The State of the Trust Gap in 2015
|
|
|
- Joy McDaniel
- 5 years ago
- Views:
Transcription
1 The State of the Trust Gap in 2015 The widespread use of mobile devices for work has driven a profound change in how employees think about the privacy of their personal data on mobile devices. Ten years ago, employers provided employees with computers and software. So most employees simply took it for granted that their data and activities on that computer would be monitored by their employer. That changed with mobile devices because, regardless of whether the device is owned by the company or by the individual, it will almost certainly be used for both business and personal tasks. In 2013, MobileIron commissioned the first Trust Gap Survey conducted by Vision Critical in order to understand the mobile privacy expectations of employees. The goal was to develop a set of practical guidelines for employers to address privacy in a world where almost every mobile device is used for both personal and corporate purposes. In 2015, MobileIron repeated the study to see if employee expectations had changed. Conducted online by Harris Poll in Winter, more than 3,500 employed adults who use a mobile device for work in France, Germany, Japan, Spain, UK, and US were asked the same questions again. This whitepaper takes the findings from the 2015 Trust Gap Survey and translates them into actionable recommendations for employers in the form of privacy-centric mobile device policies. This white paper also reviews the privacy enhancements that Apple, Google, and Microsoft have made to their operating systems. When used with an enterprise mobility management (EMM) platform, these enhancements enable a more powerful set of privacy protections than was available even two years ago. Here are the findings from the 2015 Trust Gap Survey, MobileIron s recommendations for employers, and an overview of OS-level privacy controls. 1 The State of the Trust Gap in 2015 MKT-8997 v1.0
2 Trust is lower In 2013, 66% of these workers said they trust their employer to keep their personal information private. In 2015, this number dropped to 61% and 30% said they would leave their job if their employer could see their personal information, such as personal s, texts, or photos, on their smartphone or tablet. There s a lot of confusion about what employers can and cannot see Employees generally underestimate the visibility that employers have into company data, and overestimate the visibility that employers have into personal data. What can employers see? The answer varies by mobile operating system and company policy. On ios, for example, a typical employer could potentially see carrier, country, device make and model, OS version, phone number, location, list of installed apps, and corporate . But, even if they wanted to, employers could not see personal , text messages, photos, videos, voic , and web activity. The exception to this is data traffic that goes through the corporate network. Communication can help to bridge the Trust Gap Transparency drives trust. When employees trust their employer to protect their privacy, they more quickly adopt new mobile enterprise services and BYOD programs. Gen M workers are more comfortable with employers seeing personal information Earlier this year, MobileIron published research that identified a new demographic in the workplace: Generation Mobile, or Gen M. Gen M, which is composed of mobile workers who are either men age or those with children under age 18 in their households, relies more heavily on mobile technologies than the general population and are more likely to combine work and personal activities on the same mobile device, both in and out of the workplace. What was striking about Gen M was that they were significantly more likely than non-gen M workers to be comfortable with their employer seeing personal information on their mobile device. Among Gen M workers, 62% are comfortable with their employer seeing personal information on their mobile devices, compared to 51% of non-gen M workers. One reason for this may be that these groups do more social networking on mobile devices 2 The State of the Trust Gap in 2015
3 than other groups. According to the Pew Research Center, 67% of cell phone users age and 50% of cell phone users age used their mobile devices to participate in social media, and this overlaps with the Gen M demographic. This suggests that the Gen M demographic may be more comfortable with their employer seeing personal information because they already share a lot of it on public and semipublic forums. Establish clear and logical policies Because people use their mobile devices for both personal and business activities, mobile technology requires more communication about privacy with employees than any other enterprise technology. Employers should explain, in detail, not only what information they can see, but also what information they cannot see. In addition, employers should describe what actions the employer can take with regards to information on the mobile device. Finally, employers should explain why they may need to view or take action regarding the information they can access. Example 1: An employer may need to know if an employee is using their phone outside the country in order to send roaming alerts to prevent excessive data charges. Example 2: To protect corporate data, an employer may block a mobile device from accessing the corporate network if the employer s EMM platform detects that the device has been jailbroken or has otherwise been compromised. Communicate them clearly Once an employer has defined its policies and clarified the actions it can take on an employee s device, this information needs to be communicated to employees in a simple way. While an organization may require a formal Terms of Service contract, employee communications about privacy should be made separately using clear language that all employees can understand. Make privacy information obvious and accessible to employees A best practice is to present this information when employees are most likely to be thinking about it, for example, when they activate the EMM solution and set up their device. This could mean showing a pop-up screen similar to the experience of popular productivity apps like Evernote and Dropbox or putting the information in an easy-to-find page. 3 The State of the Trust Gap in 2015
4 What do employers need to be able to do? Most CIOs will tell you that they really do not want access to their employees personal content. What they want is the appropriate controls to prevent the loss or compromise of corporate information. Thus, employers need to be able to: Control data access Access to the corporate network Corporate and attachments Corporate documents stored in apps or in cloud repositories Browser traffic to corporate websites, intranets, etc. Monitor app integrity Prevent unauthorized apps from connecting to corporate resources. Enforce codes of conduct Ensure that employees are following the corporate code of conduct for technology use. This could include blocking devices with gambling apps or password spoofing apps from accessing the corporate network. Save and access data in response to litigation hold Employees need to understand that anything going through the company s corporate servers is saved for legal reasons. New OS-level privacy controls are now available Mobile operating systems have evolved since the first Trust Gap Survey in Apple, Google, and Microsoft recognize that almost every mobile device is a mixed-use device and, therefore, it is as important to protect user privacy as it is to protect corporate data. As a result, there are several key privacy features that employers can now activate at the OS level using an EMM platform. These include the following: Apple ios privacy controls Per-App VPN: Only traffic from corporate apps, not personal apps, will go through the corporate network. Managed Open-in: Personal documents can be blocked from being opened in corporate apps and corporate data can be prevented from being opened in personal apps. 4 The State of the Trust Gap in 2015
