INTERNET SAFETY* GALEN GARRETSON RASCAL MARCH 2-3, * Sources include learnfree.org, PC World, wikpedia.com, techterms.com
|
|
|
- Sharlene Willis
- 5 years ago
- Views:
Transcription
1 INTERNET SAFETY* GALEN GARRETSON RASCAL MARCH 2-3, 2016 * Sources include learnfree.org, PC World, wikpedia.com, techterms.com
2 SOME QUESTIONS TO ASK YOURSELF. HAVE YOU.. 1. Googled yourself to see what information can be found on you? 2. Been enticed by s or advertisements with special discount offers? 3. Set your computer's security program to make sure you are getting regular updates? 4. Created an external backup source for your computer? 5. Set secure passwords for any of your online accounts? 6. Customized your privacy settings for social networking accounts like Facebook, Skype, etc?
3 INTERNET SAFETY THREATS Click on each word for a definition.
4 Install virus protection software and keep it up to date. Security suites Security suites are generally easier to manage and offer a wide range of protection, which can be useful if you are a beginner. However, in some cases the extra functions of a suite are not as good as the stand-alone products for that function. In addition, some suites have a tendency to slow down a computer. Stand-alone products More advanced users sometimes prefer to take a pick-and-mix approach, researching and selecting the best products for each component and building their own security systems.
5 Virus protection software There are many antivirus programs available. Many have a free version in addition to an upgraded Pro version. Many offer a suite of tools that include malware detection, startup management, etc. Here is a list of free antivirus software programs as presented by PC Magazine as of March 1, Please investigate what best suits your needs. PC Magazine article Avast Free Antivirus 2016 AVG AntiVirus Free (2016) Panda Free Antivirus (2016) Bitdefender Antivirus Free Edition (2014) Check Point ZoneAlarm Free Antivirus + Firewall 2016 Lavasoft Ad-Aware Free Antivirus+ 11 Sophos Home Qihoo 360 Total Security Essential Comodo Antivirus 8 FortiClient 5.0
6 Create strong passwords for any or online account. Never use personal information such as your name, birthday, or spouse's name. Personal information is often publicly available, which makes it easier for someone to guess your password. Use a longer password. Your password should be at least eight characters long, and for extra security it should ideally be at least 12 characters if the site allows it. If you need to write down your passwords, keep them in a secure place. It's even better if you encrypt your passwords, or write down hints for them that others won't be able to understand. Don't use the same password for each account. If someone discovers your password for one account, all of your other accounts will be vulnerable. Try to include numbers, symbols, and both uppercase and lowercase letters if the site allows it. Avoid using words that can be found in the dictionary. For example, swimming1 would be a weak password. Random passwords are the strongest. Password generators can be very helpful.
7
8
9
10
11
12 Password Management Programs As with antivirus programs, there are both free and paid password management programs. Most of the free password managers restrict the number of account passwords that will be managed. As an example, Roboform is free, but with a limit of only 10 accounts. Also, some managers store your passwords locally on your computer, while others store your passwords in the cloud. Here are some password managers you may want to consider, again from PC Magazine. Dashlane 4 LastPass 4.0 Premium Sticky Password Premium RoboForm Everywhere 7 Keeper Password Manager & Digital Vault 8 LogMeOnce Password Management Suite Ultimate Password Boss Premium Password Genie 4.4
13 Download with Caution One of the easiest ways malware, spyware, and adware can access your computer is through downloads; therefore, it's important to take precautions when downloading content to your computer, whether it is a software program, the latest pop song, or a cool game. There are two things that provide the best defense against infected downloads: your computer's security programs and your own judgment. Download only from trusted sites Save and then run downloads Be cautious of freeware Avoid illegal downloads Be cautious of P2P (peer-to-peer) file sharing
14 Is a site safe for shopping? The first thing to look for at every shopping website is the secure and encrypted connection. Every website that sells items, or services should encrypt connection and information between the user and the server. This is an easy thing to verify in seconds. Secure websites protect their most important pages where people can log in, sign up or make a payment. To verify that the payment page is secured look for the green lock at the top left of your browser. That lock represents a certification from trusted companies who verified the identity of the website owner, and they encrypt that page with SSL to make it secure. In Google Chrome, for example, the lock looks like the screenshot below:
15 Is a site safe for shopping? Now let s take it a step further. Left click on the green lock and then click on the connection tab. You ll will see what certificates the site has and possibly how they encrypt their information. There are a few companies in the world that are trusted by millions of users such as Truste, Norton, Geotrust.com, and Verisign.com. These companies deliver a certificate of trust and security, after doing their own check on the website that you re looking at.
16 What about safety for just plain browsing, not shopping? Web browsers have built-in safety checks. For example, Microsoft calls it SmartFilter for Internet Explorer, and Firefox has options to block "reported attack sites". Chrome and Safari use data from Google Safe Browsing; and Opera relies on AVG. Here s a screen shot from a Google Chrome block:
17 What about safety for just plain browsing, not shopping? In addition there are third party plugin or extensions that help protect you from websites that you may pick up malware or viruses. Some are reputation based. Web of Trust AVG Link Protection Trent Protect Norton Ratings And many more. In Google Chrome click menu t Then click Setting and then click Extensions. Toward the bottom of the page you will see the option to: You can then search for extensions you are interested in. Let s try it now.
18 Use the built-in browser protection Delete your browsing history regularly. In Google Chrome, left click on the Menu button.
19 Use the built-in browser protection In the Internet Explorer click on the Tools button, then:
20 Use the built-in browser protection Use the built-in pop-up blocker Pop-ups are small browser windows that automatically pop up when you visit certain sites. They may sometimes be part of the legitimate functioning of a site, or they may contain advertisements that can be annoying or objectionable. However, some pop-ups may contain malware; therefore, it's a good idea to make sure your browser's pop-up blocker is turned on. In Chrome, pop-ups are managed by going to the menu button, then settings, then to Show Advanced Settings. Click on Content Settings under Privacy. Scroll down to the Pop-up section.
21 Use the built-in browser protection Control those cookies - keep the cookies you want, get rid of the rest. Many websites add small text files to your computer called cookies. Cookies can help your computer communicate with a web server, but they can also be used to track your browsing activity. Every browser has tools for controlling, blocking, and deleting cookies from your computer. By becoming familiar with these tools, you can help protect your information from being accessed. In Chrome, cookies are managed by going to the menu button, then settings, then to Show Advanced Settings. Click on Content Settings under Privacy. Scroll down to the Cookies section.
