Data Transfer with UTM
|
|
|
- Marion Simon
- 6 years ago
- Views:
Transcription
1 Data Transfer with UTM Motif permits experienced application programmers to extend or override the data transfer capabilities of many Motif widgets. However, data transfer is typically the responsibility of widgets rather than applications. For this reason, complete details of UTM data transfer are found in the Motif Widget Writer s Guide. The UTM information in that book is a prerequisite for understanding this chapter. Nevertheless, we do begin this chapter with a brief overview of UTM from the application programmer s perspective. After this overview, the chapter suggests a few relatively straightforward ways in which an application might use UTM. Motif Programmer s Guide 1
2 What is UTM? Motif widgets support none, some, or all of the following data transfer mechanisms: Primary transfer Secondary transfer Clipboard transfer Drag and drop The Uniform Transfer Method (UTM) is not the fifth mechanism. Rather, UTM unifies and simplifies the way in which the four mechanisms are implemented. For example, consider an application that uses UTM to implement primary transfer. To add support for a UTM clipboard transfer, the application programmer need only write a little extra code. That is because UTM makes it easy for the different data transfer mechanisms to share code. As of Motif Release 2.0, all widgets and applications that implement data transfer should use UTM for that implementation. As of Motif Release 2.0, the Motif toolkit implements data transfer exclusively through UTM. Motif Programmer s Guide 2
3 Why Use UTM? Most applications will be satisfied with the supported target lists. However, some applications may want to support additional targets. In fact, this is the primary reason for using UTM. Consider the XmDrawingArea widget. This widget does not know how to convert any targets. Therefore, the standard XmDrawingArea cannot serve as a useful source for data transfer. However, XmDrawingArea does provide a UTM infrastructure. This infrastructure allows an application programmer to use UTM to supplement the data transfer capabilities of XmDrawingArea. For example, an application could supplement XmDrawingArea such that a user could copy text from an XmText widget to an XmDrawingArea widget. Similarly, an application could supplement XmDrawingArea such that a user could copy a pixmap from one XmDrawingArea to another. Motif Programmer s Guide 3
4 Ideas For Applications Your application can use two new callbacks, XmNconvertCallback and XmNdestinationCallback, to extend or override the data transfer capabilities of any Motif widget. In order to override the data transfer capability of a widget, an application has to provide the same data transfer code that a widget would. So, if those are your intentions, we refer you back to the Motif Widget Writer s Guide for complete details. If, however, your intention is to extend the data transfer capabilities of a widget, then the section you are now reading should be helpful. The following suggest several ways in which an application could extend the data transfer capabilities of a widget: Your application can extend the list of targets supported by a widget. For example, perhaps your application can support a target called _FORMATTED_TEXT, which transfers text in some kind of justified formatted. Your application can extend the widget to support a new form of data transfer. For example, perhaps your application could extend a particular widget so that it supports Drag and Drop. Your application can provide a customized data transfer that improves runtime performance. For example, Motif toolkit widgets typically transfer only one target at a time. If your application always needs to transfer the same group of three targets, your application could request a special multiple transfer. Before undertaking a UTM project in your application, you should consider the following: Data transfer code is relatively complicated to write. By extending a widget, you may run into some consistency problems. For example, suppose your application extends the data transfer capabilities of an XmLabel widget. Since other applications probably will not extend XmLabel in the same way yours has, you run the risk of confusing users. Your application s documentation will have to explain the ways in which XmLabel widgets in your application are different from standard XmLabel widgets. Motif Programmer s Guide 4
5 Implementation Overview This section provides an overview of UTM from an application programmer s perspective. For complete details, see the Motif Widget Writer s Guide. This section explores the following three kinds of routines that an application might write in order to implement a UTM data transfer: An XmNconvertCallback procedure associated with the source widget An XmNdestinationCallback procedure associated with the destination widget A transfer procedure associated with the XmNdestinationCallback procedure In brief, an XmNdestinationCallback procedure requests specific targets. An XmNconvertCallback procedure converts selections to the requested targets. A transfer procedure pastes the converted selections into the destination widget. XmNconvertCallback Procedure In order to be the source of a UTM data transfer, a widget must provide a callback resource named XmNconvertCallback. The following Motif toolkit widgets hold this resource: XmPrimitive and all its subclasses XmContainer XmDrawingArea XmScale Your application can attach an XmNconvertCallback procedure to any widget holding the XmNconvertCallback resource. UTM calls any XmNconvertCallback procedures in your application whenever the associated widget is asked to convert a selection. After calling these callbacks, UTM typically calls the widget s own internal conversion routine (the convertproc trait method of the XmQTtransfer trait) When UTM calls your application s XmNconvertCallback procedures, UTM passes a pointer to a XmConvertCallbackStruct as the client_data argument. This callback structure is defined as follows: typedef struct reason event selection int reason ; XEvent *event ; Atom selection ; Atom target ; XtPointer source_data ; XtPointer location_data ; int flags ; XtPointer parm ; int parm_format ; unsigned long parm_length ; Atom parm_type ; int status ; XtPointer value ; Atom type ; int format ; unsigned long length ; XmConvertCallbackStruct; Indicates why the callback was invoked. Points to the XEvent that triggered the callback. It can be NULL. Motif Programmer s Guide 5
6 target Indicates the selection for which conversion is being requested. Possible values are CLIPBOARD, PRIMARY, SECONDARY, and _MOTIF_DROP. source_data Indicates the target to convert. Contains information about the selection source. When the selection is _MOTIF_DROP, source_data is the DragContext. Otherwise, source_data is NULL. location_data flags parm Contains information about the location of data to be converted. If the value is NULL, the data to be transferred consists of the widget s current selection. Otherwise, the type and interpretation of the value are specific to the widget class. Indicates the status of the conversion. Following are the possible values: XmCONVERTING_NONE This flag is currently unused. XmCONVERTING_PARTIAL The target widget was able to be converted, but some data was lost. XmCONVERTING_SAME The conversion target is the source of the data to be transferred. XmCONVERTING_TRANSACT This flag is currently unused. Contains parameter data for this target. If no parameter data exists, the value is NULL. When selection is CLIPBOARD and target is _MOTIF_CLIPBOARD_TARGETS or _MOTIF_DEFERRED_CLIPBOARD_TARGETS, the value is the requested operation (XmCOPY, XmMOVE, or XmLINK). parm_format Specifies whether the data in parm should be viewed as a list of char, short, or long quantities. Possible values are 0 (when parm is NULL), 8 (when the data in parm should be viewed as a list of chars), 16 (when the data in parm should be viewed as a list of shorts), or 32 (when the data in parm should be viewed as a list of longs). Note that parm_format symbolizes a data type, not the number of bits in each list element. For example, on some machines, a parm_format of 32 means that the data in parm should be viewed as a list of 64 bit quantities, not 32 bit quantities. parm_length parm_type status Specifies the number of elements of data in parm, where each element has the size specified by parm_format. When parm is NULL, the value is 0. Specifies the parameter type of parm. An IN/OUT member that specifies the status of the conversion. The initial value is XmCONVERT_DEFAULT. The callback procedure can set this member to one of the following values: Motif Programmer s Guide 6
