Design and analysis of novel quorum-based sink location service scheme in wireless sensor networks
|
|
|
- Evangeline McKinney
- 6 years ago
- Views:
Transcription
1 Wireless Netw (214) 2: DOI 1.17/s x Design and analysis of novel quorum-based sink location service scheme in wireless sensor networks Euisin Lee Fucai Yu Soochang Park Sang-Ha Kim Youngtae Noh Eun-Kyu Lee Published online: 23 July 213 Ó Springer Science+Business Media New York 213 Abstract Geographic routing in wireless sensor networks requires sources nodes to be aware of the location information of sinks to send their data. To provide the sink location service, quorum-based schemes have been proposed, which exploit crossing points between a quorum of a sink location announcement (SLA) message from a sink and a quorum of a sink location query (SLQ) message from a source node. For guaranteeing at least one crossing point in irregular sensor networks with void areas or irregular boundaries, the previous schemes however collect and flood the network boundary information or forward a SLA and SLQ message along the whole network boundary. In this paper, we design a novel quorum-based sink location service scheme that exploits E. Lee E.-K. Lee Computer Science Department, University of California, Los Angeles (UCLA), Los Angeles, CA, USA euisinlee@ucla.edu E.-K. Lee eklee@cs.ucla.edu F. Yu Key Lab of Broadband Optical Fiber Transmission and Communication Networks, UESTC, Chengdu, China fcyu@uestc.edu.cn S. Park Réseaux et Services Multimedia Mobiles (RS2M) Département, Telecom SudParis, Evry, France Soochang.PARK@telecom-sudparis.eu S.-H. Kim (&) Computer Engineering Department, Chungnam National University, Daejeon, Korea shkim@cnu.ac.kr Y. Noh Cisco Systems Inc., San Jose, CA, USA ynoh@cisco.com circle and line quorums, which does not require the network boundary information and send a SLA and SLQ message along the whole network boundary. In the proposed scheme, a source node sends a SLQ message to the network center and sends another SLQ message to an edge node in the network boundary, thus generating a SLQ line quorum. On the other hand, a sink node sends a SLA message along a circle path whose center is the network center, thus forming a SLQ circle quorum. By this way, it is guaranteed that the SLQ and SLA quorums have at least one crossing point in irregular sensor networks. Both numerical analysis and extensive simulation results verify that the proposed scheme outperforms the existing schemes in terms of the delivery distance, the delivery hop count, and the energy consumption for providing sink location service. Keywords Wireless sensor networks Geographic routing Sink location service Energy efficiency 1 Introduction Geographic routing [1] has been considered as an attractive approach since it only exploits pure local location information instead of global topology information to route data packets. This geographic routing makes it more efficient and scalable in Wireless Sensor Networks (WSNs) consisting of a large number of energy-restricted sensor nodes. However, geographic routing fundamentally requires three necessary conditions. First, each node must know its own location information. GPS devises [2] or other localization techniques [3, 4] can fulfill this requirement. Second, each node must know the location of its one-hop neighbor nodes. This requirement can be fulfilled by exchanging beacon messages [5]. Third, a source node must know the
2 494 Wireless Netw (214) 2: location of the destination (i.e. the sink in WSNs). In WSNs, source nodes and sinks can be deployed anywhere in the network and can even move. Some well-known geographic routing schemes [1 8] merely assume that source nodes can be aware of the location of sinks by location services. However, since the sink location service is not a trivial task, it is a challenging issue in WSNs. Flooding [9] is the simplest method for providing source nodes with the sink location information. Specially, a sink globally floods its own location information throughout the entire network, thus all source nodes in the network can get the location of the sink. This flooding method consumes lots of network resources such as energy and bandwidth, and even worse when multiple mobile sinks are deployed in the network. To avoid the flooding overhead to the entire network, a local flooding scheme based on a grid structure, named TTDD [1] was proposed. In TTDD, a source node constructs a global grid structure to disseminate its location information while a sink locally floods its own location information only within about a grid cell size, thus making crossing points between the grid structure and flooding. However, although it reduces the scope of flooding region, it leads to high overhead for constructing a global grid structure. To avoid the global or local flooding in sink location service, quorum-based sink location service schemes [11 13] have been proposed. The basic concept in these scheme is to support sink location service by providing crossing points between a quorum path of a sink location announcement (SLA) message from a sink and a quorum path of a sink location query (SLQ) message from a source. As shown in Fig. 1, the simplest quorum-based sink location service solution is the so-called column-row method that a sink sends a SLA message from its location in the vertical (i.e. north-south) direction while a source sends a SLQ message from its location in the horizontal (i.e. east-west) direction. However, in the real irregular sensor networks which can contain void (called hole or local minimum) areas [14] or have non-rectangle shapes (i.e. circle, ellipse, convex, and concave shape), the two SLA and SLQ quorums may be difficult to guarantee at least one crossing point. Thus, a network boundary information-based approach such as NELS [11] and a network boundary forwarding-based approach such as XYLS [13] have been proposed to guarantee at least one crossing point between the SLA and SLQ quorums in the irregular sensor networks. The network boundary information-based approach navigates SLA and SLQ messages by using the network boundary information to guarantee one crossing point. However, the network boundary information-based approach leads to much control overhead by collecting the network boundary information and flooding the collected information to the whole network. On the other hand, the network boundary forwarding-based approach forwards SLA and SLQ messages along the entire network boundary to guarantee one crossing point. However, the network boundary forwarding-based approach leads to much communication overhead by delivering the messages along the long network boundary. As a result, the two approaches have high energy consumption due to much control or communication overhead. Therefore, to reduce the energy consumption for providing sink location service, we propose a novel quorumbased sink location service scheme that exploits a crossing point between circle and line paths. In the proposed scheme, a source node sends a SLQ message to the network center and a copy of the SLQ message to a node on the edge of the sensor network, thus generating a line quorum of a SLQ massage. On the other hand, a sink node sends a SLA message along a circle path whose center is the network center, and thus generating a circle quorum of a SLA message. By this way, it is guaranteed that the SLQ line and SLA circle quorums have at least one crossing point. Then, the sensor node located on the crossing point informs the source node of the sink location. We next present how the proposed scheme can accomplish this procedure in irregular sensor networks. Since the proposed scheme does not exploit any network boundary information and send any SLA or SLQ messages along the network boundary, it can reduce much control and communication overhead. Our numerical analysis and extensive simulation results have verified that the proposed scheme is more efficient than both NELS and XYLS in terms of the delivery distance, the hop count, and the energy consumption for sink location service in irregular sensor networks. The rest of this paper is organized as follows: Sect. 2 reviews related works about sink location service schemes. We describe our novel quorum-based sink location service scheme based on circle and line paths in Sect. 3. Analysis and simulation results are given in Sects. 4 and 5, respectively. We discuss several issues related with the proposed scheme in Sect. 6. Section 7 concludes this paper. 2 Related works In geographic routing for wireless sensor networks, sink location service schemes for providing the location information of sinks to sources can be categorized into two main approaches: a flooding-based approach and a quorumbased approach. The flooding-based approach provides the sink location to the sources by flooding the location at sinks and also can be divided into two approaches: full network flooding [9] and local network flooding [1]. The full network flooding [9] is that a sink consecutively informs its new location information to the entire network by flooding. This scheme ensures that any source in the network can be
3 Wireless Netw (214) 2: Fig. 1 The simplest quorumbased sink location service solution Sink Hole Source Source Crossing Point Irregular Shape Sink provided with the sink location, but the full network flooding can lead to large energy consumption of the sensor nodes and collisions in wireless transmissions. The energy consumption of the full network flooding increases with the number of sinks. To avoid the full network flooding, the local network flooding, named TTDD [1] was proposed. A source in TTDD constructs a global grid structure from its location and disseminates its location information to sensor nodes on the grid structure. Then, a sink floods its own location information only within about a grid cell size to find a sensor node on the grid structure. The sensor node relays the location and query information of the sink to the source via the grid structure. Local flooding only within about a grid cell size is an efficient way. However, the bigger the cell size, the wider the flooding area, thus the more flooding overhead, while small grid size incurs more overhead for the grid construction. Moreover, per-source based global grid constructions also significantly generate additional overhead. The quorum-based approach has been proposed to prevent the full and local network flooding. In the quorumbased approach, a Sink Location Announcement (SLA) message of a sink is sent to a subset (SLA quorum) of available sensor nodes, and a SLQ message of a source is sent to a potentially different subset (SLQ quorum). The two quorums are designed such that they have at least one crossing point between them. The simplest quorum-based scheme is the so-called column-row method that a sink sends a SLA packet from its location in the north-south direction while a source sends a SLQ packet from its location in the east-west direction. However, the simple column-row method can guarantee at least one crossing point only in the network of rectangle shape. Thus, the simple column-low method cannot provide at least one crossing point in the real irregular sensor networks which have void areas or are non-rectangle shapes such as circle, ellipse, convex, and concave shapes. Two quorum-based approaches have been proposed to guarantee at least one crossing points between SLA and SLQ quorums in the irregular wireless sensor networks: network boundary information-based approach [11, 12] and network boundary forwarding-based approach [13]. The network boundary information-based approach navigates SLA and SLQ messages by using the network boundary information to guarantee at least one crossing point. As shown in Fig. 2, NELS [11] collects the location information of network boundary nodes in a sensor network and selects anchor nodes among them. Then, NELS divides the anchor nodes into four parts, which are labeled as P1, P2, P3 and P4 in clockwise direction. Then, the location information of the anchor nodes is flooded in the sensor network. With the list information, a sink sends a SLA packet to a random anchor in each of P2 and P4, respectively. On the other hand, a source node sends a SLQ packet for a sink to a random anchor in each of P1 and P3, respectively. Thus, one crossing point is guaranteed in NELS. With the location information of network boundary nodes, SLS-IR [12] constructs an inner network of rectangle shape inside the whole sensor network to use the simple column-row quorum method and floods the location information of the inner rectangle network to the whole sensor network. Then, a sink construct a SLA quorum of east-west direction and a source construct a SLQ quorum of north-south direction inside the inner rectangle network. Thus, SLS-IR guarantees at least one crossing point in the inner rectangle network. Instead of using the network boundary information, the network boundary forwarding-based approach forwards SLA and SLQ messages along the network boundary to guarantee at least one crossing point. As shown in Fig. 3,in XYLS [13], a sink sends a south-north quorum of a SLA message from its location to the network boundary. A source node sends an east-west quorum of a SLQ message from its location to the network boundary. Then, the SLA
4 496 Wireless Netw (214) 2: A 14 A 13 P 1 V A 15 A 12 P 4 M A A A21 A 11 A 18 Source Sink A 41 P 2 P N U A 31 P 3 Fig. 2 NELS using the network boundary information-based approach Source P P 3 2 P 1 P 4 SLA and SLQ messages constructs both column and row quorums, that is, in both north-south and east-west directions, to provide more crossing points and fast sink location replies. However, the network boundary information-based approach leads to much control overhead by collecting the network boundary information and flooding the information to the whole network. If the network size increases, it brings out more control overhead for collecting the network boundary information due to the increased network boundary length. If the number of sensor nodes increases, it also brings out more control overhead for flooding the network boundary information due to the increased number of sensor nodes. On the other hand, the network boundary forwarding-based approach leads to much communication overhead by delivering the messages along the long network boundary, and thus makes the network boundary nodes exhaust their energy fast. If the number of sinks and sources increases, it makes this problem more seriously due to delivering more SLA and SLQ packets along the network boundary. However, since energy-efficiency is one of the most important issues in wireless sensor networks [15 18], sink location service should be provided with less control and communication overheads. Thus, for energyefficiency, the proposed sink location service scheme does not exploit any network boundary information and deliver any SLA or SLQ messages along the network boundary to guarantee at least one crossing point. The proposed scheme only uses the location information of the network center through embedding or programming it by network operators. With the network center location information, our scheme guarantees at least one crossing point between a SLA circle quorum and a SLQ line quorum. Thus, our scheme can reduce much control and communication overhead. 3 Design of the proposed scheme Sink P 5 Fig. 3 XYLS using the network boundary forwarding-based approach and SLQ messages arrive at the network boundary and then they are further forwarded along the network boundary with the clockwise direction to guarantee at least one crossing point between them. The authors in XYLS propose a variant, called CR?CR, of XYLS. In CR?CR, all of We assume in this work that each node can get its own location information either by GPS [2] or localization schemes [3, 4]. Each node can get its one-hop neighbors list and their locations by periodically exchanging beacon messages [5]. A node can know whether it is located on the edge of a sensor network either by manual identification of network operators during network deployment, or by some automatic detection methods [19, 2] after network deployment. Every node can know the information of center location C = (C x, C y ) in the sensor network by programming or embedding from network operators before network deployment, because the network operators commonly know the region of sensor field to construct the sensor network in advance.
