Setup L2TP/IPsec VPN Server on SoftEther VPN Server
|
|
|
- Bryan Rose
- 6 years ago
- Views:
Transcription
1 Setup L2TP/IPsec VPN Server on SoftEther VPN Server The IPsec VPN Server Function is disabled by default. You can enable it easily as the following steps. Configuration Guide The VPN Server configuration is very easy. Start VPN Server Manager Start SoftEther VPN Server Manager (which runs on Windows, but it can connect to remote SoftEther VPN Server running on Linux, Mac OS X or other UNIX). On the Server Manager, you can see the "L2TP/IPsec Setting" button. Click it. 01.png VPN Server Manager Main Window The following screen will appear. Each IPsec Server Function can be turned on / off on this screen.
2 02.png IPsec / L2TP / EtherIP / L2TPv3 Settings Screen The meanings of each option are followings: L2TP Server Function (L2TP over IPsec) This function is for accepting VPN connections from iphone, ipad, Android, and other smartphones, and built-in L2TP/IPsec VPN Client on Windows or Mac OS X. Enable it if you want to support one of these devices as VPN Client. L2TP Server Function (Raw L2TP with No Encryption) Some special-configured VPN router or client devices have only just a L2TP protocol without IPsec encryption. To support such a strange device, you have to enable it. EtherIP / L2TPv3 over IPsec Server Function If you want to build site-to-site VPN connection (Layer-2 Ethernet remotebridging), enable EtherIP / L2TPv3 over IPsec. You have to add your edge-side device definition on the list. IPsec Pre-Shared Key IPsec Pre-Shared Key is sometimes be called "PSK" or "Secret". This string is
3 "vpn" by default. However, changing it is recommended. You have to inform the latest key to all VPN users. How to enable and configure IPsec with vpncmd If you cannot use VPN Server Manager GUI for Windows, alternatively you can use vpncmd to activate and configure the IPsec VPN Server Function, by the IPSecEnable command. To learn how to do it in vpncmd, run "IPsecEnable?" command in the vpncmd prompt. How does a L2TP/IPsec VPN user have to specify his username to login? (with Standard Password Authentication) The principal is; when a VPN user wants to establish a VPN connection to the SoftEther VPN Server with IPsec/L2TP VPN Server Function he have to specify the destination Virtual Hub Name in the username field. For example, assume that the SoftEther VPN Server has two Virtual Hubs: "HUB1" and "HUB2". And there is a user "yas" in "HUB1", and "jiro" in "HUB2". In that case, specify the destination Virtual Hub Name after the username with appending '@' character, suchlike "yas@hub1" or "jiro@hub2". Note that both user-name and hub-name are case insensitive. However, you can specify the "Default Virtual Hub" on the IPsec setting screen. If the destination Virtual Hub Name in the login-attempting username is omitted, then the default Virtual Hub is to be assumed to be designated by the user. For example in the case if the default Virtual Hub is "HUB2", the user "jiro" on the HUB2 can be logged on by just "jiro". "@HUB2" can be omitted. How does a L2TP/IPsec VPN user have to specify his username to login? (with RADIUS OR NT Domain Authentication) The principal is; when a VPN user wants to establish a VPN connection to the SoftEther VPN Server with IPsec/L2TP VPN Server Function he have to specify the destination Virtual Hub Name in the username field. For example, assume that the SoftEther VPN Server has two Virtual Hubs: "HUB1" and "HUB2". And there is a user "yas" in "HUB1", and "jiro" in "HUB2". In that case, specify the destination Virtual Hub Name before the username with appending '\' character, suchlike "HUB1\yas" or "HUB2\jiro". Note that both username and hub-name are case insensitive.
4 However, you can specify the "Default Virtual Hub" on the IPsec setting screen. If the destination Virtual Hub Name in the login-attempting username is omitted, then the default Virtual Hub is to be assumed to be designated by the user. For example in the case if the default Virtual Hub is "HUB2", the user "jiro" on the HUB2 can be logged on by just "jiro". "HUB2\" can be omitted. User Authentication with L2TP/IPsec VPN Function You have to create a user-object before the user attempts to connect a VPN connection by using L2TP/IPsec function. You cannot use certificate authentication for L2TP/IPsec VPN Function on the current version of SoftEther VPN Server. Configuration for EtherIP / L2TPv3 EtherIP and L2TPv3 is for accepting VPN routers to build site-to-site VPNs. You can click the "EtherIP / L2TPv3 Detail Settings" button on the configuration screen to add the client-device entry on the list. On a client-device entry on the list, the ISAKMP (IKE) Phase 1 ID string, and the related credentials (username and password on a user which has been registered on the destination Virtual Hub.) You can specify the asterisk ('*') as the wildcard on the username on an entry. Such an entry will be applied for any VPN client router's login attempts from remote side. 03.png EtherIP / L2TPv3 Server Detail Settings
5 Note Disable any IPsec/L2TP function on the server computer which might conflict with SoftEther VPN Server's IPsec/L2TP function. If the UDP ports (500, 4500 and 1701) conflicts with other programs, IPsec communication will not work well. For example, disable the "Routing and Remote Access" service on Windows Server. If you enable IPsec/L2TP function of SoftEther VPN Server, the IPsec/L2TP function of Windows will be shutdown temporary. IP Address Assignment for L2TP Logged-in Users In L2TP function, an IP address of a VPN Client must be assigned automatically by a DHCP server on the destination Virtual Hub's segment. Therefore, you have to at least one running DHCP server on the destination L2 segment which the L2TP VPN Client attempts to login. An IP address will be leased from the DHCP server, and the IP address will be assigned on the L2TP VPN client session. Default gateway, subnet mask, DNS address and WINS address will be also applied on the L2TP VPN client. So if no DHCP server, no login successes. You can use any DHCP Server which is already existing on your local network. You can use SecureNAT's Virtual DHCP Server Function which is implemented on SoftEther VPN Server if you don't any DHCP servers on the LAN. How to Traverse a NAT / Firewall? If your SoftEther VPN Server is behind the NAT or firewall, you have to expose the UDP port 500 and On the NAT, UDP 500 and 4500 should be transferred to the VPN Server. If any packet filters or firewalls are existing, open UDP 500 and 4500 ports.
Setting up L2TP Over IPSec Server for remote access to LAN
 Setting up L2TP Over IPSec Server for remote access to LAN Remote clients: Android 5.0, ios v10.3, Mac OS v10.12.2 and Windows 7. Step 1. Log into the firewall. The default access to LAN is via https://192.168.10.1.
Setting up L2TP Over IPSec Server for remote access to LAN Remote clients: Android 5.0, ios v10.3, Mac OS v10.12.2 and Windows 7. Step 1. Log into the firewall. The default access to LAN is via https://192.168.10.1.