7 XmCONVERT_DEFAULT This value means that the widget s convertproc trait method, if any, is called after the callback procedures return. If the widget s convertproc trait method produces any data, it overwrites the data provided by the callback procedures in the value member. XmCONVERT_MERGE This value means that the widget s convertproc trait method, if any, is called after the callback procedures return. If the widget s convertproc trait method produces any data, it appends its data to the data provided by the callback procedures in the value member. This value is intended for use with targets that result in lists of data, such as TARGETS. XmCONVERT_DONE This value means that the callback procedure has successfully finished the conversion. The widget s convertproc trait method, if any, is not called after the callback procedures return. XmCONVERT_REFUSE This value means that the callback procedure has terminated the conversion process without completing the requested conversion. The widget s convertproc trait method, if any, is not called after the callback procedures return. value An IN/OUT parameter that contains any data that the callback procedure produces as a result of the conversion. The initial value is NULL. If the callback procedure sets this member, it must ensure that the type, format, and length members correspond to the data in value. The callback procedure is responsible for allocating memory when it sets this member. The toolkit frees this memory when it is no longer needed. type format length An IN/OUT parameter that indicates the type of the data in the value member. The initial value is INTEGER. An IN/OUT parameter that specifies whether the data in value should be viewed as a list of char, short, or long quantities. The initial value is 8. The callback procedure can set this member to 8 (for a list of char), 16 (for a list of short), or 32 (for a list of long). An IN/OUT member that specifies the number of elements of data in value, where each element has the size symbolized by format. The initial value is 0. If your application does not define any XmNconvertCallback procedures, UTM automatically calls the widget s convertproc trait method. If your application does define at least one XmNconvertCallback procedures, UTM conditionally calls the widget s convertproc trait method. Here are the conditions: If your XmNconvertCallback procedures are taking full responsibility for converting the selection to a particular target, then UTM will not call the widget s convertproc trait method. An XmNconvertCallback procedure notes that it is taking full responsibility by setting the status member of the XmConvertCallbackStruct to XmCONVERT_DONE or XmCONVERT_REFUSE. If your XmNconvertCallback procedures are not taking full responsibility for converting the selection to a particular target, then UTM will call the widget s convertproc trait method. An XmNconvertCallback procedure notes that it is not taking full responsibility by setting the status member of the XmConvertCallbackStruct to XmCONVERT_DEFAULT or XmCONVERT_MERGE. If UTM does call your widget s convertproc trait method, UTM passes it the same XmConvertCallbackStruct used by the application s XmNconvertCallback procedures. Thus, the XmConvertCallbackStruct provides a convenient conduit for the XmNconvertCallback procedures to communicate with the widget s convertproc trait method. XmNdestinationCallback Procedure In order to be the destination for a UTM data transfer, a widget must provide a callback resource named XmNdestinationCallback. Appendix B lists the widgets in the standard Motif toolkit that hold this callback resource. Your application can attach an XmNdestinationCallback procedure to any widget holding the XmNdestinationCallback resource. UTM calls any XmNdestinationCallback procedures in your application whenever the associated widget is the destination of a data transfer. After calling Motif Programmer s Guide 7
8 these callbacks, UTM typically calls the destination widget s own internal destination routine (the destinationproc trait method of the XmQTtransfer trait). When UTM calls your application s XmNdestinationCallback procedures, UTM passes a pointer to a XmDestinationCallbackStruct as the client_data argument. This callback structure is defined as follows: typedef struct reason event selection operation flags transfer_id int reason ; XEvent *event ; Atom selection ; XtEnum operation ; int flags ; XtPointer transfer_id ; XtPointer destination_data ; XtPointer location_data ; Time time ; XmDestinationCallbackStruct; Indicates why the callback was invoked. Points to the XEvent that triggered the callback. It can be NULL. Indicates the selection for which data transfer is being requested. Possible values are PRIMARY, SECONDARY, CLIPBOARD, and _MOTIF_DROP. Indicates the type of transfer operation requested. When the selection is PRIMARY or SECONDARY, possible values are XmMOVE, XmCOPY, and XmLINK. When the selection is CLIPBOARD, possible values are XmCOPY and XmLINK. When the selection is _MOTIF_DROP, possible values are XmMOVE, XmCOPY, XmLINK, and XmOTHER. A value of XmOTHER means that the callback procedure must get further information from the XmDropProcCallbackStruct in the destination_data member. Indicates whether or not the destination widget is also the source of the data to be transferred. Following are the possible values: XmCONVERTING_NONE The destination widget is not the source of the data to be transferred. XmCONVERTING_SAME The destination widget is the source of the data to be transferred. Serves as a unique ID to identify the transfer transaction. destination_data Contains information about the destination. When the selection is _MOTIF_DROP, the callback procedures are called by the drop site s XmNdropProc, and destination_data is a pointer to the XmDropProcCallbackStruct passed to the XmNdropProc procedure. When the selection is SECONDARY, destination_data is an Atom representing a target recommended by the selection owner for use in converting the selection. Otherwise, destination_data is NULL. Motif Programmer s Guide 8
9 location_data time Contains information about the location where data is to be transferred. The interpretation of this value varies considerably from widget to widget. Once XmTransferDone procedures start to be called, location_data will no longer be stable. Indicates the time when the transfer operation began. The fields in an XmConvertCallbackStruct are far more dynamic than the fields in an XmDestinationCallbackStruct. In other words, an XmNconvertCallback procedure typically modifies many of the fields of its XmConvertCallbackStruct; however, an XmNdestinationCallback procedure typically leaves all the fields of its XmDestinationCallbackStruct untouched. A typical XmNdestinationCallback procedure requests a list of targets supported by the source widget. To make this request, the procedure calls XmTransferValue. For example, here is a typical XmNdestinationCallback procedure: void DestinationCallback(w, ignore, cs) Widget w; XtPointer ignore; XmDestinationCallbackStruct *cs; Atom TARGETS = XInternAtom(XtDisplay(w), "TARGETS", False); /* Request TARGETS that the source widget can convert. */ XmTransferValue(cs > transfer_id, TARGETS, (XtCallbackProc) TransferProcedure, NULL, XtLastTimestampProcessed() ); Transfer Procedure The transfer procedure is a companion routine to the XmNdestinationCallback procedure. Typically, 1. The XmNdestinationCallback procedure calls XmTransferValue to ask for a list of targets supported by the source. 2. When the source completes the conversion, UTM returns control to the transfer procedure. 3. The transfer procedure examines the returned list of targets. If the list contains a desired target, the transfer procedure requests it by calling XmTransferValue. Steps 2 and 3 may repeat several times. Unlike the XmNconvertCallback and XmNdestinationCallback routines, the transfer procedure is not identified by a resource. Rather, the transfer procedure is identified by the third argument in a call to XmTransferValue. When UTM calls your application s transfer procedure, UTM passes a pointer to an XmSelectionCallbackStruct as the client_data argument. This callback structure is defined as follows: typedef struct reason int reason ; XEvent *event ; Atom selection ; Atom target ; Atom type ; XtPointer transfer_id ; int flags ; int remaining ; XtPointer value ; unsigned long length ; int format ; XmSelectionCallbackStruct; Motif Programmer s Guide 9
10 Indicates why the callback was invoked. event selection target type transfer_id flags remaining value length format Points to the XEvent that triggered the callback. It can be NULL. Specifies the selection that has been converted. Specifies the target to which XmTransferValue requested conversion. The value is the same as the value of the target argument to XmTransferValue. Specifies the type of the selection value. This is not the target, but the type used to represent the target. The value XT_CONVERT_FAIL means that the selection owner did not respond to the conversion request within the Intrinsics selection timeout interval. Specifies a unique indentifier for the data transfer operation. The value is the same as the value of the transfer_id argument to XmTransferValue. This member is currently unused. The value is always XmSELECTION_DEFAULT. Indicates the number of transfers remaining for the operation specified by transfer_id. Represents the data transferred by this request. The application is responsible for freeing the value by calling XtFree. Indicates the number of elements of data in value, where each element has the size symbolized by format. If value is NULL, length is 0. Indicates whether the data in value should be viewed as a list of char, short, or long quantities. Possible values are 8 (for a list of char), 16 (for a list of short), or 32 (for a list of long). Motif Programmer s Guide 10
