Advanced Threat Prevention Appliance
|
|
|
- Melanie Heath
- 5 years ago
- Views:
Transcription
1 Advanced Threat Prevention Appliance Overview Juniper Networks Advanced Threat Prevention Appliance is a distributed software platform that combines advanced threat detection, consolidated security analytics, and one-touch threat mitigation to protect organizations from cyber attacks and improve the productivity of security teams. The ATP Appliance detects threats across web, , and lateral traffic. Additionally, it can ingest logs from security devices and apply contextual analysis to present a consolidated view of all threats in the environment. Organizations worldwide face security and productivity challenges every day. Zero-day malware often goes undetected because traditional security devices, which rely on signaturebased detection, can t see it. Adding to the problem, security teams overwhelmed by large volumes of alerts often fail to recognize and act on critical incidents. The Juniper Networks Advanced Threat Prevention Appliance provides continuous, multistage detection and analysis of Web, , and lateral spread traffic moving through the network. It collects information from multiple attack vectors, using advanced machine learning and behavioral analysis technologies to identify advanced threats in as little as 15 seconds. Those threats are then combined with data collected from other security tools in the network, analyzed, and correlated, creating a consolidated timeline view of all malware events related to an infected host. Once threats are identified, one-touch policy updates are pushed to inline tools to protect against a recurrence of advanced attacks. The detection component of the ATP Appliance monitors network traffic to identify threats as they progress through the kill chain, detecting phishing, exploits, malware downloads, command and control communications, and internal threats. A multistage threat analysis process, which includes static, payload, machine learning, and behavior, as well as malware reputation analysis, continuously adapts to the changing threat landscape leveraging Juniper s Global Security Service, a cloud-based service that offers the latest threat detection and mitigation information produced by a team of security researchers, data scientists, and ethical hackers. The threat analytics component of the ATP Appliance offers a holistic view of identity and threat activity gathered from a diverse set of sources such as Active Directory, endpoint antivirus, firewalls, secure Web gateways, intrusion detection systems, and endpoint detection and response tools. The analytics component looks at data from these sources, identifies advanced malicious traits, and correlates the events to provide complete visibility into a threat s kill chain. Security analysts receive a comprehensive host and user timeline that depicts how the events that occurred on a host or user unfolded. The timeline enhances the productivity of Tier 1 and Tier 2 security analysts who work on triaging and investigating malware incidents. The ATP Appliance can integrate with other security devices to mitigate threats, giving users the ability to automatically quarantine s on Google and Office 365 using REST APIs. Communications between the infected endpoint and the command and control servers are blocked by pushing malicious IP addresses to firewall devices. Integration with network access control devices can isolate infected hosts. The ATP Appliance s open API architecture also allows it to integrate with a number of third-party security vendors such as Cisco, Palo Alto Networks, Fortinet, Bluecoat, Check Point, Carbon Black, and Bradford, among others. 1
2 Firewall Headquarters Internet Fabric SmartCore Web Lateral Detection Lateral Spread Fabric File Upload Figure 1: Juniper Networks ATP Appliance architecture Architecture and Key Components The architecture of the ATP Appliance consists of collectors deployed at critical points in the network, including remote locations. These collectors act like sensors, capturing information about Web, , and lateral traffic. Data and related executables collected across the fabric are delivered to the SmartCore analytics engine, which is fully integrated with the Juniper Networks SRX Series Services Gateways. When an SRX Series firewall is deployed as the collector, the solution can operate in an inline threat-prevention mode. Along with traffic from the native collectors, the ATP Appliance also ingests logs from other identity and security products such as Active Directory, endpoint antivirus, firewalls, secure Web gateways, intrusion detection systems, and endpoint detection and response tools. The logs can be ingested directly from third-party devices, or they can be forwarded from existing SIEM/syslog servers. Armed with data collected from various sources, the SmartCore analytics engine performs the following multistage threat analysis processes: Static analysis: Applies continuously updated rules and signatures to find known threats that may have eluded inline devices. Payload analysis: Leverages an intelligent sandbox array to gain a deeper understanding of malware behavior by detonating suspicious Web and file content that would otherwise target Windows, OSX, or Android endpoint devices. Machine learning and behavioral analysis: Employs patent-pending technologies to recognize the latest threat behaviors (such as multicomponent attacks over time) and quickly detect previously unknown threats. Malware reputation analysis: Compares analysis results with similar known threats to determine whether a newly detected threat is a variant of an existing issue or something completely new. Prioritization, risk analysis, correlation: Prioritizes threats based on threat severity, asset targets in the network, endpoint environment, and the threat s progression along the kill chain. For example, a high severity Windows malware landing on a Mac receives a lower risk score than a medium severity malware landing on a protected server. All malware events from the ATP Appliance and other security devices are correlated based on endpoint hostname and time and then plotted on a host timeline, allowing security teams to assess the risk of a threat and whether it requires immediate attention. For example, a threat detected by the ATP Appliance but missed by the antivirus solution receives a higher risk score. This allows security teams to go back in time and review all malicious events that have occurred on an infected host. Figure 2: ATP Appliance events timeline 2
3 Features and Benefits The ATP Appliance includes the following features and benefits: Inspects traffic across multiple vectors such as Web, , and lateral spread Uploads suspicious files through the Web UI for processing Supports Windows 7 and OSX operating systems Integrates fully with the SRX300, SRX4000, and SRX5000 lines, as well as the SRX550M and SRX1500; Junos 18.1 is the minimum supported release for SRX Series integration Operates in inline blocking mode when used with an SRX Series firewall in inline mode Analyzes multiple file types, including executables, DLL, Mach-o, Dmg, PDF, Office, Flash, ISO, ELF, RTF, APK, Silverlight, Archive, and JAR Includes detection techniques such as exploit detection, payload analysis, command and control (C&C) detection, YARA, and SNORT rules Provides comprehensive and well-documented APIs that allow easy integration with third-party security devices Integrates with Juniper Networks, Palo Alto Networks, Checkpoint, Cisco, Fortinet, and Bluecoat solutions to automatically block malicious IP addresses and URLs Automatically quarantines Office 365 and Gmail s Integrates with Carbon Black Protect and Response (endpoint solution) to allow upload of binaries executed on endpoints Allows clustering of multiple secondary cores via scalable architecture, increasing processing capacity Includes Manager of Central Managers (MCM) functionality