5 View only managed apps: Managed apps are ones that are distributed to an employee using the company s EMM platform. IT can choose to see the managed corporate apps installed on the device, not the personal apps. TouchID / Secure Enclave: Fingerprint data is encrypted so that no apps can access the actual fingerprint. Even though developers can prompt for TouchID, they only get a yes/no response for authentication. They do not get access to the credential. Health information collected by Apple s HealthKit platform cannot be accessed by IT or other apps without the user s explicit permission. Google Android for Work privacy controls Separated application containers: With Android for Work on Android L and above, there are separate containers for work and personal data. Administrators can decide if users can move data from personal containers into a work container. Users cannot move enterprise data to the personal container. App VPN and support for split tunneling: This enables VPN for specific apps, per container, and support for split tunneling so that only work-related data traffic is encrypted and sent to the VPN gateway. App differentiation: Android for Work features a suite of secure, badged PIM apps designed to help workers easily distinguish between personal and work apps on the device. Managed Chrome browser: IT can disable saving browser history. App permissions: With Android M, users will get a request from an app asking to access core parts of the device including location, camera, microphone, contacts, phone, SMS, calendar, and sensor. Windows 10 privacy controls App VPN: Allows only corporate apps into one corporate VPN so the personal apps on the device will not go through the corporate network. Enterprise data protection: Enterprise data is protected to ensure corporate data does not end up in personal applications. Users are still able to open personal data into enterprise applications. Managed Edge browser: IT can set the Edge browser to not track browsing history. Conclusion Since MobileIron first conducted the Trust Gap Survey two years ago, new technologies and features have been introduced at the operating system level by Apple, Google, and Microsoft that can help employers protect the privacy of their employees. While this gives companies more and better options, it also means they need to stay current on what s changing. In a world where smartphones and tablets contain increasing amounts of sensitive personal data, CIOs must remember that every device is a mixed-use device and they must protect employee privacy as fiercely as they protect corporate data. Trust Gap Survey methodology From December 17, 2014 to January 22, 2015, Harris Poll conducted an online survey on behalf of MobileIron of 3,521 full- or part-time workers who use a mobile device for work purposes in France (502), Germany (501), Japan (503), Spain (500), UK (503), and US (1012). Gen M (1,702) is defined as those who are male aged or those with children in the household under 18. The sample was weighted to the populations in each country by age, race/ethnicity, education, region, and household income data. MobileIron issued the original Trust Gap Study in July 2013, and the Gen M Study in April The State of the Trust Gap in 2015
Say Goodbye to Enterprise IT: Welcome to the Mobile First World. Sean Ginevan, Senior Director, Strategy Infosecurity Europe
 Say Goodbye to Enterprise IT: Welcome to the Mobile First World Sean Ginevan, Senior Director, Strategy Infosecurity Europe - 2015 Sean Ginevan Sr. Director, Strategy, MobileIron Linkedin.com/in/sginevan
Say Goodbye to Enterprise IT: Welcome to the Mobile First World Sean Ginevan, Senior Director, Strategy Infosecurity Europe - 2015 Sean Ginevan Sr. Director, Strategy, MobileIron Linkedin.com/in/sginevan
Securing Office 365 with MobileIron
 Securing Office 365 with MobileIron Introduction Office 365 is Microsoft s cloud-based productivity suite. It includes online versions of Microsoft s most popular solutions, like Exchange and SharePoint,
Securing Office 365 with MobileIron Introduction Office 365 is Microsoft s cloud-based productivity suite. It includes online versions of Microsoft s most popular solutions, like Exchange and SharePoint,
MOBILE SECURITY. Fixing the Disconnect Between Employer and Employee for BYOD (Bring Your Own Device)
 MOBILE SECURITY Fixing the Disconnect Between Employer and Employee for BYOD (Bring Your Own Device) INTRODUCTION BYOD SECURITY 2014 It s no surprise that there are many articles and papers on Bring Your
MOBILE SECURITY Fixing the Disconnect Between Employer and Employee for BYOD (Bring Your Own Device) INTRODUCTION BYOD SECURITY 2014 It s no surprise that there are many articles and papers on Bring Your
ANDROID PRIVACY & SECURITY GUIDE ANDROID DEVICE SETTINGS
 ANDROID PRIVACY & SECURITY GUIDE WESNET The Women s Services Network Smartphones store a lot of personal information, including email or social media accounts, reminders and notes, the number of steps
ANDROID PRIVACY & SECURITY GUIDE WESNET The Women s Services Network Smartphones store a lot of personal information, including email or social media accounts, reminders and notes, the number of steps
Zero Trust with Okta: A Modern Approach to Secure Access from Anywhere. How Okta enables a Zero Trust solution for our customers
 Zero Trust with Okta: A Modern Approach to Secure Access from Anywhere How Okta enables a Zero Trust solution for our customers Okta Inc. 301 Brannan Street, Suite 300 San Francisco, CA 94107 info@okta.com
Zero Trust with Okta: A Modern Approach to Secure Access from Anywhere How Okta enables a Zero Trust solution for our customers Okta Inc. 301 Brannan Street, Suite 300 San Francisco, CA 94107 info@okta.com
{ Mobile Printing Send Print Jobs from any Location }
 { Mobile Printing Send Print Jobs from any Location } Web Printer Driver Mobile Apps Mobile Printing Google Cloud Print Email/ Guest Printing Apple AirPrint Wep Upload The Next Step in Office Mobility
{ Mobile Printing Send Print Jobs from any Location } Web Printer Driver Mobile Apps Mobile Printing Google Cloud Print Email/ Guest Printing Apple AirPrint Wep Upload The Next Step in Office Mobility
As Enterprise Mobility Usage Escalates, So Does Security Risk
 YOUR SECURITY. CONNECTED WHITE PAPER As Enterprise Mobility Usage Escalates, So Does Security Risk Even as more organizations embrace the use of mobile devices by employees and customers to access services
YOUR SECURITY. CONNECTED WHITE PAPER As Enterprise Mobility Usage Escalates, So Does Security Risk Even as more organizations embrace the use of mobile devices by employees and customers to access services
The Future of Mobile Device Management
 The Future of Mobile Device Management Simplifying the move from BlackBerry to a multi-os environment MobileIron Advisory Services 415 E. Middlefield Road Mountain View, CA 94043 www.mobileiron.com Table
The Future of Mobile Device Management Simplifying the move from BlackBerry to a multi-os environment MobileIron Advisory Services 415 E. Middlefield Road Mountain View, CA 94043 www.mobileiron.com Table
Securing Wireless Mobile Devices. Lamaris Davis. East Carolina University 11/15/2013
