GSM Open-source intelligence
|
|
|
- Eugenia Franklin
- 6 years ago
- Views:
Transcription
1 GSM Open-source intelligence Kenneth van Rijsbergen 1 1 MSc System and Network Engineering Faculty of Science University of Amsterdam 30 June 2016 Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
2 Table of Contents 1 Introduction 2 Background 3 Results 4 Conclusion Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
3 Research question How may GSM be used for gathering OSINT by a red team? How can a Software Defined Radio (SDR) be used to passively capture GSM traffic? How can a Software Defined Radio (SDR) be used to actively capture GSM traffic? What OSINT may be extracted from this GSM data? Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
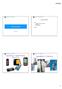
4 Software Defined Radio HackRF One 1 MHz to 6 GHz half-duplex transceiver $299.- BladeRF x40 300MHz to 3.8GHz full-duplex transceiver $420.- FIGURE HackRF One FIGURE BladeRF x40 Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
5 FIGURE Waterfall (jamming test inside faraday cage) FIGURE GSM sniffing with HackRF Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
6 Overview of mobile generations First generation (1G) 1980 s Analogue Voice only Technologies : AMPS, NMT, TACS, C-450, Radiocom 2000, RTMI, JTACS, TZ-801, TZ-802, and TZ-803 Second generation (2G) 1990 s Digital signalling, SMS, MMS, voice mail, call forwarding Encryption (A5/1 and A5/2) technologies : GSM, IS-95 (a.k.a. cdmaone), PDC, iden and IS-136 (a.k.a. D-AMPS) 2.5G : GPRS 2.75G : EDGE Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
7 Overview of mobile generations Third generation (3G) 2000 s Improved crypto (A5/3) and two-way authentication between MS and BS. Faster data transfer Technologies : W-CDMA (UMTS), TD-SCDMA (only in China), HSPA, and HSPA+, CDMA2000, LTE Recently allowed to use the 900 and 1800 Mhz band (same as GSM). Fourth generation (4G) IP based, no more circuit-switched telephone Technologies : LTE Advanced and Mobile WiMAX Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
8 GSM Architecture + Lingo MS MS BSC BS HLR + AUC BS BS BSC BSC MSC + VLR MSC + VLR ISDN + PSTN MS Mobile station BS Base Station BSC Base Station Controller MSC Mobile Switching Center VLR Visitor Location Register HLR Home Location Register AUC Authentication Center EIR Equipment Identity Register MSC + VLR FIGURE GSM Architecture Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
9 GSM authentication sequence FIGURE GSM authentication sequence Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
10 IMSI catcher FIGURE IMSI catcher Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
11 GSM Authentication A5 used to encrypt the data transmission between the MS and BS. A5/1 - Developed in Workings kept secret. - Reverse engineered in 1999 and published. - Can be cracked in seconds using rainbow tables. A5/2 - Extremely weak, developed for export markets - Can be cracked in real-time. - Discontinued by the GSM association since A5/3 - In use today. - Designed for 3G but also used for GSM. - Based on the MISTY block cypher which was later simplified into the KASUMI block cypher. - A faster than an exhaustive search attack has been found but nothing practical. Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
12 IMSI catcher IMSI International Mobile Subscriber Identity Can be used to identify a mobile subscriber. The IMSI is send by GSM unencrypted over the air during authentication. This enables tracking. Full IMSI catchers (full MITM) Half IMSI catchers (outgoing only) Both require a spoofed basestation. Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
13 IMSI catcher FIGURE Stingray I ( FIGURE NSA GSM Tripwire (NSA s ANT Division Catalog) FIGURE IMSI catcher on planes (Brian McGill The Wall Street Journal) Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
14 Passive Capturing Possible but all is encrypted Some IMSI s may (in theory) be captured when in initial authentication. But nothing that can be practically used. FIGURE GSM Decoding FIGURE GSM data in Wireshark Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
15 Demo Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
16 Spoof limitation YateBTS only supports 2.5G GPRS OpenBTS-UMTS offers 3G UMTS but requires more expensive hardware (a recent USRP) The phone will always prefer a higher standard, even if the signal is weak 1 4G LTE-Advanced 2 3G UMTS G EDGE 4 2.5G GPRS <- YateBTS 5 2G GSM Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
17 Jamming The HackRF is not suitable for jamming Test was conducted inside a Faraday cage. Jamming a specific 900Mhz GSM channel was possible, but only for the old 2G Nokia. 3G HTC phone disconnects, then recovers when setting up a new call. Higher bands (like 1800) are too wide for the HackRF to cover. Transmitting at a higher frequency requires more power ; HackRF did not have enough to disrupt 2G G jamming is even more hopeless due to spread spectrum. Would be nice to test with a real 3G jammer. The hypothesis would be that the phone drops down to EDGE instead of GPRS. Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
18 Conclusion and Future work Conclusion Passive attacks are not effective due to encryption. Active attacks can only be effective versus 2G phones or when using jamming attacks (illegal). If, however a phone connects, everything outgoing can be intercepted (Internet, Voice, SMS). Future Work Full IMSI Catcher (still relies on a successful spoof) Selective jamming* (jam all but one channel) Kenneth van Rijsbergen University of Amsterdam GSM OSINT 30 June / 18
E2-E3: CONSUMER MOBILITY. CHAPTER-5 CDMA x OVERVIEW (Date of Creation: )
 E2-E3: CONSUMER MOBILITY CHAPTER-5 CDMA 2000 1x OVERVIEW (Date of Creation: 01-04.2011) Page: 1 CDMA 2000 1X Overview Introduction CDMA (code division multiple access) is a mobile digital radio technology
E2-E3: CONSUMER MOBILITY CHAPTER-5 CDMA 2000 1x OVERVIEW (Date of Creation: 01-04.2011) Page: 1 CDMA 2000 1X Overview Introduction CDMA (code division multiple access) is a mobile digital radio technology
Dimensioning, configuration and deployment of Radio Access Networks. part 1: General considerations. Mobile Telephony Networks
 Dimensioning, configuration and deployment of Radio Access Networks. part 1: General considerations Mobile Telephony Networks 1 The Evolution of Mobile Telephony 1st Generation 2nd 3rd 4th Analogue Voice
Dimensioning, configuration and deployment of Radio Access Networks. part 1: General considerations Mobile Telephony Networks 1 The Evolution of Mobile Telephony 1st Generation 2nd 3rd 4th Analogue Voice
GLOBAL SYSTEM FOR MOBILE COMMUNICATION (2) ETI2511 Friday, 31 March 2017
 GLOBAL SYSTEM FOR MOBILE COMMUNICATION (2) ETI2511 Friday, 31 March 2017 1 SYLLABUS GSM General architecture and interfaces of cellular system and the PSTN and Internet networks: BTS, MSC, Internetworking,
GLOBAL SYSTEM FOR MOBILE COMMUNICATION (2) ETI2511 Friday, 31 March 2017 1 SYLLABUS GSM General architecture and interfaces of cellular system and the PSTN and Internet networks: BTS, MSC, Internetworking,
Security of Cellular Networks: Man-in-the Middle Attacks
 Security of Cellular Networks: Man-in-the Middle Attacks Mario Čagalj University of Split 2013/2014. Security in the GSM system by Jeremy Quirke, 2004 Introduction Nowadays, mobile phones are used by 80-90%
Security of Cellular Networks: Man-in-the Middle Attacks Mario Čagalj University of Split 2013/2014. Security in the GSM system by Jeremy Quirke, 2004 Introduction Nowadays, mobile phones are used by 80-90%
Cellular Communication
 Cellular Communication Cellular Communication Cellular communication is designed to provide communications between two moving units, or between one mobile unit and one stationary phone or land unit (PSTN).
