1 /20 2 /18 3 /20 4 /18 5 /24
|
|
|
- Bruce Dawson
- 6 years ago
- Views:
Transcription
1 M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.S084 Computation Structures Spring /20 2 /18 3 /20 4 /18 5 /24 Practice Quiz #2 Name Athena login name Score Recitation section o WF 11, (Silvina) o WF 1, (Andy) o WF 12, (Silvina) o None (pick up quiz in 32-G846) Please enter your name, Athena login name, and recitation section above. Enter your answers in the spaces provided below. You can use the extra white space and the backs of the pages for scratch work. The exam has an appendix which includes our 6.S084 reference guide and the RISC-V calling conventions. Problem 1. Assembly Language (20 points) (A) (6 points) You are given the following C code along with a partial translation of this code into RISC-V assembly. Please complete the assembly implementation of this code by fully specifying the 2 missing RISC-V instructions just before label L1. These must be actual RISC-V instructions, you may not use any pseudo-instructions. int A[1000]; for (int i = 0; i < 1000; i = i + 1) { A[i] = A[i] ^ 0x12345; // ^ is bitwise XOR in C } // Translation into RISC-V assembly: addi x11, x0, 0 // x11: i addi x12, x0, 1000 // x12: loop termination condition addi x16, x0, 0x100 // x16: array base missing instr lui x15, 0x12 missing instr addi x15, x15, 0x345 L1: bge x11, x12, L2 slli x13, x11, 2 add x17, x13, x16 lw x14, 0(x17) addi x11, x11, 1 xor x14, x14, x15 sw x14, 0(x17) jal x0, L1 L2: // byte offset into array // address of A[i] // x14 = A[i]. = 0x100 A: // contents of array A 6.S084 Spring of 11 - Practice Quiz #2
2 For the RISC-V instruction sequences below, provide the hex values of the specified registers after each sequence has been executed. Assume that each sequence execution ends when it reaches the unimp instruction. Also assume that all registers are initialized to 0 before execution of each sequence begins. (B) (6 points) li x11, 0x242 slli x12, x11, 12 li x13, 0xff or x14, x12, x13 unimp Value left in x11: 0x_242 Value left in x12: 0x_ Value left in x13: 0x_ff Value left in x14: 0x_2420ff (C) (8 points). = 0x0 li x11, 0x200 lw x11, 0(x11) blt x11, x0, L1 addi x12, x11, -1 jal x13, L2 L1: sub x12, x0, x11 L2: xori x12, x12, 0xfff unimp. = 0x200 X:.word 0x Value left in x0: 0x_0-0x = 0x789ABCDF ~(0x789ABCDF) = 0x Value left in x11: 0x_ Value left in x12: 0x_ Value left in x13: 0x_0 6.S084 Spring of 11 - Practice Quiz #2
3 Problem 2. RISC-V Assembly and Calling Conventions (18 points) Our RISC-V processor does not have a multiply instruction, so we have to do multiplications in software. The C code below shows a recursive implementation of multiplication by repeated addition of unsigned integers (in C, unsigned int denotes an unsigned integer). Ben Bitdiddle has written and hand-compiled this function into the assembly code given below, but the code is not behaving as expected. Find the bugs in Ben s assembly code and write a correct version. C code for unsigned multiplication unsigned int mul(unsigned int x, unsigned int y) { if (x == 0) { return 0; } else { unsigned int lowbit = x & 1; unsigned int p = lowbit? y : 0; return p + (mul(x >> 1, y) << 1); } } Buggy assembly code mul: addi sp, sp, -8 sw s0, 0(sp) sw ra, 4(sp) beqz a0, mul_done andi s0, a0, 1 // lowbit in s0 mv t0, zero // p in t0 beqz s0, lowbit_zero mv t0, a0 lowbit_zero: slli a0, a0, 1 jal mul srli a0, a0, 1 add a0, t0, a0 lw s0, 4(sp) lw ra, 0(sp) addi sp, sp, 8 mul_done: ret 6.S084 Spring of 11 - Practice Quiz #2
4 Rewrite assembly code so that it behaves as expected and follows the RISC-V calling convention: mul: beqz a0, mul_done addi sp, sp, -8 sw s0, 0(sp) sw ra, 4(sp) andi t0, a0, 1 // lowbit in t0 mv s0, zero // p in s0 beqz t0, lowbit_zero mv s0, a1 lowbit_zero: srli a0, a0, 1 jal mul slli a0, a0, 1 add a0, s0, a0 lw s0, 0(sp) lw ra, 4(sp) addi sp, sp, 8 mul_done: ret Errors: 1. s0 and ra are saved and restored from different offsets should be lw ra, 4(sp); lw s0, 0(sp) 2. beqz a0, mul_done should be before sp is decremented (or mul_done label should be moved up 3 instructions) 3. p cannot be in t0 because it s caller-saved and used after call; store lowbit in t0 and p in s0 instead, or use an s1 register, or add code before and after jal mul to save and restore t0. 4. Slli and srli are switched (first one should be slri, second slli) 5. p should come from a1 not a0. 6.S084 Spring of 11 - Practice Quiz #2
5 Problem 3. Procedures and Stacks (20 points) You are given an incomplete listing of a C procedure and its translation to RISC-V assembly code (shown on the right): int f(int a, int b) { int tempa = a + a; int tempb = ***; if (a < b) return a + f(tempa, tempb); else return???; } f: bge a0, a1, L1 xx: addi sp, sp, -8 sw a0, 0(sp) sw ra, 4(sp) add a0, a0, a0 addi a1, a1, 1 jal ra, f (A) (3 points) Give the HEX encoding of the jr ra instruction at the end of the program. rd = x0; rs1 = ra = x1 jr = jalr (opcode: ) offset = 0 (12 bits) Hex encoding of jr ra: 0x _8067 Imm[11:0], rs1, 000, rd, opcode 0b (B) (2 points) Give the HEX encoding of the bge a0, a1, L1 instruction at the beginning of the program. rs1 = a0 = x10; rs2 = a1 = x11 bge (opcode: ) offset = 12 words, 48 bytes L2: lw t0, 0(sp) lw ra, 4(sp) addi sp, sp, 8 add a0, a0, t0 jr ra L1: sub a0, a0, a1 jr ra Hex encoding of bge a0, a1, L1: 0x _2B55863 Imm[12][10:5], rs2, rs1, 101, Imm[4:1][11], opcode 0b (C) (2 points) What is the missing C expression corresponding to the *** in the above program? b + 1 (give C code expression) (D) (2 points) What is the missing C expression corresponding to the??? in the above program? a - b (give C code expression) (E) (2 points) Suppose the instruction jal ra, f were replaced by the instruction j f in the above program. What would be the result? Mark exactly one answer: The procedure would still work just fine: The procedure would compute the proper value, but not restore registers properly: The procedure would no longer compute f(a,b) properly: X 6.S084 Spring of 11 - Practice Quiz #2
6 The program calls f(2,5) via the instruction jal ra, f. The program is interrupted just prior to an execution (not necessarily the first) of the bge instruction at label f. The diagram in the right shows the contents of a region of memory. All addresses and data values are shown in hex. The current contents of the SP are 0x128. (F) (3 points) What are the arguments to the current (most recent) call to f? Current arguments, a = 8 ; b = 7 SP 0x12C 0x130 0x134 0x138 0x08 0x54 0x04 0x54 0x02 0xA8 0x04 (G) (2 points) What value was in SP just prior to the initial call to f? Initial contents of SP: 0x 138 (H) (2 points) What is the address of the jal ra, f instruction that made the original call to f(2,5)? 0xA8 4 = 0xA4 Address of original call to f(2,5): 0x A4 (I) (2 points) What is the hex address of the instruction at L2? Address of instruction at L2: 0x 54 6.S084 Spring of 11 - Practice Quiz #2
