Fundamentals of the Analysis of Algorithm Efficiency
|
|
|
- Kerry Dixon
- 5 years ago
- Views:
Transcription
1 Fundamentals of the Analysis of Algorithm Efficiency DR. JIRABHORN CHAIWONGSAI ดร.จ ราพร ไชยวงศ สาย D E PA R T M E N T O F C O M P U T E R E N G I N E E R I N G S C H O O L O F I N F O R M AT I O N A N D C O M M U N I C AT I O N T E C H N O L O GY U N I V E R S I T Y O F P H AYA O
2 Analysis of algorithms Correctness Time efficiency o How fast an algorithm in question runs Space efficiency o Extra space the algorithm requires Speed can be achieve much more spectacular progress than space Focus on time efficiency 2
3 Analysis framework Measuring an Input s Size All algorithms run longer on larger inputs Ex. take longer to sort larger arrays Unit for measuring running time Time efficiency is analyzed by determining the number of repetitions of the basic operation as a function of input size basic operation is the most important operation of the algorithm Contribute the total running time Compute the number of times that the basic operation is executed The most consuming operation in the algorithm 3
4 Ex.1 Sorting algorithm Work by comparing elements (keys) of a list being sorted with each other Basic operation =? Input size =? 4
5 Input size and basic operation examples Problem Searching for key in a list of n items Input size Number of list s items, i.e. n Basic operation Key comparison Multiplication of two matrices Matrix dimensions or total number of elements Multiplication of two numbers Checking primality of a given integer n Typical graph problem n size = number of digits (in binary representation) #vertices and/or edges Division Visiting a vertex or traversing an edge 5
6 Unit for measuring running time Basic operation: the operation that contributes most towards the running time of the algorithm input size running time T(n) c op C(n) execution time for basic operation Number of times basic operation is executed Let c op be the execution time of an algorithm s basic operation C(n) be the number of times this operation needs to be executed for this algorithm 6
7 Unit for measuring running time (cont.) Why do we use? c op is not always easy to assess How much faster would this algorithm run on a machine that is ten times faster than the one we have? Assume that a addition operation requires a cycle to execute We need 99 addition operations Compare the clock rate of a CPU between running at 1.0 GHz and 2.0 GHz 7
8 Unit for measuring running time (cont.) What about C(n)? Homework1 Assume that How much longer will the algorithm run if we double its input size? 8
9 Order of Growth 9
10 Order of Growth (cont.) time 10
11 Order of Growth (cont.) 11
12 Best-case, Average-case, Worst-case For some algorithms efficiency depends on form of input: Worst case: C worst (n) = maximum over inputs of size n Best case: C best (n) = minimum over inputs of size n Average case: C avg (n) = average over inputs of size n Number of times the basic operation will be executed on typical input NOT the average of worst and best case Expected number of basic operations considered as a random variable under some assumption about the probability distribution of all possible inputs 12
13 Example2: Sequential search Worst case: Best case: Average case: 13
14 Example2: Sequential search (cont.) C worst (n) = the algorithm makes the largest number of comparisons among all possible inputs of size n For any instance of size n, the running time will not exceed C worst (n) C worst (n) =? 14
15 Example2: Sequential search (cont.) C best (n) = the algorithm runs the fastest among all possible inputs of size n The best-case efficiency is not nearly as important as the worst-case C best (n) =? 15
16 Example2: Sequential search (cont.) To analyze the average-case efficiency, we must make some assumption about possible inputs of size n 16
17 Example2: Sequential search (cont.) (a) The probability of successful search = (b) The probability of the first match occurring in the -th position of the list is the same for every In case of successful search, the probability of the first match occurring in the -th position of the list is for every C avg (n) =? In case of unsuccessful search, the number of the comparisons is with the probability 17
18 Example2: Sequential search (cont.) If If = 1 (the search must be successful), (the search must be unsuccessful), 18
19 Best-case, average-case, worst-case 19
20 Best-case, average-case, worst-case Average-case efficiency is considerably more difficult than the worst-case and best-case efficiencies The average-case efficiency can t be obtained by taking the average of the worst-case and the best-case efficiencies 20
CS 6402 DESIGN AND ANALYSIS OF ALGORITHMS QUESTION BANK
 CS 6402 DESIGN AND ANALYSIS OF ALGORITHMS QUESTION BANK Page 1 UNIT I INTRODUCTION 2 marks 1. Why is the need of studying algorithms? From a practical standpoint, a standard set of algorithms from different
CS 6402 DESIGN AND ANALYSIS OF ALGORITHMS QUESTION BANK Page 1 UNIT I INTRODUCTION 2 marks 1. Why is the need of studying algorithms? From a practical standpoint, a standard set of algorithms from different
CSC Design and Analysis of Algorithms
 CSC 8301- Design and Analysis of Algorithms Lecture 6 Divide and Conquer Algorithm Design Technique Divide-and-Conquer The most-well known algorithm design strategy: 1. Divide a problem instance into two
CSC 8301- Design and Analysis of Algorithms Lecture 6 Divide and Conquer Algorithm Design Technique Divide-and-Conquer The most-well known algorithm design strategy: 1. Divide a problem instance into two
CSC Design and Analysis of Algorithms. Lecture 6. Divide and Conquer Algorithm Design Technique. Divide-and-Conquer
 CSC 8301- Design and Analysis of Algorithms Lecture 6 Divide and Conquer Algorithm Design Technique Divide-and-Conquer The most-well known algorithm design strategy: 1. Divide a problem instance into two
CSC 8301- Design and Analysis of Algorithms Lecture 6 Divide and Conquer Algorithm Design Technique Divide-and-Conquer The most-well known algorithm design strategy: 1. Divide a problem instance into two
Heaps and Priority Queues
 Unit 9, Part Heaps and Priority Queues Computer Science S-111 Harvard University David G. Sullivan, Ph.D. Priority Queue A priority queue (PQ) is a collection in which each item has an associated number
Unit 9, Part Heaps and Priority Queues Computer Science S-111 Harvard University David G. Sullivan, Ph.D. Priority Queue A priority queue (PQ) is a collection in which each item has an associated number
Divide-and-Conquer. The most-well known algorithm design strategy: smaller instances. combining these solutions
 Divide-and-Conquer The most-well known algorithm design strategy: 1. Divide instance of problem into two or more smaller instances 2. Solve smaller instances recursively 3. Obtain solution to original
Divide-and-Conquer The most-well known algorithm design strategy: 1. Divide instance of problem into two or more smaller instances 2. Solve smaller instances recursively 3. Obtain solution to original
EE 368. Week 6 (Notes)
 EE 368 Week 6 (Notes) 1 Expression Trees Binary trees provide an efficient data structure for representing expressions with binary operators. Root contains the operator Left and right children contain
EE 368 Week 6 (Notes) 1 Expression Trees Binary trees provide an efficient data structure for representing expressions with binary operators. Root contains the operator Left and right children contain
Chapter 4. Divide-and-Conquer. Copyright 2007 Pearson Addison-Wesley. All rights reserved.