Cellular Communication Cellular Communication Cellular communication is designed to provide communications between two moving units, or between one mobile unit and one stationary phone or land unit (PSTN).
Network Security: Cellular Security. Tuomas Aura T Network security Aalto University, Nov-Dec 2013
 Network Security: Cellular Security Tuomas Aura T-110.5241 Network security Aalto University, Nov-Dec 2013 Outline Cellular networks GSM security architecture and protocols Counters UMTS AKA and session
Network Security: Cellular Security Tuomas Aura T-110.5241 Network security Aalto University, Nov-Dec 2013 Outline Cellular networks GSM security architecture and protocols Counters UMTS AKA and session
How to hack your way out of home detention!
 How to hack your way out of home detention! About me! William @Amm0nRa Turner! @Assurance! About presentation! Acquire a home detention tracking system! Get a BladeRF SDR! Use open source GSM software
How to hack your way out of home detention! About me! William @Amm0nRa Turner! @Assurance! About presentation! Acquire a home detention tracking system! Get a BladeRF SDR! Use open source GSM software
COMP327 Mobile Computing Session: Lecture Set 5 - Wireless Communication Part 2
 COMP327 Mobile Computing Session: 2016-2017 Lecture Set 5 - Wireless Communication Part 2 51 SIM (Subscriber Identity Modules) Smart cards that are inserted into the GSM phone to identify the user Stores
COMP327 Mobile Computing Session: 2016-2017 Lecture Set 5 - Wireless Communication Part 2 51 SIM (Subscriber Identity Modules) Smart cards that are inserted into the GSM phone to identify the user Stores
E3-E4 (CM MODULE) CDMA x & EV-DO. For internal circulation of BSNL only
 E3-E4 (CM MODULE) CDMA 2000 1x & EV-DO WELCOME This is a presentation for the E3-E4 Technical (CM- Module)fortheTopic:CDMA20001x&EV-DO Eligibility: Those who have got the upgradation frome3toe4. This presentation
E3-E4 (CM MODULE) CDMA 2000 1x & EV-DO WELCOME This is a presentation for the E3-E4 Technical (CM- Module)fortheTopic:CDMA20001x&EV-DO Eligibility: Those who have got the upgradation frome3toe4. This presentation
Mobile Security Fall 2013
 Mobile Security 14-829 Fall 2013 Patrick Tague Class #3 Telecom Security from 1G to 4G Basics of Telecom Security Different players in the mobile ecosystem have different security concerns Security concerns
Mobile Security 14-829 Fall 2013 Patrick Tague Class #3 Telecom Security from 1G to 4G Basics of Telecom Security Different players in the mobile ecosystem have different security concerns Security concerns
GSM Hacking. Wireless Mobile Phone Communication 30 th January 2014 UNRESTRICTED EXTERNAL
 GSM Hacking Wireless Mobile Phone Communication 30 th January 2014 Labs.mwrinfosecurity.com MWR Labs 1 Labs.mwrinfosecurity.com MWR Labs Introduction to GSM June 2008 2.9 BILLION subscribers use GSM. Replaced
GSM Hacking Wireless Mobile Phone Communication 30 th January 2014 Labs.mwrinfosecurity.com MWR Labs 1 Labs.mwrinfosecurity.com MWR Labs Introduction to GSM June 2008 2.9 BILLION subscribers use GSM. Replaced
GSM Security Overview
 GSM Security Overview Mehdi Hassanzadeh Mehdi.Hassanzadeh@ii.uib.no Selmer Center, University of Bergen, Norway Norsk ryptoseminar, Bergen, November 9-10, 2011 Agenda A5 Overview : Attack History on A5/1
GSM Security Overview Mehdi Hassanzadeh Mehdi.Hassanzadeh@ii.uib.no Selmer Center, University of Bergen, Norway Norsk ryptoseminar, Bergen, November 9-10, 2011 Agenda A5 Overview : Attack History on A5/1
Wireless systems overview
 Wireless systems overview Evolution of systems from 1G to 4G 1G, 4G major features Specifications comparison 5G communication systems Summary Wireless Systems 2016 Evolution of cellular networks WiMAX
Wireless systems overview Evolution of systems from 1G to 4G 1G, 4G major features Specifications comparison 5G communication systems Summary Wireless Systems 2016 Evolution of cellular networks WiMAX
Chapter 3 GSM and Similar Architectures
 CSF645 Mobile Computing 行動計算 Chapter 3 GSM and Similar Architectures 吳俊興 國立高雄大學資訊工程學系 Chapter 3 GSM and Similar Architectures 3.1 GSM Services and System Architecture 3.2 Radio Interfaces 3.3 Protocols
CSF645 Mobile Computing 行動計算 Chapter 3 GSM and Similar Architectures 吳俊興 國立高雄大學資訊工程學系 Chapter 3 GSM and Similar Architectures 3.1 GSM Services and System Architecture 3.2 Radio Interfaces 3.3 Protocols
Basics of GSM in depth
 This document will be helpful for the telecom engineers who deal with GSM as well as for the fresher /interested readers. This document has some advantages over other GSM texts in that it quickly gets
This document will be helpful for the telecom engineers who deal with GSM as well as for the fresher /interested readers. This document has some advantages over other GSM texts in that it quickly gets
Pertemuan 7 GSM Network. DAHLAN ABDULLAH
 Pertemuan 7 GSM Network DAHLAN ABDULLAH Email : dahlan.unimal@gmail.com Contents GSM-Introduction Architecture Technical Specification & Operation Frame Structure Channels Call Routing Security Characteristics
Pertemuan 7 GSM Network DAHLAN ABDULLAH Email : dahlan.unimal@gmail.com Contents GSM-Introduction Architecture Technical Specification & Operation Frame Structure Channels Call Routing Security Characteristics
Wireless and Mobile Network Investigation
 Wireless and Mobile Network Investigation Part II.B. Techniques and Tools: Network Forensics CSF: Forensics Cyber-Security Fall 2015 Nuno Santos Summary } WiFi network investigations } Cellular network
Wireless and Mobile Network Investigation Part II.B. Techniques and Tools: Network Forensics CSF: Forensics Cyber-Security Fall 2015 Nuno Santos Summary } WiFi network investigations } Cellular network
Cellular Networks and Mobility
 Cellular Networks and Mobility Daniel Zappala CS 460 Computer Networking Brigham Young University Cellular Networks GSM 2G/3G Architecture 3/20 2G Standard 4/20 GSM: combined FDM/TDM divide into 200 khz
Cellular Networks and Mobility Daniel Zappala CS 460 Computer Networking Brigham Young University Cellular Networks GSM 2G/3G Architecture 3/20 2G Standard 4/20 GSM: combined FDM/TDM divide into 200 khz
Cellular Mobile Systems and Services (TCOM1010) GSM Architecture
 GSM Architecture 1 GSM NETWORK INFRASTRUCTURE...2 2 NETWORK SWITCHING SUBSYSTEM (NSS)...3 2.1 Home Location Register...4 2.2 Mobile Switching Center and Visitor Location Register...4 2.3 Authentication
GSM Architecture 1 GSM NETWORK INFRASTRUCTURE...2 2 NETWORK SWITCHING SUBSYSTEM (NSS)...3 2.1 Home Location Register...4 2.2 Mobile Switching Center and Visitor Location Register...4 2.3 Authentication
Chapter 2 The 3G Mobile Communications
 Chapter 2 The 3G Mobile Communications 2.1 The Vision for Third Generation (3G) Mobile Communication Systems: The vision for the emerging mobile and personal communication services for the new century
Chapter 2 The 3G Mobile Communications 2.1 The Vision for Third Generation (3G) Mobile Communication Systems: The vision for the emerging mobile and personal communication services for the new century
Nexus8610 Traffic Simulation System. Intersystem Handover Simulation. White Paper
 Traffic Simulation System Intersystem Handover Simulation White Paper Notice Every effort has been made to ensure that the information in this document was accurate at the time of printing. However, the
Traffic Simulation System Intersystem Handover Simulation White Paper Notice Every effort has been made to ensure that the information in this document was accurate at the time of printing. However, the
CHAPTER 4 SYSTEM IMPLEMENTATION 4.1 INTRODUCTION
 CHAPTER 4 SYSTEM IMPLEMENTATION 4.1 INTRODUCTION The most important part of any project i.e., implementation. It describes the various functionalities step by step under each module with their outputs.
