ECE260: Fundamentals of Computer Engineering
|
|
|
- Randolf McBride
- 6 years ago
- Views:
Transcription
1 Basics of Cache Memory James Moscola Dept. of Engineering & Computer Science York College of Pennsylvania Based on Computer Organization and Design, 5th Edition by Patterson & Hennessy
2 Cache Memory Cache memory a hardware (or software) component that stores data so future requests for that data can be served faster [from Wikipedia] Data stored in a cache is typically the result of an earlier access or computation May be a duplicate of data stored elsewhere Exploits the principle of of locality Keep often used data in quickly accessible memory Keep data that may be required soon in quickly accessible memory In hardware, cache memory is the level (or levels) of the memory hierarchy closest to the CPU Exists between the processor and the main system memory (DRAM) Cache memory made from fast SRAM Faster, but less capacity than main system memory 2
3 Cache Analogy (used by author in your textbook) You are writing a paper for a history course while sitting at a table in the library As you work you realize you need a reference book from the library stacks You stop writing, fetch the book from the stacks, and continue writing your paper You don t immediately return the book, you might need it again soon (temporal locality) You might even need multiple chapters from the same book (spatial locality) After a short while, you have a few books on your table, and you can work smoothly without needing to fetch more books from the shelves The library table is a cache for the rest of the library Now you switch to doing your biology homework You need to fetch a new reference book for your biology from the shelf If your table is full, you must return a history book to the stacks to make room for the biology book 3
4 Cache Memory on Processor Die (Quad-Core CPU) Processor die for Intel s Sandy Bridge Processor Core 1 (circa 2011) μproc Core 2 Core 3 L1 Cache I-Mem? Intel s System Agent Memory Controller PCIe Controller Media Interface Power Control Unit Thermal Management Integrated Graphics L1 Cache D-Mem? L1 Memory Hierarchy 3 Levels of Cache Core 4 L2 Cache L2 L3 Cache (Shared Between Cores) L3 Main Memory Dual Channel Memory I/O 4
5 Cache in the Memory Hierarchy Want to avoid reading data from slower main memory When processor needs to read data from a memory address First, check cache memory If data is present in cache memory (i.e. cache hit), then done If data is not present in cache (i.e. cache miss), then retrieve it from main memory and copy it into the cache for use by processor If multiple levels of cache exist, check them in order: L1 L2 L3 Main Memory Only check L2 if data not in L1 Only check L3 if data not in L2 Only check main memory if data not in L3 When data is found, copy it to higher levels of memory hierarchy (i.e. copy from L3 to L2 and L1) 5
6 Main Memory in a Computer To understand cache, first see how main memory is handled Given a processor where memory is addressed with a d-bit address Main memory range 0 to 2 d -1 Main memory is divided into blocks s are all equally sized Each block contains one or more data words (i.e. each block consists of one or more memory addresses) Just as each memory address has a number, each block can also be numbered 0 2 d - 1 Memory Addresses Main Memory n Address How many blocks total? Total Memory Size # s = Size Example: 128 Total 1024 Memory Words Size # s = s 8 Words/ Size 6
7 Finding the Right in Main Memory Suppose memory address is generated the address is between 0 and 2 d -1 In which block is a memory address located? To calculate block address, divide memory address by block size result is the block address With block size a power of 2, simply shift memory address to find block address Assume block size is 2 b (and b < d) Remove the least significant b bits (this is called the offset) Remaining d minus b bits is the block address Calculating a Address Example Example using binary and shifting Total Memory Memory Address Size # s Address = Size # s #3 = Total MemWord Memory 31Size ten 8 Words/ Size MemWord 31 ten = two 8 Words/ = 2 3 To divide by 8, shift-right by 3 SRL(11111 two ) = 11 two = #3 ten 7
8 Cache Memory in a Computer Cache memory is divided into blocks that are exactly the same size as the the main memory blocks 0 Main Memory 0 Number of blocks in cache is much less than the number of total blocks in main memory Cache contains only a subset of the blocks from main memory it is not large enough to store all blocks Many different caching techniques We will focus on direct-mapped caching To calculate cache block index, ( address) modulo (#Cache blocks) μproc 0 1 Cache Index Cache Memory 2 d - 1 Memory Addresses n Address 8
9 Direct-Mapped Cache Direct-mapped cache a cache structure in which each memory location is mapped to exactly one location in the cache 0 Main Memory 0 Number of blocks is a power of 2 size is a power of 2 Location in cache determined by block address To calculate cache block index, ( address) modulo (#Cache blocks) Cache Index = 5 modulo 2 = 1 μproc 0 1 Cache Index Cache Memory d - 1 n Memory Addresses Address 9
10 Address Subdivision To utilize cache, a memory byte address is subdivided in multiple fields: Byte offset Specifies a byte within a word Least significant two bits, typically ignored when caching Word offset (if block size > 1 word) Specifies a word within a block Cache block index Memory Address Requested by Processor Tag Index Word Offset Byte Offset d-1 0 Specifies which cache block a memory address should be stored Tag Many blocks map to the same index of cache memory Tag bits uniquely identify each block (really just high-order bits of memory address) 10
11 Cache Structure Each cache entry contains: One or more Data words Determined by cache designer Example shows only a single 32-bit word A Tag field Differentiates blocks that cache to the same block index in cache memory A Valid bit Initialized to 0 Set to 1 when cache entry is set Cache blocks are initially empty and invalid 11
12 Address Subdivision/Cache Structure Example Memory Address Requested by Processor Tag Index Word Offset Byte Offset => bits 1:0 (2 bits) Used to address bytes within a word Byte Offset d-1 0 Word Offset => Not used in this example since only 1 32-bit word per cache entry Cache Index => Bits 11:2 (10 bits) Location in cache where this memory address should be stored Tag Bits => Bits 31:12 (20 bits) Remaining bits used to differentiate blocks 12
13 Handling Cache Misses On a cache hit, CPU proceeds normally On a cache miss, cannot proceed normally because data is not available Stall the CPU pipeline Fetch desired block from next level of memory hierarchy If cache miss was Instruction Cache Restart instruction fetch If cache miss was Data Cache Complete data access 13
14 Direct-Mapped Cache Example Parameters Example of a sequence of memory references to a direct-mapped cache using word addressing For this example, the cache has 8 blocks with only 1 word per block Cache is initially empty all valid bits are initialized to 0 to indicate that the cache block is invalid Assume memory addresses are 8-bit word addresses (no byte offset bits) Total memory space of 2 8 words of memory cannot fit them all in cache First, compute various field sizes # Word Offset Bits = log 2 (# Words/) # Word Offset Bits = log 2 (1 Word/) = 0 bits # Cache Index Bits = log 2 (# s) # Cache Index Bits = log 2 (8 s) = 3 bits # Tag Bits = # Addr Bits - # Index Bits - # Offset Bits # Tag Bits = 8 Addr Bits - 3 Index Bits - 0 Offset Bits = 5 bits 14
15 Cache Example Cache Structure index numbers range from 0 to (#s - 1) Valid bits are all initially 0 to indicate invalid entry Tag bits are used to differentiate blocks that cache to the same index # Word Offset Bits = 0 bits # Cache Index Bits = 3 bits # Tag Bits = 5 bits Cache is structured as a table that is indexed using block numbers. For this example, block index numbers are shown in both binary and base-10 Index V Tag Data 000 two (0 ten ) two (1 ten ) two (2 ten ) two (3 ten ) two (4 ten ) two (5 ten ) two (6 ten ) two (7 ten ) 0 The data from the main memory that is being cached 15
16 Cache Example First Memory Access Access memory address 22 ten (this is a word address) Word Addr Word Addr (base-2) Tag Cache Index # Hit / Miss # Word Offset Bits = 0 bits # Cache Index Bits = 3 bits # Tag Bits = 5 bits 22 ten two two 110 two (6 ten ) Miss CACHE MEMORY (before access) Index V Tag Data 000 two (0 ten ) two (1 ten ) two (2 ten ) two (3 ten ) two (4 ten ) two (5 ten ) two (6 ten ) two (7 ten ) 0 index number 6 ten is set to invalid, therefore this is a cache miss. Index V Tag Data 000 two (0 ten ) two (1 ten ) two (2 ten ) two (3 ten ) two (4 ten ) two (5 ten ) two (6 ten ) two mem[22] 111 two (7 ten ) 0 CACHE MEMORY (after access) Copy data from main system memory into cache, set tag and valid bit. Resume original instruction that needed the data. 16