5 Wireless Netw (214) 2: Network initialization After network deployment of sensor nodes, a general sensor network may be shown as Fig. 4. Then, every node calculates a Height value from the center location C = (C x, C y ) as follows: Height ¼ L ð1þ R where L is the distance from the center location to itself and R is the radio range of sensor nodes. Figure 5 shows the ideal result of this process, where the thick dotted curve line indicates the boundary of the sensor network, and the thin dotted circles are the traces of the sensor nodes which have the same Height value. To facilitate discussion, all general sensor nodes are not drawn out here. After the network initialization phase, every sensor node is aware of its Height value. By including the Height value in beacon messages [5] and exchanging them with neighbor nodes, all nodes can get the Height value information of their neighbor sensor nodes. The Height value information is used for navigating SLA and SLQ messages to their destinations for supporting our sink location service scheme. 3.2 Sink location service in regular sensor networks In this section, we first describe our sink location service scheme in regular sensor networks. As shown in Fig. 5, when a sink S exists in the sensor network, it gets a Height value by querying a neighbor sensor node. Then, it initializes a SLA message that contains the following fields: Fig. 4 A general sensor network after network deployment C C Fig. 5 Network initialization and the proposed sink location service scheme Sink_Location, Sink_Interest, Height, and Direction. The Sink_Location field is set to the location of the sink S, the Sink_Interest field is set to the interest of the sink S, the Height field is set to the Height value obtained from the neighbor node, and the Direction field is set to a counter-clockwise. Then, the sink node S sends the SLA message to the farthest neighbor sensor node on the left side direction of itself, which has the same Height value. When the neighbor node receives the SLA message, it saves the location and interest information of the sink S to its sink information table, and then forwards the SLA message to its neighbor sensor node according to the same rule. This process repeats until the SLA message is eventually received by a sensor node which has forwarded it. The track of the SLA message forms a closed circle quorum as the solid circle shown in Fig. 5. When a sensor node detects an event and becomes a source node, e.g., the node E in Fig. 5, it initializes a SLQ message which contains the source node location and the detected event type. A copy of the SLQ message is sent to the center location C of the sensor network by geographic routing as the path shown in Fig. 5. All of the sensor nodes which have forwarded the SLQ message need to save the source node location and the event type in their source information table. The source node E also sends another copy of the SLQ message to the farthest neighbor sensor node whose Height value is 1 bigger than that of itself. When the farthest node receives the SLQ message, it saves the source node location and the event type in its source information table. Then, it also forwards the SLQ message P D E S
6 498 Wireless Netw (214) 2: to the farthest neighbor sensor node whose Height value is 1 bigger than that of itself. This process stops at a network edge node D which received the SLQ message. The network edge node should never reforward the received SLQ message in any case. The solid line CED in Fig. 5 shows the line quorum of the SLQ message. For guaranteeing a crossing point between a SLA quorum and a SLQ quorum, our sink location service scheme is supported by following theorem: Theorem Given a circle and a line, if one end of the line is inside the circle and the other end of the line is outside of the circle, then the circle and the line have at least one crossing point. Proof As we can see from Fig. 5, one end of the SLQ line quorum is the center location C and is inside the SLA circle quorum, while the other end of the SLQ line quorum is the network edge node D and is outside the SLA circle quorum. Thus, the SLA circle quorum and the SLQ line quorum have at least one crossing point P. From the theorem and proof, we can guarantee at least one crossing point P between a SLA message from a sink and a SLQ message from a source in our sink location service scheme. Thus, the sensor node which is located on the crossing point P received both SLQ and SLA messages becomes to know the source location and the event type from the SLQ message and the sink location and the sink interest from the SLA message. Then, if the event type matches the sink interest, the sensor node informs the source node of the sink location information as the solid curve line as shown in Fig. 5. After getting the sink location, the source node E sends data packets to the sink S by the geographic routing. This is the basic idea of the proposed sink location service scheme. In the Sect. 3.3, we discuss how our sink location service scheme guarantees one crossing point in irregular sensor networks. 3.3 Handling irregular profile sensor network Most sensor networks have irregular profiles such voids [14] or non-rectangular shapes [11 13]. Thus, our sink location service scheme must work well in any irregular profile sensor networks. Figure 6 shows an irregular profile sensor network with three hole inside it and a non-rectangular shape. A sink node S sends a SLA message to announce its location and interest to the farthest neighbor sensor node on the left side of itself for constructing a SLQ circle path by the process described in the Sect. 3.2 When the sensor node M located on the edge of the hole receives the SLA message, since there is no sensor node located on the left side of itself with the same Height value, the node M sends the SLA message to a neighbor node whose Height value is 1 less then that of itself. When the neighbor node receives the SLA message, it tries to send the SLA message to the sensor node on the left side whose Height value is closest to the Height value encapsulated in the received SLA message. If there is no such a sensor node, it also sends the SLA message to a neighbor node whose Height is 1 less then that of itself. This process repeats until the SLA message was received by the sensor node N which has the same Height value as that encapsulated in the SLA message. Then, the SLA message is continuously forwarded until it was received by a sensor node U on the irregular edge as shown in Fig. 6. The subsequent process is similar to the process of bypassing the Hole as described above. By bypassing the irregular edge, the SLA message is received by another sensor node V on the irregular edge which has the same Height value as encapsulated in the SLA message. Then, the sensor node V sends the SLA message to the farthest neighbor sensor node on the left side of itself, which has the same Height value. This process repeats until the SLA message is eventually received by a sensor node which has firstly forwarded it. As shown in Fig. 6, although the path of the SLA message does not have a circle shape, it has a closed shape similar to circles. When a source node E sends a SLQ message to the center location and a network edge in a irregular sensor network by geographic routing, the SLQ message can also meet a Hole. Thus, the SLQ message also need to bypass the Hole. When a copy of the SLQ message is sent from the source node to the center location by the greedy mode [1] in geographic routing, if it meets a Hole, a sensor node on the Hole received the SLQ D U V Hole P S E Hole C N Hole Fig. 6 The proposed sink location service scheme in any irregular profile sensor network M
7 Wireless Netw (214) 2: message changes the greedy mode[1] into the perimeter mode to bypass the hole. If the SLQ message bypasses the hole by the perimeter mode, it is also sent to the center location C by the greedy mode. By this process, the SLQ message is eventually forwarded to the center location. To forward a copy of the SLQ message to a network edge, the source node E sends the farthest neighbor sensor node whose Height value is 1 bigger than that of itself. However, since a sensor node on a Hole receives the SLQ message, it can have no any neighbor sensor node whose Height value is 1 bigger than that of itself. Then, it includes its Height value into the SLQ message and sends the SLQ message along the Hole in a counter-clockwise direction until a sensor node on the Hole, whose Height value is 1 bigger than that in the SLQ message, receives the SLQ message. This process continues until a network edge node D 2 receives the SLQ message. Thus, as shown in Fig. 6, a curve line CED is constructed between the center location C and the network edge D via the source node E. From Fig. 6, we can see that, in the irregular profile sensor network, though the SLA delivery path is not a real circle and the SLQ delivery path is not a real straight line, our sink location service scheme can guarantee that the SLA path and the SLQ path have at least one crossing point, e.g., the sensor node P. If the Event Type in the SLQ message and the Sink Interest in the SLA message are matched, the sensor node P on the crossing point also sends the location information of the sink node S to source node E by geographic routing. 3.4 Effects of multiple sinks and sources Multiple source nodes and multiple sinks may exist in the sensor network simultaneously. In this case, the SLA circle path of any sink and the SLQ line path of any source can be surely guaranteed to have at least one crossing point. Once a sink sends a SLA message, all source nodes can get the location of the sink from the nodes located on corresponding crossing points; once a source sends a SLQ message, it can get the location information of all sinks form the nodes located on the corresponding crossing points. However, if the number of sinks or source nodes increases, the number of SLA and SLQ messages increases. Thus, sensor nodes consume more energy to deliver the increased SLA and SLQ messages. We evaluate how the number of sinks and source nodes can affect the proposed scheme through analysis and simulation in the Sect. 4 and 5. 4 Numerical analysis In this section, we present numerical analysis for sink location service cost of Network Edge node-based sink Location Service (NELS) [11], XYLS [13], and the Proposed Scheme (PS). In all of sink location service schemes, since all of SLA, SLQ, and SLR messages are delivered by using geographic routing [1], we consider the delivery distance of all the messages as sink location service cost. This assumption is justified by the fact that the Euclidean distance in a dense and uniform wireless sensor network is approximately proportional to the hop count [21]. Furthermore, the energy consumption of sensor nodes is proportional to the hop count [22]. We note that such an energy model is also adapted by several power-efficient data communication protocols in wireless sensor networks [22, 23]. Thus, we numerically calculate the delivery distance for sink location service. Sink location service consists of three messages: SLA, SLQ, and SLR messages. We first present the delivery distance of each of the three messages in each sink location service scheme in next three subsections, respectively. We next present the total delivery distance of each sink location services. We last present the hop count of each sink location service through the total delivery distance and the energy consumption of sensor nodes through the hop count. For numerical analysis of sink location service, we assume a sensor network whose shape is a circle with a radius Rm. The number of sinks and sources is a and b, respectively. The number of sensor nodes in the network is n. 4.1 Delivery distance of sink location announcement A sink sends a SLA message with its location information according to sink location service schemes and thus constructs SLA quorums. In NELS, as shown in Fig. 2, a sink S delivers a SLA message from its location to a edge node U of part P 2 in the network boundary. When we assume for analysis that the sink locates around the center of the network, the length of line between S and U is almost same with the radius R. The sink also delivers a copy of the SLA from itself to a edge node V of part P 4. The length of the line between S and V also is almost same with the radius R. Therefore, the delivery distance D SLA NELS of a SLA message from a sink in NELS is calculated as follows: D SLA NELS ¼ R þ R ¼ 2 R: ð2þ In XYLS, as shown in Fig. 3, a sink sends a SLA message from its location to the network boundary both toward south and north, and thus constructing a vertical quorum in the network. Then, each of edge nodes in the network boundary of south and north sides received the SLA message sends the SLA message along edge nodes on the network boundary with the clockwise direction. Thus, the SLA message further constructs the SLA quorum to network boundary edge nodes on east and west sides in the east-west quorum of a SLQ message from a source node.
8 5 Wireless Netw (214) 2: Therefore, the delivery distance D SLA XYLS of a SLA message from a sink in XYLS consists of a vertical quorum and two network boundary circle quorum of one-quarter, and is calculated as follows: D SLA XYLS ¼ R þ R þ p R 2 þ p R ¼ 2 R þ p R: ð3þ 2 In the proposed scheme, as shown in Fig. 5, a sink sends a SLA message from its location along a circle path whose radius is the distance from its location to the center of the network. When we assume that the sink averagely locates in the center between the network center and the network boundary, the radius of the circle path is half of the network radius R. Thus, the delivery distance D SLA PS of a SLA message from a sink in the proposed scheme is calculated as follows: D SLA PS ¼ 2 p 1 R ¼ p R: ð4þ Delivery distance of sink location query A source queries the location information of the sink to send its data through geographic routing. In quorumbased sink location service schemes, a source sends a SLQ message with its location information by each sink location scheme and thus constructing SLQ quorums. In NELS, as shown in Fig. 2, a source E delivers a SLQ message from its location to a edge node M of part P 1 in the network boundary. When we assume for analysis that the source locates around the center of the network, the length of line between E and M is almost same with the radius R. The source also delivers a copy of the SLA from itself to a edge node N of part P 3. The length of the line between E and N also is almost same with the radius R. Therefore, the delivery distance D SLQ NELS of a SLA message from a source in NELS is calculated as follows: D SLQ NELS ¼ R þ R ¼ 2 R: ð5þ In XYLS, as shown in Fig. 3, a source node sends a SLQ message from its location to the network boundary both toward east and west, and thus constructing one horizontal quorum in the network. Then, each of edge nodes in the network boundary of east and west sides received the SLQ message sends the SLQ message along edge nodes on the network boundary with the clockwise direction. Thus, the SLQ message further constructs the SLQ quorum to network boundary edge nodes on north and south sides in the north-south quorum of a SLA message from a sink. Therefore, the delivery distance D SLQ XYLS of a SLQ message from a sink in XYLS consists of a horizontal quorum and two network boundary circle quorum of onequarter, and is calculated as follows: D SLQ XYLS ¼ R þ R þ p R 2 þ p R ¼ 2 R þ p R: ð6þ 2 In the proposed scheme, as shown in Fig. 5, a source sends a SLQ message from its location to the center of the network and a copy of the SLQ message to the network boundary, and constructing a quorum of one line between the network center and the network boundary via the source. Thus, the delivery distance D SLQ PS of a SLQ message from a source in the proposed scheme is calculated as follows: D SLQ PS ¼ R: ð7þ 4.3 Delivery distance of sink location reply In quorum-based sink location service schemes, a sensor node on all crossing points between the quorums of SLA message of a sink and the quorums of SLQ message of a source sends a SLR message with the location information of the sink to the source. In NELS, as shown in Fig. 2, since a SLA message of a sink is sent toward part 1 and 3 of the network boundary and a SLQ message of a source is sent toward part 2 and 4 of the network boundary, one crossing point may be around the network center. When we assume for analysis that a source node averagely locates around the center between one among part 1 and 3 and the crossing point, the distance between the crossing point and the source is half of the network radius R. Thus, the delivery distance D SLR NELS of a SLR message in ALS is as follows: D SLR NELS ¼ 1 R: ð8þ 2 In XYLS, as shown in Fig. 3, a sink sends a SLA message to the network edges of both south and north. A source sends a SLQ message to the network edges of both east and west. Then, the SLA and SLQ messages are sent along the network boundary with the clockwise direction. Thus, five crossing points can be in the network. When we assume for analysis that a source locates around the center between the east boundary and the network center, one crossing point is the east boundary and the distance between the crossing point and the source is half of the network radius R. Another crossing point is the west boundary and the distance between the crossing point and the source is 3 2 R. Another crossing point is the north boundary and the distance between the crossing point and the source is the network radius R. Another crossing point is the south boundary and the distance between the crossing point and the source is the network radius R. When a sink averagely locates around the network center, the other crossing point is around the network center and the distance between the crossing point and the source is half
