int32_t Buffer[BUFFSZ] = {-1, -1, -1, 1, -1, 1, 2, 4, 8, 16, 32, 64, 128, 256, 512, -1, -1, -1, -1, -1}; int32_t* A = &Buffer[5];
|
|
|
- Jeffrey Haynes
- 6 years ago
- Views:
Transcription
1 This assignment refers to concepts discussed in the course notes on gdb and the book The Art of Debugging by Matloff & Salzman. The questions are definitely "hands-on" and will require some reading beyond the course notes. Download the file HW09.tar and unpack it on a Linux system. It contains files you will need for this assignment. You may work in pairs for this assignment. If you choose to work with a partner, make sure only one of you submits a solution and that the file lists names and PIDs for both of you. Prepare your answers to the following questions in a single plain ASCII text file. Submit your file to the Curator system by the posted deadline for this assignment. No late submissions will be accepted. You will submit your answers to the Curator System ( under the heading HW A student is testing an implementation of the following C function: /** * Computes and returns sum of A[0]:A{Sz-1]. * Pre: * A points to an array of dimension at least Sz * A[0:Sz-1] are initialized * Returns: * sum of A[0] through A[Sz-1] */ int32_t AddEm(const int32_t* const A, uint32_t Sz); Unfortunately, the student is not going to show you the C source code for the implementation; instead, she has written a driver and compiled it with AddEm.c with the following command: gcc -c -O0 -m32 -std=c99 Wall W -g Q1main.c AddEm.c As you can see, the code is compiled to 32-bit instructions, with no optimizations, and with debugging information added (since the build did include the switch g). So, the student can use gdb to analyze the execution of the function; here's the driver she wrote: #define BUFFSZ 20 #define LISTSZ 10 int main() { int32_t Buffer[BUFFSZ] = {-1, -1, -1, 1, -1, 1, 2, 4, 8, 16, 32, 64, 128, 256, 512, -1, -1, -1, -1, -1}; int32_t* A = &Buffer[5]; int32_t Sum = AddEm(A, LISTSZ); printf("sum is %"PRId32"\n", Sum); } return 0; Here's my driver code. I created a buffer with extra space around the array I passed to the function, and set known values into the extra space. Note that AddEm() should have returned the sum But, I ran it and it returned ! 1
2 A short session with gdb verifies a few facts; the student has made notes of some observations: [jillhokie@vmcentos65 Q1]$ gdb Q1... (gdb) break AddEm.c:17 Breakpoint 1 at 0x80483e3: file AddEm.c, line 17. (gdb) run Let's run to the breakpoint in AddEm(). Starting program: /home/jillhokie/2505/addem Breakpoint 1, There is a loop in AddEm() that is supposed to compute the sum; the loop test is on line 17, so I m setting a breakpoint there. (gdb) print/x A $1 = 0xffffd1cc (gdb) print/x Curr $2 = 0xffffd1cc (gdb) print *(int32_t*) Curr $3 = 1 (gdb) print/x Stop $4 = 0xffffd1f4 (a) Let's check the parameters: So the array A is at address 0xffffd1cc. Curr is pointing to A[0], so that's OK> *Curr is 1, which is correct too. What about Stop? (gdb) print (uint32_t) Stop - (uint32_t) Curr $5 = 40 (b) Is that right? Maybe the UB for the loop is wrong... (gdb) next 18 Sum += *(int32_t*) Curr; (gdb) print Sum $6 = 0 OK, Sum has been initialized to 0; remember the code in line 18 (gdb) next 19 Curr++; (gdb) print Sum $7 = 1 Well, Sum has been updated correctly. (gdb) next (gdb) print/x Curr $8 = 0xffffd1cd (c) Is that right? (gdb) print *(int32_t*) Curr $9 = (gdb) print/x *(int32_t*) Curr $10 = 0x Well, that's NOT the next value in my array! Let's see that in hex... does that tell us anything? 2
3 (gdb) disassem Dump of assembler code for function AddEm: 0x080483c4 <+0>: push %ebp 0x080483c5 <+1>: mov %esp,%ebp 0x080483c7 <+3>: sub $0x10,%esp 0x080483ca <+6>: movl $0x0,-0xc(%ebp) 0x080483d1 <+13>: mov 0x8(%ebp),%eax 0x080483d4 <+16>: mov %eax,-0x8(%ebp) 0x080483d7 <+19>: mov 0xc(%ebp),%eax 0x080483da <+22>: shl $0x2,%eax 0x080483dd <+25>: add -0x8(%ebp),%eax 0x080483e0 <+28>: mov %eax,-0x4(%ebp) 0x080483e3 <+31>: jmp 0x80483f1 <AddEm+45> => 0x080483e5 <+33>: mov -0x8(%ebp),%eax 0x080483e8 <+36>: mov (%eax),%eax 0x080483ea <+38>: add %eax,-0xc(%ebp) 0x080483ed <+41>: addl $0x1,-0x8(%ebp) 0x080483f1 <+45>: mov -0x8(%ebp),%eax 0x080483f4 <+48>: cmp -0x4(%ebp),%eax 0x080483f7 <+51>: jb 0x80483e5 <AddEm+33> 0x080483f9 <+53>: mov -0xc(%ebp),%eax 0x080483fc <+56>: leave 0x080483fd <+57>: ret End of assembler dump. The addresses are shown relative to the beginning of the function. Remember that the function name, AddEm, becomes a label representing an address in the assembly code. The expression <+45> in the disassembly above means the instruction is at an address 45 bytes after the beginning of the function. Let's figure out where things are in the stack frame for AddEm(): Let's look at the assembly code for AddEm(). There's a loop test at <+45/51>, and it jumps to <+33>. Aha! Now I see what's going on... look at <+41>! Let me explain (gdb) p/x $ebp $20 = 0xffffd198 That's the address where the frame for AddEm() begins. (gdb) p/x &Sum $21 = 0xffffd18c (gdb) p/x &Curr $22 = 0xffffd190 (gdb) p/x &Stop $23 = 0xffffd194 (d)... and the address of Sum; that's %ebp and the address of Curr; that's %ebp and the address of Stop; that's %ebp - 4 Just for fun, here are the details of the current stack: (gdb) where full #0 AddEm (A=0xffffd1cc, Sz=10) at AddEm.c:18 Sum = Curr = 0xffffd1ce Stop = 0xffffd1f4... #1 0x in main () at Q1main.c:14 Buffer = {-1, -1, -1, 1, -1, 1, 2, 4, 8, 16, 32, 64, 128, 256, 512, -1, -1, -1, -1, -1} A = 0xffffd1cc Sum =
4 OK, enough fun with the stack... now that we know where things are, we can try reconstructing the code: 0x080483c4 <+0>: push %ebp # set up a frame 0x080483c5 <+1>: mov %esp,%ebp 0x080483c7 <+3>: sub $0x10,%esp 0x080483ca <+6>: movl $0x0,-0xc(%ebp) # Sum = 0 0x080483d1 <+13>: mov 0x8(%ebp),%eax # eax = A 0x080483d4 <+16>: mov %eax,-0x8(%ebp) # Curr = A 0x080483d7 <+19>: mov 0xc(%ebp),%eax # eax = Size 0x080483da <+22>: shl $0x2,%eax # eax = 4 * Size 0x080483dd <+25>: add -0x8(%ebp),%eax # eax = A + 4 * Size 0x080483e0 <+28>: mov %eax,-0x4(%ebp) # Stop = A + 4 * Size 0x080483e3 <+31>: jmp 0x80483f1 <AddEm+45> # goto <+45> 0x080483e5 <+33>: mov -0x8(%ebp),%eax # eax = Curr 0x080483e8 <+36>: mov (%eax),%eax # eax = *Curr 0x080483ea <+38>: add %eax,-0xc(%ebp) # Sum += *Curr 0x080483ed <+41>: addl $0x1,-0x8(%ebp) # Curr++ => 0x080483f1 <+45>: mov -0x8(%ebp),%eax # eax = Curr 0x080483f4 <+48>: cmp -0x4(%ebp),%eax # compare Curr to Stop 0x080483f7 <+51>: jb 0x80483e5 <AddEm+33> # repeat loop if less 0x080483f9 <+53>: mov -0xc(%ebp),%eax # return value is Sum 0x080483fc <+56>: leave # exit function 0x080483fd <+57>: ret We are currently at the instruction marked =>, just after the increment of Curr. Let's step through the machine code for a bit:... 0x080483f4 0x080483f7 18 Sum += *(int32_t*) Curr; (gdb) p/x Curr $18 = 0xffffd1ce 0x080483e8 18 0x080483ea 18 Sum += *(int32_t*) Curr; Sum += *(int32_t*) Curr; 19 Curr++; (gdb) p/x Curr $19 = 0xffffd1cf Again, Curr is behaving strangely... OK, that's not very revealing, but it does show how to step through machine code. Let's restart the program and see what's really going on with Curr. 4
5 (gdb) run The program being debugged has been started already. Start it from the beginning? (y or n) y Starting program: /home/jillhokie/2505/addem Breakpoint 3, We can display the contents of a block of memory; let's see what A looks like: (gdb) x/10w A 0xffffd1cc: 0x x x x xffffd1dc: 0x x x x xffffd1ec: 0x x (gdb) p/x Curr $21 = 0xffffd1cc 0xffffd1cc: 0x (gdb) delete 3 (gdb) watch Curr And check Curr and its target; that all looks OK to start with. Let's remove the breakpoint. I'm interested in what Curr is doing, not in the loop. And set a watchpoint on Curr... then continue execution... Old value = (const uint8_t *) 0xffffd1cc "\001" New value = (const uint8_t *) 0xffffd1cd "" Watchpoints cause a pause when the value of the watched expression changes. 0xffffd1cd: 0x Now, the value of *Curr is odd... compare this to the display of A above. Old value = (const uint8_t *) 0xffffd1cd "" New value = (const uint8_t *) 0xffffd1ce "" 0xffffd1ce: 0x Old value = (const uint8_t *) 0xffffd1ce "" New value = (const uint8_t *) 0xffffd1cf "" 5
