Connection-information-based connection rerouting for connection-oriented mobile communication networks
|
|
|
- Marjory O’Connor’
- 5 years ago
- Views:
Transcription
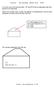
1 Dstrb. Syst. Engng 5 (1998) Prnted n the UK PII: S (98) Connecton-nformaton-based connecton reroutng for connecton-orented moble communcaton networks Mnho Song, Yanghee Cho and Chongsang Km Research Insttute of Advanced Computer Technology, Seoul Natonal Unversty, Kwanak-ku, Seoul, , Korea Department of Computer Engneerng, Seoul Natonal Unversty, Kwanak-ku, Seoul, , Korea Receved 9 August 1996 Abstract. To date, varous connecton reroutng methods for connecton-orented moble networks have been proposed. The prevous methods, however, are lmted to specfc topologes or envronments. In ths paper, we propose the connecton-nformaton-based reroutng wdely applcable to varous connecton-orented moble networks. Ths method requres nether a specfc topology nor a complex connecton, enables fast reroutng, provdes approprate route optmalty, and can be extended easly. 1. Introducton In moble computer communcaton, how to provde transparent network servces to moble users has been regarded as a dffcult problem. Much research has been carred out concernng the problem. Ths research has targeted varous envronments such as the Internet [1 6], MAN-based PCN [7 10], ATM-based PCN [11], and tradtonal or real-tme packet swtchng networks [12]. These networks are classfed nto two types, that s, the connecton-less network and the connectonorented network. The Internet belongs to the connectonless network, and the others belong to the connectonorented network. Research shows that one of the key ssues concernng the connecton-less network and that of the connecton-orented network are the data redrecton problem [1 5] and the connecton reroutng problem [9 12] respectvely. The handlng of the data redrecton problem and that of the connecton reroutng problem are smlar to some extent, but ther detals are very dfferent. There exsts a connecton between two communcatng users n the connecton-orented network whle there s no connecton for the communcatng users n the connectonless network. Therefore, when a user changes ts locaton to a new area, n the connecton-orented network ts connecton has to be rerouted to the new locaton at an approprate pont and all data addressed to the user Author to whom correspondence should be addressed. E-mal address: mhsong@twns.snu.ac.kr E-mal address: yhcho@smart.snu.ac.kr E-mal address: cskm@twns.snu.ac.kr are transmtted to hm through the rerouted connecton, whle n the connecton-less network an acton such as the connecton reroutng s not needed and each pece of data addressed to the user s redrected ndependently at an approprate pont towards the new locaton. Our nterest s n the connecton reroutng, and the motvaton of our work s the fact that exstng connecton reroutng methods are based to ther specfc envronments and so are not approprate for general connecton-orented moble network envronments. The am of ths paper s to propose a new connecton reroutng method, called the connecton-nformaton (CI)-based reroutng, whch s good for applcaton to varous connecton-orented moble networks. The connecton-orented moble network can be modelled to consst of three modules; the moble host (MH), the moble host agent (MHA), and the mobltyhandlng router (MR). The MHA medates between MHs and the fxed part of the network, and the MR handles connecton reroutng as well as tradtonal routng. Fgure 1 shows a stuaton of connecton reroutng n whch, durng a conversaton, a destnaton MH (MH d ) changes ts locaton whle ts source MH (MH s ) stays n ts area. In the example, the source MHA (MHA s ) s the agent for the source MH (MH s ), and the old MHA (MHA old ) and the new MHA (MHA new ) are the agents for the destnaton MH (MH d ) before and after the locaton change respectvely. The MR r s the reroutng pont. The MR s s the source endpont of the old connecton and the new connecton, and the MR old and the MR new are the destnaton-endpont MR of the old connecton and that of the new connecton /98/ $19.50 c 1998 The Brtsh Computer Socety, The Insttuton of Electrcal Engneers and IOP Publshng Ltd 47
2 M Song et al Fgure 1. Moble network model. respectvely. We use ths model as a bass for the followng dscussons. Wthout loss of generalty, we assume that the MH s s fxed whle the MH d s movng. In ths model, one locaton area corresponds to one subnet n an nternetwork or to one router coverage area n a subnet. Ths paper s organzed as follows. Secton 2 provdes a summary of exstng works. In secton 3, we descrbe the dea and concept of the CI-based reroutng n detal. In secton 4, we compare t wth prevous methods. In secton 5, we dscuss ts problems and solutons. In secton 6, we dscuss ts applcaton feasblty and extenson. In secton 7, we dscuss the data redrecton problem n relaton to the connecton reroutng. In secton 8, we conclude the paper. 2. Prevous works 2.1. Major reroutng methods Most connecton reroutng methods suggested for moble networks make reuse of the connecton to be rerouted for ts new one. Ths strategy s good for fast reroutng and low network processng overhead. Fve mportant such reroutng methods are as follows: (1) the connecton extenson reroutng [10], (2) the destnatonbased reroutng [9], (3) the branch-pont-traversal-based reroutng [12], (4) the multcast-jon-based reroutng [12], and (5) the vrtual-tree-based reroutng [11]. Ther reroutng procedures are shown n fgure 2, n whch the p-req (path-request), p-rsp (path-response), rr- REQ (reroutng-request), rr-rsp (reroutng-response), rr-cnfm (reroutng-confrmaton), rel-req (release- ReQuest) and rel-rsp (release-response) are the messages for the path request, the path response, the reroutng request, the reroutng response, the reroutng confrmaton, the release request and the release response respectvely. The number n and n(rel), the respectve heads of the reroutng and release messages, are the message flow sequence numbers of the reroutng and release respectvely. The rr-req s followed by the rr-rsp, and the rr-rsp s followed by the rr-cnfm, f needed. The rel-req message s sent by the reroutng MR towards the old destnaton MHA at the same tme that the rr-rsp s sent to the new destnaton MHA, so that the MRs and MHA on the old connecton branch release the resources for the branch. The rel-rsp message s sent to the MR by the old destnaton MHA as the response to the rel-req message. In the fgure, the bold arrows ndcate the flows of the rr-req, rr-rsp, and rr-cnfm messages, the thn arrows ndcate the flows of the rel-req and rel-rsp messages, and the dotted arrows ndcate the flows of the p-req and p-rsp messages. In the connecton extenson reroutng, when a communcatng destnaton MH has moved nto a new area, ts new MHA fnds the locaton of the MH s old destnatonendpont MR (MR old ) and sends the reroutng request message (rr-req) to the MR. The MR extends the MH s connecton to the new MHA, and then the extended connecton becomes the MH s new connecton. Ths method has the mert of smplcty. However, the MH s several locaton changes durng a conversaton may make the connecton largely devated from ts optmal route. In the destnaton-based reroutng, the reroutng pont s predetermned at the connecton set-up tme, and when a destnaton MH has entered a new area durng ts communcaton, ts new MHA sends the reroutng request message (rr-req) to the pre-determned pont. Ths method prevents the rerouted connecton from begn largely devated from ts optmal route to a certan extent, but t does not resolve the problem completely. In the branch-pont-traversal-based reroutng, when a destnaton MH has entered a new area durng ts communcaton, ts new MHA sends the rr-req message to the old agent of the MH (MHA old ) to request the old MHA to fnd the pont at whch the MH s connecton can branch to the new MHA, and then the old MHA ntalzes the fndng by forwardng the rr-req message over the connecton to be rerouted. The message meets a pont branchng to the new MHA at last and the pont becomes the reroutng pont. Ths method s approprate for networks whch have tree-lke topologes, but has dffcultes n beng 48
3 Connecton reroutng based on connecton nformaton Fgure 2. Reroutng procedures of prevous connecton reroutng methods. appled to the networks wth other topologes. Moreover, the traversal for fndng the reroutng pont may take a long tme. In the multcast-jon-based reroutng, the connecton s bult and managed by a multcast protocol, and the jon operaton of the protocol s used for the connecton reroutng. In the method, when a destnaton MH has entered a new area durng ts communcaton, ts new MHA ssues a jon request message towards the source MH (MH s ) or a specfc MR. The message meets the connecton at a pont at last, and the pont becomes the reroutng pont. In fact, there are three types for the jon operaton. In the frst [13] or the second type [14], the jon request message s sent towards the source MH or a specfc MR respectvely untl t meets wth an MR on the connecton to be rerouted. In the thrd type [15], a path request message (p-req) s sent towards the source MH and s captured by the agent of the source MH (MHA s ) at last, and then a path message (p-rsp) s sent to the new destnaton MHA by the source MHA, so that the new destnaton MHA can send the jon message (rr-req) along the path known by the path message to a pont whch wll be the reroutng pont. As known n the above, n the multcast-jon-based reroutng the reroutng pont s determned dynamcally rght at the reroutng tme, but the adopton of the multcast protocol for moblty handlng lmts the method only to the networks wth the capablty of multcastng. In the vrtual-tree-based reroutng, when a connecton s establshed, a tree of expected connecton branches s constructed as the destnaton end-part of the connecton. Therefore, when a destnaton MH has entered a new area durng ts communcaton, ts new MHA does not need to establsh a new connecton branch. Ths method s sutable for a specal case where the destnaton MH changes ts locaton frequently, but t may not be acceptable n most other cases because of the overhead cost of the connecton branches tree. The structures of the p-req, p-rsp, rr-req, rr- RSP, and rr-cnfm messages for the reroutng methods mentoned above can be thought to be lke those shown n fgure 3. Each of the messages conssts of the operaton feld, the destnaton address feld, the source address feld, and the CID (connecton dentfer) feld. Note that the CIDs of the messages have dfferent meanngs: the connecton to be rerouted n the p-req, p-rsp, and rr- REQ messages, the connecton rerouted n the rr-rsp and rr-cnfm messages, the connecton whch should be released n the rel-req message, and the connecton released n the rel-rsp message Problems of exstng methods and our ams When the above-mentoned exstng methods are examned n respect of general applcablty, they are found to have the followng problems. The rerouted connecton may be largely devated from ts expected optmal route (n the connecton extenson and destnaton-based reroutngs). The dstance between the reroutng pont and the new MHA may be very long, and so the reroutng may take a long tme (n the connecton extenson, destnatonbased, branch-pont-traversal-based, and multcast-jonbased reroutngs). The network s requred to have a specfc topology (n the branch-pont-traversal-based reroutng). The reroutng depends on a specfc protocol (n the multcast-jon-based reroutng). The connecton structure s complex (n the vrtualtree-based reroutng). Our proposal solves these problems, that s, t prevents the rerouted connecton from becomng abnormally long, t takes a short tme n reroutng, t does not depend on a specfc network topology or protocol, and t does not requre a complex connecton structure, so that t s sutable for general applcaton. 49
4 M Song et al Fgure 3. Reroutng message structures of prevous connecton reroutng methods. Fgure 4. Procedure of CI-based reroutng. 3. CI-based reroutng 3.1. Connecton reroutng based on CI A connecton can be represented by the combnaton of ts global connecton dentfer (GCID) and the addresses of the MRs on the connecton. We call the content the CI (connecton nformaton). The CI whch conssts of a connecton dentfer and router addresses can be consdered to be a connecton-orented verson of the route record whch s the nformaton for the datagram path n the connecton-less network and conssts of only router addresses [16]. Our reroutng method, called the CI-based reroutng, s based on the connecton nformaton. The procedure of the CI-based reroutng s as follows. (1) When a connecton s establshed, ts destnaton MH s provded wth the connecton nformaton. The source MHA, ntermedate MRs, and destnaton MHA on the connecton capture the GCID of the connecton and store t as an dentfer of the connecton durng the establshment. (2) When the MH has changed ts locaton durng a communcaton, the MH provdes ts connecton nformaton to ts new MHA. (3) The new MHA selects one MR beng closest to t for the reroutng pont of the move-n MH s connecton out of the MRs ncluded n the connecton nformaton, as shown n fgure 5. (We call the MR the closest MR.) The new MHA should be able to calculate cost dstances from t to the MRs. (4, 5) The new MHA requests the selected MR to reroute the connecton of the move-n MH. (6, 7) (6(rel), 7(rel)). The MR reroutes the connecton to the new MHA. That s, the MR requests the MRs and MHA on the old branch of the connecton to release the GCID and other resources for the connecton by sendng a release request message towards the old MHA (6(rel), 50
