1.4 VPN Processing Principle and Communication Method
|
|
|
- Wilfred Patterson
- 6 years ago
- Views:
Transcription
1 This section contains a description of operation principle and communication method of VPN that can be constructed by SoftEther VPN. An overview of the modules and functions that was used by VPN communications. And the types of VPN that can be constructed by using SoftEther VPN Conventional Ethernet Configuration SoftEther VPN implements the mechanism of Ethernet communications as it is by software and realizes VPN by creating a virtual network. The following is a brief description of the mechanism what Ethernet will operate. Ethernet Basics With LAN using common Ethernet standards (IEEE802.3) such as conventional 100Base-TX or 1000Base-T, multiple computers equipped with communications equipment (network adapter) that supports Ethernet is connected by star connection to a central switching Hub (also referred to as "layer 2 switching") and communicate freely with each other. Switching Hub and Network Adapter 1.4 VPN Processing Principle and Communication Method With Ethernet multiple computers you can communicate with each other. Here however the computers use a network adapter (also referred to as "LAN Card") which is a special device for connecting to Ethernet, and connects physically to Ethernet. In specific terms, the computer connects from the network adapter to the desired Ethernet switching Hub by a physical signal line called a "network cable". MAC Address Switching Hub and network adapter for Ethernet. Computers participating in Ethernet must communicate with IDs to prevent them from duplicating each other. Each network adapter has been assigned a unique 48-bit ID. This 48-bit ID is referred as "MAC address". As a rule, the MAC address of the physical network adapter has been assigned, computers would not be duplicated anywhere in the world (in the case of software network adapter such as SoftEther VPN 1
2 Virtual Network Adapter, a suitable algorithm whereby possibility of MAC address actually being duplicated is extremely low is generated to prevent duplication). Communication Packets (Ethernet Frames) that Flow through Ethernet 1.4 VPN Processing Principle and Communication Method Communication packets that flow through Ethernet are commonly referred to as "Ethernet frames" or "MAC frame Ethernet packets" (in this manual they are uniformly referred to as "Ethernet frames"). Ethernet frames contain several headers and the data to be actually transmitted (payload). The following four items are the most important of these. A Ethernet frame (MAC frame). The destination MAC address (48 bits) is a field which contains the MAC address that recovers indicating to which computer the Ethernet frames of the computer sending the frames will be sent. Relaying devices such as a switching Hub within Ethernet reads the destination MAC address and relay the Ethernet frames. The source MAC address (48 bits) is the field containing the MAC address of the network adapter of the computer sending the Ethernet frames. Protocol type (16 bits) indicates in a 16-bit value what protocol the data contained in the Ethernet frame (payload) uses in layer 3. For example the value is 0x0800 for IP and 0x0806 for ARP. In some cases the field may contain a value that indicates the length of the payload instead of the protocol type, but it is currently not used often. The payload (maximum 1500 bytes) is the data to be actually transmitted using Ethernet. Unicast and Broadcast There are two ways that Ethernet frames can be sent, "unicast" and "broadcast". "Unicast" is when an Ethernet frame is sent by specifying the MAC address of a certain network adapter. And as for "broadcast" is the frame that sent to all network adapters participating in Ethernet other than your own. When sending frames by unicast, the MAC address of the destination network adapter is specified for destination MAC address. And when sending frames by broadcast, the special MAC address FF:FF:FF:FF:FF:FF is specified as the destination MAC address. The frames of which the MAC address destination FF:FF:FF:FF:FF:FF are called "broadcast packets" or "broadcast frames". And as a rule this can be received by all computers (network adapters) participating in the Ethernet network. Switching Hub Mechanism The switching Hub used by Ethernet (layer 2 switch) constructs a network by Ethernet and it is an important peripheral device for communication. Switching Hubs have multiple ports (usually 8 ports, but can have from tens to hundreds). By connecting a compute to the Ethernet by network cable, etc., a physical network is connected between the switching Hub and computer's network adapter, thus enabling Ethernet communications by layer 2. 2
3 The ports of a switching Hub can also be connected to the ports of another switching Hub. Even though the connected switching Hubs were originally separate by Ethernet networks, by connecting them by network cable, they work like a single Ethernet network. This is called "cascade connection". The computers connected to the switching Hubs on the left and right in the following figure (Segment junction by cascade connection of switching hubs.) can communicate freely with each other. Segment junction by cascade connection of switching hubs. Frame Exchange and MAC Address Learning by Switching Hub Switching Hubs constantly recognize in advance which computers with what sort of MAC address are connected to the respective ports and maintain the information in an internal database. This is called a "MAC address table". When a switching Hub receives an Ethernet frame, it reads the destination MAC address of the Ethernet frame, and when the destination MAC address is registered in the MAC address table, it is sent to the concerned port. If the destination MAC address is not registered in the MAC address table or the Ethernet frame is a broadcast frame, it will be sent to all ports. The processing whereby a switching Hub learns new MAC addresses and registers them in the internal MAC address table is carried out automatically by reading the source MAC address, each time a new Ethernet frame will be received. This realizes function whereby unicast packets are only sent to required ports, and are not sent to unnecessary ports. This is called the "Frame exchange and MAC address learning by switching Hub function". Ethernet Segment (Broadcast Domain) In examples thus far, a single network through which computers participating in an Ethernet network can communicate freely with each other is called an "Ethernet segment," a "segment" or "broadcast domain". An Ethernet configured of a switching Hub is usually one segment. A segment can also be formed by connecting two originally separate segments by network cable, etc., as was previously mentioned. Cascade Connection As it has been mentioned earlier, the method of connecting two segments configured of two switching Hubs and using as a single segment is called "cascade connection". Cascade connection can consist of an 3
4 unlimited number of cascades provided the physical limit established for Ethernet is not exceeded. The fact is that cascade connection can be accomplished easily and it is one of the greatest features of using Ethernet. By cascade connecting another switching Hub to one for which the number of ports has become insufficient, you can increase the number of available ports and increase the number of computers that can be connected to the network. Bridge Connection 1.4 VPN Processing Principle and Communication Method Bridge connection enables frames to be exchanged freely by cascade connection of two physically separated Ethernet segments or similar configuration. Cascade connection and bridge connection are technically similar connection methods, but whereas cascade connection indicates connecting switching Hubs to construct a single large segment from the beginning, bridge connection means connecting networks to be used as two segments that are physically separate and are administered separately Virtual Hub With SoftEther VPN by creating a virtual switching Hub and network adapter, VPN communication that creates virtual Ethernet is realized. This section contains a brief description of Virtual Hub. A more concrete description of Virtual Hub is provided in 1.6 VPN Communication Details. Virtual Hub Functions Virtual Hub is one of the most important functions of SoftEther VPN. Virtual Hub implements the same level of functions as the existing common layer 2 switching Hub as software. Virtual Hub has a MAC address learning function and frame exchange/delivery functions based on learning. Whereas conventional switching Hubs used to handle this processing as hardware, with Virtual Hub of SoftEther VPN, the processing is handled as software. For details concerning realization of VPN communications by Virtual Hub, see 1.6 VPN Communication Details and 3.4 Virtual Hub Functions. SoftEther VPN Server can create multiple Virtual Hubs. You can create as many Virtual Hubs as memory space, CPU speed and specifications will permit. Each respective Virtual Hub conducts MAC address learning for virtual Ethernet frames flowing through the VPN. As a result virtual layer 2 Ethernet segments are realized by sending Ethernet frames to computers participating in other VPNs. 4