to enable centralized, single-pane-of-glass management in large deployments requiring multiple cores Supports access and authentication using SAML and RADIUS Correlates events across kill chain stages to monitor threat progress and risk Visualizes malware activity and groups malware traits to help incident response teams better understand malware behavior Prioritizes threats based on risk calculated from threat severity, threat progress, asset value, and other contextual data Provides timeline host view to obtain complete context about malware events that have occurred on the host Options The ATP Appliance is available as both a physical and virtual appliance. Physical appliances can be deployed in all-in-one mode (SmartCore and Fabric are installed on the same physical appliance) or in distributed mode (SmartCore and Fabric are installed on separate appliances). appliances can be deployed in distributed mode only. Malware detection for MacOS is also supported. Customers will be required to provide Mac mini hardware that can be deployed as a secondary core. The MacOS sandboxing image is available on the JATP software downloads page. Physical All in One (Objects Detonated) Up to 61,000 objects/day 1 1 Gbps SmartCore (Objects Detonated) Up to 130,000 objects/ day 1 4 Gbps MTA Receiver Maximum s per Day 2 million Supported Hypervisor VMware vsphere ESXi SmartCore Versions 5.5, 6.0 (Objects Detonated) CPU Logging 1500 events/second Disk vsc-8 Up to 46,000 objects/day GB 1.5 TB vsc-24 Up to 116,000 objects/day GB 1.5 TB CPU Disk FC-v500M 500 Mbps 4 16 GB 512 GB FC-v1G 1 Gbps 8 32 GB 512 GB FC-v2.5G 2.5 Gbps GB 512 GB MTA Receiver Maximum s per Day of vcpu vmta-m 720, GB vmta-l 1.4 million GB vmta-xl 2.4 million GB 1 s based on a traffic mix that approximates real world performance. Actual numbers may be different based on traffic mix, repeat objects, and other factors unique to user environments. 3
4 Specifications Dimensions and Power Weight 42 lbs (19 kg) Dimensions (WxHxD) 17.2 x 3.5 x 24.8 in (43.7 x 8.9 x 63 cm) Form Factor 2 U (rack mountable) AC Power Supply 920 W high efficiency (94%+) AC-DC redundant power; AC Input: V, Hz, Amp DC Power Supply Fans 850 W/1010 W high-efficiency redundant DC-to-DC power supply; DC Input: 850 W; -35Vdc to -42Vdc, 30-25A 3x8 cm 7 K RPM, 4-pin PWM fans Environment Operating Temperature 50 to 104 F (10 to 40 C) Storage Temperature -40 to 158 F (-40 to 70 C) Relative Humidity (Operating) 8 to 90 percent noncondensing Relative Humidity (Storage) 5 to 95 percent noncondensing Altitude (Operating) 6,500 ft max Altitude (Storage) 35,000 ft max Compliance and Safety Safety Certifications CSA Safety of Information Technology Equipment UL EN IEC Emissions Certifications 47CFR Part 15, (FCC) Class A ICES-003 Class A EN Class A CISPR 22 Class A EN CISPR 24 VCCI Class A AS/NZA CISPR22 Class A KN22 Class A CNS13438 Class A EN EN NEBS No RoHS Yes Hardware Specifications CPU 2x10 cores 128 GB Storage 8x900 GB K SAS, RAID 6 Traffic Ports 2xSFP+ 10GbE 4x RJ-45 GbE Console Port 1xRJ-45 DB9 serial console Compliance and Safety Safety Certifications CAN/CSA-C22.2 No UL (2nd Edition) IEC : 2005/A2:2013 Emissions Certifications EN EN 55032/CISPR 32, Class A EN 55022/CISPR 22, Class A EN 55024/CISPR 24, Class A FCC 47 CFR Part 15, Class A ICES-003, Class A AS/NZS CISPR 32 VCCI-CISPR 32, Class A BSMI CNS KN32/KN35 EN EN EN
5 Ordering Information The Juniper ATP Appliance supports flexible deployment options. The components required vary based on the deployment model. Physical deployments require a physical JATP Appliance and an associated software subscription. deployments require a software subscription only The software subscription licenses are offered in two feature packages, summarized in the table below. Feature Package Standard(STD) Enterprise(ENT) Hardware -AC- CORE -AC-COL -AC-ALL -DC- CORE -DC-COL -DC-ALL Included Features North-South Web traffic, Auto Mitigation, Analytics, (BCC), manual upload All Standard features, Lateral traffic (SMB), (MTA) appliance, AC power, Core software installed appliance, AC power, appliance, AC power, All-in-One appliance, DC power, Core software installed appliance, DC power, Software Subscription Licenses appliance, DC power, All-in-One The subscription licenses are throughput/bandwidth-based. The supported throughput levels are 100 Mbps, 500 Mbps, 1 Gbps, 2 Gbps, 5 Gbps,and 10 Gbps. Note: Integration with SRX Series firewalls requires the AppSecure feature to be installed on the SRX Series device. A separate license may be required, depending on the platform model number. JATP-100M-STD-1 JATP-500M-STD-1 JATP-1G-STD-1 JATP-2G-STD-1 JATP-5G-STD-1 Threat feature package, up to 100 Mbps, 1 year term. Threat feature package, up to 500 Mbps, 1 year term. Threat feature package, up to 1 Gbps, 1 year term. Threat feature package, up to 2 Gbps, 1 year term. Threat feature package, up to 5 Gbps, 1 year term. JATP-10G-STD-1 JATP-100M-STD-3 JATP-500M-STD-3 JATP-1G-STD-3 JATP-2G-STD-3 JATP-5G-STD-3 JATP-10G-STD-3 JATP-100M-STD-5 JATP-500M- STD-5 JATP-1G-STD-5 JATP-2G-STD-5 JATP-5G-STD-5 JATP-10G-STD-5 JATP-100M-ENT-1 JATP-500M-ENT-1 JATP-1G-ENT-1 JATP-2G-ENT-1 Threat feature package, up to 10 Gbps, 1 year term. Threat feature package, up to 100 Mbps, 3 year term. Threat feature package, up to 500 Mbps, 3 year term. Threat feature package, up to 1 Gbps, 3 year term. Threat feature package, up to 2 Gbps, 3 year term. Threat feature package, up to 5 Gbps, 3 year term. Threat feature package, up to 10 Gbps, 3 year term. Threat feature package, up to 100 Mbps, 5 year term. Threat feature package, up to 500 Mbps, 5 year term. Threat feature package, up to 1 Gbps, 5 year term. Threat feature package, up to 2 Gbps, 5 year term. Threat feature package, up to 5 Gbps, 5 year term. Threat feature package, up to 10 Gbps, 5 year term. Enterprise feature package, up to 100 Mbps, 1 year term. Enterprise feature package, up to 500 Mbps, 1 year term. Enterprise feature package, up to 1 Gbps, 1 year term. Enterprise feature package, up to 2 Gbps, 1 year term. 5
6 JATP-5G-ENT-1 Enterprise feature package, up to 5 Gbps, 1 year term. JATP-100M-ENT-5 Enterprise feature package, up to 100 Mbps, 5 year term. JATP-10G-ENT-1 Enterprise feature package, up to 10 Gbps, 1 year term. JATP-500M-ENT-5 Enterprise feature package, up to 500 Mbps, 5 year term. JATP-100M-ENT-3 Enterprise feature package, up to 100 Mbps, 3 year term. JATP-1G-ENT-5 Enterprise feature package, up to 1 Gbps, 5 year term. JATP-500M-ENT-3 Enterprise feature package, up to 500 Mbps, 3 year term. JATP-2G-ENT-5 Enterprise feature package, up to 2 Gbps, 5 year term. JATP-1G-ENT-3 Enterprise feature package, up to 1 Gbps, 3 year term. JATP-5G-ENT-5 Enterprise feature package, up to 5 Gbps, 5 year term. JATP-2G-ENT-3 JATP-5G-ENT-3 JATP-10G-ENT-3 Enterprise feature package, up to 2 Gbps, 3 year term. Enterprise feature package, up to 5 Gbps, 3 year term. Enterprise feature package, up to 10 Gbps, 3 year term. JATP-10G-ENT-5 About Juniper Networks Enterprise feature package, up to 10 Gbps, 5 year term. Juniper Networks brings simplicity to networking with products, solutions and services that connect the world. Through engineering innovation, we remove the constraints and complexities of networking in the cloud era to solve the toughest challenges our customers and partners face daily. At Juniper Networks, we believe that the network is a resource for sharing knowledge and human advancement that changes the world. We are committed to imagining groundbreaking ways to deliver automated, scalable and secure networks to move at the speed of business. Corporate and Sales Headquarters Juniper Networks, Inc Innovation Way Sunnyvale, CA USA Phone: 888.JUNIPER ( ) or Fax: APAC and EMEA Headquarters Juniper Networks International B.V. Boeing Avenue PZ Schiphol-Rijk Amsterdam, The Netherlands Phone: Fax: EXPLORE JUNIPER Get the App. Copyright 2018 Juniper Networks, Inc. All rights reserved. Juniper Networks, the Juniper Networks logo, Juniper, and Junos are registered trademarks of Juniper Networks, Inc. in the United States and other countries. All other trademarks, service marks, registered marks, or registered service marks are the property of their respective owners. Juniper Networks assumes no responsibility for any inaccuracies in this document. Juniper Networks reserves the right to change, modify, transfer, or otherwise revise this publication without notice EN Mar 2018
