Data Hiding in Video
 Data Hiding in Video J. J. Chae and B. S. Manjunath Department of Electrical and Computer Engineering University of California, Santa Barbara, CA 9316-956 Email: chaejj, manj@iplab.ece.ucsb.edu Abstract
Data Hiding in Video J. J. Chae and B. S. Manjunath Department of Electrical and Computer Engineering University of California, Santa Barbara, CA 9316-956 Email: chaejj, manj@iplab.ece.ucsb.edu Abstract
FRAGILE WATERMARKING USING SUBBAND CODING
 ICCVG 2002 Zakopane, 25-29 Sept. 2002 Roger ŚWIERCZYŃSKI Institute of Electronics and Telecommunication Poznań University of Technology roger@et.put.poznan.pl FRAGILE WATERMARKING USING SUBBAND CODING
ICCVG 2002 Zakopane, 25-29 Sept. 2002 Roger ŚWIERCZYŃSKI Institute of Electronics and Telecommunication Poznań University of Technology roger@et.put.poznan.pl FRAGILE WATERMARKING USING SUBBAND CODING
A ROBUST WATERMARKING SCHEME BASED ON EDGE DETECTION AND CONTRAST SENSITIVITY FUNCTION
 A ROBUST WATERMARKING SCHEME BASED ON EDGE DETECTION AND CONTRAST SENSITIVITY FUNCTION John N. Ellinas Department of Electronic Computer Systems,Technological Education Institute of Piraeus, 12244 Egaleo,
A ROBUST WATERMARKING SCHEME BASED ON EDGE DETECTION AND CONTRAST SENSITIVITY FUNCTION John N. Ellinas Department of Electronic Computer Systems,Technological Education Institute of Piraeus, 12244 Egaleo,
Robust Image Watermarking based on DCT-DWT- SVD Method
 Robust Image Watermarking based on DCT-DWT- SVD Sneha Jose Rajesh Cherian Roy, PhD. Sreenesh Shashidharan ABSTRACT Hybrid Image watermarking scheme proposed based on Discrete Cosine Transform (DCT)-Discrete
Robust Image Watermarking based on DCT-DWT- SVD Sneha Jose Rajesh Cherian Roy, PhD. Sreenesh Shashidharan ABSTRACT Hybrid Image watermarking scheme proposed based on Discrete Cosine Transform (DCT)-Discrete
COMPARISONS OF DCT-BASED AND DWT-BASED WATERMARKING TECHNIQUES
 COMPARISONS OF DCT-BASED AND DWT-BASED WATERMARKING TECHNIQUES H. I. Saleh 1, M. E. Elhadedy 2, M. A. Ashour 1, M. A. Aboelsaud 3 1 Radiation Engineering Dept., NCRRT, AEA, Egypt. 2 Reactor Dept., NRC,
COMPARISONS OF DCT-BASED AND DWT-BASED WATERMARKING TECHNIQUES H. I. Saleh 1, M. E. Elhadedy 2, M. A. Ashour 1, M. A. Aboelsaud 3 1 Radiation Engineering Dept., NCRRT, AEA, Egypt. 2 Reactor Dept., NRC,
Fidelity Analysis of Additive and Multiplicative Watermarked Images in Integrated Domain
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 16, Issue 5, Ver. III (Sep Oct. 2014), PP 36-41 Fidelity Analysis of Additive and Multiplicative Watermarked
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 16, Issue 5, Ver. III (Sep Oct. 2014), PP 36-41 Fidelity Analysis of Additive and Multiplicative Watermarked
A Novel Secure Digital Watermark Generation from Public Share by Using Visual Cryptography and MAC Techniques
 Bashar S. Mahdi Alia K. Abdul Hassan Department of Computer Science, University of Technology, Baghdad, Iraq A Novel Secure Digital Watermark Generation from Public Share by Using Visual Cryptography and
Bashar S. Mahdi Alia K. Abdul Hassan Department of Computer Science, University of Technology, Baghdad, Iraq A Novel Secure Digital Watermark Generation from Public Share by Using Visual Cryptography and
arxiv: v1 [cs.mm] 9 Aug 2017
![arxiv: v1 [cs.mm] 9 Aug 2017 arxiv: v1 [cs.mm] 9 Aug 2017](/thumbs/87/95906594.jpg) Robust Video Watermarking against H.264 and H.265 Compression Attacks Nematollah Zarmehi 1* and Mohammad Javad Barikbin 2 1 Advanced Communication Research Institute, Electrical Engineering Department,
Robust Video Watermarking against H.264 and H.265 Compression Attacks Nematollah Zarmehi 1* and Mohammad Javad Barikbin 2 1 Advanced Communication Research Institute, Electrical Engineering Department,
QUANTIZATION WATERMARKING IN THE JPEG2000 CODING PIPELINE
 69 QUANTIZATION WATERMARKING IN THE JPEG2000 CODING PIPELINE Peter Meerwald Department of Scientific Computing, University of Salzburg, Jakob-Haringer-Str. 2, A-5020 Salzburg, Austria pmeerw
69 QUANTIZATION WATERMARKING IN THE JPEG2000 CODING PIPELINE Peter Meerwald Department of Scientific Computing, University of Salzburg, Jakob-Haringer-Str. 2, A-5020 Salzburg, Austria pmeerw
Image Watermarking with Biorthogonal and Coiflet Wavelets at Different Levels
 International Journal of Computer Science & Communication Vol., No. 2, July-December 200, pp. 35-356 Image Watermarking with Biorthogonal and Coiflet Wavelets at Different Levels Kirti Arora Jasuja & Baljit
International Journal of Computer Science & Communication Vol., No. 2, July-December 200, pp. 35-356 Image Watermarking with Biorthogonal and Coiflet Wavelets at Different Levels Kirti Arora Jasuja & Baljit
Speech Modulation for Image Watermarking
 Speech Modulation for Image Watermarking Mourad Talbi 1, Ben Fatima Sira 2 1 Center of Researches and Technologies of Energy, Tunisia 2 Engineering School of Tunis, Tunisia Abstract Embedding a hidden
Speech Modulation for Image Watermarking Mourad Talbi 1, Ben Fatima Sira 2 1 Center of Researches and Technologies of Energy, Tunisia 2 Engineering School of Tunis, Tunisia Abstract Embedding a hidden
Digital Watermarking of Still Images using the Discrete Wavelet Transform
 Buletinul Ştiinţific al Universităţii "Politehnica" din Timişoara Seria ELECTROICĂ şi TELECOMUICAŢII TRASACTIOS on ELECTROICS and COMMUICATIOS Tom 48(62) Fascicola 1 2003 Digital Watermarking of Still
Buletinul Ştiinţific al Universităţii "Politehnica" din Timişoara Seria ELECTROICĂ şi TELECOMUICAŢII TRASACTIOS on ELECTROICS and COMMUICATIOS Tom 48(62) Fascicola 1 2003 Digital Watermarking of Still