9 Wireless Netw (214) 2: of the network radius R. Thus, the delivery distance D SLR XYLS of a SLR message in XYLS is calculated as follows: D SLR XYLS ¼ 1 2 R þ 3 2 R þ R þ R þ 1 2 R ¼ 9 R: ð9þ 2 In the proposed scheme, if a sink averagely locates in the center of the distance between the network center and the network boundary, it constructs a circle path of a SLA message in its location and thus the network is divided into two regions. A source constructs a SLQ quorum between the network center and the network boundary via itself. Thus, one crossing point happens. When a source averagely locates in the center of one among the two regions, the distance between the crossing point and the source is 1 4 R. Thus, the delivery distance D SLR PS of the SLR message in the proposed scheme is as follows: D SLR PS ¼ 1 R: ð1þ Total delivery distance for sink location service In this subsection, we calculate the total delivery distance for sink location service. The total delivery distance for sink location service is the sum of delivery distance of SLA, SLQ, and SLR messages. Thus, the total delivery D T distance of NELS, XYLS, and the proposed scheme are as follows. D SLS NELS ¼ D SLA NELS þ D SLQ NELS þ D SLR NELS ¼ 2 R þ 2 R þ 1 2 R ¼ 9 2 R ð11þ D SLS XYLS ¼ D SLA XYLS þ D SLQ XYLS þ D SLR XYLS ¼ð2 R þ p RÞþð2 R þ p RÞþ 9 2 R ¼ 17 2 R þ 2 p R D SLS PS ¼ D SLA PS þ D SLQ PS þ D SLR PS ¼ p R þ R þ 1 4 R ¼ 5 4 R þ p R ð12þ ð13þ The number of sinks and source nodes affects the total delivery distance for sink location service. Thus, we calculate the total delivery distance of sink location service for the number of sinks and sources. The number of sinks affects the number of SLA and SLR messages, and the number of source nodes affects the number of SLQ and SLR messages. When the number of sinks is a, the number of SLA and SLR messages increases a times, respectively. When the number of source nodes is b, the number of SLQ and SLR messages increases b times, respectively. When the numbers of sinks and source nodes are a and b, the total delivery distance D T of ALS, XYLS, and the proposed scheme are as follows. D Sink¼a;Source¼b SLS NELS ¼ a D SLA NELS þ b D SLQ NELS þ a b D SLR NELS D Sink¼a;Source¼b SLS XYLS ¼ a 2 R þ b 2 R þ a b 1 2 R ¼ 2 a þ 2 b þ 1 2 a b R ¼ a D SLA XYLS þ b D SLQ XYLS þ a b D SLR XYLS ¼ a ð2 R þ p RÞþb ð2 R þ p RÞ ð14þ þ a b 9 2 R ¼ 2 a þ p a þ 2 b þ p b þ 9 2 a b R D Sink¼a;Source¼b SLS PS ¼ a D SLA PS þ b D SLQ PS þ a b D SLR PS ¼ a p R þ b R þ a b 1 4 R ¼ p a þ b þ 1 4 a b R 4.5 Total hop count for sink location service ð15þ ð16þ In the subsection, we calculate the total hop count for sink location service in NELS, XYLS, and the proposed scheme. The total hop count are calculated by the total delivery distance in the Sect Given the total delivery distance, if an average single hop progress Single_Hop_Pro ave is given, the total hop count can be calculated. The Single_Hop_Pro ave is defined as the expected value of the difference between the before-hop distance (between the sender node and the destination node) and the after-hop distance (between the next-hop node and the destination node) [24]. As the Single_Hop_Pro ave, we use a value calculated by the equation (14) in [24] where q is the average number of neighbors within the transmission range r of the sender and is given by q ¼ p r 2 k where k is the expected number of nodes within a unit area. Figure 7 shows the average single hop progress for average number of neighbor sensor nodes in [24]. As shown in Fig. 7, if the average number of neighbor sensor nodes is small, the average single hop progress has very small value. However, if the average number of neighbor sensor nodes increases, the average single hop progress increases sharply first and slowly later. Thus, given the Single_Hop_Pro ave,
10 52 Wireless Netw (214) 2: Average Single Hop Progress (m) the total hop count H T for sink location service in NELS, XYLS, and the proposed scheme are calculated as follows. H Sink¼a;Source¼b SLS NELS ¼ D Sink¼a;Source¼b SLS NELS =Single Hop Pro ave ¼ 2 a þ 2 b þ 1 2 a b H Sink¼a;Source¼b R=Single Hop Pro ave ð17þ SLS XYLS ¼ D Sink¼a;Source¼b SLS XYLS =Single Hop Pro ave ¼ 2 a þ p a þ 2 b þ p b þ 9 2 a b H Sink¼a;Source¼b Average Number of Nighber Sensor Nodes, ρ Fig. 7 Average single hop progress for average number of neighbor sensor nodes in [24] R=Single Hop Pro ave SLS PS ¼ D Sink¼a;Source¼b SLS PS =Single Hop Pro ave ¼ p a þ b þ 1 4 a b R=Single Hop Pro ave 4.6 Total energy consumption for sink location service ð18þ ð19þ In this subsection, we calculate the total energy consumption for sink location service in NELS, XYLS, and the proposed scheme. The total energy consumption is calculated through multiplying the total hop count by the sum of transmitting and receiving power in one-hop transmission of sensor nodes. If we assume that the transmitting and receiving energy consumption rates are E t and E r, respectively, the total energy consumption for sink location service in NELS, XYLS, and the proposed scheme are calculated as follows. E Sink¼a;Source¼b SLS NELS ¼ H Sink¼a;Source¼b SLS NELS ðe t þ E r Þ ¼ 2 a þ 2 b þ 1 2 a b E Sink¼a;Source¼b R=Single Hop Pro ave ðe t þ E r Þ ð2þ SLS XYLS ¼ H Sink¼a;Source¼b SLS XYLS ðe t þ E r Þ ¼ 2 a þ p a þ 2 b þ p b þ 9 2 a b R=Single Hop Pro ave ðe t þ E r Þ E Sink¼a;Source¼b SLS PS ¼ H Sink¼a;Source¼b SLS PS ðe t þ E r Þ ¼ p a þ b þ 1 4 a b R=Single Hop Pro ave ðe t þ E r Þ ð21þ ð22þ However, since NELS carries out the collection and the flooding of the network boundary information in the network initialization phase for navigating SLA and SLQ messages, the control overhead for these two processes must be included in the total energy consumption for sink location service. For the process of the network boundary information collection, a boundary edge node sends a Boundary Information Collection (BIC) message along the network boundary. Thus, the delivery distance of the BIC message is same to the circumference length of a circle with a radius R. Thus, the energy consumption for sending the BIC message along the network boundary is ð2 p R=Single Hop Pro ave ÞðE t þ E r Þ. For the process of the network boundary information flooding, the boundary edge node floods a Boundary Information Announcement message to all sensor node in the network. Then, for flooding the BIA message to all sensor nodes, every sensor node receives the BIA message once and sends the BIA message once. Thus, the energy consumption for flooding the BIA message is the number n of sensor nodes times (E t? E r ), namely n ðe t þ E r Þ. Thus, the control overhead E CO NELS for the network initialization is calculated as follows, E CO NELS ¼ð2 p R=Single Hop Pro ave ÞðE t þ E r Þ þ n ðe t þ E r Þ: ð23þ Therefore, the total energy consumption for sink location service in NELS is recalculated as:
11 Wireless Netw (214) 2: E Sink¼a;Source¼b T NELS ¼ E Sink¼a;Source¼b SLS NELS þ E CO NELS ¼ 2 a þ 2 b þ 1 2 a b R=Single Hop Pro ave ðe t þ E r Þþð2pR=Single Hop Pro ave Þ ðe t þ E r ÞþnðE t þ E r Þ ¼ 2 a þ 2 b þ 1 2 a b þ 2 p R=Single Hop Pro ave þ n ðe t þ E r Þ ð24þ Delivery Distance (m) NELS-SLA NELS-SLQ NELS-SLR NELS-SLS XYLS-SLA XYLS-SLQ XYLS-SLR XYLS-SLS PS-SLA PS-SLQ PS-SLR PS-SLS As shown in the Eqs. (21), (22) and (24), the performance of NELS, XYLS, and the proposed scheme is influenced by the network size R, the sink number a, the source number b, and the sensor node density n. Thus, we evaluate how they can affect the performance of the three schemes through analysis and simulation results in the Sect Performance evaluation 5.1 Simulation environments We compare the performance of the Proposed Scheme (PS) with those of NELS [11] and XYLS [13]. We implemented these three schemes in Network Simulator Qualnet 4. [25]. The models of sensor nodes follow the specification of MICA2 [26]. The radio range r of sensor nodes is 1 m and their transmitting and receiving energy consumption rates are 49 and 29 mw, respectively. As default setting, we consider a sensor network of circular shape with a radius 1 m where 2, sensor nodes are uniformly distributed. Thus, the Single_Hop_Pro ave is about 7.9 m by the equation (14) in [24] because the average neighbor node number q of a sensor node is 2. In our simulation, one sink and one source are randomly located in the network every 1 s. In every scheme, the source and the sink send SLQ and announcement messages every 1 s. We define every 1 s as a sink location service round. The simulation time is 1, s. We use three performance evaluation metrics, the total delivery distance, the total hop count, and the total energy consumption for sink location service. Each point of the plots is the average of 1 instances with a 95 % of confidence interval. 5.2 Simulation results for network size In this section, we compare the performance of NELS, XYLS, and the proposed scheme for the network size R.We vary the network size 1 6 m at an interval of 1 m. Figures 8, 9 and 1 show analysis and simulation results of the delivery distance, the delivery hop count, and the energy Delivery Hop Counts NELS-SLS XYLS-SLS PS-SLS Network Size (m) Fig. 9 Delivery hop count for network size Energy Conumption (mw) Network Size (m) Fig. 8 Delivery distance for network size NELS-SLS (Analysis) NELS-SLS (Simulation) NELS-CO (Analysis) NELS-CO (Simulation) NELS-SLS+CO (Analysis) NELS-SLS+CO (Simulation) XYLS-SLS (Analysis) XYLS-SLS (Simulation) PS-SLS (Analysis) PS-SLS (Simulation) Network Size (m) Fig. 1 Energy consumption for network size consumption for sink location service, respectively. If the network size increases, the delivery distance of SLA, SLQ, and SLR messages for sink location service increases by the Eqs. (2) (1). Thus, as shown in Fig. 8, the delivery
12 54 Wireless Netw (214) 2: distance, namely, the sum of the delivery distance of SLA, SLQ, and SLR messages, for sink location service also increases by the Eqs. (11) (13). The delivery distance of XYLS is the longest, the second longest to that of NELS, and the shortest to that of the proposed scheme, because the increased network size makes SLA and SLQ messages in XYLS be forwarded along the increased network boundary. The delivery distance for sink location service is proportional to the delivery hop count for sink location service by the Eqs. (17) (19). However, the delivery hop count is inverse proportional to the Single_Hop_Pro ave. The Single_Hop_Pro ave is also inverse proportional to the network size because average number of neighbor sensor nodes is inverse proportional to the network size when the number of sensor nodes is fixed. Thus, Fig. 9 shows that the delivery hop count of XYLS is the most, the second most to that of NELS, and the smallest to that of the proposed scheme. If the network size increases, they exponentially increase their delivery hop count. Figure 1 shows the energy consumption for the network size. The energy consumption for sink location service is similar to the delivery hop count for sink location service, because the energy consumption is proportional to the delivery hop count by the Eqs. (2) (22). However, since NELS needs the control overhead for collecting the network boundary information and for flooding the information to the whole network by the Eq. (23), total energy consumption of the sink location service and the control overhead in NELS is very high by the Eq. (24). Thus, the energy consumption of NELS is higher than that of XYLS. However, if the network size is bigger than 6 m, the energy consumption of NELS is lower than that of XYLS, because for the increased network size, the increased control overhead of NELS is smaller than the increased energy consumption by forwarding SLA and SLQ messages along the network boundary of XYLS. Figure 1 shows that our numerical analysis result is similar to our simulation result. 5.3 Simulation results for the number of sinks In this section, we compare the performance of NELS, XYLS, and the proposed scheme for the number of sinks. We vary the number of sinks 1 6 at an interval of 1. Figures 11, 12 and 13 show the delivery distance, the delivery hop count, and the energy consumption for sink location service, respectively. If the number of sinks increases, the numbers of SLA and SLR messages is the same with the number of sinks, respectively. As shown in Fig. 11, the delivery distances for sink location service of NELS, XYLS, and the proposed scheme all increase as large as the sum of the delivery distance of SLA and SLR messages by the Eqs. (14) (16). However, each sink in Delivery Distance (m) NELS-SLA NELS-SLQ NELS-SLR NELS-SLS XYLS-SLA XYLS-SLQ XYLS-SLR XYLS-SLS PS-SLA PS-SLQ PS-SLR PS-SLS The Number of Sinks Fig. 11 Delivery distance for the number of sinks Delivery Hop Counts NELS-SLS XYLS-SLS PS-SLS The Number of Sinks Fig. 12 Delivery hop count for the number of sinks Energy Consumption (mw) NELS-SLS (Analysis) NELS-SLS (Simulation) NELS-CO (Analysis) NELS-CO (Simulation) NELS-SLS+CO (Analysis) NELS-SLS+CO (Simulation) XYLS-SLS (Analysis) XYLS-SLS (Simulation) PS-SLS (Analysis) PS-SLS (Simulation) The Number of Sinks Fig. 13 Energy consumption for the number of sinks NELS makes a SLA line quorum of the length ð2 RÞm, and each sink in the proposed scheme makes a SLA circle quorum of the length ðp RÞm, and each sink in XYLS make a SLA line quorums of the length ð2 RÞm and
13 Wireless Netw (214) 2: network boundary quorum of length ðp RÞm. Thus, XYLS has the longest delivery distance, the proposed scheme the second longest delivery distance, and NELS the shortest delivery distance. Figure 12 shows the delivery hop count for the number of sinks. The delivery hop count for sink location service is proportional to the delivery distance for sink location service by the Eqs. (17) (19). When both the network size and the number of sensor nodes are static, the average single hop progress is also static. Thus, Fig. 12 has a similar pattern to Fig. 11. Figure 13 shows the energy consumption for the number of sinks. The energy consumption for sink location service is proportional to the delivery hop count for sink location service by the Eqs. (2) (22). Thus, the energy consumption for sink location service in Fig. 13 has a similar pattern to that in Fig. 12. However, NELS has the energy consumption for the control overhead by collecting the network boundary information and flooding the information to the whole network. Thus, NELS has higher energy consumption than XYLS. However, if the number of sinks is more than about 23, NELS has lower energy consumption than XYLS, because a lot of sinks in XYLS make line quorums and network boundary quorums. Figure 13 shows that our numerical analysis result is similar to our simulation result. 5.4 Simulation results for the number of sources In this section, we compare the performance of NELS, XYLS, and the proposed scheme for the number of sources. We vary the number of sources 1 6 at an interval of 1. Figures 14, 15 and 16 show the delivery distance, the delivery hop count, and the energy consumption for sink location service, respectively. If the number of sources increases, the numbers of SLQ and SLR messages is the same with the number of sources, respectively. As shown in Fig. 14, the delivery distances for sink location service Delivery Distance (m) NELS-SLA NELS-SLQ NELS-SLR NELS-SLS XYLS-SLA XYLS-SLQ XYLS-SLR XYLS-SLS PS-SLA PS-SLQ PS-SLR PS-SLS The Number of Sources Fig. 14 Delivery distance for the number of sources Delivery Hop Counts NELS-SLS XYLS-SLS PS-SLS The Number of Sources Fig. 15 Delivery hop count for the number of sources Energy Consumption (mw) NELS-SLS (Analysis) NELS-SLS (Simulation) NELS-CO (Analysis) NELS-CO (Simulation) NELS-SLS+CO (Analysis) NELS-SLS+CO (Simulation) XYLS-SLS (Analysis) XYLS-SLS (Simulation) PS-SLS (Analysis) PS-SLS (Simulation) The Number of Sources Fig. 16 Energy consumption for the number of sources of NELS, XYLS, and the proposed scheme all increase as large as the sum of the delivery distance of SLQ and SLR messages by the Eqs. (14) (16). However, each source in NELS makes a SLQ line quorum of the length ð2 RÞm, each sink in XYLS makes a SLQ line quorum of the length ð2 RÞm and a SLQ network boundary quorum of length ðp RÞm, and each source in the proposed scheme makes a SLQ line quorum of the length ð 1 2 RÞm. Thus, XYLS has the longest delivery distance, NELS the second longest delivery distance, and the proposed scheme the shortest delivery distance. Figure 15 shows the delivery hop count for the number of sources. The delivery hop count for sink location service is proportional to the delivery distance for sink location service by the Eqs. (17) (19). When both the network size and the number of sensor nodes are static, the average single hop progress is also static. Thus, Fig. 15 has a similar pattern to Fig. 14.