Juniper Sky Advanced Threat Prevention
 Juniper Sky Advanced Threat Prevention Product Overview Juniper Sky Advanced Threat Prevention is a cloud-based service that provides complete advanced malware protection. Integrated with SRX Series Services
Juniper Sky Advanced Threat Prevention Product Overview Juniper Sky Advanced Threat Prevention is a cloud-based service that provides complete advanced malware protection. Integrated with SRX Series Services
JUNIPER SKY ADVANCED THREAT PREVENTION
 Data Sheet JUNIPER SKY ADVANCED THREAT PREVENTION Product Overview Juniper Sky Advanced Threat Prevention is a cloud-based service that provides complete advanced malware protection. Integrated with SRX
Data Sheet JUNIPER SKY ADVANCED THREAT PREVENTION Product Overview Juniper Sky Advanced Threat Prevention is a cloud-based service that provides complete advanced malware protection. Integrated with SRX
JSA Series Secure Analytics
 JSA Series Secure Analytics Product Overview The integrated approach of JSA Series Secure Analytics, used in conjunction with unparalleled data collection, analysis, correlation, and auditing capabilities,
JSA Series Secure Analytics Product Overview The integrated approach of JSA Series Secure Analytics, used in conjunction with unparalleled data collection, analysis, correlation, and auditing capabilities,
Software-Defined Secure Networks in Action
 Software-Defined Secure Networks in Action Enabling automated threat remediation without impacting business continuity Challenge Businesses need to continuously evolve to fight the increasingly sophisticated
Software-Defined Secure Networks in Action Enabling automated threat remediation without impacting business continuity Challenge Businesses need to continuously evolve to fight the increasingly sophisticated
Policy Enforcer. Product Description. Data Sheet. Product Overview
 Policy Enforcer Product Overview Juniper s Software-Defined Secure Network (SDSN) platform leverages the entire network, not just perimeter firewalls, as a threat detection and security enforcement domain.
Policy Enforcer Product Overview Juniper s Software-Defined Secure Network (SDSN) platform leverages the entire network, not just perimeter firewalls, as a threat detection and security enforcement domain.
JSA Series Secure Analytics
 JSA Series Secure Analytics Product Overview The integrated approach of JSA Series Secure Analytics, used in conjunction with unparalleled data collection, analysis, correlation, and auditing capabilities,
JSA Series Secure Analytics Product Overview The integrated approach of JSA Series Secure Analytics, used in conjunction with unparalleled data collection, analysis, correlation, and auditing capabilities,
Juniper Sky Enterprise
 Juniper Sky Enterprise Product Overview Network complexity is growing exponentially. Traffic levels continue to rise thanks to the proliferation of mobile and Internet of Things (IoT) devices being connected
Juniper Sky Enterprise Product Overview Network complexity is growing exponentially. Traffic levels continue to rise thanks to the proliferation of mobile and Internet of Things (IoT) devices being connected
JUNIPER NETWORKS PRODUCT BULLETIN
 PRODUCT BULLETIN JUNIPER NETWORKS PRODUCT BULLETIN Junos Pulse Mobile Security Suite 4.2 What s New for Enterprises and Service Providers Bulletin Date January 24, 2013 Bulletin Number 8000022 Applicable
PRODUCT BULLETIN JUNIPER NETWORKS PRODUCT BULLETIN Junos Pulse Mobile Security Suite 4.2 What s New for Enterprises and Service Providers Bulletin Date January 24, 2013 Bulletin Number 8000022 Applicable
PANORAMA. Figure 1: Panorama deployment
 PANORAMA Security deployments are complex and can overload IT teams with complex security rules and mountains of data from multiple sources. Panorama network security management empowers you with easy-to-implement,
PANORAMA Security deployments are complex and can overload IT teams with complex security rules and mountains of data from multiple sources. Panorama network security management empowers you with easy-to-implement,
McAfee Network Security Platform
 McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
McAfee Network Security Platform
 McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
Lastline Breach Detection Platform
 Lastline Breach Detection Platform Quickly and accurately detect, block and respond to active breaches in your network. Highlights Integrate with existing security systems through API to optimize IR workflows
Lastline Breach Detection Platform Quickly and accurately detect, block and respond to active breaches in your network. Highlights Integrate with existing security systems through API to optimize IR workflows
Cisco Stealthwatch Endpoint License
 Data Sheet Cisco Stealthwatch Endpoint License With the Cisco Stealthwatch Endpoint License you can conduct in-depth, context-rich investigations into endpoints that exhibit suspicious behavior. In our
Data Sheet Cisco Stealthwatch Endpoint License With the Cisco Stealthwatch Endpoint License you can conduct in-depth, context-rich investigations into endpoints that exhibit suspicious behavior. In our
ABSOLUTE REAL-TIME PROTECTION SERIES
 TM DATA SHEET ABSOLUTE REAL-TIME PROTECTION SERIES ADVANCED MALWARE BLOCKER WITH CYLANCE WITH ARTIFICIAL INTELLIGENCE OVERVIEW Enterprises globally are threatened by conventional as well as advanced zero-days,
TM DATA SHEET ABSOLUTE REAL-TIME PROTECTION SERIES ADVANCED MALWARE BLOCKER WITH CYLANCE WITH ARTIFICIAL INTELLIGENCE OVERVIEW Enterprises globally are threatened by conventional as well as advanced zero-days,
JUNOS SPACE ROUTE INSIGHT
 DATASHEET JUNOS SPACE ROUTE INSIGHT Product Overview Junos Space Route Insight is designed for network engineers and operators who manage today s complex, mission critical enterprise and service provider
DATASHEET JUNOS SPACE ROUTE INSIGHT Product Overview Junos Space Route Insight is designed for network engineers and operators who manage today s complex, mission critical enterprise and service provider
Cisco Firepower 9300 Security Appliance
 Data Sheet Cisco Firepower 9300 Security Appliance The Cisco Firepower 9300 is a scalable, carrier-grade platform designed for service providers and others requiring low latency and exceptional throughput,
Data Sheet Cisco Firepower 9300 Security Appliance The Cisco Firepower 9300 is a scalable, carrier-grade platform designed for service providers and others requiring low latency and exceptional throughput,
Extending Enterprise Security to Public and Hybrid Clouds
 Extending Enterprise Security to Public and Hybrid Clouds Juniper Security for an Ever-Evolving Market Challenge Enterprises are migrating toward public or hybrid clouds much faster than expected, creating
Extending Enterprise Security to Public and Hybrid Clouds Juniper Security for an Ever-Evolving Market Challenge Enterprises are migrating toward public or hybrid clouds much faster than expected, creating
PANORAMA. Key Security Features
 PANORAMA Security deployments are complex and can overload IT teams with complex security rules and mountains of data from multiple sources. Panorama network security management empowers you with easy-to-implement,
PANORAMA Security deployments are complex and can overload IT teams with complex security rules and mountains of data from multiple sources. Panorama network security management empowers you with easy-to-implement,
Operator s Guide. Modified: Copyright 2018, Juniper Networks, Inc.