CHAPTER 4 SYSTEM IMPLEMENTATION 4.1 INTRODUCTION The most important part of any project i.e., implementation. It describes the various functionalities step by step under each module with their outputs.
Telecommunication Services Engineering Lab
 Logistics Instructor Office: EV007-647, Tel: 1-514-8482424 ext 5846, Email: Glitho@ciiseconcordiaca URL: http://wwwececoncordiaca/~glitho/ Office hours: Tuesday: 3 pm 5 pm Time: Usually: Tuesday, 17h45-20h15
Logistics Instructor Office: EV007-647, Tel: 1-514-8482424 ext 5846, Email: Glitho@ciiseconcordiaca URL: http://wwwececoncordiaca/~glitho/ Office hours: Tuesday: 3 pm 5 pm Time: Usually: Tuesday, 17h45-20h15
CSC 401 Data and Computer Communications Networks
 CSC 401 Data and Computer Communications Networks Wireless Networks Cellular & Mobility Sec 7.4 7.8 Lina Battestilli 7.1 Introduction Wireless Chapter 7 Outline Wireless and Mobile Networks 7.2 Wireless
CSC 401 Data and Computer Communications Networks Wireless Networks Cellular & Mobility Sec 7.4 7.8 Lina Battestilli 7.1 Introduction Wireless Chapter 7 Outline Wireless and Mobile Networks 7.2 Wireless
Telecommunication Services Engineering Lab
 Logistics Instructor Office: EV006-227, Tel: 1-514-8482424 ext 5846, Email: Glitho@ciiseconcordiaca URL: http://wwwececoncordiaca/~glitho/ Office hours: Friday: 3 pm 5 pm Time: Friday, 17h45-20h15 Room
Logistics Instructor Office: EV006-227, Tel: 1-514-8482424 ext 5846, Email: Glitho@ciiseconcordiaca URL: http://wwwececoncordiaca/~glitho/ Office hours: Friday: 3 pm 5 pm Time: Friday, 17h45-20h15 Room
GSM Interception IMSI Catcher and Voice Interception
 GSM Interception IMSI Catcher and Voice Interception Part of the product line Product overview go2intercept passive: GSM interception Passive, massive, of the air. (page 3-4) go2intercept active basic:
GSM Interception IMSI Catcher and Voice Interception Part of the product line Product overview go2intercept passive: GSM interception Passive, massive, of the air. (page 3-4) go2intercept active basic:
RNV Vehicular Communications Part II Radio Networks for Vehicular Communications Roberto Verdone
 RNV Vehicular Communications Part II Radio Networks for Vehicular Communications Roberto Verdone Outline 1. Network Architectures: Evolution From GSM towards 5G 2. Mobility Management 3. 2G (GSM): Numerology
RNV Vehicular Communications Part II Radio Networks for Vehicular Communications Roberto Verdone Outline 1. Network Architectures: Evolution From GSM towards 5G 2. Mobility Management 3. 2G (GSM): Numerology
GSM. Course requirements: Understanding Telecommunications book by Ericsson (Part D PLMN) + supporting material (= these slides) GPRS
 GSM Example of a PLMN (Public Land Mobile Network) At present most successful cellular mobile system (over 200 million subscribers worldwide) Digital (2 nd Generation) cellular mobile system operating
GSM Example of a PLMN (Public Land Mobile Network) At present most successful cellular mobile system (over 200 million subscribers worldwide) Digital (2 nd Generation) cellular mobile system operating
GSM- R and CDMA Network System for the Railway Industry
 GSM- R and CDMA Network System for the Railway Industry T. Brandejský & T. Vu Dinh* Faculty of Transportation Sciences- Czech Technical University in Prague,Czech Republic *Corresponding author: vudinhthem@yahoo.com
GSM- R and CDMA Network System for the Railway Industry T. Brandejský & T. Vu Dinh* Faculty of Transportation Sciences- Czech Technical University in Prague,Czech Republic *Corresponding author: vudinhthem@yahoo.com
E1-E2 UPGRADATION COURSE CONSUMER MOBILITY. 3G Concept
 E1-E2 UPGRADATION COURSE CONSUMER MOBILITY 3G Concept Page 1 CHAPTER-TWO 3 G CONCEPT UMTS and the information society Rapid advancements in Information and Communications Technology (ICT) have already
E1-E2 UPGRADATION COURSE CONSUMER MOBILITY 3G Concept Page 1 CHAPTER-TWO 3 G CONCEPT UMTS and the information society Rapid advancements in Information and Communications Technology (ICT) have already
Communication Networks 2 Signaling 2 (Mobile)
 Communication Networks 2 Signaling 2 (Mobile) Gusztáv Adamis BME TMIT 2017 GSM signaling Signaling of GSM is based on the ISDN signaling systems SS7/DSS1 But, because of mobility, roaming, radio access
Communication Networks 2 Signaling 2 (Mobile) Gusztáv Adamis BME TMIT 2017 GSM signaling Signaling of GSM is based on the ISDN signaling systems SS7/DSS1 But, because of mobility, roaming, radio access
PCS. Reference. Wireless and Mobile Network Architectures Y-Bing Lin and Imrich Chlamtac Wiley Computer Publishing
 PCS 1 Reference Wireless and Mobile Network Architectures Y-Bing Lin and Imrich Chlamtac Wiley Computer Publishing 2 Outlines Introduction PCS Architecture Cellular Telephony Cordless Telephony and Low-Tier
PCS 1 Reference Wireless and Mobile Network Architectures Y-Bing Lin and Imrich Chlamtac Wiley Computer Publishing 2 Outlines Introduction PCS Architecture Cellular Telephony Cordless Telephony and Low-Tier
Semi-Active GSM Monitoring System SCL-5020SE
 Semi-Active GSM Monitoring System SCL-5020SE Technology Introduction: GSM networks are most popular and widespread wireless communication media across the world, having a wide customer base in Europe and
Semi-Active GSM Monitoring System SCL-5020SE Technology Introduction: GSM networks are most popular and widespread wireless communication media across the world, having a wide customer base in Europe and
Data and Voice Signal Intelligence Interception Over The GSM Um Interface