11 Case Study: Adding an Extra Target to XmText This section illustrates how an application can use UTM to supplement the list of targets that an XmText widget can convert. Here is the scenario. The application instantiates two XmText widgets. We will refer to one of these widgets as TextSource and the other as TextDestination. TextDestination has a rather unusual requirement; namely, it expects that any text transferred to it must not contain any lowercase letters. In other words, the source of a data transfer is responsible for converting any lowercase letters to uppercase before transferring the data. The standard XmText widget does not provide any targets that can do this conversion. Therefore, the application must temporarily extend XmText to handle a new target named MYTEXT. The application must do the following: The application must associate an XmNconvertCallback procedure with TextSource. This procedure must be able to convert the MYTEXT target. The application must associate an XmNdestinationCallback procedure and a transfer procedure with TextDestination. These procedures are responsible for requesting that the selection be converted to MYTEXT and for pasting the transferred data into TextDestination. The application will support three different forms of data transfer: primary, clipboard, and drag and drop. The following subsections explains how the application accomplishes its goals. The XmNconvertCallback Procedure The application must associate an XmNconvertCallback procedure with widget TextSource. The following code does just that: XtAddCallback(TextSource, XmNconvertCallback, ConvertCallback, NULL); The application must provide an XmNconvertCallback procedure named ConvertCallback. This procedure must handle the following requests: The destination could request the list of targets that the source can convert. The destination could request that the selection be converted to MYTEXT. Following are the relevant parts of the ConvertCallback routine: void ConvertCallback(Widget w, XtPointer ignore, XtPointer call_data) XmConvertCallbackStruct *ccs = (XmConvertCallbackStruct *)call_data; char *selected_text; char *copy_of_selected_text; Atom TARGETS = XInternAtom(XtDisplay(w), "TARGETS", False); Atom _MOTIF_CLIPBOARD_TARGETS = XInternAtom(XtDisplay(w), "_MOTIF_CLIPBOARD_TARGETS", False); Atom MYTEXT = XInternAtom(XtDisplay(w), "MYTEXT", False); int n=0; Atom *targs = (Atom *)XtMalloc(sizeof(Atom) * 2); if ((ccs >target == TARGETS) (ccs >target == _MOTIF_CLIPBOARD_TARGETS)) /* Use targs to hold a list of targets that my application can convert. This list will be merged with the targets that the XmText widget can convert. */ targs[n] = MYTEXT; n++; ccs >value = (XtPointer) targs; ccs >type = XA_ATOM; ccs >format = 32; ccs >length = n; ccs >status = XmCONVERT_MERGE; else if (ccs >target == MYTEXT) /* Get the selection. */ Motif Programmer s Guide 11
12 selected_text = XmTextGetSelection(w); copy_of_selected_text = selected_text; /* Convert any lowercase letters in the selection to uppercase. */ while (*selected_text++) if (islower(*selected_text)) *selected_text = toupper(*selected_text); /* Place the converted text into the XmConvertCallbackStruct. */ ccs >value = copy_of_selected_text; ccs >type = ccs >target; ccs >format = 8; ccs >length = strlen(copy_of_selected_text); ccs >status = XmCONVERT_DONE; Notice how ConvertCallback sets the value of the status member of the XmConvertCallbackStruct. For example, when the destination requests TARGETS or _MOTIF_CLIPBOARD_TARGETS, ConvertCallback sets status to XmCONVERT_MERGE. This status tells UTM to call the convertproc trait method of XmText. This trait method will add MYTEXT to the list of supported targets. As another example, consider that ConvertCallback is taking full responsibility to convert the selection to MYTEXT. For this case, ConvertCallback sets status to XmCONVERT_DONE. This status tells UTM not to bother calling the convertproc trait method of XmText. Finally, consider what happens when ConvertCallback is asked to convert a target other than TARGETS, _MOTIF_CLIPBOARD_TARGETS, or MYTEXT. In this case, the status member will retain its default value of XmCONVERT_DEFAULT. This status tells UTM to call the convertproc trait method of XmText, and that the trait method will be reponsible for converting the target. The XmNdestinationCallback Procedure The application must associate an XmNdestinationCallback procedure with widget TextDestination. The following code does just that: XtAddCallback(TextDestination, XmNdestinationCallback, DestinationCallback, NULL); The application must provide an XmNdestinationCallback procedure named DestinationCallback. We have implemented this procedure in a very basic fashion. This procedure merely requests a list of the targets that the source widget supports: void DestinationCallback(Widget w, XtPointer ignore, XtPointer call_data) XmDestinationCallbackStruct *dcs = (XmDestinationCallbackStruct *)call_data; Atom TARGETS = XInternAtom(XtDisplay(w), "TARGETS", False); /* Ask the source to return a list of all the targets supported. */ XmTransferValue(dcs >transfer_id, TARGETS, (XtCallbackProc)TransferProc, NULL, XtLastTimestampProcessed() ); The Transfer Procedure When the source returns the list of TARGETS, UTM calls the application s transfer procedure. The transfer procedure, TransferProc in this case, is named by the third argument to XmTransferValue. Here is the algorithm for the transfer procedure. The transfer procedure must examine the returned list of targets to see if the list contains MYTEXT. If it does, ask the source to convert the selection to MYTEXT. When the source completes the conversion, the transfer procedure must paste the converted text into the TextDestination widget. Following is the code for TransferProc: Motif Programmer s Guide 12
13 void TransferProc(Widget w, XtPointer ignore, XtPointer call_data) XmSelectionCallbackStruct *scs = (XmSelectionCallbackStruct *) call_data; Atom TARGETS = XInternAtom(XtDisplay(w), "TARGETS", False); Atom MYTEXT = XInternAtom(XtDisplay(w), "MYTEXT", False); Atom *targets = (Atom *)scs >value; int MYTEXT_is_supported = 0; unsigned long n; if ((scs >target == TARGETS) && (scs >type == XA_ATOM)) for (n=0; n<=scs >length; n++) /* Look through list of returned TARGETS to see if MYTEXT is there. */ if (targets[n] == MYTEXT) MYTEXT_is_supported = 1; if (MYTEXT_is_supported) /* Now ask the source widget to convert the selection to MYTEXT. */ XmTransferValue(scs >transfer_id, MYTEXT, (XtCallbackProc)TransferProc, NULL, XtLastTimestampProcessed() ); if ((scs >target == MYTEXT)) XmTextPosition current_insertion_position; /* Source widget has converted MYTEXT, paste it into the destination widget. */ current_insertion_position = XmTextGetInsertionPosition(w); XmTextInsert(w, current_insertion_position, (char *)scs >value); XmTransferDone(scs >transfer_id, XmTRANSFER_DONE_SUCCEED); Notice how TransferProc calls XmTransferDone. This call marks the end of the transfer. Therefore, UTM will not call the destinationproc trait method inside the TextDestination widget. If the source does not know how to convert MYTEXT, UTM will call the destinationproc trait method inside the TextDestination widget. Motif Programmer s Guide 13
OpenGL Drawing Widgets and Related Functions
 OpenGL Drawing Widgets and Related Functions Following is a list of the OpenGL widgets and widget-related functions, and the purpose of each. Select the item to receive more information. You may also go
OpenGL Drawing Widgets and Related Functions Following is a list of the OpenGL widgets and widget-related functions, and the purpose of each. Select the item to receive more information. You may also go
Xt Widget Classes. ApplicationShell. Composite. Constraint. Core. Object. OverrideShell. RectObj. Shell. TopLevelShell. TransientShell.
 Xt Widget Classes ApplicationShell Composite Constraint Core Object OverrideShell RectObj Shell TopLevelShell TransientShell VendorShell WMShell Motif Programmer s Reference 1 ApplicationShell (library
Xt Widget Classes ApplicationShell Composite Constraint Core Object OverrideShell RectObj Shell TopLevelShell TransientShell VendorShell WMShell Motif Programmer s Reference 1 ApplicationShell (library
Xm Data Types. XmDirection. XmFontList. XmParseMapping. XmParseTable. XmRenderTable. XmString. XmStringDirection. XmStringTable. XmTab.
