Lecture 7. SchemeList, finish up; Universal Hashing introduction
|
|
|
- Sheila Haynes
- 6 years ago
- Views:
Transcription
1 Lecture 7. SchemeList, finish up; Universal Hashing introduction CS 16 February 24, / 15
2 foldleft #!/usr/bin/python def foldleft(func, slist, init): foldleft: (<a> * <b> -> <a>) * (<b> SchemeList) * <a> -> <a> Consumes: a function of two parameters, of types <a> and <b>, returning type <a> a SchemeList whose entries are all of type <b>, and a value of type <a> Produces: a value Purpose: apply func over slist left to right, at first with init as the left arg, and subsequently with the previous result as the left arg. if slist.isempty(): return init else: val = func(init, slist.first()) return foldleft(func, slist.rest(), val) 2 / 15
3 foldleft, applied #!/usr/bin/python def length(slist) : foldl(lambda x, y: x + 1, slist, 0) def contains(slist, item) : foldl(lambda x, y: x (y == item), slist, False) def list_max(slist) : <fill in here to test your understanding> def odd_count(slist) : <fill in here to test your understanding> 3 / 15
4 Analysis of foldleft If the list has n items, and the function being folded takes time T... then the total time is O(nT ), Reason: let F (n) be the time taken by foldleft on a list of size n Then F (0) = C and F (n) K + T + F (n 1) for some constants C and K. Use induction to conclude F (n) MnT for some constant M. n.b.: it s possible that T may depend on n! 4 / 15
5 reverse def reverse(slist): reverse: SchemeList -> SchemeList Consumes: a SchemeList Produces: a SchemeList Purpose: to reverse slist if slist.isempty(): return slist else: r = reverse(slist.rest()) return append(r, slist.first()) def append(slist, item): append: SchemeList * any -> SchemeList Consumes: a SchemeList, a value Produces: a SchemeList Purpose: add item to the end of slist if slist.isempty(): return SchemeList.makeCons(item, slist) else: a = append(slist.rest(), item) return SchemeList.makeCons(slist.first(), a) 5 / 15
6 reverse Let A(n) be running time of append on list of length n By usual analysis, A(n) cn, i.e., it s O(n n) Let R(n) be running time of reverse on list of length n Then R(0) = C and R(n) K + A(n 1) + R(n 1) for n > 1 Plug-n-chug to see that R(n) nk + c((n 1) + (n 2) ) for n > 1. Then use induction to prove that (omitted) Conclude that R(n) is O(n n 2 ) 6 / 15
7 fast reverse #!/usr/bin/python def fast_reverse(slist): fast_reverse: SchemeList -> SchemeList Consumes: a SchemeList Produces: a SchemeList Purpose: to reverse slist return fr_helper(slist, SchemeList.empty()) def fr_helper(slist, partial): Consumes: two SchemeLists Produces: a SchemeList Purpose: helper function to fast_reverse if slist.isempty(): return partial else: return fr_helper(slist.rest(), SchemeList.makeCons(slist.first(), partia 7 / 15
8 Elegant,. high-level fast reverse #!/usr/bin/python def fast_reverse(slist): fast_reverse: SchemeList -> SchemeList Consumes: a SchemeList Produces: a SchemeList Purpose: to reverse slist return foldleft(schemelist.makecons, slist, SchemeList.empty()) Notice that all recursion is hidden in the folding! 8 / 15
9 Hashing Goal: to implement the Dictionary ADT so that insert, find, delete all are O(n 1) Application: maintain a table of about 250 IP addresses (each of which consists of four bytes, as in ; the individual numbers are between 0 and 255). Could implement Dictionary as a SchemeList of (key, value) pairs. insert is O(n 1) find and delete are O(n n) this is OK for very small dictionaries 9 / 15
10 Hashing IP addresses Idea 1: make an array where the index is a 32-bit integer corresponding to the four bytes of IP address. VERY large, very empty. Not good. Idea 2: make a table of 256 entries, and use the last byte of the IP address as index Problem: collisions. Solution: Each table entry is a SchemeList! Problem: if all IP addresses fall in one bucket, then find is O(n n) If we use any small table, this is bound to happen in some bad case We ll show a way to guarantee that such bad performance is extremely unlikely. Read pages of Dasgupta et al. 10 / 15
11 Introduction to Probability Goal: to make a mathematical model of everyday reasoning about how likely things are Clever idea: replace the idea of a single coin-flip with a set containing two possible outcomes, and the probability of each. Reason about this set! 11 / 15
12 Probability Space A probability space is a finite set S, together with... a function p : S R, satisfying: P 0 p(s) 1 for every s S s S p(s) = 1 Example: S 1 = {H, T } and p(h) = 0.5 and P(T ) = 0.5. This is a model of a fair coin toss. 12 / 15
13 Probability Space, II Example2: S 2 = {1, 2, 3, 4, 5, 6} and p(i) = 1/6 for i = 1, 2,..., 6. This is a model of a fair roll of a die. 13 / 15
14 Event An event is a subset E of a probability space S. For the coin-toss example, possible events are {}, {H},{T } and {H, T }. These correspond to The coin doesn t land on either face The coin comes up heads The coin comes up tails The coin comes up either heads or tails The probability of an event E is Pr{E} = P s E p(s). In the examples, Pr{} = 0, Pr{H} = 0.5, Pr{T } = 0.5, and Pr{H, T } = 1.0. Correspond to the notions that the coin never lands on its edge, heads and tails are equally likely, and the coin always comes up heads or tails. 14 / 15
15 Random Variable An random variable (or RV ) on a probability space S is a function X : S R. For the coin-toss example, if I agree to pay Ben $100 if the coin comes up heads, but $0 if it comes up tails... we can model Ben s winnings with a random variable: X (H) = 100; X (T ) = 0 Notice that X is just a function! It s not a variable, and it s not random! Next class: expected value of a random variable. 15 / 15
Solution: It may be helpful to list out exactly what is in each of these events:
 MATH 5010(002) Fall 2017 Homework 1 Solutions Please inform your instructor if you find any errors in the solutions. 1. You ask a friend to choose an integer N between 0 and 9. Let A = {N 5}, B = {3 N
MATH 5010(002) Fall 2017 Homework 1 Solutions Please inform your instructor if you find any errors in the solutions. 1. You ask a friend to choose an integer N between 0 and 9. Let A = {N 5}, B = {3 N
1 Probability Review. CS 124 Section #8 Hashing, Skip Lists 3/20/17. Expectation (weighted average): the expectation of a random quantity X is:
 CS 124 Section #8 Hashing, Skip Lists 3/20/17 1 Probability Review Expectation (weighted average): the expectation of a random quantity X is: x= x P (X = x) For each value x that X can take on, we look
CS 124 Section #8 Hashing, Skip Lists 3/20/17 1 Probability Review Expectation (weighted average): the expectation of a random quantity X is: x= x P (X = x) For each value x that X can take on, we look