 ISSN (Online): 2394-3858 ISSN (Print): 2394-3866 International Journal of Research and Innovations in Science & Technology, SAINTGITS College of Engineering, INDIA www.journals.saintgits.org Research paper
ISSN (Online): 2394-3858 ISSN (Print): 2394-3866 International Journal of Research and Innovations in Science & Technology, SAINTGITS College of Engineering, INDIA www.journals.saintgits.org Research paper
Chapter 10: Wireless Networking. School of information science and Engineering, SDU
 Chapter 10: Wireless Networking School of information science and Engineering, SDU 10.1 Introduction to Wireless Networks Requirement to the networks: Provides ubiquitous personal communications; Accommodate
Chapter 10: Wireless Networking School of information science and Engineering, SDU 10.1 Introduction to Wireless Networks Requirement to the networks: Provides ubiquitous personal communications; Accommodate
GPRS and UMTS T
 GPRS and UMTS T-110.2100 Global Packet Radio Service GPRS uses the time slots not used for circuit switched services Data rate depends on the availability of free time slots GPRS uses the multislot technique,
GPRS and UMTS T-110.2100 Global Packet Radio Service GPRS uses the time slots not used for circuit switched services Data rate depends on the availability of free time slots GPRS uses the multislot technique,
Wireless Network Introduction
 Wireless Network Introduction Module W.bas.1 Dr.M.Y.Wu@CSE Shanghai Jiaotong University Shanghai, China Dr.W.Shu@ECE University of New Mexico Albuquerque, NM, USA 1 Wireless network introduction W.bas.1-2
Wireless Network Introduction Module W.bas.1 Dr.M.Y.Wu@CSE Shanghai Jiaotong University Shanghai, China Dr.W.Shu@ECE University of New Mexico Albuquerque, NM, USA 1 Wireless network introduction W.bas.1-2
Mobility: vocabulary
 What is mobility? spectrum of mobility, from the perspective: no mobility high mobility mobile wireless user, using same access point mobile user, connecting/ disconnecting from using DHCP. mobile user,
What is mobility? spectrum of mobility, from the perspective: no mobility high mobility mobile wireless user, using same access point mobile user, connecting/ disconnecting from using DHCP. mobile user,
Practical Operator Considerations Cellular Analog Cellular Rogue Base Station Tumbling Cloning
 Practical Operator Considerations Cellular Analog Cellular Rogue Base Station Tumbling Cloning Getting paid Prevent (limit) subscriber fraud Ensure accurate clearing with other operators Reduce churn Ensure
Practical Operator Considerations Cellular Analog Cellular Rogue Base Station Tumbling Cloning Getting paid Prevent (limit) subscriber fraud Ensure accurate clearing with other operators Reduce churn Ensure
Mobile Security / /
 Mobile Security 96-835 / 18-639 / 14-829 Patrick Tague 2 Sept 2010 Class #4 Overview of Mobile/Cellular Systems Agenda Overview of mobile cellular systems System architecture and overview 2G, 2.5G, 2.75G,
Mobile Security 96-835 / 18-639 / 14-829 Patrick Tague 2 Sept 2010 Class #4 Overview of Mobile/Cellular Systems Agenda Overview of mobile cellular systems System architecture and overview 2G, 2.5G, 2.75G,
 Pilsung AB Taegyun A Fathur AB Afif A Hari A Gary A Dhika AB April AB Mulya AB Yusuf AB Anin A Rizka B Dion AB Siska AB Mirel AB Hani AB Airita AB Next Generation Network Soft Switch Long-Term Evolution
Pilsung AB Taegyun A Fathur AB Afif A Hari A Gary A Dhika AB April AB Mulya AB Yusuf AB Anin A Rizka B Dion AB Siska AB Mirel AB Hani AB Airita AB Next Generation Network Soft Switch Long-Term Evolution
Mobile Communications Chapter 11 : Outlook
 Prof. Dr.-Ing Jochen H. Schiller Inst. of Computer Science Freie Universität Berlin Germany Mobile Communications Chapter 11 : Outlook The future of mobile and wireless networks Is it 5G? All IP? Licensed?
Prof. Dr.-Ing Jochen H. Schiller Inst. of Computer Science Freie Universität Berlin Germany Mobile Communications Chapter 11 : Outlook The future of mobile and wireless networks Is it 5G? All IP? Licensed?
Wireless Networking: An Introduction. Hongwei Zhang
 Wireless Networking: An Introduction Hongwei Zhang http://www.cs.wayne.edu/~hzhang Outline Networking as resource allocation A taxonomy of current practice Technical elements Outline Networking as resource
Wireless Networking: An Introduction Hongwei Zhang http://www.cs.wayne.edu/~hzhang Outline Networking as resource allocation A taxonomy of current practice Technical elements Outline Networking as resource
Security functions in mobile communication systems
 Security functions in mobile communication systems Dr. Hannes Federrath University of Technology Dresden Security demands Security functions of GSM Known attacks on GSM Security functions of UMTS Concepts
Security functions in mobile communication systems Dr. Hannes Federrath University of Technology Dresden Security demands Security functions of GSM Known attacks on GSM Security functions of UMTS Concepts
Mobile and Sensor Systems
 Mobile and Sensor Systems Lecture 2: Mobile Medium Access Control Protocols and Wireless Systems Dr Cecilia Mascolo In this lecture We will describe medium access control protocols and wireless systems
Mobile and Sensor Systems Lecture 2: Mobile Medium Access Control Protocols and Wireless Systems Dr Cecilia Mascolo In this lecture We will describe medium access control protocols and wireless systems
Last time?! Block 3: Lecture 1! Wireless networks! Ingredients 2: Antennas! Ingredients 1: Mobile Phones, PDAs & Co.! 20/05/14. Part 3: lecture 3!