14 56 Wireless Netw (214) 2: Figure 16 shows the energy consumption for the number of sources. The energy consumption for sink location service is proportional to the delivery hop count for sink location service by the Eqs. (2) (22). Thus, the energy consumption for sink location service in Fig. 16 has a similar pattern to the delivery hop count in Fig. 15. However, NELS has the energy consumption for the control overhead by collecting the network boundary information and flooding the information to the whole network. Thus, when the number of sources is small, NELS has higher energy consumption than XYLS. However, if the number of sources is more than about 23, NELS has lower energy consumption than XYLS, because a lot of sources in XYLS make SLQ line and network boundary quorums. Figure 16 shows that our numerical analysis result is similar to our simulation result. 5.5 Simulation results for the number of sensor nodes In this section, we compare the performance of NELS, XYLS, and the proposed scheme for the number of sensor nodes (that is, the node density). We vary the number of sensor nodes 1, 6, at an interval of 1,. Figure 17 shows the energy consumption for the number of sensor nodes. If the number of sensor nodes increases, because the average number of neighbor sensor nodes increases, the single hop progress (Single_Hop_Pro ave ) increases and thus the delivery hop count slowly decreases. As a result, the energy consumption for sink location service of all of NELS, XYLS, and the proposed protocol decreases. However, If the number of sensor nodes increases, the energy consumption for the control overhead of NELS increases with the number of sensor nodes because more sensor nodes are included for collecting the network boundary information and flooding the information. Thus, the energy consumption for both sink location service and control overhead of NELS is very high. 5.6 Simulation results for network irregularity In this section, we compare the performance of NELS, XYLS, and the proposed scheme for the network irregularity. The network irregularity is considered in terms of two cases, the irregularity degree of network boundary and the number of void areas. Figure 18 shows the energy consumption for the irregularity degree of network boundary. The irregularity degree of network boundary is defined as the ratio of the total boundary length of real network to the total boundary length of network of circle. In the simulation, we consider the network of circle with a radius 1, m. As shown in Fig. 18, when the irregularity degree of network boundary increases, all of NELS, XYLS, and the proposed scheme increase the energy consumption. In terms of sink location service, NELS is hardly affected by the network boundary irregularity because SLA and SLQ quorums are not constructed in the network boundary. However, in terms of control overhead, if the irregularity degree of network boundary increases, NELS increases the energy consumption for collecting the network boundary information due to the increased network boundary length. Since the proposed scheme makes some sinks construct SLA circle quorums along some parts of network boundary, it slowly increases the energy consumption for the increased network boundary irregularity. However, since XYLS make all sinks and sources constructs SLA and SLQ quorums along the network boundary, it sharply increases for the increased network boundary irregularity. Figure 19 shows the energy consumption for the number of void areas in the sensor network. We consider circle regions of radius 5 m as the size of void areas. As shown in Fig. 19, if the number of void areas increases, all of ALS, XYLS, and the proposed scheme increase the energy consumption for sink location service because SLA, SLQ, 18 Energy Consumption (mw) NELS-SLS (Analysis) NELS-SLS (Simulation) NELS-CO (Analysis) NELS-CO (Simulation) NELS-SLS+CO (Analysis) NELS-SLS+CO (Simulation) XYLS-SLS (Analysis) XYLS-SLS (Simulation) PS-SLS (Analysis) PS-SLS (Simulation) Energy Consumption (mw) NELS-CO (Simulation) XYLS-SLS (Simulation) PS-SLS (Simulation) The Number of Sensor Nodes Fig. 17 Energy consumption for the number of sensor nodes The Irregularity Degree of Network Boundary Fig. 18 Energy consumption for the irregularity degree of network boundary
15 Wireless Netw (214) 2: Energy Consumption (mw) NELS-SLS (Simulation) XYLS-SLS (Simulation) PS-SLS (Simulation) and SLR messages can meet much more the void areas and thus must detour the void areas. Since the total delivery distance of SLA, SLQ, and SLR messages in XYLS is longest as shown in the Eqs. (11) (13), it has the most energy consumption because it is most affected by the void areas. NELS has the second most energy consumption. The proposed protocol has the least energy consumption because it has the shortest total delivery distance of SLA, SLQ, and SLR messages. 6 Discussions The Number of Void Areas Fig. 19 Energy consumption for the number of void areas In this section, we discuss several issues related with our quorum-based sink location service scheme. 6.1 Location information of the network center In the proposed scheme, the location information of the network center is a very important element for conducting two purposes. As one purpose, every node uses the information to calculate a Height value. As the other one, a source uses the information as a destination to send a SLQ message. For the two purposes, a network operator can embed the location information of the network center to sensor nodes by programming and then deploy them in an interesting sensor field. However, the location information of the network center embedded in nodes can be different from that in the sensor network actually deployed by sensor nodes. Thus, the difference will affect the performance of the proposed scheme. In the proposed scheme, a sink sends a SLA message to make a circle path quorum consisting of sensor nodes with the same Height. Then, since the difference between two network center locations can request a sink to make a circle path quorum with higher Height, the circle path quorum becomes longer. 6.2 Realistic sensor networks As sensor nodes are densely and uniformly deployed in sensor networks, the hop count between any two nodes may be proportional to the distance between them. However, realistic sensor networks can be organized with sensor nodes that are sparsely and randomly deployed. Thus, the realistic sensor networks may have irregular network shapes and void areas. In the realistic sensor networks, the proportional relation between the distance and the hop count of any two nodes cannot be fully true. The reason is because any two nodes can have irregular network shapes and void areas between them in the realistic sensor networks. Thus, an approximate hop count between any two nodes is very difficult to be derived by the distance between them. However, we think because all of NELS, XYLS, and the proposed scheme use a geographic routing, they are equally influenced by irregular network shapes and void areas. As a result, they have longer delivery distance and thus higher energy consumption in realistic sensor networks. Actually, this comment is underpinned by our simulation results 18 and Number of crossing points In quorum-based sink location service, the most important issue is to guarantee at least one crossing point between SLA and SLQ quorums. Figures 2, 3 and 5 show the overviews of NELS, XYLS, and the proposed scheme, respectively. As shown in the figures, NELS and the proposed scheme can have only one crossing point, but XYLS can have 1 5 crossing points. If any network failures such as link and node failures happen to crossing points, XYLS is more robust than NESL and the proposed scheme because it can have more crossing points. Thus, the number of crossing points may be related with the robustness of sink location service. 6.4 Location of crossing points When we see Figs. 2, 3 and 5, we can intuitionally expect where crossing points locate in NELS, XYLS, and the proposed scheme. Both NELS and the proposed scheme make crossing points locate inside the network. On the other hand, if XYLS does not have a crossing point between SLA column and SLQ low quorums, it makes crossing points locate in the network boundary. When we recognize the fact that almost source nodes locate inside the network, NELS and the proposed scheme make distances between sources and crossing points shorter than XYLS. Then, NELS and the proposed scheme can provide sink location service faster than XYLS. Thus, location of crossing points may be related with sink location service delay.
16 58 Wireless Netw (214) 2: Conclusion In this paper, we designed and evaluated novel quorumbased sink location service scheme based on circle and line paths for geographic routing in wireless sensor networks. The proposed scheme only requests each node to use the location information of network center and its Height value from the network center during the network initialization phase to guarantee at least crossing point between the SLA and SLQ messages. In the proposed scheme, a sink constructs a SLA circle quorum by sending a SLA message along a circle path with the same Height, the center of the circle is the network center. On the other hand, a source node constructs a SLQ line quorum by sending a SLQ message to the network center and a copy of the SLQ message to an edge node in the network boundary. By this way, the proposed scheme can guarantee that the SLA circle and SLQ line quorums have at least one crossing point. Then, the sensor node located on the crossing point sends a SLR message with the location information of the sink to the source node. Thus, the proposed scheme does not need to collect the network boundary information and flood the information to the whole network or to forward SLA and SLQ messages along the network boundary. Our numerical analysis and simulation results verified that the proposed scheme outperforms NELS in the network boundary information-based approach and XYLS in the network boundary forwarding-based approach in terms of the delivery distance, the delivery hop count, and the energy consumption. References 1. Karp, B., & Kung. H. T. (2). GPSR: Greedy perimeter stateless routing for wireless networks. In Proceedings of the 6th annual international conference on mobile computing and networking (pp ). Boston: ACM Press. 2. Hofmann-Wellenhof, B., Lichtenegger, H., & Collins, J. (1997). Global positioning system: Theory and practice (4th ed). Berlin: Springer. 3. Han, S., Lee, S., Lee, S., Park, J., & Park, S. (21). Node distribution-based localization for large-scale wireless sensor networks. Springer Wireless Networks, 16(5), Kannan, A., Fidan, B., & Mao, G. (211). Use of flip ambiguity probabilities in robust sensor network localization. Springer Wireless Networks, 17(5), Chen, Q., Kanhere, S., & Hassan, M. (213). Adaptive position update for geographic routing in mobile ad hoc networks. IEEE Transactions on Mobile Computing, 12(3), He, T., Stankovic, J. A., Lu, C., & Abdelzaher, T. F. (25). A spatiotemporal communication protocol for wireless sensor networks. IEEE Transactions on Parallel and Distributed Systems, 16(1), Tan, G., & Kermarrec, A. (212). Greedy geographic routing in large-scale sensor networks: A minimum network decomposition approach. IEEE/ACM Transactions on Networking, 2(3), Zeng, K., Yang, J., & Lou, W. (212). On energy efficiency of geographic opportunistic routing in lossy multihop wireless networks. Springer Wireless Networks, 18(8), Intanagonwiwat, C., Govindan, R., & Estrin, D. (2). Directed diffusion: A scalable and robust communication paradigm for sensor networks. In Proceedings of the 6th annual international conference on mobile computing and networking (pp ). Boston: ACM Press. 1. Ye, F., Luo, H., Cheng, J., Lu, S., & Zhang, L. (22). TTDD: A two-tier data dissemination model for large-scale wireless sensor networks. In Proceedings of ACM/IEEE MOBICOM(pp ). 11. Yu, F., Choi, Y., Park, S., Lee, E., Jin, M., & Kim, S. (28). Sink location service for geographic routing in wireless sensor networks. In Proceedings of the IEEE WCNC. 12. Park, H., Kim, T., Lee, J., Jin, M., & Kim, S. (29). Sink location service via inner rectangular in wireless sensor networks. In Proceedings of the IEEE AINA. 13. Stojmenovic, I., Liu, D., & Jia, X. (28). A scalable quorumbased location service in ad hoc and sensor networks. International Journal on Communication Networks and Distributed Systems, 1(1), Chen, D., & Varshney, P. (27). A survey of void handling techniques for geographic routing in wireless networks. IEEE Communication Surveys and Tutorials, Xiang, L., Luo, J., & Vasilakow, A. (211). Compressed data aggregation for energy efficient wireless sensor networks. In Proceedings of the IEEE SECON. 16. Aziz, S., & Pham, D. (213). Energy efficient image transmission in wireless multimedia sensor networks. IEEE Communications Letters, 17(6), Liu,Y.,Xiong,N.,Zhao,Y.,Vasilakos,A.,Gao,J.,&Jia,Y. (21). Multi-layer clustering routing algorithm for wireless vehicular sensor networks. IET Communications, 4(7), Guo, W., Xiong, N., Vasilakos, A., Chen, G., & Cheng, H. (211). Multi-source temporal data aggregation in wireless sensor networks. Springer Wireless Personal Communications, 56(3), Fekete, S. P., Kroeller, A., Pfisterer, D., Fischer, S., & Buschmann, C. (24). Neighborhood-based topology recognition in sensor networks. In Algorithmic aspects of wireless sensor networks: First international workshop (ALGOSENSOR) (pp. 136). 2. Bondy, J. A., & Murty, U. S. R. (1976). Graph Theory with Applications. North-Holland: Elsevier. 21. Niculescu, D., & Nath, B. (23). DV based positioning in ad hoc networks. Telecommunication Systems, 22(1 4), Kim, H. S., Abdelzaher, T. F., & Kwon, W. H. (23). Minimumenergy asynchronous dissemination to mobile sinks in wireless sensor networks. In Proceedings of the 1st ACM international conference on Embedded networked sensor systems (pp ). 23. Lee, E., Park, S., Yu, F., & Kim, S.-H. (21). Data gathering mechanism with local sink in geographic routing for wireless sensor networks. IEEE Transactions on Consumer Electronics, 56(3), Chen, D., Deng, J., & Varshney, P. (27). Selection of a forwarding area for contention-based geographic forwarding in wireless multi-hop networks. IEEE Transactions on Vehicular Technology, 56(5),
17 Wireless Netw (214) 2: Scalable Network Technologies, Qualnet, [online] available: Polastre, J., Szewczyk, R., & Culler, D. (25). Telos: Enabling ultra-low power wireless research. In Proceedings of the IEEE IPSN. Author Biographies Euisin Lee received the B.S., M.S., Ph.D. degrees in Computer Engineering from Chungnam National University, Daejeon, Korea, in 25, 27, and 212, respectively. He is currently working as a post-doctoral researcher in the Department of Computer Science at University California, Los Angeles, USA. His research interests are in the areas of computer communication and networking. He is mainly interested in routing, multicasting, mobility management, location service, and QoS (Real-time and Reliability) in Mobile Ad hoc Networks (MANETs), Wireless Sensor Networks (WSNs), and Vehicular Ad hoc Networks (VANETs). Fucai Yu received the B.S. degree in communication engineering from Lanzhou Jiaotong University, Lanzhou, China, in 1999 and M.S. and Ph.D. degrees in computer science from Chungnam National University, Daejeon, Korea, in 26 and 21, respectively. He is currently an associate professor in electrical engineering at UESTC. His current research interests include routing for MANET and sensor networks. Soochang Park received the B.S., M.S., and Ph.D. degrees in Computer Engineering from Chungnam National University Daejeon, Korea, in 25, 27, and 211, respectively. He was a postdoctoral fellow in Rutgers Center for Operations Research (RUTCOR) of Rutgers University, the State University of New Jersey, USA, in 212. He is currently a research fellow in the Service Architecture Lab of Réseaux et Services Multimedia Mobiles (RS2M) Département, Telecom SudParis, France. His research interests include mobility, multicast, QoS, and routing in sensor networks and ad hoc networks. Sang-Ha Kim received the B.S. degree from Seoul National University, Seoul, Korea, in 198, and the M.S. in chemical physics and Ph.D. degrees in computer science from University of Houston, Houston, USA, in 1984 and 1989, respectively. He joined the System Engineering Research Institute (SERI) in Korean Institute of Science and Technology (KIST), Seoul, Korea, as a senior research scientist in 199. After two years, he moved into Chungnam National University, at which he is currently working as a professor. His current research concerns are all aspects of the performance analysis, protocols, architectures, and implementation relating to all types of networks including Internet and telecommunication networks. He has the special interest in mobility and quality of services (QoS) in wired/wireless networks. Youngtae Noh is a Software Engineer at Cisco Systems, Inc. Prior to joining Cisco Systems, he received his B.S. in computer science from Chosun University in 25, an M.S. degree in Information and Communication from Gwangju Institute of Science Technology (GIST) in 27, and a Ph.D. in computer science at University of California, Los Angeles (UCLA) in 212. His research areas include data center networking, wireless networking, future Internet, and mobile/pervasive computing. Eun-Kyu Lee received the B.S. degree in Electronics Engineering from Dongguk University and the M.S. degree in Computer Engineering from Korea Advanced Institute of Science Technology (KAIST) in 2 and 22, respectively. From 22 to 28, he worked as a research scientist for Electronics and Telecommunications Research Institute (ETRI), Korea. He joined the Computer Science Department of UCLA, in 28, where he is pursuing a Doctorate degree. His research interests are mainly in network security, wireless networking, pervasive computing, and middleware systems. He has been involved in many research projects in the fields of smart grid, smart building, electric vehicle network, and mobile cloud computing.