22 Use the built-in browser protection Browse in private or incognito for extra safety Most browsers have a tool option that allows you to browse in private. When in private browsing mode, the following information will not be saved by the browser: 1. Pages you visit will not be recorded to your history or address bar. 2. Cookies will be deleted at the end of the session. 3. The cache that stores temporary Internet files will be emptied at the end of the session. 4. Forms, search bars, and text boxes will not save the data you have entered, including passwords. 5. Downloads listed in your download window or folder will be deleted, although the download itself will remain on your computer.
23 A sockpuppet is a fake identify that someone creates and uses to deceive others for some kind of personal gain. On most websites it is possible to have more than one account, so it is easy to create sockpuppets. TIPS FOR INTERNET SAFETY Social Networking on the Internet (Facebook, Skype, LinkedIn, user forums, chat rooms, etc.) If someone loses their job because of something they posted on a blog or social networking site, they have been dooced. An avatar is a virtual representation of yourself. The term usually refers to a virtual image. Meme is something that has gone viral, or spread rapidly around the internet, such as a catchphrase, hoax, topic, concept or piece of media. Instead of using your picture on a social networking profile, you might use an avatar to protect your privacy. Memes are often cute, funny or curious and make you want to pass them on! If you are forwarding an , just remember that everyone who gets that in the future could have access to your address. A comment posted by someone trying to provoke a flame, or an angry response, is called flamebait. If anyone responds to the comment, they are said to have taken the bait. A troll is a person who posts comments just to get a rise out of people and cause a distraction. Trolls might say something rude, assert incorrect information, or ask questions unrelated to the topic at hand.
24 Social Networking on the Internet (Facebook, Skype, LinkedIn, user forums, chat rooms, etc.) Screen Name It may be OK to use your full name as a screen name on sites where you can limit your sharing to the people you know. Some sites, like Facebook, may even require you to use your real full name. However, on a message board or chat room, you should use just your first name or a pseudonym because you are interacting with strangers. Profile Picture A profile picture can either be a photo or avatar (a graphical image that represents you). On Facebook, most people use photos of themselves. However, on a more public site you may want to use an avatar because it allows you to remain more anonymous. Profile Information You should be careful about what personal information you share in your profile. If possible, set up your account so only friends can see your personal information. You hould never make your birthday or home address publicly viewable.
INTERNET SAFETY IS IMPORTANT
 INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
Security Awareness. Presented by OSU Institute of Technology
 Security Awareness Presented by OSU Institute of Technology Information Technologies Division Security Awareness Topics Social Engineering Phishing Social Networks Displaying Sensitive Information Wireless
Security Awareness Presented by OSU Institute of Technology Information Technologies Division Security Awareness Topics Social Engineering Phishing Social Networks Displaying Sensitive Information Wireless
Keeping Your PC Safe. Tips on Safe Computing from Doug Copley
 Keeping Your PC Safe Tips on Safe Computing from Doug Copley Don t be an Administrator Administrator is an account that can do ANYTHING on the PC Most computers start with 1 account with administrator
Keeping Your PC Safe Tips on Safe Computing from Doug Copley Don t be an Administrator Administrator is an account that can do ANYTHING on the PC Most computers start with 1 account with administrator
NET 311 D INFORMATION SECURITY
 1 NET 311 D INFORMATION SECURITY Networks and Communication Department TUTORIAL 6 :Securing Your Windows 8 System 4 Steps to secure your windows 8 system 2 1. Configure Windows 8 Settings. 2. Installing
1 NET 311 D INFORMATION SECURITY Networks and Communication Department TUTORIAL 6 :Securing Your Windows 8 System 4 Steps to secure your windows 8 system 2 1. Configure Windows 8 Settings. 2. Installing
Quick recap on ing Security Recap on where to find things on Belvidere website & a look at the Belvidere Facebook page
 Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
Browser Cookie Settings
 Browser Cookie Settings Error Messages: Browser's cookie functionality turned off Steps to Try 1. Try enabling cookies, close all browser windows and restart browser after enabling cookies 2. Try clearing
Browser Cookie Settings Error Messages: Browser's cookie functionality turned off Steps to Try 1. Try enabling cookies, close all browser windows and restart browser after enabling cookies 2. Try clearing
Staying Safe on the Internet. Mark Schulman
 Staying Safe on the Internet Mark Schulman 1 Your Presenter Mark Schulman IT professional for almost 40 years No affiliation with any product 2 What We ll Talk About Passwords Email Safety Staying Safe
Staying Safe on the Internet Mark Schulman 1 Your Presenter Mark Schulman IT professional for almost 40 years No affiliation with any product 2 What We ll Talk About Passwords Email Safety Staying Safe
How To Remove Personal Antivirus Security Pro Virus
 How To Remove Personal Antivirus Security Pro Virus When hackers break into government servers to steal your personal data, there's not a The independent labs uniformly heap praise on Kaspersky Anti-Virus
How To Remove Personal Antivirus Security Pro Virus When hackers break into government servers to steal your personal data, there's not a The independent labs uniformly heap praise on Kaspersky Anti-Virus
2018 By: RemoveVirus.net. Remove A Virus From Your PC In 5 Simple Steps
 2018 By: RemoveVirus.net Remove A Virus From Your PC In 5 Simple Steps PCs, like Macs and Mobile Devices are susceptible to different types of malware. Avoid panicking when you realize that your PC has
2018 By: RemoveVirus.net Remove A Virus From Your PC In 5 Simple Steps PCs, like Macs and Mobile Devices are susceptible to different types of malware. Avoid panicking when you realize that your PC has
Manually Remove Of Xp Internet Security Protect
 Manually Remove Of Xp Internet Security Protect McAfee Family Protection McAfee Internet Security NOTE: To determine which McAfee Security software version you have installed, You must uninstall your McAfee
Manually Remove Of Xp Internet Security Protect McAfee Family Protection McAfee Internet Security NOTE: To determine which McAfee Security software version you have installed, You must uninstall your McAfee
How To Remove Internet Security Pro Virus. Manually >>>CLICK HERE<<<
 How To Remove Internet Security Pro Virus Manually Instructions to remove Defender PRO 2015 virus and get rid of Defender PRO 2015 malware from Windows. Tech & Internet Security / News & Guides Click the
How To Remove Internet Security Pro Virus Manually Instructions to remove Defender PRO 2015 virus and get rid of Defender PRO 2015 malware from Windows. Tech & Internet Security / News & Guides Click the
Staying Safe Online. My Best Internet Safety Tips. and the AgeWell Computer Education Center.