 Operator s Guide Modified: 2018-06-29 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net Juniper Networks, the Juniper Networks logo, Juniper, and Junos
Operator s Guide Modified: 2018-06-29 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net Juniper Networks, the Juniper Networks logo, Juniper, and Junos
Symantec Advanced Threat Protection: Endpoint
 Symantec Advanced Threat Protection: Endpoint Data Sheet: Advanced Threat Protection The Problem Virtually all of today's advanced persistent threats leverage endpoint systems in order to infiltrate their
Symantec Advanced Threat Protection: Endpoint Data Sheet: Advanced Threat Protection The Problem Virtually all of today's advanced persistent threats leverage endpoint systems in order to infiltrate their
SECURITY FOR SMALL BUSINESSES
 SECURITY FOR SMALL BUSINESSES 2017 UNCOMPROMISING PERFORMANCE A common problem with firewalls used by small businesses has to do with hardware performance. Most often, vendor-stated bandwidth claims fall
SECURITY FOR SMALL BUSINESSES 2017 UNCOMPROMISING PERFORMANCE A common problem with firewalls used by small businesses has to do with hardware performance. Most often, vendor-stated bandwidth claims fall
Appliance Comparison Chart
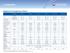 Appliance Comparison Chart Edge 0 70 570 070 070 070 Models Edge X, Edge W, Edge X ADSL, Edge W ADSL 6 7 76 57 576 07 076 07 076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65, R70 R65, R70
Appliance Comparison Chart Edge 0 70 570 070 070 070 Models Edge X, Edge W, Edge X ADSL, Edge W ADSL 6 7 76 57 576 07 076 07 076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65, R70 R65, R70
Cisco Advanced Malware Protection for Networks
 Data Sheet Cisco Advanced Malware Protection for Networks Product Overview Fighting malware effectively today requires new approaches, strategies, and technologies. Cisco Advanced Malware Protection (AMP)
Data Sheet Cisco Advanced Malware Protection for Networks Product Overview Fighting malware effectively today requires new approaches, strategies, and technologies. Cisco Advanced Malware Protection (AMP)
Cisco ASA with FirePOWER Services
 Data Sheet with FirePOWER Meet the industry s first adaptive, threat-focused next-generation firewall (NGFW) designed for a new era of threat and advanced malware protection. Cisco ASA with FirePOWER delivers
Data Sheet with FirePOWER Meet the industry s first adaptive, threat-focused next-generation firewall (NGFW) designed for a new era of threat and advanced malware protection. Cisco ASA with FirePOWER delivers
FIREFLY HOST. Product Description. Product Overview DATASHEET
 DATASHEET FIREFLY HOST Product Overview Juniper Networks Firefly Host is a comprehensive virtualization security solution that includes integrated stateful inspection firewalling, intrusion detection,
DATASHEET FIREFLY HOST Product Overview Juniper Networks Firefly Host is a comprehensive virtualization security solution that includes integrated stateful inspection firewalling, intrusion detection,
Cisco ACE30 Application Control Engine Module
 Data Sheet Cisco ACE30 Application Control Engine Module Product Overview The Cisco ACE30 Application Control Engine Module (Figure 1) belongs to the Cisco ACE family of application switches, which deliver
Data Sheet Cisco ACE30 Application Control Engine Module Product Overview The Cisco ACE30 Application Control Engine Module (Figure 1) belongs to the Cisco ACE family of application switches, which deliver
McAfee Network Security Platform 8.3
 8.3.7.44-8.3.7.14 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions Known
8.3.7.44-8.3.7.14 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions Known
Cisco ASA 5500 Series IPS Solution
 Cisco ASA 5500 Series IPS Product Overview As mobile devices and Web 2.0 applications proliferate, it becomes harder to secure corporate perimeters. Traditional firewall and intrusion prevention system
Cisco ASA 5500 Series IPS Product Overview As mobile devices and Web 2.0 applications proliferate, it becomes harder to secure corporate perimeters. Traditional firewall and intrusion prevention system
McAfee Advanced Threat Defense
 Advanced Threat Defense Detect advanced malware Advanced Threat Defense enables organizations to detect advanced, evasive malware and convert threat information into immediate action and protection. Unlike
Advanced Threat Defense Detect advanced malware Advanced Threat Defense enables organizations to detect advanced, evasive malware and convert threat information into immediate action and protection. Unlike
Cluster Upgrade. SRX Series Services Gateways for the Branch Upgrade Junos OS with Minimal Traffic Disruption and a Single Command APPLICATION NOTE
 APPLICATION NOTE Simple Chassis Cluster Upgrade SRX Series Services Gateways for the Branch Upgrade Junos OS with Minimal Traffic Disruption and a Single Command Copyright 2013, Juniper Networks, Inc.
APPLICATION NOTE Simple Chassis Cluster Upgrade SRX Series Services Gateways for the Branch Upgrade Junos OS with Minimal Traffic Disruption and a Single Command Copyright 2013, Juniper Networks, Inc.
Symantec Network Security 7100 Series
 Symantec Network Security 7100 Series Proactive intrusion prevention device protects against known and unknown attacks to secure critical networks transition can be accomplished transparent to any network
Symantec Network Security 7100 Series Proactive intrusion prevention device protects against known and unknown attacks to secure critical networks transition can be accomplished transparent to any network
Compare Security Analytics Solutions
 Compare Security Analytics Solutions Learn how Cisco Stealthwatch compares with other security analytics products. This solution scales easily, giving you visibility across the entire network. Stealthwatch
Compare Security Analytics Solutions Learn how Cisco Stealthwatch compares with other security analytics products. This solution scales easily, giving you visibility across the entire network. Stealthwatch
DELL EMC DATA DOMAIN DEDUPLICATION STORAGE SYSTEMS
 DELL EMC DATA DOMAIN DEDUPLICATION STORAGE SYSTEMS Dell EMC Data Domain deduplication storage systems continue to revolutionize disk backup, archiving, and disaster recovery with high-speed, inline deduplication.
DELL EMC DATA DOMAIN DEDUPLICATION STORAGE SYSTEMS Dell EMC Data Domain deduplication storage systems continue to revolutionize disk backup, archiving, and disaster recovery with high-speed, inline deduplication.
Cisco Secure Network Server
 Data Sheet Cisco Secure Network Server Product Overview Granting and denying network access has evolved beyond simple user name and password verifications. Today, additional attributes related to users
Data Sheet Cisco Secure Network Server Product Overview Granting and denying network access has evolved beyond simple user name and password verifications. Today, additional attributes related to users
Topology-Independent In-Service Software Upgrades on the QFX5100
 Topology-Independent In-Service Software Upgrades on the QFX5100 Juniper Innovation Brings ISSU to Data Center Top-of-Rack Switches 1 Table of Contents Executive Summary... 3 Introduction... 3 Leveraging
Topology-Independent In-Service Software Upgrades on the QFX5100 Juniper Innovation Brings ISSU to Data Center Top-of-Rack Switches 1 Table of Contents Executive Summary... 3 Introduction... 3 Leveraging
SDSN: Dynamic, Adaptive Multicloud Security
 SDSN: Dynamic, Adaptive Multicloud Security Evolving from firewall to user-intent for flexible in the cloud Challenge Legacy, which do not dynamically adapt to different workflows, must be individually
SDSN: Dynamic, Adaptive Multicloud Security Evolving from firewall to user-intent for flexible in the cloud Challenge Legacy, which do not dynamically adapt to different workflows, must be individually
TALK. agalaxy FOR THUNDER TPS REAL-TIME GLOBAL DDOS DEFENSE MANAGEMENT WITH A10 DATA SHEET DDOS DEFENSE MONITORING AND MANAGEMENT
 DATA SHEET agalaxy FOR THUNDER TPS DDOS DEFENSE MONITORING AND MANAGEMENT The A10 agalaxy management system is integrated with PLATFORMS the Thunder TPS (Threat Protection System) for DDoS protection.
