Main area: Security Additional areas: Digital Access, Information Literacy, Privacy and Reputation
|
|
|
- Godwin Black
- 5 years ago
- Views:
Transcription
1 Public Wi Fi Created: March 2016 Last Updated: July 2018 Estimated time: Group or individual activity: Ages: 60 minutes [10 minutes] Activity #1 [15 minutes] Activity #2 [10 minutes] Activity #3 [10 minutes] Activity #4 [15 minutes] Assignment Group years old Grades: Grades Online / offline elements: Areas: License: This learning experience contains links to online resources to help facilitate a group based discussion, with an offline writing assignment. Main area: Security Additional areas: Digital Access, Information Literacy, Privacy and Reputation Creative Commons Attribution ShareAlike 4.0 International license. For more information, please visit: Learning Goal Participants will learn about public Wi Fi networks and their benefits and risks. More specifically, they will learn to recognize unsecured Wi Fi when it s available to them, 1
2 understand the tradeoffs inherent in using unsecured Wi Fi and make informed decisions about when to connect to and use unsecured Wi Fi. Materials [One per group of 2 3 participants] Handout: Connection Safety [educator version and participant version] [For educator] Computer with Internet access Projector and projection screen [One per participant] Paper [One per participant] Pens or pencils Resources Article: Why You Should Be Using a VPN (and How to Choose One) by Alan Henry (Lifehacker) Article: Staying Safe On Public Wi Fi This Summer by Rebecca Kielty (The Family Online Safety Institute) Article: Choosing the VPN That s Right for You by The Electronic Frontier Foundation Wikipedia Entry: Transport Layer Security by Wikipedia Video: FTC: Public Wi Fi Networks by The United States Federal Trade Commission Activity #1: What is Wi Fi? ASK: Which devices do you use to access the Internet? How do those devices connect to the Internet? [Wi Fi] Wi Fi is a common way to connect devices to the Internet. Wi Fi uses radio signals to connect devices without a physical or wired connection. 2
3 Imagine that you have a laptop in your home that you'd like to connect to the Internet. To do that, you will need the following: [To visualize the various components of a Wi Fi connection, please project the diagram below on a projection screen.] An access point: An access point is anything that transmits a Wi Fi signal and provides access to the Internet. Your devices need to pick up these signals to connect to the Internet. Sometimes you may need special permission (e.g., a username and password) to sign in and use the wireless signal that an AP transmits. A router: A router is a device that creates a network between all the devices (such as desktop computers, tablets, mobile phones) in a given location (like a school, library, or your home). Typically, routers have an access point built into them (see diagram). Routers have a limited (usually short) range. That's why if your device is too far away from the router, you will get a weak Wi Fi signal or none at all. Also, if there is something between you and the router (such as a building or a brick wall), that will reduce your signal. Although connecting to a router offers access to a network, this does not automatically translate to Internet access. For several devices on a network to be able to connect to the Internet, a router has to be connected to a modem. A modem: A modem is a device that creates and maintains a connection to your Internet Service Provider (ISP) to give you access to the Internet. It converts 3
4 signals from outside your given location into signals that can be read by your computer and other digital devices. In a typical set up, the AP and router are a single device that is physically connected to the modem, using a special cable called an Ethernet cable. This is what is referred to when people talk about a "wired" Internet connection. Mobile devices can also use a cellular connection to connect to the Internet, especially if they are not in a school, library, or home network. Cellular connections are a type of wireless radio signal that has a much larger coverage area than a router has. Cellular connections use particular transceivers, called cell towers, to connect your mobile device to the Internet. ASK: What are the benefits of Wi Fi? What might be some of the drawbacks of Wi Fi? [If not brought up, ASK]: What might be some security concerns when using Wi Fi versus a wired Internet connection? Why is it that you lose Wi Fi access on your phone as you leave a building? Activity #2: Choosing a Wi Fi Network ASK: Are all Wi Fi networks safe? Why or why not? Sometimes, you are given a choice as to which Wi Fi network you would like to use. It s important to remember that there are serious risks if you connect to the wrong network. For instance, unsecured Wi Fi networks are those that don t require a password to log in. If you are on an unsecured network, it s possible for other people on the same network to see your information. They may steal information you send over the network or monitor what you are doing. On the other hand, secure and trusted Wi Fi networks are those that are encrypted (encryption scrambles the information you send and receive over a network, so it s much more challenging for a hacker on the same Wi Fi network to see what you are sending or receiving), and those on which you are certain the network you are signing into is the one the network name is representing. For instance, signing into a network impersonating the name of your school s network 4
5 could lead to account information disclosure. Therefore, networks that are secure and trusted are the ones that offer the most protection. One thing to consider is the context or location of the Wi Fi network. For example, if you are at the movie theater and you see your school s network name on your phone when looking for a Wi Fi connection, you might consider that network is trying to imitate or spoof your school s network to collect passwords from unsuspecting students. When setting up a password protected Wi Fi network, the owner must select an encryption protocol. Common encryption protocols are Wired Equivalent Privacy (WEP), Wi Fi Protected Access (WPA), or WPA2. These protocols make it so that the information that is sent wirelessly over the network is encrypted (or scrambled ). Encryption was created to make it more difficult for hackers to see what you are sending. All of these protocols (WEP, WPA, and WPA2), however, have been shown to be vulnerable to hacking. Therefore, it s important to also rely on secure web connections when transmitting information online. HTTPS is a standard used by websites to encrypt data passed over the Internet. Encryption can prevent any third party from easily viewing the data from your connection. It provides an extra layer of security and can be used in any browser by adding in front of the URL you use (e.g., However, not all websites support HTTPS. You should only enter sensitive information (e.g., passwords, credit card information) on web pages with the prefix. You can use software tools to ensure you always use HTTPS whenever possible. One such tool includes the browser extension HTTPS Everywhere. Most major browsers have security indicators that look like locks near the address bar to indicate HTTPS connections. Unfortunately, HTTPS does not guarantee that you are safe as some malicious websites can also support HTTPS. HTTPS secures the connection but does not ensure the website is a good actor. Secure Sockets Layer (SSL) / Transport Layer Security (TLS) are names for the technology that keeps HTTPS secure. SSL / TLS uses digital encryption keys, which work a lot like real keys. If you wrote a secret on a piece of paper for your friend, whoever found the paper could see your secret. Instead, imagine you gave them a copy of a key in person, and then sent your secrets in matching locked boxes. If someone intercepted the box, they would have a hard time seeing your secret without the key. If someone tried to replace the box with a 5
6 similar looking one, you would notice that your key would not work. SSL / TLS works the same way but with a website. Browser security indicators will also communicate Extended Validation (EV) certificate information. EV certificates are given to websites that verify their owner s identity to a certificate authority. In browsers, sometimes the EV indicator takes the form of the website s name or the registering entity next to the address bar. If you re suspicious of the content on a particular website, you can check to see if the URL in the certificate matches the URL in the browser by clicking on View Certificate. [It s helpful, on the projection screen, to demonstrate to participants how to find View Certificate. How you navigate to this varies by browser. For example, on Chrome, click on View > Developer > Developer Tools > Security tab > View Certificate. (See image below for an example of what the View Certificate screen may look like, which will depend on the site you re on).] ASK: What should you think about when connecting to any new network? [Possible answers include: location (or who owns the network), access (or who else is connected to the network), and activity (or what they are doing on the network).] Who owns your home s Wi Fi network? At school? At a coffee shop? [Their parents / caregivers own their home s Wi Fi network. The administrators and / or the district own the network at school, and the owner owns the coffee shop network.] 6