 Staying Safe Online My Best Internet Safety Tips and the AgeWell Computer Education Center Welcome to our first Webinar of 2017! Agenda o How to use the Webinar Room o Upcoming CEC Classes o My tips for
Staying Safe Online My Best Internet Safety Tips and the AgeWell Computer Education Center Welcome to our first Webinar of 2017! Agenda o How to use the Webinar Room o Upcoming CEC Classes o My tips for
How To Remove Personal Antivirus Security Pro Virus Windows 8
 How To Remove Personal Antivirus Security Pro Virus Windows 8 When hackers break into government servers to steal your personal data, there's As for just relying on the antivirus built into Windows 8.x,
How To Remove Personal Antivirus Security Pro Virus Windows 8 When hackers break into government servers to steal your personal data, there's As for just relying on the antivirus built into Windows 8.x,
Technology Basics and Social Networking Presented by Gina Lobdell Graduate Student at Purdue University
 Technology Basics and Social Networking Presented by Gina Lobdell Graduate Student at Purdue University Photo Copyright 2012 AgVenture. All Rights Reserved. Welcome Goals of the workshop: Gain a better
Technology Basics and Social Networking Presented by Gina Lobdell Graduate Student at Purdue University Photo Copyright 2012 AgVenture. All Rights Reserved. Welcome Goals of the workshop: Gain a better
Create strong passwords
 Create strong passwords Passwords are the first line of defense against break-ins to your online accounts and computer, tablet, or phone. Poorly chosen passwords can render your information vulnerable
Create strong passwords Passwords are the first line of defense against break-ins to your online accounts and computer, tablet, or phone. Poorly chosen passwords can render your information vulnerable
Manual Removal Norton Internet Security Won't Open Or
 Manual Removal Norton Internet Security Won't Open Or Dec 3, 2014. Finally during the reinstall - I had to delete a key to get a new key other wise I would I have it shown on the prgrams and features -
Manual Removal Norton Internet Security Won't Open Or Dec 3, 2014. Finally during the reinstall - I had to delete a key to get a new key other wise I would I have it shown on the prgrams and features -
How To Remove Personal Antivirus Security Pro Virus Manually
 How To Remove Personal Antivirus Security Pro Virus Manually Uninstall Antivirus Pro 2017 Virus (Manual Removal Guide) This type of virus uses false scan results and fake security alerts to scare computer
How To Remove Personal Antivirus Security Pro Virus Manually Uninstall Antivirus Pro 2017 Virus (Manual Removal Guide) This type of virus uses false scan results and fake security alerts to scare computer
Remove Mcafee Antivirus Plus 2013 Link Version For 90 Days
 Remove Mcafee Antivirus Plus 2013 Link Version For 90 Days Meanwhile McAfee Antivirus Plus insisted that my AV subscription expired, and I am getting tech help to remove it and put Microsoft essentials
Remove Mcafee Antivirus Plus 2013 Link Version For 90 Days Meanwhile McAfee Antivirus Plus insisted that my AV subscription expired, and I am getting tech help to remove it and put Microsoft essentials
By John Lortz DiscoverSkills.com
 By John Lortz DiscoverSkills.com 2015 was a banner year for online threats (viruses, malware, scams, etc.), but without a doubt, 2016 will most likely be worse. The fact is, it s becoming increasingly
By John Lortz DiscoverSkills.com 2015 was a banner year for online threats (viruses, malware, scams, etc.), but without a doubt, 2016 will most likely be worse. The fact is, it s becoming increasingly
FACEBOOK SAFETY FOR JOURNALISTS. Thanks to these partners for reviewing these safety guidelines:
 FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
Free antivirus software download windows 10
 Free antivirus software download windows 10 Search Free software download,the biggest software directory for freeware and shareware download at brothersoft.com. 2-3-2018 Protect your devices with the best
Free antivirus software download windows 10 Search Free software download,the biggest software directory for freeware and shareware download at brothersoft.com. 2-3-2018 Protect your devices with the best
ANNOYING COMPUTER PROBLEMS
 ANNOYING COMPUTER PROBLEMS And their solution Before you do this to your computer read this information. Feel free to print it out. This will make it easier to reference. Table of Contents 1. Computer
ANNOYING COMPUTER PROBLEMS And their solution Before you do this to your computer read this information. Feel free to print it out. This will make it easier to reference. Table of Contents 1. Computer
Circle Link 1 "Know Before You Go" Web Literacy Tips:
 5 th Grade Scavenger Hunt Content Circle Link 1 http://pbskids.org/privacy/literacytips.html "Know Before You Go" Web Literacy Tips: You know not to talk to strangers on the street but what about on the
5 th Grade Scavenger Hunt Content Circle Link 1 http://pbskids.org/privacy/literacytips.html "Know Before You Go" Web Literacy Tips: You know not to talk to strangers on the street but what about on the
EADS up. stop think connect
 EADS up stop think connect You text, you play games, you share photos and video. You update your status, you post comments, you probably spend some time in a virtual world. Being online connected through
EADS up stop think connect You text, you play games, you share photos and video. You update your status, you post comments, you probably spend some time in a virtual world. Being online connected through
Manually Remove Of Xp Internet Security Pro Virus Windows 7
 Manually Remove Of Xp Internet Security Pro Virus Windows 7 How to remove Defender PRO 2015 virus (Removal Guide) kits that use vulnerabilities on your computer to install this rogue antivirus without
Manually Remove Of Xp Internet Security Pro Virus Windows 7 How to remove Defender PRO 2015 virus (Removal Guide) kits that use vulnerabilities on your computer to install this rogue antivirus without
Discount Kaspersky PURE 3.0 internet download software for windows 8 ]
![Discount Kaspersky PURE 3.0 internet download software for windows 8 ] Discount Kaspersky PURE 3.0 internet download software for windows 8 ]](/thumbs/71/65538451.jpg) Discount Kaspersky PURE 3.0 internet download software for windows 8 ] Description: Extended benefits Award-winning protection against all types of Internet threats Online shopping, banking and social
Discount Kaspersky PURE 3.0 internet download software for windows 8 ] Description: Extended benefits Award-winning protection against all types of Internet threats Online shopping, banking and social
Protecting your Security and Privacy on the Web. Tony Brett Head of IT Support Staff Services IT Services. 11 March 2013
 Protecting your Security and Privacy on the Web Tony Brett Head of IT Support Staff Services IT Services 11 March 2013 Agenda Why bother? Common data leaks Email security Viruses & Trojans Phishing Why
Protecting your Security and Privacy on the Web Tony Brett Head of IT Support Staff Services IT Services 11 March 2013 Agenda Why bother? Common data leaks Email security Viruses & Trojans Phishing Why
Looking at the Internet with Google Chrome & Firefox. Scoville Memorial Library Claudia Cayne - September, 2010
 Looking at the Internet with Google Chrome & Firefox Scoville Memorial Library Claudia Cayne - ccayne@biblio.org September, 2010 Google Chrome & Firefox are web browsers - the decoder you need to view
Looking at the Internet with Google Chrome & Firefox Scoville Memorial Library Claudia Cayne - ccayne@biblio.org September, 2010 Google Chrome & Firefox are web browsers - the decoder you need to view
Free antivirus software download
 Cari untuk: Cari Cari Free antivirus software download 3-11-2015 Avast has one of the most popular antivirus apps around, due in part to offering a free version, and it's one that performs respectably.
