(12) Unlted States Patent (10) Patent N0.2 US 8,712,040 B2 Brothers (45) Date of Patent: Apr. 29, 2014
|
|
|
- Marybeth Elaine Short
- 6 years ago
- Views:
Transcription
1 USOO87140B2 (12) Unlted States Patent (10) Patent N0.2 Brothers (45) Date of Patent: Apr. 29, 14 (54) DATA-CONDITIONED ENCRYPTION 5,285,497 A 2/ 1994 Thatcher, Jr. METHOD 5,533,128 A 5,686,715 A 7/1996 Vobach 11/1997 Watanabe et a1. (76) Inventor: Harlan J. Brothers, East Haven, CT 5,727,062 5,838,796 A 3/1998 Ritter 11/1998 Mittenthal (Us) 5,902,929 A 5/1999 Okamoto et a1. 6,052,786 A 4/00 Tsuchida ( * ) Notice: Subject to any disclaimer, the term of this 6,097,812 A 8/00 Friedman patent is extended or adjusted under 35 I?uySter,, 1res U~S~C~ 1549 ) by 6 days~ 6,295,093 B1 9/01 Park et a1. 6,459,792 B2 * 10/02 Ohmori et a /37 (21) App1.No.: 13/012,534 6,507,678 B2 1/03 Yahagi 6,553,516 B1 * 4/03 Suda et a /702 (22) Filed; Jan_24,11 6,804,355 B1 10/04 Graunke 6,909,783 B2 6/05 Incarnato et a ,934,388 B1 8/05 Clark (65) Prlor Publlcatlon Data 7,006,629 B2 0% Murray Us 11/ A1 Aug ,026,964 B2 * 4/06 Baldwin et a /87 7,313,235 B2 12/07 Llang 7,529,365 B2 5/09 Lian Related US. Application Data 7,707,431 B2 4/10 Lian:.... 7,711,549 B2 5/10 F ' b t l. Provmonal application NO. on 06/ A1>1< 7/06 H 380/1 22, 10-06/ A1 * 12/06 Ananth.. 380/46 07/ A1* 5/07 Nave 380/ Int_C1_ 08/ A1 * 12/08 Hea /150 ( ) 09/ A1 * 2/09 Lablans 341/57 (52) gos4lbf/00 (0601) 09/ A1* 5/09 Tom /300 USPC /44; 713/150; 380/37; 380/46 * cited by examiner (58) Field of Classi?cation Search CPC..... G06F 9/30156; G06F 9/30178; H04L Prl f wy Exam? *Andrew Nalven _ 9/0894 ASSZSZIZI ZZ (74) Attorney, Examiner Agent, i or Firm * Ostrolenk Faber LLP USPC /44 See application?le for complete search history. (57) ABSTRACT A system and method for encryption of data is disclosed. At (56) References Cited least one block of the data is received. The at least one block U.S. PATENT DOCUMENTS 4,146,046 A 3/1979 Dobras 4,386,233 A 5/1983 Smid et a1. 4,516,246 A 5/1985 Kenemuth 5,054,067 A 10/1991 Moroney et al. of data is modi?ed to cause each unique data element Within the at least one block to appear With a respective predeter mined frequency ratio. The block of data is encrypted into ciphertext based at least on an encryption key. 21 Claims, 3 Drawing Sheets DHK (rm; 1-512) DHK (bits ) I Array pruoessor II HMS-element pre-key. J
2 US. Patent Apr. 29, 14 Sheet \ Diffie-Hellman Key (DHK) 2 LL ii a \ DHK (bits 1-512) DHK (bits ) / 4\ > /1_ 5 SHA-512 Mixen, SHA-512 / < 6 /LL bitstringpartition(8x128 bits) / Seed1 See (I) (D (D See Se ('3 N /1O i> Mixer 12 See 7%; Seed8 Array processor 1019-element pre-key, J FIGURE l
3 US. Patent Apr. 29, 14 Sheet 2 0f3 12 \ 1019-element pre-key, J,,\ U Generator sequence and matrix processor 14 \ Base matrix, M G(1'1)VG(1 2)I G(1,1019) 6(2'1),G(2'2)_ G(2,1019) G(3_1)IG(3,2)' G(3,1019) G(1Q1gl1),G(1019,2), G(1019,1019) 15 \ Shuffle matrix, S S1=G(#'1) G(# 2)_ G(#,1019) SZ=G(#,1),G(# 2)I G(#,1019) $3=G(#'1)IG(# 2)I G(#,1019) S1019=G(#I1),G(#'2), G(#,1019) 16 \ Array processor 1,\ Q 1019-element encryption key, E FIGURE 2
4 US. Patent Apr. 29, 14 Sheet 3 0f Encryption key, E Plaintext, P 2,, IL 3 1, Key manager Block encoder/processor 21 U U 22 Key sequence, K Array processor Blnary data, B / 23 LL 24 Ciphertext, c / FIGURE 3 17 Encryption key, E / ll \ Key manager < Ciphertext, C J L Q 26 \ b Decryption key sequence, K / Array processor / 24 " 22 Binary data, B / 27\ Block decoder/processor Q 19 Plaintext, P / FIGURE 4
5 1 DATA-CONDITIONED ENCRYPTION METHOD RELATED APPLICATION This application is based on and claims priority to US. Provisional Patent Application Ser. No. 61/297,722,?led on Jan. 22, 10 and entitled GRANULAR PERMUTATION CIPHER, the entire contents of which are hereby incorpo rated by reference. BACKGROUND 1. Field The present application relates, generally, to data encryp tion and, more particularly, to conditioning of data to be substantially immune to frequency analysis. 2. Description of the Prior Art In an age that depends on the private exchange of sensitive information, it is critical to have encryption methods that are fundamentally secure and relatively easy to implement. Such methods should also be reasonably immune from ever-in creasing computational power; brute force and nuanced cryp tanalysis have become relatively easy to apply. To combat these and other attacks, the key lengths have become longer, and encryption/decryption algorithms have become signi? cantly more complicated. Encryption methods date back to at least the time of the ancient Greeks, and now take a multitude of forms. The most robust modern approaches (e.g., Advanced Encryption Stan dard and Triple Data Encryption Standard) increase effective ness by combining basic methods, often including crypto graphic primitives such as hash functions and cryptographically secure pseudorandom number generators (s), into cryptographic systems. Indeed, given the often complicated combinations of techniques and operations comprising modern ciphers, it is sometimes dif?cult to cat egorize methods that combine fundamental algorithmic con cepts, such as those underlying block ciphers, stream ciphers, substitution, transposition, and permutation ciphers. It is generally accepted that there is an inverse relation between what is secure in a provable sense and what is secure from a practical standpoint. It is, therefore, a common goal in cryptography to?nd methods that can rigorously demonstrate security, while at the same time being practical to implement. It is also critical that such methods not rely on algorithmic secrecy, but rather remain open to inspection and evaluation. SUMMARY Accordingly, a system and method are provided for data encryption. In an embodiment, at least one computing device has instructions that, when executed, cause the at least one computing device to receive at least one block of the data, modify the at least one block of data to cause each unique data element within the at least one block to appear with a respec tive predetermined frequency ratio, and to encrypt the block of data into ciphertext based at least on an encryption key. In one or more embodiments, the at least one computing device may generate the encryption key or may receive the encryption key. Further, the encryption key may be generated based at least on a key exchange algorithm. Moreover, the at least one computing device may be con?gured to decrypt at least one other block of ciphertext and modify the decrypted ciphertext so that each unique data element of the decrypted ciphertext appears in the unique data element s ratio prior to being modi?ed with a respective predetermined frequency ratio. In one or more embodiments, the at least one block of data comprises a plurality of blocks of data, and further wherein the encryption key is different for at least one of the plurality of blocks of data. Further, in one or more embodiments, the at least one computing device has instructions that, when executed, cause the at least one computing device to derive the different encryption key from a respective one of the plurality of blocks of data. In one or more embodiments, the at least one computing device further receives instructions that, when executed, cause the at least one computing device to modify a character code associated with the data, wherein the respective prede termined frequency ratio is achieved by at least using the modi?ed character code. The at least one computing device may have further instructions that, when executed, cause the at least one computing device to receive the modi?ed char acter code. Moreover, the modi?ed character code may include a plurality of characters that contain a substantially same distribution of elements. In another embodiment, a system and method for encrypt ing data is provided that includes constructing at least one character code to cause each character in the at least one character code to have substantially a same distribution of elements. Further, the at least one character code is stored on at least one computing device, and the data are encoded with the stored at least one character code. Moreover, the encoded data are encrypted into ciphertext by the at least one comput ing device, based at least on one encryption key. Other features and advantages of the present application will become apparent from the following description, which refers to the accompanying drawings. BRIEF DESCRIPTION OF THE DRAWINGS For the purpose of illustration, there is shown in the draw ings an embodiment which is presently preferred; it being understood, however, that the teachings herein are not limited to the precise arrangements and instrumentalities shown. FIG. 1 is a block diagram showing the generation of a pre-key. FIG. 2 is a block diagram showing an example of an auto shuf?e algorithm that operates on the pre-key and outputs an encryption key. FIG. 3 illustrates the encryption of data. FIG. 4 illustrates the decryption of data. DETAILED DESCRIPTION OF THE PREFERRED EMBODIMENT The present application regards conditioning data to pro vide encryption methods that are substantially impervious to cryptanalytic attack, such as via frequency analysis. Referring to FIG. 1, an example method for encrypting data in accordance with the present application is described. A suitable key exchange algorithm, such as Dif?e-Hellman or ElGamal, is used to establish common key 1, which may be, for example, a 1024-bit common key for communication, referred to herein, generally, as DHK. In one or more embodiments, more than one DHK can be used per message. Key 1 is split into two halves (2 and 3) each of which is hashed using a Secure HashAlgorithm, such as SHA-512, SHA 4 and SHA 5 respectively. The hashes are then interleaved in mixer 6 such that each successive eight bits of SHA 4 are followed by the respective successive eight bits of SHA 5. The inter leaving process produces a 1024-bit string 7, which is then
6 3 partitioned into eight 128-bit seed values 8. Each seed value may be used to initialize a cryptographically strong pseudo random number generator ( ) module 9. Although the example shown in and described with refer ence to FIG. 1 regards use of eight independent s (or pseudo random number generators ( PRNGs ) in general), many other possible encryption methods for producing pseu dorandom sequences are envisioned and supported by the teachings herein. The actual choice of PRNG may depend, for example, on the speci?c application, platform, and environ ment in which the encryption takes place. For example, a single may be used to generate all eight pseudoran dom streams. Alternatively, multiple PRNGs of different designs may be employed. In an embodiment, eight pseudorandom streams are gen erated, each being composed of bit numbers, which may be integers or decimals. Continuing with reference to FIG. 1, the eight pseudoran dom streams from 9 are interleaved in mixer 10 such that each successive 32 bits, d, of the?rst stream are followed by the respective successive 32 bits of the second stream, of the third stream, and so on through to the eighth stream. Thereafter,?ve elements, d, are removed from this 1024-element array, L, by array processor 11. The removal may be accomplished in numerous suitable ways. In an embodiment that is based on an integer stream and beginning with d1, array processor 11 evaluates dl- (Mod 1024)+1 until?ve unique position pointers are found. Thereafter, the ele ments occupying the indicated positions are removed. In an alternate embodiment, the 9 simply outputs bit values, so that no elements require removal. To ensure a bijective encryption function (one with a unique inverse), the resulting 1019-element random array is then indexed from 1 to 1019 by array processor 11 to produce array, T: Thereafter, T is sorted on di and only the resulting sequence of indices are extracted. This yields an unpredictable and unknowable sequence of 1019 unique position pointers. This sequence is referred to herein, generally, as the pre-key, J 12. If the 9 is properly implemented and has not been compromised by an adversary, the non-linearity of the hash function ensures that, without knowing the exact value of DHK 1, it is highly unlikely that speci?c knowledge of J 12 will be determined. It is envisioned herein that the generation of J 12 is not limited to the precise methods or techniques with respect to the use of cryptographic primitives, described above. Many suitable alternative combinations and con?gurations are use able in accordance with the teachings herein. For example, I 12 may be generated using a Knuth-type shuf?e or a hard ware-based source of entropy and thereafter directly shared using a secure channel. Although I 12 may be used to directly shuf?e blocks of data, it is possible to incorporate more than one shuf?e algo rithm. If the block and pre-key lengths are a prime number, then the sequence of position pointers may be autoshuf?ed in a bijective fashion. As used herein, the term, autoshuf?e, refers generally to an algorithm that rearranges the order of a sequence in a non-linear manner and based on the content and number-theoretic characteristics of the sequence itself. More over, the encryption method described herein is also suitable for use with non-prime block and pre-key lengths. In cases of non-prime lengths, however, having fewer elements whose values are coprime to the sequence length