 Securing Wireless Mobile Devices Lamaris Davis East Carolina University 11/15/2013 Attract As more employees prefer to use mobile devices in the workplace, organizations are starting to adopt the Bring
Securing Wireless Mobile Devices Lamaris Davis East Carolina University 11/15/2013 Attract As more employees prefer to use mobile devices in the workplace, organizations are starting to adopt the Bring
Survey Guide: Businesses Should Begin Preparing for the Death of the Password
 Survey Guide: Businesses Should Begin Preparing for the Death of the Password Survey Guide: Businesses Should Begin Preparing for the Death of the Password The way digital enterprises connect with their
Survey Guide: Businesses Should Begin Preparing for the Death of the Password Survey Guide: Businesses Should Begin Preparing for the Death of the Password The way digital enterprises connect with their
GLOBALPROTECT. Key Usage Scenarios and Benefits. Remote Access VPN Provides secure access to internal and cloud-based business applications
 GLOBALPROTECT Prevent Breaches and Secure the Mobile Workforce GlobalProtect extends the protection of Palo Alto Networks Next-Generation Security Platform to the members of your mobile workforce, no matter
GLOBALPROTECT Prevent Breaches and Secure the Mobile Workforce GlobalProtect extends the protection of Palo Alto Networks Next-Generation Security Platform to the members of your mobile workforce, no matter
Enterprise Mobile Management (EMM) Policies
 Enterprise Mobile Management (EMM) Policies Best Practices Guide Copyright 2016 Fiberlink, an IBM Company. All rights reserved. Information in this document is subject to change without notice. The software
Enterprise Mobile Management (EMM) Policies Best Practices Guide Copyright 2016 Fiberlink, an IBM Company. All rights reserved. Information in this document is subject to change without notice. The software
Auditing Bring Your Own Devices (BYOD) Risks. Shannon Buckley
 Auditing Bring Your Own Devices (BYOD) Risks Shannon Buckley Agenda 1. Understanding the trend towards BYOD. 2. Weighing up the cost benefit vs. the risks. 3. Identifying and mitigating the risks. 4. Tips
Auditing Bring Your Own Devices (BYOD) Risks Shannon Buckley Agenda 1. Understanding the trend towards BYOD. 2. Weighing up the cost benefit vs. the risks. 3. Identifying and mitigating the risks. 4. Tips
SIMPLIFY MULTI-PLATFORM ENTERPRISE MOBILITY MANAGEMENT
 DATASHEET SIMPLIFY MULTI-PLATFORM ENTERPRISE MOBILITY MANAGEMENT Silver level EMM Enterprise Mobility Management for Corporate-owned and BYOD devices BlackBerry Enterprise Service 10 is a powerful device,
DATASHEET SIMPLIFY MULTI-PLATFORM ENTERPRISE MOBILITY MANAGEMENT Silver level EMM Enterprise Mobility Management for Corporate-owned and BYOD devices BlackBerry Enterprise Service 10 is a powerful device,
SECURE, CENTRALIZED, SIMPLE
 1 SECURE, CENTRALIZED, SIMPLE Multi-platform Enterprise Mobility Management Whitepaper 2 Controlling it all from one place BlackBerry Enterprise Service 10 (BES10) is an end-to-end, multi-platform, device,
1 SECURE, CENTRALIZED, SIMPLE Multi-platform Enterprise Mobility Management Whitepaper 2 Controlling it all from one place BlackBerry Enterprise Service 10 (BES10) is an end-to-end, multi-platform, device,
Mobile Devices prioritize User Experience
 Mobile Security 1 Uniqueness of Mobile Mobile Devices are Shared More Often Mobile Devices are Used in More Locations Mobile Devices prioritize User Experience Mobile Devices have multiple personas Mobile
Mobile Security 1 Uniqueness of Mobile Mobile Devices are Shared More Often Mobile Devices are Used in More Locations Mobile Devices prioritize User Experience Mobile Devices have multiple personas Mobile
Bring Your Own Device. Peter Silva Technical Marketing Manager
 Bring Your Own Device Peter Silva Technical Marketing Manager Bring-Your-Own-Device (BYOD) Personal devices for business apps Why implement BYOD? Increase employee satisfaction, productivity Reduce mobile
Bring Your Own Device Peter Silva Technical Marketing Manager Bring-Your-Own-Device (BYOD) Personal devices for business apps Why implement BYOD? Increase employee satisfaction, productivity Reduce mobile
Citrix XenMobile and Windows 10
 White Paper Citrix XenMobile and Windows 10 Citrix XenMobile and Windows 10 With version 10, Windows has moved the once desktop operating system firmly into the era of the mobility and the cloud. Windows
White Paper Citrix XenMobile and Windows 10 Citrix XenMobile and Windows 10 With version 10, Windows has moved the once desktop operating system firmly into the era of the mobility and the cloud. Windows
THE IMPACT OF MOBILE DEVICES ON INFORMATION SECURITY:
 June 2013 Sponsored by Introduction Mobile devices cause ongoing concern for IT teams responsible for information security. Sensitive corporate information can be easily transported and lost, while the
June 2013 Sponsored by Introduction Mobile devices cause ongoing concern for IT teams responsible for information security. Sensitive corporate information can be easily transported and lost, while the
Enterprise Mobility Management: completing the EMM story
 Enterprise Mobility Management: completing the EMM story Contents BYOD & EMM 3 Enterprise Mobility Management what is it? 4 Accessing corporate systems, apps 5 and data with EMM Apps in the container 6
Enterprise Mobility Management: completing the EMM story Contents BYOD & EMM 3 Enterprise Mobility Management what is it? 4 Accessing corporate systems, apps 5 and data with EMM Apps in the container 6
SEPARATING WORK AND PERSONAL
 SEPARATING WORK AND PERSONAL How Balance Works at the Platform Level Whitepaper 2 Why balance matters in enterprise mobility As more and more business processes go mobile, IT faces an ever-increasing number
SEPARATING WORK AND PERSONAL How Balance Works at the Platform Level Whitepaper 2 Why balance matters in enterprise mobility As more and more business processes go mobile, IT faces an ever-increasing number
MOBILEIRON: ANDROID ENTERPRISE UPGRADE GUIDE
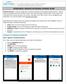 MOBILEIRON: ANDROID ENTERPRISE UPGRADE GUIDE Android Enterprise is a special configuration available to Nougat (7.0) and higher Android devices. Android Enterprise separates your personal life from your
MOBILEIRON: ANDROID ENTERPRISE UPGRADE GUIDE Android Enterprise is a special configuration available to Nougat (7.0) and higher Android devices. Android Enterprise separates your personal life from your
RHM Presentation. Maas 360 Mobile device management
 RHM Presentation Maas 360 Mobile device management Strong adoption in the enterprise Manufacturing Financial Consumer Healthcare Public Others 2 Trusted by over 9,000 customers Recognized Industry Leadership
RHM Presentation Maas 360 Mobile device management Strong adoption in the enterprise Manufacturing Financial Consumer Healthcare Public Others 2 Trusted by over 9,000 customers Recognized Industry Leadership
How to Build a Culture of Security
 How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
U.S. Mobile Benchmark Report
 U.S. Mobile Benchmark Report ADOBE DIGITAL INDEX 2014 80% 40% Methodology Report based on aggregate and anonymous data across retail, media, entertainment, financial service, and travel websites. Behavioral
U.S. Mobile Benchmark Report ADOBE DIGITAL INDEX 2014 80% 40% Methodology Report based on aggregate and anonymous data across retail, media, entertainment, financial service, and travel websites. Behavioral
A Mobile Security Checklist: The Top Ten Threats to Your Enterprise Today. White Paper
 A Mobile Security Checklist: The Top Ten Threats to Your Enterprise Today White Paper As enterprises mobilize business processes, more and more sensitive data passes through and resides on mobile devices.