6 0xffffd1cf: 0x Old value = (const uint8_t *) 0xffffd1cf "" New value = (const uint8_t *) 0xffffd1d0 "\002" 0xffffd1d0: 0x Old value = (const uint8_t *) 0xffffd1d0 "\002" New value = (const uint8_t *) 0xffffd1d1 "" 0xffffd1d1: 0x (e) Now, do you see what Curr is doing? OK, what about setting breakpoints in machine code? There are no line numbers, like in C code. But machine instructions are stored at addresses (which are shown in the disassembly). Can I set a breakpoint at an address in code? Where should I set the breakpoint? Let's set one at the beginning of the loop body. That instruction is at address 0x080483e5. I bet that if I dereference that address, gdb will interpret that and set a breakpoint at that instruction... (gdb) delete 4 (gdb) break *0x080483e5 Breakpoint 5 at 0x80483e5: file AddEm.c, line 18. (f) Yes! Now I can issue a continue and the program should run until it reaches the beginning of the loop again. OK, that's enough for now... I know what's wrong with the C code. (Actually, I've known for some time.) Do you? Let's see if you can answer some questions about the program and the debug session... look for the highlighted labels like this in the gdb session: (y) You may find it useful to look around in the gdb session for clues, not just near the labels. 6
7 a) [5 points] Given what you see about the loop test a few lines further down, does the value for Stop make sense? Explain. b) [5 points] Does the difference between Stop and Curr make sense? Why? c) [5 points] Is the value of Curr shown here what it should be? Explain. d) [5 points] Why does this tell us that Sum is stored at the address %ebp 12? e) [5 points] Explain the results of these displays of *Curr, taking into account the values displayed for A. That is, given what we know about Curr and A, why do these values make sense (even though they are not what we wanted)? f) [5 points] Now that you see how Curr is being modified (especially the assembly code instruction we saw earlier), explain what could be in the C code that would make gcc translate the update of Curr to this assembly code. 7
8 2. Another student is testing an implementation of the following C function: /** * Fills array A of dimension Sz with integer squares. * Pre: * A points to an array of dimension Sz (or larger) * Post: * A[k] = (k + 1)^2, for k = 0:Sz-1 */ void WriteSquares(int* const A, int Sz); This time, the student only has an object file for the function implementation. However, in this case it appears that the implementation does what is required. However, the student suspects his testing may be missing an array-bounds error within the implementation of WriteSquares(). So, the student writes some clever code to see if his hunch about the implementation is correct: The cleverness in this code is that the student has guaranteed that there is a known value (a canary value) just before the first element of the array, and just after the last element of the array. If the implementation of WriteSquares() does violate the array bounds, we should see a change in one or both of the canary values after WriteSquares() returns. #include <stdlib.h> #define CANARY 0XDEADBEEF #include "WriteSquares.h" int main() { DEADBEEF DEADBEEF int Sz = 100; int* MemoryBlock = malloc(sz * sizeof(int) + 16); if ( MemoryBlock == NULL ) return 1; *MemoryBlock = CANARY; *(MemoryBlock + 1) = CANARY; *(MemoryBlock + Sz + 2) = CANARY; *(MemoryBlock + Sz + 3) = CANARY; int* A = MemoryBlock + 2; DEADBEEF DEADBEEF // We suspect this function may contain a bug (or two), // and it may write outside the proper boundaries of the // array A of dimension Sz: WriteSquares(A, Sz); free(memoryblock); return 0; a) [10 points] Use gdb to examine the results of the call to WriteSquares(). You should determine what memory values are set correctly, and which are set incorrectly or modified when they should not be. Hint: setting an appropriate watchpoint in gdb can yield a very fast resolution of the question. b) [10 points] Use gdb or objdump to analyze what's wrong with the implementation of WriteSquares(). Note this is not the same as the previous question; that was concerned with effects, not causes. You must show your gdb session, or your output from objdump and reverse-engineering to support your conclusion. 8
9 3. The directory Q3 (created when you unpacked the tar file referred to above) contains three files: Q3main.c, Q3.h and Q3.o. The object file contains the compiled code for the function Q3() declared in the header file. Q3main.c contains a main() function designed to call Q3(); read the comments in Q3main.c. Experiment a bit with the code; you will discover that running Q3main results in a runtime error, unless you get very lucky and use a parameter to Q3() that satisfies a particular constraint. You must determine what constraint the parameter to Q3() must satisfy in order to avoid the runtime error. Brute force attacks can answer the question and will receive no credit. There are several ways to analyze this situation, and you have a number of tools available to aid you. You can use gdb to examine the execution of the code. You can also use objdump,with the d switch, to display the assembly code for an object or executable file. You must state the constraint the parameter to Q3() must satisfy and show what rational analysis you performed to determine the constraint. You can justify your conclusion by showing a transcript of a gdb session and/or showing objdump output with an analysis of the x86 assembly code. (It's easy to copy text from a Linux shell window and paste it into a text editor.) a) [5 points] Identify the exact assembly/machine instruction within Q3() at which the runtime error occurs. Either list the instruction, or give its address. Show exactly how you determined your answer. b) [10 points] Analyze the instruction you identified in part a), and explain exactly why executing this instruction would cause a runtime error. c) [10 points] For what parameter value(s) will Q3() not trigger a segmentation fault? Show exactly how you determined your answer(s) to this question; guessing is not a valid technique, nor is experimentation with different parameter values. 4. Repeat question 1, but with the files Q4main.c, Q4.h and Q4.o. a) [5 points] Identify the exact assembly/machine instruction within Q4() at which the runtime error occurs. Show exactly how you determined your answer. b) [10 points] Analyze the instruction you identified in part a), and explain exactly why executing this instruction would cause a runtime error. c) [10 points] For what parameter value(s) will Q4() not trigger a segmentation fault? Show exactly how you determined your answer(s) to this question; guessing is not a valid technique, nor is experimentation with different parameter values. The last two questions bear some relationship to the sorts of things you'll have to figure out when you defuse your binary bomb. So, this makes a good warmup for that assignment. 9
A short session with gdb verifies a few facts; the student has made notes of some observations:
 This assignment refers to concepts discussed in the course notes on gdb and the book The Art of Debugging by Matloff & Salzman. The questions are definitely "hands-on" and will require some reading beyond