 Chapter 4 Divide-and-Conquer Copyright 2007 Pearson Addison-Wesley. All rights reserved. Divide-and-Conquer The most-well known algorithm design strategy: 2. Divide instance of problem into two or more
Chapter 4 Divide-and-Conquer Copyright 2007 Pearson Addison-Wesley. All rights reserved. Divide-and-Conquer The most-well known algorithm design strategy: 2. Divide instance of problem into two or more
DIVIDE & CONQUER. Problem of size n. Solution to sub problem 1
 DIVIDE & CONQUER Definition: Divide & conquer is a general algorithm design strategy with a general plan as follows: 1. DIVIDE: A problem s instance is divided into several smaller instances of the same
DIVIDE & CONQUER Definition: Divide & conquer is a general algorithm design strategy with a general plan as follows: 1. DIVIDE: A problem s instance is divided into several smaller instances of the same
Algorithm Analysis. (Algorithm Analysis ) Data Structures and Programming Spring / 48
 Algorithm Analysis (Algorithm Analysis ) Data Structures and Programming Spring 2018 1 / 48 What is an Algorithm? An algorithm is a clearly specified set of instructions to be followed to solve a problem
Algorithm Analysis (Algorithm Analysis ) Data Structures and Programming Spring 2018 1 / 48 What is an Algorithm? An algorithm is a clearly specified set of instructions to be followed to solve a problem
Divide-and-Conquer. Dr. Yingwu Zhu
 Divide-and-Conquer Dr. Yingwu Zhu Divide-and-Conquer The most-well known algorithm design technique: 1. Divide instance of problem into two or more smaller instances 2. Solve smaller instances independently
Divide-and-Conquer Dr. Yingwu Zhu Divide-and-Conquer The most-well known algorithm design technique: 1. Divide instance of problem into two or more smaller instances 2. Solve smaller instances independently
Data Structure Lecture#5: Algorithm Analysis (Chapter 3) U Kang Seoul National University
 Data Structure Lecture#5: Algorithm Analysis (Chapter 3) U Kang Seoul National University U Kang 1 In This Lecture Learn how to evaluate algorithm efficiency Learn the concept of average case, best case,
Data Structure Lecture#5: Algorithm Analysis (Chapter 3) U Kang Seoul National University U Kang 1 In This Lecture Learn how to evaluate algorithm efficiency Learn the concept of average case, best case,
Parallel Algorithms for (PRAM) Computers & Some Parallel Algorithms. Reference : Horowitz, Sahni and Rajasekaran, Computer Algorithms
 Parallel Algorithms for (PRAM) Computers & Some Parallel Algorithms Reference : Horowitz, Sahni and Rajasekaran, Computer Algorithms Part 2 1 3 Maximum Selection Problem : Given n numbers, x 1, x 2,, x
Parallel Algorithms for (PRAM) Computers & Some Parallel Algorithms Reference : Horowitz, Sahni and Rajasekaran, Computer Algorithms Part 2 1 3 Maximum Selection Problem : Given n numbers, x 1, x 2,, x
Searching, Sorting. Arizona State University 1
 Searching, Sorting CSE100 Principles of Programming with C++, Fall 2018 (based off Chapter 9 slides by Pearson) Ryan Dougherty Arizona State University http://www.public.asu.edu/~redoughe/ Arizona State
Searching, Sorting CSE100 Principles of Programming with C++, Fall 2018 (based off Chapter 9 slides by Pearson) Ryan Dougherty Arizona State University http://www.public.asu.edu/~redoughe/ Arizona State
Selection, Bubble, Insertion, Merge, Heap, Quick Bucket, Radix
 Spring 2010 Review Topics Big O Notation Heaps Sorting Selection, Bubble, Insertion, Merge, Heap, Quick Bucket, Radix Hashtables Tree Balancing: AVL trees and DSW algorithm Graphs: Basic terminology and
Spring 2010 Review Topics Big O Notation Heaps Sorting Selection, Bubble, Insertion, Merge, Heap, Quick Bucket, Radix Hashtables Tree Balancing: AVL trees and DSW algorithm Graphs: Basic terminology and
Algorithm Analysis. CENG 707 Data Structures and Algorithms
 Algorithm Analysis CENG 707 Data Structures and Algorithms 1 Algorithm An algorithm is a set of instructions to be followed to solve a problem. There can be more than one solution (more than one algorithm)
Algorithm Analysis CENG 707 Data Structures and Algorithms 1 Algorithm An algorithm is a set of instructions to be followed to solve a problem. There can be more than one solution (more than one algorithm)
UNIT-2. Problem of size n. Sub-problem 1 size n/2. Sub-problem 2 size n/2. Solution to the original problem
 Divide-and-conquer method: Divide-and-conquer is probably the best known general algorithm design technique. The principle behind the Divide-and-conquer algorithm design technique is that it is easier
Divide-and-conquer method: Divide-and-conquer is probably the best known general algorithm design technique. The principle behind the Divide-and-conquer algorithm design technique is that it is easier
CSE 326: Data Structures Sorting Conclusion
 CSE 36: Data Structures Sorting Conclusion James Fogarty Spring 009 Administrivia Homework Due Homework Assigned Better be working on Project 3 (code due May 7) Sorting Recap Selection Sort Bubble Sort
CSE 36: Data Structures Sorting Conclusion James Fogarty Spring 009 Administrivia Homework Due Homework Assigned Better be working on Project 3 (code due May 7) Sorting Recap Selection Sort Bubble Sort
CSC Design and Analysis of Algorithms. Lecture 8. Transform and Conquer II Algorithm Design Technique. Transform and Conquer
 CSC 301- Design and Analysis of Algorithms Lecture Transform and Conuer II Algorithm Design Techniue Transform and Conuer This group of techniues solves a problem by a transformation to a simpler/more
CSC 301- Design and Analysis of Algorithms Lecture Transform and Conuer II Algorithm Design Techniue Transform and Conuer This group of techniues solves a problem by a transformation to a simpler/more
