User Guide. This user guide explains how to use and update Max Secure Anti Virus Enterprise Client.
|
|
|
- Jessica Johnston
- 5 years ago
- Views:
Transcription
1 User Guide This user guide explains how to use and update Max Secure Anti Virus Enterprise Client. Copyright Max Secure Software. All rights reserved.
2 Contents 2 Contents Introduction... 3 System Requirements... 4 Technical Support Overview... 7 Scan... 8 Cleaning of Detected Threats... 8 Scan Options Exclude Recovering of Excluded Threats Recover Options Internet Fix Product Information USB Manager Firewall Network Filter Application Rules... Error! Bookmark not defined. Updating Max Secure Anti Virus... 20
3 Introduction 3 Introduction Max Secure Anti-Virus Enterprise Edition (Max Secure AVEE) delivers market-leading solutions that help manage, simplify, and secure complex IT environments. Max Secure Anti Virus benefits educational institutions, health-care facilities, libraries, government organizations, and corporations. Max Secure Anti-Virus Enterprise provides protection from security threats without slowing down computers due to very fast and lean scanner. It gives you powerful anti-virus, anti-rootkit and antispyware and Firewall software in-one that protects you against today s highly complex malware threats and a complete layered security solution. Max Secure Anti Virus Client protects workstations from the following threats: Adware Rogue Security Programs Root kits Spyware Trojan Worms Mass Mailers Viruses Max Secure Antivirus Client can be installed through Max Secure Antivirus Server on any number of machines through File Sharing, msi installer, IIS web sharing or manually.
4 System Requirements 4 System Requirements The following minimum system requirements are needed to run Max Secure Anti Virus Enterprise Client: 521 MB of RAM available 1 GB of free hard disk space Internet Connectivity for Live Updates Client can be installed on any Windows Operating System starting from Windows 2000 to Windows 10. Windows 2000 Professional with Service Pack 4 Windows XP (32-bit) or Windows XP (64-bit) Windows Vista all versions (32-bit or 64 bit) Windows 7 all versions (32 or 64 bit) Windows 8 all versions (32 or 64 bit) Windows 10 all versions (32-bit or 64 bit)
5 Technical Support 5 Technical Support Every effort has been made to design this software for ease of use and to be problem free. If you encounter any issues, you can get help from many different resources such as , Chat and Phone. Phone: Website: Live Chat: (available in India only) info@maxpcsecure.com
6 6 This chapter explains how to use Max Secure Anti Virus. Overview Scan Exclude Recover Options USB Manager Firewall
7 7 (if you don t have client setup exe you can get it from server path To access server type in your browser ip... /MaxAVEE take as per your client windows Os 32bit /64 bit by clicking on it. ) Overview You can check Scan Status, Update Status and Active Protection Status from Overview tab. Figure 1 - Overview User Interface Scan Status: In the Scan Status section you can see information of Last Scan and Next Scan. You can start scanning by clicking on Scan Now button. Update Status: Here you can find Last Live Update Date and Threat Definition Version number. You can update Max Secure Anti Virus Client by clicking on Update Now button. Active Protection: You can check Active Protection is enabled or disabled from here.
8 8 Scan 1. Click on Scan button present on Main UI. 2. Select the scan option you want to perform. There are three Scan Options available - Quick Scan, Full Scan and Custom Scan. 3. Click on Start Scan button. While Max Secure Anti Virus scan is running, Figure 2 - Scan User Interface If you want to pause scanning for some time then you can do it by clicking on the Pause Scan button. When you wish to resume scan then click on the Resume button. You can stop the scanning by clicking on the Stop Scanning button. Cleaning of Detected Threats After scanning is complete, Max Secure Anti Virus will display a list of threats it detected on your PC with Quarantine action status. The following information about each threat is displayed: 1. Threat Level 2. Threat Type 3. Threat
9 9 4. Action 5. Threat Information Link Figure 3 - Scan Result Select the threats which you want to clean then click on clean button. Max Secure Anti Virus will clean all the selected threats.
10 10 Scan Options Max Secure Anti Virus provides three types of scans: Quick Scan will scan for the current operating system only. Full Scan will scan your complete PC including the operating system, program files as well as your files and documents. If your PC has more than one hard drive on it, you can select which hard drive you would like to scan in the Full Scan option. This is done by checking the appropriate checkbox before the hard drive letter (e.g. C :) in the Full Scan window. Rootkit: Rootkit Scan is based on generic, heuristics scan. A rootkit is a set of software tools intended to hide running processes, files or system data from the operating system. A rootkit substitutes malicious code in place of legitimate Operating System routines. It does so in a highly stealth-like manner by turning off certain security routines. They are difficult to detect. Rootkits are difficult to clean as they in granulate deeply within the Registry and system files. Deep: Deep Scan option does special threat scan throughout the drive so that Max Secure Anti Virus catches more special threat entries. It takes more time in first scan but subsequent scan will take less time to scan special threat on the drive. Custom Scan will scan only the selected locations by the user. Please Note: When you are running the full scan for the first time the application maps the signatures first and so takes long time for scanning the PC for the first time, also it depends on the processor speed of the PC and the total Hard Drive space that you have. But if you try to do the full scan second time it will not take so long.
11 Exclude 11 With the help of this option, user can select the threat by name or by particular entry that he/she doesn't want to be scanned by Max Secure Anti Virus. The Exclude window displays a list of the threat name and scanned entry path on your PC it detected during the last scans. You can select any threat name or particular threat entry that you d like to exclude by checking the checkbox (es) provided before the threat name(s) or entry. The Select All checkbox lets you select all the threat in the list at one go. Click the Exclude button to exclude the selected threat from the next scan. These excluded threat or particular entry will not be scanned the next time onward. The excluded threat can be scanned again if you later decide to do so by clicking on the Recover button near this Exclude window. As before, select the threat name or entry you'd like to recover before clicking on Recover. Figure 4 - Exclude User Interface Recovering of Excluded Threats With the help of this option, you can recover threat that you previously excluded from scans. The second list on this Exclude window consists of threat that you have chosen to exclude from scans. Select the programs that you want to be scanned and click on Recover.