Cari untuk: Cari Cari Free antivirus software download 3-11-2015 Avast has one of the most popular antivirus apps around, due in part to offering a free version, and it's one that performs respectably.
Firewall Antivirus For Windows Xp Full Version 2013
 Firewall Antivirus For Windows Xp Full Version 2013 Advanced Firewall, Antivirus & Anti-spyware Engine, Advanced Real-Time Antivirus, Enhanced Browser Protection, Identity Protection, Anti-Keylogging,
Firewall Antivirus For Windows Xp Full Version 2013 Advanced Firewall, Antivirus & Anti-spyware Engine, Advanced Real-Time Antivirus, Enhanced Browser Protection, Identity Protection, Anti-Keylogging,
Manually Remove Of Xp Internet Security Protect Virus Manually
 Manually Remove Of Xp Internet Security Protect Virus Manually We show you how to remove malware from a PC or laptop. You may also wish to read: Windows users: how to protect your PC from Check now: do
Manually Remove Of Xp Internet Security Protect Virus Manually We show you how to remove malware from a PC or laptop. You may also wish to read: Windows users: how to protect your PC from Check now: do
The Table Privacy Policy Last revised on August 22, 2012
 The Table Privacy Policy Last revised on August 22, 2012 The Table, an online venue through which your organization and its members/employees can connect to better fulfill its mission respects and is committed
The Table Privacy Policy Last revised on August 22, 2012 The Table, an online venue through which your organization and its members/employees can connect to better fulfill its mission respects and is committed
FAQ. Safe Anywhere PC 12. Disclaimer:
 FAQ Safe Anywhere PC 12 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch pad, F-Secure
FAQ Safe Anywhere PC 12 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch pad, F-Secure
User s Guide. SingNet Desktop Security Copyright 2010 F-Secure Corporation. All rights reserved.
 User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
How To Stop Avg Search Appearing In New Tabs On Google Chrome
 How To Stop Avg Search Appearing In New Tabs On Google Chrome I'm not completely sure when it started, but new tabs seem to randomly open up when I click somewhere while working on chrome. You will opjust
How To Stop Avg Search Appearing In New Tabs On Google Chrome I'm not completely sure when it started, but new tabs seem to randomly open up when I click somewhere while working on chrome. You will opjust
Activation Screen Virus
 How To Get Rid Of Spyware Windows Xp Activation Screen Virus Spyware Clear it's technically not a virus, but it does exhibit plenty of malicious To uninstall the Spyware Clear program from Windows XP,
How To Get Rid Of Spyware Windows Xp Activation Screen Virus Spyware Clear it's technically not a virus, but it does exhibit plenty of malicious To uninstall the Spyware Clear program from Windows XP,
Introduction to the Internet. Part 1. What is the Internet?
 Introduction to the Internet Part 1 What is the Internet? A means of connecting a computer to any other computer anywhere in the world via dedicated routers and servers. When two computers are connected
Introduction to the Internet Part 1 What is the Internet? A means of connecting a computer to any other computer anywhere in the world via dedicated routers and servers. When two computers are connected
Elementary Computing CSC 100. M. Cheng, Computer Science
 Elementary Computing CSC 100 1 Internet (2) TCP/IP and IP Addresses Hostnames and Domain Name System Internet Services Client/Server and Peer- 2- Peer Applications SPAMs & Phishing, Worms, Viruses & Trojans
Elementary Computing CSC 100 1 Internet (2) TCP/IP and IP Addresses Hostnames and Domain Name System Internet Services Client/Server and Peer- 2- Peer Applications SPAMs & Phishing, Worms, Viruses & Trojans
(electronic mail) is the exchange of computer-stored messages by telecommunication.
 What is email? E-mail (electronic mail) is the exchange of computer-stored messages by telecommunication. E-mail is one of the protocols included with the Transport Control Protocol/Internet Protocol (TCP/IP)
What is email? E-mail (electronic mail) is the exchange of computer-stored messages by telecommunication. E-mail is one of the protocols included with the Transport Control Protocol/Internet Protocol (TCP/IP)
How To Removing Personal Antivirus Security Pro From Windows 8
 How To Removing Personal Antivirus Security Pro From Windows 8 Antivirus Action, Antivirus Monitor, Antivirus 7 or Antivirus5, Antivirus 8, Antivirus 8 Fast Windows Antivirus 2011, Fix Clean Repair, Flu
How To Removing Personal Antivirus Security Pro From Windows 8 Antivirus Action, Antivirus Monitor, Antivirus 7 or Antivirus5, Antivirus 8, Antivirus 8 Fast Windows Antivirus 2011, Fix Clean Repair, Flu
CDH Top 5. Free Recommended Cyber Security Tools. 1. Malwarebytes 2. CCleaner 3. Norton Safe Web 4. EaseUS Todo Backup 5.