is not as ef?cient and requires greater care in implementation. Depending on the speci?c design of the 9, autoshuf?ing J 12 helps to erase any statistical properties that might yield useful infor mation, such as in a cryptanalytic attack. FIG. 2 illustrates an example method for autoshuf?ing a key of prime length, 7». To start, generator sequence and matrix processor 13 constructs generator sequence Gl using an offset value 6 derived from J 12. To minimize any corre lation between the input and output of the auto shuf?e method, 6 is preferably not equal to 1, (7t+1)/2, 7t 1, or 7» itself. While there are many effective ways to choose a random value for e, the value in position 1 of] 12 (i.e., 11) may used as a pointer to locate the I1 1 element of J, though the value in any position, not just position 1, may be used. For example, using an 11 element array a:{4, 7, 1, 8, 9, 3, 11, 6, 5, 10, 2}, the?rst element al:4. Element 4 (a4) sets the value of 6 equal to eight (6:8). Ifthe Jl h elementis equal to 1, 510, 1018, or 1019, thenthe I 1th element is preferably used in lieu thereof. This process of examining subsequent elements may be repeated, as neces sary, in order to establish a value for e that is not equal to 1, 510, 1018, or To construct G1, generator sequence and matrix processor 13 preferably begins with the number 1. Successive ele ments are obtained by adding 6 to the current value and taking the result modulo For example, with 6:273, G1:{1,274,547,8,74,347,6,893,147,4,693,...,747}. Finally, the value 0 is replaced with the value Next, a base matrix M 14 is preferably generated by setting the?rst row to G1. Each successive row Gl- rotates the previ ous row one position to the left. Thus, for the present example, G2:{274,547,8,74,347,6,893,147,4,693,966,...,1}. The last row G1019 is equivalent to G1 rotated 1018 positions to the left, or in this example: G1019:{747,1,274,547,8,74,347,6,893,147,4,. Continuing with reference to FIG. 2, shuf?e matrix S 15 is then obtained by sorting the rows of base matrix M 14 on J 12. The hash mark # in the subscript of the rows SI. of shuf?e matrix S 15 indicates that the row position of each GUJ) is not?xed. Instead, the row position of each GUJ) from base matrix M 14 is determined by the process of transposing {1, M}, sorting the 1019 resulting pairs of the form {Integer, Array} on the integer part, and extracting only the sequence of arrays. Array processor 16 operates to shuf?e J 12 using the rows ofs 15 as follows. First, array processor 16 shuf?es Jusing Sl (row 1 of S), and then shuf?es the output of this operation on S2. Array processor 16 continues to shuf?e each output on the following row, SM. After 1019 shuf?e operations, the?nal output is encryption key E 17, which is an unpredictable and unknowable sequence of 1019 position pointers with stan dard statistical measures and?xed point distribution that are substantially indistinguishable from those of a true random permutation of 1019 elements. Although the example method shown in and described with reference to FIG. 2 includes the use of blocks (and respective keys) of length 1019, one skilled in the art will recognize that other lengths are supported. Prime lengths are useful speci? cally when implementing the preferred auto shuf?e method described herein. Smaller blocks reduce both the length the encryption key and the bit length of its constituent elements. Moreover, it is not necessary to use blocks having a?xed size. For example, use of a safe prime (e.g., 101 9) makes it trivial to employ a combination of block sizes of 1019 and 509 (i.e.,
7 5 a Sophie Germain prime) in which the size is determined either by the parity of the sequence of elements in J 12 or by the length of the data to be encrypted. It may further be desirable to adjust the size of blocks speci?cally to best match the length of the data to be encrypted. Continuing with reference to the example method in FIG. 2, E 17 is used to shuf?e data that has been frequency-condi tioned for encryption. The purpose of conditioning the data in this manner is to render the data substantially immune to a cryptanalytic attack that uses frequency analysis. By ensuring that each unique data element appears with a predetermined frequency ratio, the data are frequency-conditioned. In an example embodiment, given k unique elements, the ratio of the appearance of each k is set to substantially equal 1/k. Thus, for binary data in a permutation-based block cipher, the predetermined frequency ratios for the symbols 1 and 0 are 50% for each. If k is not a factor of the block length, the actual ratios may differ slightly from the ideal predetermined frequency ratios over the length of a block. In a preferred embodiment, the length of the conditioned data to be encrypted is a multiple of k. In accordance with the teachings herein, two basic methods for conditioning blocks of plaintext or data, herein referred to as P (19 FIG. 3), are envisioned. In an embodiment, frequency-conditioning is accom plished by a form of coding referred to herein, generally, as parity adjusted character code (PACC). As described in greater detail below, and with reference to Table 1A, Table 1B, and Table 2, a PACC is particularly useful to deter a frequency analysis attack. Table 1A shows Example 1 of a Parity Adjusted Character Code. Table 1B shows a mapping of extended characters for Example 1 of a Parity Adjusted Character Code. Table 2 shows Example 2 of a Parity Adjusted Character Code. Referring now to Table 1A and Table 1B, below, one example of PACC is provided. The foundation of PACC is relatively simple and can be implemented in a variety of different ways. PACC may be adapted to any language, including as set forth in Table 1, English. As withascii, each character is encoded by one byte of information (a Unicode style, 16-bit format or, alternatively, a custom length format may be employed). For example, given was the ordered set of values for one byte, Thereafter, all upper and lower case letters, all numbers, and the most common punctuation are assigned to the 8-bit numbers represented by w for which There are 70 (8C4) of these values. The 27 other printable ASCII characters may be carefully be assigned by dividing them between the two groups for which For example, if the code for the left bracket symbol [ contains a combination of 3 ones and 5 zeros, the code for the right bracket symbol ] would contain a combination of ones and 3 zeros. Because these symbols are most often used in pairs, this approach helps to preserve parity in a given block of data. TABLE 1A Bit Sum = 4 (Total: 70) Char Binary Dec space , A B C D E F G H I J K L A N' P Q R S T U' \ VV X Y Z a b d e f g h j k Hi n p q r s t u v w x y
8 I TABLE 1B TABLE 2-continued Char Binary Dec Bit Surn = 4 (Total: 70) 1 Bit Surn = 3 (Total: 14) Char Binary Dec 5 LF p ( q < r [ s { t # u $ v * x y / : ~ BHISun1= 5 (Ibtm:13) CR ) > ] } space ; = # \ " i, & ( ) Tables 1A and 1B show a sample character mapping for the * common English symbols. Of course, many other mapping (555? 12$ schemes are supported by the present application, any of Z whlch can be des1gned and chosen, for example, to max1m12e encoding language~ e?iciency for a given computing _ environment and 35 /; ? Table 2, below, shows an altemat1ve and more robust map- < ping that includes one byte for converting lowercase to upper- = case, and a second byte for mapping to an alternate character ? 13; set. Here, the CAP byte is used to convert lowercase letters to uppercase. Upon decoding, the conversion effectively sub- [ tracts 32 from the subsequent ASCII character code, thereby \ converting the lower case letter to a capital letter. The ALT )?) 5?: byte 1nd1cates that the subsequent byte(s) or block'(s) are to be mappedus1ng a d1fferent, predetermmed andposs1bly custom 45 } character set. Indeed, using this scheme, the ALT byte may be ~ employed to indicate the use of a different permutation of LP h d.. h. th tpacc t c arter-to-co e mapp1ngs W1t 1n e curren sys em. CR CAP TABLE2 w [\LT Bit Sum = 4 (Total; 70) By extension and in an alternate embodiment, any block can specify the precise permutation of charter-to-code map Char Binary Dec pings to be used within the established PACC. This may take a many forms such as: b ) an explicit assignment list; ) an ex licit ermutation list' d P P _ _ ) a seed value to be used 1n COHJUIICUOII W1th a f for rearranging the assignments using, for example, a Knuth % :12 60 typeshumewr i ) a precoded instruction sequence for how to reassign the j charter-to-code mappings for a given section of the plaintext k (e.g., parameters for performing an autoshuf?e) For example using only the?rst 5 entries in Table 2 n n o n1m b: c:
9 d: e: in an embodiment using an explicit assignment list, the?rst block of plaintext might begin { } indicating that the following charter-to-code assignments are being used: a: b: c: d: e: In the speci?c case of a binary-based PACC using an odd length code, there cannot be a precisely equal distribution of elements. For example, a 9-bit code contains either 5 ones and 4 zeros, or 4 ones and 5 zeros. Codes comprising a PACC contain the substantially same distribution of elements. Thus, and in accordance with an embodiment that uses this method, any alphanumeric character may be transformed into any other character by a simple permutation rule. Encrypting frequency-conditioned data in conjunction with the block permutation cipher, substantially as described above, is equivalently secure to the known and provably secure one time pad method. Unlike the one-time pad which requires the key to be a random string, the key employed according to the teaching herein is a random permutation. Similar to the case of a one-time pad, if the key is a truly random permutation, then, theoretically, any given ciphertext can be deciphered into any plaintext message of the same length. By extension, any word or message can be transformed into any other word or message of the same length, simply by rearranging its constituent ones and zeros. For example, the following two messages are both 18 characters (144 bits) in length (including spaces and punctuation): Message 1: Attack immediately Message 2: Quick, run away!!! Using the PACC shown in Table 1, 72 of the constituent bits for each message are ones and the other 72 are zeros. Either message can be bitwise rearranged and thereby transformed into the other. There are (72!)2, or approximately 3.7><107 different ways to map Message 1 to Message 2. Moreover, any 144-bit long ciphertext can be decrypted into either mes sage depending on what key is chosen by a potential adver sary. Other base representations other than base 2 may be used in accordance with the teachings herein. Ensuring all digits (or symbols) appear with substantially equal frequency, any such frequency conditioning technique can be employed in a man ner consistent with the present application. Moreover and in an alternative embodiment, character pro cessing methods other than PACC may be used in accordance with the teachings herein. For example, a compression algo rithm (e. g., gzip) may be used on plaintext prior to encryption. In this case, the compressed?le may be padded to achieve parity, as discussed below. A block length of 1019 bits can accommodate 1016 bits of 8-bit PACC encoded plaintext or up to 1019-bits of a general purpose parity-balanced ASCII or compressed?le. Thus, when employing 8-bit PACC, 508 of the bits should be con?gured in each block to be ones. Referring now to FIG. 3, block encoder/processor 18 serves to convert P 19 into PACC and appropriately pads blocks by employing the following method. In the case of blocks having variable lengths, block encoder/processor 18 also serves to partition P 19, appropriate to the speci?c imple mentation If plaintext message P 19 contains a fully frequency-bal anced encoding (e. g., the 70 primary PACC characters from Tables 1A and 1B, or the PACC encoding shown in Table 2), P 19 need only be padded to a multiple of 1016 bits using an equal number of ones and zeros (or [1019/n] bits for an n-bit PACC, where L 1 denotes the Floor function). In cases where the plaintext message or?le P 19 does not have a monobit frequency of 1/2 (e.g., ASCII or compressed formats), the length to which the message is to be padded to achieve parity is calculated. This value is referred to herein, generally, as the parity point, 6. When using 1018 bits of data and 1 bit of padding, once 6 is calculated and if 6<101 8, the data block is to padded to length 6 accordingly (with ones or zeros). Denoting the number of ones in a binary sequence by N1 and the number of zeros by NO, the remainder, r (where F1018 6), of the data block will be?lled such that NIINOIr/2. If 6>1018, block encoder/processor 18 calculates INl NO at each bit bl- in binary representation of plaintext P 19 to determine the value of i for which lnl NOI +i: In other words, this value indicates the bit for which the current count difference, when added to the current bit index exactly?lls a 1018-bit data block. Thus, the number of frequency-condi tioned plaintext bits that will appear in the?rst 1018 bits is given by i. The remainder r of the data block is then padded to parity. For example, for the 12-bit data block p:{ } that contains 7 ones and 5 zeros, 6:10, the bit at which there are 6 ones and 4 zeros. Here, at this point in the block, :12. The