5 Connecton reroutng based on connecton nformaton Fgure 5. Selecton of the reroutng pont. Fgure 6. The format of CI feld. 7(rel)) and bulds the new branch of the connecton to the new MHA (6, 7), n parallel. When the constructon of the new branch s completed, the connecton nformaton about the new branch s provded to the MH. (8) The MH updates the correspondng part of ts old connecton nformaton wth the connecton nformaton about the new branch. (8(rel), 9(rel)). The old MHA sends a release response message to the reroutng MR. Ths method fulfls the goals presented at the end of secton 2.2 as follows. The rerouted connecton s not largely devated from ts possble optmal route because the connecton of the move-n MH s rerouted at the MR beng closest to the MH s new MHA. (Ths s dscussed n detal n secton 4.) The reroutng takes a very short tme because the dstance between the reroutng pont and the new MHA s very short. (Ths s also dscussed n detal n secton 4.) It does not depend on a specfc network topology n selectng the reroutng pont because the connecton nformaton s enough to select the reroutng pont. It does not depend on a specfc protocol because the proposed method uses only ts own protocol. The connecton structure s smple because the proposed method s based on the pont-to-pont uncast connecton and needs no addtonal connecton branches Acquston and update of connecton nformaton In our reroutng method, when a connecton s establshed, ts connecton nformaton s recorded n ts connecton setup request packet. We call ths technque the connecton recordng. The connecton recordng s dvded nto two parts, that s, the GCID recordng whch records the GCID n the connecton set-up request packet and the route recordng whch records the route record n the packet. The connecton set-up request packet must nclude a specal feld for the connecton nformaton. We call the specal feld the CI feld and defne the feld to be composed of the followng fve subfelds as shown n fgure 6. Operaton code the code of connecton recordng. GCID the unque dentfer for a connecton. Record length the maxmum number of the MR addresses to be ncluded n the CI feld. Record ponter the ponter ndcatng the next recordng poston of the route record subfeld. Route record the addresses of the preset number of MRs on a connecton. The GCID s recorded n the GCID subfeld by the source MHA and the MR addresses are recorded n the route record subfeld by the MRs. The record length s preset by the source MHA, and, n the case that all the space of the route record subfeld s used up before the connecton setup request packet reaches the destnaton MHA, the oldest MR address n the route record subfeld s overwrtten by a new one. Fnally, only the addresses of the preset number of MRs closest to the destnaton MH are provded to the MH. Ths strategy s based on the movng localty of MH. We call ths route-recordng technque the crcular route recordng. Ths route-recordng technque s very dfferent from that used n Internet [16], where n the case that all the route record space of a datagram s used up before the datagram reaches ts destnaton the route recordng s no longer performed at ongong routers and so the addresses of the foremost possble number of routers are eventually provded to the destnaton. One example of connecton recordng s shown n fgure 7. In the example, seven MRs are ncluded n a connecton, but the record length s only 5. Therefore, although all the seven MRs partcpate n connecton 51
6 M Song et al Fgure 7. Example of connecton recordng. Fgure 8. Structures of reroutng request and response messages. recordng, only the addresses of fve MRs can be ncluded n the CI feld. The crcular route recordng makes the addresses of the last fve MRs be ncluded n the CI feld. The frst overwrtng occurs at the MR 6. That s, the content of the address feld 1 n the CI feld s overwrtten wth the MR 6 address. When the connecton recordng s complete, the address feld 3, whch s the next recordng poston, ncludes the address of the MR farthest from the destnaton MHA, and the address feld 2 ncludes the address of the MR closest to the destnaton MHA. Consequently, the destnaton MH s provded wth the connecton nformaton ncludng one GCID and the addresses of the fve MRs closest to the destnaton MHA, that s, GCID, A3, A4, A5, A6, A7. Fgure 8 shows the structures of reroutng messages, that s, of the reroutng request message and of the reroutng response message. Some felds of the messages, that s, the record length feld of the rr-req message, and the record length, record ponter, and route record felds of the rr-rsp message are ncluded so that the connecton recordng can be performed at the reroutng tme. One example of the connecton recordng at the reroutng tme s shown n fgure 9. The record length of the rr-req message s ntalzed to 0, but, whle the message s beng forwarded to the reroutng MR, ts record length s ncremented by one per each ntermedate MR whch the message meets. When the rr-req message has reached the reroutng MR, the MR copes the record length of the rr-req message for that of the rr-rsp message. Whle reroutng s beng performed, the addresses of the MRs beng ncluded n the new connecton branch are recorded n the route record feld of the rr-rsp message and the nformaton about the new branch s provded to the destnaton MH at last. When the reroutng s completed, the MH updates the correspondng part of ts old connecton nformaton wth the connecton nformaton about the new branch. 52
7 Connecton reroutng based on connecton nformaton Fgure 9. Connecton recordng at connecton reroutng. Fgure 10. Comparson of reroutng procedures Release of old connecton branch The structures of the release request and response messages are the same as those shown n fgure 3, except the CID feld s renamed as the GCID feld. The release of the old connecton branch needs much care because the outstandng data to the source and destnaton MHs should be processed properly before the release [17]. We wll handle ths problem n another paper. 4. Quanttatve comparsons 4.1. Defnton of evaluaton factors We defne the followng performance evaluaton factors, so that we may compare our proposed method wth prevous ones quanttatvely. Connecton dstance number of lnks on a connecton. Movng dstance number of lnks to whch extent an MH moved. Reroute dstance ( reroute-dstance ) number of lnks on a new connecton branch. Route optmalty ( route-optmalty ) the extent to whch the real route of a rerouted connecton s close to ts optmal route, that s, the dstance of the optmal route over that of the real route. Degree of reroutng procedure ( deg-of-reroutngprocedure ) number of all the sequences of operatons for reroutng (refer to fgure 10). Sze of connecton nformaton ( sze-of-ci ) number of MR addresses ncluded n a connecton nformaton. Recordng length ( recordng-length ) number of the MRs of a connecton whch were nvolved n connecton recordng. Reroutng tme ( reroutng-tme ) the tme needed for performng all the sequences of operatons for reroutng. Sze of reroutng messages ( sze-of-reroutngmessages ) sum of the szes of the messages for reroutng. For convenence, we constran the messages to the reroutng request, response, and confrmaton messages only, and count the number of address felds for the sze of each message (refer to fgures 3 and 8) Comparson results The reroutng procedures of the prevous methods dscussed n sectons 2 and our CI-based method are compared wth each other over a connecton n fgure 10. In the fgure, the c-e, d, b-p-t, m-j, v-t, and CI are the abbrevatons of the connecton extenson reroutng, destnaton-based reroutng, branch-pont-traversal-based reroutng, multcast-jon-based reroutng, vrtual-tree-based 53
8 M Song et al reroutng, and CI-based reroutng respectvely, and the MR c-e, MR b-p-t/m-j (whch s the abbrevaton of the MR b-p-t /MR m-j ), and MR CI represent the reroutng ponts of the connecton extenson reroutng, branch-pont-traversalbased reroutng and multcast-jon-based reroutng, and CIbased reroutng respectvely. Our comparson results are as follows. Below, the reroutng methods are ndvdually dstngushed by subscrpts for each evaluaton factor, and an (evaluaton factor) /j/k/.../z s the abbrevaton of the (evaluaton factor) /(evaluaton factor) j /(evaluaton factor) k /.../(evaluaton factor) z, whch means the evaluaton factor of the reroutng method, that of the method j, that of the method k,..., and that of the method z. reroute-dstance v-t = 0, reroute-dstance CI <= reroute-dstance c-e/d/b-p-t/m-j. The dstance of the new connecton branch of the CIbased reroutng s shortest n comparson wth the other methods except the vrtual-tree-based reroutng, n whch the dstance s zero. So, we obtan the above results. route-optmalty c-e <= route-optmalty CI <= route-optmalty b-p-t/m-j. The dstance between the source MHA and the reroutng pont plus the dstance between the reroutng pont and the new MHA of the CI-based reroutng s no smaller than those of the branch-pont-traversal-based reroutng and multcast-jon-based reroutng, whch provde optmal routes, and s no larger than that of the connecton extenson reroutng. So, we obtan the above results. The route optmaltes of the destnaton-based reroutng and vrtual-tree-based reroutng cannot be compared wth those of others because the reroutng ponts of the two methods are dependent on mplementatons. deg-of-reroutng-procedure v-t = 0, deg-of-reroutng-procedure c-e/d/ci = 2, deg-of-reroutng-procedure m-j = 2or5, deg-of-reroutng-procedure b-p-t = 4. All the sequences of reroutng operatons are 1(rr- REQ) and 2(rr-RSP) n the connecton extenson reroutng, destnaton-based reroutng, and CI-based reroutng, 1(p-REQ), 2(p-RSP), 3(p-RSP), 4(rr-REQ), and 5(rr-RSP) or 4(rr-REQ) and 5(rr-RSP) n the multcast-jon-based reroutng, and 1(rr-REQ), 2(rr-REQ), 3(rr-RSP), and 4(rr- CNFM) n the branch-pont-traversal-based reroutng. The vrtual-tree-based reroutng does not have those reroutng operatons. So, we obtan the above results. sze-of-ci b-p-t/m-j/v-t = 0, sze-of-ci c-e/d = 1, 0 <= sze-of-ci CI <= k (k: record length). In the branch-pont-traversal-based reroutng, multcastjon-based reroutng, and vrtual-tree-based reroutng, no MR address s known to the destnaton MH. In the connecton extenson reroutng or destnaton-based reroutng, the destnaton endpont MR or a prefxed pont MR s known to the destnaton MH, and so the connecton nformaton szes of the two methods can be sad to be 1. In the CI-based reroutng, the record length number of MR addresses n maxmum are known to the destnaton MH. So, we obtan the above results. recordng-length b-p-t/m-j/v-t = 0, recordng-length c-e/d = 1 recordng-length CI = n (n: number of MRs on connecton). In the branch-pont-traversal-based reroutng, multcastjon-based reroutng, and vrtual-tree-based reroutng, no MR s nvolved n the connecton recordng. In the connecton extenson reroutng or destnaton-based reroutng, t can be sad that one MR s nvolved n the connecton recordng. In the CI-based reroutng, all MRs beng ncluded n a connecton are nvolved n the connecton recordng. So, we obtan the above results. reroutng-tme v-t = 0, reroutng-tme CI <= reroutng-tme c-e/d/b-p-t/m-j. The CI-based reroutng has no larger total sum of the dstances of connecton segments correspondng to the sequences of reroutng operatons than the connectonextenson reroutng, destnaton-based reroutng, branchpont-traversal-based reroutng, and multcast-jon-based reroutng. So, f we assume that the reroutng tme s manly dependent on the total sum of the dstances of the connecton segments correspondng to the sequences of reroutng operatons, we obtan the above results. sze-of-reroutng-messages v-t = 0, sze-of-reroutng-messages c-e/d/m-j = 4, sze-of-reroutng-messages b-p-t = 6, sze-of-reroutng-messages CI = 4 + reroute-dstance CI. (Referrng to fgures 3 and 8.) As shown n fgures 3 and 8, the total numbers of address felds n the reroutng (request, response, and confrmaton) messages of the connecton extenson reroutng, destnaton-based reroutng, branch-pont-traversalbased reroutng, and multcast-jon-based reroutng are 4, 4, 6, and 4 respectvely, and that of the CI-based reroutng s 4 plus the reroute dstance. The vrtual-tree-based reroutng has no reroutng messages, and so ts sze of reroutng messages s zero. So, we obtan the above results Detaled comparsons The prevous secton showed that the proposed method, keepng ts route optmalty moderate, has no longer a 54
9 Connecton reroutng based on connecton nformaton Fgure 11. Network envronment for comparson (the extended crossbar network). reroute dstance and reroutng tme than any other one whose connecton structure s the pont-to-pont. We show ths pont more clearly now. The extended crossbar network shown n fgure 11 s ntroduced for ths purpose and on the network the CI-based reroutng s compared n respect of the reroute dstance and route optmalty wth the connecton extenson reroutng and the multcast-jonbased reroutng whch have the same degree of reroutng procedure as the CI-based reroutng. The extended crossbar network provdes an envronment for smple calculaton and far comparson of reroute dstances and route optmaltes. In the network, each node except boundary nodes has eght lnks. The horzontal or vertcal lnk has the length of 1, and the slope lnk has the length of 2. Each of the eght lnks corresponds to one movng drecton of MH, and so an MH has eght movng drectons at a node. The eght movng drectons can be grouped nto fve cases for the calculaton of reroute dstances and route optmaltes. Our comparson results are as follows. Below, the connecton dstance and movng dstance are represented wth l and m respectvely. (1) Case 1: reroute-dstance c-e/ci/m-j = m. route-optmalty c-e/ci/m-j = 1. (2) Case 2: reroute-dstance c-e/ci = m. route-dstance m-j = 2 m. route-optmalty c-e/ci ={l+( 2 1)m}/(l + m). route-optmalty m-j = 1. (3) Case 3: reroute-dstance c-e/ci/m-j = m. route-optmalty c-e/ci/m-j = 1. 55