DATA SHEET agalaxy FOR THUNDER TPS DDOS DEFENSE MONITORING AND MANAGEMENT The A10 agalaxy management system is integrated with PLATFORMS the Thunder TPS (Threat Protection System) for DDoS protection.
Juniper Solutions for Turnkey, Managed Cloud Services
 Juniper Solutions for Turnkey, Managed Cloud Services Three use cases for hosting and colocation service providers looking to deliver massively scalable, highly differentiated cloud services. Challenge
Juniper Solutions for Turnkey, Managed Cloud Services Three use cases for hosting and colocation service providers looking to deliver massively scalable, highly differentiated cloud services. Challenge
Symantec & Blue Coat Technical Update Webinar 29. Juni 2017
 Avantec Blue Coat/Symantec Webinar Jean Marc Edder Senior Systems Engineer The Global Leader in Cyber Network + + Cloud Global market leader in Endpoint, Email, Data Loss Prevention and Website, User Authentication
Avantec Blue Coat/Symantec Webinar Jean Marc Edder Senior Systems Engineer The Global Leader in Cyber Network + + Cloud Global market leader in Endpoint, Email, Data Loss Prevention and Website, User Authentication
Block, Detect and Analyze Threats with Automated, Advanced Threat Protection at the Gateway
 DATA SHEET S200/S400/S500 At a glance Multi-layered security for effective defense against known and unknown threats Uses a unique, multi-detection approach to quickly analyze suspicious files and URLs,
DATA SHEET S200/S400/S500 At a glance Multi-layered security for effective defense against known and unknown threats Uses a unique, multi-detection approach to quickly analyze suspicious files and URLs,
Cisco Secure Network Server
 Data Sheet Cisco Server Product Overview Granting and denying network access has evolved beyond simple user name and password verifications. Today, additional attributes related to users and their devices
Data Sheet Cisco Server Product Overview Granting and denying network access has evolved beyond simple user name and password verifications. Today, additional attributes related to users and their devices
Cisco Mobility Services Engine: An Open, Appliance-Based Platform for Delivering Mobility Services
 Data Sheet Cisco Mobility Services Engine: An Open, Appliance-Based Platform for Delivering Mobility Services Product Overview Ten billion mobile devices will populate our planet by 2016 1, and this proliferation
Data Sheet Cisco Mobility Services Engine: An Open, Appliance-Based Platform for Delivering Mobility Services Product Overview Ten billion mobile devices will populate our planet by 2016 1, and this proliferation
Cisco SR 520-T1 Secure Router
 Secure, High-Bandwidth Connectivity for Your Small Business Part of the Cisco Small Business Pro Series Connections -- between employees, customers, partners, and suppliers -- are essential to the success
Secure, High-Bandwidth Connectivity for Your Small Business Part of the Cisco Small Business Pro Series Connections -- between employees, customers, partners, and suppliers -- are essential to the success
McAfee Network Security Platform 9.1
 9.1.7.49-9.1.3.6 Manager-M-series, Mxx30-series, XC Cluster Release Notes McAfee Network Security Platform 9.1 Revision C Contents About the release New features Enhancements Resolved issues Installation
9.1.7.49-9.1.3.6 Manager-M-series, Mxx30-series, XC Cluster Release Notes McAfee Network Security Platform 9.1 Revision C Contents About the release New features Enhancements Resolved issues Installation
How Vectra Cognito enables the implementation of an adaptive security architecture
 Compliance brief How Vectra Cognito enables the implementation of an adaptive security architecture Historically, enterprises have relied on prevention and policy-based controls for security, deploying
Compliance brief How Vectra Cognito enables the implementation of an adaptive security architecture Historically, enterprises have relied on prevention and policy-based controls for security, deploying
Software-Define Secure Networks The Future of Network Security for Digital Learning
 Software-Define Secure Networks The Future of Network Security for Digital Learning SIGS, 5.Juli 2015 Klaus Ernst, Systems Engineer Juniper Networks Threat Landscape Feels like Treading Water 2017 IT Priorities
Software-Define Secure Networks The Future of Network Security for Digital Learning SIGS, 5.Juli 2015 Klaus Ernst, Systems Engineer Juniper Networks Threat Landscape Feels like Treading Water 2017 IT Priorities
Extending Enterprise Security to Public and Hybrid Clouds
 Extending Enterprise Security to Public and Hybrid Clouds Juniper Security for an Ever-Evolving Market Challenge Enterprises are increasingly migrating to public or hybrid deployments, creating an immediate
Extending Enterprise Security to Public and Hybrid Clouds Juniper Security for an Ever-Evolving Market Challenge Enterprises are increasingly migrating to public or hybrid deployments, creating an immediate
Contrail Networking: Evolve your cloud with Containers
 Contrail Networking: Evolve your cloud with Containers INSIDE Containers and Microservices Transformation of the Cloud Building a Network for Containers Juniper Networks Contrail Solution BUILD MORE THAN
Contrail Networking: Evolve your cloud with Containers INSIDE Containers and Microservices Transformation of the Cloud Building a Network for Containers Juniper Networks Contrail Solution BUILD MORE THAN
Enhanced Threat Detection, Investigation, and Response
 Enhanced Threat Detection, Investigation, and Response What s new in Cisco Stealthwatch Enterprise Release 6.10.2 Cisco Stealthwatch Enterprise is a comprehensive visibility and security analytics solution
Enhanced Threat Detection, Investigation, and Response What s new in Cisco Stealthwatch Enterprise Release 6.10.2 Cisco Stealthwatch Enterprise is a comprehensive visibility and security analytics solution
Product Description. Product Overview. Architecture and Key Components of the MAG Series Junos Pulse Gateways
 DATASHEET MAG Series Junos Pulse Gateways Product Overview The challenge for today s technology leader is to build an infrastructure that provides easy, secure access to the corporate network for all workers
DATASHEET MAG Series Junos Pulse Gateways Product Overview The challenge for today s technology leader is to build an infrastructure that provides easy, secure access to the corporate network for all workers
JUNIPER NETWORKS AND AEROHIVE NETWORKS: CLOUD- ENABLED SOLUTIONS FOR THE ENTERPRISE
 Solution Brief JUNIPER NETWORKS AND AEROHIVE NETWORKS: CLOUD- ENABLED SOLUTIONS FOR THE ENTERPRISE Cloud-managed wired and wireless solutions for today s multicloud enterprise Challenge Enterprises are
Solution Brief JUNIPER NETWORKS AND AEROHIVE NETWORKS: CLOUD- ENABLED SOLUTIONS FOR THE ENTERPRISE Cloud-managed wired and wireless solutions for today s multicloud enterprise Challenge Enterprises are
IPS-1 Robust and accurate intrusion prevention
 Security Check Point security solutions are the marketleading choice for securing the infrastructure. IPS-1 Robust and accurate intrusion prevention Today s s operate in an environment that is ever changing,