 CDH Top 5 Free Recommended Cyber Security Tools www.cyberdefensehub.com 1. Malwarebytes 2. CCleaner 3. Norton Safe Web 4. EaseUS Todo Backup 5. Wireshark 1 Malwarebytes Malwarebytes is a free anti-malware
CDH Top 5 Free Recommended Cyber Security Tools www.cyberdefensehub.com 1. Malwarebytes 2. CCleaner 3. Norton Safe Web 4. EaseUS Todo Backup 5. Wireshark 1 Malwarebytes Malwarebytes is a free anti-malware
STEAM Clown Production. Passwords. STEAM Clown & Productions Copyright 2016 STEAM Clown. Page 1 - Cyber Security Class
 Production Passwords Page 1 - Cyber Security Class Copyright 2016 Does It Matter? Is your email password the same as your Facebook password? Is that Good? Bad? Why? Page 2 - Cyber Security Class Copyright
Production Passwords Page 1 - Cyber Security Class Copyright 2016 Does It Matter? Is your email password the same as your Facebook password? Is that Good? Bad? Why? Page 2 - Cyber Security Class Copyright
FAQ: Privacy, Security, and Data Protection at Libraries
 FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
Cybersecurity For The Small Business & Home User ( Geared toward Windows, but relevant to Apple )
 Cybersecurity For The Small Business & Home User ( Geared toward Windows, but relevant to Apple ) Topics: Antivirus / DSSO/ Email Computer Backups Security On The Go Mobile Safety Your first line of defense
Cybersecurity For The Small Business & Home User ( Geared toward Windows, but relevant to Apple ) Topics: Antivirus / DSSO/ Email Computer Backups Security On The Go Mobile Safety Your first line of defense
TxEIS on Internet Explorer 8
 TxEIS on Internet Explorer 8 General Set Up Recommendations: Several modifications will need to be made to the computer settings in Internet Explorer to ensure TxEIS runs smoothly, reports pop up as desired,
TxEIS on Internet Explorer 8 General Set Up Recommendations: Several modifications will need to be made to the computer settings in Internet Explorer to ensure TxEIS runs smoothly, reports pop up as desired,
BEST PRACTICES FOR PERSONAL Security
 BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
Cyber Security Guide. For Politicians and Political Parties
 Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
COMMON WAYS IDENTITY THEFT CAN HAPPEN:
 COMMON WAYS IDENTITY THEFT CAN HAPPEN: OLD FASHIONED STEALING / DUMPSTER DIVING Thieves typically steal wallets and purses. They also steal mail such as credit card and bank statements, pre-approved credit
COMMON WAYS IDENTITY THEFT CAN HAPPEN: OLD FASHIONED STEALING / DUMPSTER DIVING Thieves typically steal wallets and purses. They also steal mail such as credit card and bank statements, pre-approved credit
PRACTICING SAFE COMPUTING AT HOME
 PRACTICING SAFE COMPUTING AT HOME WILLIAM (THE GONZ) FLINN M.S. INFORMATION SYSTEMS SECURITY MANAGEMENT; COMPTIA SECURITY+, I-NET+, NETWORK+; CERTIFIED PATCHLINK ENGINEER ENTERPRISE INFORMATION SYSTEMS
PRACTICING SAFE COMPUTING AT HOME WILLIAM (THE GONZ) FLINN M.S. INFORMATION SYSTEMS SECURITY MANAGEMENT; COMPTIA SECURITY+, I-NET+, NETWORK+; CERTIFIED PATCHLINK ENGINEER ENTERPRISE INFORMATION SYSTEMS
PROTECTING YOUR BUSINESS ASSETS
 PROTECTING YOUR BUSINESS ASSETS How to Spot Danger Before Your Computer Gets Infected, Your Site Hosts Malware, and Your Credit Card Number Gets Stolen A MyNAMS Presentation by Regina Smola @2012 Regina
PROTECTING YOUR BUSINESS ASSETS How to Spot Danger Before Your Computer Gets Infected, Your Site Hosts Malware, and Your Credit Card Number Gets Stolen A MyNAMS Presentation by Regina Smola @2012 Regina
Course Outline (version 2)
 Course Outline (version 2) Page. 1 CERTIFIED SECURE COMPUTER USER This course is aimed at end users in order to educate them about the main threats to their data s security. It also equips the students
Course Outline (version 2) Page. 1 CERTIFIED SECURE COMPUTER USER This course is aimed at end users in order to educate them about the main threats to their data s security. It also equips the students
Keep In touch Digital skills for older people itkite.wordpress.com DON T PANIC! Just keep taking your tablet (with you)
 Keep In touch Digital skills for older people 01267 245555 kite@cavs.org.uk DON T PANIC! Just keep taking your tablet (with you) Beginners Tablet Guide The Tablet Environment... 2 Turning the tablet on
Keep In touch Digital skills for older people 01267 245555 kite@cavs.org.uk DON T PANIC! Just keep taking your tablet (with you) Beginners Tablet Guide The Tablet Environment... 2 Turning the tablet on
August 12. Tips for Gmail. Tips to save time and increase your productivity. Gmail Training
 Tips for Gmail August 12 2014 Gmail Tips to save time and increase your productivity Tips for Gmail Gmail Learn tips to save time, increase your productivity, and manage your email efficiently. Page 2
Tips for Gmail August 12 2014 Gmail Tips to save time and increase your productivity Tips for Gmail Gmail Learn tips to save time, increase your productivity, and manage your email efficiently. Page 2
Learning Center Computer and Security Settings
 Learning Center Computer and Security Settings Learning Center Computer Settings Please Note: To allow your computer to communicate most effectively with the Learning Center, and update your training record
Learning Center Computer and Security Settings Learning Center Computer Settings Please Note: To allow your computer to communicate most effectively with the Learning Center, and update your training record
Download firefox with virus protection
 P ford residence southampton, ny Download firefox with virus protection 3-11-2015 Protect your devices with the best free antivirus on the market. Download Avast antivirus and anti-spyware protection for
P ford residence southampton, ny Download firefox with virus protection 3-11-2015 Protect your devices with the best free antivirus on the market. Download Avast antivirus and anti-spyware protection for
Online Communication. Chat Rooms Instant Messaging Blogging Social Media
 Online Communication E-mail Chat Rooms Instant Messaging Blogging Social Media Advantages: Reduces cost of postage Fast and convenient Eliminates phone charges Disadvantages: May be difficult to understand
Online Communication E-mail Chat Rooms Instant Messaging Blogging Social Media Advantages: Reduces cost of postage Fast and convenient Eliminates phone charges Disadvantages: May be difficult to understand
Security Issues When Preparing for Disasters
 Security Issues When Preparing for Disasters Catherine Sanders Reach, Director American Bar Association Legal Technology Resource Center November 10, 2006 Today s Topics Disaster Planning Backup Security
Security Issues When Preparing for Disasters Catherine Sanders Reach, Director American Bar Association Legal Technology Resource Center November 10, 2006 Today s Topics Disaster Planning Backup Security
Report Course name ABSTRACT. Research and reporting. Survey Report. Nguyen Ngoc Long. Ann Viitala. Adesh Chymariya. Shu Sheng 5/2/2010.
