LECTURE 8 TEST DESIGN TECHNIQUES - I
|
|
|
- Louisa Cole
- 6 years ago
- Views:
Transcription
1 LECTURE 8 TEST DESIGN TECHNIQUES - I EQUIVALENCE CLASS PARTITIONING: Equivalence Class Partitioning is a test case design techniques in black box testing. Equivalence partitioning is a Test Case Design Technique to divide the input data of software into different equivalence data classes. Test cases are designed for equivalence data class. The equivalence partitions are frequently derived from the requirements specification for input data that influence the processing of the test object. A use of this method reduces the time necessary for testing software using less and effective test cases. Equivalence Partitioning = Equivalence Class Partitioning = ECP It can be used at any level of software for testing and is preferably a good technique to use first. In this technique, only one condition to be tested from each partition. Because we assume that, all the conditions in one partition behave in the same manner by the software. In a partition, if one condition works other will definitely work. Likewise we assume that, if one of the conditions does not work then none of the conditions in that partition will work. Equivalence partitioning is a testing technique where input values set into classes for testing. Valid Input Class = Keeps all valid inputs. Invalid Input Class = Keeps all Invalid inputs. Let's consider the behavior of tickets in the Flight reservation application, while booking a new flight. Example 1 Let's consider the behavior of tickets in the Flight reservation application, while booking a new flight. Ticket values 1 to 10 are considered valid & ticket is booked. While value 11 to 99 is considered invalid for reservation and error message will appear, "Only ten tickets may be ordered at one time". Prepared by: Engr. M. Nadeem Page 1
2 Here is the test condition 1. Any Number greater than 10 entered in the reservation column (let say 11) is considered invalid. 2. Any Number less than 1 that is 0 or below, then it is considered invalid. 3. Numbers 1 to 10 are considered valid 4. Any 3 Digit Number say -100 is invalid. We cannot test all the possible values because if done, number of test cases will be more than 100.To address this problem, we use equivalence partitioning hypothesis where we divide the possible values of tickets into groups or sets as shown below where the system behavior can be considered the same. The divided sets are called Equivalence Partitions or Equivalence Classes. Then we pick only one value from each partition for testing. The hypothesis behind this technique is that if one condition/value in a partition passes all others will also pass. Likewise, if one condition in a partition fails, all other conditions in that partition will fail. Prepared by: Engr. M. Nadeem Page 2
3 Example 2 A text field permits only numeric characters Length must be 6-10 characters long Partition according to the requirement should be like this: At the time of testing, test 4 and 12 as invalid values and 7 as valid one. It is easy to test input ranges 6 10 but harder to test input ranges Testing will be easy in the case of lesser test cases but you should be very careful. Assuming, valid input is 7. That means, you belief that the developer coded the correct valid range (6-10). Example 3 Prepared by: Engr. M. Nadeem Page 3
4 Example 4 Boundary value Analysis: In Boundary Value Analysis, you test boundaries between equivalence partitions Boundary value analysis is a test case design techniques in black box testing. Normally Boundary value analysis is part of stress and negative testing. In our earlier example instead of checking, one value for each partitions you will check the values at the partitions like 0, 1, 10, and 11 and so on. As you may observe, you test values at both valid and invalid boundaries. Boundary Value Analysis is also called range checking. For Example: Using Boundary Value Analysis technique tester creates test cases for required input field. For example; an Address text box which allows maximum 500 characters. So, writing test cases for each character once will be very difficult so that will choose boundary value analysis. Prepared by: Engr. M. Nadeem Page 4
5 Example 1 Suppose you have very important tool at office, accept valid User Name and Password field to work on that tool, and accept minimum 8 characters and maximum 12 characters. Valid range 8-12, Invalid range 7 or less than 7 and invalid range 13 or more than 13. Write Test Cases for Valid partition value, Invalid partition value and exact boundary value. Test Cases 1: Consider password length less than 8. Test Cases 2: Consider password of length exactly 8. Test Cases 3: Consider password of length between 9 and 11. Test Cases 4: Consider password of length exactly 12. Test Cases 5: Consider password of length more than 12. Example 2 Test cases for the application whose input box accepts numbers between Valid range , Invalid range 0 and Invalid range 1001 or more. Write Test Cases for Valid partition value, Invalid partition value and exact boundary value. Test Cases 1: Consider test data exactly as the input boundaries of input domain i.e. values 1 and Test Cases 2: Consider test data with values just below the extreme edges of input domains i.e. values 0 and 999. Test Cases 3: Consider test data with values just above the extreme edges of input domain i.e. values 2 and Prepared by: Engr. M. Nadeem Page 5
6 Equivalence partitioning and boundary value analysis are closely related and can be used together at all levels of testing. Example 3 Example 4 Example 5 Prepared by: Engr. M. Nadeem Page 6
Equivalence Class Partitioning and Boundary Value Analysis -Black Box Testing Techniques
 Equivalence Class Partitioning and Boundary Value Analysis -Black Box Testing Techniques In this tutorial, we will discuss the approach to design the test cases and also how to apply the boundary value
Equivalence Class Partitioning and Boundary Value Analysis -Black Box Testing Techniques In this tutorial, we will discuss the approach to design the test cases and also how to apply the boundary value
LECTURE 9 TEST DESIGN TECHNIQUES - II
 LECTURE 9 TEST DESIGN TECHNIQUES - II DECISION TABLE A decision table is a good way to deal with different combination inputs with their associated outputs and also called cause-effect table. Decision
LECTURE 9 TEST DESIGN TECHNIQUES - II DECISION TABLE A decision table is a good way to deal with different combination inputs with their associated outputs and also called cause-effect table. Decision
UNIT-4 Black Box & White Box Testing
 Black Box & White Box Testing Black Box Testing (Functional testing) o Equivalence Partitioning o Boundary Value Analysis o Cause Effect Graphing White Box Testing (Structural testing) o Coverage Testing
Black Box & White Box Testing Black Box Testing (Functional testing) o Equivalence Partitioning o Boundary Value Analysis o Cause Effect Graphing White Box Testing (Structural testing) o Coverage Testing
