cell router mobile host
|
|
|
- Gervase Clarke
- 5 years ago
- Views:
Transcription
1 In Mobile Computing, T. Imielinski and H. F. Korth eds., Kluwer Academic Publishers, STRATEGIES FOR QUERY PROCESSING IN MOBILE COMPUTING Masahiko TSUKAMOTO, Rieko KADOBAYASHI* and Shojiro NISHIO Dept. of Information Systems Engineering, Faculty of Engineering, Osaka University 2-1 Yamadaoka, Suita, Osaka 565, Japan * ATR Media Integration & Communications Research Laboratories, Seika-cho, Soraku-gun, Kyoto , Japan ABSTRACT In this paper, we discuss several strategies for ecient processing of three types of queries concerning mobile hosts; (1) queries to obtain the location of a mobile host (location queries), (2) queries to determine whether the mobile host is currently active (existence queries), and (3) queries to obtain a piece of information from a mobile host (data queries). Extracting ve fundamental strategies from those usually employed in mobile communication protocols, we shall discuss their features and then compare their performance. These ve strategies are: single broadcast notication (SBN), double broadcast notication (WBN), broadcast query forwarding (BQF), single default notication (SDN), and double default notication (WDN). We show that the optimal strategy varies according to network conditions such as network topology, network scale, migration rate, and query occurrence rate. 1 INTRODUCTION Currently, one of the most important and attractive research issues in computer networks is the development of ubiquitously-accessed networks, where users can access computer resources at anytime from anywhere through movable computers. A substantial amount of research has already been conducted on how to support mobile communications in existing network environments (see, e.g., [4], [8], [17], [18], [19], [20], and [22]). These approaches were directed at the 595
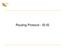
2 596 Chapter 22 realization of low cost location management of mobile hosts. In addition to the packet transmission required in conventional mobile communication protocols, the mobile computing environments currently under development must resolve several data management issues such as query processing (see, e.g., [1], [6], [9], [10], [11], and [14]). Among queries in a mobile computing environment, we consider queries called location sensitive queries which are used (1) to obtain the location of a mobile host, (2) to determine the existence of a mobile host, and (3) to obtain data stored in a mobile host (e.g., location dependent information such as the sensor value set on a mobile host). The strategies for processing such queries are considered to be rather dierent from those used for mobile communication protocols, although the key tasks for both are the management of location information of each mobile host. In this paper, we rst review the strategies currently used in mobile communication protocols, and then, extracting the fundamental ideas of these strategies, the following ve strategies will be proposed for processing location sensitive queries: single broadcast notication (SBN), double broadcast notication (WBN), broadcast query forwarding (BQF), single default notication (SDN), and double default notication (WDN). For each of these ve strategies, we shall discuss their features and then compare their performance. As a result, we show that the optimal strategy among them varies according to such conditions as network topology, network scale, and migration rate. The paper is organized as follows. First in Section 2, we extract ve basic strategies currently employed in mobile communication protocols. Then we apply these strategies to process location sensitive queries in Section 3. In Section 4, we evaluate these strategies and demonstrate that the optimal strategy changes according to several network conditions. Finally, we summarize the paper and discuss possible future work in Section 5. 2 TECHNIQUES USED IN MOBILE COMMUNICATION PROTOCOLS In this section, we study mobile communication protocols in regard to their ability to process location sensitive queries in Section 3. Here we use the model illustrated in Figure 1 as an example. A mobile host is a system which is capable of moving across wireless cells. A router is a system which forwards packets
3 Strategies for Query Processing in Mobile Computing 597 cell router mobile host Figure 1 An example of a communication network. from/to mobile hosts. A wireless cell is managed by a router, and the router can exchange packets with any mobile host located in its cell. Mobile communication protocols are concerned with correctly and eciently forwarding packets to the destination mobile host. Many researchers have proposed various protocols to support mobile communication. Teraoka et al. [19], Perkins and Bhagwat [17], and Wada et al. [22] have proposed protocols for mobile hosts in IP networks. Ioannidis et al. [8] have proposed protocols for small IP networks such as campus networks. In OSI network environments, the existing routing protocol, i.e., the IS-IS protocol [13], can deal with host migration within an area. Furthermore, several protocols for inter-area migration have been proposed by Carlberg [4] and Tsukamoto and Tanaka [20], and an eective protocol for intra-area migration has been also proposed by Tanaka and Tsukamoto [18]. Careful observation of these protocols allows us to determine that they employ the following three fundamental strategies in an integrated manner: Broadcast Notication (BN): A mobile host's location information is broadcast throughout the network on each migration. According to this information, data packets for the mobile host are forwarded to the current location. the IS-IS protocol and OSPF [16] are examples of BN. Default Forwarding (DF): A default router exists for each mobile host. The default router maintains that host's location information. A local router is
4 598 Chapter 22 located in the same network as the mobile host and noties the default router of the mobile host's current location. Data packets to the mobile host are rst forwarded to the default router and then forwarded to the local router. DF is currently the most common strategy used to support mobile hosts and is employed in [18], [19], [20], and [22]. Broadcast Query (BQ): On receiving a data packet addressed to a mobile host, the router broadcasts a query packet to all the other routers in order to forward the data packet according to the reply. BQ is used in [8]. In addition to the above three strategies, the following two strategies can be used to support mobile hosts: Default Query (DQ): Like DF above, there exists a default router for each mobile host. The default router is informed of the mobile host's current location. On receiving a data packet addressed to a mobile host, the router asks the default router for the location of the mobile host, and then forwards the data packet to the location identied in the reply. Broadcast Forwarding (BF): This strategy is based on a broadcast mechanism. The router receives data packets and then broadcasts them to the entire network. This strategy has been widely used in packet radio networks [7]. These ve strategies can be categorized from several viewpoints. In BQ and DQ, as soon as a router receives a packet, a query packet is sent for obtaining the destination mobile host's location. We call these strategies query-based strategies. On the other hand, in BF and DF, as soon as a router receives a packet, the packet is forwarded to other systems without rst using a query packet to obtain the destination mobile host's location. We call these strategies forwarding-based strategies. In DF and DQ, there is a default router for each mobile host to manage that host's location information. We call these strategies default-based strategies. In BN, BF, and BQ, a special system for mobile host location information management does not exist. In this case, broadcast is used for notication, forwarding, or querying. We call these strategies broadcastbased strategies. Among many possible parameters which aect the network environment, the three parameters, amount of trac, migration rate, and packet size, are considered to have a strong eect on the performance of the above protocols. If high trac and infrequent migration are assumed, BN is considered to be the best strategy for bandwidth utilization regardless of the packet size because
5 Strategies for Query Processing in Mobile Computing 599 large packet high traffic BN DQ BQ high migration DF BF small packet Figure 2 Best strategies for mobile communication. BN provides faster convergence. If the opposite case is assumed, BF or BQ is better than the others because no location information is sent on migration. Otherwise, if trac as well as migration rate are moderate in comparison to the abovementioned two extreme cases, then DF and DQ are eective at reducing the total trac because packets are not broadcast on both migration of mobile hosts and forwarding of data packets. If data packets are large, query-based strategies DQ and BQ are better than the forwarding-based strategies DF and BF, respectively. Caching of mobile information in each router can reduce the time it takes a query to complete and hence results in eective use of bandwidth. If the data packets are small, it is better to choose the forwarding-based strategies. Generally, default-based strategies DF and DQ are more scalable than broadcastbased strategies BF and BQ, respectively. If we consider an n-grid topology and evaluate the cost by total trac caused by control packets and data packets, the cost of default-based strategies grows as an order of O(n), while the cost of broadcast-based strategies grows as an order of O(n 2 ). However, it is possible that broadcast-based strategies reduce the total trac when used in small or low cost networks.
6 600 Chapter 22 a g k b Network f j cell query server c e i mobile host server client d h mobile host Figure 3 An example of a mobile database network. Therefore, the best strategies to support mobile communications depend on the network conditions. Figure 2 graphically shows which strategy is superior. Most of these strategies are qualitatively analyzed in [21]. 3 QUERY PROCESSING FOR LOCATION SENSITIVE QUERIES In this section, the mobile database network model assumed in this paper is described. Then, we discuss query processing functions essential to mobile communication environments using references to the features of mobile communication protocols described in Section 2. Finally, we propose several fundamental strategies for the query processing. 3.1 Model A mobile host, which can move across cells, can keep pieces of information that may be accessed by other systems. A client is a system which invokes queries about mobile hosts. A query server is a system which can handle mobile query processing according to the requests from clients. Each client is directly or indirectly connected to at least one query server through a global network.
7 Strategies for Query Processing in Mobile Computing 601 A mobile host server is a system which can directly communicate with all mobile hosts in the same cell through its wireless interface, and furthermore can communicate with all query servers through global networks. In Figure 3, we show an example of a network which includes clients, query servers, mobile host servers, and mobile hosts. As soon as a query server receives a query from a client, it starts to process the query. In its processing, the query server exchanges packets with any mobile host servers, mobile hosts and other systems as necessary. In this model, we have the following assumptions: The existence of each mobile host is known to all mobile host servers located in its wireless cell. This assumption can be realized bymechanisms such as beaconing, which is the periodic exchange of beacon packets. Such mechanisms are provided by several network protocols such as the ES-IS protocol [12], and by several datalink protocols such as IEEE [5]. Each mobile host server can multicast a packet to all query servers, and each query server can multicast a packet to all mobile host servers. These assumptions can be realized by a static conguration of all associated addresses at each server, or by a multicast protocol. Cells are disjoint in a logical level, that is, a mobile host belongs to at most one cell. This can be achieved by using an appropriate hand-o mechanism. A mobile host server can send a query packet to a mobile host in its cell to obtain a piece of information stored in the mobile host, if necessary. The following types of location sensitive queries are considered for mobile hosts. 1. Location (L) query: A query to obtain the location of a mobile host. Note that an L query is not concerned with whether the mobile host is active ornot. 2. Existence (E) query: A query to determine if the mobile host is active. 3. Data (D) query: A query to obtain a piece of information from a mobile host.
8 602 Chapter Comparison of query processing and communication protocols for mobile hosts Prior to proposing query processing strategies for mobile hosts, we discuss similarities and dierences between mobile communication protocols and our concerns regarding query processing for mobile hosts (hereafter we refer to this query processing as mobile query processing). In both mobile communication protocols and mobile query processing, location management of mobile hosts is very important. It is therefore natural to apply the location management schema of mobile communication protocols to those of mobile query processing. There are two basic types of actions taken by routers in mobile communication protocols: (1) Actions taken when routers detect migration of mobile hosts. (2) Actions taken when routers receive packets destined for mobile hosts. These two actions may be compared to their respective two types of actions in mobile query processing: (1) Actions taken by mobile host servers when they detect migration of mobile hosts. (2) Actions taken by query servers when they receive queries concerning mobile hosts. Based on this correspondence, basic strategies of mobile communication protocols such as broadcast of location information when a mobile host moves (BN), notication of location information to a certain system when a mobile host moves (DF/DQ), and no location management of a mobile host until a router receives a packet destined for the mobile host (BF/BQ), are applied in a straightforward manner to mobile query processing.
9 Strategies for Query Processing in Mobile Computing 603 However, we can nd some substantial dierences between mobile communication protocols and mobile query processing. First, the former concerns itself with how to forward a packet from a certain point to a mobile host, while the latter concerns itself with how to obtain a piece of information about a mobile host at a certain point. This causes a topological dierence of information ow; the ow for the former is from a certain point to a mobile host, and the ow for the latter is from a certain point returned to the point. Someone may think that mobile query processing can be achieved by combining packet forwarding from the query server to the mobile host and packet forwarding from the mobile host to the query server. Such a viewpoint is correct when the requested information is only stored at the mobile host. However, we can consider the case of systems other than the mobile host having the requested information. For instance, in mobile communication protocols, the default router has the location information in DQ and DF, and all routers have the location information in BN. If a similar distribution of information is applied to mobile query processing, it is possible for a query server to realize query processing without sending a packet to the mobile host. Consequently, the optimal strategies in mobile query processing cannot be obtained by simply combining the strategies for mobile communication protocols. Secondly, the size of a packet transmitted by a query server in mobile query processing is generally considered to be much smaller than that of a packet forwarded by a router in mobile communication protocols. The former is at most several hundreds of bytes since the packet contains only the query information sent to a mobile host. On the other hand, the latter is occasionally as much as several kilo-bytes since the packet has data requested by users and its size may become very large. According to the discussion in Section 2, querybased strategies perform better than forwarding-based strategies when the size of a packet is large. Therefore, query-based strategies are not eective in mobile query processing. From this point onwards we will not concern ourselves with query-based strategies in our search for optimal strategies in mobile query processing. The third important dierence lies in the assumptions made about their operations with special emphasis on their reliability and geographic scopes. In mobile communication protocols, it is generally desirable for a single protocol to be employed uniformly used throughout the whole global network since it is very important for many users to access the network from its arbitrary location. To meet such a requirement in a very large scale network, very high reliability of location information is necessary. For mobile query processing, a locally restricted area, such as a campus, an oce, or a manufacturing plant, should employ its own query processing strategy. This is due to the fact that users
10 604 Chapter 22 generally want to protect the databases stored in their mobile host from being accessed through the global network. Therefore, in mobile query processing, each strategy is usually used in a small restricted area where it is easy for users to nd the location information of mobile hosts within the same area. Thus, high reliability of the location information is not always necessary for each mobile query processing strategy. In all the mobile communication protocols that we surveyed, when we examine the high-reliability of location information, we see that notication is made by two systems for each migration of a mobile host. These two systems are the router that detects the existence of the mobile host and the router that detects that the mobile host is no longer in its cell. However it is possible to consider a protocol where notication is made by only one system for each migration of a mobile host. In this case, it is the router that detects the existence of the mobile host. This variation is considered to be valid in the case of mobile query processing, since it is ecient in decreasing the trac of packets and such query processing does not require high-reliability of location information. 3.3 Query processing strategies for mobile hosts Based on the discussion of the previous subsection, the ve strategies discussed in Section 2 are now applied to query processing for location sensitive queries according to the following policies: The actions of routers on migration of mobile hosts in mobile communication protocols are taken by mobile host servers in mobile query processing. The actions of routers for forwarding packets to mobile hosts in mobile communication protocols are taken by query servers for processing (L, E or D) queries in mobile query processing. Query-based strategies, such as DQ and BQ, will not be considered in mobile query processing. We consider two notication methods for handling mobility. (1) For each migration of a mobile host, notication is made by two mobile host servers, i.e., the previous neighbor mobile host server and new neighbor mobile host server. (2) For each migration of a mobile host, notication is made by a mobile host server, i.e., the new neighbor mobile host server.
11 Strategies for Query Processing in Mobile Computing 605 Now, we propose the following strategies for handling the three types of queries. Single Broadcast Notication (SBN): This strategy is based on the BN strategy for mobile communication protocols. As soon as a mobile host server newly detects the existence of a mobile host, the location information of the mobile host is broadcast to all query servers. In this case, even if the mobile host becomes inactive ormoves into another network, no query server notices that the information it holds has become obsolete until it sends a packet to the mobile host. For an L query from a client, each query server can reply directly. For an E and/or a D query, each query server cannot directly reply to the query. Therefore it must send a packet to the mobile host server according to the information it holds. For example, if the mobile host i moves from e's cell to f's in Figure 3, f noties all query servers a and b that it is newly adjacent to i. If the client c sends an L query of i to a, a immediately replies. For an E query or a D query of i, a should forward the query to f. Moreover, even if i moves out of f's cell, or it becomes inactive, f does not take any more action. In this way, each query server does not know whether the mobile host is really active inthe cell of the mobile host server which had previously notied it of the existence of the mobile host. double Broadcast Notication (WBN): This strategy is based on the BN strategy. As soon as a mobile host server newly detects the existence of a mobile host, the location information of the mobile host is broadcast to all query servers. Furthermore, when a mobile host server newly detects that a certain mobile host which had resided in its cell no longer exists in the cell, such non-existence information is broadcast to all query servers. In this case, if a mobile host has become inactive or moves into another network, each query server will notice that the information it holds on this mobile host has become obsolete, which makes it eliminate the entry. The IS-IS protocol uses this noti- cation method, and this is a popular method for routing in networks in which migration is not so frequent. Each query server can directly reply to every L query and E query. Only in the case of a D query, the query server cannot directly answer. Therefore it must send a packet to the mobile host server according to the information it holds. For example, if the mobile host i moves from e's cell to f's in Figure 3, besides f's action of notifying all query servers of the existence of i in its cell, e
12 606 Chapter 22 noties all query servers that i is no longer in its cell. Each query server, e.g., a, immediately replies to L queries as well as E queries. Only for a D query of i, a should forward it to f. Moreover, if i moves out of f's cell, or it becomes inactive, f noties all query servers that i is no longer in its cell. In this way, each query server knows whether the mobile host is really active in the cell of the mobile host server which has previously notied it of the existence of the mobile host. Broadcast Query Forwarding (BQF): This strategy is based on the BF strategy used in mobile communication protocols. No action is taken if a mobile host server newly detects the existence of a mobile host. No action is taken either even if a mobile host server detects that a certain mobile host which had resided in its cell no longer exists in the cell. Mobile information can be obtained by broadcasting a packet to all mobile host servers. Therefore, for any of L, E, and D queries, the query server broadcasts a packet to all mobile host servers. The mobile host server in whose cell the objective mobile host resides gives the answers to the query server. For example, even if the mobile host i moves from e's cell to f's in Figure 3, no action will be taken by either e or f. When a client c sends a query about i to a query server a, the server sends the contents of the query to all mobile host servers, and then the mobile host server f, in whose cell the mobile host i resides, replies to the query. Single Default Notication (SDN): This strategy is based on the DF strategy for mobile communication protocols. There exists a default server for each mobile host, and each mobile host server and each query server know which system is the default server of each mobile host beforehand. As soon as a mobile host server newly detects the existence of a mobile host, the default server is notied of the mobile host's location. In this case, if the mobile host becomes inactive or moves into another network, the default server cannot notice that the information being held has become obsolete unless it sends a packet to the mobile host. For an L query, a query server can reply by sending a query to its default server. For an E and a D query, the default server cannot reply. Therefore the default server must forward a packet to the mobile host server according to the information it holds. In Figure 4, let the systems l, m, n, and o be the default servers of the mobile hosts h, i, j, and k, respectively.
13 Strategies for Query Processing in Mobile Computing 607 a l (h) m (i) n (j) o (k) g k b Network f j cell query server c e i mobile host server client d h mobile host (x) default server of x Figure 4 A network example for SDN and WDN. If the mobile host i moves from e's cell to f's cell, f noties m, the default server of i, ofi's existence. If a query server a receives an L query of i from a client c, itasksm for the location of i, and then m replies to this query. For an E query and a D query of i, since m cannot directly answer, it forwards the query to f. Moreover, even if i moves out of the f's cell, or it becomes inactive, f does not take further action. With this strategy, the default server does not know whether the mobile host is really active in the cell of the mobile host server which had provided previous notication it of the mobile host's existence. double Default Notication (WDN): This strategy is based on the DF strategy for mobile communication protocols. There exists a default server for each mobile host, and each mobile host server and each query server know beforehand which system is the default server of each mobile host. As soon as a mobile host server newly detects the existence of a mobile host, the default server is notied of the mobile host's location. Furthermore, as soon as a mobile host server newly detects that the mobile host which had resided in one of its cell no longer exists in the cell, the default server is notied by the mobile host server
14 608 Chapter 22 that the mobile host no longer resides in its cell. In this case, if the mobile host becomes inactive or moves to another network, the default server will notice that the information being held has become obsolete. The default server will then eliminate the entry. For an L query and an E query, each query server can answer by sending a query to the default server. Only for a D query is the default server unable to reply. Therefore the default server must forward a packet to the mobile host server according to the information it holds. For example, in Figure 4, if the mobile host i moves from e's cell to f's cell, f informs m, the default server of i of i's existence. The mobile host server e also noties m when i is no longer in its cell. If a query server a receives an L query or an E query of i from a client c, it sends the query to m, andm replies to this query. Since m itself cannot directly answer a D query of i, it forwards the query to f Moreover, if i moves out of f's cell, or becomes inactive, f will notify m that i is no longer in its cell. With this strategy, the default server does know whether the mobile host is really active in the cell of the mobile host server which had provided previous notication it of the mobile host's existence. 4 EVALUATION In this section, we compare the costs of SBN, WBN, BQF, SDN, and WDN. Here we use the following parameters in our cost estimation: B (Q) x : the cost of broadcasting a packet from a query server x to all the mobile host servers. B (M) x : the cost of broadcasting a packet from a mobile host server x to all the query servers. H x;y : the cost of sending a packet between a query server x and D (Q) x;y : D (M) x;y : a mobile host server y. the cost of sending a packet between a query server x and the default server of a mobile host y. the cost of sending a packet between a mobile host server x and the default server of a mobile host y.
15 Strategies for Query Processing in Mobile Computing 609 Table 1 Cost estimates of each strategy strategy migration L query E query D query SBN WBN B (M) e B (M) f 0 2H a;f 2H a;f + B (M) f 0 0 2H a;f BQF 0 B (Q) a + H a;f B (Q) a + H a;f B (Q) a SDN D (M) f;i 2D (Q) a;i D (Q) a;i + D (M) f;i D (Q) a;i WDN D (M) e;i + D (M) f;i 2D (Q) a;i +H a;f +H a;f 2D (Q) a;i D (Q) a;i +H a;f + H a;f + D (M) f;i + D (M) f;i Table 1 shows the costs incurred by each strategy for the following cases: migration of the mobile host i as it moves from the cell of mobile host server e to the cell of the mobile host server f, query server a processing a L query and an E query, and a D query concerning i when i is in f's cell. In this table,we do not include the cost of transmitting a packet between a mobile host server and a mobile host. Now, similar to other approaches such as [3], [9], [11], [15], [18], and [23], we assume that migration intervals of each mobile host and query occurrence intervals are exponentially distributed. We also assume that the location to which each mobile host moves is randomly selected from all the possible mobile host servers. Let be the migration rate, i.e., the mean number of migrating mobile hosts in a unit time, and be the query occurrence rate, i.e., the mean number of queries occurring in a unit time. Queries are composed of of L queries, of E queries, and of D queries such that + + = 1. Let B (M) be the average of B (M) x for an arbitrary mobile host server x, B (Q) be the average of B (Q) x for an arbitrary query server x, H be the average of H x;y for an arbitrary combination of query server x and mobile host server y, D (M) be the average of D (M) x;y for an arbitrary combination of mobile host server x and mobile host y, and D (Q) be the average of D (Q) x;y for an arbitrary combination of query server x and mobile host y. The mean total cost in a unit time in each strategy is as follows:
16 610 Chapter 22 n n (*) (*) query server & mobile host server & default server for all mobile hosts query server & mobile host server Figure 5 n-grid topologies. SBN: WBN: BQF: SDN: WDN: B (M) +2H( + ) 2B (M) +2H (B (Q) + H)( + + ) D (M) +2D (Q) +(D (Q) + D (M) + H)( + ) 2D (M) +2D (Q) ( + ) +(D (Q) + D (M) + H) Now let us consider how the predominant strategy changes according to network parameters in two typical network topologies: n-grid topologies and binary tree topologies. Example 1: n-grid topologies. Consider the network topology shown by Figure 5, which is scaled by integer n. Here the default server for each mobile host is the most central server if n is odd, and one of the central four servers if n is even. All servers are mobile host servers. The cost is estimated by counting the hops between servers. Packet broadcast is ecient if a certain dynamic spanning tree algorithm is used. B; H, andd are expressed as follows: B (Q) = B (M) = n 2 0 1
17 Strategies for Query Processing in Mobile Computing 611 H = D (Q) = D (M) = 8 < : 2(n 0 1)(n +1) 3n (n + 1)(n 0 1) 2n n 2 (n :odd) (n :even) A campus network is a typical example of n-grid topology since it usually ranges geographically over the campus. A grid topology is often used as a typical topology for OSI networks because a dynamic routing protocol, the IS-IS protocol, can be eciently used in networks that include many highlymultiplexed paths, which are typical of a grid topology. First, we show how these three types of queries aect the total cost. Figure 6, Figure 7, and Figure 8 respectively illustrate the total costs per move for given query/migration ratio in three extreme cases, (1) =1, =0, =0, and n = 3, 10, (2) = 0, = 1, = 0, and n = 3, 10, and (3) = 0, = 0, = 1, and n = 3, 10. In these gures, the horizontal axes are the query/migration ratio =, and the vertical axes are the total cost per move. Note that query/migration ratio is similar to the call/mobility ratio in [9]. According to the query/migration ratio, the optimal strategy becomes (1) BQF, SDN, or SBN for L queries, (2) BQF, WDN, or WBN for E queries, and (3) BQF, SDN, or SBN for D queries. Next we seecomplex cases of three types of queries. The total costs for the cases = 0:2, = 0:2, = 0:6, and n = 3, 10 are illustrated in Figure 9. By this gure, we can see that, in both cases n = 3 and n = 10, an arbitrary strategy can be optimal according to the query/migration ratio. For a given query/migration ratio and a given network scale n, the domain in which each strategy is optimal is illustrated by Figure 10. We can see by this gure that all strategies can be optimal according to the query/mobility ratio and the network scale n. BQF is better than the others if migration is assumed to be frequent, while SBN or WBN are best used if the occurrence of queries is assumed to be frequent. Default-based strategies SDN and WDN are more scalable than broadcast-based strategies. The costs for SDN, WDN are O(n), while those for SBN, WBN, and BQF are O(n 2 ). From this comparison we can say that broadcast-based strategies are not appropriate for a large scale network. Example 2 : binary tree topologies (depth n). Consider the network topology shown in Figure 11, which is scaled by integer n. Here the default
18 612 Chapter 22 Total Cost 60 BQF n =3 WDN SDN 30 WBN SBN Query/Migration Ratio Total Cost 400 BQF n = WBN WDN SDN SBN Query/Migration Ratio Figure 6 Total cost comparison of an n-grid topology for L queries.
19 Strategies for Query Processing in Mobile Computing 613 Total Cost 60 BQF SDN SBN n =3 WDN 30 WBN Query/Migration Ratio n =10 Total Cost 400 BQF SBN 200 SDN WBN WDN Query/Migration Ratio Figure 7 Total cost comparison of an n-grid topology for E queries.
20 614 Chapter 22 Total Cost 60 BQF n =3 WBN WDN 30 SBN SDN Query/Migration Ratio Total Cost 400 BQF WBN n =10 SBN 200 WDN SDN Query/Migration Ratio Figure 8 Total cost comparison of an n-grid topology for D queries.
21 Strategies for Query Processing in Mobile Computing 615 Total Cost 60 BQF SDN n =3 WDN WBN SBN Query/Migration Ratio Total Cost 400 BQF n =10 WBN 200 SBN SDN WDN Query/Migration Ratio Figure 9 Total cost comparison of an n-grid topology for case = 0:2; = 0:2; =0:6.
22 616 Chapter 22 Network Scale n 10 WDN SDN 5 BQF 2 SBN 0 10 WBN Query/Migration Ratio Figure 10 Optimal strategy for n-grid topologies. (*) n (*) default server for all mobile hosts query server & mobile host server Figure 11 Binary tree topologies.
23 Strategies for Query Processing in Mobile Computing 617 Network Scale n 10 WDN 5 SDN BQF 2 SBN 0 10 WBN Query/Migration Ratio Figure 12 Optimal strategy for binary tree topologies. server for each mobile host is the root of the tree. Leaf systems are mobile host servers as well as query servers. A wide area network is a typical example of a binary tree topology. The internet, with its hierarchical construction rooted from a single backbone, is based on a binary tree topology. This topology is appropriate for the manual conguration of routing tables since there is no possibility of packet looping and no alternative choices of the forwarding direction for a given destination. The cost is estimated from the hop countbetween servers. Here we assume that queries are invoked randomly by each mobile host. B, H, and D are expressed as follows: B (Q) = B (M) =2 n 0 2 H =2(n 0 2) n D (Q) = D (M) = n 0 1 When we assume = 0:3, = 0:2, and = 0:5, the optimal strategy for a given n and the query/migration ratio is shown in Figure 12. We can see from this gure that all strategies can be optimal according to n and query/migration ratio.
24 618 Chapter 22 We can also see a similarity to grid topology in this case. Since broadcasting costs O(2 n ) in this case, the tendency in scalability is more conspicuous. 5 CONCLUSION In this paper, we have discussed three types of queries L, E, and D for dealing with mobile hosts and have shown ve strategies SBN, WBN, BQF, SDN, and WDN for query processing. We have analytically compared their performance from a network cost point of view and shown how the optimal strategies vary according to the conditions such as the migration rate of the mobile hosts, the query occurrence rate, and the scale of the network. The comparison was carried out for two typical network topologies: grid topology and tree topology. As a result of this paper, we could say that implementing all these strategies enables mobile users to select the optimal strategy when the network conditions for each user dier. The scope of this paper has been fundamental strategies. Several advanced techniques, such as cache, interception [18], hierarchical server [2] or pointer [9], were not taken into account in the cost analysis. The evaluation of the strategies using the abovementioned techniques is one of our important future research issues. REFERENCES [1] Alonso, R. and Korth, H.F., \Database System Issues in Nomadic Computing," Proc. of ACM-SIGMOD'93, pp , [2] Awerbuch, B. and Peleg, D., \ConcurrentOnline Tracking of Mobile User," Proc. of ACM-SIGCOMM'91, pp , [3] Bar-Noy, A., Kessler, I., and Sidi, M., \Mobile Users: To Update or not to Update," Proc. of IEEE INFOCOM'94, pp , [4] Carlberg, K.G., \A Routing Architecture That Supports Mobile End Systems," Proc. of IEEE MILCOM'92, pp , 1992.
25 Strategies for Query Processing in Mobile Computing 619 [5] Dieplstraten, W., Ennis, G., and Belanger, P., \DFWMAC: Distributed Foundation Wireless Medium Access Control," IEEE P /190, [6] Forman, G.H. and Zahorjian, J., \The Challenges of Mobile Computing, IEEE COMPUTER," Vol.27, No.4, pp.38-47, [7] Hahn, J.J. and Stolle, D.D., \Packet Radio Network Algorithms: A Survey," IEEE Communications Magazine, Vol.22, No.11, pp.41-47, [8] Ioannidis, J., Duchamp, D. and Maguire Jr., G.Q., \IP-based Protocols for Mobile Internetworking," Proc. ACM-SIGCOMM'91, pp , [9] Imielinski, T. and Badrinath, B.R., \Querying in Highly Mobile Distributed Environments," Proc. of VLDB'92, pp.41-52, [10] Imielinski, T. and Badrinath, B.R., \Data Management for Mobile Computing," ACM SIGMOD RECORD, Vol.22, No.1, pp.34-39, [11] Imielinski, T. and Badrinath, B.R., \Mobile Wireless Computing: Solutions and Challenges in Data Management," Technical Report DCS-TR- 296, Department of Computer Science, Rutgars University, [12] ISO 9542, \Information Processing Systems - Telecommunications and Information Exchange between Systems - End System to Intermediate System Routeing Exchange Protocol for Use in Conjunction with the Protocol for Providing the Connectionless-mode Network Service (ISO 8473)," [13] ISO/IEC 10589, \Information Technology - Telecommunications and Information Exchange between Systems - Intermediate System to Intermediate System Intra-Domain Routeing Information Exchange Protocol for Use in Conjunction with the Protocol for Providing the Connectionless-mode Network Service (ISO 8473)," [14] Korth, H.F. and Imielinski, T., \Mobile Computing: Fertile Research Area or Black Hole?," Proc. of VLDB'93, pp , [15] Madhow, U., Honig, M.L. and Steiglitz, K., \Optimization of Wireless Resources for Personal Communications MobilityTracking," Proc. of IEEE INFOCOM'94, pp , [16] Moy, J., \OSPF Version 2," RFC 1583, [17] Perkins, C.E. and Bhagwat, R., \A Mobile Networking System based on Internet Protocol," IEEE Personal Communication, Vol.1, No.1, pp.32-41, 1994.
26 620 Chapter 22 [18] Tanaka, R. and Tsukamoto, M., \A CLNP-based Protocol for Mobile End Systems within an Area," Proc. of IEEE International Conference on Network Protocols, pp.64-71, [19] Teraoka, F., Yokote, Y., and Tokoro, M., \A Network Architecture Providing Host Migration Transparency," Proc. of ACM-SIGCOMM'91, pp.45-65, [20] Tsukamoto, M. and Tanaka, R., \A Routeing Protocol for Wide Area Migration using Default Address and Remaining Lifetime Parameter," IPSJ- DPS-Report 58-3, pp.17-24, 1992 (in Japanese). [21] Tsukamoto, M., Tanaka, R., and Tsumori, O., \Supporting ES-Migration within Areas in CLNP Networks," IPSJ-DPS-Report 61-30, pp , 1993 (in Japanese). [22] Wada, H., Yozawa, T., Ohnishi, T., and Tanaka, Y., \Mobile Computing Environment Based on Internet Packet Forwarding," Proc. of 1993 Winter USENIX, pp , [23] Yuan, R., \Trac Pattern Based Mobile Routing Scheme," Computer Communications, Vol.18, No.1, pp.32-36, 1995.
An Adaptive Routing Scheme for Wireless Mobile Computing
 An Adaptive Routing Scheme for Wireless Mobile Computing Ruixi Yuan C&C Software Technology Center, NEC Systems Laboratory, Inc. 1901 Gateway Drive, Irving, TX 75038 yuan@syl.dl.nec.com Abstract This paper
An Adaptive Routing Scheme for Wireless Mobile Computing Ruixi Yuan C&C Software Technology Center, NEC Systems Laboratory, Inc. 1901 Gateway Drive, Irving, TX 75038 yuan@syl.dl.nec.com Abstract This paper
Ubiquitous Mobile Host Internetworking
 Ubiquitous Mobile Host Internetworking David B. Johnson School of Computer Science Carnegie Mellon University Pittsburgh, PA 152 13-389 1 dbj Qcs. cmu. edu 1. Introduction With the increasing popularity
Ubiquitous Mobile Host Internetworking David B. Johnson School of Computer Science Carnegie Mellon University Pittsburgh, PA 152 13-389 1 dbj Qcs. cmu. edu 1. Introduction With the increasing popularity
Mobile host protocols support host
 INTERNATIONAL JOURNAL OF NETWORK MANAGEMENT Int. J. Network Mgmt 2000; 10:191 214 Location update and routing scheme for a mobile computing environment By Anna Hać Ł and Yujing Huang We present a new hierarchical
INTERNATIONAL JOURNAL OF NETWORK MANAGEMENT Int. J. Network Mgmt 2000; 10:191 214 Location update and routing scheme for a mobile computing environment By Anna Hać Ł and Yujing Huang We present a new hierarchical
Data gathering using mobile agents for reducing traffic in dense mobile wireless sensor networks
 Mobile Information Systems 9 (23) 295 34 295 DOI.3233/MIS-364 IOS Press Data gathering using mobile agents for reducing traffic in dense mobile wireless sensor networks Keisuke Goto, Yuya Sasaki, Takahiro
Mobile Information Systems 9 (23) 295 34 295 DOI.3233/MIS-364 IOS Press Data gathering using mobile agents for reducing traffic in dense mobile wireless sensor networks Keisuke Goto, Yuya Sasaki, Takahiro
Evaluating the Performance of Mobile Agent-Based Message Communication among Mobile Hosts in Large Ad Hoc Wireless Network
 Evaluating the Performance of Mobile Agent-Based Communication among Mobile Hosts in Large Ad Hoc Wireless Network S. Bandyopadhyay Krishna Paul PricewaterhouseCoopers Limited Techna Digital Systems Sector
Evaluating the Performance of Mobile Agent-Based Communication among Mobile Hosts in Large Ad Hoc Wireless Network S. Bandyopadhyay Krishna Paul PricewaterhouseCoopers Limited Techna Digital Systems Sector
Supporting IP Multicast for Mobile Hosts. Yu Wang Weidong Chen. Southern Methodist University. May 8, 1998.
 Supporting IP Multicast for Mobile Hosts Yu Wang Weidong Chen Southern Methodist University fwy,wcheng@seas.smu.edu May 8, 1998 Abstract IP Multicast is an ecient mechanism of delivering a large amount
Supporting IP Multicast for Mobile Hosts Yu Wang Weidong Chen Southern Methodist University fwy,wcheng@seas.smu.edu May 8, 1998 Abstract IP Multicast is an ecient mechanism of delivering a large amount
Variable Length and Dynamic Addressing for Mobile Ad Hoc Networks
 Variable Length and Dynamic Addressing for Mobile Ad Hoc Networks Som Chandra Neema Venkata Nishanth Lolla {sneema,vlolla}@cs.ucr.edu Computer Science Department University of California, Riverside Abstract
Variable Length and Dynamic Addressing for Mobile Ad Hoc Networks Som Chandra Neema Venkata Nishanth Lolla {sneema,vlolla}@cs.ucr.edu Computer Science Department University of California, Riverside Abstract
Energy-Efficient Mobile Cache Invalidation
 Distributed and Parallel Databases 6, 351 372 (1998) c 1998 Kluwer Academic Publishers. Manufactured in The Netherlands. Energy-Efficient Mobile Cache Invalidation KUN-LUNG WU, PHILIP S. YU AND MING-SYAN
Distributed and Parallel Databases 6, 351 372 (1998) c 1998 Kluwer Academic Publishers. Manufactured in The Netherlands. Energy-Efficient Mobile Cache Invalidation KUN-LUNG WU, PHILIP S. YU AND MING-SYAN
A System and Trac Dependent Adaptive Routing. Algorithm for Ad Hoc Networks 1. neighbor which leads to a shortest path to the destination.
 A System and Trac Dependent Adaptive Routing Algorithm for Ad Hoc Networks 1 Piyush Gupta 2 and P. R. Kumar 3 Abstract An ad hoc network consists of a number of mobile hosts who communicate with each other
A System and Trac Dependent Adaptive Routing Algorithm for Ad Hoc Networks 1 Piyush Gupta 2 and P. R. Kumar 3 Abstract An ad hoc network consists of a number of mobile hosts who communicate with each other
A Location-based Directional Route Discovery (LDRD) Protocol in Mobile Ad-hoc Networks
 A Location-based Directional Route Discovery (LDRD) Protocol in Mobile Ad-hoc Networks Stephen S. Yau, Wei Gao, and Dazhi Huang Dept. of Computer Science and Engineering Arizona State University Tempe,
A Location-based Directional Route Discovery (LDRD) Protocol in Mobile Ad-hoc Networks Stephen S. Yau, Wei Gao, and Dazhi Huang Dept. of Computer Science and Engineering Arizona State University Tempe,
VANS: Visual Ad hoc Network Simulator
 VANS: Visual Ad hoc Network Simulator Masako Shinohara, Hideki Hayashi, Takahiro Hara, Akimitsu Kanzaki and Shojiro Nishio Graduate School of Information Science and Tech., Osaka University {sinohara.masako,
VANS: Visual Ad hoc Network Simulator Masako Shinohara, Hideki Hayashi, Takahiro Hara, Akimitsu Kanzaki and Shojiro Nishio Graduate School of Information Science and Tech., Osaka University {sinohara.masako,
A Mobile Networking System based on Internet. Computer Science Department IBM, T.J. Watson Research Center. University of Maryland Hawthorne, NY 10562
 A Mobile Networking System based on Internet Protocol(IP) Pravin Bhagwat Charles E. Perkins pravin@cs.umd.edu perk@watson.ibm.com Computer Science Department IBM, T.J. Watson Research Center University
A Mobile Networking System based on Internet Protocol(IP) Pravin Bhagwat Charles E. Perkins pravin@cs.umd.edu perk@watson.ibm.com Computer Science Department IBM, T.J. Watson Research Center University
The Interconnection Structure of. The Internet. EECC694 - Shaaban
 The Internet Evolved from the ARPANET (the Advanced Research Projects Agency Network), a project funded by The U.S. Department of Defense (DOD) in 1969. ARPANET's purpose was to provide the U.S. Defense
The Internet Evolved from the ARPANET (the Advanced Research Projects Agency Network), a project funded by The U.S. Department of Defense (DOD) in 1969. ARPANET's purpose was to provide the U.S. Defense
CS5984 Mobile Computing
 CS5984 Mobile Computing Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Part II 1 Outline Routing Protocols for Ad hoc Networks DSDV: Highly Dynamic Destination-Sequenced Distance- Vector
CS5984 Mobile Computing Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Part II 1 Outline Routing Protocols for Ad hoc Networks DSDV: Highly Dynamic Destination-Sequenced Distance- Vector
Introduction to Mobile Ad hoc Networks (MANETs)
 Introduction to Mobile Ad hoc Networks (MANETs) 1 Overview of Ad hoc Network Communication between various devices makes it possible to provide unique and innovative services. Although this inter-device
Introduction to Mobile Ad hoc Networks (MANETs) 1 Overview of Ad hoc Network Communication between various devices makes it possible to provide unique and innovative services. Although this inter-device
CACHING IN WIRELESS SENSOR NETWORKS BASED ON GRIDS
 International Journal of Wireless Communications and Networking 3(1), 2011, pp. 7-13 CACHING IN WIRELESS SENSOR NETWORKS BASED ON GRIDS Sudhanshu Pant 1, Naveen Chauhan 2 and Brij Bihari Dubey 3 Department
International Journal of Wireless Communications and Networking 3(1), 2011, pp. 7-13 CACHING IN WIRELESS SENSOR NETWORKS BASED ON GRIDS Sudhanshu Pant 1, Naveen Chauhan 2 and Brij Bihari Dubey 3 Department
1 Multipath Node-Disjoint Routing with Backup List Based on the AODV Protocol
 1 Multipath Node-Disjoint Routing with Backup List Based on the AODV Protocol Vahid Zangeneh i and Shahriar Mohammadi ii * ABSTRACT In recent years, routing has been the most focused area in ad hoc networks
1 Multipath Node-Disjoint Routing with Backup List Based on the AODV Protocol Vahid Zangeneh i and Shahriar Mohammadi ii * ABSTRACT In recent years, routing has been the most focused area in ad hoc networks
An Adaptive Query Processing Method according to System Environments in Database Broadcasting Systems
 An Query Processing Method according to System Environments in Database Broadcasting Systems M. KASHITA T. TERADA T. HARA Graduate School of Engineering, Cybermedia Center, Graduate School of Information
An Query Processing Method according to System Environments in Database Broadcasting Systems M. KASHITA T. TERADA T. HARA Graduate School of Engineering, Cybermedia Center, Graduate School of Information
Providing Seamless Communication in Mobile. Bikram S. Bakshi P. Krishna D. K. Pradhan N. H. Vaidya. Texas A&M University
 Providing Seamless Communication in Mobile Wireless Networks Bikram S. Bakshi P. Krishna D. K. Pradhan N. H. Vaidya Department of Computer Science Texas A&M University College Station, TX 77843-3112 E-mail:
Providing Seamless Communication in Mobile Wireless Networks Bikram S. Bakshi P. Krishna D. K. Pradhan N. H. Vaidya Department of Computer Science Texas A&M University College Station, TX 77843-3112 E-mail:
A Graph-based Approach to Compute Multiple Paths in Mobile Ad Hoc Networks
 A Graph-based Approach to Compute Multiple Paths in Mobile Ad Hoc Networks Gunyoung Koh, Duyoung Oh 1 and Heekyoung Woo 2 1 School of Electrical Engineering and Computer Science Seoul National University,
A Graph-based Approach to Compute Multiple Paths in Mobile Ad Hoc Networks Gunyoung Koh, Duyoung Oh 1 and Heekyoung Woo 2 1 School of Electrical Engineering and Computer Science Seoul National University,
TR Virtual Cell in Mobile Computer Communications. Kyungshik Lim and Yann-Hang Lee. University of Florida
 TR94-020 Virtual Cell in Mobile Computer Communications Kyungshik Lim and Yann-Hang Lee Computer and Information Sciences Department University of Florida Gainesville, FL 32611 Abstract This paper describes
TR94-020 Virtual Cell in Mobile Computer Communications Kyungshik Lim and Yann-Hang Lee Computer and Information Sciences Department University of Florida Gainesville, FL 32611 Abstract This paper describes
A COMPARISON OF REACTIVE ROUTING PROTOCOLS DSR, AODV AND TORA IN MANET
 ISSN: 2278 1323 All Rights Reserved 2016 IJARCET 296 A COMPARISON OF REACTIVE ROUTING PROTOCOLS DSR, AODV AND TORA IN MANET Dr. R. Shanmugavadivu 1, B. Chitra 2 1 Assistant Professor, Department of Computer
ISSN: 2278 1323 All Rights Reserved 2016 IJARCET 296 A COMPARISON OF REACTIVE ROUTING PROTOCOLS DSR, AODV AND TORA IN MANET Dr. R. Shanmugavadivu 1, B. Chitra 2 1 Assistant Professor, Department of Computer
source3 Backbone s1 s2 R2 R3
 Fast and Optimal Multicast-Server Selection Based on Receivers' Preference Akihito Hiromori 1, Hirozumi Yamaguchi 1,Keiichi Yasumoto 2, Teruo Higashino 1, and Kenichi Taniguchi 1 1 Graduate School of Engineering
Fast and Optimal Multicast-Server Selection Based on Receivers' Preference Akihito Hiromori 1, Hirozumi Yamaguchi 1,Keiichi Yasumoto 2, Teruo Higashino 1, and Kenichi Taniguchi 1 1 Graduate School of Engineering
Charles Perkins Nokia Research Center 2 July Mobility Support in IPv6 <draft-ietf-mobileip-ipv6-14.txt> Status of This Memo
 IETF Mobile IP Working Group INTERNET-DRAFT David B. Johnson Rice University Charles Perkins Nokia Research Center 2 July 2000 Mobility Support in IPv6 Status of This
IETF Mobile IP Working Group INTERNET-DRAFT David B. Johnson Rice University Charles Perkins Nokia Research Center 2 July 2000 Mobility Support in IPv6 Status of This
Localized and Incremental Monitoring of Reverse Nearest Neighbor Queries in Wireless Sensor Networks 1
 Localized and Incremental Monitoring of Reverse Nearest Neighbor Queries in Wireless Sensor Networks 1 HAI THANH MAI AND MYOUNG HO KIM Department of Computer Science Korea Advanced Institute of Science
Localized and Incremental Monitoring of Reverse Nearest Neighbor Queries in Wireless Sensor Networks 1 HAI THANH MAI AND MYOUNG HO KIM Department of Computer Science Korea Advanced Institute of Science
A Comparative study of On-Demand Data Delivery with Tables Driven and On-Demand Protocols for Mobile Ad-Hoc Network
 A Comparative study of On-Demand Data Delivery with Tables Driven and On-Demand Protocols for Mobile Ad-Hoc Network Humayun Bakht Research Fellow, London School of Commerce, United Kingdom humayunbakht@yahoo.co.uk
A Comparative study of On-Demand Data Delivery with Tables Driven and On-Demand Protocols for Mobile Ad-Hoc Network Humayun Bakht Research Fellow, London School of Commerce, United Kingdom humayunbakht@yahoo.co.uk
crossing disconnected Fixed Host Base Station Fixed Host Fixed Host Fixed Host High Speed Wireful Network Base Station Base Station Fixed Host
 MOBILE COMPUTING and DATABASES: ANYTHING NEW? Margaret H. Dunham Dept of Computer Science and Engineering Southern Methodist University mhd@seas.smu.edu Abdelsalam (Sumi) Helal Dept of Computer Science
MOBILE COMPUTING and DATABASES: ANYTHING NEW? Margaret H. Dunham Dept of Computer Science and Engineering Southern Methodist University mhd@seas.smu.edu Abdelsalam (Sumi) Helal Dept of Computer Science
Hierarchical Low Power Consumption Technique with Location Information for Sensor Networks
 Hierarchical Low Power Consumption Technique with Location Information for Sensor Networks Susumu Matsumae Graduate School of Science and Engineering Saga University Saga 840-8502, Japan Fukuhito Ooshita
Hierarchical Low Power Consumption Technique with Location Information for Sensor Networks Susumu Matsumae Graduate School of Science and Engineering Saga University Saga 840-8502, Japan Fukuhito Ooshita
Dynamic Source Routing in ad hoc wireless networks
 Dynamic Source Routing in ad hoc wireless networks David B. Johnson David A. Maltz Computer Science Department Carnegie Mellon University In Mobile Computing, vol. 353, chapter 5, T. Imielinski and H.
Dynamic Source Routing in ad hoc wireless networks David B. Johnson David A. Maltz Computer Science Department Carnegie Mellon University In Mobile Computing, vol. 353, chapter 5, T. Imielinski and H.
AODV-PA: AODV with Path Accumulation
 -PA: with Path Accumulation Sumit Gwalani Elizabeth M. Belding-Royer Department of Computer Science University of California, Santa Barbara fsumitg, ebeldingg@cs.ucsb.edu Charles E. Perkins Communications
-PA: with Path Accumulation Sumit Gwalani Elizabeth M. Belding-Royer Department of Computer Science University of California, Santa Barbara fsumitg, ebeldingg@cs.ucsb.edu Charles E. Perkins Communications
Enhancing the Performance of Mobile Ad Hoc Networks with the Aid of Internet Gateways 1
 Enhancing the Performance of Mobile Ad Hoc Networks with the Aid of Internet Gateways 1 Shiv Mehra and Chansu Yu Department of Electrical and Computer Engineering Cleveland State University E-mail: {s.mehra,c.yu91}@csuohio.edu
Enhancing the Performance of Mobile Ad Hoc Networks with the Aid of Internet Gateways 1 Shiv Mehra and Chansu Yu Department of Electrical and Computer Engineering Cleveland State University E-mail: {s.mehra,c.yu91}@csuohio.edu
A COMPARISON OF IMPROVED AODV ROUTING PROTOCOL BASED ON IEEE AND IEEE
 Journal of Engineering Science and Technology Vol. 4, No. 2 (2009) 132-141 School of Engineering, Taylor s University College A COMPARISON OF IMPROVED AODV ROUTING PROTOCOL BASED ON IEEE 802.11 AND IEEE
Journal of Engineering Science and Technology Vol. 4, No. 2 (2009) 132-141 School of Engineering, Taylor s University College A COMPARISON OF IMPROVED AODV ROUTING PROTOCOL BASED ON IEEE 802.11 AND IEEE
Routing Protocols in MANET: Comparative Study
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 7, July 2014, pg.119
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 7, July 2014, pg.119
Table of Contents. Cisco Introduction to EIGRP
 Table of Contents Introduction to EIGRP...1 Introduction...1 Before You Begin...1 Conventions...1 Prerequisites...1 Components Used...1 What is IGRP?...2 What is EIGRP?...2 How Does EIGRP Work?...2 EIGRP
Table of Contents Introduction to EIGRP...1 Introduction...1 Before You Begin...1 Conventions...1 Prerequisites...1 Components Used...1 What is IGRP?...2 What is EIGRP?...2 How Does EIGRP Work?...2 EIGRP
A Comparative Analysis of Pro-active Routing Protocols in MANET
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 6, June 2014, pg.144
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 6, June 2014, pg.144
A Review of Reactive, Proactive & Hybrid Routing Protocols for Mobile Ad Hoc Network
 ShriRam College of Engineering & Management 1 A Review of Reactive, Proactive & Hybrid Routing Protocols for Mobile Ad Hoc Network M.Ramaiya Rohit Gupta Rachit Jain Head,Dept. Computer Science Dept. Computer
ShriRam College of Engineering & Management 1 A Review of Reactive, Proactive & Hybrid Routing Protocols for Mobile Ad Hoc Network M.Ramaiya Rohit Gupta Rachit Jain Head,Dept. Computer Science Dept. Computer
Throughput Analysis of Many to One Multihop Wireless Mesh Ad hoc Network
 Throughput Analysis of Many to One Multihop Wireless Mesh Ad hoc Network Dr.S.Senthil Kumar,Assistant Professor, Dept of Electrical and Electronics Engineering, Government College of Engineering, Salem,India
Throughput Analysis of Many to One Multihop Wireless Mesh Ad hoc Network Dr.S.Senthil Kumar,Assistant Professor, Dept of Electrical and Electronics Engineering, Government College of Engineering, Salem,India
Performance Evaluation of Mesh - Based Multicast Routing Protocols in MANET s
 Performance Evaluation of Mesh - Based Multicast Routing Protocols in MANET s M. Nagaratna Assistant Professor Dept. of CSE JNTUH, Hyderabad, India V. Kamakshi Prasad Prof & Additional Cont. of. Examinations
Performance Evaluation of Mesh - Based Multicast Routing Protocols in MANET s M. Nagaratna Assistant Professor Dept. of CSE JNTUH, Hyderabad, India V. Kamakshi Prasad Prof & Additional Cont. of. Examinations
Dynamic Routing Tables Using Simple Balanced. Search Trees
 Dynamic Routing Tables Using Simple Balanced Search Trees Y.-K. Chang and Y.-C. Lin Department of Computer Science and Information Engineering National Cheng Kung University Tainan, Taiwan R.O.C. ykchang@mail.ncku.edu.tw
Dynamic Routing Tables Using Simple Balanced Search Trees Y.-K. Chang and Y.-C. Lin Department of Computer Science and Information Engineering National Cheng Kung University Tainan, Taiwan R.O.C. ykchang@mail.ncku.edu.tw
AN EFFICIENT MAC PROTOCOL FOR SUPPORTING QOS IN WIRELESS SENSOR NETWORKS
 AN EFFICIENT MAC PROTOCOL FOR SUPPORTING QOS IN WIRELESS SENSOR NETWORKS YINGHUI QIU School of Electrical and Electronic Engineering, North China Electric Power University, Beijing, 102206, China ABSTRACT
AN EFFICIENT MAC PROTOCOL FOR SUPPORTING QOS IN WIRELESS SENSOR NETWORKS YINGHUI QIU School of Electrical and Electronic Engineering, North China Electric Power University, Beijing, 102206, China ABSTRACT
Growth. Individual departments in a university buy LANs for their own machines and eventually want to interconnect with other campus LANs.
 Internetworking Multiple networks are a fact of life: Growth. Individual departments in a university buy LANs for their own machines and eventually want to interconnect with other campus LANs. Fault isolation,
Internetworking Multiple networks are a fact of life: Growth. Individual departments in a university buy LANs for their own machines and eventually want to interconnect with other campus LANs. Fault isolation,
Optimized Paging Cache Mappings for efficient location management Hyun Jun Lee, Myoung Chul Jung, and Jai Yong Lee
 Optimized Paging Cache Mappings for efficient location management Hyun Jun Lee, Myoung Chul Jung, and Jai Yong Lee Abstract Cellular IP maintains distributed cache for location management and routing purposes.
Optimized Paging Cache Mappings for efficient location management Hyun Jun Lee, Myoung Chul Jung, and Jai Yong Lee Abstract Cellular IP maintains distributed cache for location management and routing purposes.
Lecture 2. Computer Networks Models. Network Models 1-1
 Lecture 2 Computer Networks Models Network Models 1-1 Agenda Introduction to the Internet Reference Models for Computer Networks The OSI Model The TCP/IP Model Network Models 1-2 Announcements Bonus -
Lecture 2 Computer Networks Models Network Models 1-1 Agenda Introduction to the Internet Reference Models for Computer Networks The OSI Model The TCP/IP Model Network Models 1-2 Announcements Bonus -
A FORWARDING CACHE VLAN PROTOCOL (FCVP) IN WIRELESS NETWORKS
 A FORWARDING CACHE VLAN PROTOCOL (FCVP) IN WIRELESS NETWORKS Tzu-Chiang Chiang,, Ching-Hung Yeh, Yueh-Min Huang and Fenglien Lee Department of Engineering Science, National Cheng-Kung University, Taiwan,
A FORWARDING CACHE VLAN PROTOCOL (FCVP) IN WIRELESS NETWORKS Tzu-Chiang Chiang,, Ching-Hung Yeh, Yueh-Min Huang and Fenglien Lee Department of Engineering Science, National Cheng-Kung University, Taiwan,
DYNAMIC SEARCH TECHNIQUE USED FOR IMPROVING PASSIVE SOURCE ROUTING PROTOCOL IN MANET
 DYNAMIC SEARCH TECHNIQUE USED FOR IMPROVING PASSIVE SOURCE ROUTING PROTOCOL IN MANET S. J. Sultanuddin 1 and Mohammed Ali Hussain 2 1 Department of Computer Science Engineering, Sathyabama University,
DYNAMIC SEARCH TECHNIQUE USED FOR IMPROVING PASSIVE SOURCE ROUTING PROTOCOL IN MANET S. J. Sultanuddin 1 and Mohammed Ali Hussain 2 1 Department of Computer Science Engineering, Sathyabama University,
NetWare Link-Services Protocol
 44 CHAPTER Chapter Goals Describe the Network Link-Service Protocol. Describe routing with NLSP. Describe the data packet used by NLSP. Background The (NLSP) is a link-state routing protocol from Novell
44 CHAPTER Chapter Goals Describe the Network Link-Service Protocol. Describe routing with NLSP. Describe the data packet used by NLSP. Background The (NLSP) is a link-state routing protocol from Novell
Analysis of Multiple Trees on Path Discovery for Beacon-Based Routing Protocols
 Analysis of Multiple Trees on Path Discovery for Beacon-Based Routing Protocols Baruch Awerbuch, David Holmer and Herbert Rubens Johns Hopkins University Department of Computer Science Baltimore, MD, USA
Analysis of Multiple Trees on Path Discovery for Beacon-Based Routing Protocols Baruch Awerbuch, David Holmer and Herbert Rubens Johns Hopkins University Department of Computer Science Baltimore, MD, USA
A Distributed Routing Algorithm for Supporting Connection-Oriented Service in Wireless Networks with Time-Varying Connectivity
 A Distributed Routing Algorithm for Supporting Connection-Oriented Service in Wireless Networks with Time-Varying Connectivity Anastassios Michail Department of Electrical Engineering and Institute for
A Distributed Routing Algorithm for Supporting Connection-Oriented Service in Wireless Networks with Time-Varying Connectivity Anastassios Michail Department of Electrical Engineering and Institute for
Performance Analysis of MANET Routing Protocols OLSR and AODV
 VOL. 2, NO. 3, SEPTEMBER 211 Performance Analysis of MANET Routing Protocols OLSR and AODV Jiri Hosek Faculty of Electrical Engineering and Communication, Brno University of Technology Email: hosek@feec.vutbr.cz
VOL. 2, NO. 3, SEPTEMBER 211 Performance Analysis of MANET Routing Protocols OLSR and AODV Jiri Hosek Faculty of Electrical Engineering and Communication, Brno University of Technology Email: hosek@feec.vutbr.cz
End-To-End Delay Optimization in Wireless Sensor Network (WSN)
 Shweta K. Kanhere 1, Mahesh Goudar 2, Vijay M. Wadhai 3 1,2 Dept. of Electronics Engineering Maharashtra Academy of Engineering, Alandi (D), Pune, India 3 MITCOE Pune, India E-mail: shweta.kanhere@gmail.com,
Shweta K. Kanhere 1, Mahesh Goudar 2, Vijay M. Wadhai 3 1,2 Dept. of Electronics Engineering Maharashtra Academy of Engineering, Alandi (D), Pune, India 3 MITCOE Pune, India E-mail: shweta.kanhere@gmail.com,
Minimizing the Routing Delay in Ad Hoc Networks through Route-Cache TTL Optimization
 Minimizing the Routing Delay in Ad Hoc Networks through Route-Cache TTL Optimization Ben Liang and Zygmunt J. Haas School of Electrical and Computer Engineering, Cornell University, Ithaca, NY 14853, USA
Minimizing the Routing Delay in Ad Hoc Networks through Route-Cache TTL Optimization Ben Liang and Zygmunt J. Haas School of Electrical and Computer Engineering, Cornell University, Ithaca, NY 14853, USA
Egemen Tanin, Tahsin M. Kurc, Cevdet Aykanat, Bulent Ozguc. Abstract. Direct Volume Rendering (DVR) is a powerful technique for
 Comparison of Two Image-Space Subdivision Algorithms for Direct Volume Rendering on Distributed-Memory Multicomputers Egemen Tanin, Tahsin M. Kurc, Cevdet Aykanat, Bulent Ozguc Dept. of Computer Eng. and
Comparison of Two Image-Space Subdivision Algorithms for Direct Volume Rendering on Distributed-Memory Multicomputers Egemen Tanin, Tahsin M. Kurc, Cevdet Aykanat, Bulent Ozguc Dept. of Computer Eng. and
3. Evaluation of Selected Tree and Mesh based Routing Protocols
 33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
An Adaptive Self-Organization Protocol for Wireless Sensor Networks
 An Adaptive Self-Organization Protocol for Wireless Sensor Networks Kil-Woong Jang 1 and Byung-Soon Kim 2 1 Dept. of Mathematical and Information Science, Korea Maritime University 1 YeongDo-Gu Dongsam-Dong,
An Adaptive Self-Organization Protocol for Wireless Sensor Networks Kil-Woong Jang 1 and Byung-Soon Kim 2 1 Dept. of Mathematical and Information Science, Korea Maritime University 1 YeongDo-Gu Dongsam-Dong,
Course Routing Classification Properties Routing Protocols 1/39
 Course 8 3. Routing Classification Properties Routing Protocols 1/39 Routing Algorithms Types Static versus dynamic Single-path versus multipath Flat versus hierarchical Host-intelligent versus router-intelligent
Course 8 3. Routing Classification Properties Routing Protocols 1/39 Routing Algorithms Types Static versus dynamic Single-path versus multipath Flat versus hierarchical Host-intelligent versus router-intelligent
ROUTE STABILITY MODEL FOR DSR IN WIRELESS ADHOC NETWORKS
 ROUTE STABILITY MODEL FOR DSR IN WIRELESS ADHOC NETWORKS Ganga S 1, Binu Chandran R 2 1, 2 Mohandas College Of Engineering And Technology Abstract: Wireless Ad-Hoc Network is a collection of wireless mobile
ROUTE STABILITY MODEL FOR DSR IN WIRELESS ADHOC NETWORKS Ganga S 1, Binu Chandran R 2 1, 2 Mohandas College Of Engineering And Technology Abstract: Wireless Ad-Hoc Network is a collection of wireless mobile
Reducing Router-Crossings in a Mobile Intranet. Ibrahim Korpeoglu Rohit Dube Satish K. Tripathi. University of Maryland. College Park, MD 20742
 Reducing Router-Crossings in a Mobile Intranet Ibrahim Korpeoglu Rohit Dube Satish K. Tripathi Mobile Computing and Multimedia Laboratory University of Maryland College Park, MD 20742 fkorpe,rohit,tripathig@cs.umd.edu
Reducing Router-Crossings in a Mobile Intranet Ibrahim Korpeoglu Rohit Dube Satish K. Tripathi Mobile Computing and Multimedia Laboratory University of Maryland College Park, MD 20742 fkorpe,rohit,tripathig@cs.umd.edu
Top-Down Network Design
 Top-Down Network Design Chapter Seven Selecting Switching and Routing Protocols Original slides by Cisco Press & Priscilla Oppenheimer Selection Criteria for Switching and Routing Protocols Network traffic
Top-Down Network Design Chapter Seven Selecting Switching and Routing Protocols Original slides by Cisco Press & Priscilla Oppenheimer Selection Criteria for Switching and Routing Protocols Network traffic
Performance of Multihop Communications Using Logical Topologies on Optical Torus Networks
 Performance of Multihop Communications Using Logical Topologies on Optical Torus Networks X. Yuan, R. Melhem and R. Gupta Department of Computer Science University of Pittsburgh Pittsburgh, PA 156 fxyuan,
Performance of Multihop Communications Using Logical Topologies on Optical Torus Networks X. Yuan, R. Melhem and R. Gupta Department of Computer Science University of Pittsburgh Pittsburgh, PA 156 fxyuan,
Performance Analysis of Hierarchical Mobile IPv6 in IP-based Cellular Networks
 Performance Analysis of Hierarchical Mobile IPv6 in IP-based Cellular Networks Sangheon Pack and Yanghee Choi School of Computer Science & Engineering Seoul National University Seoul, Korea Abstract Next-generation
Performance Analysis of Hierarchical Mobile IPv6 in IP-based Cellular Networks Sangheon Pack and Yanghee Choi School of Computer Science & Engineering Seoul National University Seoul, Korea Abstract Next-generation
Routing Protocol - IS-IS
 Routing Protocol - IS-IS What is IS-IS? Intermediate System to Intermediate System intra-domain routing protocol :: IS, ES Is a Link State Protocol Is a dynamic routing protocol based on SPF routing algorithm
Routing Protocol - IS-IS What is IS-IS? Intermediate System to Intermediate System intra-domain routing protocol :: IS, ES Is a Link State Protocol Is a dynamic routing protocol based on SPF routing algorithm
An Efficient Proactive Routing Method for Mobile Ad Hoc Networks using Peer-to-Peer and Cellular Communication System
 An Efficient Proactive Routing Method for Mobile Ad Hoc Networks using Peer-to-Peer and Cellular Communication System Hiroaki Morinot, Tadao 8aitot:j: and Mitsuo Nohara:j: t Research and Development Initiative
An Efficient Proactive Routing Method for Mobile Ad Hoc Networks using Peer-to-Peer and Cellular Communication System Hiroaki Morinot, Tadao 8aitot:j: and Mitsuo Nohara:j: t Research and Development Initiative
Chapter 5 OSI Network Layer
 Chapter 5 OSI Network Layer The protocols of the OSI model Network layer specify addressing and processes that enable Transport layer data to be packaged and transported. The Network layer encapsulation
Chapter 5 OSI Network Layer The protocols of the OSI model Network layer specify addressing and processes that enable Transport layer data to be packaged and transported. The Network layer encapsulation
Numerical Evaluation of Hierarchical QoS Routing. Sungjoon Ahn, Gayathri Chittiappa, A. Udaya Shankar. Computer Science Department and UMIACS
 Numerical Evaluation of Hierarchical QoS Routing Sungjoon Ahn, Gayathri Chittiappa, A. Udaya Shankar Computer Science Department and UMIACS University of Maryland, College Park CS-TR-395 April 3, 1998
Numerical Evaluation of Hierarchical QoS Routing Sungjoon Ahn, Gayathri Chittiappa, A. Udaya Shankar Computer Science Department and UMIACS University of Maryland, College Park CS-TR-395 April 3, 1998
A Study on Mobile Internet Protocol and Mobile Adhoc Network Routing Protocols
 International Journal of Computer Science & Communication Vol. 1, No. 2, July-December 2010, pp. 185-189 A Study on Mobile Internet Protocol and Mobile Adhoc Network Routing Protocols B.V. Manikyala Rao
International Journal of Computer Science & Communication Vol. 1, No. 2, July-December 2010, pp. 185-189 A Study on Mobile Internet Protocol and Mobile Adhoc Network Routing Protocols B.V. Manikyala Rao
A Streaming Method with Trick Play on Time Division based Multicast
 A Streaming Method with Trick Play on Time Division based Yoshitaka Nakamura, Kazuki Murakoshi Yoh Shiraishi and Osamu Takahashi School of Systems Information Science, Future University Hakodate, Japan
A Streaming Method with Trick Play on Time Division based Yoshitaka Nakamura, Kazuki Murakoshi Yoh Shiraishi and Osamu Takahashi School of Systems Information Science, Future University Hakodate, Japan
Performance Analysis of Aodv Protocol under Black Hole Attack
 International Journal of Scientific & Engineering Research Volume 2, Issue 8,August-2011 1 Performance Analysis of Aodv Protocol under Black Hole Attack Monika Roopak, Dr. Bvr Reddy ABSTRACT- Mobile Ad-hoc
International Journal of Scientific & Engineering Research Volume 2, Issue 8,August-2011 1 Performance Analysis of Aodv Protocol under Black Hole Attack Monika Roopak, Dr. Bvr Reddy ABSTRACT- Mobile Ad-hoc
Open Shortest Path First (OSPF)
 CHAPTER 42 Open Shortest Path First (OSPF) Background Open Shortest Path First (OSPF) is a routing protocol developed for Internet Protocol (IP) networks by the interior gateway protocol (IGP) working
CHAPTER 42 Open Shortest Path First (OSPF) Background Open Shortest Path First (OSPF) is a routing protocol developed for Internet Protocol (IP) networks by the interior gateway protocol (IGP) working
Local Area Network(LAN)
 Local Area Network(LAN) A local area network (LAN) is a computer network that interconnects computers within a limited area. Example: a residence, school, laboratory, university campus,office building
Local Area Network(LAN) A local area network (LAN) is a computer network that interconnects computers within a limited area. Example: a residence, school, laboratory, university campus,office building
MULTICAST EXTENSIONS TO OSPF (MOSPF)
 MULTICAST EXTENSIONS TO OSPF (MOSPF) Version 2 of the Open Shortest Path First (OSPF) routing protocol is defined in RFC-1583. It is an Interior Gateway Protocol (IGP) specifically designed to distribute
MULTICAST EXTENSIONS TO OSPF (MOSPF) Version 2 of the Open Shortest Path First (OSPF) routing protocol is defined in RFC-1583. It is an Interior Gateway Protocol (IGP) specifically designed to distribute
Architectures for Distributed Systems
 Distributed Systems and Middleware 2013 2: Architectures Architectures for Distributed Systems Components A distributed system consists of components Each component has well-defined interface, can be replaced
Distributed Systems and Middleware 2013 2: Architectures Architectures for Distributed Systems Components A distributed system consists of components Each component has well-defined interface, can be replaced
Top-Down Network Design, Ch. 7: Selecting Switching and Routing Protocols. Top-Down Network Design. Selecting Switching and Routing Protocols
 Top-Down Network Design Chapter Seven Selecting Switching and Routing Protocols Copyright 2010 Cisco Press & Priscilla Oppenheimer 1 Switching 2 Page 1 Objectives MAC address table Describe the features
Top-Down Network Design Chapter Seven Selecting Switching and Routing Protocols Copyright 2010 Cisco Press & Priscilla Oppenheimer 1 Switching 2 Page 1 Objectives MAC address table Describe the features
QoS-Aware Hierarchical Multicast Routing on Next Generation Internetworks
 QoS-Aware Hierarchical Multicast Routing on Next Generation Internetworks Satyabrata Pradhan, Yi Li, and Muthucumaru Maheswaran Advanced Networking Research Laboratory Department of Computer Science University
QoS-Aware Hierarchical Multicast Routing on Next Generation Internetworks Satyabrata Pradhan, Yi Li, and Muthucumaru Maheswaran Advanced Networking Research Laboratory Department of Computer Science University
Shortcut Tree Routing using Neighbor Table in ZigBee Wireless Networks
 Shortcut Tree Routing using Neighbor Table in ZigBee Wireless Networks Salmu K.P 1, Chinchu James 2 1,2 Department of Computer Science, IIET, Nellikuzhi Abstract- ZigBee is a worldwide standard for wireless
Shortcut Tree Routing using Neighbor Table in ZigBee Wireless Networks Salmu K.P 1, Chinchu James 2 1,2 Department of Computer Science, IIET, Nellikuzhi Abstract- ZigBee is a worldwide standard for wireless
CAPACITY COMPATIBLE TWO-LEVEL LINK STATE ROUTING FOR MOBILE AD HOC NETWORKS
 CAPACITY COMPATIBLE TWO-LEVEL LINK STATE ROUTING FOR MOBILE AD HOC NETWORKS John Sucec and Ivan Marsic Rutgers University ABSTRACT The throughput of mobile ad hoc networks (MANETs has been analyzed previously.
CAPACITY COMPATIBLE TWO-LEVEL LINK STATE ROUTING FOR MOBILE AD HOC NETWORKS John Sucec and Ivan Marsic Rutgers University ABSTRACT The throughput of mobile ad hoc networks (MANETs has been analyzed previously.
Interface The exit interface a packet will take when destined for a specific network.
 The Network Layer The Network layer (also called layer 3) manages device addressing, tracks the location of devices on the network, and determines the best way to move data, which means that the Network
The Network Layer The Network layer (also called layer 3) manages device addressing, tracks the location of devices on the network, and determines the best way to move data, which means that the Network
Tree-Based Minimization of TCAM Entries for Packet Classification
 Tree-Based Minimization of TCAM Entries for Packet Classification YanSunandMinSikKim School of Electrical Engineering and Computer Science Washington State University Pullman, Washington 99164-2752, U.S.A.
Tree-Based Minimization of TCAM Entries for Packet Classification YanSunandMinSikKim School of Electrical Engineering and Computer Science Washington State University Pullman, Washington 99164-2752, U.S.A.
BSCI. Section 5. Intermediate System-to- Intermediate System (IS-IS)
 BSCI Section 5 Intermediate System-to- Intermediate System () Intermediate System-to-Intermediate System () is a routing protocol developed by the ISO. It is a link-state protocol and behaves much like
BSCI Section 5 Intermediate System-to- Intermediate System () Intermediate System-to-Intermediate System () is a routing protocol developed by the ISO. It is a link-state protocol and behaves much like
Andrew T. Campbell, Javier Gomez. Center for Telecommunications Research, Columbia University, New York. [campbell,
 An Overview of Cellular IP Andrew T. Campbell, Javier Gomez Center for Telecommunications Research, Columbia University, New York [campbell, javierg]@comet.columbia.edu Andras G. Valko Ericsson Research
An Overview of Cellular IP Andrew T. Campbell, Javier Gomez Center for Telecommunications Research, Columbia University, New York [campbell, javierg]@comet.columbia.edu Andras G. Valko Ericsson Research
/$10.00 (c) 1998 IEEE
 Dual Busy Tone Multiple Access (DBTMA) - Performance Results Zygmunt J. Haas and Jing Deng School of Electrical Engineering Frank Rhodes Hall Cornell University Ithaca, NY 85 E-mail: haas, jing@ee.cornell.edu
Dual Busy Tone Multiple Access (DBTMA) - Performance Results Zygmunt J. Haas and Jing Deng School of Electrical Engineering Frank Rhodes Hall Cornell University Ithaca, NY 85 E-mail: haas, jing@ee.cornell.edu
Mobile NFS. Fixed NFS. MFS Proxy. Client. Client. Standard NFS Server. Fixed NFS MFS: Proxy. Mobile. Client NFS. Wired Network.
 On Building a File System for Mobile Environments Using Generic Services F. Andre M.T. Segarra IRISA Research Institute IRISA Research Institute Campus de Beaulieu Campus de Beaulieu 35042 Rennes Cedex,
On Building a File System for Mobile Environments Using Generic Services F. Andre M.T. Segarra IRISA Research Institute IRISA Research Institute Campus de Beaulieu Campus de Beaulieu 35042 Rennes Cedex,
A Survey on Path Weight Based routing Over Wireless Mesh Networks
 A Survey on Path Weight Based routing Over Wireless Mesh Networks Ankush Sharma Assistant Professor, Dept. Of C.S.E, Chandigarh University Gharuan, India Anuj Gupta Head C.S.E and M.C.A Dept, RIMT Mandi
A Survey on Path Weight Based routing Over Wireless Mesh Networks Ankush Sharma Assistant Professor, Dept. Of C.S.E, Chandigarh University Gharuan, India Anuj Gupta Head C.S.E and M.C.A Dept, RIMT Mandi
Multimedia Contents Caching Scheme in Mobile Ad-Hoc Network. Backhyun Kim 1 and Iksoo Kim 2*
 , pp. 157-166 http://dx.doi.org/10.14257/ijmue.2014.9.12.15 Multimedia Contents Caching Scheme in Mobile Ad-Hoc Network Backhyun Kim 1 and Iksoo Kim 2* 1 Faculty of Liberal Education, Incheon National
, pp. 157-166 http://dx.doi.org/10.14257/ijmue.2014.9.12.15 Multimedia Contents Caching Scheme in Mobile Ad-Hoc Network Backhyun Kim 1 and Iksoo Kim 2* 1 Faculty of Liberal Education, Incheon National
Congestion Propagation among Routers in the Internet
 Congestion Propagation among Routers in the Internet Kouhei Sugiyama, Hiroyuki Ohsaki and Makoto Imase Graduate School of Information Science and Technology, Osaka University -, Yamadaoka, Suita, Osaka,
Congestion Propagation among Routers in the Internet Kouhei Sugiyama, Hiroyuki Ohsaki and Makoto Imase Graduate School of Information Science and Technology, Osaka University -, Yamadaoka, Suita, Osaka,
Design of a Real-Time Trader for Mobile Objects in Open Distributed Environments
 Design of a Real-Time for Mobile Objects in Open Distributed Environments Song-yi Yi, Heonshik Shin Department of Computer Engineering Seoul National University Seoul 151-742, Korea fyis, shinhsg@ce2.snu.ac.kr
Design of a Real-Time for Mobile Objects in Open Distributed Environments Song-yi Yi, Heonshik Shin Department of Computer Engineering Seoul National University Seoul 151-742, Korea fyis, shinhsg@ce2.snu.ac.kr
Improving Performance in Ad hoc Networks through Location based Multi Hop Forwarding
 Improving Performance in Ad hoc Networks through Location based Multi Hop Forwarding v.vallinayagi research scholar, manonmanium university tirunelveli-11 Dr.G.M.Nasira Assistant professor dept of computer
Improving Performance in Ad hoc Networks through Location based Multi Hop Forwarding v.vallinayagi research scholar, manonmanium university tirunelveli-11 Dr.G.M.Nasira Assistant professor dept of computer
Structuring a Token Based Distributed Mutual Exclusion Algorithm for Mobile Hosts 1 Deepshikha Sharma, 2 Latika Sharma
 Structuring a Token Based Distributed Mutual Exclusion Algorithm for Mobile Hosts 1 Deepshikha Sharma, 2 Latika Sharma Computer Science and Engineering Bharat Institute of Technology - Meerut, India Abstract
Structuring a Token Based Distributed Mutual Exclusion Algorithm for Mobile Hosts 1 Deepshikha Sharma, 2 Latika Sharma Computer Science and Engineering Bharat Institute of Technology - Meerut, India Abstract
An efficient implementation of the greedy forwarding strategy
 An efficient implementation of the greedy forwarding strategy Hannes Stratil Embedded Computing Systems Group E182/2 Technische Universität Wien Treitlstraße 3 A-1040 Vienna Email: hannes@ecs.tuwien.ac.at
An efficient implementation of the greedy forwarding strategy Hannes Stratil Embedded Computing Systems Group E182/2 Technische Universität Wien Treitlstraße 3 A-1040 Vienna Email: hannes@ecs.tuwien.ac.at
Replica Distribution Scheme for Location-Dependent Data in Vehicular Ad Hoc Networks using a Small Number of Fixed Nodes
 Replica Distribution Scheme for Location-Dependent Data in Vehicular d Hoc Networks using a Small Number of Fixed Nodes Junichiro Okamoto and Susumu Ishihara Graduate School of Engineering, Shizuoka University,
Replica Distribution Scheme for Location-Dependent Data in Vehicular d Hoc Networks using a Small Number of Fixed Nodes Junichiro Okamoto and Susumu Ishihara Graduate School of Engineering, Shizuoka University,
Dynamic Search Technique Used for Improving Passive Source Routing Protocol in Manet
 African Journal of Basic & Applied Sciences 9 (1): 27-32, 2017 ISSN 2079-2034 IDOSI Publications, 2017 DOI: 10.5829/idosi.ajbas.2017.27.32 Dynamic Search Technique Used for Improving Passive Source Routing
African Journal of Basic & Applied Sciences 9 (1): 27-32, 2017 ISSN 2079-2034 IDOSI Publications, 2017 DOI: 10.5829/idosi.ajbas.2017.27.32 Dynamic Search Technique Used for Improving Passive Source Routing
An efficient traffic management framework for multi-channel wireless backbone networks
 An efficient traffic management framework for multi-channel wireless backbone networks Yuzo Taenaka 1a) and Kazuya Tsukamoto 2 1 Information Technology Center, The University of Tokyo 2 11 16 Yayoi, Bunkyo,
An efficient traffic management framework for multi-channel wireless backbone networks Yuzo Taenaka 1a) and Kazuya Tsukamoto 2 1 Information Technology Center, The University of Tokyo 2 11 16 Yayoi, Bunkyo,
Arvind Krishnamurthy Fall 2003
 Ad-hoc Routing Arvind Krishnamurthy Fall 2003 Ad Hoc Routing Create multi-hop connectivity among set of wireless, possibly moving, nodes Mobile, wireless hosts act as forwarding nodes as well as end systems
Ad-hoc Routing Arvind Krishnamurthy Fall 2003 Ad Hoc Routing Create multi-hop connectivity among set of wireless, possibly moving, nodes Mobile, wireless hosts act as forwarding nodes as well as end systems
Network Working Group Request for Comments: 1768 Category: Experimental March 1995
 Network Working Group D. Marlow Request for Comments: 1768 NSWC-DD Category: Experimental March 1995 Status of this Memo Host Group Extensions for CLNP Multicasting This memo defines an Experimental Protocol
Network Working Group D. Marlow Request for Comments: 1768 NSWC-DD Category: Experimental March 1995 Status of this Memo Host Group Extensions for CLNP Multicasting This memo defines an Experimental Protocol
FIGURE 3. Two-Level Internet Address Structure. FIGURE 4. Principle Classful IP Address Formats
 Classful IP Addressing When IP was first standardized in September 1981, the specification required that each system attached to an IP-based Internet be assigned a unique, 32-bit Internet address value.
Classful IP Addressing When IP was first standardized in September 1981, the specification required that each system attached to an IP-based Internet be assigned a unique, 32-bit Internet address value.
Performance Analysis of Broadcast Based Mobile Adhoc Routing Protocols AODV and DSDV
 INTERNATIONAL JOURNAL OF COMPUTER SCIENCE AND MOBILE APPLICATIONS IJCSMA Performance Analysis of Broadcast Based Mobile Adhoc Routing Protocols AODV and DSDV Er. Sandeep Singh Khehra 1, Er. Abhinash Singla
INTERNATIONAL JOURNAL OF COMPUTER SCIENCE AND MOBILE APPLICATIONS IJCSMA Performance Analysis of Broadcast Based Mobile Adhoc Routing Protocols AODV and DSDV Er. Sandeep Singh Khehra 1, Er. Abhinash Singla
Expected Path Bandwidth Based Efficient Routing Mechanism in Wireless Mesh Network
 Expected Path Bandwidth Based Efficient Routing Mechanism in Wireless Mesh Network K Anandkumar, D.Vijendra Babu PG Student, Chennai, India Head, Chennai, India ABSTRACT : Wireless mesh networks (WMNs)
Expected Path Bandwidth Based Efficient Routing Mechanism in Wireless Mesh Network K Anandkumar, D.Vijendra Babu PG Student, Chennai, India Head, Chennai, India ABSTRACT : Wireless mesh networks (WMNs)
Anil Saini Ph.D. Research Scholar Department of Comp. Sci. & Applns, India. Keywords AODV, CBR, DSDV, DSR, MANETs, PDF, Pause Time, Speed, Throughput.
 Volume 6, Issue 7, July 2016 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Performance Analysis
Volume 6, Issue 7, July 2016 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Performance Analysis
EEC-684/584 Computer Networks
 EEC-684/584 Computer Networks Lecture 14 wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline 2 Review of last lecture Internetworking
EEC-684/584 Computer Networks Lecture 14 wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline 2 Review of last lecture Internetworking
ASN.1/PL. ASN.1 Type Definition Module. Source Code. ASN.1 Database System
 A Database System Based on ASN.1: Its System Architecture and Database Programming Language 3 Kaname HARUMOTO y Masahiko TSUKAMOTO z Shojiro NISHIO y y Department of Information Systems Engineering z Information
A Database System Based on ASN.1: Its System Architecture and Database Programming Language 3 Kaname HARUMOTO y Masahiko TSUKAMOTO z Shojiro NISHIO y y Department of Information Systems Engineering z Information
Approaches to Green Networks
 Approaches to Green Networks Mitsuaki Kakemizu Akira Chugo (Manuscript received March 26, 2009) Communication networks show promise as a means of reducing carbon dioxide emissions. However, as networks
Approaches to Green Networks Mitsuaki Kakemizu Akira Chugo (Manuscript received March 26, 2009) Communication networks show promise as a means of reducing carbon dioxide emissions. However, as networks