 Course name Assignment Authors Research and reporting Survey Nguyen Ngoc Long Ann Viitala Adesh Chymariya Shu Sheng Date of the report 5/2/2010 ABSTRACT CONTENTS 1 INTRODUCTION 3 2 THEORETICAL FRAMEWORK,
Course name Assignment Authors Research and reporting Survey Nguyen Ngoc Long Ann Viitala Adesh Chymariya Shu Sheng Date of the report 5/2/2010 ABSTRACT CONTENTS 1 INTRODUCTION 3 2 THEORETICAL FRAMEWORK,
Last tested with CHROME version 63 Jim McKnight Chrome.lwp revised
 Last tested with CHROME version 63 Jim McKnight www.jimopi.net Chrome.lwp revised 12-21-2017 CONTENTS: o GET & INSTALL CHROME o CHROME TIPS o ADD-ON s TIPS GOOGLE CHROME TIPS o SETUP & CONFIGURE CHROME
Last tested with CHROME version 63 Jim McKnight www.jimopi.net Chrome.lwp revised 12-21-2017 CONTENTS: o GET & INSTALL CHROME o CHROME TIPS o ADD-ON s TIPS GOOGLE CHROME TIPS o SETUP & CONFIGURE CHROME
Keeping Your Computer Secure Quick Reference Guide
 Keeping Your Computer Secure Quick Reference Guide Created: 3/16/2010 Page 1 of 1 Table Of Contents 1. Introduction... 3 2. Keeping Your Computer Up to Date... 4 2.1 Windows... 4 2.2 Mac... 6 3. Malware
Keeping Your Computer Secure Quick Reference Guide Created: 3/16/2010 Page 1 of 1 Table Of Contents 1. Introduction... 3 2. Keeping Your Computer Up to Date... 4 2.1 Windows... 4 2.2 Mac... 6 3. Malware
Safety and Security. April 2015
 Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
About Lavasoft. Contact. Key Facts:
 About Lavasoft Lavasoft is the original anti-malware company, creating award-winning, free security and privacy software since 1999. Born of the belief that online security should be available to everybody,
About Lavasoft Lavasoft is the original anti-malware company, creating award-winning, free security and privacy software since 1999. Born of the belief that online security should be available to everybody,
Internet Crimes Against Children:
 Internet Crimes Against Children: Web, 2011 PROGRAM MATERIALS Presented By Professor Donald R. Mason Associate Director & Research Professor The National Center for Justice & the Rule of Law at The University
Internet Crimes Against Children: Web, 2011 PROGRAM MATERIALS Presented By Professor Donald R. Mason Associate Director & Research Professor The National Center for Justice & the Rule of Law at The University
CCleaner* Available at: ccleaner.com. Galen Garretson 6/26/2018. *segments from ccleaner.com
 CCleaner* Available at: ccleaner.com Galen Garretson 6/26/2018 *segments from ccleaner.com What is CCleaner? CCleaner is a system optimization, privacy and cleaning tool. It removes unused files from your
CCleaner* Available at: ccleaner.com Galen Garretson 6/26/2018 *segments from ccleaner.com What is CCleaner? CCleaner is a system optimization, privacy and cleaning tool. It removes unused files from your
Browser Configuration Reference
 Sitecore CMS 7.0 or later Browser Configuration Reference Rev: 2013-09-30 Sitecore CMS 7.0 or later Browser Configuration Reference Optimizing Internet Explorer and other web browsers to work with Sitecore
Sitecore CMS 7.0 or later Browser Configuration Reference Rev: 2013-09-30 Sitecore CMS 7.0 or later Browser Configuration Reference Optimizing Internet Explorer and other web browsers to work with Sitecore
Introduction to
 Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting
Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting
Quick Heal Total Security for Mac. Simple, fast and seamless protection for Mac.
 Simple, fast and seamless protection for Mac. Product Highlights Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth email
Simple, fast and seamless protection for Mac. Product Highlights Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth email
How to Encrypt Files Containing Sensitive Data (using 7zip software or Microsoft password protection) How to Create Strong Passwords
 How to Encrypt Files Containing Sensitive Data (using 7zip software or Microsoft password protection) How to Create Strong Passwords School IT Systems Support Standards and School Effectiveness Hertfordshire
How to Encrypt Files Containing Sensitive Data (using 7zip software or Microsoft password protection) How to Create Strong Passwords School IT Systems Support Standards and School Effectiveness Hertfordshire
Private Browsing: an Inquiry on Usability and Privacy Protection
 Private Browsing: an Inquiry on Usability and Privacy Protection Xianyi Gao*, Yulong Yang*, Huiqing Fu*, Janne Lindqvist*, Yang Wang+ *Rutgers University +Syracuse University Published in WPES 2014 What
Private Browsing: an Inquiry on Usability and Privacy Protection Xianyi Gao*, Yulong Yang*, Huiqing Fu*, Janne Lindqvist*, Yang Wang+ *Rutgers University +Syracuse University Published in WPES 2014 What
Browser Settings. Updated 4/30/ SSF
 Browser Settings Updated 4/30/2014 - SSF Contents How to Locate the Online Banking URL... 3 Initial Steps for Browser Settings... 8 Internet Explorer... 9 Firefox... 13 Chrome... 18 Safari 6.0.5 and up...
Browser Settings Updated 4/30/2014 - SSF Contents How to Locate the Online Banking URL... 3 Initial Steps for Browser Settings... 8 Internet Explorer... 9 Firefox... 13 Chrome... 18 Safari 6.0.5 and up...