UNIT-4 Black Box & White Box Testing
 Black Box & White Box Testing Black Box Testing (Functional testing) o Equivalence Partitioning o Boundary Value Analysis o Cause Effect Graphing White Box Testing (Structural testing) o Coverage Testing
Black Box & White Box Testing Black Box Testing (Functional testing) o Equivalence Partitioning o Boundary Value Analysis o Cause Effect Graphing White Box Testing (Structural testing) o Coverage Testing
Software Testing Prof. Rajib Mall Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur
 Software Testing Prof. Rajib Mall Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 06 Equivalence and Boundary Value Testing Welcome to this session, we
Software Testing Prof. Rajib Mall Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 06 Equivalence and Boundary Value Testing Welcome to this session, we
CS 424 Software Quality Assurance & Testing LECTURE 3 BASIC CONCEPTS OF SOFTWARE TESTING - I
 LECTURE 3 BASIC CONCEPTS OF SOFTWARE TESTING - I WHAT IS SOFTWARE TESTING? Testing can find faults in the software but cannot prove that the software is error-free. OBJECTIVES OF SOFTWARE TESTING To test
LECTURE 3 BASIC CONCEPTS OF SOFTWARE TESTING - I WHAT IS SOFTWARE TESTING? Testing can find faults in the software but cannot prove that the software is error-free. OBJECTIVES OF SOFTWARE TESTING To test
No Source Code. EEC 521: Software Engineering. Specification-Based Testing. Advantages
 No Source Code : Software Testing Black-Box Testing Test-Driven Development No access to source code So test cases don t worry about structure Emphasis is only on ensuring that the contract is met Specification-Based
No Source Code : Software Testing Black-Box Testing Test-Driven Development No access to source code So test cases don t worry about structure Emphasis is only on ensuring that the contract is met Specification-Based
Black Box Testing. EEC 521: Software Engineering. Specification-Based Testing. No Source Code. Software Testing
 Black Box Testing EEC 521: Software Engineering Software Testing Black-Box Testing Test-Driven Development Also known as specification-based testing Tester has access only to running code and the specification
Black Box Testing EEC 521: Software Engineering Software Testing Black-Box Testing Test-Driven Development Also known as specification-based testing Tester has access only to running code and the specification
CS 451 Software Engineering Winter 2009
 CS 451 Software Engineering Winter 2009 Yuanfang Cai Room 104, University Crossings 215.895.0298 yfcai@cs.drexel.edu 1 Software Testing Techniques FUNDAMENTALS The goal of testing is to find errors. A
CS 451 Software Engineering Winter 2009 Yuanfang Cai Room 104, University Crossings 215.895.0298 yfcai@cs.drexel.edu 1 Software Testing Techniques FUNDAMENTALS The goal of testing is to find errors. A
QUIZ #5 - Solutions (5pts each)
 CS 435 Spring 2014 SOFTWARE ENGINEERING Department of Computer Science Name QUIZ #5 - Solutions (5pts each) 1. The best reason for using Independent software test teams is that a. software developers do
CS 435 Spring 2014 SOFTWARE ENGINEERING Department of Computer Science Name QUIZ #5 - Solutions (5pts each) 1. The best reason for using Independent software test teams is that a. software developers do
Software Testing. Software Testing. in the textbook. Chapter 8. Verification and Validation. Verification Techniques
 Software Testing in the textbook Software Testing Chapter 8 Introduction (Verification and Validation) 8.1 Development testing 8.2 Test-driven development 8.3 Release testing 8.4 User testing 1 2 Verification
Software Testing in the textbook Software Testing Chapter 8 Introduction (Verification and Validation) 8.1 Development testing 8.2 Test-driven development 8.3 Release testing 8.4 User testing 1 2 Verification
Software Testing Prof. Rajib Mall Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur
 Software Testing Prof. Rajib Mall Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture - 07 Special Value Testing Welcome to this session. So far we had looked
Software Testing Prof. Rajib Mall Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture - 07 Special Value Testing Welcome to this session. So far we had looked
Black-box Testing Techniques
 T-76.5613 Software Testing and Quality Assurance Lecture 4, 20.9.2006 Black-box Testing Techniques SoberIT Black-box test case design techniques Basic techniques Equivalence partitioning Boundary value
T-76.5613 Software Testing and Quality Assurance Lecture 4, 20.9.2006 Black-box Testing Techniques SoberIT Black-box test case design techniques Basic techniques Equivalence partitioning Boundary value
Analysis for Testing. by: rex Black. quality matters Q3 2009
 Using Domain by: rex Black Analysis for Testing This article is excerpted from Chapter 16 of Rex Black s book Pragmatic Software Testing. Many of you are probably familiar with basic test techniques like
Using Domain by: rex Black Analysis for Testing This article is excerpted from Chapter 16 of Rex Black s book Pragmatic Software Testing. Many of you are probably familiar with basic test techniques like
Testing & Debugging TB-1
 Testing & Debugging TB-1 Need for Testing Software systems are inherently complex» Large systems 1 to 3 errors per 100 lines of code (LOC) Extensive verification and validiation is required to build quality
Testing & Debugging TB-1 Need for Testing Software systems are inherently complex» Large systems 1 to 3 errors per 100 lines of code (LOC) Extensive verification and validiation is required to build quality
Darshan Institute of Engineering & Technology for Diploma Studies
 CODING Good software development organizations normally require their programmers to follow some welldefined and standard style of coding called coding standards. Most software development organizations
CODING Good software development organizations normally require their programmers to follow some welldefined and standard style of coding called coding standards. Most software development organizations
Chapter 9. Software Testing
 Chapter 9. Software Testing Table of Contents Objectives... 1 Introduction to software testing... 1 The testers... 2 The developers... 2 An independent testing team... 2 The customer... 2 Principles of
Chapter 9. Software Testing Table of Contents Objectives... 1 Introduction to software testing... 1 The testers... 2 The developers... 2 An independent testing team... 2 The customer... 2 Principles of
Chapter 11, Testing. Using UML, Patterns, and Java. Object-Oriented Software Engineering
 Chapter 11, Testing Using UML, Patterns, and Java Object-Oriented Software Engineering Outline Terminology Types of errors Dealing with errors Quality assurance vs Testing Component Testing! Unit testing!
Chapter 11, Testing Using UML, Patterns, and Java Object-Oriented Software Engineering Outline Terminology Types of errors Dealing with errors Quality assurance vs Testing Component Testing! Unit testing!
