Pluralsight CEU-Eligible Courses for CompTIA A+ updated March 2018
|
|
|
- Kristian Cameron
- 6 years ago
- Views:
Transcription
1 Pluralsight CEU-Eligible Courses for CompTIA A+ updated March 2018 Access Control Lists (ACLs) for Cisco CCNA / Administering Office 365 Quick Start Advanced Access Control with Cisco ISE for CCNP Security ( ) SISAS Advanced Malware Analysis: Combating Exploit Kits Advanced Persistent Threats: The Big Picture Advanced Security for CCNA Security ( ) IINS Advanced Web Application Penetration Testing with Burp Suite Applying SQL Server 2016 Features to Real-world Data Problems Architecting and Implementing Azure Networking Architecting Azure Solutions (70-534): Application Storage and Data Access Strategy Architecting Azure Solutions (70-534): Design an Advanced Application Architecting Azure Solutions (70-534): Management, Monitoring, and Business Continuity Architecting Azure Solutions (70-534): Secure Resources Architecting Microsoft Azure Solutions (70-534): Design Web Apps Assessing and Mitigating Security Risks Automating AWS and vsphere with Terraform Automating Deployment and Scale of Azure IaaS Solutions AWS Certified Solutions Architect - Associate AWS Certified Solutions Architect - Professional AWS Security Fundamentals AWS Security Operations: Designing for Acceptable Risk and Compliance AWS Security Operations: Securing Access to Object Storage AWS Security Operations: Securing Core AWS Infrastructure Services AWS Security Operations: Securing Managed Services Azure Resource Manager Deep Dive Azure Site Recovery: IaaS Migration and Disaster Recovery Azure SQL Data Warehouse: First Look Azure SQL Database for the SQL Server DBA Cisco ACI Programmability Cisco Data Center Network Design for CCDA DESGN ( ) Cisco Edge Network Design for CCDA DESGN ( ) Cisco ISE Guest Access for CCNP Security ( ) SISAS Cisco Network Design Blocks for CCDA DESGN ( ) CISSP - Communications and Network Security CISSP - Identity and Access Management CISSP - Security and Risk Management CISSP - Security Engineering CISSP - Security Operations CISSP : Security Assessment and Testing Citrix Networking Deep Dive Citrix XenDesktop/XenApp 7.6 LTSR CCA-V: Introduction Citrix XenDesktop/XenApp 7.6 LTSR CCA-V: Maintaining Citrix XenDesktop/XenApp 7.6 LTSR CCA-V: Managing Citrix XenDesktop/XenApp 7.6 LTSR CCA-V: Monitoring Citrix XenDesktop/XenApp 7.6 LTSR CCA-V: Troubleshooting Citrix XenDesktop/XenApp 7.6 LTSR CCP-V: Configuring Citrix XenDesktop/XenApp 7.6 LTSR CCP-V: Installing 1
2 Citrix XenDesktop/XenApp 7.6 LTSR CCP-V: Introduction Citrix XenDesktop/XenApp 7.6 LTSR CCP-V: Pre-installation Citrix XenDesktop/XenApp 7.6 LTSR CCP-V: Testing Computing, Communication, and Business Integration for CASP (CAS-002) Conducting Network Vulnerability Analysis Configuring a Cisco Router for Cisco CCNA / Configuring Windows 10 (70-697): Lab Setup Configuring Windows 10 Core Services Create and Manage Virtual Machines on Microsoft Azure Creating a DMZ in Azure Cryptography: The Big Picture CSSLP : Secure Software Concepts CSSLP : Secure Software Requirements Cyber Security Awareness: Backing up Your Data Cyber Security Awareness: Digital Data Protection Cyber Security Awareness: Electronic Commerce Security Cyber Security Awareness: Identifying Personally Identifiable Information (PII) Cyber Security Awareness: Malware Explained Cyber Security Awareness: Mobile Device Security Cyber Security Awareness: Pairing Physical and Digital Security Cyber Security Awareness: Phishing and Whaling Cyber Security Awareness: Safer Digital Communications Cyber Security Awareness: Security by Geolocation Cyber Security Awareness: Security for Cloud Services Cyber Security Awareness: Security Overview Cyber Security Awareness: Social Engineering Cyber Security Awareness: Social Networking at Work Cyber Security Awareness: The Importance of Identity Protection Cyber Security Awareness: The Internet of Things (IoT) Cyber Security Awareness: The Protection and Destruction of Portable Data Cybersecurity Threats: Ransomware Data Center Infrastructure for CCNA Data Center ( / ) Deploy Azure Virtual Networks, VPNs, and Gateways Deploy Windows 10 Images Deploying and Integrating Azure AD Deploying and Managing Azure IaaS Virtual Machines Deploying Windows 10 Anniversary Edition (v1607) with MDT Design a Database Environment with SQL Server 2014 (70-465) Design a Database Structure with SQL Server 2014 (70-465) Designing a Hybrid Cloud in Azure Designing and Implementing Security Policies Designing/Deploying Exchange 2016 (70-345): Client Access Designing/Deploying Exchange 2016 (70-345): Compliance & Archiving Designing/Deploying Exchange 2016 (70-345): Hybrid & Migrations Designing/Deploying Exchange 2016 (70-345): Mailbox Databases Designing/Deploying Exchange 2016 (70-345): Recipients & Security Designing/Deploying Exchange 2016 (70-345): Transport Digital Forensics: Getting Started with File Systems 2
3 Disaster Recovery for CompTIA Server+ (SK0-004) Enabling Office 365 (70-347) Exchange Online (End User and Planning) Enabling Office 365 (70-347) MCSA and the Exam Enabling Office 365 (70-347) Plan/Configure Skype for Business Online Enterprise Campus Design for CCDA DESGN ( ) Enterprise IP Routing Design for CCDA DESGN ( ) Enterprise IPv4/IPv6 Design for CCDA DESGN ( ) Enterprise LAN Switching for Cisco CCNA / Enterprise Security for CASP (CAS-002) Enterprise Security for CASP (CAS-002) Enterprise Security: Policies, Practices, and Procedures Enterprise Security: Policies, Practices, and Procedures Enterprise WAN Network Design for Cisco CCDP ARCH ( ) Ethical Hacking: Buffer Overflow Ethical Hacking: Cloud Computing Ethical Hacking: Cryptography Ethical Hacking: Denial of Service Ethical Hacking: Evading IDS, Firewalls, and Honeypots Ethical Hacking: Hacking Mobile Platforms Ethical Hacking: Hacking Wireless Networks Ethical Hacking: Penetration Testing Ethical Hacking: Sniffing Ethical Hacking: Social Engineering Exam Review for CCNP R&S TSHOOT Exchange Server 2016 Recipient Administration Exploit Development and Execution with the Metasploit Framework Exploitation: Evading Detection and Bypassing Countermeasures External Footprinting: Reconnaissance and Mapping Firewalls for CCNA Security ( ) IINS Fundamentals of Cloud Computing Fundamentals of Using Cisco ACI Getting Started Analyzing Malware Infections Getting Started with AWS Athena Getting Started with Azure Automation Getting Started with Azure Machine Learning Getting Started with Azure Operational Insights Getting Started with Citrix NetScaler Gateway 11 for XenDesktop Administrators Getting Started with OWASP Zed Attack Proxy (ZAP) for Web Application Penetration Testing Getting Started with the Microsoft Enterprise Mobility Suite Getting Started: Hybrid Identity with Microsoft Azure Google Cloud Platform Fundamentals Hands-On Incident Response Fundamentals How to Stop Man-in-the-Middle and Downgrade Attacks in Your Apps Implement Active Directory Domain Services in Windows Server 2016 Implement Windows Server 2016 IP Address Management (IPAM) Implementing a Security Assessment and Authorization Process Implementing Active Directory Certificate Services in Windows Server 2016 Implementing and Managing Azure Multi-factor Authentication 3