CPSC 331 Term Test #2 March 26, 2007
 CPSC 331 Term Test #2 March 26, 2007 Name: Please DO NOT write your ID number on this page. Instructions: Answer all questions in the space provided. Point form answers are acceptable if complete enough
CPSC 331 Term Test #2 March 26, 2007 Name: Please DO NOT write your ID number on this page. Instructions: Answer all questions in the space provided. Point form answers are acceptable if complete enough
CSC Design and Analysis of Algorithms. Lecture 8. Transform and Conquer II Algorithm Design Technique. Transform and Conquer
 CSC 301- Design and Analysis of Algorithms Lecture Transform and Conquer II Algorithm Design Technique Transform and Conquer This group of techniques solves a problem by a transformation to a simpler/more
CSC 301- Design and Analysis of Algorithms Lecture Transform and Conquer II Algorithm Design Technique Transform and Conquer This group of techniques solves a problem by a transformation to a simpler/more
Organisation. Assessment
 Week 1 s s Getting Started 1 3 4 5 - - Lecturer Dr Lectures Tuesday 1-13 Fulton House Lecture room Tuesday 15-16 Fulton House Lecture room Thursday 11-1 Fulton House Lecture room Friday 10-11 Glyndwr C
Week 1 s s Getting Started 1 3 4 5 - - Lecturer Dr Lectures Tuesday 1-13 Fulton House Lecture room Tuesday 15-16 Fulton House Lecture room Thursday 11-1 Fulton House Lecture room Friday 10-11 Glyndwr C
Algorithm Analysis. Gunnar Gotshalks. AlgAnalysis 1
 Algorithm Analysis AlgAnalysis 1 How Fast is an Algorithm? 1 Measure the running time» Run the program for many data types > Use System.currentTimeMillis to record the time Worst Time Average Best» Usually
Algorithm Analysis AlgAnalysis 1 How Fast is an Algorithm? 1 Measure the running time» Run the program for many data types > Use System.currentTimeMillis to record the time Worst Time Average Best» Usually
Algorithm Analysis and Design
 Algorithm Analysis and Design Dr. Truong Tuan Anh Faculty of Computer Science and Engineering Ho Chi Minh City University of Technology VNU- Ho Chi Minh City 1 References [1] Cormen, T. H., Leiserson,
Algorithm Analysis and Design Dr. Truong Tuan Anh Faculty of Computer Science and Engineering Ho Chi Minh City University of Technology VNU- Ho Chi Minh City 1 References [1] Cormen, T. H., Leiserson,
CSC630/CSC730 Parallel & Distributed Computing
 CSC630/CSC730 Parallel & Distributed Computing Analytical Modeling of Parallel Programs Chapter 5 1 Contents Sources of Parallel Overhead Performance Metrics Granularity and Data Mapping Scalability 2
CSC630/CSC730 Parallel & Distributed Computing Analytical Modeling of Parallel Programs Chapter 5 1 Contents Sources of Parallel Overhead Performance Metrics Granularity and Data Mapping Scalability 2
PARALLEL PROCESSING UNIT 3. Dr. Ahmed Sallam
 PARALLEL PROCESSING 1 UNIT 3 Dr. Ahmed Sallam FUNDAMENTAL GPU ALGORITHMS More Patterns Reduce Scan 2 OUTLINES Efficiency Measure Reduce primitive Reduce model Reduce Implementation and complexity analysis
PARALLEL PROCESSING 1 UNIT 3 Dr. Ahmed Sallam FUNDAMENTAL GPU ALGORITHMS More Patterns Reduce Scan 2 OUTLINES Efficiency Measure Reduce primitive Reduce model Reduce Implementation and complexity analysis
CSC Design and Analysis of Algorithms. Lecture 5. Decrease and Conquer Algorithm Design Technique. Decrease-and-Conquer
 CSC 8301- Design and Analysis of Algorithms Lecture 5 Decrease and Conquer Algorithm Design Technique Decrease-and-Conquer This algorithm design technique is based on exploiting a relationship between
CSC 8301- Design and Analysis of Algorithms Lecture 5 Decrease and Conquer Algorithm Design Technique Decrease-and-Conquer This algorithm design technique is based on exploiting a relationship between
Understand how to deal with collisions
 Understand the basic structure of a hash table and its associated hash function Understand what makes a good (and a bad) hash function Understand how to deal with collisions Open addressing Separate chaining
Understand the basic structure of a hash table and its associated hash function Understand what makes a good (and a bad) hash function Understand how to deal with collisions Open addressing Separate chaining
CS Divide and Conquer
 CS483-07 Divide and Conquer Instructor: Fei Li Room 443 ST II Office hours: Tue. & Thur. 1:30pm - 2:30pm or by appointments lifei@cs.gmu.edu with subject: CS483 http://www.cs.gmu.edu/ lifei/teaching/cs483_fall07/
CS483-07 Divide and Conquer Instructor: Fei Li Room 443 ST II Office hours: Tue. & Thur. 1:30pm - 2:30pm or by appointments lifei@cs.gmu.edu with subject: CS483 http://www.cs.gmu.edu/ lifei/teaching/cs483_fall07/
PESIT Bangalore South Campus Hosur road, 1km before Electronic City, Bengaluru -100 Department of MCA
 INTERNAL ASSESSMENT TEST 2 Date : 30/3/15 Max Marks : 50 Name of faculty : Sabeeha Sultana Subject & Code : ADA(13MCA41) Answer any five full question: 1.Illustrate Mergesort for the dataset 8,3,2,9,7,1,5,4.
INTERNAL ASSESSMENT TEST 2 Date : 30/3/15 Max Marks : 50 Name of faculty : Sabeeha Sultana Subject & Code : ADA(13MCA41) Answer any five full question: 1.Illustrate Mergesort for the dataset 8,3,2,9,7,1,5,4.
ECE/CS 552: Introduction to Computer Architecture ASSIGNMENT #1 Due Date: At the beginning of lecture, September 22 nd, 2010
 ECE/CS 552: Introduction to Computer Architecture ASSIGNMENT #1 Due Date: At the beginning of lecture, September 22 nd, 2010 This homework is to be done individually. Total 9 Questions, 100 points 1. (8
ECE/CS 552: Introduction to Computer Architecture ASSIGNMENT #1 Due Date: At the beginning of lecture, September 22 nd, 2010 This homework is to be done individually. Total 9 Questions, 100 points 1. (8
2. (a) Explain when the Quick sort is preferred to merge sort and vice-versa.