A New Approach to Compressed Image Steganography Using Wavelet Transform
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 17, Issue 5, Ver. III (Sep. Oct. 2015), PP 53-59 www.iosrjournals.org A New Approach to Compressed Image Steganography
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661,p-ISSN: 2278-8727, Volume 17, Issue 5, Ver. III (Sep. Oct. 2015), PP 53-59 www.iosrjournals.org A New Approach to Compressed Image Steganography
ROBUST VISUAL HASHING USING JPEG 2000
 ROBUST VISUAL HASHING USING JPEG 000 Roland Norcen and Andreas Uhl Department of Scientific Computing, Salzburg University Abstract Robust visual hash functions have been designed to ensure the data integrity
ROBUST VISUAL HASHING USING JPEG 000 Roland Norcen and Andreas Uhl Department of Scientific Computing, Salzburg University Abstract Robust visual hash functions have been designed to ensure the data integrity
Bit-Plane Decomposition Steganography Using Wavelet Compressed Video
 Bit-Plane Decomposition Steganography Using Wavelet Compressed Video Tomonori Furuta, Hideki Noda, Michiharu Niimi, Eiji Kawaguchi Kyushu Institute of Technology, Dept. of Electrical, Electronic and Computer
Bit-Plane Decomposition Steganography Using Wavelet Compressed Video Tomonori Furuta, Hideki Noda, Michiharu Niimi, Eiji Kawaguchi Kyushu Institute of Technology, Dept. of Electrical, Electronic and Computer
No Reference Medical Image Quality Measurement Based on Spread Spectrum and Discrete Wavelet Transform using ROI Processing
 No Reference Medical Image Quality Measurement Based on Spread Spectrum and Discrete Wavelet Transform using ROI Processing Arash Ashtari Nakhaie, Shahriar Baradaran Shokouhi Iran University of Science
No Reference Medical Image Quality Measurement Based on Spread Spectrum and Discrete Wavelet Transform using ROI Processing Arash Ashtari Nakhaie, Shahriar Baradaran Shokouhi Iran University of Science
Authentication and Secret Message Transmission Technique Using Discrete Fourier Transformation
 , 2009, 5, 363-370 doi:10.4236/ijcns.2009.25040 Published Online August 2009 (http://www.scirp.org/journal/ijcns/). Authentication and Secret Message Transmission Technique Using Discrete Fourier Transformation
, 2009, 5, 363-370 doi:10.4236/ijcns.2009.25040 Published Online August 2009 (http://www.scirp.org/journal/ijcns/). Authentication and Secret Message Transmission Technique Using Discrete Fourier Transformation
ENTROPY-BASED IMAGE WATERMARKING USING DWT AND HVS
 SETIT 2005 3 rd International Conference: Sciences of Electronic, Technologies of Information and Telecommunications March 27-31, 2005 TUNISIA ENTROPY-BASED IMAGE WATERMARKING USING DWT AND HVS Shiva Zaboli
SETIT 2005 3 rd International Conference: Sciences of Electronic, Technologies of Information and Telecommunications March 27-31, 2005 TUNISIA ENTROPY-BASED IMAGE WATERMARKING USING DWT AND HVS Shiva Zaboli
Research Article A Novel Steganalytic Algorithm based on III Level DWT with Energy as Feature
 Research Journal of Applied Sciences, Engineering and Technology 7(19): 4100-4105, 2014 DOI:10.19026/rjaset.7.773 ISSN: 2040-7459; e-issn: 2040-7467 2014 Maxwell Scientific Publication Corp. Submitted:
Research Journal of Applied Sciences, Engineering and Technology 7(19): 4100-4105, 2014 DOI:10.19026/rjaset.7.773 ISSN: 2040-7459; e-issn: 2040-7467 2014 Maxwell Scientific Publication Corp. Submitted:
A NEW ROBUST IMAGE WATERMARKING SCHEME BASED ON DWT WITH SVD
 A NEW ROBUST IMAGE WATERMARKING SCHEME BASED ON WITH S.Shanmugaprabha PG Scholar, Dept of Computer Science & Engineering VMKV Engineering College, Salem India N.Malmurugan Director Sri Ranganathar Institute
A NEW ROBUST IMAGE WATERMARKING SCHEME BASED ON WITH S.Shanmugaprabha PG Scholar, Dept of Computer Science & Engineering VMKV Engineering College, Salem India N.Malmurugan Director Sri Ranganathar Institute
A NEW DCT-BASED WATERMARKING METHOD FOR COPYRIGHT PROTECTION OF DIGITAL AUDIO
 International journal of computer science & information Technology (IJCSIT) Vol., No.5, October A NEW DCT-BASED WATERMARKING METHOD FOR COPYRIGHT PROTECTION OF DIGITAL AUDIO Pranab Kumar Dhar *, Mohammad
International journal of computer science & information Technology (IJCSIT) Vol., No.5, October A NEW DCT-BASED WATERMARKING METHOD FOR COPYRIGHT PROTECTION OF DIGITAL AUDIO Pranab Kumar Dhar *, Mohammad
Robust Image Watermarking based on Discrete Wavelet Transform, Discrete Cosine Transform & Singular Value Decomposition
 Advance in Electronic and Electric Engineering. ISSN 2231-1297, Volume 3, Number 8 (2013), pp. 971-976 Research India Publications http://www.ripublication.com/aeee.htm Robust Image Watermarking based
Advance in Electronic and Electric Engineering. ISSN 2231-1297, Volume 3, Number 8 (2013), pp. 971-976 Research India Publications http://www.ripublication.com/aeee.htm Robust Image Watermarking based
DIGITAL IMAGE WATERMARKING TECHNIQUES FOR IMAGES USING TWO-DIMENSIONAL WALSH CODING
 DIGITAL IMAGE WATERMARKING TECHNIQUES FOR IMAGES USING TWO-DIMENSIONAL WALSH CODING Ajeet Pratap Singh 1, Sachin Kumar 2 1,2 Department of ECE, ASET, Amity University, Lucknow, U.P., (India) ABSTRACT The
DIGITAL IMAGE WATERMARKING TECHNIQUES FOR IMAGES USING TWO-DIMENSIONAL WALSH CODING Ajeet Pratap Singh 1, Sachin Kumar 2 1,2 Department of ECE, ASET, Amity University, Lucknow, U.P., (India) ABSTRACT The
Analysis of Information Hiding Techniques in HEVC.