12 12 Next time when you scan the PC, these threat will be scanned for and will be shown in the list if found on your PC.
13 13 Recover Click on Recover button in the main window and you will see all of the threats that you had quarantined so far. Your PC is safe and isolated from these threats. After quarantining threats found during a scan, you can either delete these malicious programs or recover them out of quarantine vault from here. Recovering them will result in all the threats becoming active again and your PC will become infected. So recover with caution. Figure 5 - Recover User Interface To recover any threat entry and do not want Max Secure Anti Virus to scan it again, click on Recover & Exclude button. To recover the threat, click on Recover button. To permanently remove the programs from your system, click on Delete button. Please Note: 1. Quarantine has already disabled the threat but the programs will remain on your PC in a dormant stage and can not cause any harm. 2. Threats Deleted using the Delete option are permanently removed and cannot be recovered.
14 14 Options From Options tab you can fix your Internet connection and also view the Product Information. Figure 6-Options User Interface Internet Fix Max Secure Anti Virus displays a list of installed network drivers on your PC. If you want to fix Internet problems on your PC, click on the Fix Internet button. This will restore to your PC the original list of LSPs that were installed during your operating system's installation. Any LSPs installed by users or programs since then will be removed. If you want to export the list to a file for future reference, click on Export. In the window that opens, select the name and location of the text file that you wish to save the list in and click OK. The list will be saved in that location with that name. Warning: Use this option only if you have Internet connection or network problems. If you use this option without any purpose, some valid applications using LSPs may stop working properly. Product Information The Product Information section displays the versions of various Max Secure Anti Virus engines in the system. These version numbers are updated every time you run Live Update and the corresponding engines are updated. This section also displays the last date when Live Update was run.
15 15 USB Manager Scan Setting Scan Removable Devices: Checking this option will scan removable devices which user attached to the PC. Manual: On selecting this option, any time a removable device is attached to the PC, a popup window will open with options - Scan and Cancel. Clicking on Scan would scan the removable devices only. Auto: On checking this option, any time a removable device is attached to the PC; Max Secure Anti Virus will start scanning. This will only scan the removable devices. USB Secure Autorun.inf Block: The Auto Run function in Windows can launch installers and other programs automatically when you insert a CD or flash drive, but this convenience poses a serious security risk. Every recent version of Windows has features known as AutoPlay and AutoRun. These functions are designed to launch applications automatically from an external device containing the necessary AutoRun information. This is what causes an installer window to pop up when you insert a software disc into your CD or DVD drive, for example, or makes a pop-up menu icon appear in the taskbar tray when you insert a USB flash drive. However convenient this might be, unfortunately, AutoRun also opens a huge door for viruses, Trojan horses, and worms. All it takes is a USB flash drive with an autorun.inf file and an executable in its root. Once inserted, a worm launched in this manner can infect every disk partition it finds, jumping from computer to computer as network users connect to an infected drive. USB Manager allows you to block autorun automatically so that you have control over when contents of USB drive run on your PC or not.
16 16 Figure 7- USB Manager User Interface Total Block: This is a very useful feature. These days data protection is very important where anyone can connect USB to your PC or company PC and download all the information on the drive and take away. This unauthorized access is now manageable using a password. This feature can totally secure your PC from unwanted programs running on your PC from USB device. Password Protection: When you set the password in Password Protection section then as soon as you attach a removable device to the PC; it will ask for password to open Removable Device Scan window.
17 17 Firewall A firewall is a piece of software or hardware that helps screen out hackers, viruses, and worms that try to reach your computer over the Internet. If you are a home user or a business user, using a firewall is the most effective and important first step you can take to help protect your computer. Max Secure Firewall provides a robust way to effectively filter network traffic, prevent malicious behavior, protect running processes and filter web content. It provides filtering of I/O requests at the kernel and user levels. Max Secure Firewall is one of the best defenses against malicious software attacks on your system. Network Filter The network filter is an IP Based rule which helps in restricting any application to connect to a remote machine. Here you can specify a range of IP Address along with the port that should be blocked or allowed. The following example shows where you want the client to be allowed full access to the Local Intranet inbound and outbound. Figure 8- Network Filter User Interface
18 18 Figure 9 Firewall Insert IP User Interface Figure 10 Firewall Insert IP User Interface The added Network Monitor Rule for will be blocked by Max Secure Firewall & will displayed like below,
19 19 Figure 11 Blocked by Max Secure Firewall Browser Edit: By using this button provided at Network Monitor user can edit the already added Network Monitor Rules by selecting the rule from User added only. The rules added from system cannot be edited anyway as they are default websites and marked as Default Black List. Delete: By using this button provided at Network Monitor UI user can Delete the Network Monitor Rules Added by him i.e. by user. The rules added from system cannot be deleted anyway as they are default websites and marked as Default Black List. Save: By using this button provided at Network Monitor UI user can save the total changes done by him that may be either added any new rule or Edited ant existing rule or it may be deleted any rule from Network Monitor List.
20 Updating Max Secure Anti Virus 20 Updating Max Secure Anti Virus Max Secure is continuously updating database of virus, spyware, bad cookies, bad BHOs and bad ActiveX controls for your protection. You can benefit from these updates using the Update Now button present in Update Status section of Overview tab. After clicking on the Update Now button; Live Update window opens which downloads the latest versions of the database file, version file and other files necessary to update your copy of Max Secure Anti Virus. Figure 12- Live Update User Interface
Seqrite Antivirus for Server
 Best server security with optimum performance. Product Highlights Easy installation, optimized antivirus scanning, and minimum resource utilization. Robust and interoperable technology makes it one of
Best server security with optimum performance. Product Highlights Easy installation, optimized antivirus scanning, and minimum resource utilization. Robust and interoperable technology makes it one of
Quick Heal AntiVirus Pro Advanced. Protects your computer from viruses, malware, and Internet threats.