Discrete Mathematics and Probability Theory Fall 2013 Midterm #2
 CS 70 Discrete Mathematics and Probability Theory Fall 013 Midterm # 1. (30 points) Short Answer. No justification necessary. Please write only the answer in the space provided after each question. Please
CS 70 Discrete Mathematics and Probability Theory Fall 013 Midterm # 1. (30 points) Short Answer. No justification necessary. Please write only the answer in the space provided after each question. Please
1KOd17RMoURxjn2 CSE 20 DISCRETE MATH Fall
 CSE 20 https://goo.gl/forms/1o 1KOd17RMoURxjn2 DISCRETE MATH Fall 2017 http://cseweb.ucsd.edu/classes/fa17/cse20-ab/ Today's learning goals Explain the steps in a proof by mathematical and/or structural
CSE 20 https://goo.gl/forms/1o 1KOd17RMoURxjn2 DISCRETE MATH Fall 2017 http://cseweb.ucsd.edu/classes/fa17/cse20-ab/ Today's learning goals Explain the steps in a proof by mathematical and/or structural
Skip Lists S 3 S 2 S 1. Skip Lists Goodrich, Tamassia
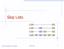 Skip Lists S 3 15 15 23 10 15 23 36 Skip Lists 1 What is a Skip List A skip list for a set S of distinct (key, element) items is a series of lists,,, S h such that Each list S i contains the special keys
Skip Lists S 3 15 15 23 10 15 23 36 Skip Lists 1 What is a Skip List A skip list for a set S of distinct (key, element) items is a series of lists,,, S h such that Each list S i contains the special keys
COT 3100 Spring 2010 Midterm 2
 COT 3100 Spring 2010 Midterm 2 For the first two questions #1 and #2, do ONLY ONE of them. If you do both, only question #1 will be graded. 1. (20 pts) Give iterative and recursive algorithms for finding
COT 3100 Spring 2010 Midterm 2 For the first two questions #1 and #2, do ONLY ONE of them. If you do both, only question #1 will be graded. 1. (20 pts) Give iterative and recursive algorithms for finding
F28PL1 Programming Languages. Lecture 14: Standard ML 4
 F28PL1 Programming Languages Lecture 14: Standard ML 4 Polymorphic list operations length of list base case: [] ==> 0 recursion case: (h::t) => 1 more than length of t - fun length [] = 0 length (_::t)
F28PL1 Programming Languages Lecture 14: Standard ML 4 Polymorphic list operations length of list base case: [] ==> 0 recursion case: (h::t) => 1 more than length of t - fun length [] = 0 length (_::t)
Python review. 1 Python basics. References. CS 234 Naomi Nishimura
 Python review CS 234 Naomi Nishimura The sections below indicate Python material, the degree to which it will be used in the course, and various resources you can use to review the material. You are not
Python review CS 234 Naomi Nishimura The sections below indicate Python material, the degree to which it will be used in the course, and various resources you can use to review the material. You are not
User-defined Functions. Conditional Expressions in Scheme
 User-defined Functions The list (lambda (args (body s to a function with (args as its argument list and (body as the function body. No quotes are needed for (args or (body. (lambda (x (+ x 1 s to the increment
User-defined Functions The list (lambda (args (body s to a function with (args as its argument list and (body as the function body. No quotes are needed for (args or (body. (lambda (x (+ x 1 s to the increment
Interpreters and Tail Calls Fall 2017 Discussion 8: November 1, 2017 Solutions. 1 Calculator. calc> (+ 2 2) 4
 CS 61A Interpreters and Tail Calls Fall 2017 Discussion 8: November 1, 2017 Solutions 1 Calculator We are beginning to dive into the realm of interpreting computer programs that is, writing programs that
CS 61A Interpreters and Tail Calls Fall 2017 Discussion 8: November 1, 2017 Solutions 1 Calculator We are beginning to dive into the realm of interpreting computer programs that is, writing programs that
UCSD CSE 21, Spring 2014 [Section B00] Mathematics for Algorithm and System Analysis
![UCSD CSE 21, Spring 2014 [Section B00] Mathematics for Algorithm and System Analysis UCSD CSE 21, Spring 2014 [Section B00] Mathematics for Algorithm and System Analysis](/thumbs/89/99028465.jpg) UCSD CSE 21, Spring 2014 [Section B00] Mathematics for Algorithm and System Analysis Lecture 11 Class URL: http://vlsicad.ucsd.edu/courses/cse21-s14/ Lecture 11 Notes Goals for this week (Tuesday) Linearity
UCSD CSE 21, Spring 2014 [Section B00] Mathematics for Algorithm and System Analysis Lecture 11 Class URL: http://vlsicad.ucsd.edu/courses/cse21-s14/ Lecture 11 Notes Goals for this week (Tuesday) Linearity
Fall Lecture 3 September 4. Stephen Brookes
 15-150 Fall 2018 Lecture 3 September 4 Stephen Brookes Today A brief remark about equality types Using patterns Specifying what a function does equality in ML e1 = e2 Only for expressions whose type is
15-150 Fall 2018 Lecture 3 September 4 Stephen Brookes Today A brief remark about equality types Using patterns Specifying what a function does equality in ML e1 = e2 Only for expressions whose type is
Midterm Exam 2B Answer key
 Midterm Exam 2B Answer key 15110 Principles of Computing Fall 2015 April 6, 2015 Name: Andrew ID: Lab section: Instructions Answer each question neatly in the space provided. There are 6 questions totaling
Midterm Exam 2B Answer key 15110 Principles of Computing Fall 2015 April 6, 2015 Name: Andrew ID: Lab section: Instructions Answer each question neatly in the space provided. There are 6 questions totaling
Lecture Notes for Chapter 2: Getting Started
 Instant download and all chapters Instructor's Manual Introduction To Algorithms 2nd Edition Thomas H. Cormen, Clara Lee, Erica Lin https://testbankdata.com/download/instructors-manual-introduction-algorithms-2ndedition-thomas-h-cormen-clara-lee-erica-lin/
Instant download and all chapters Instructor's Manual Introduction To Algorithms 2nd Edition Thomas H. Cormen, Clara Lee, Erica Lin https://testbankdata.com/download/instructors-manual-introduction-algorithms-2ndedition-thomas-h-cormen-clara-lee-erica-lin/
CSC 1351: Quiz 6: Sort and Search
 CSC 1351: Quiz 6: Sort and Search Name: 0.1 You want to implement combat within a role playing game on a computer. Specifically, the game rules for damage inflicted by a hit are: In order to figure out
CSC 1351: Quiz 6: Sort and Search Name: 0.1 You want to implement combat within a role playing game on a computer. Specifically, the game rules for damage inflicted by a hit are: In order to figure out
Randomized Algorithms, Hash Functions
 Randomized Algorithms, Hash Functions Lecture A Tiefenbruck MWF 9-9:50am Center 212 Lecture B Jones MWF 2-2:50pm Center 214 Lecture C Tiefenbruck MWF 11-11:50am Center 212 http://cseweb.ucsd.edu/classes/wi16/cse21-abc/