A Mobile Security Checklist: The Top Ten Threats to Your Enterprise Today White Paper As enterprises mobilize business processes, more and more sensitive data passes through and resides on mobile devices.
Xperia TM. in Business. Product overview. Read about the enterprise policies and features supported in Xperia devices.
 Xperia TM in Business Product overview Read about the enterprise policies and features supported in Xperia devices February 2017 About this document Products covered This document describes Xperia in Business
Xperia TM in Business Product overview Read about the enterprise policies and features supported in Xperia devices February 2017 About this document Products covered This document describes Xperia in Business
MaaS360 Secure Productivity Suite
 MaaS360 Secure Productivity Suite Frequently Asked Questions (FAQs) What is MaaS360 Secure Productivity Suite? MaaS360 Secure Productivity Suite integrates a set of comprehensive mobile security and productivity
MaaS360 Secure Productivity Suite Frequently Asked Questions (FAQs) What is MaaS360 Secure Productivity Suite? MaaS360 Secure Productivity Suite integrates a set of comprehensive mobile security and productivity
Cloud UC. Program Downloads I WOULD LIKE TO... DOWNLOADING THE CLIENT SOFTWARE
 I WOULD LIKE TO... Cloud UC Program Downloads Avaya Cloud allows you to setup your telephone to be used the way you want it to. There are additional programs that extend the abilities of the application
I WOULD LIKE TO... Cloud UC Program Downloads Avaya Cloud allows you to setup your telephone to be used the way you want it to. There are additional programs that extend the abilities of the application
US 2013 Consumer Data Privacy Study Mobile Edition
 RESEARCH REPORT US 2013 Consumer Data Privacy Study Mobile Edition 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0
RESEARCH REPORT US 2013 Consumer Data Privacy Study Mobile Edition 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0 1 0
Unlocking Office 365 without a password. How to Secure Access to Your Business Information in the Cloud without needing to remember another password.
 Unlocking Office 365 without a password How to Secure Access to Your Business Information in the Cloud without needing to remember another password. Introduction It is highly likely that if you have downloaded
Unlocking Office 365 without a password How to Secure Access to Your Business Information in the Cloud without needing to remember another password. Introduction It is highly likely that if you have downloaded
WDC RDS Connection for Android Users
 WDC RDS Connection for Android Users Introduction The WDC Remote Desktop Service (RDS) can be connected to most personal computer devices, including Android Smartphones and tablets, even though the RD
WDC RDS Connection for Android Users Introduction The WDC Remote Desktop Service (RDS) can be connected to most personal computer devices, including Android Smartphones and tablets, even though the RD
Xperia TM. in Business. Product overview. Read about the enterprise policies and features supported in Xperia devices. March 2018
 Xperia TM in Business Product overview Read about the enterprise policies and features supported in Xperia devices March 2018 About this document Products covered This document describes Xperia in Business
Xperia TM in Business Product overview Read about the enterprise policies and features supported in Xperia devices March 2018 About this document Products covered This document describes Xperia in Business
Accessing CharityMaster data from another location
 Accessing CharityMaster data from another location When all of your computers are on the same Local Area Network (LAN), you can place the back end files (including your data and the Word templates) onto
Accessing CharityMaster data from another location When all of your computers are on the same Local Area Network (LAN), you can place the back end files (including your data and the Word templates) onto
3-Part Guide to Developing a BYOD Strategy
 An IT admin s guide to implementation considerations and best practices when developing a BYOD strategy As the consumerization of IT continues to grow, so has the popularity of Bring Your Own Device (BYOD)
An IT admin s guide to implementation considerations and best practices when developing a BYOD strategy As the consumerization of IT continues to grow, so has the popularity of Bring Your Own Device (BYOD)
PRIVACY POLICY QUICK GUIDE TO CONTENTS
 PRIVACY POLICY This privacy policy describes the policies and practices of Comodo Security Solutions, Inc. and Comodo Security Solutions Ltd. (collectively and individually referred to herein as "Comodo"),
PRIVACY POLICY This privacy policy describes the policies and practices of Comodo Security Solutions, Inc. and Comodo Security Solutions Ltd. (collectively and individually referred to herein as "Comodo"),
Google on BeyondCorp: Empowering employees with security for the cloud era
 SESSION ID: EXP-F02 Google on BeyondCorp: Empowering employees with security for the cloud era Jennifer Lin Director, Product Management, Security & Privacy Google Cloud What is BeyondCorp? Enterprise
SESSION ID: EXP-F02 Google on BeyondCorp: Empowering employees with security for the cloud era Jennifer Lin Director, Product Management, Security & Privacy Google Cloud What is BeyondCorp? Enterprise
State of Mobile Commerce. Q
 State of Mobile Commerce. Q4 2014. JANUARY 2015 Executive Summary. Mobile commerce adoption is far ahead of expectations. Globally, mobile now accounts for 30% of ecommerce transactions. It is expected
State of Mobile Commerce. Q4 2014. JANUARY 2015 Executive Summary. Mobile commerce adoption is far ahead of expectations. Globally, mobile now accounts for 30% of ecommerce transactions. It is expected
Managing Devices and Corporate Data on ios
 Managing Devices and Corporate Data on ios Overview Businesses everywhere are empowering their employees with iphone and ipad. Contents Overview Management Basics Separating Work and Personal Data Flexible
Managing Devices and Corporate Data on ios Overview Businesses everywhere are empowering their employees with iphone and ipad. Contents Overview Management Basics Separating Work and Personal Data Flexible
WHITE PAPER AIRWATCH SUPPORT FOR OFFICE 365
 WHITE PAPER AIRWATCH SUPPORT FOR OFFICE 365 Airwatch Support for Office 365 One of the most common questions being asked by many customers recently is How does AirWatch support Office 365? Customers often
WHITE PAPER AIRWATCH SUPPORT FOR OFFICE 365 Airwatch Support for Office 365 One of the most common questions being asked by many customers recently is How does AirWatch support Office 365? Customers often