5 Connection between Virtual Hubs or between Virtual Network Adapters. Creation and Administration of Multiple Virtual Hubs When multiple Virtual Hubs are created within a single VPN server, those Virtual Hubs cannot communicate with each other. Consequently if multiple Virtual Hubs are created, it means multiple Ethernet segments are formed within the VPN Server. Unlike the physical switching Hub in conventional Ethernet, the Virtual Hub of SoftEther VPN is connected by TCP/IP-based tunneling protocol (SoftEther VPN protocol) via an existing IP network (such as the Internet) rather than direct connection by network cable. In other words, there is a function whereby a virtual port equal to port connected to a physical switching Hub by network cable stands by for connection to the Virtual Hub, enabling VPN connection by SoftEther VPN protocol, just like as if it is connected by network cable to virtual port from another computer. Role of Administration Unit Segment separation by Virtual Hub within VPN Server. As was previously mentioned, you can connect to Virtual Hub from a remote location by SoftEther VPN protocol, but when the connection is permitted by anybody, a third party whom is not permitted can connect to the Virtual Hub. To prevent this the administrator defines users who can connect to the Virtual 5
6 Hub, and can set so that only users successfully authenticated are accepted (either password authentication or certificate authentication may be used). Concerning communication within the Virtual Hub as well, permitting all communication contents by default but applying packet filtering and security policy, some types of communication can be blocked. These setting contents are completely independent for each Virtual Hub, and administration is divided into units so each individual administrator can administrate it separately. Administrators of VPN Servers at large can manage all Virtual Hubs, but administrators granted authority concerning some Virtual Hubs from the VPN Server administrator can manage only those Virtual Hubs and those are unable to manage other Virtual Hubs. Method of Connecting Virtual Hubs to each other Virtual Hubs can be cascade connected to Virtual Hubs operating on the same VPN Server or VPN Server operating on another computer, and the cascade connected Virtual Hubs that were originally separate segments are joined to work as a single segment. For Virtual Hubs operating on the same VPN Server, via virtual layer 3 switch by IP routing, network among Virtual Hubs can be connected by layer Virtual Network Adapter With SoftEther VPN, a physical switching Hub can be made virtual to realize Virtual Hub. Similarly, a physical network adapter can be made virtual by software to realize a Virtual Network Adapter. Virtual Network Adapter can connect to a Virtual Hub operating within SoftEther VPN Server at a remote location through a network by TCP/IP-based SoftEther VPN protocol. For details concerning SoftEther VPN Client and Virtual Network Adapter, see 4. SoftEther VPN Client Manual. 6
7 SoftEther VPN Virtual Network Adapter recognized as a network adapter by the operating system. Virtual Network Adapter software is currently offered as a SoftEther VPN Client for Windows and Linux. Computers installed with SoftEther VPN Client can connect the VPN Server as a VPN client. Multiple Virtual Network Adapters can be created on a client computer as a SoftEther VPN Client setting. Because the created Virtual Network Adapter is recognized as a network adapter just as physical network adapter by almost any communications application is running on the operating system, as a rule almost all network protocols that support Ethernet communications and TCP/IP protocol can communicate on VPN via Virtual Hub. Property window of Virtual Network Adapter Cascade connection and virtual layer 3 switch With SoftEther VPN Server, you can create multiple Virtual Hubs and operate them at the same time. In the initial state however Virtual Hubs have only independent layer 2 segments, and although computers connected to the same Virtual Hub can communicate freely, computers connected to separate Virtual Hubs cannot communicate with each other. Cascade Connection Using the cascade connection function, you can connect to a Virtual Hub on which the same VPN Server or other computer's VPN Server is operating. By combining cascade connection and bridge connection functions, you can easily construct base-to-base connection VPN. For details on cascade connection, see 3.4 Virtual Hub Functions. For examples of VPN construction combining cascade and bridge connection functions, see 10.5 Build a LAN-to-LAN VPN (Using L2 Bridge). Virtual Layer 3 Switch The virtual layer 3 switch function emulates a communications device for IP routing by IP protocol called "layer 3 switch" or "IP router". 7
8 Layer 3 switches and IP routers can be joined as a layer 3 IP network with physically separated layer 2 segments with split broadcast domain. In this case layer 2 segments separated by IP routing that communicate via layer 3 switch or router and IP packets can arrive at another network across networks sequentially via 3 switch or router. Massive IP networks such as the Internet are realized by combination of layer 3 switch and router. Using the virtual layer 3 switch function of SoftEther VPN Server enables IP routing among multiple Virtual Hubs. When conducting IP routing among multiple Virtual Hubs with the previous version of SoftEther 1.0, etc., you had to conduct IP routing with a physical layer 3 switch or special router by bridge connecting each respective Virtual Hub segment to a physical Ethernet segment. However SoftEther VPN Server's support of virtual layer 3 switch function enables network administrators to easily realize communication among Virtual Hubs by IP routing among multiple Virtual Hubs. IP routing among Virtual Hubs by virtual layer 3 switch. When connecting multiple networks bases by VPN by SoftEther VPN, a combination of local bridge function and cascade connection function is usually sufficient, but if connecting networks to each other by VPN, you might have to use a combination of IP routing by virtual layer 3 switch function. For VPN construction examples using virtual layer 3 switch function, see 10.6 Build a LAN-to-LAN VPN (Using L3 IP Routing) Bridge Connection of Virtual Network and Physical Network SoftEther VPN Server and SoftEther VPN Bridge are equipped with a local bridge function. Using the local bridge function enables you to bridge connect Virtual Hub and physical network adapter. In other words, you can join two segments such as Virtual Hub and existing physical network as a single segment. For details see 3.6 Local Bridges. By connecting Virtual Hub and physical existing LAN by multiple bases and by furthermore cascade connecting Virtual Hubs existing physical LAN of multiple bases can be easily made a single segment via Internet to realize base-to-base VPN. 8
9 1.4.6 Computer-to-computer VPN Example of base-to-base connection by SoftEther VPN. Networks that realize SoftEther VPN can roughly be divided into the following three forms: Computer-to-computer VPN Remote access VPN Base-to-base connection VPN A sophisticated VPN can be constructed by separating or combining these forms. For actual network construction examples, see 10. Examples of Building VPN Networks. Computer-to-computer VPN is the simplest form of VPN built using SoftEther VPN. The range of communication via VPN that can be constructed extremely easily, is not very wide. With computer-to-computer VPN, for Virtual Hub of SoftEther VPN Server established at one location, multiple computers connecting network adapter of SoftEther VPN Client to Virtual Hub by VPN is enable any Ethernet frame to be sent or received among computers participating in VPN. So that the communication can be carried out freely and safely without depending on physical network form. All VPN communication is encrypted to prevent eavesdropping and tampering. With computer-to-computer VPN, however, computers installed with SoftEther VPN Client can communicate freely, but computers other than these cannot participate in VPN. For specific connection method, see 10.3 Build a PC-to-PC VPN. 9