Randomized Algorithms, Hash Functions Lecture A Tiefenbruck MWF 9-9:50am Center 212 Lecture B Jones MWF 2-2:50pm Center 214 Lecture C Tiefenbruck MWF 11-11:50am Center 212 http://cseweb.ucsd.edu/classes/wi16/cse21-abc/
Structure and Interpretation of Computer Programs
 CS 6A Fall 206 Structure and Interpretation of Computer Programs Final Solutions INSTRUCTIONS You have hours to complete the exam. The exam is closed book, closed notes, closed computer, closed calculator,
CS 6A Fall 206 Structure and Interpretation of Computer Programs Final Solutions INSTRUCTIONS You have hours to complete the exam. The exam is closed book, closed notes, closed computer, closed calculator,
function [A,V,a] = spherical cap(r,h) % Returns the area, volume and radius of a spherical cap % cut from a sphere of radius r, and cap height h
![function [A,V,a] = spherical cap(r,h) % Returns the area, volume and radius of a spherical cap % cut from a sphere of radius r, and cap height h function [A,V,a] = spherical cap(r,h) % Returns the area, volume and radius of a spherical cap % cut from a sphere of radius r, and cap height h](/thumbs/80/81585938.jpg) 1 Spherical Cap 1.a Area and Volume In this part all you have to do is to transfer the given mathematical formulas into assignments using arithmetic operators in MATLAB. When you run the script file, test
1 Spherical Cap 1.a Area and Volume In this part all you have to do is to transfer the given mathematical formulas into assignments using arithmetic operators in MATLAB. When you run the script file, test
Mini-ML. CS 502 Lecture 2 8/28/08
 Mini-ML CS 502 Lecture 2 8/28/08 ML This course focuses on compilation techniques for functional languages Programs expressed in Standard ML Mini-ML (the source language) is an expressive core subset of
Mini-ML CS 502 Lecture 2 8/28/08 ML This course focuses on compilation techniques for functional languages Programs expressed in Standard ML Mini-ML (the source language) is an expressive core subset of
Recap from last time. Programming Languages. CSE 130 : Fall Lecture 3: Data Types. Put it together: a filter function
 CSE 130 : Fall 2011 Recap from last time Programming Languages Lecture 3: Data Types Ranjit Jhala UC San Diego 1 2 A shorthand for function binding Put it together: a filter function # let neg = fun f
CSE 130 : Fall 2011 Recap from last time Programming Languages Lecture 3: Data Types Ranjit Jhala UC San Diego 1 2 A shorthand for function binding Put it together: a filter function # let neg = fun f
CS Lecture 6: Map and Fold. Prof. Clarkson Fall Today s music: Selections from the soundtrack to 2001: A Space Odyssey
 CS 3110 Lecture 6: Map and Fold Prof. Clarkson Fall 2014 Today s music: Selections from the soundtrack to 2001: A Space Odyssey Review Features so far: variables, operators, let expressions, if expressions,
CS 3110 Lecture 6: Map and Fold Prof. Clarkson Fall 2014 Today s music: Selections from the soundtrack to 2001: A Space Odyssey Review Features so far: variables, operators, let expressions, if expressions,
CS 321 Programming Languages
 CS 321 Programming Languages Intro to OCaml Lists Baris Aktemur Özyeğin University Last update made on Monday 2 nd October, 2017 at 19:27. Some of the contents here are taken from Elsa Gunter and Sam Kamin
CS 321 Programming Languages Intro to OCaml Lists Baris Aktemur Özyeğin University Last update made on Monday 2 nd October, 2017 at 19:27. Some of the contents here are taken from Elsa Gunter and Sam Kamin
Discrete Mathematics Course Review 3
 21-228 Discrete Mathematics Course Review 3 This document contains a list of the important definitions and theorems that have been covered thus far in the course. It is not a complete listing of what has
21-228 Discrete Mathematics Course Review 3 This document contains a list of the important definitions and theorems that have been covered thus far in the course. It is not a complete listing of what has
Map and Fold. Prof. Clarkson Fall Today s music: Selections from the soundtrack to 2001: A Space Odyssey
 Map and Fold Prof. Clarkson Fall 2015 Today s music: Selections from the soundtrack to 2001: A Space Odyssey Question How much progress have you made on A1? A. I'm still figuring out how Enigma works.
Map and Fold Prof. Clarkson Fall 2015 Today s music: Selections from the soundtrack to 2001: A Space Odyssey Question How much progress have you made on A1? A. I'm still figuring out how Enigma works.
Lecture 15 Binary Search Trees
 Lecture 15 Binary Search Trees 15-122: Principles of Imperative Computation (Fall 2017) Frank Pfenning, André Platzer, Rob Simmons, Iliano Cervesato In this lecture, we will continue considering ways to
Lecture 15 Binary Search Trees 15-122: Principles of Imperative Computation (Fall 2017) Frank Pfenning, André Platzer, Rob Simmons, Iliano Cervesato In this lecture, we will continue considering ways to
Graph Contraction. Graph Contraction CSE341T/CSE549T 10/20/2014. Lecture 14
 CSE341T/CSE549T 10/20/2014 Lecture 14 Graph Contraction Graph Contraction So far we have mostly talking about standard techniques for solving problems on graphs that were developed in the context of sequential
CSE341T/CSE549T 10/20/2014 Lecture 14 Graph Contraction Graph Contraction So far we have mostly talking about standard techniques for solving problems on graphs that were developed in the context of sequential
(a) (4 pts) Prove that if a and b are rational, then ab is rational. Since a and b are rational they can be written as the ratio of integers a 1
 CS 70 Discrete Mathematics for CS Fall 2000 Wagner MT1 Sol Solutions to Midterm 1 1. (16 pts.) Theorems and proofs (a) (4 pts) Prove that if a and b are rational, then ab is rational. Since a and b are
CS 70 Discrete Mathematics for CS Fall 2000 Wagner MT1 Sol Solutions to Midterm 1 1. (16 pts.) Theorems and proofs (a) (4 pts) Prove that if a and b are rational, then ab is rational. Since a and b are
CS302 Data Structures using C++
 CS302 Data Structures using C++ Study Guide for the Final Exam Fall 2018 Revision 1.1 This document serves to help you prepare towards the final exam for the Fall 2018 semester. 1. What topics are to be
CS302 Data Structures using C++ Study Guide for the Final Exam Fall 2018 Revision 1.1 This document serves to help you prepare towards the final exam for the Fall 2018 semester. 1. What topics are to be
Functional Programming. Pure Functional Programming
 Functional Programming Pure Functional Programming Computation is largely performed by applying functions to values. The value of an expression depends only on the values of its sub-expressions (if any).
Functional Programming Pure Functional Programming Computation is largely performed by applying functions to values. The value of an expression depends only on the values of its sub-expressions (if any).