3. How is technology used to serve our advertisements on other Sites that you visit and what choices do you have?
 Privacy Policy for U.S. Websites Scope. This Privacy Policy applies to personal information collected online, used and disclosed by Stanley Black & Decker, Inc. s affiliates including but not limited to
Privacy Policy for U.S. Websites Scope. This Privacy Policy applies to personal information collected online, used and disclosed by Stanley Black & Decker, Inc. s affiliates including but not limited to
BYOD Success Kit. Table of Contents. Current state of BYOD in enterprise Checklist for BYOD Success Helpful Pilot Tips
 Table of Contents Current state of BYOD in enterprise Checklist for BYOD Success Helpful Pilot Tips 2 Current State of BYOD in the Enterprise Defining BYOD Bring-Your-Own-Device (BYOD): a business practice
Table of Contents Current state of BYOD in enterprise Checklist for BYOD Success Helpful Pilot Tips 2 Current State of BYOD in the Enterprise Defining BYOD Bring-Your-Own-Device (BYOD): a business practice
Privacy, Law, and Smartphones
 CyLab Privacy, Law, and Smartphones Engineering & Public Policy acy & Secur ity Priv e l :// C DU HT TP ratory bo La Oct. 29, 2015 CyLab U sab Rebecca Balebako U P S.C S.C M U.E 1 Agenda Quiz Reading discussion
CyLab Privacy, Law, and Smartphones Engineering & Public Policy acy & Secur ity Priv e l :// C DU HT TP ratory bo La Oct. 29, 2015 CyLab U sab Rebecca Balebako U P S.C S.C M U.E 1 Agenda Quiz Reading discussion
Survey Questions and Methodology
 Survey Questions and Methodology Winter Tracking Survey 2012 Final Topline 02/22/2012 Data for January 20 February 19, 2012 Princeton Survey Research Associates International for the Pew Research Center
Survey Questions and Methodology Winter Tracking Survey 2012 Final Topline 02/22/2012 Data for January 20 February 19, 2012 Princeton Survey Research Associates International for the Pew Research Center
Cloud Platform. Version User's Guide
 Cloud Platform Version 1.1.5 User's Guide January 2018 www.lexmark.com Contents 2 Contents Change history... 3 Overview... 4 Getting started... 5 System requirements...5 Accessing the Cloud Platform home
Cloud Platform Version 1.1.5 User's Guide January 2018 www.lexmark.com Contents 2 Contents Change history... 3 Overview... 4 Getting started... 5 System requirements...5 Accessing the Cloud Platform home
Securing Enterprise or User Brought mobile devices
 Securing Enterprise or User Brought mobile devices Wilfried Baeten Business Line Director Projects&Consulting Econocom Managed Services 20/09/2013 WWW.ECONOCOM.COM Agenda Introduction The mobile security
Securing Enterprise or User Brought mobile devices Wilfried Baeten Business Line Director Projects&Consulting Econocom Managed Services 20/09/2013 WWW.ECONOCOM.COM Agenda Introduction The mobile security
Enterprise Guest Access
 Data Sheet Published Date July 2015 Service Overview Whether large or small, companies have guests. Guests can be virtually anyone who conducts business with the company but is not an employee. Many of
Data Sheet Published Date July 2015 Service Overview Whether large or small, companies have guests. Guests can be virtually anyone who conducts business with the company but is not an employee. Many of
How to find your IP address information
 How to set up a VPN server on Windows 10 Source: https://pureinfotech.com/setup-vpn-server-windows-10/ Here are the step-by-step instructions to set up a VPN server using the built-in Incoming Connection
How to set up a VPN server on Windows 10 Source: https://pureinfotech.com/setup-vpn-server-windows-10/ Here are the step-by-step instructions to set up a VPN server using the built-in Incoming Connection
Exploring the potential of Mobile Connect: From authentication to identity and attribute sharing. Janne Jutila, Head of Business Development, GSMA
 Exploring the potential of Mobile Connect: From authentication to identity and attribute sharing Janne Jutila, Head of Business Development, GSMA Fragility of passwords No matter what you tell them, users
Exploring the potential of Mobile Connect: From authentication to identity and attribute sharing Janne Jutila, Head of Business Development, GSMA Fragility of passwords No matter what you tell them, users
Fencing the Cloud. Roger Casals. Senior Director Product Management. Shared vision for the Identity: Fencing the Cloud 1
 Fencing the Cloud with Identity Roger Casals Senior Director Product Management Shared vision for the Identity: Fencing the Cloud 1 Disclaimer Copyright 2014 Symantec Corporation. All rights reserved.
Fencing the Cloud with Identity Roger Casals Senior Director Product Management Shared vision for the Identity: Fencing the Cloud 1 Disclaimer Copyright 2014 Symantec Corporation. All rights reserved.
Mobile Internet & Smartphone Adoption
 Mobile Internet & Smartphone Adoption New Insights into Consumer Usage of Mobile Devices, the Shift to Smartphones & the Emergence of Tablets United States (US), United Kingdom (UK), Germany (DE), France
Mobile Internet & Smartphone Adoption New Insights into Consumer Usage of Mobile Devices, the Shift to Smartphones & the Emergence of Tablets United States (US), United Kingdom (UK), Germany (DE), France
Smartphone Ownership 2013 Update
 www.pewresearch.org JUNE 5, 2013 Smartphone Ownership 2013 Update 56% of American adults now own a smartphone of some kind; Android and iphone owners account for half of the cell phone user population.
www.pewresearch.org JUNE 5, 2013 Smartphone Ownership 2013 Update 56% of American adults now own a smartphone of some kind; Android and iphone owners account for half of the cell phone user population.
The Smartphone Consumer June 2012
 The Smartphone Consumer 2012 June 2012 Methodology In January/February 2012, Edison Research and Arbitron conducted a national telephone survey offered in both English and Spanish language (landline and
The Smartphone Consumer 2012 June 2012 Methodology In January/February 2012, Edison Research and Arbitron conducted a national telephone survey offered in both English and Spanish language (landline and
Dr. Jassine Boulkheir International Sales and Marketing Manager
 Dr. Jassine Boulkheir International Sales and Marketing Manager ybo@bit4id.com www.bit4id.com About BIT4ID Established in 2004 with headquarters in Italy, Bit4id was born to make simple, secure and consistent
Dr. Jassine Boulkheir International Sales and Marketing Manager ybo@bit4id.com www.bit4id.com About BIT4ID Established in 2004 with headquarters in Italy, Bit4id was born to make simple, secure and consistent
BYOD: BRING YOUR OWN DEVICE.