7 Problem 4. Hardware Implementation (18 points) We want to add the following instruction to the RISC-V ISA: lwr rd, rs1, rs2 The behavior of this new lwr instruction is that it adds the contents of source registers rs1 and rs2 and uses the result as the address for your load. In other words: reg[rd] <= mem[reg[rs1] + reg[rs2]] pc <= pc + 4 Suppose you were given a decoder that was fully functioning prior to the addition of this new instruction, and you were told that a new type IType LWR has been added for this instruction. Fill in the required changes to the Decode and Execute functions in order to support adding this instruction. We have included relevant portions of these functions below to simplify this task. Assume that the rest of the hardware implementation is the same as what you have seen in lecture and lab. (A) (12 points) Fill in the required additions to the code below. typedef enum { OP, OPIMM, BRANCH, LUI, JAL, JALR, LOAD, STORE, GCD, AUIPC, LWR, Unsupported} IType deriving (Bits, Eq, FShow); function DecodedInst decode(bit#(32) inst); Bit#(7) oplwr = 7'b ; // or other available opcode DecodedInst dinst =?; dinst.itype = Unsupported; case(opcode) opload: if (funct3 == fnlw) begin dinst = DecodedInst { rd: tagged Valid rd, rs1: rs1, rs2:?, imm: immi, brfunc:?, alufunc:?, itype: LOAD }; end oplwr: dinst = DecodedInst { rd: tagged Valid rd, rs1: rs1, rs2: rs2, imm:?, brfunc:?, alufunc:?, itype: LWR }; endcase return dinst; endfunction Write your code below. Please add arrows to indicate where your code fits in the decode function. 6.S084 Spring of 11 - Practice Quiz #2
8 function ExecInst execute(decodedinst dinst, Word rval1, Word rval2, Word pc); let imm = dinst.imm; let brfunc = dinst.brfunc; let alufunc = dinst.alufunc; Word data =?; Word nextpc =?; Word addr =?; case (dinst.itype) OP: begin data = alu(rval1, rval2, alufunc); nextpc = pc+4; end OPIMM: begin data = alu(rval1, imm, alufunc); nextpc = pc+4; end BRANCH: begin nextpc=alubr(rval1,rval2,brfunc)? pc+imm : pc+4; end LUI: begin data = imm; nextpc = pc+4; end JAL: begin data = pc+4; nextpc = pc+imm; end JALR: begin data = pc+4; nextpc = (rval1+imm) & ~1; end LOAD: begin addr = rval1+imm; nextpc = pc+4; end STORE: begin data = rval2; addr = rval1+imm; nextpc = pc+4; end AUIPC: begin data = pc+imm; nextpc = pc+4; end LWR: begin addr = rval1+rval2; nextpc = pc+4; end endcase ExecInst einst =?; einst.itype = dinst.itype; einst.rd = dinst.rd; einst.data = data; einst.addr = addr; einst.nextpc = nextpc; return einst; endfunction Write your code below. Please add arrows to indicate where your code fits in the execute function. (B) (3 points) Could a store operation that calculated the address in the same manner as lwr be added without major changes to the RISC-V ISA? No Yes No (C) (3 points) If you answered Yes to B then provide a brief summary of the required changes. If you answered No to B then explain why not. A store instruction already makes use of rs1, and rs2 because it needs rs2 to hold the data to be written to memory. So this kind of address calculation would not be possible for a store operation. 6.S084 Spring of 11 - Practice Quiz #2
9 Problem 5. Caches (24 points) Consider the diagram to the right for a 2-way set associative cache to be used with our RISC-V processor. Each cache line holds a single 32-bit word of data along with its associated tag and valid bit (0 when the cache line is invalid, 1 when the cache line is valid). Cache index Valid bit Tag A Data[31:0] Row 0 Row 1 Row 2 Row 3 Row 4 Row 5 Row 6 Valid bit Tag B Data[31:0] (A) (2 points) RISC-V uses 32-bit byte addresses, A[31:0]. To ensure the best cache performance, which address bits should be used for the cache index? Which address bits should be used for the tag field? Tag field Hit? =? Row 7 =? Data to CPU address bits used for cache index: A[ 4 : 2 ] address bits used for tag field: A[_31 : 5 ] (B) (2 points) Suppose the processor does a read of location 0x5678. Identify which cache location(s) would be checked to see if that location is in the cache. For each location, specify the cache way (A or B) and set (row) number (0 through 7). E.g., 3A for set 3, way A. If there is a cache hit on this access, what would be the contents of the tag data for the cache line that holds the data for this location? A[4:2] = 0b110; A[31:5] = 0b = 0x2B3 cache location(s) checked on access to 0x5678: 6A, 6B cache tag data on hit for location 0x5678 (hex): 0x 2B3 (C) (2 points) Assume that checking the cache on each read takes 1 cycle and that refilling the cache line on a miss takes an additional 8 cycles. If we wanted the average access time over many reads to be 1.1 cycles, what is the minimum hit ratio the cache must achieve during that period of time? You needn t simplify your answer. 1.1 = 1 + (1 HR)8 minimum hit ratio for 1.1 cycle average access time: 7.9/8 6.S084 Spring of 11 - Practice Quiz #2
10 (D) (5 points) Find the cache hit ratio for the following program. Because the loop is executed many times, you can ignore code before/after the loop and focus on the average behavior of a loop iterations. Assume the cache is empty before execution begins (all valid bits are 0) and that an LRU replacement policy is used. Remember the cache is used for both instruction and data accesses.. = 0 // Code starts at address 0 addi x4, x0, 0x100 mv x1, x0 lui x2, 1 // x2 = 0x1000 loop: lw x3, 0(x4) addi x4, x4, 4 add x1, x1, x3 addi x2, x2, -1 bnez x2, loop sw x1, 0x100(x0) unimp // halt. = 0x100 source:. =. + 0x4000 // Set source to 0x100, reserve 0x1000 words Each iteration: 5 instr hits; 1 data miss hit ratio: 5/6 (E) (3 points) After the program of part (D) has finished execution what information is stored in set (row) 4 of the cache? Give the addresses for the two locations that are cached (one in each of the sections) or briefly explain why that information can t be determined. Last array element at address 0x = 0x40FC (row 7), so row 4 has 0x40F0. Addresses whose data is cached in set 4: 0x10 and 0x40F0 For the rest of this problem, the cache is modified so that it has a block size of 2 words per line and the number of words in the cache remains the same (i.e., the cache now has 4 lines per way). (F) (2 points) Specify which bits of the address should be used for the block offset, the cache index and the tag. address bits used for block and byte offset: A[ 2 : 0 ] address bits used for cache index: A[ 4 : 3 ] address bits used for tag field: A[ 31_: 5 ] (G) (4 points) Find the hit ratio for the program in part (D) using this new cache configuration. Every 2 iterations: 10 instr hits; 1 data hit; 1 data miss hit ratio: 11/12 END OF PRACTICE QUIZ 2! 6.S084 Spring of 11 - Practice Quiz #2
11 Appendix: RISC-V Calling conventions: 6.S084 Spring of 11 - Practice Quiz #2
1 /20 2 /18 3 /20 4 /18 5 /24
 M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.S084 Computation Structures Spring 2018 1 /20 2 /18 3 /20 4 /18 5 /24 Practice
M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.S084 Computation Structures Spring 2018 1 /20 2 /18 3 /20 4 /18 5 /24 Practice
1 /15 2 /20 3 /20 4 /25 5 /20
 M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.S084 Computation Structures Spring 2018 1 /15 2 /20 3 /20 4 /25 5 /20 Quiz
M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.S084 Computation Structures Spring 2018 1 /15 2 /20 3 /20 4 /25 5 /20 Quiz
1 /18 2 /16 3 /18 4 /26 5 /22
 M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.004 Computation Structures Fall 2018 Quiz #2 1 /18 2 /16 3 /18 4 /26 5 /22
M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.004 Computation Structures Fall 2018 Quiz #2 1 /18 2 /16 3 /18 4 /26 5 /22
1 /18 2 /16 3 /18 4 /26 5 /22
 M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.004 Computation Structures Fall 2018 Quiz #2 1 /18 2 /16 3 /18 4 /26 5 /22