10 M Song et al (4) Case 4: reroute-dstance c-e/m-j = m. reroute-dstance CI = m/ 2. route-optmalty c-e ={l+(1 2)m}/(l + m). route-optmalty CI ={l+(1 2)m}/l. route-optmalty m-j = 1. (5) Case 5: reroute-dstance c-e = m. reroute-dstance CI/m-j = 0. route-optmalty c-e = (1 m)/(l + m). route-optmalty CI/m-j = l. When we assume that the probablty wth whch an MH moves n each drecton at a node s 1, we can calculate 8 the average reroute dstance and route optmalty for each reroutng method as follows. Below, the fve cases are dstngushed by superscrpts for each of the reroute dstances and route optmaltes reroute-dstance average ={1 reroute-dstance case1 +2 reroute-dstance case2 +2 reroute-dstance case3 +2 reroute-dstance case4 +1 reroute-dstance case5 }/8. route-optmalty average ={1 route-optmalty case1 +2 route-optmalty case2 +2 route-optmalty case3 +2 route-optmalty case4 +1 route-optmalty case5 }/8. The above results wth the connecton dstance (l) beng from 10 to 12 are depcted n fgure 12. The movng dstance (m) ranges from 0 to 10, excludng the 11 and 12 for convenence. We can see the followng facts from the fgure. On average, the reroute dstance of the CI-based reroutng s shorter than those of the connecton extenson reroutng and multcast-jon-based reroutng, and the route optmalty of the CI-based reroutng s between that of the connecton extenson reroutng and that of the multcastjon-based reroutng, for the movng dstances above 0, as the average case shows. Case (4) shows ths fact best. Some nterestng facts can be seen from cases (1) (3) and (5). That s, n each of the four cases, two or all three reroutng methods have the same reroute dstance and route optmalty as follows. In cases (1) and (3), all the three reroutng methods have the same reroute dstance and route optmalty. In case (2), the CI-based reroutng and the connecton extenson reroutng have the same reroute dstance and route optmalty. In case (5), the CI-based reroutng and the multcast-jon-based reroutng have the same reroute dstance and route optmalty. These nterestng facts mean that the three reroutng methods make lttle dfference n some cases Normalzed comparson One specal pont whch we can see from fgure 12 s that the route optmaltes of the connecton extenson reroutng and CI-based reroutng are dependent on the connecton dstance l as well as on the movng dstance m n cases (2), (4), and (5). That s, the route optmalty ncreases as l ncreases for the same m n the two reroutng methods of the three cases. Ths s because the movng dstance relatve to the connecton dstance, that s, m to l rato (m/l) decreases as l ncreases for the same m. Consderng now general envronments where l and m can have any values, ncludng 10 12, we normalze m nto m/l. When we represent the m/l wth r and assume that the r ranges from 0 to 1, we can rewrte the prevous equatons as follows. (1) Case 1: reroute-d c-e/ci/m-j = r. route-optmalty c-e/ci/m-j = 1. (2) Case 2: reroute-d c-e/ci = r. reroute-d m-j = 2r. route-optmalty c-e/ci ={l+( 2 1)m}/(l + m) ={(l + m) + ( 2 2)m}/(l + m) = 1 (2 2)m/(l + m) = 1 (2 2)r/(1 + r) route-optmalty m-j = 1. (3) Case 3: reroute-d c-e/ci/m-j = r. route-optmalty c-e/ci/m-j = 1. (4) Case 4: reroute-d c-e/m-j = r. reroute-d CI = r/ 2. route-optmalty c e ={l+(1 2)m}/(l + m) = 1 2m/(l + m) = 1 2r/(1 + r) route-optmalty CI ={l+(1 2)m}/l = 1+(1 2)r. (5) Case 5: reroute-d c-e = m. reroute-dstance CI/m-j = 0. route-optmalty c-e = (l m)/(l + m) ={(l + m) 2m}/(l + m) = 1 2r/(1 + r). route-optmalty CI/m-j = 1. The new reroute dstances and route optmaltes accordng to the normalzed movng dstance (r) are depcted n fgure 13. The graphs of the fgure can show now the reroute dstances and route optmaltes for the m over any values of l, ncludng
11 Connecton reroutng based on connecton nformaton Fgure 12. Comparson of reroute dstances and route optmaltes wth l = 10,11, and
12 M Song et al Fgure 12. (Contnued) 5. Problems and solutons The proposed method s based on the connecton nformaton. The connecton nformaton gves the generalty of applcaton to the proposed method. However, some problems are generated from the connecton nformaton and connecton recordng. In fact, the comparson results shown n the prevous secton stated that the proposed method s worst n respect to the sze of connecton nformaton and the dstance of connecton recordng among the compared ones. We now dscuss the problems due to the connecton nformaton and connecton recordng. The connecton nformaton ncreases the sze of the connecton set-up request message and of the reroutng response message, and so ncreases the network traffc. However, ths s not a serous problem when the maxmum sze of the connecton nformaton, that s, the record length, s adjusted approprately small at the connecton set-up tme, or when the connecton has a long sesson and the MH does not move so frequently, n whch case the overhead of the connecton nformaton s not of so large a rato to the total traffc of the sesson. However, the connecton nformaton may be a heavy overhead to the network when the sesson s short or the MH moves very frequently. One soluton to ths problem s to dfferentate the maxmum connecton nformaton sze accordng to the types of connecton sesson and the movng frequency of MH. One example s that the maxmum connecton nformaton sze s forced to be small when the connecton sesson s short or the movng frequency s very hgh, whle the maxmum connecton nformaton sze s allowed to be large when the connecton sesson s long and the movng frequency s not so hgh. The connecton recordng may make the connecton set-up be delayed at each of the MRs beng ncluded n the connecton. Ths problem, however, s smply resolved when the operaton of connecton set-up and that of the connecton recordng are performed n parallel n the MRs. Another soluton s that the source MHA gets all the addresses of the MRs to be ncluded n the connecton through a fast source routng technque [18] so that the source MHA can record the connecton nformaton n a connecton set-up request packet at one tme and establshng the connecton can be accelerated. 6. Consderatons for applcatons 6.1. CI acquston The ntroducton of connecton nformaton nto the connecton reroutng s a unque strategy of the CIbased reroutng. Therefore, we need to examne whether or not the connecton nformaton can be provded to the destnaton MH through a connecton set-up request message n real networks. We examne t n the mportant emergng connecton-orented moble networks based on the X.25 [19], ST2 [13], ATM [11, 20, 21], and DQDB [7, 22] network. 58
13 Connecton reroutng based on connecton nformaton Fgure 13. Comparson of reroute dstances and route optmaltes wth normalzed movng dstances. The X.25 connecton set-up request packet has the user data area, and the area can be used for other purposes. When we assume that the operaton code, record length, and record ponter of a CI feld requre one octet respectvely, and that the GCID s composed of the address and local connecton dentfer (LCI) of the source MH, the user data area (whch s assumed to be 128 octets) can nclude one GCID and fve MR addresses because the maxmum length of the X.25 network address NSAP (network servce access pont) s 20 octets [23], and the LCI, called VCI (vrtual crcut dentfer), requres 1.5 octet [19]. The ST2 connecton set-up packet ncludes the feld for a global connecton dentfer, called the stream dentfer (SID) feld, and the optonal route record feld. The couple of a SID and a route record corresponds to our connecton nformaton exactly, and therefore the proposed CI-based reroutng can be easly realzed n the ST2 network. In the sgnallng protocol of the ATM network, that s, n Q.2931 [24], varable length nformaton elements can be defned for specal purposes, and the connecton (call) setup request packet of the Q.2931 can nclude some varable nformaton elements. The GCID (global call ID) and TL (transt lst) nformaton elements have been proposed for the leave-ntated jon n the communcaton on the multpont-to-multpont connecton and for the source routng n P-NNI (prvate-network-to-network nterface) respectvely [25, 26]. Referrng to the two nformaton elements, we can defne the CI nformaton element for the ATM-based moble network. The CI nformaton element of the DQDB-based moble network, whose sgnallng protocol s Q.931, can be defned smlarly Connecton fluctuaton When a node or lnk fals n a network, the connectons traversng the lnk or the node have to be rerouted. Ths nternal connecton reroutng nvaldates the connecton nformaton about the connectons whch s mantaned n the related MHs, and so the CI-based reroutng cannot be appled to these connectons. The soluton to ths problem s as follows. Frst, we extend the CI feld so that t ncludes two addtonal subfelds, that s, the CHANGED subfeld and the address of MHA s(d) subfeld as shown n fgure 14. The CHANGED flag s for the status of a connecton, that s, t ndcates whether or not the connecton s fluctuated due to the node or lnk falure. The flag s ntalzed to 0, but s changed to 1 when the connecton s fluctuated. The subfeld of the address of MHA s(d) s for the address of a source or destnaton MHA. The address of a source or destnaton MHA s a new addton to the connecton nformaton and s used when the connecton fluctuaton occurs. Second, the rr-req message s extended and modfed somewhat. That s, the CHANGED subfeld s nserted nto the second subfeld of the rr-req message, and the address of selected MR subfeld of the message s renamed 59
14 M Song et al Fgure 13. (Contnued) as the address of selected MR/MHA s(d) subfeld, as shown n fgure 15. Thrd, when the connecton s fluctuated, the reroutng pont s selected by another method. In the case that a connecton s fluctuated, each endpont MR on the fluctuated part of the connecton reports the event to the source and destnaton MHs. When each MH receves the report, t changes the CHANGED flag for the connecton to 1. When such an MH has changed ts locaton, ts new MHA ssues the reroutng request message towards ts peer MHA (smlarly as n the frst type of the multcast-jonbased reroutng mentoned n secton 2.1) nstead of sendng the message to the closest MR. Fnally, the message meets one of the MRs over the connecton to be rerouted, and then the MR, whch we call the optmal MR, becomes the reroutng pont of the connecton. Fgure 16 shows a smple example for the reroutng of a fluctuated connecton, where the destnaton MH changes ts locaton and then the new destnaton MHA ssues the reroutng request message towards the source MHA. Note that the operatons for connecton recordng descrbed at the end of secton 3.2 do not need to be performed durng the reroutng request and response for a fluctuated connecton because the connecton nformaton wll no longer be used for the connecton. The second verson of the CI-based reroutng whch consders the connecton fluctuaton s descrbed below. (Handlng of the release request and response s the same as the frst verson, and so s omtted.) 60
15 Connecton reroutng based on connecton nformaton Fgure 13. (Contnued) Fgure 14. Extended CI feld. Fgure 15. Extended rr-req message. (1) When a connecton s establshed, ts destnaton MH s provded wth the connecton nformaton through connecton recordng. The MH ntalzes the CHANGED flag of ts CI to 0. (If the connecton s fluctuated, the CHANGED flag s changed to 1.) (2) When the destnaton MH has changed ts locaton durng a communcaton, the MH provdes ts CI to ts new MHA. (3, 4, 5) If the CHANGED flag of the CI s 1 (ths means that the connecton of the move-n MH was fluctuated), the MHA ssues the reroutng request message towards ts peer MHA, that s, the source MHA. The message meets one of the MRs on the connecton to be rerouted at last, and the MR becomes the reroutng pont of the connecton. If the CHANGED flag s 0, the new MHA selects one MR beng closest to the MHA out of the MRs ncluded n the CI for the reroutng pont, and then requests the MR to reroute the connecton by sendng the reroutng request message to the MR. (6, 7) The MR whch becomes the reroutng pont reroutes the connecton to the new MHA. If the CHANGED flag of the reroutng request message whch the MR receved s 0, the connecton recordng s performed n parallel to the reroutng so that the connecton nformaton about the new connecton branch s provded to the MH. If the flag s 1, the connecton recordng s not performed. (8) If the CHANGED flag of the CI s 0 n the MH, the MH updates the correspondng part of ts CI wth the connecton nformaton about the new branch. If the flag s 1, the MH does not need such a update acton Support to varous reroutng methods In the second verson of the CI-based reroutng, the closest MR s selected for the reroutng pont by default, but the optmal MR s selected for the reroutng pont when the connecton has experenced the fluctuaton. In ths secton, we call the second verson of the CI-based reroutng the extended closest pont reroutng and extend t fur- 61