 white paper BYOD: BRING YOUR OWN DEVICE. On-BOaRDING and Securing DEVICES IN YOUR Corporate NetWORk PrepaRING YOUR NetWORk to MEEt DEVICE DEMaND The proliferation of smartphones and tablets brings increased
white paper BYOD: BRING YOUR OWN DEVICE. On-BOaRDING and Securing DEVICES IN YOUR Corporate NetWORk PrepaRING YOUR NetWORk to MEEt DEVICE DEMaND The proliferation of smartphones and tablets brings increased
Organization information. When you create an organization on icentrex, we collect your address (as the Organization Owner), your
 Privacy policy icentrex Sweden AB Privacy Policy Updated: November 3, 2017 This privacy policy is here to help you understand what information we collect at icentrex, how we use it, and what choices you
Privacy policy icentrex Sweden AB Privacy Policy Updated: November 3, 2017 This privacy policy is here to help you understand what information we collect at icentrex, how we use it, and what choices you
Purchase Intentions Spring 2013 EMEA
 Consumerization of IT and BYOD Plans Purchase Intentions Spring 2013 EMEA 1 Key Takeaways: Primary drivers of BYOD: - To make workers more productive - To make worker collaboration better - Pressure from
Consumerization of IT and BYOD Plans Purchase Intentions Spring 2013 EMEA 1 Key Takeaways: Primary drivers of BYOD: - To make workers more productive - To make worker collaboration better - Pressure from
WHITEPAPER. How to secure your Post-perimeter world
 How to secure your Post-perimeter world WHAT IS THE POST-PERIMETER WORLD? In an increasingly cloud and mobile focused world, there are three key realities enterprises must consider in order to move forward
How to secure your Post-perimeter world WHAT IS THE POST-PERIMETER WORLD? In an increasingly cloud and mobile focused world, there are three key realities enterprises must consider in order to move forward
TIS/App Delivery Mobility Job Aid: Install and Configure Microsoft Outlook on Your Android Phone. Overview. Job Aid: Outlook for Mobile - Android
 TIS/App Delivery Mobility Job Aid: Install and Configure Microsoft Outlook on Your Android Phone Job Aid: Outlook for Mobile - Android Overview The job aid is for Colleagues that want to access Outlook
TIS/App Delivery Mobility Job Aid: Install and Configure Microsoft Outlook on Your Android Phone Job Aid: Outlook for Mobile - Android Overview The job aid is for Colleagues that want to access Outlook
Thanks for using Dropbox! Here we describe how we collect, use and handle your information when
 Dropbox Privacy Policy Posted: October 3December 8, 2016 Effective: February 10, 2017 Thanks for using Dropbox! Here we describe how we collect, use and handle your information when you use our websites,
Dropbox Privacy Policy Posted: October 3December 8, 2016 Effective: February 10, 2017 Thanks for using Dropbox! Here we describe how we collect, use and handle your information when you use our websites,
Duo Security Enrollment Guide
 Duo Security Enrollment Guide Duo's self-enrollment process makes it easy to register your phone and install the Duo Mobile application on your smartphone or tablet. Supported Browsers: Chrome, Firefox,
Duo Security Enrollment Guide Duo's self-enrollment process makes it easy to register your phone and install the Duo Mobile application on your smartphone or tablet. Supported Browsers: Chrome, Firefox,
Enable the Always Offline Mode to Provide Faster Access to Files
 Enable the Always Offline Mode to Provide Faster Access to Files 13 out of 16 rated this helpful - Rate this topic Published: April 18, 2012 Updated: July 3, 2013 Applies To: Windows 8, Windows 8.1, Windows
Enable the Always Offline Mode to Provide Faster Access to Files 13 out of 16 rated this helpful - Rate this topic Published: April 18, 2012 Updated: July 3, 2013 Applies To: Windows 8, Windows 8.1, Windows
BELTUG Market Trends Survey Results V-ICT-OR members - August 2015
 BELTUG Market Trends Survey 2015 Results V-ICT-OR members - August 2015 P. 1 - BELTUG market study - results V-ICT-OR members June 2015 1. Why a BELTUG V-ICT-OR Survey? 2. Who answered for V-ICT-OR? 3.
BELTUG Market Trends Survey 2015 Results V-ICT-OR members - August 2015 P. 1 - BELTUG market study - results V-ICT-OR members June 2015 1. Why a BELTUG V-ICT-OR Survey? 2. Who answered for V-ICT-OR? 3.
Thomas Lippert Principal Product Manager. Sophos Mobile. Spring 2017
 Thomas Lippert Principal Product Manager Sophos Mobile Spring 2017 Market Overview Trends Security or data breaches involving mobile devices are on the rise More people use mobile devices for work than
Thomas Lippert Principal Product Manager Sophos Mobile Spring 2017 Market Overview Trends Security or data breaches involving mobile devices are on the rise More people use mobile devices for work than
REGISTERING YOUR BYOD DEVICE
 REGISTERING YOUR BYOD DEVICE Bring Your Own Device (BYOD) Registration for Android Devices with MobileIron The MobileIron app (Mobile@Work) connects your Android device to the MobileIron server and provides
REGISTERING YOUR BYOD DEVICE Bring Your Own Device (BYOD) Registration for Android Devices with MobileIron The MobileIron app (Mobile@Work) connects your Android device to the MobileIron server and provides
Daymar College is excited to announce the launch of our NEW Daymar App, available on Apple and Android devices.
 Daymar College is excited to announce the launch of our NEW Daymar App, available on Apple and Android devices. Students and Alumni can easily stay connected with the latest school news and events on their
Daymar College is excited to announce the launch of our NEW Daymar App, available on Apple and Android devices. Students and Alumni can easily stay connected with the latest school news and events on their
INSIGHT on the Issues
 INSIGHT on the Issues Improving Mobile Device Privacy Disclosures Neal Walters AARP Public Policy Institute AARP Public Policy Institute There is increasing concern about the amount of personal information
INSIGHT on the Issues Improving Mobile Device Privacy Disclosures Neal Walters AARP Public Policy Institute AARP Public Policy Institute There is increasing concern about the amount of personal information
2016 BITGLASS, INC. mobile. solution brief
 mobile solution brief BYOD Security has been a constant challenge for many enterprises. Stories of failed MDM deployments are rampant, with firms struggling achieve meaningful adoption. According to the
mobile solution brief BYOD Security has been a constant challenge for many enterprises. Stories of failed MDM deployments are rampant, with firms struggling achieve meaningful adoption. According to the
The State of Mobile Advertising Q2 2012
 Q2 2012 Executive summary In our first edition of the State of Mobile Advertising report, we take an in-depth look at the monetization of mobile advertising from four perspectives within the ad delivery
Q2 2012 Executive summary In our first edition of the State of Mobile Advertising report, we take an in-depth look at the monetization of mobile advertising from four perspectives within the ad delivery
owncloud Android App Manual
 owncloud Android App Manual Release 2.7.0 The owncloud developers October 30, 2018 CONTENTS 1 Release Notes 1 1.1 Changes in 2.7.0............................................. 1 1.2 Changes in 2.6.0.............................................
owncloud Android App Manual Release 2.7.0 The owncloud developers October 30, 2018 CONTENTS 1 Release Notes 1 1.1 Changes in 2.7.0............................................. 1 1.2 Changes in 2.6.0.............................................