Discrete Structures Lecture The Basics of Counting
 Introduction Good morning. Combinatorics is the study of arrangements of objects. Perhaps, the first application of the study of combinatorics was in the study of gambling games. Understanding combinatorics
Introduction Good morning. Combinatorics is the study of arrangements of objects. Perhaps, the first application of the study of combinatorics was in the study of gambling games. Understanding combinatorics
Introduction to Domain Testing
 Introduction to Domain Testing Cem Kaner January, 2018 Copyright (c) 2018 Cem Kaner Domain Testing 1 What Is Domain Testing? The most widely taught technique for designing software tests Copyright (c)
Introduction to Domain Testing Cem Kaner January, 2018 Copyright (c) 2018 Cem Kaner Domain Testing 1 What Is Domain Testing? The most widely taught technique for designing software tests Copyright (c)
Testing is a very big and important topic when it comes to software development. Testing has a number of aspects that need to be considered.
 Testing Testing is a very big and important topic when it comes to software development. Testing has a number of aspects that need to be considered. System stability is the system going to crash or not?
Testing Testing is a very big and important topic when it comes to software development. Testing has a number of aspects that need to be considered. System stability is the system going to crash or not?
Contents Introduction to RezDesk... 3 Activating your Account... 4 Logging In... 5 Editing a New Travel Profile... 6 Contact Information...
 Contents Introduction to RezDesk... 3 Activating your Account... 4 Logging In... 5 Editing a New Travel Profile... 6 Contact Information... 7 Profile - Continued... 8 Addresses... 9 Account Questions and
Contents Introduction to RezDesk... 3 Activating your Account... 4 Logging In... 5 Editing a New Travel Profile... 6 Contact Information... 7 Profile - Continued... 8 Addresses... 9 Account Questions and
COS 226 Midterm Exam, Spring 2011
 NAME: login ID: Precept (circle one): P01 P01A P01B P02 P02A P03 COS 226 Midterm Exam, Spring 2011 This test is 9 questions, weighted as indicated. The exam is closed book, except that you are allowed
NAME: login ID: Precept (circle one): P01 P01A P01B P02 P02A P03 COS 226 Midterm Exam, Spring 2011 This test is 9 questions, weighted as indicated. The exam is closed book, except that you are allowed
Types of Software Testing: Different Testing Types with Details
 Types of Software Testing: Different Testing Types with Details What are the different Types of Software Testing? We, as testers are aware of the various types of Software Testing such as Functional Testing,
Types of Software Testing: Different Testing Types with Details What are the different Types of Software Testing? We, as testers are aware of the various types of Software Testing such as Functional Testing,
k-selection Yufei Tao Department of Computer Science and Engineering Chinese University of Hong Kong
 Department of Computer Science and Engineering Chinese University of Hong Kong In this lecture, we will put randomization to some real use, by using it to solve a non-trivial problem called k-selection
Department of Computer Science and Engineering Chinese University of Hong Kong In this lecture, we will put randomization to some real use, by using it to solve a non-trivial problem called k-selection
CISC-235* Test #3 March 19, 2018
 CISC-235* Test #3 March 19, 2018 Student Number (Required) Name (Optional) This is a closed book test. You may not refer to any resources. This is a 50 minute test. Please write your answers in ink. Pencil
CISC-235* Test #3 March 19, 2018 Student Number (Required) Name (Optional) This is a closed book test. You may not refer to any resources. This is a 50 minute test. Please write your answers in ink. Pencil
Nearest Neighbor Classification. Machine Learning Fall 2017
 Nearest Neighbor Classification Machine Learning Fall 2017 1 This lecture K-nearest neighbor classification The basic algorithm Different distance measures Some practical aspects Voronoi Diagrams and Decision
Nearest Neighbor Classification Machine Learning Fall 2017 1 This lecture K-nearest neighbor classification The basic algorithm Different distance measures Some practical aspects Voronoi Diagrams and Decision
The Specification Phase
 The Specification Phase CS427: Elements of Software Engineering Lecture 4.1 10am, 30 Jan 2012 CS427 The Specification Phase 1/16 Outline 1 Recall... The Requirements Phase 2 Phase 2: Specifications 3 Requirements
The Specification Phase CS427: Elements of Software Engineering Lecture 4.1 10am, 30 Jan 2012 CS427 The Specification Phase 1/16 Outline 1 Recall... The Requirements Phase 2 Phase 2: Specifications 3 Requirements
Discrete Wiskunde II. Lecture 6: Planar Graphs
 , 2009 Lecture 6: Planar Graphs University of Twente m.uetz@utwente.nl wwwhome.math.utwente.nl/~uetzm/dw/ Planar Graphs Given an undirected graph (or multigraph) G = (V, E). A planar embedding of G is
, 2009 Lecture 6: Planar Graphs University of Twente m.uetz@utwente.nl wwwhome.math.utwente.nl/~uetzm/dw/ Planar Graphs Given an undirected graph (or multigraph) G = (V, E). A planar embedding of G is
CA Test Data Manager Key Scenarios
 WHITE PAPER APRIL 2016 CA Test Data Manager Key Scenarios Generate and secure all the data needed for rigorous testing, and provision it to highly distributed teams on demand. Muhammad Arif Application
WHITE PAPER APRIL 2016 CA Test Data Manager Key Scenarios Generate and secure all the data needed for rigorous testing, and provision it to highly distributed teams on demand. Muhammad Arif Application
4.7 Approximate Integration
 4.7 Approximate Integration Some anti-derivatives are difficult to impossible to find. For example, 1 0 e x2 dx or 1 1 1 + x3 dx We came across this situation back in calculus I when we introduced the
4.7 Approximate Integration Some anti-derivatives are difficult to impossible to find. For example, 1 0 e x2 dx or 1 1 1 + x3 dx We came across this situation back in calculus I when we introduced the
2. You are required to enter a password of up to 100 characters. The characters must be lower ASCII, printing characters.