Security Check Point security solutions are the marketleading choice for securing the infrastructure. IPS-1 Robust and accurate intrusion prevention Today s s operate in an environment that is ever changing,
Agile Security Solutions
 Agile Security Solutions Piotr Linke Security Engineer CISSP CISA CRISC CISM Open Source SNORT 2 Consider these guys All were smart. All had security. All were seriously compromised. 3 The Industrialization
Agile Security Solutions Piotr Linke Security Engineer CISSP CISA CRISC CISM Open Source SNORT 2 Consider these guys All were smart. All had security. All were seriously compromised. 3 The Industrialization
Cisco Advanced Malware Protection for Networks
 Data Sheet Cisco Advanced Malware Protection for Networks Product Overview Fighting malware effectively today requires new approaches, strategies, and technologies. Cisco Advanced Malware Protection (AMP)
Data Sheet Cisco Advanced Malware Protection for Networks Product Overview Fighting malware effectively today requires new approaches, strategies, and technologies. Cisco Advanced Malware Protection (AMP)
Data Sheet Fujitsu ETERNUS DX500 S3 Disk Storage System
 Data Sheet Fujitsu ETERNUS DX500 S3 Disk Storage System Leading storage performance, automated quality of service ETERNUS DX - Business-centric Storage ETERNUS DX500 S3 Combining leading performance architecture
Data Sheet Fujitsu ETERNUS DX500 S3 Disk Storage System Leading storage performance, automated quality of service ETERNUS DX - Business-centric Storage ETERNUS DX500 S3 Combining leading performance architecture
SYMANTEC DATA CENTER SECURITY
 SYMANTEC DATA CENTER SECURITY SYMANTEC UNIFIED SECURITY STRATEGY Users Cyber Security Services Monitoring, Incident Response, Simulation, Adversary Threat Intelligence Data Threat Protection Information
SYMANTEC DATA CENTER SECURITY SYMANTEC UNIFIED SECURITY STRATEGY Users Cyber Security Services Monitoring, Incident Response, Simulation, Adversary Threat Intelligence Data Threat Protection Information
Cisco UCS C200 M2 High-Density Rack-Mount Server
 Cisco UCS C200 M2 High-Density Rack-Mount Server Product Overview Cisco UCS C-Series Rack-Mount Servers extend unified computing innovations to an industry-standard form factor to help reduce total cost
Cisco UCS C200 M2 High-Density Rack-Mount Server Product Overview Cisco UCS C-Series Rack-Mount Servers extend unified computing innovations to an industry-standard form factor to help reduce total cost
Cisco NAC Network Module for Integrated Services Routers
 Cisco NAC Network Module for Integrated Services Routers The Cisco NAC Network Module for Integrated Services Routers (NME-NAC-K9) brings the feature-rich Cisco NAC Appliance Server capabilities to Cisco
Cisco NAC Network Module for Integrated Services Routers The Cisco NAC Network Module for Integrated Services Routers (NME-NAC-K9) brings the feature-rich Cisco NAC Appliance Server capabilities to Cisco
DATA SHEET AlienVault USM Anywhere Powerful Threat Detection and Incident Response for All Your Critical Infrastructure
 DATA SHEET AlienVault USM Anywhere Powerful Threat Detection and Incident Response for All Your Critical Infrastructure AlienVault USM Anywhere accelerates and centralizes threat detection, incident response,
DATA SHEET AlienVault USM Anywhere Powerful Threat Detection and Incident Response for All Your Critical Infrastructure AlienVault USM Anywhere accelerates and centralizes threat detection, incident response,
Data Sheet Fujitsu ETERNUS DX200 S3 Disk Storage System
 Data Sheet Fujitsu ETERNUS DX200 S3 Disk Storage System The all-in-one storage system for SMBs or subsidiaries ETERNUS DX - Business-centric Storage ETERNUS DX200 S3 Combining leading performance architecture
Data Sheet Fujitsu ETERNUS DX200 S3 Disk Storage System The all-in-one storage system for SMBs or subsidiaries ETERNUS DX - Business-centric Storage ETERNUS DX200 S3 Combining leading performance architecture
Alcatel-Lucent OmniAccess Mobility Master
 Alcatel-Lucent OmniAccess Mobility Master Next generation master WLAN controller The Alcatel-Lucent OmniAccess Mobility Master is a next generation master controller that can be deployed as a virtual machine
Alcatel-Lucent OmniAccess Mobility Master Next generation master WLAN controller The Alcatel-Lucent OmniAccess Mobility Master is a next generation master controller that can be deployed as a virtual machine
Symantec Ransomware Protection
 Symantec Ransomware Protection Protection Against Ransomware Defense in depth across all control points is required to stop ransomware @ Email Symantec Email Security.cloud, Symantec Messaging Gateway
Symantec Ransomware Protection Protection Against Ransomware Defense in depth across all control points is required to stop ransomware @ Email Symantec Email Security.cloud, Symantec Messaging Gateway
Datasheet Fujitsu ETERNUS DX8700 S2 Disk Storage System
 Datasheet Fujitsu ETERNUS DX8700 S2 Disk Storage System The Flexible Data Safe for Dynamic Infrastructures. ETERNUS DX S2 DISK STORAGE SYSTEMS The Fujitsu second generation of ETERNUS DX disk storage systems,
Datasheet Fujitsu ETERNUS DX8700 S2 Disk Storage System The Flexible Data Safe for Dynamic Infrastructures. ETERNUS DX S2 DISK STORAGE SYSTEMS The Fujitsu second generation of ETERNUS DX disk storage systems,
Product Description. Product Overview DATASHEET
 DATASHEET VGW Gateway Product Overview Juniper Networks vgw Gateway is a comprehensive virtualization security solution that includes integrated stateful inspection firewalling, intrusion detection, compliance
DATASHEET VGW Gateway Product Overview Juniper Networks vgw Gateway is a comprehensive virtualization security solution that includes integrated stateful inspection firewalling, intrusion detection, compliance
Cisco UCS B230 M2 Blade Server
 Data Sheet Cisco UCS B230 M2 Blade Server Product Overview The Cisco UCS B230 M2 Blade Server is one of the industry s highest-density two-socket blade server platforms. It is a critical new building block
Data Sheet Cisco UCS B230 M2 Blade Server Product Overview The Cisco UCS B230 M2 Blade Server is one of the industry s highest-density two-socket blade server platforms. It is a critical new building block
Securing Your Amazon Web Services Virtual Networks
 Securing Your Amazon Web Services s IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up a workload,
Securing Your Amazon Web Services s IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up a workload,
DELL EMC DATA DOMAIN DEDUPLICATION STORAGE SYSTEMS
 SPEC SHEET DELL EMC DATA DOMAIN DEDUPLICATION STORAGE SYSTEMS Data Domain Systems Dell EMC Data Domain deduplication storage systems continue to revolutionize disk backup, archiving, and disaster recovery
SPEC SHEET DELL EMC DATA DOMAIN DEDUPLICATION STORAGE SYSTEMS Data Domain Systems Dell EMC Data Domain deduplication storage systems continue to revolutionize disk backup, archiving, and disaster recovery
The Cisco ASA 5500 Series Adaptive Security Appliances
 Cisco ASA 5500 Series Adaptive Security Appliances Cisco ASA 5500 Series Adaptive Security Appliances deliver a robust suite of highly integrated, marketleading security services for small and medium-sized