 AntiVirus Pro Advanced Protects your computer from viruses, malware, and Internet threats. Features List Ransomware Protection anti-ransomware feature is more effective and advanced than other anti-ransomware
AntiVirus Pro Advanced Protects your computer from viruses, malware, and Internet threats. Features List Ransomware Protection anti-ransomware feature is more effective and advanced than other anti-ransomware
Quick Heal AntiVirus for Server. Optimized Antivirus Scanning. Low on Resources. Strong on Technology.
 Optimized Antivirus Scanning. Low on Resources. Strong on Technology. Product Highlights Quick Heal» Easy installation, optimized antivirus scanning, and minimum resource utilization.» Robust and interoperable
Optimized Antivirus Scanning. Low on Resources. Strong on Technology. Product Highlights Quick Heal» Easy installation, optimized antivirus scanning, and minimum resource utilization.» Robust and interoperable
Quick Heal AntiVirus Pro. Tough on malware, light on your PC.
 Tough on malware, light on your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware tools. Signature based detection Detects
Tough on malware, light on your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware tools. Signature based detection Detects
Airtel PC Secure Trouble Shooting Guide
 Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Quick Heal Total Security for Mac. Simple, fast and seamless protection for Mac.
 Simple, fast and seamless protection for Mac. Product Highlights Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth email
Simple, fast and seamless protection for Mac. Product Highlights Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth email
McAfee Internet Security Suite Quick-Start Guide
 Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
Quick Heal Total Security for Mac. Simple, fast and seamless protection for Mac.
 Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth
Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth
Getting Started Guide. This document provides step-by-step instructions for installing Max Secure Anti-Virus and its prerequisite software.
 Getting Started Guide This document provides step-by-step instructions for installing Max Secure Anti-Virus and its prerequisite software. Contents 2 Contents Introduction... 3 System Requirements... 4
Getting Started Guide This document provides step-by-step instructions for installing Max Secure Anti-Virus and its prerequisite software. Contents 2 Contents Introduction... 3 System Requirements... 4
Quick Heal Total Security
 For secure online banking, smooth Internet surfing, and robust protection for your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware
For secure online banking, smooth Internet surfing, and robust protection for your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware
Zillya Internet Security User Guide
 Zillya Internet Security User Guide Content Download Zillya Internet Security... 4 Installation Zillya Internet Security... 4 System Status... 7 System Scanning... 9 When Zillya Internet Security finds
Zillya Internet Security User Guide Content Download Zillya Internet Security... 4 Installation Zillya Internet Security... 4 System Status... 7 System Scanning... 9 When Zillya Internet Security finds
How To Remove Virus From Computer Without Using Antivirus In Windows Xp
 How To Remove Virus From Computer Without Using Antivirus In Windows Xp How to remove a virus - how to clean PC and laptop of virus, spyware and other PC internet security software that includes up to
How To Remove Virus From Computer Without Using Antivirus In Windows Xp How to remove a virus - how to clean PC and laptop of virus, spyware and other PC internet security software that includes up to
ESET NOD32 ANTIVIRUS 8
 ESET NOD32 ANTIVIRUS 8 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
ESET NOD32 ANTIVIRUS 8 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
ESET NOD32 ANTIVIRUS 7
 ESET NOD32 ANTIVIRUS 7 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
ESET NOD32 ANTIVIRUS 7 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
Get Max Internet Security where to buy software for students ]
![Get Max Internet Security where to buy software for students ] Get Max Internet Security where to buy software for students ]](/thumbs/87/95239861.jpg) Get Max Internet Security where to buy software for students ] Description: Features of Max Secure Internet Security 2013 Exciting, Easy to understand GUI Easy, Quick installation Get immediate protection
Get Max Internet Security where to buy software for students ] Description: Features of Max Secure Internet Security 2013 Exciting, Easy to understand GUI Easy, Quick installation Get immediate protection
Anti-virus SCEP and Windows Defender. Common symptoms of an infection. How to Open SCEP or Windows Defender
 Anti-virus SCEP and Windows Defender The University of Aberdeen uses System Center Endpoint Protection software (SCEP) and Windows Defender to protect servers and networked Windows PCs against viruses,
Anti-virus SCEP and Windows Defender The University of Aberdeen uses System Center Endpoint Protection software (SCEP) and Windows Defender to protect servers and networked Windows PCs against viruses,
FAQ. Safe Anywhere PC 12. Disclaimer:
 FAQ Safe Anywhere PC 12 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch pad, F-Secure
FAQ Safe Anywhere PC 12 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch pad, F-Secure
User s Guide. SingNet Desktop Security Copyright 2010 F-Secure Corporation. All rights reserved.
 User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
SecureAPlus User Guide. Version 3.4
 SecureAPlus User Guide Version 3.4 September 2015 Copyright Information Information in this document is subject to change without notice. Companies, names and data used in examples herein are fictitious
SecureAPlus User Guide Version 3.4 September 2015 Copyright Information Information in this document is subject to change without notice. Companies, names and data used in examples herein are fictitious
Manually Remove Of Xp Internet Security Protect Virus Manually
 Manually Remove Of Xp Internet Security Protect Virus Manually We show you how to remove malware from a PC or laptop. You may also wish to read: Windows users: how to protect your PC from Check now: do
Manually Remove Of Xp Internet Security Protect Virus Manually We show you how to remove malware from a PC or laptop. You may also wish to read: Windows users: how to protect your PC from Check now: do
How To Remove A Virus Manually Windows 7 Without Antivirus Security Pro
 How To Remove A Virus Manually Windows 7 Without Antivirus Security Pro Security Defender is a fake antivirus program, it should not be trusted, since it is a The program usually installs on PCs without
How To Remove A Virus Manually Windows 7 Without Antivirus Security Pro Security Defender is a fake antivirus program, it should not be trusted, since it is a The program usually installs on PCs without
Activation Screen Virus
 How To Get Rid Of Spyware Windows Xp Activation Screen Virus Spyware Clear it's technically not a virus, but it does exhibit plenty of malicious To uninstall the Spyware Clear program from Windows XP,
How To Get Rid Of Spyware Windows Xp Activation Screen Virus Spyware Clear it's technically not a virus, but it does exhibit plenty of malicious To uninstall the Spyware Clear program from Windows XP,
Protegent Total Security Solution USER GUIDE Unistal Systems Pvt. Ltd. All rights Reserved Page 1
 Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
Security+ Guide to Network Security Fundamentals, Third Edition. Chapter 3 Protecting Systems
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 3 Protecting Systems Objectives Explain how to harden operating systems List ways to prevent attacks through a Web browser Define
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 3 Protecting Systems Objectives Explain how to harden operating systems List ways to prevent attacks through a Web browser Define
Comodo Antivirus Software Version 2.2
 Comodo Antivirus Software Version 2.2 User Guide Guide Version 2.2.082318 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Comodo Antivirus Software Version 2.2 User Guide Guide Version 2.2.082318 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
User Guide. Quick Heal Technologies Ltd.
