Checks and Balances - Constraint Solving without Surprises in Object-Constraint Programming Languages: Full Formal Development
|
|
|
- Marilynn Newton
- 5 years ago
- Views:
Transcription
1 Checks and Balances - Constraint Solving without Surprises in Object-Constraint Programming Languages: Full Formal Development Tim Felgentreff, Todd Millstein, Alan Borning and Robert Hirschfeld Viewpoints Research Institute, 1025 Westwood Blvd 2nd flr, Los Angeles, CA t: (310)
2 Checks and Balances Constraint Solving without Surprises in Object-Constraint Programming Languages: Full Formal Development Tim Felgentreff, Todd Millstein, Alan Borning, and Robert Hirschfeld, August Babelsberg/UID and Two Key Theorems This technical report is intended to accompany the conference paper Checks and Balances Constraint Solving without Surprises in Object-Constraint Programming Languages, and presents the full formalism and proofs for two theorems that capture key properties of the Babelsberg/UID core language. These theorems are stated (without the proofs) in Section 3.3 of that paper. 1.1 Syntax We use the following syntax for Babelsberg/UID: Statement s ::= skip L := e x := new o always C once C s;s if e then s else s while e do s Constraint C ::= ρ e C C Expression e ::= v L e e L==L D Object Literal o ::= {l 1 :e 1,...,l n :e n } L-Value L ::= x L.l Constant c ::= true false nil base type constants Variable x ::= variable names Label l ::= record label names Reference r ::= references to heap records Dereference D ::= H(e) Value v ::= c r Metavariable c ranges over the nil value, booleans, and primitive type constants. A finite set of operators on primitives is ranged over by. We assume that includes an equality operator for each primitive type; for convenience we use the symbol = to denote each of these operators. We also assume it includes an operator for boolean conjunction. The operator == tests for identity for primitive values this behaves the same as =. The symbol ρ ranges over constraint priorities and is assumed to include a bottom element weak and a top element required. The syntax requires the priority to be explicit; for simplicity we sometimes omit it in the rules and assume a required priority. 1
3 In the syntax, we treat H as a keyword used for dereferencing. Source programs will not use expressions of the form H(e), but they are introduced as part of constraints given to the solver, which we assume will treat H as an uninterpreted function. We also assume that the solver supports records and record equality, which we also denote with the = operator. 1.2 Operational Semantics The semantics includes an environment E and a heap H. The former is a function that maps variable names to values, while the latter is a function that maps mutable references to objects of the form {l 1 :v 1,...,l n :v n }. When convenient, we also treat both E and H as a set of pairs ({(x,v),...} and {(r,o),...}, respectively). The currently active value constraints are kept as a compound constraint C; identity constraints are kept as a single conjunction referred to as I. E;H e v Expression e evaluates to value v in the context of environment E and heap H. The rules for evaluation are mostly as expected in an imperative language. We do not give rules for expressions of the form H(e), because they are not meant to appear in source. For each operator in the language we assume the existence of a corresponding semantic function denoted. E;H c c E(x) = v E;H x v E;H L r H(r) = {l 1 :v 1,...,l n :v n } 1 i n E;H L.l i v i E;H r r E;H e 1 v 1 E;H e 2 v 2 v 1 v 2 = v E;H e 1 e 2 v E;H L 1 v E;H L 2 v E;H L 1 == L 2 true (E-Const) (E-Var) (E-Field) (E-Ref) (E-Op) (E-IdentityTrue) E;H L 1 v 1 E;H L 2 v 2 v 1 v 2 E;H L 1 == L 2 false (E-IdentityFalse) E;H e : T E;H C Expression e has type T in the context of environment E and heap H. Constraint C is well formed in the context of environment E and heap H. 2
4 We use a notion of typechecking to prevent undesirable non-determinism in constraints. Specifically, we want constraint solving to preserve the structure of the values of variables, changing only the underlying primitive data as part of a solution. We formalize our notion of structure through a simple syntax of types: Type T ::= PrimitiveType {l 1 :T 1,...,l n :T n } The typechecking rules are mostly standard. We check expressions dynamically just before constraint solving, so we typecheck in the context of a runtime environment. Note that we do not include type rules for identities. This ensures that constraints involving them do not typecheck, so identity checks cannot occur in ordinary constraints. E;H c : PrimitiveType H(r)={l 1 :v 1,...,l n :v n } E;H v 1 : T 1 E;H v n : T n E;H r : {l 1 :T 1,...,l n :T n } E(x) = v E;H x : T E;H v : T (T-Const) (T-Ref) (T-Var) E;H L : {l 1 :T 1,...,l n :T n } E;H L.l i : T i 1 i n (T-Field) E;H e 1 : PrimitiveType E;H e 2 : PrimitiveType E;H e 1 e 2 : PrimitiveType E;H e : T E;H ρ e (T-Op) (T-Priority) E;H C 1 E;H C 2 E;H C 1 C 2 (T-Conjunction) E;H = C This judgment represents a call to the constraint solver, which we treat as a black box. The proposition E;H = C denotes that environment E and heap H are an optimal solution to the constraint C, according to the solver s semantics. We assume several well-formedness properties about a solution E and H to constraints C: any object reference appearing in the range of E also appears in the domain of H any object reference appearing in the range of H also appears in the domain of H for all variables x in the domain of E there is some type T such that E;H x : T E;H C stay(x=v, ρ) = C 3
5 stay(r=o, ρ) = C stay(e, ρ) = C stay(h, ρ) = C As in Kaleidoscope, the semantics ensure that each variable has a stay constraint to keep it at its current value, if possible. The stay rules take a priority as a parameter. When solving value constraints, this priority is set to required, to ensure that the structures of objects and the relationship between l-values and object references cannot change. When solving identity constraints as part of executing an assignment statement, the priority is set to weak to allow structural changes. To properly account for the heap in the constraint solver, we employ an uninterpreted function H that maps references to objects (i.e., records). The rules below employ this function in order to define stay constraints for references. stay(x=c, ρ) = weak x=c stay(x=r, ρ) = ρ x=r (StayConst) (StayRef) x 1 fresh x n fresh stay(x 1 =v 1, ρ) = C 1 stay(x n =v n, ρ) = C n stay(r = {l 1 :v 1,...,l n :v n }, ρ) = (required H(r)={l 1 :x 1,...,l n :x n }) C 1 C n (StayObject) E= {(x 1, v 1 ),..., (x n, v n )} stay(x 1 =v 1, ρ) = C 1 stay(x n =v n, ρ) = C n stay(e, ρ) = C 1 C n (StayEnv) H= {(r 1, o 1 ),..., (r n, o n )} stay(r 1 =o 1, ρ) = C 1 stay(r n =o n, ρ) = C n stay(h, ρ) = C 1 C n (StayHeap) stayprefix(e, H, L) = C stayprefix(e, H, I) = C These judgments are another form of stay constraints that ensure that the prefix L of an l-value L.l is unchanged; this is necessary to ensure that updates to the value of L.l are deterministic. stayprefix(e, H, x) = true (StayPrefixVar) L = x.l l n n > 0 E;H x r 0 E;H r 0.l 1 r 1 E;H r n 2.l n 1 r n 1 stayprefix(e, H, L) = x=r 0 r 0.l 1 =r 1 r n 2.l n 1 =r n 1 (StayPrefixField) I = L 1 ==L 2 L 2n 1 ==L 2n stayprefix(e, H, L 1 ) = C 1 stayprefix(e, H, L 2n ) = C 2n stayprefix(e, H, I) = C 1 C 2n (StayPrefixIdent) 4
6 E;H C C We use these judgments to translate a constraint into a constraint suitable for the solver. Specifically, each occurrence of an expression of the form L.l, where L refers to a heap reference r, is translated into H(L).l (recursively, as required), and each occurrence of the identity operator == is replaced by ordinary equality. We do not give these rules, because they are straightforward. solve(e, H, C, ρ) = E ;H Solving constraint C in the context of E and H using stay constraints with priority ρ produces the new environment and heap E and H. This judgment represents one phase of constraint solving either solving value constraints or identity constraints. stay(e, ρ) = C E stay(h, ρ) = C H E;H C C E ;H = (C C E C H ) solve(e, H, C, ρ) = E ;H (Solve) <E H C I s> <E H C I > Execution starting from configuration <E H C I s> ends in state <E H C I >. A configuration defining the state of an execution includes a concrete context, represented by the environment and heap, a symbolic context, represented by the constraint and identity constraint stores, and a statement to be executed. The environment, heap, and statement are standard, while the constraint stores are not part of the state of a computation in most languages. Intuitively, the environment and heap come from constraint solving during the evaluation of the immediately preceding statement, and the constraint records the always constraints that have been declared so far during execution. Note that our execution implicitly gets stuck if the solver cannot produce a model. The rule below describes the semantics of assignments. We employ a two-phase process. First the identity constraints are solved in the context of the new assignment. This phase propagates the effect of the assignment through the identities, potentially changing the structures of objects as well as the relationships among objects in the environment and heap. In the second phase, the value constraints are typechecked against the new environment and heap resulting from the first phase. If they are well typed, then we proceed to solve them. This phase can change the values of primitives but will not modify the structure of any object. Implicitly this rule gets stuck if either a) the identity constraints cannot be solved, b) the value constraints do not typecheck, or c) the value constraints cannot be solved. A practical implementation would add explicit exceptions for these cases that the programmer could handle. E;H e v stayprefix(e, H, L) = C L stayprefix(e, H, I) = C I solve(e, H, C L C I L=v I, weak) = E ;H E ;H C solve(e, H, C L=v, required) = E ;H <E H C I L := e> <E H C I> (S-Asgn) The next rule describes the semantics of object creation, which is straightforward. For simplicity we require a new object to be initially assigned to a fresh variable, but this is no loss of expressiveness. 5