CS1800 Discrete Structures Final Version B
 CS1800 Discrete Structures Fall 2017 Profs. Aslam, Gold, & Pavlu December 15, 2017 CS1800 Discrete Structures Final Version B Instructions: 1. The exam is closed book and closed notes. You may not use
CS1800 Discrete Structures Fall 2017 Profs. Aslam, Gold, & Pavlu December 15, 2017 CS1800 Discrete Structures Final Version B Instructions: 1. The exam is closed book and closed notes. You may not use
CS 61B Discussion 5: Inheritance II Fall 2014
 CS 61B Discussion 5: Inheritance II Fall 2014 1 WeirdList Below is a partial solution to the WeirdList problem from homework 3 showing only the most important lines. Part A. Complete the implementation
CS 61B Discussion 5: Inheritance II Fall 2014 1 WeirdList Below is a partial solution to the WeirdList problem from homework 3 showing only the most important lines. Part A. Complete the implementation
4.2 Function definitions the basics
 4.2. FUNCTION DEFINITIONS THE BASICS 89 4.2 Function definitions the basics There are three questions you must answer before you can write a function definition: What will the function do? What inputs
4.2. FUNCTION DEFINITIONS THE BASICS 89 4.2 Function definitions the basics There are three questions you must answer before you can write a function definition: What will the function do? What inputs
CMSC 330: Organization of Programming Languages. Functional Programming with Lists
 CMSC 330: Organization of Programming Languages Functional Programming with Lists 1 Lists in OCaml The basic data structure in OCaml Lists can be of arbitrary length Implemented as a linked data structure
CMSC 330: Organization of Programming Languages Functional Programming with Lists 1 Lists in OCaml The basic data structure in OCaml Lists can be of arbitrary length Implemented as a linked data structure
PROGRAMMING IN HASKELL. CS Chapter 6 - Recursive Functions
 PROGRAMMING IN HASKELL CS-205 - Chapter 6 - Recursive Functions 0 Introduction As we have seen, many functions can naturally be defined in terms of other functions. factorial :: Int Int factorial n product
PROGRAMMING IN HASKELL CS-205 - Chapter 6 - Recursive Functions 0 Introduction As we have seen, many functions can naturally be defined in terms of other functions. factorial :: Int Int factorial n product
Sorting. There exist sorting algorithms which have shown to be more efficient in practice.
 Sorting Next to storing and retrieving data, sorting of data is one of the more common algorithmic tasks, with many different ways to perform it. Whenever we perform a web search and/or view statistics
Sorting Next to storing and retrieving data, sorting of data is one of the more common algorithmic tasks, with many different ways to perform it. Whenever we perform a web search and/or view statistics
Denotational Semantics
 Denotational Semantics 8 12 lectures for Part II CST 2010/11 Marcelo Fiore Course web page: http://www.cl.cam.ac.uk/teaching/1011/denotsem/ 1 Lecture 1 Introduction 2 What is this course about? General
Denotational Semantics 8 12 lectures for Part II CST 2010/11 Marcelo Fiore Course web page: http://www.cl.cam.ac.uk/teaching/1011/denotsem/ 1 Lecture 1 Introduction 2 What is this course about? General
CIS192 Python Programming
 CIS192 Python Programming Probability, Simulations & Course Wrap-Up Raymond Yin University of Pennsylvania December 8, 2016 Raymond Yin (University of Pennsylvania) CIS 192 December 8, 2016 1 / 21 Outline
CIS192 Python Programming Probability, Simulations & Course Wrap-Up Raymond Yin University of Pennsylvania December 8, 2016 Raymond Yin (University of Pennsylvania) CIS 192 December 8, 2016 1 / 21 Outline
Problem Set 4 Solutions
 Design and Analysis of Algorithms March 5, 205 Massachusetts Institute of Technology 6.046J/8.40J Profs. Erik Demaine, Srini Devadas, and Nancy Lynch Problem Set 4 Solutions Problem Set 4 Solutions This
Design and Analysis of Algorithms March 5, 205 Massachusetts Institute of Technology 6.046J/8.40J Profs. Erik Demaine, Srini Devadas, and Nancy Lynch Problem Set 4 Solutions Problem Set 4 Solutions This
Lecture 6: Sequential Sorting
 15-150 Lecture 6: Sequential Sorting Lecture by Dan Licata February 2, 2012 Today s lecture is about sorting. Along the way, we ll learn about divide and conquer algorithms, the tree method, and complete
15-150 Lecture 6: Sequential Sorting Lecture by Dan Licata February 2, 2012 Today s lecture is about sorting. Along the way, we ll learn about divide and conquer algorithms, the tree method, and complete
Abstract Data Types. CS 234, Fall Types, Data Types Abstraction Abstract Data Types Preconditions, Postconditions ADT Examples
 Abstract Data Types CS 234, Fall 2017 Types, Data Types Abstraction Abstract Data Types Preconditions, Postconditions ADT Examples Data Types Data is stored in a computer as a sequence of binary digits:
Abstract Data Types CS 234, Fall 2017 Types, Data Types Abstraction Abstract Data Types Preconditions, Postconditions ADT Examples Data Types Data is stored in a computer as a sequence of binary digits:
CMSC 330, Fall 2013, Practice Problems 3
 CMSC 330, Fall 2013, Practice Problems 3 1. OCaml and Functional Programming a. Define functional programming b. Define imperative programming c. Define higher-order functions d. Describe the relationship
CMSC 330, Fall 2013, Practice Problems 3 1. OCaml and Functional Programming a. Define functional programming b. Define imperative programming c. Define higher-order functions d. Describe the relationship
CHAPTER 9 HASH TABLES, MAPS, AND SKIP LISTS
 0 1 2 025-612-0001 981-101-0002 3 4 451-229-0004 CHAPTER 9 HASH TABLES, MAPS, AND SKIP LISTS ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH,
0 1 2 025-612-0001 981-101-0002 3 4 451-229-0004 CHAPTER 9 HASH TABLES, MAPS, AND SKIP LISTS ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH,
TAIL RECURSION, SCOPE, AND PROJECT 4 11
 TAIL RECURSION, SCOPE, AND PROJECT 4 11 COMPUTER SCIENCE 61A Noveber 12, 2012 1 Tail Recursion Today we will look at Tail Recursion and Tail Call Optimizations in Scheme, and how they relate to iteration
TAIL RECURSION, SCOPE, AND PROJECT 4 11 COMPUTER SCIENCE 61A Noveber 12, 2012 1 Tail Recursion Today we will look at Tail Recursion and Tail Call Optimizations in Scheme, and how they relate to iteration
CS Lecture 6: Map and Fold. Prof. Clarkson Spring Today s music: Selections from the soundtrack to 2001: A Space Odyssey
 CS 3110 Lecture 6: Map and Fold Prof. Clarkson Spring 2015 Today s music: Selections from the soundtrack to 2001: A Space Odyssey Review Course so far: Syntax and semantics of (most of) OCaml Today: No
CS 3110 Lecture 6: Map and Fold Prof. Clarkson Spring 2015 Today s music: Selections from the soundtrack to 2001: A Space Odyssey Review Course so far: Syntax and semantics of (most of) OCaml Today: No
Induction and Semantics in Dafny
 15-414 Lecture 11 1 Instructor: Matt Fredrikson Induction and Semantics in Dafny TA: Ryan Wagner Encoding the syntax of Imp Recall the abstract syntax of Imp: a AExp ::= n Z x Var a 1 + a 2 b BExp ::=
15-414 Lecture 11 1 Instructor: Matt Fredrikson Induction and Semantics in Dafny TA: Ryan Wagner Encoding the syntax of Imp Recall the abstract syntax of Imp: a AExp ::= n Z x Var a 1 + a 2 b BExp ::=