7 Do you know these people personally? Do you trust these people? [Engage participants in a discussion about how they might trust these people differently.] You should know and trust the person hosting the Wi Fi network you are using. Sometimes, you can determine who the owner is using the network s SSID. The Service Set Identifier (SSID) is the name given to a Wi Fi network that you can see when you try to connect. The SSID is often used to communicate who owns the network and other details about the network. Be careful though as nearly anyone (who knows how to) can create a SSID. For example, someone can create create a SSID that is identical to the one you use at school. This is an example of impersonating a known and trusted network, to potentially harvest usernames and passwords. Knowing who is hosting the network can help you determine whether the network is secure. If it belongs to a person or organization you trust, then you will likely feel comfortable connecting. However, if it s an unknown network, you should not connect as you don t know who owns the router to which you are connecting [For more information about what a router is, please view Activity #1: What is Wi Fi? ]. Because all traffic on the network goes through the router, the owner could be monitoring or recording your web traffic. When you connect to Wi Fi, your device is connected to a local network of devices, and that network connects to the broader Internet. Because your device is exchanging information with this network, it s important to trust the other devices you re connected with and that means any device on the network. It s just like group work you do in school you want to be able to trust the other people you re working with! Using a password on the network may limit who can connect to it. This means you will have a better idea of who is on the network whether it s your family, your friends, or other customers in a coffee shop than if the network was completely open. Whether or not you decide to join a network that may might seem suspicious comes down to the trade offs you are willing to make in terms of online security. You might consider, how should I weigh the potential of my account being breached versus the convenience of joining an available network? ASK: Should you read online news / a blog using your home s Wi Fi network? At school? At a coffee shop? [Explain that the content of a webpage is generally not sensitive information. You can probably do this on any network.] 7
8 Should you send a credit card number using your home s Wi Fi network? At school? At a coffee shop? [Engage in a discussion around why it s safest to do so with their home Wi Fi and not with the coffee shop Wi Fi. Also discuss how, while a school s network is likely trustworthy, it may not be worth the risk since this particular information is highly sensitive.] Should you check your personal using your home s Wi Fi network? At school? At a coffee shop? [Discuss how it s probably safest to do so with their home network, depending on the content of the account. For example, some individuals have multiple s accounts that they use for different purposes (e.g., marketing / promotion s for one account; s to friends and family on another account).] Sensitive information, including passwords and bank information, are better sent / viewed on a private and secure network, on websites using SSL / TLS rather than on a shared public network. This private information is at risk if you submit or access it while on a shared network being used by people you don t know or trust. It may not be clear how sensitive or not sensitive information is because privacy is a personal decision that you must make for yourself. It s important to consider each situation on its own to determine whether you should connect to the network. Ask yourself if you trust the network s owner, others connected to it, what activity you are doing online, and what information you are sharing before deciding to connect or not. Activity #3: Secured and Unsecured Networks [Please note: Part of the content of this activity has been covered in Activity #2: Choosing a Wi Fi Network. We defer to your judgment regarding whether or not you would like to go over this material again if you have already engaged in Activity #2, or skip it.] Unsecured Wi Fi networks are those that don t require a password to log in. The use of unsecured networks poses a risk to the data you transmit and receive over the network. 8
9 Secured Wi Fi networks are those that require a password and have encryption enabled. The person who configured the network is the one who chooses whether or not to enable encryption. Encryption scrambles the information you send and receive over a network, so it s much more difficult for a hacker on the same Wi Fi network to see what you are sending or receiving. Just because a network is secured does not mean that your data is safe. It s certainly more reliable than using an unsecured network; however, a determined hacker may still find a way to access your information. There are three common encryption protocols for Wi Fi networks: They are Wired Equivalent Privacy (WEP), Wi Fi Protected Access (WPA), or WPA2. WEP and WPA are outdated, and relying on these should be thought of as unsecured. Furthermore, WPA2 has also been shown to be vulnerable to hacking. To make sure your information is protected to the fullest extent, check to see that the websites you are using are encrypted using SSL / TLS. ASK: Can anyone think of an example of a password protected network that they have used? [Some examples include their home Wi Fi, a school s Wi Fi, and Wi Fi networks at some public locations like cafes.] Can anyone think of an example of an unsecured network that they have used? How about examples of a secured network? You can check whether a Wi Fi network is encrypted by examining the network or wireless settings on your device. [Before this activity, conduct an Internet search to review how to check Wi Fi network encryption types for different operating systems. Then, on the projection screen, demonstrate how to find out what kind of encryption a network uses. For instance, on MacOS, click on System Preferences > Network > Select Wi Fi > Select the appropriate Network Name. Under the Wi Fi tab, there will be a list of known networks and a column indicating which encryption type is used.] Not all connections are equal. When a network is unsecured, anyone can connect to the network, and it s unclear who controls the network. Joining an unsecured network leaves you vulnerable, because the information you send and receive, like your web traffic (pages, passwords, etc.), could potentially be viewed by anyone on the network if you aren't using an SSL / TLS connection. 9
10 [Depending on your participants technical knowledge, you may wish to discuss the use of Virtual Private Networks (VPN) as an additional layer of security when using Wi Fi. Please refer to the VPN link in the Resources section for further information.] Activity #4: Recognizing Connection Safety [Divide participants into groups of 2 3. Pass out Connection Safety: Participant Handout and assign a scenario to each of the groups. Give participants 5 minutes to discuss their scenarios. Afterwards, ask groups to share their responses. The answers are in green on the educator handout.] Assignment 1. Draw a timeline of a regular day, marking the Wi Fi networks to which you connect. 2. From the selected networks depicted on the timeline, choose two, and in a short paragraph for each, describe the network who else is connected to it? How secure is it? 3. Additionally for the two networks chosen describe what opportunities connecting to these networks come with and what the associated risks might be. 10
11 Connection Safety: Participant Handout For each scenario, consider the location, level of access, and the activity you are doing online. Then determine whether the risk of doing the activity is low, medium, or high and explain why. Location Access Activity Risk Friend s house Your friend s family Online game Coffee shop Customers only Social media Library Members only Financial transaction Airport General public 11
12 Connection Safety: Educator Handout For each scenario, consider the location, level of access, and the activity you are doing online. Then determine whether the risk of doing the activity is low, medium, or high and explain why. Location Access Activity Risk Friend s house Your friend s family Online game Low: There is a small number of people on the network, and you trust them. The activity probably does not include sensitive information. Coffee shop Customers only Social media Medium: Social media is not necessarily sensitive, but anyone who has been to the cafe before will have access to the network and may be able to steal your passwords. Library Members only Financial transaction High: Banking information is highly sensitive, and while the library s access is somewhat limited, you don t know who might maliciously access your information. Airport General public High: Even if your is not sensitive, using a public network is unsafe. 12
SECURITY ON PUBLIC WI-FI New Zealand. A guide to help you stay safe online while using public Wi-Fi
 SECURITY ON PUBLIC WI-FI New Zealand A guide to help you stay safe online while using public Wi-Fi WHAT S YOUR WI-FI PASSWORD? Enter password for the COFFEE_TIME Wi-Fi network An all too common question
SECURITY ON PUBLIC WI-FI New Zealand A guide to help you stay safe online while using public Wi-Fi WHAT S YOUR WI-FI PASSWORD? Enter password for the COFFEE_TIME Wi-Fi network An all too common question
NORTON WI-FI RISK REPORT: U.S. Results
 NORTON WI-FI RISK REPORT: U.S. Results Research Objective Norton by Symantec commissioned its second annual online survey, this year expanded to 15 global markets, in order to better understand consumers
NORTON WI-FI RISK REPORT: U.S. Results Research Objective Norton by Symantec commissioned its second annual online survey, this year expanded to 15 global markets, in order to better understand consumers
Definitions Know What I Mean?