M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.004 Computation Structures Fall 2018 Quiz #2 1 /18 2 /16 3 /18 4 /26 5 /22
6.004 Tutorial Problems L3 Procedures and Stacks
 6.004 Tutorial Problems L3 Procedures and Stacks RISC-V Calling Conventions: Caller places arguments in registers a0-a7 Caller transfers control to callee using jal (jump-and-link) to capture the urn address
6.004 Tutorial Problems L3 Procedures and Stacks RISC-V Calling Conventions: Caller places arguments in registers a0-a7 Caller transfers control to callee using jal (jump-and-link) to capture the urn address
Implementing RISC-V Interpreter in Hardware
 Implementing RISC-V Interpreter in Hardware Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology October 16, 2018 MIT 6.004 Fall 2018 L11-1 Instruction interpreter
Implementing RISC-V Interpreter in Hardware Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology October 16, 2018 MIT 6.004 Fall 2018 L11-1 Instruction interpreter
6.004 Recitation Problems L11 RISC-V Interpreter
 6.004 Recitation Problems L11 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. New Bluespec Constructs: Maybe Types // Maybe#() is a
6.004 Recitation Problems L11 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. New Bluespec Constructs: Maybe Types // Maybe#() is a
6.004 Recitation Problems L11 RISC-V Interpreter
 6.004 Recitation Problems L11 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. New Bluespec Constructs: Maybe Types // Maybe#() is a
6.004 Recitation Problems L11 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. New Bluespec Constructs: Maybe Types // Maybe#() is a
6.004 Recitation Problems L13 RISC-V Interpreter
 6.004 Recitation Problems L13 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. RISC-V Interpreter: Components Register File typedef Bit#(32)
6.004 Recitation Problems L13 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. RISC-V Interpreter: Components Register File typedef Bit#(32)
6.004 Recitation Problems L13 RISC-V Interpreter
 6.004 Recitation Problems L13 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. RISC-V Interpreter: Components Register File typedef Bit#(32)
6.004 Recitation Problems L13 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. RISC-V Interpreter: Components Register File typedef Bit#(32)
Control Unit. Main Memory. control. status. address instructions. address data. Internal storage Datapath
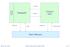 control Internal storage Datapath status Control Unit address data address instructions Main Memory March 20, 2018 http://csg.csail.mit.edu/6.s084 L11-1 Our interpreter is a Single-Cycle RISC-V Processor
control Internal storage Datapath status Control Unit address data address instructions Main Memory March 20, 2018 http://csg.csail.mit.edu/6.s084 L11-1 Our interpreter is a Single-Cycle RISC-V Processor
Non-Pipelined Processors
 Constructive Computer Architecture: Non-Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L10-1 Single-Cycle RISC Processor As an illustrative
Constructive Computer Architecture: Non-Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L10-1 Single-Cycle RISC Processor As an illustrative
6.004 Tutorial Problems L14 Cache Implementation
 6.004 Tutorial Problems L14 Cache Implementation Cache Miss Types Compulsory Miss: Starting with an empty cache, a cache line is first referenced (invalid) Capacity Miss: The cache is not big enough to
6.004 Tutorial Problems L14 Cache Implementation Cache Miss Types Compulsory Miss: Starting with an empty cache, a cache line is first referenced (invalid) Capacity Miss: The cache is not big enough to
Non-pipelined Multicycle processors
 Non-pipelined Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology Code for the lecture is available on the course website under the code tab
Non-pipelined Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology Code for the lecture is available on the course website under the code tab
ece4750-tinyrv-isa.txt
 ========================================================================== Tiny RISC-V Instruction Set Architecture ========================================================================== # Author :
========================================================================== Tiny RISC-V Instruction Set Architecture ========================================================================== # Author :
1 /10 2 /16 3 /18 4 /15 5 /20 6 /9 7 /12
 M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.004 Computation Structures Fall 2018 Practice Quiz #3B Name Athena login
M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.004 Computation Structures Fall 2018 Practice Quiz #3B Name Athena login
6.004 Tutorial Problems L14 Cache Implementation
 6.004 Tutorial Problems L14 Cache Implementation Cache Miss Types Compulsory Miss: Starting with an empty cache, a cache line is first referenced (invalid) Capacity Miss: The cache is not big enough to
6.004 Tutorial Problems L14 Cache Implementation Cache Miss Types Compulsory Miss: Starting with an empty cache, a cache line is first referenced (invalid) Capacity Miss: The cache is not big enough to
Procedures and Stacks
 Procedures and Stacks Daniel Sanchez Computer Science & Artificial Intelligence Lab M.I.T. March 15, 2018 L10-1 Announcements Schedule has shifted due to snow day Quiz 2 is now on Thu 4/12 (one week later)
Procedures and Stacks Daniel Sanchez Computer Science & Artificial Intelligence Lab M.I.T. March 15, 2018 L10-1 Announcements Schedule has shifted due to snow day Quiz 2 is now on Thu 4/12 (one week later)
Programmable Machines
 Programmable Machines Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab M.I.T. Quiz 1: next week Covers L1-L8 Oct 11, 7:30-9:30PM Walker memorial 50-340 L09-1 6.004 So Far Using Combinational
Programmable Machines Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab M.I.T. Quiz 1: next week Covers L1-L8 Oct 11, 7:30-9:30PM Walker memorial 50-340 L09-1 6.004 So Far Using Combinational
Non-Pipelined Processors
 Constructive Computer Architecture: Non-Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology September 29, 2014 http://csg.csail.mit.edu/6.175
Constructive Computer Architecture: Non-Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology September 29, 2014 http://csg.csail.mit.edu/6.175
Programmable Machines
 Programmable Machines Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab M.I.T. Quiz 1: next week Covers L1-L8 Oct 11, 7:30-9:30PM Walker memorial 50-340 L09-1 6.004 So Far Using Combinational
Programmable Machines Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab M.I.T. Quiz 1: next week Covers L1-L8 Oct 11, 7:30-9:30PM Walker memorial 50-340 L09-1 6.004 So Far Using Combinational
MIPS%Assembly% E155%
 MIPS%Assembly% E155% Outline MIPS Architecture ISA Instruction types Machine codes Procedure call Stack 2 The MIPS Register Set Name Register Number Usage $0 0 the constant value 0 $at 1 assembler temporary
MIPS%Assembly% E155% Outline MIPS Architecture ISA Instruction types Machine codes Procedure call Stack 2 The MIPS Register Set Name Register Number Usage $0 0 the constant value 0 $at 1 assembler temporary
Examples of branch instructions
 Examples of branch instructions Beq rs,rt,target #go to target if rs = rt Beqz rs, target #go to target if rs = 0 Bne rs,rt,target #go to target if rs!= rt Bltz rs, target #go to target if rs < 0 etc.