 User Guide Quick Heal Total Security Quick Heal Total Shield Quick Heal Internet Security Quick Heal Internet Security Essentials Quick Heal AntiVirus Pro Advanced Quick Heal AntiVirus Pro Quick Heal AntiVirus
User Guide Quick Heal Total Security Quick Heal Total Shield Quick Heal Internet Security Quick Heal Internet Security Essentials Quick Heal AntiVirus Pro Advanced Quick Heal AntiVirus Pro Quick Heal AntiVirus
Cracked BitDefender Security for File Servers 2 Years 55 PCs pc repair software for free ]
![Cracked BitDefender Security for File Servers 2 Years 55 PCs pc repair software for free ] Cracked BitDefender Security for File Servers 2 Years 55 PCs pc repair software for free ]](/thumbs/95/125054845.jpg) Cracked BitDefender Security for File Servers 2 Years 55 PCs pc repair software for free ] Description: FILE SERVERS - THE BACKBONE OF THE NETWORK File servers are not just a network repository for the
Cracked BitDefender Security for File Servers 2 Years 55 PCs pc repair software for free ] Description: FILE SERVERS - THE BACKBONE OF THE NETWORK File servers are not just a network repository for the
ESET Mobile Security for Windows Mobile. Installation Manual and User Guide - Public Beta
 ESET Mobile Security for Windows Mobile Installation Manual and User Guide - Public Beta Contents...3 1. Installation of ESET Mobile Security 1.1 Minimum...3 system requirements 1.2 Installation...3 1.2.1
ESET Mobile Security for Windows Mobile Installation Manual and User Guide - Public Beta Contents...3 1. Installation of ESET Mobile Security 1.1 Minimum...3 system requirements 1.2 Installation...3 1.2.1
SEP for Windows: FAQ. Updating Security. Definitions (AV and IPS) it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu)
 Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > SEP for Windows: FAQ SEP for Windows: FAQ Cyndi Galvan
Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > SEP for Windows: FAQ SEP for Windows: FAQ Cyndi Galvan
Contents. Introduction 5. McAfee SecurityCenter 7. McAfee QuickClean 39. McAfee Shredder 45
 User Guide i Contents Introduction 5 McAfee SecurityCenter 7 Features... 8 Using SecurityCenter... 9 Header... 9 Left column... 9 Main pane... 10 Understanding SecurityCenter icons... 11 Understanding
User Guide i Contents Introduction 5 McAfee SecurityCenter 7 Features... 8 Using SecurityCenter... 9 Header... 9 Left column... 9 Main pane... 10 Understanding SecurityCenter icons... 11 Understanding
CERT-In. Indian Computer Emergency Response Team ANTI VIRUS POLICY & BEST PRACTICES
 CERT-In Indian Computer Emergency Response Team ANTI VIRUS POLICY & BEST PRACTICES Department of Information Technology Ministry of Communications and Information Technology Government of India Anti Virus
CERT-In Indian Computer Emergency Response Team ANTI VIRUS POLICY & BEST PRACTICES Department of Information Technology Ministry of Communications and Information Technology Government of India Anti Virus
Quick Start Guide. Microsoft Windows 7 / Vista / XP / 2000 / 2003 / 2008
 Quick Start Guide Microsoft Windows 7 / Vista / XP / 2000 / 2003 / 2008 ESET NOD32 Antivirus provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning
Quick Start Guide Microsoft Windows 7 / Vista / XP / 2000 / 2003 / 2008 ESET NOD32 Antivirus provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning
Key Features. DATA SHEET
 DATA SHEET Total Defense THREAT MANAGER r12 Overview: Total Defense Threat Manager r12 integrates anti-malware, groupware protection and network access control in one easy-touse solution, providing comprehensive
DATA SHEET Total Defense THREAT MANAGER r12 Overview: Total Defense Threat Manager r12 integrates anti-malware, groupware protection and network access control in one easy-touse solution, providing comprehensive
ESET ENDPOINT SECURITY
 ESET ENDPOINT SECURITY User Guide Microsoft Windows 8 / 7 / Vista / XP / 2000 / Home Server Click here to download the most recent version of this document ESET ENDPOINT SECURITY Copyright 2013 by ESET,
ESET ENDPOINT SECURITY User Guide Microsoft Windows 8 / 7 / Vista / XP / 2000 / Home Server Click here to download the most recent version of this document ESET ENDPOINT SECURITY Copyright 2013 by ESET,
Notification Center...65 Ignored Notifications...67 Language...69 Notifications and Balloons...70 Tray Application...71 How To...
 Table of Contents Product Information... 4 Ad-Aware Features... 4 System Requirements... 5 Copyright... 6 Installation and Uninstallation... 7 Ad-Aware Install... 7 Ad-Aware Uninstall...18 Ad-Aware Overview...22
Table of Contents Product Information... 4 Ad-Aware Features... 4 System Requirements... 5 Copyright... 6 Installation and Uninstallation... 7 Ad-Aware Install... 7 Ad-Aware Uninstall...18 Ad-Aware Overview...22
Quick Heal Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac.
 Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to
Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to
Avira Premium Security Suite User Manual
 Avira Premium Security Suite User Manual Trademarks and Copyright Trademarks AntiVir is a registered trademark of Avira GmbH. Windows is a registered trademark of the Microsoft Corporation in the United
Avira Premium Security Suite User Manual Trademarks and Copyright Trademarks AntiVir is a registered trademark of Avira GmbH. Windows is a registered trademark of the Microsoft Corporation in the United
QUICK START GUIDE. Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server Click here to download the most recent version of this document
 QUICK START GUIDE Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011 Click here to download the most recent version of this document ESET INTERNET SECURITY IS ALL-IN-ONE INTERNET SECURITY SOFTWARE.
QUICK START GUIDE Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011 Click here to download the most recent version of this document ESET INTERNET SECURITY IS ALL-IN-ONE INTERNET SECURITY SOFTWARE.
Guardian Total Security User Guide
 Guardian Total Security User Guide Guardian Total Security http://www.guardianav.co.in Copyright & License Information Copyright 2018 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication
Guardian Total Security User Guide Guardian Total Security http://www.guardianav.co.in Copyright & License Information Copyright 2018 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com)
 ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 1.0.0 Antivirus Site Protection (by SiteGuarding.com) 1.0.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE..
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 1.0.0 Antivirus Site Protection (by SiteGuarding.com) 1.0.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE..
QUICK START GUIDE. Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server Click here to download the most recent version of this document
 QUICK START GUIDE Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011 Click here to download the most recent version of this document ESET NOD32 ANTIVIRUS PROVIDES STATE-OF-THE-ART PROTECTION
QUICK START GUIDE Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011 Click here to download the most recent version of this document ESET NOD32 ANTIVIRUS PROVIDES STATE-OF-THE-ART PROTECTION
Comodo Antivirus Software Version 2.1
 Comodo Antivirus Software Version 2.1 User Guide Guide Version 2.1.030515 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Comodo Antivirus Software Version 2.1 User Guide Guide Version 2.1.030515 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Full file at
 Chapter 2 Solutions Answers to the Chapter 2 Review Questions 1. The Melissa virus was transported by. c. e-mail 2. Which of the following are used for updates in Windows XP Professional? (Choose all that
Chapter 2 Solutions Answers to the Chapter 2 Review Questions 1. The Melissa virus was transported by. c. e-mail 2. Which of the following are used for updates in Windows XP Professional? (Choose all that
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com)
 ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 0.1.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE.. 7 2 1. INTRODUCTION Antivirus Site Protection
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 0.1.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE.. 7 2 1. INTRODUCTION Antivirus Site Protection
Even a non-technical user can even operate it with ease.the user can do any task in CCS with just a few clicks.
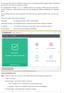 The Comodo Client Security identifies all security risks and provides protection against it.now, the interface of the Comodo Client Security is made very simple. It is integrated with Firewall, Antivirus,
The Comodo Client Security identifies all security risks and provides protection against it.now, the interface of the Comodo Client Security is made very simple. It is integrated with Firewall, Antivirus,
FOR macos. Quick Start Guide. Click here to download the most recent version of this document
 FOR macos Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against malicious code. Based
FOR macos Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against malicious code. Based
ESET CYBER SECURITY PRO for Mac
 ESET CYBER SECURITY PRO for Mac Installation Manual and User Guide Click here to download the most recent version of this document ESET CYBER SECURITY PRO Copyright 2012 by ESET, spol. s r.o. ESET Cyber
ESET CYBER SECURITY PRO for Mac Installation Manual and User Guide Click here to download the most recent version of this document ESET CYBER SECURITY PRO Copyright 2012 by ESET, spol. s r.o. ESET Cyber
How To Removing Personal Antivirus Security Pro From Windows 8
 How To Removing Personal Antivirus Security Pro From Windows 8 Antivirus Action, Antivirus Monitor, Antivirus 7 or Antivirus5, Antivirus 8, Antivirus 8 Fast Windows Antivirus 2011, Fix Clean Repair, Flu
How To Removing Personal Antivirus Security Pro From Windows 8 Antivirus Action, Antivirus Monitor, Antivirus 7 or Antivirus5, Antivirus 8, Antivirus 8 Fast Windows Antivirus 2011, Fix Clean Repair, Flu
EICAR institute (European Institute for Computer Antivirus Research) to test the functionality of antivirus programs.
 ESET Cybersecurity As the popularity of Unix-based operating systems increases, malware authors are developing more threats to target Mac users. ESET Cybersecurity offers powerful and efficient protection
ESET Cybersecurity As the popularity of Unix-based operating systems increases, malware authors are developing more threats to target Mac users. ESET Cybersecurity offers powerful and efficient protection
Small Office Security 2. Scan PC for viruses and vulnerabilities
 Small Office Security 2 Scan PC for viruses and vulnerabilities Table of content Table of content... 1 Scan PC for viruses... 2 What is Scan... 2 Starting scan... 2 Starting scan from the main application
Small Office Security 2 Scan PC for viruses and vulnerabilities Table of content Table of content... 1 Scan PC for viruses... 2 What is Scan... 2 Starting scan... 2 Starting scan from the main application
Avira Endpoint Security. HowTo
 Avira Endpoint Security HowTo Table of contents 1. Introduction... 3 2. Product Information... 3 2.1 Operation mode... 3 2.2 Scope of services... 3 2.3 Optimum protection. Fast updates. Efficient administration...4
Avira Endpoint Security HowTo Table of contents 1. Introduction... 3 2. Product Information... 3 2.1 Operation mode... 3 2.2 Scope of services... 3 2.3 Optimum protection. Fast updates. Efficient administration...4
Seqrite Endpoint Security
 Enterprise Security Solutions by Quick Heal Integrated enterprise security and unified endpoint management console Enterprise Suite Edition Product Highlights Innovative endpoint security that prevents
Enterprise Security Solutions by Quick Heal Integrated enterprise security and unified endpoint management console Enterprise Suite Edition Product Highlights Innovative endpoint security that prevents
Comodo Antivirus Software Version 2.0
 Comodo Antivirus Software Version 2.0 User Guide Guide Version 2.0.010215 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Comodo Antivirus Software Version 2.0 User Guide Guide Version 2.0.010215 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
ESET SMART SECURITY 10
 ESET SMART SECURITY 10 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista Quick Start Guide Click here to download the most recent version of this document ESET Smart Security is all-in-one Internet security software.