4 Implementing and Securing Windows Server 2016 Core Networking Implementing Azure Application Services Implementing Containers on Windows Server 2016 Implementing High Availability in Windows Server 2016 Implementing Microsoft Azure Networking Implementing Physical Security Implementing Windows 10 Implementing Windows Server 2016 Connectivity and Remote Access Implementing Windows Server 2016 DHCP Implementing Windows Server 2016 Distributed Networking Services Implementing Windows Server 2016 DNS Implementing Windows Server 2016 Hyper-V Implementing Windows Server 2016 Identity Federation and Access Implementing Windows Server 2016 Software Defined Networking Implementing Windows Server 2016 Storage Solutions Importing and Exporting Oracle Data for DBAs Information Security Manager: Information Security Governance Information Systems Auditing: The Big Picture Information Systems Auditor: Acquisition and Development Information Systems Auditor: Governance and Management Information Systems Auditor: Operations, Maintenance, and Service Information Systems Auditor: Protection of Information Assets Information Systems Auditor: The Process of Auditing Infrastructure Security for CCNP Routing & Switching SWITCH Installing and Configuring Windows 10 Installing Windows Server 2016 Introduction to Installing and Configuring Windows 10 and Configuring Windows Devices Introduction to Penetration Testing Using Metasploit IPv6 and Microsoft Windows ISE Posture Services for CCNP Security ( ) SISAS ISE Profiling Services for CCNP Security ( ) SISAS ISO/IEC Information Security: The Big Picture Juniper Networks JNCIS-ENT (JN0-343): Layer 2 Security Juniper Networks JNCIS-ENT (JN0-343): Layer 2 Switching and VLANs Juniper Networks JNCIS-ENT (JN0-343): Open Shortest Path First Juniper Networks JNCIS-ENT (JN0-343): Protocol-independent Routing Juniper Networks JNCIS-ENT (JN0-343): Spanning Tree Juniper Networks JNCIS-ENT: Intermediate System to Intermediate System Layer 2 Security for CCNA Security ( ) IINS LFCE: Advanced Linux Networking LFCE: Advanced Network and System Administration LFCE: Linux Service Management - HTTP Services LFCE: Network and Host Security LFCS: Linux Essentials LFCS: Linux Networking LFCS: Linux Operation Essentials LFCS: Linux Service Management LFCS: Linux Storage Management 4
5 LFCS: Linux User and Group Management LFCS: Linux Virtualization Management Linux Encryption Security (LPIC-3 303) Linux High Availability Cluster Management (LPIC Part 2/2) Linux Network Programming Linux Network Security (LPIC-3 303) Linux Server Skills for Windows Administrators Linux Server Virtualization (LPIC Part 1/2) Linux: Managing Web Services (LPIC-2) LPI: Linux Essentials ( ) Mac OS X Support: Applications and Processes Mac OS X Support: Data Management Mac OS X Support: File Systems Mac OS X Support: Installation and Configuration Mac OS X Support: User Accounts Maintain Windows 10 Images Maintaining and Monitoring Windows Server 2016 Malware Analysis Fundamentals Malware Analysis: The Big Picture Manage and Maintain Active Directory Domain Services in Windows Server 2016 Managing and Maintaining Windows 10 Managing and Supporting DirectAccess with Windows Server 2016 Managing AWS Security and Identity Managing Azure AD Managing Azure IaaS with PowerShell Managing Certificates with AWS Certificate Manager Managing Configurations with Azure Automation DSC Managing Configurations with Azure Automation DSC Managing Information Security Incidents (ISO/IEC 27002) Managing Information Security Threats & Risks (ISO/IEC 27002) Managing Infrastructure with Microsoft Azure - Getting Started Managing Inventory, Change, and Compliance with AWS Config Managing PCs and Devices with Microsoft Intune Mastering AWS Command-line Interface Operations Mastering Microsoft Azure Resource Manager Microsoft Azure Administration for AWS Administrators Microsoft Azure Architecture - Getting Started Microsoft Azure Architecture for AWS Architects Microsoft Azure IaaS Monitoring and Management - Getting Started Microsoft Azure Security - Getting Started Microsoft Azure Virtual Machines - Getting Started Migrating to Exchange Server 2016 Monitoring Servers and Services with AWS CloudWatch Monitoring with AWS CloudTrail Network Fundamentals and Protocols Network Interface Layer and Ethernet Operation for Cisco CCNA / Network Penetration Testing Using Python and Kali Linux Network Services for Cisco CCNA /
6 Network Vulnerability Scanning with OpenVAS Networking for CompTIA Server+ (SK0-004) Office 365: Deploying & Updating Microsoft Office 365 ProPlus OpenStack: Getting to Know OpenStack and the COA OpenStack: Installing the Lab Environment OpenStack: Managing Identities and Objects OpenStack: Nova and Neutron OPSEC for Penetration Testers Payment Card Security, Processing, and the PCI Standards PCI DSS: The Big Picture Penetration Testing Automation Using Python and Kali Linux Penetration Testing Life Cycle Explained Penetration Testing OSINT Gathering with Recon-ng Penetration Testing SharePoint Penetration Testing: Setting the Scope and Rules of Engagement Penetration Testing: The Big Picture Performing and Analyzing Network Reconnaissance Performing OSINT Gathering on Corporate Targets Planning and Designing Microsoft Azure Compute Solutions Planning and Designing Microsoft Azure Networking Solutions Planning and Designing Microsoft Azure Security Solutions Play by Play: Elastic Scale and Consistency with Azure Automation DSC Play by Play: Enterprise Data Encryption with Azure Revealed Play by Play: Ethical Hacking - Deconstructing the Hack Play by Play: Exploring the Internet of Vulnerabilities Play by Play: Social Engineering with Troy Hunt and Lars Klint Post Exploitation: Performing Infrastructure Analysis Practical SQL Server In-Memory OLTP Tables and Objects Practical SQL Server Security, Compliance, and Auditing Pre Create and Manage Virtual Machines for Azure Solutions (70-532) Pre Design and Implement Web Apps for Azure Solutions (70-532) Pre Implementing Active Directory for Azure Infrastructure (70-533) Pre Implementing Storage for Azure Infrastructure (70-533) Pre Implementing Virtual Machines for Azure Infrastructure (70-533) Pre Implementing Virtual Networks for Azure Infrastructure (70-533) Pre Implementing Web Apps for Azure Infrastructure (70-533) Pre Prepare to Pass the Azure Solutions (70-532) Exam Pre Preparing to Pass the Microsoft Azure (70-533) Exam Providing Disaster Recovery with Azure Services Puppet 4: Hiera, the Single Source of Truth Puppet 4: Language Essentials Puppet 4: Server and Puppet Enterprise Puppet 4: Working with Files and Templates Puppet 4: Working with Modules and Classes Research and Analysis for CASP (CAS-002) Risk Management and Incident Response for CASP (CAS-002) Risk Management and Information Systems Control: Introduction to Risk Risk Management and Information Systems Control: IT Risk Assessment 6
7 Risk Management and Information Systems Control: Risk and Control Monitoring and Reporting Risk Management and Information Systems Control: Risk Identification Risk Management and Information Systems Control: Risk Response and Mitigation Risks, Vulnerabilities, and Threats Routing IPv4 and IPv6 for Cisco CCNA / Secure Software Development Securing AWS Using CIS Foundations Benchmark Security Standard Securing Linux Servers Securing Multi-tenant ASP.NET Web Apps Securing Network Devices for CCNA Security ( ) IINS Securing Virtual Machines with Azure Key Vault Securing Windows 10: Data at Rest, in Use, and in Transit Securing Your Node.js Web App Security Concepts for CCNA Security ( ) IINS Security for CompTIA Server+ (SK0-004) Security for Hackers and Developers: Code Auditing Security for Hackers and Developers: Exploit Development Security for Hackers and Developers: Fuzzing Security for Hackers and Developers: Overview Security for Hackers and Developers: Reverse Engineering Security Management: The Big Picture Server Administration for CompTIA Server+ (SK0-004) Server Architecture for CompTIA Server+ (SK0-004) Setting up an Office 365 Hybrid Environment Solving Real World Problems with SQL Server 2016 Query Store SQL Server 2016 New Features for Developers SQL Server Reporting Services Playbook SQL Server Standard Edition Survival Guide SQL Server: Analyzing Query Performance for Developers SQL Server: Building Simple Asynchronous Applications SQL Server: Consolidation Tactics and Best Practices SQL Server: Improving Storage Subsystem Performance SQL Server: Indexing for Performance SQL Server: Installing and Configuring SQL Server 2016 SQL Server: Introduction to Query Store SQL Server: Replacing Profiler with Extended Events SQL Server: Scaling SQL Server 2012 and 2014: Part 2 SQL Server: Understanding and Using Azure SQL Database SQL Server: Understanding and Using DBCC Commands SQL Server: Upgrading and Migrating to SQL Server 2016 Storage for CompTIA Server+ (SK0-004) Technical Integration of Enterprise Components for CASP (CAS-002) The Information Security Big Picture The Issues of Identity and Access Management (IAM) Threat Intelligence: The Big Picture Threat Modeling Fundamentals Threat Modeling: The Big Picture Troubleshooting and Exam Prep for Cisco CCNA /