How to use VPN L2TP over IPsec
 How to use VPN L2TP over IPsec Server/Client on TW-EAV510 AC Note: 1. Please make sure that both LAN side networks are in different subnet. 2. Just some OS support L2TP Tunnel authentication, like Android
How to use VPN L2TP over IPsec Server/Client on TW-EAV510 AC Note: 1. Please make sure that both LAN side networks are in different subnet. 2. Just some OS support L2TP Tunnel authentication, like Android
1. Ultimate Powerful VPN Connectivity
 1.1. Firewall, Proxy and NAT Transparency One of the key features of SoftEther VPN is the transparency for firewalls, proxy servers and NATs (Network Address Translators). NATs are sometimes implemented
1.1. Firewall, Proxy and NAT Transparency One of the key features of SoftEther VPN is the transparency for firewalls, proxy servers and NATs (Network Address Translators). NATs are sometimes implemented
How to Configure a Client-to-Site L2TP/IPsec VPN
 Follow the instructions in this article to configure a client-to-site L2TP/IPsec VPN. With this configuration, IPsec encrypts the payload data of the VPN because L2TP does not provide encryption. In this
Follow the instructions in this article to configure a client-to-site L2TP/IPsec VPN. With this configuration, IPsec encrypts the payload data of the VPN because L2TP does not provide encryption. In this
Use Shrew Soft VPN Client to Connect with IPSec VPN Server on RV130 and RV130W
 Use Shrew Soft VPN Client to Connect with IPSec VPN Server on RV130 and RV130W Objective IPSec VPN (Virtual Private Network) enables you to securely obtain remote resources by establishing an encrypted
Use Shrew Soft VPN Client to Connect with IPSec VPN Server on RV130 and RV130W Objective IPSec VPN (Virtual Private Network) enables you to securely obtain remote resources by establishing an encrypted
Configuration of Shrew VPN Client on RV042, RV042G and RV082 VPN Routers through Windows
 Configuration of Shrew VPN Client on RV042, RV042G and RV082 VPN Routers through Windows Objective A Virtual Private Network (VPN) is a method for remote users to virtually connect to a private network
Configuration of Shrew VPN Client on RV042, RV042G and RV082 VPN Routers through Windows Objective A Virtual Private Network (VPN) is a method for remote users to virtually connect to a private network
Configuration Guide SuperStack 3 Firewall L2TP/IPSec VPN Client
 Overview This guide is used as a supplement to the SuperStack 3 Firewall manual, and details how to configure the native Windows VPN client to work with the Firewall, via the Microsoft recommended Layer
Overview This guide is used as a supplement to the SuperStack 3 Firewall manual, and details how to configure the native Windows VPN client to work with the Firewall, via the Microsoft recommended Layer
TopGlobal MB8000 VPN Solution
 TopGlobal Solution Top Global MobileBridge connects 3G and Ethernet network, as well as WiFi network. MB8000 is a product of MobileBridge serials. MB8000 provides a gateway service for its LAN (including
TopGlobal Solution Top Global MobileBridge connects 3G and Ethernet network, as well as WiFi network. MB8000 is a product of MobileBridge serials. MB8000 provides a gateway service for its LAN (including
Remote Access via Cisco VPN Client
 Remote Access via Cisco VPN Client General Information This guide describes step by step the configuration of a remote access to the Astaro Security Gateway by using the Cisco VPN Client. The Cisco VPN
Remote Access via Cisco VPN Client General Information This guide describes step by step the configuration of a remote access to the Astaro Security Gateway by using the Cisco VPN Client. The Cisco VPN
REMOTE ACCESS IPSEC. Course /14/2014 Global Technology Associates, Inc.
 REMOTE ACCESS IPSEC Course 4002 1 Remote Access Features! Granular Network Access and Authorization based on groups and policies.! Windows, Linux, and MAC client support. Windows ShrewSoft Client MAC IPSecuritas
REMOTE ACCESS IPSEC Course 4002 1 Remote Access Features! Granular Network Access and Authorization based on groups and policies.! Windows, Linux, and MAC client support. Windows ShrewSoft Client MAC IPSecuritas
Client VPN OS Configuration. Android
 Client VPN OS Configuration This article outlines instructions to configure a client VPN connection on commonly-used operating systems. For more information about client VPN, please refer to our documentation.
Client VPN OS Configuration This article outlines instructions to configure a client VPN connection on commonly-used operating systems. For more information about client VPN, please refer to our documentation.
MWA Deployment Guide. VPN Termination from Smartphone to Cisco ISR G2 Router
 MWA Deployment Guide Mobile Workforce Architecture: VPN Deployment Guide for Microsoft Windows Mobile and Android Devices with Cisco Integrated Services Router Generation 2 This deployment guide explains
MWA Deployment Guide Mobile Workforce Architecture: VPN Deployment Guide for Microsoft Windows Mobile and Android Devices with Cisco Integrated Services Router Generation 2 This deployment guide explains
How to Configure Mobile VPN for Forcepoint NGFW TECHNICAL DOCUMENT
 How to Configure Mobile VPN for Forcepoint NGFW TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS 1 BACKGROUND 2 WINDOWS SERVER CONFIGURATION STEPS 2 CONFIGURING USER AUTHENTICATION 3 ACTIVE DIRECTORY
How to Configure Mobile VPN for Forcepoint NGFW TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS 1 BACKGROUND 2 WINDOWS SERVER CONFIGURATION STEPS 2 CONFIGURING USER AUTHENTICATION 3 ACTIVE DIRECTORY
Configuring L2TP over IPsec
 CHAPTER 62 This chapter describes how to configure L2TP over IPsec on the ASA. This chapter includes the following topics: Information About L2TP over IPsec, page 62-1 Licensing Requirements for L2TP over
CHAPTER 62 This chapter describes how to configure L2TP over IPsec on the ASA. This chapter includes the following topics: Information About L2TP over IPsec, page 62-1 Licensing Requirements for L2TP over
Accessing an Extremely Secure LAN Via Remote Access That Was Not Possible With Previous Technologies
 Before, administrator rights were a necessity when setting up a remote access VPN. But by using the SecureNAT capability built in to SoftEther VPN Server and SoftEther VPN Bridge you can build a remote
Before, administrator rights were a necessity when setting up a remote access VPN. But by using the SecureNAT capability built in to SoftEther VPN Server and SoftEther VPN Bridge you can build a remote
UK TV ACCESS SET UP GUIDE
 UK TV ACCESS SET UP GUIDE For technical support please contact us at: support@uktvaccess.com If it is a new set up you are having trouble with, please tell us which device and operating system you are
UK TV ACCESS SET UP GUIDE For technical support please contact us at: support@uktvaccess.com If it is a new set up you are having trouble with, please tell us which device and operating system you are
WIALAN Technologies, Inc. Unit Configuration Thursday, March 24, 2005 Version 1.1
 WIALAN Technologies, Inc. Unit Configuration Thursday, March 24, 2005 Version 1.1 Table of Content I. Introduction...3 II. Logging into WiSAP... 3 III. WiSAP Overview... 5 Splash Screen... 5 System Status...