16 M Song et al Fgure 16. Example of connecton reroutng of a fluctuated connecton. Fgure 17. Re-extenson of the CI-feld and the frst extended rr-req and rr-rsp messages. ther so that three mportant exstng reroutng methods can be ncorporated nto t. The three reroutng methods are the connecton extenson reroutng, the destnaton-based reroutng, and the multcast-jon-based reroutng wth some changes. We call them now the endpont reroutng, the prefxed pont reroutng, and the optmal pont reroutng respectvely. The thrd verson of the CI-based reroutng has four reroutng modes, each of whch corresponds to one of the extended closest pont reroutng and the above three reroutng methods beng ncorporated. The four reroutng modes are compared n table 1. The further extended structures of the CI-feld and the frst extended rr-req and rr- RSP messages are also shown n fgure 17. The re-extended structures nclude the felds for the reroutng mode. Some mportant notes to the thrd verson are as follows. Frst, the connecton recordng strateges of the endpont reroutng and the prefxed pont reroutng are left to local technques because the crcular recordng s a waste to them. Second, the address of MHA s/d subfeld s needed only for the extended closest pont reroutng and the optmal pont reroutng. Thrd, the connecton recordng at the tme of reroutng s needed only n the extended closest pont reroutng and the endpont reroutng. The procedure of the thrd verson of the CI-based reroutng s as follows. 62
17 1. Extended closest pont reroutng Connecton reroutng based on connecton nformaton Table 1. Comparson of reroutng modes. (n.u.: not used; u.: used; addr.(s): address(es).) Contents Intal Connecton connecton CHANGED Address of Record recordng at the Reroutng modes nformaton flag MHA s(d) length tme of reroutng 2. Optmal pont reroutng 3. Endpont reroutng 4. Pre-fxed pont reroutng not fluctuated GCID + addr. of MHA s(d) + addr.s of MRs 0 u. 1 n MRs on new branch fluctuated 1 0 no MR GCID + addr. of MHA s(d) n.u. u. 0 no MR GCID + one addr. of MR n.u. n.u. 1 endpont MR n.u. n.u. 1 no MR Fgure 18. Four approaches of data redrecton. (1) When a connecton s establshed, ts destnaton MH s provded wth the connecton nformaton through connecton recordng. The connecton recordng depends on the reroutng mode set by the source MH. If the reroutng mode s 1, the connecton nformaton s made through the crcular recordng. If the mode s 2, only the address of the source MHA s provded to the destnaton MH as the connecton nformaton. If the mode s 3 or 4, the address of the destnaton endpont MR or a prefxed pont MR s provded to the destnaton MH as the connecton nformaton by a local technque. (If the connecton s fluctuated, the CHANGED flag s changed to 1.) (2) When the destnaton MH has changed ts locaton durng a communcaton, the MH provdes ts CI to ts new MHA. (3, 4, 5) If the reroutng mode and the CHANGED flag of the CI are 1 and 0 respectvely, the new MHA selects one MR beng closest from the MHA out of the MRs ncluded n the CI for the reroutng pont, and then requests the MR to reroute the connecton by sendng the reroutng request message to the MR. If both of the reroutng mode and the CHANGED flag are 1 or f the reroutng mode s 2, the MHA ssues the reroutng request message towards the source MHA (MHA s ) on the connecton to be rerouted. The message meets one of the MRs on the connecton at last, and the MR becomes the reroutng pont. If the reroutng mode s 3 or 4, the MHA sends the reroutng request message to the destnaton endpont MR or a prefxed pont MR, whch address s the unque MR address n the CI. (6, 7) The MR whch becomes the reroutng pont reroutes the connecton to the new MHA. If the reroutng mode and the CHANGED flag of the reroutng request message whch the MR receved are 1 and 0 respectvely, the connecton recordng s performed by the crcular recordng so that the connecton nformaton about the new connecton branch s provded to the destnaton MH. If both the reroutng mode and the CHANGED flag are 1, or f the reroutng mode s 2 or 4, the connecton recordng s not performed. If the reroutng mode s 3, the connecton recordng s performed by a local technque so that the address of the new destnaton endpont MR s provded to the destnaton MH. (8) If the reroutng mode and the CHANGED flag of the CI are 1 and 0 n the MH respectvely, the MH updates the correspondng part of ts CI wth the connecton nformaton about the new branch. If the reroutng mode s 3, the address of the old destnaton endpont MR s replaced wth that of the new one n the CI. In the other cases, the MH does not need such update actons. 63
18 M Song et al 7. Data redrecton and connecton reroutng We now turn our dscusson to the data redrecton problem of the connecton-less moble network and relate the data redrecton problem to the connecton reroutng. The mportant dfference of the data redrecton from the connecton reroutng s that the data redrecton can be made at the MHA [1, 3 5] as well as at the MR [2], and all data addressed to a user do not have the same redrecton pont n a communcaton [3, 5]. Consderng the dfference, we classfy exstng data redrecton methods by the followng four approaches as shown n fgure 18. The four approaches can be used ndvdually or n combnaton. (1) Redrecton at MHA old. The data are redrected towards the new destnaton MHA at the old destnaton MHA (MHA old ). In ths case, the new locaton of an MH should always be known to ts MHA old. (2) Redrecton at MHA home. The data are redrected towards the new destnaton MHA at the home MHA (MHA home ). In ths case, the new locaton of an MH should always be known to ts MHA home. (In the connectonless moble network, each MH s related to a home MHA, whch mantans the nformaton about the MH, especally the current locaton of the MH.) (3) Redrecton at MHA s. The data are redrected towards the new destnaton MHA at the source MHA (MHA s ). In ths case, the new locaton of an MH should always be known to ts MHA s. (4) Redrecton at an MR on a path between MHA new and MHA home. The data are redrected towards the new destnaton MHA at an MR on a path between the new destnaton MHA (MHA new ) and the home MHA (MHA home ). In ths case, the new locaton of an MH should always be known to the MRs on a path between ts MHA new and MHA home. Out of the proposals for the connecton-less moble network servces, the Columba proposal [1], the IBM proposal [4], and the Sony proposal [2] use only approaches (1), (2), and (4) respectvely. The Matsushta proposal [3] uses approaches (1) (3) n combnaton. The IETF (Internet Engneerng Task Force) proposal [5] uses approach (2) n basc and approaches (1) and (3) optonally. In the four data redrecton approaches, when we consder the MHA as the MR, we obtan the followng nterestng results. The frst redrecton approach s smlar to the connecton extenson reroutng n that the old destnaton-endpont s the pont at whch the data addressed to the destnaton MH turns to the new locaton of the destnaton MH. The second redrecton approach s smlar to the destnaton-based reroutng n that a prefxed pont s the turnng pont. The thrd approach s smlar to the full-reestablshment reroutng method [12] n that the source-endpont s the turnng pont. The fourth approach s smlar to the second type of the multcastjon-based reroutng n that an MR on a path between the new MHA and a specfc pont (whch s an MR n the multcast-jon-based reroutng and s a home MHA n the fourth data redrecton approach) s the turnng pont. We can see from these facts that the data redrecton problem and the connecton reroutng problem can be handled consstently, although the two problems belong to dfferent types of networks. Moreover, we can extract from the above dscussons that our CI-based reroutng can be appled to the connecton-less moble network so that the closest MR may be the redrecton pont. More detal about ths wll be handled n a separate work. 8. Concluson In ths paper, we proposed a new connecton reroutng method called the CI-based reroutng, compared t wth prevous methods, and dscussed ts problems and solutons, the consderatons for applcatons, ts extensons, and ts applcablty to the connecton-less moble network. Ths method s wdely applcable to varous connecton-orented moble networks because t does not requre a specfc topology or connecton, prevents a rerouted connecton from beng largely devated from ts possble optmal route, enables fast reroutng, and can be extended easly. Our ongong work s to apply the method to the ATM-based moble network n detal, and to extend t further for the moble multcast communcaton. References [1] Ioannds J, Duchamp D and Magure G Q Jr 1991 IP-based-Protocols for Moble Internetworkng (ACM SIGCOMM 91) pp [2] Teraoka F, Yokote Y and Tokoro M September 1991 A Network Archtecture Provdng Host Mgraton Transparency (ACM SIGCOMM 91) pp [3] Wanda H, Yozawa T, Ohnsh T and Tanaka Y 1993 Moble Computng Envronment based on Internet Packet Forwardng USENIX pp [4] Bhagwat P and Perkns C E 1993 A Moble Networkng System based on Internet Protocol (USENIX Assocaton Moble and Locaton-Independent Computng System) pp [5] Moble IP Workng Group 1993 Routng Supports for IP Moble Hosts RFC Draft [6] Carlberg K 1992 A routng archtecture that supports moble end systems IEEE MILCOM 92 [7] Huang N and Ko-Shung 1994 A dstrbuted path mgraton scheme for IEEE based personal communcaton networks IEEE J. Selected Areas Commun [8] Leung VCM,Qan N, Malyan A D and Donaldson R W 1994 Call control and traffc transport for connecton-orented hgh speed wreless personal communcatons over metropoltan area networks IEEE J. Selected Areas Commun [9] Nanda S, Dravada S and Samad B May 1993 Handoff management and performance for wreless access usng metropoltan area networks IEEE VTC 93 pp [10] Polln G P, Meer-Hellstern K S and Goodman D J 1992 Handover protocols between metropoltan area networks IEEE GLOBECOM 92 pp [11] Acampora A S and Naghshneh M 1994 An archtecture and methodology for moble-executed handoff n cellular ATM networks IEEE J. Selected Areas Commun [12] Keeton K, Mah B A, Sehan S, Karz R H and Ferrar D 1993 Provdng connecton-orented network servces to moble hosts USENIX Symp. 93 pp
A Binarization Algorithm specialized on Document Images and Photos
 A Bnarzaton Algorthm specalzed on Document mages and Photos Ergna Kavalleratou Dept. of nformaton and Communcaton Systems Engneerng Unversty of the Aegean kavalleratou@aegean.gr Abstract n ths paper, a
A Bnarzaton Algorthm specalzed on Document mages and Photos Ergna Kavalleratou Dept. of nformaton and Communcaton Systems Engneerng Unversty of the Aegean kavalleratou@aegean.gr Abstract n ths paper, a
Load-Balanced Anycast Routing
 Load-Balanced Anycast Routng Chng-Yu Ln, Jung-Hua Lo, and Sy-Yen Kuo Department of Electrcal Engneerng atonal Tawan Unversty, Tape, Tawan sykuo@cc.ee.ntu.edu.tw Abstract For fault-tolerance and load-balance
Load-Balanced Anycast Routng Chng-Yu Ln, Jung-Hua Lo, and Sy-Yen Kuo Department of Electrcal Engneerng atonal Tawan Unversty, Tape, Tawan sykuo@cc.ee.ntu.edu.tw Abstract For fault-tolerance and load-balance
Evaluation of an Enhanced Scheme for High-level Nested Network Mobility
 IJCSNS Internatonal Journal of Computer Scence and Network Securty, VOL.15 No.10, October 2015 1 Evaluaton of an Enhanced Scheme for Hgh-level Nested Network Moblty Mohammed Babker Al Mohammed, Asha Hassan.
IJCSNS Internatonal Journal of Computer Scence and Network Securty, VOL.15 No.10, October 2015 1 Evaluaton of an Enhanced Scheme for Hgh-level Nested Network Moblty Mohammed Babker Al Mohammed, Asha Hassan.
For instance, ; the five basic number-sets are increasingly more n A B & B A A = B (1)
 Secton 1.2 Subsets and the Boolean operatons on sets If every element of the set A s an element of the set B, we say that A s a subset of B, or that A s contaned n B, or that B contans A, and we wrte A
Secton 1.2 Subsets and the Boolean operatons on sets If every element of the set A s an element of the set B, we say that A s a subset of B, or that A s contaned n B, or that B contans A, and we wrte A
Parallelism for Nested Loops with Non-uniform and Flow Dependences
 Parallelsm for Nested Loops wth Non-unform and Flow Dependences Sam-Jn Jeong Dept. of Informaton & Communcaton Engneerng, Cheonan Unversty, 5, Anseo-dong, Cheonan, Chungnam, 330-80, Korea. seong@cheonan.ac.kr
Parallelsm for Nested Loops wth Non-unform and Flow Dependences Sam-Jn Jeong Dept. of Informaton & Communcaton Engneerng, Cheonan Unversty, 5, Anseo-dong, Cheonan, Chungnam, 330-80, Korea. seong@cheonan.ac.kr
Cluster Analysis of Electrical Behavior
 Journal of Computer and Communcatons, 205, 3, 88-93 Publshed Onlne May 205 n ScRes. http://www.scrp.org/ournal/cc http://dx.do.org/0.4236/cc.205.350 Cluster Analyss of Electrcal Behavor Ln Lu Ln Lu, School
Journal of Computer and Communcatons, 205, 3, 88-93 Publshed Onlne May 205 n ScRes. http://www.scrp.org/ournal/cc http://dx.do.org/0.4236/cc.205.350 Cluster Analyss of Electrcal Behavor Ln Lu Ln Lu, School
Virtual Memory. Background. No. 10. Virtual Memory: concept. Logical Memory Space (review) Demand Paging(1) Virtual Memory
 Background EECS. Operatng System Fundamentals No. Vrtual Memory Prof. Hu Jang Department of Electrcal Engneerng and Computer Scence, York Unversty Memory-management methods normally requres the entre process
Background EECS. Operatng System Fundamentals No. Vrtual Memory Prof. Hu Jang Department of Electrcal Engneerng and Computer Scence, York Unversty Memory-management methods normally requres the entre process
BioTechnology. An Indian Journal FULL PAPER. Trade Science Inc.