 Xm Data Types XmDirection XmFontList XmParseMapping XmParseTable XmRenderTable XmString XmStringDirection XmStringTable XmTab XmTabList XmTextPosition Motif Programmer s Reference 1 XmDirection (library
Xm Data Types XmDirection XmFontList XmParseMapping XmParseTable XmRenderTable XmString XmStringDirection XmStringTable XmTab XmTabList XmTextPosition Motif Programmer s Reference 1 XmDirection (library
Short Notes of CS201
 #includes: Short Notes of CS201 The #include directive instructs the preprocessor to read and include a file into a source code file. The file name is typically enclosed with < and > if the file is a system
#includes: Short Notes of CS201 The #include directive instructs the preprocessor to read and include a file into a source code file. The file name is typically enclosed with < and > if the file is a system
CS201 - Introduction to Programming Glossary By
 CS201 - Introduction to Programming Glossary By #include : The #include directive instructs the preprocessor to read and include a file into a source code file. The file name is typically enclosed with
CS201 - Introduction to Programming Glossary By #include : The #include directive instructs the preprocessor to read and include a file into a source code file. The file name is typically enclosed with
Display PostScript System
 Display PostScript System Adobe Systems Incorporated Display PostScript Toolkit for X 15 April 1993 Adobe Systems Incorporated Adobe Developer Technologies 345 Park Avenue San Jose, CA 95110 http://partners.adobe.com/
Display PostScript System Adobe Systems Incorporated Display PostScript Toolkit for X 15 April 1993 Adobe Systems Incorporated Adobe Developer Technologies 345 Park Avenue San Jose, CA 95110 http://partners.adobe.com/
CS261: HOMEWORK 2 Due 04/13/2012, at 2pm
 CS261: HOMEWORK 2 Due 04/13/2012, at 2pm Submit six *.c files via the TEACH website: https://secure.engr.oregonstate.edu:8000/teach.php?type=want_auth 1. Introduction The purpose of HW2 is to help you
CS261: HOMEWORK 2 Due 04/13/2012, at 2pm Submit six *.c files via the TEACH website: https://secure.engr.oregonstate.edu:8000/teach.php?type=want_auth 1. Introduction The purpose of HW2 is to help you
Algorithms & Data Structures
 GATE- 2016-17 Postal Correspondence 1 Algorithms & Data Structures Computer Science & Information Technology (CS) 20 Rank under AIR 100 Postal Correspondence Examination Oriented Theory, Practice Set Key
GATE- 2016-17 Postal Correspondence 1 Algorithms & Data Structures Computer Science & Information Technology (CS) 20 Rank under AIR 100 Postal Correspondence Examination Oriented Theory, Practice Set Key
SpiNNaker Application Programming Interface (API)
 SpiNNaker Application Programming Interface (API) Version 2.0.0 10 March 2016 Application programming interface (API) Event-driven programming model The SpiNNaker API programming model is a simple, event-driven
SpiNNaker Application Programming Interface (API) Version 2.0.0 10 March 2016 Application programming interface (API) Event-driven programming model The SpiNNaker API programming model is a simple, event-driven
EL6483: Brief Overview of C Programming Language
 EL6483: Brief Overview of C Programming Language EL6483 Spring 2016 EL6483 EL6483: Brief Overview of C Programming Language Spring 2016 1 / 30 Preprocessor macros, Syntax for comments Macro definitions
EL6483: Brief Overview of C Programming Language EL6483 Spring 2016 EL6483 EL6483: Brief Overview of C Programming Language Spring 2016 1 / 30 Preprocessor macros, Syntax for comments Macro definitions
QUIZ. 1. Explain the meaning of the angle brackets in the declaration of v below:
 QUIZ 1. Explain the meaning of the angle brackets in the declaration of v below: This is a template, used for generic programming! QUIZ 2. Why is the vector class called a container? 3. Explain how the
QUIZ 1. Explain the meaning of the angle brackets in the declaration of v below: This is a template, used for generic programming! QUIZ 2. Why is the vector class called a container? 3. Explain how the
Converting a Lowercase Letter Character to Uppercase (Or Vice Versa)
 Looping Forward Through the Characters of a C String A lot of C string algorithms require looping forward through all of the characters of the string. We can use a for loop to do that. The first character
Looping Forward Through the Characters of a C String A lot of C string algorithms require looping forward through all of the characters of the string. We can use a for loop to do that. The first character
We do not teach programming
 We do not teach programming We do not teach C Take a course Read a book The C Programming Language, Kernighan, Richie Georgios Georgiadis Negin F.Nejad This is a brief tutorial on C s traps and pitfalls
We do not teach programming We do not teach C Take a course Read a book The C Programming Language, Kernighan, Richie Georgios Georgiadis Negin F.Nejad This is a brief tutorial on C s traps and pitfalls
Bits, Words, and Integers
 Computer Science 52 Bits, Words, and Integers Spring Semester, 2017 In this document, we look at how bits are organized into meaningful data. In particular, we will see the details of how integers are
Computer Science 52 Bits, Words, and Integers Spring Semester, 2017 In this document, we look at how bits are organized into meaningful data. In particular, we will see the details of how integers are
Contents. Chapter 1 Overview of the JavaScript C Engine...1. Chapter 2 JavaScript API Reference...23
 Contents Chapter 1 Overview of the JavaScript C Engine...1 Supported Versions of JavaScript...1 How Do You Use the Engine?...2 How Does the Engine Relate to Applications?...2 Building the Engine...6 What
Contents Chapter 1 Overview of the JavaScript C Engine...1 Supported Versions of JavaScript...1 How Do You Use the Engine?...2 How Does the Engine Relate to Applications?...2 Building the Engine...6 What
Basic Controls. Motif Programmer s Guide 1
 Basic Controls Controls are widgets and gadgets with which the user interacts directly. They form the leaves of the widget tree whose root is the application s top level shell. In most cases, controls
Basic Controls Controls are widgets and gadgets with which the user interacts directly. They form the leaves of the widget tree whose root is the application s top level shell. In most cases, controls
Characters, c-strings, and the string Class. CS 1: Problem Solving & Program Design Using C++
 Characters, c-strings, and the string Class CS 1: Problem Solving & Program Design Using C++ Objectives Perform character checks and conversions Knock down the C-string fundamentals Point at pointers and
Characters, c-strings, and the string Class CS 1: Problem Solving & Program Design Using C++ Objectives Perform character checks and conversions Knock down the C-string fundamentals Point at pointers and
Preprocessor Directives
 C++ By 6 EXAMPLE Preprocessor Directives As you might recall from Chapter 2, What Is a Program?, the C++ compiler routes your programs through a preprocessor before it compiles them. The preprocessor can
C++ By 6 EXAMPLE Preprocessor Directives As you might recall from Chapter 2, What Is a Program?, the C++ compiler routes your programs through a preprocessor before it compiles them. The preprocessor can
Kakadu and Java. David Taubman, UNSW June 3, 2003
 Kakadu and Java David Taubman, UNSW June 3, 2003 1 Brief Summary The Kakadu software framework is implemented in C++ using a fairly rigorous object oriented design strategy. All classes which are intended
Kakadu and Java David Taubman, UNSW June 3, 2003 1 Brief Summary The Kakadu software framework is implemented in C++ using a fairly rigorous object oriented design strategy. All classes which are intended
The X Selection Mechanism
 The X Selection Mechanism or How to Cut and Paste in 1000 lines or more Keith Packard X Consortium Laboratory for Computer Science Massachusetts Institute of Technology ABSTRACT While the existance of
The X Selection Mechanism or How to Cut and Paste in 1000 lines or more Keith Packard X Consortium Laboratory for Computer Science Massachusetts Institute of Technology ABSTRACT While the existance of
C Language, Token, Keywords, Constant, variable
 C Language, Token, Keywords, Constant, variable A language written by Brian Kernighan and Dennis Ritchie. This was to be the language that UNIX was written in to become the first "portable" language. C
C Language, Token, Keywords, Constant, variable A language written by Brian Kernighan and Dennis Ritchie. This was to be the language that UNIX was written in to become the first "portable" language. C
CS 385 Operating Systems Fall 2011 Homework Assignment 5 Process Synchronization and Communications
 CS 385 Operating Systems Fall 2011 Homework Assignment 5 Process Synchronization and Communications Due: Friday December 2 at 8:00 P.M. via Blackboard Overall Assignment Man Pages For this assignment,
CS 385 Operating Systems Fall 2011 Homework Assignment 5 Process Synchronization and Communications Due: Friday December 2 at 8:00 P.M. via Blackboard Overall Assignment Man Pages For this assignment,
A Fast Review of C Essentials Part I
 A Fast Review of C Essentials Part I Structural Programming by Z. Cihan TAYSI Outline Program development C Essentials Functions Variables & constants Names Formatting Comments Preprocessor Data types
A Fast Review of C Essentials Part I Structural Programming by Z. Cihan TAYSI Outline Program development C Essentials Functions Variables & constants Names Formatting Comments Preprocessor Data types
Xm Widget Classes. XmArrowButton. XmArrowButtonGadget. XmBulletinBoard. XmCascadeButton. XmCascadeButtonGadget. XmComboBox. XmCommand.