8 Troubleshooting Cisco Networks: Infrastructure Services for CCNP R&S TSHOOT Troubleshooting Cisco Networks: Internet Security for CCNP R&S TSHOOT Troubleshooting Cisco Networks: IPv4 Routing Protocols for CCNP R&S TSHOOT Troubleshooting Cisco Networks: IPv6 Routing Protocols for CCNP R&S TSHOOT Troubleshooting Cisco Networks: Layer 2 Protocols for CCNP R&S TSHOOT Troubleshooting Difficult Problems in Windows Troubleshooting Essentials for Cisco CCNA / Troubleshooting for CompTIA Server+ (SK0-004) Understanding and Using Azure Storage Understanding the Difference Between Microsoft Azure and Amazon AWS USB Forensics: Duplication USB Forensics: Writeblocking and Impersonation Using Cisco ACI with VMware vsphere Integration Using Docker with AWS Elastic Beanstalk Using Failover Clusters in Windows Server 2016 VMware Horizon 7: Configure and Administer VMware Mirage VMware Horizon 7: Configure and Manage App Volumes VMware Horizon 7: Configure and Manage User Environment Manager VMware Horizon 7: Configure and Manage VMware Identity Manager VMware Horizon 7: Configure vrealize Operations Manager VMware Horizon 7: Create and Configure Pools VMware Horizon 7: Install and Configure Horizon Server Components VMware Horizon 7: Introduction VPNs for CCNA Security ( ) IINS vsphere 6 Foundations: Availability and Resource Management vsphere 6 Foundations: Perform Basic Monitoring vsphere 6 Foundations: Perform Basic Troubleshooting Web App Hacking: Caching Problems Web App Hacking: Cookie Attacks Web App Hacking: Hacking Authentication Web App Hacking: Hacking Password Reset Functionality Web App Hacking: Sensitive Data Exposure Web Application Penetration Testing Fundamentals Web Application Penetration Testing with Burp Suite What's New in SQL Server 2016 Reporting Services Windows 10 Configuring (70-697): Configure Networking Windows 10 Configuring (70-697): Configure Storage Windows 10 Configuring (70-697): Manage Apps Windows 10 Configuring (70-697): Manage Data Access and Protection Windows 10 Configuring (70-697): Manage Identity Windows 10 Configuring (70-697): Manage Remote Access Windows 10 Configuring (70-697): Manage Updates and Recovery Windows 10 Configuring (70-697): Plan and Implement Microsoft Intune Windows Registry Troubleshooting Windows Server 2016 Security Hardening Windows Server Administration Fundamentals Using PowerShell Windows: How It's Hacked, How to Protect It Wireless Network Penetration Testing 8
9 Wireless Network Penetration Testing Advanced Techniques Writing Penetration Testing Reports 9
Pluralsight CEU-Eligible Courses for CompTIA Network+ updated March 2018
 Pluralsight CEU-Eligible Courses for CompTIA Network+ updated March 2018 Access Control Lists (ACLs) for Cisco CCNA 200-125/100-105 Advanced Access Control with Cisco ISE for CCNP Security (300-208) SISAS
Pluralsight CEU-Eligible Courses for CompTIA Network+ updated March 2018 Access Control Lists (ACLs) for Cisco CCNA 200-125/100-105 Advanced Access Control with Cisco ISE for CCNP Security (300-208) SISAS
Skillsoft Pre-Approved for CompTIA CEUs
 Skillsoft Pre-Approved for CompTIA CEUs Note: Approved training courses in this document are subject to change without prior notification. Training submitted based on prior approval will remain valid.
Skillsoft Pre-Approved for CompTIA CEUs Note: Approved training courses in this document are subject to change without prior notification. Training submitted based on prior approval will remain valid.
P a g e 1. Teknologisk Institut. Online kursus k SysAdmin & DevOps Collection
 P a g e 1 Online kursus k72751 SysAdmin & DevOps Collection P a g e 2 Title Estimated Duration (hrs) Ruby on Rails - Fundamentals 1,5 Ruby on Rails - Database Fundamentals 1,22 Python: The Basics 3,5 Python:
P a g e 1 Online kursus k72751 SysAdmin & DevOps Collection P a g e 2 Title Estimated Duration (hrs) Ruby on Rails - Fundamentals 1,5 Ruby on Rails - Database Fundamentals 1,22 Python: The Basics 3,5 Python:
Skillsoft Pre-Approved for CompTIA CEUs
 Skillsoft Pre-Approved for CompTIA CEUs Note: Approved training courses in this document are subject to change without prior notification. Training submitted based on prior approval will remain valid.
Skillsoft Pre-Approved for CompTIA CEUs Note: Approved training courses in this document are subject to change without prior notification. Training submitted based on prior approval will remain valid.
Product Catalog Platinum 529,00 (1 jaar toegang) CertKit includes: Quizzes, Tips & Tricks, 24/7 help, practise tests and e-learning CompTIA
 Product Catalog Platinum 529,00 (1 jaar toegang) CertKit includes: Quizzes, Tips & Tricks, 24/7 help, practise tests and e-learning 220-902 CompTIA A+ 1Z0-808: Java SE 8 Programming I 1Z0-809: Java SE
Product Catalog Platinum 529,00 (1 jaar toegang) CertKit includes: Quizzes, Tips & Tricks, 24/7 help, practise tests and e-learning 220-902 CompTIA A+ 1Z0-808: Java SE 8 Programming I 1Z0-809: Java SE
NetCom Learning Training Courses Pre-Approved for CompTIA CEUs
 NetCom Learning Training Courses Pre-Approved for CompTIA CEUs CE System Activity Name: Completed a Training Course Max CEUs Earned Per CE Cycle: CompTIA A+ - 16 CEUs CompTIA Network+ - 24 CEUs CompTIA
NetCom Learning Training Courses Pre-Approved for CompTIA CEUs CE System Activity Name: Completed a Training Course Max CEUs Earned Per CE Cycle: CompTIA A+ - 16 CEUs CompTIA Network+ - 24 CEUs CompTIA
Unlocking Potential Through Learning
 Unlocking Potential Through Learning CORPORATE HEAD OFFICE: 6, Babatola Drive, Off Obafemi Awolowo way, Behind Awolowo Glass house, Ikeja, Lagos. 08 Training Calender @ Newhorizonsnige @ new horizon solution
Unlocking Potential Through Learning CORPORATE HEAD OFFICE: 6, Babatola Drive, Off Obafemi Awolowo way, Behind Awolowo Glass house, Ikeja, Lagos. 08 Training Calender @ Newhorizonsnige @ new horizon solution
Hacker Academy Ltd COURSES CATALOGUE. Hacker Academy Ltd. LONDON UK
 Hacker Academy Ltd COURSES CATALOGUE Hacker Academy Ltd. LONDON UK TABLE OF CONTENTS Basic Level Courses... 3 1. Information Security Awareness for End Users... 3 2. Information Security Awareness for
Hacker Academy Ltd COURSES CATALOGUE Hacker Academy Ltd. LONDON UK TABLE OF CONTENTS Basic Level Courses... 3 1. Information Security Awareness for End Users... 3 2. Information Security Awareness for
Skillsoft Pre-Approved for CompTIA CEUs
 Skillsoft Pre-Approved for CompTIA CEUs Note: Approved training courses in this document are subject to change without prior notification. Training submitted based on prior approval will remain valid.
Skillsoft Pre-Approved for CompTIA CEUs Note: Approved training courses in this document are subject to change without prior notification. Training submitted based on prior approval will remain valid.