Data gathering using mobile agents for reducing traffic in dense mobile wireless sensor networks
 Mobile Information Systems 9 (23) 295 34 295 DOI.3233/MIS-364 IOS Press Data gathering using mobile agents for reducing traffic in dense mobile wireless sensor networks Keisuke Goto, Yuya Sasaki, Takahiro
Mobile Information Systems 9 (23) 295 34 295 DOI.3233/MIS-364 IOS Press Data gathering using mobile agents for reducing traffic in dense mobile wireless sensor networks Keisuke Goto, Yuya Sasaki, Takahiro
FERMA: An Efficient Geocasting Protocol for Wireless Sensor Networks with Multiple Target Regions
 FERMA: An Efficient Geocasting Protocol for Wireless Sensor Networks with Multiple Target Regions Young-Mi Song, Sung-Hee Lee, and Young-Bae Ko College of Information and Communication, Ajou University,
FERMA: An Efficient Geocasting Protocol for Wireless Sensor Networks with Multiple Target Regions Young-Mi Song, Sung-Hee Lee, and Young-Bae Ko College of Information and Communication, Ajou University,
Mobile Sink to Track Multiple Targets in Wireless Visual Sensor Networks
 Mobile Sink to Track Multiple Targets in Wireless Visual Sensor Networks William Shaw 1, Yifeng He 1, and Ivan Lee 1,2 1 Department of Electrical and Computer Engineering, Ryerson University, Toronto,
Mobile Sink to Track Multiple Targets in Wireless Visual Sensor Networks William Shaw 1, Yifeng He 1, and Ivan Lee 1,2 1 Department of Electrical and Computer Engineering, Ryerson University, Toronto,
On the scalability of rendezvous-based location services for geographic wireless ad hoc routing
 Computer Networks 51 (2007) 3693 3714 www.elsevier.com/locate/comnet On the scalability of rendezvous-based location services for geographic wireless ad hoc routing Saumitra M. Das, Himabindu Pucha, Y.
Computer Networks 51 (2007) 3693 3714 www.elsevier.com/locate/comnet On the scalability of rendezvous-based location services for geographic wireless ad hoc routing Saumitra M. Das, Himabindu Pucha, Y.
Energy aware geographic routing in wireless sensor networks with anchor nodes. Mircea Cretu Stancu Utrecht University Computing Science May 2013
 Energy aware geographic routing in wireless sensor networks with anchor nodes Mircea Cretu Stancu Utrecht University Computing Science May 2013 Overview Introduction Current paradigm EAGR preliminaries
Energy aware geographic routing in wireless sensor networks with anchor nodes Mircea Cretu Stancu Utrecht University Computing Science May 2013 Overview Introduction Current paradigm EAGR preliminaries
Localized and Incremental Monitoring of Reverse Nearest Neighbor Queries in Wireless Sensor Networks 1
 Localized and Incremental Monitoring of Reverse Nearest Neighbor Queries in Wireless Sensor Networks 1 HAI THANH MAI AND MYOUNG HO KIM Department of Computer Science Korea Advanced Institute of Science
Localized and Incremental Monitoring of Reverse Nearest Neighbor Queries in Wireless Sensor Networks 1 HAI THANH MAI AND MYOUNG HO KIM Department of Computer Science Korea Advanced Institute of Science
Performance Comparison of Scalable Location Services for Geographic Ad Hoc Routing
 Performance Comparison of Scalable Location Services for Geographic Ad Hoc Routing Saumitra M. Das, Himabindu Pucha and Y. Charlie Hu School of Electrical and Computer Engineering Purdue University West
Performance Comparison of Scalable Location Services for Geographic Ad Hoc Routing Saumitra M. Das, Himabindu Pucha and Y. Charlie Hu School of Electrical and Computer Engineering Purdue University West
CS 229 Final Report: Location Based Adaptive Routing Protocol(LBAR) using Reinforcement Learning
 CS 229 Final Report: Location Based Adaptive Routing Protocol(LBAR) using Reinforcement Learning By: Eunjoon Cho and Kevin Wong Abstract In this paper we present an algorithm for a location based adaptive
CS 229 Final Report: Location Based Adaptive Routing Protocol(LBAR) using Reinforcement Learning By: Eunjoon Cho and Kevin Wong Abstract In this paper we present an algorithm for a location based adaptive
Table of Contents. 1. Introduction. 2. Geographic Routing. 2.1 Routing Mechanisms. 2.2 Destination Location. 2.3 Location Inaccuracy. 3.
 Geographic Protocols in Sensor Networks Karim Seada, Ahmed Helmy Electrical Engineering Department, University of Southern California {seada, helmy}@usc.edu Table of Contents 1. Introduction 2. Geographic
Geographic Protocols in Sensor Networks Karim Seada, Ahmed Helmy Electrical Engineering Department, University of Southern California {seada, helmy}@usc.edu Table of Contents 1. Introduction 2. Geographic
Energy Aware Node Placement Algorithm for Wireless Sensor Network
 Advance in Electronic and Electric Engineering. ISSN 2231-1297, Volume 4, Number 6 (2014), pp. 541-548 Research India Publications http://www.ripublication.com/aeee.htm Energy Aware Node Placement Algorithm
Advance in Electronic and Electric Engineering. ISSN 2231-1297, Volume 4, Number 6 (2014), pp. 541-548 Research India Publications http://www.ripublication.com/aeee.htm Energy Aware Node Placement Algorithm
Routing protocols in WSN
 Routing protocols in WSN 1.1 WSN Routing Scheme Data collected by sensor nodes in a WSN is typically propagated toward a base station (gateway) that links the WSN with other networks where the data can
Routing protocols in WSN 1.1 WSN Routing Scheme Data collected by sensor nodes in a WSN is typically propagated toward a base station (gateway) that links the WSN with other networks where the data can
CACHING IN WIRELESS SENSOR NETWORKS BASED ON GRIDS
 International Journal of Wireless Communications and Networking 3(1), 2011, pp. 7-13 CACHING IN WIRELESS SENSOR NETWORKS BASED ON GRIDS Sudhanshu Pant 1, Naveen Chauhan 2 and Brij Bihari Dubey 3 Department
International Journal of Wireless Communications and Networking 3(1), 2011, pp. 7-13 CACHING IN WIRELESS SENSOR NETWORKS BASED ON GRIDS Sudhanshu Pant 1, Naveen Chauhan 2 and Brij Bihari Dubey 3 Department
Scheduling of Multiple Applications in Wireless Sensor Networks Using Knowledge of Applications and Network
 International Journal of Information and Computer Science (IJICS) Volume 5, 2016 doi: 10.14355/ijics.2016.05.002 www.iji-cs.org Scheduling of Multiple Applications in Wireless Sensor Networks Using Knowledge
International Journal of Information and Computer Science (IJICS) Volume 5, 2016 doi: 10.14355/ijics.2016.05.002 www.iji-cs.org Scheduling of Multiple Applications in Wireless Sensor Networks Using Knowledge
CHAPTER 5 PROPAGATION DELAY
 98 CHAPTER 5 PROPAGATION DELAY Underwater wireless sensor networks deployed of sensor nodes with sensing, forwarding and processing abilities that operate in underwater. In this environment brought challenges,
98 CHAPTER 5 PROPAGATION DELAY Underwater wireless sensor networks deployed of sensor nodes with sensing, forwarding and processing abilities that operate in underwater. In this environment brought challenges,
A Location-based Directional Route Discovery (LDRD) Protocol in Mobile Ad-hoc Networks
 A Location-based Directional Route Discovery (LDRD) Protocol in Mobile Ad-hoc Networks Stephen S. Yau, Wei Gao, and Dazhi Huang Dept. of Computer Science and Engineering Arizona State University Tempe,
A Location-based Directional Route Discovery (LDRD) Protocol in Mobile Ad-hoc Networks Stephen S. Yau, Wei Gao, and Dazhi Huang Dept. of Computer Science and Engineering Arizona State University Tempe,
Fault-Tolerant Routing Algorithm in Meshes with Solid Faults
 Fault-Tolerant Routing Algorithm in Meshes with Solid Faults Jong-Hoon Youn Bella Bose Seungjin Park Dept. of Computer Science Dept. of Computer Science Dept. of Computer Science Oregon State University
Fault-Tolerant Routing Algorithm in Meshes with Solid Faults Jong-Hoon Youn Bella Bose Seungjin Park Dept. of Computer Science Dept. of Computer Science Dept. of Computer Science Oregon State University
Trail-Based Search for Efficient Event Report to Mobile Actors in Wireless Sensor and Actor Networks
 sensors Article Trail-Based Search for Efficient Event Report to Mobile Actors in Wireless Sensor and Actor Networks Zhezhuang Xu 1, *, Guanglun Liu 1, Haotian Yan 2, Bin Cheng 3 and Feilong Lin 4 1 School
sensors Article Trail-Based Search for Efficient Event Report to Mobile Actors in Wireless Sensor and Actor Networks Zhezhuang Xu 1, *, Guanglun Liu 1, Haotian Yan 2, Bin Cheng 3 and Feilong Lin 4 1 School
An efficient implementation of the greedy forwarding strategy
 An efficient implementation of the greedy forwarding strategy Hannes Stratil Embedded Computing Systems Group E182/2 Technische Universität Wien Treitlstraße 3 A-1040 Vienna Email: hannes@ecs.tuwien.ac.at
An efficient implementation of the greedy forwarding strategy Hannes Stratil Embedded Computing Systems Group E182/2 Technische Universität Wien Treitlstraße 3 A-1040 Vienna Email: hannes@ecs.tuwien.ac.at
Zonal Rumor Routing for. Wireless Sensor Networks
 Tarun Banka Department of Electrical and Computer Engineering tarunb@engr.colostate.edu Zonal Rumor Routing for. Wireless Sensor Networks Gagan Tandon Department of Computer Science gagan@cs.colostate.edu
Tarun Banka Department of Electrical and Computer Engineering tarunb@engr.colostate.edu Zonal Rumor Routing for. Wireless Sensor Networks Gagan Tandon Department of Computer Science gagan@cs.colostate.edu
Sleep scheduling with expected common coverage in wireless sensor networks
 DOI 10.1007/s11276-010-0262-2 Sleep scheduling with expected common coverage in wireless sensor networks Eyuphan Bulut Ibrahim Korpeoglu Ó Springer Science+Business Media, LLC 2010 Abstract Sleep scheduling,
DOI 10.1007/s11276-010-0262-2 Sleep scheduling with expected common coverage in wireless sensor networks Eyuphan Bulut Ibrahim Korpeoglu Ó Springer Science+Business Media, LLC 2010 Abstract Sleep scheduling,
ARROW: Azimuth-Range ROuting for large-scale Wireless sensor networks
 Kulakowski et al. EURASIP Journal on Wireless Communications and Networking 2013, 2013:93 RESEARCH Open Access ARROW: Azimuth-Range ROuting for large-scale Wireless sensor networks Pawel Kulakowski 1*,
Kulakowski et al. EURASIP Journal on Wireless Communications and Networking 2013, 2013:93 RESEARCH Open Access ARROW: Azimuth-Range ROuting for large-scale Wireless sensor networks Pawel Kulakowski 1*,
Challenges in Geographic Routing: Sparse Networks, Obstacles, and Traffic Provisioning
 Challenges in Geographic Routing: Sparse Networks, Obstacles, and Traffic Provisioning Brad Karp Berkeley, CA bkarp@icsi.berkeley.edu DIMACS Pervasive Networking Workshop 2 May, 2 Motivating Examples Vast
Challenges in Geographic Routing: Sparse Networks, Obstacles, and Traffic Provisioning Brad Karp Berkeley, CA bkarp@icsi.berkeley.edu DIMACS Pervasive Networking Workshop 2 May, 2 Motivating Examples Vast
Hole Detection and Boundary Recognition in Wireless Sensor Networks
 Hole Detection and Boundary Recognition in Wireless Sensor Networks Kun-Ying Hsieh Dept. of Computer Science and Information Engineering National Central University Jhongli, 32054, Taiwan E-mail: rocky@axp1.csie.ncu.edu.tw
Hole Detection and Boundary Recognition in Wireless Sensor Networks Kun-Ying Hsieh Dept. of Computer Science and Information Engineering National Central University Jhongli, 32054, Taiwan E-mail: rocky@axp1.csie.ncu.edu.tw
Analysis of Cluster-Based Energy-Dynamic Routing Protocols in WSN
 Analysis of Cluster-Based Energy-Dynamic Routing Protocols in WSN Mr. V. Narsing Rao 1, Dr.K.Bhargavi 2 1,2 Asst. Professor in CSE Dept., Sphoorthy Engineering College, Hyderabad Abstract- Wireless Sensor
Analysis of Cluster-Based Energy-Dynamic Routing Protocols in WSN Mr. V. Narsing Rao 1, Dr.K.Bhargavi 2 1,2 Asst. Professor in CSE Dept., Sphoorthy Engineering College, Hyderabad Abstract- Wireless Sensor
A Simple Sink Mobility Support Algorithm for Routing Protocols in Wireless Sensor Networks
 A Simple Mobility Support Algorithm for Routing Protocols in Wireless Sensor Networks Chun-Su Park, You-Sun Kim, Kwang-Wook Lee, Seung-Kyun Kim, and Sung-Jea Ko Department of Electronics Engineering, Korea