 Analysis of Information Hiding Techniques in HEVC. Multimedia Processing EE 5359 spring 2015 Advisor: Dr. K. R. Rao Department of Electrical Engineering University of Texas, Arlington Rahul Ankushrao Kawadgave
Analysis of Information Hiding Techniques in HEVC. Multimedia Processing EE 5359 spring 2015 Advisor: Dr. K. R. Rao Department of Electrical Engineering University of Texas, Arlington Rahul Ankushrao Kawadgave
An Improvement Technique based on Structural Similarity Thresholding for Digital Watermarking
 An Improvement Technique based on Structural Similarity Thresholding for Digital Watermarking Amin Banitalebi-Dehkordi1, Mehdi Banitalebi-Dehkordi2, Jamshid Abouei3, and Said Nader-Esfahani4 1 Department
An Improvement Technique based on Structural Similarity Thresholding for Digital Watermarking Amin Banitalebi-Dehkordi1, Mehdi Banitalebi-Dehkordi2, Jamshid Abouei3, and Said Nader-Esfahani4 1 Department
Watermarking Moble Phone Color Images With Error Correction Codes
 IOSR Journal of Electronics & Communication Engineering (IOSR-JECE) ISSN(e) : 2278-1684 ISSN(p) : 2320-334X, PP 05-09 www.iosrjournals.org Watermarking Moble Phone Color Images With Error Correction Codes
IOSR Journal of Electronics & Communication Engineering (IOSR-JECE) ISSN(e) : 2278-1684 ISSN(p) : 2320-334X, PP 05-09 www.iosrjournals.org Watermarking Moble Phone Color Images With Error Correction Codes
Digital Watermarking with Copyright Authentication for Image Communication
 Digital Watermarking with Copyright Authentication for Image Communication Keta Raval Dept. of Electronics and Communication Patel Institute of Engineering and Science RGPV, Bhopal, M.P., India ketaraval@yahoo.com
Digital Watermarking with Copyright Authentication for Image Communication Keta Raval Dept. of Electronics and Communication Patel Institute of Engineering and Science RGPV, Bhopal, M.P., India ketaraval@yahoo.com
Implementation of Audio Watermarking Using Wavelet Families
 Implementation of Audio Watermarking Using Wavelet Families Mr. Kamlesh.C.Badhe, Prof.Jagruti.R.Panchal Dept. of E&TC, SCOE, Sudumbare, Pune, India Dept. of E&TC, SCOE, Sudumbare, Pune, India Abstract
Implementation of Audio Watermarking Using Wavelet Families Mr. Kamlesh.C.Badhe, Prof.Jagruti.R.Panchal Dept. of E&TC, SCOE, Sudumbare, Pune, India Dept. of E&TC, SCOE, Sudumbare, Pune, India Abstract
Implementation of Audio Watermarking Using Wavelet Families
 Implementation of Audio Watermarking Using Wavelet Families Mr. Kamlesh.C.Badhe Dept. of E&TC, SCOE Sudumbare, Pune, India kcbadhe@gmail.com Prof.Jagruti.R.Panchal Dept. of E&TC, SCOE Sudumbare, Pune,
Implementation of Audio Watermarking Using Wavelet Families Mr. Kamlesh.C.Badhe Dept. of E&TC, SCOE Sudumbare, Pune, India kcbadhe@gmail.com Prof.Jagruti.R.Panchal Dept. of E&TC, SCOE Sudumbare, Pune,
An Improved Images Watermarking Scheme Using FABEMD Decomposition and DCT
 An Improved Images Watermarking Scheme Using FABEMD Decomposition and DCT Noura Aherrahrou and Hamid Tairi University Sidi Mohamed Ben Abdellah, Faculty of Sciences, Dhar El mahraz, LIIAN, Department of
An Improved Images Watermarking Scheme Using FABEMD Decomposition and DCT Noura Aherrahrou and Hamid Tairi University Sidi Mohamed Ben Abdellah, Faculty of Sciences, Dhar El mahraz, LIIAN, Department of
Visual Communications and Image Processing 2003, Touradj Ebrahimi, Thomas Sikora, Editors, Proceedings of SPIE Vol (2003) 2003 SPIE
 Zerotree Image Compression using An Wavelet Packet Transform Rade Kutil University of Salzburg, Dept. of Scientific Computing, Austria ABSTRACT The wavelet packet transform is an extension of the conventional
Zerotree Image Compression using An Wavelet Packet Transform Rade Kutil University of Salzburg, Dept. of Scientific Computing, Austria ABSTRACT The wavelet packet transform is an extension of the conventional
Feature Based Watermarking Algorithm by Adopting Arnold Transform
 Feature Based Watermarking Algorithm by Adopting Arnold Transform S.S. Sujatha 1 and M. Mohamed Sathik 2 1 Assistant Professor in Computer Science, S.T. Hindu College, Nagercoil, Tamilnadu, India 2 Associate
Feature Based Watermarking Algorithm by Adopting Arnold Transform S.S. Sujatha 1 and M. Mohamed Sathik 2 1 Assistant Professor in Computer Science, S.T. Hindu College, Nagercoil, Tamilnadu, India 2 Associate
Invisible Digital Watermarking using Discrete Wavelet Transformation and Singular Value Decomposition
 Invisible Digital Watermarking using Discrete Wavelet Transformation and Singular Value Decomposition Nilay Mistry 1, Dhruv Dave 2 1 Computer Department, KSV University L.D.R.P Institute of Technology
Invisible Digital Watermarking using Discrete Wavelet Transformation and Singular Value Decomposition Nilay Mistry 1, Dhruv Dave 2 1 Computer Department, KSV University L.D.R.P Institute of Technology
International Journal for Research in Applied Science & Engineering Technology (IJRASET) Denoising Of Speech Signals Using Wavelets
 Denoising Of Speech Signals Using Wavelets Prashant Arora 1, Kulwinder Singh 2 1,2 Bhai Maha Singh College of Engineering, Sri Muktsar Sahib Abstract: In this paper, we introduced two wavelet i.e. daubechies
Denoising Of Speech Signals Using Wavelets Prashant Arora 1, Kulwinder Singh 2 1,2 Bhai Maha Singh College of Engineering, Sri Muktsar Sahib Abstract: In this paper, we introduced two wavelet i.e. daubechies
Navjot Singh *1, Deepak Sharma 2 ABSTRACT I. INTRODUCTION
 2017 IJSRSET Volume 3 Issue 1 Print ISSN: 2395-1990 Online ISSN : 2394-4099 Themed Section: Engineering and Technology An Efficient Multiple Data Hiding Technique for Medical Images Using QR Code Authentication
2017 IJSRSET Volume 3 Issue 1 Print ISSN: 2395-1990 Online ISSN : 2394-4099 Themed Section: Engineering and Technology An Efficient Multiple Data Hiding Technique for Medical Images Using QR Code Authentication
Evolved Multi-resolution Transforms for Optimized Image Compression and Reconstruction under Quantization
 Evolved Multi-resolution Transforms for Optimized Image Compression and Reconstruction under Quantization FRANK W. MOORE Mathematical Sciences Department University of Alaska Anchorage CAS 154, 3211 Providence
Evolved Multi-resolution Transforms for Optimized Image Compression and Reconstruction under Quantization FRANK W. MOORE Mathematical Sciences Department University of Alaska Anchorage CAS 154, 3211 Providence
An Efficient Watermarking Algorithm Based on DWT and FFT Approach
 An Efficient Watermarking Algorithm Based on DWT and FFT Approach S.Manikanda prabu Assistant Professor, Department of CSE, Tamilnadu College of Engineering, Coimbatore, India smaniprabume@gmail.com Dr.S.Ayyasamy
An Efficient Watermarking Algorithm Based on DWT and FFT Approach S.Manikanda prabu Assistant Professor, Department of CSE, Tamilnadu College of Engineering, Coimbatore, India smaniprabume@gmail.com Dr.S.Ayyasamy
FRACTAL IMAGE COMPRESSION OF GRAYSCALE AND RGB IMAGES USING DCT WITH QUADTREE DECOMPOSITION AND HUFFMAN CODING. Moheb R. Girgis and Mohammed M.