ESET SMART SECURITY 10 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista Quick Start Guide Click here to download the most recent version of this document ESET Smart Security is all-in-one Internet security software.
Unit 2 Assignment 2. Software Utilities?
 1 Unit 2 Assignment 2 Software Utilities? OBJECTIVES Identify software utility types and examples of common software Why are software utilities used? Identify and describe the various networking threats.
1 Unit 2 Assignment 2 Software Utilities? OBJECTIVES Identify software utility types and examples of common software Why are software utilities used? Identify and describe the various networking threats.
About Lavasoft. Contact. Key Facts:
 About Lavasoft Lavasoft is the original anti-malware company, creating award-winning, free security and privacy software since 1999. Born of the belief that online security should be available to everybody,
About Lavasoft Lavasoft is the original anti-malware company, creating award-winning, free security and privacy software since 1999. Born of the belief that online security should be available to everybody,
Kaseya 2. User Guide. Version 1.1
 Kaseya 2 Anti-Malware User Guide Version 1.1 July 11, 2011 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
Kaseya 2 Anti-Malware User Guide Version 1.1 July 11, 2011 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
Guardian Internet Security User Guide
 Guardian Internet Security User Guide Guardian Internet Security http://www.guardianav.co.in Copyright & License Information Copyright 2018 Quick Heal Technologies Ltd. All Rights Reserved. No part of
Guardian Internet Security User Guide Guardian Internet Security http://www.guardianav.co.in Copyright & License Information Copyright 2018 Quick Heal Technologies Ltd. All Rights Reserved. No part of
Prevx 3.0 v Product Overview - Core Functionality. April, includes overviews of. MyPrevx, Prevx 3.0 Enterprise,
 Prevx 3.0 v3.0.1.65 Product Overview - Core Functionality April, 2009 includes overviews of MyPrevx, Prevx 3.0 Enterprise, and Prevx 3.0 Banking and Ecommerce editions Copyright Prevx Limited 2007,2008,2009
Prevx 3.0 v3.0.1.65 Product Overview - Core Functionality April, 2009 includes overviews of MyPrevx, Prevx 3.0 Enterprise, and Prevx 3.0 Banking and Ecommerce editions Copyright Prevx Limited 2007,2008,2009
Computer Security. Solutions
 Computer Security Solutions What is the Problem? In general, the security issues we are trying to prevent include: illegal or unwanted access to your computer access to your personal information loss or
Computer Security Solutions What is the Problem? In general, the security issues we are trying to prevent include: illegal or unwanted access to your computer access to your personal information loss or
How To Remove Virus Without Antivirus In >>>CLICK HERE<<<
 How To Remove Virus Without Antivirus In Windows 7 Pdf Remove virus without antivirus, Here I have all necessary things and also I have steps to Few Effective Steps To Remove Virus Without Antivirus In
How To Remove Virus Without Antivirus In Windows 7 Pdf Remove virus without antivirus, Here I have all necessary things and also I have steps to Few Effective Steps To Remove Virus Without Antivirus In
Perform Manual System Restore Xp Safe Mode Command Prompt
 Perform Manual System Restore Xp Safe Mode Command Prompt Dell support article tagged with: System restore, windows, XP, WinXP, Safe Mode, Command Prompt. This is This article provides information on the
Perform Manual System Restore Xp Safe Mode Command Prompt Dell support article tagged with: System restore, windows, XP, WinXP, Safe Mode, Command Prompt. This is This article provides information on the
ANNOYING COMPUTER PROBLEMS
 ANNOYING COMPUTER PROBLEMS And their solution Before you do this to your computer read this information. Feel free to print it out. This will make it easier to reference. Table of Contents 1. Computer
ANNOYING COMPUTER PROBLEMS And their solution Before you do this to your computer read this information. Feel free to print it out. This will make it easier to reference. Table of Contents 1. Computer
AVG 8.5 Anti-Virus plus Firewall
 AVG 8.5 Anti-Virus plus Firewall User Manual Document revision 85.7 (8.9.2009) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective owners.
AVG 8.5 Anti-Virus plus Firewall User Manual Document revision 85.7 (8.9.2009) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective owners.
Kaspersky Security for Windows Server
 Kaspersky Security for Windows Server User's Guide Application version: 10.1.0.622 Dear User, Thank you for choosing Kaspersky Lab as your security software provider. We hope that this document helps you
Kaspersky Security for Windows Server User's Guide Application version: 10.1.0.622 Dear User, Thank you for choosing Kaspersky Lab as your security software provider. We hope that this document helps you
Comodo. Cloud Antivirus. User Guide. Software Version Guide Version
 Comodo Cloud Antivirus Software Version 1.14 User Guide Guide Version 1.14.111717 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Table of Contents 1. Introduction to Comodo
Comodo Cloud Antivirus Software Version 1.14 User Guide Guide Version 1.14.111717 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Table of Contents 1. Introduction to Comodo
Kaseya 2. User Guide. Version 2.1
 Kaseya 2 Endpoint Security User Guide Version 2.1 July 19, 2011 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations.
Kaseya 2 Endpoint Security User Guide Version 2.1 July 19, 2011 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations.
Table of Contents. User Guide
 Table of Contents Locate Laptop Laptop Tracking & Data Security 2 Feature: 2 Port Locker Stop Information & File Leaks 3 Feature 3 BitDefender Internet Security Secure Your Every Bit 3 Feature: 3 PROTEGENT
Table of Contents Locate Laptop Laptop Tracking & Data Security 2 Feature: 2 Port Locker Stop Information & File Leaks 3 Feature 3 BitDefender Internet Security Secure Your Every Bit 3 Feature: 3 PROTEGENT
User Guide. Version 2.1
 Kaseya Endpoint Security User Guide Version 2.1 February 23, 2010 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations.
Kaseya Endpoint Security User Guide Version 2.1 February 23, 2010 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations.