 [Type text] [Type text] [Type text] ISSN : 0974-74 Volume 0 Issue BoTechnology 04 An Indan Journal FULL PAPER BTAIJ 0() 04 [684-689] Revew on Chna s sports ndustry fnancng market based on market -orented
[Type text] [Type text] [Type text] ISSN : 0974-74 Volume 0 Issue BoTechnology 04 An Indan Journal FULL PAPER BTAIJ 0() 04 [684-689] Revew on Chna s sports ndustry fnancng market based on market -orented
Simulation Based Analysis of FAST TCP using OMNET++
 Smulaton Based Analyss of FAST TCP usng OMNET++ Umar ul Hassan 04030038@lums.edu.pk Md Term Report CS678 Topcs n Internet Research Sprng, 2006 Introducton Internet traffc s doublng roughly every 3 months
Smulaton Based Analyss of FAST TCP usng OMNET++ Umar ul Hassan 04030038@lums.edu.pk Md Term Report CS678 Topcs n Internet Research Sprng, 2006 Introducton Internet traffc s doublng roughly every 3 months
User Authentication Based On Behavioral Mouse Dynamics Biometrics
 User Authentcaton Based On Behavoral Mouse Dynamcs Bometrcs Chee-Hyung Yoon Danel Donghyun Km Department of Computer Scence Department of Computer Scence Stanford Unversty Stanford Unversty Stanford, CA
User Authentcaton Based On Behavoral Mouse Dynamcs Bometrcs Chee-Hyung Yoon Danel Donghyun Km Department of Computer Scence Department of Computer Scence Stanford Unversty Stanford Unversty Stanford, CA
Term Weighting Classification System Using the Chi-square Statistic for the Classification Subtask at NTCIR-6 Patent Retrieval Task
 Proceedngs of NTCIR-6 Workshop Meetng, May 15-18, 2007, Tokyo, Japan Term Weghtng Classfcaton System Usng the Ch-square Statstc for the Classfcaton Subtask at NTCIR-6 Patent Retreval Task Kotaro Hashmoto
Proceedngs of NTCIR-6 Workshop Meetng, May 15-18, 2007, Tokyo, Japan Term Weghtng Classfcaton System Usng the Ch-square Statstc for the Classfcaton Subtask at NTCIR-6 Patent Retreval Task Kotaro Hashmoto
3D vector computer graphics
 3D vector computer graphcs Paolo Varagnolo: freelance engneer Padova Aprl 2016 Prvate Practce ----------------------------------- 1. Introducton Vector 3D model representaton n computer graphcs requres
3D vector computer graphcs Paolo Varagnolo: freelance engneer Padova Aprl 2016 Prvate Practce ----------------------------------- 1. Introducton Vector 3D model representaton n computer graphcs requres
Analysis of Continuous Beams in General
 Analyss of Contnuous Beams n General Contnuous beams consdered here are prsmatc, rgdly connected to each beam segment and supported at varous ponts along the beam. onts are selected at ponts of support,
Analyss of Contnuous Beams n General Contnuous beams consdered here are prsmatc, rgdly connected to each beam segment and supported at varous ponts along the beam. onts are selected at ponts of support,
A MOVING MESH APPROACH FOR SIMULATION BUDGET ALLOCATION ON CONTINUOUS DOMAINS
 Proceedngs of the Wnter Smulaton Conference M E Kuhl, N M Steger, F B Armstrong, and J A Jones, eds A MOVING MESH APPROACH FOR SIMULATION BUDGET ALLOCATION ON CONTINUOUS DOMAINS Mark W Brantley Chun-Hung
Proceedngs of the Wnter Smulaton Conference M E Kuhl, N M Steger, F B Armstrong, and J A Jones, eds A MOVING MESH APPROACH FOR SIMULATION BUDGET ALLOCATION ON CONTINUOUS DOMAINS Mark W Brantley Chun-Hung
OPTIMAL CONFIGURATION FOR NODES IN MIXED CELLULAR AND MOBILE AD HOC NETWORK FOR INET
 OPTIMAL CONFIGURATION FOR NODE IN MIED CELLULAR AND MOBILE AD HOC NETWORK FOR INET Olusola Babalola D.E. Department of Electrcal and Computer Engneerng Morgan tate Unversty Dr. Rchard Dean Faculty Advsor
OPTIMAL CONFIGURATION FOR NODE IN MIED CELLULAR AND MOBILE AD HOC NETWORK FOR INET Olusola Babalola D.E. Department of Electrcal and Computer Engneerng Morgan tate Unversty Dr. Rchard Dean Faculty Advsor
R s s f. m y s. SPH3UW Unit 7.3 Spherical Concave Mirrors Page 1 of 12. Notes
 SPH3UW Unt 7.3 Sphercal Concave Mrrors Page 1 of 1 Notes Physcs Tool box Concave Mrror If the reflectng surface takes place on the nner surface of the sphercal shape so that the centre of the mrror bulges
SPH3UW Unt 7.3 Sphercal Concave Mrrors Page 1 of 1 Notes Physcs Tool box Concave Mrror If the reflectng surface takes place on the nner surface of the sphercal shape so that the centre of the mrror bulges
IP mobility support is becoming very important as the
 706 IEEE TRANSACTIONS ON COMPUTERS, VOL. 52, NO. 6, JUNE 2003 A New Scheme for Reducng Lnk and Sgnalng Costs n Moble IP Young J. Lee and Ian F. Akyldz, Fellow, IEEE Abstract IP moblty support s provded
706 IEEE TRANSACTIONS ON COMPUTERS, VOL. 52, NO. 6, JUNE 2003 A New Scheme for Reducng Lnk and Sgnalng Costs n Moble IP Young J. Lee and Ian F. Akyldz, Fellow, IEEE Abstract IP moblty support s provded
An Optimal Algorithm for Prufer Codes *
 J. Software Engneerng & Applcatons, 2009, 2: 111-115 do:10.4236/jsea.2009.22016 Publshed Onlne July 2009 (www.scrp.org/journal/jsea) An Optmal Algorthm for Prufer Codes * Xaodong Wang 1, 2, Le Wang 3,
J. Software Engneerng & Applcatons, 2009, 2: 111-115 do:10.4236/jsea.2009.22016 Publshed Onlne July 2009 (www.scrp.org/journal/jsea) An Optmal Algorthm for Prufer Codes * Xaodong Wang 1, 2, Le Wang 3,
Efficient Distributed File System (EDFS)
 Effcent Dstrbuted Fle System (EDFS) (Sem-Centralzed) Debessay(Debsh) Fesehaye, Rahul Malk & Klara Naherstedt Unversty of Illnos-Urbana Champagn Contents Problem Statement, Related Work, EDFS Desgn Rate
Effcent Dstrbuted Fle System (EDFS) (Sem-Centralzed) Debessay(Debsh) Fesehaye, Rahul Malk & Klara Naherstedt Unversty of Illnos-Urbana Champagn Contents Problem Statement, Related Work, EDFS Desgn Rate
Compiler Design. Spring Register Allocation. Sample Exercises and Solutions. Prof. Pedro C. Diniz
 Compler Desgn Sprng 2014 Regster Allocaton Sample Exercses and Solutons Prof. Pedro C. Dnz USC / Informaton Scences Insttute 4676 Admralty Way, Sute 1001 Marna del Rey, Calforna 90292 pedro@s.edu Regster
Compler Desgn Sprng 2014 Regster Allocaton Sample Exercses and Solutons Prof. Pedro C. Dnz USC / Informaton Scences Insttute 4676 Admralty Way, Sute 1001 Marna del Rey, Calforna 90292 pedro@s.edu Regster
DEAR: A DEVICE AND ENERGY AWARE ROUTING PROTOCOL FOR MOBILE AD HOC NETWORKS
 DEAR: A DEVICE AND ENERGY AWARE ROUTING PROTOCOL FOR MOBILE AD HOC NETWORKS Arun Avudanayagam Yuguang Fang Wenjng Lou Department of Electrcal and Computer Engneerng Unversty of Florda Ganesvlle, FL 3261
DEAR: A DEVICE AND ENERGY AWARE ROUTING PROTOCOL FOR MOBILE AD HOC NETWORKS Arun Avudanayagam Yuguang Fang Wenjng Lou Department of Electrcal and Computer Engneerng Unversty of Florda Ganesvlle, FL 3261
Helsinki University Of Technology, Systems Analysis Laboratory Mat Independent research projects in applied mathematics (3 cr)
 Helsnk Unversty Of Technology, Systems Analyss Laboratory Mat-2.08 Independent research projects n appled mathematcs (3 cr) "! #$&% Antt Laukkanen 506 R ajlaukka@cc.hut.f 2 Introducton...3 2 Multattrbute
Helsnk Unversty Of Technology, Systems Analyss Laboratory Mat-2.08 Independent research projects n appled mathematcs (3 cr) "! #$&% Antt Laukkanen 506 R ajlaukka@cc.hut.f 2 Introducton...3 2 Multattrbute
S1 Note. Basis functions.
 S1 Note. Bass functons. Contents Types of bass functons...1 The Fourer bass...2 B-splne bass...3 Power and type I error rates wth dfferent numbers of bass functons...4 Table S1. Smulaton results of type
S1 Note. Bass functons. Contents Types of bass functons...1 The Fourer bass...2 B-splne bass...3 Power and type I error rates wth dfferent numbers of bass functons...4 Table S1. Smulaton results of type
A mathematical programming approach to the analysis, design and scheduling of offshore oilfields
 17 th European Symposum on Computer Aded Process Engneerng ESCAPE17 V. Plesu and P.S. Agach (Edtors) 2007 Elsever B.V. All rghts reserved. 1 A mathematcal programmng approach to the analyss, desgn and
17 th European Symposum on Computer Aded Process Engneerng ESCAPE17 V. Plesu and P.S. Agach (Edtors) 2007 Elsever B.V. All rghts reserved. 1 A mathematcal programmng approach to the analyss, desgn and
On Some Entertaining Applications of the Concept of Set in Computer Science Course
 On Some Entertanng Applcatons of the Concept of Set n Computer Scence Course Krasmr Yordzhev *, Hrstna Kostadnova ** * Assocate Professor Krasmr Yordzhev, Ph.D., Faculty of Mathematcs and Natural Scences,
On Some Entertanng Applcatons of the Concept of Set n Computer Scence Course Krasmr Yordzhev *, Hrstna Kostadnova ** * Assocate Professor Krasmr Yordzhev, Ph.D., Faculty of Mathematcs and Natural Scences,
VRT012 User s guide V0.1. Address: Žirmūnų g. 27, Vilnius LT-09105, Phone: (370-5) , Fax: (370-5) ,
 VRT012 User s gude V0.1 Thank you for purchasng our product. We hope ths user-frendly devce wll be helpful n realsng your deas and brngng comfort to your lfe. Please take few mnutes to read ths manual
VRT012 User s gude V0.1 Thank you for purchasng our product. We hope ths user-frendly devce wll be helpful n realsng your deas and brngng comfort to your lfe. Please take few mnutes to read ths manual
Constructing Minimum Connected Dominating Set: Algorithmic approach
 Constructng Mnmum Connected Domnatng Set: Algorthmc approach G.N. Puroht and Usha Sharma Centre for Mathematcal Scences, Banasthal Unversty, Rajasthan 304022 usha.sharma94@yahoo.com Abstract: Connected
Constructng Mnmum Connected Domnatng Set: Algorthmc approach G.N. Puroht and Usha Sharma Centre for Mathematcal Scences, Banasthal Unversty, Rajasthan 304022 usha.sharma94@yahoo.com Abstract: Connected
CMPS 10 Introduction to Computer Science Lecture Notes
 CPS 0 Introducton to Computer Scence Lecture Notes Chapter : Algorthm Desgn How should we present algorthms? Natural languages lke Englsh, Spansh, or French whch are rch n nterpretaton and meanng are not
CPS 0 Introducton to Computer Scence Lecture Notes Chapter : Algorthm Desgn How should we present algorthms? Natural languages lke Englsh, Spansh, or French whch are rch n nterpretaton and meanng are not
Mathematics 256 a course in differential equations for engineering students
 Mathematcs 56 a course n dfferental equatons for engneerng students Chapter 5. More effcent methods of numercal soluton Euler s method s qute neffcent. Because the error s essentally proportonal to the
Mathematcs 56 a course n dfferental equatons for engneerng students Chapter 5. More effcent methods of numercal soluton Euler s method s qute neffcent. Because the error s essentally proportonal to the
A New Transaction Processing Model Based on Optimistic Concurrency Control
 A New Transacton Processng Model Based on Optmstc Concurrency Control Wang Pedong,Duan Xpng,Jr. Abstract-- In ths paper, to support moblty and dsconnecton of moble clents effectvely n moble computng envronment,
A New Transacton Processng Model Based on Optmstc Concurrency Control Wang Pedong,Duan Xpng,Jr. Abstract-- In ths paper, to support moblty and dsconnecton of moble clents effectvely n moble computng envronment,
Related-Mode Attacks on CTR Encryption Mode
 Internatonal Journal of Network Securty, Vol.4, No.3, PP.282 287, May 2007 282 Related-Mode Attacks on CTR Encrypton Mode Dayn Wang, Dongda Ln, and Wenlng Wu (Correspondng author: Dayn Wang) Key Laboratory
Internatonal Journal of Network Securty, Vol.4, No.3, PP.282 287, May 2007 282 Related-Mode Attacks on CTR Encrypton Mode Dayn Wang, Dongda Ln, and Wenlng Wu (Correspondng author: Dayn Wang) Key Laboratory
Complex Numbers. Now we also saw that if a and b were both positive then ab = a b. For a second let s forget that restriction and do the following.