Course overview. CompTIA Security+ Certification (Exam SY0-501) Study Guide (G635eng v107)
 Overview This course is intended for those wishing to qualify with CompTIA Security+. CompTIA's Security+ Certification is a foundation-level certificate designed for IT administrators with 2 years' experience
Overview This course is intended for those wishing to qualify with CompTIA Security+. CompTIA's Security+ Certification is a foundation-level certificate designed for IT administrators with 2 years' experience
Business Skills Learning Sessions* SINGLE COURSE TITLES
 Business Skills Learning Sessions* ACCOUNTING TITLES Introduction to Business Accounting Bookkeeping and Payroll LEGAL TITLES Introduction to Legal Concepts Legal Office Administration HUMAN RESOURCES
Business Skills Learning Sessions* ACCOUNTING TITLES Introduction to Business Accounting Bookkeeping and Payroll LEGAL TITLES Introduction to Legal Concepts Legal Office Administration HUMAN RESOURCES
Computer Information Systems (CIS) CIS 105 Current Operating Systems/Security CIS 101 Introduction to Computers
 Computer Information Systems (CIS) CIS 101 Introduction to Computers This course provides an overview of the computing field and its typical applications. Key terminology and components of computer hardware,
Computer Information Systems (CIS) CIS 101 Introduction to Computers This course provides an overview of the computing field and its typical applications. Key terminology and components of computer hardware,
Aston Martin Institute
 Aston Martin Institute Your membership includes FREE Unlimited Access to 1,200+ IT, Cyber Security, Project Management, IT Service Management and Business Skills video courses with university Certificates
Aston Martin Institute Your membership includes FREE Unlimited Access to 1,200+ IT, Cyber Security, Project Management, IT Service Management and Business Skills video courses with university Certificates
Ethical Hacking and Prevention
 Ethical Hacking and Prevention This course is mapped to the popular Ethical Hacking and Prevention Certification Exam from US-Council. This course is meant for those professionals who are looking for comprehensive
Ethical Hacking and Prevention This course is mapped to the popular Ethical Hacking and Prevention Certification Exam from US-Council. This course is meant for those professionals who are looking for comprehensive
TECHNICAL. Unlimited Access to Over 200 Live, Virtual Instructor-Led Technical Classes for 12 Months
 TECHNICAL Unlimited Access to Over 200 Live, Virtual Instructor-Led Technical Classes for 12 Months The Technical Club Membership provides the ultimate in flexibility and value. Take as many classes as
TECHNICAL Unlimited Access to Over 200 Live, Virtual Instructor-Led Technical Classes for 12 Months The Technical Club Membership provides the ultimate in flexibility and value. Take as many classes as
TECHNICAL. Unlimited Access to Over 200 Live, Virtual Instructor-Led Technical Classes for 12 Months
 TECHNICAL Unlimited Access to Over 200 Live, Virtual Instructor-Led Technical Classes for 12 Months The Technical Club Membership provides the ultimate in flexibility and value. Take as many classes as
TECHNICAL Unlimited Access to Over 200 Live, Virtual Instructor-Led Technical Classes for 12 Months The Technical Club Membership provides the ultimate in flexibility and value. Take as many classes as
Windows Server 2016 MCSA Bootcamp
 Course Overview This course will provide experienced IT professionals who wish to either upgrade their skills for the purpose of certifying on Microsoft Windows Server 2016 or who wish to gain information
Course Overview This course will provide experienced IT professionals who wish to either upgrade their skills for the purpose of certifying on Microsoft Windows Server 2016 or who wish to gain information
TECHNICAL. Unlimited Access to Over 200 Live, Virtual Instructor-Led Technical Classes for 12 Months
 TECHNICAL Unlimited Access to Over 200 Live, Virtual Instructor-Led Technical Classes for 12 Months The Technical Club Membership provides the ultimate in flexibility and value. Take as many classes as
TECHNICAL Unlimited Access to Over 200 Live, Virtual Instructor-Led Technical Classes for 12 Months The Technical Club Membership provides the ultimate in flexibility and value. Take as many classes as
CISSP CEH PKI SECURITY + CEHv9: Certified Ethical Hacker. Upcoming Dates. Course Description. Course Outline
 CISSP CEH PKI SECURITY + CEHv9: Certified Ethical Hacker Learn to find security vulnerabilities before the bad guys do! The Certified Ethical Hacker (CEH) class immerses students in an interactive environment
CISSP CEH PKI SECURITY + CEHv9: Certified Ethical Hacker Learn to find security vulnerabilities before the bad guys do! The Certified Ethical Hacker (CEH) class immerses students in an interactive environment
Ingram Micro Cyber Security Portfolio
 Ingram Micro Cyber Security Portfolio Ingram Micro Inc. 1 Ingram Micro Cyber Security Portfolio Services Trainings Vendors Technical Assessment General Training Consultancy Service Certification Training
Ingram Micro Cyber Security Portfolio Ingram Micro Inc. 1 Ingram Micro Cyber Security Portfolio Services Trainings Vendors Technical Assessment General Training Consultancy Service Certification Training
CompTIA Cybersecurity Analyst+
 CompTIA Cybersecurity Analyst+ Course CT-04 Five days Instructor-Led, Hands-on Introduction This five-day, instructor-led course is intended for those wishing to qualify with CompTIA CSA+ Cybersecurity
CompTIA Cybersecurity Analyst+ Course CT-04 Five days Instructor-Led, Hands-on Introduction This five-day, instructor-led course is intended for those wishing to qualify with CompTIA CSA+ Cybersecurity
MCSA: Windows Server MCSA 2016 Windows 2016 Server 2016 MCSA 2016 MCSA : Installation, Storage, and Compute with Windows Server 2016
 indows Server 2016 MCSA 2016 MCSA: Windows Server MCSA 2016 Windows 2016 Server 2016 MCSA 2016 MCSA 2016 70-740: Installation, Storage, and Compute with Windows Server 2016 70-741: Networking with Windows
indows Server 2016 MCSA 2016 MCSA: Windows Server MCSA 2016 Windows 2016 Server 2016 MCSA 2016 MCSA 2016 70-740: Installation, Storage, and Compute with Windows Server 2016 70-741: Networking with Windows
IT Foundations Networking Specialist Certification with Exam
 IT Foundations Networking Specialist Certification with Exam MSIT113 / 200 Hours / 12 Months / Self-Paced / Materials Included Course Overview: Gain hands-on expertise in CompTIA A+ certification exam
IT Foundations Networking Specialist Certification with Exam MSIT113 / 200 Hours / 12 Months / Self-Paced / Materials Included Course Overview: Gain hands-on expertise in CompTIA A+ certification exam
AURA ACADEMY Training With Expertised Faculty Call Us On For Free Demo
 ETHICAL HACKING (CEH) CURRICULUM Introduction to Ethical Hacking What is Hacking? Who is a Hacker? Skills of a Hacker? Types of Hackers? What are the Ethics and Legality?? Who are at the risk of Hacking
ETHICAL HACKING (CEH) CURRICULUM Introduction to Ethical Hacking What is Hacking? Who is a Hacker? Skills of a Hacker? Types of Hackers? What are the Ethics and Legality?? Who are at the risk of Hacking
Diploma in Network (LAN/WAN) Administration
 Diploma in Network (LAN/WAN) Administration The Diploma in Network (LAN/WAN) Administration program prepares students to setup Local & Wide Area Networks using Cisco routers and Catalyst switches in a
Diploma in Network (LAN/WAN) Administration The Diploma in Network (LAN/WAN) Administration program prepares students to setup Local & Wide Area Networks using Cisco routers and Catalyst switches in a
Security+ SY0-501 Study Guide Table of Contents
 Security+ SY0-501 Study Guide Table of Contents Course Introduction Table of Contents About This Course About CompTIA Certifications Module 1 / Threats, Attacks, and Vulnerabilities Module 1 / Unit 1 Indicators
Security+ SY0-501 Study Guide Table of Contents Course Introduction Table of Contents About This Course About CompTIA Certifications Module 1 / Threats, Attacks, and Vulnerabilities Module 1 / Unit 1 Indicators
CHCSS. Certified Hands-on Cyber Security Specialist (510)
 CHCSS Certified Hands-on Cyber Security Specialist () SYLLABUS 2018 Certified Hands-on Cyber Security Specialist () 2 Course Description Entry level cyber security course intended for an audience looking
CHCSS Certified Hands-on Cyber Security Specialist () SYLLABUS 2018 Certified Hands-on Cyber Security Specialist () 2 Course Description Entry level cyber security course intended for an audience looking
DIABLO VALLEY COLLEGE CATALOG
 COMPUTER NETWORK TECHNOLOGY CNT Despina Prapavessi, Dean Math and Computer Sciences Division Math Building, Room 267 Possible career opportunities These CNT-courses prepare students for a career path in
COMPUTER NETWORK TECHNOLOGY CNT Despina Prapavessi, Dean Math and Computer Sciences Division Math Building, Room 267 Possible career opportunities These CNT-courses prepare students for a career path in
Academic Services Group. Master Course List (Revised November 6, 2015)
 Academic Services Group Master Course List (Revised November 6, 015) This is the course list for free, online, self-paced training offered to ASU UTO employees from Jan 1 May 30, 016. The courses are divided
Academic Services Group Master Course List (Revised November 6, 015) This is the course list for free, online, self-paced training offered to ASU UTO employees from Jan 1 May 30, 016. The courses are divided
PUBLIC COURSE SCHEDULE. January - June 2017
 PUBLIC COURSE SCHEDULE January - June 7 January - June 7 /6 ABU Yose. Yose. FCPRO LPROX. PNK APPLE ipad Apple ipad for Business Use OS X Yosemite - OS X Support Essentials. Yosemite - OS X Server Essentials.