frequency-conditioned data block thus becomes { } with 6 ones and 6 zeros, and the last two data bits of p, {10} are carried to the start of the subsequent block. The same process of determining 6 and then padding accordingly is applied to the subsequent bits in the plaintext, thereby generating as many frequency-conditioned blocks as required to represent the full message or?le as a binary sequence with a monobit frequency of 1/2. Depending on the speci?c implementation, it may be appropriate to prepend each block with a header that encodes the parity point. In this case, the header can be encrypted by an XOR with a random string derived from the key establishment process (e. g., 1, 4, 9, 12). The header only has useful informational value after the ciphertext has been decoded. When using 8-bit PACC with 1019-bit blocks, three bits (e.g., {101}) must be added to the 127 byte frequency-con ditioned plaintext block before encrypting the frequency conditioned plaintext in order to have 1019 elements. For general purpose parity-balanced data, one bit is preferably added. Depending on the speci?c implementation, this bit may be either padding or an additional data bit. Although the above-described examples employ a block cipher technique, frequency-conditioning data in accordance with the teachings herein is not limited to use in block ciphers. Other encryption techniques such as stream cipher tech niques, may be used. For example, blocks may be of any arbitrary size, including the full length of the plaintext P 19, and the output of a may be XORed with a fre quency-conditioned block of data in a manner consistent with the teachings herein. After block encoder/processor 18 converts P 19 into a frequency-conditioned format and appropriately pads each block, key manager may use output from block encoder/ processor 18 to determine a length of the key sequence, such that each block may be encrypted with a unique key of the appropriate length. Said key sequence can be obtained by establishing a new DHK 1, via a secure channel or, altema
10 11 tively, by expanding the current key using various stages of key establishment. In a preferred embodiment, the key sequence for additional blocks can be derived from a fre quency-conditioned seed encrypted within a block of data. This seed may then be used in conjunction with a, in a manner similar to that described above and with reference to FIG. 1. In an example that includes bit blocks of data with the 8-bit PACC shown in Table 2, the?rst block may simply contain: {{560 bits explicit PACC assignments}, {459 bits seed} Subsequent blocks may then contain the plaintext message which has been encoded by block encoder/processor 18 with the designated PACC assignments and shuf?ed by the output of a initialized using the speci?ed seed. Generally, any block may substantially take the form of a collection of one or more substrings, such as in the example below: where the substrings v:control or instruction character(s) (e. g., ALT ) w:speci?cation of charter-to-code mappings x: seed y:data eradding may appear in a suitably arranged order and in multiple instances. One skilled in the art will recognize that data blocks may contain other suitable substrings, as well. Moreover, it is possible to generate new key material in numerous ways consistent with the teachings herein. Begin ning with E 17, key manager generates key sequence K 21. For a one block message, K will be equal to E (KIE). The binary data B 22 is encrypted by array processor 23 using K 21 in the following manner. For each block, an array Q is generated by attaching each element of K 21 to the corresponding bit bl. in B 22. Using the?rst block as an example, Sorting Q on K 21 shuf?es B 22 which, when extracted, yields ciphertext C 24. If F is the bijective function that applies K 21 to B 22, then F(B):C. Referring to FIG. 4, to decrypt C 24, an array, R, is gener ated by array processor which associates an index value with each element of K 21: Sorting R on K and extracting the shuf?ed indices produces the decryption key sequence, K' 26. Thereafter, an array, Q', is generated by attaching each element of K' to the corresponding bit cl- in C 24: Sorting Q' on K' unshuf?es C 24 which, when extracted, yields B 22. If F 1 is the inverse function that applies the decryption key K' to C, then F_1(C):B. Once B 22 is retrieved, block decoder/processor 27 strips any post data padding, and converts the remaining binary code is to plaintext P 19 consistent with the chosen method of data conditioning. Although the present application has been described in relation to particular embodiments thereof, many other varia tions and modi?cations and other uses will become apparent to those skilled in the art. It is preferred, therefore, that the present application be limited not by the speci?c disclosure herein, but only by the appended claims. What is claimed: 1. A system for data encryption, the system comprising: at least one computing device having instructions that, when executed by a data processor device, cause the at least one computing device: to receive at least one block of the data comprising kunique data elements; to modify the at least one block of data to cause each of the k unique data elements within the at least one block to appear with a respective predeter mined frequency ratio substantially equal to 1/k; wherein the modi?cation of the at least one block of data is performed according to a character code representing alphanumeric characters, such that each character is rep resented in the character code by a plurality of the unique data elements; and to encrypt the block of data into ciphertext based at least on an encryption key. 2. The system of claim 1, wherein the at least one comput ing device has further instructions that, when executed, cause the at least one computing device to generate the encryption key. 3. The system of claim 1, wherein the at least one comput ing device has further instructions that, when executed, cause the at least one computing device to receive the encryption key. 4. The system of claim 1, wherein the encryption key is generated based at least on a key exchange algorithm. 5. The system of claim 1, further comprising a decrypter con?gured to decrypt the block of ciphertext and to modify the decrypted ciphertext so that each unique data element of the decrypted ciphertext appears in the unique data element s ratio prior to being modi?ed to appear with the respective predetermined frequency ratio. 6. The system of claim 1, wherein the at least one block of data comprises a plurality of blocks of data, and further wherein the encryption key is different for at least one of the plurality of blocks of data. 7. The system of claim 6, wherein the at least one comput ing device has further instructions that, when executed, cause the at least one computing device to derive the different encryption key from a respective one of the plurality of blocks of data. 8. The system of claim 1, wherein at least one of the at least one block of data has a length equal to a prime number. 9. The system of claim 1, wherein each of the at least one block of data has a respective variable length. 10. The system of claim 1, wherein the modifying the at least one block comprises causing a plurality of data elements to appear with respective predetermined frequency ratios, and further wherein each of the respective predetermined fre quency ratios is substantially equal. 11. The system of claim 1, wherein the at least one com puting device further receives instructions that, when executed, cause the at least one computing device to modify a character code associated with the data, wherein the respective predetermined frequency ratio is achieved by at least using the modi?ed character code. 12. The system of claim 11, wherein the at least one com puting device has further instructions that, when executed, cause the at least one computing device to receive the modi?ed character code. 13. The system of claim 11, wherein the modi?ed character code includes a plurality of characters that contain a substan tially same distribution of elements.
11 The system of claim 11, wherein at least one of the at least one block of data contains one other modi?ed character code. 15. The system of claim 1, Wherein the at least one com puting device has further instructions that, When executed, cause the at least one computing device to pad each of the at least one block of data, Wherein the respective predetermined frequency ratio is achieved at least using the padding. 16. The system of claim 1, Wherein the at least one com puting device has further instructions that, When executed, cause the at least one computing device to rearrange positions of data elements in each of the at least one block of data, and further Wherein the encrypting comprises the rearranging. 17. The system of claim 1, Wherein the at least one com puting device has further instructions that, When executed, cause the at least one computing device to modify the encryp tion key based on at least one inherent property of the encryp tion key, Wherein the at least one inherent property comprises one or more of a number theoretic characteristic, an element value, and a key length. 18. A method for encrypting data, the method comprising: constructing at least one character code representing char acters, such that each character is represented in the at least one character code by a plurality of unique data elements, and each character includes a?rst unique data element having substantially a same frequency distribu tion in the character as every remaining unique data element of the plurality of unique data elements; storing the at least one character code on at least one computing device; encoding the data, by the at least one computing device, according to the stored at least one character code to generate encoded data; and encrypting the encoded data into ciphertext by the at least one computing device, based at least on one encryption key. 19. The method of claim 18, Wherein the encrypting includes rearranging the encoded data.. A method for data encryption by a computing device comprising a data processor, the method comprising: receiving, by at least one computing device, at least one block of the data comprising k unique data elements; modifying, by the at least one computing device, the at least one block of data to cause each of the k unique data elements Within the at least one block to appear With a respective predetermined frequency ratio substantially equal to 1/k; Wherein the modi?cation of the at least one block of data is performed according to a character code represent ing alphanumeric characters, such that each character is represented in the character code by a plurality of the unique data elements; and encrypting, by the at least one computing device, the block of data into ciphertext based at least on an encryption key. 21. The system of claim 1, Wherein each unique data ele ment is a bit and k:2. * * * * *
(12) United States Patent Scheidt et al.
 (12) United States Patent Scheidt et al. US006542608B2 (10) Patent N0.: (45) Date of Patent: *Apr. 1, 2003 (54) (75) (73) ( * ) (21) (22) (65) (62) (60) (51) (52) (58) CRYPTOGRAPHIC KEY SPLIT COMBINER
(12) United States Patent Scheidt et al. US006542608B2 (10) Patent N0.: (45) Date of Patent: *Apr. 1, 2003 (54) (75) (73) ( * ) (21) (22) (65) (62) (60) (51) (52) (58) CRYPTOGRAPHIC KEY SPLIT COMBINER
, 186; 708/250, 254,
 (12) United States Patent Scheidt et al. US006606386B2 () Patent N0.: (45) Date of Patent: Aug. 12, 2003 (54) CRYPTOGRAPHIC KEY SPLIT COMBINER (75) Inventors: Edward M. Scheidt, McLean, VA (US); C. Jay
(12) United States Patent Scheidt et al. US006606386B2 () Patent N0.: (45) Date of Patent: Aug. 12, 2003 (54) CRYPTOGRAPHIC KEY SPLIT COMBINER (75) Inventors: Edward M. Scheidt, McLean, VA (US); C. Jay
wo W /1997 * cited by examiner
 111111 1111111111111111111111111111111111111111111111111111111111111 US006963980Bl (12) United States Patent Matts son (10) Patent No.: US 6,963,980 Bl (45) Date of Patent: Nov. 8, 2005 (54) COMBINED HARDWARE
111111 1111111111111111111111111111111111111111111111111111111111111 US006963980Bl (12) United States Patent Matts son (10) Patent No.: US 6,963,980 Bl (45) Date of Patent: Nov. 8, 2005 (54) COMBINED HARDWARE
(12) United States Patent (10) Patent No.: US 8,536,920 B2 Shen
 l 1 L L IL L. I 1 L _ I L L L L US008536920B2 (12) United States Patent (10) Patent No.: US 8,536,920 B2 Shen (45) Date of Patent: Sep. 17, 2013 (54) CLOCK CIRCUIT WITH DELAY FUNCTIONS AND RELATED METHOD
l 1 L L IL L. I 1 L _ I L L L L US008536920B2 (12) United States Patent (10) Patent No.: US 8,536,920 B2 Shen (45) Date of Patent: Sep. 17, 2013 (54) CLOCK CIRCUIT WITH DELAY FUNCTIONS AND RELATED METHOD
(73) Assignee: Nokia Networks Oy (FI) Wii: 12: 'We (*) Notice: Subject to any disclaimer, the term of this * cited by examiner
 USOO6246871B1 12) United States Patent 10) Patent No.: US 6,246,871 B1 9 9 Ala-Laurila (45) Date of Patent: Jun. 12, 2001 (54) METHOD AND APPARATUS FOR 5,941,946 8/1999 Baldwin et al.. PROVIDING ACCESS
USOO6246871B1 12) United States Patent 10) Patent No.: US 6,246,871 B1 9 9 Ala-Laurila (45) Date of Patent: Jun. 12, 2001 (54) METHOD AND APPARATUS FOR 5,941,946 8/1999 Baldwin et al.. PROVIDING ACCESS
/ client computer. \ single sign-on. application program server (AP) network. server (SS0) (12) United States Patent Hsieh et a].