Examples of branch instructions Beq rs,rt,target #go to target if rs = rt Beqz rs, target #go to target if rs = 0 Bne rs,rt,target #go to target if rs!= rt Bltz rs, target #go to target if rs < 0 etc.
Compiling Code, Procedures and Stacks
 Compiling Code, Procedures and Stacks L03-1 RISC-V Recap Computational Instructions executed by ALU Register-Register: op dest, src1, src2 Register-Immediate: op dest, src1, const Control flow instructions
Compiling Code, Procedures and Stacks L03-1 RISC-V Recap Computational Instructions executed by ALU Register-Register: op dest, src1, src2 Register-Immediate: op dest, src1, const Control flow instructions
Flow of Control -- Conditional branch instructions
 Flow of Control -- Conditional branch instructions You can compare directly Equality or inequality of two registers One register with 0 (>,
Flow of Control -- Conditional branch instructions You can compare directly Equality or inequality of two registers One register with 0 (>,
RISC-V Assembly and Binary Notation
 RISC-V Assembly and Binary Notation L02-1 Course Mechanics Reminders Course website: http://6004.mit.edu All lectures, videos, tutorials, and exam material can be found under Information/Resources tab.
RISC-V Assembly and Binary Notation L02-1 Course Mechanics Reminders Course website: http://6004.mit.edu All lectures, videos, tutorials, and exam material can be found under Information/Resources tab.
Virtual Memory and Interrupts
 Constructive Computer Architecture Virtual Memory and Interrupts Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology November 13, 2015 http://csg.csail.mit.edu/6.175
Constructive Computer Architecture Virtual Memory and Interrupts Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology November 13, 2015 http://csg.csail.mit.edu/6.175
2) Using the same instruction set for the TinyProc2, convert the following hex values to assembly language: x0f
 CS2 Fall 28 Exam 2 Name: ) The Logisim TinyProc2 has four instructions, each using 8 bits. The instruction format is DR SR SR2 OpCode with OpCodes of for add, for subtract, and for multiply. Load Immediate
CS2 Fall 28 Exam 2 Name: ) The Logisim TinyProc2 has four instructions, each using 8 bits. The instruction format is DR SR SR2 OpCode with OpCodes of for add, for subtract, and for multiply. Load Immediate
Operating Systems and Interrupts/Exceptions
 Operating Systems and Interrupts/Exceptions Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology Code for the lecture is available on the course website under the
Operating Systems and Interrupts/Exceptions Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology Code for the lecture is available on the course website under the
 --------------------------------------------------------------------------------------------------------------------- 1. Objectives: Using the Logisim simulator Designing and testing a Pipelined 16-bit
--------------------------------------------------------------------------------------------------------------------- 1. Objectives: Using the Logisim simulator Designing and testing a Pipelined 16-bit
Branch Addressing. Jump Addressing. Target Addressing Example. The University of Adelaide, School of Computer Science 28 September 2015
 Branch Addressing Branch instructions specify Opcode, two registers, target address Most branch targets are near branch Forward or backward op rs rt constant or address 6 bits 5 bits 5 bits 16 bits PC-relative
Branch Addressing Branch instructions specify Opcode, two registers, target address Most branch targets are near branch Forward or backward op rs rt constant or address 6 bits 5 bits 5 bits 16 bits PC-relative
Course Administration
 Fall 2018 EE 3613: Computer Organization Chapter 2: Instruction Set Architecture Introduction 4/4 Avinash Karanth Department of Electrical Engineering & Computer Science Ohio University, Athens, Ohio 45701
Fall 2018 EE 3613: Computer Organization Chapter 2: Instruction Set Architecture Introduction 4/4 Avinash Karanth Department of Electrical Engineering & Computer Science Ohio University, Athens, Ohio 45701
CISC 662 Graduate Computer Architecture. Lecture 4 - ISA
 CISC 662 Graduate Computer Architecture Lecture 4 - ISA Michela Taufer http://www.cis.udel.edu/~taufer/courses Powerpoint Lecture Notes from John Hennessy and David Patterson s: Computer Architecture,
CISC 662 Graduate Computer Architecture Lecture 4 - ISA Michela Taufer http://www.cis.udel.edu/~taufer/courses Powerpoint Lecture Notes from John Hennessy and David Patterson s: Computer Architecture,
Chapter 2A Instructions: Language of the Computer
 Chapter 2A Instructions: Language of the Computer Copyright 2009 Elsevier, Inc. All rights reserved. Instruction Set The repertoire of instructions of a computer Different computers have different instruction
Chapter 2A Instructions: Language of the Computer Copyright 2009 Elsevier, Inc. All rights reserved. Instruction Set The repertoire of instructions of a computer Different computers have different instruction
ENGN1640: Design of Computing Systems Topic 03: Instruction Set Architecture Design
 ENGN1640: Design of Computing Systems Topic 03: Instruction Set Architecture Design Professor Sherief Reda http://scale.engin.brown.edu School of Engineering Brown University Spring 2014 Sources: Computer
ENGN1640: Design of Computing Systems Topic 03: Instruction Set Architecture Design Professor Sherief Reda http://scale.engin.brown.edu School of Engineering Brown University Spring 2014 Sources: Computer
CENG3420 Lecture 03 Review
 CENG3420 Lecture 03 Review Bei Yu byu@cse.cuhk.edu.hk 2017 Spring 1 / 38 CISC vs. RISC Complex Instruction Set Computer (CISC) Lots of instructions of variable size, very memory optimal, typically less
CENG3420 Lecture 03 Review Bei Yu byu@cse.cuhk.edu.hk 2017 Spring 1 / 38 CISC vs. RISC Complex Instruction Set Computer (CISC) Lots of instructions of variable size, very memory optimal, typically less
CISC 662 Graduate Computer Architecture. Lecture 4 - ISA MIPS ISA. In a CPU. (vonneumann) Processor Organization
 CISC 662 Graduate Computer Architecture Lecture 4 - ISA MIPS ISA Michela Taufer http://www.cis.udel.edu/~taufer/courses Powerpoint Lecture Notes from John Hennessy and David Patterson s: Computer Architecture,
CISC 662 Graduate Computer Architecture Lecture 4 - ISA MIPS ISA Michela Taufer http://www.cis.udel.edu/~taufer/courses Powerpoint Lecture Notes from John Hennessy and David Patterson s: Computer Architecture,
MIPS ISA and MIPS Assembly. CS301 Prof. Szajda
 MIPS ISA and MIPS Assembly CS301 Prof. Szajda Administrative HW #2 due Wednesday (9/11) at 5pm Lab #2 due Friday (9/13) 1:30pm Read Appendix B5, B6, B.9 and Chapter 2.5-2.9 (if you have not already done
MIPS ISA and MIPS Assembly CS301 Prof. Szajda Administrative HW #2 due Wednesday (9/11) at 5pm Lab #2 due Friday (9/13) 1:30pm Read Appendix B5, B6, B.9 and Chapter 2.5-2.9 (if you have not already done
MIPS Functions and the Runtime Stack
 MIPS Functions and the Runtime Stack COE 301 Computer Organization Prof. Muhamed Mudawar College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals Presentation Outline