 Definitions Know What I Mean? The list below contains words you will read about in this resource and that your children probably use regularly as they are a normal part of their school world (if not their
Definitions Know What I Mean? The list below contains words you will read about in this resource and that your children probably use regularly as they are a normal part of their school world (if not their
How to Stay Safe on Public Wi-Fi Networks
 How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
BEST PRACTICES FOR PERSONAL Security
 BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
5 Tips to Fortify your Wireless Network
 Article ID: 5035 5 Tips to Fortify your Wireless Network Objective Although Wi-Fi networks are convenient for you and your employees, there may be unwanted clients using up the bandwidth you pay for. In
Article ID: 5035 5 Tips to Fortify your Wireless Network Objective Although Wi-Fi networks are convenient for you and your employees, there may be unwanted clients using up the bandwidth you pay for. In
Methodology USA UK AUSTRALIA CANADA JAPAN N=1,008 MOE=+/-3% N=1,044 MOE=+/- 3% N=1,028 MOE=+/- 3% N=1,025 MOE=+/- 3% N=1,005 MOE=+/- 3%
 Norton by Symantec commissioned an online survey across nine countries in order to better understand consumers public Wi-Fi perceptions and practices, unveiling consumer misconceptions and worries about
Norton by Symantec commissioned an online survey across nine countries in order to better understand consumers public Wi-Fi perceptions and practices, unveiling consumer misconceptions and worries about
FAQ: Privacy, Security, and Data Protection at Libraries
 FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
Packet: Data can be broken into distinct pieces or packets and then reassembled after delivery. Computers on the Internet communicate via packets.
 Broadband Setup from A to Z Print out all the info below and get to work...have fun!! A word of caution! It is very important that you SECURE your wireless network using WEP or WPA encryption (password).
Broadband Setup from A to Z Print out all the info below and get to work...have fun!! A word of caution! It is very important that you SECURE your wireless network using WEP or WPA encryption (password).
How to Build a Culture of Security
 How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
Frequently Asked Questions
 FAQs 10010410NC-RR Frequently Asked Questions Connecting Your Valet to the Internet 1 What computer operating systems does the Valet/Valet Plus support? 1 Why can t I connect my computer or device to my
FAQs 10010410NC-RR Frequently Asked Questions Connecting Your Valet to the Internet 1 What computer operating systems does the Valet/Valet Plus support? 1 Why can t I connect my computer or device to my
Digital Entertainment. Networking Made Easy
 Digital Entertainment 2003 by TiVo Inc. Reproduction in whole or in part without written permission is prohibited. All rights reserved. Printed in the USA. TiVo, TiVo Central, and TiVolution are registered
Digital Entertainment 2003 by TiVo Inc. Reproduction in whole or in part without written permission is prohibited. All rights reserved. Printed in the USA. TiVo, TiVo Central, and TiVolution are registered
Introduction to Information Security Dr. Rick Jerz
 Introduction to Information Security Dr. Rick Jerz 1 Goals Explain the various types of threats to the security of information Discuss the different categorizations of security technologies and solutions
Introduction to Information Security Dr. Rick Jerz 1 Goals Explain the various types of threats to the security of information Discuss the different categorizations of security technologies and solutions
Internet Quick Start Guide. Get the most out of your Midco internet service with these handy instructions.
 Internet Quick Start Guide Get the most out of your Midco internet service with these handy instructions. 1 Contents Wi-Fi Name and Password..................................................... 4 Why Change
Internet Quick Start Guide Get the most out of your Midco internet service with these handy instructions. 1 Contents Wi-Fi Name and Password..................................................... 4 Why Change
Cyber Security Guidelines for Public Wi-Fi Networks
 Cyber Security Guidelines for Public Wi-Fi Networks Version: 1.0 Author: Cyber Security Policy and Standards Document Classification: PUBLIC Published Date: April 2018 Document History: Version Description
Cyber Security Guidelines for Public Wi-Fi Networks Version: 1.0 Author: Cyber Security Policy and Standards Document Classification: PUBLIC Published Date: April 2018 Document History: Version Description
FACEBOOK SAFETY FOR JOURNALISTS. Thanks to these partners for reviewing these safety guidelines:
 FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
Chapter 5 Local Area Networks. Computer Concepts 2013
 Chapter 5 Local Area Networks Computer Concepts 2013 5 Chapter Contents Section A: Network Building Blocks Section B: Wired and Wireless Technologies Section C: Network Setup Section D: Sharing Files Section
Chapter 5 Local Area Networks Computer Concepts 2013 5 Chapter Contents Section A: Network Building Blocks Section B: Wired and Wireless Technologies Section C: Network Setup Section D: Sharing Files Section
Introduction to the Internet. Part 1. What is the Internet?