![/ client computer. \ single sign-on. application program server (AP) network. server (SS0) (12) United States Patent Hsieh et a]. / client computer. \ single sign-on. application program server (AP) network. server (SS0) (12) United States Patent Hsieh et a].](/thumbs/90/103929709.jpg) US007278155B2 (12) United States Patent Hsieh et a]. (10) Patent N0.: (45) Date of Patent: US 7,278,155 B2 Oct. 2, 2007 (54) (75) (73) (*) (21) (22) (65) (30) Foreign Application Priority Data Oct. 22,
US007278155B2 (12) United States Patent Hsieh et a]. (10) Patent N0.: (45) Date of Patent: US 7,278,155 B2 Oct. 2, 2007 (54) (75) (73) (*) (21) (22) (65) (30) Foreign Application Priority Data Oct. 22,
(12) Patent Application Publication (10) Pub. No.: US 2011/ A1
 (19) United States US 20110149932A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0149932 A1 KM et al. (43) Pub. Date: (54) ZIGBEE GATEWAY AND MESSAGE Publication Classification IDENTIFICATION
(19) United States US 20110149932A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0149932 A1 KM et al. (43) Pub. Date: (54) ZIGBEE GATEWAY AND MESSAGE Publication Classification IDENTIFICATION
(12) United States Patent (10) Patent N0.: US 6,446,174 B1 Dow (45) Date of Patent: Sep. 3, 2002
 US006446174B1 (12) United States Patent (10) Patent N0.: US 6,446,174 B1 Dow (45) Date of Patent: Sep. 3, 2002 (54) COMPUTER SYSTEM WITH DRAM BUS 5,969,728 A 10/1999 Dye et al...... 345/515 6,003,121 A
US006446174B1 (12) United States Patent (10) Patent N0.: US 6,446,174 B1 Dow (45) Date of Patent: Sep. 3, 2002 (54) COMPUTER SYSTEM WITH DRAM BUS 5,969,728 A 10/1999 Dye et al...... 345/515 6,003,121 A
(12) Patent Application Publication (10) Pub. No.: US 2004/ A1
 (19) United States US 2004O231004A1 (12) Patent Application Publication (10) Pub. No.: US 2004/0231004 A1 Seo (43) Pub. Date: (54) HTTP BASED VIDEO STREAMING APPARATUS AND METHOD IN MOBILE COMMUNICATION
(19) United States US 2004O231004A1 (12) Patent Application Publication (10) Pub. No.: US 2004/0231004 A1 Seo (43) Pub. Date: (54) HTTP BASED VIDEO STREAMING APPARATUS AND METHOD IN MOBILE COMMUNICATION
(12) United States Patent
 (12) United States Patent Ramaswamy USOO6480717B1 (10) Patent No.: (45) Date of Patent: Nov. 12, 2002 (54) (75) (73) (*) (21) (22) (51) (52) (58) (56) TUNNELING OF NON-GSM SIGNALNG MESSAGES IN A GSM BASED
(12) United States Patent Ramaswamy USOO6480717B1 (10) Patent No.: (45) Date of Patent: Nov. 12, 2002 (54) (75) (73) (*) (21) (22) (51) (52) (58) (56) TUNNELING OF NON-GSM SIGNALNG MESSAGES IN A GSM BASED
(12) United States Patent Cunningham et al.
 US007765264B2 (12) United States Patent Cunningham et al. (10) Patent N0.: (45) Date of Patent: Jul. 27, 2010 (54) SELECTION OF MODE ACCORDING TO MESSAGE CHARACTERISTICS (75) Inventors: Ivy F. Cunningham,
US007765264B2 (12) United States Patent Cunningham et al. (10) Patent N0.: (45) Date of Patent: Jul. 27, 2010 (54) SELECTION OF MODE ACCORDING TO MESSAGE CHARACTERISTICS (75) Inventors: Ivy F. Cunningham,
US 9,531,657 B2. 1 of 8. I lllll llllllll Ill lllll lllll lllll lllll lllll
 I lllll llllllll Ill lllll lllll lllll lllll lllll 111111111111111111111111111111111 US009531657B2 c12) United States Patent Ratnakar US 9,531,657 B2 (IO) Patent No.: (45) Date of Patent: *Dec. 27, 2016
I lllll llllllll Ill lllll lllll lllll lllll lllll 111111111111111111111111111111111 US009531657B2 c12) United States Patent Ratnakar US 9,531,657 B2 (IO) Patent No.: (45) Date of Patent: *Dec. 27, 2016
(12) United States Patent (10) Patent No.: US 6,199,058 B1
 USOO6199058B1 (12) United States Patent (10) Patent No.: US 6,199,058 B1 Wong et al. (45) Date of Patent: Mar. 6, 2001 (54) REPORT SERVER CACHING 5,168,444 12/1992 Cukor et al.... 705/1 5,625,818 4/1997
USOO6199058B1 (12) United States Patent (10) Patent No.: US 6,199,058 B1 Wong et al. (45) Date of Patent: Mar. 6, 2001 (54) REPORT SERVER CACHING 5,168,444 12/1992 Cukor et al.... 705/1 5,625,818 4/1997
(12) Patent Application Publication (10) Pub. No.: US 2006/ A1
 (19) United States US 20060O881 67A1 (12) Patent Application Publication (10) Pub. No.: US 2006/0088167 A1 Bade et al. (43) Pub. Date: Apr. 27, 2006 (54) METHOD AND SYSTEM FOR BACKUP AND RESTORE OF A CONTEXT
(19) United States US 20060O881 67A1 (12) Patent Application Publication (10) Pub. No.: US 2006/0088167 A1 Bade et al. (43) Pub. Date: Apr. 27, 2006 (54) METHOD AND SYSTEM FOR BACKUP AND RESTORE OF A CONTEXT
(12) United States Patent (10) Patent No.: US 7,002,560 B2
 USOO700256OB2 (12) United States Patent (10) Patent No.: US 7,002,560 B2 Graham (45) Date of Patent: Feb. 21, 2006 (54) METHOD OF COMBINING DATA ENTRY OF 6,049,329 A * 4/2000 Zetts et al.... 345/179 HANDWRITTEN
USOO700256OB2 (12) United States Patent (10) Patent No.: US 7,002,560 B2 Graham (45) Date of Patent: Feb. 21, 2006 (54) METHOD OF COMBINING DATA ENTRY OF 6,049,329 A * 4/2000 Zetts et al.... 345/179 HANDWRITTEN
(12) Patent Application Publication (10) Pub. No.: US 2016/ A1
 US 20160261583A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2016/0261583 A1 ZHANG (43) Pub. Date: Sep. 8, 2016 (54) METHOD AND APPARATUS FOR USER Publication Classification
US 20160261583A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2016/0261583 A1 ZHANG (43) Pub. Date: Sep. 8, 2016 (54) METHOD AND APPARATUS FOR USER Publication Classification
(12) Patent Application Publication (10) Pub. No.: US 2007/ A1
 (19) United States US 200700 10333A1 (12) Patent Application Publication (10) Pub. No.: US 2007/0010333 A1 Chiu et al. (43) Pub. Date: Jan. 11, 2007 (54) COMPUTER GAME DEVELOPMENT SYSTEMAND METHOD (75)
(19) United States US 200700 10333A1 (12) Patent Application Publication (10) Pub. No.: US 2007/0010333 A1 Chiu et al. (43) Pub. Date: Jan. 11, 2007 (54) COMPUTER GAME DEVELOPMENT SYSTEMAND METHOD (75)
(12) United States Patent
 USOO97296.58B2 (12) United States Patent Trahan et al. (10) Patent No.: (45) Date of Patent: Aug. 8, 2017 (54) SYSTEM FOR MANAGING WEB-BASED CONTENT DATA AND APPLICATIONS (76) Inventors: Chris Trahan,
USOO97296.58B2 (12) United States Patent Trahan et al. (10) Patent No.: (45) Date of Patent: Aug. 8, 2017 (54) SYSTEM FOR MANAGING WEB-BASED CONTENT DATA AND APPLICATIONS (76) Inventors: Chris Trahan,
(12) United States Patent
 US007107617B2 (12) United States Patent Hursey et al. (10) Patent No.: (45) Date of Patent: Sep. 12, 2006 (54) MALWARE SCANNING OF COMPRESSED COMPUTER S (75) Inventors: Nell John Hursey, Hertfordshire
US007107617B2 (12) United States Patent Hursey et al. (10) Patent No.: (45) Date of Patent: Sep. 12, 2006 (54) MALWARE SCANNING OF COMPRESSED COMPUTER S (75) Inventors: Nell John Hursey, Hertfordshire
(12) Patent Application Publication (10) Pub. No.: US 2008/ A1
 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2008/0317029 A1 TASAK et al. US 20080317029A1 (43) Pub. Date: Dec. 25, 2008 (54) (75) (73) (21) (22) (60) UNICAST/MULTICAST SYSTEM
(19) United States (12) Patent Application Publication (10) Pub. No.: US 2008/0317029 A1 TASAK et al. US 20080317029A1 (43) Pub. Date: Dec. 25, 2008 (54) (75) (73) (21) (22) (60) UNICAST/MULTICAST SYSTEM
(12) United States Patent (10) Patent No.: US 8,385,897 B1
 US0083.85897 B1 (12) United States Patent (10) Patent No.: Yadav-Ranjan (45) Date of Patent: Feb. 26, 2013 (54) GLOBAL TEXT MESSAGING SYSTEMAND (56) References Cited METHOD U.S. PATENT DOCUMENTS (75) Inventor:
US0083.85897 B1 (12) United States Patent (10) Patent No.: Yadav-Ranjan (45) Date of Patent: Feb. 26, 2013 (54) GLOBAL TEXT MESSAGING SYSTEMAND (56) References Cited METHOD U.S. PATENT DOCUMENTS (75) Inventor:
(12) United States Patent (10) Patent No.: US 6,408,074 B1
 USOO6408074B1 (12) United States Patent (10) Patent No.: LOughran (45) Date of Patent: Jun. 18, 2002 (54) HARDWARE ARCHITECTURE FOR A 4.914,697 A * 4/1990 Dabbish et al.... 380/28 CONFIGURABLE CIPHER DEVICE
USOO6408074B1 (12) United States Patent (10) Patent No.: LOughran (45) Date of Patent: Jun. 18, 2002 (54) HARDWARE ARCHITECTURE FOR A 4.914,697 A * 4/1990 Dabbish et al.... 380/28 CONFIGURABLE CIPHER DEVICE
US A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/ A1 Joshi et al. (43) Pub. Date: Nov.