17 Cache Example Second Memory Access Access memory address 26 ten Word Addr Word Addr (base-2) Tag Cache Index # Hit / Miss # Word Offset Bits = 0 bits # Cache Index Bits = 3 bits # Tag Bits = 5 bits 26 ten two two 010 two (2 ten ) Miss CACHE MEMORY (before access) Index V Tag Data 000 two (0 ten ) two (1 ten ) two (2 ten ) two (3 ten ) two (4 ten ) two (5 ten ) two (6 ten ) two mem[22] 111 two (7 ten ) 0 index number 2 ten is set to invalid, therefore this is a cache miss. Index V Tag Data 000 two (0 ten ) two (1 ten ) two (2 ten ) two mem[26] 011 two (3 ten ) two (4 ten ) two (5 ten ) two (6 ten ) two mem[22] 111 two (7 ten ) 0 CACHE MEMORY (after access) Copy data from main system memory into cache, set tag and valid bit. Resume original instruction that needed the data. 17
18 Cache Example Third Memory Access Access memory address 22 ten (again) Word Addr Word Addr (base-2) Tag Cache Index # Hit / Miss # Word Offset Bits = 0 bits # Cache Index Bits = 3 bits # Tag Bits = 5 bits 22 ten two two 110 two (6 ten ) Hit CACHE MEMORY (before access) Index V Tag Data 000 two (0 ten ) two (1 ten ) two (2 ten ) two mem[26] 011 two (3 ten ) two (4 ten ) two (5 ten ) two (6 ten ) two mem[22] 111 two (7 ten ) 0 index number 6 ten is set to valid AND the tag in the cache memory matches the tag field of the requested memory address, therefore this is a cache hit. Index V Tag Data 000 two (0 ten ) two (1 ten ) two (2 ten ) two mem[26] 011 two (3 ten ) two (4 ten ) two (5 ten ) two (6 ten ) two mem[22] 111 two (7 ten ) 0 CACHE MEMORY (after access) No need to access main system memory. Provide requested data to processor. 18
19 Cache Example Fourth Memory Access Access memory address 26 ten (again) Word Addr Word Addr (base-2) Tag Cache Index # Hit / Miss # Word Offset Bits = 0 bits # Cache Index Bits = 3 bits # Tag Bits = 5 bits 26 ten two two 010 two (2 ten ) Hit CACHE MEMORY (before access) Index V Tag Data 000 two (0 ten ) two (1 ten ) two (2 ten ) two mem[26] 011 two (3 ten ) two (4 ten ) two (5 ten ) two (6 ten ) two mem[22] 111 two (7 ten ) 0 index number 2 ten is set to valid AND the tag in the cache memory matches the tag field of the requested memory address, therefore this is a cache hit. Index V Tag Data 000 two (0 ten ) two (1 ten ) two (2 ten ) two mem[26] 011 two (3 ten ) two (4 ten ) two (5 ten ) two (6 ten ) two mem[22] 111 two (7 ten ) 0 CACHE MEMORY (after access) No need to access main system memory. Provide requested data to processor. 19
20 Cache Example Fifth Memory Access Access memory address 16 ten Word Addr Word Addr (base-2) Tag Cache Index # Hit / Miss # Word Offset Bits = 0 bits # Cache Index Bits = 3 bits # Tag Bits = 5 bits 16 ten two two 000 two (0 ten ) Miss CACHE MEMORY (before access) Index V Tag Data 000 two (0 ten ) two (1 ten ) two (2 ten ) two mem[26] 011 two (3 ten ) two (4 ten ) two (5 ten ) two (6 ten ) two mem[22] 111 two (7 ten ) 0 index number 0 ten is set to invalid, therefore this is a cache miss. Index V Tag Data 000 two (0 ten ) two mem[16] 001 two (1 ten ) two (2 ten ) two mem[26] 011 two (3 ten ) two (4 ten ) two (5 ten ) two (6 ten ) two mem[22] 111 two (7 ten ) 0 CACHE MEMORY (after access) Copy data from main system memory into cache, set tag and valid bit. Resume original instruction that needed the data. 20
21 Cache Example Sixth Memory Access Access memory address 18 ten Word Addr Word Addr (base-2) Tag Cache Index # Hit / Miss # Word Offset Bits = 0 bits # Cache Index Bits = 3 bits # Tag Bits = 5 bits 18 ten two two 010 two (2 ten ) Miss CACHE MEMORY (before access) Index V Tag Data 000 two (0 ten ) two mem[16] 001 two (1 ten ) two (2 ten ) two mem[26] 011 two (3 ten ) two (4 ten ) two (5 ten ) two (6 ten ) two mem[22] 111 two (7 ten ) 0 index number 2 ten is set to valid. HOWEVER, the tag in the cache DOES NOT MATCH the tag field of the requested memory address, therefore this is a cache miss. Index V Tag Data 000 two (0 ten ) two mem[16] 001 two (1 ten ) two (2 ten ) two mem[18] 011 two (3 ten ) two (4 ten ) two (5 ten ) two (6 ten ) two mem[22] 111 two (7 ten ) 0 CACHE MEMORY (after access) Copy data from main system memory into cache OVERWRITING previous contents, set new tag value. Resume original instruction that needed the data. 21
22 Direct-Mapped Cache Example #2 Parameters Example of a sequence of memory references to a direct-mapped cache using byte addressing For this example, the cache has 4 blocks with 16 bytes per block (i.e. 4 words per block) Cache is initially empty all valid bits are initialized to 0 to indicate that the cache block is invalid Assume memory addresses are 8-bit byte addresses Two least significant bits specify byte offset within a word remove these bits Total memory space of 2 8 bytes of memory cannot fit them all in cache First, compute various field sizes # Word Offset Bits = log 2 (# Words/) # Word Offset Bits = log 2 (4 Words/) = 2 bits # Cache Index Bits = log 2 (# s) # Cache Index Bits = log 2 (4 s) = 2 bits # Tag Bits = # Addr Bits - # Index Bits - # Offset Bits - Byte Offset Bits # Tag Bits = 8 Addr Bits - 2 Index Bits - 2 Offset Bits - 2 Byte Offset Bits = 2 bits 22
23 Cache Example #2 Cache Structure This cache structure stores multiple data words per block When one of the data words is accessed, the entire block is brought into the cache from main system memory # Word Offset Bits = 2 bits # Cache Index Bits = 2 bits # Tag Bits = 2 bits Data (4 words) Index V Tag 00 two (0 ten ) 0 01 two (1 ten ) 0 10 two (2 ten ) 0 11 two (3 ten ) 0 Offset 3 Offset 2 Offset 1 Offset 0 23
24 Cache Example #2 First Memory Access Access byte address 12 ten (this is a byte address, i.e. word address 3 ten ) Byte Addr Byte Addr (base-2) Tag Cache Index # Offset Hit / Miss # Word Offset Bits = 2 bits # Cache Index Bits = 2 bits # Tag Bits = 2 bits 12 ten two 00 two 00 two (0 ten ) 11 two (3 ten ) Miss Data (4 words) CACHE MEMORY (before access) Index V Tag 00 two (0 ten ) 0 01 two (1 ten ) 0 Offset 3 Offset 2 Offset 1 Offset 0 index number 0 ten is set to invalid, therefore this is a cache miss. 10 two (2 ten ) 0 11 two (3 ten ) 0 CACHE MEMORY (after access) Data (4 words) Index V Tag Offset 3 Offset 2 Offset 1 Offset 0 00 two (0 ten ) 1 00 two mem[12] mem[8] mem[4] mem[0] 01 two (1 ten ) 0 10 two (2 ten ) 0 11 two (3 ten ) 0 On cache miss, find the block in which address 12 ten resides, copy entire block from main system memory into cache. Also, set tag and valid bit and resume original instruction that needed data. 24
25 Cache Example #2 Second Memory Access Access byte address 104 ten (this is a byte address, i.e. word address 26 ten ) Byte Addr Byte Addr (base-2) Tag Cache Index # Offset Hit / Miss # Word Offset Bits = 2 bits # Cache Index Bits = 2 bits # Tag Bits = 2 bits 104 ten two 01 two 10 two (2 ten ) 10 two (2 ten ) Miss CACHE MEMORY (before access) Data (4 words) Index V Tag Offset 3 Offset 2 Offset 1 Offset 0 00 two (0 ten ) 1 00 two mem[12] mem[8] mem[4] mem[0] 01 two (1 ten ) 0 10 two (2 ten ) 0 11 two (3 ten ) 0 index number 2 ten is set to invalid, therefore this is a cache miss. CACHE MEMORY (after access) Data (4 words) Index V Tag Offset 3 Offset 2 Offset 1 Offset 0 00 two (0 ten ) 1 00 two mem[12] mem[8] mem[4] mem[0] 01 two (1 ten ) 0 10 two (2 ten ) 1 01 two mem[108] mem[104] mem[100] mem[96] 11 two (3 ten ) 0 On cache miss, find the block in which address 104 ten resides, copy entire block from main system memory into cache. Also, set tag and valid bit and resume original instruction that needed data. 25
26 Cache Example #2 Third Memory Access Access byte address 96 ten (this is a byte address, i.e. word address 24 ten ) Byte Addr Byte Addr (base-2) Tag Cache Index # Offset Hit / Miss # Word Offset Bits = 2 bits # Cache Index Bits = 2 bits # Tag Bits = 2 bits 96 ten two 01 two 10 two (2 ten ) 00 two (0 ten ) Hit CACHE MEMORY (before access) Data (4 words) Index V Tag Offset 3 Offset 2 Offset 1 Offset 0 00 two (0 ten ) 1 00 two mem[12] mem[8] mem[4] mem[0] 01 two (1 ten ) 0 10 two (2 ten ) 1 01 two mem[108] mem[104] mem[100] mem[96] 11 two (3 ten ) 0 index number 2 ten is set to valid AND the tag in the cache memory matches the tag field of the requested memory address, therefore this is a cache hit. CACHE MEMORY (after access) Data (4 words) Index V Tag Offset 3 Offset 2 Offset 1 Offset 0 00 two (0 ten ) 1 00 two mem[12] mem[8] mem[4] mem[0] 01 two (1 ten ) 0 10 two (2 ten ) 1 01 two mem[108] mem[104] mem[100] mem[96] 11 two (3 ten ) 0 On cache miss, find the block in which address 104 ten resides, copy entire block from main system memory into cache. Also, set tag and valid bit and resume original instruction that needed data. 26