 322 FRACTAL IMAGE COMPRESSION OF GRAYSCALE AND RGB IMAGES USING DCT WITH QUADTREE DECOMPOSITION AND HUFFMAN CODING Moheb R. Girgis and Mohammed M. Talaat Abstract: Fractal image compression (FIC) is a
322 FRACTAL IMAGE COMPRESSION OF GRAYSCALE AND RGB IMAGES USING DCT WITH QUADTREE DECOMPOSITION AND HUFFMAN CODING Moheb R. Girgis and Mohammed M. Talaat Abstract: Fractal image compression (FIC) is a
CHAPTER 3 DIFFERENT DOMAINS OF WATERMARKING. domain. In spatial domain the watermark bits directly added to the pixels of the cover
 38 CHAPTER 3 DIFFERENT DOMAINS OF WATERMARKING Digital image watermarking can be done in both spatial domain and transform domain. In spatial domain the watermark bits directly added to the pixels of the
38 CHAPTER 3 DIFFERENT DOMAINS OF WATERMARKING Digital image watermarking can be done in both spatial domain and transform domain. In spatial domain the watermark bits directly added to the pixels of the
A Robust Image Watermarking Scheme using Image Moment Normalization
 A Robust Image ing Scheme using Image Moment Normalization Latha Parameswaran, and K. Anbumani Abstract Multimedia security is an incredibly significant area of concern. A number of papers on robust digital
A Robust Image ing Scheme using Image Moment Normalization Latha Parameswaran, and K. Anbumani Abstract Multimedia security is an incredibly significant area of concern. A number of papers on robust digital
Robust Digital Image Watermarking based on complex wavelet transform
 Robust Digital Image Watermarking based on complex wavelet transform TERZIJA NATAŠA, GEISSELHARDT WALTER Institute of Information Technology University Duisburg-Essen Bismarckstr. 81, 47057 Duisburg GERMANY
Robust Digital Image Watermarking based on complex wavelet transform TERZIJA NATAŠA, GEISSELHARDT WALTER Institute of Information Technology University Duisburg-Essen Bismarckstr. 81, 47057 Duisburg GERMANY
SPREAD SPECTRUM AUDIO WATERMARKING SCHEME BASED ON PSYCHOACOUSTIC MODEL
 SPREAD SPECTRUM WATERMARKING SCHEME BASED ON PSYCHOACOUSTIC MODEL 1 Yüksel Tokur 2 Ergun Erçelebi e-mail: tokur@gantep.edu.tr e-mail: ercelebi@gantep.edu.tr 1 Gaziantep University, MYO, 27310, Gaziantep,
SPREAD SPECTRUM WATERMARKING SCHEME BASED ON PSYCHOACOUSTIC MODEL 1 Yüksel Tokur 2 Ergun Erçelebi e-mail: tokur@gantep.edu.tr e-mail: ercelebi@gantep.edu.tr 1 Gaziantep University, MYO, 27310, Gaziantep,
SCALED WAVELET TRANSFORM VIDEO WATERMARKING METHOD USING HYBRID TECHNIQUE: SWT-SVD-DCT
 SCALED WAVELET TRANSFORM VIDEO WATERMARKING METHOD USING HYBRID TECHNIQUE: SWT- Shaveta 1, Daljit Kaur 2 1 PG Scholar, 2 Assistant Professor, Dept of IT, Chandigarh Engineering College, Landran, Mohali,
SCALED WAVELET TRANSFORM VIDEO WATERMARKING METHOD USING HYBRID TECHNIQUE: SWT- Shaveta 1, Daljit Kaur 2 1 PG Scholar, 2 Assistant Professor, Dept of IT, Chandigarh Engineering College, Landran, Mohali,
DIGITAL IMAGE WATERMARKING BASED ON A RELATION BETWEEN SPATIAL AND FREQUENCY DOMAINS
 DIGITAL IMAGE WATERMARKING BASED ON A RELATION BETWEEN SPATIAL AND FREQUENCY DOMAINS Murat Furat Mustafa Oral e-mail: mfurat@cu.edu.tr e-mail: moral@mku.edu.tr Cukurova University, Faculty of Engineering,
DIGITAL IMAGE WATERMARKING BASED ON A RELATION BETWEEN SPATIAL AND FREQUENCY DOMAINS Murat Furat Mustafa Oral e-mail: mfurat@cu.edu.tr e-mail: moral@mku.edu.tr Cukurova University, Faculty of Engineering,
DIGITAL WATERMARKING FOR GRAY-LEVEL WATERMARKS
 DICTA22: Digital Image Computing Techniques and Applications, 2 22 January 22, Melbourne, Australia. DIGITAL WATERMARKING FOR GRAY-LEVEL WATERMARKS *Yuk Ying CHUNG, Man To WONG *Basser Department of Computer
DICTA22: Digital Image Computing Techniques and Applications, 2 22 January 22, Melbourne, Australia. DIGITAL WATERMARKING FOR GRAY-LEVEL WATERMARKS *Yuk Ying CHUNG, Man To WONG *Basser Department of Computer
WAVELET TRANSFORM BASED FEATURE DETECTION
 WAVELET TRANSFORM BASED FEATURE DETECTION David Bařina Doctoral Degree Programme (1), DCGM, FIT BUT E-mail: ibarina@fit.vutbr.cz Supervised by: Pavel Zemčík E-mail: zemcik@fit.vutbr.cz ABSTRACT This paper
WAVELET TRANSFORM BASED FEATURE DETECTION David Bařina Doctoral Degree Programme (1), DCGM, FIT BUT E-mail: ibarina@fit.vutbr.cz Supervised by: Pavel Zemčík E-mail: zemcik@fit.vutbr.cz ABSTRACT This paper
CHAPTER 4 REVERSIBLE IMAGE WATERMARKING USING BIT PLANE CODING AND LIFTING WAVELET TRANSFORM
 74 CHAPTER 4 REVERSIBLE IMAGE WATERMARKING USING BIT PLANE CODING AND LIFTING WAVELET TRANSFORM Many data embedding methods use procedures that in which the original image is distorted by quite a small
74 CHAPTER 4 REVERSIBLE IMAGE WATERMARKING USING BIT PLANE CODING AND LIFTING WAVELET TRANSFORM Many data embedding methods use procedures that in which the original image is distorted by quite a small
Performance Analysis of Discrete Wavelet Transform based Audio Watermarking on Indian Classical Songs
 Volume 73 No.6, July 2013 Performance Analysis of Discrete Wavelet Transform based Audio ing on Indian Classical Songs C. M. Juli Janardhanan Department of ECE Government Engineering College, Wayanad Mananthavady,
Volume 73 No.6, July 2013 Performance Analysis of Discrete Wavelet Transform based Audio ing on Indian Classical Songs C. M. Juli Janardhanan Department of ECE Government Engineering College, Wayanad Mananthavady,
Wavelet Transform (WT) & JPEG-2000
 Chapter 8 Wavelet Transform (WT) & JPEG-2000 8.1 A Review of WT 8.1.1 Wave vs. Wavelet [castleman] 1 0-1 -2-3 -4-5 -6-7 -8 0 100 200 300 400 500 600 Figure 8.1 Sinusoidal waves (top two) and wavelets (bottom
Chapter 8 Wavelet Transform (WT) & JPEG-2000 8.1 A Review of WT 8.1.1 Wave vs. Wavelet [castleman] 1 0-1 -2-3 -4-5 -6-7 -8 0 100 200 300 400 500 600 Figure 8.1 Sinusoidal waves (top two) and wavelets (bottom