 Introduction to the Internet Part 1 What is the Internet? A means of connecting a computer to any other computer anywhere in the world via dedicated routers and servers. When two computers are connected
Introduction to the Internet Part 1 What is the Internet? A means of connecting a computer to any other computer anywhere in the world via dedicated routers and servers. When two computers are connected
If you have multiple computers in the same place, you may find it convenient
 Chapter 1: Networking Your Macs In This Chapter Creating a wired network Creating a wireless network Setting up an Airport Extreme base station Connecting to a mobile phone or PDA If you have multiple
Chapter 1: Networking Your Macs In This Chapter Creating a wired network Creating a wireless network Setting up an Airport Extreme base station Connecting to a mobile phone or PDA If you have multiple
Wireless Attacks and Countermeasures
 Wireless Attacks and Countermeasures Wireless Network Technology Wireless network refers to any type of computer network which is wireless, and is commonly associated with a network whose interconnections
Wireless Attacks and Countermeasures Wireless Network Technology Wireless network refers to any type of computer network which is wireless, and is commonly associated with a network whose interconnections
Wireless Security Algorithms
 (NOTE: If you are using a virtual lab to run your attacks you will need an external Wi Fi attachment. The other option is to have a direct install on your computer. Virtual labs cannot access your wireless
(NOTE: If you are using a virtual lab to run your attacks you will need an external Wi Fi attachment. The other option is to have a direct install on your computer. Virtual labs cannot access your wireless
5 IT security hot topics How safe are you?
 5 IT security hot topics How safe are you? Why this whitepaper? We meet many people in IT, of various levels of experience and fields of work. This whitepaper is written for everybody who wants to read
5 IT security hot topics How safe are you? Why this whitepaper? We meet many people in IT, of various levels of experience and fields of work. This whitepaper is written for everybody who wants to read
Abthorpe Broadband Association Ltd.
 Abthorpe Broadband Association Ltd. Wi-Fi Home Network issues Bringing Broadband to the community since 2003. Introduction Tove Valley Broadband provide your property with a single wired network connection
Abthorpe Broadband Association Ltd. Wi-Fi Home Network issues Bringing Broadband to the community since 2003. Introduction Tove Valley Broadband provide your property with a single wired network connection
INTERNET SAFETY IS IMPORTANT
 INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
Personal Internet Security Basics. Dan Ficker Twin Cities DrupalCamp 2018
 Personal Internet Security Basics Dan Ficker Twin Cities DrupalCamp 2018 Overview Security is an aspiration, not a state. Encryption is your friend. Passwords are very important. Make a back-up plan. About
Personal Internet Security Basics Dan Ficker Twin Cities DrupalCamp 2018 Overview Security is an aspiration, not a state. Encryption is your friend. Passwords are very important. Make a back-up plan. About
تاثیرفناوری اطالعات برسازمان ومدیریت جلسه هشتم و نهم
 بنام خدا تاثیرفناوری اطالعات برسازمان ومدیریت جلسه هشتم و نهم امنیت بخشی به سیستمهای فناوری اطالعات Securing Information Systems 1 Learning Objectives Describe the business value of security and control.
بنام خدا تاثیرفناوری اطالعات برسازمان ومدیریت جلسه هشتم و نهم امنیت بخشی به سیستمهای فناوری اطالعات Securing Information Systems 1 Learning Objectives Describe the business value of security and control.
TECHNICAL DOCUMENT ref: 3Hv2
 Wi-Fi Frequently Asked Questions Wi-Fi Basics... 2 The connection process... 2 What is an IP address?... 2 IP address changes... 2 Wi-Fi coverage and signal strength... 3 Wi-Fi terminology... 4 General...
Wi-Fi Frequently Asked Questions Wi-Fi Basics... 2 The connection process... 2 What is an IP address?... 2 IP address changes... 2 Wi-Fi coverage and signal strength... 3 Wi-Fi terminology... 4 General...
Chapter 6 Network and Internet Security and Privacy
 Chapter 6 Network and Internet Security and Privacy Learning Objectives LO6.1: Explain network and Internet security concerns LO6.2: Identify online threats LO6.3: Describe cyberstalking and other personal
Chapter 6 Network and Internet Security and Privacy Learning Objectives LO6.1: Explain network and Internet security concerns LO6.2: Identify online threats LO6.3: Describe cyberstalking and other personal
Introduction to SSL. Copyright 2005 by Sericon Technology Inc.
 Introduction to SSL The cornerstone of e-commerce is a Web site s ability to prevent eavesdropping on data transmitted to and from its site. Without this, consumers would justifiably be afraid to enter
Introduction to SSL The cornerstone of e-commerce is a Web site s ability to prevent eavesdropping on data transmitted to and from its site. Without this, consumers would justifiably be afraid to enter
Wayward Wi-Fi. How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk
 Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
Hide ip address wireless network. Hide ip address wireless network.zip
 Hide ip address wireless network Hide ip address wireless network.zip Easy-Hide-IP hides your unique Internet address from online tracking so you Easy- Hide-IP hides your unique Internet address from online
Hide ip address wireless network Hide ip address wireless network.zip Easy-Hide-IP hides your unique Internet address from online tracking so you Easy- Hide-IP hides your unique Internet address from online
Internet Quick Start Guide. Get the most out of your Midco internet service with these handy instructions.
 Internet Quick Start Guide Get the most out of your Midco internet service with these handy instructions. 1 Contents Internet Security................................................................ 4
Internet Quick Start Guide Get the most out of your Midco internet service with these handy instructions. 1 Contents Internet Security................................................................ 4
facebook a guide to social networking for massage therapists
 facebook a guide to social networking for massage therapists table of contents 2 3 5 6 7 9 10 13 15 get the facts first the importance of social media, facebook and the difference between different facebook
facebook a guide to social networking for massage therapists table of contents 2 3 5 6 7 9 10 13 15 get the facts first the importance of social media, facebook and the difference between different facebook
Wi-Net Window and Rogue Access Points
 Wi-Net Window and Rogue Access Points The Wi-Net Window (WP150) has several features that make it ideal for detecting and locating rogue access points: A rogue access point is a wireless access point that
Wi-Net Window and Rogue Access Points The Wi-Net Window (WP150) has several features that make it ideal for detecting and locating rogue access points: A rogue access point is a wireless access point that
commtech Online Holiday Shopping Tips A Guide Presented by: CommTech Industries
 Online Holiday Shopping Tips A Guide Presented by: CommTech Industries Holiday season is already upon us and that means high traffic for online shopping and higher risk for internet scams. The scammers
Online Holiday Shopping Tips A Guide Presented by: CommTech Industries Holiday season is already upon us and that means high traffic for online shopping and higher risk for internet scams. The scammers
Manually Connected To Wireless Network Macbook Pro Will Not Stay
 Manually Connected To Wireless Network Macbook Pro Will Not Stay Learn how to troubleshoot Wi-Fi network connectivity issues on your Mac. using OS X Mountain Lion or later, you can use Wireless Diagnostics
Manually Connected To Wireless Network Macbook Pro Will Not Stay Learn how to troubleshoot Wi-Fi network connectivity issues on your Mac. using OS X Mountain Lion or later, you can use Wireless Diagnostics
Can I Add A Second Wireless Router To My Home Network
 Can I Add A Second Wireless Router To My Home Network How do I connect another router to my existing Linksys router? Improve the performance of the network without removing your older router, Connect The
Can I Add A Second Wireless Router To My Home Network How do I connect another router to my existing Linksys router? Improve the performance of the network without removing your older router, Connect The
Best Practices Guide to Electronic Banking
 Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
CONTENTS. Getting connected. Ethernet Setup. Connecting a Router. Logging on. Configuring DHCP in Windows. Configuring DHCP on a Mac.