This assignment refers to concepts discussed in the course notes on gdb and the book The Art of Debugging by Matloff & Salzman. The questions are definitely "hands-on" and will require some reading beyond
1. A student is testing an implementation of a C function; when compiled with gcc, the following x86-32 assembly code is produced:
 This assignment refers to concepts discussed in the course notes on gdb and the book The Art of Debugging by Matloff & Salzman. The questions are definitely "hands-on" and will require some reading beyond
This assignment refers to concepts discussed in the course notes on gdb and the book The Art of Debugging by Matloff & Salzman. The questions are definitely "hands-on" and will require some reading beyond
1. A student is testing an implementation of a C function; when compiled with gcc, the following x86-64 assembly code is produced:
 This assignment refers to concepts discussed in sections 2.1.1 2.1.3, 2.1.8, 2.2.1 2.2.6, 3.2, 3.4, and 3.7.1of csapp; see that material for discussions of x86 assembly language and its relationship to
This assignment refers to concepts discussed in sections 2.1.1 2.1.3, 2.1.8, 2.2.1 2.2.6, 3.2, 3.4, and 3.7.1of csapp; see that material for discussions of x86 assembly language and its relationship to
CS 2505 Computer Organization I Test 2. Do not start the test until instructed to do so! printed
 Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other electronic devices
Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other electronic devices
CS 2505 Computer Organization I Test 2. Do not start the test until instructed to do so! printed
 Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other electronic devices
Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other electronic devices
CS 2505 Computer Organization I Test 2. Do not start the test until instructed to do so! printed
 Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other electronic devices
Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other electronic devices
Download the tarball for this session. It will include the following files:
 Getting Started 1 Download the tarball for this session. It will include the following files: driver driver.c bomb.h bomb.o 64-bit executable C driver source declaration for "bomb" 64-bit object code for
Getting Started 1 Download the tarball for this session. It will include the following files: driver driver.c bomb.h bomb.o 64-bit executable C driver source declaration for "bomb" 64-bit object code for
CSE 361S Intro to Systems Software Lab Assignment #4
 Due: Thursday, October 23, 2008. CSE 361S Intro to Systems Software Lab Assignment #4 In this lab, you will mount a buffer overflow attack on your own program. As stated in class, we do not condone using
Due: Thursday, October 23, 2008. CSE 361S Intro to Systems Software Lab Assignment #4 In this lab, you will mount a buffer overflow attack on your own program. As stated in class, we do not condone using
CS 2505 Computer Organization I Test 2. Do not start the test until instructed to do so! printed
 Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page fact sheet. Your fact sheet may contain definitions and examples,
Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page fact sheet. Your fact sheet may contain definitions and examples,
Download the tarball for this session. It will include the following files:
 Getting Started 1 Download the tarball for this session. It will include the following files: driver driver.c bomb.h bomb.o 64-bit executable C driver source declaration for "bomb" 64-bit object code for
Getting Started 1 Download the tarball for this session. It will include the following files: driver driver.c bomb.h bomb.o 64-bit executable C driver source declaration for "bomb" 64-bit object code for
CS 2505 Computer Organization I
 Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other computing devices may
Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other computing devices may
Exercise Session 6 Computer Architecture and Systems Programming
 Systems Group Department of Computer Science ETH Zürich Exercise Session 6 Computer Architecture and Systems Programming Herbstsemester 2016 Agenda GDB Outlook on assignment 6 GDB The GNU Debugger 3 Debugging..
Systems Group Department of Computer Science ETH Zürich Exercise Session 6 Computer Architecture and Systems Programming Herbstsemester 2016 Agenda GDB Outlook on assignment 6 GDB The GNU Debugger 3 Debugging..
CS 3214 Spring # Problem Points Min Max Average Median SD Grader. 1 Memory Layout and Locality Bill
 CS 3214 # Problem Points Min Max Average Median SD Grader 1 Memory Layout and Locality 25 2 25 14.2 14 5.7 Bill 2 Stack 25 3 22 12.6 13 4.2 Peter 3 Compilation and Linking 25 0 19 7.6 6 4.7 Maggie 4 Execution
CS 3214 # Problem Points Min Max Average Median SD Grader 1 Memory Layout and Locality 25 2 25 14.2 14 5.7 Bill 2 Stack 25 3 22 12.6 13 4.2 Peter 3 Compilation and Linking 25 0 19 7.6 6 4.7 Maggie 4 Execution
Binghamton University. CS-220 Spring X86 Debug. Computer Systems Section 3.11
 X86 Debug Computer Systems Section 3.11 GDB is a Source Level debugger We have learned how to debug at the C level Now, C has been translated to X86 assembler! How does GDB play the shell game? Makes it
X86 Debug Computer Systems Section 3.11 GDB is a Source Level debugger We have learned how to debug at the C level Now, C has been translated to X86 assembler! How does GDB play the shell game? Makes it
Lecture 08 Control-flow Hijacking Defenses
 Lecture 08 Control-flow Hijacking Defenses Stephen Checkoway University of Illinois at Chicago CS 487 Fall 2017 Slides adapted from Miller, Bailey, and Brumley Control Flow Hijack: Always control + computation
Lecture 08 Control-flow Hijacking Defenses Stephen Checkoway University of Illinois at Chicago CS 487 Fall 2017 Slides adapted from Miller, Bailey, and Brumley Control Flow Hijack: Always control + computation
CSC 373, Winter 2012 Lab Assignment 3: The Buffer Bomb
 CSC 373, Winter 2012 Lab Assignment 3: The Buffer Bomb Contact Glenn Lancaster (glancast@cs.depaul.edu) for questions/hints on this assignment. Introduction This assignment helps you develop a detailed
CSC 373, Winter 2012 Lab Assignment 3: The Buffer Bomb Contact Glenn Lancaster (glancast@cs.depaul.edu) for questions/hints on this assignment. Introduction This assignment helps you develop a detailed
Here is a C function that will print a selected block of bytes from such a memory block, using an array-based view of the necessary logic:
 Pointer Manipulations Pointer Casts and Data Accesses Viewing Memory The contents of a block of memory may be viewed as a collection of hex nybbles indicating the contents of the byte in the memory region;
Pointer Manipulations Pointer Casts and Data Accesses Viewing Memory The contents of a block of memory may be viewed as a collection of hex nybbles indicating the contents of the byte in the memory region;
CS 2505 Computer Organization I
 Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other computing devices may
Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other computing devices may
CSC 2400: Computing Systems. X86 Assembly: Function Calls
 CSC 24: Computing Systems X86 Assembly: Function Calls 1 Lecture Goals Challenges of supporting functions Providing information for the called function Function arguments and local variables Allowing the
CSC 24: Computing Systems X86 Assembly: Function Calls 1 Lecture Goals Challenges of supporting functions Providing information for the called function Function arguments and local variables Allowing the
Buffer Overflow Attack
 Buffer Overflow Attack What every applicant for the hacker should know about the foundation of buffer overflow attacks By (Dalgona@wowhacker.org) Email: zinwon@gmail.com 2005 9 5 Abstract Buffer overflow.