WIALAN Technologies, Inc. Unit Configuration Thursday, March 24, 2005 Version 1.1 Table of Content I. Introduction...3 II. Logging into WiSAP... 3 III. WiSAP Overview... 5 Splash Screen... 5 System Status...
OpenVPN protocol. Restrictions in Conel routers. Modified on: Thu, 14 Aug, 2014 at 2:29 AM
 1/2/2016 OpenVPN protocol : Support Portal OpenVPN protocol Modified on: Thu, 14 Aug, 2014 at 2:29 AM OpenVPN (Open Virtual Private Network) is a means of interconnection of several computers through an
1/2/2016 OpenVPN protocol : Support Portal OpenVPN protocol Modified on: Thu, 14 Aug, 2014 at 2:29 AM OpenVPN (Open Virtual Private Network) is a means of interconnection of several computers through an
L2TP over IPsec. About L2TP over IPsec/IKEv1 VPN
 This chapter describes how to configure /IKEv1 on the ASA. About /IKEv1 VPN, on page 1 Licensing Requirements for, on page 3 Prerequisites for Configuring, on page 4 Guidelines and Limitations, on page
This chapter describes how to configure /IKEv1 on the ASA. About /IKEv1 VPN, on page 1 Licensing Requirements for, on page 3 Prerequisites for Configuring, on page 4 Guidelines and Limitations, on page
firewall { all-ping enable broadcast-ping disable ipv6-receive-redirects disable ipv6-src-route disable ip-src-route disable log-martians enable name
 firewall { all-ping enable broadcast-ping disable ipv6-receive-redirects disable ipv6-src-route disable ip-src-route disable log-martians enable name WAN_IN { default-action drop description "WAN to internal"
firewall { all-ping enable broadcast-ping disable ipv6-receive-redirects disable ipv6-src-route disable ip-src-route disable log-martians enable name WAN_IN { default-action drop description "WAN to internal"
V7610 TELSTRA BUSINESS GATEWAY
 V7610 TELSTRA BUSINESS GATEWAY VPN Configuration Guide Date: Oct 16, 2015 Revision Num: 1.0 1 V7610 VPN Configuration Guide Rev1.0, October 2015 Revision History Date Release Author Description Oct 16,
V7610 TELSTRA BUSINESS GATEWAY VPN Configuration Guide Date: Oct 16, 2015 Revision Num: 1.0 1 V7610 VPN Configuration Guide Rev1.0, October 2015 Revision History Date Release Author Description Oct 16,
Configuration Guide. How to connect to an IPSec VPN using an iphone in ios. Overview
 Configuration Guide How to connect to an IPSec VPN using an iphone in ios Overview Currently, users can conveniently use the built-in IPSec client on an iphone to connect to a VPN server. IPSec VPN can
Configuration Guide How to connect to an IPSec VPN using an iphone in ios Overview Currently, users can conveniently use the built-in IPSec client on an iphone to connect to a VPN server. IPSec VPN can
Proxicast IPSec VPN Client Example
 Proxicast IPSec VPN Client Example Technote LCTN0013 Proxicast, LLC 312 Sunnyfield Drive Suite 200 Glenshaw, PA 15116 1-877-77PROXI 1-877-777-7694 1-412-213-2477 Fax: 1-412-492-9386 E-Mail: support@proxicast.com
Proxicast IPSec VPN Client Example Technote LCTN0013 Proxicast, LLC 312 Sunnyfield Drive Suite 200 Glenshaw, PA 15116 1-877-77PROXI 1-877-777-7694 1-412-213-2477 Fax: 1-412-492-9386 E-Mail: support@proxicast.com
Example - Configuring a Site-to-Site IPsec VPN Tunnel
 Example - Configuring a Site-to-Site IPsec VPN Tunnel To configure a Site-to-Site VPN connection between two Barracuda NextGen X-Series Firewalls, in which one unit (Location 1) has a dynamic Internet
Example - Configuring a Site-to-Site IPsec VPN Tunnel To configure a Site-to-Site VPN connection between two Barracuda NextGen X-Series Firewalls, in which one unit (Location 1) has a dynamic Internet
VPN Tracker for Mac OS X
 VPN Tracker for Mac OS X How-to: Interoperability with Check Point VPN-1 GateWay Rev. 1.1 Copyright 2003 equinux USA Inc. All rights reserved. 1. Introduction 1. Introduction This document describes how
VPN Tracker for Mac OS X How-to: Interoperability with Check Point VPN-1 GateWay Rev. 1.1 Copyright 2003 equinux USA Inc. All rights reserved. 1. Introduction 1. Introduction This document describes how
CHAPTER 7 ADVANCED ADMINISTRATION PC
 ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
VPN2S. Handbook VPN VPN2S. Default Login Details. Firmware V1.12(ABLN.0)b9 Edition 1, 5/ LAN Port IP Address
 VPN2S VPN2S VPN Firmware V1.12(ABLN.0)b9 Edition 1, 5/2018 Handbook Default Login Details LAN Port IP Address https://192.168.1.1 User Name admin Password 1234 Copyright 2018 ZyXEL Communications Corporation
VPN2S VPN2S VPN Firmware V1.12(ABLN.0)b9 Edition 1, 5/2018 Handbook Default Login Details LAN Port IP Address https://192.168.1.1 User Name admin Password 1234 Copyright 2018 ZyXEL Communications Corporation
ZyWALL 70. Internet Security Appliance. Quick Start Guide Version 3.62 December 2003
 ZyWALL 70 Internet Security Appliance Quick Start Guide Version 3.62 December 2003 Introducing the ZyWALL The ZyWALL 70 is the ideal secure gateway for all data passing between the Internet and the LAN.
ZyWALL 70 Internet Security Appliance Quick Start Guide Version 3.62 December 2003 Introducing the ZyWALL The ZyWALL 70 is the ideal secure gateway for all data passing between the Internet and the LAN.
G806+H3C WSR realize VPN networking
 G806+H3C WSR800-10 realize VPN networking File Version: V1.0.0 1 1.Configure H3C WSR 800-10 1.1.Enter H3C WSR 800-10 Web Server Power the H3C WSR 800-10 and connect PC Ethernet interface to H3C WSR 800-10
G806+H3C WSR800-10 realize VPN networking File Version: V1.0.0 1 1.Configure H3C WSR 800-10 1.1.Enter H3C WSR 800-10 Web Server Power the H3C WSR 800-10 and connect PC Ethernet interface to H3C WSR 800-10
Dialog Box Displaying the VPN Connection Status.