PUBLIC COURSE SCHEDULE January - June 7 January - June 7 /6 ABU Yose. Yose. FCPRO LPROX. PNK APPLE ipad Apple ipad for Business Use OS X Yosemite - OS X Support Essentials. Yosemite - OS X Server Essentials.
IT Technician Pathways Course Guide
 IT Technician Pathways Course Guide Stage Computer Retail Sales and Support Course Name or Topic Introduction to Retail or Business Fundamentals Related 3 rd Party Certifications C-ID IT-MC C-ID BUS 100
IT Technician Pathways Course Guide Stage Computer Retail Sales and Support Course Name or Topic Introduction to Retail or Business Fundamentals Related 3 rd Party Certifications C-ID IT-MC C-ID BUS 100
This course prepares candidates for the CompTIA Network+ examination (2018 Objectives) N
 CompTIA Network+ (Exam N10-007) Course Description: CompTIA Network+ is the first certification IT professionals specializing in network administration and support should earn. Network+ is aimed at IT
CompTIA Network+ (Exam N10-007) Course Description: CompTIA Network+ is the first certification IT professionals specializing in network administration and support should earn. Network+ is aimed at IT
Microsoft Certified System Engineer
 529 Hahn Ave. Suite 101 Glendale CA 91203-1052 Tel 818.550.0770 Fax 818.550.8293 www.brandcollege.edu Microsoft Certified System Engineer Program Summary This instructor-led program with a combination
529 Hahn Ave. Suite 101 Glendale CA 91203-1052 Tel 818.550.0770 Fax 818.550.8293 www.brandcollege.edu Microsoft Certified System Engineer Program Summary This instructor-led program with a combination
CompTIA Network+ Study Guide Table of Contents
 CompTIA Network+ Study Guide Table of Contents Course Introduction Table of Contents Getting Started About This Course About CompTIA Certifications Module 1 / Local Area Networks Module 1 / Unit 1 Topologies
CompTIA Network+ Study Guide Table of Contents Course Introduction Table of Contents Getting Started About This Course About CompTIA Certifications Module 1 / Local Area Networks Module 1 / Unit 1 Topologies
Idaho's Premiere Learning Center. Voted Best of Idaho Length. 5 Days Days 16. 2hrs. 1 day. Length. Length. 2 Days. 1 Day.
 10051 W. Emerald Street, Suite 120 Boise, Idaho 83704 PHONE: (208) 327-0768 Idaho's Premiere Learning Center Voted Best of Idaho 2017 http://www.etidaho.com Trending Now 20740 Installation, Storage and
10051 W. Emerald Street, Suite 120 Boise, Idaho 83704 PHONE: (208) 327-0768 Idaho's Premiere Learning Center Voted Best of Idaho 2017 http://www.etidaho.com Trending Now 20740 Installation, Storage and
Computer Information Systems (CIS) CIS 105 Current Operating Systems/Security CIS 101 Introduction to Computers
 Computer Information Systems (CIS) CIS 101 Introduction to Computers This course provides an overview of the computing field and its typical applications. Key terminology and components of computer hardware,
Computer Information Systems (CIS) CIS 101 Introduction to Computers This course provides an overview of the computing field and its typical applications. Key terminology and components of computer hardware,
Certified Ethical Hacker (CEH)
 Certified Ethical Hacker (CEH) COURSE OVERVIEW: The most effective cybersecurity professionals are able to predict attacks before they happen. Training in Ethical Hacking provides professionals with the
Certified Ethical Hacker (CEH) COURSE OVERVIEW: The most effective cybersecurity professionals are able to predict attacks before they happen. Training in Ethical Hacking provides professionals with the
TERIBITE TECHNOLOGIES ACADEMY
 Phone: 09080699264, 08088649 CISCO COURSES CCNA-DC - CCNA Data Center DCNXK - Implementing the Cisco Nexus 000 and 2000 v2.0 DCNX7K - Configuring Cisco Nexus 7000 Switches v.0 DCUCI - Data Center Unified
Phone: 09080699264, 08088649 CISCO COURSES CCNA-DC - CCNA Data Center DCNXK - Implementing the Cisco Nexus 000 and 2000 v2.0 DCNX7K - Configuring Cisco Nexus 7000 Switches v.0 DCUCI - Data Center Unified
Technical Classes. Cisco. Cisco Authorized Courses CISSP. Coding & Programming. CCNA Certification Bootcamp ( exam) 2/6/2015 9am-4:30pm
 Technical Classes Cisco CCNA Certification Bootcamp (200-120 exam) 2/9/2015 2/13/2015 9am-5pm 4/20/2015 4/24/2015 9am-5pm Cisco Authorized Courses CCNP: ROUTE 4/13/2015 4/17/2015 9am-5pm CCNP: SWITCH CCNP:
Technical Classes Cisco CCNA Certification Bootcamp (200-120 exam) 2/9/2015 2/13/2015 9am-5pm 4/20/2015 4/24/2015 9am-5pm Cisco Authorized Courses CCNP: ROUTE 4/13/2015 4/17/2015 9am-5pm CCNP: SWITCH CCNP:
Type Vendor Exam # Name Size. Technical Cisco Interconnecting Cisco Networking Devices Part 1 (ICND1) 180
 s Technical Cisco 100-105 Interconnecting Cisco Networking Devices Part 1 (ICND1) 180 Technical Cisco 200-105 Interconnecting Cisco Networking Devices Part 2 (ICND2) 137 Technical Cisco 200-125 Cisco Certified
s Technical Cisco 100-105 Interconnecting Cisco Networking Devices Part 1 (ICND1) 180 Technical Cisco 200-105 Interconnecting Cisco Networking Devices Part 2 (ICND2) 137 Technical Cisco 200-125 Cisco Certified
This ethical hacking course puts you in the driver's seat of a hands-on environment with a systematic process.
 EC Council Certified Ethical Hacker V9 This ethical hacking course puts you in the driver's seat of a hands-on environment with a systematic process. Here, you will be exposed to an entirely different
EC Council Certified Ethical Hacker V9 This ethical hacking course puts you in the driver's seat of a hands-on environment with a systematic process. Here, you will be exposed to an entirely different
PUBLIC COURSE SCHEDULE. July - December 2017
 PUBLIC COURSE SCHEDULE July - December 2017 July - December 2017 BIG DATA days cost BDIDA Introduction to Data Analysis 2 650 150 (d) 18-19 BDB Big Data Bootcamp (Apache Hadoop/Pig/Hive) 2 650 150(d) 02-03
PUBLIC COURSE SCHEDULE July - December 2017 July - December 2017 BIG DATA days cost BDIDA Introduction to Data Analysis 2 650 150 (d) 18-19 BDB Big Data Bootcamp (Apache Hadoop/Pig/Hive) 2 650 150(d) 02-03
6 MILLION AVERAGE PAY. CYBER Security. How many cyber security professionals will be added in 2019? for popular indursty positions are
 PROGRAM Objective Cyber Security is the most sought after domain, and NASSCOM projects a requirment of over 1 million trained professionals by 2025. Tevel training program is an industry & employability
PROGRAM Objective Cyber Security is the most sought after domain, and NASSCOM projects a requirment of over 1 million trained professionals by 2025. Tevel training program is an industry & employability
Managing Microsoft 365 Identity and Access
 Course MS-500T01-A: Managing Microsoft 365 Identity and Access Page 1 of 3 Managing Microsoft 365 Identity and Access Course MS-500T01-A: 1 day; Instructor-Led Introduction Help protect against credential
Course MS-500T01-A: Managing Microsoft 365 Identity and Access Page 1 of 3 Managing Microsoft 365 Identity and Access Course MS-500T01-A: 1 day; Instructor-Led Introduction Help protect against credential
CASP CompTIA Advanced Security Practitioner Study Guide: (Exam CAS-001)
 CASP CompTIA Advanced Security Practitioner Study Guide: (Exam CAS-001) Gregg, Michael ISBN-13: 9781118083192 Table of Contents Foreword xxi Introduction xxvii Assessment Test xliv Chapter 1 Cryptographic
CASP CompTIA Advanced Security Practitioner Study Guide: (Exam CAS-001) Gregg, Michael ISBN-13: 9781118083192 Table of Contents Foreword xxi Introduction xxvii Assessment Test xliv Chapter 1 Cryptographic
Network Engineering/Cyber Security I & II
 Network Engineering/Cyber Security I & II Program Description: The first year course teaches the basic techniques of computer safety and maintenance. Students learn to assemble/disassemble personal computers
Network Engineering/Cyber Security I & II Program Description: The first year course teaches the basic techniques of computer safety and maintenance. Students learn to assemble/disassemble personal computers
ifuture ifuture have delivered Technical and Management trainings across PAN India, APAC and Middle East region
 ifuture ifuture technologies o er wide range of trainings as a Microsoft Silver Learning Partner and we o er authorized training program. We o er Core technology trainings which are highly focused on Industry