A Simple Mobility Support Algorithm for Routing Protocols in Wireless Sensor Networks Chun-Su Park, You-Sun Kim, Kwang-Wook Lee, Seung-Kyun Kim, and Sung-Jea Ko Department of Electronics Engineering, Korea
I. INTRODUCTION. Keywords: Novelty Filter, Routing, Singular Value Decomposition, Wireless Sensor Networks, Virtual Coordinates
 Dimension Reduction of Virtual Coordinate Systems in Wireless Sensor Networks * Dulanjalie C. Dhanapala and Anura P. Jayasumana Department of Electrical and Computer Engineering, Colorado State University,
Dimension Reduction of Virtual Coordinate Systems in Wireless Sensor Networks * Dulanjalie C. Dhanapala and Anura P. Jayasumana Department of Electrical and Computer Engineering, Colorado State University,
IMPACT OF LEADER SELECTION STRATEGIES ON THE PEGASIS DATA GATHERING PROTOCOL FOR WIRELESS SENSOR NETWORKS
 IMPACT OF LEADER SELECTION STRATEGIES ON THE PEGASIS DATA GATHERING PROTOCOL FOR WIRELESS SENSOR NETWORKS Indu Shukla, Natarajan Meghanathan Jackson State University, Jackson MS, USA indu.shukla@jsums.edu,
IMPACT OF LEADER SELECTION STRATEGIES ON THE PEGASIS DATA GATHERING PROTOCOL FOR WIRELESS SENSOR NETWORKS Indu Shukla, Natarajan Meghanathan Jackson State University, Jackson MS, USA indu.shukla@jsums.edu,
ORE Open Research Exeter
 ORE Open Research Exeter TITLE Energy-aware Dual-path Geographic Routing to Bypass Routing Holes in Wireless Sensor Networks AUTHORS Huang, H; Yin, H; Min, G; et al. JOURNAL IEEE Transactions on Mobile
ORE Open Research Exeter TITLE Energy-aware Dual-path Geographic Routing to Bypass Routing Holes in Wireless Sensor Networks AUTHORS Huang, H; Yin, H; Min, G; et al. JOURNAL IEEE Transactions on Mobile
CHAPTER 2 WIRELESS SENSOR NETWORKS AND NEED OF TOPOLOGY CONTROL
 WIRELESS SENSOR NETWORKS AND NEED OF TOPOLOGY CONTROL 2.1 Topology Control in Wireless Sensor Networks Network topology control is about management of network topology to support network-wide requirement.
WIRELESS SENSOR NETWORKS AND NEED OF TOPOLOGY CONTROL 2.1 Topology Control in Wireless Sensor Networks Network topology control is about management of network topology to support network-wide requirement.
A More Realistic Energy Dissipation Model for Sensor Nodes
 A More Realistic Energy Dissipation Model for Sensor Nodes Raquel A.F. Mini 2, Antonio A.F. Loureiro, Badri Nath 3 Department of Computer Science Federal University of Minas Gerais Belo Horizonte, MG,
A More Realistic Energy Dissipation Model for Sensor Nodes Raquel A.F. Mini 2, Antonio A.F. Loureiro, Badri Nath 3 Department of Computer Science Federal University of Minas Gerais Belo Horizonte, MG,
End-To-End Delay Optimization in Wireless Sensor Network (WSN)
 Shweta K. Kanhere 1, Mahesh Goudar 2, Vijay M. Wadhai 3 1,2 Dept. of Electronics Engineering Maharashtra Academy of Engineering, Alandi (D), Pune, India 3 MITCOE Pune, India E-mail: shweta.kanhere@gmail.com,
Shweta K. Kanhere 1, Mahesh Goudar 2, Vijay M. Wadhai 3 1,2 Dept. of Electronics Engineering Maharashtra Academy of Engineering, Alandi (D), Pune, India 3 MITCOE Pune, India E-mail: shweta.kanhere@gmail.com,
Nearest Neighbor Query in Location- Aware Mobile Ad-Hoc Network
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 3, March 2015,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 3, March 2015,
Geographical Routing Algorithms In Asynchronous Wireless Sensor Network
 Geographical Routing Algorithms In Asynchronous Wireless Sensor Network Vaishali.S.K, N.G.Palan Electronics and telecommunication, Cummins College of engineering for women Karvenagar, Pune, India Abstract-
Geographical Routing Algorithms In Asynchronous Wireless Sensor Network Vaishali.S.K, N.G.Palan Electronics and telecommunication, Cummins College of engineering for women Karvenagar, Pune, India Abstract-
ROUTING ALGORITHMS Part 2: Data centric and hierarchical protocols
 ROUTING ALGORITHMS Part 2: Data centric and hierarchical protocols 1 Negative Reinforcement Time out Explicitly degrade the path by re-sending interest with lower data rate. Source Gradient New Data Path
ROUTING ALGORITHMS Part 2: Data centric and hierarchical protocols 1 Negative Reinforcement Time out Explicitly degrade the path by re-sending interest with lower data rate. Source Gradient New Data Path
Routing in Sensor Networks
 Routing in Sensor Networks Routing in Sensor Networks Large scale sensor networks will be deployed, and require richer inter-node communication In-network storage (DCS, GHT, DIM, DIFS) In-network processing
Routing in Sensor Networks Routing in Sensor Networks Large scale sensor networks will be deployed, and require richer inter-node communication In-network storage (DCS, GHT, DIM, DIFS) In-network processing
ROUTING is an important issue that affects wireless
 1 Virtual-Coordinate-Based Delivery-Guaranteed Routing Protocol in Wireless Sensor Networks Ming-Jer Tsai, Hong-Yen Yang, Bing-Hong Liu, and Wen-Qian Huang Abstract In this paper, we first propose a method,,
1 Virtual-Coordinate-Based Delivery-Guaranteed Routing Protocol in Wireless Sensor Networks Ming-Jer Tsai, Hong-Yen Yang, Bing-Hong Liu, and Wen-Qian Huang Abstract In this paper, we first propose a method,,
Replica Distribution Scheme for Location-Dependent Data in Vehicular Ad Hoc Networks using a Small Number of Fixed Nodes
 Replica Distribution Scheme for Location-Dependent Data in Vehicular d Hoc Networks using a Small Number of Fixed Nodes Junichiro Okamoto and Susumu Ishihara Graduate School of Engineering, Shizuoka University,
Replica Distribution Scheme for Location-Dependent Data in Vehicular d Hoc Networks using a Small Number of Fixed Nodes Junichiro Okamoto and Susumu Ishihara Graduate School of Engineering, Shizuoka University,
Geo-Routing. Chapter 2. Ad Hoc and Sensor Networks Roger Wattenhofer
 Geo-Routing Chapter 2 Ad Hoc and Sensor Networks Roger Wattenhofer 2/1 Application of the Week: Mesh Networking (Roofnet) Sharing Internet access Cheaper for everybody Several gateways fault-tolerance
Geo-Routing Chapter 2 Ad Hoc and Sensor Networks Roger Wattenhofer 2/1 Application of the Week: Mesh Networking (Roofnet) Sharing Internet access Cheaper for everybody Several gateways fault-tolerance
TIMSS 2011 Fourth Grade Mathematics Item Descriptions developed during the TIMSS 2011 Benchmarking
 TIMSS 2011 Fourth Grade Mathematics Item Descriptions developed during the TIMSS 2011 Benchmarking Items at Low International Benchmark (400) M01_05 M05_01 M07_04 M08_01 M09_01 M13_01 Solves a word problem
TIMSS 2011 Fourth Grade Mathematics Item Descriptions developed during the TIMSS 2011 Benchmarking Items at Low International Benchmark (400) M01_05 M05_01 M07_04 M08_01 M09_01 M13_01 Solves a word problem
A Color-theory-based Energy Efficient Routing Algorithm for Wireless Sensor Networks
 A Color-theory-based Energy Efficient Routing Algorithm for Wireless Sensor Networks Tai-Jung Chang Kuochen Wang 1 Yi-Ling Hsieh Department of Computer Science National Chiao Tung University Hsinchu Taiwan
A Color-theory-based Energy Efficient Routing Algorithm for Wireless Sensor Networks Tai-Jung Chang Kuochen Wang 1 Yi-Ling Hsieh Department of Computer Science National Chiao Tung University Hsinchu Taiwan
Information Brokerage
 Information Brokerage Sensing Networking Leonidas Guibas Stanford University Computation CS321 Information Brokerage Services in Dynamic Environments Information Brokerage Information providers (sources,
Information Brokerage Sensing Networking Leonidas Guibas Stanford University Computation CS321 Information Brokerage Services in Dynamic Environments Information Brokerage Information providers (sources,
An Energy-Efficient MAC using Dynamic Phase Shift for Wireless Sensor Networks
 An Energy-Efficient MAC using Dynamic Phase Shift for Wireless Sensor Networks Yoh-han Lee Department of Electrical Engineering Korea Advanced Institute of Science & Technology Daejeon, KOREA yohhanlee@kaist.ac.kr
An Energy-Efficient MAC using Dynamic Phase Shift for Wireless Sensor Networks Yoh-han Lee Department of Electrical Engineering Korea Advanced Institute of Science & Technology Daejeon, KOREA yohhanlee@kaist.ac.kr
QoS-Enabled Video Streaming in Wireless Sensor Networks
 QoS-Enabled Video Streaming in Wireless Sensor Networks S. Guo and T.D.C. Little Department of Electrical and Computer Engineering Boston University, Boston, MA 02215 {guosong, tdcl}@bu.edu MCL Technical
QoS-Enabled Video Streaming in Wireless Sensor Networks S. Guo and T.D.C. Little Department of Electrical and Computer Engineering Boston University, Boston, MA 02215 {guosong, tdcl}@bu.edu MCL Technical
Distributed Indexing and Data Dissemination in Large Scale Wireless Sensor Networks
 Distributed Indexing and Data Dissemination in Large Scale Wireless Sensor Networks Yiwei Wu Department of Computer Science Georgia State University Email: wyw@cs.gsu.edu Yingshu Li Department of Computer
Distributed Indexing and Data Dissemination in Large Scale Wireless Sensor Networks Yiwei Wu Department of Computer Science Georgia State University Email: wyw@cs.gsu.edu Yingshu Li Department of Computer
Geographic Routing Without Location Information. AP, Sylvia, Ion, Scott and Christos
 Geographic Routing Without Location Information AP, Sylvia, Ion, Scott and Christos Routing in Wireless Networks Distance vector DSDV On-demand DSR, TORA, AODV Discovers and caches routes on demand Geographic
Geographic Routing Without Location Information AP, Sylvia, Ion, Scott and Christos Routing in Wireless Networks Distance vector DSDV On-demand DSR, TORA, AODV Discovers and caches routes on demand Geographic
Course Number: Course Title: Geometry
 Course Number: 1206310 Course Title: Geometry RELATED GLOSSARY TERM DEFINITIONS (89) Altitude The perpendicular distance from the top of a geometric figure to its opposite side. Angle Two rays or two line
Course Number: 1206310 Course Title: Geometry RELATED GLOSSARY TERM DEFINITIONS (89) Altitude The perpendicular distance from the top of a geometric figure to its opposite side. Angle Two rays or two line
IMPROVING THE DATA COLLECTION RATE IN WIRELESS SENSOR NETWORKS BY USING THE MOBILE RELAYS
 IMPROVING THE DATA COLLECTION RATE IN WIRELESS SENSOR NETWORKS BY USING THE MOBILE RELAYS 1 K MADHURI, 2 J.KRISHNA, 3 C.SIVABALAJI II M.Tech CSE, AITS, Asst Professor CSE, AITS, Asst Professor CSE, NIST
IMPROVING THE DATA COLLECTION RATE IN WIRELESS SENSOR NETWORKS BY USING THE MOBILE RELAYS 1 K MADHURI, 2 J.KRISHNA, 3 C.SIVABALAJI II M.Tech CSE, AITS, Asst Professor CSE, AITS, Asst Professor CSE, NIST
Nodes Energy Conserving Algorithms to prevent Partitioning in Wireless Sensor Networks
 IJCSNS International Journal of Computer Science and Network Security, VOL.17 No.9, September 2017 139 Nodes Energy Conserving Algorithms to prevent Partitioning in Wireless Sensor Networks MINA MAHDAVI
IJCSNS International Journal of Computer Science and Network Security, VOL.17 No.9, September 2017 139 Nodes Energy Conserving Algorithms to prevent Partitioning in Wireless Sensor Networks MINA MAHDAVI
Optimization on TEEN routing protocol in cognitive wireless sensor network
 Ge et al. EURASIP Journal on Wireless Communications and Networking (2018) 2018:27 DOI 10.1186/s13638-018-1039-z RESEARCH Optimization on TEEN routing protocol in cognitive wireless sensor network Yanhong
Ge et al. EURASIP Journal on Wireless Communications and Networking (2018) 2018:27 DOI 10.1186/s13638-018-1039-z RESEARCH Optimization on TEEN routing protocol in cognitive wireless sensor network Yanhong
3. Evaluation of Selected Tree and Mesh based Routing Protocols
 33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
Energy-efficient Data Dissemination in Wireless Sensor Networks
 Energy-efficient Data Dissemination in Wireless Sensor Networks Ji-Han Jiang 1 Kuo-Hua Kao 2 Singing ee 2 1 Department of Computer Science and Information Engineering National Formosa University, Yun-in,