 By using SoftEther VPN Client to define the required connection settings of a connection setting and then connecting to that connection setting, you can start the connection to VPN Server. 4.5.1 Starting
By using SoftEther VPN Client to define the required connection settings of a connection setting and then connecting to that connection setting, you can start the connection to VPN Server. 4.5.1 Starting
FAQ about Communication
 FAQ about Communication Establishing a VPN Tunnel between PC Station and SCALANCE S 61x via the Internet Using the Microsoft Management Console FAQ Entry ID: 26098354 Table of Contents Table of Contents...
FAQ about Communication Establishing a VPN Tunnel between PC Station and SCALANCE S 61x via the Internet Using the Microsoft Management Console FAQ Entry ID: 26098354 Table of Contents Table of Contents...
Configuring Cisco VPN Concentrator to Support Avaya 96xx Phones Issue 1.0. Issue th October 2009 ABSTRACT
 Avaya CAD-SV Configuring Cisco VPN Concentrator to Support Avaya 96xx Phones Issue 1.0 Issue 1.0 30th October 2009 ABSTRACT These Application Notes describe the steps to configure the Cisco VPN 3000 Concentrator
Avaya CAD-SV Configuring Cisco VPN Concentrator to Support Avaya 96xx Phones Issue 1.0 Issue 1.0 30th October 2009 ABSTRACT These Application Notes describe the steps to configure the Cisco VPN 3000 Concentrator
Configuring VPN from Proventia M Series Appliance to NetScreen Systems
 Configuring VPN from Proventia M Series Appliance to NetScreen Systems January 13, 2004 Overview This document describes how to configure a VPN tunnel from a Proventia M series appliance to NetScreen 208
Configuring VPN from Proventia M Series Appliance to NetScreen Systems January 13, 2004 Overview This document describes how to configure a VPN tunnel from a Proventia M series appliance to NetScreen 208
Yamaha Router Configuration Training ~ Web GUI ~
 Yamaha Router Configuration Training ~ Web GUI ~ Equipment RTX810 Gigabit VPN Router SWX2200-8G/24G Smart L2 Switch GbE 5, USB 3G modem 1Gbps throughput All GbE Cooperation with RTX810 200Mbps VPN throughput
Yamaha Router Configuration Training ~ Web GUI ~ Equipment RTX810 Gigabit VPN Router SWX2200-8G/24G Smart L2 Switch GbE 5, USB 3G modem 1Gbps throughput All GbE Cooperation with RTX810 200Mbps VPN throughput
Identify the features of network and client operating systems (Windows, NetWare, Linux, Mac OS)
 Course Outline Network+ Duration: 5 days (30 hours) Learning Objectives: Install and configure a network card Define the concepts of network layers Understand and implement the TCP/IP protocol Install
Course Outline Network+ Duration: 5 days (30 hours) Learning Objectives: Install and configure a network card Define the concepts of network layers Understand and implement the TCP/IP protocol Install
YAMAHA RTX??????? L2TPv3???? VPN???? (IPv4, IPv6??)
 YAMAHA RTX??????? L2TPv3???? VPN???? (IPv4, IPv6??) SoftEther VPN Server? Build 9582??????????YAMAHA????? (RTX????)????? L2TPv3 over IPsec VPN????? (?????? 2??????)?????????????????????????????????????
YAMAHA RTX??????? L2TPv3???? VPN???? (IPv4, IPv6??) SoftEther VPN Server? Build 9582??????????YAMAHA????? (RTX????)????? L2TPv3 over IPsec VPN????? (?????? 2??????)?????????????????????????????????????
5. Easy Installation and Management
 5. Easy Installation and Management 5.1. Provided as Software Programs SoftEther VPN is not a hardware VPN product. You can download it and install it today on your computer. If you want to try SoftEther
5. Easy Installation and Management 5.1. Provided as Software Programs SoftEther VPN is not a hardware VPN product. You can download it and install it today on your computer. If you want to try SoftEther
Configuring a VPN Using Easy VPN and an IPSec Tunnel, page 1
 Configuring a VPN Using Easy VPN and an IPSec Tunnel This chapter provides an overview of the creation of Virtual Private Networks (VPNs) that can be configured on the Cisco 819, Cisco 860, and Cisco 880
Configuring a VPN Using Easy VPN and an IPSec Tunnel This chapter provides an overview of the creation of Virtual Private Networks (VPNs) that can be configured on the Cisco 819, Cisco 860, and Cisco 880
SonicWALL strongly recommends you follow these steps before installing Global VPN Client (GVC) 4.0.0:
 GVC SonicWALL Global VPN Client 4.0.0 Contents Pre-installation Recommendations... 1 Platform Compatibility... 1 New Features... 2 Known Issues... 3 Resolved Known Issues... 4 Troubleshooting... 5 Pre-installation
GVC SonicWALL Global VPN Client 4.0.0 Contents Pre-installation Recommendations... 1 Platform Compatibility... 1 New Features... 2 Known Issues... 3 Resolved Known Issues... 4 Troubleshooting... 5 Pre-installation
Application Note. Providing Secure Remote Access to Industrial Control Systems Using McAfee Firewall Enterprise (Sidewinder )
 Application Note Providing Secure Remote Access to Industrial Control Systems Using McAfee Firewall Enterprise (Sidewinder ) This document describes how to configure McAfee Firewall Enterprise to provide
Application Note Providing Secure Remote Access to Industrial Control Systems Using McAfee Firewall Enterprise (Sidewinder ) This document describes how to configure McAfee Firewall Enterprise to provide
Brocade Vyatta Network OS Remote Access IPsec VPN Configuration Guide, 5.2R1
 CONFIGURATION GUIDE Brocade Vyatta Network OS Remote Access IPsec VPN Configuration Guide, 5.2R1 Supporting Brocade 5600 vrouter, VNF Platform, and Distributed Services Platform 53-1004736-01 24 October
CONFIGURATION GUIDE Brocade Vyatta Network OS Remote Access IPsec VPN Configuration Guide, 5.2R1 Supporting Brocade 5600 vrouter, VNF Platform, and Distributed Services Platform 53-1004736-01 24 October
QNAP VPN (Virtual Private Network) Secure network experience
 QNAP VPN (Virtual Private Network) Secure network experience What is VPN (Virtual Private Network) The general Internet style Internet What is VPN? UNENCRYPTED ENCRYPTED ANONYMOUS When you connect through
QNAP VPN (Virtual Private Network) Secure network experience What is VPN (Virtual Private Network) The general Internet style Internet What is VPN? UNENCRYPTED ENCRYPTED ANONYMOUS When you connect through
Broadband Router DC-202. User's Guide
 Broadband Router DC-202 User's Guide Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband Router Features... 1 Package Contents... 3 Physical Details...3 CHAPTER 2 INSTALLATION... 5 Requirements...