 Xm Widget Classes XmArrowButton XmArrowButtonGadget XmBulletinBoard XmCascadeButton XmCascadeButtonGadget XmComboBox XmCommand XmContainer XmDialogShell XmDisplay XmDragContext XmDragIcon XmDrawingArea
Xm Widget Classes XmArrowButton XmArrowButtonGadget XmBulletinBoard XmCascadeButton XmCascadeButtonGadget XmComboBox XmCommand XmContainer XmDialogShell XmDisplay XmDragContext XmDragIcon XmDrawingArea
P2: Collaborations. CSE 335, Spring 2009
 P2: Collaborations CSE 335, Spring 2009 Milestone #1 due by Thursday, March 19 at 11:59 p.m. Completed project due by Thursday, April 2 at 11:59 p.m. Objectives Develop an application with a graphical
P2: Collaborations CSE 335, Spring 2009 Milestone #1 due by Thursday, March 19 at 11:59 p.m. Completed project due by Thursday, April 2 at 11:59 p.m. Objectives Develop an application with a graphical
Tokens, Expressions and Control Structures
 3 Tokens, Expressions and Control Structures Tokens Keywords Identifiers Data types User-defined types Derived types Symbolic constants Declaration of variables Initialization Reference variables Type
3 Tokens, Expressions and Control Structures Tokens Keywords Identifiers Data types User-defined types Derived types Symbolic constants Declaration of variables Initialization Reference variables Type
Full file at
 Java Programming: From Problem Analysis to Program Design, 3 rd Edition 2-1 Chapter 2 Basic Elements of Java At a Glance Instructor s Manual Table of Contents Overview Objectives s Quick Quizzes Class
Java Programming: From Problem Analysis to Program Design, 3 rd Edition 2-1 Chapter 2 Basic Elements of Java At a Glance Instructor s Manual Table of Contents Overview Objectives s Quick Quizzes Class
Stanford University Computer Science Department CS 295 midterm. May 14, (45 points) (30 points) total
 Stanford University Computer Science Department CS 295 midterm May 14, 2008 This is an open-book exam. You have 75 minutes. Write all of your answers directly on the paper. Make your answers as concise
Stanford University Computer Science Department CS 295 midterm May 14, 2008 This is an open-book exam. You have 75 minutes. Write all of your answers directly on the paper. Make your answers as concise
Chapter 3: Operators, Expressions and Type Conversion
 101 Chapter 3 Operators, Expressions and Type Conversion Chapter 3: Operators, Expressions and Type Conversion Objectives To use basic arithmetic operators. To use increment and decrement operators. To
101 Chapter 3 Operators, Expressions and Type Conversion Chapter 3: Operators, Expressions and Type Conversion Objectives To use basic arithmetic operators. To use increment and decrement operators. To
Shapes leading to CAD system project
 EXERCISES Shapes leading to CAD system project Strings leading to distribution control project Tables leading to infinite precision arithmetic project Conversions leading to instrument control project
EXERCISES Shapes leading to CAD system project Strings leading to distribution control project Tables leading to infinite precision arithmetic project Conversions leading to instrument control project
Java Threads and intrinsic locks
 Java Threads and intrinsic locks 1. Java and OOP background fundamentals 1.1. Objects, methods and data One significant advantage of OOP (object oriented programming) is data encapsulation. Each object
Java Threads and intrinsic locks 1. Java and OOP background fundamentals 1.1. Objects, methods and data One significant advantage of OOP (object oriented programming) is data encapsulation. Each object
C OVERVIEW BASIC C PROGRAM STRUCTURE. C Overview. Basic C Program Structure
 C Overview Basic C Program Structure C OVERVIEW BASIC C PROGRAM STRUCTURE Goals The function main( )is found in every C program and is where every C program begins speed execution portability C uses braces
C Overview Basic C Program Structure C OVERVIEW BASIC C PROGRAM STRUCTURE Goals The function main( )is found in every C program and is where every C program begins speed execution portability C uses braces
Functions, Pointers, and the Basics of C++ Classes
 Functions, Pointers, and the Basics of C++ Classes William E. Skeith III Functions in C++ Vocabulary You should be familiar with all of the following terms already, but if not, you will be after today.
Functions, Pointers, and the Basics of C++ Classes William E. Skeith III Functions in C++ Vocabulary You should be familiar with all of the following terms already, but if not, you will be after today.
VueMetrix Firmware Uploader
 VueMetrix Firmware Uploader Release 1.0 Date of this document: August 20. 2010 The Firmware Uploader is a set of C language programming tools that uploads a new version of firmware into any VueMetrix controller.
VueMetrix Firmware Uploader Release 1.0 Date of this document: August 20. 2010 The Firmware Uploader is a set of C language programming tools that uploads a new version of firmware into any VueMetrix controller.
DECLARATIONS. Character Set, Keywords, Identifiers, Constants, Variables. Designed by Parul Khurana, LIECA.
 DECLARATIONS Character Set, Keywords, Identifiers, Constants, Variables Character Set C uses the uppercase letters A to Z. C uses the lowercase letters a to z. C uses digits 0 to 9. C uses certain Special
DECLARATIONS Character Set, Keywords, Identifiers, Constants, Variables Character Set C uses the uppercase letters A to Z. C uses the lowercase letters a to z. C uses digits 0 to 9. C uses certain Special
AET60 BioCARDKey. Application Programming Interface. Subject to change without prior notice
 AET60 BioCARDKey Application Programming Interface Subject to change without prior notice Table of Contents 1.0. Introduction... 3 2.0. Application Programming Interface... 4 2.1. Overview...4 2.2. Data
AET60 BioCARDKey Application Programming Interface Subject to change without prior notice Table of Contents 1.0. Introduction... 3 2.0. Application Programming Interface... 4 2.1. Overview...4 2.2. Data
Robust Programming. Style of programming that prevents abnormal termination and unexpected actions
 Robust Programming Style of programming that prevents abnormal termination and unexpected actions Code handles bad inputs reasonably Code assumes errors will occur and takes appropriate action Also called
Robust Programming Style of programming that prevents abnormal termination and unexpected actions Code handles bad inputs reasonably Code assumes errors will occur and takes appropriate action Also called
United States Naval Academy Electrical and Computer Engineering Department EC310-6 Week Midterm Spring AY2017
 United States Naval Academy Electrical and Computer Engineering Department EC310-6 Week Midterm Spring AY2017 1. Do a page check: you should have 8 pages including this cover sheet. 2. You have 50 minutes
United States Naval Academy Electrical and Computer Engineering Department EC310-6 Week Midterm Spring AY2017 1. Do a page check: you should have 8 pages including this cover sheet. 2. You have 50 minutes
C OVERVIEW. C Overview. Goals speed portability allow access to features of the architecture speed
 C Overview C OVERVIEW Goals speed portability allow access to features of the architecture speed C fast executables allows high-level structure without losing access to machine features many popular languages
C Overview C OVERVIEW Goals speed portability allow access to features of the architecture speed C fast executables allows high-level structure without losing access to machine features many popular languages
C How to Program, 6/e by Pearson Education, Inc. All Rights Reserved.
 C How to Program, 6/e 1992-2010 by Pearson Education, Inc. An important part of the solution to any problem is the presentation of the results. In this chapter, we discuss in depth the formatting features
C How to Program, 6/e 1992-2010 by Pearson Education, Inc. An important part of the solution to any problem is the presentation of the results. In this chapter, we discuss in depth the formatting features
ECE 2035 Programming HW/SW Systems Fall problems, 5 pages Exam Three 28 November 2012
 Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand and I will come to you. Please work the exam in pencil and do not separate
Instructions: This is a closed book, closed note exam. Calculators are not permitted. If you have a question, raise your hand and I will come to you. Please work the exam in pencil and do not separate
Lecture Notes on Memory Layout
 Lecture Notes on Memory Layout 15-122: Principles of Imperative Computation Frank Pfenning André Platzer Lecture 11 1 Introduction In order to understand how programs work, we can consider the functions,
Lecture Notes on Memory Layout 15-122: Principles of Imperative Computation Frank Pfenning André Platzer Lecture 11 1 Introduction In order to understand how programs work, we can consider the functions,
ITC213: STRUCTURED PROGRAMMING. Bhaskar Shrestha National College of Computer Studies Tribhuvan University
 ITC213: STRUCTURED PROGRAMMING Bhaskar Shrestha National College of Computer Studies Tribhuvan University Lecture 07: Data Input and Output Readings: Chapter 4 Input /Output Operations A program needs
ITC213: STRUCTURED PROGRAMMING Bhaskar Shrestha National College of Computer Studies Tribhuvan University Lecture 07: Data Input and Output Readings: Chapter 4 Input /Output Operations A program needs
B.V. Patel Institute of Business Management, Computer & Information Technology, Uka Tarsadia University
 Unit 1 Programming Language and Overview of C 1. State whether the following statements are true or false. a. Every line in a C program should end with a semicolon. b. In C language lowercase letters are
Unit 1 Programming Language and Overview of C 1. State whether the following statements are true or false. a. Every line in a C program should end with a semicolon. b. In C language lowercase letters are
CS Exam 1 Review Suggestions
 CS 235 - Fall 2015 - Exam 1 Review Suggestions p. 1 last modified: 2015-09-30 CS 235 - Exam 1 Review Suggestions You are responsible for material covered in class sessions, lab exercises, and homeworks;
CS 235 - Fall 2015 - Exam 1 Review Suggestions p. 1 last modified: 2015-09-30 CS 235 - Exam 1 Review Suggestions You are responsible for material covered in class sessions, lab exercises, and homeworks;
EL2310 Scientific Programming
 Lecture 11: Memory, Files and Bitoperations (yaseminb@kth.se) Overview Overview Lecture 11: Memory, Files and Bit operations Main function; reading and writing Bitwise Operations Lecture 11: Memory, Files
Lecture 11: Memory, Files and Bitoperations (yaseminb@kth.se) Overview Overview Lecture 11: Memory, Files and Bit operations Main function; reading and writing Bitwise Operations Lecture 11: Memory, Files
SYSC 2006 C Winter String Processing in C. D.L. Bailey, Systems and Computer Engineering, Carleton University
 SYSC 2006 C Winter 2012 String Processing in C D.L. Bailey, Systems and Computer Engineering, Carleton University References Hanly & Koffman, Chapter 9 Some examples adapted from code in The C Programming
SYSC 2006 C Winter 2012 String Processing in C D.L. Bailey, Systems and Computer Engineering, Carleton University References Hanly & Koffman, Chapter 9 Some examples adapted from code in The C Programming
,879 B FAT #1 FAT #2 root directory data. Figure 1: Disk layout for a 1.44 Mb DOS diskette. B is the boot sector.