7 E;H e 1 v n E;H e n v n E(x) H(r) E = E {(x, r)} H = H {(r, {l 1 :v 1,...,l n :v n })} <E H C I x := new {l 1 :e 1,...,l n :e n }> <E H C I> (S-AsgnNew) The next two rules describe the semantics of identity constraints. The rules require than identity constraint already be satisfied when it is asserted; hence the environment and heap are unchanged. E;H L 0 v <E H C I once L 0 E;H L 1 v == L 1 > <E H C I> (S-OnceIdentity) <E H C I once L 0 == L 1 > <E H C I> I = I L 0 == L 1 <E H C I always L 0 == L 1 > <E H C I > (S-AlwaysIdentity) The following two rules describe the semantics of value constraints. Recall that these constraints cannot contain identity constraints in them (because identity constraints do not typecheck). As we show later, solving value constraints cannot change the structure of any objects on the environment and heap. E;H C 0 solve(e, H, C C 0, required) = E ;H <E H C I once C 0 > <E H C I> (S-Once) <E H C I once C 0 > <E H C I> C = C C 0 <E H C I always C 0 > <E H C I> (S-Always) The remaining rules are standard for imperative languages, only augmented with constraint stores, and are only given for completeness. <E H C I skip> <E H C I> <E H C I s 1 > <E H C I > <E H C I s 2 > <E H C I > <E H C I s 1 ;s 2 > <E H C I > E;H e true <E H C I s 1 > <E H C I > <E H C I if e then s 1 else s 2 > <E H C I > E;H e false <E H C I s 2 > <E H C I > <E H C I if e then s 1 else s 2 > <E H C I > E;H e true <E C H I s> <E H C I > <E H C I while e do s> <E H C I > <E H C I while e do s> <E H C I > (S-Skip) (S-Seq) (S-IfThen) (S-IfElse) (S-WhileDo) E;H e false <E H C I while e do s> <E H C I> (S-WhileSkip) 6
8 1.3 Properties Here we state and prove two key theorems about our formalism. We assume that a given configuration E H C I is well formed, meaning that it satisfies these sanity conditions: any object reference appearing in the range of E also appears in the domain of H any object reference appearing in the range of H also appears in the domain of H for all variables x in the domain of E there is some type T such that E;H x : T E;H C E;H I true Well-formedness follows from the assumptions made on the constraint solver described earlier. The first theorem formalizes the idea that any solution to a value constraint preserves the structures of the objects on the environment and heap: Theorem 1 (Structure Preservation) If <E H C I s> <E H C I > and s either has the form once C 0 or always C 0 and E;H C 0 and E;H L : T, then E ;H L : T. Proof. If s has the form once C 0 then the result follows by Lemma 1. If s has the form always C 0, then since <E H C I s> <E H C I > and C 0 is not an identity test, by rule S-Always we have <E H C I once C 0 > <E H C I>. Then again the result follows from Lemma 1. Lemma 1 If <E H C I once C 0 > <E H C I > and E;H C 0 and E;H L : T, then E ;H L : T. Proof. Since <E H C I once C 0 > <E H C I > and C 0 is not an identity test, by S-Once we have that E;H C 0 and solve(e, H, C C 0, required) = E ;H. By the assumption of well-formedness we have E;H C so by T-Conjunction also E;H C C 0. Therefore the result follows from Lemma 2. Lemma 2 If E;H C and solve(e, H, C, required) = E ;H and E;H L : T, then E ;H L : T. Proof. Since solve(e, H, C, required) = E ;H by Solve we have that stay(e, required) = C Es and stay(h, required) = C Hs and E;H C C and E ;H = (C C Es C Hs ). We prove this lemma by structural induction on T. By Lemma 3 there exists a value v such that E;H L v and E;H v : T. Then by Lemma 4 there exists a value v such that E ;H L v. Furthermore, if v is an object reference r, then also v = r. Case analysis on the form of v : Case v is a constant c. Then also v is a constant c. Since E;H v : T, the last rule in this derivation must be T-Const so T is PrimitiveType and the result follows from T-Const. Case v is a reference r. Since E ;H L v by Lemma 5 there is a type T such that E ;H L : T and E ;H r : T. So it suffices to show that T = T. Case analysis on the form of v: 7
9 Case v is a constant c. Since E;H v : T, the last rule in this derivation must be T-Const, so we have T = PrimitiveType. Case analysis on the last rule in the derivation of E;H L v: Case E-Variable. Then L is a variable x and E(x) = c. Since stay(e, required) = C Es, by StayEnv we have that C Es includes a conjunct C x such that stay(x=c, required) = C x, and by StayConst C x has the form weak x=c. Since E ;H L r, the last rule in this derivation must be E-Variable, so we have E (x) = r. We know that assigning x to c satisfies the weak stay constraint above. Therefore there must be some constraint on x in C that causes the change in value for x from c to r. Case E-Field. Then L has the form L 0.l i and E;H L 0 r 0 and H(r 0 ) = {l 1 :v 1,...,l n :v n } and 1 i n and r = v i. Since stay(h, required) = C Hs, by StayHeap we have C Hs includes a conjunct C r0 such that stay(r 0 ={l 1 :v 1,...,l n :v n }, required) = C r0. By StayObject C r0 has the form (required H(r 0 )={l 1 :x 1,...,l n :x n }) C 1 C n, where x 1... x n are fresh variables and stay(x i =v i, required) = C i. Then by StayConst C i has the form weak x i =c. Since E;H L 0 r 0, by Lemma 4 we have E ;H L 0 r 0. Since E ;H L r, the last rule in this derivation must be E-Field, so we have that H (r 0 ) = {l 1 :v 1,...,l n :v n} where v i, and hence x i is r. We know that assigning x i to c satisfies the weak stay constraint above. Therefore there must be some constraint on an l-value of the form L 00.l i in C, where E;H L 00 r 0, that causes the change in value for x i from c to r. Therefore in either case, there must be some constraint on an l-value L in C, where E;H L c but E ;H L r. By Lemma 5 there is some T such that E;H L : T and E;H c : T. The last rule in the derivation of E;H c : T must be T-Const so T is PrimitiveType. We argue a contradiction by case analysis of the immediate parent expression of any occurrence of L in C. We are given E;H C so this parent expression must also be well typed. Case L.l. Then by T-Field L must have a record type, contradicting the fact that E;H L : PrimitiveType. Case L is an immediate subexpression of an operation. But these operations only apply to primitives, so the solver cannot satisfy them by assigning x to r. Case ρ L. This constraint is only satisfied if x is a boolean, so the solver will not assign x to r. Case v is a reference r. Then r = r. Since E;H v : T, by T-Ref we have that H(r)={l 1 :v 1,...,l n :v n } and E;H v 1 : T 1 E;H v n : T n and T is {l 1 :T 1,...,l n :T n }. By T-Field we have E;H L.l i : T i for each 1 i n, so by induction E ;H L.l i : T i for each 1 i n. Since stay(h, required) = C Hs, by StayHeap we have that C Hs includes a conjunct C r such that stay(r={l 1 :v 1,...,l n :v n }, required) = C r. By StayObject C r has the form (required H(r)={l 1 :x 1,...,l n :x n }) C 1 C n, where x 1... x n are fresh variables and stay(x i =v i, required) = C i. Therefore any solution to (C C Es C Hs ) must map r to an object value of the form {l 1 :v 1,...,l n :v n} in H. Since E ;H L.l i : T i for each 1 i n, by Lemma 3 we have E;H L.l i v i and E;H v i : T i for each 1 i n. Since the last rule in each of these evaluation derivations must be E-Field we have that v i = v i for each 1 i n. Finally, since E ;H r : T, the last rule in this derivation must be T-Ref, so we have that T = {l 1 :T 1,...,l n :T n }. Lemma 3 If E;H L : T, then there exists a value v such that E;H L v and E;H v : T. 8
10 Proof. By structural induction on L: Case L is a variable x: Then by T-Var we have that E(x) = v and E;H v : T. Finally by E-Var we have E;H x v. Case L has the form L.l i : By T-Field we have that E;H L : {l 1 :T 1,...,l n :T n } and 1 i n and T = T i. By induction there exists a value v such that E;H L v and E;H v : {l 1 :T 1,...,l n :T n }. Case analysis of the derivation of E;H v : {l 1 :T 1,...,l n :T n }: Case T-Const: Then {l 1 :T 1,...,l n :T n } = PrimitiveType and we have a contradiction. Case T-Ref: Then we have v = r and H(r)={l 1 :v 1,...,l n :v n } and E;H v i : T i. Finally, by E-Field we have E;H L.l i v i. Lemma 4 If E;H C and solve(e, H, C, required) = E ;H and E;H L v, then there exists a value v such that E ;H L v. Furthermore, if v is an object reference r, then also v = r. Proof. Since solve(e, H, C, required) = E ;H by Solve we have that stay(e, required) = C Es and stay(h, required) = C Hs and E;H C C and E ;H = (C C Es C Hs ). We proceed by structural induction on L: Case L is a variable x. Since E;H L v, by E-Var we have that E(x) = v. Then since stay(e, required) = C Es, by StayEnv we have that C Es includes a conjunct C x such that stay(x=v, required) = C x. Case analysis of the rule used in the derivation of stay(x=v, required) = C x : StayConst: Then C x has the form weak x=v and v is a constant c. Therefore the variable x appears in the constraint (C C Es C Hs ), so any solution to the constraint must include some value v for x in E, and the result follows by E-Var. StayRef: Then C x has the form required x=v and v is an object reference r. Therefore any solution to (C C Es C Hs ) must map x to r in E, and the result follows by E-Var. Case L has the form L.l i. Then by E-Field we have E;H L r and H(r) = {l 1 :v 1,...,l n :v n } and 1 i n and v = v i. By induction we have E ;H L r. Since stay(h, required) = C Hs, by StayHeap we have that C Hs includes a conjunct C r such that stay(r={l 1 :v 1,...,l n :v n }, required) = C r. By StayObject C r has the form (required H(r)={l 1 :x 1,...,l n :x n }) C 1 C n, where x 1... x n are fresh variables and stay(x i =v i, required) = C i. Therefore any solution to (C C Es C Hs ) must map r to an object value of the form {l 1 :v 1,...,l n :v n} in H, where v i is the value assigned to variable x i by the solution. Therefore by E-Field we have E;H L.l i v i. Finally suppose v i is an object reference r i. Then by StayRef C i has the form required x i = r i so any solution to the constraints must map x i to r i, so also v i is r i. Lemma 5 If E;H L v then there is some type T such that E;H L : T and E;H v : T. Proof. By induction on the derivation of E;H L v: 9
