1 GB IO INTRODUCTION 1
|
|
|
- Theodora George
- 5 years ago
- Views:
Transcription
1 1 GB IO INTRODUCTION 1 1. Introduction. This is GB IO, the input/output module used by all GraphBase routines to access data files. It doesn t actually do any output; but somehow input/output sounds like a more useful title than just input. All files of GraphBase data are designed to produce identical results on almost all existing computers and operating systems. Each line of each file contains at most 79 characters. Each character is either a blank or a digit or an uppercase letter or a lowercase letter or a standard punctuation mark. Blank characters at the end of each line are invisible ; that is, they have no perceivable effect. Hence identical results will be obtained on record-oriented systems that pad every line with blanks. The data is carefully sum-checked so that defective input files have little chance of being accepted. 2. Changes might be needed when these routines are ported to different systems. Sections of the program that are most likely to require such changes are listed under system dependencies in the index. A validation program is provided so that installers can tell if GB IO is working properly. To make the test, simply run test_io. test_io.c 2 #include "gb_io.h" / all users of GB IO should include this header file / #define exit test (m) / we invoke this macro if something goes wrong / fprintf (stderr, "%s!\n(error code = %ld)\n",m,io errors ); return 1; int main () Test the gb open routine; exit if there s trouble 28 ; Test the sample data lines; exit if there s trouble 27 ; Test the gb close routine; exit if there s trouble 38 ; printf ("OK, the gb_io routines seem to work!\n"); return 0; 3. The external variable io errors mentioned in the previous section will be set nonzero if any anomalies are detected. Errors won t occur in normal use of GraphBase programs, so no attempt has been made to provide a user-friendly way to decode the nonzero values that io errors might assume. Information is simply gathered in binary form; system wizards who might need to do a bit of troubleshooting should be able to decode io errors without great pain. #define cant open file # 1 / bit set in io errors if fopen fails / #define cant close file # 2 / bit set if fclose fails / #define bad first line # 4 / bit set if the data file s first line isn t legit / #define bad second line # 8 / bit set if the second line doesn t pass muster / #define bad third line # 10 / bit set if the third line is awry / #define bad fourth line # 20 / guess when this bit is set / #define file ended prematurely # 40 / bit set if fgets fails / #define missing newline # 80 / bit set if line is too long or \n is missing / #define wrong number of lines # 100 / bit set if the line count is wrong / #define wrong checksum # 200 / bit set if the check sum is wrong / #define no file open # 400 / bit set if user tries to close an unopened file / #define bad last line # 800 / bit set if final line has incorrect form /
2 2 INTRODUCTION GB IO 4 4. The C code for GB IO doesn t have a main routine; it s just a bunch of subroutines to be incorporated into programs at a higher level via the system loading routine. Here is the general outline of gb_io.c: Header files to include 7 Preprocessor definitions External declarations 5 Private declarations 8 Internal functions 9 External functions Every external variable is declared twice in this CWEB file: once for GB IO itself (the real declaration for storage allocation purposes) and once in gb_io.h (for cross-references by GB IO users). External declarations 5 long io errors ; / record of anomalies noted by GB IO routines / This code is used in section gb_io.h 6 Header files to include 7 extern long io errors ; / record of anomalies noted by GB IO routines / See also sections 13, 16, 19, 21, 23, 25, 29, and We will stick to standard C-type input conventions. We ll also have occasion to use some of the standard string operations. Header files to include 7 #include <stdio.h> #ifdef SYSV #include <string.h> #else #include <strings.h> #endif This code is used in sections 4 and 6.
3 8 GB IO INPUTTING A LINE 3 8. Inputting a line. The GB IO routines get their input from an array called buffer. This array is internal to GB IO its contents are hidden from user programs. We make it 81 characters long, since the data is supposed to have at most 79 characters per line, followed by newline and null. Private declarations 8 static char buffer [81]; / the current line of input / static char cur pos = buffer ; / the current character of interest / static FILE cur file ; / current file, or Λ is none is open / See also sections 10, 11, and 33. This code is used in section Here s a basic subroutine to fill the buffer. The main feature of interest is the removal of trailing blanks. We assume that cur file is open. Notice that a line of 79 characters (followed by \n ) will just fit into the buffer, and will cause no errors. A line of 80 characters will be split into two lines and the missing newline message will occur, because of the way fgets is defined. A missing newline error will also occur if the file ends in the middle of a line, or if a null character ( \0 ) occurs within a line. Internal functions 9 static void fill buf () register char p; if ( fgets (buffer, 81, cur file)) io errors = file ended prematurely ; buffer [0] = more data =0; for (p = buffer ; p; p++); / advance to first null character / if (p buffer p \n ) io errors = missing newline ; p++; while ( p buffer p ) ; / move back over trailing blanks / ++p = \n ; ++p =0; / newline and null are always present at end of line / cur pos = buffer ; / get ready to read buffer [0] / See also section 15. This code is used in section 4.
4 4 CHECKSUMS GB IO Checksums. Each data file has a magic number, which is defined to be ( ) 2 l c l mod p. l Here p is a large prime number, and c l denotes the internal code corresponding to the lth-from-last data character read (including newlines but not nulls). The internal codes c l are computed in a system-independent way: Each character c in the actual encoding scheme being used has a corresponding icode, which is the same on all systems. For example, the icode of 0 is zero, regardless of whether 0 is actually represented in ASCII or EBCDIC or some other scheme. (We assume that every modern computer system is capable of printing at least 95 different characters, including a blank space.) We will accept a data file as error-free if it has the correct number of lines and ends with the proper magic number. Private declarations 8 + static char icode [256]; / mapping of characters to internal codes / static long checksum prime =(1 L 30) 83; / large prime such that 2p won t overflow / static long magic; / current checksum value / static long line no; / current line number in file / static long final magic; / desired final magic number / static long tot lines ; / total number of data lines / static char more data ; / is there data still waiting to be read? / 11. The icode mapping is defined by a single string, imap, such that character imap [k] hasicode value k. There are 96 characters in imap, namely the 94 standard visible ASCII codes plus space and newline. If EBCDIC code is used instead of ASCII, the cents sign /c should take the place of single-left-quote, and should take the place of ~. All characters that don t appear in imap are given the same icode value, called unexpected char. Such characters should be avoided in GraphBase files whenever possible. (If they do appear, they can still get into a user s data, but we don t distinguish them from each other for checksumming purposes.) The icode table actually plays a dual role, because we ve rigged it so that codes 0 15 come from the characters " ABCDEF". This facilitates conversion of decimal and hexadecimal data. We can also use it for radices higher than 16. #define unexpected char 127 / default icode value / Private declarations 8 + static char imap = " ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvw\ xyz_^~&@,;.:?!%#$+ */ \\<=>()[] \" \n";
5 12 GB IO CHECKSUMS Users of GB IO can look at the imap, but they can t change it. External functions 12 char imap chr (d) long d; return d<0 d>strlen (imap )? \0 : imap [d]; long imap ord (c) char c; Make sure that icode has been initialized 14 ; return (c <0 c>255)? unexpected char : icode [c]; See also sections 17, 18, 20, 22, 24, 26, 30, 32, 39, and 42. This code is used in section gb_io.h 6 + #define unexpected char 127 extern char imap chr (); / the character that maps to a given character / extern long imap ord (); / the ordinal number of a given character / 14. Make sure that icode has been initialized 14 if ( icode [ 1 ]) icode setup(); This code is used in sections 12 and Internal functions 9 + static void icode setup() register long k; register char p; for (k =0; k < 256; k++) icode [k] =unexpected char ; for (p = imap,k = 0; p; p++,k++) icode [ p] = k; 16. Now we re ready to specify some external subroutines that do input. Calling gb newline ( ) will read thenextlineofdataintobuffer and update the magic number accordingly. gb_io.h 6 + extern void gb newline (); / advance to next line of the data file / extern long new checksum (); / compute change in magic number / 17. Users can compute checksums as gb newline does, but they can t change the (private) value of magic. External functions 12 + long new checksum (s, old checksum ) char s; / astring / long old checksum; register long a = old checksum ; register char p; for (p = s; p; p++) a =(a + a + icode [ p]) % checksum prime ; return a;
6 6 CHECKSUMS GB IO The magic checksum is not affected by lines that begin with *. External functions 12 + void gb newline () if (++line no > tot lines ) more data =0; if (more data ) fill buf (); if (buffer [0] * ) magic = new checksum (buffer, magic); 19. Another simple routine allows a user to read (but not write) the variable more data. gb_io.h 6 + extern long gb eof (); / has the data all been read? / 20. External functions 12 + long gb eof () return more data ;
7 21 GB IO PARSING A LINE Parsing a line. The user can input characters from the buffer in several ways. First, there s a basic gb char ( ) routine, which returns a single character. The character is \n if the last character on the line has already been read (and it continues to be \n until the user calls gb newline ). The current position in the line, cur pos, always advances when gb char is called, unless cur pos was already at the end of the line. There s also a gb backup( ) routine, which moves cur pos one place to the left unless it was already at the beginning. gb_io.h 6 + extern char gb char (); / get next character of current line, or \n / extern void gb backup (); / move back ready to scan a character again / 22. External functions 12 + char gb char () if ( cur pos ) return ( cur pos ++); return \n ; void gb backup () if (cur pos > buffer ) cur pos ; 23. There are two ways to read numerical data. The first, gb digit (d), expects to read a single character in radix d, usingicode values to specify digits greater than 9. (Thus, for example, A represents the hexadecimal digit for decimal 10.) If the next character is a valid d-git, cur pos moves to the next character and the numerical value is returned. Otherwise cur pos stays in the same place and 1 is returned. The second routine, gb number (d), reads characters and forms an unsigned radix-d number until the first non-digit is encountered. The resulting number is returned; it is zero if no digits were found. No errors are possible with this routine, because it uses unsigned long arithmetic. gb_io.h 6 + extern long gb digit (); / gb digit (d) reads a digit between 0 and d 1 / extern unsigned long gb number (); / gb number (d) readsaradix-dnumber / 24. The value of d should be at most 127, if users want their programs to be portable, because C does not treat larger char values in a well-defined manner. In most applications, d is of course either 10 or 16. External functions 12 + long gb digit (d) char d; if (icode [ cur pos ] <d) return icode [ cur pos ++]; return 1; unsigned long gb number (d) char d; register unsigned long a =0; icode [0] = d; / make sure \0 is a nondigit / while (icode [ cur pos ] <d) a = a d + icode [ cur pos ++]; return a;
8 8 PARSING A LINE GB IO The final subroutine for fetching data is gb string (p, c), which stores a null-terminated string into locations starting at p. The string starts at cur pos and ends just before the first appearance of character c. If c \n, the string will stop at the end of the line. If c doesn t appear in the buffer at or after cur pos, the last character of the string will be the \n that is always inserted at the end of a line, unless the entire line has already been read. (If the entire line has previously been read, the empty string is always returned.) After the string has been copied, cur pos advances past it. In order to use this routine safely, the user should first check that there is room to store up to 81 characters beginning at location p. A suitable place to put the result, called str buf,isprovidedforthe user s convenience. The location following the stored string is returned. Thus, if the stored string has length l (not counting the null character that is stored at the end), the value returned will be p + l +1. gb_io.h 6 + #define STR_BUF_LENGTH 160 extern char str buf []; / safe place to receive output of gb string / extern char gb string (); / gb string (p, c) reads a string delimited by c into bytes starting at p / 26. #define STR_BUF_LENGTH 160 External functions 12 + char str buf [STR_BUF_LENGTH]; / users can put strings here if they wish / char gb string (p, c) char p; / where to put the result / char c; / character following the string / while ( cur pos cur pos c) p++ = cur pos ++; p++ =0; return p;
9 27 GB IO PARSING A LINE Here s how we test those routines in test_io: The first line of test data consists of 79 characters, beginning with 64 zeroes and ending with ABCDEF. The second line is completely blank. The third and final line says Oops:(intentional mistake). Test the sample data lines; exit if there s trouble 27 if (gb number (10) ) io errors = 1 L 20; / decimal number not working / if (gb digit (16) 10) io errors = 1 L 21; / we missed the A following the decimal number / gb backup(); gb backup(); / get set to read 9A again / if (gb number (16) # 9ABCDEF) io errors = 1 L 22; / hexadecimal number not working / gb newline (); / now we should be scanning a blank line / if (gb char () \n ) io errors = 1 L 23; / newline not inserted at end / if (gb char () \n ) io errors = 1 L 24; / newline not implied after end / if (gb number (60) 0) io errors = 1 L 25; / number should stop at null character / char temp[100]; if (gb string (temp, \n ) temp +1) io errors = 1 L 26; / string should be null after end of line / gb newline (); if (gb string (temp, : ) temp +5 strcmp(temp, "Oops")) io errors = 1 L 27; / string not read properly / if (io errors ) exit test ("Sorry, it failed. Look at the error code for clues"); if (gb digit (10) 1) exit test ("Digit error not detected"); if (gb char () : ) io errors = 1 L 28; / lost synch after gb string and gb digit / if (gb eof ()) io errors = 1 L 29; / premature end-of-file indication / gb newline (); if ( gb eof ()) io errors = 1 L 30; / postmature end-of-file indication / This code is used in section 2.
10 10 OPENING A FILE GB IO Opening a file. The call gb raw open ("foo") will open file "foo" and initialize the checksumming process. If the file cannot be opened, io errors will be set to cant open file, otherwiseio errors will be initialized to zero. The call gb open ("foo") is a stronger version of gb raw open, which is used for standard GraphBase data files like "words.dat" to make doubly sure that they have not been corrupted. It returns the current value of io errors, which will be nonzero if any problems were detected at the beginning of the file. Test the gb open routine; exit if there s trouble 28 if (gb open ("test.dat") 0) exit test ("Can t open test.dat"); This code is used in section #define gb raw open gb r open / abbreviation for Procrustean external linkage / gb_io.h 6 + #define gb raw open gb r open extern void gb raw open (); / open a file for GraphBase input / extern long gb open (); / open a GraphBase data file; return 0 if OK / 30. External functions 12 + void gb raw open (f) char f; Make sure that icode has been initialized 14 ; Try to open f 31 ; if (cur file) io errors =0; more data =1; line no = magic =0; tot lines = # 7fffffff; / allow infinitely many lines / fill buf (); else io errors = cant open file; 31. Here s a possibly system-dependent part of the code: We try first to open the data file by using the file name itself as the path name; failing that, we try to prefix the file name with the name of the standard directory for GraphBase data, if the program has been compiled with DATA_DIRECTORY defined. Try to open f 31 cur file = fopen (f,"r"); #ifdef DATA_DIRECTORY if ( cur file (strlen (DATA_DIRECTORY)+strlen (f) < STR_BUF_LENGTH)) sprintf (str buf, "%s%s", DATA_DIRECTORY,f); cur file = fopen (str buf, "r"); #endif DATA_DIRECTORY This code is used in section 30.
11 32 GB IO OPENING A FILE External functions 12 + long gb open (f) char f; strncpy (file name,f,19); / save the name for use by gb close / gb raw open (f); if (cur file) Check the first line; return if unsuccessful 34 ; Check the second line; return if unsuccessful 35 ; Check the third line; return if unsuccessful 36 ; Check the fourth line; return if unsuccessful 37 ; gb newline (); / the first line of real data is now in the buffer / return io errors ; 33. Private declarations 8 + static char file name [20]; / name of the data file, without a prefix / 34. The first four lines of a typical data file should look something like this: * File "words.dat" from the Stanford GraphBase (C) 1993 Stanford University * A database of English 5 letter words * This file may be freely copied but please do not change it in any way! * (Checksum parameters 5757, ) We actually verify only that the first four lines of a data file named "foo" begin respectively with the characters * File "foo" * * * (Checksum parameters l, m) where l and m are decimal numbers. The values of l and m are stored away as tot lines and final magic, to be matched at the end of the file. Check the first line; return if unsuccessful 34 sprintf (str buf, "* File \"%s\"",f); if (strncmp(buffer, str buf, strlen (str buf ))) return (io errors = bad first line ); This code is used in section Check the second line; return if unsuccessful 35 fill buf (); if ( buffer * ) return (io errors = bad second line ); This code is used in section Check the third line; return if unsuccessful 36 fill buf (); if ( buffer * ) return (io errors = bad third line ); This code is used in section 32.
12 12 OPENING A FILE GB IO Check the fourth line; return if unsuccessful 37 fill buf (); if (strncmp(buffer, "* (Checksum parameters ", 23)) return (io errors = bad fourth line ); cur pos += 23; tot lines = gb number (10); if (gb char (), ) return (io errors = bad fourth line ); final magic = gb number (10); if (gb char () ) ) return (io errors = bad fourth line ); This code is used in section 32.
13 38 GB IO CLOSING A FILE Closing a file. After all data has been input, or should have been input, we check that the file was open and that it had the correct number of lines, the correct magic number, and a correct final line. The subroutine gb close, like gb open, returns the value of io errors, which will be nonzero if at least one problem was noticed. Test the gb close routine; exit if there s trouble 38 if (gb close () 0) exit test ("Bad checksum, or difficulty closing the file"); This code is used in section External functions 12 + long gb close () if ( cur file ) return (io errors = no file open ); fill buf (); sprintf (str buf, "* End of file \"%s\"", file name ); if (strncmp(buffer, str buf, strlen (str buf ))) io errors = bad last line ; more data = buffer [0] = 0; / now the GB IO routines are effectively shut down / / we have cur pos = buffer / if (fclose (cur file ) 0) return (io errors = cant close file); cur file =Λ; if (line no tot lines +1) return (io errors = wrong number of lines ); if (magic final magic) return (io errors = wrong checksum); return io errors ; 40. There is also a less paranoid routine, gb raw close, that closes user-generated files. It simply closes the current file, if any, and returns the value of the magic checksum. Example: The restore graph subroutine in GB SAVE uses gb raw open and gb raw close to provide systemindependent input that is almost as foolproof as the reading of standard GraphBase data. 41. #define gb raw close gb r close / for Procrustean external linkage / gb_io.h 6 + #define gb raw close gb r close extern long gb close (); / close a GraphBase data file; return 0 if OK / extern long gb raw close (); / close file and return the checksum / 42. External functions 12 + long gb raw close () if (cur file) fclose (cur file); more data = buffer [0] = 0; cur pos = buffer ; cur file =Λ; return magic;
14 14 INDEX GB IO Index. Here is a list that shows where the identifiers of this program are defined and used. a: 17, 24. bad first line : 3, 34. bad fourth line : 3, 37. bad last line : 3, 39. bad second line : 3, 35. bad third line : 3, 36. buffer : 8, 9, 16, 18, 22, 34, 35, 36, 37, 39, 42. c: 12, 26. cant close file: 3, 39. cant open file : 3, 28, 30. checksum prime : 10, 17. cur file : 8, 9, 30, 31, 32, 39, 42. cur pos : 8, 9, 21, 22, 23, 24, 25, 26, 37, 39, 42. d: 12, 24. DATA_DIRECTORY: 31. exit test : 2, 27, 28, 38. f: 30, 32. fclose : 3, 39, 42. fgets : 3, 9. file ended prematurely : 3,9. file name: 32, 33, 39. fill buf : 9, 18, 30, 35, 36, 37, 39. final magic: 10, 34, 37, 39. fopen : 3, 31. fprintf : 2. gb backup: 21,22, 27. gb char : 21,22, 27, 37. gb close : 32, 38, 39, 41. gb digit : 23, 24, 27. gb eof : 19, 20, 27. gb newline : 16, 17, 18, 21, 27, 32. gb number : 23,24, 27, 37. gb open : 28, 29, 32, 38. gb r close : 41. gb r open : 29. gb raw close : 40, 41, 42. gb raw open : 28, 29, 30, 32, 40. gb string : 25, 26, 27. icode : 10, 11, 12, 14, 15, 17, 23, 24. icode setup: 14, 15. imap : 11, 12, 15. imap chr : 12, 13. imap ord : 12, 13. io errors : 2, 3, 5,6, 9, 27, 28, 30, 32, 34, 35, 36, 37, 38, 39. k: 15. line no: 10, 18, 30, 39. magic: 10, 17, 18, 30, 39, 40, 42. main : 2. missing newline : 3,9. more data : 9, 10, 18, 19, 20, 30, 39, 42. new checksum : 16,17, 18. no file open : 3, 39. old checksum : 17. p: 9, 15, 17, 26. printf : 2. restore graph : 40. s: 17. sprintf : 31, 34, 39. stderr : 2. str buf : 25,26, 31, 34, 39. STR_BUF_LENGTH: 25,26, 31. strcmp: 27. strlen : 12, 31, 34, 39. strncmp: 34, 37, 39. strncpy : 32. system dependencies: 31. SYSV: 7. temp: 27. tot lines : 10, 18, 30, 34, 37, 39. unexpected char : 11, 12, 13, 15. wrong checksum : 3, 39. wrong number of lines : 3, 39.
15 GB IO NAMES OF THE SECTIONS 15 Check the first line; return if unsuccessful 34 Used in section 32. Check the fourth line; return if unsuccessful 37 Used in section 32. Check the second line; return if unsuccessful 35 Used in section 32. Check the third line; return if unsuccessful 36 Used in section 32. External declarations 5 Used in section 4. External functions 12, 17, 18, 20, 22, 24, 26, 30, 32, 39, 42 Used in section 4. Header files to include 7 Used in sections 4 and 6. Internal functions 9, 15 Used in section 4. Make sure that icode has been initialized 14 Used in sections 12 and 30. Private declarations 8, 10, 11, 33 Used in section 4. Test the sample data lines; exit if there s trouble 27 Used in section 2. Test the gb close routine; exit if there s trouble 38 Used in section 2. Test the gb open routine; exit if there s trouble 28 Used in section 2. Try to open f 31 Used in section 30. gb_io.h 6, 13, 16, 19, 21, 23, 25, 29, 41 test_io.c 2
16 January 12, 1994 at 23:13 GB IO Section Page Introduction Inputtingaline Checksums Parsingaline Openingafile Closingafile Index c 1993 Stanford University This file may be freely copied and distributed, provided that no changes whatsoever are made. All users are asked to help keep the Stanford GraphBase files consistent and uncorrupted, identical everywhere in the world. Changes are permissible only if the modified file is given a new name, different from the names of existing files in the Stanford GraphBase, and only if the modified file is clearly identified as not being part of that GraphBase. (The CWEB system has a change file facility by which users can easily make minor alterations without modifying the master source files in any way. Everybody is supposed to use change files instead of changing the files.) The author has tried his best to produce correct and useful programs, in order to help promote computer science research, but no warranty of any kind should be assumed. Preliminary work on the Stanford GraphBase project was supported in part by National Science Foundation grant CCR
1 GB FLIP INTRODUCTION Introduction. This is GB FLIP, the module used by GraphBase programs to generate random numbers.
 1 GB FLIP INTRODUCTION 1 1. Introduction. This is GB FLIP, the module used by GraphBase programs to generate random numbers. To use the routines in this file, first call the function gb init rand (seed
1 GB FLIP INTRODUCTION 1 1. Introduction. This is GB FLIP, the module used by GraphBase programs to generate random numbers. To use the routines in this file, first call the function gb init rand (seed
1 GB DIJK INTRODUCTION 1. Important: Before reading GB DIJK, please read or at least skim the program for GB GRAPH.
 1 GB DIJK INTRODUCTION 1 Important: Before reading GB DIJK, please read or at least skim the program for GB GRAPH. 1. Introduction. The GraphBase demonstration routine dijkstra (uu, vv, gg, hh ) finds
1 GB DIJK INTRODUCTION 1 Important: Before reading GB DIJK, please read or at least skim the program for GB GRAPH. 1. Introduction. The GraphBase demonstration routine dijkstra (uu, vv, gg, hh ) finds
CS113: Lecture 7. Topics: The C Preprocessor. I/O, Streams, Files
 CS113: Lecture 7 Topics: The C Preprocessor I/O, Streams, Files 1 Remember the name: Pre-processor Most commonly used features: #include, #define. Think of the preprocessor as processing the file so as
CS113: Lecture 7 Topics: The C Preprocessor I/O, Streams, Files 1 Remember the name: Pre-processor Most commonly used features: #include, #define. Think of the preprocessor as processing the file so as
1 MMOIMG INTRODUCTION 1
 1 MMOIMG INTRODUCTION 1 1*. Introduction. This program reads a binary mmo file output by the MMIXAL processor and extracts from it an image file. The image file will contain a true image of the MMIX memory
1 MMOIMG INTRODUCTION 1 1*. Introduction. This program reads a binary mmo file output by the MMIXAL processor and extracts from it an image file. The image file will contain a true image of the MMIX memory
C mini reference. 5 Binary numbers 12
 C mini reference Contents 1 Input/Output: stdio.h 2 1.1 int printf ( const char * format,... );......................... 2 1.2 int scanf ( const char * format,... );.......................... 2 1.3 char
C mini reference Contents 1 Input/Output: stdio.h 2 1.1 int printf ( const char * format,... );......................... 2 1.2 int scanf ( const char * format,... );.......................... 2 1.3 char
1 The CTIE processor INTRODUCTION 1
 1 The CTIE processor INTRODUCTION 1 1. Introduction. Whenever a programmer wants to change a given WEB or CWEB program (referred to as a WEB program throughout this program) because of system dependencies,
1 The CTIE processor INTRODUCTION 1 1. Introduction. Whenever a programmer wants to change a given WEB or CWEB program (referred to as a WEB program throughout this program) because of system dependencies,
LESSON 4. The DATA TYPE char
 LESSON 4 This lesson introduces some of the basic ideas involved in character processing. The lesson discusses how characters are stored and manipulated by the C language, how characters can be treated
LESSON 4 This lesson introduces some of the basic ideas involved in character processing. The lesson discusses how characters are stored and manipulated by the C language, how characters can be treated
1 APPENDIX D: COMMON INTRODUCTION 29
 1 APPENDIX D: COMMON INTRODUCTION 29 1. Introduction. This file contains code common to both CTANGLE and CWEAVE, which roughly concerns the following problems: character uniformity, input routines, error
1 APPENDIX D: COMMON INTRODUCTION 29 1. Introduction. This file contains code common to both CTANGLE and CWEAVE, which roughly concerns the following problems: character uniformity, input routines, error
CSE 333 Midterm Exam July 24, Name UW ID#
 Name UW ID# There are 6 questions worth a total of 100 points. Please budget your time so you get to all of the questions. Keep your answers brief and to the point. The exam is closed book, closed notes,
Name UW ID# There are 6 questions worth a total of 100 points. Please budget your time so you get to all of the questions. Keep your answers brief and to the point. The exam is closed book, closed notes,
Rule 1-3: Use white space to break a function into paragraphs. Rule 1-5: Avoid very long statements. Use multiple shorter statements instead.
 Chapter 9: Rules Chapter 1:Style and Program Organization Rule 1-1: Organize programs for readability, just as you would expect an author to organize a book. Rule 1-2: Divide each module up into a public
Chapter 9: Rules Chapter 1:Style and Program Organization Rule 1-1: Organize programs for readability, just as you would expect an author to organize a book. Rule 1-2: Divide each module up into a public
8. Characters, Strings and Files
 REGZ9280: Global Education Short Course - Engineering 8. Characters, Strings and Files Reading: Moffat, Chapter 7, 11 REGZ9280 14s2 8. Characters and Arrays 1 ASCII The ASCII table gives a correspondence
REGZ9280: Global Education Short Course - Engineering 8. Characters, Strings and Files Reading: Moffat, Chapter 7, 11 REGZ9280 14s2 8. Characters and Arrays 1 ASCII The ASCII table gives a correspondence
Introduction to Programming in C Department of Computer Science and Engineering. Lecture No. #54. Organizing Code in multiple files
 Introduction to Programming in C Department of Computer Science and Engineering Lecture No. #54 Organizing Code in multiple files (Refer Slide Time: 00:09) In this lecture, let us look at one particular
Introduction to Programming in C Department of Computer Science and Engineering Lecture No. #54 Organizing Code in multiple files (Refer Slide Time: 00:09) In this lecture, let us look at one particular
1 GB MILES INTRODUCTION 1. Important: Before reading GB MILES, please read or at least skim the programs for GB GRAPH and GB IO.
 1 GB MILES INTRODUCTION 1 Important: Before reading GB MILES, please read or at least skim the programs for GB GRAPH and GB IO. 1. Introduction. This GraphBase module contains the miles subroutine, which
1 GB MILES INTRODUCTION 1 Important: Before reading GB MILES, please read or at least skim the programs for GB GRAPH and GB IO. 1. Introduction. This GraphBase module contains the miles subroutine, which
Standard File Pointers
 1 Programming in C Standard File Pointers Assigned to console unless redirected Standard input = stdin Used by scan function Can be redirected: cmd < input-file Standard output = stdout Used by printf
1 Programming in C Standard File Pointers Assigned to console unless redirected Standard input = stdin Used by scan function Can be redirected: cmd < input-file Standard output = stdout Used by printf
Lecture 12 CSE July Today we ll cover the things that you still don t know that you need to know in order to do the assignment.
 Lecture 12 CSE 110 20 July 1992 Today we ll cover the things that you still don t know that you need to know in order to do the assignment. 1 The NULL Pointer For each pointer type, there is one special
Lecture 12 CSE 110 20 July 1992 Today we ll cover the things that you still don t know that you need to know in order to do the assignment. 1 The NULL Pointer For each pointer type, there is one special
CS 220: Introduction to Parallel Computing. Input/Output. Lecture 7
 CS 220: Introduction to Parallel Computing Input/Output Lecture 7 Input/Output Most useful programs will provide some type of input or output Thus far, we ve prompted the user to enter their input directly
CS 220: Introduction to Parallel Computing Input/Output Lecture 7 Input/Output Most useful programs will provide some type of input or output Thus far, we ve prompted the user to enter their input directly
Standard C Library Functions
 Demo lecture slides Although I will not usually give slides for demo lectures, the first two demo lectures involve practice with things which you should really know from G51PRG Since I covered much of
Demo lecture slides Although I will not usually give slides for demo lectures, the first two demo lectures involve practice with things which you should really know from G51PRG Since I covered much of
CHAPTER 5 VARIABLES AND OTHER BASIC ELEMENTS IN JAVA PROGRAMS
 These are sample pages from Kari Laitinen s book "A Natural Introduction to Computer Programming with Java". For more information, please visit http://www.naturalprogramming.com/javabook.html CHAPTER 5
These are sample pages from Kari Laitinen s book "A Natural Introduction to Computer Programming with Java". For more information, please visit http://www.naturalprogramming.com/javabook.html CHAPTER 5
Fundamentals of Programming Session 4
 Fundamentals of Programming Session 4 Instructor: Reza Entezari-Maleki Email: entezari@ce.sharif.edu 1 Fall 2011 These slides are created using Deitel s slides, ( 1992-2010 by Pearson Education, Inc).
Fundamentals of Programming Session 4 Instructor: Reza Entezari-Maleki Email: entezari@ce.sharif.edu 1 Fall 2011 These slides are created using Deitel s slides, ( 1992-2010 by Pearson Education, Inc).
Course organization. Course introduction ( Week 1)
 Course organization Course introduction ( Week 1) Code editor: Emacs Part I: Introduction to C programming language (Week 2-9) Chapter 1: Overall Introduction (Week 1-3) Chapter 2: Types, operators and
Course organization Course introduction ( Week 1) Code editor: Emacs Part I: Introduction to C programming language (Week 2-9) Chapter 1: Overall Introduction (Week 1-3) Chapter 2: Types, operators and
CSci 4061 Introduction to Operating Systems. Input/Output: High-level
 CSci 4061 Introduction to Operating Systems Input/Output: High-level I/O Topics First, cover high-level I/O Next, talk about low-level device I/O I/O not part of the C language! High-level I/O Hide device
CSci 4061 Introduction to Operating Systems Input/Output: High-level I/O Topics First, cover high-level I/O Next, talk about low-level device I/O I/O not part of the C language! High-level I/O Hide device
1 BOOK COMPONENTS BICOMPONENTS 1. Important: Before reading BOOK COMPONENTS, please read or at least skim the program for GB BOOKS.
 1 BOOK COMPONENTS BICOMPONENTS 1 Important: Before reading BOOK COMPONENTS, please read or at least skim the program for GB BOOKS. 1. Bicomponents. This demonstration program computes the biconnected components
1 BOOK COMPONENTS BICOMPONENTS 1 Important: Before reading BOOK COMPONENTS, please read or at least skim the program for GB BOOKS. 1. Bicomponents. This demonstration program computes the biconnected components
today cs3157-fall2002-sklar-lect05 1
 today homework #1 due on monday sep 23, 6am some miscellaneous topics: logical operators random numbers character handling functions FILE I/O strings arrays pointers cs3157-fall2002-sklar-lect05 1 logical
today homework #1 due on monday sep 23, 6am some miscellaneous topics: logical operators random numbers character handling functions FILE I/O strings arrays pointers cs3157-fall2002-sklar-lect05 1 logical
ECS 153 Discussion Section. April 6, 2015
 ECS 153 Discussion Section April 6, 2015 1 What We ll Cover Goal: To discuss buffer overflows in detail Stack- based buffer overflows Smashing the stack : execution from the stack ARC (or return- to- libc)
ECS 153 Discussion Section April 6, 2015 1 What We ll Cover Goal: To discuss buffer overflows in detail Stack- based buffer overflows Smashing the stack : execution from the stack ARC (or return- to- libc)
CSE 12 Spring 2018 Week One, Lecture Two
 CSE 12 Spring 2018 Week One, Lecture Two Homework One and Two: - Introduction to C - Review of basic programming principles - Building from fgetc and fputc - Input and output strings and numbers - Introduction
CSE 12 Spring 2018 Week One, Lecture Two Homework One and Two: - Introduction to C - Review of basic programming principles - Building from fgetc and fputc - Input and output strings and numbers - Introduction
THE FUNDAMENTAL DATA TYPES
 THE FUNDAMENTAL DATA TYPES Declarations, Expressions, and Assignments Variables and constants are the objects that a prog. manipulates. All variables must be declared before they can be used. #include
THE FUNDAMENTAL DATA TYPES Declarations, Expressions, and Assignments Variables and constants are the objects that a prog. manipulates. All variables must be declared before they can be used. #include
C Libraries. Bart Childs Complementary to the text(s)
 C Libraries Bart Childs Complementary to the text(s) 2006 C was designed to make extensive use of a number of libraries. A great reference for student purposes is appendix B of the K&R book. This list
C Libraries Bart Childs Complementary to the text(s) 2006 C was designed to make extensive use of a number of libraries. A great reference for student purposes is appendix B of the K&R book. This list
CS240: Programming in C. Lecture 14: Errors
 CS240: Programming in C Lecture 14: Errors Errors We ve already seen a number of instances where unexpected (and uncaught) errors can take place: Memory buffer overflow/underflow unintended casts misuse
CS240: Programming in C Lecture 14: Errors Errors We ve already seen a number of instances where unexpected (and uncaught) errors can take place: Memory buffer overflow/underflow unintended casts misuse
Lecture 16 CSE July 1992
 Lecture 16 CSE 110 28 July 1992 1 Dynamic Memory Allocation We are finally going to learn how to allocate memory on the fly, getting more when we need it, a subject not usually covered in introductory
Lecture 16 CSE 110 28 July 1992 1 Dynamic Memory Allocation We are finally going to learn how to allocate memory on the fly, getting more when we need it, a subject not usually covered in introductory
String constants. /* Demo: string constant */ #include <stdio.h> int main() {
 Strings 1 String constants 2 /* Demo: string constant */ #include s1.c int main() { printf("hi\n"); } String constants are in double quotes A backslash \ is used to include 'special' characters,
Strings 1 String constants 2 /* Demo: string constant */ #include s1.c int main() { printf("hi\n"); } String constants are in double quotes A backslash \ is used to include 'special' characters,
Computers Programming Course 5. Iulian Năstac
 Computers Programming Course 5 Iulian Năstac Recap from previous course Classification of the programming languages High level (Ada, Pascal, Fortran, etc.) programming languages with strong abstraction
Computers Programming Course 5 Iulian Năstac Recap from previous course Classification of the programming languages High level (Ada, Pascal, Fortran, etc.) programming languages with strong abstraction
A Fast Review of C Essentials Part I
 A Fast Review of C Essentials Part I Structural Programming by Z. Cihan TAYSI Outline Program development C Essentials Functions Variables & constants Names Formatting Comments Preprocessor Data types
A Fast Review of C Essentials Part I Structural Programming by Z. Cihan TAYSI Outline Program development C Essentials Functions Variables & constants Names Formatting Comments Preprocessor Data types
Chapter 10: File Input / Output
 C: Chapter10 Page 1 of 6 C Tutorial.......... File input/output Chapter 10: File Input / Output OUTPUT TO A FILE Load and display the file named formout.c for your first example of writing data to a file.
C: Chapter10 Page 1 of 6 C Tutorial.......... File input/output Chapter 10: File Input / Output OUTPUT TO A FILE Load and display the file named formout.c for your first example of writing data to a file.
Fundamental Data Types. CSE 130: Introduction to Programming in C Stony Brook University
 Fundamental Data Types CSE 130: Introduction to Programming in C Stony Brook University Program Organization in C The C System C consists of several parts: The C language The preprocessor The compiler
Fundamental Data Types CSE 130: Introduction to Programming in C Stony Brook University Program Organization in C The C System C consists of several parts: The C language The preprocessor The compiler
COP 3223 Final Review
 COP 3223 Final Review Jennifer Brown December 2, 2018 1 Introduction 1.1 Variables I. How can we store data in a program? Initializing variables with data types A. Which of these are valid names for variables?
COP 3223 Final Review Jennifer Brown December 2, 2018 1 Introduction 1.1 Variables I. How can we store data in a program? Initializing variables with data types A. Which of these are valid names for variables?
Arrays, Strings, & Pointers
 Arrays, Strings, & Pointers Alexander Nelson August 31, 2018 University of Arkansas - Department of Computer Science and Computer Engineering Arrays, Strings, & Pointers Arrays, Strings, & Pointers are
Arrays, Strings, & Pointers Alexander Nelson August 31, 2018 University of Arkansas - Department of Computer Science and Computer Engineering Arrays, Strings, & Pointers Arrays, Strings, & Pointers are
School of Computer Science & Software Engineering The University of Western Australia. Mid-Semester Test September 2017
 School of Computer Science & Software Engineering The University of Western Australia Mid-Semester Test September 2017 () This paper contains 1 section This paper contains: 8 pages (including this title
School of Computer Science & Software Engineering The University of Western Australia Mid-Semester Test September 2017 () This paper contains 1 section This paper contains: 8 pages (including this title
Slide Set 2. for ENCM 335 in Fall Steve Norman, PhD, PEng
 Slide Set 2 for ENCM 335 in Fall 2018 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary September 2018 ENCM 335 Fall 2018 Slide Set 2 slide
Slide Set 2 for ENCM 335 in Fall 2018 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary September 2018 ENCM 335 Fall 2018 Slide Set 2 slide
Features of C. Portable Procedural / Modular Structured Language Statically typed Middle level language
 1 History C is a general-purpose, high-level language that was originally developed by Dennis M. Ritchie to develop the UNIX operating system at Bell Labs. C was originally first implemented on the DEC
1 History C is a general-purpose, high-level language that was originally developed by Dennis M. Ritchie to develop the UNIX operating system at Bell Labs. C was originally first implemented on the DEC
Java How to Program, 10/e. Copyright by Pearson Education, Inc. All Rights Reserved.
 Java How to Program, 10/e Education, Inc. All Rights Reserved. Each class you create becomes a new type that can be used to declare variables and create objects. You can declare new classes as needed;
Java How to Program, 10/e Education, Inc. All Rights Reserved. Each class you create becomes a new type that can be used to declare variables and create objects. You can declare new classes as needed;
CSE 12 Spring 2016 Week One, Lecture Two
 CSE 12 Spring 2016 Week One, Lecture Two Homework One and Two: hw2: Discuss in section today - Introduction to C - Review of basic programming principles - Building from fgetc and fputc - Input and output
CSE 12 Spring 2016 Week One, Lecture Two Homework One and Two: hw2: Discuss in section today - Introduction to C - Review of basic programming principles - Building from fgetc and fputc - Input and output
The type of all data used in a C++ program must be specified
 The type of all data used in a C++ program must be specified A data type is a description of the data being represented That is, a set of possible values and a set of operations on those values There are
The type of all data used in a C++ program must be specified A data type is a description of the data being represented That is, a set of possible values and a set of operations on those values There are
A Crash Course in C. Steven Reeves
 A Crash Course in C Steven Reeves This class will rely heavily on C and C++. As a result this section will help students who are not familiar with C or who need a refresher. By the end of this section
A Crash Course in C Steven Reeves This class will rely heavily on C and C++. As a result this section will help students who are not familiar with C or who need a refresher. By the end of this section
Language Basics. /* The NUMBER GAME - User tries to guess a number between 1 and 10 */ /* Generate a random number between 1 and 10 */
 Overview Language Basics This chapter describes the basic elements of Rexx. It discusses the simple components that make up the language. These include script structure, elements of the language, operators,
Overview Language Basics This chapter describes the basic elements of Rexx. It discusses the simple components that make up the language. These include script structure, elements of the language, operators,
ECE551 Midterm Version 1
 Name: ECE551 Midterm Version 1 NetID: There are 7 questions, with the point values as shown below. You have 75 minutes with a total of 75 points. Pace yourself accordingly. This exam must be individual
Name: ECE551 Midterm Version 1 NetID: There are 7 questions, with the point values as shown below. You have 75 minutes with a total of 75 points. Pace yourself accordingly. This exam must be individual
Goals of C "" The Goals of C (cont.) "" Goals of this Lecture"" The Design of C: A Rational Reconstruction"
 Goals of this Lecture The Design of C: A Rational Reconstruction Help you learn about: The decisions that were available to the designers of C The decisions that were made by the designers of C Why? Learning
Goals of this Lecture The Design of C: A Rational Reconstruction Help you learn about: The decisions that were available to the designers of C The decisions that were made by the designers of C Why? Learning
QUIZ. What is wrong with this code that uses default arguments?
 QUIZ What is wrong with this code that uses default arguments? Solution The value of the default argument should be placed in either declaration or definition, not both! QUIZ What is wrong with this code
QUIZ What is wrong with this code that uses default arguments? Solution The value of the default argument should be placed in either declaration or definition, not both! QUIZ What is wrong with this code
EE 355 Lab 4 - Party Like A Char Star
 1 Introduction In this lab you will implement a "hangman" game where the user is shown blanks representing letter of a word and then tries to guess and fill in the letters with a limited number of guesses
1 Introduction In this lab you will implement a "hangman" game where the user is shown blanks representing letter of a word and then tries to guess and fill in the letters with a limited number of guesses
Input / Output Functions
 CSE 2421: Systems I Low-Level Programming and Computer Organization Input / Output Functions Presentation G Read/Study: Reek Chapter 15 Gojko Babić 10-03-2018 Input and Output Functions The stdio.h contain
CSE 2421: Systems I Low-Level Programming and Computer Organization Input / Output Functions Presentation G Read/Study: Reek Chapter 15 Gojko Babić 10-03-2018 Input and Output Functions The stdio.h contain
CSE 374 Programming Concepts & Tools
 CSE 374 Programming Concepts & Tools Hal Perkins Fall 2017 Lecture 8 C: Miscellanea Control, Declarations, Preprocessor, printf/scanf 1 The story so far The low-level execution model of a process (one
CSE 374 Programming Concepts & Tools Hal Perkins Fall 2017 Lecture 8 C: Miscellanea Control, Declarations, Preprocessor, printf/scanf 1 The story so far The low-level execution model of a process (one
Preprocessor Directives
 C++ By 6 EXAMPLE Preprocessor Directives As you might recall from Chapter 2, What Is a Program?, the C++ compiler routes your programs through a preprocessor before it compiles them. The preprocessor can
C++ By 6 EXAMPLE Preprocessor Directives As you might recall from Chapter 2, What Is a Program?, the C++ compiler routes your programs through a preprocessor before it compiles them. The preprocessor can
File Handling in C. EECS 2031 Fall October 27, 2014
 File Handling in C EECS 2031 Fall 2014 October 27, 2014 1 Reading from and writing to files in C l stdio.h contains several functions that allow us to read from and write to files l Their names typically
File Handling in C EECS 2031 Fall 2014 October 27, 2014 1 Reading from and writing to files in C l stdio.h contains several functions that allow us to read from and write to files l Their names typically
Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display.
 Chapter 18 I/O in C Standard C Library I/O commands are not included as part of the C language. Instead, they are part of the Standard C Library. A collection of functions and macros that must be implemented
Chapter 18 I/O in C Standard C Library I/O commands are not included as part of the C language. Instead, they are part of the Standard C Library. A collection of functions and macros that must be implemented
Intermediate Programming, Spring 2017*
 600.120 Intermediate Programming, Spring 2017* Misha Kazhdan *Much of the code in these examples is not commented because it would otherwise not fit on the slides. This is bad coding practice in general
600.120 Intermediate Programming, Spring 2017* Misha Kazhdan *Much of the code in these examples is not commented because it would otherwise not fit on the slides. This is bad coding practice in general
Engineering program development 7. Edited by Péter Vass
 Engineering program development 7 Edited by Péter Vass Functions Function is a separate computational unit which has its own name (identifier). The objective of a function is solving a well-defined problem.
Engineering program development 7 Edited by Péter Vass Functions Function is a separate computational unit which has its own name (identifier). The objective of a function is solving a well-defined problem.
Introduction to string
 1 Introduction to string String is a sequence of characters enclosed in double quotes. Normally, it is used for storing data like name, address, city etc. ASCII code is internally used to represent string
1 Introduction to string String is a sequence of characters enclosed in double quotes. Normally, it is used for storing data like name, address, city etc. ASCII code is internally used to represent string
Computer Security. Robust and secure programming in C. Marius Minea. 12 October 2017
 Computer Security Robust and secure programming in C Marius Minea marius@cs.upt.ro 12 October 2017 In this lecture Write correct code minimizing risks with proper error handling avoiding security pitfalls
Computer Security Robust and secure programming in C Marius Minea marius@cs.upt.ro 12 October 2017 In this lecture Write correct code minimizing risks with proper error handling avoiding security pitfalls
Programming for Engineers Introduction to C
 Programming for Engineers Introduction to C ICEN 200 Spring 2018 Prof. Dola Saha 1 Simple Program 2 Comments // Fig. 2.1: fig02_01.c // A first program in C begin with //, indicating that these two lines
Programming for Engineers Introduction to C ICEN 200 Spring 2018 Prof. Dola Saha 1 Simple Program 2 Comments // Fig. 2.1: fig02_01.c // A first program in C begin with //, indicating that these two lines
https://www.eskimo.com/~scs/cclass/notes/sx8.html
 1 de 6 20-10-2015 10:41 Chapter 8: Strings Strings in C are represented by arrays of characters. The end of the string is marked with a special character, the null character, which is simply the character
1 de 6 20-10-2015 10:41 Chapter 8: Strings Strings in C are represented by arrays of characters. The end of the string is marked with a special character, the null character, which is simply the character
Agenda. Peer Instruction Question 1. Peer Instruction Answer 1. Peer Instruction Question 2 6/22/2011
 CS 61C: Great Ideas in Computer Architecture (Machine Structures) Introduction to C (Part II) Instructors: Randy H. Katz David A. Patterson http://inst.eecs.berkeley.edu/~cs61c/sp11 Spring 2011 -- Lecture
CS 61C: Great Ideas in Computer Architecture (Machine Structures) Introduction to C (Part II) Instructors: Randy H. Katz David A. Patterson http://inst.eecs.berkeley.edu/~cs61c/sp11 Spring 2011 -- Lecture
1 SAT-DANCE-HEULE INTRO 1
 1 SAT-DANCE-HEULE INTRO 1 May 19, 2018 at 02:31 1. Intro. Given an exact cover problem, presented on stdin in the format used by DANCE, we generate clauses for an equivalent satisfiability problem in the
1 SAT-DANCE-HEULE INTRO 1 May 19, 2018 at 02:31 1. Intro. Given an exact cover problem, presented on stdin in the format used by DANCE, we generate clauses for an equivalent satisfiability problem in the
COP 3223 Final Review
 COP 3223 Final Review Jennifer Brown December 2, 2018 1 Introduction 1.1 Variables I. How can we store data in a program? A. Which of these are valid names for variables? i. 9length ii. hello iii. IamASuperCoolName
COP 3223 Final Review Jennifer Brown December 2, 2018 1 Introduction 1.1 Variables I. How can we store data in a program? A. Which of these are valid names for variables? i. 9length ii. hello iii. IamASuperCoolName
C for C++ Programmers
 C for C++ Programmers CS230/330 - Operating Systems (Winter 2001). The good news is that C syntax is almost identical to that of C++. However, there are many things you're used to that aren't available
C for C++ Programmers CS230/330 - Operating Systems (Winter 2001). The good news is that C syntax is almost identical to that of C++. However, there are many things you're used to that aren't available
Text Input and Conditionals
 Text Input and Conditionals Text Input Many programs allow the user to enter information, like a username and password. Python makes taking input from the user seamless with a single line of code: input()
Text Input and Conditionals Text Input Many programs allow the user to enter information, like a username and password. Python makes taking input from the user seamless with a single line of code: input()
UNIT IV-2. The I/O library functions can be classified into two broad categories:
 UNIT IV-2 6.0 INTRODUCTION Reading, processing and writing of data are the three essential functions of a computer program. Most programs take some data as input and display the processed data, often known
UNIT IV-2 6.0 INTRODUCTION Reading, processing and writing of data are the three essential functions of a computer program. Most programs take some data as input and display the processed data, often known
PROGRAMMAZIONE I A.A. 2017/2018
 PROGRAMMAZIONE I A.A. 2017/2018 INPUT/OUTPUT INPUT AND OUTPUT Programs must be able to write data to files or to physical output devices such as displays or printers, and to read in data from files or
PROGRAMMAZIONE I A.A. 2017/2018 INPUT/OUTPUT INPUT AND OUTPUT Programs must be able to write data to files or to physical output devices such as displays or printers, and to read in data from files or
gcc hello.c a.out Hello, world gcc -o hello hello.c hello Hello, world
 alun@debian:~$ gcc hello.c alun@debian:~$ a.out Hello, world alun@debian:~$ gcc -o hello hello.c alun@debian:~$ hello Hello, world alun@debian:~$ 1 A Quick guide to C for Networks and Operating Systems
alun@debian:~$ gcc hello.c alun@debian:~$ a.out Hello, world alun@debian:~$ gcc -o hello hello.c alun@debian:~$ hello Hello, world alun@debian:~$ 1 A Quick guide to C for Networks and Operating Systems
C programming basics T3-1 -
 C programming basics T3-1 - Outline 1. Introduction 2. Basic concepts 3. Functions 4. Data types 5. Control structures 6. Arrays and pointers 7. File management T3-2 - 3.1: Introduction T3-3 - Review of
C programming basics T3-1 - Outline 1. Introduction 2. Basic concepts 3. Functions 4. Data types 5. Control structures 6. Arrays and pointers 7. File management T3-2 - 3.1: Introduction T3-3 - Review of
In the case of the dynamic array, the space must be deallocated when the program is finished with it. free(x);
 C Notes Relation Between Pointers and Arrays Space for static arrays in C is allocated on the stack when the function that defines them is called and is automatically deleted when the function ends, just
C Notes Relation Between Pointers and Arrays Space for static arrays in C is allocated on the stack when the function that defines them is called and is automatically deleted when the function ends, just
INTRODUCTION 1 AND REVIEW
 INTRODUTION 1 AND REVIEW hapter SYS-ED/ OMPUTER EDUATION TEHNIQUES, IN. Programming: Advanced Objectives You will learn: Program structure. Program statements. Datatypes. Pointers. Arrays. Structures.
INTRODUTION 1 AND REVIEW hapter SYS-ED/ OMPUTER EDUATION TEHNIQUES, IN. Programming: Advanced Objectives You will learn: Program structure. Program statements. Datatypes. Pointers. Arrays. Structures.
cs3157: another C lecture (mon-21-feb-2005) C pre-processor (3).
 cs3157: another C lecture (mon-21-feb-2005) C pre-processor (1). today: C pre-processor command-line arguments more on data types and operators: booleans in C logical and bitwise operators type conversion
cs3157: another C lecture (mon-21-feb-2005) C pre-processor (1). today: C pre-processor command-line arguments more on data types and operators: booleans in C logical and bitwise operators type conversion
Introduction to C. Robert Escriva. Cornell CS 4411, August 30, Geared toward programmers
 Introduction to C Geared toward programmers Robert Escriva Slide heritage: Alin Dobra Niranjan Nagarajan Owen Arden Cornell CS 4411, August 30, 2010 1 Why C? 2 A Quick Example 3 Programmer s Responsibilities
Introduction to C Geared toward programmers Robert Escriva Slide heritage: Alin Dobra Niranjan Nagarajan Owen Arden Cornell CS 4411, August 30, 2010 1 Why C? 2 A Quick Example 3 Programmer s Responsibilities
Systems Programming. 08. Standard I/O Library. Alexander Holupirek
 Systems Programming 08. Standard I/O Library Alexander Holupirek Database and Information Systems Group Department of Computer & Information Science University of Konstanz Summer Term 2008 Last lecture:
Systems Programming 08. Standard I/O Library Alexander Holupirek Database and Information Systems Group Department of Computer & Information Science University of Konstanz Summer Term 2008 Last lecture:
Basic I/O. COSC Software Tools. Streams. Standard I/O. Standard I/O. Formatted Output
 Basic I/O COSC2031 - Software Tools C - Input/Output (K+R Ch. 7) We know how to do some basic input and output: getchar - reading characters putchar - writing characters printf - formatted output Input
Basic I/O COSC2031 - Software Tools C - Input/Output (K+R Ch. 7) We know how to do some basic input and output: getchar - reading characters putchar - writing characters printf - formatted output Input
C Review. MaxMSP Developers Workshop Summer 2009 CNMAT
 C Review MaxMSP Developers Workshop Summer 2009 CNMAT C Syntax Program control (loops, branches): Function calls Math: +, -, *, /, ++, -- Variables, types, structures, assignment Pointers and memory (***
C Review MaxMSP Developers Workshop Summer 2009 CNMAT C Syntax Program control (loops, branches): Function calls Math: +, -, *, /, ++, -- Variables, types, structures, assignment Pointers and memory (***
File IO and command line input CSE 2451
 File IO and command line input CSE 2451 File functions Open/Close files fopen() open a stream for a file fclose() closes a stream One character at a time: fgetc() similar to getchar() fputc() similar to
File IO and command line input CSE 2451 File functions Open/Close files fopen() open a stream for a file fclose() closes a stream One character at a time: fgetc() similar to getchar() fputc() similar to
1. We have a code sequence that is potentially executed twice.
 Long Jump Long Jump Local Jumps In the following example: 1. We have a code sequence that is potentially executed twice. 2. A flag is used to determine whether the sequence is being executed the first
Long Jump Long Jump Local Jumps In the following example: 1. We have a code sequence that is potentially executed twice. 2. A flag is used to determine whether the sequence is being executed the first
Annotation Annotation or block comments Provide high-level description and documentation of section of code More detail than simple comments
 Variables, Data Types, and More Introduction In this lesson will introduce and study C annotation and comments C variables Identifiers C data types First thoughts on good coding style Declarations vs.
Variables, Data Types, and More Introduction In this lesson will introduce and study C annotation and comments C variables Identifiers C data types First thoughts on good coding style Declarations vs.
Foundation Exam - Sample Problems for New Topics
 Foundation Exam - Sample Problems for New Topics Fall 2016 Dynamic Memory Allocation Sample Question #1 Consider the following struct to store a single Uno playing card: typedef struct char color[20];
Foundation Exam - Sample Problems for New Topics Fall 2016 Dynamic Memory Allocation Sample Question #1 Consider the following struct to store a single Uno playing card: typedef struct char color[20];
CMPT 125: Lecture 3 Data and Expressions
 CMPT 125: Lecture 3 Data and Expressions Tamara Smyth, tamaras@cs.sfu.ca School of Computing Science, Simon Fraser University January 3, 2009 1 Character Strings A character string is an object in Java,
CMPT 125: Lecture 3 Data and Expressions Tamara Smyth, tamaras@cs.sfu.ca School of Computing Science, Simon Fraser University January 3, 2009 1 Character Strings A character string is an object in Java,
CS 326 Operating Systems C Programming. Greg Benson Department of Computer Science University of San Francisco
 CS 326 Operating Systems C Programming Greg Benson Department of Computer Science University of San Francisco Why C? Fast (good optimizing compilers) Not too high-level (Java, Python, Lisp) Not too low-level
CS 326 Operating Systems C Programming Greg Benson Department of Computer Science University of San Francisco Why C? Fast (good optimizing compilers) Not too high-level (Java, Python, Lisp) Not too low-level
211: Computer Architecture Summer 2016
 211: Computer Architecture Summer 2016 Liu Liu Topic: C Programming Data Representation I/O: - (example) cprintf.c Memory: - memory address - stack / heap / constant space - basic data layout Pointer:
211: Computer Architecture Summer 2016 Liu Liu Topic: C Programming Data Representation I/O: - (example) cprintf.c Memory: - memory address - stack / heap / constant space - basic data layout Pointer:
Lecture 03 Bits, Bytes and Data Types
 Lecture 03 Bits, Bytes and Data Types Computer Languages A computer language is a language that is used to communicate with a machine. Like all languages, computer languages have syntax (form) and semantics
Lecture 03 Bits, Bytes and Data Types Computer Languages A computer language is a language that is used to communicate with a machine. Like all languages, computer languages have syntax (form) and semantics
Strings. Arrays of characters. Pallab Dasgupta Professor, Dept. of Computer Sc & Engg INDIAN INSTITUTE OF TECHNOLOGY
 Strings Arrays of characters Pallab Dasgupta Professor, Dept. of Computer Sc & Engg INDIAN INSTITUTE OF TECHNOLOGY 1 Basics Strings A string is a sequence of characters treated as a group We have already
Strings Arrays of characters Pallab Dasgupta Professor, Dept. of Computer Sc & Engg INDIAN INSTITUTE OF TECHNOLOGY 1 Basics Strings A string is a sequence of characters treated as a group We have already
printf( Please enter another number: ); scanf( %d, &num2);
 CIT 593 Intro to Computer Systems Lecture #13 (11/1/12) Now that we've looked at how an assembly language program runs on a computer, we're ready to move up a level and start working with more powerful
CIT 593 Intro to Computer Systems Lecture #13 (11/1/12) Now that we've looked at how an assembly language program runs on a computer, we're ready to move up a level and start working with more powerful
Homework 3 CS161 Computer Security, Fall 2008 Assigned 10/07/08 Due 10/13/08
 Homework 3 CS161 Computer Security, Fall 2008 Assigned 10/07/08 Due 10/13/08 For your solutions you should submit a hard copy; either hand written pages stapled together or a print out of a typeset document
Homework 3 CS161 Computer Security, Fall 2008 Assigned 10/07/08 Due 10/13/08 For your solutions you should submit a hard copy; either hand written pages stapled together or a print out of a typeset document
Topic 8: I/O. Reading: Chapter 7 in Kernighan & Ritchie more details in Appendix B (optional) even more details in GNU C Library manual (optional)
 Topic 8: I/O Reading: Chapter 7 in Kernighan & Ritchie more details in Appendix B (optional) even more details in GNU C Library manual (optional) No C language primitives for I/O; all done via function
Topic 8: I/O Reading: Chapter 7 in Kernighan & Ritchie more details in Appendix B (optional) even more details in GNU C Library manual (optional) No C language primitives for I/O; all done via function
Chapter 1 & 2 Introduction to C Language
 1 Chapter 1 & 2 Introduction to C Language Copyright 2007 by Deitel & Associates, Inc. and Pearson Education Inc. All Rights Reserved. Chapter 1 & 2 - Introduction to C Language 2 Outline 1.1 The History
1 Chapter 1 & 2 Introduction to C Language Copyright 2007 by Deitel & Associates, Inc. and Pearson Education Inc. All Rights Reserved. Chapter 1 & 2 - Introduction to C Language 2 Outline 1.1 The History
Arrays array array length fixed array fixed length array fixed size array Array elements and subscripting
 Arrays Fortunately, structs are not the only aggregate data type in C++. An array is an aggregate data type that lets us access many variables of the same type through a single identifier. Consider the
Arrays Fortunately, structs are not the only aggregate data type in C++. An array is an aggregate data type that lets us access many variables of the same type through a single identifier. Consider the
ECE551 Midterm Version 1
 Name: ECE551 Midterm Version 1 NetID: There are 7 questions, with the point values as shown below. You have 75 minutes with a total of 75 points. Pace yourself accordingly. This exam must be individual
Name: ECE551 Midterm Version 1 NetID: There are 7 questions, with the point values as shown below. You have 75 minutes with a total of 75 points. Pace yourself accordingly. This exam must be individual
Work relative to other classes
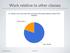 Work relative to other classes 1 Hours/week on projects 2 C BOOTCAMP DAY 1 CS3600, Northeastern University Slides adapted from Anandha Gopalan s CS132 course at Univ. of Pittsburgh Overview C: A language
Work relative to other classes 1 Hours/week on projects 2 C BOOTCAMP DAY 1 CS3600, Northeastern University Slides adapted from Anandha Gopalan s CS132 course at Univ. of Pittsburgh Overview C: A language
Basic Types and Formatted I/O
 Basic Types and Formatted I/O C Variables Names (1) Variable Names Names may contain letters, digits and underscores The first character must be a letter or an underscore. the underscore can be used but
Basic Types and Formatted I/O C Variables Names (1) Variable Names Names may contain letters, digits and underscores The first character must be a letter or an underscore. the underscore can be used but
ATOMS. 3.1 Interface. The Atom interface is simple: atom.h #ifndef ATOM_INCLUDED #define ATOM_INCLUDED
 3 ATOMS An atom is a pointer to a unique, immutable sequence of zero or more arbitrary bytes. Most atoms are pointers to null-terminated strings, but a pointer to any sequence of bytes can be an atom.
3 ATOMS An atom is a pointer to a unique, immutable sequence of zero or more arbitrary bytes. Most atoms are pointers to null-terminated strings, but a pointer to any sequence of bytes can be an atom.
CSE 333 Midterm Exam July 24, 2017 Sample Solution
 Sample Solution Question 1. (14 points) Making things. Suppose we have the following C header and implementation files, showing the various #include and #if directives in each one: widget.h #ifndef _WIDGET_H_
Sample Solution Question 1. (14 points) Making things. Suppose we have the following C header and implementation files, showing the various #include and #if directives in each one: widget.h #ifndef _WIDGET_H_
CS 261 Fall Mike Lam, Professor. Structs and I/O
 CS 261 Fall 2018 Mike Lam, Professor Structs and I/O Typedefs A typedef is a way to create a new type name Basically a synonym for another type Useful for shortening long types or providing more meaningful
CS 261 Fall 2018 Mike Lam, Professor Structs and I/O Typedefs A typedef is a way to create a new type name Basically a synonym for another type Useful for shortening long types or providing more meaningful
ECE551 Midterm Version 2
 Name: ECE551 Midterm Version 2 NetID: There are 7 questions, with the point values as shown below. You have 75 minutes with a total of 75 points. Pace yourself accordingly. This exam must be individual
Name: ECE551 Midterm Version 2 NetID: There are 7 questions, with the point values as shown below. You have 75 minutes with a total of 75 points. Pace yourself accordingly. This exam must be individual
1. Lexical Analysis Phase
 1. Lexical Analysis Phase The purpose of the lexical analyzer is to read the source program, one character at time, and to translate it into a sequence of primitive units called tokens. Keywords, identifiers,
1. Lexical Analysis Phase The purpose of the lexical analyzer is to read the source program, one character at time, and to translate it into a sequence of primitive units called tokens. Keywords, identifiers,
CSC209H Lecture 3. Dan Zingaro. January 21, 2015
 CSC209H Lecture 3 Dan Zingaro January 21, 2015 Streams (King 22.1) Stream: source of input or destination for output We access a stream through a file pointer (FILE *) Three streams are available without
CSC209H Lecture 3 Dan Zingaro January 21, 2015 Streams (King 22.1) Stream: source of input or destination for output We access a stream through a file pointer (FILE *) Three streams are available without
Design and development of embedded systems for the Internet of Things (IoT) Fabio Angeletti Fabrizio Gattuso
 Design and development of embedded systems for the Internet of Things (IoT) Fabio Angeletti Fabrizio Gattuso Why C? Test on 21 Android Devices with 32-bits and 64-bits processors and different versions
Design and development of embedded systems for the Internet of Things (IoT) Fabio Angeletti Fabrizio Gattuso Why C? Test on 21 Android Devices with 32-bits and 64-bits processors and different versions
Slide Set 3. for ENCM 339 Fall Steve Norman, PhD, PEng. Electrical & Computer Engineering Schulich School of Engineering University of Calgary
 Slide Set 3 for ENCM 339 Fall 2016 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary September 2016 ENCM 339 Fall 2016 Slide Set 3 slide 2/46
Slide Set 3 for ENCM 339 Fall 2016 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary September 2016 ENCM 339 Fall 2016 Slide Set 3 slide 2/46