MIPS Functions and the Runtime Stack COE 301 Computer Organization Prof. Muhamed Mudawar College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals Presentation Outline
Multicycle processors. Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology
 Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L14-1 Single-Cycle RISC Processor As an illustrative example, we use a subset of RISC-V
Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L14-1 Single-Cycle RISC Processor As an illustrative example, we use a subset of RISC-V
comp 180 Lecture 10 Outline of Lecture Procedure calls Saving and restoring registers Summary of MIPS instructions
 Outline of Lecture Procedure calls Saving and restoring registers Summary of MIPS instructions Procedure Calls A procedure of a subroutine is like an agent which needs certain information to perform a
Outline of Lecture Procedure calls Saving and restoring registers Summary of MIPS instructions Procedure Calls A procedure of a subroutine is like an agent which needs certain information to perform a
Chapter 2. Computer Abstractions and Technology. Lesson 4: MIPS (cont )
 Chapter 2 Computer Abstractions and Technology Lesson 4: MIPS (cont ) Logical Operations Instructions for bitwise manipulation Operation C Java MIPS Shift left >>> srl Bitwise
Chapter 2 Computer Abstractions and Technology Lesson 4: MIPS (cont ) Logical Operations Instructions for bitwise manipulation Operation C Java MIPS Shift left >>> srl Bitwise
Control Instructions. Computer Organization Architectures for Embedded Computing. Thursday, 26 September Summary
 Control Instructions Computer Organization Architectures for Embedded Computing Thursday, 26 September 2013 Many slides adapted from: Computer Organization and Design, Patterson & Hennessy 4th Edition,
Control Instructions Computer Organization Architectures for Embedded Computing Thursday, 26 September 2013 Many slides adapted from: Computer Organization and Design, Patterson & Hennessy 4th Edition,
Control Instructions
 Control Instructions Tuesday 22 September 15 Many slides adapted from: and Design, Patterson & Hennessy 5th Edition, 2014, MK and from Prof. Mary Jane Irwin, PSU Summary Previous Class Instruction Set
Control Instructions Tuesday 22 September 15 Many slides adapted from: and Design, Patterson & Hennessy 5th Edition, 2014, MK and from Prof. Mary Jane Irwin, PSU Summary Previous Class Instruction Set
Thomas Polzer Institut für Technische Informatik
 Thomas Polzer tpolzer@ecs.tuwien.ac.at Institut für Technische Informatik Branch to a labeled instruction if a condition is true Otherwise, continue sequentially beq rs, rt, L1 if (rs == rt) branch to
Thomas Polzer tpolzer@ecs.tuwien.ac.at Institut für Technische Informatik Branch to a labeled instruction if a condition is true Otherwise, continue sequentially beq rs, rt, L1 if (rs == rt) branch to
ELEC / Computer Architecture and Design Fall 2013 Instruction Set Architecture (Chapter 2)
 ELEC 5200-001/6200-001 Computer Architecture and Design Fall 2013 Instruction Set Architecture (Chapter 2) Victor P. Nelson, Professor & Asst. Chair Vishwani D. Agrawal, James J. Danaher Professor Department
ELEC 5200-001/6200-001 Computer Architecture and Design Fall 2013 Instruction Set Architecture (Chapter 2) Victor P. Nelson, Professor & Asst. Chair Vishwani D. Agrawal, James J. Danaher Professor Department
6.004 Recitation Problems L13 Caches
 6.004 Recitation Problems L13 Caches Keep the most often-used data in a small, fast SRAM (often local to CPU chip). The reason this strategy works: LOCALITY. Temporal locality: If a location has been accessed
6.004 Recitation Problems L13 Caches Keep the most often-used data in a small, fast SRAM (often local to CPU chip). The reason this strategy works: LOCALITY. Temporal locality: If a location has been accessed
EN164: Design of Computing Systems Topic 03: Instruction Set Architecture Design
 EN164: Design of Computing Systems Topic 03: Instruction Set Architecture Design Professor Sherief Reda http://scale.engin.brown.edu Electrical Sciences and Computer Engineering School of Engineering Brown
EN164: Design of Computing Systems Topic 03: Instruction Set Architecture Design Professor Sherief Reda http://scale.engin.brown.edu Electrical Sciences and Computer Engineering School of Engineering Brown
Computer Organization and Components
 2 Course Structure Computer Organization and Components Module 4: Memory Hierarchy Module 1: Logic Design IS1500, fall 2014 Lecture 4: and F1 DC Ö1 F2 DC Ö2 F7b Lab: dicom F8 Module 2: C and Associate
2 Course Structure Computer Organization and Components Module 4: Memory Hierarchy Module 1: Logic Design IS1500, fall 2014 Lecture 4: and F1 DC Ö1 F2 DC Ö2 F7b Lab: dicom F8 Module 2: C and Associate
Chapter 2. Instructions: Language of the Computer. Adapted by Paulo Lopes
 Chapter 2 Instructions: Language of the Computer Adapted by Paulo Lopes Instruction Set The repertoire of instructions of a computer Different computers have different instruction sets But with many aspects
Chapter 2 Instructions: Language of the Computer Adapted by Paulo Lopes Instruction Set The repertoire of instructions of a computer Different computers have different instruction sets But with many aspects
MIPS R-format Instructions. Representing Instructions. Hexadecimal. R-format Example. MIPS I-format Example. MIPS I-format Instructions
 Representing Instructions Instructions are encoded in binary Called machine code MIPS instructions Encoded as 32-bit instruction words Small number of formats encoding operation code (opcode), register
Representing Instructions Instructions are encoded in binary Called machine code MIPS instructions Encoded as 32-bit instruction words Small number of formats encoding operation code (opcode), register
Lecture 2. Instructions: Language of the Computer (Chapter 2 of the textbook)
 Lecture 2 Instructions: Language of the Computer (Chapter 2 of the textbook) Instructions: tell computers what to do Chapter 2 Instructions: Language of the Computer 2 Introduction Chapter 2.1 Chapter
Lecture 2 Instructions: Language of the Computer (Chapter 2 of the textbook) Instructions: tell computers what to do Chapter 2 Instructions: Language of the Computer 2 Introduction Chapter 2.1 Chapter
A Model RISC Processor. DLX Architecture
 DLX Architecture A Model RISC Processor 1 General Features Flat memory model with 32-bit address Data types Integers (32-bit) Floating Point Single precision (32-bit) Double precision (64 bits) Register-register
DLX Architecture A Model RISC Processor 1 General Features Flat memory model with 32-bit address Data types Integers (32-bit) Floating Point Single precision (32-bit) Double precision (64 bits) Register-register
Wawrzynek & Weaver CS 61C. Sp 2018 Great Ideas in Computer Architecture MT 1. Print your name:,
 Wawrzynek & Weaver CS 61C Sp 2018 Great Ideas in Computer Architecture MT 1 Print your name:, (last) (first) I am aware of the Berkeley Campus Code of Student Conduct and acknowledge that any academic