Structure and Interpretation of Computer Programs
 CS 6A Fall 25 Structure and Interpretation of Computer Programs Midterm 2 Solutions INSTRUCTIONS You have 2 hours to complete the exam. The exam is closed book, closed notes, closed computer, closed calculator,
CS 6A Fall 25 Structure and Interpretation of Computer Programs Midterm 2 Solutions INSTRUCTIONS You have 2 hours to complete the exam. The exam is closed book, closed notes, closed computer, closed calculator,
/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Sorting lower bound and Linear-time sorting Date: 9/19/17
 601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Sorting lower bound and Linear-time sorting Date: 9/19/17 5.1 Introduction You should all know a few ways of sorting in O(n log n)
601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Sorting lower bound and Linear-time sorting Date: 9/19/17 5.1 Introduction You should all know a few ways of sorting in O(n log n)
Analyze the obvious algorithm, 5 points Here is the most obvious algorithm for this problem: (LastLargerElement[A[1..n]:
![Analyze the obvious algorithm, 5 points Here is the most obvious algorithm for this problem: (LastLargerElement[A[1..n]: Analyze the obvious algorithm, 5 points Here is the most obvious algorithm for this problem: (LastLargerElement[A[1..n]:](/thumbs/90/104324109.jpg) CSE 101 Homework 1 Background (Order and Recurrence Relations), correctness proofs, time analysis, and speeding up algorithms with restructuring, preprocessing and data structures. Due Thursday, April
CSE 101 Homework 1 Background (Order and Recurrence Relations), correctness proofs, time analysis, and speeding up algorithms with restructuring, preprocessing and data structures. Due Thursday, April
Structure and Interpretation of Computer Programs
 CS 61A Fall 2016 Structure and Interpretation of Computer Programs Final INSTRUCTIONS You have 3 hours to complete the exam. The exam is closed book, closed notes, closed computer, closed calculator, except
CS 61A Fall 2016 Structure and Interpretation of Computer Programs Final INSTRUCTIONS You have 3 hours to complete the exam. The exam is closed book, closed notes, closed computer, closed calculator, except
Lecture 3.4: Recursive Algorithms
 Lecture 3.4: Recursive Algorithms CS 250, Discrete Structures, Fall 2014 Nitesh Saxena Adopted from previous lectures by Zeph Grunschlag Course Admin Graded Mid-Term 1 Please pick them up, if you haven
Lecture 3.4: Recursive Algorithms CS 250, Discrete Structures, Fall 2014 Nitesh Saxena Adopted from previous lectures by Zeph Grunschlag Course Admin Graded Mid-Term 1 Please pick them up, if you haven
Solutions to Problem Set 1
 CSCI-GA.3520-001 Honors Analysis of Algorithms Solutions to Problem Set 1 Problem 1 An O(n) algorithm that finds the kth integer in an array a = (a 1,..., a n ) of n distinct integers. Basic Idea Using
CSCI-GA.3520-001 Honors Analysis of Algorithms Solutions to Problem Set 1 Problem 1 An O(n) algorithm that finds the kth integer in an array a = (a 1,..., a n ) of n distinct integers. Basic Idea Using
Statistical Computing
 SERIES I ARTICLE Statistical Computing 1. Understanding Randomness and Random Numbers Sudhakar Kunte Elements of statistical computing are discussed in this series. We begin with the notion of random numbers
SERIES I ARTICLE Statistical Computing 1. Understanding Randomness and Random Numbers Sudhakar Kunte Elements of statistical computing are discussed in this series. We begin with the notion of random numbers
Agenda. We ve done Growth of functions Asymptotic Notations (O, o,,!, ) Now Binary search as an example Recurrence relations, solving them
 Agenda We ve done Growth of functions Asymptotic Notations (O, o,,!, ) Now Binary search as an example Recurrence relations, solving them c Hung Q. Ngo (SUNY at Buffalo) CSE 250 Data Structures in C++
Agenda We ve done Growth of functions Asymptotic Notations (O, o,,!, ) Now Binary search as an example Recurrence relations, solving them c Hung Q. Ngo (SUNY at Buffalo) CSE 250 Data Structures in C++
Fall 2017 December 4, Scheme. Instructions
 CS 61A Final Review Fall 2017 December 4, 2017 Instructions Form a small group. Start on the first problem. Check off with a helper or discuss your solution process with another group once everyone understands
CS 61A Final Review Fall 2017 December 4, 2017 Instructions Form a small group. Start on the first problem. Check off with a helper or discuss your solution process with another group once everyone understands
Lecture 9: Sorting Algorithms
 Lecture 9: Sorting Algorithms Bo Tang @ SUSTech, Spring 2018 Sorting problem Sorting Problem Input: an array A[1..n] with n integers Output: a sorted array A (in ascending order) Problem is: sort A[1..n]
Lecture 9: Sorting Algorithms Bo Tang @ SUSTech, Spring 2018 Sorting problem Sorting Problem Input: an array A[1..n] with n integers Output: a sorted array A (in ascending order) Problem is: sort A[1..n]
CMSC 330: Organization of Programming Languages. Functional Programming with Lists
 CMSC 330: Organization of Programming Languages Functional Programming with Lists CMSC330 Spring 2018 1 Lists in OCaml The basic data structure in OCaml Lists can be of arbitrary length Implemented as
CMSC 330: Organization of Programming Languages Functional Programming with Lists CMSC330 Spring 2018 1 Lists in OCaml The basic data structure in OCaml Lists can be of arbitrary length Implemented as
Fall 2017 December 4, 2017
 CS 61A Final Review Fall 2017 December 4, 2017 Instructions Form a small group. Start on the first problem. Check off with a helper or discuss your solution process with another group once everyone understands
CS 61A Final Review Fall 2017 December 4, 2017 Instructions Form a small group. Start on the first problem. Check off with a helper or discuss your solution process with another group once everyone understands
Fall 2018 Lecture 1
 15-150 Fall 2018 Lecture 1 Stephen Brookes 1 Themes functional programming correctness, termination, and performance types, specifications, and proofs evaluation and equivalence referential transparency
15-150 Fall 2018 Lecture 1 Stephen Brookes 1 Themes functional programming correctness, termination, and performance types, specifications, and proofs evaluation and equivalence referential transparency
Algorithms and Data Structures (INF1) Lecture 8/15 Hua Lu
 Algorithms and Data Structures (INF1) Lecture 8/15 Hua Lu Department of Computer Science Aalborg University Fall 2007 This Lecture Trees Basics Rooted trees Binary trees Binary tree ADT Tree traversal
Algorithms and Data Structures (INF1) Lecture 8/15 Hua Lu Department of Computer Science Aalborg University Fall 2007 This Lecture Trees Basics Rooted trees Binary trees Binary tree ADT Tree traversal
Function definitions. CSE341: Programming Languages Lecture 2 Functions, Pairs, Lists. Example, extended. Some gotchas. Zach Tatlock Winter 2018
 Function definitions CSE341: Programming Languages Lecture 2 Functions, Pairs, Lists Zach Tatlock Winter 2018 Functions: the most important building block in the whole course Like Java methods, have arguments