 CONTENTS 1 2 3 4 5 7 8 Getting connected Ethernet Setup Connecting a Router Logging on Configuring DHCP in Windows Configuring DHCP on a Mac Troubleshooting HELP TIP: Visit support.getwireless.net for
CONTENTS 1 2 3 4 5 7 8 Getting connected Ethernet Setup Connecting a Router Logging on Configuring DHCP in Windows Configuring DHCP on a Mac Troubleshooting HELP TIP: Visit support.getwireless.net for
EADS up. stop think connect
 EADS up stop think connect You text, you play games, you share photos and video. You update your status, you post comments, you probably spend some time in a virtual world. Being online connected through
EADS up stop think connect You text, you play games, you share photos and video. You update your status, you post comments, you probably spend some time in a virtual world. Being online connected through
Ages Donʼt Fall for Fake: Activity 1 Don t bite that phishing hook! Goals for children. Letʼs talk
 Ages 11-14 Donʼt Fall for : Activity 1 Don t bite that phishing hook! Children play a game where they study various emails and texts and try to decide which messages are legit and which are phishing scams.
Ages 11-14 Donʼt Fall for : Activity 1 Don t bite that phishing hook! Children play a game where they study various emails and texts and try to decide which messages are legit and which are phishing scams.
Security and Privacy. SWE 432, Fall 2016 Design and Implementation of Software for the Web
 Security and Privacy SWE 432, Fall 2016 Design and Implementation of Software for the Web Today Security What is it? Most important types of attacks Privacy For further reading: https://www.owasp.org/index.php/
Security and Privacy SWE 432, Fall 2016 Design and Implementation of Software for the Web Today Security What is it? Most important types of attacks Privacy For further reading: https://www.owasp.org/index.php/
ANDROID PRIVACY & SECURITY GUIDE ANDROID DEVICE SETTINGS
 ANDROID PRIVACY & SECURITY GUIDE WESNET The Women s Services Network Smartphones store a lot of personal information, including email or social media accounts, reminders and notes, the number of steps
ANDROID PRIVACY & SECURITY GUIDE WESNET The Women s Services Network Smartphones store a lot of personal information, including email or social media accounts, reminders and notes, the number of steps
Wireless Printing Updated 10/30/2008 POLICY. The use of Wireless Networking is not permitted at any site for full client/server networking of Taxwise.
 Updated 10/30/2008 POLICY Tax-Aide Wireless Printing Policy The use of Wireless Networking is not permitted at any site for full client/server networking of Taxwise. Wireless networking, for the purpose
Updated 10/30/2008 POLICY Tax-Aide Wireless Printing Policy The use of Wireless Networking is not permitted at any site for full client/server networking of Taxwise. Wireless networking, for the purpose
Technology Safety Quick Tips
 Technology Safety Quick Tips Spyware: Computer & Phone Monitoring Software It enables a person to secretly monitor someone else s entire computer activity. It can be installed remotely by sending an email,
Technology Safety Quick Tips Spyware: Computer & Phone Monitoring Software It enables a person to secretly monitor someone else s entire computer activity. It can be installed remotely by sending an email,
Ayrstone AyrMesh Router Setup
 Ayrstone AyrMesh Router Setup This guide should help you set up AyrMesh Router SP. The setup is relatively simple but should you need more detailed directions, such as slide shows, video, or troubleshooting
Ayrstone AyrMesh Router Setup This guide should help you set up AyrMesh Router SP. The setup is relatively simple but should you need more detailed directions, such as slide shows, video, or troubleshooting
It s still very important that you take some steps to help keep up security when you re online:
 PRIVACY & SECURITY The protection and privacy of your personal information is a priority to us. Privacy & Security The protection and privacy of your personal information is a priority to us. This means
PRIVACY & SECURITY The protection and privacy of your personal information is a priority to us. Privacy & Security The protection and privacy of your personal information is a priority to us. This means
APSCN VPN Setup Guide for Windows 7
 APSCN VPN Setup Guide for Windows 7 Beginning in the 2014 2015 school year the Bergman School District will be transitioning from GradeQuick as our district grade book system, to eschool. We will provide
APSCN VPN Setup Guide for Windows 7 Beginning in the 2014 2015 school year the Bergman School District will be transitioning from GradeQuick as our district grade book system, to eschool. We will provide
E-Commerce/Web Security
 E-Commerce/Web Security Prepared For: Software Engineering 4C03 Kartik Sivaramakrishnan McMaster University 2005 Prepared by James Allin 9902847 1.0 - Introduction... 3 2.0 - E-Commerce Transaction Overview...
E-Commerce/Web Security Prepared For: Software Engineering 4C03 Kartik Sivaramakrishnan McMaster University 2005 Prepared by James Allin 9902847 1.0 - Introduction... 3 2.0 - E-Commerce Transaction Overview...