BYOD Risks, Challenges and Solutions. The primary challenges companies face when it comes to BYOD and how these challenges can be handled
 BYOD Risks, Challenges and Solutions. The primary challenges companies face when it comes to BYOD and how these challenges can be handled effectively. Contents Introduction.... 3 Primary Bring Your Own
BYOD Risks, Challenges and Solutions. The primary challenges companies face when it comes to BYOD and how these challenges can be handled effectively. Contents Introduction.... 3 Primary Bring Your Own
Getting Started Accessing Okta All Employees
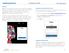 Purpose Okta is a cloud platform that provides single sign-on for Magellan applications. HR systems such as Workday, Saba, VERN along with communication platforms and collaboration tools such as MagellanNOW,
Purpose Okta is a cloud platform that provides single sign-on for Magellan applications. HR systems such as Workday, Saba, VERN along with communication platforms and collaboration tools such as MagellanNOW,
Methodology USA UK AUSTRALIA CANADA JAPAN N=1,008 MOE=+/-3% N=1,044 MOE=+/- 3% N=1,028 MOE=+/- 3% N=1,025 MOE=+/- 3% N=1,005 MOE=+/- 3%
 Norton by Symantec commissioned an online survey across nine countries in order to better understand consumers public Wi-Fi perceptions and practices, unveiling consumer misconceptions and worries about
Norton by Symantec commissioned an online survey across nine countries in order to better understand consumers public Wi-Fi perceptions and practices, unveiling consumer misconceptions and worries about
Mobile Security using IBM Endpoint Manager Mobile Device Management
 Mobile Security using IBM Endpoint Manager Mobile Device Management Mahendra Chopra Security Solution Architect @ IBM CIO Lab, Innovation mahendra.chopra@in.ibm.com Agenda Market Trends Mobile Security?
Mobile Security using IBM Endpoint Manager Mobile Device Management Mahendra Chopra Security Solution Architect @ IBM CIO Lab, Innovation mahendra.chopra@in.ibm.com Agenda Market Trends Mobile Security?
TIS/App Delivery Mobility Job Aid: Install and Configure Microsoft Outlook on Your iphone. Overview. Job Aid: Outlook for Mobile - iphone
 TIS/App Delivery Mobility Job Aid: Install and Configure Microsoft Outlook on Your iphone Overview The job aid is for Colleagues that want to access Outlook (part of Office O365) work email on their mobile
TIS/App Delivery Mobility Job Aid: Install and Configure Microsoft Outlook on Your iphone Overview The job aid is for Colleagues that want to access Outlook (part of Office O365) work email on their mobile
Survey Questions and Methodology
 Survey Questions and Methodology Spring Tracking Survey 2012 Data for March 15 April 3, 2012 Princeton Survey Research Associates International for the Pew Research Center s Internet & American Life Project
Survey Questions and Methodology Spring Tracking Survey 2012 Data for March 15 April 3, 2012 Princeton Survey Research Associates International for the Pew Research Center s Internet & American Life Project
Willis Mobile Device Access Security Policy. Date: July-2014 Version: 2.0 FINAL
 Willis Mobile Device Access Security Policy Date: July-2014 Version: 2.0 FINAL Willis Mobile Device Access Security Policy v2.0.docx Page: 1/8 30-Jul-2014 Contents Introduction... 3 Supported Platforms...
Willis Mobile Device Access Security Policy Date: July-2014 Version: 2.0 FINAL Willis Mobile Device Access Security Policy v2.0.docx Page: 1/8 30-Jul-2014 Contents Introduction... 3 Supported Platforms...
RingCentral for MINDBODY. User Guide
 RingCentral for MINDBODY User Guide RingCentral for MINDBODY User Guide Contents 2 Contents Introduction.............................................................. 3 About RingCentral for MINDBODY.....................................................
RingCentral for MINDBODY User Guide RingCentral for MINDBODY User Guide Contents 2 Contents Introduction.............................................................. 3 About RingCentral for MINDBODY.....................................................
Althea UK and Ireland Limited Privacy Policy
 Althea UK and Ireland Limited Privacy Policy BMS Ref: ALT23 V1.1 Page 1 of 7 Document Control Version Date Author/Reviewer/Approver Revision notes V1.0 Draft 18-5-18 Legal Author Authors draft V1.1 20-5-18
Althea UK and Ireland Limited Privacy Policy BMS Ref: ALT23 V1.1 Page 1 of 7 Document Control Version Date Author/Reviewer/Approver Revision notes V1.0 Draft 18-5-18 Legal Author Authors draft V1.1 20-5-18
Internet, Science & Tech RESEARCH AREAS. Mobile Fact Sheet MORE FACT SHEETS: INTERNET/BROADBAND SOCIAL MEDIA
 NUMBERS, FACTS AND TRENDS SHAPING YOUR WORLD ABOUT FOLLOW US Search Internet, Science & Tech MENU RESEARCH AREAS FACT SHEET JANUARY 12, 217 Mobile Fact Sheet MORE FACT SHEETS: INTERNET/BROADBAND SOCIAL
NUMBERS, FACTS AND TRENDS SHAPING YOUR WORLD ABOUT FOLLOW US Search Internet, Science & Tech MENU RESEARCH AREAS FACT SHEET JANUARY 12, 217 Mobile Fact Sheet MORE FACT SHEETS: INTERNET/BROADBAND SOCIAL
The HIPAA Omnibus Rule
 The HIPAA Omnibus Rule What You Should Know and Do as Enforcement Begins Rebecca Fayed, Associate General Counsel and Privacy Officer Eric Banks, Information Security Officer 3 Biographies Rebecca C. Fayed
The HIPAA Omnibus Rule What You Should Know and Do as Enforcement Begins Rebecca Fayed, Associate General Counsel and Privacy Officer Eric Banks, Information Security Officer 3 Biographies Rebecca C. Fayed
The Device Has Left the Building
 The Device Has Left the Building Mobile Security Made Easy With Managed PKI Christian Brindley Principal Systems Engineer, Symantec Identity and Information Protection Agenda 1 2 3 Mobile Trends and Use
The Device Has Left the Building Mobile Security Made Easy With Managed PKI Christian Brindley Principal Systems Engineer, Symantec Identity and Information Protection Agenda 1 2 3 Mobile Trends and Use
Mobile Messaging Apps Study : India. August 2014
 Mobile Messaging Apps Study : India August 2014 Contents 1. Research Objectives & Methodology 2. Key Findings 3. Mobile Consumption Behavior 4. Message Apps Usage & Behaviors Download Intent App Awareness
Mobile Messaging Apps Study : India August 2014 Contents 1. Research Objectives & Methodology 2. Key Findings 3. Mobile Consumption Behavior 4. Message Apps Usage & Behaviors Download Intent App Awareness
Administering Jive Mobile Apps
 Administering Jive Mobile Apps Contents 2 Contents Administering Jive Mobile Apps...3 Configuring Jive for Android and ios... 3 Custom App Wrapping for ios... 4 Native App Caching: Android...4 Native App
Administering Jive Mobile Apps Contents 2 Contents Administering Jive Mobile Apps...3 Configuring Jive for Android and ios... 3 Custom App Wrapping for ios... 4 Native App Caching: Android...4 Native App
Mobile call termination. Research Annex