AVG 8.5 Internet Security
 AVG 8.5 Internet Security User Manual Document revision 85.7 (8.9.2009) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. This
AVG 8.5 Internet Security User Manual Document revision 85.7 (8.9.2009) Copyright AVG Technologies CZ, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. This
ESET NOD32 ANTIVIRUS 6
 ESET NOD32 ANTIVIRUS 6 User Guide (intended for product version 6.0 and higher) Microsoft Windows 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Click here to download the most recent version
ESET NOD32 ANTIVIRUS 6 User Guide (intended for product version 6.0 and higher) Microsoft Windows 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Click here to download the most recent version
Avira Free Mac Security Version HowTo
 Avira Free Mac Security Version 2.0.4 HowTo Table of contents 1. Introduction... 3 1.1 Features... 3 1.2 System Requirements...4 2. Installation...4 2.1 Installation with the install wizard...4 2.2 Installation
Avira Free Mac Security Version 2.0.4 HowTo Table of contents 1. Introduction... 3 1.1 Features... 3 1.2 System Requirements...4 2. Installation...4 2.1 Installation with the install wizard...4 2.2 Installation
Exam : Title : symantec small Business security. Version : DEMO
 Exam : 250-101 Title : symantec small Business security Version : DEMO 1. Which heuristic technology does Symantec AntiVirus use? A. Q-Factor B. Bloodhound C. pattern matching D. regular expression 2.
Exam : 250-101 Title : symantec small Business security Version : DEMO 1. Which heuristic technology does Symantec AntiVirus use? A. Q-Factor B. Bloodhound C. pattern matching D. regular expression 2.
How To Remove A Virus Manually Windows 7 Laptop Using Antivirus Program
 How To Remove A Virus Manually Windows 7 Laptop Using Antivirus Program How to find out if malware--a Trojan, virus, or worm got past your anti-virus and firewall, how to remove the malicious code manually.
How To Remove A Virus Manually Windows 7 Laptop Using Antivirus Program How to find out if malware--a Trojan, virus, or worm got past your anti-virus and firewall, how to remove the malicious code manually.
Antivirus: Proactively detects and disables more known and even unknown new malware threats than any other security product.
 Quick Start Guide ESET Cybersecurity provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning engine first introduced in the award-winning NOD32
Quick Start Guide ESET Cybersecurity provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning engine first introduced in the award-winning NOD32
User's Guide. Copyright 2012 Bitdefender
 User's Guide Copyright 2012 Bitdefender Bitdefender Antivirus Plus 2013 User's Guide Publication date 08/21/2012 Copyright 2012 Bitdefender Legal Notice All rights reserved. No part of this book may be
User's Guide Copyright 2012 Bitdefender Bitdefender Antivirus Plus 2013 User's Guide Publication date 08/21/2012 Copyright 2012 Bitdefender Legal Notice All rights reserved. No part of this book may be
F-Secure Client Security. Administrator's Guide
 F-Secure Client Security Administrator's Guide F-Secure Client Security TOC 2 Contents Chapter 1: Introduction...7 1.1 System requirements...8 1.1.1 Policy Manager Server...8 1.1.2 Policy Manager Console...8
F-Secure Client Security Administrator's Guide F-Secure Client Security TOC 2 Contents Chapter 1: Introduction...7 1.1 System requirements...8 1.1.1 Policy Manager Server...8 1.1.2 Policy Manager Console...8
Symantec Endpoint Protection
 The next generation of antivirus technology from Overview Advanced threat protection combines AntiVirus with advanced threat prevention to deliver an unmatched defense against malware for laptops, desktops,
The next generation of antivirus technology from Overview Advanced threat protection combines AntiVirus with advanced threat prevention to deliver an unmatched defense against malware for laptops, desktops,
Kaseya 2. User Guide. Version 7.0. English
 Kaseya 2 AntiMalware User Guide Version 7.0 English January 6, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as
Kaseya 2 AntiMalware User Guide Version 7.0 English January 6, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as
Guardian NetSecure User Guide
 Guardian NetSecure User Guide Guardian NetSecure http://www.guardianav.co.in Copyright & License Information Copyright 2017 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication
Guardian NetSecure User Guide Guardian NetSecure http://www.guardianav.co.in Copyright & License Information Copyright 2017 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication
AVG 9.0 File Server. User Manual. Document revision 90.4 ( )
 AVG 9.0 File Server User Manual Document revision 90.4 (8.1.2010) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. This product
AVG 9.0 File Server User Manual Document revision 90.4 (8.1.2010) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. This product
Typical Installation Guide. Installation Guide. Typical installation only. Standard version 2.5
 E s s e n t i a l S e c u r i t y a g a i n s t E v o l v i n g T h r e a t s Typical Installation Guide 2 Installation Guide Typical installation only Standard version 2.5 2 Copyright 1997 2005 Eset LLC.
E s s e n t i a l S e c u r i t y a g a i n s t E v o l v i n g T h r e a t s Typical Installation Guide 2 Installation Guide Typical installation only Standard version 2.5 2 Copyright 1997 2005 Eset LLC.
CDH Top 5. Free Recommended Cyber Security Tools. 1. Malwarebytes 2. CCleaner 3. Norton Safe Web 4. EaseUS Todo Backup 5.