Broadband Router DC-202 User's Guide Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband Router Features... 1 Package Contents... 3 Physical Details...3 CHAPTER 2 INSTALLATION... 5 Requirements...
Chapter 3 LAN Configuration
 Chapter 3 LAN Configuration This chapter describes how to configure the advanced LAN features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. This chapter contains the following sections
Chapter 3 LAN Configuration This chapter describes how to configure the advanced LAN features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. This chapter contains the following sections
AirCruiser G Wireless Router GN-BR01G
 AirCruiser G Wireless Router GN-BR01G User s Guide i Contents Chapter 1 Introduction... 1 Overview...1 Features...1 Package Contents...2 AirCruiser G Wireless Router Rear Panel...2 AirCruiser G Wireless
AirCruiser G Wireless Router GN-BR01G User s Guide i Contents Chapter 1 Introduction... 1 Overview...1 Features...1 Package Contents...2 AirCruiser G Wireless Router Rear Panel...2 AirCruiser G Wireless
Pre-Installation Recommendations... 1 Platform Compatibility... 1 New Features... 2 Known Issues... 2 Resolved Issues... 3 Troubleshooting...
 Global VPN Client SonicWALL Global VPN Client 4.6.4 Contents Pre-Installation Recommendations... 1 Platform Compatibility... 1 New Features... 2 Known Issues... 2 Resolved Issues... 3 Troubleshooting...
Global VPN Client SonicWALL Global VPN Client 4.6.4 Contents Pre-Installation Recommendations... 1 Platform Compatibility... 1 New Features... 2 Known Issues... 2 Resolved Issues... 3 Troubleshooting...
Vendor: Cisco. Exam Code: Exam Name: Cisco Interconnecting Cisco Networking Devices Part 1 (ICND1 v3.0) Version: Demo
 Vendor: Cisco Exam Code: 100-105 Exam Name: Cisco Interconnecting Cisco Networking Devices Part 1 (ICND1 v3.0) Version: Demo DEMO QUESTION 1 If the resume command is entered after the sequence that is
Vendor: Cisco Exam Code: 100-105 Exam Name: Cisco Interconnecting Cisco Networking Devices Part 1 (ICND1 v3.0) Version: Demo DEMO QUESTION 1 If the resume command is entered after the sequence that is
MTA_98-366_Vindicator930
 MTA_98-366_Vindicator930 Number: 98-366 Passing Score: 700 Time Limit: 45 min File Version: 1.0 http://www.gratisexam.com/ Microsoft Technology Associate Networking Fundamentals MTA 98-366 Exam A QUESTION
MTA_98-366_Vindicator930 Number: 98-366 Passing Score: 700 Time Limit: 45 min File Version: 1.0 http://www.gratisexam.com/ Microsoft Technology Associate Networking Fundamentals MTA 98-366 Exam A QUESTION
VPN Definition SonicWall:
 VPN Definition SonicWall: Note: If you have only DHCP-WAN IP at the EdgeMAX side, unfortunatly you must input the WAN-IP as Peer IKE ID. If you have also a DHCP-WAN IP at the SonicWall side, you can input
VPN Definition SonicWall: Note: If you have only DHCP-WAN IP at the EdgeMAX side, unfortunatly you must input the WAN-IP as Peer IKE ID. If you have also a DHCP-WAN IP at the SonicWall side, you can input
VPN and IPsec. Network Administration Using Linux. Virtual Private Network and IPSec 04/2009
 VPN and IPsec Network Administration Using Linux Virtual Private Network and IPSec 04/2009 What is VPN? VPN is an emulation of a private Wide Area Network (WAN) using shared or public IP facilities. A
VPN and IPsec Network Administration Using Linux Virtual Private Network and IPSec 04/2009 What is VPN? VPN is an emulation of a private Wide Area Network (WAN) using shared or public IP facilities. A
Manual Overview. This manual contains the following sections:
 Table of Contents Manual Overview This manual contains the following sections: Section 1 - Product Overview describes what is included with the DIR-130 router, and things to consider before installing
Table of Contents Manual Overview This manual contains the following sections: Section 1 - Product Overview describes what is included with the DIR-130 router, and things to consider before installing
Virtual Private Network with Open Source and Vendor Based Systems
 Paper 192, IT 303 Virtual Private Network with Open Source and Vendor Based Systems Abstract Veeramuthu Rajaravivarma SUNY, Farmingdale State College, Farmingdale Rajarav@farmingdale.edu Heavy dependency
Paper 192, IT 303 Virtual Private Network with Open Source and Vendor Based Systems Abstract Veeramuthu Rajaravivarma SUNY, Farmingdale State College, Farmingdale Rajarav@farmingdale.edu Heavy dependency
Configuration of an IPSec VPN Server on RV130 and RV130W
 Configuration of an IPSec VPN Server on RV130 and RV130W Objective IPSec VPN (Virtual Private Network) enables you to securely obtain remote access to corporate resources by establishing an encrypted tunnel
Configuration of an IPSec VPN Server on RV130 and RV130W Objective IPSec VPN (Virtual Private Network) enables you to securely obtain remote access to corporate resources by establishing an encrypted tunnel
ZyWALL (ZLD) VPN Troubleshooting
 ZyWALL (ZLD) VPN Troubleshooting L2TP VPN will not connect No traffic flow through L2TP VPN tunnel Client-to-Site (RoadWarrior) VPN will not connect No traffic flow through client-to-site IPSec VPN tunnel
ZyWALL (ZLD) VPN Troubleshooting L2TP VPN will not connect No traffic flow through L2TP VPN tunnel Client-to-Site (RoadWarrior) VPN will not connect No traffic flow through client-to-site IPSec VPN tunnel
ARCSERVE UDP CLOUD DIRECT DISASTER RECOVERY APPLIANCE VMWARE
 ARCSERVE UDP CLOUD DIRECT DISASTER RECOVERY APPLIANCE VMWARE [COMPANY NAME] [Company address] Table of Contents Arcserve UDP Cloud Direct Disaster Recovery Appliance for VMware... 2 Download the Arcserve
ARCSERVE UDP CLOUD DIRECT DISASTER RECOVERY APPLIANCE VMWARE [COMPANY NAME] [Company address] Table of Contents Arcserve UDP Cloud Direct Disaster Recovery Appliance for VMware... 2 Download the Arcserve
On the left hand side of the screen, click on Setup Wizard and go through the Wizard.
 Q: How do I configure the TEW-435/504BRM (b1) to a DSL, PPPoE connection? A: Step 1 Open your web browser and type the IP address of the TEW-435/504BRM in the address bar. The default IP address is 192.168.0.1.