10 1.4.7 Remote Access VPN Computer-to-computer VPN. Remote access VPN is a type of VPN that can be built by using SoftEther VPN. You can freely access the computers out in the field or at home that cannot be accessed from Internet such as common company LAN, and can communicate with the application of your choice. From before remote access to company LAN has been frequently accomplished by using PPP protocol by dial-up network such as telephone line or ISDN. Communication speed for these methods is however low, and because it was pay-as-you-go, it was difficult to send or receive a large quantities of data that had taken an extended amount of time. With remote access VPN by SoftEther VPN, by installing SoftEther VPN Client, as a rule, as long as you had an environment where the Internet could be connected to, you could easily connect by VPN to a SoftEther VPN Server set up in company LAN from anywhere in the world, thereby enabling company LAN access. All VPN communication is also encrypted to prevent eavesdropping and tampering. In order to realize remote access VPN, a SoftEther VPN Server is established in the company LAN and the Virtual Hub and existing physical Ethernet segment created in VPN Server that are connected by bridge connection. Connecting by computer installed with VPN Client from remote to concern the Virtual Hub enables the remote access to company LAN. With conventional VPN protocol, even protocols other than TCP/IP that has been hard to use in many cases will c be used via virtual Ethernet. VPN sessions can furthermore be easily established via proxy servers, firewall or NAT that use to be hard for conventional VPN protocol to get through. For specific connection method, see 10.4 Build a Generic Remote Access VPN. 10
11 1.4.8 Base-to-Base VPN of Ordinary Scale Remote access VPN. Remote access VPN is the form of VPN that enables multiple computers installed with VPN Client to access one base via Internet or other bases from a remote location. Base-to-base VPN, on the other hand it is a VPN connection method whereby multiple bases in physically separated locations that can connect with each other. It is probably the best way for companies or departments where two or more bases already exist or are considering increasing the number of bases. With base-to-base VPN, the set up computers installed with VPN Server or VPN Bridge at multiple bases and connecting existing physical Ethernet segments of each base and Virtual Hub within the VPN Server or VPN Bridge by local bridge connection. Virtual Hub of another VPN Bridge, etc., is connected by cascade connection to VPN Server of one of several bases. By doing so, physical layer 2 segments of multiple separated bases recognize each other as a single segment. After physical networks among multiple bases are connected to each other, so they can be used as a single segment by SoftEther VPN, they are used just as if they are physically connected by cascade connection using an extremely long network cable. All VPN communication is also encrypted to prevent eavesdropping and tampering. Base-to-base connection VPN function to bridge bases can realize economic and secure service through the Internet that is the same as that of conventional broadband Ethernet service as communication carriers. For specific connection method, see 10.5 Build a LAN-to-LAN VPN (Using L2 Bridge). 11
12 1.4.9 Base-to-Base VPN of Large Scale Base-to-base VPN of ordinary scale. The method of connecting physical Ethernet segments of multiple bases such as by the previously described base-to-base VPN connection of ordinary scale works well if there are a total of several hundred clients at each base connected by VPN, but if the number of computers exceeds this when totaled and you want to connect respective computers to each other, several limitations such as the following may occur. If the number of computers exceeds several hundred, the volume of communication by protocol using broadcast frames such as ARP and NetBIOS increases and increases the load of VPN connection among bases. Because networks that were originally separate become a single large network with the system of connecting layer 2 segments alike, as a rule, it is preferable that computers in the segments belong to the same IP network, but if the total number of computers is too large, it will costs a lot to alter the configuration. In the case where such limitations may pose problems, by combining the virtual layer 3 switch function, layer 2 local bridge function and cascade connection function of SoftEther VPN Server, you can use IP routing by layer 3 instead of direct cascade connection of base networks by layer 2. Using this method is especially effective if realizing large scale base-to-base connection VPN. This however requires knowledge of IP routing for designing and building and improves level of difficulty. For specific connection method, see 10.6 Build a LAN-to-LAN VPN (Using L3 IP Routing). By this method, same or better base-to-base VPN communication supported older VPN protocols such as PPTP and L2TP/IPSec can be easily realized by SoftEther VPN software. 12
13 Base-to-base VPN of large scale. 13
Create New Virtual Hub window.
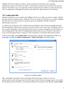 SoftEther VPN Server makes it possible to create a plurality of Virtual Hubs, and to separate administration objects and VPN session layer 2 communication between each Virtual Hub. This manual explains
SoftEther VPN Server makes it possible to create a plurality of Virtual Hubs, and to separate administration objects and VPN session layer 2 communication between each Virtual Hub. This manual explains
SoftEther VPN Server supports the clustering function. This section explains the clustering function.
 SoftEther VPN Server supports the clustering function. This section explains the clustering function. 3.9.1 What is Clustering? Clustering Necessity In general terms, clustering is a processing method
SoftEther VPN Server supports the clustering function. This section explains the clustering function. 3.9.1 What is Clustering? Clustering Necessity In general terms, clustering is a processing method
PUCPR. Internet Protocol. Edgard Jamhour E N G L I S H S E M E S T E R
 PUCPR Internet Protocol Address Resolution and Routing Edgard Jamhour 2014 E N G L I S H S E M E S T E R 1. Address Resolution The IP address does not identify, indeed, a computer, but a network interface.
PUCPR Internet Protocol Address Resolution and Routing Edgard Jamhour 2014 E N G L I S H S E M E S T E R 1. Address Resolution The IP address does not identify, indeed, a computer, but a network interface.
Accessing an Extremely Secure LAN Via Remote Access That Was Not Possible With Previous Technologies
 Before, administrator rights were a necessity when setting up a remote access VPN. But by using the SecureNAT capability built in to SoftEther VPN Server and SoftEther VPN Bridge you can build a remote
Before, administrator rights were a necessity when setting up a remote access VPN. But by using the SecureNAT capability built in to SoftEther VPN Server and SoftEther VPN Bridge you can build a remote
2. LAN Topologies Gilbert Ndjatou Page 1
 2. LAN Topologies Two basic categories of network topologies exist, physical topologies and logical topologies. The physical topology of a network is the cabling layout used to link devices. This refers
2. LAN Topologies Two basic categories of network topologies exist, physical topologies and logical topologies. The physical topology of a network is the cabling layout used to link devices. This refers
Dialog Box Displaying the VPN Connection Status.
 By using SoftEther VPN Client to define the required connection settings of a connection setting and then connecting to that connection setting, you can start the connection to VPN Server. 4.5.1 Starting
By using SoftEther VPN Client to define the required connection settings of a connection setting and then connecting to that connection setting, you can start the connection to VPN Server. 4.5.1 Starting
Cisco How Virtual Private Networks Work
 Table of Contents How Virtual Private Networks Work...1 Introduction...1 Before You Begin...1 Conventions...1 Prerequisites...1 Components Used...1 Background Information...1 What Makes a VPN?...2 Analogy:
Table of Contents How Virtual Private Networks Work...1 Introduction...1 Before You Begin...1 Conventions...1 Prerequisites...1 Components Used...1 Background Information...1 What Makes a VPN?...2 Analogy:
4.1 Introduction to Media and Devices
 Chapter 4 Network Hardware 4.1 Introduction to Media and Devices Many of the issues discussed in this course, such as topology, scalability, and speed, depend on hardware. Unlike many of your computer
Chapter 4 Network Hardware 4.1 Introduction to Media and Devices Many of the issues discussed in this course, such as topology, scalability, and speed, depend on hardware. Unlike many of your computer
INTRODUCTION TO ICT.