 Homework 11 Spring 2012 File Systems: Part 2 MAT 4970 April 18, 2012 Background To complete this assignment, you need to know how directories and files are stored on a 1.44 Mb diskette, formatted for DOS/Windows.
Homework 11 Spring 2012 File Systems: Part 2 MAT 4970 April 18, 2012 Background To complete this assignment, you need to know how directories and files are stored on a 1.44 Mb diskette, formatted for DOS/Windows.
Writing TMS320C8x PP Code Under the Multitasking Executive
 TMS320 DSP DESIGNER S NOTEBOOK Writing TMS320C8x PP Code Under the Multitasking Executive APPLICATION BRIEF: SPRA269 Leor Brenman Digital Signal Processing Products Semiconductor Group Texas Instruments
TMS320 DSP DESIGNER S NOTEBOOK Writing TMS320C8x PP Code Under the Multitasking Executive APPLICATION BRIEF: SPRA269 Leor Brenman Digital Signal Processing Products Semiconductor Group Texas Instruments
CS 237 Meeting 19 10/24/12
 CS 237 Meeting 19 10/24/12 Announcements 1. Midterm: New date: Oct 29th. In class open book/notes. 2. Try to complete the linear feedback shift register lab in one sitting (and please put all the equipment
CS 237 Meeting 19 10/24/12 Announcements 1. Midterm: New date: Oct 29th. In class open book/notes. 2. Try to complete the linear feedback shift register lab in one sitting (and please put all the equipment
In the CERTAINTY project, an application is defined as a network of independent processes with the following features:
 C/C++ Coding Guide G. Giannopoulou, P. Huang, N. Stoimenov, L. Thiele April 15, 2014 This document describes how to program DOL-Critical applications using C/C++ as programming language. To be able to
C/C++ Coding Guide G. Giannopoulou, P. Huang, N. Stoimenov, L. Thiele April 15, 2014 This document describes how to program DOL-Critical applications using C/C++ as programming language. To be able to
C: How to Program. Week /Mar/05
 1 C: How to Program Week 2 2007/Mar/05 Chapter 2 - Introduction to C Programming 2 Outline 2.1 Introduction 2.2 A Simple C Program: Printing a Line of Text 2.3 Another Simple C Program: Adding Two Integers
1 C: How to Program Week 2 2007/Mar/05 Chapter 2 - Introduction to C Programming 2 Outline 2.1 Introduction 2.2 A Simple C Program: Printing a Line of Text 2.3 Another Simple C Program: Adding Two Integers
Programming Languages
 Programming Languages Tevfik Koşar Lecture - VIII February 9 th, 2006 1 Roadmap Allocation techniques Static Allocation Stack-based Allocation Heap-based Allocation Scope Rules Static Scopes Dynamic Scopes
Programming Languages Tevfik Koşar Lecture - VIII February 9 th, 2006 1 Roadmap Allocation techniques Static Allocation Stack-based Allocation Heap-based Allocation Scope Rules Static Scopes Dynamic Scopes
GNU dbm. A Database Manager. by Philip A. Nelson and Jason Downs. Manual by Pierre Gaumond, Philip A. Nelson and Jason Downs. Edition 1.
 GNU dbm A Database Manager by Philip A. Nelson and Jason Downs Manual by Pierre Gaumond, Philip A. Nelson and Jason Downs Edition 1.5 for GNU dbm, Version 1.8.3. Copyright c 1993-99 Free Software Foundation,
GNU dbm A Database Manager by Philip A. Nelson and Jason Downs Manual by Pierre Gaumond, Philip A. Nelson and Jason Downs Edition 1.5 for GNU dbm, Version 1.8.3. Copyright c 1993-99 Free Software Foundation,
6Using the Install and. Licensing APIs 6CHAPTER
 6CHAPTER 6Using the Install and Chapter Licensing APIs This chapter describes how to use the functions in the InterBase Install API as part of an application install. It includes the following topics:
6CHAPTER 6Using the Install and Chapter Licensing APIs This chapter describes how to use the functions in the InterBase Install API as part of an application install. It includes the following topics:
Computer Science & Information Technology (CS) Rank under AIR 100. Examination Oriented Theory, Practice Set Key concepts, Analysis & Summary
 GATE- 2016-17 Postal Correspondence 1 C-Programming Computer Science & Information Technology (CS) 20 Rank under AIR 100 Postal Correspondence Examination Oriented Theory, Practice Set Key concepts, Analysis
GATE- 2016-17 Postal Correspondence 1 C-Programming Computer Science & Information Technology (CS) 20 Rank under AIR 100 Postal Correspondence Examination Oriented Theory, Practice Set Key concepts, Analysis
Mid-term Exam. Fall Semester 2017 KAIST EE209 Programming Structures for Electrical Engineering. Name: Student ID:
 Fall Semester 2017 KAIST EE209 Programming Structures for Electrical Engineering Mid-term Exam Name: This exam is closed book and notes. Read the questions carefully and focus your answers on what has
Fall Semester 2017 KAIST EE209 Programming Structures for Electrical Engineering Mid-term Exam Name: This exam is closed book and notes. Read the questions carefully and focus your answers on what has
QUIZ. What are 3 differences between C and C++ const variables?
 QUIZ What are 3 differences between C and C++ const variables? Solution QUIZ Source: http://stackoverflow.com/questions/17349387/scope-of-macros-in-c Solution The C/C++ preprocessor substitutes mechanically,
QUIZ What are 3 differences between C and C++ const variables? Solution QUIZ Source: http://stackoverflow.com/questions/17349387/scope-of-macros-in-c Solution The C/C++ preprocessor substitutes mechanically,
Stack. 4. In Stack all Operations such as Insertion and Deletion are permitted at only one end. Size of the Stack 6. Maximum Value of Stack Top 5
 What is Stack? Stack 1. Stack is LIFO Structure [ Last in First Out ] 2. Stack is Ordered List of Elements of Same Type. 3. Stack is Linear List 4. In Stack all Operations such as Insertion and Deletion
What is Stack? Stack 1. Stack is LIFO Structure [ Last in First Out ] 2. Stack is Ordered List of Elements of Same Type. 3. Stack is Linear List 4. In Stack all Operations such as Insertion and Deletion
Week 3 Lecture 2. Types Constants and Variables
 Lecture 2 Types Constants and Variables Types Computers store bits: strings of 0s and 1s Types define how bits are interpreted They can be integers (whole numbers): 1, 2, 3 They can be characters 'a',
Lecture 2 Types Constants and Variables Types Computers store bits: strings of 0s and 1s Types define how bits are interpreted They can be integers (whole numbers): 1, 2, 3 They can be characters 'a',
FORM 2 (Please put your name and form # on the scantron!!!!) CS 161 Exam II:
 FORM 2 (Please put your name and form # on the scantron!!!!) CS 161 Exam II: True (A)/False(B) (2 pts each): 1. The declaration below declares three pointer variables of type pointer to double that is
FORM 2 (Please put your name and form # on the scantron!!!!) CS 161 Exam II: True (A)/False(B) (2 pts each): 1. The declaration below declares three pointer variables of type pointer to double that is
Programmer s Guide to the TBL Facility
 Programmer s Guide to the TBL Facility A Facility for Manipulating Tables in a Relational Database David E. Beecher Mallinckrodt Institute of Radiology Electronic Radiology Laboratory 510 South Kingshighway
Programmer s Guide to the TBL Facility A Facility for Manipulating Tables in a Relational Database David E. Beecher Mallinckrodt Institute of Radiology Electronic Radiology Laboratory 510 South Kingshighway
Name Definition Example Differences
 Big Integer Instantiation Don't create instances of already existing BigInteger (BigInteger.ZERO, BigInteger.ONE) andfor Java 1.5 onwards, BigInteger.TEN and BigDecimal (BigDecimal.ZERO, BigDecimal.ONE,
Big Integer Instantiation Don't create instances of already existing BigInteger (BigInteger.ZERO, BigInteger.ONE) andfor Java 1.5 onwards, BigInteger.TEN and BigDecimal (BigDecimal.ZERO, BigDecimal.ONE,
CS 103 Lab - Party Like A Char Star
 1 Introduction In this lab you will implement a "hangman" game where the user is shown blanks representing letter of a word and then tries to guess and fill in the letters with a limited number of guesses.