 20/05/14 Last time? WiFi Block 3: Lecture 1 Part 3: lecture 3 Wireless s Speed and ranges and channels Specifications DCF mechanisms WiMax Mobile s Ingredients 1: Mobile Phones, PDAs & Co. Ingredients
20/05/14 Last time? WiFi Block 3: Lecture 1 Part 3: lecture 3 Wireless s Speed and ranges and channels Specifications DCF mechanisms WiMax Mobile s Ingredients 1: Mobile Phones, PDAs & Co. Ingredients
Femtocell: Femtostep to the Holy Grail
 .... Femtocell: Femtostep to the Holy Grail Ravishankar Borgaonkar, Kévin Redon Technische Universität Berlin, SecT ravii/kredon@sec.t-labs.tu-berlin.de TROOPERS 2011, 30 March 2011 3G/UMTS femtocells
.... Femtocell: Femtostep to the Holy Grail Ravishankar Borgaonkar, Kévin Redon Technische Universität Berlin, SecT ravii/kredon@sec.t-labs.tu-berlin.de TROOPERS 2011, 30 March 2011 3G/UMTS femtocells
CSC 4900 Computer Networks: Wireless Networks
 CSC 4900 Computer Networks: Wireless Networks Professor Henry Carter Fall 2017 Last Time Mobile applications are taking off! What about current platforms is fueling this? How are an application s permission
CSC 4900 Computer Networks: Wireless Networks Professor Henry Carter Fall 2017 Last Time Mobile applications are taking off! What about current platforms is fueling this? How are an application s permission
Hands-On Modern Mobile and Long Term Evolution LTE
 Hands-On LTE Course Description With 3G mobile technologies already rolled out by over 200 operators in over 80 countries, standards bodies, manufacturers and operators are looking towards the next generation
Hands-On LTE Course Description With 3G mobile technologies already rolled out by over 200 operators in over 80 countries, standards bodies, manufacturers and operators are looking towards the next generation
Advanced Security for Systems Engineering VO 10: Mobile Applications
 Advanced Security for Systems Engineering VO 10: Mobile Applications Clemens Hlauschek Lukas Brandstetter Christian Schanes INSO Industrial Software Institute of Computer Aided Automation Faculty of Informatics
Advanced Security for Systems Engineering VO 10: Mobile Applications Clemens Hlauschek Lukas Brandstetter Christian Schanes INSO Industrial Software Institute of Computer Aided Automation Faculty of Informatics
Internal. GSM Fundamentals.
 Internal GSM Fundamentals www.huawei.com HUAWEI TECHNOLOGIES CO., LTD. All rights reserved Chapter 1 GSM System Overview Chapter 2 GSM Network Structure Chapter 3 Service Area and Number Planning Chapter
Internal GSM Fundamentals www.huawei.com HUAWEI TECHNOLOGIES CO., LTD. All rights reserved Chapter 1 GSM System Overview Chapter 2 GSM Network Structure Chapter 3 Service Area and Number Planning Chapter
Mobile Communications Chapter 11 : Outlook
 Mobile Communications Chapter 11 : Outlook The future of mobile and wireless networks Is it 4G? All IP? Licensed? Public? Private? Prof. Dr.-Ing. Jochen Schiller, http://www.jochenschiller.de/ MC SS05
Mobile Communications Chapter 11 : Outlook The future of mobile and wireless networks Is it 4G? All IP? Licensed? Public? Private? Prof. Dr.-Ing. Jochen Schiller, http://www.jochenschiller.de/ MC SS05
Evolution from 2G To 4G Mobile Telecommunication systems
 Evolution from 2G To 4G Mobile Telecommunication systems Wireless versus wireline Advantages : Mobility High efficiency in use of common Resources Wireless versus wireline Limitations : Multipath channel
Evolution from 2G To 4G Mobile Telecommunication systems Wireless versus wireline Advantages : Mobility High efficiency in use of common Resources Wireless versus wireline Limitations : Multipath channel
Chapter 7. Wireless and Mobile Networks. Computer Networking: A Top Down Approach
 Chapter 7 Wireless and Mobile Networks Computer Networking: A Top Down Approach 7 th edition Jim Kurose, Keith Ross Pearson/Addison Wesley April 2016 7-1 Background: # wireless (mobile) phone subscribers
Chapter 7 Wireless and Mobile Networks Computer Networking: A Top Down Approach 7 th edition Jim Kurose, Keith Ross Pearson/Addison Wesley April 2016 7-1 Background: # wireless (mobile) phone subscribers
International Journal of Scientific & Engineering Research, Volume 4, Issue 11, November-2013 ISSN
 7 Location Management Strategies in Mobile Networks Vivek Kumar Department of Computer Science & Engineering Graphic Era University, Dehradun, INDIA vivekror7@gmail.com Narayan Chaturvedi Department of
7 Location Management Strategies in Mobile Networks Vivek Kumar Department of Computer Science & Engineering Graphic Era University, Dehradun, INDIA vivekror7@gmail.com Narayan Chaturvedi Department of
EUROPEAN ETS TELECOMMUNICATION November 1996 STANDARD
 EUROPEAN ETS 300 522 TELECOMMUNICATION November 1996 STANDARD Third Edition Source: ETSI TC-SMG Reference: RE/SMG-030302PR2 ICS: 33.020 Key words: Digital cellular telecommunications system, Global System
EUROPEAN ETS 300 522 TELECOMMUNICATION November 1996 STANDARD Third Edition Source: ETSI TC-SMG Reference: RE/SMG-030302PR2 ICS: 33.020 Key words: Digital cellular telecommunications system, Global System
Contents. GSM and UMTS Security. Cellular Radio Network Architecture. Introduction to Mobile Telecommunications
 Royal Holloway, University of London, IC3 Network Security, 13 November 2006 Contents GSM and UMTS Security Introduction to mobile telecommunications Second generation systems - GSM security Third generation
Royal Holloway, University of London, IC3 Network Security, 13 November 2006 Contents GSM and UMTS Security Introduction to mobile telecommunications Second generation systems - GSM security Third generation
Mobile Security Fall 2014
 Mobile Security Fall 2014 Patrick Tague Class #3 Telecom Security Issues 1 Class #3 Brief history of telecom security Attacks on telecom networks A few project pitches 2 A3 RES A8 Kc RAND K more than And
Mobile Security Fall 2014 Patrick Tague Class #3 Telecom Security Issues 1 Class #3 Brief history of telecom security Attacks on telecom networks A few project pitches 2 A3 RES A8 Kc RAND K more than And
Advanced Computer Networks Exercise Session 4. Qin Yin Spring Semester 2013
 Advanced Computer Networks 263-3501-00 Exercise Session 4 Qin Yin Spring Semester 2013 1 Administration If you haven't received any email about your submission We got your solutions for A1 & A2 About solutions
Advanced Computer Networks 263-3501-00 Exercise Session 4 Qin Yin Spring Semester 2013 1 Administration If you haven't received any email about your submission We got your solutions for A1 & A2 About solutions
Defeating IMSI Catchers. Fabian van den Broek et al. CCS 2015
 Defeating IMSI Catchers Fabian van den Broek et al. CCS 2015 Ren-Jay Wang CS598 - COMPUTER SECURITY IN THE PHYSICAL ckground 3GPP 3GPP 3 rd Generation Partnership Project Encompasses: GSM and related 2G
Defeating IMSI Catchers Fabian van den Broek et al. CCS 2015 Ren-Jay Wang CS598 - COMPUTER SECURITY IN THE PHYSICAL ckground 3GPP 3GPP 3 rd Generation Partnership Project Encompasses: GSM and related 2G
Rab Nawaz Jadoon. Cellular Systems - II DCS. Assistant Professor. Department of Computer Science. COMSATS Institute of Information Technology
 Cellular Systems - II Rab Nawaz Jadoon DCS Assistant Professor COMSATS IIT, Abbottabad Pakistan COMSATS Institute of Information Technology Mobile Communication UMTS Architecture A UMTS network consist
Cellular Systems - II Rab Nawaz Jadoon DCS Assistant Professor COMSATS IIT, Abbottabad Pakistan COMSATS Institute of Information Technology Mobile Communication UMTS Architecture A UMTS network consist
Big Picture. ~10 years between generations
 Big Picture ~10 years between generations 7 Who is Who? Mobile Operators ITU Members ITU GSM, W-CDMA, UMTS IS-95), IS-41, IS- 2000, IS-835 Third Generation Patnership Project (3GPP) CWTS (China) Third
Big Picture ~10 years between generations 7 Who is Who? Mobile Operators ITU Members ITU GSM, W-CDMA, UMTS IS-95), IS-41, IS- 2000, IS-835 Third Generation Patnership Project (3GPP) CWTS (China) Third
GSM System Overview. Ph.D. Phone Lin.