 BLACK BOX SOFTWARE TESTING SPRING 2005 DOMAIN TESTING LAB PROJECT -- GRADING NOTES For all of the cases below, do the traditional equivalence class and boundary analysis. Draw one table and use a new line
BLACK BOX SOFTWARE TESTING SPRING 2005 DOMAIN TESTING LAB PROJECT -- GRADING NOTES For all of the cases below, do the traditional equivalence class and boundary analysis. Draw one table and use a new line
Lesson 16: More on Modeling Relationships with a Line
 Student Outcomes Students use the least squares line to predict values for a given data set. Students use residuals to evaluate the accuracy of predictions based on the least squares line. Lesson Notes
Student Outcomes Students use the least squares line to predict values for a given data set. Students use residuals to evaluate the accuracy of predictions based on the least squares line. Lesson Notes
Computer Science and Software Engineering University of Wisconsin - Platteville 9-Software Testing, Verification and Validation
 Computer Science and Software Engineering University of Wisconsin - Platteville 9-Software Testing, Verification and Validation Yan Shi SE 2730 Lecture Notes Verification and Validation Verification: Are
Computer Science and Software Engineering University of Wisconsin - Platteville 9-Software Testing, Verification and Validation Yan Shi SE 2730 Lecture Notes Verification and Validation Verification: Are
HASH CRACK: PASSWORD CRACKING MANUAL BY JOSHUA PICOLET DOWNLOAD EBOOK : HASH CRACK: PASSWORD CRACKING MANUAL BY JOSHUA PICOLET PDF
 Read Online and Download Ebook HASH CRACK: PASSWORD CRACKING MANUAL BY JOSHUA PICOLET DOWNLOAD EBOOK : HASH CRACK: PASSWORD CRACKING MANUAL BY Click link bellow and free register to download ebook: HASH
Read Online and Download Ebook HASH CRACK: PASSWORD CRACKING MANUAL BY JOSHUA PICOLET DOWNLOAD EBOOK : HASH CRACK: PASSWORD CRACKING MANUAL BY Click link bellow and free register to download ebook: HASH
ASTQB Advance Test Analyst Sample Exam Answer Key and Rationale
 ASTQB Advance Test Analyst Sample Exam Answer Key and Rationale Total number points = 120 points Total number points to pass = 78 points Question Answer Explanation / Rationale Learning 1 A A is correct.
ASTQB Advance Test Analyst Sample Exam Answer Key and Rationale Total number points = 120 points Total number points to pass = 78 points Question Answer Explanation / Rationale Learning 1 A A is correct.
MS&E 226: Small Data
 MS&E 226: Small Data Lecture 14: Introduction to hypothesis testing (v2) Ramesh Johari ramesh.johari@stanford.edu 1 / 10 Hypotheses 2 / 10 Quantifying uncertainty Recall the two key goals of inference:
MS&E 226: Small Data Lecture 14: Introduction to hypothesis testing (v2) Ramesh Johari ramesh.johari@stanford.edu 1 / 10 Hypotheses 2 / 10 Quantifying uncertainty Recall the two key goals of inference:
LECTURE 11 TEST DESIGN TECHNIQUES IV
 Code Coverage Testing 1. Statement coverage testing 2. Branch coverage testing 3. Conditional coverage testing LECTURE 11 TEST DESIGN TECHNIQUES IV Code Complexity Testing 1. Cyclomatic Complexity s V
Code Coverage Testing 1. Statement coverage testing 2. Branch coverage testing 3. Conditional coverage testing LECTURE 11 TEST DESIGN TECHNIQUES IV Code Complexity Testing 1. Cyclomatic Complexity s V
Privacy and Security in Online Social Networks Department of Computer Science and Engineering Indian Institute of Technology, Madras
 Privacy and Security in Online Social Networks Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 08 Tutorial 2, Part 2, Facebook API (Refer Slide Time: 00:12)
Privacy and Security in Online Social Networks Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 08 Tutorial 2, Part 2, Facebook API (Refer Slide Time: 00:12)
HMMT February 2018 February 10, 2018
 HMMT February 2018 February 10, 2018 Combinatorics 1. Consider a 2 3 grid where each entry is one of 0, 1, and 2. For how many such grids is the sum of the numbers in every row and in every column a multiple
HMMT February 2018 February 10, 2018 Combinatorics 1. Consider a 2 3 grid where each entry is one of 0, 1, and 2. For how many such grids is the sum of the numbers in every row and in every column a multiple
Software Testing. Lecturer: Sebastian Coope Ashton Building, Room G.18
 Lecturer: Sebastian Coope Ashton Building, Room G.18 E-mail: coopes@liverpool.ac.uk COMP 201 web-page: http://www.csc.liv.ac.uk/~coopes/comp201 Software Testing 1 Defect Testing Defect testing involves
Lecturer: Sebastian Coope Ashton Building, Room G.18 E-mail: coopes@liverpool.ac.uk COMP 201 web-page: http://www.csc.liv.ac.uk/~coopes/comp201 Software Testing 1 Defect Testing Defect testing involves
Bureau of Water System Engineering
 Physical Connection E-Permitting Quarterly Service Instructions (includes instructions for registering with NJDEP Online and for reporting results) NJDEP Bureau of Water System Engineering January 2015
Physical Connection E-Permitting Quarterly Service Instructions (includes instructions for registering with NJDEP Online and for reporting results) NJDEP Bureau of Water System Engineering January 2015
Concur Cliqbook Travel New User Interface
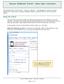 The enhanced User Interface (UI) known as Hooville was designed to improve the user experience in many ways, including increased usability, improved filtering, and more search results. Using the wizard
The enhanced User Interface (UI) known as Hooville was designed to improve the user experience in many ways, including increased usability, improved filtering, and more search results. Using the wizard
Complexity Classes and Polynomial-time Reductions
 COMPSCI 330: Design and Analysis of Algorithms April 19, 2016 Complexity Classes and Polynomial-time Reductions Lecturer: Debmalya Panigrahi Scribe: Tianqi Song 1 Overview In this lecture, we introduce