 US 20090287845A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0287845 A1 Joshi et al. (43) Pub. Date: Nov. 19, 2009 (54) (75) (73) MEDIATOR WITH INTERLEAVED STATIC AND
US 20090287845A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0287845 A1 Joshi et al. (43) Pub. Date: Nov. 19, 2009 (54) (75) (73) MEDIATOR WITH INTERLEAVED STATIC AND
(12) Patent Application Publication (10) Pub. No.: US 2006/ A1. Choi et al. (43) Pub. Date: Apr. 27, 2006
 US 20060090088A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/0090088 A1 Choi et al. (43) Pub. Date: Apr. 27, 2006 (54) METHOD AND APPARATUS FOR Publication Classification
US 20060090088A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/0090088 A1 Choi et al. (43) Pub. Date: Apr. 27, 2006 (54) METHOD AND APPARATUS FOR Publication Classification
US A United States Patent (19) 11 Patent Number: 6,058,048 KWOn (45) Date of Patent: May 2, 2000
 US006058048A United States Patent (19) 11 Patent Number: 6,058,048 KWOn (45) Date of Patent: May 2, 2000 54) FLASH MEMORY DEVICE USED ASA 56) References Cited BOOT-UP MEMORY IN A COMPUTER SYSTEM U.S. PATENT
US006058048A United States Patent (19) 11 Patent Number: 6,058,048 KWOn (45) Date of Patent: May 2, 2000 54) FLASH MEMORY DEVICE USED ASA 56) References Cited BOOT-UP MEMORY IN A COMPUTER SYSTEM U.S. PATENT
(12) United States Patent (10) Patent No.: US 6,611,682 B1
 USOO661 1682B1 (12) United States Patent (10) Patent No.: Pröjtz (45) Date of Patent: Aug. 26, 2003 (54) MOBILE TELEPHONE APPARATUS AND 6,188.888 B1 * 2/2001 Bartle et al.... 455/417 METHOD FOR CALL DIVERT
USOO661 1682B1 (12) United States Patent (10) Patent No.: Pröjtz (45) Date of Patent: Aug. 26, 2003 (54) MOBILE TELEPHONE APPARATUS AND 6,188.888 B1 * 2/2001 Bartle et al.... 455/417 METHOD FOR CALL DIVERT
(12) United States Patent
 USOO9442667B2 (12) United States Patent Drosch (10) Patent No.: (45) Date of Patent: US 9.442,667 B2 Sep. 13, 2016 (54) (71) (72) (*) (21) (22) (86) (87) (65) (60) (30) (51) (52) APPARATUS AND METHOD FOR
USOO9442667B2 (12) United States Patent Drosch (10) Patent No.: (45) Date of Patent: US 9.442,667 B2 Sep. 13, 2016 (54) (71) (72) (*) (21) (22) (86) (87) (65) (60) (30) (51) (52) APPARATUS AND METHOD FOR
(12) United States Patent (10) Patent No.: US 7,739,050 B2
 USOO773905OB2 (12) United States Patent (10) Patent No.: US 7,739,050 B2 Tatro (45) Date of Patent: Jun. 15, 2010 (54) SOFTWARE-BASED QUALITY CONTROL (56) References Cited ANALYSIS OF WELL LOG DATA U.S.
USOO773905OB2 (12) United States Patent (10) Patent No.: US 7,739,050 B2 Tatro (45) Date of Patent: Jun. 15, 2010 (54) SOFTWARE-BASED QUALITY CONTROL (56) References Cited ANALYSIS OF WELL LOG DATA U.S.
(12) United States Patent
 US007617236B2 (12) United States Patent Gaurav et al. (10) Patent No.: (45) Date of Patent: Nov. 10, 2009 (54) METHOD AND SYSTEM FOR DISPLAYING RESULTS OF A DYNAMIC SEARCH (75) Inventors: Vishal Gaurav,
US007617236B2 (12) United States Patent Gaurav et al. (10) Patent No.: (45) Date of Patent: Nov. 10, 2009 (54) METHOD AND SYSTEM FOR DISPLAYING RESULTS OF A DYNAMIC SEARCH (75) Inventors: Vishal Gaurav,
(12) United States Patent
 (12) United States Patent US007 140922B2 (10) Patent No.: US 7,140,922 B2 Lulu et al. (45) Date of Patent: Nov. 28, 2006 (54) MULTI-OUTLET AC/DC ADAPTER (56) References Cited (75) Inventors: Daniel V.
(12) United States Patent US007 140922B2 (10) Patent No.: US 7,140,922 B2 Lulu et al. (45) Date of Patent: Nov. 28, 2006 (54) MULTI-OUTLET AC/DC ADAPTER (56) References Cited (75) Inventors: Daniel V.
(12) Patent Application Publication (10) Pub. No.: US 2012/ A1
 (19) United States US 201200O8852A1 (12) Patent Application Publication (10) Pub. No.: US 2012/0008852 A1 NU et al. (43) Pub. Date: Jan. 12, 2012 (54) SYSTEMAND METHOD OF ENHANCING Publication Classification
(19) United States US 201200O8852A1 (12) Patent Application Publication (10) Pub. No.: US 2012/0008852 A1 NU et al. (43) Pub. Date: Jan. 12, 2012 (54) SYSTEMAND METHOD OF ENHANCING Publication Classification
(12) United States Patent (10) Patent No.: US 7,640,289 B2
 USOO7640289B2 (12) United States Patent (10) Patent No.: Chen (45) Date of Patent: *Dec. 29, 2009 (54) INTELLIGENT COMPUTER SWITCH 6,388,658 B1 5/2002 Ahern et al. 6,567,869 B2 5/2003 Shirley (75) Inventor:
USOO7640289B2 (12) United States Patent (10) Patent No.: Chen (45) Date of Patent: *Dec. 29, 2009 (54) INTELLIGENT COMPUTER SWITCH 6,388,658 B1 5/2002 Ahern et al. 6,567,869 B2 5/2003 Shirley (75) Inventor:
(12) United States Patent
 USOO9729447B2 (12) United States Patent Wang et al. (10) Patent No.: (45) Date of Patent: US 9,729.447 B2 *Aug. 8, 2017 (54) APPARATUS AND METHOD FOR (71) (72) (73) (*) (21) (22) (65) (63) (60) (51) (52)
USOO9729447B2 (12) United States Patent Wang et al. (10) Patent No.: (45) Date of Patent: US 9,729.447 B2 *Aug. 8, 2017 (54) APPARATUS AND METHOD FOR (71) (72) (73) (*) (21) (22) (65) (63) (60) (51) (52)
(12) (10) Patent No.: US 7,103,736 B2. Sachs (45) Date of Patent: Sep. 5, 2006
 United States Patent US007103736B2 (12) (10) Patent No.: Sachs (45) Date of Patent: Sep. 5, 2006 (54) SYSTEM FOR REPAIR OF ROM 5.325,504 A * 6/1994 Tipley et al.... T11/128 PROGRAMMING ERRORS ORDEFECTS
United States Patent US007103736B2 (12) (10) Patent No.: Sachs (45) Date of Patent: Sep. 5, 2006 (54) SYSTEM FOR REPAIR OF ROM 5.325,504 A * 6/1994 Tipley et al.... T11/128 PROGRAMMING ERRORS ORDEFECTS
(12) United States Patent
 (12) United States Patent Matsuda USOO6211649B1 (10) Patent No.: (45) Date of Patent: Apr. 3, 2001 (54) USB CABLE AND METHOD FOR CHARGING BATTERY OF EXTERNAL APPARATUS BY USING USB CABLE (75) Inventor:
(12) United States Patent Matsuda USOO6211649B1 (10) Patent No.: (45) Date of Patent: Apr. 3, 2001 (54) USB CABLE AND METHOD FOR CHARGING BATTERY OF EXTERNAL APPARATUS BY USING USB CABLE (75) Inventor:
(12) (10) Patent N0.: US 6,879,518 B1. Curry (45) Date of Patent: Apr. 12, 2005
 United States Patent US006879518B1 (12) (10) Patent N0.: Curry (45) Date of Patent: Apr. 12, 2005 (54) EMBEDDED MEMORY WITH SECURITY 6,076,149 A * 6/2000 Usami et a1...... 711/163 ROW LOCK PROTECTION 6,088,262
United States Patent US006879518B1 (12) (10) Patent N0.: Curry (45) Date of Patent: Apr. 12, 2005 (54) EMBEDDED MEMORY WITH SECURITY 6,076,149 A * 6/2000 Usami et a1...... 711/163 ROW LOCK PROTECTION 6,088,262
(12) United States Patent
 (12) United States Patent USOO6941277B2 (10) Patent No.: Imag0 (45) Date of Patent: Sep. 6, 2005 (54) METHODS AND SYSTEMS FOR PROVIDING (56) References Cited ONLINE INFORMATION FOR NETWORKED DEVICES U.S.
(12) United States Patent USOO6941277B2 (10) Patent No.: Imag0 (45) Date of Patent: Sep. 6, 2005 (54) METHODS AND SYSTEMS FOR PROVIDING (56) References Cited ONLINE INFORMATION FOR NETWORKED DEVICES U.S.
mm m I1111(1)]!6l(l)lll7llltillllllllll mm m
![mm m I1111(1)]!6l(l)lll7llltillllllllll mm m mm m I1111(1)]!6l(l)lll7llltillllllllll mm m](/thumbs/87/95118329.jpg) United States Patent [19] Wisor et al. mm m I1111(1)]!6l(l)lll7llltillllllllll mm m [11] Patent Number: [45] Date of Patent: Feb., 1997 [541 [75] [21] [22] [63] [511 [52] [58] [56] SYSTEM MANAGEMENT INTERRUPT
United States Patent [19] Wisor et al. mm m I1111(1)]!6l(l)lll7llltillllllllll mm m [11] Patent Number: [45] Date of Patent: Feb., 1997 [541 [75] [21] [22] [63] [511 [52] [58] [56] SYSTEM MANAGEMENT INTERRUPT
(12) Patent Application Publication (10) Pub. No.: US 2011/ A1
 US 2011 O270691A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0270691 A1 Park (43) Pub. Date: Nov. 3, 2011 (54) METHOD AND SYSTEM FOR PROVIDING Publication Classification
US 2011 O270691A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0270691 A1 Park (43) Pub. Date: Nov. 3, 2011 (54) METHOD AND SYSTEM FOR PROVIDING Publication Classification
(12) Patent Application Publication (10) Pub. No.: US 2011/ A1
 (19) United States US 2011 0004845A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0004845 A1 Ciabarra (43) Pub. Date: Jan. 6, 2011 (54) METHOD AND SYSTEM FOR NOTIFYINGA USER OF AN EVENT OR
(19) United States US 2011 0004845A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0004845 A1 Ciabarra (43) Pub. Date: Jan. 6, 2011 (54) METHOD AND SYSTEM FOR NOTIFYINGA USER OF AN EVENT OR
(12) Unlted States Patent (10) Patent N0.: US 8,965,995 B2 Kuo (45) Date of Patent: Feb. 24, 2015
 USOO8965995B2 (12) Unlted States Patent (10) Patent N0.: US 8,965,995 B2 Kuo (45) Date of Patent: Feb. 24, 2015 (54) WIRELESS STORAGE MANAGEMENT (56) References Cited SYSTEM U.S. PATENT DOCUMENTS (75)
USOO8965995B2 (12) Unlted States Patent (10) Patent N0.: US 8,965,995 B2 Kuo (45) Date of Patent: Feb. 24, 2015 (54) WIRELESS STORAGE MANAGEMENT (56) References Cited SYSTEM U.S. PATENT DOCUMENTS (75)
(12) United States Patent (10) Patent No.: US 6,731,259 B2
 USOO6731259B2 (12) United States Patent (10) Patent No.: US 6,731,259 B2 Yer et al. (45) Date of Patent: May 4, 2004 (54) DRIVING CIRCUIT OF A LIQUID CRYSTAL 6,121.950 A * 9/2000 Zavracky et al.... 34.5/101
USOO6731259B2 (12) United States Patent (10) Patent No.: US 6,731,259 B2 Yer et al. (45) Date of Patent: May 4, 2004 (54) DRIVING CIRCUIT OF A LIQUID CRYSTAL 6,121.950 A * 9/2000 Zavracky et al.... 34.5/101
(12) United States Patent
 (12) United States Patent USOO8836702B2 (10) Patent No.: US 8,836,702 B2 Yoon et al. (45) Date of Patent: Sep. 16, 2014 (54) RAY TRACING CORE AND METHOD FOR (58) Field of Classification Search PROCESSING
(12) United States Patent USOO8836702B2 (10) Patent No.: US 8,836,702 B2 Yoon et al. (45) Date of Patent: Sep. 16, 2014 (54) RAY TRACING CORE AND METHOD FOR (58) Field of Classification Search PROCESSING
(12) Ulllted States Patent (10) Patent N0.: US 7,725,615 B1 Chester (45) Date of Patent: May 25, 2010
 US007725615B1 (12) Ulllted States Patent (10) Patent N0.: US 7,725,615 B1 Chester (45) Date of Patent: May 25, 2010 (54) UNIVERSAL NETWORK DRIVER 2002/0144242 A1* 10/2002 Owhadi..... 717/137 INTERFACE
US007725615B1 (12) Ulllted States Patent (10) Patent N0.: US 7,725,615 B1 Chester (45) Date of Patent: May 25, 2010 (54) UNIVERSAL NETWORK DRIVER 2002/0144242 A1* 10/2002 Owhadi..... 717/137 INTERFACE