Function definitions CSE341: Programming Languages Lecture 2 Functions, Pairs, Lists Zach Tatlock Winter 2018 Functions: the most important building block in the whole course Like Java methods, have arguments
CSE341: Programming Languages Lecture 2 Functions, Pairs, Lists. Zach Tatlock Winter 2018
 CSE341: Programming Languages Lecture 2 Functions, Pairs, Lists Zach Tatlock Winter 2018 Function definitions Functions: the most important building block in the whole course Like Java methods, have arguments
CSE341: Programming Languages Lecture 2 Functions, Pairs, Lists Zach Tatlock Winter 2018 Function definitions Functions: the most important building block in the whole course Like Java methods, have arguments
Overview. Probabilistic Programming. Dijkstra s guarded command language: Syntax. Elementary pgcl ingredients. Lecture #4: Probabilistic GCL
 Overview Lecture #4: Probabilistic GCL 1 Joost-Pieter Katoen 2 3 Recursion RWTH Lecture Series on 2018 Joost-Pieter Katoen 1/31 Joost-Pieter Katoen 2/31 Dijkstra s guarded command language: Syntax Elementary
Overview Lecture #4: Probabilistic GCL 1 Joost-Pieter Katoen 2 3 Recursion RWTH Lecture Series on 2018 Joost-Pieter Katoen 1/31 Joost-Pieter Katoen 2/31 Dijkstra s guarded command language: Syntax Elementary
INTERPRETERS 8. 1 Calculator COMPUTER SCIENCE 61A. November 3, 2016
 INTERPRETERS 8 COMPUTER SCIENCE 61A November 3, 2016 1 Calculator We are beginning to dive into the realm of interpreting computer programs that is, writing programs that understand other programs. In
INTERPRETERS 8 COMPUTER SCIENCE 61A November 3, 2016 1 Calculator We are beginning to dive into the realm of interpreting computer programs that is, writing programs that understand other programs. In
Lecture 16. Reading: Weiss Ch. 5 CSE 100, UCSD: LEC 16. Page 1 of 40
 Lecture 16 Hashing Hash table and hash function design Hash functions for integers and strings Collision resolution strategies: linear probing, double hashing, random hashing, separate chaining Hash table
Lecture 16 Hashing Hash table and hash function design Hash functions for integers and strings Collision resolution strategies: linear probing, double hashing, random hashing, separate chaining Hash table
Booleans (aka Truth Values) Programming Languages and Compilers (CS 421) Booleans and Short-Circuit Evaluation. Tuples as Values.
 Booleans (aka Truth Values) Programming Languages and Compilers (CS 421) Elsa L Gunter 2112 SC, UIUC https://courses.engr.illinois.edu/cs421/fa2017/cs421d # true;; - : bool = true # false;; - : bool =
Booleans (aka Truth Values) Programming Languages and Compilers (CS 421) Elsa L Gunter 2112 SC, UIUC https://courses.engr.illinois.edu/cs421/fa2017/cs421d # true;; - : bool = true # false;; - : bool =
CSE332 Summer 2010: Midterm Exam Sample Solutions
 CSE332 Summer 2010: Midterm Exam Sample Solutions Closed notes, closed book; calculator ok. Read the instructions for each problem carefully before answering. Problems vary in point-values, difficulty
CSE332 Summer 2010: Midterm Exam Sample Solutions Closed notes, closed book; calculator ok. Read the instructions for each problem carefully before answering. Problems vary in point-values, difficulty
CSE341: Programming Languages Lecture 2 Functions, Pairs, Lists. Dan Grossman Fall 2011
 CSE341: Programming Languages Lecture 2 Functions, Pairs, Lists Dan Grossman Fall 2011 Review Building up SML one construct at a time via precise definitions Constructs have syntax, type-checking rules,
CSE341: Programming Languages Lecture 2 Functions, Pairs, Lists Dan Grossman Fall 2011 Review Building up SML one construct at a time via precise definitions Constructs have syntax, type-checking rules,
Chapter 10 Recursion
 Chapter 10 Recursion Written by Dr. Mark Snyder [minor edits for this semester by Dr. Kinga Dobolyi] Recursion implies that something is defined in terms of itself. We will see in detail how code can be
Chapter 10 Recursion Written by Dr. Mark Snyder [minor edits for this semester by Dr. Kinga Dobolyi] Recursion implies that something is defined in terms of itself. We will see in detail how code can be
CS 139 Practice Midterm Questions #2
 CS 139 Practice Midterm Questions #2 Spring 2016 Name: 1. Write Java statements to accomplish each of the following. (a) Declares numbers to be an array of int s. (b) Initializes numbers to contain a reference
CS 139 Practice Midterm Questions #2 Spring 2016 Name: 1. Write Java statements to accomplish each of the following. (a) Declares numbers to be an array of int s. (b) Initializes numbers to contain a reference
Structure and Interpretation of Computer Programs
 CS 61A Summer 2014 Structure and Interpretation of Computer Programs Final Solutions INSTRUCTIONS ˆ You have 3 hours to complete the exam. ˆ The exam is closed book, closed notes, and closed electronics,
CS 61A Summer 2014 Structure and Interpretation of Computer Programs Final Solutions INSTRUCTIONS ˆ You have 3 hours to complete the exam. ˆ The exam is closed book, closed notes, and closed electronics,
CSE 332 Autumn 2013: Midterm Exam (closed book, closed notes, no calculators)
 Name: Email address: Quiz Section: CSE 332 Autumn 2013: Midterm Exam (closed book, closed notes, no calculators) Instructions: Read the directions for each question carefully before answering. We will
Name: Email address: Quiz Section: CSE 332 Autumn 2013: Midterm Exam (closed book, closed notes, no calculators) Instructions: Read the directions for each question carefully before answering. We will
;;; Determines if e is a primitive by looking it up in the primitive environment. ;;; Define indentation and output routines for the output for
 Page 1/11 (require (lib "trace")) Allow tracing to be turned on and off (define tracing #f) Define a string to hold the error messages created during syntax checking (define error msg ""); Used for fancy
Page 1/11 (require (lib "trace")) Allow tracing to be turned on and off (define tracing #f) Define a string to hold the error messages created during syntax checking (define error msg ""); Used for fancy
University of Illinois at Urbana-Champaign Department of Computer Science. Final Examination
 University of Illinois at Urbana-Champaign Department of Computer Science Final Examination CS 225 Data Structures and Software Principles Fall 2009 7-10p, Tuesday, December 15 Name: NetID: Lab Section
University of Illinois at Urbana-Champaign Department of Computer Science Final Examination CS 225 Data Structures and Software Principles Fall 2009 7-10p, Tuesday, December 15 Name: NetID: Lab Section
Lecture 15 Notes Binary Search Trees
 Lecture 15 Notes Binary Search Trees 15-122: Principles of Imperative Computation (Spring 2016) Frank Pfenning, André Platzer, Rob Simmons 1 Introduction In this lecture, we will continue considering ways
Lecture 15 Notes Binary Search Trees 15-122: Principles of Imperative Computation (Spring 2016) Frank Pfenning, André Platzer, Rob Simmons 1 Introduction In this lecture, we will continue considering ways
1. Find the type and value of each of the following expressions. Warning: several of these expressions will result in an error.