COMPSCI 330: Design and Analysis of Algorithms April 19, 2016 Complexity Classes and Polynomial-time Reductions Lecturer: Debmalya Panigrahi Scribe: Tianqi Song 1 Overview In this lecture, we introduce
COS 226 Fall 2015 Midterm Exam pts.; 60 minutes; 8 Qs; 15 pgs :00 p.m. Name:
 COS 226 Fall 2015 Midterm Exam 1 60 + 10 pts.; 60 minutes; 8 Qs; 15 pgs. 2015-10-08 2:00 p.m. c 2015 Sudarshan S. Chawathe Name: 1. (1 pt.) Read all material carefully. If in doubt whether something is
COS 226 Fall 2015 Midterm Exam 1 60 + 10 pts.; 60 minutes; 8 Qs; 15 pgs. 2015-10-08 2:00 p.m. c 2015 Sudarshan S. Chawathe Name: 1. (1 pt.) Read all material carefully. If in doubt whether something is
5 Graphs
 5 Graphs jacques@ucsd.edu Some of the putnam problems are to do with graphs. They do not assume more than a basic familiarity with the definitions and terminology of graph theory. 5.1 Basic definitions
5 Graphs jacques@ucsd.edu Some of the putnam problems are to do with graphs. They do not assume more than a basic familiarity with the definitions and terminology of graph theory. 5.1 Basic definitions
Testing & Continuous Integration. Kenneth M. Anderson University of Colorado, Boulder CSCI 5828 Lecture 20 03/19/2010
 esting & Continuous Integration Kenneth M. Anderson University of Colorado, Boulder CSCI 5828 Lecture 20 03/1/20 University of Colorado, 20 1 Goals 2 Review material from Chapter of Pilone & Miles esting
esting & Continuous Integration Kenneth M. Anderson University of Colorado, Boulder CSCI 5828 Lecture 20 03/1/20 University of Colorado, 20 1 Goals 2 Review material from Chapter of Pilone & Miles esting
2010 SMT Power Round
 Definitions 2010 SMT Power Round A graph is a collection of points (vertices) connected by line segments (edges). In this test, all graphs will be simple any two vertices will be connected by at most one
Definitions 2010 SMT Power Round A graph is a collection of points (vertices) connected by line segments (edges). In this test, all graphs will be simple any two vertices will be connected by at most one
CSE 6242/CX Ensemble Methods. Or, Model Combination. Based on lecture by Parikshit Ram
 CSE 6242/CX 4242 Ensemble Methods Or, Model Combination Based on lecture by Parikshit Ram Numerous Possible Classifiers! Classifier Training time Cross validation Testing time Accuracy knn classifier None
CSE 6242/CX 4242 Ensemble Methods Or, Model Combination Based on lecture by Parikshit Ram Numerous Possible Classifiers! Classifier Training time Cross validation Testing time Accuracy knn classifier None
Lecture-14 Lookup Functions
 Lecture-14 Lookup Functions How do I write a formula to compute tax rates based on income? Given a product ID, how can I look up the product s price? Suppose that a product s price changes over time. I
Lecture-14 Lookup Functions How do I write a formula to compute tax rates based on income? Given a product ID, how can I look up the product s price? Suppose that a product s price changes over time. I
Software Testing CS 408
 Software Testing CS 408 1/09/18 Course Webpage: http://www.cs.purdue.edu/homes/suresh/408-spring2018 1 The Course Understand testing in the context of an Agile software development methodology - Detail
Software Testing CS 408 1/09/18 Course Webpage: http://www.cs.purdue.edu/homes/suresh/408-spring2018 1 The Course Understand testing in the context of an Agile software development methodology - Detail
GSE Scale Systems M660 CUSTOM TRANSMIT
 M660 CUSTOM TRANSMIT A custom transmit is a sequence of characters, control codes and parameter values to be transmitted out a communication port to a peripheral device such as a printer, remote display,
M660 CUSTOM TRANSMIT A custom transmit is a sequence of characters, control codes and parameter values to be transmitted out a communication port to a peripheral device such as a printer, remote display,
Functional Testing (Black Box Testing)
 Functional Testing (Black Box Testing) In black box testing, program is treated as a black box. Implementation details do not matter. Takes a user point of view. Functional testing verifies that each function
Functional Testing (Black Box Testing) In black box testing, program is treated as a black box. Implementation details do not matter. Takes a user point of view. Functional testing verifies that each function
NOM SIMULATOR TEST PLAN. Sections. A.1 Introduction
 NOM SIMULATOR TEST PLAN A.1 Introduction A.2 Test Plan A.3 Test Design Specifications A.4 Test Case Specification A.5 Test Log A.6 Test Summary Report Sections [1] page 8 A.1 Introduction 1.1 Scope This
NOM SIMULATOR TEST PLAN A.1 Introduction A.2 Test Plan A.3 Test Design Specifications A.4 Test Case Specification A.5 Test Log A.6 Test Summary Report Sections [1] page 8 A.1 Introduction 1.1 Scope This
10.2 Basic Concepts of Limits
 10.2 Basic Concepts of Limits Question 1: How do you evaluate a limit from a table? Question 2: How do you evaluate a limit from a graph? In this chapter, we ll examine the concept of a limit. in its simplest
10.2 Basic Concepts of Limits Question 1: How do you evaluate a limit from a table? Question 2: How do you evaluate a limit from a graph? In this chapter, we ll examine the concept of a limit. in its simplest
Software Design Models, Tools & Processes. Lecture 6: Transition Phase Cecilia Mascolo
 Software Design Models, Tools & Processes Lecture 6: Transition Phase Cecilia Mascolo UML Component diagram Component documentation Your own classes should be documented the same way library classes are.
Software Design Models, Tools & Processes Lecture 6: Transition Phase Cecilia Mascolo UML Component diagram Component documentation Your own classes should be documented the same way library classes are.