 INTRODUCTION TO ICT. (Introducing Basic Network Concepts) Lecture # 24-25 By: M.Nadeem Akhtar. Department of CS & IT. URL: https://sites.google.com/site/nadeemcsuoliict/home/lectures 1 INTRODUCTION TO
INTRODUCTION TO ICT. (Introducing Basic Network Concepts) Lecture # 24-25 By: M.Nadeem Akhtar. Department of CS & IT. URL: https://sites.google.com/site/nadeemcsuoliict/home/lectures 1 INTRODUCTION TO
1. Ultimate Powerful VPN Connectivity
 1.1. Firewall, Proxy and NAT Transparency One of the key features of SoftEther VPN is the transparency for firewalls, proxy servers and NATs (Network Address Translators). NATs are sometimes implemented
1.1. Firewall, Proxy and NAT Transparency One of the key features of SoftEther VPN is the transparency for firewalls, proxy servers and NATs (Network Address Translators). NATs are sometimes implemented
2. Layer-2 Ethernet-based VPN
 2.1. Full Ethernet Virtualization The key concept of the method of realizing VPN by SoftEther VPN is the full virtualization of Ethernet segments, layer-2 Ethernet switches and Ethernet adapters. In order
2.1. Full Ethernet Virtualization The key concept of the method of realizing VPN by SoftEther VPN is the full virtualization of Ethernet segments, layer-2 Ethernet switches and Ethernet adapters. In order
Networking interview questions
 Networking interview questions What is LAN? LAN is a computer network that spans a relatively small area. Most LANs are confined to a single building or group of buildings. However, one LAN can be connected
Networking interview questions What is LAN? LAN is a computer network that spans a relatively small area. Most LANs are confined to a single building or group of buildings. However, one LAN can be connected
Configuring L2TP over IPsec
 CHAPTER 62 This chapter describes how to configure L2TP over IPsec on the ASA. This chapter includes the following topics: Information About L2TP over IPsec, page 62-1 Licensing Requirements for L2TP over
CHAPTER 62 This chapter describes how to configure L2TP over IPsec on the ASA. This chapter includes the following topics: Information About L2TP over IPsec, page 62-1 Licensing Requirements for L2TP over
Cisco Cisco Certified Network Associate (CCNA)
 Cisco 200-125 Cisco Certified Network Associate (CCNA) http://killexams.com/pass4sure/exam-detail/200-125 Question: 769 Refer to exhibit: Which destination addresses will be used by Host A to send data
Cisco 200-125 Cisco Certified Network Associate (CCNA) http://killexams.com/pass4sure/exam-detail/200-125 Question: 769 Refer to exhibit: Which destination addresses will be used by Host A to send data
Setup L2TP/IPsec VPN Server on SoftEther VPN Server
 Setup L2TP/IPsec VPN Server on SoftEther VPN Server The IPsec VPN Server Function is disabled by default. You can enable it easily as the following steps. Configuration Guide The VPN Server configuration
Setup L2TP/IPsec VPN Server on SoftEther VPN Server The IPsec VPN Server Function is disabled by default. You can enable it easily as the following steps. Configuration Guide The VPN Server configuration
Chapter Motivation For Internetworking
 Chapter 17-20 Internetworking Part 1 (Concept, IP Addressing, IP Routing, IP Datagrams, Address Resolution 1 Motivation For Internetworking LANs Low cost Limited distance WANs High cost Unlimited distance
Chapter 17-20 Internetworking Part 1 (Concept, IP Addressing, IP Routing, IP Datagrams, Address Resolution 1 Motivation For Internetworking LANs Low cost Limited distance WANs High cost Unlimited distance
Chapter 6: Network Communications and Protocols
 Learning Objectives Chapter 6: Network Communications and Protocols Understand the function and structure of packets in a network, and analyze and understand those packets Understand the function of protocols
Learning Objectives Chapter 6: Network Communications and Protocols Understand the function and structure of packets in a network, and analyze and understand those packets Understand the function of protocols
How to Configure Mobile VPN for Forcepoint NGFW TECHNICAL DOCUMENT
 How to Configure Mobile VPN for Forcepoint NGFW TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS 1 BACKGROUND 2 WINDOWS SERVER CONFIGURATION STEPS 2 CONFIGURING USER AUTHENTICATION 3 ACTIVE DIRECTORY
How to Configure Mobile VPN for Forcepoint NGFW TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS 1 BACKGROUND 2 WINDOWS SERVER CONFIGURATION STEPS 2 CONFIGURING USER AUTHENTICATION 3 ACTIVE DIRECTORY
A+ Certification Guide. Chapter 16 (Part B) Networking
 A+ Certification Guide Chapter 16 (Part B) Networking Chapter 16 (Part B) Objectives Installing and Configuring Network Interface Cards Networking Configuration for Small Network Switches and Routers Setting
A+ Certification Guide Chapter 16 (Part B) Networking Chapter 16 (Part B) Objectives Installing and Configuring Network Interface Cards Networking Configuration for Small Network Switches and Routers Setting
Connecting to the Network
 Connecting to the Network Networking for Home and Small Businesses Chapter 3 1 Objectives Explain the concept of networking and the benefits of networks. Explain the concept of communication protocols.
Connecting to the Network Networking for Home and Small Businesses Chapter 3 1 Objectives Explain the concept of networking and the benefits of networks. Explain the concept of communication protocols.
Implementing, Managing, and Maintaining a Microsoft Windows Server 2003 Network Infrastructure
 Question Number (ID) : 1 (jaamsp_mngnwi-088) You are the administrator for medium-sized network with many users who connect remotely. You have configured a server running Microsoft Windows Server 2003,
Question Number (ID) : 1 (jaamsp_mngnwi-088) You are the administrator for medium-sized network with many users who connect remotely. You have configured a server running Microsoft Windows Server 2003,
Network+ Guide to Networks 6 th Edition
 Network+ Guide to Networks 6 th Edition Chapter 10 Virtual Networks and Remote Access Objectives 1. Explain virtualization and identify characteristics of virtual network components 2. Create and configure
Network+ Guide to Networks 6 th Edition Chapter 10 Virtual Networks and Remote Access Objectives 1. Explain virtualization and identify characteristics of virtual network components 2. Create and configure
Data Server for PC5200 as Remote Terminal V1.00 9/22/05
 Data Server for PC5200 as Remote Terminal V1.00 9/22/05 Mirador Software, Inc. 1040 West End Blvd. Winston-Salem, NC 27101 Telephone: 770-850-9100 / FAX: 770-881-7958 Website: http://www.pc8800.com Copyright
Data Server for PC5200 as Remote Terminal V1.00 9/22/05 Mirador Software, Inc. 1040 West End Blvd. Winston-Salem, NC 27101 Telephone: 770-850-9100 / FAX: 770-881-7958 Website: http://www.pc8800.com Copyright
Examsheets Questions and Answers
 640-802 Examsheets Questions and Answers Number: 640-802 Passing Score: 800 Time Limit: 120 min File Version: 17.6 http://www.gratisexam.com/ 640-802 Questions and Answers Exam Name: Cisco Cisco Certified
640-802 Examsheets Questions and Answers Number: 640-802 Passing Score: 800 Time Limit: 120 min File Version: 17.6 http://www.gratisexam.com/ 640-802 Questions and Answers Exam Name: Cisco Cisco Certified
Configuration Guide TL-ER5120/TL-ER6020/TL-ER REV3.0.0
 Configuration Guide TL-ER5120/TL-ER6020/TL-ER6120 1910012186 REV3.0.0 June 2017 CONTENTS About This Guide Intended Readers... 1 Conventions... 1 More Information... 1 Viewing Status Information... 2 System
Configuration Guide TL-ER5120/TL-ER6020/TL-ER6120 1910012186 REV3.0.0 June 2017 CONTENTS About This Guide Intended Readers... 1 Conventions... 1 More Information... 1 Viewing Status Information... 2 System
DPX8000 Series Deep Service Switching Gateway User Configuration Guide Firewall Service Board Module v1.0
 DPX8000 Series Deep Service Switching Gateway User Configuration Guide Firewall Service Board Module v1.0 i Hangzhou DPtech Technologies Co., Ltd. provides full- range technical support. If you need any
DPX8000 Series Deep Service Switching Gateway User Configuration Guide Firewall Service Board Module v1.0 i Hangzhou DPtech Technologies Co., Ltd. provides full- range technical support. If you need any
Defining Networks with the OSI Model. Module 2
 Defining Networks with the OSI Model Module 2 Objectives Skills Concepts Objective Domain Description Objective Domain Number Understanding OSI Basics Defining the Communications Subnetwork Defining the
Defining Networks with the OSI Model Module 2 Objectives Skills Concepts Objective Domain Description Objective Domain Number Understanding OSI Basics Defining the Communications Subnetwork Defining the
VPN Virtual Private Networks
 VPN Virtual Private Networks Mathias Schäfer WS 2003/2004 Overview 2 Overview Why VPNs VPN-use-cases Requirements Security Performance Conclusion Why VPNs 3 Why VPNs In business-solutions VPN-technology
VPN Virtual Private Networks Mathias Schäfer WS 2003/2004 Overview 2 Overview Why VPNs VPN-use-cases Requirements Security Performance Conclusion Why VPNs 3 Why VPNs In business-solutions VPN-technology
SonicWALL Addendum. A Supplement to the SonicWALL Internet Security Appliance User's Guide
 SonicWALL 6.2.0.0 Addendum A Supplement to the SonicWALL Internet Security Appliance User's Guide Contents SonicWALL Addendum 6.2.0.0... 3 New Network Features... 3 NAT with L2TP Client... 3 New Tools
SonicWALL 6.2.0.0 Addendum A Supplement to the SonicWALL Internet Security Appliance User's Guide Contents SonicWALL Addendum 6.2.0.0... 3 New Network Features... 3 NAT with L2TP Client... 3 New Tools
On Distributed Communications, Rand Report RM-3420-PR, Paul Baran, August 1964
 The requirements for a future all-digital-data distributed network which provides common user service for a wide range of users having different requirements is considered. The use of a standard format
The requirements for a future all-digital-data distributed network which provides common user service for a wide range of users having different requirements is considered. The use of a standard format
PART X. Internetworking Part 1. (Concept, IP Addressing, IP Routing, IP Datagrams, Address Resolution)
 PART X Internetworking Part 1 (Concept, IP Addressing, IP Routing, IP Datagrams, Address Resolution) CS422 Part 10 1 Spring 1999 Motivation For Internetworking LANs Low cost Limited distance WANs High
PART X Internetworking Part 1 (Concept, IP Addressing, IP Routing, IP Datagrams, Address Resolution) CS422 Part 10 1 Spring 1999 Motivation For Internetworking LANs Low cost Limited distance WANs High
6.1.2 Repeaters. Figure Repeater connecting two LAN segments. Figure Operation of a repeater as a level-1 relay
 6.1.2 Repeaters A single Ethernet segment can have a maximum length of 500 meters with a maximum of 100 stations (in a cheapernet segment it is 185m). To extend the length of the network, a repeater may
6.1.2 Repeaters A single Ethernet segment can have a maximum length of 500 meters with a maximum of 100 stations (in a cheapernet segment it is 185m). To extend the length of the network, a repeater may
Identify the features of network and client operating systems (Windows, NetWare, Linux, Mac OS)
 Course Outline Network+ Duration: 5 days (30 hours) Learning Objectives: Install and configure a network card Define the concepts of network layers Understand and implement the TCP/IP protocol Install
Course Outline Network+ Duration: 5 days (30 hours) Learning Objectives: Install and configure a network card Define the concepts of network layers Understand and implement the TCP/IP protocol Install
Ethernet. Network Fundamentals Chapter Cisco Systems, Inc. All rights reserved. Cisco Public 1
 Ethernet Network Fundamentals Chapter 9 1 Objectives Identify the basic characteristics of network media used in Ethernet. Describe the physical and data link features of Ethernet. Describe the function
Ethernet Network Fundamentals Chapter 9 1 Objectives Identify the basic characteristics of network media used in Ethernet. Describe the physical and data link features of Ethernet. Describe the function
Configuring Port-Based and Client-Based Access Control (802.1X)
 9 Configuring Port-Based and Client-Based Access Control (802.1X) Contents Overview..................................................... 9-3 Why Use Port-Based or Client-Based Access Control?............