Q: How do I configure the TEW-435/504BRM (b1) to a DSL, PPPoE connection? A: Step 1 Open your web browser and type the IP address of the TEW-435/504BRM in the address bar. The default IP address is 192.168.0.1.
Configuring Easy VPN Services on the ASA 5505
 CHAPTER 67 Configuring Easy VPN Services on the ASA 5505 This chapter describes how to configure the ASA 5505 as an Easy VPN hardware client. This chapter assumes you have configured the switch ports and
CHAPTER 67 Configuring Easy VPN Services on the ASA 5505 This chapter describes how to configure the ASA 5505 as an Easy VPN hardware client. This chapter assumes you have configured the switch ports and
Configuring a Hub & Spoke VPN in AOS
 June 2008 Quick Configuration Guide Configuring a Hub & Spoke VPN in AOS Configuring a Hub & Spoke VPN in AOS Introduction The traditional VPN connection is used to connect two private subnets using a
June 2008 Quick Configuration Guide Configuring a Hub & Spoke VPN in AOS Configuring a Hub & Spoke VPN in AOS Introduction The traditional VPN connection is used to connect two private subnets using a
L2TP IPsec Support for NAT and PAT Windows Clients
 L2TP IPsec Support for NAT and PAT Windows Clients The L2TP IPsec Support for NAT and PAT Windows Clients feature allows mulitple Windows client to connect to an IPsec-enabled Cisco IOS Layer 2 Tunneling
L2TP IPsec Support for NAT and PAT Windows Clients The L2TP IPsec Support for NAT and PAT Windows Clients feature allows mulitple Windows client to connect to an IPsec-enabled Cisco IOS Layer 2 Tunneling
Wireless-G Router User s Guide
 Wireless-G Router User s Guide 1 Table of Contents Chapter 1: Introduction Installing Your Router System Requirements Installation Instructions Chapter 2: Preparing Your Network Preparing Your Network
Wireless-G Router User s Guide 1 Table of Contents Chapter 1: Introduction Installing Your Router System Requirements Installation Instructions Chapter 2: Preparing Your Network Preparing Your Network
Brocade 5600 vrouter Remote Access IPsec VPN Configuration Guide, 5.0R1
 CONFIGURATION GUIDE Brocade 5600 vrouter Remote Access IPsec VPN Configuration Guide, 5.0R1 Supporting Brocade 5600 vrouter 5.0R1 53-1004509-01 15 August 2016 2016, Brocade Communications Systems, Inc.
CONFIGURATION GUIDE Brocade 5600 vrouter Remote Access IPsec VPN Configuration Guide, 5.0R1 Supporting Brocade 5600 vrouter 5.0R1 53-1004509-01 15 August 2016 2016, Brocade Communications Systems, Inc.
802.11N Wireless ADSL Router
 802.11N Wireless ADSL Router Pre-N Wireless Access Point ADSL Modem NAT Router WPS 4-Port Switching Hub User's Guide Table of Contents CHAPTER 1 INTRODUCTION...1 Wireless ADSL Router Features...1 Package
802.11N Wireless ADSL Router Pre-N Wireless Access Point ADSL Modem NAT Router WPS 4-Port Switching Hub User's Guide Table of Contents CHAPTER 1 INTRODUCTION...1 Wireless ADSL Router Features...1 Package
Secure Access Configuration Guide For Wireless Clients
 ProCurve Networking Secure Access Configuration Guide For Wireless Clients Secure Access Configuration Guide For Wireless Clients Introduction... 2 Configuration Scenarios... 2 Required Network Services...
ProCurve Networking Secure Access Configuration Guide For Wireless Clients Secure Access Configuration Guide For Wireless Clients Introduction... 2 Configuration Scenarios... 2 Required Network Services...
A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e. Chapter 8 Networking Essentials
 A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e Chapter 8 Networking Essentials Objectives Learn about the protocols and standards Windows uses for networking Learn how to connect
A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e Chapter 8 Networking Essentials Objectives Learn about the protocols and standards Windows uses for networking Learn how to connect
LevelOne WBR User s Manual. 11g Wireless ADSL VPN Router. Ver
 LevelOne WBR-3407 11g Wireless ADSL VPN Router User s Manual Ver 1.00-0510 Table of Contents CHAPTER 1 INTRODUCTION... 1 Wireless ADSL Router Features... 1 Package Contents... 5 Physical Details... 6 CHAPTER
LevelOne WBR-3407 11g Wireless ADSL VPN Router User s Manual Ver 1.00-0510 Table of Contents CHAPTER 1 INTRODUCTION... 1 Wireless ADSL Router Features... 1 Package Contents... 5 Physical Details... 6 CHAPTER
DPX8000 Series Deep Service Switching Gateway User Configuration Guide BRAS Service Board Module v1.0
 DPX8000 Series Deep Service Switching Gateway User Configuration Guide BRAS Service Board Module v1.0 i Hangzhou DPtech Technologies Co., Ltd. provides full- range technical support. If you need any help,
DPX8000 Series Deep Service Switching Gateway User Configuration Guide BRAS Service Board Module v1.0 i Hangzhou DPtech Technologies Co., Ltd. provides full- range technical support. If you need any help,
SonicWALL Addendum. A Supplement to the SonicWALL Internet Security Appliance User's Guide
 SonicWALL 6.2.0.0 Addendum A Supplement to the SonicWALL Internet Security Appliance User's Guide Contents SonicWALL Addendum 6.2.0.0... 3 New Network Features... 3 NAT with L2TP Client... 3 New Tools
SonicWALL 6.2.0.0 Addendum A Supplement to the SonicWALL Internet Security Appliance User's Guide Contents SonicWALL Addendum 6.2.0.0... 3 New Network Features... 3 NAT with L2TP Client... 3 New Tools
IP806GA/GB Wireless ADSL Router
 IP806GA/GB Wireless ADSL Router 802.11g/802.11b Wireless Access Point ADSL Modem NAT Router 4-Port Switching Hub User's Guide Table of Contents CHAPTER 1 INTRODUCTION... 1 Wireless ADSL Router Features...
IP806GA/GB Wireless ADSL Router 802.11g/802.11b Wireless Access Point ADSL Modem NAT Router 4-Port Switching Hub User's Guide Table of Contents CHAPTER 1 INTRODUCTION... 1 Wireless ADSL Router Features...