User/Phone Add Configuration
 CHAPTER 91 The following topics contain information on adding and configuring end users at the End User, Phone, DN, and LA Configuration window: User and Device Configuration Settings, page 91-1 Adding
CHAPTER 91 The following topics contain information on adding and configuring end users at the End User, Phone, DN, and LA Configuration window: User and Device Configuration Settings, page 91-1 Adding
Many of the slides in this lecture are either from or adapted from slides provided by the authors of the textbook Computer Systems: A Programmer s
 Many of the slides in this lecture are either from or adapted from slides provided by the authors of the textbook Computer Systems: A Programmer s Perspective, 2 nd Edition and are provided from the website
Many of the slides in this lecture are either from or adapted from slides provided by the authors of the textbook Computer Systems: A Programmer s Perspective, 2 nd Edition and are provided from the website
CS454/654 Midterm Exam Fall 2004
 CS454/654 Midterm Exam Fall 2004 (3 November 2004) Question 1: Distributed System Models (18 pts) (a) [4 pts] Explain two benefits of middleware to distributed system programmers, providing an example
CS454/654 Midterm Exam Fall 2004 (3 November 2004) Question 1: Distributed System Models (18 pts) (a) [4 pts] Explain two benefits of middleware to distributed system programmers, providing an example
Lecture 15 of unit 2 on us discussed both those testing methods in test selections criteria in previous session, (Refer Slide Time: 00:23)
 Welcome you to the next embedded software testing session. (Refer Slide Time: 00:07) Lecture 15 of unit 2 on us discussed both those testing methods in test selections criteria in previous session, (Refer
Welcome you to the next embedded software testing session. (Refer Slide Time: 00:07) Lecture 15 of unit 2 on us discussed both those testing methods in test selections criteria in previous session, (Refer
Software Testing. Testing 1
 Software Testing Testing 1 Background Main objectives of a project: High Quality & High Productivity (Q&P) Quality has many dimensions reliability, maintainability, interoperability etc. Reliability is
Software Testing Testing 1 Background Main objectives of a project: High Quality & High Productivity (Q&P) Quality has many dimensions reliability, maintainability, interoperability etc. Reliability is
Finding Strongly Connected Components
 Yufei Tao ITEE University of Queensland We just can t get enough of the beautiful algorithm of DFS! In this lecture, we will use it to solve a problem finding strongly connected components that seems to
Yufei Tao ITEE University of Queensland We just can t get enough of the beautiful algorithm of DFS! In this lecture, we will use it to solve a problem finding strongly connected components that seems to
CSE 403: Software Engineering, Fall courses.cs.washington.edu/courses/cse403/16au/ Unit Testing. Emina Torlak
 CSE 403: Software Engineering, Fall 2016 courses.cs.washington.edu/courses/cse403/16au/ Unit Testing Emina Torlak emina@cs.washington.edu Outline Software quality control Effective unit testing Coverage
CSE 403: Software Engineering, Fall 2016 courses.cs.washington.edu/courses/cse403/16au/ Unit Testing Emina Torlak emina@cs.washington.edu Outline Software quality control Effective unit testing Coverage
Math 3336 Section 6.1 The Basics of Counting The Product Rule The Sum Rule The Subtraction Rule The Division Rule
 Math 3336 Section 6.1 The Basics of Counting The Product Rule The Sum Rule The Subtraction Rule The Division Rule Examples, Examples, and Examples Tree Diagrams Basic Counting Principles: The Product Rule
Math 3336 Section 6.1 The Basics of Counting The Product Rule The Sum Rule The Subtraction Rule The Division Rule Examples, Examples, and Examples Tree Diagrams Basic Counting Principles: The Product Rule
Ontology Summit 2013: Ontology Evaluation Across the Ontology Lifecyle Track B: Extrinsic Aspects of Ontology Evaluation
 Ontology Summit 2013: Ontology Evaluation Across the Ontology Lifecyle Track B: Extrinsic Aspects of Ontology Evaluation Black Box Testing Paradigm in the TCPC #014168-PA Mary Balboni, Doug Toppin, Thanh-Van
Ontology Summit 2013: Ontology Evaluation Across the Ontology Lifecyle Track B: Extrinsic Aspects of Ontology Evaluation Black Box Testing Paradigm in the TCPC #014168-PA Mary Balboni, Doug Toppin, Thanh-Van
Introduction to Algorithms April 21, 2004 Massachusetts Institute of Technology. Quiz 2 Solutions
 Introduction to Algorithms April 21, 2004 Massachusetts Institute of Technology 6.046J/18.410J Professors Erik Demaine and Shafi Goldwasser Quiz 2 Solutions Quiz 2 Solutions Do not open this quiz booklet
Introduction to Algorithms April 21, 2004 Massachusetts Institute of Technology 6.046J/18.410J Professors Erik Demaine and Shafi Goldwasser Quiz 2 Solutions Quiz 2 Solutions Do not open this quiz booklet
kalmstrom.com Business Solutions
 E-mail Converter for Outlook and SharePoint User Manual Contents 1 INTRODUCTION... 2 1.1 LANGUAGES... 2 1.2 REQUIREMENTS... 3 2 THE SHAREPOINT SITE... 4 2.1 PERMISSIONS... 4 3 INSTALLATION OF E-MAIL CONVERTER...
E-mail Converter for Outlook and SharePoint User Manual Contents 1 INTRODUCTION... 2 1.1 LANGUAGES... 2 1.2 REQUIREMENTS... 3 2 THE SHAREPOINT SITE... 4 2.1 PERMISSIONS... 4 3 INSTALLATION OF E-MAIL CONVERTER...
1 Minimum Spanning Tree (MST)
 Lecture Notes CS:5360 Randomized Algorithms Lectures 10, 11, and 12: Sep 20, Sep 25, and Sep 27, 2018 Scribe: Hankyu Jang 1 Minimum Spanning Tree (MST) MST is another example of sampling. Input: An edge-weighted,
Lecture Notes CS:5360 Randomized Algorithms Lectures 10, 11, and 12: Sep 20, Sep 25, and Sep 27, 2018 Scribe: Hankyu Jang 1 Minimum Spanning Tree (MST) MST is another example of sampling. Input: An edge-weighted,
Theme 2 Program Design and Testing
 Theme 2 Program Design and Testing Systematic Testing 1 Learning Objectives to present a few systematic testing techniques that increase the chance of finding defects while keeping the number of test cases
Theme 2 Program Design and Testing Systematic Testing 1 Learning Objectives to present a few systematic testing techniques that increase the chance of finding defects while keeping the number of test cases
EXTREME POINTS AND AFFINE EQUIVALENCE
 EXTREME POINTS AND AFFINE EQUIVALENCE The purpose of this note is to use the notions of extreme points and affine transformations which are studied in the file affine-convex.pdf to prove that certain standard
EXTREME POINTS AND AFFINE EQUIVALENCE The purpose of this note is to use the notions of extreme points and affine transformations which are studied in the file affine-convex.pdf to prove that certain standard
HHS ENTERPRISE PORTAL
 HHS ENTERPRISE PORTAL The HHS Enterprise Portal is the secure, easy-to-use site that allows you to access or request new/modified access to multiple state applications from just one location! The portal
HHS ENTERPRISE PORTAL The HHS Enterprise Portal is the secure, easy-to-use site that allows you to access or request new/modified access to multiple state applications from just one location! The portal
Progress from objects/ Numicon to bead string to number track to number line.