 Code No: RR210504 Set No. 1 1. (a) Order the following functions according to their order of growth (from the lowest to the highest). (n-2)!, 5 log (n+100) 10,2 2n, 0.001n 4 +3n 3 +1, ln 2 n, n 1/3, 3
Code No: RR210504 Set No. 1 1. (a) Order the following functions according to their order of growth (from the lowest to the highest). (n-2)!, 5 log (n+100) 10,2 2n, 0.001n 4 +3n 3 +1, ln 2 n, n 1/3, 3
Assignment 1 (concept): Solutions
 CS10b Data Structures and Algorithms Due: Thursday, January 0th Assignment 1 (concept): Solutions Note, throughout Exercises 1 to 4, n denotes the input size of a problem. 1. (10%) Rank the following functions
CS10b Data Structures and Algorithms Due: Thursday, January 0th Assignment 1 (concept): Solutions Note, throughout Exercises 1 to 4, n denotes the input size of a problem. 1. (10%) Rank the following functions
Multiplying and Dividing by Powers of 10
 Multiplying and Dividing by Powers of 10 1.) Complete stations A-F around the room. Copy each problem and answer it below. Problem A B C D E F Answer = = = = = = 2.) Where is the decimal point in a whole
Multiplying and Dividing by Powers of 10 1.) Complete stations A-F around the room. Copy each problem and answer it below. Problem A B C D E F Answer = = = = = = 2.) Where is the decimal point in a whole
17/05/2018. Outline. Outline. Divide and Conquer. Control Abstraction for Divide &Conquer. Outline. Module 2: Divide and Conquer
 Module 2: Divide and Conquer Divide and Conquer Control Abstraction for Divide &Conquer 1 Recurrence equation for Divide and Conquer: If the size of problem p is n and the sizes of the k sub problems are
Module 2: Divide and Conquer Divide and Conquer Control Abstraction for Divide &Conquer 1 Recurrence equation for Divide and Conquer: If the size of problem p is n and the sizes of the k sub problems are
Information Science 2
 Information Science 2 - Basic Search Algorithms- Week 04 College of Information Science and Engineering Ritsumeikan University Agenda Week 03 review Search algorithms on linear data structures - Linear
Information Science 2 - Basic Search Algorithms- Week 04 College of Information Science and Engineering Ritsumeikan University Agenda Week 03 review Search algorithms on linear data structures - Linear
Introduction to Linked List: Review. Source:
 Introduction to Linked List: Review Source: http://www.geeksforgeeks.org/data-structures/linked-list/ Linked List Fundamental data structures in C Like arrays, linked list is a linear data structure Unlike
Introduction to Linked List: Review Source: http://www.geeksforgeeks.org/data-structures/linked-list/ Linked List Fundamental data structures in C Like arrays, linked list is a linear data structure Unlike
Fast Bit Sort. A New In Place Sorting Technique. Nando Favaro February 2009
 Fast Bit Sort A New In Place Sorting Technique Nando Favaro February 2009 1. INTRODUCTION 1.1. A New Sorting Algorithm In Computer Science, the role of sorting data into an order list is a fundamental
Fast Bit Sort A New In Place Sorting Technique Nando Favaro February 2009 1. INTRODUCTION 1.1. A New Sorting Algorithm In Computer Science, the role of sorting data into an order list is a fundamental
Algorithm Analysis. College of Computing & Information Technology King Abdulaziz University. CPCS-204 Data Structures I
 Algorithm Analysis College of Computing & Information Technology King Abdulaziz University CPCS-204 Data Structures I Order Analysis Judging the Efficiency/Speed of an Algorithm Thus far, we ve looked
Algorithm Analysis College of Computing & Information Technology King Abdulaziz University CPCS-204 Data Structures I Order Analysis Judging the Efficiency/Speed of an Algorithm Thus far, we ve looked
IE 495 Lecture 3. Septermber 5, 2000
 IE 495 Lecture 3 Septermber 5, 2000 Reading for this lecture Primary Miller and Boxer, Chapter 1 Aho, Hopcroft, and Ullman, Chapter 1 Secondary Parberry, Chapters 3 and 4 Cosnard and Trystram, Chapter
IE 495 Lecture 3 Septermber 5, 2000 Reading for this lecture Primary Miller and Boxer, Chapter 1 Aho, Hopcroft, and Ullman, Chapter 1 Secondary Parberry, Chapters 3 and 4 Cosnard and Trystram, Chapter
CSC Design and Analysis of Algorithms. Lecture 4 Brute Force, Exhaustive Search, Graph Traversal Algorithms. Brute-Force Approach
 CSC 8301- Design and Analysis of Algorithms Lecture 4 Brute Force, Exhaustive Search, Graph Traversal Algorithms Brute-Force Approach Brute force is a straightforward approach to solving a problem, usually
CSC 8301- Design and Analysis of Algorithms Lecture 4 Brute Force, Exhaustive Search, Graph Traversal Algorithms Brute-Force Approach Brute force is a straightforward approach to solving a problem, usually
Design and Analysis of Algorithms Lecture- 9: B- Trees
 Design and Analysis of Algorithms Lecture- 9: B- Trees Dr. Chung- Wen Albert Tsao atsao@svuca.edu www.408codingschool.com/cs502_algorithm 1/12/16 Slide Source: http://www.slideshare.net/anujmodi555/b-trees-in-data-structure
Design and Analysis of Algorithms Lecture- 9: B- Trees Dr. Chung- Wen Albert Tsao atsao@svuca.edu www.408codingschool.com/cs502_algorithm 1/12/16 Slide Source: http://www.slideshare.net/anujmodi555/b-trees-in-data-structure
Chapter 6 INTRODUCTION TO DATA STRUCTURES AND ALGORITHMS
 Chapter 6 INTRODUCTION TO DATA STRUCTURES AND ALGORITHMS 1 Reference books: The C Programming Language by Brian W. Kernighan and Dennis M. Ritchie Programming in C (3rd Edition) by Stephen G. Kochan. Data
Chapter 6 INTRODUCTION TO DATA STRUCTURES AND ALGORITHMS 1 Reference books: The C Programming Language by Brian W. Kernighan and Dennis M. Ritchie Programming in C (3rd Edition) by Stephen G. Kochan. Data
CSC Design and Analysis of Algorithms. Lecture 6. Divide and Conquer Algorithm Design Technique. Divide-and-Conquer
 CSC 8301- Design and Analysis of Algorithms Lecture 6 Divide and Conuer Algorithm Design Techniue Divide-and-Conuer The most-well known algorithm design strategy: 1. Divide a problem instance into two
CSC 8301- Design and Analysis of Algorithms Lecture 6 Divide and Conuer Algorithm Design Techniue Divide-and-Conuer The most-well known algorithm design strategy: 1. Divide a problem instance into two
Algorithm. Algorithm Analysis. Algorithm. Algorithm. Analyzing Sorting Algorithms (Insertion Sort) Analyzing Algorithms 8/31/2017
 8/3/07 Analysis Introduction to Analysis Model of Analysis Mathematical Preliminaries for Analysis Set Notation Asymptotic Analysis What is an algorithm? An algorithm is any well-defined computational
8/3/07 Analysis Introduction to Analysis Model of Analysis Mathematical Preliminaries for Analysis Set Notation Asymptotic Analysis What is an algorithm? An algorithm is any well-defined computational
Table ADT and Sorting. Algorithm topics continuing (or reviewing?) CS 24 curriculum
 Table ADT and Sorting Algorithm topics continuing (or reviewing?) CS 24 curriculum A table ADT (a.k.a. Dictionary, Map) Table public interface: // Put information in the table, and a unique key to identify
Table ADT and Sorting Algorithm topics continuing (or reviewing?) CS 24 curriculum A table ADT (a.k.a. Dictionary, Map) Table public interface: // Put information in the table, and a unique key to identify
Algorithm Efficiency & Sorting. Algorithm efficiency Big-O notation Searching algorithms Sorting algorithms
 Algorithm Efficiency & Sorting Algorithm efficiency Big-O notation Searching algorithms Sorting algorithms Overview Writing programs to solve problem consists of a large number of decisions how to represent
Algorithm Efficiency & Sorting Algorithm efficiency Big-O notation Searching algorithms Sorting algorithms Overview Writing programs to solve problem consists of a large number of decisions how to represent
Computer Science 385 Analysis of Algorithms Siena College Spring Topic Notes: Divide and Conquer
 Computer Science 385 Analysis of Algorithms Siena College Spring 2011 Topic Notes: Divide and Conquer Divide and-conquer is a very common and very powerful algorithm design technique. The general idea:
Computer Science 385 Analysis of Algorithms Siena College Spring 2011 Topic Notes: Divide and Conquer Divide and-conquer is a very common and very powerful algorithm design technique. The general idea:
DATA STRUCTURES AND ALGORITHMS. Asymptotic analysis of the algorithms
 DATA STRUCTURES AND ALGORITHMS Asymptotic analysis of the algorithms Summary of the previous lecture Algorithm definition Representation of the algorithms: Flowchart, Pseudocode Description Types of the
DATA STRUCTURES AND ALGORITHMS Asymptotic analysis of the algorithms Summary of the previous lecture Algorithm definition Representation of the algorithms: Flowchart, Pseudocode Description Types of the
(Refer Slide Time: 00:50)
 Programming, Data Structures and Algorithms Prof. N.S. Narayanaswamy Department of Computer Science and Engineering Indian Institute of Technology Madras Module - 03 Lecture 30 Searching Unordered linear
Programming, Data Structures and Algorithms Prof. N.S. Narayanaswamy Department of Computer Science and Engineering Indian Institute of Technology Madras Module - 03 Lecture 30 Searching Unordered linear
Chapter 3:- Divide and Conquer. Compiled By:- Sanjay Patel Assistant Professor, SVBIT.