Buffer Overflow Attack What every applicant for the hacker should know about the foundation of buffer overflow attacks By (Dalgona@wowhacker.org) Email: zinwon@gmail.com 2005 9 5 Abstract Buffer overflow.
Machine Language, Assemblers and Linkers"
 Machine Language, Assemblers and Linkers 1 Goals for this Lecture Help you to learn about: IA-32 machine language The assembly and linking processes 2 1 Why Learn Machine Language Last stop on the language
Machine Language, Assemblers and Linkers 1 Goals for this Lecture Help you to learn about: IA-32 machine language The assembly and linking processes 2 1 Why Learn Machine Language Last stop on the language
Compila(on, Disassembly, and Profiling
 Compila(on, Disassembly, and Profiling (in Linux) CS 485: Systems Programming Fall 2015 Instructor: James Griffioen 1 Recall the compila(on process/steps 2 Turning C into Object Code Code in files p1.c
Compila(on, Disassembly, and Profiling (in Linux) CS 485: Systems Programming Fall 2015 Instructor: James Griffioen 1 Recall the compila(on process/steps 2 Turning C into Object Code Code in files p1.c
CS 3214 Computer Systems. Do not start the test until instructed to do so! printed
 Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other computing devices may
Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other computing devices may
Buffer-Overflow Attacks on the Stack
 Computer Systems Buffer-Overflow Attacks on the Stack Introduction A buffer overflow occurs when a program, while writing data to a buffer, overruns the buffer's boundary and overwrites memory in adjacent
Computer Systems Buffer-Overflow Attacks on the Stack Introduction A buffer overflow occurs when a program, while writing data to a buffer, overruns the buffer's boundary and overwrites memory in adjacent
Lab 10: Introduction to x86 Assembly
 CS342 Computer Security Handout # 8 Prof. Lyn Turbak Wednesday, Nov. 07, 2012 Wellesley College Revised Nov. 09, 2012 Lab 10: Introduction to x86 Assembly Revisions: Nov. 9 The sos O3.s file on p. 10 was
CS342 Computer Security Handout # 8 Prof. Lyn Turbak Wednesday, Nov. 07, 2012 Wellesley College Revised Nov. 09, 2012 Lab 10: Introduction to x86 Assembly Revisions: Nov. 9 The sos O3.s file on p. 10 was
Assembly Programmer s View Lecture 4A Machine-Level Programming I: Introduction
 Assembly Programmer s View Lecture 4A Machine-Level Programming I: Introduction E I P CPU isters Condition Codes Addresses Data Instructions Memory Object Code Program Data OS Data Topics Assembly Programmer
Assembly Programmer s View Lecture 4A Machine-Level Programming I: Introduction E I P CPU isters Condition Codes Addresses Data Instructions Memory Object Code Program Data OS Data Topics Assembly Programmer
CS356: Discussion #5 Debugging with GDB. Marco Paolieri
 CS356: Discussion #5 Debugging with GDB Marco Paolieri (paolieri@usc.edu) Schedule: Exams and Assignments Week 1: Binary Representation HW0. Week 2: Integer Operations Week 3: Floating-Point Operations
CS356: Discussion #5 Debugging with GDB Marco Paolieri (paolieri@usc.edu) Schedule: Exams and Assignments Week 1: Binary Representation HW0. Week 2: Integer Operations Week 3: Floating-Point Operations
Advanced Buffer Overflow
 Pattern Recognition and Applications Lab Advanced Buffer Overflow Ing. Davide Maiorca, Ph.D. davide.maiorca@diee.unica.it Computer Security A.Y. 2016/2017 Department of Electrical and Electronic Engineering
Pattern Recognition and Applications Lab Advanced Buffer Overflow Ing. Davide Maiorca, Ph.D. davide.maiorca@diee.unica.it Computer Security A.Y. 2016/2017 Department of Electrical and Electronic Engineering
18-600: Recitation #3
 18-600: Recitation #3 Bomb Lab & GDB Overview September 12th, 2017 1 Today X86-64 Overview Bomb Lab Introduction GDB Tutorial 2 3 x86-64: Register Conventions Arguments passed in registers: %rdi, %rsi,
18-600: Recitation #3 Bomb Lab & GDB Overview September 12th, 2017 1 Today X86-64 Overview Bomb Lab Introduction GDB Tutorial 2 3 x86-64: Register Conventions Arguments passed in registers: %rdi, %rsi,
Machine Programming 1: Introduction
 Machine Programming 1: Introduction CS61, Lecture 3 Prof. Stephen Chong September 8, 2011 Announcements (1/2) Assignment 1 due Tuesday Please fill in survey by 5pm today! Assignment 2 will be released
Machine Programming 1: Introduction CS61, Lecture 3 Prof. Stephen Chong September 8, 2011 Announcements (1/2) Assignment 1 due Tuesday Please fill in survey by 5pm today! Assignment 2 will be released
buffer overflow exploitation
 buffer overflow exploitation Samuele Andreoli, Nicolò Fornari, Giuseppe Vitto May 11, 2016 University of Trento Introduction 1 introduction A Buffer Overflow is an anomaly where a program, while writing
buffer overflow exploitation Samuele Andreoli, Nicolò Fornari, Giuseppe Vitto May 11, 2016 University of Trento Introduction 1 introduction A Buffer Overflow is an anomaly where a program, while writing
Pointer Casts and Data Accesses
 C Programming Pointer Casts and Data Accesses For this assignment, you will implement a C function similar to printf(). While implementing the function you will encounter pointers, strings, and bit-wise
C Programming Pointer Casts and Data Accesses For this assignment, you will implement a C function similar to printf(). While implementing the function you will encounter pointers, strings, and bit-wise
EECS 213 Introduction to Computer Systems Dinda, Spring Homework 3. Memory and Cache
 Homework 3 Memory and Cache 1. Reorder the fields in this structure so that the structure will (a) consume the most space and (b) consume the least space on an IA32 machine on Linux. struct foo { double
Homework 3 Memory and Cache 1. Reorder the fields in this structure so that the structure will (a) consume the most space and (b) consume the least space on an IA32 machine on Linux. struct foo { double
Here is a C function that will print a selected block of bytes from such a memory block, using an array-based view of the necessary logic:
 Pointer Manipulations Pointer Casts and Data Accesses Viewing Memory The contents of a block of memory may be viewed as a collection of hex nybbles indicating the contents of the byte in the memory region;
Pointer Manipulations Pointer Casts and Data Accesses Viewing Memory The contents of a block of memory may be viewed as a collection of hex nybbles indicating the contents of the byte in the memory region;
ANITA S SUPER AWESOME RECITATION SLIDES
 ANITA S SUPER AWESOME RECITATION SLIDES 15/18-213: Introduction to Computer Systems Stacks and Buflab, 11 Jun 2013 Anita Zhang, Section M WHAT S NEW (OR NOT) Bomblab is due tonight, 11:59 PM EDT Your late
ANITA S SUPER AWESOME RECITATION SLIDES 15/18-213: Introduction to Computer Systems Stacks and Buflab, 11 Jun 2013 Anita Zhang, Section M WHAT S NEW (OR NOT) Bomblab is due tonight, 11:59 PM EDT Your late
UW CSE 351, Winter 2013 Midterm Exam
 Full Name: Student ID: UW CSE 351, Winter 2013 Midterm Exam February 15, 2013 Instructions: Make sure that your exam is not missing any of the 9 pages, then write your full name and UW student ID on the
Full Name: Student ID: UW CSE 351, Winter 2013 Midterm Exam February 15, 2013 Instructions: Make sure that your exam is not missing any of the 9 pages, then write your full name and UW student ID on the
MACHINE-LEVEL PROGRAMMING I: BASICS COMPUTER ARCHITECTURE AND ORGANIZATION