 Year 1 Read, write and interpret mathematical statements involving subtraction (-) and equals (=) signs Vocabulary: Number bonds, number line Inverse Half, halve Equals, is the same as (including equals
Year 1 Read, write and interpret mathematical statements involving subtraction (-) and equals (=) signs Vocabulary: Number bonds, number line Inverse Half, halve Equals, is the same as (including equals
Test design: Part I. Software Testing: INF3121 / INF4121
 Test design: Part I Software Testing: INF3121 / INF4121 Summary: Week 4 Test development process Analysis / Design / Implementation Categories of test design techniques Static / Dynamic Specification-based
Test design: Part I Software Testing: INF3121 / INF4121 Summary: Week 4 Test development process Analysis / Design / Implementation Categories of test design techniques Static / Dynamic Specification-based
Sample Questions ISTQB Foundation Answers
 Sample Questions ISTQB Foundation Answers Questions Prepared By Released January 2017 1 C C is correct. This is a defect that directly causes harm to the environment. A is not correct because the unhappy
Sample Questions ISTQB Foundation Answers Questions Prepared By Released January 2017 1 C C is correct. This is a defect that directly causes harm to the environment. A is not correct because the unhappy
Choices for Using Wildcard Masks
 Choices f Using Wildcard Masks 1 Wildcard masks are usually set up to do one of four things: 1. Match a specific host. 2. Match an entire subnet. 3. Match a specific range. 4. Match all addresses. 1. Matching
Choices f Using Wildcard Masks 1 Wildcard masks are usually set up to do one of four things: 1. Match a specific host. 2. Match an entire subnet. 3. Match a specific range. 4. Match all addresses. 1. Matching
Lecture 9: Linear Programming
 Lecture 9: Linear Programming A common optimization problem involves finding the maximum of a linear function of N variables N Z = a i x i i= 1 (the objective function ) where the x i are all non-negative
Lecture 9: Linear Programming A common optimization problem involves finding the maximum of a linear function of N variables N Z = a i x i i= 1 (the objective function ) where the x i are all non-negative
7.0 Test Design Techniques & Dynamic Testing
 7.0 Test Design Techniques & Dynamic Testing Test Design Techniques 7.1 The Test Development Process 7.2 Categories of Test Design Techniques 7.3 Specification based or Black Box Techniques 7.4 Structure
7.0 Test Design Techniques & Dynamic Testing Test Design Techniques 7.1 The Test Development Process 7.2 Categories of Test Design Techniques 7.3 Specification based or Black Box Techniques 7.4 Structure
Lecture 10: Introduction to Correctness
 Lecture 10: Introduction to Correctness Aims: To look at the different types of errors that programs can contain; To look at how we might detect each of these errors; To look at the difficulty of detecting
Lecture 10: Introduction to Correctness Aims: To look at the different types of errors that programs can contain; To look at how we might detect each of these errors; To look at the difficulty of detecting
Lecture 15 Software Testing
 Lecture 15 Software Testing Includes slides from the companion website for Sommerville, Software Engineering, 10/e. Pearson Higher Education, 2016. All rights reserved. Used with permission. Topics covered
Lecture 15 Software Testing Includes slides from the companion website for Sommerville, Software Engineering, 10/e. Pearson Higher Education, 2016. All rights reserved. Used with permission. Topics covered
Part 5. Verification and Validation
 Software Engineering Part 5. Verification and Validation - Verification and Validation - Software Testing Ver. 1.7 This lecture note is based on materials from Ian Sommerville 2006. Anyone can use this
Software Engineering Part 5. Verification and Validation - Verification and Validation - Software Testing Ver. 1.7 This lecture note is based on materials from Ian Sommerville 2006. Anyone can use this
MEDIAZONE EVENT DISPLAY DOCUMENTATION VERSION 1.2
 VERSION 1.2 JUNE 2015 TABLE OF CONTENTS Introduction... 3 SignWave and MediaZone Event Display... 4 MediaZone Pro Editor... 5 Overwrite file... 6 MediaZone Event Configuration Utility... 7 MediaZone Event
VERSION 1.2 JUNE 2015 TABLE OF CONTENTS Introduction... 3 SignWave and MediaZone Event Display... 4 MediaZone Pro Editor... 5 Overwrite file... 6 MediaZone Event Configuration Utility... 7 MediaZone Event
High Availability Options
 , on page 1 Load Balancing, on page 2 Distributed VPN Clustering, Load balancing and Failover are high-availability features that function differently and have different requirements. In some circumstances
, on page 1 Load Balancing, on page 2 Distributed VPN Clustering, Load balancing and Failover are high-availability features that function differently and have different requirements. In some circumstances
V4 Matrix algorithms and graph partitioning
 V4 Matrix algorithms and graph partitioning - Community detection - Simple modularity maximization - Spectral modularity maximization - Division into more than two groups - Other algorithms for community
V4 Matrix algorithms and graph partitioning - Community detection - Simple modularity maximization - Spectral modularity maximization - Division into more than two groups - Other algorithms for community
ORGANIZING THE DATA IN A FREQUENCY TABLE
 ORGANIZING THE DATA IN A FREQUENCY TABLE Suppose the scores obtained by 5 students on a standardized test are as follows: 68, 55, 61, 55, 43, 59, 55, 58, 77, 6, 56, 53, 58, 7, 57, 62, 5, 69, 44, 63, 48,79,
ORGANIZING THE DATA IN A FREQUENCY TABLE Suppose the scores obtained by 5 students on a standardized test are as follows: 68, 55, 61, 55, 43, 59, 55, 58, 77, 6, 56, 53, 58, 7, 57, 62, 5, 69, 44, 63, 48,79,
Software Engineering Prof.N.L.Sarda IIT Bombay. Lecture-11 Data Modelling- ER diagrams, Mapping to relational model (Part -II)
 Software Engineering Prof.N.L.Sarda IIT Bombay Lecture-11 Data Modelling- ER diagrams, Mapping to relational model (Part -II) We will continue our discussion on process modeling. In the previous lecture
Software Engineering Prof.N.L.Sarda IIT Bombay Lecture-11 Data Modelling- ER diagrams, Mapping to relational model (Part -II) We will continue our discussion on process modeling. In the previous lecture
Grade 7/8 Math Circles Graph Theory - Solutions October 13/14, 2015
 Faculty of Mathematics Waterloo, Ontario N2L 3G1 Centre for Education in Mathematics and Computing Grade 7/8 Math Circles Graph Theory - Solutions October 13/14, 2015 The Seven Bridges of Königsberg In
Faculty of Mathematics Waterloo, Ontario N2L 3G1 Centre for Education in Mathematics and Computing Grade 7/8 Math Circles Graph Theory - Solutions October 13/14, 2015 The Seven Bridges of Königsberg In
CAMERA User s Guide. They are most easily launched from the main menu application. To do this, all the class files must reside in the same directory.