 This was the final CS1 exam given in May, 2014. I eliminated one question concerning classes and objects, and clarified a few points that were unclear in the original version. I also translated some things
This was the final CS1 exam given in May, 2014. I eliminated one question concerning classes and objects, and clarified a few points that were unclear in the original version. I also translated some things
CS 261: Data Structures. Skip Lists
 CS 261: Data Structures Skip Lists 1 Complexity Lists and Arrays OPERATIONS ORDINARY LISTS AND ARRAYS SORTED ARRAYS SORTED LISTS Add O(1) O(n) O(n) Remove O(n) O(n) O(n) Contains O(n) O(log n) O(n) 2 Sorted
CS 261: Data Structures Skip Lists 1 Complexity Lists and Arrays OPERATIONS ORDINARY LISTS AND ARRAYS SORTED ARRAYS SORTED LISTS Add O(1) O(n) O(n) Remove O(n) O(n) O(n) Contains O(n) O(log n) O(n) 2 Sorted
PostFix. PostFix command semanccs (except exec) PostFix Syntax. A PostFix Interpreter in Racket. CS251 Programming Languages Fall 2017, Lyn Turbak
 PostFix A PostFix Interpreter in Racket CS251 Programming Languages Fall 2017, Lyn Turbak Department of Computer Science Wellesley College PostFix is a stack-based mini-language that will be our first
PostFix A PostFix Interpreter in Racket CS251 Programming Languages Fall 2017, Lyn Turbak Department of Computer Science Wellesley College PostFix is a stack-based mini-language that will be our first
Denotational Semantics
 Denotational Semantics 10 lectures for Part II CST 2011/12 Andrew Pitts Course web page: http://www.cl.cam.ac.uk/teaching/1112/denotsem/ 1 Styles of formal semantics Operational. Meanings for program phrases
Denotational Semantics 10 lectures for Part II CST 2011/12 Andrew Pitts Course web page: http://www.cl.cam.ac.uk/teaching/1112/denotsem/ 1 Styles of formal semantics Operational. Meanings for program phrases
Intro to Algorithms. Professor Kevin Gold
 Intro to Algorithms Professor Kevin Gold What is an Algorithm? An algorithm is a procedure for producing outputs from inputs. A chocolate chip cookie recipe technically qualifies. An algorithm taught in
Intro to Algorithms Professor Kevin Gold What is an Algorithm? An algorithm is a procedure for producing outputs from inputs. A chocolate chip cookie recipe technically qualifies. An algorithm taught in
COSE212: Programming Languages. Lecture 3 Functional Programming in OCaml
 COSE212: Programming Languages Lecture 3 Functional Programming in OCaml Hakjoo Oh 2017 Fall Hakjoo Oh COSE212 2017 Fall, Lecture 3 September 18, 2017 1 / 44 Why learn ML? Learning ML is a good way of
COSE212: Programming Languages Lecture 3 Functional Programming in OCaml Hakjoo Oh 2017 Fall Hakjoo Oh COSE212 2017 Fall, Lecture 3 September 18, 2017 1 / 44 Why learn ML? Learning ML is a good way of
Lecture 15: The subspace topology, Closed sets
 Lecture 15: The subspace topology, Closed sets 1 The Subspace Topology Definition 1.1. Let (X, T) be a topological space with topology T. subset of X, the collection If Y is a T Y = {Y U U T} is a topology
Lecture 15: The subspace topology, Closed sets 1 The Subspace Topology Definition 1.1. Let (X, T) be a topological space with topology T. subset of X, the collection If Y is a T Y = {Y U U T} is a topology
Jana Kosecka. Linear Time Sorting, Median, Order Statistics. Many slides here are based on E. Demaine, D. Luebke slides
 Jana Kosecka Linear Time Sorting, Median, Order Statistics Many slides here are based on E. Demaine, D. Luebke slides Insertion sort: Easy to code Fast on small inputs (less than ~50 elements) Fast on
Jana Kosecka Linear Time Sorting, Median, Order Statistics Many slides here are based on E. Demaine, D. Luebke slides Insertion sort: Easy to code Fast on small inputs (less than ~50 elements) Fast on
Working with recursion. From definition to template. Readings: HtDP, sections 11, 12, 13 (Intermezzo 2).