Semi-Fragile Watermarking in Biometric Systems: Template Self-Embedding
 Semi-Fragile Watermarking in Biometric Systems: Template Self-Embedding Reinhard Huber 1, Herbert Stögner 1, and Andreas Uhl 1,2 1 School of CEIT, Carinthia University of Applied Sciences, Austria 2 Department
Semi-Fragile Watermarking in Biometric Systems: Template Self-Embedding Reinhard Huber 1, Herbert Stögner 1, and Andreas Uhl 1,2 1 School of CEIT, Carinthia University of Applied Sciences, Austria 2 Department
Lifting Wavelet Transform and Singular Values Decomposition for Secure Image Watermarking
 Lifting Wavelet Transform and Singular Values Decomposition for Secure Image Watermarking Siraa Ben Ftima, Mourad Talbi, Tahar Ezzedine Abstract In this paper, we present a technique of secure watermarking
Lifting Wavelet Transform and Singular Values Decomposition for Secure Image Watermarking Siraa Ben Ftima, Mourad Talbi, Tahar Ezzedine Abstract In this paper, we present a technique of secure watermarking
An Improved Blind Watermarking Scheme in Wavelet Domain
 An Improved Blind Watermarking Scheme in Wavelet Domain Hai Tao 1, Jasni Mohamad Zain 1, Ahmed N. Abd Alla 2, Wang Jing 1 1 Faculty of Computer Systems and Software Engineering University Malaysia Pahang
An Improved Blind Watermarking Scheme in Wavelet Domain Hai Tao 1, Jasni Mohamad Zain 1, Ahmed N. Abd Alla 2, Wang Jing 1 1 Faculty of Computer Systems and Software Engineering University Malaysia Pahang
Using Wavelets to Embed Images in Images
 University of Tennessee, Knoxville Trace: Tennessee Research and Creative Exchange University of Tennessee Honors Thesis Projects University of Tennessee Honors Program 3-2004 Using Wavelets to Embed Images
University of Tennessee, Knoxville Trace: Tennessee Research and Creative Exchange University of Tennessee Honors Thesis Projects University of Tennessee Honors Program 3-2004 Using Wavelets to Embed Images
Digital Watermarking: Combining DCT and DWT Techniques
 Digital Watermarking: Combining DCT and DWT Techniques 1 MR. D.G.VAGHELA, 2 MR. V.P.GOHIL, 3 PROF. RAMLAL YADAV 1 M.Tech. [CSE] Student, Department of Computer Engineering, Kautilya Institute Of Technology
Digital Watermarking: Combining DCT and DWT Techniques 1 MR. D.G.VAGHELA, 2 MR. V.P.GOHIL, 3 PROF. RAMLAL YADAV 1 M.Tech. [CSE] Student, Department of Computer Engineering, Kautilya Institute Of Technology
DWT-SVD based Multiple Watermarking Techniques
 International Journal of Engineering Science Invention (IJESI) ISSN (Online): 2319 6734, ISSN (Print): 2319 6726 www.ijesi.org PP. 01-05 DWT-SVD based Multiple Watermarking Techniques C. Ananth 1, Dr.M.Karthikeyan
International Journal of Engineering Science Invention (IJESI) ISSN (Online): 2319 6734, ISSN (Print): 2319 6726 www.ijesi.org PP. 01-05 DWT-SVD based Multiple Watermarking Techniques C. Ananth 1, Dr.M.Karthikeyan
Improved Geometric Warping-Based Watermarking
 Improved Geometric Warping-Based Watermarking Dima Pröfrock, Mathias Schlauweg, Erika Müller Institute of Communication Engineering, Faculty of Computer Science and Electrical Engineering, University of
Improved Geometric Warping-Based Watermarking Dima Pröfrock, Mathias Schlauweg, Erika Müller Institute of Communication Engineering, Faculty of Computer Science and Electrical Engineering, University of
The Choice of Filter Banks for Wavelet-based Robust Digital Watermarking p. 1/18
 The Choice of Filter Banks for Wavelet-based Robust Digital Watermarking Martin Dietze martin.dietze@buckingham.ac.uk Sabah Jassim sabah.jassim@buckingham.ac.uk The University of Buckingham United Kingdom
The Choice of Filter Banks for Wavelet-based Robust Digital Watermarking Martin Dietze martin.dietze@buckingham.ac.uk Sabah Jassim sabah.jassim@buckingham.ac.uk The University of Buckingham United Kingdom
CHAPTER-6 WATERMARKING OF JPEG IMAGES
 CHAPTER-6 WATERMARKING OF JPEG IMAGES 6.1 INTRODUCTION In the Chapter 4, we have discussed that we can improve the robustness of DCT and DWT based watermarking schemes against some well known attacks by
CHAPTER-6 WATERMARKING OF JPEG IMAGES 6.1 INTRODUCTION In the Chapter 4, we have discussed that we can improve the robustness of DCT and DWT based watermarking schemes against some well known attacks by
Digital Image Watermarking using Fuzzy Logic approach based on DWT and SVD
 Digital Watermarking using Fuzzy Logic approach based on DWT and SVD T.Sridevi Associate Professor CBIT Hyderabad,India S Sameena Fatima,Ph.D Professor, OU, Hyderabad,India ABSTRACT Digital image watermarking
Digital Watermarking using Fuzzy Logic approach based on DWT and SVD T.Sridevi Associate Professor CBIT Hyderabad,India S Sameena Fatima,Ph.D Professor, OU, Hyderabad,India ABSTRACT Digital image watermarking
ROBUST WATERMARKING OF REMOTE SENSING IMAGES WITHOUT THE LOSS OF SPATIAL INFORMATION
 ROBUST WATERMARKING OF REMOTE SENSING IMAGES WITHOUT THE LOSS OF SPATIAL INFORMATION T.HEMALATHA, V.JOEVIVEK, K.SUKUMAR, K.P.SOMAN CEN, Amrita Vishwa Vidyapeetham, Coimbatore, Tamilnadu, India. hemahems@gmail.com
ROBUST WATERMARKING OF REMOTE SENSING IMAGES WITHOUT THE LOSS OF SPATIAL INFORMATION T.HEMALATHA, V.JOEVIVEK, K.SUKUMAR, K.P.SOMAN CEN, Amrita Vishwa Vidyapeetham, Coimbatore, Tamilnadu, India. hemahems@gmail.com
Image Enhancement in Digital Image Watermarking Using Hybrid Image Transformation Techniques
 IOSR Journal of Electronics and Communication Engineering (IOSR-JECE) e-issn: 2278-2834,p- ISSN: 2278-8735.Volume 11, Issue 3, Ver. II (May-Jun.2016), PP 116-121 www.iosrjournals.org Image Enhancement
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE) e-issn: 2278-2834,p- ISSN: 2278-8735.Volume 11, Issue 3, Ver. II (May-Jun.2016), PP 116-121 www.iosrjournals.org Image Enhancement