ifuture ifuture technologies o er wide range of trainings as a Microsoft Silver Learning Partner and we o er authorized training program. We o er Core technology trainings which are highly focused on Industry
Course 831 Certified Ethical Hacker v9
 Course 831 Certified Ethical Hacker v9 Duration: 5 days What You Get: CEH v9 Certification exam voucher 5 days of high quality classroom training 18 comprehensive modules 40% of class hours dedicated to
Course 831 Certified Ethical Hacker v9 Duration: 5 days What You Get: CEH v9 Certification exam voucher 5 days of high quality classroom training 18 comprehensive modules 40% of class hours dedicated to
Installation, Storage, and Compute with Windows Server
 Installation, Storage, and Compute with Windows Server 2016-740 Module 1: Installing, upgrading, and migrating servers and workloadst Introducing Windows Server 2016 Preparing and installing Nano Server
Installation, Storage, and Compute with Windows Server 2016-740 Module 1: Installing, upgrading, and migrating servers and workloadst Introducing Windows Server 2016 Preparing and installing Nano Server
Federal Virtual Training Environment (FedVTE) Pre-Approved for CompTIA CEUs
 Federal Virtual Training Environment (FedVTE) Pre-Approved for CompTIA CEUs You can earn 1 CEU for each hour of training. Follow these requirements to earn and receive CEUs. All training must be at least
Federal Virtual Training Environment (FedVTE) Pre-Approved for CompTIA CEUs You can earn 1 CEU for each hour of training. Follow these requirements to earn and receive CEUs. All training must be at least
Advanced Diploma on Information Security
 Course Name: Course Duration: Prerequisites: Course Fee: Advanced Diploma on Information Security 300 Hours; 12 Months (10 Months Training + 2 Months Project Work) Candidate should be HSC Pass & Basic
Course Name: Course Duration: Prerequisites: Course Fee: Advanced Diploma on Information Security 300 Hours; 12 Months (10 Months Training + 2 Months Project Work) Candidate should be HSC Pass & Basic
CompTIA Security+ Study Guide (SY0-501)
 CompTIA Security+ Study Guide (SY0-501) Syllabus Session 1 At the end of this session, students will understand what risk is and the basics of what it means to have security in an organization. This includes
CompTIA Security+ Study Guide (SY0-501) Syllabus Session 1 At the end of this session, students will understand what risk is and the basics of what it means to have security in an organization. This includes
About Us. We re now the world s largest independent IT training company, and we continue to lead
 About Us As changes in technology have accelerated, it s become even more essential for people to master technology to be productive, invaluable employees who optimize, program and invent solutions and
About Us As changes in technology have accelerated, it s become even more essential for people to master technology to be productive, invaluable employees who optimize, program and invent solutions and
ETHICAL HACKING & COMPUTER FORENSIC SECURITY
 ETHICAL HACKING & COMPUTER FORENSIC SECURITY Course Description From forensic computing to network security, the course covers a wide range of subjects. You will learn about web hacking, password cracking,
ETHICAL HACKING & COMPUTER FORENSIC SECURITY Course Description From forensic computing to network security, the course covers a wide range of subjects. You will learn about web hacking, password cracking,
Designing Windows Server 2008 Network and Applications Infrastructure
 Designing Windows Server 2008 Network and Applications Infrastructure Course No. 6435B - 5 Days Instructor-led, Hands-on Introduction This five-day course will provide students with an understanding of
Designing Windows Server 2008 Network and Applications Infrastructure Course No. 6435B - 5 Days Instructor-led, Hands-on Introduction This five-day course will provide students with an understanding of
Experience working with Windows Server 2008 or Windows Server Experience working in a Windows Server infrastructure enterprise environment
 Networking with Windows Server 2016 va Day(s): 5 Course Code: M20741 Version: A Overview This 5-day classroom-based course provides the fundamental networking skills required to deploy and support Windows
Networking with Windows Server 2016 va Day(s): 5 Course Code: M20741 Version: A Overview This 5-day classroom-based course provides the fundamental networking skills required to deploy and support Windows
MCSA Windows Server 2012
 MCSA Windows Server 2012 This Training Program prepares and enables learners to Pass Microsoft MCSA: Windows Server 2012 exams 1. MCSA: Windows Server 2012 / 70-410 Exam (Installing and Configuring Windows
MCSA Windows Server 2012 This Training Program prepares and enables learners to Pass Microsoft MCSA: Windows Server 2012 exams 1. MCSA: Windows Server 2012 / 70-410 Exam (Installing and Configuring Windows
CompTIA Security+ Pre-approved Training for CompTIA Security+ Continuing Education Units (CEUs)
 CompTIA Security+ Pre-approved Training for CompTIA Security+ Continuing Education Units (CEUs) Note: Approved training courses in this document are subject to change without prior notification. Training
CompTIA Security+ Pre-approved Training for CompTIA Security+ Continuing Education Units (CEUs) Note: Approved training courses in this document are subject to change without prior notification. Training
EZY Intellect Pte. Ltd.,
 Microsoft Certified Solutions Associate (MCSA) Course 20741B: Networking with Windows Server 2016 Duration: 5 Days Associate Level: Window Server 2016 About this course This 5-day classroom-based course
Microsoft Certified Solutions Associate (MCSA) Course 20741B: Networking with Windows Server 2016 Duration: 5 Days Associate Level: Window Server 2016 About this course This 5-day classroom-based course
Upgrading Your Skills to MCSA: Windows Server 2016
 Upgrading Your Skills to MCSA: Windows Server 2016 20743B; 5 days, Instructor-led Course Description This five-day, instructor-led course explains how to implement and configure new Windows Server 2016
Upgrading Your Skills to MCSA: Windows Server 2016 20743B; 5 days, Instructor-led Course Description This five-day, instructor-led course explains how to implement and configure new Windows Server 2016
IT Security Training MS-500: Microsoft 365 Security Administration. Upcoming Dates. Course Description. Course Outline $2,
 IT Security Training MS-500: Microsoft 365 Security Administration $2,595.00 4 Days Upcoming Dates Course Description Day 1: Managing Microsoft 365 Identity and Access (MS-500T01-A) Help protect against
IT Security Training MS-500: Microsoft 365 Security Administration $2,595.00 4 Days Upcoming Dates Course Description Day 1: Managing Microsoft 365 Identity and Access (MS-500T01-A) Help protect against
COURSE 20741B: NETWORKING WITH WINDOWS SERVER 2016
 ABOUT THIS COURSE This 5-day classroom-based course provides the fundamental networking skills required to deploy and support Windows Server 2016 in most organizations. It covers IP fundamentals, remote
ABOUT THIS COURSE This 5-day classroom-based course provides the fundamental networking skills required to deploy and support Windows Server 2016 in most organizations. It covers IP fundamentals, remote
Application Training Application Courses
 Office Adobe Microsoft Office 2013 (Word/Excel/Pow erpoint/outlook) Adobe CC Photoshop/InDesi gn/illustrator Quarter 1 Jan 17 - Jan 21, Mar 13 - Mar 17, Jan 24 - Quarter 2 Application Training Application
Office Adobe Microsoft Office 2013 (Word/Excel/Pow erpoint/outlook) Adobe CC Photoshop/InDesi gn/illustrator Quarter 1 Jan 17 - Jan 21, Mar 13 - Mar 17, Jan 24 - Quarter 2 Application Training Application
TestOut Network Pro - English 5.0.x COURSE OUTLINE. Modified
 TestOut Network Pro - English 5.0.x COURSE OUTLINE Modified 2018-03-06 TestOut Network Pro Outline - English 5.0.x Videos: 130 (17:10:31) Demonstrations: 78 (8:46:15) Simulations: 88 Fact Sheets: 136 Exams:
TestOut Network Pro - English 5.0.x COURSE OUTLINE Modified 2018-03-06 TestOut Network Pro Outline - English 5.0.x Videos: 130 (17:10:31) Demonstrations: 78 (8:46:15) Simulations: 88 Fact Sheets: 136 Exams:
Course 831 EC-Council Certified Ethical Hacker v10 (CEH)
 Course 831 EC-Council Certified Ethical Hacker v10 (CEH) Duration: 5 days What You Get: CEH v10 Certification exam voucher 5 days of high quality classroom training 18 comprehensive modules 40% of class