Cisco ASA 5500 Series Adaptive Security Appliances Cisco ASA 5500 Series Adaptive Security Appliances deliver a robust suite of highly integrated, marketleading security services for small and medium-sized
Data Sheet Fujitsu ETERNUS DX400 S2 Series Disk Storage Systems
 Data Sheet Fujitsu ETERNUS DX400 S2 Series Disk Storage Systems The Flexible Data Safe for Dynamic Infrastructures ETERNUS DX S2 Disk Storage Systems The second generation of ETERNUS DX disk storage systems
Data Sheet Fujitsu ETERNUS DX400 S2 Series Disk Storage Systems The Flexible Data Safe for Dynamic Infrastructures ETERNUS DX S2 Disk Storage Systems The second generation of ETERNUS DX disk storage systems
DELL EMC DATA DOMAIN DEDUPLICATION STORAGE SYSTEMS
 Data Domain Systems Table 1. DELL EMC DATA DOMAIN DEDUPLICATION STORAGE SYSTEMS Dell EMC Data Domain deduplication storage systems continue to revolutionize disk backup, archiving, and disaster recovery
Data Domain Systems Table 1. DELL EMC DATA DOMAIN DEDUPLICATION STORAGE SYSTEMS Dell EMC Data Domain deduplication storage systems continue to revolutionize disk backup, archiving, and disaster recovery
Juniper Networks and Aerohive Networks: Cloud-Enabled Solutions for the Enterprise
 Juniper Networks and Aerohive Networks: Cloud-Enabled Solutions for the Enterprise Cloud-managed wired and wireless solutions for today s multicloud enterprise Challenge Enterprises are increasingly challenged
Juniper Networks and Aerohive Networks: Cloud-Enabled Solutions for the Enterprise Cloud-managed wired and wireless solutions for today s multicloud enterprise Challenge Enterprises are increasingly challenged
SECURING THE NEXT GENERATION DATA CENTER. Leslie K. Lambert Juniper Networks VP & Chief Information Security Officer July 18, 2011
 SECURING THE NEXT GENERATION DATA CENTER Leslie K. Lambert Juniper Networks VP & Chief Information Security Officer July 18, 2011 JUNIPER SECURITY LEADERSHIP Market Leadership Data Center with High-End
SECURING THE NEXT GENERATION DATA CENTER Leslie K. Lambert Juniper Networks VP & Chief Information Security Officer July 18, 2011 JUNIPER SECURITY LEADERSHIP Market Leadership Data Center with High-End
Building a Software-Defined Secure Network for Healthcare
 Building a Software-Defined Secure Network for Healthcare Detect, adapt, and enforce security policies faster with network-wide visibility, orchestration, and control Challenge Enable digital transformation
Building a Software-Defined Secure Network for Healthcare Detect, adapt, and enforce security policies faster with network-wide visibility, orchestration, and control Challenge Enable digital transformation
Flex System FC port 16Gb FC Adapter Lenovo Press Product Guide
 Flex System FC5022 2-port 16Gb FC Adapter Lenovo Press Product Guide The network architecture on the Flex System platform has been specifically designed to address network challenges, giving you a very
Flex System FC5022 2-port 16Gb FC Adapter Lenovo Press Product Guide The network architecture on the Flex System platform has been specifically designed to address network challenges, giving you a very
CONFIGURING WEBAPP SECURE TO PROTECT AGAINST CREDENTIAL ATTACKS
 APPLICATION NOTE CONFIGURING WEBAPP SECURE TO PROTECT AGAINST CREDENTIAL ATTACKS Protect your Web Applications from Brute Force Credential Attacks Using WebApp Secure and Intrusion Deception Technology
APPLICATION NOTE CONFIGURING WEBAPP SECURE TO PROTECT AGAINST CREDENTIAL ATTACKS Protect your Web Applications from Brute Force Credential Attacks Using WebApp Secure and Intrusion Deception Technology
McAfee Network Security Platform 9.1
 9.1.7.15-9.1.3.3 Manager-NTBA Release Notes McAfee Network Security Platform 9.1 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions Known issues
9.1.7.15-9.1.3.3 Manager-NTBA Release Notes McAfee Network Security Platform 9.1 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions Known issues
Securing Your Microsoft Azure Virtual Networks
 Securing Your Microsoft Azure Virtual Networks IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up
Securing Your Microsoft Azure Virtual Networks IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up
Protecting Against Modern Attacks. Protection Against Modern Attack Vectors
 Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
Datasheet Fujitsu ETERNUS DX90 S2 Disk Storage System
 Datasheet Fujitsu ETERNUS DX90 S2 Disk Storage System The Flexible Data Safe for Dynamic Infrastructures. ETERNUS DX S2 DISK STORAGE SYSTEMS Fujitsu s second generation of ETERNUS DX disk storage systems,
Datasheet Fujitsu ETERNUS DX90 S2 Disk Storage System The Flexible Data Safe for Dynamic Infrastructures. ETERNUS DX S2 DISK STORAGE SYSTEMS Fujitsu s second generation of ETERNUS DX disk storage systems,
Delivers fast, accurate data about security threats:
 DATASHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Product Overview Delivers fast, accurate
DATASHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Product Overview Delivers fast, accurate
ATTIVO NETWORKS THREATDEFEND INTEGRATION WITH MCAFEE SOLUTIONS
 PARTNER BRIEF ATTIVO NETWORKS THREATDEFEND INTEGRATION WITH MCAFEE SOLUTIONS INTRODUCTION Attivo Networks has partnered with McAfee to detect real-time in-network threats and to automate incident response
PARTNER BRIEF ATTIVO NETWORKS THREATDEFEND INTEGRATION WITH MCAFEE SOLUTIONS INTRODUCTION Attivo Networks has partnered with McAfee to detect real-time in-network threats and to automate incident response
Extreme Management Center
 Data Sheet Highlights Deliver a Superior User Experience Mitigate performance issues quickly with data-driven insights into network and application performance across your wired and wireless network Monitor
Data Sheet Highlights Deliver a Superior User Experience Mitigate performance issues quickly with data-driven insights into network and application performance across your wired and wireless network Monitor
4 PWR XL: Catalyst 3524 PWR XL Stackable 10/100 Ethernet
 4 PWR XL: Catalyst 3524 PWR XL Stackable 10/100 Ethernet Table of Contents...1 Contents...1 Introduction...1 Ordering Information...1 Key Features/Benefits...2 Flexible and Scalable Switch Clustering Architecture...3
4 PWR XL: Catalyst 3524 PWR XL Stackable 10/100 Ethernet Table of Contents...1 Contents...1 Introduction...1 Ordering Information...1 Key Features/Benefits...2 Flexible and Scalable Switch Clustering Architecture...3
JSA Series Secure Analytics
 JSA Series Secure Analytics Product Overview The integrated approach of JSA Series Secure Analytics, used in conjunction with unparalleled data collection, analysis, correlation, and auditing capabilities,
JSA Series Secure Analytics Product Overview The integrated approach of JSA Series Secure Analytics, used in conjunction with unparalleled data collection, analysis, correlation, and auditing capabilities,
DELL EMC DATA DOMAIN DEDUPLICATION STORAGE SYSTEMS
 SPEC SHEET DELL EMC DATA DOMAIN DEDUPLICATION STORAGE SYSTEMS Data Domain Systems Dell EMC Data Domain deduplication storage systems continue to revolutionize disk backup, archiving, and disaster recovery