9 Configuring Port-Based and Client-Based Access Control (802.1X) Contents Overview..................................................... 9-3 Why Use Port-Based or Client-Based Access Control?............
Networking Basics. Crystal Printer Network Installation Guidelines
 Networking Basics & Crystal Printer Network Installation Guidelines 1. Overview This guide is intended to provide the necessary basic knowledge of wireless networking needed to enable the Crystal printer
Networking Basics & Crystal Printer Network Installation Guidelines 1. Overview This guide is intended to provide the necessary basic knowledge of wireless networking needed to enable the Crystal printer
IP Addressing and Subnetting
 IP Addressing and Subnetting Internet Layer The purpose of the Internet layer is to send packets from a network node and have them arrive at the destination node independent of the path taken. Internet
IP Addressing and Subnetting Internet Layer The purpose of the Internet layer is to send packets from a network node and have them arrive at the destination node independent of the path taken. Internet
Data Communications. Connecting Devices
 Data Communications Connecting Devices Connecting Devices Networks do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs, or segments of LANs, we use
Data Communications Connecting Devices Connecting Devices Networks do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs, or segments of LANs, we use
Configure ISDN Connectivity between Remote Sites
 Case Study 1 Configure ISDN Connectivity between Remote Sites Cisco Networking Academy Program CCNP 2: Remote Access v3.1 Objectives In this case study, the following concepts are covered: Asynchronous
Case Study 1 Configure ISDN Connectivity between Remote Sites Cisco Networking Academy Program CCNP 2: Remote Access v3.1 Objectives In this case study, the following concepts are covered: Asynchronous
The trace is here: https://kevincurran.org/com320/labs/wireshark/trace-dhcp.pcap
 Lab Exercise DHCP Objective To see how DHCP (Dynamic Host Configuration Protocol) works. The trace is here: https://kevincurran.org/com320/labs/wireshark/trace-dhcp.pcap Network Setup Recall that DHCP
Lab Exercise DHCP Objective To see how DHCP (Dynamic Host Configuration Protocol) works. The trace is here: https://kevincurran.org/com320/labs/wireshark/trace-dhcp.pcap Network Setup Recall that DHCP
Industrial Control System Security white paper
 Industrial Control System Security white paper The top 10 threats to automation and process control systems and their countermeasures with INSYS routers Introduction With the advent of M2M (machine to
Industrial Control System Security white paper The top 10 threats to automation and process control systems and their countermeasures with INSYS routers Introduction With the advent of M2M (machine to
CISCO SYSTEM ADMINISTRATION (41)
 CISCO SYSTEM ADMININSTRATION PAGE 1 OF 11 CONTESTANT ID# Time Rank CISCO SYSTEM ADMINISTRATION (41) Regional 2012 TOTAL POINTS (500) Failure to adhere to any of the following rules will result in disqualification:
CISCO SYSTEM ADMININSTRATION PAGE 1 OF 11 CONTESTANT ID# Time Rank CISCO SYSTEM ADMINISTRATION (41) Regional 2012 TOTAL POINTS (500) Failure to adhere to any of the following rules will result in disqualification:
QUESTION BANK ENGINEERS ACADEMY. Computer Networks Computer Network Basics Segentation is done in. 12. Session layer is used for
 Computer Networks Computer Network Basics 1 QUESTION BANK 1. Segentation is done in (a) transport layer (c) data link layer 2. Network layer activities are: (d) physical layer (a) logical addressing (b)
Computer Networks Computer Network Basics 1 QUESTION BANK 1. Segentation is done in (a) transport layer (c) data link layer 2. Network layer activities are: (d) physical layer (a) logical addressing (b)
Lehrstuhl für Informatik 4 Kommunikation und verteilte Systeme. Auxiliary Protocols
 Auxiliary Protocols IP serves only for sending packets with well-known addresses. Some questions however remain open, which are handled by auxiliary protocols: Address Resolution Protocol (ARP) Reverse
Auxiliary Protocols IP serves only for sending packets with well-known addresses. Some questions however remain open, which are handled by auxiliary protocols: Address Resolution Protocol (ARP) Reverse
A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e. Chapter 8 Networking Essentials
 A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e Chapter 8 Networking Essentials Objectives Learn about the protocols and standards Windows uses for networking Learn how to connect
A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e Chapter 8 Networking Essentials Objectives Learn about the protocols and standards Windows uses for networking Learn how to connect
Network Devices,Frame Relay and X.25
 Network Devices,Frame Relay and X.25 Hardware/Networking Devices: Networking hardware may also be known as network equipment computer networking devices. Network Interface Card (NIC): NIC provides a physical
Network Devices,Frame Relay and X.25 Hardware/Networking Devices: Networking hardware may also be known as network equipment computer networking devices. Network Interface Card (NIC): NIC provides a physical
CS 458 Internet Engineering Spring First Exam
 CS 458 Internet Engineering Spring 2005 First Exam Instructions (read carefully): There are 6 problems for a total of 60 points. This is a closed book and closed notes in-class exam. If any problem is
CS 458 Internet Engineering Spring 2005 First Exam Instructions (read carefully): There are 6 problems for a total of 60 points. This is a closed book and closed notes in-class exam. If any problem is
The MAC Address Format
 Directing data is what addressing is all about. At the Data Link layer, this is done by pointing PDUs to the destination MAC address for delivery of a frame within a LAN. The MAC address is the number
Directing data is what addressing is all about. At the Data Link layer, this is done by pointing PDUs to the destination MAC address for delivery of a frame within a LAN. The MAC address is the number
Introduction to Information Technology Turban, Rainer and Potter John Wiley & Sons, Inc. Copyright 2005
 Introduction to Information Technology Turban, Rainer and Potter John Wiley & Sons, Inc. Copyright 2005 Network and Telecommunications Basics Chapter Outline The telecommunications system Network services
Introduction to Information Technology Turban, Rainer and Potter John Wiley & Sons, Inc. Copyright 2005 Network and Telecommunications Basics Chapter Outline The telecommunications system Network services
n Describe sniffing concepts, including active and passive sniffing n Describe sniffing countermeasures n Describe signature analysis within Snort
 Outline n Describe sniffing concepts, including active and passive sniffing and protocols susceptible to sniffing n Describe ethical hacking techniques for Layer 2 traffic Chapter #4: n Describe sniffing
Outline n Describe sniffing concepts, including active and passive sniffing and protocols susceptible to sniffing n Describe ethical hacking techniques for Layer 2 traffic Chapter #4: n Describe sniffing