 Chapter 3:- Divide and Conquer Compiled By:- Assistant Professor, SVBIT. Outline Introduction Multiplying large Integers Problem Problem Solving using divide and conquer algorithm - Binary Search Sorting
Chapter 3:- Divide and Conquer Compiled By:- Assistant Professor, SVBIT. Outline Introduction Multiplying large Integers Problem Problem Solving using divide and conquer algorithm - Binary Search Sorting
Computer Science Approach to problem solving
 Computer Science Approach to problem solving If my boss / supervisor / teacher formulates a problem to be solved urgently, can I write a program to efficiently solve this problem??? Polynomial-Time Brute
Computer Science Approach to problem solving If my boss / supervisor / teacher formulates a problem to be solved urgently, can I write a program to efficiently solve this problem??? Polynomial-Time Brute
Module 2: Classical Algorithm Design Techniques
 Module 2: Classical Algorithm Design Techniques Dr. Natarajan Meghanathan Associate Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu Module
Module 2: Classical Algorithm Design Techniques Dr. Natarajan Meghanathan Associate Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu Module
EE/CSCI 451 Midterm 1
 EE/CSCI 451 Midterm 1 Spring 2018 Instructor: Xuehai Qian Friday: 02/26/2018 Problem # Topic Points Score 1 Definitions 20 2 Memory System Performance 10 3 Cache Performance 10 4 Shared Memory Programming
EE/CSCI 451 Midterm 1 Spring 2018 Instructor: Xuehai Qian Friday: 02/26/2018 Problem # Topic Points Score 1 Definitions 20 2 Memory System Performance 10 3 Cache Performance 10 4 Shared Memory Programming
List of Practical for Master in Computer Application (5 Year Integrated) (Through Distance Education)
 List of Practical for Master in Computer Application (5 Year Integrated) (Through Distance Education) Directorate of Distance Education Guru Jambeshwar University of Science & Technology, Hissar First
List of Practical for Master in Computer Application (5 Year Integrated) (Through Distance Education) Directorate of Distance Education Guru Jambeshwar University of Science & Technology, Hissar First
UML CS Algorithms Qualifying Exam Fall, 2003 ALGORITHMS QUALIFYING EXAM
 NAME: This exam is open: - books - notes and closed: - neighbors - calculators ALGORITHMS QUALIFYING EXAM The upper bound on exam time is 3 hours. Please put all your work on the exam paper. (Partial credit
NAME: This exam is open: - books - notes and closed: - neighbors - calculators ALGORITHMS QUALIFYING EXAM The upper bound on exam time is 3 hours. Please put all your work on the exam paper. (Partial credit
Chapter 5. Decrease-and-Conquer. Copyright 2007 Pearson Addison-Wesley. All rights reserved.
 Chapter 5 Decrease-and-Conquer Copyright 2007 Pearson Addison-Wesley. All rights reserved. Decrease-and-Conquer 1. Reduce problem instance to smaller instance of the same problem 2. Solve smaller instance
Chapter 5 Decrease-and-Conquer Copyright 2007 Pearson Addison-Wesley. All rights reserved. Decrease-and-Conquer 1. Reduce problem instance to smaller instance of the same problem 2. Solve smaller instance
Introduction to Computers & Programming
 16.070 Introduction to Computers & Programming Introduction to: Data Structures and Algorithm Analysis Prof. Kristina Lundqvist Dept. of Aero/Astro, MIT Slides based on: A Practical Introduction to Data
16.070 Introduction to Computers & Programming Introduction to: Data Structures and Algorithm Analysis Prof. Kristina Lundqvist Dept. of Aero/Astro, MIT Slides based on: A Practical Introduction to Data
Module 1: Asymptotic Time Complexity and Intro to Abstract Data Types
 Module 1: Asymptotic Time Complexity and Intro to Abstract Data Types Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu
Module 1: Asymptotic Time Complexity and Intro to Abstract Data Types Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu
Analysis of Algorithms - Introduction -
 Analysis of Algorithms - Introduction - Andreas Ermedahl MRTC (Mälardalens Real-Time Research Center) andreas.ermedahl@mdh.se Autumn 004 Administrative stuff Course leader: Andreas Ermedahl Email: andreas.ermedahl@mdh.se
Analysis of Algorithms - Introduction - Andreas Ermedahl MRTC (Mälardalens Real-Time Research Center) andreas.ermedahl@mdh.se Autumn 004 Administrative stuff Course leader: Andreas Ermedahl Email: andreas.ermedahl@mdh.se