 GSM System Overview Phone Lin Ph.D. Email: plin@csie.ntu.edu.tw 1 Outlines Introduction GSM Architecture Location Tracking and Call Setup Security GSM Data Services Unstructured Supplementary Service Data
GSM System Overview Phone Lin Ph.D. Email: plin@csie.ntu.edu.tw 1 Outlines Introduction GSM Architecture Location Tracking and Call Setup Security GSM Data Services Unstructured Supplementary Service Data
Mobile Communications
 Mobile Communications 3GPP Public Land Mobile Networks: GSM, GPRS Manuel P. Ricardo Faculdade de Engenharia da Universidade do Porto 1 What is the architecture of the GSM network network elements, interfaces,
Mobile Communications 3GPP Public Land Mobile Networks: GSM, GPRS Manuel P. Ricardo Faculdade de Engenharia da Universidade do Porto 1 What is the architecture of the GSM network network elements, interfaces,
GSM and Similar Architectures Lesson 13 GPRS
 GSM and Similar Architectures Lesson 13 GPRS 1 Two switching modes Circuit Switching Packet switching 2 Circuit switching A connection first sets up Then the entire data transmits through the path that
GSM and Similar Architectures Lesson 13 GPRS 1 Two switching modes Circuit Switching Packet switching 2 Circuit switching A connection first sets up Then the entire data transmits through the path that
3G Mobile UMTS. Raghavendra J 1, Anji Reddy Y 2, Deepak Kumar R 2, Ravi T 3
 International Journal of Scientific and Research Publications, Volume 2, Issue 12, December 2012 1 3G Mobile UMTS Raghavendra J 1, Anji Reddy Y 2, Deepak Kumar R 2, Ravi T 3 1,2 Final Year B.Tech, Dept.
International Journal of Scientific and Research Publications, Volume 2, Issue 12, December 2012 1 3G Mobile UMTS Raghavendra J 1, Anji Reddy Y 2, Deepak Kumar R 2, Ravi T 3 1,2 Final Year B.Tech, Dept.
Communication Systems for the Mobile Information Society
 Communication Systems for the Mobile Information Society Martin Sauter Nortel Networks, Germany John Wiley Si Sons, Ltd Contents Preface List of Figures List of Tables List of Abbreviations xi xiii xix
Communication Systems for the Mobile Information Society Martin Sauter Nortel Networks, Germany John Wiley Si Sons, Ltd Contents Preface List of Figures List of Tables List of Abbreviations xi xiii xix
LTE Security How Good Is It?
 SESSION ID: TECH-RO3 LTE Security How Good Is It? Jeffrey Cichonski IT Specialist (Security) National Institute of Standards & Technology @jchonski Joshua Franklin IT Specialist (Security) National Institute
SESSION ID: TECH-RO3 LTE Security How Good Is It? Jeffrey Cichonski IT Specialist (Security) National Institute of Standards & Technology @jchonski Joshua Franklin IT Specialist (Security) National Institute
COMP327 Mobile Computing Session:
 COMP327 Mobile Computing Session: 2018-2019 Lecture Set 5 - Wireless Communication [ last updated: 21 October 2018 ] 1 In this Lecture Set Review of the Evolution from 2G to 4G 2G Communications History,
COMP327 Mobile Computing Session: 2018-2019 Lecture Set 5 - Wireless Communication [ last updated: 21 October 2018 ] 1 In this Lecture Set Review of the Evolution from 2G to 4G 2G Communications History,
Design of a Routing Mechanism to Provide Multiple Mobile Network Service on a Single SIM Card Boobalan. P, Krishna. P, Udhayakumar. P, Santhosh.
 Design of a Routing Mechanism to Provide Multiple Mobile Network Service on a Single SIM Card Boobalan. P, Krishna. P, Udhayakumar. P, Santhosh. A Abstract-The current scenario in mobile networks is that
Design of a Routing Mechanism to Provide Multiple Mobile Network Service on a Single SIM Card Boobalan. P, Krishna. P, Udhayakumar. P, Santhosh. A Abstract-The current scenario in mobile networks is that
10 Call Set-up. Objectives After this chapter the student will: be able to describe the activities in the network during a call set-up.
 10 Call Set-up Objectives After this chapter the student will: be able to describe the activities in the network during a call set-up. 10.1 INTRODUCTION... 2 10.2 CALL TO MS (MT)... 3 10.3 CALL FROM MS
10 Call Set-up Objectives After this chapter the student will: be able to describe the activities in the network during a call set-up. 10.1 INTRODUCTION... 2 10.2 CALL TO MS (MT)... 3 10.3 CALL FROM MS
Glossary. xii. Marina Yue Zhang and Mark Dodgson Downloaded from Elgar Online at 02/04/ :16:01PM via free access
 Glossary 2.5G Second-and-a-half Generation mobile communications system 3G Third Generation mobile communications system 3GPP The Third Generation Partnership Project ADSL Asymmetric Digital Subscriber
Glossary 2.5G Second-and-a-half Generation mobile communications system 3G Third Generation mobile communications system 3GPP The Third Generation Partnership Project ADSL Asymmetric Digital Subscriber
Diminishing Signaling Traffic for Authentication in Mobile Communication System
 Diminishing Signaling Traffic for Authentication in Mobile Communication System Chi-Chun Lo and Kuen-Liang Sue Institute of Information Management National Chiao Tung University Hsinchu, Taiwan cclo@cc.nctu.edu.tw,
Diminishing Signaling Traffic for Authentication in Mobile Communication System Chi-Chun Lo and Kuen-Liang Sue Institute of Information Management National Chiao Tung University Hsinchu, Taiwan cclo@cc.nctu.edu.tw,
COPYRIGHTED MATERIAL. Introduction. Harri Holma and Antti Toskala. 1.1 WCDMA in Third-Generation Systems
 1 Introduction Harri Holma and Antti Toskala 1.1 WCDMA in Third-Generation Systems Analog cellular systems are commonly referred to as first-generation systems. The digital systems, such as Global System
1 Introduction Harri Holma and Antti Toskala 1.1 WCDMA in Third-Generation Systems Analog cellular systems are commonly referred to as first-generation systems. The digital systems, such as Global System
Mobile systems: an overview
 Mobile systems: an overview History A GSM Primer Packets over the air Going wideband Towards an all IP network Observations Mobile Networks: the history Mobile Business Evolution New mobile businesses
Mobile systems: an overview History A GSM Primer Packets over the air Going wideband Towards an all IP network Observations Mobile Networks: the history Mobile Business Evolution New mobile businesses
Secure and Authentication Communication in GSM, GPRS, and UMTS Using Asymmetric Cryptography.