Schematic Antivirus 2013 For Windows Xp Full Version
 Schematic Antivirus 2013 For Windows Xp Full Version Download Bitdefender's free antivirus software and enjoy award-winning, nag-free protection against e-threats. Bitdefender Virus & Spyware Removal Bitdefender
Schematic Antivirus 2013 For Windows Xp Full Version Download Bitdefender's free antivirus software and enjoy award-winning, nag-free protection against e-threats. Bitdefender Virus & Spyware Removal Bitdefender
Comodo Internet Security Software Version 10.0
 Comodo Internet Security Software Version 10.0 Installation Guide Guide Version 10.0.010918 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States 1. CIS Installation Before you install
Comodo Internet Security Software Version 10.0 Installation Guide Guide Version 10.0.010918 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States 1. CIS Installation Before you install
But you can also click CC/BCC to send a carbon copy or a blind carbon copy.
 Gmail Basics, Part 2 Message Management The examples in this handout were created using Gmail, a free Web-based e-mail service. The processes described may vary among different e-mail services. Sending
Gmail Basics, Part 2 Message Management The examples in this handout were created using Gmail, a free Web-based e-mail service. The processes described may vary among different e-mail services. Sending
Privacy Policy. LAST UPDATED: 23 June March 2017
 Privacy Policy LAST UPDATED: 23 June 20156 March 2017 VERSION 3.0 2.0 Comment [A1]: The Privacy Policy has been updated because we now use Google Analytics, to help improve our services and our communications
Privacy Policy LAST UPDATED: 23 June 20156 March 2017 VERSION 3.0 2.0 Comment [A1]: The Privacy Policy has been updated because we now use Google Analytics, to help improve our services and our communications
CS Paul Krzyzanowski
 Computer Security 17. Tor & Anonymous Connectivity Anonymous Connectivity Paul Krzyzanowski Rutgers University Spring 2018 1 2 Anonymity on the Internet Often considered bad Only criminals need to hide
Computer Security 17. Tor & Anonymous Connectivity Anonymous Connectivity Paul Krzyzanowski Rutgers University Spring 2018 1 2 Anonymity on the Internet Often considered bad Only criminals need to hide
Conveying Emotion. Chapter 12: Computers In Polite Society: Social Implications of IT. Improving the Effectiveness of . Problems with
 Chapter 12: Computers In Polite Society: Social Implications of IT Fluency with Information Technology Third Edition by Lawrence Snyder Improving the Effectiveness of Email Problems with email: Conveying
Chapter 12: Computers In Polite Society: Social Implications of IT Fluency with Information Technology Third Edition by Lawrence Snyder Improving the Effectiveness of Email Problems with email: Conveying
EDGE, MICROSOFT S BROWSER
 EDGE, MICROSOFT S BROWSER To launch Microsoft Edge, click the Microsoft Edge button (it s the solid blue E) on the Windows Taskbar. Edge Replaces Internet Explorer Internet Explorer is no longer the default
EDGE, MICROSOFT S BROWSER To launch Microsoft Edge, click the Microsoft Edge button (it s the solid blue E) on the Windows Taskbar. Edge Replaces Internet Explorer Internet Explorer is no longer the default
RNDC / NDC MicroStrategy Supplier Web Troubleshooting Guide
 RNDC / NDC MicroStrategy Supplier Web Troubleshooting Guide Where do I log into MicroStrategy for RNDC markets? 2 Where do I log into MicroStrategy for NDC markets? 3 Why can t I log in? Most common log
RNDC / NDC MicroStrategy Supplier Web Troubleshooting Guide Where do I log into MicroStrategy for RNDC markets? 2 Where do I log into MicroStrategy for NDC markets? 3 Why can t I log in? Most common log
Internet Explorer 6 and 7 Users
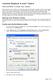 Internet Explorer 6 and 7 Users How and Why to Clear Your Cache Often referred to as the cache, the Temporary Internet Files folder contains a kind of travel record of the items you have seen, heard, or
Internet Explorer 6 and 7 Users How and Why to Clear Your Cache Often referred to as the cache, the Temporary Internet Files folder contains a kind of travel record of the items you have seen, heard, or
7, 8, 8.1, 10. You can still get windows ten upgrade from 7, 8 and 8.1 now. Just need the right file to upgrade, I have it.
 7, 8, 8.1, 10 This presentation is on windows 10. Most if not all procedures we will discuss today will work on all 4 versions of windows talk about today. Below is when support ends for each version.
7, 8, 8.1, 10 This presentation is on windows 10. Most if not all procedures we will discuss today will work on all 4 versions of windows talk about today. Below is when support ends for each version.
Norton 360 vs trend micro vs mcafee vs symantec: which anti-virus solution is best
 Norton 360 vs trend micro vs mcafee vs symantec: which anti-virus solution is best Search 4 days ago. However, Windows antivirus tools still play an important role in the enterprise security strategy..
Norton 360 vs trend micro vs mcafee vs symantec: which anti-virus solution is best Search 4 days ago. However, Windows antivirus tools still play an important role in the enterprise security strategy..
Quick Heal Total Security
 For secure online banking, smooth Internet surfing, and robust protection for your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware
For secure online banking, smooth Internet surfing, and robust protection for your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware
Getting Started Guide
 Getting Started Guide for education accounts Setup Manual Edition 7 Last updated: September 15th, 2016 Note: Click on File and select Make a copy to save this to your Google Drive, or select Print, to
Getting Started Guide for education accounts Setup Manual Edition 7 Last updated: September 15th, 2016 Note: Click on File and select Make a copy to save this to your Google Drive, or select Print, to
SUMMARIES OF INTERACTIVE MULTIMEDIA
 SUMMARIES OF INTERACTIVE MULTIMEDIA GRADE 10-12 INTERNET TECHNOLOGIES 1. Introduction to Electronic Communications Use this lesson to: Understand the differences between the various e-communications modes
SUMMARIES OF INTERACTIVE MULTIMEDIA GRADE 10-12 INTERNET TECHNOLOGIES 1. Introduction to Electronic Communications Use this lesson to: Understand the differences between the various e-communications modes
Welcome to our Moodle site! What is Moodle?
 Welcome to our Moodle site! We are excited to introduce the use of this online e-learning platform in our "Get SMART FAST" Training Program! We believe the use of this virtual classroom and training format
Welcome to our Moodle site! We are excited to introduce the use of this online e-learning platform in our "Get SMART FAST" Training Program! We believe the use of this virtual classroom and training format
How To Remove A Virus Manually Windows 7 Without Antivirus Security Pro
 How To Remove A Virus Manually Windows 7 Without Antivirus Security Pro Security Defender is a fake antivirus program, it should not be trusted, since it is a The program usually installs on PCs without
How To Remove A Virus Manually Windows 7 Without Antivirus Security Pro Security Defender is a fake antivirus program, it should not be trusted, since it is a The program usually installs on PCs without
GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE
 GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE TABLE OF CONTENTS PROTECTIVE MEASURES... 2 PREPARATION CHECKLIST... 2 IF YOU SUSPECT YOUR ACCOUNT IS COMPROMISED, THE FOLLOWING ACTIONS ARE ADVISED:...
GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE TABLE OF CONTENTS PROTECTIVE MEASURES... 2 PREPARATION CHECKLIST... 2 IF YOU SUSPECT YOUR ACCOUNT IS COMPROMISED, THE FOLLOWING ACTIONS ARE ADVISED:...
Features. Product Highlights. Not just an app, but a friend for your phone. Optimization. Speed. Battery. Storage. Data Usage
 PRO Not just an app, but a friend for your phone. Product Highlights Fonetastic is an all-in-one app for Android devices. Built with multiple productivity and security features, it enhances your device
PRO Not just an app, but a friend for your phone. Product Highlights Fonetastic is an all-in-one app for Android devices. Built with multiple productivity and security features, it enhances your device
3.5 SECURITY. How can you reduce the risk of getting a virus?
 3.5 SECURITY 3.5.4 MALWARE WHAT IS MALWARE? Malware, short for malicious software, is any software used to disrupt the computer s operation, gather sensitive information without your knowledge, or gain
3.5 SECURITY 3.5.4 MALWARE WHAT IS MALWARE? Malware, short for malicious software, is any software used to disrupt the computer s operation, gather sensitive information without your knowledge, or gain
Cyber Smarts Using Social Media Wisely
 Cyber Smarts Using Social Media Wisely Posted on March 24, 2016 by Shridevi Stock Photo You have access to the world s largest museum, art gallery, library and social group ever created. You also have
Cyber Smarts Using Social Media Wisely Posted on March 24, 2016 by Shridevi Stock Photo You have access to the world s largest museum, art gallery, library and social group ever created. You also have
A global network of computers that share pages of information called webpages or websites. Internet Service Provider
 INTERNET: A global network of computers that share pages of information called webpages or websites Computer Basics 3 Internet CONNECTING TO THE INTERNET Internet Service Provider INTERNET SERVICE PROVIDER
INTERNET: A global network of computers that share pages of information called webpages or websites Computer Basics 3 Internet CONNECTING TO THE INTERNET Internet Service Provider INTERNET SERVICE PROVIDER
Symantec Antivirus Manual Removal Tool Corporate Edition 10.x
 Symantec Antivirus Manual Removal Tool Corporate Edition 10.x Learn how to download and run the Norton Removal Tool to uninstall the Norton products from your Looking for a free Virus and Spyware removal
Symantec Antivirus Manual Removal Tool Corporate Edition 10.x Learn how to download and run the Norton Removal Tool to uninstall the Norton products from your Looking for a free Virus and Spyware removal
Learning Center Computer and Security Settings
 Learning Center Computer and Security Settings Learning Center Computer Settings Please Note: To allow your computer to communicate most effectively with the Learning Center, and update your training record
Learning Center Computer and Security Settings Learning Center Computer Settings Please Note: To allow your computer to communicate most effectively with the Learning Center, and update your training record
Comodo Internet Security Software Version 10.1
 Comodo Internet Security Software Version 10.1 Installation Guide Guide Version 10.1.012218 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States 1. CIS Installation Please read
Comodo Internet Security Software Version 10.1 Installation Guide Guide Version 10.1.012218 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States 1. CIS Installation Please read
Learning and Development. UWE Staff Profiles (USP) User Guide
 Learning and Development UWE Staff Profiles (USP) User Guide About this training manual This manual is yours to keep and is intended as a guide to be used during the training course and as a reference
Learning and Development UWE Staff Profiles (USP) User Guide About this training manual This manual is yours to keep and is intended as a guide to be used during the training course and as a reference
ASTE 2016 Ning Network access our Ning on a mobile device, browsers FREE should NOT To join the ASTE 2016 Ning
 ASTE 2016 Ning Network Ning is a social networking site where groups of people can interact in a number of ways, including forums, photos, videos, and other options as the site expands. Ning also uses
ASTE 2016 Ning Network Ning is a social networking site where groups of people can interact in a number of ways, including forums, photos, videos, and other options as the site expands. Ning also uses
UPLOADING AN IMAGE TO FACEBOOK AND MAKING IT YOUR PROFILE PICTURE
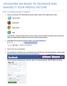 UPLOADING AN IMAGE TO FACEBOOK AND MAKING IT YOUR PROFILE PICTURE PART 1: UPLOADING AN IMAGE TO FACEBOOK 1. Open your web browser. This will most likely be Internet Explorer, Mozilla Firefox, Google Chrome
UPLOADING AN IMAGE TO FACEBOOK AND MAKING IT YOUR PROFILE PICTURE PART 1: UPLOADING AN IMAGE TO FACEBOOK 1. Open your web browser. This will most likely be Internet Explorer, Mozilla Firefox, Google Chrome
Comodo Internet Security Software Version 11.0
 Comodo Internet Security Software Version 11.0 Installation Guide Guide Version 11.0.080918 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States 1. CIS Installation Please read
Comodo Internet Security Software Version 11.0 Installation Guide Guide Version 11.0.080918 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States 1. CIS Installation Please read
Chromebooks boot in seconds, and resume instantly. When you turn on a Chromebook and sign in, you can get online fast.
 chromebook meet chromebook What is a chromebook? Chromebooks are... A new type of computer that is fast, simple and secure. Built for the web best of Google and access to thousands of online web apps.
chromebook meet chromebook What is a chromebook? Chromebooks are... A new type of computer that is fast, simple and secure. Built for the web best of Google and access to thousands of online web apps.
How To Delete Avira Antivirus From My >>>CLICK HERE<<<
 How To Delete Avira Antivirus From My Computer Windows 7 Dec 31, 2014. It would not update properly, so I decided to uninstall it. I used Revo Windows 7 Home Premium 64 bit. 44 posts I re-installed the
How To Delete Avira Antivirus From My Computer Windows 7 Dec 31, 2014. It would not update properly, so I decided to uninstall it. I used Revo Windows 7 Home Premium 64 bit. 44 posts I re-installed the