27 Cache Example #2 Fourth Memory Access Access byte address 172 ten (this is a byte address, i.e. word address 43 ten ) Byte Addr Byte Addr (base-2) Tag Cache Index # Offset Hit / Miss # Word Offset Bits = 2 bits # Cache Index Bits = 2 bits # Tag Bits = 2 bits 172 ten two 10 two 10 two (2 ten ) 11 two (3 ten ) Miss CACHE MEMORY (before access) Data (4 words) Index V Tag Offset 3 Offset 2 Offset 1 Offset 0 00 two (0 ten ) 1 00 two mem[12] mem[8] mem[4] mem[0] 01 two (1 ten ) 0 10 two (2 ten ) 1 01 two mem[108] mem[104] mem[100] mem[96] 11 two (3 ten ) 0 index number 2 ten is set to valid. HOWEVER, the tag in the cache DOES NOT MATCH the tag field of the requested memory address, therefore this is a cache miss. CACHE MEMORY (after access) Data (4 words) Index V Tag Offset 3 Offset 2 Offset 1 Offset 0 00 two (0 ten ) 1 00 two mem[12] mem[8] mem[4] mem[0] 01 two (1 ten ) 0 10 two (2 ten ) 1 10 two mem[172] mem[168] mem[164] mem[160] 11 two (3 ten ) 0 On cache miss, find the block in which address 172 ten resides, copy entire block from main system memory into cache OVERWRITING previous contents. Set new tag value and resume original instruction that needed the data. 27
28 Calculating Address and Index Numbers Using cache parameters from previous example: 4 blocks with 16 bytes per block address references the address of a block in main system memory Address = Memory Byte Address / Bytes per Address = 104 ten / 16 Bytes per = 6.5 = 6 Example byte address: 104 ten JUST SHIFT or remove low-order bits index number references the index location into which the block should be stored Index Number = Address modulo # Cache s Index Number = 6 modulo 4 = 2 JUST grab low-order bits 28
29 Size Considerations Larger block sizes should reduce miss rate Due to spatial locality However, in a fixed-sized cache Larger blocks means there are fewer of them More competition for blocks means an increased miss rate may be overwritten in cache before program is done with it Larger block size also means larger miss penalty When a miss occurs, must copy more data from main system memory for larger blocks Can override benefit of reduced miss rate 29
30 Size Considerations (continued) Each line represents a different cache size. Larger caches have smaller miss rate. Making blocks too large can increase miss rate. 30
31 Handling Writes Write-Through On data-write hit, could just update the block in cache and not the main system memory However, then cache and main system memory would be inconsistent In a write-through scheme, when cache is written also write the data to main system memory May negatively impact performance Each write to main system memory takes time Doesn t take advantage of burst write mode Data may be updated repeatedly, no need to write transient data to main memory (e.g. loop variable) Various methods exist to help alleviate the performance issues caused by the write-through scheme However, better schemes exist 31
32 Handling Writes Write-Back Alternative to write-through scheme On data-write hit, just update the block in cache and not the main system memory Keep track of whether each block is dirty Dirty blocks are blocks that have been modified but not yet written back to main system memory Anytime a dirty block is replaced Write it back to main system memory before overwriting with new block Can use a write buffer to allow replacing block to be read first 32
CSE 2021: Computer Organization
 CSE 2021: Computer Organization Lecture-12a Caches-1 The basics of caches Shakil M. Khan Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB
CSE 2021: Computer Organization Lecture-12a Caches-1 The basics of caches Shakil M. Khan Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB
CSE 2021: Computer Organization
 CSE 2021: Computer Organization Lecture-12 Caches-1 The basics of caches Shakil M. Khan Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB
CSE 2021: Computer Organization Lecture-12 Caches-1 The basics of caches Shakil M. Khan Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB
ECE331: Hardware Organization and Design
 ECE331: Hardware Organization and Design Lecture 22: Direct Mapped Cache Adapted from Computer Organization and Design, Patterson & Hennessy, UCB Intel 8-core i7-5960x 3 GHz, 8-core, 20 MB of cache, 140
ECE331: Hardware Organization and Design Lecture 22: Direct Mapped Cache Adapted from Computer Organization and Design, Patterson & Hennessy, UCB Intel 8-core i7-5960x 3 GHz, 8-core, 20 MB of cache, 140
ECE232: Hardware Organization and Design
 ECE232: Hardware Organization and Design Lecture 22: Introduction to Caches Adapted from Computer Organization and Design, Patterson & Hennessy, UCB Overview Caches hold a subset of data from the main
ECE232: Hardware Organization and Design Lecture 22: Introduction to Caches Adapted from Computer Organization and Design, Patterson & Hennessy, UCB Overview Caches hold a subset of data from the main
Chapter 5. Memory Technology
 Chapter 5 Large and Fast: Exploiting Memory Hierarchy Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic disk 5ms 20ms, $0.20 $2 per
Chapter 5 Large and Fast: Exploiting Memory Hierarchy Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic disk 5ms 20ms, $0.20 $2 per
Memory Technology. Caches 1. Static RAM (SRAM) Dynamic RAM (DRAM) Magnetic disk. Ideal memory. 0.5ns 2.5ns, $2000 $5000 per GB
 Memory Technology Caches 1 Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic disk 5ms 20ms, $0.20 $2 per GB Ideal memory Average access time similar
Memory Technology Caches 1 Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic disk 5ms 20ms, $0.20 $2 per GB Ideal memory Average access time similar
Computer Systems Laboratory Sungkyunkwan University
 Caches Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns
Caches Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns
CSF Cache Introduction. [Adapted from Computer Organization and Design, Patterson & Hennessy, 2005]
![CSF Cache Introduction. [Adapted from Computer Organization and Design, Patterson & Hennessy, 2005] CSF Cache Introduction. [Adapted from Computer Organization and Design, Patterson & Hennessy, 2005]](/thumbs/73/69213006.jpg) CSF Cache Introduction [Adapted from Computer Organization and Design, Patterson & Hennessy, 2005] Review: The Memory Hierarchy Take advantage of the principle of locality to present the user with as much
CSF Cache Introduction [Adapted from Computer Organization and Design, Patterson & Hennessy, 2005] Review: The Memory Hierarchy Take advantage of the principle of locality to present the user with as much
Chapter 5. Large and Fast: Exploiting Memory Hierarchy
 Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address space at any time Temporal locality Items accessed recently are likely to
Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address space at any time Temporal locality Items accessed recently are likely to
Memory Hierarchy, Fully Associative Caches. Instructor: Nick Riasanovsky
 Memory Hierarchy, Fully Associative Caches Instructor: Nick Riasanovsky Review Hazards reduce effectiveness of pipelining Cause stalls/bubbles Structural Hazards Conflict in use of datapath component Data
Memory Hierarchy, Fully Associative Caches Instructor: Nick Riasanovsky Review Hazards reduce effectiveness of pipelining Cause stalls/bubbles Structural Hazards Conflict in use of datapath component Data
Chapter 5. Large and Fast: Exploiting Memory Hierarchy
 Chapter 5 Large and Fast: Exploiting Memory Hierarchy Processor-Memory Performance Gap 10000 µproc 55%/year (2X/1.5yr) Performance 1000 100 10 1 1980 1983 1986 1989 Moore s Law Processor-Memory Performance
Chapter 5 Large and Fast: Exploiting Memory Hierarchy Processor-Memory Performance Gap 10000 µproc 55%/year (2X/1.5yr) Performance 1000 100 10 1 1980 1983 1986 1989 Moore s Law Processor-Memory Performance
Chapter 5. Large and Fast: Exploiting Memory Hierarchy
 Chapter 5 Large and Fast: Exploiting Memory Hierarchy Processor-Memory Performance Gap 10000 µproc 55%/year (2X/1.5yr) Performance 1000 100 10 1 1980 1983 1986 1989 Moore s Law Processor-Memory Performance
Chapter 5 Large and Fast: Exploiting Memory Hierarchy Processor-Memory Performance Gap 10000 µproc 55%/year (2X/1.5yr) Performance 1000 100 10 1 1980 1983 1986 1989 Moore s Law Processor-Memory Performance
EE 4683/5683: COMPUTER ARCHITECTURE
 EE 4683/5683: COMPUTER ARCHITECTURE Lecture 6A: Cache Design Avinash Kodi, kodi@ohioedu Agenda 2 Review: Memory Hierarchy Review: Cache Organization Direct-mapped Set- Associative Fully-Associative 1 Major
EE 4683/5683: COMPUTER ARCHITECTURE Lecture 6A: Cache Design Avinash Kodi, kodi@ohioedu Agenda 2 Review: Memory Hierarchy Review: Cache Organization Direct-mapped Set- Associative Fully-Associative 1 Major
CS 61C: Great Ideas in Computer Architecture. The Memory Hierarchy, Fully Associative Caches
 CS 61C: Great Ideas in Computer Architecture The Memory Hierarchy, Fully Associative Caches Instructor: Alan Christopher 7/09/2014 Summer 2014 -- Lecture #10 1 Review of Last Lecture Floating point (single
CS 61C: Great Ideas in Computer Architecture The Memory Hierarchy, Fully Associative Caches Instructor: Alan Christopher 7/09/2014 Summer 2014 -- Lecture #10 1 Review of Last Lecture Floating point (single
EEC 170 Computer Architecture Fall Cache Introduction Review. Review: The Memory Hierarchy. The Memory Hierarchy: Why Does it Work?