(12) United States Patent (10) Patent No.: US 6,467,088 B1
 USOO6467088B1 (12) United States Patent (10) Patent No.: US 6,467,088 B1 alsafadi et al. (45) Date of Patent: Oct. 15, 2002 (54) RECONFIGURATION MANAGER FOR WO WO9015394 6/1990... GO6F/15/46 CONTROLLING
USOO6467088B1 (12) United States Patent (10) Patent No.: US 6,467,088 B1 alsafadi et al. (45) Date of Patent: Oct. 15, 2002 (54) RECONFIGURATION MANAGER FOR WO WO9015394 6/1990... GO6F/15/46 CONTROLLING
(12) United States Patent (10) Patent No.: US 8,253,777 B2
 US008253777B2 (12) United States Patent (10) Patent No.: US 8,253,777 B2 Lin (45) Date of Patent: Aug. 28, 2012 (54) PANORAMIC CAMERA WITH A PLURALITY 7,424,218 B2 * 9/2008 Baudisch et al.... 396,322 OF
US008253777B2 (12) United States Patent (10) Patent No.: US 8,253,777 B2 Lin (45) Date of Patent: Aug. 28, 2012 (54) PANORAMIC CAMERA WITH A PLURALITY 7,424,218 B2 * 9/2008 Baudisch et al.... 396,322 OF
US 7.663,338 B2. Feb. 16, (45) Date of Patent: (10) Patent No.: Guthrie et al. used to receive a USB bus voltage from the USB interface and (51)
 USOO7663338B2 (12) United States Patent Guthrie et al. (10) Patent No.: (45) Date of Patent: US 7.663,338 B2 Feb. 16, 2010 (54) (75) (73) (*) (21) (22) (65) (60) (51) (52) (58) (56) METHOD AND APPARATUS
USOO7663338B2 (12) United States Patent Guthrie et al. (10) Patent No.: (45) Date of Patent: US 7.663,338 B2 Feb. 16, 2010 (54) (75) (73) (*) (21) (22) (65) (60) (51) (52) (58) (56) METHOD AND APPARATUS
(12) United States Patent
 (12) United States Patent US006625752B1 (10) Patent N0.: US 6,625,752 B1 Kader et al. (45) Date of Patent: Sep. 23, 2003 (54) METHOD FOR IMPROVING SYSTEM 5,513,354 A * 4/1996 Dwork et a1...... 709/106
(12) United States Patent US006625752B1 (10) Patent N0.: US 6,625,752 B1 Kader et al. (45) Date of Patent: Sep. 23, 2003 (54) METHOD FOR IMPROVING SYSTEM 5,513,354 A * 4/1996 Dwork et a1...... 709/106
Medina (45) Date of Patent: Aug. 18, (54) FOOT CONTROLLED COMPUTER MOUSE 2004/ A1* 11/2004 Koda et al , 183
 (12) United States Patent US007576729B2 (10) Patent No.: Medina (45) Date of Patent: Aug. 18, 2009 (54) FOOT CONTROLLED COMPUTER MOUSE 2004/022.7741 A1* 11/2004 Koda et al.... 345, 183 WITH FINGER CLICKERS
(12) United States Patent US007576729B2 (10) Patent No.: Medina (45) Date of Patent: Aug. 18, 2009 (54) FOOT CONTROLLED COMPUTER MOUSE 2004/022.7741 A1* 11/2004 Koda et al.... 345, 183 WITH FINGER CLICKERS
(12) Patent Application Publication (10) Pub. No.: US 2005/ A1
 (19) United States US 20050281269A1 (12) Patent Application Publication (10) Pub. No.: US 2005/0281269 A1 Choi (43) Pub. Date: (54) MOBILE TELECOMMUNICATION SYSTEM (30) Foreign Application Priority Data
(19) United States US 20050281269A1 (12) Patent Application Publication (10) Pub. No.: US 2005/0281269 A1 Choi (43) Pub. Date: (54) MOBILE TELECOMMUNICATION SYSTEM (30) Foreign Application Priority Data
(12) Patent Application Publication (10) Pub. No.: US 2012/ A1
 (19) United States US 20120047545A1 (12) Patent Application Publication (10) Pub. No.: US 2012/0047545 A1 SELLERS et al. (43) Pub. Date: Feb. 23, 2012 (54) TOPOGRAPHIC FRAUD DETECTION (52) U.S. Cl....
(19) United States US 20120047545A1 (12) Patent Application Publication (10) Pub. No.: US 2012/0047545 A1 SELLERS et al. (43) Pub. Date: Feb. 23, 2012 (54) TOPOGRAPHIC FRAUD DETECTION (52) U.S. Cl....
(12) United States Patent
 (12) United States Patent Margalit et al. USOO6554621B1 (10) Patent No.: (45) Date of Patent: Apr. 29, 2003 (54) CABLE APPARATUS (75) Inventors: Yanki Margalit, Ramat Gan (IL); Dany Margalit, Ramat Gan
(12) United States Patent Margalit et al. USOO6554621B1 (10) Patent No.: (45) Date of Patent: Apr. 29, 2003 (54) CABLE APPARATUS (75) Inventors: Yanki Margalit, Ramat Gan (IL); Dany Margalit, Ramat Gan
United States Patent 19 Norris
 United States Patent 19 Norris 54 75 73 21 22 63 51 52 58 56 DYNAMIC PROCESSOR PERFORMANCE AND POWER MANAGEMENT INA COMPUTER SYSTEM Inventor: David Norris, Portland, Oreg. Assignee: Intel Corporation,
United States Patent 19 Norris 54 75 73 21 22 63 51 52 58 56 DYNAMIC PROCESSOR PERFORMANCE AND POWER MANAGEMENT INA COMPUTER SYSTEM Inventor: David Norris, Portland, Oreg. Assignee: Intel Corporation,
(12) United States Patent (10) Patent No.: US 7423,692 B2
 USOO7423692B2 (12) United States Patent (10) Patent No.: US 7423,692 B2 Chen (45) Date of Patent: Sep. 9, 2008 (54) DE-INTERLACE METHOD AND METHOD 6,930,729 B2 * 8/2005 Min... 348/607 FOR GENERATING DE-INTERLACE
USOO7423692B2 (12) United States Patent (10) Patent No.: US 7423,692 B2 Chen (45) Date of Patent: Sep. 9, 2008 (54) DE-INTERLACE METHOD AND METHOD 6,930,729 B2 * 8/2005 Min... 348/607 FOR GENERATING DE-INTERLACE
(12) United States Patent
 US0088.12887B2 (12) United States Patent Liu et al. (54) ELECTRONIC DISPLAY DEVICE AUTOMATICALLY TURNS ON OR OFF ACCORDING TO WHETHER AUSERN FRONT OF THE DISPLAY (75) Inventors: Xu Liu, Shanghai (CN);
US0088.12887B2 (12) United States Patent Liu et al. (54) ELECTRONIC DISPLAY DEVICE AUTOMATICALLY TURNS ON OR OFF ACCORDING TO WHETHER AUSERN FRONT OF THE DISPLAY (75) Inventors: Xu Liu, Shanghai (CN);
(12) Patent Application Publication (10) Pub. No.: US 2016/ A1
 (19) United States (12) Patent Application Publication (10) Pub. No.: CHEN et al. US 20160366367A1 (43) Pub. Date: Dec. 15, 2016 (54) (71) (72) (21) (22) FALLBACK IN FRAME RATE CONVERSION SYSTEM Applicant:
(19) United States (12) Patent Application Publication (10) Pub. No.: CHEN et al. US 20160366367A1 (43) Pub. Date: Dec. 15, 2016 (54) (71) (72) (21) (22) FALLBACK IN FRAME RATE CONVERSION SYSTEM Applicant:
(12) Patent Application Publication (10) Pub. No.: US 2015/ A1
 US 20150358424A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2015/0358424 A1 BRAUN et al. (43) Pub. Date: Dec. 10, 2015 (54) SYSTEMAND METHOD FOR PROVIDING (52) U.S. Cl. DATABASE
US 20150358424A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2015/0358424 A1 BRAUN et al. (43) Pub. Date: Dec. 10, 2015 (54) SYSTEMAND METHOD FOR PROVIDING (52) U.S. Cl. DATABASE
(12) Ulllted States Patent (10) Patent N0.: US 7,596,216 B2 Pearson et al. (45) Date of Patent: *Sep. 29, 2009
 US007596216B2 (12) Ulllted States Patent (10) Patent N0.: US 7,596,216 B2 Pearson et al. (45) Date of Patent: *Sep. 29, 2009 (54) SYSTEM AND METHOD FOR IDENTIFYING (51) Int. Cl. REDIRECTED CALLS H04M 3/42
US007596216B2 (12) Ulllted States Patent (10) Patent N0.: US 7,596,216 B2 Pearson et al. (45) Date of Patent: *Sep. 29, 2009 (54) SYSTEM AND METHOD FOR IDENTIFYING (51) Int. Cl. REDIRECTED CALLS H04M 3/42
(12) Patent Application Publication (10) Pub. No.: US 2010/ A1. Breiner et al. (43) Pub. Date: Mar. 4, 2010
 US 20100057686A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2010/0057686 A1 Breiner et al. (43) Pub. Date: Mar. 4, 2010 - (54) DEEP WEB SEARCH Publication Classification (76)
US 20100057686A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2010/0057686 A1 Breiner et al. (43) Pub. Date: Mar. 4, 2010 - (54) DEEP WEB SEARCH Publication Classification (76)
(12) United States Patent (10) Patent No.: US 8, B2. Cha et al. (45) Date of Patent: Oct. 8, 2013
 US008554.937B2 (12) United States Patent (10) Patent No.: US 8,554.937 B2 Cha et al. (45) Date of Patent: Oct. 8, 2013 (54) METHOD AND SYSTEM FOR 6,259,701 B1* 7/2001 Shur et al.... 370/401 6,836,806 B1*
US008554.937B2 (12) United States Patent (10) Patent No.: US 8,554.937 B2 Cha et al. (45) Date of Patent: Oct. 8, 2013 (54) METHOD AND SYSTEM FOR 6,259,701 B1* 7/2001 Shur et al.... 370/401 6,836,806 B1*
(12) United States Patent
 USOO7490248B1 (12) United States Patent Valfridsson et al. (10) Patent No.: (45) Date of Patent: US 7.490,248 B1 Feb. 10, 2009 (54) METHOD FOR REENCRYPTION OF A DATABASE (75) Inventors: Thomas Valfridsson,
USOO7490248B1 (12) United States Patent Valfridsson et al. (10) Patent No.: (45) Date of Patent: US 7.490,248 B1 Feb. 10, 2009 (54) METHOD FOR REENCRYPTION OF A DATABASE (75) Inventors: Thomas Valfridsson,
336w 330 FPGA / 330 MW} Compgnenf _/14 / 38 US 7,774,801 B1. Aug. 10, 2010 (56) (10) Patent N0.: (45) Date of Patent: (12) United States Patent Fitkin
 US007774801B1 (12) United States Patent Fitkin (10) Patent N0.: (45) Date of Patent: Aug. 10, 2010 (54) (75) (73) (21) (22) (51) (52) (58) (56) CORBA FIELD PROGRAMMABLE GATE ARRAY/DIGITAL SIGNAL PROCESSOR
US007774801B1 (12) United States Patent Fitkin (10) Patent N0.: (45) Date of Patent: Aug. 10, 2010 (54) (75) (73) (21) (22) (51) (52) (58) (56) CORBA FIELD PROGRAMMABLE GATE ARRAY/DIGITAL SIGNAL PROCESSOR
(12) United States Patent (10) Patent No.: US 6,931,133 B2
 USOO6931.133B2 (12) United States Patent (10) Patent No.: US 6,931,133 B2 Andrews et al. (45) Date of Patent: Aug. 16, 2005 (54) METHOD AND SYSTEM OF SECURELY 5,825,880 A * 10/1998 Sudia et al.... 713/18O
USOO6931.133B2 (12) United States Patent (10) Patent No.: US 6,931,133 B2 Andrews et al. (45) Date of Patent: Aug. 16, 2005 (54) METHOD AND SYSTEM OF SECURELY 5,825,880 A * 10/1998 Sudia et al.... 713/18O
(12) United States Patent (10) Patent No.: US 6,701,320 B1
 USOO670132OB1 (12) United States Patent (10) Patent No.: Marple () Date of Patent: Mar. 2, 2004 (54) SYSTEM AND METHOD FOR 6,539,118 B1 * 3/2003 Murray et al.... 382/229 DETERMINING A CHARACTER ENCODING
USOO670132OB1 (12) United States Patent (10) Patent No.: Marple () Date of Patent: Mar. 2, 2004 (54) SYSTEM AND METHOD FOR 6,539,118 B1 * 3/2003 Murray et al.... 382/229 DETERMINING A CHARACTER ENCODING
(12) Patent Application Publication (10) Pub. No.: US 2007/ A1
 (19) United States US 20070073878A1 (12) Patent Application Publication (10) Pub. No.: US 2007/0073878A1 Issa (43) Pub. Date: Mar. 29, 2007 (54) SYSTEM AND METHOD FOR LOWERING (52) U.S. Cl.... 709/225
(19) United States US 20070073878A1 (12) Patent Application Publication (10) Pub. No.: US 2007/0073878A1 Issa (43) Pub. Date: Mar. 29, 2007 (54) SYSTEM AND METHOD FOR LOWERING (52) U.S. Cl.... 709/225
(12) United States Patent (10) Patent No.: US 7, B2
 USOO7561411 B2 (12) United States Patent (10) Patent No.: US 7,561.411 B2 Johnson, Jr. (45) Date of Patent: Jul. 14, 2009 (54) UNINTERRUPTIBLE POWER DISTRIBUTION 7,400,066 B2 * 7/2008 Tassitino et al....