Configuring the VPN Client
 Configuring the VPN Client This chapter explains how to configure the VPN Client. To configure the VPN Client, you enter values for a set of parameters known as a connection entry. The VPN Client uses
Configuring the VPN Client This chapter explains how to configure the VPN Client. To configure the VPN Client, you enter values for a set of parameters known as a connection entry. The VPN Client uses
Virtual Private Networks
 EN-2000 Reference Manual Document 8 Virtual Private Networks O ne of the principal features of routers is their support of virtual private networks (VPNs). This document discusses transmission security,
EN-2000 Reference Manual Document 8 Virtual Private Networks O ne of the principal features of routers is their support of virtual private networks (VPNs). This document discusses transmission security,
SonicWALL strongly recommends you follow these steps before installing Global VPN Client (GVC) 4.1.0:
 GVC SonicWALL Global VPN Client 4.1.0 Contents Pre-installation Recommendations Platform Compatibility New Features Known Issues Resolved Known Issues Troubleshooting Pre-installation Recommendations SonicWALL
GVC SonicWALL Global VPN Client 4.1.0 Contents Pre-installation Recommendations Platform Compatibility New Features Known Issues Resolved Known Issues Troubleshooting Pre-installation Recommendations SonicWALL
IP Office 403 and SG VPN Application Note September
 IP Office 403 and SG VPN Application Note September 22 2004 Table of Contents 1. Introduction... 3 2. Requirements... 3 3. Network Diagram... 3 4. SG installation... 4 5. Central Site Configuration...
IP Office 403 and SG VPN Application Note September 22 2004 Table of Contents 1. Introduction... 3 2. Requirements... 3 3. Network Diagram... 3 4. SG installation... 4 5. Central Site Configuration...
Site-to-Site VPN with SonicWall Firewalls 6300-CX
 Site-to-Site VPN with SonicWall Firewalls 6300-CX Skill level: Expert (requires knowledge of IPSec tunnel setup) Goal To build an IPSec tunnel through the 63xx router's WAN internet connection, and use
Site-to-Site VPN with SonicWall Firewalls 6300-CX Skill level: Expert (requires knowledge of IPSec tunnel setup) Goal To build an IPSec tunnel through the 63xx router's WAN internet connection, and use
MAC Address Filtering Setup (3G18Wn)
 MAC Address Filtering Setup (3G18Wn) MAC Address Filtering MAC address filtering refers to the process of allowing (or denying) access to your wireless network based on the hardware address of the device
MAC Address Filtering Setup (3G18Wn) MAC Address Filtering MAC address filtering refers to the process of allowing (or denying) access to your wireless network based on the hardware address of the device
Create New Virtual Hub window.
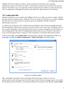 SoftEther VPN Server makes it possible to create a plurality of Virtual Hubs, and to separate administration objects and VPN session layer 2 communication between each Virtual Hub. This manual explains
SoftEther VPN Server makes it possible to create a plurality of Virtual Hubs, and to separate administration objects and VPN session layer 2 communication between each Virtual Hub. This manual explains
Configuring VPN from Proventia M Series Appliance to Proventia M Series Appliance
 Configuring VPN from Proventia M Series Appliance to Proventia M Series Appliance January 13, 2004 Overview Introduction This document describes how to configure a VPN tunnel from one Proventia M series
Configuring VPN from Proventia M Series Appliance to Proventia M Series Appliance January 13, 2004 Overview Introduction This document describes how to configure a VPN tunnel from one Proventia M series
Hacom pfsense Deployment Guide
 Hacom pfsense Deployment Guide Bao Ha Copyright 2008 Hacom Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any
Hacom pfsense Deployment Guide Bao Ha Copyright 2008 Hacom Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any
HTG XROADS NETWORKS. Network Appliance How To Guide: PPTP Client. How To Guide
 HTG X XROADS NETWORKS Network Appliance How To Guide: PPTP Client How To Guide V 3. 3 E D G E N E T W O R K A P P L I A N C E How To Guide PPTP Client XRoads Networks 17165 Von Karman Suite 112 888-9-XROADS
HTG X XROADS NETWORKS Network Appliance How To Guide: PPTP Client How To Guide V 3. 3 E D G E N E T W O R K A P P L I A N C E How To Guide PPTP Client XRoads Networks 17165 Von Karman Suite 112 888-9-XROADS
1.4 VPN Processing Principle and Communication Method
 This section contains a description of operation principle and communication method of VPN that can be constructed by SoftEther VPN. An overview of the modules and functions that was used by VPN communications.
This section contains a description of operation principle and communication method of VPN that can be constructed by SoftEther VPN. An overview of the modules and functions that was used by VPN communications.
How to setup Remote VPN access using Windows Radius Server and Unifi USG/Controller
 How to setup Remote VPN access using Windows Radius Server and Unifi USG/Controller Prerequisites: Windows Server 2012 or newer Domain Controller Services running Unifi USG (Pro, XG or 3P) Administrative
How to setup Remote VPN access using Windows Radius Server and Unifi USG/Controller Prerequisites: Windows Server 2012 or newer Domain Controller Services running Unifi USG (Pro, XG or 3P) Administrative
Firewall. Access Control, Port Forwarding, Custom NAT and Packet Filtering. Applies to the xrd and ADSL Range. APPLICATION NOTE: AN-005-WUK
 APPLICATION NOTE: AN-005-WUK Firewall Access Control, Port Forwarding, Custom NAT and Packet Filtering. Applies to the xrd and ADSL Range. FIREWALL Access Control The Access Control page allows configuration
APPLICATION NOTE: AN-005-WUK Firewall Access Control, Port Forwarding, Custom NAT and Packet Filtering. Applies to the xrd and ADSL Range. FIREWALL Access Control The Access Control page allows configuration
UIP1869V User Interface Guide
 UIP1869V User Interface Guide (Firmware version 0.1.8 and later) Table of Contents Opening the UIP1869V's Configuration Utility... 3 Connecting to Your Broadband Modem... 5 Setting up with DHCP... 5 Updating
UIP1869V User Interface Guide (Firmware version 0.1.8 and later) Table of Contents Opening the UIP1869V's Configuration Utility... 3 Connecting to Your Broadband Modem... 5 Setting up with DHCP... 5 Updating
- PIX Advanced IPSEC Lab -
 1 - PIX Advanced IPSEC Lab - Configuring Advanced PIX IPSEC Lab Basic Objectives: 1. Configure and cable the Ethernet interfaces as indicated in the above diagram. 2. Configure a web server for each network,
1 - PIX Advanced IPSEC Lab - Configuring Advanced PIX IPSEC Lab Basic Objectives: 1. Configure and cable the Ethernet interfaces as indicated in the above diagram. 2. Configure a web server for each network,
CCNA Security PT Practice SBA
 A few things to keep in mind while completing this activity: 1. Do not use the browser Back button or close or reload any Exam windows during the exam. 2. Do not close Packet Tracer when you are done.
A few things to keep in mind while completing this activity: 1. Do not use the browser Back button or close or reload any Exam windows during the exam. 2. Do not close Packet Tracer when you are done.