User Guide TL-R470T+/TL-R480T REV9.0.2
 User Guide TL-R470T+/TL-R480T+ 1910012468 REV9.0.2 September 2018 CONTENTS About This Guide Intended Readers... 1 Conventions... 1 More Information... 1 Accessing the Router Overview... 3 Web Interface
User Guide TL-R470T+/TL-R480T+ 1910012468 REV9.0.2 September 2018 CONTENTS About This Guide Intended Readers... 1 Conventions... 1 More Information... 1 Accessing the Router Overview... 3 Web Interface
UIP1869V User Interface Guide
 UIP1869V User Interface Guide (Firmware version 0.1.8 and later) Table of Contents Opening the UIP1869V's Configuration Utility... 3 Connecting to Your Broadband Modem... 5 Setting up with DHCP... 5 Updating
UIP1869V User Interface Guide (Firmware version 0.1.8 and later) Table of Contents Opening the UIP1869V's Configuration Utility... 3 Connecting to Your Broadband Modem... 5 Setting up with DHCP... 5 Updating
Q-Balancer Range FAQ The Q-Balance LB Series General Sales FAQ
 Q-Balancer Range FAQ The Q-Balance LB Series The Q-Balance Balance Series is designed for Small and medium enterprises (SMEs) to provide cost-effective solutions for link resilience and load balancing
Q-Balancer Range FAQ The Q-Balance LB Series The Q-Balance Balance Series is designed for Small and medium enterprises (SMEs) to provide cost-effective solutions for link resilience and load balancing
Integrated Services. Integrated Services. RSVP Resource reservation Protocol. Expedited Forwarding. Assured Forwarding.
 Integrated Services An architecture for streaming multimedia Aimed at both unicast and multicast applications An example of unicast: a single user streaming a video clip from a news site An example of
Integrated Services An architecture for streaming multimedia Aimed at both unicast and multicast applications An example of unicast: a single user streaming a video clip from a news site An example of
CCENT Practice Certification Exam # 2 - CCNA Exploration: Accessing the WAN (Version 4.0)
 CCENT Practice Certification Exam # 2 - CCNA Exploration: Accessing the WAN (Version 4.0) 1. Data is being sent from a source PC to a destination server. Which three statements correctly describe the function
CCENT Practice Certification Exam # 2 - CCNA Exploration: Accessing the WAN (Version 4.0) 1. Data is being sent from a source PC to a destination server. Which three statements correctly describe the function
The Features and Uses of Computer Networking. Unit 11 Task 1
 The Features and Uses of Computer Networking Unit 11 Task 1 Features Office Network Peer to peer A peer to peer network is mostly used in homes or small businesses. The network consists of two or more
The Features and Uses of Computer Networking Unit 11 Task 1 Features Office Network Peer to peer A peer to peer network is mostly used in homes or small businesses. The network consists of two or more
CSE 123: Computer Networks
 CSE 123: Computer Networks Homework 3 Out: 11/19 Due: 11/26 Instructions 1. Turn in a physical copy at the beginning of the class on 11/26 2. Ensure the HW cover page has the following information clearly
CSE 123: Computer Networks Homework 3 Out: 11/19 Due: 11/26 Instructions 1. Turn in a physical copy at the beginning of the class on 11/26 2. Ensure the HW cover page has the following information clearly
Gigabit SSL VPN Security Router
 As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is the ideal to help the SMBs increase the
As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is the ideal to help the SMBs increase the
COPYRIGHTED MATERIAL. Con t e n t s. Chapter 1 Introduction to Networking 1. Chapter 2 Overview of Networking Components 21.
 Con t e n t s Introduction xix Chapter 1 Introduction to Networking 1 Comparing Logical and Physical Networks.... 1 Networking Home Computers........................................... 2 Networking Small
Con t e n t s Introduction xix Chapter 1 Introduction to Networking 1 Comparing Logical and Physical Networks.... 1 Networking Home Computers........................................... 2 Networking Small
Firewalls, Tunnels, and Network Intrusion Detection
 Firewalls, Tunnels, and Network Intrusion Detection 1 Firewalls A firewall is an integrated collection of security measures designed to prevent unauthorized electronic access to a networked computer system.
Firewalls, Tunnels, and Network Intrusion Detection 1 Firewalls A firewall is an integrated collection of security measures designed to prevent unauthorized electronic access to a networked computer system.
Router Router Microprocessor controlled traffic direction home router DSL modem Computer Enterprise routers Core routers
 Router Router is a Microprocessor controlled device that forwards data packets across the computer network. It is used to connect two or more data lines from different net works. The function of the router
Router Router is a Microprocessor controlled device that forwards data packets across the computer network. It is used to connect two or more data lines from different net works. The function of the router
Virtual private networks
 Technical papers Virtual private networks Virtual private networks Virtual private networks (VPNs) offer low-cost, secure, dynamic access to private networks. Such access would otherwise only be possible
Technical papers Virtual private networks Virtual private networks Virtual private networks (VPNs) offer low-cost, secure, dynamic access to private networks. Such access would otherwise only be possible
VPN and IPsec. Network Administration Using Linux. Virtual Private Network and IPSec 04/2009
 VPN and IPsec Network Administration Using Linux Virtual Private Network and IPSec 04/2009 What is VPN? VPN is an emulation of a private Wide Area Network (WAN) using shared or public IP facilities. A
VPN and IPsec Network Administration Using Linux Virtual Private Network and IPSec 04/2009 What is VPN? VPN is an emulation of a private Wide Area Network (WAN) using shared or public IP facilities. A
Table of Contents 1 VLAN Configuration 1-1
 Table of Contents 1 VLAN Configuration 1-1 Overview 1-1 Introduction to VLAN 1-1 VLAN Fundamentals 1-2 Types of VLAN 1-3 Introduction to Port-Based VLAN 1-3 Configuring a VLAN 1-4 Configuration Task List
Table of Contents 1 VLAN Configuration 1-1 Overview 1-1 Introduction to VLAN 1-1 VLAN Fundamentals 1-2 Types of VLAN 1-3 Introduction to Port-Based VLAN 1-3 Configuring a VLAN 1-4 Configuration Task List
1: Review Of Semester Provide an overview of encapsulation.
 1: Review Of Semester 1 1.1.1.1. Provide an overview of encapsulation. Networking evolves to support current and future applications. By dividing and organizing the networking tasks into separate layers/functions,
1: Review Of Semester 1 1.1.1.1. Provide an overview of encapsulation. Networking evolves to support current and future applications. By dividing and organizing the networking tasks into separate layers/functions,
Content 1 OVERVIEW HARDWARE DESCRIPTION HARDWARE INSTALLATION PC CONFIGURATION GUIDE... 5 WEB-BASED MANAGEMENT GUIDE...