Course 831 EC-Council Certified Ethical Hacker v10 (CEH) Duration: 5 days What You Get: CEH v10 Certification exam voucher 5 days of high quality classroom training 18 comprehensive modules 40% of class
Microsoft Office Courses
 Microsoft Office Courses Word processing Duration Fees Word (Basic) 1 Day $80 Word (Intermediate) 1 Day $80 Word (Advanced) 1 Day $80 Spreadsheets Excel (Basic) 1 Day $80 Excel (Intermediate) 1 Day $80
Microsoft Office Courses Word processing Duration Fees Word (Basic) 1 Day $80 Word (Intermediate) 1 Day $80 Word (Advanced) 1 Day $80 Spreadsheets Excel (Basic) 1 Day $80 Excel (Intermediate) 1 Day $80
MCSA Windows Server 2012
 MCSA Windows Server 2012 This course is developed for IT professionals who need to design, plan, implement, manage and support Microsoft Windows 2012 networks or who plan to take the related MCSE and MCSA
MCSA Windows Server 2012 This course is developed for IT professionals who need to design, plan, implement, manage and support Microsoft Windows 2012 networks or who plan to take the related MCSE and MCSA
TestOut Network Pro - English 4.1.x COURSE OUTLINE. Modified
 TestOut Network Pro - English 4.1.x COURSE OUTLINE Modified 2017-07-06 TestOut Network Pro Outline - English 4.1.x Videos: 141 (18:42:14) Demonstrations: 81 (10:38:59) Simulations: 92 Fact Sheets: 145
TestOut Network Pro - English 4.1.x COURSE OUTLINE Modified 2017-07-06 TestOut Network Pro Outline - English 4.1.x Videos: 141 (18:42:14) Demonstrations: 81 (10:38:59) Simulations: 92 Fact Sheets: 145
New Horizons Computer Learning Center Training
 New Horizons Computer Learning Center Training Professional Feb Mar Apr May CND Certified Network Defender Program 12-Feb CEH v9 Certified Ethical Hacker 18-22 Jan 8-12 CNFE Certified Network Forensics
New Horizons Computer Learning Center Training Professional Feb Mar Apr May CND Certified Network Defender Program 12-Feb CEH v9 Certified Ethical Hacker 18-22 Jan 8-12 CNFE Certified Network Forensics
Certified Ethical Hacker
 Certified Ethical Hacker Certified Ethical Hacker Course Objective Describe how perimeter defenses function by ethically scanning and attacking networks Conduct information systems security audits by understanding
Certified Ethical Hacker Certified Ethical Hacker Course Objective Describe how perimeter defenses function by ethically scanning and attacking networks Conduct information systems security audits by understanding
GLOBAL INFOSKILLS SDN BHD
 1 COMPUTER TECHNICAL COURSES SCHEDULE 2019( LOCATION:GISB ) JAN FEB MAC APR MAY JUNE MICROSOFT AZURE MS10978 Introduction to Azure for Developers 1 5 3500 7-11 11-15 4-8 1-5 6-10 10-14 MS20487 Developing
1 COMPUTER TECHNICAL COURSES SCHEDULE 2019( LOCATION:GISB ) JAN FEB MAC APR MAY JUNE MICROSOFT AZURE MS10978 Introduction to Azure for Developers 1 5 3500 7-11 11-15 4-8 1-5 6-10 10-14 MS20487 Developing
GLOBAL INFOSKILLS SDN BHD
 1 JAN FEB MAC APR MAY JUNE MICROSOFT AZURE MS10978 Introduction to Azure for Developers 1 5 3500 8-12 5-9 26-30 16-20 21-25 4-8 MS20487 Developing Microsoft Azure and Web Services 1 5 3500 15-19 19-23
1 JAN FEB MAC APR MAY JUNE MICROSOFT AZURE MS10978 Introduction to Azure for Developers 1 5 3500 8-12 5-9 26-30 16-20 21-25 4-8 MS20487 Developing Microsoft Azure and Web Services 1 5 3500 15-19 19-23
Microsoft Certified Solution Associate Windows Server 2016 Training
 Microsoft Certified Solution Associate Windows Server 2016 Training INNOVATIVE ACADEMY s Best Microsoft Training in Bangalore is designed so Innovative to help you clear the Microsoft Certified Solution
Microsoft Certified Solution Associate Windows Server 2016 Training INNOVATIVE ACADEMY s Best Microsoft Training in Bangalore is designed so Innovative to help you clear the Microsoft Certified Solution
Exam : Implementing Microsoft Azure Infrastructure Solutions
 Exam 70-533: Implementing Microsoft Azure Infrastructure Solutions Objective Domain Note: This document shows tracked changes that are effective as of January 18, 2018. Design and Implement Azure App Service
Exam 70-533: Implementing Microsoft Azure Infrastructure Solutions Objective Domain Note: This document shows tracked changes that are effective as of January 18, 2018. Design and Implement Azure App Service
20741 Networking with Windows Server 2016
 20741 Networking with Windows Server 2016 This 5-day classroom-based course provides the fundamental networking skills required to deploy and support Windows Server 2016 in most organizations. It covers
20741 Networking with Windows Server 2016 This 5-day classroom-based course provides the fundamental networking skills required to deploy and support Windows Server 2016 in most organizations. It covers
Networking with Windows Server 2016
 Networking with Windows Server 2016 OD20741B; On-Demand, Video-based Course Description This course provides the fundamental networking skills required to deploy and support Windows Server 2016 in most
Networking with Windows Server 2016 OD20741B; On-Demand, Video-based Course Description This course provides the fundamental networking skills required to deploy and support Windows Server 2016 in most
EC-Council Certified Network Defender (CND) Duration: 5 Days Method: Instructor-Led
 EC-Council Certified Network Defender (CND) Duration: 5 Days Method: Instructor-Led Certification: Certified Network Defender Exam: 312-38 Course Description This course is a vendor-neutral, hands-on,
EC-Council Certified Network Defender (CND) Duration: 5 Days Method: Instructor-Led Certification: Certified Network Defender Exam: 312-38 Course Description This course is a vendor-neutral, hands-on,
CPTE: Certified Penetration Testing Engineer
 www.peaklearningllc.com CPTE: Certified Penetration Testing Engineer (5 Days) *Includes exam voucher, course video, an exam preparation guide About this course Certified Penetration Testing Engineer certification
www.peaklearningllc.com CPTE: Certified Penetration Testing Engineer (5 Days) *Includes exam voucher, course video, an exam preparation guide About this course Certified Penetration Testing Engineer certification
Windows 8 Boot Camp 6439; 5 Days, Instructor-led
 Windows 8 Boot Camp 6439; 5 Days, Instructor-led Course Description: In an intensive and immersive hands-on learning environment, you will build the skills needed configure, manage, and maintain a Windows
Windows 8 Boot Camp 6439; 5 Days, Instructor-led Course Description: In an intensive and immersive hands-on learning environment, you will build the skills needed configure, manage, and maintain a Windows
Managing and Auditing Organizational Migration to the Cloud TELASA SECURITY
 Managing and Auditing Organizational Migration to the Cloud 1 TELASA SECURITY About Me Brian Greidanus bgreidan@telasasecurity.com 18+ years of security and compliance experience delivering consulting
Managing and Auditing Organizational Migration to the Cloud 1 TELASA SECURITY About Me Brian Greidanus bgreidan@telasasecurity.com 18+ years of security and compliance experience delivering consulting
[MS20347]: Enabling and Managing Office 365
![[MS20347]: Enabling and Managing Office 365 [MS20347]: Enabling and Managing Office 365](/thumbs/77/76084176.jpg) [MS20347]: Enabling and Managing Office 365 Length : 5 Days Audience(s) : IT Professionals Level : 200 Technology : Microsoft Office Delivery Method : Instructor-led (Classroom) Course Overview This is
[MS20347]: Enabling and Managing Office 365 Length : 5 Days Audience(s) : IT Professionals Level : 200 Technology : Microsoft Office Delivery Method : Instructor-led (Classroom) Course Overview This is
CEH: CERTIFIED ETHICAL HACKER v9
 CEH: CERTIFIED ETHICAL HACKER v9 SUMMARY The Certified Ethical Hacker (CEH) program is the core of the most desired information security training system any information security professional will ever
CEH: CERTIFIED ETHICAL HACKER v9 SUMMARY The Certified Ethical Hacker (CEH) program is the core of the most desired information security training system any information security professional will ever
Upgrading your Skills to MCSA Windows Server 2012
 Upgrading your Skills to MCSA Windows Server 2012 OD20417D; On-Demand, Video-based Course Description Get hands-on instruction and practice configuring and implementing new features and functionality in