 EEC 17 Computer Architecture Fall 25 Introduction Review Review: The Hierarchy Take advantage of the principle of locality to present the user with as much memory as is available in the cheapest technology
EEC 17 Computer Architecture Fall 25 Introduction Review Review: The Hierarchy Take advantage of the principle of locality to present the user with as much memory as is available in the cheapest technology
registers data 1 registers MEMORY ADDRESS on-chip cache off-chip cache main memory: real address space part of virtual addr. sp.
 Cache associativity Cache and performance 12 1 CMPE110 Spring 2005 A. Di Blas 110 Spring 2005 CMPE Cache Direct-mapped cache Reads and writes Textbook Edition: 7.1 to 7.3 Second Third Edition: 7.1 to 7.3
Cache associativity Cache and performance 12 1 CMPE110 Spring 2005 A. Di Blas 110 Spring 2005 CMPE Cache Direct-mapped cache Reads and writes Textbook Edition: 7.1 to 7.3 Second Third Edition: 7.1 to 7.3
CS 61C: Great Ideas in Computer Architecture (Machine Structures) Caches Part 1
 CS 61C: Great Ideas in Computer Architecture (Machine Structures) Caches Part 1 Instructors: Nicholas Weaver & Vladimir Stojanovic http://inst.eecs.berkeley.edu/~cs61c/ Components of a Computer Processor
CS 61C: Great Ideas in Computer Architecture (Machine Structures) Caches Part 1 Instructors: Nicholas Weaver & Vladimir Stojanovic http://inst.eecs.berkeley.edu/~cs61c/ Components of a Computer Processor
CS 61C: Great Ideas in Computer Architecture. Direct Mapped Caches
 CS 61C: Great Ideas in Computer Architecture Direct Mapped Caches Instructor: Justin Hsia 7/05/2012 Summer 2012 Lecture #11 1 Review of Last Lecture Floating point (single and double precision) approximates
CS 61C: Great Ideas in Computer Architecture Direct Mapped Caches Instructor: Justin Hsia 7/05/2012 Summer 2012 Lecture #11 1 Review of Last Lecture Floating point (single and double precision) approximates
Advanced Memory Organizations
 CSE 3421: Introduction to Computer Architecture Advanced Memory Organizations Study: 5.1, 5.2, 5.3, 5.4 (only parts) Gojko Babić 03-29-2018 1 Growth in Performance of DRAM & CPU Huge mismatch between CPU
CSE 3421: Introduction to Computer Architecture Advanced Memory Organizations Study: 5.1, 5.2, 5.3, 5.4 (only parts) Gojko Babić 03-29-2018 1 Growth in Performance of DRAM & CPU Huge mismatch between CPU
V. Primary & Secondary Memory!
 V. Primary & Secondary Memory! Computer Architecture and Operating Systems & Operating Systems: 725G84 Ahmed Rezine 1 Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM)
V. Primary & Secondary Memory! Computer Architecture and Operating Systems & Operating Systems: 725G84 Ahmed Rezine 1 Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM)
CS3350B Computer Architecture
 CS335B Computer Architecture Winter 25 Lecture 32: Exploiting Memory Hierarchy: How? Marc Moreno Maza wwwcsduwoca/courses/cs335b [Adapted from lectures on Computer Organization and Design, Patterson &
CS335B Computer Architecture Winter 25 Lecture 32: Exploiting Memory Hierarchy: How? Marc Moreno Maza wwwcsduwoca/courses/cs335b [Adapted from lectures on Computer Organization and Design, Patterson &
Chapter 5A. Large and Fast: Exploiting Memory Hierarchy
 Chapter 5A Large and Fast: Exploiting Memory Hierarchy Memory Technology Static RAM (SRAM) Fast, expensive Dynamic RAM (DRAM) In between Magnetic disk Slow, inexpensive Ideal memory Access time of SRAM
Chapter 5A Large and Fast: Exploiting Memory Hierarchy Memory Technology Static RAM (SRAM) Fast, expensive Dynamic RAM (DRAM) In between Magnetic disk Slow, inexpensive Ideal memory Access time of SRAM
EN1640: Design of Computing Systems Topic 06: Memory System
 EN164: Design of Computing Systems Topic 6: Memory System Professor Sherief Reda http://scale.engin.brown.edu Electrical Sciences and Computer Engineering School of Engineering Brown University Spring
EN164: Design of Computing Systems Topic 6: Memory System Professor Sherief Reda http://scale.engin.brown.edu Electrical Sciences and Computer Engineering School of Engineering Brown University Spring
Page 1. Memory Hierarchies (Part 2)
 Memory Hierarchies (Part ) Outline of Lectures on Memory Systems Memory Hierarchies Cache Memory 3 Virtual Memory 4 The future Increasing distance from the processor in access time Review: The Memory Hierarchy
Memory Hierarchies (Part ) Outline of Lectures on Memory Systems Memory Hierarchies Cache Memory 3 Virtual Memory 4 The future Increasing distance from the processor in access time Review: The Memory Hierarchy
CSE 431 Computer Architecture Fall Chapter 5A: Exploiting the Memory Hierarchy, Part 1
 CSE 431 Computer Architecture Fall 2008 Chapter 5A: Exploiting the Memory Hierarchy, Part 1 Mary Jane Irwin ( www.cse.psu.edu/~mji ) [Adapted from Computer Organization and Design, 4 th Edition, Patterson
CSE 431 Computer Architecture Fall 2008 Chapter 5A: Exploiting the Memory Hierarchy, Part 1 Mary Jane Irwin ( www.cse.psu.edu/~mji ) [Adapted from Computer Organization and Design, 4 th Edition, Patterson
5. Memory Hierarchy Computer Architecture COMP SCI 2GA3 / SFWR ENG 2GA3. Emil Sekerinski, McMaster University, Fall Term 2015/16
 5. Memory Hierarchy Computer Architecture COMP SCI 2GA3 / SFWR ENG 2GA3 Emil Sekerinski, McMaster University, Fall Term 2015/16 Movie Rental Store You have a huge warehouse with every movie ever made.
5. Memory Hierarchy Computer Architecture COMP SCI 2GA3 / SFWR ENG 2GA3 Emil Sekerinski, McMaster University, Fall Term 2015/16 Movie Rental Store You have a huge warehouse with every movie ever made.
Course Administration
 Spring 207 EE 363: Computer Organization Chapter 5: Large and Fast: Exploiting Memory Hierarchy - Avinash Kodi Department of Electrical Engineering & Computer Science Ohio University, Athens, Ohio 4570
Spring 207 EE 363: Computer Organization Chapter 5: Large and Fast: Exploiting Memory Hierarchy - Avinash Kodi Department of Electrical Engineering & Computer Science Ohio University, Athens, Ohio 4570
ECE331: Hardware Organization and Design
 ECE331: Hardware Organization and Design Lecture 24: Cache Performance Analysis Adapted from Computer Organization and Design, Patterson & Hennessy, UCB Overview Last time: Associative caches How do we
ECE331: Hardware Organization and Design Lecture 24: Cache Performance Analysis Adapted from Computer Organization and Design, Patterson & Hennessy, UCB Overview Last time: Associative caches How do we
Memory Hierarchy. ENG3380 Computer Organization and Architecture Cache Memory Part II. Topics. References. Memory Hierarchy
 ENG338 Computer Organization and Architecture Part II Winter 217 S. Areibi School of Engineering University of Guelph Hierarchy Topics Hierarchy Locality Motivation Principles Elements of Design: Addresses
ENG338 Computer Organization and Architecture Part II Winter 217 S. Areibi School of Engineering University of Guelph Hierarchy Topics Hierarchy Locality Motivation Principles Elements of Design: Addresses
registers data 1 registers MEMORY ADDRESS on-chip cache off-chip cache main memory: real address space part of virtual addr. sp.