 Secure and Authentication Communication in GSM, GPRS, and UMTS Using Asymmetric Cryptography T K Mohanta 1, R K Samantaray 2, S Panda 3 1. Dept.of Electronics & Communication.Engg, Sudhananda Engg & Research
Secure and Authentication Communication in GSM, GPRS, and UMTS Using Asymmetric Cryptography T K Mohanta 1, R K Samantaray 2, S Panda 3 1. Dept.of Electronics & Communication.Engg, Sudhananda Engg & Research
EKT 450 Mobile Communication System
 EKT 450 Mobile Communication System Chapter 1: Introduction to Mobile Communication System Prof Dr. Sabira Khatun, Dr. Muzammil Jusoh, Dr. Norsuhaida Ahmad School of Computer and Communication Engineering
EKT 450 Mobile Communication System Chapter 1: Introduction to Mobile Communication System Prof Dr. Sabira Khatun, Dr. Muzammil Jusoh, Dr. Norsuhaida Ahmad School of Computer and Communication Engineering
Välkomna till Avancerad Telekommunikation. Welcome to Advanced Telecommunication. Ulf Körner
 Välkomna till Avancerad Telekommunikation Welcome to Advanced Telecommunication Ulf Körner Advanced Telecommunication The course is devided into two parts: 1. Theoretical studies; (about 4.5 cr out of
Välkomna till Avancerad Telekommunikation Welcome to Advanced Telecommunication Ulf Körner Advanced Telecommunication The course is devided into two parts: 1. Theoretical studies; (about 4.5 cr out of
GOPALAN COLLEGE OF ENGINEERING AND MANAGEMENT Electronics and communication Department
 Appendix - F GOPALAN COLLEGE OF ENGINEERING AND MANAGEMENT Electronics and communication Department Academic Year: 2016-17 Semester: EVEN 6. COURSE PLAN Semester: VI Subject Code: 10EC81 Name of Subject:
Appendix - F GOPALAN COLLEGE OF ENGINEERING AND MANAGEMENT Electronics and communication Department Academic Year: 2016-17 Semester: EVEN 6. COURSE PLAN Semester: VI Subject Code: 10EC81 Name of Subject:
Implementing CDMA in TDMA Networks Leveraging the success of CDMA
 Implementing CDMA in TDMA Networks Leveraging the success of CDMA Place your image on top of this gray box. If no graphic is applicable, delete gray box and notch-out behind gray box, from the Title Master
Implementing CDMA in TDMA Networks Leveraging the success of CDMA Place your image on top of this gray box. If no graphic is applicable, delete gray box and notch-out behind gray box, from the Title Master
Optical Fiber 6 Days ( 1 Day Theoretical & 5 Days Practical ) Fiber Optic Cables Preparing & Splicing. Fiber Optic Cables Measurements
 Course Title: Transmission Technology Package Duration: 22 Days Optical Fiber 6 Days ( 1 Day Theoretical & 5 Days Practical ) Fiber Optic Fundamentals Fiber Optic Cables Preparing & Splicing Fiber Optic
Course Title: Transmission Technology Package Duration: 22 Days Optical Fiber 6 Days ( 1 Day Theoretical & 5 Days Practical ) Fiber Optic Fundamentals Fiber Optic Cables Preparing & Splicing Fiber Optic
Mobile Security Fall 2013
 Mobile Security 14-829 Fall 2013 Patrick Tague Class #4 Telecom System Security General Vulnerabilities Service interruption vulnerabilities Due to increased capacity offered by high speed communication
Mobile Security 14-829 Fall 2013 Patrick Tague Class #4 Telecom System Security General Vulnerabilities Service interruption vulnerabilities Due to increased capacity offered by high speed communication
Understanding Carrier Wireless Systems
 Understanding Course Description This course provides a detailed scope of modern mobile and cellular network technologies used for second generation, 2G+, 3G and 4G networks. It provides an understanding
Understanding Course Description This course provides a detailed scope of modern mobile and cellular network technologies used for second generation, 2G+, 3G and 4G networks. It provides an understanding
A COMPREHENSIVE SURVEY OF THE WIRELESS GENERATIONS
 INTERNATIONAL JOURNAL OF RESEARCH IN COMPUTER APPLICATIONS AND ROBOTICS ISSN 2320-7345 A COMPREHENSIVE SURVEY OF THE WIRELESS GENERATIONS Rajinder Vir H.No. 35 Street No: 8 Sadar Bazaar, Jalandhar Cantt.
INTERNATIONAL JOURNAL OF RESEARCH IN COMPUTER APPLICATIONS AND ROBOTICS ISSN 2320-7345 A COMPREHENSIVE SURVEY OF THE WIRELESS GENERATIONS Rajinder Vir H.No. 35 Street No: 8 Sadar Bazaar, Jalandhar Cantt.
Convergence of IP and Mobile Communications. Albert Coronel RedLink Communications Co., Ltd. MMNOG, November 21, 2015
 Convergence of IP and Mobile Communications Albert Coronel RedLink Communications Co., Ltd. MMNOG, November 21, 2015 Mobile terminals Netgear Skype phone first released 2007 Makes and receives Skype calls
Convergence of IP and Mobile Communications Albert Coronel RedLink Communications Co., Ltd. MMNOG, November 21, 2015 Mobile terminals Netgear Skype phone first released 2007 Makes and receives Skype calls
Seamless integration of heterogeneous wireless network technologies -?/!