CSC Design and Analysis of Algorithms. Lecture 5. Decrease and Conquer Algorithm Design Technique. Decrease-and-Conquer
 CSC 8301- Design and Analysis of Algorithms Lecture 5 Decrease and Conuer Algorithm Design Techniue Decrease-and-Conuer This algorithm design techniue is based on exploiting a relationship between a solution
CSC 8301- Design and Analysis of Algorithms Lecture 5 Decrease and Conuer Algorithm Design Techniue Decrease-and-Conuer This algorithm design techniue is based on exploiting a relationship between a solution
Encoding/Decoding, Counting graphs
 Encoding/Decoding, Counting graphs Russell Impagliazzo and Miles Jones Thanks to Janine Tiefenbruck http://cseweb.ucsd.edu/classes/sp16/cse21-bd/ May 13, 2016 11-avoiding binary strings Let s consider
Encoding/Decoding, Counting graphs Russell Impagliazzo and Miles Jones Thanks to Janine Tiefenbruck http://cseweb.ucsd.edu/classes/sp16/cse21-bd/ May 13, 2016 11-avoiding binary strings Let s consider
NET/JRF-COMPUTER SCIENCE & APPLICATIONS. Time: 01 : 00 Hour Date : M.M. : 50
 1 NET/JRF-COMPUTER SCIENCE & APPLICATIONS UNIT TEST : DATA STRUCTURE Time: 01 : 00 Hour Date : 02-06-2017 M.M. : 50 INSTRUCTION: Attempt all the 25 questions. Each question carry TWO marks. 1. Consider
1 NET/JRF-COMPUTER SCIENCE & APPLICATIONS UNIT TEST : DATA STRUCTURE Time: 01 : 00 Hour Date : 02-06-2017 M.M. : 50 INSTRUCTION: Attempt all the 25 questions. Each question carry TWO marks. 1. Consider
University of Waterloo Department of Electrical and Computer Engineering ECE250 Algorithms and Data Structures Fall 2017
 University of Waterloo Department of Electrical and Computer Engineering ECE250 Algorithms and Data Structures Fall 207 Midterm Examination Instructor: Dr. Ladan Tahvildari, PEng, SMIEEE Date: Wednesday,
University of Waterloo Department of Electrical and Computer Engineering ECE250 Algorithms and Data Structures Fall 207 Midterm Examination Instructor: Dr. Ladan Tahvildari, PEng, SMIEEE Date: Wednesday,
CS 251, LE 2 Fall MIDTERM 2 Tuesday, November 1, 2016 Version 00 - KEY
 CS 251, LE 2 Fall 2016 MIDTERM 2 Tuesday, November 1, 2016 Version 00 - KEY W1.) (i) Show one possible valid 2-3 tree containing the nine elements: 1 3 4 5 6 8 9 10 12. (ii) Draw the final binary search
CS 251, LE 2 Fall 2016 MIDTERM 2 Tuesday, November 1, 2016 Version 00 - KEY W1.) (i) Show one possible valid 2-3 tree containing the nine elements: 1 3 4 5 6 8 9 10 12. (ii) Draw the final binary search
EE/CSCI 451: Parallel and Distributed Computation
 EE/CSCI 451: Parallel and Distributed Computation Lecture #11 2/21/2017 Xuehai Qian Xuehai.qian@usc.edu http://alchem.usc.edu/portal/xuehaiq.html University of Southern California 1 Outline Midterm 1:
EE/CSCI 451: Parallel and Distributed Computation Lecture #11 2/21/2017 Xuehai Qian Xuehai.qian@usc.edu http://alchem.usc.edu/portal/xuehaiq.html University of Southern California 1 Outline Midterm 1:
END-TERM EXAMINATION
 (Please Write your Exam Roll No. immediately) Exam. Roll No... END-TERM EXAMINATION Paper Code : MCA-205 DECEMBER 2006 Subject: Design and analysis of algorithm Time: 3 Hours Maximum Marks: 60 Note: Attempt
(Please Write your Exam Roll No. immediately) Exam. Roll No... END-TERM EXAMINATION Paper Code : MCA-205 DECEMBER 2006 Subject: Design and analysis of algorithm Time: 3 Hours Maximum Marks: 60 Note: Attempt
Computer Science 210 Data Structures Siena College Fall Topic Notes: Complexity and Asymptotic Analysis
 Computer Science 210 Data Structures Siena College Fall 2017 Topic Notes: Complexity and Asymptotic Analysis Consider the abstract data type, the Vector or ArrayList. This structure affords us the opportunity
Computer Science 210 Data Structures Siena College Fall 2017 Topic Notes: Complexity and Asymptotic Analysis Consider the abstract data type, the Vector or ArrayList. This structure affords us the opportunity
COT 5407: Introduction to Algorithms. Giri Narasimhan. ECS 254A; Phone: x3748
 COT 5407: Introduction to Algorithms Giri Narasimhan ECS 254A; Phone: x3748 giri@cis.fiu.edu http://www.cis.fiu.edu/~giri/teach/5407s17.html https://moodle.cis.fiu.edu/v3.1/course/view.php?id=1494 8/28/07
COT 5407: Introduction to Algorithms Giri Narasimhan ECS 254A; Phone: x3748 giri@cis.fiu.edu http://www.cis.fiu.edu/~giri/teach/5407s17.html https://moodle.cis.fiu.edu/v3.1/course/view.php?id=1494 8/28/07
How many leaves on the decision tree? There are n! leaves, because every permutation appears at least once.