 Complex Numbers The last topc n ths secton s not really related to most of what we ve done n ths chapter, although t s somewhat related to the radcals secton as we wll see. We also won t need the materal
Complex Numbers The last topc n ths secton s not really related to most of what we ve done n ths chapter, although t s somewhat related to the radcals secton as we wll see. We also won t need the materal
A KIND OF ROUTING MODEL IN PEER-TO-PEER NETWORK BASED ON SUCCESSFUL ACCESSING RATE
 A KIND OF ROUTING MODEL IN PEER-TO-PEER NETWORK BASED ON SUCCESSFUL ACCESSING RATE 1 TAO LIU, 2 JI-JUN XU 1 College of Informaton Scence and Technology, Zhengzhou Normal Unversty, Chna 2 School of Mathematcs
A KIND OF ROUTING MODEL IN PEER-TO-PEER NETWORK BASED ON SUCCESSFUL ACCESSING RATE 1 TAO LIU, 2 JI-JUN XU 1 College of Informaton Scence and Technology, Zhengzhou Normal Unversty, Chna 2 School of Mathematcs
RAP. Speed/RAP/CODA. Real-time Systems. Modeling the sensor networks. Real-time Systems. Modeling the sensor networks. Real-time systems:
 Speed/RAP/CODA Presented by Octav Chpara Real-tme Systems Many wreless sensor network applcatons requre real-tme support Survellance and trackng Border patrol Fre fghtng Real-tme systems: Hard real-tme:
Speed/RAP/CODA Presented by Octav Chpara Real-tme Systems Many wreless sensor network applcatons requre real-tme support Survellance and trackng Border patrol Fre fghtng Real-tme systems: Hard real-tme:
THE MAP MATCHING ALGORITHM OF GPS DATA WITH RELATIVELY LONG POLLING TIME INTERVALS
 THE MA MATCHING ALGORITHM OF GS DATA WITH RELATIVELY LONG OLLING TIME INTERVALS Jae-seok YANG Graduate Student Graduate School of Engneerng Seoul Natonal Unversty San56-, Shllm-dong, Gwanak-gu, Seoul,
THE MA MATCHING ALGORITHM OF GS DATA WITH RELATIVELY LONG OLLING TIME INTERVALS Jae-seok YANG Graduate Student Graduate School of Engneerng Seoul Natonal Unversty San56-, Shllm-dong, Gwanak-gu, Seoul,
ON SOME ENTERTAINING APPLICATIONS OF THE CONCEPT OF SET IN COMPUTER SCIENCE COURSE
 Yordzhev K., Kostadnova H. Інформаційні технології в освіті ON SOME ENTERTAINING APPLICATIONS OF THE CONCEPT OF SET IN COMPUTER SCIENCE COURSE Yordzhev K., Kostadnova H. Some aspects of programmng educaton
Yordzhev K., Kostadnova H. Інформаційні технології в освіті ON SOME ENTERTAINING APPLICATIONS OF THE CONCEPT OF SET IN COMPUTER SCIENCE COURSE Yordzhev K., Kostadnova H. Some aspects of programmng educaton
Real-time Motion Capture System Using One Video Camera Based on Color and Edge Distribution
 Real-tme Moton Capture System Usng One Vdeo Camera Based on Color and Edge Dstrbuton YOSHIAKI AKAZAWA, YOSHIHIRO OKADA, AND KOICHI NIIJIMA Graduate School of Informaton Scence and Electrcal Engneerng,
Real-tme Moton Capture System Usng One Vdeo Camera Based on Color and Edge Dstrbuton YOSHIAKI AKAZAWA, YOSHIHIRO OKADA, AND KOICHI NIIJIMA Graduate School of Informaton Scence and Electrcal Engneerng,
Optimal Distribution of Remotely-Subscribed Multicast Traffic within a Proxy Mobile IPv6 Domain by Using Explicit Multicast
 ptmal strbuton of Remotely-Subscrbed Multcast Traffc wthn a Proxy Moble v6 oman by Usng Explct Multcast us M. Contreras *, Carlos J. Bernardos * Core Networ Evoluton Telefónca I+ on Ramón de la Cruz, 82-84,
ptmal strbuton of Remotely-Subscrbed Multcast Traffc wthn a Proxy Moble v6 oman by Usng Explct Multcast us M. Contreras *, Carlos J. Bernardos * Core Networ Evoluton Telefónca I+ on Ramón de la Cruz, 82-84,
Load Balancing for Hex-Cell Interconnection Network
 Int. J. Communcatons, Network and System Scences,,, - Publshed Onlne Aprl n ScRes. http://www.scrp.org/journal/jcns http://dx.do.org/./jcns.. Load Balancng for Hex-Cell Interconnecton Network Saher Manaseer,
Int. J. Communcatons, Network and System Scences,,, - Publshed Onlne Aprl n ScRes. http://www.scrp.org/journal/jcns http://dx.do.org/./jcns.. Load Balancng for Hex-Cell Interconnecton Network Saher Manaseer,
Scheduling Remote Access to Scientific Instruments in Cyberinfrastructure for Education and Research
 Schedulng Remote Access to Scentfc Instruments n Cybernfrastructure for Educaton and Research Je Yn 1, Junwe Cao 2,3,*, Yuexuan Wang 4, Lanchen Lu 1,3 and Cheng Wu 1,3 1 Natonal CIMS Engneerng and Research
Schedulng Remote Access to Scentfc Instruments n Cybernfrastructure for Educaton and Research Je Yn 1, Junwe Cao 2,3,*, Yuexuan Wang 4, Lanchen Lu 1,3 and Cheng Wu 1,3 1 Natonal CIMS Engneerng and Research
A Fast Visual Tracking Algorithm Based on Circle Pixels Matching
 A Fast Vsual Trackng Algorthm Based on Crcle Pxels Matchng Zhqang Hou hou_zhq@sohu.com Chongzhao Han czhan@mal.xjtu.edu.cn Ln Zheng Abstract: A fast vsual trackng algorthm based on crcle pxels matchng
A Fast Vsual Trackng Algorthm Based on Crcle Pxels Matchng Zhqang Hou hou_zhq@sohu.com Chongzhao Han czhan@mal.xjtu.edu.cn Ln Zheng Abstract: A fast vsual trackng algorthm based on crcle pxels matchng
Assembler. Building a Modern Computer From First Principles.
 Assembler Buldng a Modern Computer From Frst Prncples www.nand2tetrs.org Elements of Computng Systems, Nsan & Schocken, MIT Press, www.nand2tetrs.org, Chapter 6: Assembler slde Where we are at: Human Thought
Assembler Buldng a Modern Computer From Frst Prncples www.nand2tetrs.org Elements of Computng Systems, Nsan & Schocken, MIT Press, www.nand2tetrs.org, Chapter 6: Assembler slde Where we are at: Human Thought
Analysis of Collaborative Distributed Admission Control in x Networks
 1 Analyss of Collaboratve Dstrbuted Admsson Control n 82.11x Networks Thnh Nguyen, Member, IEEE, Ken Nguyen, Member, IEEE, Lnha He, Member, IEEE, Abstract Wth the recent surge of wreless home networks,
1 Analyss of Collaboratve Dstrbuted Admsson Control n 82.11x Networks Thnh Nguyen, Member, IEEE, Ken Nguyen, Member, IEEE, Lnha He, Member, IEEE, Abstract Wth the recent surge of wreless home networks,
Tsinghua University at TAC 2009: Summarizing Multi-documents by Information Distance
 Tsnghua Unversty at TAC 2009: Summarzng Mult-documents by Informaton Dstance Chong Long, Mnle Huang, Xaoyan Zhu State Key Laboratory of Intellgent Technology and Systems, Tsnghua Natonal Laboratory for
Tsnghua Unversty at TAC 2009: Summarzng Mult-documents by Informaton Dstance Chong Long, Mnle Huang, Xaoyan Zhu State Key Laboratory of Intellgent Technology and Systems, Tsnghua Natonal Laboratory for
Performance Evaluation of Information Retrieval Systems
 Why System Evaluaton? Performance Evaluaton of Informaton Retreval Systems Many sldes n ths secton are adapted from Prof. Joydeep Ghosh (UT ECE) who n turn adapted them from Prof. Dk Lee (Unv. of Scence
Why System Evaluaton? Performance Evaluaton of Informaton Retreval Systems Many sldes n ths secton are adapted from Prof. Joydeep Ghosh (UT ECE) who n turn adapted them from Prof. Dk Lee (Unv. of Scence
Wightman. Mobility. Quick Reference Guide THIS SPACE INTENTIONALLY LEFT BLANK
 Wghtman Moblty Quck Reference Gude THIS SPACE INTENTIONALLY LEFT BLANK WIGHTMAN MOBILITY BASICS How to Set Up Your Vocemal 1. On your phone s dal screen, press and hold 1 to access your vocemal. If your
Wghtman Moblty Quck Reference Gude THIS SPACE INTENTIONALLY LEFT BLANK WIGHTMAN MOBILITY BASICS How to Set Up Your Vocemal 1. On your phone s dal screen, press and hold 1 to access your vocemal. If your
Learning-Based Top-N Selection Query Evaluation over Relational Databases
 Learnng-Based Top-N Selecton Query Evaluaton over Relatonal Databases Lang Zhu *, Wey Meng ** * School of Mathematcs and Computer Scence, Hebe Unversty, Baodng, Hebe 071002, Chna, zhu@mal.hbu.edu.cn **
Learnng-Based Top-N Selecton Query Evaluaton over Relatonal Databases Lang Zhu *, Wey Meng ** * School of Mathematcs and Computer Scence, Hebe Unversty, Baodng, Hebe 071002, Chna, zhu@mal.hbu.edu.cn **
Advanced Computer Networks
 Char of Network Archtectures and Servces Department of Informatcs Techncal Unversty of Munch Note: Durng the attendance check a stcker contanng a unque QR code wll be put on ths exam. Ths QR code contans
Char of Network Archtectures and Servces Department of Informatcs Techncal Unversty of Munch Note: Durng the attendance check a stcker contanng a unque QR code wll be put on ths exam. Ths QR code contans
Performance Improvement of Direct Diffusion Algorithm in Sensor Networks
 Mddle-East Journal of Scentfc Research 2 (): 566-574, 202 ISSN 990-9233 IDOSI Publcatons, 202 DOI: 0.5829/dos.mejsr.202.2..43 Performance Improvement of Drect Dffuson Algorthm n Sensor Networks Akbar Bemana
Mddle-East Journal of Scentfc Research 2 (): 566-574, 202 ISSN 990-9233 IDOSI Publcatons, 202 DOI: 0.5829/dos.mejsr.202.2..43 Performance Improvement of Drect Dffuson Algorthm n Sensor Networks Akbar Bemana
Module Management Tool in Software Development Organizations
 Journal of Computer Scence (5): 8-, 7 ISSN 59-66 7 Scence Publcatons Management Tool n Software Development Organzatons Ahmad A. Al-Rababah and Mohammad A. Al-Rababah Faculty of IT, Al-Ahlyyah Amman Unversty,
Journal of Computer Scence (5): 8-, 7 ISSN 59-66 7 Scence Publcatons Management Tool n Software Development Organzatons Ahmad A. Al-Rababah and Mohammad A. Al-Rababah Faculty of IT, Al-Ahlyyah Amman Unversty,
NUMERICAL SOLVING OPTIMAL CONTROL PROBLEMS BY THE METHOD OF VARIATIONS
 ARPN Journal of Engneerng and Appled Scences 006-017 Asan Research Publshng Network (ARPN). All rghts reserved. NUMERICAL SOLVING OPTIMAL CONTROL PROBLEMS BY THE METHOD OF VARIATIONS Igor Grgoryev, Svetlana
ARPN Journal of Engneerng and Appled Scences 006-017 Asan Research Publshng Network (ARPN). All rghts reserved. NUMERICAL SOLVING OPTIMAL CONTROL PROBLEMS BY THE METHOD OF VARIATIONS Igor Grgoryev, Svetlana
Report on On-line Graph Coloring
 2003 Fall Semester Comp 670K Onlne Algorthm Report on LO Yuet Me (00086365) cndylo@ust.hk Abstract Onlne algorthm deals wth data that has no future nformaton. Lots of examples demonstrate that onlne algorthm
2003 Fall Semester Comp 670K Onlne Algorthm Report on LO Yuet Me (00086365) cndylo@ust.hk Abstract Onlne algorthm deals wth data that has no future nformaton. Lots of examples demonstrate that onlne algorthm
kccvoip.com basic voip training NAT/PAT extract 2008
 kccvop.com basc vop tranng NAT/PAT extract 28 As we have seen n the prevous sldes, SIP and H2 both use addressng nsde ther packets to rely nformaton. Thnk of an envelope where we place the addresses of
kccvop.com basc vop tranng NAT/PAT extract 28 As we have seen n the prevous sldes, SIP and H2 both use addressng nsde ther packets to rely nformaton. Thnk of an envelope where we place the addresses of
Edge Detection in Noisy Images Using the Support Vector Machines
 Edge Detecton n Nosy Images Usng the Support Vector Machnes Hlaro Gómez-Moreno, Saturnno Maldonado-Bascón, Francsco López-Ferreras Sgnal Theory and Communcatons Department. Unversty of Alcalá Crta. Madrd-Barcelona
Edge Detecton n Nosy Images Usng the Support Vector Machnes Hlaro Gómez-Moreno, Saturnno Maldonado-Bascón, Francsco López-Ferreras Sgnal Theory and Communcatons Department. Unversty of Alcalá Crta. Madrd-Barcelona
Performance Comparison of a QoS Aware Routing Protocol for Wireless Sensor Networks
 Communcatons and Network, 2016, 8, 45-55 Publshed Onlne February 2016 n ScRes. http://www.scrp.org/journal/cn http://dx.do.org/10.4236/cn.2016.81006 Performance Comparson of a QoS Aware Routng Protocol
Communcatons and Network, 2016, 8, 45-55 Publshed Onlne February 2016 n ScRes. http://www.scrp.org/journal/cn http://dx.do.org/10.4236/cn.2016.81006 Performance Comparson of a QoS Aware Routng Protocol
Problem Definitions and Evaluation Criteria for Computational Expensive Optimization
 Problem efntons and Evaluaton Crtera for Computatonal Expensve Optmzaton B. Lu 1, Q. Chen and Q. Zhang 3, J. J. Lang 4, P. N. Suganthan, B. Y. Qu 6 1 epartment of Computng, Glyndwr Unversty, UK Faclty
Problem efntons and Evaluaton Crtera for Computatonal Expensve Optmzaton B. Lu 1, Q. Chen and Q. Zhang 3, J. J. Lang 4, P. N. Suganthan, B. Y. Qu 6 1 epartment of Computng, Glyndwr Unversty, UK Faclty
Subspace clustering. Clustering. Fundamental to all clustering techniques is the choice of distance measure between data points;
 Subspace clusterng Clusterng Fundamental to all clusterng technques s the choce of dstance measure between data ponts; D q ( ) ( ) 2 x x = x x, j k = 1 k jk Squared Eucldean dstance Assumpton: All features
Subspace clusterng Clusterng Fundamental to all clusterng technques s the choce of dstance measure between data ponts; D q ( ) ( ) 2 x x = x x, j k = 1 k jk Squared Eucldean dstance Assumpton: All features
A Traffic Aware Routing Protocol for Congestion Avoidance in Content-Centric Network
 , pp.69-80 http://dx.do.org/10.14257/jmue.2014.9.9.08 A Traffc Aware Routng Protocol for Congeston Avodance n Content-Centrc Network Jung-Jae Km 1, Mn-Woo Ryu 2*, S-Ho Cha 3 and Kuk-Hyun Cho 1 1 Dept.
, pp.69-80 http://dx.do.org/10.14257/jmue.2014.9.9.08 A Traffc Aware Routng Protocol for Congeston Avodance n Content-Centrc Network Jung-Jae Km 1, Mn-Woo Ryu 2*, S-Ho Cha 3 and Kuk-Hyun Cho 1 1 Dept.
Virtual Machine Migration based on Trust Measurement of Computer Node
 Appled Mechancs and Materals Onlne: 2014-04-04 ISSN: 1662-7482, Vols. 536-537, pp 678-682 do:10.4028/www.scentfc.net/amm.536-537.678 2014 Trans Tech Publcatons, Swtzerland Vrtual Machne Mgraton based on
Appled Mechancs and Materals Onlne: 2014-04-04 ISSN: 1662-7482, Vols. 536-537, pp 678-682 do:10.4028/www.scentfc.net/amm.536-537.678 2014 Trans Tech Publcatons, Swtzerland Vrtual Machne Mgraton based on
High-Boost Mesh Filtering for 3-D Shape Enhancement
 Hgh-Boost Mesh Flterng for 3-D Shape Enhancement Hrokazu Yagou Λ Alexander Belyaev y Damng We z Λ y z ; ; Shape Modelng Laboratory, Unversty of Azu, Azu-Wakamatsu 965-8580 Japan y Computer Graphcs Group,
Hgh-Boost Mesh Flterng for 3-D Shape Enhancement Hrokazu Yagou Λ Alexander Belyaev y Damng We z Λ y z ; ; Shape Modelng Laboratory, Unversty of Azu, Azu-Wakamatsu 965-8580 Japan y Computer Graphcs Group,
Brave New World Pseudocode Reference
 Brave New World Pseudocode Reference Pseudocode s a way to descrbe how to accomplsh tasks usng basc steps lke those a computer mght perform. In ths week s lab, you'll see how a form of pseudocode can be
Brave New World Pseudocode Reference Pseudocode s a way to descrbe how to accomplsh tasks usng basc steps lke those a computer mght perform. In ths week s lab, you'll see how a form of pseudocode can be
An Efficient Garbage Collection for Flash Memory-Based Virtual Memory Systems
 S. J and D. Shn: An Effcent Garbage Collecton for Flash Memory-Based Vrtual Memory Systems 2355 An Effcent Garbage Collecton for Flash Memory-Based Vrtual Memory Systems Seunggu J and Dongkun Shn, Member,
S. J and D. Shn: An Effcent Garbage Collecton for Flash Memory-Based Vrtual Memory Systems 2355 An Effcent Garbage Collecton for Flash Memory-Based Vrtual Memory Systems Seunggu J and Dongkun Shn, Member,
Wishing you all a Total Quality New Year!
 Total Qualty Management and Sx Sgma Post Graduate Program 214-15 Sesson 4 Vnay Kumar Kalakband Assstant Professor Operatons & Systems Area 1 Wshng you all a Total Qualty New Year! Hope you acheve Sx sgma
Total Qualty Management and Sx Sgma Post Graduate Program 214-15 Sesson 4 Vnay Kumar Kalakband Assstant Professor Operatons & Systems Area 1 Wshng you all a Total Qualty New Year! Hope you acheve Sx sgma
AADL : about scheduling analysis
 AADL : about schedulng analyss Schedulng analyss, what s t? Embedded real-tme crtcal systems have temporal constrants to meet (e.g. deadlne). Many systems are bult wth operatng systems provdng multtaskng
AADL : about schedulng analyss Schedulng analyss, what s t? Embedded real-tme crtcal systems have temporal constrants to meet (e.g. deadlne). Many systems are bult wth operatng systems provdng multtaskng
FEATURE EXTRACTION. Dr. K.Vijayarekha. Associate Dean School of Electrical and Electronics Engineering SASTRA University, Thanjavur
 FEATURE EXTRACTION Dr. K.Vjayarekha Assocate Dean School of Electrcal and Electroncs Engneerng SASTRA Unversty, Thanjavur613 41 Jont Intatve of IITs and IISc Funded by MHRD Page 1 of 8 Table of Contents
FEATURE EXTRACTION Dr. K.Vjayarekha Assocate Dean School of Electrcal and Electroncs Engneerng SASTRA Unversty, Thanjavur613 41 Jont Intatve of IITs and IISc Funded by MHRD Page 1 of 8 Table of Contents
Assignment # 2. Farrukh Jabeen Algorithms 510 Assignment #2 Due Date: June 15, 2009.
 Farrukh Jabeen Algorthms 51 Assgnment #2 Due Date: June 15, 29. Assgnment # 2 Chapter 3 Dscrete Fourer Transforms Implement the FFT for the DFT. Descrbed n sectons 3.1 and 3.2. Delverables: 1. Concse descrpton
Farrukh Jabeen Algorthms 51 Assgnment #2 Due Date: June 15, 29. Assgnment # 2 Chapter 3 Dscrete Fourer Transforms Implement the FFT for the DFT. Descrbed n sectons 3.1 and 3.2. Delverables: 1. Concse descrpton
IP Camera Configuration Software Instruction Manual
 IP Camera 9483 - Confguraton Software Instructon Manual VBD 612-4 (10.14) Dear Customer, Wth your purchase of ths IP Camera, you have chosen a qualty product manufactured by RADEMACHER. Thank you for the
IP Camera 9483 - Confguraton Software Instructon Manual VBD 612-4 (10.14) Dear Customer, Wth your purchase of ths IP Camera, you have chosen a qualty product manufactured by RADEMACHER. Thank you for the
Improvement of Spatial Resolution Using BlockMatching Based Motion Estimation and Frame. Integration
 Improvement of Spatal Resoluton Usng BlockMatchng Based Moton Estmaton and Frame Integraton Danya Suga and Takayuk Hamamoto Graduate School of Engneerng, Tokyo Unversty of Scence, 6-3-1, Nuku, Katsuska-ku,
Improvement of Spatal Resoluton Usng BlockMatchng Based Moton Estmaton and Frame Integraton Danya Suga and Takayuk Hamamoto Graduate School of Engneerng, Tokyo Unversty of Scence, 6-3-1, Nuku, Katsuska-ku,
Classifier Selection Based on Data Complexity Measures *
 Classfer Selecton Based on Data Complexty Measures * Edth Hernández-Reyes, J.A. Carrasco-Ochoa, and J.Fco. Martínez-Trndad Natonal Insttute for Astrophyscs, Optcs and Electroncs, Lus Enrque Erro No.1 Sta.
Classfer Selecton Based on Data Complexty Measures * Edth Hernández-Reyes, J.A. Carrasco-Ochoa, and J.Fco. Martínez-Trndad Natonal Insttute for Astrophyscs, Optcs and Electroncs, Lus Enrque Erro No.1 Sta.
Overview. Basic Setup [9] Motivation and Tasks. Modularization 2008/2/20 IMPROVED COVERAGE CONTROL USING ONLY LOCAL INFORMATION
![Overview. Basic Setup [9] Motivation and Tasks. Modularization 2008/2/20 IMPROVED COVERAGE CONTROL USING ONLY LOCAL INFORMATION Overview. Basic Setup [9] Motivation and Tasks. Modularization 2008/2/20 IMPROVED COVERAGE CONTROL USING ONLY LOCAL INFORMATION](/thumbs/89/100766536.jpg) Overvew 2 IMPROVED COVERAGE CONTROL USING ONLY LOCAL INFORMATION Introducton Mult- Smulator MASIM Theoretcal Work and Smulaton Results Concluson Jay Wagenpfel, Adran Trachte Motvaton and Tasks Basc Setup
Overvew 2 IMPROVED COVERAGE CONTROL USING ONLY LOCAL INFORMATION Introducton Mult- Smulator MASIM Theoretcal Work and Smulaton Results Concluson Jay Wagenpfel, Adran Trachte Motvaton and Tasks Basc Setup
X- Chart Using ANOM Approach
 ISSN 1684-8403 Journal of Statstcs Volume 17, 010, pp. 3-3 Abstract X- Chart Usng ANOM Approach Gullapall Chakravarth 1 and Chaluvad Venkateswara Rao Control lmts for ndvdual measurements (X) chart are
ISSN 1684-8403 Journal of Statstcs Volume 17, 010, pp. 3-3 Abstract X- Chart Usng ANOM Approach Gullapall Chakravarth 1 and Chaluvad Venkateswara Rao Control lmts for ndvdual measurements (X) chart are
MULTISPECTRAL IMAGES CLASSIFICATION BASED ON KLT AND ATR AUTOMATIC TARGET RECOGNITION
 MULTISPECTRAL IMAGES CLASSIFICATION BASED ON KLT AND ATR AUTOMATIC TARGET RECOGNITION Paulo Quntlano 1 & Antono Santa-Rosa 1 Federal Polce Department, Brasla, Brazl. E-mals: quntlano.pqs@dpf.gov.br and
MULTISPECTRAL IMAGES CLASSIFICATION BASED ON KLT AND ATR AUTOMATIC TARGET RECOGNITION Paulo Quntlano 1 & Antono Santa-Rosa 1 Federal Polce Department, Brasla, Brazl. E-mals: quntlano.pqs@dpf.gov.br and
A Hybrid Genetic Algorithm for Routing Optimization in IP Networks Utilizing Bandwidth and Delay Metrics
 A Hybrd Genetc Algorthm for Routng Optmzaton n IP Networks Utlzng Bandwdth and Delay Metrcs Anton Redl Insttute of Communcaton Networks, Munch Unversty of Technology, Arcsstr. 21, 80290 Munch, Germany
A Hybrd Genetc Algorthm for Routng Optmzaton n IP Networks Utlzng Bandwdth and Delay Metrcs Anton Redl Insttute of Communcaton Networks, Munch Unversty of Technology, Arcsstr. 21, 80290 Munch, Germany
A New Approach For the Ranking of Fuzzy Sets With Different Heights
 New pproach For the ankng of Fuzzy Sets Wth Dfferent Heghts Pushpnder Sngh School of Mathematcs Computer pplcatons Thapar Unversty, Patala-7 00 Inda pushpndersnl@gmalcom STCT ankng of fuzzy sets plays
New pproach For the ankng of Fuzzy Sets Wth Dfferent Heghts Pushpnder Sngh School of Mathematcs Computer pplcatons Thapar Unversty, Patala-7 00 Inda pushpndersnl@gmalcom STCT ankng of fuzzy sets plays
A Low-Overhead Routing Protocol for Ad Hoc Networks with selfish nodes
 A Low-Oerhead Routng Protocol for Ad Hoc Networks wth selfsh nodes Dongbn Wang 1, Xaofeng Wang 2, Xangzhan Yu 3, Kacheng Q 1, Zhbn Xa 1 1 School of Software Engneerng, Bejng Unersty of Posts and Telecommuncatons,100876,
A Low-Oerhead Routng Protocol for Ad Hoc Networks wth selfsh nodes Dongbn Wang 1, Xaofeng Wang 2, Xangzhan Yu 3, Kacheng Q 1, Zhbn Xa 1 1 School of Software Engneerng, Bejng Unersty of Posts and Telecommuncatons,100876,
SLAM Summer School 2006 Practical 2: SLAM using Monocular Vision
 SLAM Summer School 2006 Practcal 2: SLAM usng Monocular Vson Javer Cvera, Unversty of Zaragoza Andrew J. Davson, Imperal College London J.M.M Montel, Unversty of Zaragoza. josemar@unzar.es, jcvera@unzar.es,
SLAM Summer School 2006 Practcal 2: SLAM usng Monocular Vson Javer Cvera, Unversty of Zaragoza Andrew J. Davson, Imperal College London J.M.M Montel, Unversty of Zaragoza. josemar@unzar.es, jcvera@unzar.es,
Cell Count Method on a Network with SANET
 CSIS Dscusson Paper No.59 Cell Count Method on a Network wth SANET Atsuyuk Okabe* and Shno Shode** Center for Spatal Informaton Scence, Unversty of Tokyo 7-3-1, Hongo, Bunkyo-ku, Tokyo 113-8656, Japan
CSIS Dscusson Paper No.59 Cell Count Method on a Network wth SANET Atsuyuk Okabe* and Shno Shode** Center for Spatal Informaton Scence, Unversty of Tokyo 7-3-1, Hongo, Bunkyo-ku, Tokyo 113-8656, Japan
Wireless Sensor Network Localization Research
 Sensors & Transducers 014 by IFSA Publshng, S L http://wwwsensorsportalcom Wreless Sensor Network Localzaton Research Lang Xn School of Informaton Scence and Engneerng, Hunan Internatonal Economcs Unversty,
Sensors & Transducers 014 by IFSA Publshng, S L http://wwwsensorsportalcom Wreless Sensor Network Localzaton Research Lang Xn School of Informaton Scence and Engneerng, Hunan Internatonal Economcs Unversty,
Deadlock-Free Path-Based Fault-Tolerant Multicast Communications on 2-D Mesh Networks-on-Chip
 The CSI Journal on Computer Scence and Engneerng Vol. 6, No. 2 & 4 (b), 2008 Pages 36-45 Short Paper Deadlock-Free Path-Based Fault-Tolerant Multcast Communcatons on 2-D Mesh Networks-on-Chp Majed ValadBeg
The CSI Journal on Computer Scence and Engneerng Vol. 6, No. 2 & 4 (b), 2008 Pages 36-45 Short Paper Deadlock-Free Path-Based Fault-Tolerant Multcast Communcatons on 2-D Mesh Networks-on-Chp Majed ValadBeg
A fair buffer allocation scheme
 A far buffer allocaton scheme Juha Henanen and Kalev Klkk Telecom Fnland P.O. Box 228, SF-330 Tampere, Fnland E-mal: juha.henanen@tele.f Abstract An approprate servce for data traffc n ATM networks requres
A far buffer allocaton scheme Juha Henanen and Kalev Klkk Telecom Fnland P.O. Box 228, SF-330 Tampere, Fnland E-mal: juha.henanen@tele.f Abstract An approprate servce for data traffc n ATM networks requres
DESIGNING TRANSMISSION SCHEDULES FOR WIRELESS AD HOC NETWORKS TO MAXIMIZE NETWORK THROUGHPUT
 DESIGNING TRANSMISSION SCHEDULES FOR WIRELESS AD HOC NETWORKS TO MAXIMIZE NETWORK THROUGHPUT Bran J. Wolf, Joseph L. Hammond, and Harlan B. Russell Dept. of Electrcal and Computer Engneerng, Clemson Unversty,
DESIGNING TRANSMISSION SCHEDULES FOR WIRELESS AD HOC NETWORKS TO MAXIMIZE NETWORK THROUGHPUT Bran J. Wolf, Joseph L. Hammond, and Harlan B. Russell Dept. of Electrcal and Computer Engneerng, Clemson Unversty,
S.P.H. : A SOLUTION TO AVOID USING EROSION CRITERION?
 S.P.H. : A SOLUTION TO AVOID USING EROSION CRITERION? Célne GALLET ENSICA 1 place Emle Bloun 31056 TOULOUSE CEDEX e-mal :cgallet@ensca.fr Jean Luc LACOME DYNALIS Immeuble AEROPOLE - Bat 1 5, Avenue Albert
S.P.H. : A SOLUTION TO AVOID USING EROSION CRITERION? Célne GALLET ENSICA 1 place Emle Bloun 31056 TOULOUSE CEDEX e-mal :cgallet@ensca.fr Jean Luc LACOME DYNALIS Immeuble AEROPOLE - Bat 1 5, Avenue Albert
An Iterative Solution Approach to Process Plant Layout using Mixed Integer Optimisation
 17 th European Symposum on Computer Aded Process Engneerng ESCAPE17 V. Plesu and P.S. Agach (Edtors) 2007 Elsever B.V. All rghts reserved. 1 An Iteratve Soluton Approach to Process Plant Layout usng Mxed
17 th European Symposum on Computer Aded Process Engneerng ESCAPE17 V. Plesu and P.S. Agach (Edtors) 2007 Elsever B.V. All rghts reserved. 1 An Iteratve Soluton Approach to Process Plant Layout usng Mxed
Solving two-person zero-sum game by Matlab
 Appled Mechancs and Materals Onlne: 2011-02-02 ISSN: 1662-7482, Vols. 50-51, pp 262-265 do:10.4028/www.scentfc.net/amm.50-51.262 2011 Trans Tech Publcatons, Swtzerland Solvng two-person zero-sum game by
Appled Mechancs and Materals Onlne: 2011-02-02 ISSN: 1662-7482, Vols. 50-51, pp 262-265 do:10.4028/www.scentfc.net/amm.50-51.262 2011 Trans Tech Publcatons, Swtzerland Solvng two-person zero-sum game by
Parallel matrix-vector multiplication
 Appendx A Parallel matrx-vector multplcaton The reduced transton matrx of the three-dmensonal cage model for gel electrophoress, descrbed n secton 3.2, becomes excessvely large for polymer lengths more
Appendx A Parallel matrx-vector multplcaton The reduced transton matrx of the three-dmensonal cage model for gel electrophoress, descrbed n secton 3.2, becomes excessvely large for polymer lengths more
Notes on Organizing Java Code: Packages, Visibility, and Scope
 Notes on Organzng Java Code: Packages, Vsblty, and Scope CS 112 Wayne Snyder Java programmng n large measure s a process of defnng enttes (.e., packages, classes, methods, or felds) by name and then usng
Notes on Organzng Java Code: Packages, Vsblty, and Scope CS 112 Wayne Snyder Java programmng n large measure s a process of defnng enttes (.e., packages, classes, methods, or felds) by name and then usng
MODELING THE RELIABILITY OF INFORMATION MANAGEMENT SYSTEMS BASED ON MISSION SPECIFIC TOOLS SET SOFTWARE
 Knowledge Dynamcs MODELING THE ELIABILITY OF INFOMATION MANAGEMENT SYSTEMS BASED ON MISSION SPECIFIC TOOLS SET SOFTWAE Cezar VASILESCU Assocate Professor, egonal Department of Defense esources Management
Knowledge Dynamcs MODELING THE ELIABILITY OF INFOMATION MANAGEMENT SYSTEMS BASED ON MISSION SPECIFIC TOOLS SET SOFTWAE Cezar VASILESCU Assocate Professor, egonal Department of Defense esources Management
Optimal Fault-Tolerant Routing in Hypercubes Using Extended Safety Vectors
 Optmal Fault-Tolerant Routng n Hypercubes Usng Extended Safety Vectors Je Wu Department of Computer Scence and Engneerng Florda Atlantc Unversty Boca Raton, FL 3343 Feng Gao, Zhongcheng L, and Ynghua Mn
Optmal Fault-Tolerant Routng n Hypercubes Usng Extended Safety Vectors Je Wu Department of Computer Scence and Engneerng Florda Atlantc Unversty Boca Raton, FL 3343 Feng Gao, Zhongcheng L, and Ynghua Mn
News. Recap: While Loop Example. Reading. Recap: Do Loop Example. Recap: For Loop Example
 Unversty of Brtsh Columba CPSC, Intro to Computaton Jan-Apr Tamara Munzner News Assgnment correctons to ASCIIArtste.java posted defntely read WebCT bboards Arrays Lecture, Tue Feb based on sldes by Kurt
Unversty of Brtsh Columba CPSC, Intro to Computaton Jan-Apr Tamara Munzner News Assgnment correctons to ASCIIArtste.java posted defntely read WebCT bboards Arrays Lecture, Tue Feb based on sldes by Kurt
Solutions to Programming Assignment Five Interpolation and Numerical Differentiation
 College of Engneerng and Coputer Scence Mechancal Engneerng Departent Mechancal Engneerng 309 Nuercal Analyss of Engneerng Systes Sprng 04 Nuber: 537 Instructor: Larry Caretto Solutons to Prograng Assgnent
College of Engneerng and Coputer Scence Mechancal Engneerng Departent Mechancal Engneerng 309 Nuercal Analyss of Engneerng Systes Sprng 04 Nuber: 537 Instructor: Larry Caretto Solutons to Prograng Assgnent
Fault Detection in Rule-Based Software Systems
 Fault Detecton n Rule-Based Software Systems Dong Wang, Rubng Hao and Davd Lee Bell Labs Research Chna Bejng, Chna, 100080 {wangd, rbhao, leedavd}@lucent.com Abstract Motvated by packet flterng of frewall
Fault Detecton n Rule-Based Software Systems Dong Wang, Rubng Hao and Davd Lee Bell Labs Research Chna Bejng, Chna, 100080 {wangd, rbhao, leedavd}@lucent.com Abstract Motvated by packet flterng of frewall
MODULE DESIGN BASED ON INTERFACE INTEGRATION TO MAXIMIZE PRODUCT VARIETY AND MINIMIZE FAMILY COST
 INTERNATIONAL CONFERENCE ON ENGINEERING DESIGN, ICED 07 28-31 AUGUST 2007, CITE DES SCIENCES ET DE L'INDUSTRIE, PARIS, FRANCE MODULE DESIGN BASED ON INTERFACE INTEGRATION TO MAIMIZE PRODUCT VARIETY AND
INTERNATIONAL CONFERENCE ON ENGINEERING DESIGN, ICED 07 28-31 AUGUST 2007, CITE DES SCIENCES ET DE L'INDUSTRIE, PARIS, FRANCE MODULE DESIGN BASED ON INTERFACE INTEGRATION TO MAIMIZE PRODUCT VARIETY AND
The Greedy Method. Outline and Reading. Change Money Problem. Greedy Algorithms. Applications of the Greedy Strategy. The Greedy Method Technique
 //00 :0 AM Outlne and Readng The Greedy Method The Greedy Method Technque (secton.) Fractonal Knapsack Problem (secton..) Task Schedulng (secton..) Mnmum Spannng Trees (secton.) Change Money Problem Greedy
//00 :0 AM Outlne and Readng The Greedy Method The Greedy Method Technque (secton.) Fractonal Knapsack Problem (secton..) Task Schedulng (secton..) Mnmum Spannng Trees (secton.) Change Money Problem Greedy
Support Vector Machines
 /9/207 MIST.6060 Busness Intellgence and Data Mnng What are Support Vector Machnes? Support Vector Machnes Support Vector Machnes (SVMs) are supervsed learnng technques that analyze data and recognze patterns.
/9/207 MIST.6060 Busness Intellgence and Data Mnng What are Support Vector Machnes? Support Vector Machnes Support Vector Machnes (SVMs) are supervsed learnng technques that analyze data and recognze patterns.
TN348: Openlab Module - Colocalization
 TN348: Openlab Module - Colocalzaton Topc The Colocalzaton module provdes the faclty to vsualze and quantfy colocalzaton between pars of mages. The Colocalzaton wndow contans a prevew of the two mages
TN348: Openlab Module - Colocalzaton Topc The Colocalzaton module provdes the faclty to vsualze and quantfy colocalzaton between pars of mages. The Colocalzaton wndow contans a prevew of the two mages
Sample Solution. Advanced Computer Networks P 1 P 2 P 3 P 4 P 5. Module: IN2097 Date: Examiner: Prof. Dr.-Ing. Georg Carle Exam: Final exam
 Char of Network Archtectures and Servces Department of Informatcs Techncal Unversty of Munch Note: Durng the attendance check a stcker contanng a unque QR code wll be put on ths exam. Ths QR code contans
Char of Network Archtectures and Servces Department of Informatcs Techncal Unversty of Munch Note: Durng the attendance check a stcker contanng a unque QR code wll be put on ths exam. Ths QR code contans
Research of Dynamic Access to Cloud Database Based on Improved Pheromone Algorithm
 , pp.197-202 http://dx.do.org/10.14257/dta.2016.9.5.20 Research of Dynamc Access to Cloud Database Based on Improved Pheromone Algorthm Yongqang L 1 and Jn Pan 2 1 (Software Technology Vocatonal College,
, pp.197-202 http://dx.do.org/10.14257/dta.2016.9.5.20 Research of Dynamc Access to Cloud Database Based on Improved Pheromone Algorthm Yongqang L 1 and Jn Pan 2 1 (Software Technology Vocatonal College,
Conditional Speculative Decimal Addition*
 Condtonal Speculatve Decmal Addton Alvaro Vazquez and Elsardo Antelo Dep. of Electronc and Computer Engneerng Unv. of Santago de Compostela, Span Ths work was supported n part by Xunta de Galca under grant
Condtonal Speculatve Decmal Addton Alvaro Vazquez and Elsardo Antelo Dep. of Electronc and Computer Engneerng Unv. of Santago de Compostela, Span Ths work was supported n part by Xunta de Galca under grant
USING GRAPHING SKILLS
 Name: BOLOGY: Date: _ Class: USNG GRAPHNG SKLLS NTRODUCTON: Recorded data can be plotted on a graph. A graph s a pctoral representaton of nformaton recorded n a data table. t s used to show a relatonshp
Name: BOLOGY: Date: _ Class: USNG GRAPHNG SKLLS NTRODUCTON: Recorded data can be plotted on a graph. A graph s a pctoral representaton of nformaton recorded n a data table. t s used to show a relatonshp
3D Virtual Eyeglass Frames Modeling from Multiple Camera Image Data Based on the GFFD Deformation Method
 NICOGRAPH Internatonal 2012, pp. 114-119 3D Vrtual Eyeglass Frames Modelng from Multple Camera Image Data Based on the GFFD Deformaton Method Norak Tamura, Somsangouane Sngthemphone and Katsuhro Ktama
NICOGRAPH Internatonal 2012, pp. 114-119 3D Vrtual Eyeglass Frames Modelng from Multple Camera Image Data Based on the GFFD Deformaton Method Norak Tamura, Somsangouane Sngthemphone and Katsuhro Ktama