 MACHINE-LEVEL PROGRAMMING I: BASICS COMPUTER ARCHITECTURE AND ORGANIZATION Today: Machine Programming I: Basics History of Intel processors and architectures C, assembly, machine code Assembly Basics:
MACHINE-LEVEL PROGRAMMING I: BASICS COMPUTER ARCHITECTURE AND ORGANIZATION Today: Machine Programming I: Basics History of Intel processors and architectures C, assembly, machine code Assembly Basics:
Buffer-Overflow Attacks on the Stack
 Computer Systems Buffer-Overflow Attacks on the Stack Introduction A buffer overflow occurs when a program, while writing data to a buffer, overruns the buffer's boundary and overwrites memory in adjacent
Computer Systems Buffer-Overflow Attacks on the Stack Introduction A buffer overflow occurs when a program, while writing data to a buffer, overruns the buffer's boundary and overwrites memory in adjacent
Both parts center on the concept of a "mesa", and make use of the following data type:
 C Programming Simple Array Processing This assignment consists of two parts. The first part focuses on array read accesses and computational logic. The second part requires solving the same problem using
C Programming Simple Array Processing This assignment consists of two parts. The first part focuses on array read accesses and computational logic. The second part requires solving the same problem using
The First Real Bug. gdb. Computer Organization I McQuain
 The First Real Bug 1 Debugging vs Testing 2 Software testing is any activity aimed at evaluating an attribute or capability of a program and determining whether it meets its specified results All about
The First Real Bug 1 Debugging vs Testing 2 Software testing is any activity aimed at evaluating an attribute or capability of a program and determining whether it meets its specified results All about
Creating a String Data Type in C
 C Programming Creating a String Data Type in C For this assignment, you will use the struct mechanism in C to implement a data type that models a character string: struct _String { char data; dynamically-allocated
C Programming Creating a String Data Type in C For this assignment, you will use the struct mechanism in C to implement a data type that models a character string: struct _String { char data; dynamically-allocated
Jackson State University Department of Computer Science CSC / Advanced Information Security Spring 2013 Lab Project # 5
 Jackson State University Department of Computer Science CSC 439-01/539-02 Advanced Information Security Spring 2013 Lab Project # 5 Use of GNU Debugger (GDB) for Reverse Engineering of C Programs in a
Jackson State University Department of Computer Science CSC 439-01/539-02 Advanced Information Security Spring 2013 Lab Project # 5 Use of GNU Debugger (GDB) for Reverse Engineering of C Programs in a
CS/ECE 354 Practice Midterm Exam Solutions Spring 2016
 CS/ECE 354 Practice Midterm Exam Solutions Spring 2016 C Programming 1. The reason for using pointers in a C program is a. Pointers allow different functions to share and modify their local variables.
CS/ECE 354 Practice Midterm Exam Solutions Spring 2016 C Programming 1. The reason for using pointers in a C program is a. Pointers allow different functions to share and modify their local variables.
20: Exploits and Containment
 20: Exploits and Containment Mark Handley Andrea Bittau What is an exploit? Programs contain bugs. These bugs could have security implications (vulnerabilities) An exploit is a tool which exploits a vulnerability
20: Exploits and Containment Mark Handley Andrea Bittau What is an exploit? Programs contain bugs. These bugs could have security implications (vulnerabilities) An exploit is a tool which exploits a vulnerability
The assignment requires solving a matrix access problem using only pointers to access the array elements, and introduces the use of struct data types.
 C Programming Simple Array Processing The assignment requires solving a matrix access problem using only pointers to access the array elements, and introduces the use of struct data types. Both parts center
C Programming Simple Array Processing The assignment requires solving a matrix access problem using only pointers to access the array elements, and introduces the use of struct data types. Both parts center
Accessing Data in Memory
 Accessing Data in Memory You will implement a simple C function that parses a tangled list of binary records in memory, processing them nonsequentially, and produces a simple text report. The function
Accessing Data in Memory You will implement a simple C function that parses a tangled list of binary records in memory, processing them nonsequentially, and produces a simple text report. The function
gcc o driver std=c99 -Wall driver.c bigmesa.c
 C Programming Simple Array Processing This assignment consists of two parts. The first part focuses on array read accesses and computational logic. The second part focuses on array read/write access and
C Programming Simple Array Processing This assignment consists of two parts. The first part focuses on array read accesses and computational logic. The second part focuses on array read/write access and
Turning C into Object Code Code in files p1.c p2.c Compile with command: gcc -O p1.c p2.c -o p Use optimizations (-O) Put resulting binary in file p
 Turning C into Object Code Code in files p1.c p2.c Compile with command: gcc -O p1.c p2.c -o p Use optimizations (-O) Put resulting binary in file p text C program (p1.c p2.c) Compiler (gcc -S) text Asm
Turning C into Object Code Code in files p1.c p2.c Compile with command: gcc -O p1.c p2.c -o p Use optimizations (-O) Put resulting binary in file p text C program (p1.c p2.c) Compiler (gcc -S) text Asm
Advanced Buffer Overflow
 Pattern Recognition and Applications Lab Advanced Buffer Overflow Ing. Davide Maiorca, Ph.D. davide.maiorca@diee.unica.it Computer Security A.Y. 2017/2018 Department of Electrical and Electronic Engineering
Pattern Recognition and Applications Lab Advanced Buffer Overflow Ing. Davide Maiorca, Ph.D. davide.maiorca@diee.unica.it Computer Security A.Y. 2017/2018 Department of Electrical and Electronic Engineering
CSC 2400: Computing Systems. X86 Assembly: Function Calls"
 CSC 24: Computing Systems X86 Assembly: Function Calls" 1 Lecture Goals! Challenges of supporting functions" Providing information for the called function" Function arguments and local variables" Allowing
CSC 24: Computing Systems X86 Assembly: Function Calls" 1 Lecture Goals! Challenges of supporting functions" Providing information for the called function" Function arguments and local variables" Allowing
Pointer Accesses to Memory and Bitwise Manipulation
 C Programming Pointer Accesses to Memory and Bitwise Manipulation This assignment consists of implementing a function that can be executed in two modes, controlled by a switch specified by a parameter
C Programming Pointer Accesses to Memory and Bitwise Manipulation This assignment consists of implementing a function that can be executed in two modes, controlled by a switch specified by a parameter
Università Ca Foscari Venezia
 Stack Overflow Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Introduction Buffer overflow is due to careless programming in unsafe languages like C
Stack Overflow Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Introduction Buffer overflow is due to careless programming in unsafe languages like C
CS165 Computer Security. Understanding low-level program execution Oct 1 st, 2015