 CDH Top 5 Free Recommended Cyber Security Tools www.cyberdefensehub.com 1. Malwarebytes 2. CCleaner 3. Norton Safe Web 4. EaseUS Todo Backup 5. Wireshark 1 Malwarebytes Malwarebytes is a free anti-malware
CDH Top 5 Free Recommended Cyber Security Tools www.cyberdefensehub.com 1. Malwarebytes 2. CCleaner 3. Norton Safe Web 4. EaseUS Todo Backup 5. Wireshark 1 Malwarebytes Malwarebytes is a free anti-malware
Comodo Internet Security Software Version 10.0
 Comodo Internet Security Software Version 10.0 Quick Start Guide Guide Version 10.0.102017 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Comodo Internet Security - Quick
Comodo Internet Security Software Version 10.0 Quick Start Guide Guide Version 10.0.102017 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Comodo Internet Security - Quick
Bitdefender Antivirus Plus 2016 User's Guide
 USER'S GUIDE Bitdefender Antivirus Plus 2016 User's Guide Publication date 09/05/2015 Copyright 2015 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted
USER'S GUIDE Bitdefender Antivirus Plus 2016 User's Guide Publication date 09/05/2015 Copyright 2015 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted
2008 CAMS-ii Users Conference
 2008 CAMS-ii Users Conference CAMS-ii and Technology The Good, The Bad, The Other Technology Topics LAN, WAN, WLAN, WWAN Firewalls Intrusion Detection Email Encryption Phishing Anti-Virus, Anti-Spyware
2008 CAMS-ii Users Conference CAMS-ii and Technology The Good, The Bad, The Other Technology Topics LAN, WAN, WLAN, WWAN Firewalls Intrusion Detection Email Encryption Phishing Anti-Virus, Anti-Spyware
User Guide. Version R95. English
 Anti-Malware (Classic) User Guide Version R95 English July 20, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept
Anti-Malware (Classic) User Guide Version R95 English July 20, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept
Manually Remove Of Xp Internet Security Protect
 Manually Remove Of Xp Internet Security Protect McAfee Family Protection McAfee Internet Security NOTE: To determine which McAfee Security software version you have installed, You must uninstall your McAfee
Manually Remove Of Xp Internet Security Protect McAfee Family Protection McAfee Internet Security NOTE: To determine which McAfee Security software version you have installed, You must uninstall your McAfee
Seqrite Antivirus Server Edition
 Seqrite Antivirus Server Edition User Guide www.seqrite.com Copyright & License Information Copyright 2017 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication may be reproduced,
Seqrite Antivirus Server Edition User Guide www.seqrite.com Copyright & License Information Copyright 2017 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication may be reproduced,
Single Product Review. escan Internet Security 11. Language: English September 2010 Last revision: 13 nd October
 Single Product Review escan Internet Security 11 Language: English September 2010 Last revision: 13 nd October 2010-1 - Content Downloading and installing the trial version... 3 Post-installation... 4
Single Product Review escan Internet Security 11 Language: English September 2010 Last revision: 13 nd October 2010-1 - Content Downloading and installing the trial version... 3 Post-installation... 4
Client Guide for Symantec Endpoint Protection and Symantec Network Access Control. For Microsoft Windows
 Client Guide for Symantec Endpoint Protection and Symantec Network Access Control For Microsoft Windows Client Guide for Symantec Endpoint Protection and Symantec Network Access Control The software described
Client Guide for Symantec Endpoint Protection and Symantec Network Access Control For Microsoft Windows Client Guide for Symantec Endpoint Protection and Symantec Network Access Control The software described
Comodo Internet Security Software Version 11.0
 Comodo Internet Security Software Version 11.0 Quick Start Guide Guide Version 11.0.113018 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Comodo Internet Security - Quick
Comodo Internet Security Software Version 11.0 Quick Start Guide Guide Version 11.0.113018 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Comodo Internet Security - Quick
User's Guide. Copyright 2013 Bitdefender
 User's Guide Copyright 2013 Bitdefender Bitdefender Antivirus Plus User's Guide Publication date 06/12/2013 Copyright 2013 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced
User's Guide Copyright 2013 Bitdefender Bitdefender Antivirus Plus User's Guide Publication date 06/12/2013 Copyright 2013 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced
User Manual for Imation Flash Login Software
 User Manual for Imation Flash Login Software Introducing Imation Flash Login You can use Imation Flash Login to create a password protected secure partition on Imation Swivel Pro USB 2.0 flash drive. System
User Manual for Imation Flash Login Software Introducing Imation Flash Login You can use Imation Flash Login to create a password protected secure partition on Imation Swivel Pro USB 2.0 flash drive. System
How To Remove Personal Antivirus Security Pro Virus Manually
 How To Remove Personal Antivirus Security Pro Virus Manually Uninstall Antivirus Pro 2017 Virus (Manual Removal Guide) This type of virus uses false scan results and fake security alerts to scare computer
How To Remove Personal Antivirus Security Pro Virus Manually Uninstall Antivirus Pro 2017 Virus (Manual Removal Guide) This type of virus uses false scan results and fake security alerts to scare computer
Comodo. Cloud Antivirus. User Guide. Software Version Guide Version
 Comodo Cloud Antivirus Software Version 1.11 User Guide Guide Version 1.11.050317 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Table of Contents 1. Introduction to Comodo
Comodo Cloud Antivirus Software Version 1.11 User Guide Guide Version 1.11.050317 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Table of Contents 1. Introduction to Comodo
ESET ENDPOINT ANTIVIRUS
 ESET ENDPOINT ANTIVIRUS User Guide Microsoft Windows 8 / 7 / Vista / XP / 2000 / Home Server / NT4 (SP6) Click here to download the most recent version of this document ESET ENDPOINT ANTIVIRUS Copyright
ESET ENDPOINT ANTIVIRUS User Guide Microsoft Windows 8 / 7 / Vista / XP / 2000 / Home Server / NT4 (SP6) Click here to download the most recent version of this document ESET ENDPOINT ANTIVIRUS Copyright
University of Tennessee at Chattanooga ARCS, Michael Ward, Basic Windows Security
 University of Tennessee at Chattanooga ARCS, Michael Ward, 2005-7-27 Basic Windows Security Nothing, besides turning off the power, can insure that your PC will be completely protected from hazards such
University of Tennessee at Chattanooga ARCS, Michael Ward, 2005-7-27 Basic Windows Security Nothing, besides turning off the power, can insure that your PC will be completely protected from hazards such
User Guide. Quick Heal Total Security Multi-Device. Quick Heal Technologies Ltd.
 User Guide Quick Heal Total Security Multi-Device Quick Heal Technologies Ltd. www.quickheal.com Copyright & License Information Copyright 2017 Quick Heal Technologies Ltd. All Rights Reserved. No part
User Guide Quick Heal Total Security Multi-Device Quick Heal Technologies Ltd. www.quickheal.com Copyright & License Information Copyright 2017 Quick Heal Technologies Ltd. All Rights Reserved. No part