USOO7561411 B2 (12) United States Patent (10) Patent No.: US 7,561.411 B2 Johnson, Jr. (45) Date of Patent: Jul. 14, 2009 (54) UNINTERRUPTIBLE POWER DISTRIBUTION 7,400,066 B2 * 7/2008 Tassitino et al....
(12) Patent Application Publication (10) Pub. No.: US 2015/ A1. (51) Int. Cl. (52) U.S. Cl COMMUNICATIONS
 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2015/0036568 A1 HWANG US 2015.0036568A1 (43) Pub. Date: Feb. 5, 2015 (54) (71) (72) (73) (21) (22) (30) WIRELESS COMMUNICATIONSTERMINAL
(19) United States (12) Patent Application Publication (10) Pub. No.: US 2015/0036568 A1 HWANG US 2015.0036568A1 (43) Pub. Date: Feb. 5, 2015 (54) (71) (72) (73) (21) (22) (30) WIRELESS COMMUNICATIONSTERMINAL
(12) Patent Application Publication (10) Pub. No.: US 2011/ A1
 (19) United States US 2011 0231.630A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0231630 A1 Dannowski et al. (43) Pub. Date: Sep. 22, 2011 (54) ADDRESS MAPPING IN VIRTUALIZED (52) U.S.
(19) United States US 2011 0231.630A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0231630 A1 Dannowski et al. (43) Pub. Date: Sep. 22, 2011 (54) ADDRESS MAPPING IN VIRTUALIZED (52) U.S.
SCSI routing table (90) and a SCSI to Fibre Channel routing table (92). The system receives a cross bus transfer of data
 US00604.1381A United States Patent (19) 11 Patent Number: 6,041,381 Hoese (45) Date of Patent: Mar. 21, 2000 54 FIBRE CHANNEL TO SCSI ADDRESSING OTHER PUBLICATIONS METHOD AND SYSTEM Hoese, Geoffrey B.,
US00604.1381A United States Patent (19) 11 Patent Number: 6,041,381 Hoese (45) Date of Patent: Mar. 21, 2000 54 FIBRE CHANNEL TO SCSI ADDRESSING OTHER PUBLICATIONS METHOD AND SYSTEM Hoese, Geoffrey B.,
(12) Patent Application Publication (10) Pub. No.: US 2012/ A1. Hsu et al. (43) Pub. Date: Jan. 26, 2012
 US 20120023517A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0023517 A1 Hsu et al. (43) Pub. Date: Jan. 26, 2012 (54) METHOD AND SYSTEM FOR MEASURING AN INTERNET PROTOCOL
US 20120023517A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0023517 A1 Hsu et al. (43) Pub. Date: Jan. 26, 2012 (54) METHOD AND SYSTEM FOR MEASURING AN INTERNET PROTOCOL
(12) (10) Patent No.: US 7, B2. Peng (45) Date of Patent: Mar. 20, 2007
 United States Patent US007194291B2 (12) (10) Patent No.: US 7,194.291 B2 Peng (45) Date of Patent: Mar. 20, 2007 (54) PROTECTIVE MASK OF MOBILE PHONE 6,591,088 B1* 7/2003 Watanabe... 455/90.3 6,594,472
United States Patent US007194291B2 (12) (10) Patent No.: US 7,194.291 B2 Peng (45) Date of Patent: Mar. 20, 2007 (54) PROTECTIVE MASK OF MOBILE PHONE 6,591,088 B1* 7/2003 Watanabe... 455/90.3 6,594,472
Printer. Data input/ Printout unit. processor) Control unit. (Raster image RIP. Display unit. Image
 (19) United States US 20070057978A1 (12) Patent Application Publication (10) Pub. No.: US 2007/0057978A1 Hagiwara (43) Pub. Date: Mar. 15, 2007 (54) PRINTER AND PRINTING METHOD (75) Inventor: Takahiro
(19) United States US 20070057978A1 (12) Patent Application Publication (10) Pub. No.: US 2007/0057978A1 Hagiwara (43) Pub. Date: Mar. 15, 2007 (54) PRINTER AND PRINTING METHOD (75) Inventor: Takahiro
(12) Patent Application Publication (10) Pub. No.: US 2006/ A1. Zhou et al. (43) Pub. Date: Jun. 29, 2006
 US 2006O1394.94A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/01394.94 A1 Zhou et al. (43) Pub. Date: Jun. 29, 2006 (54) METHOD OF TEMPORAL NOISE (52) U.S. Cl.... 348/607;
US 2006O1394.94A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/01394.94 A1 Zhou et al. (43) Pub. Date: Jun. 29, 2006 (54) METHOD OF TEMPORAL NOISE (52) U.S. Cl.... 348/607;
$26) 6, 2. (12) Patent Application Publication (10) Pub. No.: US 2013/ A1. (19) United States Chien (43) Pub. Date: Jun.
 (19) United States US 2013 0147960A1 (12) Patent Application Publication (10) Pub. No.: US 2013/0147960 A1 Chien (43) Pub. Date: Jun. 13, 2013 (54) PLUG AND PLAYNETWORKSYSTEM, PLUG AND PLAYNETWORKVIDEO
(19) United States US 2013 0147960A1 (12) Patent Application Publication (10) Pub. No.: US 2013/0147960 A1 Chien (43) Pub. Date: Jun. 13, 2013 (54) PLUG AND PLAYNETWORKSYSTEM, PLUG AND PLAYNETWORKVIDEO
Wireless devices supports in a simple environment
 USOO8868690B2 (12) United States Patent (10) Patent No.: US 8,868,690 B2 Tsao (45) Date of Patent: *Oct. 21, 2014 (54) SYSTEMAND METHOD FOR SUPPORT (52) U.S. Cl. (71) (72) (73) (*) (21) (22) (65) (63)
USOO8868690B2 (12) United States Patent (10) Patent No.: US 8,868,690 B2 Tsao (45) Date of Patent: *Oct. 21, 2014 (54) SYSTEMAND METHOD FOR SUPPORT (52) U.S. Cl. (71) (72) (73) (*) (21) (22) (65) (63)
(12) United States Patent (10) Patent No.: US 6,199,163 B1
 USOO6199163B1 (12) United States Patent (10) Patent No.: US 6,199,163 B1 Dumas et al. 45) Date of Patent: Mar. 6, 2001 9 (54) HARD DISK PASSWORD LOCK 5,231,662 * 7/1993 van Rumpt et al.... 380/9 5,283,828
USOO6199163B1 (12) United States Patent (10) Patent No.: US 6,199,163 B1 Dumas et al. 45) Date of Patent: Mar. 6, 2001 9 (54) HARD DISK PASSWORD LOCK 5,231,662 * 7/1993 van Rumpt et al.... 380/9 5,283,828
US A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2015/ A1 HUI (43) Pub. Date: Mar.
 US 20150067353A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2015/0067353 A1 HUI (43) Pub. Date: Mar. 5, 2015 (54) STORAGE MANAGEMENT DEVICE AND (52) US. Cl. STORAGE MANAGEMENT
US 20150067353A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2015/0067353 A1 HUI (43) Pub. Date: Mar. 5, 2015 (54) STORAGE MANAGEMENT DEVICE AND (52) US. Cl. STORAGE MANAGEMENT
6,000,859 Dec. 14, 1999
 United States Patent [19] Mulcahy et al. US006000859A [11] Patent Number: [45] Date of Patent: 6,000,859 Dec. 14, 1999 [54] CAMERA AND FLASH UNIT POSITIONING DEVICE [76] Inventors: Timothy G. Mulcahy,
United States Patent [19] Mulcahy et al. US006000859A [11] Patent Number: [45] Date of Patent: 6,000,859 Dec. 14, 1999 [54] CAMERA AND FLASH UNIT POSITIONING DEVICE [76] Inventors: Timothy G. Mulcahy,
(12) United States Patent (10) Patent No.: US 7,917,832 B2
 US007.917832B2 (12) United States Patent (10) Patent No.: US 7,917,832 B2 Hsieh et al. (45) Date of Patent: Mar. 29, 2011 (54) APPARATUS FOR IMPROVING DATA 6,725,321 B1 4/2004 Sinclair et al.... T11 103
US007.917832B2 (12) United States Patent (10) Patent No.: US 7,917,832 B2 Hsieh et al. (45) Date of Patent: Mar. 29, 2011 (54) APPARATUS FOR IMPROVING DATA 6,725,321 B1 4/2004 Sinclair et al.... T11 103
58 Field of Search ,154.15s, a housing adapted to be affixed to the interior of the mailbox,
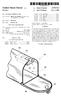 USOO5975713A United States Patent (19) 11 Patent Number: 5,975,713 Brothers (45) Date of Patent: Nov. 2, 1999 54 INTERIOR MAILBOX LIGHT 2,411,100 11/1946 MacDonald... 362/155 2,772,349 11/1956 Chamberlin......
USOO5975713A United States Patent (19) 11 Patent Number: 5,975,713 Brothers (45) Date of Patent: Nov. 2, 1999 54 INTERIOR MAILBOX LIGHT 2,411,100 11/1946 MacDonald... 362/155 2,772,349 11/1956 Chamberlin......