A Novel Audio Watermarking Algorithm Based On Reduced Singular Value Decomposition
 A Novel Audio Watermarking Algorithm Based On Reduced Singular Value Decomposition Jian Wang 1, Ron Healy 2, Joe Timoney 3 Computer Science Department NUI Maynooth, Co. Kildare, Ireland jwang@cs.nuim.ie
A Novel Audio Watermarking Algorithm Based On Reduced Singular Value Decomposition Jian Wang 1, Ron Healy 2, Joe Timoney 3 Computer Science Department NUI Maynooth, Co. Kildare, Ireland jwang@cs.nuim.ie
Compression of RADARSAT Data with Block Adaptive Wavelets Abstract: 1. Introduction
 Compression of RADARSAT Data with Block Adaptive Wavelets Ian Cumming and Jing Wang Department of Electrical and Computer Engineering The University of British Columbia 2356 Main Mall, Vancouver, BC, Canada
Compression of RADARSAT Data with Block Adaptive Wavelets Ian Cumming and Jing Wang Department of Electrical and Computer Engineering The University of British Columbia 2356 Main Mall, Vancouver, BC, Canada
Optimized Progressive Coding of Stereo Images Using Discrete Wavelet Transform
 Optimized Progressive Coding of Stereo Images Using Discrete Wavelet Transform Torsten Palfner, Alexander Mali and Erika Müller Institute of Telecommunications and Information Technology, University of
Optimized Progressive Coding of Stereo Images Using Discrete Wavelet Transform Torsten Palfner, Alexander Mali and Erika Müller Institute of Telecommunications and Information Technology, University of
The Choice of Filter Banks for Wavelet-based Robust Digital Watermarking
 The Choice of Filter Banks for Wavelet-based Robust Digital Watermarking Martin Dietze martin.dietze@buckingham.ac.uk Sabah Jassim sabah.jassim@buckingham.ac.uk The University of Buckingham United Kingdom
The Choice of Filter Banks for Wavelet-based Robust Digital Watermarking Martin Dietze martin.dietze@buckingham.ac.uk Sabah Jassim sabah.jassim@buckingham.ac.uk The University of Buckingham United Kingdom
DIGITAL watermarking technology is emerging as a
 126 IEEE TRANSACTIONS ON IMAGE PROCESSING, VOL. 13, NO. 2, FEBRUARY 2004 Analysis and Design of Watermarking Algorithms for Improved Resistance to Compression Chuhong Fei, Deepa Kundur, Senior Member,
126 IEEE TRANSACTIONS ON IMAGE PROCESSING, VOL. 13, NO. 2, FEBRUARY 2004 Analysis and Design of Watermarking Algorithms for Improved Resistance to Compression Chuhong Fei, Deepa Kundur, Senior Member,
Keywords: DWT, wavelet, coefficient, image steganography, decomposition, stego
 Volume 3, Issue 6, June 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com A DWT Method for
Volume 3, Issue 6, June 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com A DWT Method for
Improved Qualitative Color Image Steganography Based on DWT
 Improved Qualitative Color Image Steganography Based on DWT 1 Naresh Goud M, II Arjun Nelikanti I, II M. Tech student I, II Dept. of CSE, I, II Vardhaman College of Eng. Hyderabad, India Muni Sekhar V
Improved Qualitative Color Image Steganography Based on DWT 1 Naresh Goud M, II Arjun Nelikanti I, II M. Tech student I, II Dept. of CSE, I, II Vardhaman College of Eng. Hyderabad, India Muni Sekhar V
Comparison of Digital Image Watermarking Algorithms. Xu Zhou Colorado School of Mines December 1, 2014
 Comparison of Digital Image Watermarking Algorithms Xu Zhou Colorado School of Mines December 1, 2014 Outlier Introduction Background on digital image watermarking Comparison of several algorithms Experimental
Comparison of Digital Image Watermarking Algorithms Xu Zhou Colorado School of Mines December 1, 2014 Outlier Introduction Background on digital image watermarking Comparison of several algorithms Experimental
Implementation of ContourLet Transform For Copyright Protection of Color Images
 Implementation of ContourLet Transform For Copyright Protection of Color Images * S.janardhanaRao,** Dr K.Rameshbabu Abstract In this paper, a watermarking algorithm that uses the wavelet transform with
Implementation of ContourLet Transform For Copyright Protection of Color Images * S.janardhanaRao,** Dr K.Rameshbabu Abstract In this paper, a watermarking algorithm that uses the wavelet transform with
A Detailed look of Audio Steganography Techniques using LSB and Genetic Algorithm Approach
 www.ijcsi.org 402 A Detailed look of Audio Steganography Techniques using LSB and Genetic Algorithm Approach Gunjan Nehru 1, Puja Dhar 2 1 Department of Information Technology, IEC-Group of Institutions
www.ijcsi.org 402 A Detailed look of Audio Steganography Techniques using LSB and Genetic Algorithm Approach Gunjan Nehru 1, Puja Dhar 2 1 Department of Information Technology, IEC-Group of Institutions
VARIATION-FREE WATERMARKING TECHNIQUE BASED ON SCALE RELATIONSHIP
 ABSTRACT VARIATION-FREE WATERMARKING TECHNIQUE BASED ON SCALE RELATIONSHIP Jung-San Lee, Hsiao-Shan Wong, and Yi-Hua Wang Department of Information Engineering and Computer Science, Feng Chia University,
ABSTRACT VARIATION-FREE WATERMARKING TECHNIQUE BASED ON SCALE RELATIONSHIP Jung-San Lee, Hsiao-Shan Wong, and Yi-Hua Wang Department of Information Engineering and Computer Science, Feng Chia University,
Information Hiding Method Using Best DCT and Wavelet Coefficients and Its Watermark Competition
 Entropy 2015, 17, 1218-1235; doi:10.3390/e17031218 OPEN ACCESS entropy ISSN 1099-4300 www.mdpi.com/journal/entropy Article Information Hiding Method Using Best DCT and Wavelet Coefficients and Its Watermark
Entropy 2015, 17, 1218-1235; doi:10.3390/e17031218 OPEN ACCESS entropy ISSN 1099-4300 www.mdpi.com/journal/entropy Article Information Hiding Method Using Best DCT and Wavelet Coefficients and Its Watermark
Reconstruction PSNR [db]