SPEC SHEET DELL EMC DATA DOMAIN DEDUPLICATION STORAGE SYSTEMS Data Domain Systems Dell EMC Data Domain deduplication storage systems continue to revolutionize disk backup, archiving, and disaster recovery
Data Sheet FUJITSU Storage ETERNUS DX60 S4 Disk Storage System
 Data Sheet FUJITSU Storage ETERNUS DX60 S4 Disk Storage System Data Sheet FUJITSU Storage ETERNUS DX60 S4 Disk Storage System The Economy Storage System for SMBs ETERNUS DX - Business-centric Storage FUJITSU
Data Sheet FUJITSU Storage ETERNUS DX60 S4 Disk Storage System Data Sheet FUJITSU Storage ETERNUS DX60 S4 Disk Storage System The Economy Storage System for SMBs ETERNUS DX - Business-centric Storage FUJITSU
Cisco UCS B460 M4 Blade Server
 Data Sheet Cisco UCS B460 M4 Blade Server Product Overview The new Cisco UCS B460 M4 Blade Server uses the power of the latest Intel Xeon processor E7 v3 product family to add new levels of performance
Data Sheet Cisco UCS B460 M4 Blade Server Product Overview The new Cisco UCS B460 M4 Blade Server uses the power of the latest Intel Xeon processor E7 v3 product family to add new levels of performance
JSA SERIES SECURE ANALYTICS
 DATASHEET JSA SERIES SECURE ANALYTICS Product Overview The integrated approach of JSA Series Secure Analytics, used in conjunction with unparalleled data collection, analysis, correlation, and auditing
DATASHEET JSA SERIES SECURE ANALYTICS Product Overview The integrated approach of JSA Series Secure Analytics, used in conjunction with unparalleled data collection, analysis, correlation, and auditing
Datasheet Fujitsu ETERNUS DX60 S2 Disk Storage System
 Datasheet Fujitsu ETERNUS DX60 S2 Disk Storage System The Economy Storage ETERNUS DX S2 DISK STORAGE SYSTEMS Fujitsu s second generation of ETERNUS DX disk storage systems, ETERNUS DX S2, are The Flexible
Datasheet Fujitsu ETERNUS DX60 S2 Disk Storage System The Economy Storage ETERNUS DX S2 DISK STORAGE SYSTEMS Fujitsu s second generation of ETERNUS DX disk storage systems, ETERNUS DX S2, are The Flexible
Data Sheet FUJITSU Storage ETERNUS DX60 S3 Disk Storage System
 Data Sheet FUJITSU Storage ETERNUS DX60 S3 Disk Storage System Data Sheet FUJITSU Storage ETERNUS DX60 S3 Disk Storage System The Economy Storage System for SMBs ETERNUS DX - Business-centric Storage Combining
Data Sheet FUJITSU Storage ETERNUS DX60 S3 Disk Storage System Data Sheet FUJITSU Storage ETERNUS DX60 S3 Disk Storage System The Economy Storage System for SMBs ETERNUS DX - Business-centric Storage Combining
ASA5525-FPWR-K9 Datasheet. Overview. Check its price: Click Here. Quick Specs
 ASA5525-FPWR-K9 Datasheet Check its price: Click Here Overview Cisco ASA with FirePOWER Services brings distinctive threat-focused next-generation security services to the Cisco ASA 5500-X Series Next-
ASA5525-FPWR-K9 Datasheet Check its price: Click Here Overview Cisco ASA with FirePOWER Services brings distinctive threat-focused next-generation security services to the Cisco ASA 5500-X Series Next-
Data Sheet: Endpoint Security Symantec Multi-tier Protection Trusted protection for endpoints and messaging environments
 Trusted protection for endpoints and messaging environments Overview creates a protected endpoint and messaging environment that is secure against today s complex data loss, malware, and spam threats controlling
Trusted protection for endpoints and messaging environments Overview creates a protected endpoint and messaging environment that is secure against today s complex data loss, malware, and spam threats controlling
Cisco UCS C24 M3 Server
 Data Sheet Cisco UCS C24 M3 Rack Server Product Overview The form-factor-agnostic Cisco Unified Computing System (Cisco UCS ) combines Cisco UCS C-Series Rack Servers and B-Series Blade Servers with networking
Data Sheet Cisco UCS C24 M3 Rack Server Product Overview The form-factor-agnostic Cisco Unified Computing System (Cisco UCS ) combines Cisco UCS C-Series Rack Servers and B-Series Blade Servers with networking
McAfee Network Security Platform 8.3
 8.3.7.28-8.3.3.9 Manager-Mxx30-series Release Notes McAfee Network Security Platform 8.3 Revision C Contents About this release New features Enhancements Resolved issues Installation instructions Known
8.3.7.28-8.3.3.9 Manager-Mxx30-series Release Notes McAfee Network Security Platform 8.3 Revision C Contents About this release New features Enhancements Resolved issues Installation instructions Known
Data Sheet FUJITSU ETERNUS DX60 S3 Disk Storage System
 Data Sheet FUJITSU ETERNUS DX60 S3 Disk Storage System Data Sheet FUJITSU ETERNUS DX60 S3 Disk Storage System The Economy Storage System for SMBs ETERNUS DX Storage Combining leading performance architecture
Data Sheet FUJITSU ETERNUS DX60 S3 Disk Storage System Data Sheet FUJITSU ETERNUS DX60 S3 Disk Storage System The Economy Storage System for SMBs ETERNUS DX Storage Combining leading performance architecture
Protection - Before, During And After Attack
 Advanced Malware Protection for FirePOWER TM BENEFITS Continuous detection of malware - immediately and retrospectively Inline detection of sophisticated malware that evades traditional network protections
Advanced Malware Protection for FirePOWER TM BENEFITS Continuous detection of malware - immediately and retrospectively Inline detection of sophisticated malware that evades traditional network protections
STRM SERIES SECURITY THREAT RESPONSE MANAGERS
 DATASHEET STRM SERIES SECURITY THREAT RESPONSE MANAGERS Product Overview The integrated approach of the STRM Series used in conjunction with unparalleled data collection, analysis, correlation and auditing
DATASHEET STRM SERIES SECURITY THREAT RESPONSE MANAGERS Product Overview The integrated approach of the STRM Series used in conjunction with unparalleled data collection, analysis, correlation and auditing
Securing the Software-Defined Data Center
 Securing the Software-Defined Data Center The future of the data center is software defined Key Advantages McAfee Network Platform 8.4 Delivers best-in-class IPS security across physical and softwaredefined
Securing the Software-Defined Data Center The future of the data center is software defined Key Advantages McAfee Network Platform 8.4 Delivers best-in-class IPS security across physical and softwaredefined
MAKING THE CLOUD A SECURE EXTENSION OF YOUR DATACENTER
 MAKING THE CLOUD A SECURE EXTENSION OF YOUR DATACENTER Bret Hartman Cisco / Security & Government Group Session ID: SPO1-W25 Session Classification: General Interest 1 Mobility Cloud Threat Customer centric
MAKING THE CLOUD A SECURE EXTENSION OF YOUR DATACENTER Bret Hartman Cisco / Security & Government Group Session ID: SPO1-W25 Session Classification: General Interest 1 Mobility Cloud Threat Customer centric
Seceon s Open Threat Management software
 Seceon s Open Threat Management software Seceon s Open Threat Management software (OTM), is a cyber-security advanced threat management platform that visualizes, detects, and eliminates threats in real
Seceon s Open Threat Management software Seceon s Open Threat Management software (OTM), is a cyber-security advanced threat management platform that visualizes, detects, and eliminates threats in real