Energy-efficient Data Dissemination in Wireless Sensor Networks Ji-Han Jiang 1 Kuo-Hua Kao 2 Singing ee 2 1 Department of Computer Science and Information Engineering National Formosa University, Yun-in,
Evaluation of Cartesian-based Routing Metrics for Wireless Sensor Networks
 Evaluation of Cartesian-based Routing Metrics for Wireless Sensor Networks Ayad Salhieh Department of Electrical and Computer Engineering Wayne State University Detroit, MI 48202 ai4874@wayne.edu Loren
Evaluation of Cartesian-based Routing Metrics for Wireless Sensor Networks Ayad Salhieh Department of Electrical and Computer Engineering Wayne State University Detroit, MI 48202 ai4874@wayne.edu Loren
An Iterative Greedy Approach Using Geographical Destination Routing In WSN
 ISSN (Online) : 2319-8753 ISSN (Print) : 2347-6710 International Journal of Innovative Research in Science, Engineering and Technology Volume 3, Special Issue 3, March 2014 2014 International Conference
ISSN (Online) : 2319-8753 ISSN (Print) : 2347-6710 International Journal of Innovative Research in Science, Engineering and Technology Volume 3, Special Issue 3, March 2014 2014 International Conference
WSN Routing Protocols
 WSN Routing Protocols 1 Routing Challenges and Design Issues in WSNs 2 Overview The design of routing protocols in WSNs is influenced by many challenging factors. These factors must be overcome before
WSN Routing Protocols 1 Routing Challenges and Design Issues in WSNs 2 Overview The design of routing protocols in WSNs is influenced by many challenging factors. These factors must be overcome before
Hybrid gateway advertisement scheme for connecting mobile ad hoc networks to the Internet
 * gateway advertisement scheme for connecting mobile ad hoc networks to the Internet Jeongkeun Lee (), Dongkyun Kim (2), J.J.Garcia-Luna-Aceves (3), Yanghee Choi (), Jihyuk Choi (4), Sangwoo Nam (4) ()
* gateway advertisement scheme for connecting mobile ad hoc networks to the Internet Jeongkeun Lee (), Dongkyun Kim (2), J.J.Garcia-Luna-Aceves (3), Yanghee Choi (), Jihyuk Choi (4), Sangwoo Nam (4) ()
Geographic Adaptive Fidelity and Geographic Energy Aware Routing in Ad Hoc Routing
 309 Geographic Adaptive Fidelity and Geographic Energy Aware Routing in Ad Hoc Routing Sinchan Roychowdhury Instrumentation Control Engineering Calcutta Institute of Engineering & Management Kolkata, India
309 Geographic Adaptive Fidelity and Geographic Energy Aware Routing in Ad Hoc Routing Sinchan Roychowdhury Instrumentation Control Engineering Calcutta Institute of Engineering & Management Kolkata, India
Location Based Energy-Efficient Reliable Routing Protocol for Wireless Sensor Networks
 Location Based Energy-Efficient Reliable Routing Protocol for Wireless Sensor Networks RAFE ALASEM 1, AHMED REDA 2 AND MAHMUD MANSOUR 3 (1) Computer Science Department Imam Muhammad ibn Saud Islamic University
Location Based Energy-Efficient Reliable Routing Protocol for Wireless Sensor Networks RAFE ALASEM 1, AHMED REDA 2 AND MAHMUD MANSOUR 3 (1) Computer Science Department Imam Muhammad ibn Saud Islamic University
An Energy Efficiency Routing Algorithm of Wireless Sensor Network Based on Round Model. Zhang Ying-Hui
 Joint International Mechanical, Electronic and Information Technology Conference (JIMET 2015) An Energy Efficiency Routing Algorithm of Wireless Sensor Network Based on Round Model Zhang Ying-Hui Software
Joint International Mechanical, Electronic and Information Technology Conference (JIMET 2015) An Energy Efficiency Routing Algorithm of Wireless Sensor Network Based on Round Model Zhang Ying-Hui Software
CHAPTER 5 MULTICAST GEOGRAPHY BASED ROUTING IN AD HOC NETWORKS
 89 CHAPTER 5 MULTICAST GEOGRAPHY BASED ROUTING IN AD HOC NETWORKS 5.1 INTRODUCTION Efficient routing in MANET is a tough task due to their highly dynamic network topology, bandwidth controlled links and
89 CHAPTER 5 MULTICAST GEOGRAPHY BASED ROUTING IN AD HOC NETWORKS 5.1 INTRODUCTION Efficient routing in MANET is a tough task due to their highly dynamic network topology, bandwidth controlled links and
Example of TORA operations. From last time, this was the DAG that was built. A was the source and X was the destination.
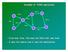 Example of TORA operations A Link 2 D Link 6 Y Link 1 Link 3 C Link 4 Link 8 B Link 5 E Link 7 X From last time, this was the DAG that was built. A was the source and X was the destination. Link 1 A B
Example of TORA operations A Link 2 D Link 6 Y Link 1 Link 3 C Link 4 Link 8 B Link 5 E Link 7 X From last time, this was the DAG that was built. A was the source and X was the destination. Link 1 A B
Reliable Time Synchronization Protocol for Wireless Sensor Networks
 Reliable Time Synchronization Protocol for Wireless Sensor Networks Soyoung Hwang and Yunju Baek Department of Computer Science and Engineering Pusan National University, Busan 69-735, South Korea {youngox,yunju}@pnu.edu
Reliable Time Synchronization Protocol for Wireless Sensor Networks Soyoung Hwang and Yunju Baek Department of Computer Science and Engineering Pusan National University, Busan 69-735, South Korea {youngox,yunju}@pnu.edu
OPTIMIZATION ALGORITHMS FOR INFORMATION RETRIEVAL AND TRANSMISSION IN DISTRIBUTED AD HOC NETWORKS. A Dissertation HONG LU
 OPTIMIZATION ALGORITHMS FOR INFORMATION RETRIEVAL AND TRANSMISSION IN DISTRIBUTED AD HOC NETWORKS A Dissertation by HONG LU Submitted to the Office of Graduate Studies of Texas A&M University in partial
OPTIMIZATION ALGORITHMS FOR INFORMATION RETRIEVAL AND TRANSMISSION IN DISTRIBUTED AD HOC NETWORKS A Dissertation by HONG LU Submitted to the Office of Graduate Studies of Texas A&M University in partial
Model and Algorithms for the Density, Coverage and Connectivity Control Problem in Flat WSNs
 Model and Algorithms for the Density, Coverage and Connectivity Control Problem in Flat WSNs Flávio V. C. Martins, cruzeiro@dcc.ufmg.br Frederico P. Quintão, fred@dcc.ufmg.br Fabíola G. Nakamura fgnaka@dcc.ufmg.br,fabiola@dcc.ufam.edu.br
Model and Algorithms for the Density, Coverage and Connectivity Control Problem in Flat WSNs Flávio V. C. Martins, cruzeiro@dcc.ufmg.br Frederico P. Quintão, fred@dcc.ufmg.br Fabíola G. Nakamura fgnaka@dcc.ufmg.br,fabiola@dcc.ufam.edu.br
Analysis of GPS and Zone Based Vehicular Routing on Urban City Roads
 Analysis of GPS and Zone Based Vehicular Routing on Urban City Roads Aye Zarchi Minn 1, May Zin Oo 2, Mazliza Othman 3 1,2 Department of Information Technology, Mandalay Technological University, Myanmar
Analysis of GPS and Zone Based Vehicular Routing on Urban City Roads Aye Zarchi Minn 1, May Zin Oo 2, Mazliza Othman 3 1,2 Department of Information Technology, Mandalay Technological University, Myanmar
Rendered Path: Range-Free Localization in Anisotropic Sensor Networks With Holes Mo Li, Member, IEEE, and Yunhao Liu, Senior Member, IEEE
 320 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 18, NO. 1, FEBRUARY 2010 Rendered Path: Range-Free Localization in Anisotropic Sensor Networks With Holes Mo Li, Member, IEEE, and Yunhao Liu, Senior Member,
320 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 18, NO. 1, FEBRUARY 2010 Rendered Path: Range-Free Localization in Anisotropic Sensor Networks With Holes Mo Li, Member, IEEE, and Yunhao Liu, Senior Member,
CompSci 356: Computer Network Architectures. Lecture 8: Spanning Tree Algorithm and Basic Internetworking Ch & 3.2. Xiaowei Yang
 CompSci 356: Computer Network Architectures Lecture 8: Spanning Tree Algorithm and Basic Internetworking Ch 3.1.5 & 3.2 Xiaowei Yang xwy@cs.duke.edu Review Past lectures Single link networks Point-to-point,
CompSci 356: Computer Network Architectures Lecture 8: Spanning Tree Algorithm and Basic Internetworking Ch 3.1.5 & 3.2 Xiaowei Yang xwy@cs.duke.edu Review Past lectures Single link networks Point-to-point,
Efficient load balancing and QoS-based location aware service discovery protocol for vehicular ad hoc networks
 RESEARCH Open Access Efficient load balancing and QoS-based location aware service discovery protocol for vehicular ad hoc networks Kaouther Abrougui 1,2*, Azzedine Boukerche 1,2 and Hussam Ramadan 3 Abstract
RESEARCH Open Access Efficient load balancing and QoS-based location aware service discovery protocol for vehicular ad hoc networks Kaouther Abrougui 1,2*, Azzedine Boukerche 1,2 and Hussam Ramadan 3 Abstract
Rumor Routing Algorithm
 Aleksi.Ahtiainen@hut.fi T-79.194 Seminar on Theoretical Computer Science Feb 9 2005 Contents Introduction The Algorithm Research Results Future Work Criticism Conclusions Introduction is described in paper:
Aleksi.Ahtiainen@hut.fi T-79.194 Seminar on Theoretical Computer Science Feb 9 2005 Contents Introduction The Algorithm Research Results Future Work Criticism Conclusions Introduction is described in paper:
Fig. 2: Architecture of sensor node
 Volume 4, Issue 11, November 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com To Reduce
Volume 4, Issue 11, November 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com To Reduce
An AIAD-Based Adaptive Routing Protocol in Ad-Hoc Wireless Networks
 An AIAD-Based Adaptive Routing Protocol in Ad-Hoc Wireless Networks Youn-Sik Hong 1 and Ki-Young Lee 2 1 Department of Computer Science and Eng. 2 Department of Information and Telecommunication Eng.,
An AIAD-Based Adaptive Routing Protocol in Ad-Hoc Wireless Networks Youn-Sik Hong 1 and Ki-Young Lee 2 1 Department of Computer Science and Eng. 2 Department of Information and Telecommunication Eng.,
ScienceDirect. Analogy between immune system and sensor replacement using mobile robots on wireless sensor networks
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 35 (2014 ) 1352 1359 18 th International Conference in Knowledge Based and Intelligent Information & Engineering Systems
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 35 (2014 ) 1352 1359 18 th International Conference in Knowledge Based and Intelligent Information & Engineering Systems
AN EFFICIENT MAC PROTOCOL FOR SUPPORTING QOS IN WIRELESS SENSOR NETWORKS
 AN EFFICIENT MAC PROTOCOL FOR SUPPORTING QOS IN WIRELESS SENSOR NETWORKS YINGHUI QIU School of Electrical and Electronic Engineering, North China Electric Power University, Beijing, 102206, China ABSTRACT
AN EFFICIENT MAC PROTOCOL FOR SUPPORTING QOS IN WIRELESS SENSOR NETWORKS YINGHUI QIU School of Electrical and Electronic Engineering, North China Electric Power University, Beijing, 102206, China ABSTRACT
The Impact of Clustering on the Average Path Length in Wireless Sensor Networks
 The Impact of Clustering on the Average Path Length in Wireless Sensor Networks Azrina Abd Aziz Y. Ahmet Şekercioğlu Department of Electrical and Computer Systems Engineering, Monash University, Australia
The Impact of Clustering on the Average Path Length in Wireless Sensor Networks Azrina Abd Aziz Y. Ahmet Şekercioğlu Department of Electrical and Computer Systems Engineering, Monash University, Australia
Sensor Network Protocols
 EE360: Lecture 15 Outline Sensor Network Protocols Announcements 2nd paper summary due March 7 Reschedule Wed lecture: 11-12:15? 12-1:15? 5-6:15? Project poster session March 15 5:30pm? Next HW posted
EE360: Lecture 15 Outline Sensor Network Protocols Announcements 2nd paper summary due March 7 Reschedule Wed lecture: 11-12:15? 12-1:15? 5-6:15? Project poster session March 15 5:30pm? Next HW posted
Geographic Routing in Simulation: GPSR
 Geographic Routing in Simulation: GPSR Brad Karp UCL Computer Science CS M038/GZ06 23 rd January 2013 Context: Ad hoc Routing Early 90s: availability of off-the-shelf wireless network cards and laptops
Geographic Routing in Simulation: GPSR Brad Karp UCL Computer Science CS M038/GZ06 23 rd January 2013 Context: Ad hoc Routing Early 90s: availability of off-the-shelf wireless network cards and laptops
Research on Relative Coordinate Localization of Nodes Based on Topology Control
 Journal of Information Hiding and Multimedia Signal Processing c 2018 ISSN 2073-4212 Ubiquitous International Volume 9, Number 2, March 2018 Research on Relative Coordinate Localization of Nodes Based