![Reconstruction PSNR [db] Reconstruction PSNR [db]](/thumbs/72/66578785.jpg) Proc. Vision, Modeling, and Visualization VMV-2000 Saarbrücken, Germany, pp. 199-203, November 2000 Progressive Compression and Rendering of Light Fields Marcus Magnor, Andreas Endmann Telecommunications
Proc. Vision, Modeling, and Visualization VMV-2000 Saarbrücken, Germany, pp. 199-203, November 2000 Progressive Compression and Rendering of Light Fields Marcus Magnor, Andreas Endmann Telecommunications
A Image Comparative Study using DCT, Fast Fourier, Wavelet Transforms and Huffman Algorithm
 International Journal of Engineering Research and General Science Volume 3, Issue 4, July-August, 15 ISSN 91-2730 A Image Comparative Study using DCT, Fast Fourier, Wavelet Transforms and Huffman Algorithm
International Journal of Engineering Research and General Science Volume 3, Issue 4, July-August, 15 ISSN 91-2730 A Image Comparative Study using DCT, Fast Fourier, Wavelet Transforms and Huffman Algorithm
On domain selection for additive, blind image watermarking
 BULLETIN OF THE POLISH ACADEY OF SCIENCES TECHNICAL SCIENCES, Vol. 60, No. 2, 2012 DOI: 10.2478/v10175-012-0042-5 DEDICATED PAPERS On domain selection for additive, blind image watermarking P. LIPIŃSKI
BULLETIN OF THE POLISH ACADEY OF SCIENCES TECHNICAL SCIENCES, Vol. 60, No. 2, 2012 DOI: 10.2478/v10175-012-0042-5 DEDICATED PAPERS On domain selection for additive, blind image watermarking P. LIPIŃSKI
A NOVEL APPROACH FOR IMAGE WATERMARKING USING DCT AND JND TECHNIQUES
 A NOVEL APPROACH FOR IMAGE WATERMARKING USING DCT AND JND TECHNIQUES Mrs. R.J. Shelke, Dept of Electronics Engineering, Walchand Institute of Technology, Solapur 43002, India ABSTRACT Dr. Mrs. S.S. Apte,
A NOVEL APPROACH FOR IMAGE WATERMARKING USING DCT AND JND TECHNIQUES Mrs. R.J. Shelke, Dept of Electronics Engineering, Walchand Institute of Technology, Solapur 43002, India ABSTRACT Dr. Mrs. S.S. Apte,
SPEECH WATERMARKING USING DISCRETE WAVELET TRANSFORM, DISCRETE COSINE TRANSFORM AND SINGULAR VALUE DECOMPOSITION
 SPEECH WATERMARKING USING DISCRETE WAVELET TRANSFORM, DISCRETE COSINE TRANSFORM AND SINGULAR VALUE DECOMPOSITION D. AMBIKA *, Research Scholar, Department of Computer Science, Avinashilingam Institute
SPEECH WATERMARKING USING DISCRETE WAVELET TRANSFORM, DISCRETE COSINE TRANSFORM AND SINGULAR VALUE DECOMPOSITION D. AMBIKA *, Research Scholar, Department of Computer Science, Avinashilingam Institute
A new robust watermarking scheme based on PDE decomposition *
 A new robust watermarking scheme based on PDE decomposition * Noura Aherrahrou University Sidi Mohamed Ben Abdellah Faculty of Sciences Dhar El mahraz LIIAN, Department of Informatics Fez, Morocco Hamid
A new robust watermarking scheme based on PDE decomposition * Noura Aherrahrou University Sidi Mohamed Ben Abdellah Faculty of Sciences Dhar El mahraz LIIAN, Department of Informatics Fez, Morocco Hamid
Application of Daubechies Wavelets for Image Compression
 Application of Daubechies Wavelets for Image Compression Heydari. Aghile 1,*, Naseri.Roghaye 2 1 Department of Math., Payame Noor University, Mashad, IRAN, Email Address a_heidari@pnu.ac.ir, Funded by
Application of Daubechies Wavelets for Image Compression Heydari. Aghile 1,*, Naseri.Roghaye 2 1 Department of Math., Payame Noor University, Mashad, IRAN, Email Address a_heidari@pnu.ac.ir, Funded by
A Wavelet-Based Watermarking for Still Images
 Buletinul Ştiinţific al Universităţii "Politehnica" din Timişoara Seria ELECTRONICĂ şi TELECOMUNICAŢII TRANSACTIONS on ELECTRONICS and COMMUNICATIONS Tom 49(63) Fascicola 2 2004 A Wavelet-Based Watermarking
Buletinul Ştiinţific al Universităţii "Politehnica" din Timişoara Seria ELECTRONICĂ şi TELECOMUNICAŢII TRANSACTIONS on ELECTRONICS and COMMUNICATIONS Tom 49(63) Fascicola 2 2004 A Wavelet-Based Watermarking
Contour Extraction & Compression from Watermarked Image using Discrete Wavelet Transform & Ramer Method
 Contour Extraction & Compression from Watermarked Image using Discrete Wavelet Transform & Ramer Method Ali Ukasha, Majdi Elbireki, and Mohammad Abdullah Abstract In this paper we have implemented a digital
Contour Extraction & Compression from Watermarked Image using Discrete Wavelet Transform & Ramer Method Ali Ukasha, Majdi Elbireki, and Mohammad Abdullah Abstract In this paper we have implemented a digital
Region Based Even Odd Watermarking Method With Fuzzy Wavelet
 Region Based Even Odd Watermarking Method With Fuzzy Wavelet S.Maruthuperumal 1, G.Rosline Nesakumari 1, Dr.V.Vijayakumar 2 1 Research Scholar, Dr.MGR University Chennai. Associate Professor, GIET Rajahmundry,
Region Based Even Odd Watermarking Method With Fuzzy Wavelet S.Maruthuperumal 1, G.Rosline Nesakumari 1, Dr.V.Vijayakumar 2 1 Research Scholar, Dr.MGR University Chennai. Associate Professor, GIET Rajahmundry,
Spatial, Transform and Fractional Domain Digital Image Watermarking Techniques
 Spatial, Transform and Fractional Domain Digital Image Watermarking Techniques Dr.Harpal Singh Professor, Chandigarh Engineering College, Landran, Mohali, Punjab, Pin code 140307, India Puneet Mehta Faculty,
Spatial, Transform and Fractional Domain Digital Image Watermarking Techniques Dr.Harpal Singh Professor, Chandigarh Engineering College, Landran, Mohali, Punjab, Pin code 140307, India Puneet Mehta Faculty,
Dr. Nasseer M. Basheer, Lecturer, Technical Engineering College/Mosul Northern Technical University/Iraq
 Volume 6, Issue 7, July 2016 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Arduino Based Text
Volume 6, Issue 7, July 2016 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Arduino Based Text
A Steganography method for JPEG2000 Baseline System