 Chapter 8. Sorting in Linear Time Types of Sort Algorithms The only operation that may be used to gain order information about a sequence is comparison of pairs of elements. Quick Sort -- comparison-based
Chapter 8. Sorting in Linear Time Types of Sort Algorithms The only operation that may be used to gain order information about a sequence is comparison of pairs of elements. Quick Sort -- comparison-based
Graphs and Network Flows IE411. Lecture 21. Dr. Ted Ralphs
 Graphs and Network Flows IE411 Lecture 21 Dr. Ted Ralphs IE411 Lecture 21 1 Combinatorial Optimization and Network Flows In general, most combinatorial optimization and integer programming problems are
Graphs and Network Flows IE411 Lecture 21 Dr. Ted Ralphs IE411 Lecture 21 1 Combinatorial Optimization and Network Flows In general, most combinatorial optimization and integer programming problems are
Algorithms: Efficiency, Analysis, techniques for solving problems using computer approach or methodology but not programming
 Chapter 1 Algorithms: Efficiency, Analysis, and dod Order Preface techniques for solving problems using computer approach or methodology but not programming language e.g., search Collie Collean in phone
Chapter 1 Algorithms: Efficiency, Analysis, and dod Order Preface techniques for solving problems using computer approach or methodology but not programming language e.g., search Collie Collean in phone
Binary Search Trees > = 2014 Goodrich, Tamassia, Goldwasser. Binary Search Trees 1
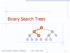 Binary Search Trees < > = Binary Search Trees 1 Ordered Dictionary (Map) ADT get (k): record with key k put (k,data): add record (k,data) remove (k): delete record with key k smallest(): record with smallest
Binary Search Trees < > = Binary Search Trees 1 Ordered Dictionary (Map) ADT get (k): record with key k put (k,data): add record (k,data) remove (k): delete record with key k smallest(): record with smallest
Exam 3 Practice Problems
 Exam 3 Practice Problems HONOR CODE: You are allowed to work in groups on these problems, and also to talk to the TAs (the TAs have not seen these problems before and they do not know the solutions but
Exam 3 Practice Problems HONOR CODE: You are allowed to work in groups on these problems, and also to talk to the TAs (the TAs have not seen these problems before and they do not know the solutions but
CS 261 Data Structures. Big-Oh Analysis: A Review
 CS 261 Data Structures Big-Oh Analysis: A Review Big-Oh: Purpose How can we characterize the runtime or space usage of an algorithm? We want a method that: doesn t depend upon hardware used (e.g., PC,
CS 261 Data Structures Big-Oh Analysis: A Review Big-Oh: Purpose How can we characterize the runtime or space usage of an algorithm? We want a method that: doesn t depend upon hardware used (e.g., PC,
Deterministic Parallel Graph Coloring with Symmetry Breaking
 Deterministic Parallel Graph Coloring with Symmetry Breaking Per Normann, Johan Öfverstedt October 05 Abstract In this paper we propose a deterministic parallel graph coloring algorithm that enables Multi-Coloring
Deterministic Parallel Graph Coloring with Symmetry Breaking Per Normann, Johan Öfverstedt October 05 Abstract In this paper we propose a deterministic parallel graph coloring algorithm that enables Multi-Coloring
Computer Programming: C++
 The Islamic University of Gaza Engineering Faculty Department of Computer Engineering Fall 2017 ECOM 2003 Muath i.alnabris Computer Programming: C++ Experiment #7 Arrays Part II Passing Array to a Function
The Islamic University of Gaza Engineering Faculty Department of Computer Engineering Fall 2017 ECOM 2003 Muath i.alnabris Computer Programming: C++ Experiment #7 Arrays Part II Passing Array to a Function
How do we compare algorithms meaningfully? (i.e.) the same algorithm will 1) run at different speeds 2) require different amounts of space
 How do we compare algorithms meaningfully? (i.e.) the same algorithm will 1) run at different speeds 2) require different amounts of space when run on different computers! for (i = n-1; i > 0; i--) { maxposition
How do we compare algorithms meaningfully? (i.e.) the same algorithm will 1) run at different speeds 2) require different amounts of space when run on different computers! for (i = n-1; i > 0; i--) { maxposition
Lecture 2: Algorithm Analysis
 ECE4050/CSC5050 Algorithms and Data Structures Lecture 2: Algorithm Analysis 1 Mathematical Background Logarithms Summations Recursion Induction Proofs Recurrence Relations 2 2 Logarithm Definition: 3
ECE4050/CSC5050 Algorithms and Data Structures Lecture 2: Algorithm Analysis 1 Mathematical Background Logarithms Summations Recursion Induction Proofs Recurrence Relations 2 2 Logarithm Definition: 3
QuickSort and Others. Data Structures and Algorithms Andrei Bulatov
 QuickSort and Others Data Structures and Algorithms Andrei Bulatov Algorithms Quicksort 5-2 Heap Property A heap is a nearly complete binary tree, satisfying an extra condition Let Parent(i) denote the
QuickSort and Others Data Structures and Algorithms Andrei Bulatov Algorithms Quicksort 5-2 Heap Property A heap is a nearly complete binary tree, satisfying an extra condition Let Parent(i) denote the
Module 2: Computer Arithmetic
 Module 2: Computer Arithmetic 1 B O O K : C O M P U T E R O R G A N I Z A T I O N A N D D E S I G N, 3 E D, D A V I D L. P A T T E R S O N A N D J O H N L. H A N N E S S Y, M O R G A N K A U F M A N N
Module 2: Computer Arithmetic 1 B O O K : C O M P U T E R O R G A N I Z A T I O N A N D D E S I G N, 3 E D, D A V I D L. P A T T E R S O N A N D J O H N L. H A N N E S S Y, M O R G A N K A U F M A N N
Hash Tables. Hashing Probing Separate Chaining Hash Function
 Hash Tables Hashing Probing Separate Chaining Hash Function Introduction In Chapter 4 we saw: linear search O( n ) binary search O( log n ) Can we improve the search operation to achieve better than O(
Hash Tables Hashing Probing Separate Chaining Hash Function Introduction In Chapter 4 we saw: linear search O( n ) binary search O( log n ) Can we improve the search operation to achieve better than O(
CS420: Operating Systems
 Main Memory James Moscola Department of Engineering & Computer Science York College of Pennsylvania Based on Operating System Concepts, 9th Edition by Silberschatz, Galvin, Gagne Background Program must
Main Memory James Moscola Department of Engineering & Computer Science York College of Pennsylvania Based on Operating System Concepts, 9th Edition by Silberschatz, Galvin, Gagne Background Program must
Advanced Databases. Lecture 1- Query Processing. Masood Niazi Torshiz Islamic Azad university- Mashhad Branch
 Advanced Databases Lecture 1- Query Processing Masood Niazi Torshiz Islamic Azad university- Mashhad Branch www.mniazi.ir Overview Measures of Query Cost Selection Operation Sorting Join Operation Other
Advanced Databases Lecture 1- Query Processing Masood Niazi Torshiz Islamic Azad university- Mashhad Branch www.mniazi.ir Overview Measures of Query Cost Selection Operation Sorting Join Operation Other
Practical Session #11 Sorting in Linear Time
 Practical Session #11 Counting-Sort A sort algorithm that is not based on comparisons, and supports duplicate keys. A is an input array of length n. B is the output array of length n too. C is an auxiliary
Practical Session #11 Counting-Sort A sort algorithm that is not based on comparisons, and supports duplicate keys. A is an input array of length n. B is the output array of length n too. C is an auxiliary