 13 1 CMPE110 Computer Architecture, Winter 2009 Andrea Di Blas 110 Winter 2009 CMPE Cache Direct-mapped cache Reads and writes Cache associativity Cache and performance Textbook Edition: 7.1 to 7.3 Third
13 1 CMPE110 Computer Architecture, Winter 2009 Andrea Di Blas 110 Winter 2009 CMPE Cache Direct-mapped cache Reads and writes Cache associativity Cache and performance Textbook Edition: 7.1 to 7.3 Third
Computer Architecture Computer Science & Engineering. Chapter 5. Memory Hierachy BK TP.HCM
 Computer Architecture Computer Science & Engineering Chapter 5 Memory Hierachy Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic
Computer Architecture Computer Science & Engineering Chapter 5 Memory Hierachy Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic
EN1640: Design of Computing Systems Topic 06: Memory System
 EN164: Design of Computing Systems Topic 6: Memory System Professor Sherief Reda http://scale.engin.brown.edu Electrical Sciences and Computer Engineering School of Engineering Brown University Spring
EN164: Design of Computing Systems Topic 6: Memory System Professor Sherief Reda http://scale.engin.brown.edu Electrical Sciences and Computer Engineering School of Engineering Brown University Spring
Chapter 5. Large and Fast: Exploiting Memory Hierarchy
 Chapter 5 Large and Fast: Exploiting Memory Hierarchy Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic disk 5ms 20ms, $0.20 $2 per
Chapter 5 Large and Fast: Exploiting Memory Hierarchy Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic disk 5ms 20ms, $0.20 $2 per
Chapter 5. Large and Fast: Exploiting Memory Hierarchy
 Chapter 5 Large and Fast: Exploiting Memory Hierarchy Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic disk 5ms 20ms, $0.20 $2 per
Chapter 5 Large and Fast: Exploiting Memory Hierarchy Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic disk 5ms 20ms, $0.20 $2 per
Caches. Hiding Memory Access Times
 Caches Hiding Memory Access Times PC Instruction Memory 4 M U X Registers Sign Ext M U X Sh L 2 Data Memory M U X C O N T R O L ALU CTL INSTRUCTION FETCH INSTR DECODE REG FETCH EXECUTE/ ADDRESS CALC MEMORY
Caches Hiding Memory Access Times PC Instruction Memory 4 M U X Registers Sign Ext M U X Sh L 2 Data Memory M U X C O N T R O L ALU CTL INSTRUCTION FETCH INSTR DECODE REG FETCH EXECUTE/ ADDRESS CALC MEMORY
Chapter 5 Large and Fast: Exploiting Memory Hierarchy (Part 1)
 Department of Electr rical Eng ineering, Chapter 5 Large and Fast: Exploiting Memory Hierarchy (Part 1) 王振傑 (Chen-Chieh Wang) ccwang@mail.ee.ncku.edu.tw ncku edu Depar rtment of Electr rical Engineering,
Department of Electr rical Eng ineering, Chapter 5 Large and Fast: Exploiting Memory Hierarchy (Part 1) 王振傑 (Chen-Chieh Wang) ccwang@mail.ee.ncku.edu.tw ncku edu Depar rtment of Electr rical Engineering,
CSF Improving Cache Performance. [Adapted from Computer Organization and Design, Patterson & Hennessy, 2005]
![CSF Improving Cache Performance. [Adapted from Computer Organization and Design, Patterson & Hennessy, 2005] CSF Improving Cache Performance. [Adapted from Computer Organization and Design, Patterson & Hennessy, 2005]](/thumbs/76/74076691.jpg) CSF Improving Cache Performance [Adapted from Computer Organization and Design, Patterson & Hennessy, 2005] Review: The Memory Hierarchy Take advantage of the principle of locality to present the user
CSF Improving Cache Performance [Adapted from Computer Organization and Design, Patterson & Hennessy, 2005] Review: The Memory Hierarchy Take advantage of the principle of locality to present the user
Computer Organization and Structure. Bing-Yu Chen National Taiwan University
 Computer Organization and Structure Bing-Yu Chen National Taiwan University Large and Fast: Exploiting Memory Hierarchy The Basic of Caches Measuring & Improving Cache Performance Virtual Memory A Common
Computer Organization and Structure Bing-Yu Chen National Taiwan University Large and Fast: Exploiting Memory Hierarchy The Basic of Caches Measuring & Improving Cache Performance Virtual Memory A Common
LECTURE 11. Memory Hierarchy
 LECTURE 11 Memory Hierarchy MEMORY HIERARCHY When it comes to memory, there are two universally desirable properties: Large Size: ideally, we want to never have to worry about running out of memory. Speed
LECTURE 11 Memory Hierarchy MEMORY HIERARCHY When it comes to memory, there are two universally desirable properties: Large Size: ideally, we want to never have to worry about running out of memory. Speed
COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface. 5 th. Edition. Chapter 5. Large and Fast: Exploiting Memory Hierarchy
 COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface 5 th Edition Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address
COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface 5 th Edition Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address
The Memory Hierarchy. Cache, Main Memory, and Virtual Memory (Part 2)
 The Memory Hierarchy Cache, Main Memory, and Virtual Memory (Part 2) Lecture for CPSC 5155 Edward Bosworth, Ph.D. Computer Science Department Columbus State University Cache Line Replacement The cache
The Memory Hierarchy Cache, Main Memory, and Virtual Memory (Part 2) Lecture for CPSC 5155 Edward Bosworth, Ph.D. Computer Science Department Columbus State University Cache Line Replacement The cache
CS/ECE 3330 Computer Architecture. Chapter 5 Memory
 CS/ECE 3330 Computer Architecture Chapter 5 Memory Last Chapter n Focused exclusively on processor itself n Made a lot of simplifying assumptions IF ID EX MEM WB n Reality: The Memory Wall 10 6 Relative
CS/ECE 3330 Computer Architecture Chapter 5 Memory Last Chapter n Focused exclusively on processor itself n Made a lot of simplifying assumptions IF ID EX MEM WB n Reality: The Memory Wall 10 6 Relative
Memory. Principle of Locality. It is impossible to have memory that is both. We create an illusion for the programmer. Employ memory hierarchy
 Datorarkitektur och operativsystem Lecture 7 Memory It is impossible to have memory that is both Unlimited (large in capacity) And fast 5.1 Intr roduction We create an illusion for the programmer Before
Datorarkitektur och operativsystem Lecture 7 Memory It is impossible to have memory that is both Unlimited (large in capacity) And fast 5.1 Intr roduction We create an illusion for the programmer Before
Memory Hierarchy Design (Appendix B and Chapter 2)
 CS359: Computer Architecture Memory Hierarchy Design (Appendix B and Chapter 2) Yanyan Shen Department of Computer Science and Engineering 1 Four Memory Hierarchy Questions Q1 (block placement): where
CS359: Computer Architecture Memory Hierarchy Design (Appendix B and Chapter 2) Yanyan Shen Department of Computer Science and Engineering 1 Four Memory Hierarchy Questions Q1 (block placement): where
Memory Hierarchy. Memory Flavors Principle of Locality Program Traces Memory Hierarchies Associativity. (Study Chapter 5)
 Memory Hierarchy Why are you dressed like that? Halloween was weeks ago! It makes me look faster, don t you think? Memory Flavors Principle of Locality Program Traces Memory Hierarchies Associativity (Study
Memory Hierarchy Why are you dressed like that? Halloween was weeks ago! It makes me look faster, don t you think? Memory Flavors Principle of Locality Program Traces Memory Hierarchies Associativity (Study