 Mobile call termination Research Annex Publication date: 27 March 2007 Contents Section Page 1 Research Annex 1 Section 1 1 Research Annex Background 1.1 Ofcom conducted research in October 2006 to specifically
Mobile call termination Research Annex Publication date: 27 March 2007 Contents Section Page 1 Research Annex 1 Section 1 1 Research Annex Background 1.1 Ofcom conducted research in October 2006 to specifically
Protecting Health Information
 Agenda Protecting Health Information BRONSON HEALTHCARE GROUP INFORMATION TECHNOLOGY SECURITY ENGINEERING MICHAEL SMITH Personal device usage with sensitive data Mobile devices and BYOD Secure messaging
Agenda Protecting Health Information BRONSON HEALTHCARE GROUP INFORMATION TECHNOLOGY SECURITY ENGINEERING MICHAEL SMITH Personal device usage with sensitive data Mobile devices and BYOD Secure messaging
- Samsung Tablet Photo - Tablets Mean Business. Survey of IT pros reflects growing trend toward tablets for workforce mobility and more
 - Samsung Tablet Photo - Tablets Mean Business Survey of IT pros reflects growing trend toward tablets for workforce mobility and more Table of contents Introduction 2 Giving employees what they want pays
- Samsung Tablet Photo - Tablets Mean Business Survey of IT pros reflects growing trend toward tablets for workforce mobility and more Table of contents Introduction 2 Giving employees what they want pays
The Center for Affiliated Learning ( the CAL ) Privacy Policy
 The Center for Affiliated Learning ( the CAL ) Privacy Policy Welcome to the Center for Affiliated Learning ( the CAL ) an education and training platform owned and operated by Affiliates Risk Management
The Center for Affiliated Learning ( the CAL ) Privacy Policy Welcome to the Center for Affiliated Learning ( the CAL ) an education and training platform owned and operated by Affiliates Risk Management
CHANGING FACE OF MOBILITY RAISES THE STAKES FOR ENDPOINT DATA PROTECTION
 CHANGING FACE OF MOBILITY RAISES THE STAKES FOR ENDPOINT DATA PROTECTION CONTENTS: Enterprise Mobility Strategy and BYOD Policies Endpoint Vulnerabilities and Challenges Conclusion For several decades,
CHANGING FACE OF MOBILITY RAISES THE STAKES FOR ENDPOINT DATA PROTECTION CONTENTS: Enterprise Mobility Strategy and BYOD Policies Endpoint Vulnerabilities and Challenges Conclusion For several decades,
How to access Launchpad and Textbooks online
 Quest Tech Tips Launchpad & Textbooks Online Directions (front and back) How to setup your mobile device to receive school/district notifications (front and back) Edline parent instructions Free Microsoft
Quest Tech Tips Launchpad & Textbooks Online Directions (front and back) How to setup your mobile device to receive school/district notifications (front and back) Edline parent instructions Free Microsoft
Securing Institutional Data in a Mobile World
 University of Wisconsin Madison Securing Institutional Data in a Mobile World July 13, 2017 Securing Institutional Data in a Mobile World / Agenda 01 What is a mobile device? 02 Protecting institutional
University of Wisconsin Madison Securing Institutional Data in a Mobile World July 13, 2017 Securing Institutional Data in a Mobile World / Agenda 01 What is a mobile device? 02 Protecting institutional
GROUPON.COM - PRIVACY POLICY
 PRIVACY STATEMENT Last Updated: September 13, 2012 This Privacy Statement ( Privacy Statement ) explains how Groupon, Inc. ( Groupon, us, our, and we ) uses your information and applies to all who use
PRIVACY STATEMENT Last Updated: September 13, 2012 This Privacy Statement ( Privacy Statement ) explains how Groupon, Inc. ( Groupon, us, our, and we ) uses your information and applies to all who use
Getting Started Accessing Okta All Employees
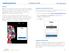 Purpose Okta is a cloud platform that provides single sign-on for Magellan applications. HR systems such as Workday, Saba, VERN along with communication platforms and collaboration tools such as MagellanNOW,
Purpose Okta is a cloud platform that provides single sign-on for Magellan applications. HR systems such as Workday, Saba, VERN along with communication platforms and collaboration tools such as MagellanNOW,
DISCOVERABILITY. How Canadians Find TV Content
 DISCOVERABILITY How Canadians Find TV Content Table of Contents Introduction...3 Executive Summary...4 TV Viewing is Diverse... 6 Discoverability... 10 Paid, Owned and Earned...18 Appendix Methodology
DISCOVERABILITY How Canadians Find TV Content Table of Contents Introduction...3 Executive Summary...4 TV Viewing is Diverse... 6 Discoverability... 10 Paid, Owned and Earned...18 Appendix Methodology
Google Identity Services for work
 INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
Administrator s Guide
 Administrator s Guide (January 2017) Welcome! You have been invited to manage the subscriber community who will be using this videoconferencing service within your organization. This guide will provide
Administrator s Guide (January 2017) Welcome! You have been invited to manage the subscriber community who will be using this videoconferencing service within your organization. This guide will provide
ENTERPRISE MOBILITY TRENDS
 ENTERPRISE MOBILITY TRENDS Raghuram Nair, Nandakishore Bellore Enterprise Mobility has emerged as a top technology trend globally. Every enterprise with a mobile workforce has an imperative to deploy a
ENTERPRISE MOBILITY TRENDS Raghuram Nair, Nandakishore Bellore Enterprise Mobility has emerged as a top technology trend globally. Every enterprise with a mobile workforce has an imperative to deploy a
Using the Mobile App for Defense Connect Online
 Using the Mobile App for Defense Connect Online Conduct and Attend Meetings Virtually Anywhere AUTHOR Aaron W Wolf DCO Evangelist Carahsoft Technology Corp. 703.889.9781 aaron.w.wolf@carahsoft.com Defense
Using the Mobile App for Defense Connect Online Conduct and Attend Meetings Virtually Anywhere AUTHOR Aaron W Wolf DCO Evangelist Carahsoft Technology Corp. 703.889.9781 aaron.w.wolf@carahsoft.com Defense
Secure Container DME. SecureContainer - DME is available for ios and Android.
 Secure Container DME Soliton SecureContainer - DME is a remote access solution enabling employees to securely access corporate data using their mobile devices. Corporate e-mail, calendar, to-do s and other
Secure Container DME Soliton SecureContainer - DME is a remote access solution enabling employees to securely access corporate data using their mobile devices. Corporate e-mail, calendar, to-do s and other
Sample: n=2,252 national adults, age 18 and older, including 1,127 cell phone interviews Interviewing dates:
 Survey Questions Spring 2013 Tracking Survey Final Topline 5/21/2013 Data for April 17-May 19, 2013 Princeton Survey Research Associates International for the Pew Research Center s Internet & American
Survey Questions Spring 2013 Tracking Survey Final Topline 5/21/2013 Data for April 17-May 19, 2013 Princeton Survey Research Associates International for the Pew Research Center s Internet & American