 A Steganography method for JPEG2000 Baseline System P.Ramakrishna Rao M.Tech.,[CSE], Teaching Associate, Department of Computer Science, Dr.B.R.Ambedkar University, Etcherla Srikaulam, 532 410. Abstract
A Steganography method for JPEG2000 Baseline System P.Ramakrishna Rao M.Tech.,[CSE], Teaching Associate, Department of Computer Science, Dr.B.R.Ambedkar University, Etcherla Srikaulam, 532 410. Abstract
RGB Digital Image Forgery Detection Using Singular Value Decomposition and One Dimensional Cellular Automata
 RGB Digital Image Forgery Detection Using Singular Value Decomposition and One Dimensional Cellular Automata Ahmad Pahlavan Tafti Mohammad V. Malakooti Department of Computer Engineering IAU, UAE Branch
RGB Digital Image Forgery Detection Using Singular Value Decomposition and One Dimensional Cellular Automata Ahmad Pahlavan Tafti Mohammad V. Malakooti Department of Computer Engineering IAU, UAE Branch
FINGERPRINTING SCHEME FOR FILE SHARING IN TRANSFORM DOMAIN
 FINGERPRINTING SCHEME FOR FILE SHARING IN TRANSFORM DOMAIN S.Manikandaprabu 1 P.Kalaiyarasi 2 1 Department of CSE, Tamilnadu College of Engineering, Coimbatore, India smaniprabume@gmail.com 2 Department
FINGERPRINTING SCHEME FOR FILE SHARING IN TRANSFORM DOMAIN S.Manikandaprabu 1 P.Kalaiyarasi 2 1 Department of CSE, Tamilnadu College of Engineering, Coimbatore, India smaniprabume@gmail.com 2 Department
TERM PAPER ON The Compressive Sensing Based on Biorthogonal Wavelet Basis
 TERM PAPER ON The Compressive Sensing Based on Biorthogonal Wavelet Basis Submitted By: Amrita Mishra 11104163 Manoj C 11104059 Under the Guidance of Dr. Sumana Gupta Professor Department of Electrical
TERM PAPER ON The Compressive Sensing Based on Biorthogonal Wavelet Basis Submitted By: Amrita Mishra 11104163 Manoj C 11104059 Under the Guidance of Dr. Sumana Gupta Professor Department of Electrical
Using Daubechies' Wavelets and Error Correcting Coding. James Ze Wang and Gio Wiederhold. Stanford University, Stanford, CA 94305, USA ABSTRACT
 WaveMark: Digital Image Watermarking Using Daubechies' Wavelets and Error Correcting Coding James Ze Wang and Gio Wiederhold Stanford University, Stanford, CA 94305, USA ABSTRACT As more and more digital
WaveMark: Digital Image Watermarking Using Daubechies' Wavelets and Error Correcting Coding James Ze Wang and Gio Wiederhold Stanford University, Stanford, CA 94305, USA ABSTRACT As more and more digital
Digital Image Watermarking Scheme Based on LWT and DCT
 Digital Image ing Scheme Based on LWT and Amy Tun and Yadana Thein Abstract As a potential solution to defend unauthorized replication of digital multimedia objects, digital watermarking technology is
Digital Image ing Scheme Based on LWT and Amy Tun and Yadana Thein Abstract As a potential solution to defend unauthorized replication of digital multimedia objects, digital watermarking technology is
Image Compression Algorithm for Different Wavelet Codes
 Image Compression Algorithm for Different Wavelet Codes Tanveer Sultana Department of Information Technology Deccan college of Engineering and Technology, Hyderabad, Telangana, India. Abstract: - This
Image Compression Algorithm for Different Wavelet Codes Tanveer Sultana Department of Information Technology Deccan college of Engineering and Technology, Hyderabad, Telangana, India. Abstract: - This
Analysis of Robustness of Digital Watermarking Techniques under Various Attacks
 International Journal of Engineering Research and Development e-issn : 2278-067X, p-issn : 2278-800X, www.ijerd.com Volume 2, Issue 6 (August 2012), PP. 28-34 Analysis of Robustness of Digital Watermarking
International Journal of Engineering Research and Development e-issn : 2278-067X, p-issn : 2278-800X, www.ijerd.com Volume 2, Issue 6 (August 2012), PP. 28-34 Analysis of Robustness of Digital Watermarking
An Improved Performance of Watermarking In DWT Domain Using SVD
 An Improved Performance of Watermarking In DWT Domain Using SVD Ramandeep Kaur 1 and Harpal Singh 2 1 Research Scholar, Department of Electronics & Communication Engineering, RBIEBT, Kharar, Pin code 140301,
An Improved Performance of Watermarking In DWT Domain Using SVD Ramandeep Kaur 1 and Harpal Singh 2 1 Research Scholar, Department of Electronics & Communication Engineering, RBIEBT, Kharar, Pin code 140301,
Image Transformation Techniques Dr. Rajeev Srivastava Dept. of Computer Engineering, ITBHU, Varanasi
 Image Transformation Techniques Dr. Rajeev Srivastava Dept. of Computer Engineering, ITBHU, Varanasi 1. Introduction The choice of a particular transform in a given application depends on the amount of
Image Transformation Techniques Dr. Rajeev Srivastava Dept. of Computer Engineering, ITBHU, Varanasi 1. Introduction The choice of a particular transform in a given application depends on the amount of
Robust DWT Based Technique for Digital Watermarking
 Robust DWT Based Technique for Digital Watermarking Mamta Jain Department of Electronics & Communication Institute of Engineering & Technology Alwar er.mamtajain@gmail.com Abstract Hiding the information
Robust DWT Based Technique for Digital Watermarking Mamta Jain Department of Electronics & Communication Institute of Engineering & Technology Alwar er.mamtajain@gmail.com Abstract Hiding the information
c Springer Verlag. The copyright for this contribution is held by Springer Verlag. The original publication is available at
 c Springer Verlag. The copyright for this contribution is held by Springer Verlag. The original publication is available at www.springerlink.com. Scalability evaluation of blind spread-spectrum image watermarking
c Springer Verlag. The copyright for this contribution is held by Springer Verlag. The original publication is available at www.springerlink.com. Scalability evaluation of blind spread-spectrum image watermarking