Wawrzynek & Weaver CS 61C Sp 2018 Great Ideas in Computer Architecture MT 1 Print your name:, (last) (first) I am aware of the Berkeley Campus Code of Student Conduct and acknowledge that any academic
MIPS Functions and Instruction Formats
 MIPS Functions and Instruction Formats 1 The Contract: The MIPS Calling Convention You write functions, your compiler writes functions, other compilers write functions And all your functions call other
MIPS Functions and Instruction Formats 1 The Contract: The MIPS Calling Convention You write functions, your compiler writes functions, other compilers write functions And all your functions call other
Multicycle processors. Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology
 Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L12-1 Single-Cycle RISC Processor As an illustrative example, we use a subset of RISC-V
Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L12-1 Single-Cycle RISC Processor As an illustrative example, we use a subset of RISC-V
SPIM Instruction Set
 SPIM Instruction Set This document gives an overview of the more common instructions used in the SPIM simulator. Overview The SPIM simulator implements the full MIPS instruction set, as well as a large
SPIM Instruction Set This document gives an overview of the more common instructions used in the SPIM simulator. Overview The SPIM simulator implements the full MIPS instruction set, as well as a large
Concocting an Instruction Set
 Concocting an Instruction Set Nerd Chef at work. move flour,bowl add milk,bowl add egg,bowl move bowl,mixer rotate mixer... Read: Chapter 2.1-2.7 L03 Instruction Set 1 A General-Purpose Computer The von
Concocting an Instruction Set Nerd Chef at work. move flour,bowl add milk,bowl add egg,bowl move bowl,mixer rotate mixer... Read: Chapter 2.1-2.7 L03 Instruction Set 1 A General-Purpose Computer The von
Wawrzynek & Weaver CS 61C. Sp 2018 Great Ideas in Computer Architecture MT 1. Print your name:,
 Wawrzynek & Weaver CS 61C Sp 2018 Great Ideas in Computer Architecture MT 1 Print your name:, (last) (first) I am aware of the Berkeley Campus Code of Student Conduct and acknowledge that any academic
Wawrzynek & Weaver CS 61C Sp 2018 Great Ideas in Computer Architecture MT 1 Print your name:, (last) (first) I am aware of the Berkeley Campus Code of Student Conduct and acknowledge that any academic
Procedure Call Instructions
 Procedure Calling Steps required 1. Place parameters in registers x10 to x17 2. Transfer control to procedure 3. Acquire storage for procedure 4. Perform procedure s operations 5. Place result in register
Procedure Calling Steps required 1. Place parameters in registers x10 to x17 2. Transfer control to procedure 3. Acquire storage for procedure 4. Perform procedure s operations 5. Place result in register
Chapter 2. Instruction Set. RISC vs. CISC Instruction set. The University of Adelaide, School of Computer Science 18 September 2017
 COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface RISC-V Edition Chapter 2 Instructions: Language of the Computer These slides are based on the slides by the authors. The slides doesn t
COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface RISC-V Edition Chapter 2 Instructions: Language of the Computer These slides are based on the slides by the authors. The slides doesn t
Examples of IO, Interrupts, and Exceptions
 Examples of IO, Interrupts, and Exceptions Andy Wright, Thomas Bourgeat, Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L15-1 Keyboard Input
Examples of IO, Interrupts, and Exceptions Andy Wright, Thomas Bourgeat, Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L15-1 Keyboard Input
Lecture 2: RISC V Instruction Set Architecture. Housekeeping
 S 17 L2 1 18 447 Lecture 2: RISC V Instruction Set Architecture James C. Hoe Department of ECE Carnegie Mellon University Housekeeping S 17 L2 2 Your goal today get bootstrapped on RISC V RV32I to start
S 17 L2 1 18 447 Lecture 2: RISC V Instruction Set Architecture James C. Hoe Department of ECE Carnegie Mellon University Housekeeping S 17 L2 2 Your goal today get bootstrapped on RISC V RV32I to start
Computer Organization MIPS ISA
 CPE 335 Computer Organization MIPS ISA Dr. Iyad Jafar Adapted from Dr. Gheith Abandah Slides http://www.abandah.com/gheith/courses/cpe335_s08/index.html CPE 232 MIPS ISA 1 (vonneumann) Processor Organization
CPE 335 Computer Organization MIPS ISA Dr. Iyad Jafar Adapted from Dr. Gheith Abandah Slides http://www.abandah.com/gheith/courses/cpe335_s08/index.html CPE 232 MIPS ISA 1 (vonneumann) Processor Organization
A General-Purpose Computer The von Neumann Model. Concocting an Instruction Set. Meaning of an Instruction. Anatomy of an Instruction
 page 1 Concocting an Instruction Set Nerd Chef at work. move flour,bowl add milk,bowl add egg,bowl move bowl,mixer rotate mixer... A General-Purpose Computer The von Neumann Model Many architectural approaches
page 1 Concocting an Instruction Set Nerd Chef at work. move flour,bowl add milk,bowl add egg,bowl move bowl,mixer rotate mixer... A General-Purpose Computer The von Neumann Model Many architectural approaches
EEC 581 Computer Architecture Lecture 1 Review MIPS
 EEC 581 Computer Architecture Lecture 1 Review MIPS 1 Supercomputing: Suddenly Fancy 2 1 Instructions: Language of the Machine More primitive than higher level languages e.g., no sophisticated control
EEC 581 Computer Architecture Lecture 1 Review MIPS 1 Supercomputing: Suddenly Fancy 2 1 Instructions: Language of the Machine More primitive than higher level languages e.g., no sophisticated control
Lecture 2: RISC V Instruction Set Architecture. James C. Hoe Department of ECE Carnegie Mellon University
 18 447 Lecture 2: RISC V Instruction Set Architecture James C. Hoe Department of ECE Carnegie Mellon University 18 447 S18 L02 S1, James C. Hoe, CMU/ECE/CALCM, 2018 Your goal today Housekeeping get bootstrapped
18 447 Lecture 2: RISC V Instruction Set Architecture James C. Hoe Department of ECE Carnegie Mellon University 18 447 S18 L02 S1, James C. Hoe, CMU/ECE/CALCM, 2018 Your goal today Housekeeping get bootstrapped
Computer Architecture. The Language of the Machine
 Computer Architecture The Language of the Machine Instruction Sets Basic ISA Classes, Addressing, Format Administrative Matters Operations, Branching, Calling conventions Break Organization All computers
Computer Architecture The Language of the Machine Instruction Sets Basic ISA Classes, Addressing, Format Administrative Matters Operations, Branching, Calling conventions Break Organization All computers
Computer Science and Engineering 331. Midterm Examination #1. Fall Name: Solutions S.S.#:
 Computer Science and Engineering 331 Midterm Examination #1 Fall 2000 Name: Solutions S.S.#: 1 41 2 13 3 18 4 28 Total 100 Instructions: This exam contains 4 questions. It is closed book and notes. Calculators
Computer Science and Engineering 331 Midterm Examination #1 Fall 2000 Name: Solutions S.S.#: 1 41 2 13 3 18 4 28 Total 100 Instructions: This exam contains 4 questions. It is closed book and notes. Calculators
MIPS Instruction Set Architecture (2)
 MIPS Instruction Set Architecture (2) Jinkyu Jeong (jinkyu@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu EEE3050: Theory on Computer Architectures, Spring 2017, Jinkyu