Page 1. Multilevel Memories (Improving performance using a little cash )
 Page 1 Multilevel Memories (Improving performance using a little cash ) 1 Page 2 CPU-Memory Bottleneck CPU Memory Performance of high-speed computers is usually limited by memory bandwidth & latency Latency
Page 1 Multilevel Memories (Improving performance using a little cash ) 1 Page 2 CPU-Memory Bottleneck CPU Memory Performance of high-speed computers is usually limited by memory bandwidth & latency Latency
Chapter 5. Large and Fast: Exploiting Memory Hierarchy
 Chapter 5 Large and Fast: Exploiting Memory Hierarchy Review: Major Components of a Computer Processor Devices Control Memory Input Datapath Output Secondary Memory (Disk) Main Memory Cache Performance
Chapter 5 Large and Fast: Exploiting Memory Hierarchy Review: Major Components of a Computer Processor Devices Control Memory Input Datapath Output Secondary Memory (Disk) Main Memory Cache Performance
CENG 3420 Computer Organization and Design. Lecture 08: Cache Review. Bei Yu
 CENG 3420 Computer Organization and Design Lecture 08: Cache Review Bei Yu CEG3420 L08.1 Spring 2016 A Typical Memory Hierarchy q Take advantage of the principle of locality to present the user with as
CENG 3420 Computer Organization and Design Lecture 08: Cache Review Bei Yu CEG3420 L08.1 Spring 2016 A Typical Memory Hierarchy q Take advantage of the principle of locality to present the user with as
Review: Computer Organization
 Review: Computer Organization Cache Chansu Yu Caches: The Basic Idea A smaller set of storage locations storing a subset of information from a larger set. Typically, SRAM for DRAM main memory: Processor
Review: Computer Organization Cache Chansu Yu Caches: The Basic Idea A smaller set of storage locations storing a subset of information from a larger set. Typically, SRAM for DRAM main memory: Processor
Chapter 5. Large and Fast: Exploiting Memory Hierarchy
 Chapter 5 Large and Fast: Exploiting Memory Hierarchy Static RAM (SRAM) Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic disk 0.5ns 2.5ns, $2000 $5000 per GB 5.1 Introduction Memory Technology 5ms
Chapter 5 Large and Fast: Exploiting Memory Hierarchy Static RAM (SRAM) Dynamic RAM (DRAM) 50ns 70ns, $20 $75 per GB Magnetic disk 0.5ns 2.5ns, $2000 $5000 per GB 5.1 Introduction Memory Technology 5ms
ECE 485/585 Microprocessor System Design
 Microprocessor System Design Lecture 8: Principle of Locality Cache Architecture Cache Replacement Policies Zeshan Chishti Electrical and Computer Engineering Dept Maseeh College of Engineering and Computer
Microprocessor System Design Lecture 8: Principle of Locality Cache Architecture Cache Replacement Policies Zeshan Chishti Electrical and Computer Engineering Dept Maseeh College of Engineering and Computer
Chapter 7 Large and Fast: Exploiting Memory Hierarchy. Memory Hierarchy. Locality. Memories: Review
 Memories: Review Chapter 7 Large and Fast: Exploiting Hierarchy DRAM (Dynamic Random Access ): value is stored as a charge on capacitor that must be periodically refreshed, which is why it is called dynamic
Memories: Review Chapter 7 Large and Fast: Exploiting Hierarchy DRAM (Dynamic Random Access ): value is stored as a charge on capacitor that must be periodically refreshed, which is why it is called dynamic
LECTURE 4: LARGE AND FAST: EXPLOITING MEMORY HIERARCHY
 LECTURE 4: LARGE AND FAST: EXPLOITING MEMORY HIERARCHY Abridged version of Patterson & Hennessy (2013):Ch.5 Principle of Locality Programs access a small proportion of their address space at any time Temporal
LECTURE 4: LARGE AND FAST: EXPLOITING MEMORY HIERARCHY Abridged version of Patterson & Hennessy (2013):Ch.5 Principle of Locality Programs access a small proportion of their address space at any time Temporal
EE 457 Unit 7a. Cache and Memory Hierarchy
 EE 457 Unit 7a Cache and Memory Hierarchy 2 Memory Hierarchy & Caching Use several levels of faster and faster memory to hide delay of upper levels Registers Unit of Transfer:, Half, or Byte (LW, LH, LB
EE 457 Unit 7a Cache and Memory Hierarchy 2 Memory Hierarchy & Caching Use several levels of faster and faster memory to hide delay of upper levels Registers Unit of Transfer:, Half, or Byte (LW, LH, LB
ECE7995 (6) Improving Cache Performance. [Adapted from Mary Jane Irwin s slides (PSU)]
![ECE7995 (6) Improving Cache Performance. [Adapted from Mary Jane Irwin s slides (PSU)] ECE7995 (6) Improving Cache Performance. [Adapted from Mary Jane Irwin s slides (PSU)]](/thumbs/72/68075397.jpg) ECE7995 (6) Improving Cache Performance [Adapted from Mary Jane Irwin s slides (PSU)] Measuring Cache Performance Assuming cache hit costs are included as part of the normal CPU execution cycle, then CPU
ECE7995 (6) Improving Cache Performance [Adapted from Mary Jane Irwin s slides (PSU)] Measuring Cache Performance Assuming cache hit costs are included as part of the normal CPU execution cycle, then CPU
Donn Morrison Department of Computer Science. TDT4255 Memory hierarchies
 TDT4255 Lecture 10: Memory hierarchies Donn Morrison Department of Computer Science 2 Outline Chapter 5 - Memory hierarchies (5.1-5.5) Temporal and spacial locality Hits and misses Direct-mapped, set associative,
TDT4255 Lecture 10: Memory hierarchies Donn Morrison Department of Computer Science 2 Outline Chapter 5 - Memory hierarchies (5.1-5.5) Temporal and spacial locality Hits and misses Direct-mapped, set associative,
Basic Memory Hierarchy Principles. Appendix C (Not all will be covered by the lecture; studying the textbook is recommended!)
 Basic Memory Hierarchy Principles Appendix C (Not all will be covered by the lecture; studying the textbook is recommended!) Cache memory idea Use a small faster memory, a cache memory, to store recently
Basic Memory Hierarchy Principles Appendix C (Not all will be covered by the lecture; studying the textbook is recommended!) Cache memory idea Use a small faster memory, a cache memory, to store recently
Chapter Seven. Large & Fast: Exploring Memory Hierarchy
 Chapter Seven Large & Fast: Exploring Memory Hierarchy 1 Memories: Review SRAM (Static Random Access Memory): value is stored on a pair of inverting gates very fast but takes up more space than DRAM DRAM
Chapter Seven Large & Fast: Exploring Memory Hierarchy 1 Memories: Review SRAM (Static Random Access Memory): value is stored on a pair of inverting gates very fast but takes up more space than DRAM DRAM
Memory Technology. Chapter 5. Principle of Locality. Chapter 5 Large and Fast: Exploiting Memory Hierarchy 1
 COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface Chapter 5 Large and Fast: Exploiting Memory Hierarchy 5 th Edition Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic
COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface Chapter 5 Large and Fast: Exploiting Memory Hierarchy 5 th Edition Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic
Caches II. CSE 351 Spring Instructor: Ruth Anderson
 Caches II CSE 35 Spring 27 Instructor: Ruth Anderson Teaching Assistants: Dylan Johnson Kevin Bi Linxing Preston Jiang Cody Ohlsen Yufang Sun Joshua Curtis Administrivia Office Hours Changes check calendar!!
Caches II CSE 35 Spring 27 Instructor: Ruth Anderson Teaching Assistants: Dylan Johnson Kevin Bi Linxing Preston Jiang Cody Ohlsen Yufang Sun Joshua Curtis Administrivia Office Hours Changes check calendar!!