Journal of Information Hiding and Multimedia Signal Processing c 2018 ISSN 2073-4212 Ubiquitous International Volume 9, Number 2, March 2018 Research on Relative Coordinate Localization of Nodes Based
ROUTING ALGORITHMS Part 1: Data centric and hierarchical protocols
 ROUTING ALGORITHMS Part 1: Data centric and hierarchical protocols 1 Why can t we use conventional routing algorithms here?? A sensor node does not have an identity (address) Content based and data centric
ROUTING ALGORITHMS Part 1: Data centric and hierarchical protocols 1 Why can t we use conventional routing algorithms here?? A sensor node does not have an identity (address) Content based and data centric
Distributed load balancing mechanism for detouring schemes of geographic routing in wireless sensor networks
 International Journal of Parallel, Emergent and Distributed Systems, 213 Vol. 28, No. 2, 184 197, http://dx.doi.org/1.18/1744576.212.66151 Distributed load balancing mechanism for detouring schemes of
International Journal of Parallel, Emergent and Distributed Systems, 213 Vol. 28, No. 2, 184 197, http://dx.doi.org/1.18/1744576.212.66151 Distributed load balancing mechanism for detouring schemes of
Data Communication. Guaranteed Delivery Based on Memorization
 Data Communication Guaranteed Delivery Based on Memorization Motivation Many greedy routing schemes perform well in dense networks Greedy routing has a small communication overhead Desirable to run Greedy
Data Communication Guaranteed Delivery Based on Memorization Motivation Many greedy routing schemes perform well in dense networks Greedy routing has a small communication overhead Desirable to run Greedy
A Logical Group Formation and Management Mechanism Using RSSI for Wireless Sensor Networks *
 A Logical Group Formation and Management Mechanism Using RSSI for Wireless Sensor Networks * Jihyuk Heo, Jin Ho Kim, and Choong Seon Hong ** Department of Computer Engineering, Kyung Hee University, Sochen-ri,
A Logical Group Formation and Management Mechanism Using RSSI for Wireless Sensor Networks * Jihyuk Heo, Jin Ho Kim, and Choong Seon Hong ** Department of Computer Engineering, Kyung Hee University, Sochen-ri,
sensors ISSN Article
 Sensors 2009, 9, 8047-8072; doi:10.3390/s91008047 OPEN ACCESS sensors ISSN 1424-8220 www.mdpi.com/journal/sensors Article A Radio-Aware Routing Algorithm for Reliable Directed Diffusion in Lossy Wireless
Sensors 2009, 9, 8047-8072; doi:10.3390/s91008047 OPEN ACCESS sensors ISSN 1424-8220 www.mdpi.com/journal/sensors Article A Radio-Aware Routing Algorithm for Reliable Directed Diffusion in Lossy Wireless
A Real-Time Directed Routing Protocol Based on Projection of Convex Holes on Underwater Acoustic Networks
 I.J. Wireless and Microwave Technologies, 01,, 65-73 Published Online April 01 in MECS (http://www.mecs-press.net) DOI: 10.5815/ijwmt.01.0.10 Available online at http://www.mecs-press.net/ijwmt A Real-Time
I.J. Wireless and Microwave Technologies, 01,, 65-73 Published Online April 01 in MECS (http://www.mecs-press.net) DOI: 10.5815/ijwmt.01.0.10 Available online at http://www.mecs-press.net/ijwmt A Real-Time
ViTAMin: A Virtual Backbone Tree Algorithm for Minimal Energy Consumption in Wireless Sensor Network Routing
 ViTAMin: A Virtual Backbone Tree Algorithm for Minimal Energy Consumption in Wireless Sensor Network Routing Jaekwang Kim Department of Electrical and Computer Engineering, Sungkyunkwan University, Suwon,
ViTAMin: A Virtual Backbone Tree Algorithm for Minimal Energy Consumption in Wireless Sensor Network Routing Jaekwang Kim Department of Electrical and Computer Engineering, Sungkyunkwan University, Suwon,
PROJECT REPORT VIRTUAL COORDINATE GENERATOR AND ROUTING SIMULATION TOOL FOR WIRELESS SENSOR NETWORKS IN 2 AND 3-DIMENSIONAL NETWORK SPACE
 PROJECT REPORT VIRTUAL COORDINATE GENERATOR AND ROUTING SIMULATION TOOL FOR WIRELESS SENSOR NETWORKS IN 2 AND 3-DIMENSIONAL NETWORK SPACE Submitted by Aravindhan Vijayaraj Department of Electrical and
PROJECT REPORT VIRTUAL COORDINATE GENERATOR AND ROUTING SIMULATION TOOL FOR WIRELESS SENSOR NETWORKS IN 2 AND 3-DIMENSIONAL NETWORK SPACE Submitted by Aravindhan Vijayaraj Department of Electrical and
SIPCache: A Distributed SIP Location Service for Mobile Ad-Hoc Networks
 SIPCache: A Distributed SIP Location Service for Mobile Ad-Hoc Networks Simone Leggio Hugo Miranda Kimmo Raatikainen Luís Rodrigues University of Helsinki University of Lisbon August 16, 2006 Abstract
SIPCache: A Distributed SIP Location Service for Mobile Ad-Hoc Networks Simone Leggio Hugo Miranda Kimmo Raatikainen Luís Rodrigues University of Helsinki University of Lisbon August 16, 2006 Abstract
Hierarchical Low Power Consumption Technique with Location Information for Sensor Networks
 Hierarchical Low Power Consumption Technique with Location Information for Sensor Networks Susumu Matsumae Graduate School of Science and Engineering Saga University Saga 840-8502, Japan Fukuhito Ooshita
Hierarchical Low Power Consumption Technique with Location Information for Sensor Networks Susumu Matsumae Graduate School of Science and Engineering Saga University Saga 840-8502, Japan Fukuhito Ooshita
Efficient Broadcasting in Ad Hoc Wireless Networks Using Directional Antennas
 Efficient Broadcasting in Ad Hoc Wireless Networks Using Directional Antennas Fei Dai Department of Electrical and Computer Engineering North Dakota State University Fargo, ND 5805 Email: fdai@ece.ndsu.edu
Efficient Broadcasting in Ad Hoc Wireless Networks Using Directional Antennas Fei Dai Department of Electrical and Computer Engineering North Dakota State University Fargo, ND 5805 Email: fdai@ece.ndsu.edu
Context-aware Geographic Routing for Sensor Networks with Routing Holes
 Context-aware Geographic Routing for Sensor Networks with Routing Holes Jiaxi You, ominik Lieckfeldt, Frank Reichenbach, and irk Timmermann University of Rostock, Germany {jiaxi.you, dominik.lieckfeldt,
Context-aware Geographic Routing for Sensor Networks with Routing Holes Jiaxi You, ominik Lieckfeldt, Frank Reichenbach, and irk Timmermann University of Rostock, Germany {jiaxi.you, dominik.lieckfeldt,
Wireless Sensor Networks Localization Methods: Multidimensional Scaling vs. Semidefinite Programming Approach
 Wireless Sensor Networks Localization Methods: Multidimensional Scaling vs. Semidefinite Programming Approach Biljana Stojkoska, Ilinka Ivanoska, Danco Davcev, 1 Faculty of Electrical Engineering and Information
Wireless Sensor Networks Localization Methods: Multidimensional Scaling vs. Semidefinite Programming Approach Biljana Stojkoska, Ilinka Ivanoska, Danco Davcev, 1 Faculty of Electrical Engineering and Information
Experiment and Evaluation of a Mobile Ad Hoc Network with AODV Routing Protocol
 Experiment and Evaluation of a Mobile Ad Hoc Network with AODV Routing Protocol Kalyan Kalepu, Shiv Mehra and Chansu Yu, Department of Electrical and Computer Engineering Cleveland State University 2121
Experiment and Evaluation of a Mobile Ad Hoc Network with AODV Routing Protocol Kalyan Kalepu, Shiv Mehra and Chansu Yu, Department of Electrical and Computer Engineering Cleveland State University 2121
SLALoM: A Scalable Location Management Scheme for Large Mobile Ad-hoc Networks
 SLALoM A Scalable Location Management Scheme for Large Mobile Ad-hoc Networks Christine T. Cheng *, Howard L. Lemberg, Sumesh J. Philip, Eric van den Berg and Tao Zhang * Institute for Math & its Applications,
SLALoM A Scalable Location Management Scheme for Large Mobile Ad-hoc Networks Christine T. Cheng *, Howard L. Lemberg, Sumesh J. Philip, Eric van den Berg and Tao Zhang * Institute for Math & its Applications,
R2D2: Rendezvous Regions for Data Discovery Karim Seada 1, Ahmed Helmy 2
 R2D2: Rendezvous Regions for Data Discovery Karim Seada 1, Ahmed Helmy 2 1 Nokia Research Center, Palo Alto 2 Computer and Information Science and Engineering Department, University of Florida, Gainesville
R2D2: Rendezvous Regions for Data Discovery Karim Seada 1, Ahmed Helmy 2 1 Nokia Research Center, Palo Alto 2 Computer and Information Science and Engineering Department, University of Florida, Gainesville
Performance Evaluation of Routing Protocols in Wireless Mesh Networks. Motlhame Edwin Sejake, Zenzo Polite Ncube and Naison Gasela
 Performance Evaluation of Routing Protocols in Wireless Mesh Networks Motlhame Edwin Sejake, Zenzo Polite Ncube and Naison Gasela Department of Computer Science, North West University, Mafikeng Campus,
Performance Evaluation of Routing Protocols in Wireless Mesh Networks Motlhame Edwin Sejake, Zenzo Polite Ncube and Naison Gasela Department of Computer Science, North West University, Mafikeng Campus,
Efficient Hybrid Multicast Routing Protocol for Ad-Hoc Wireless Networks
 Efficient Hybrid Multicast Routing Protocol for Ad-Hoc Wireless Networks Jayanta Biswas and Mukti Barai and S. K. Nandy CAD Lab, Indian Institute of Science Bangalore, 56, India {jayanta@cadl, mbarai@cadl,
Efficient Hybrid Multicast Routing Protocol for Ad-Hoc Wireless Networks Jayanta Biswas and Mukti Barai and S. K. Nandy CAD Lab, Indian Institute of Science Bangalore, 56, India {jayanta@cadl, mbarai@cadl,
M-Geocast: Robust and Energy-Efficient Geometric Routing for Mobile Sensor Networks
 M-Geocast: Robust and Energy-Efficient Geometric Routing for Mobile Sensor Networks Lynn Choi 1, Jae Kyun Jung 1, Byong-Ha Cho 1, and Hyohyun Choi 2 1 Korea University, Anam-Dong, Sungbuk-Ku, Seoul, Korea
M-Geocast: Robust and Energy-Efficient Geometric Routing for Mobile Sensor Networks Lynn Choi 1, Jae Kyun Jung 1, Byong-Ha Cho 1, and Hyohyun Choi 2 1 Korea University, Anam-Dong, Sungbuk-Ku, Seoul, Korea
UAMAC: Unidirectional-Link Aware MAC Protocol for Heterogeneous Ad Hoc Networks
 UAMAC: Unidirectional-Link Aware MAC Protocol for Heterogeneous Ad Hoc Networks Sung-Hee Lee, Jong-Mu Choi, and Young-Bae Ko College of Information and Communication, Ajou University, South Korea shlee@dmc.ajou.ac.kr,
UAMAC: Unidirectional-Link Aware MAC Protocol for Heterogeneous Ad Hoc Networks Sung-Hee Lee, Jong-Mu Choi, and Young-Bae Ko College of Information and Communication, Ajou University, South Korea shlee@dmc.ajou.ac.kr,
Analysis of Multiple Trees on Path Discovery for Beacon-Based Routing Protocols
 Analysis of Multiple Trees on Path Discovery for Beacon-Based Routing Protocols Baruch Awerbuch, David Holmer and Herbert Rubens Johns Hopkins University Department of Computer Science Baltimore, MD, USA
Analysis of Multiple Trees on Path Discovery for Beacon-Based Routing Protocols Baruch Awerbuch, David Holmer and Herbert Rubens Johns Hopkins University Department of Computer Science Baltimore, MD, USA
Blackhole Attack Detection in Wireless Sensor Networks Using Support Vector Machine
 International Journal of Wireless Communications, Networking and Mobile Computing 2016; 3(5): 48-52 http://www.aascit.org/journal/wcnmc ISSN: 2381-1137 (Print); ISSN: 2381-1145 (Online) Blackhole Attack
International Journal of Wireless Communications, Networking and Mobile Computing 2016; 3(5): 48-52 http://www.aascit.org/journal/wcnmc ISSN: 2381-1137 (Print); ISSN: 2381-1145 (Online) Blackhole Attack
Topology Control in Wireless Networks 4/24/06
 Topology Control in Wireless Networks 4/4/06 1 Topology control Choose the transmission power of the nodes so as to satisfy some properties Connectivity Minimize power consumption, etc. Last class Percolation:
Topology Control in Wireless Networks 4/4/06 1 Topology control Choose the transmission power of the nodes so as to satisfy some properties Connectivity Minimize power consumption, etc. Last class Percolation:
Investigation on OLSR Routing Protocol Efficiency
 Investigation on OLSR Routing Protocol Efficiency JIRI HOSEK 1, KAROL MOLNAR 2 Department of Telecommunications Faculty of Electrical Engineering and Communication, Brno University of Technology Purkynova
Investigation on OLSR Routing Protocol Efficiency JIRI HOSEK 1, KAROL MOLNAR 2 Department of Telecommunications Faculty of Electrical Engineering and Communication, Brno University of Technology Purkynova