Upgrading your Skills to MCSA Windows Server 2012 OD20417D; On-Demand, Video-based Course Description Get hands-on instruction and practice configuring and implementing new features and functionality in
Launching a Highly-regulated Startup in the Cloud
 Launching a Highly-regulated Startup in the Cloud Poornaprajna Udupi (@poornaudupi) 1 Starting in the 86%by 2020 Cloud Cisco Global Cloud Index: Forecast and Methodology, 2015 2020 2 Building blocks, Cost,
Launching a Highly-regulated Startup in the Cloud Poornaprajna Udupi (@poornaudupi) 1 Starting in the 86%by 2020 Cloud Cisco Global Cloud Index: Forecast and Methodology, 2015 2020 2 Building blocks, Cost,
Course No. MCSA Days Instructor-led, Hands-on
 MCSA: Windows Server 2012 Course No. MCSA2012 9 Days Instructor-led, Hands-on Introduction In this accelerated course nine day course, students will gain the skills and knowledge necessary to administer
MCSA: Windows Server 2012 Course No. MCSA2012 9 Days Instructor-led, Hands-on Introduction In this accelerated course nine day course, students will gain the skills and knowledge necessary to administer
Designing and Deploying Microsoft Exchange Server 2016
 Course Content Course Description: This course provides experienced Exchange Server administrators with the knowledge to design and implement an Exchange Server 2016 messaging environment. Students will
Course Content Course Description: This course provides experienced Exchange Server administrators with the knowledge to design and implement an Exchange Server 2016 messaging environment. Students will
Cloud Essentials for Architects using OpenStack
 Cloud Essentials for Architects using OpenStack Course Overview Start Date 5th March 2015 Duration 2 Days Location Dublin Course Code SS15-13 Programme Overview Cloud Computing is gaining increasing attention
Cloud Essentials for Architects using OpenStack Course Overview Start Date 5th March 2015 Duration 2 Days Location Dublin Course Code SS15-13 Programme Overview Cloud Computing is gaining increasing attention
Networking with Windows Server 2016
 Course 20741: Networking with Windows Server 2016 Page 1 of 7 Networking with Windows Server 2016 Course 20741: 4 days; Instructor-Led Introduction This 4-day classroom-based course provides the fundamental
Course 20741: Networking with Windows Server 2016 Page 1 of 7 Networking with Windows Server 2016 Course 20741: 4 days; Instructor-Led Introduction This 4-day classroom-based course provides the fundamental
Architecting Microsoft Azure Solutions (proposed exam 535)
 Architecting Microsoft Azure Solutions (proposed exam 535) IMPORTANT: Significant changes are in progress for exam 534 and its content. As a result, we are retiring this exam on December 31, 2017, and
Architecting Microsoft Azure Solutions (proposed exam 535) IMPORTANT: Significant changes are in progress for exam 534 and its content. As a result, we are retiring this exam on December 31, 2017, and
Cyber Security & Ethical Hacking Training. Introduction to Cyber Security Introduction to Cyber Security. Linux Operating System and Networking: LINUX
 Cyber Security & Ethical Hacking Training. Introduction to Cyber Security Introduction to Cyber Security HTML PHP Database Linux Operating System and Networking: LINUX NETWORKING Information Gathering:
Cyber Security & Ethical Hacking Training. Introduction to Cyber Security Introduction to Cyber Security HTML PHP Database Linux Operating System and Networking: LINUX NETWORKING Information Gathering:
Upgrading Your Skills to MCSA Windows 8.1
 Upgrading Your Skills to MCSA Windows 8.1 Course 20689D - Three days - Instructor-led - Hands-on Introduction This three day course is designed primarily for IT Professionals who want to upgrade their
Upgrading Your Skills to MCSA Windows 8.1 Course 20689D - Three days - Instructor-led - Hands-on Introduction This three day course is designed primarily for IT Professionals who want to upgrade their
MCSA Office 365 Bootcamp
 MCSA Office 365 Bootcamp Length: 6 days Format: Bootcamp Time: Day About This Course Demonstrate your skills in transitioning to and administering cloud-hosted business applications with Microsoft Office
MCSA Office 365 Bootcamp Length: 6 days Format: Bootcamp Time: Day About This Course Demonstrate your skills in transitioning to and administering cloud-hosted business applications with Microsoft Office
20347: Enabling and Managing Office hours
 20347: Enabling and Managing Office 365 35 hours About this course This is a 5-day instructor-led training (ILT) course that targets the needs of IT professionals who take part in evaluating, planning,
20347: Enabling and Managing Office 365 35 hours About this course This is a 5-day instructor-led training (ILT) course that targets the needs of IT professionals who take part in evaluating, planning,
Security. Protect your business from security threats with Pearl Technology. The Connection That Matters Most
 Security Protect your business from security threats with Pearl Technology The Connection That Matters Most Committed to Your Future When it comes to your business, security can mean many things. But to
Security Protect your business from security threats with Pearl Technology The Connection That Matters Most Committed to Your Future When it comes to your business, security can mean many things. But to
[MS20743]: Upgrading Your Skills to MCSA: Windows Server 2016
![[MS20743]: Upgrading Your Skills to MCSA: Windows Server 2016 [MS20743]: Upgrading Your Skills to MCSA: Windows Server 2016](/thumbs/77/75954743.jpg) [MS20743]: Upgrading Your Skills to MCSA: Windows Server 2016 Length : 5 Days Audience(s) : IT Professionals Level : 300 Technology : Windows Server Delivery Method : Instructor-led (Classroom) Course
[MS20743]: Upgrading Your Skills to MCSA: Windows Server 2016 Length : 5 Days Audience(s) : IT Professionals Level : 300 Technology : Windows Server Delivery Method : Instructor-led (Classroom) Course
Certified LAN and WAN Specialist (CLWS)
 529 Hahn Ave. Suite 101 Glendale CA 91203-1052 Tel 818.550.0770 Fax 818.550.8293 www.brandcollege.edu Certified LAN and WAN Specialist (CLWS) Program Summary This instructor-led program with a combination
529 Hahn Ave. Suite 101 Glendale CA 91203-1052 Tel 818.550.0770 Fax 818.550.8293 www.brandcollege.edu Certified LAN and WAN Specialist (CLWS) Program Summary This instructor-led program with a combination
CIT 480: Securing Computer Systems. Putting It All Together
 CIT 480: Securing Computer Systems Putting It All Together Assurance 1. Asset identification 1. Systems and information assets. 2. Infrastructure model and control 1. Network diagrams and inventory database.
CIT 480: Securing Computer Systems Putting It All Together Assurance 1. Asset identification 1. Systems and information assets. 2. Infrastructure model and control 1. Network diagrams and inventory database.
MCSE Mobility Earned: MCSE Cloud Platform & Infrastructure Earned: 2017 MCSE MCSE. MCSD App Builder. MCSE Business Applications Earned 2017
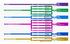 MOBILITY 10 Mobility CLOUD PLATFORM & INFRASTRUCTURE Server 2012 Server 2016 MCSA Linux on Azure Cloud Platform & Infrastructure MCSA Cloud Platform PRODUCTIVITY Server 2012 or 2016 MCSA Office 365 Productivity
MOBILITY 10 Mobility CLOUD PLATFORM & INFRASTRUCTURE Server 2012 Server 2016 MCSA Linux on Azure Cloud Platform & Infrastructure MCSA Cloud Platform PRODUCTIVITY Server 2012 or 2016 MCSA Office 365 Productivity
MCSE Cloud Platform & Infrastructure CLOUD PLATFORM & INFRASTRUCTURE.
 Exam 410: Installing and Configuring Server 2012 Exam 411: Administering Server 2012 Exam 412: Configuring Advanced Server 2012 services Server 2012 CLOUD PLATFORM & INFRASTRUCTURE Exam 740: Installation,
Exam 410: Installing and Configuring Server 2012 Exam 411: Administering Server 2012 Exam 412: Configuring Advanced Server 2012 services Server 2012 CLOUD PLATFORM & INFRASTRUCTURE Exam 740: Installation,
Microsoft Certified Solutions Associate (MCSA)
 Microsoft Certified Solutions Associate (MCSA) Installing and Configuring Windows Server 2012 (70-410) Module 1: Deploying and Managing Windows Server 2012 Windows Server 2012 Overview Overview of Windows
Microsoft Certified Solutions Associate (MCSA) Installing and Configuring Windows Server 2012 (70-410) Module 1: Deploying and Managing Windows Server 2012 Windows Server 2012 Overview Overview of Windows