11 Case E-Variable. Then L is a variable x and E(x) = v. Then by well formedness there is some type T such that E;H x : T and by T-Var also E;H v : T. Case E-Field. Then L has the form L.l i and E;H L r and H(r) = {l 1 :v 1,...,l n :v n } and 1 i n and v = v i. By induction there is some type T such that E;H L : T and E;H r : T. Then by T-Ref T has the form {l 1 :T 1,...,l n :T n } where E;H v i : T i. Then by T-Field also E;H L : T i. Lemma 6 If E;H L r then r is in the domain of H. Proof. Case analysis on the last rule in the evaluation derivation. Case E-Variable. Then L is a variable x and E(x) = r. Then the result follows from the assumption that E and H are well formed. Case E-Field. Then L has the form L.l i and E;H L r and H(r) = {l 1 :v 1,...,l n :v n } and 1 i n and r = v i. Then the result follows from the assumption that E and H are well formed. The second theorem formalizes the idea that all solutions to an assignment will produce structurally equivalent environments and heaps: Theorem 2 (Structural Determinism) If <E H C I L := e> <E 1 H 1 C 1 I 1 > and <E H C I L := e> <E 2 H 2 C 2 I 2 > and E;H x : T 0, then there exists a type T such that E 1 ;H 1 x : T and E 2 ;H 2 x : T. Proof. By S-Asgn we have E;H e v and stayprefix(e, H, L) = C L and stayprefix(e, H, I) = C I and solve(e, H, C L C I L=v I, weak) = E 1;H 1 and E 1;H 1 C and solve(e 1, H 1, C L=v, required) = E 1 ;H 1. Also by S-Asgn and Lemma 13 we have solve(e, H, C L C I L=v I, weak) = E 2;H 2 and E 2;H 2 C and solve(e 2, H 2, C L=v, required) = E 2 ;H 2. By Lemma 7 we have that E 1 = E 2 and H 1 = H 2. Since E;H x : T 0, by T-Var x is in the domain of E, so it is also in the domain of E 1 and by E-Var we have E 1;H 1 x v x where E 1(x) = v x. Then by Lemma 5 there is some type T such that E 1;H 1 v x : T and E 1;H 1 x : T. Finally by Lemma 2 we have that E 1 ;H 1 x : T and E 2 ;H 2 x : T, so the result is shown with T = T. Definition 1 We say that L 1 and L 2 are aliases given E and H if either: L 1 and L 2 are the same variable x L 1 has the form L 1.l and L 2 has the form L 2.l and there is a reference r such that E;H L 1 r and E;H L 2 r Definition 2 We say that L and L are the operands of the constraint L == L. 10
12 Definition 3 We define the induced graph of I and L given E and H as follows. Let S be the set that includes L as well as all operands of identity tests in I. Partition S into equivalence classes defined by the alias relation: L 1 and L 2 are in the same equivalence class if and only if they are aliases given E and H. Then the induced graph has one node per equivalence class and an undirected edge between nodes N 1 and N 2 if there is a conjunct L 1 ==L 2 in I such that L 1 belongs to node N 1 and L 2 belongs to node N 2. Definition 4 We say that a node in the induced graph of I and L given E and H is relevant if it is reachable from L s node in the graph; an l-value is relevant if its node in the graph is relevant. Definition 5 The relevant update of E and H for I and L=v is the environment E and heap H that are identical to E and H except that for each relevant l-value L 0 in the induced graph of I and L given E and H: If L 0 is a variable x, then E (x) = v. If L 0 has the form L 0.l and E;H L 0 r, then E ;H r.l v. Lemma 7 If stayprefix(e, H, L) = C L and stayprefix(e, H, I) = C I and solve(e, H, C L C I L=v I, weak) = E 1 ;H 1 and solve(e, H, C L C I L=v I, weak) = E 2 ;H 2, then E 1 = E 2 and H 1 = H 2. Proof. By Solve we have stay(e, weak) = C E and stay(h, weak) = C H and E;H (C L C I L=v I) C and E ;H = (C C E C H ) and E ;H = (C C E C H ). By Lemma 9, E and H include all the updates of the relevant update (which we will call E 0 and H 0 ) of E and H for I and L=v, and similarly for E and H. To complete the proof we argue that both of these solutions are in fact identical to the relevant update. WLOG we consider E and H. By Lemma 8 the relevant update of E and H for I and L=v is a solution to the constraint C C E C H. Therefore if E and H is not the relevant update, then by Definition 5 either: there is a variable x such that E 0 (x) = E(x) but E (x) has a different value there is a reference r and field label l such that H 0 (r).l = H(r).l but H (r).l has a different value Consider the former. Since stay(e, weak) = C E, by StayEnv, StayConst, and StayRef we have that C E includes a weak constraint x=v x, where E(x) = v x. Since E and H include all the updates of the relevant update, E and H satisfy strictly fewer weak constraints than the relevant update, contradicting the optimality of E and H. Similarly, consider the latter. Since stay(h, weak) = C H, by StayHeap and StayObject C H includes a required constraint H(r)={l 1 :x 1,...,l n :x n } where the x i variables are fresh and l is some l i. Then by StayConst and StayRef there is a weak constraint of the form x i = v i where H(r).l i = v i. Since E and H include all the updates of the relevant update, E and H satisfy strictly fewer weak constraints than the relevant update, contradicting the optimality of E and H. Lemma 8 If stay(e, weak) = C E and stay(h, weak) = C H and stayprefix(e, H, L) = C L and stayprefix(e, H, I) = C I and E;H (C L C I L=v I) C and the constraint C C E C H is satisfiable, then the relevant update E and H of E and H for I and L=v is a solution to the constraint C C E C H. 11
13 Proof. It suffices to show that all required constraints in C C E C H are satisfied in E and H. We consider the various constraints in turn: C E : Since stay(e, weak) = C E, by StayEnv, StayConst, and StayRef there are no required constraints in C E, so all required constraints are satisfied vacuously. C H : Since stay(h, weak) = C H, by StayHeap, StayObject, StayConst, and StayRef the only required constraints in C H have the form H(r)={l 1 :x 1,...,l n :x n } where the x i variables are fresh and H maps r to some value of the form {l 1 :v 1,...,l n :v n }. By Definition 5 also H maps r to a value of the form {l 1 :v 1,...,l n :v n} so the constraint is satisfied. C L : By StayPrefixField the conjuncts in C L have the form x=v or r.l=v. Suppose the relevant update fails to satisfy one of these conjuncts. We consider each form in turn: x=v: Then the relevant update maps x to some v v in E. But by Solve and Lemma 9 any solution to the constraint C C E C H must map x to v in the environment, which violates the constraint x=v. So there must be no solution to the constraints, contradicting our assumption of satisfiability. r.l=v: Then the relevant update maps r.l to some v v in H. But by Solve and Lemma 9 any solution to the constraint C C E C H must map r.l to v in the environment, which violates the constraint r.l=v. So there must be no solution to the constraints, contradicting our assumption of satisfiability. C I : By StayPrefixIdent the conjuncts in C L have the form x=v or r.l=v. identical to that above for the C L constraint. So the argument is L=v: By Definitions 3 and 5 we have that L is relevant for I and L given E and H. Then by Lemma 10 we have E ;H L v, so by E-Op and the semantics of equality we have E ;H L=v true. I: Consider a conjunct L 0 == L 1 in I. We have two cases: L 0 is relevant for I and L given E and H. By Definitions 4 and 3, L 1 is also relevant. Then by Lemma 10 we have E ;H L 0 v and E ;H L 1 v, so by E-IdentityTrue we have E ;H L 0 ==L 1 true. L 0 is not relevant for I and L given E and H. By Definitions 4 and 3, L 1 is also not relevant. By well formedness we have E;H L 0 ==L 1 true, so by E-IdentityTrue there is some v 0 such that E;H L 0 v 0 and E;H L 1 v 0. Then by Lemma 11 we have E ;H L 0 v 0 and E ;H L 1 v 0, so by E-IdentityTrue we have E ;H L 0 ==L 1 true. Lemma 9 If stayprefix(e, H, L) = C L and stayprefix(e, H, I) = C I and solve(e, H, C L C I L=v I, weak) = E ;H and L 0 is a relevant l-value of I and L given E and H, then E ;H L 0 v and: If L 0 is a variable x, then E (x) = v. If L 0 has the form L 0.l and E;H L 0 r, then E ;H r.l v. Proof. By Definition 4, we know that L 0 s node in the induced graph for I and L given E and H is reachable from L s node. The proof proceeds by induction on the length k of the path between these nodes. 12