 CS165 Computer Security Understanding low-level program execution Oct 1 st, 2015 A computer lets you make more mistakes faster than any invention in human history - with the possible exceptions of handguns
CS165 Computer Security Understanding low-level program execution Oct 1 st, 2015 A computer lets you make more mistakes faster than any invention in human history - with the possible exceptions of handguns
The Dynamic Debugger gdb
 Introduction The Dynamic Debugger gdb This handout introduces the basics of using gdb, a very powerful dynamic debugging tool. No-one always writes programs that execute perfectly every time, and while
Introduction The Dynamic Debugger gdb This handout introduces the basics of using gdb, a very powerful dynamic debugging tool. No-one always writes programs that execute perfectly every time, and while
CSCE 212H, Spring 2008 Lab Assignment 3: Assembly Language Assigned: Feb. 7, Due: Feb. 14, 11:59PM
 CSCE 212H, Spring 2008 Lab Assignment 3: Assembly Language Assigned: Feb. 7, Due: Feb. 14, 11:59PM February 7, 2008 1 Overview The purpose of this assignment is to introduce you to the assembly language
CSCE 212H, Spring 2008 Lab Assignment 3: Assembly Language Assigned: Feb. 7, Due: Feb. 14, 11:59PM February 7, 2008 1 Overview The purpose of this assignment is to introduce you to the assembly language
15-213/18-213, Fall 2011 Exam 1
 Andrew ID (print clearly!): Full Name: 15-213/18-213, Fall 2011 Exam 1 Tuesday, October 18, 2011 Instructions: Make sure that your exam is not missing any sheets, then write your Andrew ID and full name
Andrew ID (print clearly!): Full Name: 15-213/18-213, Fall 2011 Exam 1 Tuesday, October 18, 2011 Instructions: Make sure that your exam is not missing any sheets, then write your Andrew ID and full name
CS 2505 Computer Organization I Test 1. Do not start the test until instructed to do so! printed
 Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. This examination is closed book and closed
Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. This examination is closed book and closed
CS 2505 Computer Organization I Test 1. Do not start the test until instructed to do so! printed
 Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. This examination is closed book and closed
Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. This examination is closed book and closed
Stack overflow exploitation
 Stack overflow exploitation In order to illustrate how the stack overflow exploitation goes I m going to use the following c code: #include #include #include static void
Stack overflow exploitation In order to illustrate how the stack overflow exploitation goes I m going to use the following c code: #include #include #include static void
Instruction Set Architectures
 Instruction Set Architectures ISAs Brief history of processors and architectures C, assembly, machine code Assembly basics: registers, operands, move instructions 1 What should the HW/SW interface contain?
Instruction Set Architectures ISAs Brief history of processors and architectures C, assembly, machine code Assembly basics: registers, operands, move instructions 1 What should the HW/SW interface contain?
Computer Systems Architecture I. CSE 560M Lecture 3 Prof. Patrick Crowley
 Computer Systems Architecture I CSE 560M Lecture 3 Prof. Patrick Crowley Plan for Today Announcements Readings are extremely important! No class meeting next Monday Questions Commentaries A few remaining
Computer Systems Architecture I CSE 560M Lecture 3 Prof. Patrick Crowley Plan for Today Announcements Readings are extremely important! No class meeting next Monday Questions Commentaries A few remaining
Pointer Accesses to Memory and Bitwise Manipulation
 C Programming Pointer Accesses to Memory and Bitwise Manipulation This assignment consists of two parts, the second extending the solution to the first. Q1 [80%] Accessing Data in Memory Here is a hexdump
C Programming Pointer Accesses to Memory and Bitwise Manipulation This assignment consists of two parts, the second extending the solution to the first. Q1 [80%] Accessing Data in Memory Here is a hexdump
Sungkyunkwan University
 November, 1988 Internet Worm attacks thousands of Internet hosts. How did it happen? November, 1988 Internet Worm attacks thousands of Internet hosts. How did it happen? July, 1999 Microsoft launches MSN
November, 1988 Internet Worm attacks thousands of Internet hosts. How did it happen? November, 1988 Internet Worm attacks thousands of Internet hosts. How did it happen? July, 1999 Microsoft launches MSN
15-213/18-243, Fall 2010 Exam 1 - Version A
 Andrew login ID: Full Name: Section: 15-213/18-243, Fall 2010 Exam 1 - Version A Tuesday, September 28, 2010 Instructions: Make sure that your exam is not missing any sheets, then write your Andrew login
Andrew login ID: Full Name: Section: 15-213/18-243, Fall 2010 Exam 1 - Version A Tuesday, September 28, 2010 Instructions: Make sure that your exam is not missing any sheets, then write your Andrew login
GDB Tutorial. A Walkthrough with Examples. CMSC Spring Last modified March 22, GDB Tutorial
 A Walkthrough with Examples CMSC 212 - Spring 2009 Last modified March 22, 2009 What is gdb? GNU Debugger A debugger for several languages, including C and C++ It allows you to inspect what the program
A Walkthrough with Examples CMSC 212 - Spring 2009 Last modified March 22, 2009 What is gdb? GNU Debugger A debugger for several languages, including C and C++ It allows you to inspect what the program
You may work with a partner on this quiz; both of you must submit your answers.
 Instructions: Choose the best answer for each of the following questions. It is possible that several answers are partially correct, but one answer is best. It is also possible that several answers are
Instructions: Choose the best answer for each of the following questions. It is possible that several answers are partially correct, but one answer is best. It is also possible that several answers are
CS 105, Fall Lab 4: The Buffer Bomb. See Calendar for Dates
 CS 105, Fall 2003 Lab 4: The Buffer Bomb See Calendar for Dates October 15, 2003 8h 39min Geoff (geoff@cs.cmu.edu) and Mike(mike@cs.cmu.edu) are the leads for this assignment. Introduction This assignment
CS 105, Fall 2003 Lab 4: The Buffer Bomb See Calendar for Dates October 15, 2003 8h 39min Geoff (geoff@cs.cmu.edu) and Mike(mike@cs.cmu.edu) are the leads for this assignment. Introduction This assignment
CS354 gdb Tutorial Written by Chris Feilbach
 CS354 gdb Tutorial Written by Chris Feilbach Purpose This tutorial aims to show you the basics of using gdb to debug C programs. gdb is the GNU debugger, and is provided on systems that
CS354 gdb Tutorial Written by Chris Feilbach Purpose This tutorial aims to show you the basics of using gdb to debug C programs. gdb is the GNU debugger, and is provided on systems that
EECS 213, Fall 2009 Exploit Lab
 EECS 213, Fall 2009 Exploit Lab Introduction This assignment helps you develop a detailed understanding of the calling stack organization on an IA32 processor. It involves applying a series of buffer overflow
EECS 213, Fall 2009 Exploit Lab Introduction This assignment helps you develop a detailed understanding of the calling stack organization on an IA32 processor. It involves applying a series of buffer overflow
The following notes illustrate debugging a linked list implementation with gdb.