Connecting the DI-804V Broadband Router to your network
 Before you begin Make sure that any existing Firewall Software/Devices are disabled and/or shutdown before beginning installation of your new D-Link DI-804V Broadband Router. Contents of Package DI-804V
Before you begin Make sure that any existing Firewall Software/Devices are disabled and/or shutdown before beginning installation of your new D-Link DI-804V Broadband Router. Contents of Package DI-804V
Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide
 Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide Table of Contents SUPPORTED DEVICES... 5 INTRODUCTION... 6 GWN7000 VPN FEATURE... 7 OPENVPN CONFIGURATION... 8 OpenVPN
Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide Table of Contents SUPPORTED DEVICES... 5 INTRODUCTION... 6 GWN7000 VPN FEATURE... 7 OPENVPN CONFIGURATION... 8 OpenVPN
VPN Quick Configuration Guide. D-Link
 VPN Quick Configuration Guide D-Link 2017 equinux AG and equinux USA, Inc. All rights reserved. Under copyright law, this configuration guide may not be copied, in whole or in part, without the written
VPN Quick Configuration Guide D-Link 2017 equinux AG and equinux USA, Inc. All rights reserved. Under copyright law, this configuration guide may not be copied, in whole or in part, without the written
??????????????? HTTP/HTTPS???????????????? SoftEther VPN? HTTPS???????????????????????????????
 1.1.???????????????? NAT??? SoftEther VPN??????? 1????????????????????????? NAT (Network Address Translators)???????????????????????NAT??????????????????????????????????????????? HTTP/HTTPS????????????????
1.1.???????????????? NAT??? SoftEther VPN??????? 1????????????????????????? NAT (Network Address Translators)???????????????????????NAT??????????????????????????????????????????? HTTP/HTTPS????????????????
Gigabit SSL VPN Security Router
 As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is the ideal to help the SMBs increase the
As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is the ideal to help the SMBs increase the
Click on Close button to close Network Connection Details. You are back to the Local Area Connection Status window.
 How to configure EW-7228APn/EW-7416APn as a Repeater to extend wireless range This article can apply on EW-7228APn and EW-7416APn. We used screen shots of EW-7416APn in this instruction. We recommend you
How to configure EW-7228APn/EW-7416APn as a Repeater to extend wireless range This article can apply on EW-7228APn and EW-7416APn. We used screen shots of EW-7416APn in this instruction. We recommend you
Cisco IOS Firewall Authentication Proxy
 Cisco IOS Firewall Authentication Proxy This feature module describes the Cisco IOS Firewall Authentication Proxy feature. It includes information on the benefits of the feature, supported platforms, configuration
Cisco IOS Firewall Authentication Proxy This feature module describes the Cisco IOS Firewall Authentication Proxy feature. It includes information on the benefits of the feature, supported platforms, configuration
How to Set Up an IPsec Connection Between Two Ingate Firewalls/SIParators. Lisa Hallingström Paul Donald
 How to Set Up an IPsec Connection Between Two Ingate Firewalls/SIParators Lisa Hallingström Paul Donald Table of Contents How to configure Ingate Firewall/SIParator for IPsec connections...3 Certificates...3
How to Set Up an IPsec Connection Between Two Ingate Firewalls/SIParators Lisa Hallingström Paul Donald Table of Contents How to configure Ingate Firewall/SIParator for IPsec connections...3 Certificates...3
Grandstream Networks, Inc. GWN7000 Command Line Guide
 Grandstream Networks, Inc. Table of Contents INTRODUCTION... 3 CONNECTING AND ACCESSING THE GWN7XXX... 4 Connecting the GWN7000... 4 SSH Access... 5 USING THE CLI MENU... 6 Menu Structure And Navigation...
Grandstream Networks, Inc. Table of Contents INTRODUCTION... 3 CONNECTING AND ACCESSING THE GWN7XXX... 4 Connecting the GWN7000... 4 SSH Access... 5 USING THE CLI MENU... 6 Menu Structure And Navigation...
Cisco ASA 5500 LAB Guide
 INGRAM MICRO Cisco ASA 5500 LAB Guide Ingram Micro 4/1/2009 The following LAB Guide will provide you with the basic steps involved in performing some fundamental configurations on a Cisco ASA 5500 series
INGRAM MICRO Cisco ASA 5500 LAB Guide Ingram Micro 4/1/2009 The following LAB Guide will provide you with the basic steps involved in performing some fundamental configurations on a Cisco ASA 5500 series
VPN Tracker for Mac OS X
 VPN Tracker for Mac OS X How-to: Interoperability with NETGEAR VPN Router Appliances Rev. 1.2 Copyright 2003 equinux USA Inc. All rights reserved. 1. Introduction 1. Introduction This document describes
VPN Tracker for Mac OS X How-to: Interoperability with NETGEAR VPN Router Appliances Rev. 1.2 Copyright 2003 equinux USA Inc. All rights reserved. 1. Introduction 1. Introduction This document describes
VI. Corente Services Client
 VI. Corente Services Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 II. Corente Client Configuration...
VI. Corente Services Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 II. Corente Client Configuration...
Multi-site Configuration and Installation Guide Port Forwarding Option
 Multi-site Configuration and Installation Guide Port Forwarding Option V1.0 7-24-2006 Overview What this guide covers This guide will assist you in setting up a Wide Area Network (WAN) that allows your
Multi-site Configuration and Installation Guide Port Forwarding Option V1.0 7-24-2006 Overview What this guide covers This guide will assist you in setting up a Wide Area Network (WAN) that allows your
D-Link DSR Series Router
 D-Link DSR Series Router U s e r M a n u a l Copyright 2010 TeamF1, Inc. All rights reserved Names mentioned are trademarks, registered trademarks or service marks of their respective companies. Part No.:
D-Link DSR Series Router U s e r M a n u a l Copyright 2010 TeamF1, Inc. All rights reserved Names mentioned are trademarks, registered trademarks or service marks of their respective companies. Part No.:
Savvius Insight Initial Configuration
 The configuration utility on Savvius Insight lets you configure device, network, time settings, and reporting options. Important! Savvius Insight comes pre-configured to obtain its IP address via DHCP.
The configuration utility on Savvius Insight lets you configure device, network, time settings, and reporting options. Important! Savvius Insight comes pre-configured to obtain its IP address via DHCP.
VPN Tracker for Mac OS X
 VPN Tracker for Mac OS X How-to: Interoperability with SonicWALL Internet Security Appliances Rev. 4.0 Copyright 2003-2005 equinux USA Inc. All rights reserved. 1. Introduction 1. Introduction This document
VPN Tracker for Mac OS X How-to: Interoperability with SonicWALL Internet Security Appliances Rev. 4.0 Copyright 2003-2005 equinux USA Inc. All rights reserved. 1. Introduction 1. Introduction This document