 Seamless integration of heterogeneous wireless network technologies -?/! Jochen Schiller Computer Systems & Telematics Freie Universität Berlin Germany schiller@computer.org Prof. Dr.-Ing. Jochen Schiller,
Seamless integration of heterogeneous wireless network technologies -?/! Jochen Schiller Computer Systems & Telematics Freie Universität Berlin Germany schiller@computer.org Prof. Dr.-Ing. Jochen Schiller,
RF OPTIMIZATION FOR QUALITY IMPROVEMENT IN GSM NETWORK
 International Journal of Electrical Engineering & Technology (IJEET) Volume 6, Issue 8, Sep-Oct, 2015, pp.53-62, Article ID: IJEET_06_08_006 Available online at http://www.iaeme.com/ijeetissues.asp?jtype=ijeet&vtype=6&itype=8
International Journal of Electrical Engineering & Technology (IJEET) Volume 6, Issue 8, Sep-Oct, 2015, pp.53-62, Article ID: IJEET_06_08_006 Available online at http://www.iaeme.com/ijeetissues.asp?jtype=ijeet&vtype=6&itype=8
GSM and Mobile Telephony Trends
 Review Article AJTL 2018,1:4 American Journal of Transportation and Logistics (DOI:10.28933/AJTL) GSM and Mobile Telephony Trends Damilola Fowora*, Oludele Awodele, Olakunle Olayinka and Oyebode Aduragbemi
Review Article AJTL 2018,1:4 American Journal of Transportation and Logistics (DOI:10.28933/AJTL) GSM and Mobile Telephony Trends Damilola Fowora*, Oludele Awodele, Olakunle Olayinka and Oyebode Aduragbemi
REPORT ON GUEST LECTURER (INDUSTRY) BTS, GSM ARCHITECTURE & CALL FLOW IN GSM
 RADHAKRISHNA INSTITUTE OF TECHNOLOGY AND ENGINEERING REPORT ON GUEST LECTURER (INDUSTRY) BTS, GSM ARCHITECTURE & CALL FLOW IN GSM Background: Date and Venue: Electronic communications engineering is the
RADHAKRISHNA INSTITUTE OF TECHNOLOGY AND ENGINEERING REPORT ON GUEST LECTURER (INDUSTRY) BTS, GSM ARCHITECTURE & CALL FLOW IN GSM Background: Date and Venue: Electronic communications engineering is the
Connecting Mobile Phones to the Internet Simply (CoMPIS) IETF London DISPATCH WG Jim Forster, Mike Iedema, Harvind Samra - Range Networks Tim Panton
 Connecting Mobile Phones to the Internet Simply (CoMPIS) IETF London DISPATCH WG Jim Forster, Mike Iedema, Harvind Samra - Range Networks Tim Panton!1 Problem Statement Many people have no mobile service.
Connecting Mobile Phones to the Internet Simply (CoMPIS) IETF London DISPATCH WG Jim Forster, Mike Iedema, Harvind Samra - Range Networks Tim Panton!1 Problem Statement Many people have no mobile service.
Network Node for IMT-2000
 Network Node for IMT-2000 vkenya Tanaka vmitsuyuki Mizuno vkazuhiro Sato (Manuscript received August 30, 2002) Fujitsu has developed a Mobile Switching Node for IMT-2000 3G Networks. This system is an
Network Node for IMT-2000 vkenya Tanaka vmitsuyuki Mizuno vkazuhiro Sato (Manuscript received August 30, 2002) Fujitsu has developed a Mobile Switching Node for IMT-2000 3G Networks. This system is an
Evolution from GSM to UMTS (IMT-2000)*
 Evolution from GSM to UMTS (IMT-2000)* MARIO BAUMGARTEN Siemens Ltda ICN Sao Paulo - BRAZIL * This presentation is a draft submitted by the author and the final version will be available at: http://www.itu
Evolution from GSM to UMTS (IMT-2000)* MARIO BAUMGARTEN Siemens Ltda ICN Sao Paulo - BRAZIL * This presentation is a draft submitted by the author and the final version will be available at: http://www.itu
Beyond 3G Wireless. K.Raghunandan (RAGHU) Construction Administrator (Wireless) Communication Engineering New York City Transit (MTA)
 Beyond 3G Wireless K.Raghunandan (RAGHU) Construction Administrator (Wireless) Communication Engineering New York City Transit (MTA) 3G Deployments today Rev C? 3G -1X EVDO CDMA2000 Rev A 3G -1XRTT CDMA2000
Beyond 3G Wireless K.Raghunandan (RAGHU) Construction Administrator (Wireless) Communication Engineering New York City Transit (MTA) 3G Deployments today Rev C? 3G -1X EVDO CDMA2000 Rev A 3G -1XRTT CDMA2000
Performance Challenge of 3G over Satellite Methods for Increasing Revenue & Quality of Experience. February 2018
 Performance Challenge of 3G over Satellite Methods for Increasing Revenue & Quality of Experience February 2018 Mobile telephony has been in existence for over 40 years. The first generation (1G) developed
Performance Challenge of 3G over Satellite Methods for Increasing Revenue & Quality of Experience February 2018 Mobile telephony has been in existence for over 40 years. The first generation (1G) developed
EC Wireless Networks VIII - Semester Questions Bank
 EC 6802 - Wireless Networks VIII - Semester Questions Bank UNIT I PART A 1. Find out the capacity of a single IS-95 cell that uses QPSK modulation and convolutional coding 3 db < Sr < 9 db, and bandwidth
EC 6802 - Wireless Networks VIII - Semester Questions Bank UNIT I PART A 1. Find out the capacity of a single IS-95 cell that uses QPSK modulation and convolutional coding 3 db < Sr < 9 db, and bandwidth
COMP327 Mobile Computing Session: Lecture Set 7 - Wireless Communication
 COMP327 Mobile Computing Session: 2011-2012 Lecture Set 7 - Wireless Communication 1 In this Lecture Set Review of the Evolution from 2G to 3G 2G Communications History, Multiplexing and Handoff GPS /
COMP327 Mobile Computing Session: 2011-2012 Lecture Set 7 - Wireless Communication 1 In this Lecture Set Review of the Evolution from 2G to 3G 2G Communications History, Multiplexing and Handoff GPS /
CS 332 Computer Networks Wireless Networks
 CS 332 Computer Networks Wireless Networks Professor Szajda Chapter 6: Wireless and Mobile Networks Background: # wireless (mobile) phone subscribers now exceeds # wired phone subscribers! computer nets:
CS 332 Computer Networks Wireless Networks Professor Szajda Chapter 6: Wireless and Mobile Networks Background: # wireless (mobile) phone subscribers now exceeds # wired phone subscribers! computer nets:
GSM security country report: Thailand
 GSM security country report: Thailand GSM Map Project gsmmap@srlabs.de Security Research Labs, Berlin February 2013 Abstract. GSM networks differ widely in their protection capabilities against common
GSM security country report: Thailand GSM Map Project gsmmap@srlabs.de Security Research Labs, Berlin February 2013 Abstract. GSM networks differ widely in their protection capabilities against common
INTRODUCTION TO GSM DATA SERVICES. ETI25111 Monday, April 3, 2017
 INTRODUCTION TO GSM DATA SERVICES ETI25111 Monday, April 3, 2017 BASIC GSM SERVICES 1. Teleservices (a) Voice full-rate (13kbs) (b) Voice Half-rate (6.5 kbps) (c) SMS (up to 160 characters) (d) MMS (e)
INTRODUCTION TO GSM DATA SERVICES ETI25111 Monday, April 3, 2017 BASIC GSM SERVICES 1. Teleservices (a) Voice full-rate (13kbs) (b) Voice Half-rate (6.5 kbps) (c) SMS (up to 160 characters) (d) MMS (e)
G 364: Mobile and Wireless Networking. CLASS 19, Mon. Mar Stefano Basagni Spring 2004 M-W, 11:40am-1:20pm, 109 Rob
 G 364: Mobile and Wireless Networking CLASS 19, Mon. Mar. 22 2004 Stefano Basagni Spring 2004 M-W, 11:40am-1:20pm, 109 Rob Mobility Management Crucial problem in PCS Affect the performance of the system
G 364: Mobile and Wireless Networking CLASS 19, Mon. Mar. 22 2004 Stefano Basagni Spring 2004 M-W, 11:40am-1:20pm, 109 Rob Mobility Management Crucial problem in PCS Affect the performance of the system