14:332:331. Week 13 Basics of Cache
 14:332:331 Computer Architecture and Assembly Language Spring 2006 Week 13 Basics of Cache [Adapted from Dave Patterson s UCB CS152 slides and Mary Jane Irwin s PSU CSE331 slides] 331 Week131 Spring 2006
14:332:331 Computer Architecture and Assembly Language Spring 2006 Week 13 Basics of Cache [Adapted from Dave Patterson s UCB CS152 slides and Mary Jane Irwin s PSU CSE331 slides] 331 Week131 Spring 2006
Caches Part 1. Instructor: Sören Schwertfeger. School of Information Science and Technology SIST
 CS 110 Computer Architecture Caches Part 1 Instructor: Sören Schwertfeger http://shtech.org/courses/ca/ School of Information Science and Technology SIST ShanghaiTech University Slides based on UC Berkley's
CS 110 Computer Architecture Caches Part 1 Instructor: Sören Schwertfeger http://shtech.org/courses/ca/ School of Information Science and Technology SIST ShanghaiTech University Slides based on UC Berkley's
The Memory Hierarchy Cache, Main Memory, and Virtual Memory
 The Memory Hierarchy Cache, Main Memory, and Virtual Memory Lecture for CPSC 5155 Edward Bosworth, Ph.D. Computer Science Department Columbus State University The Simple View of Memory The simplest view
The Memory Hierarchy Cache, Main Memory, and Virtual Memory Lecture for CPSC 5155 Edward Bosworth, Ph.D. Computer Science Department Columbus State University The Simple View of Memory The simplest view
Key Point. What are Cache lines
 Caching 1 Key Point What are Cache lines Tags Index offset How do we find data in the cache? How do we tell if it s the right data? What decisions do we need to make in designing a cache? What are possible
Caching 1 Key Point What are Cache lines Tags Index offset How do we find data in the cache? How do we tell if it s the right data? What decisions do we need to make in designing a cache? What are possible
CS161 Design and Architecture of Computer Systems. Cache $$$$$
 CS161 Design and Architecture of Computer Systems Cache $$$$$ Memory Systems! How can we supply the CPU with enough data to keep it busy?! We will focus on memory issues,! which are frequently bottlenecks
CS161 Design and Architecture of Computer Systems Cache $$$$$ Memory Systems! How can we supply the CPU with enough data to keep it busy?! We will focus on memory issues,! which are frequently bottlenecks
Computer Architecture: Optional Homework Set
 Computer Architecture: Optional Homework Set Black Board due date: Hard Copy due date: Monday April 27 th, at Midnight. Tuesday April 28 th, during Class. Exercise 1: (50 Points) Patterson and Hennessy
Computer Architecture: Optional Homework Set Black Board due date: Hard Copy due date: Monday April 27 th, at Midnight. Tuesday April 28 th, during Class. Exercise 1: (50 Points) Patterson and Hennessy
Chapter 7: Large and Fast: Exploiting Memory Hierarchy
 Chapter 7: Large and Fast: Exploiting Memory Hierarchy Basic Memory Requirements Users/Programmers Demand: Large computer memory ery Fast access memory Technology Limitations Large Computer memory relatively
Chapter 7: Large and Fast: Exploiting Memory Hierarchy Basic Memory Requirements Users/Programmers Demand: Large computer memory ery Fast access memory Technology Limitations Large Computer memory relatively
Memory Hierarchies. Instructor: Dmitri A. Gusev. Fall Lecture 10, October 8, CS 502: Computers and Communications Technology
 Memory Hierarchies Instructor: Dmitri A. Gusev Fall 2007 CS 502: Computers and Communications Technology Lecture 10, October 8, 2007 Memories SRAM: value is stored on a pair of inverting gates very fast
Memory Hierarchies Instructor: Dmitri A. Gusev Fall 2007 CS 502: Computers and Communications Technology Lecture 10, October 8, 2007 Memories SRAM: value is stored on a pair of inverting gates very fast
Memory Hierarchy. Reading. Sections 5.1, 5.2, 5.3, 5.4, 5.8 (some elements), 5.9 (2) Lecture notes from MKP, H. H. Lee and S.
 Memory Hierarchy Lecture notes from MKP, H. H. Lee and S. Yalamanchili Sections 5.1, 5.2, 5.3, 5.4, 5.8 (some elements), 5.9 Reading (2) 1 SRAM: Value is stored on a pair of inerting gates Very fast but
Memory Hierarchy Lecture notes from MKP, H. H. Lee and S. Yalamanchili Sections 5.1, 5.2, 5.3, 5.4, 5.8 (some elements), 5.9 Reading (2) 1 SRAM: Value is stored on a pair of inerting gates Very fast but
Caches. Jin-Soo Kim Computer Systems Laboratory Sungkyunkwan University
 Caches Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns
Caches Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM) 50ns
ELEC 5200/6200 Computer Architecture and Design Spring 2017 Lecture 6: Memory Organization Part I
 ELEC 5200/6200 Computer Architecture and Design Spring 2017 Lecture 6: Memory Organization Part I Ujjwal Guin, Assistant Professor Department of Electrical and Computer Engineering Auburn University, Auburn,
ELEC 5200/6200 Computer Architecture and Design Spring 2017 Lecture 6: Memory Organization Part I Ujjwal Guin, Assistant Professor Department of Electrical and Computer Engineering Auburn University, Auburn,
Chapter Seven. Memories: Review. Exploiting Memory Hierarchy CACHE MEMORY AND VIRTUAL MEMORY
 Chapter Seven CACHE MEMORY AND VIRTUAL MEMORY 1 Memories: Review SRAM: value is stored on a pair of inverting gates very fast but takes up more space than DRAM (4 to 6 transistors) DRAM: value is stored
Chapter Seven CACHE MEMORY AND VIRTUAL MEMORY 1 Memories: Review SRAM: value is stored on a pair of inverting gates very fast but takes up more space than DRAM (4 to 6 transistors) DRAM: value is stored
 Cache Architectures Design of Digital Circuits 217 Srdjan Capkun Onur Mutlu http://www.syssec.ethz.ch/education/digitaltechnik_17 Adapted from Digital Design and Computer Architecture, David Money Harris
Cache Architectures Design of Digital Circuits 217 Srdjan Capkun Onur Mutlu http://www.syssec.ethz.ch/education/digitaltechnik_17 Adapted from Digital Design and Computer Architecture, David Money Harris
Registers. Instruction Memory A L U. Data Memory C O N T R O L M U X A D D A D D. Sh L 2 M U X. Sign Ext M U X ALU CTL INSTRUCTION FETCH
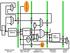 PC Instruction Memory 4 M U X Registers Sign Ext M U X Sh L 2 Data Memory M U X C O T R O L ALU CTL ISTRUCTIO FETCH ISTR DECODE REG FETCH EXECUTE/ ADDRESS CALC MEMOR ACCESS WRITE BACK A D D A D D A L U
PC Instruction Memory 4 M U X Registers Sign Ext M U X Sh L 2 Data Memory M U X C O T R O L ALU CTL ISTRUCTIO FETCH ISTR DECODE REG FETCH EXECUTE/ ADDRESS CALC MEMOR ACCESS WRITE BACK A D D A D D A L U
Chapter 7-1. Large and Fast: Exploiting Memory Hierarchy (part I: cache) 臺大電機系吳安宇教授. V1 11/24/2004 V2 12/01/2004 V3 12/08/2004 (minor)
 Chapter 7-1 Large and Fast: Exploiting Memory Hierarchy (part I: cache) 臺大電機系吳安宇教授 V1 11/24/2004 V2 12/01/2004 V3 12/08/2004 (minor) 臺大電機吳安宇教授 - 計算機結構 1 Outline 7.1 Introduction 7.2 The Basics of Caches
Chapter 7-1 Large and Fast: Exploiting Memory Hierarchy (part I: cache) 臺大電機系吳安宇教授 V1 11/24/2004 V2 12/01/2004 V3 12/08/2004 (minor) 臺大電機吳安宇教授 - 計算機結構 1 Outline 7.1 Introduction 7.2 The Basics of Caches
CS356: Discussion #9 Memory Hierarchy and Caches. Marco Paolieri Illustrations from CS:APP3e textbook
 CS356: Discussion #9 Memory Hierarchy and Caches Marco Paolieri (paolieri@usc.edu) Illustrations from CS:APP3e textbook The Memory Hierarchy So far... We modeled the memory system as an abstract array
CS356: Discussion #9 Memory Hierarchy and Caches Marco Paolieri (paolieri@usc.edu) Illustrations from CS:APP3e textbook The Memory Hierarchy So far... We modeled the memory system as an abstract array
Review: Performance Latency vs. Throughput. Time (seconds/program) is performance measure Instructions Clock cycles Seconds.