MIPS Instruction Set Architecture (2) Jinkyu Jeong (jinkyu@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu EEE3050: Theory on Computer Architectures, Spring 2017, Jinkyu
Instruction Set Architecture part 1 (Introduction) Mehran Rezaei
 Instruction Set Architecture part 1 (Introduction) Mehran Rezaei Overview Last Lecture s Review Execution Cycle Levels of Computer Languages Stored Program Computer/Instruction Execution Cycle SPIM, a
Instruction Set Architecture part 1 (Introduction) Mehran Rezaei Overview Last Lecture s Review Execution Cycle Levels of Computer Languages Stored Program Computer/Instruction Execution Cycle SPIM, a
CS 351 Exam 2 Mon. 11/2/2015
 CS 351 Exam 2 Mon. 11/2/2015 Name: Rules and Hints The MIPS cheat sheet and datapath diagram are attached at the end of this exam for your reference. You may use one handwritten 8.5 11 cheat sheet (front
CS 351 Exam 2 Mon. 11/2/2015 Name: Rules and Hints The MIPS cheat sheet and datapath diagram are attached at the end of this exam for your reference. You may use one handwritten 8.5 11 cheat sheet (front
Course Administration
 Fall 2017 EE 3613: Computer Organization Chapter 2: Instruction Set Architecture 2/4 Avinash Kodi Department of Electrical Engineering & Computer Science Ohio University, Athens, Ohio 45701 E-mail: kodi@ohio.edu
Fall 2017 EE 3613: Computer Organization Chapter 2: Instruction Set Architecture 2/4 Avinash Kodi Department of Electrical Engineering & Computer Science Ohio University, Athens, Ohio 45701 E-mail: kodi@ohio.edu
Computer System Architecture Quiz #1 March 8th, 2019
 Computer System Architecture 6.823 Quiz #1 March 8th, 2019 Name: This is a closed book, closed notes exam. 80 Minutes 14 Pages (+2 Scratch) Notes: Not all questions are of equal difficulty, so look over
Computer System Architecture 6.823 Quiz #1 March 8th, 2019 Name: This is a closed book, closed notes exam. 80 Minutes 14 Pages (+2 Scratch) Notes: Not all questions are of equal difficulty, so look over
Overview. Introduction to the MIPS ISA. MIPS ISA Overview. Overview (2)
 Introduction to the MIPS ISA Overview Remember that the machine only understands very basic instructions (machine instructions) It is the compiler s job to translate your high-level (e.g. C program) into
Introduction to the MIPS ISA Overview Remember that the machine only understands very basic instructions (machine instructions) It is the compiler s job to translate your high-level (e.g. C program) into
8*4 + 4 = 36 each int is 4 bytes
 CS 61CL (Clancy) Solutions and grading standards for exam 1 Spring 2009 169 students took the exam. The average score was 43.6; the median was 46. Scores ranged from 1 to 59. There were 89 scores between
CS 61CL (Clancy) Solutions and grading standards for exam 1 Spring 2009 169 students took the exam. The average score was 43.6; the median was 46. Scores ranged from 1 to 59. There were 89 scores between
Instruction Set Architectures Part I: From C to MIPS. Readings:
 Instruction Set Architectures Part I: From C to MIPS Readings: 2.1-2.14 1 Goals for this Class Understand how CPUs run programs How do we express the computation the CPU? How does the CPU execute it? How
Instruction Set Architectures Part I: From C to MIPS Readings: 2.1-2.14 1 Goals for this Class Understand how CPUs run programs How do we express the computation the CPU? How does the CPU execute it? How
COMPSCI 313 S Computer Organization. 7 MIPS Instruction Set
 COMPSCI 313 S2 2018 Computer Organization 7 MIPS Instruction Set Agenda & Reading MIPS instruction set MIPS I-format instructions MIPS R-format instructions 2 7.1 MIPS Instruction Set MIPS Instruction
COMPSCI 313 S2 2018 Computer Organization 7 MIPS Instruction Set Agenda & Reading MIPS instruction set MIPS I-format instructions MIPS R-format instructions 2 7.1 MIPS Instruction Set MIPS Instruction
Concocting an Instruction Set
 Concocting an Instruction Set Nerd Chef at work. move flour,bowl add milk,bowl add egg,bowl move bowl,mixer rotate mixer... Lab is posted. Do your prelab! Stay tuned for the first problem set. L04 Instruction
Concocting an Instruction Set Nerd Chef at work. move flour,bowl add milk,bowl add egg,bowl move bowl,mixer rotate mixer... Lab is posted. Do your prelab! Stay tuned for the first problem set. L04 Instruction
COMPUTER ORGANIZATION AND DESIGN
 COMPUTER ORGANIZATION AND DESIGN 5 th The Hardware/Software Interface Edition Chapter 2 Instructions: Language of the Computer 2.1 Introduction Instruction Set The repertoire of instructions of a computer
COMPUTER ORGANIZATION AND DESIGN 5 th The Hardware/Software Interface Edition Chapter 2 Instructions: Language of the Computer 2.1 Introduction Instruction Set The repertoire of instructions of a computer
Assembler. Lecture 8 CS301
 Assembler Lecture 8 CS301 Discussion Given the following function header, int foo(int a, int b); what will be on the stack before any of the calculations in foo are performed? Assume foo() calls some other
Assembler Lecture 8 CS301 Discussion Given the following function header, int foo(int a, int b); what will be on the stack before any of the calculations in foo are performed? Assume foo() calls some other
CS 61c: Great Ideas in Computer Architecture
 MIPS Instruction Formats July 2, 2014 Review New registers: $a0-$a3, $v0-$v1, $ra, $sp New instructions: slt, la, li, jal, jr Saved registers: $s0-$s7, $sp, $ra Volatile registers: $t0-$t9, $v0-$v1, $a0-$a3
MIPS Instruction Formats July 2, 2014 Review New registers: $a0-$a3, $v0-$v1, $ra, $sp New instructions: slt, la, li, jal, jr Saved registers: $s0-$s7, $sp, $ra Volatile registers: $t0-$t9, $v0-$v1, $a0-$a3
Computer System Architecture Midterm Examination Spring 2002
 Computer System Architecture 6.823 Midterm Examination Spring 2002 Name: This is an open book, open notes exam. 110 Minutes 1 Pages Notes: Not all questions are of equal difficulty, so look over the entire
Computer System Architecture 6.823 Midterm Examination Spring 2002 Name: This is an open book, open notes exam. 110 Minutes 1 Pages Notes: Not all questions are of equal difficulty, so look over the entire
Concocting an Instruction Set
 Concocting an Instruction Set Nerd Chef at work. move flour,bowl add milk,bowl add egg,bowl move bowl,mixer rotate mixer... Read: Chapter 2.1-2.6 L04 Instruction Set 1 A General-Purpose Computer The von
Concocting an Instruction Set Nerd Chef at work. move flour,bowl add milk,bowl add egg,bowl move bowl,mixer rotate mixer... Read: Chapter 2.1-2.6 L04 Instruction Set 1 A General-Purpose Computer The von
Instructions: MIPS ISA. Chapter 2 Instructions: Language of the Computer 1
 Instructions: MIPS ISA Chapter 2 Instructions: Language of the Computer 1 PH Chapter 2 Pt A Instructions: MIPS ISA Based on Text: Patterson Henessey Publisher: Morgan Kaufmann Edited by Y.K. Malaiya for
Instructions: MIPS ISA Chapter 2 Instructions: Language of the Computer 1 PH Chapter 2 Pt A Instructions: MIPS ISA Based on Text: Patterson Henessey Publisher: Morgan Kaufmann Edited by Y.K. Malaiya for