14 Case k = 0. Then by Definition 3, L and L 0 are aliases given E and H. Case analysis on the structure of L: Case L is a variable x. Then by Definition 1 also L 0 is x. Since solve(e, H, C L C I L=v I, weak) = E ;H we must have E ;H x=v true, so by E-Op and the semantics of equality we have E ;H x v. Then by E-Var also E (x) = v. Case L has the form L.l. Then by Definition 1 also L 0 has the form L 0.l and E;H L r and E;H L 0 r. We are given stayprefix(e, H, L) = C L. Then since solve(e, H, C L C I L=v I, weak) = E ;H we must have E ;H C L true. Similarly we are given stayprefix(e, H, I) = C I so by StayPrefixIdent we have also stayprefix(e, H, L 0 ) = C L0 where C L0 is a conjunct within C I. Then since solve(e, H, C L C I L=v I, weak) = E ;H we must have E ;H C L0 true. So by Lemma 13 and Lemma 12 we have E ;H L r and E ;H L 0 r. We also know E ;H L=v true, so by E-Op and the semantics of equality we have E ;H L v. Then by E-Field we have H (r) is a record whose l field has value v. Then by E-Field also E ;H r.l v and E ;H L 0 v. Case k > 0. Then by Definition 3 there is some neighbor node of L 0 s node that is only k 1 hops away from L s node, which contains an l-value L 1 such that L 0 == L 1 or vice versa is in I, where L 0 is an alias of L 0 given E and H. By induction we have E ;H L 1 v. Then since the identities in I are satisfied in E and H, by E-IdentityTrue also E ;H L 0 v. Case analysis on the structure of L 0: Case L 0 is a variable x. Then by Definition 1 also L 0 is x and by E-Var also E (x) = v. Case L 0 has the form L.l. Then by Definition 1 also L 0 has the form L 00.l and E;H L r and E;H L 00 r. We are given stayprefix(e, H, I) = C I so by StayPrefixIdent we have also stayprefix(e, H, L 0) = C L 0 where C L 0 is a conjunct within C I. Then since solve(e, H, C L C I L=v I, weak) = E ;H we must have E ;H C L 0 true. By the same argument we must also have E ;H C L0 true where stayprefix(e, H, L 0 ) = C L0. So by Lemma 13 and Lemma 12 we have E ;H L r and E ;H L 00 r. Then since E ;H L 0 v by E-Field we have H (r) is a record whose l field has value v. Then by E-Field also E ;H r.l v and E ;H L 0 v. Lemma 10 If stayprefix(e, H, L) = C L and stayprefix(e, H, I) = C I and E and H is the relevant update of E and H for I and L=v and E ;H C L true and and E ;H C I true and L 0 is a relevant l-value for I and L given E and H, then E ;H L 0 v. Proof. Case analysis of the structure of L 0 : Case L 0 is a variable x: By Definition 5 E (x) = v, so the result follows by E-Var. Case L 0 has the form L.l: First we argue that stayprefix(e, H, L 0 ) = C L0 and E ;H C L0 true. If L 0 is L, then these follow from the assumptions of the lemma. Otherwise, by Definition 4 L 0 is an operand in an identity test in I. Then since stayprefix(e, H, I) = C I by StayPrefixIdent we have stayprefix(e, H, L 0 ) = C L0, where C L0 is a conjunct in C I. Then since E ;H C I true also E ;H C L0 true. Then by Lemma 12 there is some r such that E;H L r and E ;H L r. By Lemma 13 and Definition 5 we have E;H r.l v and the result follows by E-Field. 13
15 Lemma 11 If stayprefix(e, H, L) = C L and stayprefix(e, H, I) = C I and E and H is the relevant update of E and H for I and L=v and E ;H C L true and and E ;H C I true and L 0 is an operand of an identity test in I and L 0 is not relevant for I and L given E and H and E;H L 0 v 0, E ;H L 0 v 0. Proof. Case analysis on the structure of L 0 : Case L 0 is a variable x. Since x is not relevant, by Definition 5 the value of x in E is the same as that in Euid. Since E;H L 0 v 0, by E-Var we have E(x) = v 0, so also E (x) = v 0 and the result follows by E-Var. Case L 0 has the form L.l. Since L 0 is an operand in an identity test in I and stayprefix(e, H, I) = C I, by StayPrefixIdent we have stayprefix(e, H, L 0 ) = C L0, where C L0 is a conjunct in C I. Then since E ;H C I true also E ;H C L0 true. Therefore by Lemma 12 there is some r such that E;H L r and E ;H L r. Since E;H L 0 v 0 by E-Field and Lemma 13 we have that H(r ).l is v 0. By Definition 5 H (r ) also has a field with label l, so by E-Field we are done if that field s value is v 0. Suppose not. Then by Definition 5 there is some relevant l-value L 1 of the form L 1.l such that E;H L 1 r. But then by Definition 1 we have that L 0 and L 1 are aliases so they correspond to the same node in the induced graph of I and L given E and H by Definition 3. But then since L 1 is relevant, by Definition 4 so is L 0 and we have a contradiction. Lemma 12 If stayprefix(e, H, L.f) = C and E ;H C true, then there is some reference r such that E;H L r and E ;H L r. Proof. By StayPrefixField we have L.f = x.l l n and n > 0 and E;H x r and E;H x.l 1 r 1 E;H x.l l n 1 r n 1 and C is x=r x.l 1 =r 1 x.l l n 1 =r n 1. Case n = 1. Then L is x and C is x=r. Since E ;H C true, by E-Op and the semantics of equality we have E ;H x v 1 and E ;H r v 2 and v 1 = v 2. By E-Ref we have that v 2 = r, so the result follows. Case n > 1. Then L is x.l l n 1. Since E ;H C true, by E-Op and the semantics of equality we have E ;H L v 1 and E ;H r n 1 v 2 and v 1 = v 2. By E-Ref we have that v 2 = r n 1, so the result follows. Lemma 13 (Determinism) If E;H e v 1 and E;H e v 2 then v 1 = v 2. If stay(e, ρ) = C 1 and stay(e, ρ) = C 2 then C 1 = C 2. If stay(h, ρ) = C 1 and stay(h, ρ) = C 2 then C 1 = C 2. If stayprefix(e, H, L) = C 1 and stayprefix(e, H, L) = C 2 then C 1 = C 2. 14
16 If stayprefix(e, H, I) = C 1 and stayprefix(e, H, I) = C 2 then C 1 = C 2. Proof. Straightforward. 15
Developing a Formal Semantics for Babelsberg: A Step-by-Step Approach
 Developing a Formal Semantics for Babelsberg: A Step-by-Step Approach Tim Felgentreff, Todd Millstein, and Alan Borning VPRI Technical Report TR-2014-002 September 2014 1 Introduction Babelsberg [4] is
Developing a Formal Semantics for Babelsberg: A Step-by-Step Approach Tim Felgentreff, Todd Millstein, and Alan Borning VPRI Technical Report TR-2014-002 September 2014 1 Introduction Babelsberg [4] is
Developing a Formal Semantics for Babelsberg: A Step-by-Step Approach (DRAFT)
 Developing a Formal Semantics for Babelsberg: A Step-by-Step Approach (DRAFT) Tim Felgentreff, Todd Millstein, and Alan Borning Viewpoints Research Institute, 1025 Westwood Blvd 2nd flr, Los Angeles, CA
Developing a Formal Semantics for Babelsberg: A Step-by-Step Approach (DRAFT) Tim Felgentreff, Todd Millstein, and Alan Borning Viewpoints Research Institute, 1025 Westwood Blvd 2nd flr, Los Angeles, CA
Induction and Semantics in Dafny
 15-414 Lecture 11 1 Instructor: Matt Fredrikson Induction and Semantics in Dafny TA: Ryan Wagner Encoding the syntax of Imp Recall the abstract syntax of Imp: a AExp ::= n Z x Var a 1 + a 2 b BExp ::=
15-414 Lecture 11 1 Instructor: Matt Fredrikson Induction and Semantics in Dafny TA: Ryan Wagner Encoding the syntax of Imp Recall the abstract syntax of Imp: a AExp ::= n Z x Var a 1 + a 2 b BExp ::=
Mutable References. Chapter 1
 Chapter 1 Mutable References In the (typed or untyped) λ-calculus, or in pure functional languages, a variable is immutable in that once bound to a value as the result of a substitution, its contents never
Chapter 1 Mutable References In the (typed or untyped) λ-calculus, or in pure functional languages, a variable is immutable in that once bound to a value as the result of a substitution, its contents never
Treewidth and graph minors
 Treewidth and graph minors Lectures 9 and 10, December 29, 2011, January 5, 2012 We shall touch upon the theory of Graph Minors by Robertson and Seymour. This theory gives a very general condition under
Treewidth and graph minors Lectures 9 and 10, December 29, 2011, January 5, 2012 We shall touch upon the theory of Graph Minors by Robertson and Seymour. This theory gives a very general condition under
CS4215 Programming Language Implementation. Martin Henz
 CS4215 Programming Language Implementation Martin Henz Thursday 26 January, 2012 2 Chapter 4 The Language simpl In this chapter, we are exting the language epl in order to provide a more powerful programming
CS4215 Programming Language Implementation Martin Henz Thursday 26 January, 2012 2 Chapter 4 The Language simpl In this chapter, we are exting the language epl in order to provide a more powerful programming
The PCAT Programming Language Reference Manual
 The PCAT Programming Language Reference Manual Andrew Tolmach and Jingke Li Dept. of Computer Science Portland State University September 27, 1995 (revised October 15, 2002) 1 Introduction The PCAT language
The PCAT Programming Language Reference Manual Andrew Tolmach and Jingke Li Dept. of Computer Science Portland State University September 27, 1995 (revised October 15, 2002) 1 Introduction The PCAT language
Treaps. 1 Binary Search Trees (BSTs) CSE341T/CSE549T 11/05/2014. Lecture 19
 CSE34T/CSE549T /05/04 Lecture 9 Treaps Binary Search Trees (BSTs) Search trees are tree-based data structures that can be used to store and search for items that satisfy a total order. There are many types
CSE34T/CSE549T /05/04 Lecture 9 Treaps Binary Search Trees (BSTs) Search trees are tree-based data structures that can be used to store and search for items that satisfy a total order. There are many types
Programming Languages Fall 2014
 Programming Languages Fall 2014 Lecture 7: Simple Types and Simply-Typed Lambda Calculus Prof. Liang Huang huang@qc.cs.cuny.edu 1 Types stuck terms? how to fix it? 2 Plan First I For today, we ll go back
Programming Languages Fall 2014 Lecture 7: Simple Types and Simply-Typed Lambda Calculus Prof. Liang Huang huang@qc.cs.cuny.edu 1 Types stuck terms? how to fix it? 2 Plan First I For today, we ll go back
We defined congruence rules that determine the order of evaluation, using the following evaluation
 CS 4110 Programming Languages and Logics Lectures #21: Advanced Types 1 Overview In this lecture we will extend the simply-typed λ-calculus with several features we saw earlier in the course, including
CS 4110 Programming Languages and Logics Lectures #21: Advanced Types 1 Overview In this lecture we will extend the simply-typed λ-calculus with several features we saw earlier in the course, including
Discharging and reducible configurations
 Discharging and reducible configurations Zdeněk Dvořák March 24, 2018 Suppose we want to show that graphs from some hereditary class G are k- colorable. Clearly, we can restrict our attention to graphs
Discharging and reducible configurations Zdeněk Dvořák March 24, 2018 Suppose we want to show that graphs from some hereditary class G are k- colorable. Clearly, we can restrict our attention to graphs
SEQUENCES, MATHEMATICAL INDUCTION, AND RECURSION
 CHAPTER 5 SEQUENCES, MATHEMATICAL INDUCTION, AND RECURSION Alessandro Artale UniBZ - http://www.inf.unibz.it/ artale/ SECTION 5.5 Application: Correctness of Algorithms Copyright Cengage Learning. All
CHAPTER 5 SEQUENCES, MATHEMATICAL INDUCTION, AND RECURSION Alessandro Artale UniBZ - http://www.inf.unibz.it/ artale/ SECTION 5.5 Application: Correctness of Algorithms Copyright Cengage Learning. All
Chapter 13: Reference. Why reference Typing Evaluation Store Typings Safety Notes
 Chapter 13: Reference Why reference Typing Evaluation Store Typings Safety Notes References Computational Effects Also known as side effects. A function or expression is said to have a side effect if,
Chapter 13: Reference Why reference Typing Evaluation Store Typings Safety Notes References Computational Effects Also known as side effects. A function or expression is said to have a side effect if,
CS2 Algorithms and Data Structures Note 10. Depth-First Search and Topological Sorting
 CS2 Algorithms and Data Structures Note 10 Depth-First Search and Topological Sorting In this lecture, we will analyse the running time of DFS and discuss a few applications. 10.1 A recursive implementation
CS2 Algorithms and Data Structures Note 10 Depth-First Search and Topological Sorting In this lecture, we will analyse the running time of DFS and discuss a few applications. 10.1 A recursive implementation
1 Introduction. 3 Syntax
 CS 6110 S18 Lecture 19 Typed λ-calculus 1 Introduction Type checking is a lightweight technique for proving simple properties of programs. Unlike theorem-proving techniques based on axiomatic semantics,
CS 6110 S18 Lecture 19 Typed λ-calculus 1 Introduction Type checking is a lightweight technique for proving simple properties of programs. Unlike theorem-proving techniques based on axiomatic semantics,
A proof-producing CSP solver: A proof supplement
 A proof-producing CSP solver: A proof supplement Report IE/IS-2010-02 Michael Veksler Ofer Strichman mveksler@tx.technion.ac.il ofers@ie.technion.ac.il Technion Institute of Technology April 12, 2010 Abstract
A proof-producing CSP solver: A proof supplement Report IE/IS-2010-02 Michael Veksler Ofer Strichman mveksler@tx.technion.ac.il ofers@ie.technion.ac.il Technion Institute of Technology April 12, 2010 Abstract
Joint Entity Resolution
 Joint Entity Resolution Steven Euijong Whang, Hector Garcia-Molina Computer Science Department, Stanford University 353 Serra Mall, Stanford, CA 94305, USA {swhang, hector}@cs.stanford.edu No Institute
Joint Entity Resolution Steven Euijong Whang, Hector Garcia-Molina Computer Science Department, Stanford University 353 Serra Mall, Stanford, CA 94305, USA {swhang, hector}@cs.stanford.edu No Institute
Chapter 13: Reference. Why reference Typing Evaluation Store Typings Safety Notes
 Chapter 13: Reference Why reference Typing Evaluation Store Typings Safety Notes References Mutability So far, what we discussed does not include computational effects (also known as side effects). In
Chapter 13: Reference Why reference Typing Evaluation Store Typings Safety Notes References Mutability So far, what we discussed does not include computational effects (also known as side effects). In
SEQUENCES, MATHEMATICAL INDUCTION, AND RECURSION
 CHAPTER 5 SEQUENCES, MATHEMATICAL INDUCTION, AND RECURSION Copyright Cengage Learning. All rights reserved. SECTION 5.5 Application: Correctness of Algorithms Copyright Cengage Learning. All rights reserved.
CHAPTER 5 SEQUENCES, MATHEMATICAL INDUCTION, AND RECURSION Copyright Cengage Learning. All rights reserved. SECTION 5.5 Application: Correctness of Algorithms Copyright Cengage Learning. All rights reserved.
The SPL Programming Language Reference Manual
 The SPL Programming Language Reference Manual Leonidas Fegaras University of Texas at Arlington Arlington, TX 76019 fegaras@cse.uta.edu February 27, 2018 1 Introduction The SPL language is a Small Programming
The SPL Programming Language Reference Manual Leonidas Fegaras University of Texas at Arlington Arlington, TX 76019 fegaras@cse.uta.edu February 27, 2018 1 Introduction The SPL language is a Small Programming
Matching Algorithms. Proof. If a bipartite graph has a perfect matching, then it is easy to see that the right hand side is a necessary condition.
 18.433 Combinatorial Optimization Matching Algorithms September 9,14,16 Lecturer: Santosh Vempala Given a graph G = (V, E), a matching M is a set of edges with the property that no two of the edges have
18.433 Combinatorial Optimization Matching Algorithms September 9,14,16 Lecturer: Santosh Vempala Given a graph G = (V, E), a matching M is a set of edges with the property that no two of the edges have
CS558 Programming Languages
 CS558 Programming Languages Fall 2016 Lecture 7a Andrew Tolmach Portland State University 1994-2016 Values and Types We divide the universe of values according to types A type is a set of values and a
CS558 Programming Languages Fall 2016 Lecture 7a Andrew Tolmach Portland State University 1994-2016 Values and Types We divide the universe of values according to types A type is a set of values and a
Chapter 3. The While programming language
 Chapter 3 The While programming language 1 Contents 3 The While programming language 1 3.1 Big-step semantics........................... 2 3.2 Small-step semantics.......................... 9 3.3 Properties................................
Chapter 3 The While programming language 1 Contents 3 The While programming language 1 3.1 Big-step semantics........................... 2 3.2 Small-step semantics.......................... 9 3.3 Properties................................
1 Dijkstra s Algorithm
 Lecture 11 Dijkstra s Algorithm Scribes: Himanshu Bhandoh (2015), Virginia Williams, and Date: November 1, 2017 Anthony Kim (2016), G. Valiant (2017), M. Wootters (2017) (Adapted from Virginia Williams
Lecture 11 Dijkstra s Algorithm Scribes: Himanshu Bhandoh (2015), Virginia Williams, and Date: November 1, 2017 Anthony Kim (2016), G. Valiant (2017), M. Wootters (2017) (Adapted from Virginia Williams
CS 6110 S11 Lecture 25 Typed λ-calculus 6 April 2011
 CS 6110 S11 Lecture 25 Typed λ-calculus 6 April 2011 1 Introduction Type checking is a lightweight technique for proving simple properties of programs. Unlike theorem-proving techniques based on axiomatic
CS 6110 S11 Lecture 25 Typed λ-calculus 6 April 2011 1 Introduction Type checking is a lightweight technique for proving simple properties of programs. Unlike theorem-proving techniques based on axiomatic
6. Hoare Logic and Weakest Preconditions
 6. Hoare Logic and Weakest Preconditions Program Verification ETH Zurich, Spring Semester 07 Alexander J. Summers 30 Program Correctness There are many notions of correctness properties for a given program
6. Hoare Logic and Weakest Preconditions Program Verification ETH Zurich, Spring Semester 07 Alexander J. Summers 30 Program Correctness There are many notions of correctness properties for a given program
A Semantics to Generate the Context-sensitive Synchronized Control-Flow Graph (extended)
 A Semantics to Generate the Context-sensitive Synchronized Control-Flow Graph (extended) Marisa Llorens, Javier Oliver, Josep Silva, and Salvador Tamarit Universidad Politécnica de Valencia, Camino de
A Semantics to Generate the Context-sensitive Synchronized Control-Flow Graph (extended) Marisa Llorens, Javier Oliver, Josep Silva, and Salvador Tamarit Universidad Politécnica de Valencia, Camino de
Type Systems Winter Semester 2006
 Type Systems Winter Semester 2006 Week 9 December 13 December 13, 2006 - version 1.0 Plan PREVIOUSLY: unit, sequencing, let, pairs, sums TODAY: 1. recursion 2. state 3.??? NEXT: exceptions? NEXT: polymorphic
Type Systems Winter Semester 2006 Week 9 December 13 December 13, 2006 - version 1.0 Plan PREVIOUSLY: unit, sequencing, let, pairs, sums TODAY: 1. recursion 2. state 3.??? NEXT: exceptions? NEXT: polymorphic
The Encoding Complexity of Network Coding
 The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
The Rule of Constancy(Derived Frame Rule)
 The Rule of Constancy(Derived Frame Rule) The following derived rule is used on the next slide The rule of constancy {P } C {Q} {P R} C {Q R} where no variable assigned to in C occurs in R Outline of derivation
The Rule of Constancy(Derived Frame Rule) The following derived rule is used on the next slide The rule of constancy {P } C {Q} {P R} C {Q R} where no variable assigned to in C occurs in R Outline of derivation
Quiz 1: Solutions J/18.400J: Automata, Computability and Complexity. Nati Srebro, Susan Hohenberger
 6.45J/8.4J: utomata, Computability and Complexity Quiz : Solutions Prof. Nancy Lynch Nati Srebro, Susan Hohenberger Please write your name in the upper corner of each page. (2 Points) Q- Problem : True
6.45J/8.4J: utomata, Computability and Complexity Quiz : Solutions Prof. Nancy Lynch Nati Srebro, Susan Hohenberger Please write your name in the upper corner of each page. (2 Points) Q- Problem : True
Part VI. Imperative Functional Programming
 Part VI Imperative Functional Programming Chapter 14 Mutable Storage MinML is said to be a pure language because the execution model consists entirely of evaluating an expression for its value. ML is
Part VI Imperative Functional Programming Chapter 14 Mutable Storage MinML is said to be a pure language because the execution model consists entirely of evaluating an expression for its value. ML is
Semantics. A. Demers Jan This material is primarily from Ch. 2 of the text. We present an imperative
 CS411 Notes 1: IMP and Large Step Operational Semantics A. Demers 23-25 Jan 2001 This material is primarily from Ch. 2 of the text. We present an imperative language called IMP; wegive a formal definition
CS411 Notes 1: IMP and Large Step Operational Semantics A. Demers 23-25 Jan 2001 This material is primarily from Ch. 2 of the text. We present an imperative language called IMP; wegive a formal definition
Programming Languages Fall 2013
 Programming Languages Fall 2013 Lecture 3: Induction Prof. Liang Huang huang@qc.cs.cuny.edu Recursive Data Types (trees) data Ast = ANum Integer APlus Ast Ast ATimes Ast Ast eval (ANum x) = x eval (ATimes
Programming Languages Fall 2013 Lecture 3: Induction Prof. Liang Huang huang@qc.cs.cuny.edu Recursive Data Types (trees) data Ast = ANum Integer APlus Ast Ast ATimes Ast Ast eval (ANum x) = x eval (ATimes
Semantics via Syntax. f (4) = if define f (x) =2 x + 55.
 1 Semantics via Syntax The specification of a programming language starts with its syntax. As every programmer knows, the syntax of a language comes in the shape of a variant of a BNF (Backus-Naur Form)
1 Semantics via Syntax The specification of a programming language starts with its syntax. As every programmer knows, the syntax of a language comes in the shape of a variant of a BNF (Backus-Naur Form)
1 The language χ. Models of Computation
 Bengt Nordström, 1 2017-10-13 Department of Computing Science, Chalmers and University of Göteborg, Göteborg, Sweden 1 The language χ The main purpose of the language χ is to illustrate some basic results
Bengt Nordström, 1 2017-10-13 Department of Computing Science, Chalmers and University of Göteborg, Göteborg, Sweden 1 The language χ The main purpose of the language χ is to illustrate some basic results
COL351: Analysis and Design of Algorithms (CSE, IITD, Semester-I ) Name: Entry number:
 Name: Entry number: There are 6 questions for a total of 75 points. 1. Consider functions f(n) = 10n2 n + 3 n and g(n) = n3 n. Answer the following: (a) ( 1 / 2 point) State true or false: f(n) is O(g(n)).
Name: Entry number: There are 6 questions for a total of 75 points. 1. Consider functions f(n) = 10n2 n + 3 n and g(n) = n3 n. Answer the following: (a) ( 1 / 2 point) State true or false: f(n) is O(g(n)).
Byzantine Consensus in Directed Graphs
 Byzantine Consensus in Directed Graphs Lewis Tseng 1,3, and Nitin Vaidya 2,3 1 Department of Computer Science, 2 Department of Electrical and Computer Engineering, and 3 Coordinated Science Laboratory
Byzantine Consensus in Directed Graphs Lewis Tseng 1,3, and Nitin Vaidya 2,3 1 Department of Computer Science, 2 Department of Electrical and Computer Engineering, and 3 Coordinated Science Laboratory
Meeting13:Denotations
 Meeting13:Denotations Announcements Homework 3 due next week Friday at 6:00pm Homework2Comments Time: 29.2 hours avg Difficulty: 5.4 avg Issues Length? (Part 2 out Wed instead of Mon) Misunderstanding
Meeting13:Denotations Announcements Homework 3 due next week Friday at 6:00pm Homework2Comments Time: 29.2 hours avg Difficulty: 5.4 avg Issues Length? (Part 2 out Wed instead of Mon) Misunderstanding
Polymorphic lambda calculus Princ. of Progr. Languages (and Extended ) The University of Birmingham. c Uday Reddy
 06-02552 Princ. of Progr. Languages (and Extended ) The University of Birmingham Spring Semester 2016-17 School of Computer Science c Uday Reddy2016-17 Handout 6: Polymorphic Type Systems 1. Polymorphic
06-02552 Princ. of Progr. Languages (and Extended ) The University of Birmingham Spring Semester 2016-17 School of Computer Science c Uday Reddy2016-17 Handout 6: Polymorphic Type Systems 1. Polymorphic
Hoare logic. WHILE p, a language with pointers. Introduction. Syntax of WHILE p. Lecture 5: Introduction to separation logic
 Introduction Hoare logic Lecture 5: Introduction to separation logic In the previous lectures, we have considered a language, WHILE, where mutability only concerned program variables. Jean Pichon-Pharabod
Introduction Hoare logic Lecture 5: Introduction to separation logic In the previous lectures, we have considered a language, WHILE, where mutability only concerned program variables. Jean Pichon-Pharabod
Softwaretechnik. Lecture 03: Types and Type Soundness. Peter Thiemann. University of Freiburg, Germany SS 2008
 Softwaretechnik Lecture 03: Types and Type Soundness Peter Thiemann University of Freiburg, Germany SS 2008 Peter Thiemann (Univ. Freiburg) Softwaretechnik SWT 1 / 35 Table of Contents Types and Type correctness
Softwaretechnik Lecture 03: Types and Type Soundness Peter Thiemann University of Freiburg, Germany SS 2008 Peter Thiemann (Univ. Freiburg) Softwaretechnik SWT 1 / 35 Table of Contents Types and Type correctness
Computer Science Technical Report
 Computer Science Technical Report Feasibility of Stepwise Addition of Multitolerance to High Atomicity Programs Ali Ebnenasir and Sandeep S. Kulkarni Michigan Technological University Computer Science
Computer Science Technical Report Feasibility of Stepwise Addition of Multitolerance to High Atomicity Programs Ali Ebnenasir and Sandeep S. Kulkarni Michigan Technological University Computer Science
COMP 382: Reasoning about algorithms
 Spring 2015 Unit 2: Models of computation What is an algorithm? So far... An inductively defined function Limitation Doesn t capture mutation of data Imperative models of computation Computation = sequence
Spring 2015 Unit 2: Models of computation What is an algorithm? So far... An inductively defined function Limitation Doesn t capture mutation of data Imperative models of computation Computation = sequence
Hoare logic. Lecture 5: Introduction to separation logic. Jean Pichon-Pharabod University of Cambridge. CST Part II 2017/18
 Hoare logic Lecture 5: Introduction to separation logic Jean Pichon-Pharabod University of Cambridge CST Part II 2017/18 Introduction In the previous lectures, we have considered a language, WHILE, where
Hoare logic Lecture 5: Introduction to separation logic Jean Pichon-Pharabod University of Cambridge CST Part II 2017/18 Introduction In the previous lectures, we have considered a language, WHILE, where
SAT-CNF Is N P-complete
 SAT-CNF Is N P-complete Rod Howell Kansas State University November 9, 2000 The purpose of this paper is to give a detailed presentation of an N P- completeness proof using the definition of N P given
SAT-CNF Is N P-complete Rod Howell Kansas State University November 9, 2000 The purpose of this paper is to give a detailed presentation of an N P- completeness proof using the definition of N P given
Wallingford: Toward a Constraint Reactive Programming Language
 Wallingford: Toward a Constraint Reactive Programming Language Alan Borning VPRI Technical Report TR-2016-001 Viewpoints Research Institute, 1025 Westwood Blvd 2nd flr, Los Angeles, CA 90024 t: (310) 208-0524
Wallingford: Toward a Constraint Reactive Programming Language Alan Borning VPRI Technical Report TR-2016-001 Viewpoints Research Institute, 1025 Westwood Blvd 2nd flr, Los Angeles, CA 90024 t: (310) 208-0524
Fundamental Concepts. Chapter 1
 Chapter 1 Fundamental Concepts This book is about the mathematical foundations of programming, with a special attention on computing with infinite objects. How can mathematics help in programming? There
Chapter 1 Fundamental Concepts This book is about the mathematical foundations of programming, with a special attention on computing with infinite objects. How can mathematics help in programming? There
EXTREME POINTS AND AFFINE EQUIVALENCE
 EXTREME POINTS AND AFFINE EQUIVALENCE The purpose of this note is to use the notions of extreme points and affine transformations which are studied in the file affine-convex.pdf to prove that certain standard
EXTREME POINTS AND AFFINE EQUIVALENCE The purpose of this note is to use the notions of extreme points and affine transformations which are studied in the file affine-convex.pdf to prove that certain standard
Incompatibility Dimensions and Integration of Atomic Commit Protocols
 The International Arab Journal of Information Technology, Vol. 5, No. 4, October 2008 381 Incompatibility Dimensions and Integration of Atomic Commit Protocols Yousef Al-Houmaily Department of Computer
The International Arab Journal of Information Technology, Vol. 5, No. 4, October 2008 381 Incompatibility Dimensions and Integration of Atomic Commit Protocols Yousef Al-Houmaily Department of Computer
COMPUTABILITY THEORY AND RECURSIVELY ENUMERABLE SETS
 COMPUTABILITY THEORY AND RECURSIVELY ENUMERABLE SETS JOSHUA LENERS Abstract. An algorithm is function from ω to ω defined by a finite set of instructions to transform a given input x to the desired output
COMPUTABILITY THEORY AND RECURSIVELY ENUMERABLE SETS JOSHUA LENERS Abstract. An algorithm is function from ω to ω defined by a finite set of instructions to transform a given input x to the desired output
Meeting14:Denotations
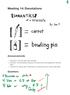 Meeting14:Denotations Announcements Homework 3 due next week Friday at 6:00pm Reminder: 5-minute feedback discussion with Sean is part of the assignment ("interview light") Talk (with me, with the class
Meeting14:Denotations Announcements Homework 3 due next week Friday at 6:00pm Reminder: 5-minute feedback discussion with Sean is part of the assignment ("interview light") Talk (with me, with the class
CSE505, Fall 2012, Midterm Examination October 30, 2012
 CSE505, Fall 2012, Midterm Examination October 30, 2012 Rules: The exam is closed-book, closed-notes, except for one side of one 8.5x11in piece of paper. Please stop promptly at Noon. You can rip apart
CSE505, Fall 2012, Midterm Examination October 30, 2012 Rules: The exam is closed-book, closed-notes, except for one side of one 8.5x11in piece of paper. Please stop promptly at Noon. You can rip apart
Hoare Logic and Model Checking
 Hoare Logic and Model Checking Kasper Svendsen University of Cambridge CST Part II 2016/17 Acknowledgement: slides heavily based on previous versions by Mike Gordon and Alan Mycroft Pointers Pointers and
Hoare Logic and Model Checking Kasper Svendsen University of Cambridge CST Part II 2016/17 Acknowledgement: slides heavily based on previous versions by Mike Gordon and Alan Mycroft Pointers Pointers and
CS558 Programming Languages
 CS558 Programming Languages Winter 2017 Lecture 7b Andrew Tolmach Portland State University 1994-2017 Values and Types We divide the universe of values according to types A type is a set of values and
CS558 Programming Languages Winter 2017 Lecture 7b Andrew Tolmach Portland State University 1994-2017 Values and Types We divide the universe of values according to types A type is a set of values and
Formal Syntax and Semantics of Programming Languages
 Formal Syntax and Semantics of Programming Languages Mooly Sagiv Reference: Semantics with Applications Chapter 2 H. Nielson and F. Nielson http://www.daimi.au.dk/~bra8130/wiley_book/wiley.html The While
Formal Syntax and Semantics of Programming Languages Mooly Sagiv Reference: Semantics with Applications Chapter 2 H. Nielson and F. Nielson http://www.daimi.au.dk/~bra8130/wiley_book/wiley.html The While
CS 161 Lecture 11 BFS, Dijkstra s algorithm Jessica Su (some parts copied from CLRS) 1 Review
 1 Review 1 Something I did not emphasize enough last time is that during the execution of depth-firstsearch, we construct depth-first-search trees. One graph may have multiple depth-firstsearch trees,
1 Review 1 Something I did not emphasize enough last time is that during the execution of depth-firstsearch, we construct depth-first-search trees. One graph may have multiple depth-firstsearch trees,
Weak Dynamic Coloring of Planar Graphs
 Weak Dynamic Coloring of Planar Graphs Caroline Accurso 1,5, Vitaliy Chernyshov 2,5, Leaha Hand 3,5, Sogol Jahanbekam 2,4,5, and Paul Wenger 2 Abstract The k-weak-dynamic number of a graph G is the smallest
Weak Dynamic Coloring of Planar Graphs Caroline Accurso 1,5, Vitaliy Chernyshov 2,5, Leaha Hand 3,5, Sogol Jahanbekam 2,4,5, and Paul Wenger 2 Abstract The k-weak-dynamic number of a graph G is the smallest
5 Matchings in Bipartite Graphs and Their Applications
 5 Matchings in Bipartite Graphs and Their Applications 5.1 Matchings Definition 5.1 A matching M in a graph G is a set of edges of G, none of which is a loop, such that no two edges in M have a common
5 Matchings in Bipartite Graphs and Their Applications 5.1 Matchings Definition 5.1 A matching M in a graph G is a set of edges of G, none of which is a loop, such that no two edges in M have a common
STABILITY AND PARADOX IN ALGORITHMIC LOGIC
 STABILITY AND PARADOX IN ALGORITHMIC LOGIC WAYNE AITKEN, JEFFREY A. BARRETT Abstract. Algorithmic logic is the logic of basic statements concerning algorithms and the algorithmic rules of deduction between
STABILITY AND PARADOX IN ALGORITHMIC LOGIC WAYNE AITKEN, JEFFREY A. BARRETT Abstract. Algorithmic logic is the logic of basic statements concerning algorithms and the algorithmic rules of deduction between
3.7 Denotational Semantics
 3.7 Denotational Semantics Denotational semantics, also known as fixed-point semantics, associates to each programming language construct a well-defined and rigorously understood mathematical object. These
3.7 Denotational Semantics Denotational semantics, also known as fixed-point semantics, associates to each programming language construct a well-defined and rigorously understood mathematical object. These
SDD Advanced-User Manual Version 1.1
 SDD Advanced-User Manual Version 1.1 Arthur Choi and Adnan Darwiche Automated Reasoning Group Computer Science Department University of California, Los Angeles Email: sdd@cs.ucla.edu Download: http://reasoning.cs.ucla.edu/sdd
SDD Advanced-User Manual Version 1.1 Arthur Choi and Adnan Darwiche Automated Reasoning Group Computer Science Department University of California, Los Angeles Email: sdd@cs.ucla.edu Download: http://reasoning.cs.ucla.edu/sdd
Propositional Logic Formal Syntax and Semantics. Computability and Logic
 Propositional Logic Formal Syntax and Semantics Computability and Logic Syntax and Semantics Syntax: The study of how expressions are structured (think: grammar) Semantics: The study of the relationship
Propositional Logic Formal Syntax and Semantics Computability and Logic Syntax and Semantics Syntax: The study of how expressions are structured (think: grammar) Semantics: The study of the relationship
Handout 9: Imperative Programs and State
 06-02552 Princ. of Progr. Languages (and Extended ) The University of Birmingham Spring Semester 2016-17 School of Computer Science c Uday Reddy2016-17 Handout 9: Imperative Programs and State Imperative
06-02552 Princ. of Progr. Languages (and Extended ) The University of Birmingham Spring Semester 2016-17 School of Computer Science c Uday Reddy2016-17 Handout 9: Imperative Programs and State Imperative
CSE 505: Concepts of Programming Languages
 CSE 505: Concepts of Programming Languages Dan Grossman Fall 2009 Lecture 4 Proofs about Operational Semantics; Pseudo-Denotational Semantics Dan Grossman CSE505 Fall 2009, Lecture 4 1 This lecture Continue
CSE 505: Concepts of Programming Languages Dan Grossman Fall 2009 Lecture 4 Proofs about Operational Semantics; Pseudo-Denotational Semantics Dan Grossman CSE505 Fall 2009, Lecture 4 1 This lecture Continue
2386 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 6, JUNE 2006
 2386 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 6, JUNE 2006 The Encoding Complexity of Network Coding Michael Langberg, Member, IEEE, Alexander Sprintson, Member, IEEE, and Jehoshua Bruck,
2386 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 6, JUNE 2006 The Encoding Complexity of Network Coding Michael Langberg, Member, IEEE, Alexander Sprintson, Member, IEEE, and Jehoshua Bruck,
Adjacent: Two distinct vertices u, v are adjacent if there is an edge with ends u, v. In this case we let uv denote such an edge.
 1 Graph Basics What is a graph? Graph: a graph G consists of a set of vertices, denoted V (G), a set of edges, denoted E(G), and a relation called incidence so that each edge is incident with either one
1 Graph Basics What is a graph? Graph: a graph G consists of a set of vertices, denoted V (G), a set of edges, denoted E(G), and a relation called incidence so that each edge is incident with either one
Principles of Programming Languages
 Principles of Programming Languages Lesson 14 Type Checking Collaboration and Management Dana Fisman www.cs.bgu.ac.il/~ppl172 1 Type Checking We return to the issue of type safety we discussed informally,
Principles of Programming Languages Lesson 14 Type Checking Collaboration and Management Dana Fisman www.cs.bgu.ac.il/~ppl172 1 Type Checking We return to the issue of type safety we discussed informally,
Definition: A context-free grammar (CFG) is a 4- tuple. variables = nonterminals, terminals, rules = productions,,
 CMPSCI 601: Recall From Last Time Lecture 5 Definition: A context-free grammar (CFG) is a 4- tuple, variables = nonterminals, terminals, rules = productions,,, are all finite. 1 ( ) $ Pumping Lemma for
CMPSCI 601: Recall From Last Time Lecture 5 Definition: A context-free grammar (CFG) is a 4- tuple, variables = nonterminals, terminals, rules = productions,,, are all finite. 1 ( ) $ Pumping Lemma for
Graph Theory Questions from Past Papers
 Graph Theory Questions from Past Papers Bilkent University, Laurence Barker, 19 October 2017 Do not forget to justify your answers in terms which could be understood by people who know the background theory
Graph Theory Questions from Past Papers Bilkent University, Laurence Barker, 19 October 2017 Do not forget to justify your answers in terms which could be understood by people who know the background theory
CS473-Algorithms I. Lecture 13-A. Graphs. Cevdet Aykanat - Bilkent University Computer Engineering Department
 CS473-Algorithms I Lecture 3-A Graphs Graphs A directed graph (or digraph) G is a pair (V, E), where V is a finite set, and E is a binary relation on V The set V: Vertex set of G The set E: Edge set of
CS473-Algorithms I Lecture 3-A Graphs Graphs A directed graph (or digraph) G is a pair (V, E), where V is a finite set, and E is a binary relation on V The set V: Vertex set of G The set E: Edge set of
CPS 102: Discrete Mathematics. Quiz 3 Date: Wednesday November 30, Instructor: Bruce Maggs NAME: Prob # Score. Total 60
 CPS 102: Discrete Mathematics Instructor: Bruce Maggs Quiz 3 Date: Wednesday November 30, 2011 NAME: Prob # Score Max Score 1 10 2 10 3 10 4 10 5 10 6 10 Total 60 1 Problem 1 [10 points] Find a minimum-cost
CPS 102: Discrete Mathematics Instructor: Bruce Maggs Quiz 3 Date: Wednesday November 30, 2011 NAME: Prob # Score Max Score 1 10 2 10 3 10 4 10 5 10 6 10 Total 60 1 Problem 1 [10 points] Find a minimum-cost
Programming Languages Lecture 15: Recursive Types & Subtyping
 CSE 230: Winter 2008 Principles of Programming Languages Lecture 15: Recursive Types & Subtyping Ranjit Jhala UC San Diego News? Formalize first-order type systems Simple types (integers and booleans)
CSE 230: Winter 2008 Principles of Programming Languages Lecture 15: Recursive Types & Subtyping Ranjit Jhala UC San Diego News? Formalize first-order type systems Simple types (integers and booleans)
Lecture 3: Art Gallery Problems and Polygon Triangulation
 EECS 396/496: Computational Geometry Fall 2017 Lecture 3: Art Gallery Problems and Polygon Triangulation Lecturer: Huck Bennett In this lecture, we study the problem of guarding an art gallery (specified
EECS 396/496: Computational Geometry Fall 2017 Lecture 3: Art Gallery Problems and Polygon Triangulation Lecturer: Huck Bennett In this lecture, we study the problem of guarding an art gallery (specified
No model may be available. Software Abstractions. Recap on Model Checking. Model Checking for SW Verif. More on the big picture. Abst -> MC -> Refine
 No model may be available Programmer Software Abstractions Tests Coverage Code Abhik Roychoudhury CS 5219 National University of Singapore Testing Debug Today s lecture Abstract model (Boolean pgm.) Desirable
No model may be available Programmer Software Abstractions Tests Coverage Code Abhik Roychoudhury CS 5219 National University of Singapore Testing Debug Today s lecture Abstract model (Boolean pgm.) Desirable
These are not polished as solutions, but ought to give a correct idea of solutions that work. Note that most problems have multiple good solutions.
 CSE 591 HW Sketch Sample Solutions These are not polished as solutions, but ought to give a correct idea of solutions that work. Note that most problems have multiple good solutions. Problem 1 (a) Any
CSE 591 HW Sketch Sample Solutions These are not polished as solutions, but ought to give a correct idea of solutions that work. Note that most problems have multiple good solutions. Problem 1 (a) Any
Bootcamp. Christoph Thiele. Summer An example of a primitive universe
 Bootcamp Christoph Thiele Summer 2012 0.1 An example of a primitive universe A primitive universe consists of primitive objects and primitive sets. This allows to form primitive statements as to which
Bootcamp Christoph Thiele Summer 2012 0.1 An example of a primitive universe A primitive universe consists of primitive objects and primitive sets. This allows to form primitive statements as to which
CONVENTIONAL EXECUTABLE SEMANTICS. Grigore Rosu CS422 Programming Language Design
 CONVENTIONAL EXECUTABLE SEMANTICS Grigore Rosu CS422 Programming Language Design Conventional Semantic Approaches A language designer should understand the existing design approaches, techniques and tools,
CONVENTIONAL EXECUTABLE SEMANTICS Grigore Rosu CS422 Programming Language Design Conventional Semantic Approaches A language designer should understand the existing design approaches, techniques and tools,
Fundamental Properties of Graphs
 Chapter three In many real-life situations we need to know how robust a graph that represents a certain network is, how edges or vertices can be removed without completely destroying the overall connectivity,
Chapter three In many real-life situations we need to know how robust a graph that represents a certain network is, how edges or vertices can be removed without completely destroying the overall connectivity,
COMP 181. Agenda. Midterm topics. Today: type checking. Purpose of types. Type errors. Type checking
 Agenda COMP 181 Type checking October 21, 2009 Next week OOPSLA: Object-oriented Programming Systems Languages and Applications One of the top PL conferences Monday (Oct 26 th ) In-class midterm Review
Agenda COMP 181 Type checking October 21, 2009 Next week OOPSLA: Object-oriented Programming Systems Languages and Applications One of the top PL conferences Monday (Oct 26 th ) In-class midterm Review
Variables. Substitution
 Variables Elements of Programming Languages Lecture 4: Variables, binding and substitution James Cheney University of Edinburgh October 6, 2015 A variable is a symbol that can stand for another expression.
Variables Elements of Programming Languages Lecture 4: Variables, binding and substitution James Cheney University of Edinburgh October 6, 2015 A variable is a symbol that can stand for another expression.
Winning Positions in Simplicial Nim
 Winning Positions in Simplicial Nim David Horrocks Department of Mathematics and Statistics University of Prince Edward Island Charlottetown, Prince Edward Island, Canada, C1A 4P3 dhorrocks@upei.ca Submitted:
Winning Positions in Simplicial Nim David Horrocks Department of Mathematics and Statistics University of Prince Edward Island Charlottetown, Prince Edward Island, Canada, C1A 4P3 dhorrocks@upei.ca Submitted:
Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science Algorithms For Inference Fall 2014
 Suggested Reading: Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.438 Algorithms For Inference Fall 2014 Probabilistic Modelling and Reasoning: The Junction
Suggested Reading: Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.438 Algorithms For Inference Fall 2014 Probabilistic Modelling and Reasoning: The Junction
Computing intersections in a set of line segments: the Bentley-Ottmann algorithm
 Computing intersections in a set of line segments: the Bentley-Ottmann algorithm Michiel Smid October 14, 2003 1 Introduction In these notes, we introduce a powerful technique for solving geometric problems.
Computing intersections in a set of line segments: the Bentley-Ottmann algorithm Michiel Smid October 14, 2003 1 Introduction In these notes, we introduce a powerful technique for solving geometric problems.
Applied Algorithm Design Lecture 3
 Applied Algorithm Design Lecture 3 Pietro Michiardi Eurecom Pietro Michiardi (Eurecom) Applied Algorithm Design Lecture 3 1 / 75 PART I : GREEDY ALGORITHMS Pietro Michiardi (Eurecom) Applied Algorithm
Applied Algorithm Design Lecture 3 Pietro Michiardi Eurecom Pietro Michiardi (Eurecom) Applied Algorithm Design Lecture 3 1 / 75 PART I : GREEDY ALGORITHMS Pietro Michiardi (Eurecom) Applied Algorithm
Chapter 3: Propositional Languages
 Chapter 3: Propositional Languages We define here a general notion of a propositional language. We show how to obtain, as specific cases, various languages for propositional classical logic and some non-classical
Chapter 3: Propositional Languages We define here a general notion of a propositional language. We show how to obtain, as specific cases, various languages for propositional classical logic and some non-classical
Operational Semantics of Cool
 Operational Semantics of Cool Key Concepts semantics: the meaning of a program, what does program do? how the code is executed? operational semantics: high level code generation steps of calculating values
Operational Semantics of Cool Key Concepts semantics: the meaning of a program, what does program do? how the code is executed? operational semantics: high level code generation steps of calculating values
CONVENTIONAL EXECUTABLE SEMANTICS. Grigore Rosu CS522 Programming Language Semantics
 CONVENTIONAL EXECUTABLE SEMANTICS Grigore Rosu CS522 Programming Language Semantics Conventional Semantic Approaches A language designer should understand the existing design approaches, techniques and
CONVENTIONAL EXECUTABLE SEMANTICS Grigore Rosu CS522 Programming Language Semantics Conventional Semantic Approaches A language designer should understand the existing design approaches, techniques and
CS152: Programming Languages. Lecture 2 Syntax. Dan Grossman Spring 2011
 CS152: Programming Languages Lecture 2 Syntax Dan Grossman Spring 2011 Finally, some formal PL content For our first formal language, let s leave out functions, objects, records, threads, exceptions,...
CS152: Programming Languages Lecture 2 Syntax Dan Grossman Spring 2011 Finally, some formal PL content For our first formal language, let s leave out functions, objects, records, threads, exceptions,...
Generalized Verification Support for Magic Wands
 Generalized Verification Support for Magic Wands Bachelor s Thesis Nils Becker, nbecker@student.ethz.ch Supervisors: Malte Schwerhoff, malte.schwerhoff@inf.ethz.ch Alexander J. Summers, alexander.summers@inf.ethz.ch
Generalized Verification Support for Magic Wands Bachelor s Thesis Nils Becker, nbecker@student.ethz.ch Supervisors: Malte Schwerhoff, malte.schwerhoff@inf.ethz.ch Alexander J. Summers, alexander.summers@inf.ethz.ch
Type Checking and Type Equality
 Type Checking and Type Equality Type systems are the biggest point of variation across programming languages. Even languages that look similar are often greatly different when it comes to their type systems.
Type Checking and Type Equality Type systems are the biggest point of variation across programming languages. Even languages that look similar are often greatly different when it comes to their type systems.
ACONCURRENT system may be viewed as a collection of
 252 IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS, VOL. 10, NO. 3, MARCH 1999 Constructing a Reliable Test&Set Bit Frank Stomp and Gadi Taubenfeld AbstractÐThe problem of computing with faulty
252 IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS, VOL. 10, NO. 3, MARCH 1999 Constructing a Reliable Test&Set Bit Frank Stomp and Gadi Taubenfeld AbstractÐThe problem of computing with faulty
Efficient Prefix Computation on Faulty Hypercubes
 JOURNAL OF INFORMATION SCIENCE AND ENGINEERING 17, 1-21 (21) Efficient Prefix Computation on Faulty Hypercubes YU-WEI CHEN AND KUO-LIANG CHUNG + Department of Computer and Information Science Aletheia
JOURNAL OF INFORMATION SCIENCE AND ENGINEERING 17, 1-21 (21) Efficient Prefix Computation on Faulty Hypercubes YU-WEI CHEN AND KUO-LIANG CHUNG + Department of Computer and Information Science Aletheia
CMSC 330: Organization of Programming Languages. Formal Semantics of a Prog. Lang. Specifying Syntax, Semantics
 Recall Architecture of Compilers, Interpreters CMSC 330: Organization of Programming Languages Source Scanner Parser Static Analyzer Operational Semantics Intermediate Representation Front End Back End
Recall Architecture of Compilers, Interpreters CMSC 330: Organization of Programming Languages Source Scanner Parser Static Analyzer Operational Semantics Intermediate Representation Front End Back End
The Resolution Algorithm
 The Resolution Algorithm Introduction In this lecture we introduce the Resolution algorithm for solving instances of the NP-complete CNF- SAT decision problem. Although the algorithm does not run in polynomial
The Resolution Algorithm Introduction In this lecture we introduce the Resolution algorithm for solving instances of the NP-complete CNF- SAT decision problem. Although the algorithm does not run in polynomial
Type Checking. Outline. General properties of type systems. Types in programming languages. Notation for type rules.
 Outline Type Checking General properties of type systems Types in programming languages Notation for type rules Logical rules of inference Common type rules 2 Static Checking Refers to the compile-time
Outline Type Checking General properties of type systems Types in programming languages Notation for type rules Logical rules of inference Common type rules 2 Static Checking Refers to the compile-time
Module 11. Directed Graphs. Contents
 Module 11 Directed Graphs Contents 11.1 Basic concepts......................... 256 Underlying graph of a digraph................ 257 Out-degrees and in-degrees.................. 258 Isomorphism..........................
Module 11 Directed Graphs Contents 11.1 Basic concepts......................... 256 Underlying graph of a digraph................ 257 Out-degrees and in-degrees.................. 258 Isomorphism..........................
An algorithm for Performance Analysis of Single-Source Acyclic graphs
 An algorithm for Performance Analysis of Single-Source Acyclic graphs Gabriele Mencagli September 26, 2011 In this document we face with the problem of exploiting the performance analysis of acyclic graphs
An algorithm for Performance Analysis of Single-Source Acyclic graphs Gabriele Mencagli September 26, 2011 In this document we face with the problem of exploiting the performance analysis of acyclic graphs
The Systematic Generation of Channelling Constraints
 The Systematic Generation of Channelling Constraints Bernadette Martínez-Hernández and Alan M. Frisch Artificial Intelligence Group, Dept. of Computer Science, Univ. of York, York, UK Abstract. The automatic
The Systematic Generation of Channelling Constraints Bernadette Martínez-Hernández and Alan M. Frisch Artificial Intelligence Group, Dept. of Computer Science, Univ. of York, York, UK Abstract. The automatic
Reasoning about modules: data refinement and simulation
 Reasoning about modules: data refinement and simulation David Naumann naumann@cs.stevens-tech.edu Stevens Institute of Technology Naumann - POPL 02 Java Verification Workshop p.1/17 Objectives of talk
Reasoning about modules: data refinement and simulation David Naumann naumann@cs.stevens-tech.edu Stevens Institute of Technology Naumann - POPL 02 Java Verification Workshop p.1/17 Objectives of talk