 Performance 980 98 982 983 984 985 986 987 988 989 990 99 992 993 994 995 996 997 998 999 2000 7/4/20 CS 6C: Great Ideas in Computer Architecture (Machine Structures) Caches Instructor: Michael Greenbaum
Performance 980 98 982 983 984 985 986 987 988 989 990 99 992 993 994 995 996 997 998 999 2000 7/4/20 CS 6C: Great Ideas in Computer Architecture (Machine Structures) Caches Instructor: Michael Greenbaum
Slide Set 9. for ENCM 369 Winter 2018 Section 01. Steve Norman, PhD, PEng
 Slide Set 9 for ENCM 369 Winter 2018 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary March 2018 ENCM 369 Winter 2018 Section 01
Slide Set 9 for ENCM 369 Winter 2018 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary March 2018 ENCM 369 Winter 2018 Section 01
COMPUTER ORGANIZATION AND DESIGN
 COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface 5 th Edition Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address
COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface 5 th Edition Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address
EEC 483 Computer Organization
 EEC 48 Computer Organization 5. The Basics of Cache Chansu Yu Caches: The Basic Idea A smaller set of storage locations storing a subset of information from a larger set (memory) Unlike registers or memory,
EEC 48 Computer Organization 5. The Basics of Cache Chansu Yu Caches: The Basic Idea A smaller set of storage locations storing a subset of information from a larger set (memory) Unlike registers or memory,
10/11/17. New-School Machine Structures. Review: Single Cycle Instruction Timing. Review: Single-Cycle RISC-V RV32I Datapath. Components of a Computer
 // CS C: Great Ideas in Computer Architecture (Machine Structures) s Part Instructors: Krste Asanović & Randy H Katz http://insteecsberkeleyedu/~csc/ // Fall - Lecture # Parallel Requests Assigned to computer
// CS C: Great Ideas in Computer Architecture (Machine Structures) s Part Instructors: Krste Asanović & Randy H Katz http://insteecsberkeleyedu/~csc/ // Fall - Lecture # Parallel Requests Assigned to computer
LECTURE 5: MEMORY HIERARCHY DESIGN
 LECTURE 5: MEMORY HIERARCHY DESIGN Abridged version of Hennessy & Patterson (2012):Ch.2 Introduction Programmers want unlimited amounts of memory with low latency Fast memory technology is more expensive
LECTURE 5: MEMORY HIERARCHY DESIGN Abridged version of Hennessy & Patterson (2012):Ch.2 Introduction Programmers want unlimited amounts of memory with low latency Fast memory technology is more expensive
CS 152 Computer Architecture and Engineering. Lecture 7 - Memory Hierarchy-II
 CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~krste
CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~krste
3Introduction. Memory Hierarchy. Chapter 2. Memory Hierarchy Design. Computer Architecture A Quantitative Approach, Fifth Edition
 Computer Architecture A Quantitative Approach, Fifth Edition Chapter 2 Memory Hierarchy Design 1 Introduction Programmers want unlimited amounts of memory with low latency Fast memory technology is more
Computer Architecture A Quantitative Approach, Fifth Edition Chapter 2 Memory Hierarchy Design 1 Introduction Programmers want unlimited amounts of memory with low latency Fast memory technology is more
Memory Hierarchy Y. K. Malaiya
 Memory Hierarchy Y. K. Malaiya Acknowledgements Computer Architecture, Quantitative Approach - Hennessy, Patterson Vishwani D. Agrawal Review: Major Components of a Computer Processor Control Datapath
Memory Hierarchy Y. K. Malaiya Acknowledgements Computer Architecture, Quantitative Approach - Hennessy, Patterson Vishwani D. Agrawal Review: Major Components of a Computer Processor Control Datapath
Memory. Lecture 22 CS301
 Memory Lecture 22 CS301 Administrative Daily Review of today s lecture w Due tomorrow (11/13) at 8am HW #8 due today at 5pm Program #2 due Friday, 11/16 at 11:59pm Test #2 Wednesday Pipelined Machine Fetch
Memory Lecture 22 CS301 Administrative Daily Review of today s lecture w Due tomorrow (11/13) at 8am HW #8 due today at 5pm Program #2 due Friday, 11/16 at 11:59pm Test #2 Wednesday Pipelined Machine Fetch
14:332:331. Week 13 Basics of Cache
 14:332:331 Computer Architecture and Assembly Language Fall 2003 Week 13 Basics of Cache [Adapted from Dave Patterson s UCB CS152 slides and Mary Jane Irwin s PSU CSE331 slides] 331 Lec20.1 Fall 2003 Head
14:332:331 Computer Architecture and Assembly Language Fall 2003 Week 13 Basics of Cache [Adapted from Dave Patterson s UCB CS152 slides and Mary Jane Irwin s PSU CSE331 slides] 331 Lec20.1 Fall 2003 Head
What is Cache Memory? EE 352 Unit 11. Motivation for Cache Memory. Memory Hierarchy. Cache Definitions Cache Address Mapping Cache Performance
 What is EE 352 Unit 11 Definitions Address Mapping Performance memory is a small, fast memory used to hold of data that the processor will likely need to access in the near future sits between the processor
What is EE 352 Unit 11 Definitions Address Mapping Performance memory is a small, fast memory used to hold of data that the processor will likely need to access in the near future sits between the processor
Cache Optimization. Jin-Soo Kim Computer Systems Laboratory Sungkyunkwan University
 Cache Optimization Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Cache Misses On cache hit CPU proceeds normally On cache miss Stall the CPU pipeline
Cache Optimization Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Cache Misses On cache hit CPU proceeds normally On cache miss Stall the CPU pipeline
CS 152 Computer Architecture and Engineering. Lecture 7 - Memory Hierarchy-II
 CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~krste!
CS 152 Computer Architecture and Engineering Lecture 7 - Memory Hierarchy-II Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~krste!
Sarah L. Harris and David Money Harris. Digital Design and Computer Architecture: ARM Edition Chapter 8 <1>
 Chapter 8 Digital Design and Computer Architecture: ARM Edition Sarah L. Harris and David Money Harris Digital Design and Computer Architecture: ARM Edition 215 Chapter 8 Chapter 8 :: Topics Introduction
Chapter 8 Digital Design and Computer Architecture: ARM Edition Sarah L. Harris and David Money Harris Digital Design and Computer Architecture: ARM Edition 215 Chapter 8 Chapter 8 :: Topics Introduction
Trying to design a simple yet efficient L1 cache. Jean-François Nguyen
 Trying to design a simple yet efficient L1 cache Jean-François Nguyen 1 Background Minerva is a 32-bit RISC-V soft CPU It is described in plain Python using nmigen FPGA-friendly Designed for reasonable
Trying to design a simple yet efficient L1 cache Jean-François Nguyen 1 Background Minerva is a 32-bit RISC-V soft CPU It is described in plain Python using nmigen FPGA-friendly Designed for reasonable
CMPT 300 Introduction to Operating Systems
 CMPT 300 Introduction to Operating Systems Cache 0 Acknowledgement: some slides are taken from CS61C course material at UC Berkeley Agenda Memory Hierarchy Direct Mapped Caches Cache Performance Set Associative
CMPT 300 Introduction to Operating Systems Cache 0 Acknowledgement: some slides are taken from CS61C course material at UC Berkeley Agenda Memory Hierarchy Direct Mapped Caches Cache Performance Set Associative
CS 61C: Great Ideas in Computer Architecture (Machine Structures) Caches Part 1
 CS 61C: Great Ideas in Computer Architecture (Machine Structures) Caches Part 1 Instructors: Krste Asanović & Randy H. Katz http://inst.eecs.berkeley.edu/~cs61c/ 10/11/17 Fall 2017 - Lecture #14 1 Parallel
CS 61C: Great Ideas in Computer Architecture (Machine Structures) Caches Part 1 Instructors: Krste Asanović & Randy H. Katz http://inst.eecs.berkeley.edu/~cs61c/ 10/11/17 Fall 2017 - Lecture #14 1 Parallel
Caches. Han Wang CS 3410, Spring 2012 Computer Science Cornell University. See P&H 5.1, 5.2 (except writes)
 Caches Han Wang CS 3410, Spring 2012 Computer Science Cornell University See P&H 5.1, 5.2 (except writes) This week: Announcements PA2 Work-in-progress submission Next six weeks: Two labs and two projects
Caches Han Wang CS 3410, Spring 2012 Computer Science Cornell University See P&H 5.1, 5.2 (except writes) This week: Announcements PA2 Work-in-progress submission Next six weeks: Two labs and two projects
Copyright 2012, Elsevier Inc. All rights reserved.
 Computer Architecture A Quantitative Approach, Fifth Edition Chapter 2 Memory Hierarchy Design 1 Introduction Programmers want unlimited amounts of memory with low latency Fast memory technology is more
Computer Architecture A Quantitative Approach, Fifth Edition Chapter 2 Memory Hierarchy Design 1 Introduction Programmers want unlimited amounts of memory with low latency Fast memory technology is more
CS61C : Machine Structures
 inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture #24 Cache II 27-8-6 Scott Beamer, Instructor New Flow Based Routers CS61C L24 Cache II (1) www.anagran.com Caching Terminology When we try
inst.eecs.berkeley.edu/~cs61c CS61C : Machine Structures Lecture #24 Cache II 27-8-6 Scott Beamer, Instructor New Flow Based Routers CS61C L24 Cache II (1) www.anagran.com Caching Terminology When we try
CACHE MEMORIES ADVANCED COMPUTER ARCHITECTURES. Slides by: Pedro Tomás
 CACHE MEMORIES Slides by: Pedro Tomás Additional reading: Computer Architecture: A Quantitative Approach, 5th edition, Chapter 2 and Appendix B, John L. Hennessy and David A. Patterson, Morgan Kaufmann,
CACHE MEMORIES Slides by: Pedro Tomás Additional reading: Computer Architecture: A Quantitative Approach, 5th edition, Chapter 2 and Appendix B, John L. Hennessy and David A. Patterson, Morgan Kaufmann,
CSCI 402: Computer Architectures. Fengguang Song Department of Computer & Information Science IUPUI. Recall
 CSCI 402: Computer Architectures Memory Hierarchy (2) Fengguang Song Department of Computer & Information Science IUPUI Recall What is memory hierarchy? Where each level is located? Each level s speed,
CSCI 402: Computer Architectures Memory Hierarchy (2) Fengguang Song Department of Computer & Information Science IUPUI Recall What is memory hierarchy? Where each level is located? Each level s speed,
The Memory Hierarchy & Cache Review of Memory Hierarchy & Cache Basics (from 350):
 The Memory Hierarchy & Cache Review of Memory Hierarchy & Cache Basics (from 350): Motivation for The Memory Hierarchy: { CPU/Memory Performance Gap The Principle Of Locality Cache $$$$$ Cache Basics:
The Memory Hierarchy & Cache Review of Memory Hierarchy & Cache Basics (from 350): Motivation for The Memory Hierarchy: { CPU/Memory Performance Gap The Principle Of Locality Cache $$$$$ Cache Basics:
