RPKI-Based Origin Validation Lab RPKI Lab Creative Commons: Attribution & Share Alike
|
|
|
- Kristian Copeland
- 5 years ago
- Views:
Transcription
1 RPKI-Based Origin Validation Lab 1
2 Issuing Parties Relying Parties GUI altca Publication Protocol Trust Anchor Resource PKI RCynic Gatherer Pseudo IRR route: /16! descr: /16-16! origin: AS3130! notify: mnt-by: MAINT-RPKI! changed: ! source: RPKI! GUI Up Down JPNIC Publication Protocol SIA Pointers Resource PKI Validated Cache NOC Tools GUI Up Down IIJ Publication Protocol SIA Pointers Resource PKI Our Focus Today BGP Decision Process 2
3 Today Register Our Prefixes in CA Issue ROAs Using CA s Web Portal Configure Routers to get ROAs from Caches RPKI Lab Creative Commons: Attribution & Share Alike
4 Get Copy of This Preso So You Can Copy and Paste 4
5 Lab Overview GUI django RPKI Engine RCynic Gatherer Cache RPKI to Rtr Protocol BGP Decision Process Publication Protocol Repository Mgt RPKI Repo 5
6 Lab Environment ubu01 ubu02 ubu03 ubu04 ubu05 ubu16 Ubuntu/KVM Server in Ashburn GUI RPKI-Rtr Protocol AS65000 AS65001 RP - cache0.vmini CA - ca0.vmini Mac Mini running Ubuntu KVM 6
7 DynaMIPS on MacMini /8 RPKI Cache RPKI-Rtr Protocol AS Global Internet AS /16! /24! /24!! /24! AS3130 Seattle Dallas AS /16! /24! /24!! /24! 7
8 Student Routers r1 r16 default default vmini kvm host NATted / /24 b0 default IPTables NAT br0 etc ssh Tunnels /24 b1 default because BGP is often blocked by firewalls ca cache
9 Issuing Parties Relying Parties GUI altca Publication Protocol Trust Anchor Resource PKI RCynic Gatherer Pseudo IRR route: /16! descr: /16-16! origin: AS3130! notify: mnt-by: MAINT-RPKI! changed: ! source: RPKI! GUI Up Down JPNIC Publication Protocol SIA Pointers Resource PKI Validated Cache Our NOC Tools GUI Up Down IIJ Publication Protocol SIA Pointers Resource PKI Focus Today BGP Decision Process 9
10 Today Trust Anchor GUI altca Publication Protocol Resource PKI Up Down SIA Pointers GUI workshop Publication Protocol Resource PKI Up Down SIA Pointers GUI not used Publication Protocol Resource PKI 10
11 IP Address Allocation /16 ARIN Experimental Allocation /24 Instructors Play /24 labuser /24 labuser /24 labuser32 11
12 GUI Accounts UserID labuser01 labuser02 labuser03 labuser16 Password fnord fnord fnord fnord 12
13 labusernn fnord 13
14 The Dashboard 14
15 Create a ROA 15
16 What Will Happen? 16
17 Routers Use Your Own! (in production images from C&J) 16 DynaMIPS 7200s in Lab 17
18 Be Careful! Some Caches Have a LOT of ROAs Do Not Configure DynaMIPS to a Server With RIR TALs Because RIPE Data Has Thousands of ROAs dfw0, Has Full BGP Table if you want to crash DynaMIPS 18
19 In-Lab Router Accounts ssh password: fnord user: isplab password: lab-pw # enable password: lab-pw (N is your user number) 19
20 BGP Configuration rn#conf t Enter configuration commands, one per line. End with CNTL/Z. rn(config)#router bgp 651NN rn(config-router)#bgp rpki server tcp port \ refresh 60 rn(config-router)#end That s All 20
21 Cisco Adventure rn#show ip bgp rpki? servers Display RPKI cache server information table Display RPKI table entries 21
22 Check Server rn#show ip bgp rpki servers BGP SOVC neighbor is /43779 connected to port Flags 0, Refresh time is 600, Serial number is InQ has 0 messages, OutQ has 0 messages, formatted msg 345 Session IO flags 3, Session flags 4008 Neighbor Statistics: Nets Processed 624 Connection state is ESTAB, I/O status: 1, unread input bytes: 0 Connection is ECN Disabled Mininum incoming TTL 0, Outgoing TTL 255 Local host: , Local port: Foreign host: , Foreign port: Connection tableid (VRF): 0 22
23 Look at Table rn#show ip bgp rpki table 76 BGP sovc network entries using 6688 bytes of memory 78 BGP sovc record entries using 1560 bytes of memory Network Maxlen Origin-AS Source Neighbor / / / / / / / / / / / / / / / / / / / /
24 Look at BGP Table rn#sh ip bgp Network Next Hop Metric LocPrf Weight Path * i I i *> I i * I i *> V i * V i *> N i * N i *> N i * N i 24
25 Mis-Origination Caught RN#sh ip bgp NN.0/24 BGP routing table entry for /24, version 94 Paths: (2 available, best #2, table default) Advertised to update-groups: 1 Refresh Epoch from ( ) Origin IGP, localpref 100, valid, external path 6802D4DC RPKI State invalid Refresh Epoch from ( ) Origin IGP, localpref 100, valid, external, best path 6802D7C8 RPKI State valid 25
26 Fat-Finger Detected ROA show ip bgp / /16 AS65000 AS65001 AS 3130 Global Internet AS3130 AS /16! /16! Seattle Dallas 26
27 ROA Controls Validity ROA show ip bgp / /16 AS65000 AS65001 AS 4128 Global Internet AS3130 AS /16! /16! Seattle Dallas 27
28 Try Your Own /24 ROA show ip bgp /16 show ip bgp X.0/ /16 AS 4128 ROA AS65000 AS X.0/24 AS 3130 Global Internet AS3130 AS X.0/24! X.0/24! 28
29 Now You Know How to Prevent YouTube Incident-2 And Stay Out of The Newspapers 29
30 Please Do Try This At Home 30
RPKI-Based Origin Validation, Routers, & Caches
 RPKI-Based Origin Validation, Routers, & Caches RPKIWS / Berlin 2013.07.26 Randy Bush Rob Austein Michael Elkins Matthias Waehlisch
RPKI-Based Origin Validation, Routers, & Caches RPKIWS / Berlin 2013.07.26 Randy Bush Rob Austein Michael Elkins Matthias Waehlisch
BGP Origin Validation
 BGP Origin Validation ISP Workshops These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/) Last updated
BGP Origin Validation ISP Workshops These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/) Last updated
RPKI Workshop Routing Lab
 RPKI Workshop Routing Lab NANOG / Denver 2011.06.12 Randy Bush Michael Elkins Rob Austein Serpil Bayraktar 2011.06.12 RPKI Router Lab
RPKI Workshop Routing Lab NANOG / Denver 2011.06.12 Randy Bush Michael Elkins Rob Austein Serpil Bayraktar 2011.06.12 RPKI Router Lab
Resource PKI. NetSec Tutorial. NZNOG Queenstown. 24 Jan 2018
 Resource PKI NetSec Tutorial NZNOG2018 - Queenstown 24 Jan 2018 1 Fat-finger/Hijacks/Leaks Bharti (AS9498) originates 103.0.0.0/10 Dec 2017 (~ 2 days) No damage more than 8K specific routes! Google brings
Resource PKI NetSec Tutorial NZNOG2018 - Queenstown 24 Jan 2018 1 Fat-finger/Hijacks/Leaks Bharti (AS9498) originates 103.0.0.0/10 Dec 2017 (~ 2 days) No damage more than 8K specific routes! Google brings
Securing BGP - RPKI. ThaiNOG Bangkok. 21 May Tashi Phuntsho
 Securing BGP - RPKI ThaiNOG2018 - Bangkok 21 May 2018 Tashi Phuntsho (tashi@apnic.net) 1 Fat-finger/Hijacks/Leaks Amazon (AS16509) Route53 hijack April2018 AS10279 (enet) announced/originated more specifics
Securing BGP - RPKI ThaiNOG2018 - Bangkok 21 May 2018 Tashi Phuntsho (tashi@apnic.net) 1 Fat-finger/Hijacks/Leaks Amazon (AS16509) Route53 hijack April2018 AS10279 (enet) announced/originated more specifics
The RPKI and BGP Origin Validation
 The RPKI and BGP Origin Validation APRICOT / New Delhi 2012.02.27 Randy Bush Rob Austein Steve Bellovin And a cast of thousands! Well, dozens :) 2012.02.27
The RPKI and BGP Origin Validation APRICOT / New Delhi 2012.02.27 Randy Bush Rob Austein Steve Bellovin And a cast of thousands! Well, dozens :) 2012.02.27
The RPKI & Origin Validation
 The RPKI & Origin Validation RIPE / Praha 2010.05.03 Randy Bush Rob Austein Steve Bellovin And a cast of thousands! Well, dozens :) 2010.05.03 RIPE RPKI
The RPKI & Origin Validation RIPE / Praha 2010.05.03 Randy Bush Rob Austein Steve Bellovin And a cast of thousands! Well, dozens :) 2010.05.03 RIPE RPKI
Secure Routing with RPKI. APNIC44 Security Workshop
 Secure Routing with RPKI APNIC44 Security Workshop Misdirection / Hijacking Incidents YouTube Incident Occurred 24 Feb 2008 (for about 2 hours) Pakistan Telecom announced YT block Google (AS15169) services
Secure Routing with RPKI APNIC44 Security Workshop Misdirection / Hijacking Incidents YouTube Incident Occurred 24 Feb 2008 (for about 2 hours) Pakistan Telecom announced YT block Google (AS15169) services
RPKI. Resource Pubic Key Infrastructure
 RPKI Resource Pubic Key Infrastructure Purpose of RPKI RPKI replaces IRR or lives side by side? Side by side: different advantages Security, almost real time, simple interface: RPKI Purpose of RPKI Is
RPKI Resource Pubic Key Infrastructure Purpose of RPKI RPKI replaces IRR or lives side by side? Side by side: different advantages Security, almost real time, simple interface: RPKI Purpose of RPKI Is
Misdirection / Hijacking Incidents
 Security Tutorial @ TWNOG SECURE ROUTING WITH RPKI 1 Misdirection / Hijacking Incidents YouTube Incident Occurred 24 Feb 2008 (for about 2 hours) Pakistan Telecom announced YT block Google (AS15169) services
Security Tutorial @ TWNOG SECURE ROUTING WITH RPKI 1 Misdirection / Hijacking Incidents YouTube Incident Occurred 24 Feb 2008 (for about 2 hours) Pakistan Telecom announced YT block Google (AS15169) services
The RPKI & Origin Validation
 The RPKI & Origin Validation NANOG / Denver 2011.06.12 Randy Bush Rob Austein Steve Bellovin Michael Elkins And a cast of thousands!
The RPKI & Origin Validation NANOG / Denver 2011.06.12 Randy Bush Rob Austein Steve Bellovin Michael Elkins And a cast of thousands!
Deploying RPKI An Intro to the RPKI Infrastructure
 Deploying RPKI An Intro to the RPKI Infrastructure VNIX-NOG 24 November 2016 Hanoi, Vietnam Issue Date: Revision: Misdirection / Hijacking Incidents YouTube Incident Occurred 24 Feb 2008 (for about 2 hours)
Deploying RPKI An Intro to the RPKI Infrastructure VNIX-NOG 24 November 2016 Hanoi, Vietnam Issue Date: Revision: Misdirection / Hijacking Incidents YouTube Incident Occurred 24 Feb 2008 (for about 2 hours)
RPKI Introduction. APNIC Technical Workshop July 5-6, 2018 in Beijing, China. Hosted By:
 RPKI Introduction APNIC Technical Workshop July 5-6, 2018 in Beijing, China. Hosted By: 1 Content Why do we need RPKI What is RPKI How to deploy RPKI Configuration case Misdirection / Hijacking Incidents
RPKI Introduction APNIC Technical Workshop July 5-6, 2018 in Beijing, China. Hosted By: 1 Content Why do we need RPKI What is RPKI How to deploy RPKI Configuration case Misdirection / Hijacking Incidents
Resource Certification. Alex Band, Product Manager DENIC Technical Meeting
 Resource Certification Alex Band, Product Manager DENIC Technical Meeting Internet Routing Routing is non-hierarchical, open and free Freedom comes at a price: - You can announce any address block on your
Resource Certification Alex Band, Product Manager DENIC Technical Meeting Internet Routing Routing is non-hierarchical, open and free Freedom comes at a price: - You can announce any address block on your
Resource Public Key Infrastructure (RPKI) Nurul Islam Roman, APNIC
 Resource Public Key Infrastructure (RPKI) Nurul Islam Roman, APNIC Target Audience Knowledge of Internet Routing(specially BGP) Fair idea on Routing Policy No need to know Cryptography Basic knowledge
Resource Public Key Infrastructure (RPKI) Nurul Islam Roman, APNIC Target Audience Knowledge of Internet Routing(specially BGP) Fair idea on Routing Policy No need to know Cryptography Basic knowledge
Resource Public Key Infrastructure
 Resource Public Key Infrastructure A pilot for the Internet2 Community to secure the global route table Andrew Gallo The Basics The Internet is a self organizing network of networks. How do you find your
Resource Public Key Infrastructure A pilot for the Internet2 Community to secure the global route table Andrew Gallo The Basics The Internet is a self organizing network of networks. How do you find your
BGP AS-Override Split-Horizon
 The feature enables a Provider Edge (PE) device using split-horizon to avoid advertisement of routes propagated by a Customer Edge (CE) device to the same CE device. The BGP AS-Override Split-Horizon feature
The feature enables a Provider Edge (PE) device using split-horizon to avoid advertisement of routes propagated by a Customer Edge (CE) device to the same CE device. The BGP AS-Override Split-Horizon feature
Route Security for Inter-domain Routing
 Route Security for Inter-domain Routing Alvaro Retana (aretana@cisco.com) Distinguished Engineer, Cisco Services 3 This could happen to YOUR network 4 This could happen be happening to YOUR network 5 Agenda
Route Security for Inter-domain Routing Alvaro Retana (aretana@cisco.com) Distinguished Engineer, Cisco Services 3 This could happen to YOUR network 4 This could happen be happening to YOUR network 5 Agenda
BGP Origin AS Validation
 The feature helps prevent network administrators from inadvertently advertising routes to networks they do not control. This feature uses a Resource Public Key Infrastructure (RPKI) server to authenticate
The feature helps prevent network administrators from inadvertently advertising routes to networks they do not control. This feature uses a Resource Public Key Infrastructure (RPKI) server to authenticate
Configuring IPv6 Provider Edge over MPLS (6PE)
 Finding Feature Information, page 1 Configuring 6PE, page 1 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature
Finding Feature Information, page 1 Configuring 6PE, page 1 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature
RPKI and Internet Routing Security ~ The regional ISP operator view ~
 RPKI and Internet Routing Security ~ The regional ISP operator view ~ APNIC 29/APRICOT 2010 NEC BIGLOBE, Ltd. (AS2518) Seiichi Kawamura 1 Agenda Routing practices of the regional ISP today How this may
RPKI and Internet Routing Security ~ The regional ISP operator view ~ APNIC 29/APRICOT 2010 NEC BIGLOBE, Ltd. (AS2518) Seiichi Kawamura 1 Agenda Routing practices of the regional ISP today How this may
RPKI deployment at AFRINIC Status Update. Alain P. AINA RPKI Project Manager
 RPKI deployment at AFRINIC Status Update Alain P. AINA RPKI Project Manager What is Resource Certifcation? Resource Certifcation is a security framework for verifying the association between resource holders
RPKI deployment at AFRINIC Status Update Alain P. AINA RPKI Project Manager What is Resource Certifcation? Resource Certifcation is a security framework for verifying the association between resource holders
BGP FlowSpec Route-reflector Support
 The BGP (Border Gateway Protocol) Flowspec (Flow Specification) Route Reflector feature enables service providers to control traffic flows in their network. This helps in filtering traffic and helps in
The BGP (Border Gateway Protocol) Flowspec (Flow Specification) Route Reflector feature enables service providers to control traffic flows in their network. This helps in filtering traffic and helps in
Life After IPv4 Depletion
 1 Life After IPv4 Depletion Jon Worley Analyst Securing Core Internet Functions Resource Certification, RPKI Mark Kosters Chief Technology Officer 2 Core Internet Functions: Routing & DNS The Internet
1 Life After IPv4 Depletion Jon Worley Analyst Securing Core Internet Functions Resource Certification, RPKI Mark Kosters Chief Technology Officer 2 Core Internet Functions: Routing & DNS The Internet
Introduction to BGP. ISP Workshops. Last updated 30 October 2013
 Introduction to BGP ISP Workshops Last updated 30 October 2013 1 Border Gateway Protocol p A Routing Protocol used to exchange routing information between different networks n Exterior gateway protocol
Introduction to BGP ISP Workshops Last updated 30 October 2013 1 Border Gateway Protocol p A Routing Protocol used to exchange routing information between different networks n Exterior gateway protocol
Secure Inter-domain Routing with RPKI
 Secure Inter-domain Routing with RPKI Srinivas (Sunny) Chendi VNIX-NOG 2018, Da Nang sunny@apnic.net Xin chào và chào buổi sáng 1 3 4 What is the fundamental Problem? An underlying problem in routing
Secure Inter-domain Routing with RPKI Srinivas (Sunny) Chendi VNIX-NOG 2018, Da Nang sunny@apnic.net Xin chào và chào buổi sáng 1 3 4 What is the fundamental Problem? An underlying problem in routing
BGP Persistence. Restrictions for BGP Persistence. Information About BGP Persistence
 BGP persistence enables the router to retain routes that it has learnt from the configured neighbor even when the neighbor session is down. BGP persistence is also referred as long lived graceful restart
BGP persistence enables the router to retain routes that it has learnt from the configured neighbor even when the neighbor session is down. BGP persistence is also referred as long lived graceful restart
Idealized BGPsec: Formally Verifiable BGP
 Idealized BGPsec: Formally Verifiable BGP JaNOG 27.5 / Tokyo 2011.04.14 Randy Bush for the Informal BGPsec Design Group 2011.04.14 JaNOG BGPsec 1 Informal BGPsec Group chris morrow (google)
Idealized BGPsec: Formally Verifiable BGP JaNOG 27.5 / Tokyo 2011.04.14 Randy Bush for the Informal BGPsec Design Group 2011.04.14 JaNOG BGPsec 1 Informal BGPsec Group chris morrow (google)
 ISP 1 AS 1 Prefix P peer ISP 2 AS 2 Route leak (P) propagates Prefix P update Route update P Route leak (P) to upstream 2 AS 3 Customer BGP Update messages Route update A ISP A Prefix A ISP B B leaks
ISP 1 AS 1 Prefix P peer ISP 2 AS 2 Route leak (P) propagates Prefix P update Route update P Route leak (P) to upstream 2 AS 3 Customer BGP Update messages Route update A ISP A Prefix A ISP B B leaks
APNIC s role in stability and security. Adam Gosling Senior Policy Specialist, APNIC 4th APT Cybersecurity Forum, 3-5 December 2013
 APNIC s role in stability and security Adam Gosling Senior Policy Specialist, APNIC 4th APT Cybersecurity Forum, 3-5 December 2013 Overview Introducing APNIC Working with LEAs The APNIC Whois Database
APNIC s role in stability and security Adam Gosling Senior Policy Specialist, APNIC 4th APT Cybersecurity Forum, 3-5 December 2013 Overview Introducing APNIC Working with LEAs The APNIC Whois Database
Resource Certification
 Resource Certification CISSP, science group manager RIPE NCC robert@ripe.net 1 Contents Motivation for Resource Certification (RPKI) Architecture overview Participating in RPKI Most importantly: use cases
Resource Certification CISSP, science group manager RIPE NCC robert@ripe.net 1 Contents Motivation for Resource Certification (RPKI) Architecture overview Participating in RPKI Most importantly: use cases
Introducción al RPKI (Resource Public Key Infrastructure)
 Introducción al RPKI (Resource Public Key Infrastructure) Roque Gagliano rogaglia@cisco.com 4 Septiembre 2013 Quito, Equator 2011 Cisco and/or its affiliates. All rights reserved. 1 Review of problem to
Introducción al RPKI (Resource Public Key Infrastructure) Roque Gagliano rogaglia@cisco.com 4 Septiembre 2013 Quito, Equator 2011 Cisco and/or its affiliates. All rights reserved. 1 Review of problem to
IETF81 Secure IDR Rollup TREX Workshop David Freedman, Claranet
 IETF81 Secure IDR Rollup TREX Workshop 2011 David Freedman, Claranet Introduction to Secure IDR (SIDR) You are in a darkened room at the IETF. You are surrounded by vendors. A lone operator stands quietly
IETF81 Secure IDR Rollup TREX Workshop 2011 David Freedman, Claranet Introduction to Secure IDR (SIDR) You are in a darkened room at the IETF. You are surrounded by vendors. A lone operator stands quietly
Multiprotocol BGP Extensions for IP Multicast Commands
 Multiprotocol BGP Extensions for IP Multicast Commands Use the commands in this chapter to configure and monitor multiprotocol BGP. Multiprotocol BGP is based on RFC 2283, Multiprotocol Extensions for
Multiprotocol BGP Extensions for IP Multicast Commands Use the commands in this chapter to configure and monitor multiprotocol BGP. Multiprotocol BGP is based on RFC 2283, Multiprotocol Extensions for
APNIC elearning: BGP Basics. 30 September :00 PM AEST Brisbane (UTC+10) Revision: 2.0
 APNIC elearning: BGP Basics 30 September 2015 1:00 PM AEST Brisbane (UTC+10) Issue Date: 07 July 2015 Revision: 2.0 Presenter Nurul Islam (Roman) Senior Training Specialist, APNIC Nurul maintains the APNIC
APNIC elearning: BGP Basics 30 September 2015 1:00 PM AEST Brisbane (UTC+10) Issue Date: 07 July 2015 Revision: 2.0 Presenter Nurul Islam (Roman) Senior Training Specialist, APNIC Nurul maintains the APNIC
RPKI in practice. Sebastian Wiesinger DE-CIX Technical Meeting June 2017
 RPKI in practice Sebastian Wiesinger sebastian.wiesinger@noris.net DE-CIX Technical Meeting June 2017 Generate ROAs Generate ROAs for your prefixes RIPE NCC makes this very easy Available at the LIR portal
RPKI in practice Sebastian Wiesinger sebastian.wiesinger@noris.net DE-CIX Technical Meeting June 2017 Generate ROAs Generate ROAs for your prefixes RIPE NCC makes this very easy Available at the LIR portal
Contents. Introduction. Prerequisites. Configure. Requirements. Components Used
 Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations CE1 CE2 PE1 PE2 Verify Case 1: Accepting and exchanging customer routes over MP-BGP Case 2: Leaking
Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations CE1 CE2 PE1 PE2 Verify Case 1: Accepting and exchanging customer routes over MP-BGP Case 2: Leaking
Implementation of RPKI and IRR filtering on the AMS-IX platform. Stavros Konstantaras NOC Engineer
 Implementation of RPKI and IRR filtering on the AMS-IX platform Stavros Konstantaras NOC Engineer RIPE EDUCA 2018 Agenda AMS-IX Route Servers Architecture Features Filtering IRRdb RPKI BGP Communities
Implementation of RPKI and IRR filtering on the AMS-IX platform Stavros Konstantaras NOC Engineer RIPE EDUCA 2018 Agenda AMS-IX Route Servers Architecture Features Filtering IRRdb RPKI BGP Communities
BGP Policy Lab - Partial Routing
 2016/09/08 10:01 1/6 BGP Policy Lab - Partial Routing BGP Policy Lab - Partial Routing Introduction The purpose of this exercise is to: Apply the concepts of BGP policy learned in class to achieve the
2016/09/08 10:01 1/6 BGP Policy Lab - Partial Routing BGP Policy Lab - Partial Routing Introduction The purpose of this exercise is to: Apply the concepts of BGP policy learned in class to achieve the
Just give me a button!
 Just give me a button! The challenges of routing security RIPE NCC Members organisation founded in 1992 Manages IP and ASN allocations in Europe, Middle East and former Soviet Union - Ensure unique holdership
Just give me a button! The challenges of routing security RIPE NCC Members organisation founded in 1992 Manages IP and ASN allocations in Europe, Middle East and former Soviet Union - Ensure unique holdership
Overview of the Resource PKI (RPKI) Dr. Stephen Kent VP & Chief Scientist BBN Technologies
 Overview of the Resource PKI (RPKI) Dr. Stephen Kent VP & Chief Scientist BBN Technologies Presentation Outline The BGP security problem RPKI overiew Address & AS number allocation system Certificates
Overview of the Resource PKI (RPKI) Dr. Stephen Kent VP & Chief Scientist BBN Technologies Presentation Outline The BGP security problem RPKI overiew Address & AS number allocation system Certificates
Chapter 5: Maintaining and Troubleshooting Routing Solutions
 Chapter 5: Maintaining and Troubleshooting Routing Solutions CCNP TSHOOT: Maintaining and Troubleshooting IP Networks Course v6 1 Troubleshooting Network Layer Connectivity 2 Routing and Routing Data Structures
Chapter 5: Maintaining and Troubleshooting Routing Solutions CCNP TSHOOT: Maintaining and Troubleshooting IP Networks Course v6 1 Troubleshooting Network Layer Connectivity 2 Routing and Routing Data Structures
Security in inter-domain routing
 DD2491 p2 2011 Security in inter-domain routing Olof Hagsand KTH CSC 1 Literature Practical BGP pages Chapter 9 See reading instructions Beware of BGP Attacks (Nordström, Dovrolis) Examples of attacks
DD2491 p2 2011 Security in inter-domain routing Olof Hagsand KTH CSC 1 Literature Practical BGP pages Chapter 9 See reading instructions Beware of BGP Attacks (Nordström, Dovrolis) Examples of attacks
RPKI Deployment Considerations: Problem Analysis and Alternative Solutions. 95 SIDR meeting
 RPKI Deployment Considerations: Problem Analysis and Alternative Solutions draft-lee-sidr-rpki-deployment-01 @IETF 95 SIDR meeting fuyu@cnnic.cn Background RPKI in China CNNIC deploy a platform to provide
RPKI Deployment Considerations: Problem Analysis and Alternative Solutions draft-lee-sidr-rpki-deployment-01 @IETF 95 SIDR meeting fuyu@cnnic.cn Background RPKI in China CNNIC deploy a platform to provide
Securing Core Internet Functions Resource Certification, RPKI. Mark Kosters ARIN CTO
 Securing Core Internet Functions Resource Certification, RPKI Mark Kosters ARIN CTO Core Internet Functions: Routing & DNS The Internet relies on two critical resources DNS: Translates domain names to
Securing Core Internet Functions Resource Certification, RPKI Mark Kosters ARIN CTO Core Internet Functions: Routing & DNS The Internet relies on two critical resources DNS: Translates domain names to
BGP Table Version. Contents. Introduction. Network Diagram. Best Path
 BGP Table Version Document ID: 116511 Contributed by Luc De Ghein, Cisco TAC Engineer. Sep 30, 2013 Contents Introduction Network Diagram Best Path Types of Table Versions Initial Table Version Number
BGP Table Version Document ID: 116511 Contributed by Luc De Ghein, Cisco TAC Engineer. Sep 30, 2013 Contents Introduction Network Diagram Best Path Types of Table Versions Initial Table Version Number
BGP Support for 4-byte ASN
 The Cisco implementation of 4-byte autonomous system (AS) numbers uses asplain (65538, for example) as the default regular expression match and the output display format for AS numbers. However, you can
The Cisco implementation of 4-byte autonomous system (AS) numbers uses asplain (65538, for example) as the default regular expression match and the output display format for AS numbers. However, you can
RPKI and Routing Security
 Presentation September 2015 Yerevan Regional Meeting Routing Security 2 Routing Registry route objects RPKI (Resource Public Key Infrastructure) ROAs (Route Origin Authorisation) What is the Purpose of
Presentation September 2015 Yerevan Regional Meeting Routing Security 2 Routing Registry route objects RPKI (Resource Public Key Infrastructure) ROAs (Route Origin Authorisation) What is the Purpose of
Module 6 Implementing BGP
 Module 6 Implementing BGP Lesson 1 Explaining BGP Concepts and Terminology BGP Border Gateway Protocol Using BGP to Connect to the Internet If only one ISP, do not need BGP. If multiple ISPs, use BGP,
Module 6 Implementing BGP Lesson 1 Explaining BGP Concepts and Terminology BGP Border Gateway Protocol Using BGP to Connect to the Internet If only one ISP, do not need BGP. If multiple ISPs, use BGP,
Update on Resource Certification. Geoff Huston, APNIC Mark Kosters, ARIN IEPG, March 2008
 Update on Resource Certification Geoff Huston, APNIC Mark Kosters, ARIN IEPG, March 2008 Address and Routing Security What we have had for many years is a relatively insecure interdomain routing system
Update on Resource Certification Geoff Huston, APNIC Mark Kosters, ARIN IEPG, March 2008 Address and Routing Security What we have had for many years is a relatively insecure interdomain routing system
Configuring a Basic BGP Network
 Configuring a Basic BGP Network This module describes the basic tasks to configure a basic Border Gateway Protocol (BGP) network. BGP is an interdomain routing protocol that is designed to provide loop-free
Configuring a Basic BGP Network This module describes the basic tasks to configure a basic Border Gateway Protocol (BGP) network. BGP is an interdomain routing protocol that is designed to provide loop-free
ibgp Multipath Load Sharing
 ibgp Multipath Load haring Feature History Release 12.2(2)T 12.2(14) Modification This feature was introduced. This feature was integrated into. This feature module describes the ibgp Multipath Load haring
ibgp Multipath Load haring Feature History Release 12.2(2)T 12.2(14) Modification This feature was introduced. This feature was integrated into. This feature module describes the ibgp Multipath Load haring
MPLS VPN Inter-AS Option AB
 First Published: December 17, 2007 Last Updated: September 21, 2011 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol
First Published: December 17, 2007 Last Updated: September 21, 2011 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol
ARIN Support for DNSSEC and RPKI. ION San Diego 11 December 2012 Pete Toscano, ARIN
 ARIN Support for DNSSEC and ION San Diego 11 December 2012 Pete Toscano, ARIN 2 DNS and BGP They have been around for a long time. DNS: 1982 BGP: 1989 They are not very secure. Methods for securing them
ARIN Support for DNSSEC and ION San Diego 11 December 2012 Pete Toscano, ARIN 2 DNS and BGP They have been around for a long time. DNS: 1982 BGP: 1989 They are not very secure. Methods for securing them
32-bit ASNs. Philip Smith. AfNOG rd April 1st May Abuja, Nigeria
 32-bit ASNs Philip Smith AfNOG 2007 23rd April 1st May Abuja, Nigeria Autonomous System (AS) AS 100 Collection of networks with same routing policy Single routing protocol Usually under single ownership,
32-bit ASNs Philip Smith AfNOG 2007 23rd April 1st May Abuja, Nigeria Autonomous System (AS) AS 100 Collection of networks with same routing policy Single routing protocol Usually under single ownership,
BGP Enhancements for IPv6. ISP Training Workshops
 BGP Enhancements for IPv6 ISP Training Workshops Adding IPv6 to BGP RFC4760 Defines Multi-protocol Extensions for BGP4 Enables BGP to carry routing information of protocols other than IPv4 e.g. MPLS, IPv6,
BGP Enhancements for IPv6 ISP Training Workshops Adding IPv6 to BGP RFC4760 Defines Multi-protocol Extensions for BGP4 Enables BGP to carry routing information of protocols other than IPv4 e.g. MPLS, IPv6,
MPLS VPN--Inter-AS Option AB
 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service provider
The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service provider
IOS Implementation of the ibgp PE CE Feature
 IOS Implementation of the ibgp PE CE Feature Document ID: 117567 Contributed by Luc De Ghein, Cisco TAC Engineer. Apr 04, 2014 Contents Introduction Background Information Implement ibgp PE CE BGP Customer
IOS Implementation of the ibgp PE CE Feature Document ID: 117567 Contributed by Luc De Ghein, Cisco TAC Engineer. Apr 04, 2014 Contents Introduction Background Information Implement ibgp PE CE BGP Customer
Internetwork Expert s CCNP Bootcamp. Border Gateway Protocol (BGP) What Is BGP?
 Internetwork Expert s CCNP Bootcamp Border Gateway Protocol (BGP) http:// What Is BGP? Border Gateway Protocol Version 4 Standards based RFC 4271 A Border Gateway Protocol 4 (BGP-4) Exterior Gateway Protocol
Internetwork Expert s CCNP Bootcamp Border Gateway Protocol (BGP) http:// What Is BGP? Border Gateway Protocol Version 4 Standards based RFC 4271 A Border Gateway Protocol 4 (BGP-4) Exterior Gateway Protocol
Contents. Introduction. Prerequisites. Requirements. Components Used
 Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations OSPF EIGRP RIP Troubleshoot Introduction This document describes how to redistribute Internal Border
Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations OSPF EIGRP RIP Troubleshoot Introduction This document describes how to redistribute Internal Border
MPLS VPN Multipath Support for Inter-AS VPNs
 The feature supports Virtual Private Network (VPN)v4 multipath for Autonomous System Boundary Routers (ASBRs) in the interautonomous system (Inter-AS) Multiprotocol Label Switching (MPLS) VPN environment.
The feature supports Virtual Private Network (VPN)v4 multipath for Autonomous System Boundary Routers (ASBRs) in the interautonomous system (Inter-AS) Multiprotocol Label Switching (MPLS) VPN environment.
Implementing DCI VXLAN Layer 3 Gateway
 This chapter module provides conceptual and configuration information for Data Center Interconnect (DCI) VXLAN Layer 3 Gateway on Cisco ASR 9000 Series Router. Release Modification Release 5.3.2 This feature
This chapter module provides conceptual and configuration information for Data Center Interconnect (DCI) VXLAN Layer 3 Gateway on Cisco ASR 9000 Series Router. Release Modification Release 5.3.2 This feature
Internet Resource Certification and Inter- Domain Routing Security! Eric Osterweil!
 Internet Resource Certification and Inter- Domain Routing Security! Eric Osterweil! Who is allowed to do what?! BGP (the Internet s inter-domain routing protocol) runs by rumor Participants assert reachability
Internet Resource Certification and Inter- Domain Routing Security! Eric Osterweil! Who is allowed to do what?! BGP (the Internet s inter-domain routing protocol) runs by rumor Participants assert reachability
Deploy VPLS. APNIC Technical Workshop October 23 to 25, Selangor, Malaysia Hosted by:
 Deploy VPLS APNIC Technical Workshop October 23 to 25, 2017. Selangor, Malaysia Hosted by: Issue Date: [201609] Revision: [01] Acknowledgement Cisco Systems 2 VPLS Overview 3 Virtual Private LAN Service
Deploy VPLS APNIC Technical Workshop October 23 to 25, 2017. Selangor, Malaysia Hosted by: Issue Date: [201609] Revision: [01] Acknowledgement Cisco Systems 2 VPLS Overview 3 Virtual Private LAN Service
Introduction to BGP. ISP/IXP Workshops
 Introduction to BGP ISP/IXP Workshops 1 Border Gateway Protocol A Routing Protocol used to exchange routing information between different networks Exterior gateway protocol Described in RFC4271 RFC4276
Introduction to BGP ISP/IXP Workshops 1 Border Gateway Protocol A Routing Protocol used to exchange routing information between different networks Exterior gateway protocol Described in RFC4271 RFC4276
Lessons learned running an RPKI service
 Lessons learned running an RPKI service Alex Band Product Manager @alexander_band NANOG 63, San Antonio, Texas RPKI: Ultra Quick Intro 2 RIR becomes a Certificate Authority - Puts IPs and ASNs on a digital
Lessons learned running an RPKI service Alex Band Product Manager @alexander_band NANOG 63, San Antonio, Texas RPKI: Ultra Quick Intro 2 RIR becomes a Certificate Authority - Puts IPs and ASNs on a digital
IPv4 Run-Out, Trading, and the RPKI
 IPv4 Run-Out, Trading, and the RPKI MENOG 3 / Salmiya 2008.04.15 Randy Bush http://rip.psg.com/~randy/080415.menog-v4-trad-rpki.pdf 2008.04.15 MENOG v4 Trade RPKI 2 Internet Initiative
IPv4 Run-Out, Trading, and the RPKI MENOG 3 / Salmiya 2008.04.15 Randy Bush http://rip.psg.com/~randy/080415.menog-v4-trad-rpki.pdf 2008.04.15 MENOG v4 Trade RPKI 2 Internet Initiative
2016/09/07 08:37 1/5 Internal BGP Lab. Set up Internal BGP (ibgp) within the each Group autonomous system to carry routing information within the AS.
 2016/09/07 08:37 1/5 Internal BGP Lab Internal BGP Lab Introduction The purpose of this exercise is to: Set up Internal BGP (ibgp) within the each Group autonomous system to carry routing information within
2016/09/07 08:37 1/5 Internal BGP Lab Internal BGP Lab Introduction The purpose of this exercise is to: Set up Internal BGP (ibgp) within the each Group autonomous system to carry routing information within
Page1. Cisco IOS Software, Linux Software (I86BI_LINUX-ADVENTERPRISEK9-M), Version 15.2(4)M1, DEVELOPMENT TEST SOFTWARE
 BGP Disclaimer This Configuration Guide is designed to assist members to enhance their skills in particular technology area. While every effort has been made to ensure that all material is as complete
BGP Disclaimer This Configuration Guide is designed to assist members to enhance their skills in particular technology area. While every effort has been made to ensure that all material is as complete
IPv4 Run-Out, Trading, and the RPKI
 IPv4 Run-Out, Trading, and the RPKI RIPE 56 / Berlin 2008.05.07 Randy Bush http://rip.psg.com/~randy/080507.ripe-v4-trad-rpki.pdf 2008.05.07 RIPE v4 Trade RPKI 2 Internet Initiative Japan
IPv4 Run-Out, Trading, and the RPKI RIPE 56 / Berlin 2008.05.07 Randy Bush http://rip.psg.com/~randy/080507.ripe-v4-trad-rpki.pdf 2008.05.07 RIPE v4 Trade RPKI 2 Internet Initiative Japan
Chapter 5 Lab 5-3, BGP
 Chapter 5 Lab 5-3, BGP Physical Topology (Baseline) All contents are Copyright 1992 2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 27 Logical Topology
Chapter 5 Lab 5-3, BGP Physical Topology (Baseline) All contents are Copyright 1992 2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 27 Logical Topology
BGP security. 19 april 2018 Copenhagen
 BGP security 19 april 2018 Copenhagen Agenda 14:30 Welcome and registration 15:00 Presentation 17:00 Questions 17:30 Beer & Burgers & 2 Who are we? Lucas Senior network engineer @ NL-ix in ISP business
BGP security 19 april 2018 Copenhagen Agenda 14:30 Welcome and registration 15:00 Presentation 17:00 Questions 17:30 Beer & Burgers & 2 Who are we? Lucas Senior network engineer @ NL-ix in ISP business
Chapter 7 Lab 7-1, Configuring BGP with Default Routing
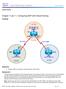 Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
Module 6 ibgp and Basic ebgp
 ISP Workshop Lab Module 6 ibgp and Basic ebgp Objective: Simulate four different interconnected ISP backbones using a combination of IS-IS, internal BGP, and external BGP. Prerequisites: Module 1 (IS-IS)
ISP Workshop Lab Module 6 ibgp and Basic ebgp Objective: Simulate four different interconnected ISP backbones using a combination of IS-IS, internal BGP, and external BGP. Prerequisites: Module 1 (IS-IS)
BGP Link Bandwidth. Finding Feature Information. Prerequisites for BGP Link Bandwidth
 The Border Gateway Protocol (BGP) Link Bandwidth feature is used to advertise the bandwidth of an autonomous system exit link as an extended community. This feature is configured for links between directly
The Border Gateway Protocol (BGP) Link Bandwidth feature is used to advertise the bandwidth of an autonomous system exit link as an extended community. This feature is configured for links between directly
SDN Workshop. Contact: WSDN01_v0.1
 SDN Workshop Contact: training@apnic.net WSDN01_v0.1 Issue Date: [Date] Revision: [xx] BGP-LS - Lab SDN Workshop WSDN01_v0.1 Issue Date: [Date] Revision: [xx] BGP-LS Configuration 3 Configuration Example
SDN Workshop Contact: training@apnic.net WSDN01_v0.1 Issue Date: [Date] Revision: [xx] BGP-LS - Lab SDN Workshop WSDN01_v0.1 Issue Date: [Date] Revision: [xx] BGP-LS Configuration 3 Configuration Example
LAB1: BGP IPv4. BGP: Initial Config. Disclaimer
 Page1 LAB1: BGP IPv4 Disclaimer This Configuration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 LAB1: BGP IPv4 Disclaimer This Configuration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Golden Prefixes IRR Lockdown Job Snijders
 Golden Prefixes IRR Lockdown Job Snijders Agenda What s the problem? IRR not ideal A possible solution: Golden prefixes Making the best of IRR: IRR Lockdown Actual Frustrations The Youtube
Golden Prefixes IRR Lockdown Job Snijders Agenda What s the problem? IRR not ideal A possible solution: Golden prefixes Making the best of IRR: IRR Lockdown Actual Frustrations The Youtube
Module 6x ibgp and Basic ebgp
 Module 6x ibgp and Basic ebgp Objective: Simulate four different interconnected ISP backbones using a combination of IS-IS, internal BGP, and external BGP. Topology : Figure 1 BGP AS Numbers 1 Wednesday,
Module 6x ibgp and Basic ebgp Objective: Simulate four different interconnected ISP backbones using a combination of IS-IS, internal BGP, and external BGP. Topology : Figure 1 BGP AS Numbers 1 Wednesday,
scope scope {global vrf vrf-name} no scope {global vrf vrf-name} Syntax Description
 Multi-Toplogy Routing Commands scope scope To define the scope for a Border Gateway Protocol (BGP) routing session and to enter router scope configuration mode, use the scope command in router configuration
Multi-Toplogy Routing Commands scope scope To define the scope for a Border Gateway Protocol (BGP) routing session and to enter router scope configuration mode, use the scope command in router configuration
BGP Origin Validation (RPKI)
 University of Amsterdam System & Network Engineering BGP Origin Validation (RPKI) July 5, 2013 Authors: Remy de Boer Javy de Koning Supervisors: Jac Kloots
University of Amsterdam System & Network Engineering BGP Origin Validation (RPKI) July 5, 2013 Authors: Remy de Boer Javy de Koning Supervisors: Jac Kloots
Adventures in RPKI (non) deployment. Wes George
 Adventures in RPKI (non) deployment Wes George wesley.george@twcable.com @wesgeorge Background March 2013 FCC CSRIC III WG 6 report on Secure BGP Accurate Records, better measurements Cautious, staged
Adventures in RPKI (non) deployment Wes George wesley.george@twcable.com @wesgeorge Background March 2013 FCC CSRIC III WG 6 report on Secure BGP Accurate Records, better measurements Cautious, staged
<36 th APNIC Meeting, XIAN CHINA> KISA(KRNIC) UPDATE. YOUNGSUN LA Korea Internet & Security Agency
 KISA(KRNIC) UPDATE YOUNGSUN LA (rays@kisa.or.kr) Korea Internet & Security Agency 1 Contents IPv6 Verified NSDs R&D WHOIS User Analysis & Statistics RPKI Testbed 2 IPv6
KISA(KRNIC) UPDATE YOUNGSUN LA (rays@kisa.or.kr) Korea Internet & Security Agency 1 Contents IPv6 Verified NSDs R&D WHOIS User Analysis & Statistics RPKI Testbed 2 IPv6
BGP Link-State. Finding Feature Information. Overview of Link-State Information in BGP
 (LS) is an Address Family Identifier (AFI) and Sub-address Family Identifier (SAFI) defined to carry interior gateway protocol (IGP) link-state database through BGP. BGP-LS delivers network topology information
(LS) is an Address Family Identifier (AFI) and Sub-address Family Identifier (SAFI) defined to carry interior gateway protocol (IGP) link-state database through BGP. BGP-LS delivers network topology information
Securing BGP: The current state of RPKI. Geoff Huston Chief Scientist, APNIC
 Securing BGP: The current state of RPKI Geoff Huston Chief Scientist, APNIC Incidents What happens when I announce your addresses in BGP? All the traffic that used to go to you will now come to me I can
Securing BGP: The current state of RPKI Geoff Huston Chief Scientist, APNIC Incidents What happens when I announce your addresses in BGP? All the traffic that used to go to you will now come to me I can
RPKI Trust Anchor. Geoff Huston APNIC
 RPKI Trust Anchor Geoff Huston APNIC Public Keys How can you trust a digital signature?? What if you have never met the signer and have no knowledge of them or their keys? One approach is transitive trust
RPKI Trust Anchor Geoff Huston APNIC Public Keys How can you trust a digital signature?? What if you have never met the signer and have no knowledge of them or their keys? One approach is transitive trust
Module 6 More ibgp, and Basic ebgp Configuration
 ISP Workshop Lab Module 6 More ibgp, and Basic ebgp Configuration Objective: Simulate four different interconnected ISP backbones using a combination of ISIS, internal BGP, and external BGP. Prerequisites:
ISP Workshop Lab Module 6 More ibgp, and Basic ebgp Configuration Objective: Simulate four different interconnected ISP backbones using a combination of ISIS, internal BGP, and external BGP. Prerequisites:
How to Access and Use Quagga Shell using Avi CLI
 Page 1 of 5 How to Access and Use Quagga Shell using Avi CLI view online Background Quagga is a network routing software suite providing implementations of various routing protocols. Avi Vantage uses Quagga
Page 1 of 5 How to Access and Use Quagga Shell using Avi CLI view online Background Quagga is a network routing software suite providing implementations of various routing protocols. Avi Vantage uses Quagga
Requirements for Resource Public Key Infrastructure (RPKI) Relying Parties (draft-madi-sidrops-rp-00) Di Ma & Stephen Kent.