 Payload Type The following notes illustrate debugging a linked list implementation with. The example makes use of the following payload type: struct _WordRecord { char* Word; // zero-terminated C-string
Payload Type The following notes illustrate debugging a linked list implementation with. The example makes use of the following payload type: struct _WordRecord { char* Word; // zero-terminated C-string
Pointer Accesses to Memory and Bitwise Manipulation
 C Programming Pointer Accesses to Memory and Bitwise Manipulation This assignment consists of two parts, the second extending the solution to the first. Q1 [80%] Accessing Data in Memory Here is a hexdump
C Programming Pointer Accesses to Memory and Bitwise Manipulation This assignment consists of two parts, the second extending the solution to the first. Q1 [80%] Accessing Data in Memory Here is a hexdump
CS 201 Winter 2014 (Karavanic) Final Exam
 CS 201 Winter 2014 (Karavanic) Final Exam Your Name: (1 point) Instructions: - Be sure to write your name on the first sheet. - All answers, and all work submitted in support of answers, should be written
CS 201 Winter 2014 (Karavanic) Final Exam Your Name: (1 point) Instructions: - Be sure to write your name on the first sheet. - All answers, and all work submitted in support of answers, should be written
Binghamton University. CS-220 Spring X86 Debug. Computer Systems Section 3.11
 X86 Debug Computer Systems Section 3.11 GDB is a Source Level debugger We have learned how to debug at the C level But the machine is executing X86 object code! How does GDB play the shell game? Makes
X86 Debug Computer Systems Section 3.11 GDB is a Source Level debugger We have learned how to debug at the C level But the machine is executing X86 object code! How does GDB play the shell game? Makes
CS341, Spring 2014 The Buffer Bomb Assigned: 9:30AM Thursday, February 27th, 2014 Due: 9:30AM Thursday, March 13th, 2014
 CS341, Spring 2014 The Buffer Bomb Assigned: 9:30AM Thursday, February 27th, 2014 Due: 9:30AM Thursday, March 13th, 2014 Brady Key (bradykey@gmail.com) is the lead person for this assignment. Introduction
CS341, Spring 2014 The Buffer Bomb Assigned: 9:30AM Thursday, February 27th, 2014 Due: 9:30AM Thursday, March 13th, 2014 Brady Key (bradykey@gmail.com) is the lead person for this assignment. Introduction
CNIT 127: Exploit Development. Ch 2: Stack Overflows in Linux
 CNIT 127: Exploit Development Ch 2: Stack Overflows in Linux Stack-based Buffer Overflows Most popular and best understood exploitation method Aleph One's "Smashing the Stack for Fun and Profit" (1996)
CNIT 127: Exploit Development Ch 2: Stack Overflows in Linux Stack-based Buffer Overflows Most popular and best understood exploitation method Aleph One's "Smashing the Stack for Fun and Profit" (1996)
TIE: Principled Reverse Engineering of Types in Binary Programs! JongHyup Lee, Thanassis Avgerinos, and David Brumley
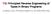 TIE: Principled Reverse Engineering of Types in Binary Programs! JongHyup Lee, Thanassis Avgerinos, and David Brumley Reverse engineering on binary programs! 1.Code structure 2.Data abstractions TIE 2
TIE: Principled Reverse Engineering of Types in Binary Programs! JongHyup Lee, Thanassis Avgerinos, and David Brumley Reverse engineering on binary programs! 1.Code structure 2.Data abstractions TIE 2
Project 1 Notes and Demo
 Project 1 Notes and Demo Overview You ll be given the source code for 7 short buggy programs (target[1-7].c). These programs will be installed with setuid root Your job is to write exploits (sploit[1-7].c)
Project 1 Notes and Demo Overview You ll be given the source code for 7 short buggy programs (target[1-7].c). These programs will be installed with setuid root Your job is to write exploits (sploit[1-7].c)
CS , Fall 2002 Exam 1
 Andrew login ID: Full Name: CS 15-213, Fall 2002 Exam 1 October 8, 2002 Instructions: Make sure that your exam is not missing any sheets, then write your full name and Andrew login ID on the front. Write
Andrew login ID: Full Name: CS 15-213, Fall 2002 Exam 1 October 8, 2002 Instructions: Make sure that your exam is not missing any sheets, then write your full name and Andrew login ID on the front. Write
CS / ECE , Spring 2010 Exam 1
 Andrew login ID: Full Name: Recitation Section: CS 15-213 / ECE 18-243, Spring 2010 Exam 1 Version 1100101 Tuesday, March 2nd, 2010 Instructions: Make sure that your exam is not missing any sheets, then
Andrew login ID: Full Name: Recitation Section: CS 15-213 / ECE 18-243, Spring 2010 Exam 1 Version 1100101 Tuesday, March 2nd, 2010 Instructions: Make sure that your exam is not missing any sheets, then
Intro x86 Part 3: Linux Tools & Analysis
 Intro x86 Part 3: Linux Tools & Analysis Xeno Kovah 2009/2010 xkovah at gmail Approved for Public Release: 10-3348. Distribution Unlimited All materials is licensed under a Creative Commons Share Alike
Intro x86 Part 3: Linux Tools & Analysis Xeno Kovah 2009/2010 xkovah at gmail Approved for Public Release: 10-3348. Distribution Unlimited All materials is licensed under a Creative Commons Share Alike
Systems I. Machine-Level Programming I: Introduction
 Systems I Machine-Level Programming I: Introduction Topics Assembly Programmerʼs Execution Model Accessing Information Registers IA32 Processors Totally Dominate General Purpose CPU Market Evolutionary
Systems I Machine-Level Programming I: Introduction Topics Assembly Programmerʼs Execution Model Accessing Information Registers IA32 Processors Totally Dominate General Purpose CPU Market Evolutionary
Buffer Overflow Attacks
 CS- Spring Buffer Overflow Attacks Computer Systems..-, CS- Spring Hacking Roots in phone phreaking White Hat vs Gray Hat vs Black Hat Over % of Modern Software Development is Black Hat! Tip the balance:
CS- Spring Buffer Overflow Attacks Computer Systems..-, CS- Spring Hacking Roots in phone phreaking White Hat vs Gray Hat vs Black Hat Over % of Modern Software Development is Black Hat! Tip the balance:
Machine-level Representation of Programs. Jin-Soo Kim Computer Systems Laboratory Sungkyunkwan University
 Machine-level Representation of Programs Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Program? 짬뽕라면 준비시간 :10 분, 조리시간 :10 분 재료라면 1개, 스프 1봉지, 오징어
Machine-level Representation of Programs Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Program? 짬뽕라면 준비시간 :10 분, 조리시간 :10 분 재료라면 1개, 스프 1봉지, 오징어
15-213/18-243, Summer 2011 Exam 1 Tuesday, June 28, 2011
 Andrew login ID: Full Name: Section: 15-213/18-243, Summer 2011 Exam 1 Tuesday, June 28, 2011 Instructions: Make sure that your exam is not missing any sheets, then write your Andrew login ID, full name,
Andrew login ID: Full Name: Section: 15-213/18-243, Summer 2011 Exam 1 Tuesday, June 28, 2011 Instructions: Make sure that your exam is not missing any sheets, then write your Andrew login ID, full name,
struct _Rational { int64_t Top; // numerator int64_t Bottom; // denominator }; typedef struct _Rational Rational;
 Creating a Data Type in C Rational Numbers For this assignment, you will use the struct mechanism in C to implement a data type that represents rational numbers. A set can be modeled using the C struct:
Creating a Data Type in C Rational Numbers For this assignment, you will use the struct mechanism in C to implement a data type that represents rational numbers. A set can be modeled using the C struct:
Instruction Set Architectures
 Instruction Set Architectures! ISAs! Brief history of processors and architectures! C, assembly, machine code! Assembly basics: registers, operands, move instructions 1 What should the HW/SW interface
Instruction Set Architectures! ISAs! Brief history of processors and architectures! C, assembly, machine code! Assembly basics: registers, operands, move instructions 1 What should the HW/SW interface
This time. Defenses and other memory safety vulnerabilities. Everything you ve always wanted to know about gdb but were too afraid to ask
 This time We will continue Buffer overflows By looking at Overflow Defenses and other memory safety vulnerabilities Everything you ve always wanted to know about gdb but were too afraid to ask Overflow
This time We will continue Buffer overflows By looking at Overflow Defenses and other memory safety vulnerabilities Everything you ve always wanted to know about gdb but were too afraid to ask Overflow
CMPSC 497 Buffer Overflow Vulnerabilities
 Systems and Internet Infrastructure Security Network and Security Research Center Department of Computer Science and Engineering Pennsylvania State University, University Park PA CMPSC 497 Buffer Overflow
Systems and Internet Infrastructure Security Network and Security Research Center Department of Computer Science and Engineering Pennsylvania State University, University Park PA CMPSC 497 Buffer Overflow
Obstacle Course Buffer Overflow Hacking Exercise
 Obstacle Course Buffer Overflow Hacking Exercise JerseySTEM Cyber Security program Introduction This exercise helps you develop a detailed understanding of the calling stack organization on an Intel x86/32-
Obstacle Course Buffer Overflow Hacking Exercise JerseySTEM Cyber Security program Introduction This exercise helps you develop a detailed understanding of the calling stack organization on an Intel x86/32-
GDB Tutorial. Young W. Lim Tue. Young W. Lim GDB Tutorial Tue 1 / 32
 GDB Tutorial Young W. Lim 2017-02-14 Tue Young W. Lim GDB Tutorial 2017-02-14 Tue 1 / 32 Outline 1 Introduction Young W. Lim GDB Tutorial 2017-02-14 Tue 2 / 32 Based on "Self-service Linux: Mastering the
GDB Tutorial Young W. Lim 2017-02-14 Tue Young W. Lim GDB Tutorial 2017-02-14 Tue 1 / 32 Outline 1 Introduction Young W. Lim GDB Tutorial 2017-02-14 Tue 2 / 32 Based on "Self-service Linux: Mastering the
CSE 351 Midterm - Winter 2017
 CSE 351 Midterm - Winter 2017 February 08, 2017 Please read through the entire examination first, and make sure you write your name and NetID on all pages! We designed this exam so that it can be completed
CSE 351 Midterm - Winter 2017 February 08, 2017 Please read through the entire examination first, and make sure you write your name and NetID on all pages! We designed this exam so that it can be completed
CS/COE 0449 term 2174 Lab 5: gdb
 CS/COE 0449 term 2174 Lab 5: gdb What is a debugger? A debugger is a program that helps you find logical mistakes in your programs by running them in a controlled way. Undoubtedly by this point in your
CS/COE 0449 term 2174 Lab 5: gdb What is a debugger? A debugger is a program that helps you find logical mistakes in your programs by running them in a controlled way. Undoubtedly by this point in your
War Industries Presents: An Introduction to Programming for Hackers Part V - Functions. By Lovepump, Visit:
 War Industries Presents: An Introduction to Programming for Hackers Part V - Functions By Lovepump, 2004 Visit: www.warindustries.com Goals: At the end of Part IV, you should be able to competently code
War Industries Presents: An Introduction to Programming for Hackers Part V - Functions By Lovepump, 2004 Visit: www.warindustries.com Goals: At the end of Part IV, you should be able to competently code
CSE 410: Systems Programming
 CSE 410: Systems Programming Recitation 4: Introduction to gdb Introduction The GNU Debugger, or gdb, is a powerful symbolic debugger. Symbolic debuggers are available for many languages and platforms,
CSE 410: Systems Programming Recitation 4: Introduction to gdb Introduction The GNU Debugger, or gdb, is a powerful symbolic debugger. Symbolic debuggers are available for many languages and platforms,
MACHINE-LEVEL PROGRAMMING I: BASICS
 MACHINE-LEVEL PROGRAMMING I: BASICS CS 429H: SYSTEMS I Instructor: Emmett Witchel Today: Machine Programming I: Basics History of Intel processors and architectures C, assembly, machine code Assembly Basics:
MACHINE-LEVEL PROGRAMMING I: BASICS CS 429H: SYSTEMS I Instructor: Emmett Witchel Today: Machine Programming I: Basics History of Intel processors and architectures C, assembly, machine code Assembly Basics:
CPS104 Recitation: Assembly Programming
 CPS104 Recitation: Assembly Programming Alexandru Duțu 1 Facts OS kernel and embedded software engineers use assembly for some parts of their code some OSes had their entire GUIs written in assembly in
CPS104 Recitation: Assembly Programming Alexandru Duțu 1 Facts OS kernel and embedded software engineers use assembly for some parts of their code some OSes had their entire GUIs written in assembly in
Introduction to Computer Systems , fall th Lecture, Sep. 28 th
 Introduction to Computer Systems 15 213, fall 2009 9 th Lecture, Sep. 28 th Instructors: Majd Sakr and Khaled Harras Last Time: Structures struct rec { int i; int a[3]; int *p; }; Memory Layout i a p 0
Introduction to Computer Systems 15 213, fall 2009 9 th Lecture, Sep. 28 th Instructors: Majd Sakr and Khaled Harras Last Time: Structures struct rec { int i; int a[3]; int *p; }; Memory Layout i a p 0
Intro to Segmentation Fault Handling in Linux. By Khanh Ngo-Duy
 Intro to Segmentation Fault Handling in Linux By Khanh Ngo-Duy Khanhnd@elarion.com Seminar What is Segmentation Fault (Segfault) Examples and Screenshots Tips to get Segfault information What is Segmentation
Intro to Segmentation Fault Handling in Linux By Khanh Ngo-Duy Khanhnd@elarion.com Seminar What is Segmentation Fault (Segfault) Examples and Screenshots Tips to get Segfault information What is Segmentation
The X86 Assembly Language Instruction Nop Means
 The X86 Assembly Language Instruction Nop Means As little as 1 CPU cycle is "wasted" to execute a NOP instruction (the exact and other "assembly tricks", as explained also in this thread on Programmers.
The X86 Assembly Language Instruction Nop Means As little as 1 CPU cycle is "wasted" to execute a NOP instruction (the exact and other "assembly tricks", as explained also in this thread on Programmers.
Problem Set 1: Unix Commands 1
 Problem Set 1: Unix Commands 1 WARNING: IF YOU DO NOT FIND THIS PROBLEM SET TRIVIAL, I WOULD NOT RECOMMEND YOU TAKE THIS OFFERING OF 300 AS YOU DO NOT POSSESS THE REQUISITE BACKGROUND TO PASS THE COURSE.
Problem Set 1: Unix Commands 1 WARNING: IF YOU DO NOT FIND THIS PROBLEM SET TRIVIAL, I WOULD NOT RECOMMEND YOU TAKE THIS OFFERING OF 300 AS YOU DO NOT POSSESS THE REQUISITE BACKGROUND TO PASS THE COURSE.