1 Introduction In this lab you will implement a "hangman" game where the user is shown blanks representing letter of a word and then tries to guess and fill in the letters with a limited number of guesses.
QUIZ. What is wrong with this code that uses default arguments?
 QUIZ What is wrong with this code that uses default arguments? Solution The value of the default argument should be placed in either declaration or definition, not both! QUIZ What is wrong with this code
QUIZ What is wrong with this code that uses default arguments? Solution The value of the default argument should be placed in either declaration or definition, not both! QUIZ What is wrong with this code
BLM2031 Structured Programming. Zeyneb KURT
 BLM2031 Structured Programming Zeyneb KURT 1 Contact Contact info office : D-219 e-mail zeynebkurt@gmail.com, zeyneb@ce.yildiz.edu.tr When to contact e-mail first, take an appointment What to expect help
BLM2031 Structured Programming Zeyneb KURT 1 Contact Contact info office : D-219 e-mail zeynebkurt@gmail.com, zeyneb@ce.yildiz.edu.tr When to contact e-mail first, take an appointment What to expect help
Practical Example of Tcl Command Design in a Qt/C++ Graphical Application. Tony Johnson Mentor Graphics, a Siemen s Company
 Practical Example of Tcl Command Design in a Qt/C++ Graphical Application Tony Johnson Mentor Graphics, a Siemen s Company tony_johnson@mentor.com Paper Motivation Why write this paper? Explain why creating
Practical Example of Tcl Command Design in a Qt/C++ Graphical Application Tony Johnson Mentor Graphics, a Siemen s Company tony_johnson@mentor.com Paper Motivation Why write this paper? Explain why creating
Memory Addressing, Binary, and Hexadecimal Review
 C++ By A EXAMPLE Memory Addressing, Binary, and Hexadecimal Review You do not have to understand the concepts in this appendix to become well-versed in C++. You can master C++, however, only if you spend
C++ By A EXAMPLE Memory Addressing, Binary, and Hexadecimal Review You do not have to understand the concepts in this appendix to become well-versed in C++. You can master C++, however, only if you spend
This resource describes how to program the myrio in C to perform timer interrupts.
 Resource 07 Timer interrupts This resource describes how to program the myrio in C to perform timer interrupts. C.07.1 Main thread: background Initializing the timer interrupt is similar to initializing
Resource 07 Timer interrupts This resource describes how to program the myrio in C to perform timer interrupts. C.07.1 Main thread: background Initializing the timer interrupt is similar to initializing
Libgdb. Version 0.3 Oct Thomas Lord
 Libgdb Version 0.3 Oct 1993 Thomas Lord Permission is granted to make and distribute verbatim copies of this manual provided the copyright notice and this permission notice are preserved on all copies.
Libgdb Version 0.3 Oct 1993 Thomas Lord Permission is granted to make and distribute verbatim copies of this manual provided the copyright notice and this permission notice are preserved on all copies.
C How to Program, 6/e by Pearson Education, Inc. All Rights Reserved.
 C How to Program, 6/e Storage of data in variables and arrays is temporary such data is lost when a program terminates. Files are used for permanent retention of data. Computers store files on secondary
C How to Program, 6/e Storage of data in variables and arrays is temporary such data is lost when a program terminates. Files are used for permanent retention of data. Computers store files on secondary
A3-R3: PROGRAMMING AND PROBLEM SOLVING THROUGH 'C' LANGUAGE
 A3-R3: PROGRAMMING AND PROBLEM SOLVING THROUGH 'C' LANGUAGE NOTE: 1. There are TWO PARTS in this Module/Paper. PART ONE contains FOUR questions and PART TWO contains FIVE questions. 2. PART ONE is to be
A3-R3: PROGRAMMING AND PROBLEM SOLVING THROUGH 'C' LANGUAGE NOTE: 1. There are TWO PARTS in this Module/Paper. PART ONE contains FOUR questions and PART TWO contains FIVE questions. 2. PART ONE is to be
Chapter 2 - Introduction to C Programming
 Chapter 2 - Introduction to C Programming 2 Outline 2.1 Introduction 2.2 A Simple C Program: Printing a Line of Text 2.3 Another Simple C Program: Adding Two Integers 2.4 Memory Concepts 2.5 Arithmetic
Chapter 2 - Introduction to C Programming 2 Outline 2.1 Introduction 2.2 A Simple C Program: Printing a Line of Text 2.3 Another Simple C Program: Adding Two Integers 2.4 Memory Concepts 2.5 Arithmetic
OSEK/VDX. Communication. Version January 29, 2003
 Open Systems and the Corresponding Interfaces for Automotive Electronics OSEK/VDX Communication Version 3.0.1 January 29, 2003 This document is an official release and replaces all previously distributed
Open Systems and the Corresponding Interfaces for Automotive Electronics OSEK/VDX Communication Version 3.0.1 January 29, 2003 This document is an official release and replaces all previously distributed
Creating a C++ Program
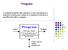 Program A computer program (also software, or just a program) is a sequence of instructions written in a sequence to perform a specified task with a computer. 1 Creating a C++ Program created using an
Program A computer program (also software, or just a program) is a sequence of instructions written in a sequence to perform a specified task with a computer. 1 Creating a C++ Program created using an
INTRODUCTION 1 AND REVIEW
 INTRODUTION 1 AND REVIEW hapter SYS-ED/ OMPUTER EDUATION TEHNIQUES, IN. Programming: Advanced Objectives You will learn: Program structure. Program statements. Datatypes. Pointers. Arrays. Structures.
INTRODUTION 1 AND REVIEW hapter SYS-ED/ OMPUTER EDUATION TEHNIQUES, IN. Programming: Advanced Objectives You will learn: Program structure. Program statements. Datatypes. Pointers. Arrays. Structures.
EMBEDDED SYSTEMS PROGRAMMING More About Languages
 EMBEDDED SYSTEMS PROGRAMMING 2015-16 More About Languages JAVA: ANNOTATIONS (1/2) Structured comments to source code (=metadata). They provide data about the code, but they are not part of the code itself
EMBEDDED SYSTEMS PROGRAMMING 2015-16 More About Languages JAVA: ANNOTATIONS (1/2) Structured comments to source code (=metadata). They provide data about the code, but they are not part of the code itself
Introduction to Programming Using Java (98-388)
 Introduction to Programming Using Java (98-388) Understand Java fundamentals Describe the use of main in a Java application Signature of main, why it is static; how to consume an instance of your own class;
Introduction to Programming Using Java (98-388) Understand Java fundamentals Describe the use of main in a Java application Signature of main, why it is static; how to consume an instance of your own class;
CSc Introduction to Computing
 CSc 10200 Introduction to Computing Lecture 2 Edgardo Molina Fall 2011 - City College of New York Thursday, September 1, 2011 Introduction to C++ Modular program: A program consisting of interrelated segments
CSc 10200 Introduction to Computing Lecture 2 Edgardo Molina Fall 2011 - City College of New York Thursday, September 1, 2011 Introduction to C++ Modular program: A program consisting of interrelated segments
Call DLL from Limnor Applications
 Call DLL from Limnor Applications There is a lot of computer software in the format of dynamic link libraries (DLL). DLLCaller performer allows your applications to call DLL functions directly. Here we
Call DLL from Limnor Applications There is a lot of computer software in the format of dynamic link libraries (DLL). DLLCaller performer allows your applications to call DLL functions directly. Here we
BBM 201 DATA STRUCTURES
 BBM 201 DATA STRUCTURES Lecture 8: Dynamically Allocated Linked Lists 2017-2018 Fall int x; x = 8; int A[4]; An array is stored as one contiguous block of memory. How can we add a fifth element to the
BBM 201 DATA STRUCTURES Lecture 8: Dynamically Allocated Linked Lists 2017-2018 Fall int x; x = 8; int A[4]; An array is stored as one contiguous block of memory. How can we add a fifth element to the
Lecture Notes on Interfaces
 Lecture Notes on Interfaces 15-122: Principles of Imperative Computation Frank Pfenning Lecture 14 October 16, 2012 1 Introduction The notion of an interface to an implementation of an abstract data type
Lecture Notes on Interfaces 15-122: Principles of Imperative Computation Frank Pfenning Lecture 14 October 16, 2012 1 Introduction The notion of an interface to an implementation of an abstract data type
Structure of a Program Using UIL and MRM
 Structure of a Program Using UIL and MRM The User Interface Language (UIL) allows an application developer to separate the specification of particular widget hierarchies from the application source code.