 CAMERA User s Guide 1 Quick Start CAMERA is a collection of concise, intuitive and visually inspiring workbenches for cache mapping schemes and virtual memory. The CAMERA workbenches are standalone applications
CAMERA User s Guide 1 Quick Start CAMERA is a collection of concise, intuitive and visually inspiring workbenches for cache mapping schemes and virtual memory. The CAMERA workbenches are standalone applications
Assignment # 4 Selected Solutions
 Assignment # 4 Selected Solutions Problem 2.3.3 Let G be a connected graph which is not a tree (did you notice this is redundant?) and let C be a cycle in G. Prove that the complement of any spanning tree
Assignment # 4 Selected Solutions Problem 2.3.3 Let G be a connected graph which is not a tree (did you notice this is redundant?) and let C be a cycle in G. Prove that the complement of any spanning tree
Verification and Validation. Ian Sommerville 2004 Software Engineering, 7th edition. Chapter 22 Slide 1
 Verification and Validation Ian Sommerville 2004 Software Engineering, 7th edition. Chapter 22 Slide 1 Verification vs validation Verification: "Are we building the product right?. The software should
Verification and Validation Ian Sommerville 2004 Software Engineering, 7th edition. Chapter 22 Slide 1 Verification vs validation Verification: "Are we building the product right?. The software should
4.2 ALGORITHM DESIGN METHODS
 4.2 ALGORITHM DESIGN METHODS 4.2.2 JACKSON STRUCTURED PROGRAMMING (JSP) JACKSON STRUCTURED PROGRAMMING (JSP) Jackson Structured Programming (JSP) is a method for program design and modeling in the small.
4.2 ALGORITHM DESIGN METHODS 4.2.2 JACKSON STRUCTURED PROGRAMMING (JSP) JACKSON STRUCTURED PROGRAMMING (JSP) Jackson Structured Programming (JSP) is a method for program design and modeling in the small.
Equivalence Class Partitioning. Equivalence Partitioning. Definition and Example. Example set of classes
 Equivalence Class Partitioning Equivalence Partitioning From S. Somé, A. Williams 1 Suppose that we were going to test a method that implements the absolute value function for integers. Definition public
Equivalence Class Partitioning Equivalence Partitioning From S. Somé, A. Williams 1 Suppose that we were going to test a method that implements the absolute value function for integers. Definition public
Definitions. Key Objectives
 CHAPTER 2 Definitions Key Objectives & Types of models & & Black box versus white box Definition of a test Functional verification requires that several elements are in place. It relies on the ability
CHAPTER 2 Definitions Key Objectives & Types of models & & Black box versus white box Definition of a test Functional verification requires that several elements are in place. It relies on the ability
Object-Oriented Software Engineering Practical Software Development using UML and Java
 Object-Oriented Software Engineering Practical Software Development using UML and Java Chapter 10: Testing and Inspecting to Ensure High Quality Lecture 3 Errors and failure Inputs Error revealing inputs
Object-Oriented Software Engineering Practical Software Development using UML and Java Chapter 10: Testing and Inspecting to Ensure High Quality Lecture 3 Errors and failure Inputs Error revealing inputs
Chapter 3: Dynamic Testing Techniques
 Chapter 3: Dynamic Testing Techniques " The system was not fully tested to a satisfactory level of quality and resilience before full implementation on 26 October 1992." Extract from the main conclusions
Chapter 3: Dynamic Testing Techniques " The system was not fully tested to a satisfactory level of quality and resilience before full implementation on 26 October 1992." Extract from the main conclusions
Software Testing. Software Testing. Theory, Practise and Reality IBM Corporation
 Software Testing Software Testing Theory, Practise and Reality Who am I? David Vines (dvines@uk.ibm.com) Degree in Computer Science and Operational Research Joined IBM in 1984 Been involved in product
Software Testing Software Testing Theory, Practise and Reality Who am I? David Vines (dvines@uk.ibm.com) Degree in Computer Science and Operational Research Joined IBM in 1984 Been involved in product
**BEFORE YOU BEGIN: PLEASE NOTE **
 **BEFORE YOU BEGIN: PLEASE NOTE ** Primary Season Ticket Members can perform ticket exchanges before a game is played, either online through MyBlueJays, or in person at the Rogers Centre Box Office. All
**BEFORE YOU BEGIN: PLEASE NOTE ** Primary Season Ticket Members can perform ticket exchanges before a game is played, either online through MyBlueJays, or in person at the Rogers Centre Box Office. All
Chapter 2: The Normal Distribution
 Chapter 2: The Normal Distribution 2.1 Density Curves and the Normal Distributions 2.2 Standard Normal Calculations 1 2 Histogram for Strength of Yarn Bobbins 15.60 16.10 16.60 17.10 17.60 18.10 18.60
Chapter 2: The Normal Distribution 2.1 Density Curves and the Normal Distributions 2.2 Standard Normal Calculations 1 2 Histogram for Strength of Yarn Bobbins 15.60 16.10 16.60 17.10 17.60 18.10 18.60
CS 5803 Introduction to High Performance Computer Architecture: RISC vs. CISC. A.R. Hurson 323 Computer Science Building, Missouri S&T
 CS 5803 Introduction to High Performance Computer Architecture: RISC vs. CISC A.R. Hurson 323 Computer Science Building, Missouri S&T hurson@mst.edu 1 Outline How to improve CPU time? Complex Instruction
CS 5803 Introduction to High Performance Computer Architecture: RISC vs. CISC A.R. Hurson 323 Computer Science Building, Missouri S&T hurson@mst.edu 1 Outline How to improve CPU time? Complex Instruction
A Proposed Method in Agile Practices to Create Requirements Documentation and Test Cases
 A Proposed Method in Agile Practices to Create Requirements Documentation and Cases Palash Bera 1 and Abhimanyu Gupta 2 1 Saint Louis University pbera@slu.edu 2 Saint Louis University abhimanyugupta@slu.edu
A Proposed Method in Agile Practices to Create Requirements Documentation and Cases Palash Bera 1 and Abhimanyu Gupta 2 1 Saint Louis University pbera@slu.edu 2 Saint Louis University abhimanyugupta@slu.edu
14.1 Answer: 14.2 Answer: 14.3 Answer: 14.4 Answer:
 14.1 Suppose that there is a database system that never fails. Is a recovery manager required for this system? Even in this case the recovery manager is needed to perform roll-back of aborted transactions.
14.1 Suppose that there is a database system that never fails. Is a recovery manager required for this system? Even in this case the recovery manager is needed to perform roll-back of aborted transactions.