(12) Patent Application Publication (10) Pub. No.: US 2002/ A1
 (19) United States US 2002009 1840A1 (12) Patent Application Publication (10) Pub. No.: US 2002/0091840 A1 Pulier et al. (43) Pub. Date: Jul. 11, 2002 (54) REAL-TIME OPTIMIZATION OF STREAMING MEDIA FROM
(19) United States US 2002009 1840A1 (12) Patent Application Publication (10) Pub. No.: US 2002/0091840 A1 Pulier et al. (43) Pub. Date: Jul. 11, 2002 (54) REAL-TIME OPTIMIZATION OF STREAMING MEDIA FROM
PERFORM R ~/~104
 US 20100088018A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2010/0088018 A1 Tsurutome et al. (43) Pub. Date: Apr. 8, 2010 (54) (76) (21) (22) (60) GLANCE AHEAD NAVIGATION
US 20100088018A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2010/0088018 A1 Tsurutome et al. (43) Pub. Date: Apr. 8, 2010 (54) (76) (21) (22) (60) GLANCE AHEAD NAVIGATION
III. United States Patent Patent Number: 5,748,253. Chatinsky et al. (45) Date of Patent: May 5, 1998
 III USO05748253A United States Patent 19 11 Patent Number: 5,748,253 Chatinsky et al. (45) Date of Patent: May 5, 1998 54 DIRECT KEYBOARD ACCESS TO WIDEO 5,001,473 3/1991 Ritter et al.... 340/825.52 EDTING
III USO05748253A United States Patent 19 11 Patent Number: 5,748,253 Chatinsky et al. (45) Date of Patent: May 5, 1998 54 DIRECT KEYBOARD ACCESS TO WIDEO 5,001,473 3/1991 Ritter et al.... 340/825.52 EDTING
(12) United States Patent (10) Patent No.: US 9,198,206 B2
 US009 1982O6B2 (12) United States Patent () Patent No.: US 9,198,206 B2 Li et al. (45) Date of Patent: Nov. 24, 2015 (54) AUTOMATIC CONNECTION METHOD AND (56) References Cited APPARATUS BETWEEN AN AUTOMOBILE
US009 1982O6B2 (12) United States Patent () Patent No.: US 9,198,206 B2 Li et al. (45) Date of Patent: Nov. 24, 2015 (54) AUTOMATIC CONNECTION METHOD AND (56) References Cited APPARATUS BETWEEN AN AUTOMOBILE
(12) United States Patent (10) Patent No.: US 9,399,323 B1
 US0093.99323B1 (12) United States Patent (10) Patent No.: Lu et al. (45) Date of Patent: Jul. 26, 2016 (54) THREE-DIMENSIONAL PRINTING USPC... 425/470; 264/401, 497, 212, 308 STRUCTURE See application
US0093.99323B1 (12) United States Patent (10) Patent No.: Lu et al. (45) Date of Patent: Jul. 26, 2016 (54) THREE-DIMENSIONAL PRINTING USPC... 425/470; 264/401, 497, 212, 308 STRUCTURE See application
Secret Key Cryptography
 Secret Key Cryptography 1 Block Cipher Scheme Encrypt Plaintext block of length N Decrypt Secret key Cipher block of length N 2 Generic Block Encryption Convert a plaintext block into an encrypted block:
Secret Key Cryptography 1 Block Cipher Scheme Encrypt Plaintext block of length N Decrypt Secret key Cipher block of length N 2 Generic Block Encryption Convert a plaintext block into an encrypted block:
(12) Patent Application Publication (10) Pub. No.: US 2006/ A1
 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/0152762 A1 Asano et al. US 2006O152762A1 (43) Pub. Date: Jul. 13, 2006 (54) (75) (73) (21) (22) (30) IMAGE FORMING APPARATUS
(19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/0152762 A1 Asano et al. US 2006O152762A1 (43) Pub. Date: Jul. 13, 2006 (54) (75) (73) (21) (22) (30) IMAGE FORMING APPARATUS
contact United States Patent (19) (11) 3,967,257 Hager (45) June 29, 1976 CURRENT MONITOR LOAD DEVICE 73) Assignee: Westinghouse Electric Corporation,
 United States Patent (19) Hager 54 CURRENT MNITR CIRCUITS (75) Inventor: Robert E. Hager, Pittsburgh, Pa. 73) Assignee: Westinghouse Electric Corporation, Pittsburgh, Pa. 22 Filed: Jan. 7, 1975 (21) Appl.
United States Patent (19) Hager 54 CURRENT MNITR CIRCUITS (75) Inventor: Robert E. Hager, Pittsburgh, Pa. 73) Assignee: Westinghouse Electric Corporation, Pittsburgh, Pa. 22 Filed: Jan. 7, 1975 (21) Appl.
(12) United States Patent (10) Patent No.: US 6,446,087 B1. Lai (45) Date of Patent: Sep. 3, 2002
 USOO6446087B1 (12) United States Patent (10) Patent No.: Lai (45) Date of Patent: Sep. 3, 2002 (54) SYSTEM FOR MAINTAINING THE (74) Attorney, Agent, or Firm-Patton Boggs, LLP INTEGRITY OF APPLICATION DATA
USOO6446087B1 (12) United States Patent (10) Patent No.: Lai (45) Date of Patent: Sep. 3, 2002 (54) SYSTEM FOR MAINTAINING THE (74) Attorney, Agent, or Firm-Patton Boggs, LLP INTEGRITY OF APPLICATION DATA
(12) United States Patent
 (12) United States Patent Xiao US006663420B1 (10) Patent No.: (45) Date of Patent: Dec. 16, 2003 (54) ADAPTER FOR EXCHANGING DATA AND TRANSMITTING POWER BETWEEN PC AND PORTABLE DEVICE (75) Inventor: Hui
(12) United States Patent Xiao US006663420B1 (10) Patent No.: (45) Date of Patent: Dec. 16, 2003 (54) ADAPTER FOR EXCHANGING DATA AND TRANSMITTING POWER BETWEEN PC AND PORTABLE DEVICE (75) Inventor: Hui
(12) (10) Patent No.: US 7, B1. Liu (45) Date of Patent: Aug. 22, 2006 (54) INTERNET FILE SAFETY INFORMATION OTHER PUBLICATIONS
 United States Patent US007096493B1 (12) (10) Patent No.: US 7,096.493 B1 Liu (45) Date of Patent: Aug. 22, 2006 (54) INTERNET FILE SAFETY INFORMATION OTHER PUBLICATIONS CENTER A software infrastructure
United States Patent US007096493B1 (12) (10) Patent No.: US 7,096.493 B1 Liu (45) Date of Patent: Aug. 22, 2006 (54) INTERNET FILE SAFETY INFORMATION OTHER PUBLICATIONS CENTER A software infrastructure
(12) United States Patent (10) Patent No.: US 6,437,711 B1
 USOO6437711B1 (12) United States Patent (10) Patent No.: Nieminen et al. (45) Date of Patent: Aug. 20, 2002 (54) SEGMENTATION MECHANISM FOR A 5,386.212 A 1/1995 Shen et al.... 341/67 BLOCK ENCODER AND
USOO6437711B1 (12) United States Patent (10) Patent No.: Nieminen et al. (45) Date of Patent: Aug. 20, 2002 (54) SEGMENTATION MECHANISM FOR A 5,386.212 A 1/1995 Shen et al.... 341/67 BLOCK ENCODER AND
(12) Patent Application Publication (10) Pub. No.: US 2004/ A1
 (19) United States US 2004.00399.96A1 (12) Patent Application Publication (10) Pub. No.: US 2004/0039996 A1 Flam (43) Pub. Date: Feb. 26, 2004 (54) BIDIRECTIONAL NETWORK LANGUAGE SUPPORT (75) Inventor:
(19) United States US 2004.00399.96A1 (12) Patent Application Publication (10) Pub. No.: US 2004/0039996 A1 Flam (43) Pub. Date: Feb. 26, 2004 (54) BIDIRECTIONAL NETWORK LANGUAGE SUPPORT (75) Inventor:
(12) Patent Application Publication (10) Pub. No.: US 2006/ A1
 (19) United States US 200601 01189A1 (12) Patent Application Publication (10) Pub. No.: US 2006/0101189 A1 Chandrasekaran et al. (43) Pub. Date: (54) SYSTEM AND METHOD FOR HOT (52) U.S. Cl.... 711 f6 CLONING
(19) United States US 200601 01189A1 (12) Patent Application Publication (10) Pub. No.: US 2006/0101189 A1 Chandrasekaran et al. (43) Pub. Date: (54) SYSTEM AND METHOD FOR HOT (52) U.S. Cl.... 711 f6 CLONING
Practical Aspects of Modern Cryptography
 Practical Aspects of Modern Cryptography Lecture 3: Symmetric s and Hash Functions Josh Benaloh & Brian LaMacchia Meet Alice and Bob Alice Bob Message Modern Symmetric s Setup: Alice wants to send a private
Practical Aspects of Modern Cryptography Lecture 3: Symmetric s and Hash Functions Josh Benaloh & Brian LaMacchia Meet Alice and Bob Alice Bob Message Modern Symmetric s Setup: Alice wants to send a private
(12) United States Patent (10) Patent No.: US 6,377,725 B1
 USOO6377725B1 (12) United States Patent (10) Patent No.: Stevens et al. 45) Date of Patent: Apr. 23, 2002 9 (54) OPTICAL WAVELENGTH DIVISION 5,907,551 A * 5/1999 Nishio et al. MULTIPLEXED INTERCONNECT
USOO6377725B1 (12) United States Patent (10) Patent No.: Stevens et al. 45) Date of Patent: Apr. 23, 2002 9 (54) OPTICAL WAVELENGTH DIVISION 5,907,551 A * 5/1999 Nishio et al. MULTIPLEXED INTERCONNECT
(12) Patent Application Publication (10) Pub. No.: US 2010/ A1
 (19) United States US 2010O278338A1 (12) Patent Application Publication (10) Pub. No.: US 2010/0278338A1 Chang et al. (43) Pub. Date: Nov. 4, 2010 (54) CODING DEVICE AND METHOD WITH RECONFIGURABLE AND
(19) United States US 2010O278338A1 (12) Patent Application Publication (10) Pub. No.: US 2010/0278338A1 Chang et al. (43) Pub. Date: Nov. 4, 2010 (54) CODING DEVICE AND METHOD WITH RECONFIGURABLE AND
(12) Patent Application Publication (10) Pub. No.: US 2012/ A1
 (19) United States US 20120033670A1 (12) Patent Application Publication (10) Pub. No.: US 2012/0033670 A1 Olakangil (43) Pub. Date: Feb. 9, 2012 (54) EGRESS PROCESSING OF INGRESS VLAN (52) U.S. Cl....
(19) United States US 20120033670A1 (12) Patent Application Publication (10) Pub. No.: US 2012/0033670 A1 Olakangil (43) Pub. Date: Feb. 9, 2012 (54) EGRESS PROCESSING OF INGRESS VLAN (52) U.S. Cl....
(12) Patent Application Publication (10) Pub. No.: US 2005/ A1
 US 2005O153733A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0153733 A1 Park et al. (43) Pub. Date: Jul. 14, 2005 (54) CALL CONTROL METHOD FOR Publication Classification
US 2005O153733A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0153733 A1 Park et al. (43) Pub. Date: Jul. 14, 2005 (54) CALL CONTROL METHOD FOR Publication Classification
(12) Patent Application Publication (10) Pub. No.: US 2008/ A1
 (19) United States US 20080244164A1 (12) Patent Application Publication (10) Pub. No.: US 2008/0244164 A1 Chang et al. (43) Pub. Date: Oct. 2, 2008 (54) STORAGE DEVICE EQUIPPED WITH NAND FLASH MEMORY AND
(19) United States US 20080244164A1 (12) Patent Application Publication (10) Pub. No.: US 2008/0244164 A1 Chang et al. (43) Pub. Date: Oct. 2, 2008 (54) STORAGE DEVICE EQUIPPED WITH NAND FLASH MEMORY AND