 Content 1 OVERVIEW...1 1.1FEATURES...1 1.2 PACKETCONTENTS...3 1.3 SYSTEM REQUIREMENTS... 1.4 FACTORY DEFAULTS...4 1.5 WARNINGS AND CAUTIONS...4 2 HARDWARE DESCRIPTION... 6 3 HARDWARE INSTALLATION...8 4
Content 1 OVERVIEW...1 1.1FEATURES...1 1.2 PACKETCONTENTS...3 1.3 SYSTEM REQUIREMENTS... 1.4 FACTORY DEFAULTS...4 1.5 WARNINGS AND CAUTIONS...4 2 HARDWARE DESCRIPTION... 6 3 HARDWARE INSTALLATION...8 4
3.5 CONNECTING DEVICES
 3.5 CONNECTING DEVICES LANs or WANs do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs and WANs together we use connecting devices. Connecting devices
3.5 CONNECTING DEVICES LANs or WANs do not normally operate in isolation. They are connected to one another or to the Internet. To connect LANs and WANs together we use connecting devices. Connecting devices
Wireless Networks. Lecture 4: Wireless Networking Devices. Assistant Teacher Samraa Adnan Al-Asadi 1
 Wireless Networks Lecture 4: Wireless Networking Devices Assistant Teacher Samraa Adnan Al-Asadi 1 Contents wireless LAN adapter cards wireless access Points wireless bridges wireless routers Assistant
Wireless Networks Lecture 4: Wireless Networking Devices Assistant Teacher Samraa Adnan Al-Asadi 1 Contents wireless LAN adapter cards wireless access Points wireless bridges wireless routers Assistant
Chapter 4 Configuring 802.1X Port Security
 Chapter 4 Configuring 802.1X Port Security Overview HP devices support the IEEE 802.1X standard for authenticating devices attached to LAN ports. Using 802.1X port security, you can configure an HP device
Chapter 4 Configuring 802.1X Port Security Overview HP devices support the IEEE 802.1X standard for authenticating devices attached to LAN ports. Using 802.1X port security, you can configure an HP device
Wireless LAN Controller (WLC) Mobility Groups FAQ
 Wireless LAN Controller (WLC) Mobility Groups FAQ Document ID: 107188 Contents Introduction What is a Mobility Group? What are the prerequisites for a Mobility Group? How do I configure a Mobility Group
Wireless LAN Controller (WLC) Mobility Groups FAQ Document ID: 107188 Contents Introduction What is a Mobility Group? What are the prerequisites for a Mobility Group? How do I configure a Mobility Group
Advanced option settings on the command line. Set the interface and ports for the OpenVPN daemons
 Advanced option settings on the command line docs.openvpn.net/command-line/advanced-option-settings-on-the-command-line Set the interface and ports for the OpenVPN daemons In the Admin UI under Server
Advanced option settings on the command line docs.openvpn.net/command-line/advanced-option-settings-on-the-command-line Set the interface and ports for the OpenVPN daemons In the Admin UI under Server
IPv6 Feature Facts
 12.1.2 IPv6 Feature Facts The current IP addressing standard, version 4, will eventually run out of unique addresses, so a new system is being developed. It is named IP version 6 or IPv6. You should know
12.1.2 IPv6 Feature Facts The current IP addressing standard, version 4, will eventually run out of unique addresses, so a new system is being developed. It is named IP version 6 or IPv6. You should know
DPX8000 Series Deep Service Switching Gateway User Configuration Guide BRAS Service Board Module v1.0
 DPX8000 Series Deep Service Switching Gateway User Configuration Guide BRAS Service Board Module v1.0 i Hangzhou DPtech Technologies Co., Ltd. provides full- range technical support. If you need any help,
DPX8000 Series Deep Service Switching Gateway User Configuration Guide BRAS Service Board Module v1.0 i Hangzhou DPtech Technologies Co., Ltd. provides full- range technical support. If you need any help,
Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide
 Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide Table of Contents SUPPORTED DEVICES... 5 INTRODUCTION... 6 GWN7000 VPN FEATURE... 7 OPENVPN CONFIGURATION... 8 OpenVPN
Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide Table of Contents SUPPORTED DEVICES... 5 INTRODUCTION... 6 GWN7000 VPN FEATURE... 7 OPENVPN CONFIGURATION... 8 OpenVPN
PART IV. Internetworking Using TCP/IP
 PART IV Internetworking Using TCP/IP Internet architecture, addressing, binding, encapsulation, and protocols in the TCP/IP suite Chapters 20 Internetworking: Concepts, Architecture, and Protocols 21 IP:
PART IV Internetworking Using TCP/IP Internet architecture, addressing, binding, encapsulation, and protocols in the TCP/IP suite Chapters 20 Internetworking: Concepts, Architecture, and Protocols 21 IP:
MTA_98-366_Vindicator930
 MTA_98-366_Vindicator930 Number: 98-366 Passing Score: 700 Time Limit: 45 min File Version: 1.0 http://www.gratisexam.com/ Microsoft Technology Associate Networking Fundamentals MTA 98-366 Exam A QUESTION
MTA_98-366_Vindicator930 Number: 98-366 Passing Score: 700 Time Limit: 45 min File Version: 1.0 http://www.gratisexam.com/ Microsoft Technology Associate Networking Fundamentals MTA 98-366 Exam A QUESTION
RS232+LAN INTERFACE USER MANUAL
 LAN202 USER MANUAL May 2006 - Ed. 1 English 1 SUMMARY 1 LAN202 module... 3 1.1 Connections via Ethernet... 4 2 Configuration... 5 2.1 Saving and protection of the configuration... 8 3 Virtual COM... 9
LAN202 USER MANUAL May 2006 - Ed. 1 English 1 SUMMARY 1 LAN202 module... 3 1.1 Connections via Ethernet... 4 2 Configuration... 5 2.1 Saving and protection of the configuration... 8 3 Virtual COM... 9
The Data Link Layer. 32 PART I Networking Basics
 32 PART I Networking Basics weather station. More realistic devices use duplex mode, where all systems can send or receive with equal facility. This is often further distinguished as half-duplex (the system
32 PART I Networking Basics weather station. More realistic devices use duplex mode, where all systems can send or receive with equal facility. This is often further distinguished as half-duplex (the system
 Seite von 7 05.0.200 Close Window Assessment System Exam Viewer - CCNA Practice Certification Exam # - (Version 4.0) Below you will find the assessment items as presented on the exam as well as the scoring
Seite von 7 05.0.200 Close Window Assessment System Exam Viewer - CCNA Practice Certification Exam # - (Version 4.0) Below you will find the assessment items as presented on the exam as well as the scoring
Fundamentals of Networking Introduction to Networking Devices
 Fundamentals of Networking Introduction to Networking Devices Kuldeep Sonar 1 NIC (Network Interface Card) A network interface provides connectivity from an end-user PC or laptop to the public network.
Fundamentals of Networking Introduction to Networking Devices Kuldeep Sonar 1 NIC (Network Interface Card) A network interface provides connectivity from an end-user PC or laptop to the public network.
Introduction to Computer Networks. CS 166: Introduction to Computer Systems Security
 Introduction to Computer Networks CS 166: Introduction to Computer Systems Security Network Communication Communication in modern networks is characterized by the following fundamental principles Packet
Introduction to Computer Networks CS 166: Introduction to Computer Systems Security Network Communication Communication in modern networks is characterized by the following fundamental principles Packet
Cisco EXAM CCNA Cisco Certified Network Associate. Buy Full Product.
 Cisco EXAM - 200-120 CCNA Cisco Certified Network Associate Buy Full Product http://www.examskey.com/200-120.html Examskey Cisco 200-120 exam demo product is here for you to test the quality of the product.
Cisco EXAM - 200-120 CCNA Cisco Certified Network Associate Buy Full Product http://www.examskey.com/200-120.html Examskey Cisco 200-120 exam demo product is here for you to test the quality of the product.
SC/CSE 3213 Winter Sebastian Magierowski York University CSE 3213, W13 L8: TCP/IP. Outline. Forwarding over network and data link layers
 SC/CSE 3213 Winter 2013 L8: TCP/IP Overview Sebastian Magierowski York University 1 Outline TCP/IP Reference Model A set of protocols for internetworking The basis of the modern IP Datagram Exchange Examples
SC/CSE 3213 Winter 2013 L8: TCP/IP Overview Sebastian Magierowski York University 1 Outline TCP/IP Reference Model A set of protocols for internetworking The basis of the modern IP Datagram Exchange Examples
Unicasts, Multicasts and Broadcasts
 Unicasts, Multicasts and Broadcasts Part 1: Frame-Based LAN Operation V1.0: Geoff Bennett Contents LANs as a Shared Medium A "Private" Conversation Multicast Addressing Performance Issues In this tutorial
Unicasts, Multicasts and Broadcasts Part 1: Frame-Based LAN Operation V1.0: Geoff Bennett Contents LANs as a Shared Medium A "Private" Conversation Multicast Addressing Performance Issues In this tutorial
Mixed-Media Bridging
 CHAPTER 31 Mixed-Media Bridging Background Transparent bridges are found predominantly in Ethernet networks, and source-route bridges (SRBs) are found almost exclusively in Ring networks. For more information
CHAPTER 31 Mixed-Media Bridging Background Transparent bridges are found predominantly in Ethernet networks, and source-route bridges (SRBs) are found almost exclusively in Ring networks. For more information
To make a difference between logical address (IP address), which is used at the network layer, and physical address (MAC address),which is used at
 To make a difference between logical address (IP address), which is used at the network layer, and physical address (MAC address),which is used at the data link layer. To describe how the mapping of a
To make a difference between logical address (IP address), which is used at the network layer, and physical address (MAC address),which is used at the data link layer. To describe how the mapping of a
APPENDIX F THE TCP/IP PROTOCOL ARCHITECTURE
 APPENDIX F THE TCP/IP PROTOCOL ARCHITECTURE William Stallings F.1 TCP/IP LAYERS... 2 F.2 TCP AND UDP... 4 F.3 OPERATION OF TCP/IP... 6 F.4 TCP/IP APPLICATIONS... 10 Copyright 2014 Supplement to Computer
APPENDIX F THE TCP/IP PROTOCOL ARCHITECTURE William Stallings F.1 TCP/IP LAYERS... 2 F.2 TCP AND UDP... 4 F.3 OPERATION OF TCP/IP... 6 F.4 TCP/IP APPLICATIONS... 10 Copyright 2014 Supplement to Computer
Table of Contents X Configuration 1-1
 Table of Contents 1 802.1X Configuration 1-1 802.1X Overview 1-1 Architecture of 802.1X 1-2 Authentication Modes of 802.1X 1-2 Basic Concepts of 802.1X 1-3 EAP over LAN 1-4 EAP over RADIUS 1-5 802.1X Authentication
Table of Contents 1 802.1X Configuration 1-1 802.1X Overview 1-1 Architecture of 802.1X 1-2 Authentication Modes of 802.1X 1-2 Basic Concepts of 802.1X 1-3 EAP over LAN 1-4 EAP over RADIUS 1-5 802.1X Authentication
Configuring Virtual Private LAN Services
 Virtual Private LAN Services (VPLS) enables enterprises to link together their Ethernet-based LANs from multiple sites via the infrastructure provided by their service provider. This module explains VPLS
Virtual Private LAN Services (VPLS) enables enterprises to link together their Ethernet-based LANs from multiple sites via the infrastructure provided by their service provider. This module explains VPLS
EdgeXOS Platform QuickStart Guide
 EdgeXOS Platform QuickStart Guide EdgeXOS Functionality Overview The EdgeXOS platform is a Unified Bandwidth Management device, meaning that it has the ability to support multiple bandwidth management
EdgeXOS Platform QuickStart Guide EdgeXOS Functionality Overview The EdgeXOS platform is a Unified Bandwidth Management device, meaning that it has the ability to support multiple bandwidth management
Introduction To Routers
 Introduction To Routers Introduction Welcome to the Routers section. Here we will analyse routers quite some depth; what they do and how they work. I point out to you that you should have some knowlege
Introduction To Routers Introduction Welcome to the Routers section. Here we will analyse routers quite some depth; what they do and how they work. I point out to you that you should have some knowlege
Virtual Private Networks (VPNs)
 CHAPTER 19 Virtual Private Networks (VPNs) Virtual private network is defined as customer connectivity deployed on a shared infrastructure with the same policies as a private network. The shared infrastructure
CHAPTER 19 Virtual Private Networks (VPNs) Virtual private network is defined as customer connectivity deployed on a shared infrastructure with the same policies as a private network. The shared infrastructure
Internetworking is connecting two or more computer networks with some sort of routing device to exchange traffic back and forth, and guide traffic on
 CBCN4103 Internetworking is connecting two or more computer networks with some sort of routing device to exchange traffic back and forth, and guide traffic on the correct path across the complete network
CBCN4103 Internetworking is connecting two or more computer networks with some sort of routing device to exchange traffic back and forth, and guide traffic on the correct path across the complete network
Chapter 3. Underlying Technology. TCP/IP Protocol Suite 1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display.
 Chapter 3 Underlying Technology TCP/IP Protocol Suite 1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. OBJECTIVES: To briefly discuss the technology of dominant
Chapter 3 Underlying Technology TCP/IP Protocol Suite 1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. OBJECTIVES: To briefly discuss the technology of dominant
SYSTEMS ADMINISTRATION USING CISCO (315)
 Page 1 of 10 Contestant Number: Time: Rank: SYSTEMS ADMINISTRATION USING CISCO (315) REGIONAL 2014 TOTAL POINTS (500) Failure to adhere to any of the following rules will result in disqualification: 1.
Page 1 of 10 Contestant Number: Time: Rank: SYSTEMS ADMINISTRATION USING CISCO (315) REGIONAL 2014 TOTAL POINTS (500) Failure to adhere to any of the following rules will result in disqualification: 1.
FINAL EXAM REVIEW PLEASE NOTE THE MATERIAL FROM LECTURE #16 at the end. Exam 1 Review Material
 FINAL EXAM REVIEW PLEASE NOTE THE MATERIAL FROM LECTURE #16 at the end Chapters in the book 1, 2, 3, 5, 6 Exam 1 Review Material Topics You are also responsible for the reading in the chapters understanding
FINAL EXAM REVIEW PLEASE NOTE THE MATERIAL FROM LECTURE #16 at the end Chapters in the book 1, 2, 3, 5, 6 Exam 1 Review Material Topics You are also responsible for the reading in the chapters understanding
Virtual Private Networks.
 Virtual Private Networks thm@informatik.uni-rostock.de http://wwwiuk.informatik.uni-rostock.de/ Content Virtual Private Networks VPN Basics Protocols (IPSec, PPTP, L2TP) Objectives of VPNs Earlier Companies
Virtual Private Networks thm@informatik.uni-rostock.de http://wwwiuk.informatik.uni-rostock.de/ Content Virtual Private Networks VPN Basics Protocols (IPSec, PPTP, L2TP) Objectives of VPNs Earlier Companies
IP Routing & Bridging
 CHAPTER 2 TCP/IP Routing: Ethernet Dialog Box To access this dialog box (Figure 2-1), select Ethernet/TCP/IP Routing from the Device View. Figure 2-1 TCP/IP Routing: Ethernet Configuration Dialog Box If
CHAPTER 2 TCP/IP Routing: Ethernet Dialog Box To access this dialog box (Figure 2-1), select Ethernet/TCP/IP Routing from the Device View. Figure 2-1 TCP/IP Routing: Ethernet Configuration Dialog Box If
LAN Emulation Overview
 This overview chapter gives a high-level description of (LANE). Procedures for configuring LANE are provided in the following chapters in this publication: Configuring chapter Configuring Token Ring chapter
This overview chapter gives a high-level description of (LANE). Procedures for configuring LANE are provided in the following chapters in this publication: Configuring chapter Configuring Token Ring chapter
Automatic Repeat Request Data Link Layer Traffic Management
 Automatic Repeat Request Data Link Layer Traffic Management Reliable Communications with Retransmission How to transport data units over an unreliable data link in a reliable way? End to End E.g.. TCP
Automatic Repeat Request Data Link Layer Traffic Management Reliable Communications with Retransmission How to transport data units over an unreliable data link in a reliable way? End to End E.g.. TCP