 Working with recursion Readings: HtDP, sections 11, 12, 13 (Intermezzo 2). We can extend the idea of a self-referential definition to defining the natural numbers, which leads to the use of recursion in
Working with recursion Readings: HtDP, sections 11, 12, 13 (Intermezzo 2). We can extend the idea of a self-referential definition to defining the natural numbers, which leads to the use of recursion in
Copyright 2000, Kevin Wayne 1
 Guessing Game: NP-Complete? 1. LONGEST-PATH: Given a graph G = (V, E), does there exists a simple path of length at least k edges? YES. SHORTEST-PATH: Given a graph G = (V, E), does there exists a simple
Guessing Game: NP-Complete? 1. LONGEST-PATH: Given a graph G = (V, E), does there exists a simple path of length at least k edges? YES. SHORTEST-PATH: Given a graph G = (V, E), does there exists a simple
Section 05: Solutions
 Section 05: Solutions 1. Memory and B-Tree (a) Based on your understanding of how computers access and store memory, why might it be faster to access all the elements of an array-based queue than to access
Section 05: Solutions 1. Memory and B-Tree (a) Based on your understanding of how computers access and store memory, why might it be faster to access all the elements of an array-based queue than to access
List Ranking. Chapter 4
 List Ranking Chapter 4 Problem on linked lists 2-level memory model List Ranking problem Given a (mono directional) linked list L of n items, compute the distance of each item from the tail of L. Id Succ
List Ranking Chapter 4 Problem on linked lists 2-level memory model List Ranking problem Given a (mono directional) linked list L of n items, compute the distance of each item from the tail of L. Id Succ
HO #13 Fall 2015 Gary Chan. Hashing (N:12)
 HO #13 Fall 2015 Gary Chan Hashing (N:12) Outline Motivation Hashing Algorithms and Improving the Hash Functions Collisions Strategies Open addressing and linear probing Separate chaining COMP2012H (Hashing)
HO #13 Fall 2015 Gary Chan Hashing (N:12) Outline Motivation Hashing Algorithms and Improving the Hash Functions Collisions Strategies Open addressing and linear probing Separate chaining COMP2012H (Hashing)
CS 342 Lecture 8 Data Abstraction By: Hridesh Rajan
 CS 342 Lecture 8 Data Abstraction By: Hridesh Rajan 1 Com S 342 so far So far we have studied: Language design goals, Basic functional programming, Flat recursion over lists, Notion of Scheme procedures
CS 342 Lecture 8 Data Abstraction By: Hridesh Rajan 1 Com S 342 so far So far we have studied: Language design goals, Basic functional programming, Flat recursion over lists, Notion of Scheme procedures
List Ranking. Chapter 4
 List Ranking Chapter 4 Problem on linked lists 2-level memory model List Ranking problem Given a (mono directional) linked list L of n items, compute the distance of each item from the tail of L. Id Succ
List Ranking Chapter 4 Problem on linked lists 2-level memory model List Ranking problem Given a (mono directional) linked list L of n items, compute the distance of each item from the tail of L. Id Succ
Recursion I and II. Discrete Structures (CS 173) Madhusudan Parthasarathy, University of Illinois 1
 Recursion I and II Discrete Structures (CS 173) Madhusudan Parthasarathy, University of Illinois 1 Recursive definitions of functions 2 One simple form In other words, f(n) is defined in terms of f(n-1)
Recursion I and II Discrete Structures (CS 173) Madhusudan Parthasarathy, University of Illinois 1 Recursive definitions of functions 2 One simple form In other words, f(n) is defined in terms of f(n-1)
Lecture Notes on Binary Search Trees
 Lecture Notes on Binary Search Trees 15-122: Principles of Imperative Computation Frank Pfenning André Platzer Lecture 15 March 6, 2014 1 Introduction In this lecture, we will continue considering associative
Lecture Notes on Binary Search Trees 15-122: Principles of Imperative Computation Frank Pfenning André Platzer Lecture 15 March 6, 2014 1 Introduction In this lecture, we will continue considering associative
CS 106B Lecture 26: Esoteric Data Structures: Skip Lists and Bloom Filters
 CS 106B Lecture 26: Esoteric Data Structures: Skip Lists and Bloom Filters Monday, August 14, 2017 Programming Abstractions Summer 2017 Stanford University Computer Science Department Lecturer: Chris Gregg
CS 106B Lecture 26: Esoteric Data Structures: Skip Lists and Bloom Filters Monday, August 14, 2017 Programming Abstractions Summer 2017 Stanford University Computer Science Department Lecturer: Chris Gregg
Lecture 16: Binary Search Trees
 Extended Introduction to Computer Science CS1001.py Lecture 16: Binary Search Trees Instructors: Daniel Deutch, Amir Rubinstein Teaching Assistants: Michal Kleinbort, Amir Gilad School of Computer Science
Extended Introduction to Computer Science CS1001.py Lecture 16: Binary Search Trees Instructors: Daniel Deutch, Amir Rubinstein Teaching Assistants: Michal Kleinbort, Amir Gilad School of Computer Science
University of Illinois at Urbana-Champaign Department of Computer Science. Second Examination
 University of Illinois at Urbana-Champaign Department of Computer Science Second Examination CS 225 Data Structures and Software Principles Spring 2014 7-10p, Tuesday, April 8 Name: NetID: Lab Section
University of Illinois at Urbana-Champaign Department of Computer Science Second Examination CS 225 Data Structures and Software Principles Spring 2014 7-10p, Tuesday, April 8 Name: NetID: Lab Section
Lecture - 8A: Subbasis of Topology
 Lecture - 8A: Dr. Department of Mathematics Lovely Professional University Punjab, India October 18, 2014 Outline 1 Introduction 2 3 4 Introduction I As we know that topology generated by a basis B may
Lecture - 8A: Dr. Department of Mathematics Lovely Professional University Punjab, India October 18, 2014 Outline 1 Introduction 2 3 4 Introduction I As we know that topology generated by a basis B may
Lists. Michael P. Fourman. February 2, 2010
 Lists Michael P. Fourman February 2, 2010 1 Introduction The list is a fundamental datatype in most functional languages. ML is no exception; list is a built-in ML type constructor. However, to introduce
Lists Michael P. Fourman February 2, 2010 1 Introduction The list is a fundamental datatype in most functional languages. ML is no exception; list is a built-in ML type constructor. However, to introduce
Lecture 3: Recursion; Structural Induction
 15-150 Lecture 3: Recursion; Structural Induction Lecture by Dan Licata January 24, 2012 Today, we are going to talk about one of the most important ideas in functional programming, structural recursion
15-150 Lecture 3: Recursion; Structural Induction Lecture by Dan Licata January 24, 2012 Today, we are going to talk about one of the most important ideas in functional programming, structural recursion
CS 61A Interpreters, Tail Calls, Macros, Streams, Iterators. Spring 2019 Guerrilla Section 5: April 20, Interpreters.
 CS 61A Spring 2019 Guerrilla Section 5: April 20, 2019 1 Interpreters 1.1 Determine the number of calls to scheme eval and the number of calls to scheme apply for the following expressions. > (+ 1 2) 3
CS 61A Spring 2019 Guerrilla Section 5: April 20, 2019 1 Interpreters 1.1 Determine the number of calls to scheme eval and the number of calls to scheme apply for the following expressions. > (+ 1 2) 3
Priority Queue ADT. Revised based on textbook author s notes.
 Priority Queue ADT Revised based on textbook author s notes. Priority Queues Some applications require the use of a queue in which items are assigned a priority. higher priority items are dequeued first.
Priority Queue ADT Revised based on textbook author s notes. Priority Queues Some applications require the use of a queue in which items are assigned a priority. higher priority items are dequeued first.
CPL 2016, week 10. Clojure functional core. Oleg Batrashev. April 11, Institute of Computer Science, Tartu, Estonia
 CPL 2016, week 10 Clojure functional core Oleg Batrashev Institute of Computer Science, Tartu, Estonia April 11, 2016 Overview Today Clojure language core Next weeks Immutable data structures Clojure simple
CPL 2016, week 10 Clojure functional core Oleg Batrashev Institute of Computer Science, Tartu, Estonia April 11, 2016 Overview Today Clojure language core Next weeks Immutable data structures Clojure simple