Algorithm Analysis. Algorithm Efficiency Best, Worst, Average Cases Asymptotic Analysis (Big Oh) Space Complexity
 Algorithm Analysis Algorithm Efficiency Best, Worst, Average Cases Asymptotic Analysis (Big Oh) Space Complexity ITCS 2214:Data Structures 1 Mathematical Fundamentals Measuring Algorithm Efficiency Empirical
Algorithm Analysis Algorithm Efficiency Best, Worst, Average Cases Asymptotic Analysis (Big Oh) Space Complexity ITCS 2214:Data Structures 1 Mathematical Fundamentals Measuring Algorithm Efficiency Empirical
CSc 225 Algorithms and Data Structures I Algorithm Analysis
 CSc 225 Algorithms and Data Structures I Algorithm Analysis Jianping Pan Fall 2007 09/06/07 CSc 225 1 What is an Algorithm? An algorithm is a sequence of unambiguous instructions for solving a problem
CSc 225 Algorithms and Data Structures I Algorithm Analysis Jianping Pan Fall 2007 09/06/07 CSc 225 1 What is an Algorithm? An algorithm is a sequence of unambiguous instructions for solving a problem
Introduction to Engineering Using Robotics Laboratories Algorithms
 Introduction to Engineering Using Robotics Laboratories Algorithms Dr. Yinong Chen Roadmap The Concept of Algorithms Algorithm Primitives Algorithm Complexity Examples of Algorithms Robotics Algorithms
Introduction to Engineering Using Robotics Laboratories Algorithms Dr. Yinong Chen Roadmap The Concept of Algorithms Algorithm Primitives Algorithm Complexity Examples of Algorithms Robotics Algorithms
Physical Level of Databases: B+-Trees
 Physical Level of Databases: B+-Trees Adnan YAZICI Computer Engineering Department METU (Fall 2005) 1 B + -Tree Index Files l Disadvantage of indexed-sequential files: performance degrades as file grows,
Physical Level of Databases: B+-Trees Adnan YAZICI Computer Engineering Department METU (Fall 2005) 1 B + -Tree Index Files l Disadvantage of indexed-sequential files: performance degrades as file grows,
CS Data Structures and Algorithm Analysis
 CS 483 - Data Structures and Algorithm Analysis Lecture VI: Chapter 5, part 2; Chapter 6, part 1 R. Paul Wiegand George Mason University, Department of Computer Science March 8, 2006 Outline 1 Topological
CS 483 - Data Structures and Algorithm Analysis Lecture VI: Chapter 5, part 2; Chapter 6, part 1 R. Paul Wiegand George Mason University, Department of Computer Science March 8, 2006 Outline 1 Topological
Mean Value Analysis and Related Techniques
 Mean Value Analysis and Related Techniques 34-1 Overview 1. Analysis of Open Queueing Networks 2. Mean-Value Analysis 3. Approximate MVA 4. Balanced Job Bounds 34-2 Analysis of Open Queueing Networks Used
Mean Value Analysis and Related Techniques 34-1 Overview 1. Analysis of Open Queueing Networks 2. Mean-Value Analysis 3. Approximate MVA 4. Balanced Job Bounds 34-2 Analysis of Open Queueing Networks Used
PRAM Divide and Conquer Algorithms
 PRAM Divide and Conquer Algorithms (Chapter Five) Introduction: Really three fundamental operations: Divide is the partitioning process Conquer the the process of (eventually) solving the eventual base
PRAM Divide and Conquer Algorithms (Chapter Five) Introduction: Really three fundamental operations: Divide is the partitioning process Conquer the the process of (eventually) solving the eventual base
Designing for Performance. Patrick Happ Raul Feitosa
 Designing for Performance Patrick Happ Raul Feitosa Objective In this section we examine the most common approach to assessing processor and computer system performance W. Stallings Designing for Performance
Designing for Performance Patrick Happ Raul Feitosa Objective In this section we examine the most common approach to assessing processor and computer system performance W. Stallings Designing for Performance
CSCI 104 Log Structured Merge Trees. Mark Redekopp
 1 CSCI 10 Log Structured Merge Trees Mark Redekopp Series Summation Review Let n = 1 + + + + k = σk i=0 n = k+1-1 i. What is n? What is log (1) + log () + log () + log (8)++ log ( k ) = 0 + 1 + + 3+ +
1 CSCI 10 Log Structured Merge Trees Mark Redekopp Series Summation Review Let n = 1 + + + + k = σk i=0 n = k+1-1 i. What is n? What is log (1) + log () + log () + log (8)++ log ( k ) = 0 + 1 + + 3+ +
(6-2) Efficiency of Algorithms D & D Chapter 20. Instructor - Andrew S. O Fallon CptS 122 (July 11, 2018) Washington State University
 (6-2) Efficiency of Algorithms D & D Chapter 20 Instructor - Andrew S. O Fallon CptS 122 (July 11, 2018) Washington State University Analysis of Algorithms (1) 2 In general, we want to determine central
(6-2) Efficiency of Algorithms D & D Chapter 20 Instructor - Andrew S. O Fallon CptS 122 (July 11, 2018) Washington State University Analysis of Algorithms (1) 2 In general, we want to determine central
DESIGN AND ANALYSIS OF ALGORITHMS
 DESIGN AND ANALYSIS OF ALGORITHMS QUESTION BANK Module 1 OBJECTIVE: Algorithms play the central role in both the science and the practice of computing. There are compelling reasons to study algorithms.
DESIGN AND ANALYSIS OF ALGORITHMS QUESTION BANK Module 1 OBJECTIVE: Algorithms play the central role in both the science and the practice of computing. There are compelling reasons to study algorithms.
Divide and Conquer Sorting Algorithms and Noncomparison-based
 Divide and Conquer Sorting Algorithms and Noncomparison-based Sorting Algorithms COMP1927 16x1 Sedgewick Chapters 7 and 8 Sedgewick Chapter 6.10, Chapter 10 DIVIDE AND CONQUER SORTING ALGORITHMS Step 1
Divide and Conquer Sorting Algorithms and Noncomparison-based Sorting Algorithms COMP1927 16x1 Sedgewick Chapters 7 and 8 Sedgewick Chapter 6.10, Chapter 10 DIVIDE AND CONQUER SORTING ALGORITHMS Step 1
CO Computer Architecture and Programming Languages CAPL. Lecture 15
 CO20-320241 Computer Architecture and Programming Languages CAPL Lecture 15 Dr. Kinga Lipskoch Fall 2017 How to Compute a Binary Float Decimal fraction: 8.703125 Integral part: 8 1000 Fraction part: 0.703125
CO20-320241 Computer Architecture and Programming Languages CAPL Lecture 15 Dr. Kinga Lipskoch Fall 2017 How to Compute a Binary Float Decimal fraction: 8.703125 Integral part: 8 1000 Fraction part: 0.703125
Student Number: CSE191 Midterm II Spring Plagiarism will earn you an F in the course and a recommendation of expulsion from the university.
 Plagiarism will earn you an F in the course and a recommendation of expulsion from the university. (1 pt each) For Questions 1-5, when asked for a running time or the result of a summation, you must choose
Plagiarism will earn you an F in the course and a recommendation of expulsion from the university. (1 pt each) For Questions 1-5, when asked for a running time or the result of a summation, you must choose
Lecture 7. Transform-and-Conquer
 Lecture 7 Transform-and-Conquer 6-1 Transform and Conquer This group of techniques solves a problem by a transformation to a simpler/more convenient instance of the same problem (instance simplification)
Lecture 7 Transform-and-Conquer 6-1 Transform and Conquer This group of techniques solves a problem by a transformation to a simpler/more convenient instance of the same problem (instance simplification)
Open Addressing: Linear Probing (cont.)
 Open Addressing: Linear Probing (cont.) Cons of Linear Probing () more complex insert, find, remove methods () primary clustering phenomenon items tend to cluster together in the bucket array, as clustering
Open Addressing: Linear Probing (cont.) Cons of Linear Probing () more complex insert, find, remove methods () primary clustering phenomenon items tend to cluster together in the bucket array, as clustering