 Requirements for Resource Public Key Infrastructure (RPKI) Relying Parties (draft-madi-sidrops-rp-00) Di Ma & Stephen Kent IETF 99, Prague 1 Background (1/2) Requirements imposed on Relying Parties (RPs)
Requirements for Resource Public Key Infrastructure (RPKI) Relying Parties (draft-madi-sidrops-rp-00) Di Ma & Stephen Kent IETF 99, Prague 1 Background (1/2) Requirements imposed on Relying Parties (RPs)
Networkers 2001, Australia
 Networkers 2001, Australia March 28-30, Brisbane 1 Troubleshooting BGP Phil Smith Presentation_ID 2001, Cisco Systems, Inc. 2 BGP in Large Scale Networks Scalable Stable Simple 3 Avoid the Problem in the
Networkers 2001, Australia March 28-30, Brisbane 1 Troubleshooting BGP Phil Smith Presentation_ID 2001, Cisco Systems, Inc. 2 BGP in Large Scale Networks Scalable Stable Simple 3 Avoid the Problem in the
BGP Dynamic Neighbors
 BGP dynamic neighbor support allows BGP peering to a group of remote neighbors that are defined by a range of IP addresses. Each range can be configured as a subnet IP address. BGP dynamic neighbors are
BGP dynamic neighbor support allows BGP peering to a group of remote neighbors that are defined by a range of IP addresses. Each range can be configured as a subnet IP address. BGP dynamic neighbors are
address-family ipv4 vrf vrf-name - Selects a per-vrf instance of a routing protocol.
 LAB 1: Initial MPLS VPN Setup LAB 2: Running OSPF between PE and CE Routers LAB 3: Running BGP between PE and CE Routers LAB 4: Overlapping VPNs LAB 1: Initial MPLS VPN Setup Introduction: Introduction
LAB 1: Initial MPLS VPN Setup LAB 2: Running OSPF between PE and CE Routers LAB 3: Running BGP between PE and CE Routers LAB 4: Overlapping VPNs LAB 1: Initial MPLS VPN Setup Introduction: Introduction
BGP Event-Based VPN Import
 The feature introduces a modification to the existing Border Gateway Protocol (BGP) path import process. The enhanced BGP path import is driven by events; when a BGP path changes, all of its imported copies
The feature introduces a modification to the existing Border Gateway Protocol (BGP) path import process. The enhanced BGP path import is driven by events; when a BGP path changes, all of its imported copies
Troubleshooting Routing Solutions
 Chapter 5: Maintaining and Troubleshooting Routing Solutions CCNP TSHOOT: Maintaining and Troubleshooting IP Networks Course v6 1 Chapter 5 Objectives Diagnose network layer connectivity problems using
Chapter 5: Maintaining and Troubleshooting Routing Solutions CCNP TSHOOT: Maintaining and Troubleshooting IP Networks Course v6 1 Chapter 5 Objectives Diagnose network layer connectivity problems using
Contents. Configuring MSDP 1
 Contents Configuring MSDP 1 Overview 1 How MSDP works 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 7 Configuring basic MSDP features 7 Configuration prerequisites 7
Contents Configuring MSDP 1 Overview 1 How MSDP works 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 7 Configuring basic MSDP features 7 Configuration prerequisites 7
Contents. BGP commands 1
 Contents BGP commands 1 address-family ipv4 1 address-family ipv6 2 address-family link-state 3 advertise-rib-active 4 aggregate 5 balance 7 balance as-path-neglect 9 bestroute as-path-neglect 10 bestroute
Contents BGP commands 1 address-family ipv4 1 address-family ipv6 2 address-family link-state 3 advertise-rib-active 4 aggregate 5 balance 7 balance as-path-neglect 9 bestroute as-path-neglect 10 bestroute
H3C BGP Configuration Examples
 H3C BGP Configuration Examples Copyright 2017 New H3C Technologies Co., Ltd. All rights reserved. No part of this manual may be reproduced or transmitted in any form or by any means without prior written
H3C BGP Configuration Examples Copyright 2017 New H3C Technologies Co., Ltd. All rights reserved. No part of this manual may be reproduced or transmitted in any form or by any means without prior written
Segment Routing on Cisco Nexus 9500, 9300, 9200, 3200, and 3100 Platform Switches
 White Paper Segment Routing on Cisco Nexus 9500, 9300, 9200, 3200, and 3100 Platform Switches Authors Ambrish Mehta, Cisco Systems Inc. Haider Salman, Cisco Systems Inc. 2017 Cisco and/or its affiliates.
White Paper Segment Routing on Cisco Nexus 9500, 9300, 9200, 3200, and 3100 Platform Switches Authors Ambrish Mehta, Cisco Systems Inc. Haider Salman, Cisco Systems Inc. 2017 Cisco and/or its affiliates.
How to Access and Use Quagga Shell using Avi CLI
 Page 1 of 5 How to Access and Use Quagga Shell using Avi CLI view online Background Quagga is a network routing software suite providing implementations of various routing protocols. Avi Vantage uses Quagga
Page 1 of 5 How to Access and Use Quagga Shell using Avi CLI view online Background Quagga is a network routing software suite providing implementations of various routing protocols. Avi Vantage uses Quagga
- PIX Advanced IPSEC Lab -
 1 - PIX Advanced IPSEC Lab - Configuring Advanced PIX IPSEC Lab Basic Objectives: 1. Configure and cable the Ethernet interfaces as indicated in the above diagram. 2. Configure a web server for each network,
1 - PIX Advanced IPSEC Lab - Configuring Advanced PIX IPSEC Lab Basic Objectives: 1. Configure and cable the Ethernet interfaces as indicated in the above diagram. 2. Configure a web server for each network,