Adobe Security Survey
 Adobe Security Survey October 2016 Edelman + Adobe INTRODUCTION Methodology Coinciding with National Cyber Security Awareness Month (NCSAM), Edelman Intelligence, on behalf of Adobe, conducted a nationally
Adobe Security Survey October 2016 Edelman + Adobe INTRODUCTION Methodology Coinciding with National Cyber Security Awareness Month (NCSAM), Edelman Intelligence, on behalf of Adobe, conducted a nationally
An introduction to wireless security at home, on the road and on campus. Sherry Callahan and Kyle Crane
 Out of Thin Air! An introduction to wireless security at home, on the road and on campus Sherry Callahan and Kyle Crane University of Kansas Medical Center October 5, 2009 Wireless Networking at Home Sherry
Out of Thin Air! An introduction to wireless security at home, on the road and on campus Sherry Callahan and Kyle Crane University of Kansas Medical Center October 5, 2009 Wireless Networking at Home Sherry
Bowie Senior Center Surfing the Web
 Bowie Senior Center Surfing the Web (Without a wetsuit) Introduction Surfing the web is just another term for the activity of searching the Internet for web sites of interest. The Internet is a very powerful
Bowie Senior Center Surfing the Web (Without a wetsuit) Introduction Surfing the web is just another term for the activity of searching the Internet for web sites of interest. The Internet is a very powerful
Home Computer and Internet User Security
 Home Computer and Internet User Security Lawrence R. Rogers Version 1.0.4 CERT Training and Education Networked Systems Survivability Software Engineering Institute Carnegie Mellon University Pittsburgh,
Home Computer and Internet User Security Lawrence R. Rogers Version 1.0.4 CERT Training and Education Networked Systems Survivability Software Engineering Institute Carnegie Mellon University Pittsburgh,
Certificate-based authentication for data security
 Technical white paper Certificate-based authentication for data security Table of Contents Introduction... 2 Analogy: A simple checking account... 2 Verifying a digital certificate... 2 Summary... 8 Important
Technical white paper Certificate-based authentication for data security Table of Contents Introduction... 2 Analogy: A simple checking account... 2 Verifying a digital certificate... 2 Summary... 8 Important
The ICT4me Curriculum
 The ICT4me Curriculum About ICT4me ICT4me is an after school and summer curriculum for middle school youth to develop ICT fluency, interest in mathematics, and knowledge of information, communication,
The ICT4me Curriculum About ICT4me ICT4me is an after school and summer curriculum for middle school youth to develop ICT fluency, interest in mathematics, and knowledge of information, communication,
The ICT4me Curriculum
 The ICT4me Curriculum About ICT4me ICT4me is an after school and summer curriculum for middle school youth to develop ICT fluency, interest in mathematics, and knowledge of information, communication,
The ICT4me Curriculum About ICT4me ICT4me is an after school and summer curriculum for middle school youth to develop ICT fluency, interest in mathematics, and knowledge of information, communication,
Welcome to Fetch. Welcome 3. Connect Fetch to your home Wi-Fi 4. Tips to improve Wi-Fi in your home 8. Can t connect to Wi-Fi 10
 Wi-Fi User Guide Welcome to Fetch Welcome 3 Connect Fetch to your home Wi-Fi 4 Tips to improve Wi-Fi in your home 8 Can t connect to Wi-Fi 10 Advanced Wi-Fi troubleshooting 1 Welcome This guide will help
Wi-Fi User Guide Welcome to Fetch Welcome 3 Connect Fetch to your home Wi-Fi 4 Tips to improve Wi-Fi in your home 8 Can t connect to Wi-Fi 10 Advanced Wi-Fi troubleshooting 1 Welcome This guide will help
Best Practices for Keeping Your Home Network Secure
 Best Practices for Keeping Your Home Network Secure The cyber threat is no longer limited to your office network and work persona. Adversaries realize that targets are typically more vulnerable when operating
Best Practices for Keeping Your Home Network Secure The cyber threat is no longer limited to your office network and work persona. Adversaries realize that targets are typically more vulnerable when operating
Security and Privacy
 E-mail Security and Privacy Department of Computer Science Montclair State University Course : CMPT 320 Internet/Intranet Security Semester : Fall 2008 Student Instructor : Alex Chen : Dr. Stefan Robila
E-mail Security and Privacy Department of Computer Science Montclair State University Course : CMPT 320 Internet/Intranet Security Semester : Fall 2008 Student Instructor : Alex Chen : Dr. Stefan Robila
6 TIPS FOR IMPROVING YOUR WEB PRESENCE
 6 TIPS FOR IMPROVING YOUR WEB PRESENCE 6 TIPS FOR IMPROVING YOUR WEB PRESENCE We all want to get noticed on the web. If you are running a business you want to be on the first page in Google via organic
6 TIPS FOR IMPROVING YOUR WEB PRESENCE 6 TIPS FOR IMPROVING YOUR WEB PRESENCE We all want to get noticed on the web. If you are running a business you want to be on the first page in Google via organic
CYBER ATTACKS EXPLAINED: WIRELESS ATTACKS
 CYBER ATTACKS EXPLAINED: WIRELESS ATTACKS Wireless networks are everywhere, from the home to corporate data centres. They make our lives easier by avoiding bulky cables and related problems. But with these
CYBER ATTACKS EXPLAINED: WIRELESS ATTACKS Wireless networks are everywhere, from the home to corporate data centres. They make our lives easier by avoiding bulky cables and related problems. But with these
Social Media Reputation Management
 Social Media Reputation Management If you are using social media sites such as Facebook or Twitter, there are some simple steps you can take to manage your reputation and protect your identity. Even if
Social Media Reputation Management If you are using social media sites such as Facebook or Twitter, there are some simple steps you can take to manage your reputation and protect your identity. Even if
Expected Outcomes Able to design the network security for the entire network Able to develop and suggest the security plan and policy
 CHAPTER 9 DEVELOPING NETWORK SECURITY STRATEGIES Expected Outcomes Able to design the network security for the entire network Able to develop and suggest the security plan and policy Network Security Design
CHAPTER 9 DEVELOPING NETWORK SECURITY STRATEGIES Expected Outcomes Able to design the network security for the entire network Able to develop and suggest the security plan and policy Network Security Design
How to set up your wireless network
 How to set up your wireless network There are several steps involved in securing your wireless network. I recommend that you take these steps in order and only change one item at a time. While this may
How to set up your wireless network There are several steps involved in securing your wireless network. I recommend that you take these steps in order and only change one item at a time. While this may
Wireless (Select Models Only) User Guide
 Wireless (Select Models Only) User Guide Copyright 2008 Hewlett-Packard Development Company, L.P. Windows is a U.S. registered trademark of Microsoft Corporation. Bluetooth is a trademark owned by its
Wireless (Select Models Only) User Guide Copyright 2008 Hewlett-Packard Development Company, L.P. Windows is a U.S. registered trademark of Microsoft Corporation. Bluetooth is a trademark owned by its
Using Picasa Web Albums North Canton City Schools - Eric Curts
 Using Picasa Web Albums North Canton City Schools - Eric Curts Table of Contents: What is Picasa Web Albums? How to upload an image to Picasa web Albums How to manage an image you have added How to edit
Using Picasa Web Albums North Canton City Schools - Eric Curts Table of Contents: What is Picasa Web Albums? How to upload an image to Picasa web Albums How to manage an image you have added How to edit
Quick Start Guide for Standalone EAP
 Quick Start Guide for Standalone EAP CHAPTERS 1. Determine the Management Method 2. Build the Network Topology 3. Log In to the EAP 4. Edit the SSID 5. Configure and Manage the EAP This guide applies to:
Quick Start Guide for Standalone EAP CHAPTERS 1. Determine the Management Method 2. Build the Network Topology 3. Log In to the EAP 4. Edit the SSID 5. Configure and Manage the EAP This guide applies to:
The essential guide to creating a School Bring Your Own Device Policy. (BYOD)
 The essential guide to creating a School Bring Your Own Device Policy. (BYOD) Contents Introduction.... 3 Considerations when creating a BYOD policy.... 3 General Guidelines for use (Acceptable Use Policy)....
The essential guide to creating a School Bring Your Own Device Policy. (BYOD) Contents Introduction.... 3 Considerations when creating a BYOD policy.... 3 General Guidelines for use (Acceptable Use Policy)....
FINRA DR Portal. User Guide for Arbitration and Mediation Case Participants
 FINRA DR Portal for Arbitration and Mediation Case Participants April 2014 Disclaimer These materials are for training and instructional purposes only. No part of this publication may be reproduced, stored
FINRA DR Portal for Arbitration and Mediation Case Participants April 2014 Disclaimer These materials are for training and instructional purposes only. No part of this publication may be reproduced, stored
School of Computer Sciences Universiti Sains Malaysia Pulau Pinang
 School of Computer Sciences Universiti Sains Malaysia Pulau Pinang Information Security & Assurance Assignment 2 White Paper Virtual Private Network (VPN) By Lim Teck Boon (107593) Page 1 Table of Content
School of Computer Sciences Universiti Sains Malaysia Pulau Pinang Information Security & Assurance Assignment 2 White Paper Virtual Private Network (VPN) By Lim Teck Boon (107593) Page 1 Table of Content
WPA SECURITY (Wi-Fi Protected Access) Presentation. Douglas Cheathem (csc Spring 2007)
 WPA SECURITY (Wi-Fi Protected Access) Presentation By Douglas Cheathem (csc 650.01 Spring 2007) OUTLINE Introduction Security Risk Vulnerabilities Prevention Conclusion Live Demo Q & A INTRODUCTION! WPA
WPA SECURITY (Wi-Fi Protected Access) Presentation By Douglas Cheathem (csc 650.01 Spring 2007) OUTLINE Introduction Security Risk Vulnerabilities Prevention Conclusion Live Demo Q & A INTRODUCTION! WPA
CONTENTS. Getting connected. Ethernet Setup. Connecting a Router. Logging on. Configuring DHCP in Windows. Configuring DHCP on a Mac.
 Username: Password: CONTENTS 1 2 3 4 5 7 8 Getting connected Ethernet Setup Connecting a Router Logging on Configuring DHCP in Windows Configuring DHCP on a Mac Troubleshooting HELP TIP: Visit dojonetworks.com/support
Username: Password: CONTENTS 1 2 3 4 5 7 8 Getting connected Ethernet Setup Connecting a Router Logging on Configuring DHCP in Windows Configuring DHCP on a Mac Troubleshooting HELP TIP: Visit dojonetworks.com/support
Laptop computers started as very expensive
 Discovering the Laptop Advantage Laptop computers started as very expensive options for those who travelled on business and were willing to carry almost ten pounds of machine to be able to use a computer
Discovering the Laptop Advantage Laptop computers started as very expensive options for those who travelled on business and were willing to carry almost ten pounds of machine to be able to use a computer
Ayrstone AyrMesh Router SP Setup
 Ayrstone AyrMesh Router SP Setup This guide should help you set up AyrMesh Router SP. The setup is relatively simple but should you need more detailed directions, such as slide shows, video, or troubleshooting
Ayrstone AyrMesh Router SP Setup This guide should help you set up AyrMesh Router SP. The setup is relatively simple but should you need more detailed directions, such as slide shows, video, or troubleshooting
Fix Home Network. Thousands of satisfied users! Easy steps to setup Wireless router with Cable or DSL internet service provider.
 Fix Home Network Thousands of satisfied users! Easy steps to setup Wireless router with Cable or DSL internet service provider. Copyright, Legal Notice and Disclaimer: This publication is protected under
Fix Home Network Thousands of satisfied users! Easy steps to setup Wireless router with Cable or DSL internet service provider. Copyright, Legal Notice and Disclaimer: This publication is protected under
ClassDojo Guide for Parents
 ClassDojo Guide for Parents Contents What is ClassDojo?... 1 How Do I Set-Up My child s Account?... 2 How does my child log in at home?... 4 Create a Parent Account... 6 Adding Multiple Students or Classes
ClassDojo Guide for Parents Contents What is ClassDojo?... 1 How Do I Set-Up My child s Account?... 2 How does my child log in at home?... 4 Create a Parent Account... 6 Adding Multiple Students or Classes
TPS ISS ipad Setup Process. Setup your mobile Device
 TPS ISS ipad Setup Process Setup your mobile Device This document will walk you through the steps to setup you device to TPS network and exchange server. Drink, Linda 10/31/2013 Table of Contents TPS ipad
TPS ISS ipad Setup Process Setup your mobile Device This document will walk you through the steps to setup you device to TPS network and exchange server. Drink, Linda 10/31/2013 Table of Contents TPS ipad
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
The Launch GDS can be updated via a wireless internet connection as well as by USB or cat5 cable.
 LAUNCH Wifi Setup Procedure The Launch GDS can be updated via a wireless internet connection as well as by USB or cat5 cable. If you are in a wifi hotspot or have an open network available simply choose
LAUNCH Wifi Setup Procedure The Launch GDS can be updated via a wireless internet connection as well as by USB or cat5 cable. If you are in a wifi hotspot or have an open network available simply choose
COMP 2000 W 2012 Lab no. 3 Page 1 of 11
 COMP 2000 W 2012 Lab no. 3 Page 1 of 11 Lab Introduction Background The Internet is based on packet-switched protocols. Information is carried in packets (it is divided into packets), which can be imagined
COMP 2000 W 2012 Lab no. 3 Page 1 of 11 Lab Introduction Background The Internet is based on packet-switched protocols. Information is carried in packets (it is divided into packets), which can be imagined
Get to know your Modem 1. Modem Technical Overview 3
 User Manual Get to know your Modem 1 Modem Technical Overview 3 Managing your Modem Settings How to view your Modem settings 5 Understanding the front page 6 Changing your Modem login password 7 Upgrading
User Manual Get to know your Modem 1 Modem Technical Overview 3 Managing your Modem Settings How to view your Modem settings 5 Understanding the front page 6 Changing your Modem login password 7 Upgrading
What is MyCCCov? Table of Contents
 What is MyCCCov? MyCCCov (our personalized Church Community Builder/CCB ) provides a private, safe and personal place for you to stay connected at CCCov. Here s a snapshot of how MyCCCov will benefit you:
What is MyCCCov? MyCCCov (our personalized Church Community Builder/CCB ) provides a private, safe and personal place for you to stay connected at CCCov. Here s a snapshot of how MyCCCov will benefit you:
How to connect to a Wi-Fi or Wireless Network
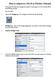 How to connect to a Wi-Fi or Wireless Network This guide will walk you through the steps of connecting to a Wi-Fi network that is broadcasting its name. Start the ipad. 1. Tap on the Settings app. The
How to connect to a Wi-Fi or Wireless Network This guide will walk you through the steps of connecting to a Wi-Fi network that is broadcasting its name. Start the ipad. 1. Tap on the Settings app. The
Internet and Mini.K.G Senior Scientist, FRAD, CMFRI
 Internet and E-Mail Mini.K.G Senior Scientist, FRAD, CMFRI Email: mini.anish02@gmail.com 28 Introduction to Internet Internet is a worldwide system of interconnected computer networks. It connects several
Internet and E-Mail Mini.K.G Senior Scientist, FRAD, CMFRI Email: mini.anish02@gmail.com 28 Introduction to Internet Internet is a worldwide system of interconnected computer networks. It connects several
AirCruiser G Wireless Router GN-BR01G
 AirCruiser G Wireless Router GN-BR01G User s Guide i Contents Chapter 1 Introduction... 1 Overview...1 Features...1 Package Contents...2 AirCruiser G Wireless Router Rear Panel...2 AirCruiser G Wireless
AirCruiser G Wireless Router GN-BR01G User s Guide i Contents Chapter 1 Introduction... 1 Overview...1 Features...1 Package Contents...2 AirCruiser G Wireless Router Rear Panel...2 AirCruiser G Wireless
 Assistance with University Projects? Research Reports? Writing Skills? We ve got you covered! www.assignmentstudio.net WhatsApp: +61-424-295050 Toll Free: 1-800-794-425 Email: contact@assignmentstudio.net
Assistance with University Projects? Research Reports? Writing Skills? We ve got you covered! www.assignmentstudio.net WhatsApp: +61-424-295050 Toll Free: 1-800-794-425 Email: contact@assignmentstudio.net
Introduction to
 Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting
Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting
I entered and it failed to open the Web Menu.
 I entered http://setup.ampedwireless.com and it failed to open the Web Menu. 1. Make sure your computer is connected to the Range Extender s Wi-Fi network: Amped_REC10 2. Try to use a different web browser.
I entered http://setup.ampedwireless.com and it failed to open the Web Menu. 1. Make sure your computer is connected to the Range Extender s Wi-Fi network: Amped_REC10 2. Try to use a different web browser.
Table of Contents. Blog and Personal Web Site Policy
 Table of Contents Blog and Personal Web Sites Policy... 2 Policy... 2 Rights to content... 3 Option for More Restrictive License Terms... 3 Attribution... 4 Guidelines... 4 Personal Website and Blog Guidelines
Table of Contents Blog and Personal Web Sites Policy... 2 Policy... 2 Rights to content... 3 Option for More Restrictive License Terms... 3 Attribution... 4 Guidelines... 4 Personal Website and Blog Guidelines
Google Drive. Lesson Planet
 Google Drive Lesson Planet 2014 www.lessonplanet.com Introduction Trying to stay up to speed with the latest technology can be exhausting. Luckily this book is here to help, taking you step by step through
Google Drive Lesson Planet 2014 www.lessonplanet.com Introduction Trying to stay up to speed with the latest technology can be exhausting. Luckily this book is here to help, taking you step by step through
User Guide MAX-STREAM AC1750 MU-MIMO GIGABIT ROUTER. Model # EA7300
 User Guide MAX-STREAM AC1750 MU-MIMO GIGABIT ROUTER Model # EA7300 Contents Product Overview...3 Top view... 3 Back view... 4 Setting Up: Basics...6 Where to find more help... 6 How to install your router...
User Guide MAX-STREAM AC1750 MU-MIMO GIGABIT ROUTER Model # EA7300 Contents Product Overview...3 Top view... 3 Back view... 4 Setting Up: Basics...6 Where to find more help... 6 How to install your router...
Session Booklet Facebook part 2
 Session Booklet Facebook part 2 Facebook, like any online or offline meeting place, carries with it some risks. Remember that you should apply the same common sense and safety rules as you do when you
Session Booklet Facebook part 2 Facebook, like any online or offline meeting place, carries with it some risks. Remember that you should apply the same common sense and safety rules as you do when you
SOCIAL MEDIA SNAPSHOT FACEBOOK PRIVACY SETTINGS FEBRUARY 2011 UPDATED FOR HTTPS
 SOCIAL MEDIA SNAPSHOT FACEBOOK PRIVACY SETTINGS FEBRUARY 2011 UPDATED FOR HTTPS If you have already adjusted your settings based on the August 2010 recommendations, you may skip ahead to only the slides
SOCIAL MEDIA SNAPSHOT FACEBOOK PRIVACY SETTINGS FEBRUARY 2011 UPDATED FOR HTTPS If you have already adjusted your settings based on the August 2010 recommendations, you may skip ahead to only the slides
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
Understanding Routers, Switches, and Network Hardware
 Understanding Routers, Switches, and Network Hardware Rather than start off with a glossary of networking terms and in the process slam you with a technical terms with no easy point of reference let s
Understanding Routers, Switches, and Network Hardware Rather than start off with a glossary of networking terms and in the process slam you with a technical terms with no easy point of reference let s
Password Managers: Devil s in the Details
 Password Managers: Devil s in the Details How Can Giving all your Passwords to a Password Manager be Safe? AUGUST 2018 Passwords are dead; long live the password! Passwords are unequivocally the most used
Password Managers: Devil s in the Details How Can Giving all your Passwords to a Password Manager be Safe? AUGUST 2018 Passwords are dead; long live the password! Passwords are unequivocally the most used
3. How is technology used to serve our advertisements on other Sites that you visit and what choices do you have?
 Privacy Policy for U.S. Websites Scope. This Privacy Policy applies to personal information collected online, used and disclosed by Stanley Black & Decker, Inc. s affiliates including but not limited to
Privacy Policy for U.S. Websites Scope. This Privacy Policy applies to personal information collected online, used and disclosed by Stanley Black & Decker, Inc. s affiliates including but not limited to
USER GUIDE. Wireless-G Broadband Router. Model No: WRT54G2 V1
 USER GUIDE Wireless-G Broadband Router Model No: WRT54G2 V1 About This Guide About This Guide Icon Descriptions While reading through the User Guide you may see various icons that call attention to specific
USER GUIDE Wireless-G Broadband Router Model No: WRT54G2 V1 About This Guide About This Guide Icon Descriptions While reading through the User Guide you may see various icons that call attention to specific
Frequently Asked Questions (FAQ)
 Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
(electronic mail) is the exchange of computer-stored messages by telecommunication.
 What is email? E-mail (electronic mail) is the exchange of computer-stored messages by telecommunication. E-mail is one of the protocols included with the Transport Control Protocol/Internet Protocol (TCP/IP)
What is email? E-mail (electronic mail) is the exchange of computer-stored messages by telecommunication. E-mail is one of the protocols included with the Transport Control Protocol/Internet Protocol (TCP/IP)