ICS DEPARTMENT ICS 233 COMPUTER ARCHITECTURE & ASSEMBLY LANGUAGE. Midterm Exam. First Semester (141) Time: 1:00-3:30 PM. Student Name : _KEY
 Page 1 of 14 Nov. 22, 2014 ICS DEPARTMENT ICS 233 COMPUTER ARCHITECTURE & ASSEMBLY LANGUAGE Midterm Exam First Semester (141) Time: 1:00-3:30 PM Student Name : _KEY Student ID. : Question Max Points Score
Page 1 of 14 Nov. 22, 2014 ICS DEPARTMENT ICS 233 COMPUTER ARCHITECTURE & ASSEMBLY LANGUAGE Midterm Exam First Semester (141) Time: 1:00-3:30 PM Student Name : _KEY Student ID. : Question Max Points Score
CS 61C: Great Ideas in Computer Architecture RISC-V Instruction Formats
 CS 61C: Great Ideas in Computer Architecture RISC-V Instruction Formats Instructors: Krste Asanović and Randy H. Katz http://inst.eecs.berkeley.edu/~cs61c/fa17 9/14/17 Fall 2017 - Lecture #7 1 Levels of
CS 61C: Great Ideas in Computer Architecture RISC-V Instruction Formats Instructors: Krste Asanović and Randy H. Katz http://inst.eecs.berkeley.edu/~cs61c/fa17 9/14/17 Fall 2017 - Lecture #7 1 Levels of
9/14/17. Levels of Representation/Interpretation. Big Idea: Stored-Program Computer
 CS 61C: Great Ideas in Computer Architecture RISC-V Instruction Formats Instructors: Krste Asanović and Randy H. Katz http://inst.eecs.berkeley.edu/~cs61c/fa17 Fall 2017 - Lecture #7 1 Levels of Representation/Interpretation
CS 61C: Great Ideas in Computer Architecture RISC-V Instruction Formats Instructors: Krste Asanović and Randy H. Katz http://inst.eecs.berkeley.edu/~cs61c/fa17 Fall 2017 - Lecture #7 1 Levels of Representation/Interpretation
Computer Hardware Engineering
 2 Course Structure Computer Hardware ngineering IS1200, spring 2015 Lecture 3: Languages Module 4: I/O Systems Module 1: Logic Design L DCÖ1 L DCÖ2 Lab:dicom L7 Module 2: C and Assembly Programming Associate
2 Course Structure Computer Hardware ngineering IS1200, spring 2015 Lecture 3: Languages Module 4: I/O Systems Module 1: Logic Design L DCÖ1 L DCÖ2 Lab:dicom L7 Module 2: C and Assembly Programming Associate
CSc 256 Midterm (green) Fall 2018
 CSc 256 Midterm (green) Fall 2018 NAME: Problem 1 (5 points): Suppose we are tracing a C/C++ program using a debugger such as gdb. The code showing all function calls looks like this: main() { bat(5);
CSc 256 Midterm (green) Fall 2018 NAME: Problem 1 (5 points): Suppose we are tracing a C/C++ program using a debugger such as gdb. The code showing all function calls looks like this: main() { bat(5);
Computer Architecture
 CS3350B Computer Architecture Winter 2015 Lecture 4.2: MIPS ISA -- Instruction Representation Marc Moreno Maza www.csd.uwo.ca/courses/cs3350b [Adapted from lectures on Computer Organization and Design,
CS3350B Computer Architecture Winter 2015 Lecture 4.2: MIPS ISA -- Instruction Representation Marc Moreno Maza www.csd.uwo.ca/courses/cs3350b [Adapted from lectures on Computer Organization and Design,
Concocting an Instruction Set
 Concocting an Instruction Set Nerd Chef at work. move flour,bowl add milk,bowl add egg,bowl move bowl,mixer rotate mixer... Read: Chapter 2.1-2.7 L04 Instruction Set 1 A General-Purpose Computer The von
Concocting an Instruction Set Nerd Chef at work. move flour,bowl add milk,bowl add egg,bowl move bowl,mixer rotate mixer... Read: Chapter 2.1-2.7 L04 Instruction Set 1 A General-Purpose Computer The von
EN164: Design of Computing Systems Lecture 11: Processor / ISA 4
 EN164: Design of Computing Systems Lecture 11: Processor / ISA 4 Professor Sherief Reda http://scale.engin.brown.edu Electrical Sciences and Computer Engineering School of Engineering Brown University
EN164: Design of Computing Systems Lecture 11: Processor / ISA 4 Professor Sherief Reda http://scale.engin.brown.edu Electrical Sciences and Computer Engineering School of Engineering Brown University
Introduction to the MIPS. Lecture for CPSC 5155 Edward Bosworth, Ph.D. Computer Science Department Columbus State University
 Introduction to the MIPS Lecture for CPSC 5155 Edward Bosworth, Ph.D. Computer Science Department Columbus State University Introduction to the MIPS The Microprocessor without Interlocked Pipeline Stages
Introduction to the MIPS Lecture for CPSC 5155 Edward Bosworth, Ph.D. Computer Science Department Columbus State University Introduction to the MIPS The Microprocessor without Interlocked Pipeline Stages
Machine Language Instructions Introduction. Instructions Words of a language understood by machine. Instruction set Vocabulary of the machine
 Machine Language Instructions Introduction Instructions Words of a language understood by machine Instruction set Vocabulary of the machine Current goal: to relate a high level language to instruction
Machine Language Instructions Introduction Instructions Words of a language understood by machine Instruction set Vocabulary of the machine Current goal: to relate a high level language to instruction
CS 4200/5200 Computer Architecture I
 CS 4200/5200 Computer Architecture I MIPS Instruction Set Architecture Dr. Xiaobo Zhou Department of Computer Science CS420/520 Lec3.1 UC. Colorado Springs Adapted from UCB97 & UCB03 Review: Organizational
CS 4200/5200 Computer Architecture I MIPS Instruction Set Architecture Dr. Xiaobo Zhou Department of Computer Science CS420/520 Lec3.1 UC. Colorado Springs Adapted from UCB97 & UCB03 Review: Organizational
Anne Bracy CS 3410 Computer Science Cornell University. See P&H Chapter: , , Appendix B
 Anne Bracy CS 3410 Computer Science Cornell University The slides are the product of many rounds of teaching CS 3410 by Professors Weatherspoon, Bala, Bracy, and Sirer. See P&H Chapter: 2.16-2.20, 4.1-4.4,
Anne Bracy CS 3410 Computer Science Cornell University The slides are the product of many rounds of teaching CS 3410 by Professors Weatherspoon, Bala, Bracy, and Sirer. See P&H Chapter: 2.16-2.20, 4.1-4.4,
Instruction Set Architecture
 Computer Architecture Instruction Set Architecture Lynn Choi Korea University Machine Language Programming language High-level programming languages Procedural languages: C, PASCAL, FORTRAN Object-oriented
Computer Architecture Instruction Set Architecture Lynn Choi Korea University Machine Language Programming language High-level programming languages Procedural languages: C, PASCAL, FORTRAN Object-oriented
Computer Organization and Structure. Bing-Yu Chen National Taiwan University
 Computer Organization and Structure Bing-Yu Chen National Taiwan University Instructions: Language of the Computer Operations and Operands of the Computer Hardware Signed and Unsigned Numbers Representing
Computer Organization and Structure Bing-Yu Chen National Taiwan University Instructions: Language of the Computer Operations and Operands of the Computer Hardware Signed and Unsigned Numbers Representing
MIPS Assembly Language. Today s Lecture
 MIPS Assembly Language Computer Science 104 Lecture 6 Homework #2 Midterm I Feb 22 (in class closed book) Outline Assembly Programming Reading Chapter 2, Appendix B Today s Lecture 2 Review: A Program
MIPS Assembly Language Computer Science 104 Lecture 6 Homework #2 Midterm I Feb 22 (in class closed book) Outline Assembly Programming Reading Chapter 2, Appendix B Today s Lecture 2 Review: A Program