Structure of a Program Using UIL and MRM The User Interface Language (UIL) allows an application developer to separate the specification of particular widget hierarchies from the application source code.
16.216: ECE Application Programming Spring 2015 Exam 3 Solution
 16.216: ECE Application Programming Spring 2015 Exam 3 Solution 1. (20 points, 4 points per part) Multiple choice For each of the multiple choice questions below, clearly indicate your response by circling
16.216: ECE Application Programming Spring 2015 Exam 3 Solution 1. (20 points, 4 points per part) Multiple choice For each of the multiple choice questions below, clearly indicate your response by circling
Final assignment: Hash map
 Final assignment: Hash map 1 Introduction In this final assignment you will implement a hash map 1. A hash map is a data structure that associates a key with a value (a chunk of data). Most hash maps are
Final assignment: Hash map 1 Introduction In this final assignment you will implement a hash map 1. A hash map is a data structure that associates a key with a value (a chunk of data). Most hash maps are
Have examined process Creating program Have developed program Written in C Source code
 Preprocessing, Compiling, Assembling, and Linking Introduction In this lesson will examine Architecture of C program Introduce C preprocessor and preprocessor directives How to use preprocessor s directives
Preprocessing, Compiling, Assembling, and Linking Introduction In this lesson will examine Architecture of C program Introduce C preprocessor and preprocessor directives How to use preprocessor s directives
Binghamton University. CS-211 Fall Syntax. What the Compiler needs to understand your program
 Syntax What the Compiler needs to understand your program 1 Pre-Processing Any line that starts with # is a pre-processor directive Pre-processor consumes that entire line Possibly replacing it with other
Syntax What the Compiler needs to understand your program 1 Pre-Processing Any line that starts with # is a pre-processor directive Pre-processor consumes that entire line Possibly replacing it with other
Designing Interactive Systems II
 Designing Interactive Systems II Computer Science Graduate Program SS 2011 Prof. Dr. Jan Borchers Media Computing Group RWTH Aachen University http://hci.rwth-aachen.de/dis2 Jan Borchers 1 Review: WM,
Designing Interactive Systems II Computer Science Graduate Program SS 2011 Prof. Dr. Jan Borchers Media Computing Group RWTH Aachen University http://hci.rwth-aachen.de/dis2 Jan Borchers 1 Review: WM,
CS11001/CS11002 Programming and Data Structures (PDS) (Theory: 3-1-0) Allocating Space
 CS11001/CS11002 Programming and Data Structures (PDS) (Theory: 3-1-0) Allocating Space Dynamic Memory Allocation All variables, arrays, structures and unions that we worked with so far are statically allocated,
CS11001/CS11002 Programming and Data Structures (PDS) (Theory: 3-1-0) Allocating Space Dynamic Memory Allocation All variables, arrays, structures and unions that we worked with so far are statically allocated,
Type Checking. Prof. James L. Frankel Harvard University
 Type Checking Prof. James L. Frankel Harvard University Version of 7:10 PM 27-Feb-2018 Copyright 2018, 2016, 2015 James L. Frankel. All rights reserved. C Types C Types Type Category Type Category Type
Type Checking Prof. James L. Frankel Harvard University Version of 7:10 PM 27-Feb-2018 Copyright 2018, 2016, 2015 James L. Frankel. All rights reserved. C Types C Types Type Category Type Category Type
Chapter 1 Getting Started
 Chapter 1 Getting Started The C# class Just like all object oriented programming languages, C# supports the concept of a class. A class is a little like a data structure in that it aggregates different
Chapter 1 Getting Started The C# class Just like all object oriented programming languages, C# supports the concept of a class. A class is a little like a data structure in that it aggregates different
CYSE 411/AIT681 Secure Software Engineering Topic #12. Secure Coding: Formatted Output
 CYSE 411/AIT681 Secure Software Engineering Topic #12. Secure Coding: Formatted Output Instructor: Dr. Kun Sun 1 This lecture: [Seacord]: Chapter 6 Readings 2 Secure Coding String management Pointer Subterfuge
CYSE 411/AIT681 Secure Software Engineering Topic #12. Secure Coding: Formatted Output Instructor: Dr. Kun Sun 1 This lecture: [Seacord]: Chapter 6 Readings 2 Secure Coding String management Pointer Subterfuge
2/9/18. CYSE 411/AIT681 Secure Software Engineering. Readings. Secure Coding. This lecture: String management Pointer Subterfuge
 CYSE 411/AIT681 Secure Software Engineering Topic #12. Secure Coding: Formatted Output Instructor: Dr. Kun Sun 1 This lecture: [Seacord]: Chapter 6 Readings 2 String management Pointer Subterfuge Secure
CYSE 411/AIT681 Secure Software Engineering Topic #12. Secure Coding: Formatted Output Instructor: Dr. Kun Sun 1 This lecture: [Seacord]: Chapter 6 Readings 2 String management Pointer Subterfuge Secure
LSN 4 GUI Programming Using The WIN32 API
 LSN 4 GUI Programming Using The WIN32 API ECT362 Operating Systems Department of Engineering Technology LSN 4 Why program GUIs? This application will help introduce you to using the Win32 API Gain familiarity
LSN 4 GUI Programming Using The WIN32 API ECT362 Operating Systems Department of Engineering Technology LSN 4 Why program GUIs? This application will help introduce you to using the Win32 API Gain familiarity
Do not start the test until instructed to do so!
 Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other electronic devices
Instructions: Print your name in the space provided below. This examination is closed book and closed notes, aside from the permitted one-page formula sheet. No calculators or other electronic devices
The Dynamic Typing Interlude
 CHAPTER 6 The Dynamic Typing Interlude In the prior chapter, we began exploring Python s core object types in depth with a look at Python numbers. We ll resume our object type tour in the next chapter,
CHAPTER 6 The Dynamic Typing Interlude In the prior chapter, we began exploring Python s core object types in depth with a look at Python numbers. We ll resume our object type tour in the next chapter,
CSCI 171 Chapter Outlines
 Contents CSCI 171 Chapter 1 Overview... 2 CSCI 171 Chapter 2 Programming Components... 3 CSCI 171 Chapter 3 (Sections 1 4) Selection Structures... 5 CSCI 171 Chapter 3 (Sections 5 & 6) Iteration Structures
Contents CSCI 171 Chapter 1 Overview... 2 CSCI 171 Chapter 2 Programming Components... 3 CSCI 171 Chapter 3 (Sections 1 4) Selection Structures... 5 CSCI 171 Chapter 3 (Sections 5 & 6) Iteration Structures
CAN Module Documentation
 CAN Module Documentation Thomas Craig twc22 12/11/2009 Overview Purpose To provide a standard and robust C-language ARM7 software interface to the Controller Area Network (CAN) busses that form the main
CAN Module Documentation Thomas Craig twc22 12/11/2009 Overview Purpose To provide a standard and robust C-language ARM7 software interface to the Controller Area Network (CAN) busses that form the main
>B<82. 2Soft ware. C Language manual. Copyright COSMIC Software 1999, 2001 All rights reserved.
 >B
>B
Visual Profiler. User Guide
 Visual Profiler User Guide Version 3.0 Document No. 06-RM-1136 Revision: 4.B February 2008 Visual Profiler User Guide Table of contents Table of contents 1 Introduction................................................
Visual Profiler User Guide Version 3.0 Document No. 06-RM-1136 Revision: 4.B February 2008 Visual Profiler User Guide Table of contents Table of contents 1 Introduction................................................
