Ad hoc Network Routing Wireless Systems, a.a 2015/2016
|
|
|
- Derrick McCoy
- 6 years ago
- Views:
Transcription
1 Ad hoc Network Routing Wireless Systems, a.a 2015/2016 Un. of Rome La Sapienza Chiara Petrioli Department of Computer Science University of Rome Sapienza Italy
2 Why traditional approaches have limits? Proactive protocols are costly in terms of overhead (the bandwidth and energy are critical resources) The cost of maintaining routes updated may not make sense in an environment in which Medium-high mobility Medium-high dynamicity (awake/asleep states) Motivate frequent changes in the the optimum route (requiring updates) while Traffic is generally low (so the cost of maintaining always updated routes is not balanced by their use) If this is the scenario what can we do? 2
3 2 Primary Approaches (cont.) Reactive (on-demand) Source build routes on-demand by flooding Maintain only active routes Route discovery cycle Typically, less control overhead, better scaling properties Drawback: route acquisition latency Example: AODV, DSR 3
4 Ad hoc On-Demand Distance Vector Routing AODV: Reactive (nodes that do not lie on active paths neither maintain any routing information nor participate in any periodic routing table exchange; a node does not have to discover/maintain a route to a destination till it is on a path to it or has to send messages to it) Route discovery cycle used for route finding Maintenance of active routes Sequence numbers used for loop prevention and as route freshness criteria Descendant of DSDV (standard distance vector approach mapped to ad hoc networks), in AODV no periodic updates but pure on-demand operation. Provides unicast and multicast communication 4
5 AODV: Route Discovery S A B C 1. Node S needs a route to D AND does not have routing info for it in its table D 5
6 AODV: Route Discovery B S 1. Node S needs a route to D 2. Creates a Route Request (RREQ) Enters D s IP addr, seq#, A S s IP addr, seq# C hopcount (=0), broadcast ID D 6
7 AODV: Route Discovery S RREQ A 1. Node S needs a route to D 2. Creates a Route Request (RREQ) Enters D s IP addr, seq#, S s IP addr, seq# hopcount (=0), broadcast ID 3. Node S broadcasts RREQ to neighbors B C D 7
8 AODV: Route Discovery S RREQ A B C 4. Node A receives RREQ Makes reverse route entry for S dest=s, nexthop=s, hopcnt=1,expiration time for reverse path Source node, Source node SN,D,broadcastID also maintained It has no route to D, so it rebroadcasts RREQ (hopcount increased) If it has already received that request (same source and broadcast ID) it discards the RREQ if it knows a valid path to D it will send back a reply to the source D 8
9 AODV: Route Discovery RREQ B S 4. Node A receives RREQ Makes reverse route entry for S dest=s, nexthop=s, hopcnt=1 A It has no route to D, so it rebroadcasts RREQ C D 9
10 AODV: Route Discovery RREQ B S 5. Node C receives RREQ Makes reverse route entry for S dest=s, nexthop=a, hopcnt=2 A C It has a route to D, and the seq# for route to D is >= D s seq# in RREQ D 10
11 AODV: Route Discovery S RREQ A B C 5. Node C receives RREQ (cont.) C creates a Route Reply (RREP) Enters D s IP addr, seq# S s IP addr, hopcount to D (= 1), lifetime of the forward route Unicasts RREP to A D 11
12 AODV: Route Discovery S 5. Node C receives RREQ (cont.) C creates a Route Reply (RREP) Enters D s IP addr, seq# A S s IP addr, hopcount to D (= 1). Unicasts RREP to A B RREP C D 12
13 AODV: Route Discovery S RREP A 6. Node A receives RREP Makes forward route entry to D dest = D, nexthop = C, hopcount = 2 Unicasts RREP to S B RREP C D 13
14 AODV: Route Discovery S RREP 7. Node S receives RREP Makes forward route entry to D dest = D, nexthop = A, hopcount = 3 A B C D Also the latest SN of the destination is updated when receiving the RREP Nodes not along the path determined by the RREP will timeout after ACTIVE_ROUTE_TIMEOUT (3000ms) and will delete the reverse pointer 14
15 AODV: Route Discovery B S A 7. Node S receives RREP Makes forward route entry to D dest = D, nexthop = A, hopcount = 3 Sends data packets on route to D C D 15
16 What if. A node receives further RREPs for the same request? (e.g. more neighbors of a node had paths to the destination in cache)? upon reception of another RREP the node updates its routing information and propagates the RREP only if the RREP contains either a greater destination SN, or the same destination SN with a smaller hopcount 16
17 Other info maintained Each node maintains the list of active neighbors, neighbors sending to a given destination through it useful for route maintenance Routing table entries: dest,next hop, hopcount, dest SN, active neighbors for this route, expiration time for route table entry (updates each time the route is used for transmitting data à routes entries are maintained if the route is active) 17
18 AODV: Route Maintenance S A 1. Link between C and D breaks 2. Node C invalidates route to D in route table 3. Node C creates Route Error (RERR) message Lists all destinations which are now unreachable Sends to upstream neighbors Increases of one the SN of the destination B RERR C D 18
19 AODV: Route Maintenance S RERR A 4. Node A receives RERR Checks whether C is its next hop on route to D Deletes route to D Forwards RERR to S B RERR C D 19
20 AODV: Route Maintenance S RERR A 5. Node S receives RERR Checks whether A is its next hop on route to D Deletes route to D B C Rediscovers route if still needed (in that case it sends a RREQ with a SN which is equal to the last known destination Sequence Number +1) D 20
21 AODV: Optimizations Expanding Ring Search Prevents flooding of network during route discovery Control Time To Live (TTL) of RREQ to search incrementally larger areas of network Advantage: Less overhead when successful Disadvantage: Longer delay if route not found immediately 21
22 AODV: Optimizations (cont.) Local Repair Repair breaks in active routes locally instead of notifying source Use small TTL because destination probably hasn t moved far If first repair attempt is unsuccessful, send RERR to source Advantage: repair links with less overhead, delay and packet loss Disadvantage: longer delay and greater packet loss when unsuccessful 22
23 AODV: Summary Reactive/on-demand Sequence numbers used for route freshness and loop prevention Route discovery cycle Maintain only active routes Optimizations can be used to reduce overhead and increase scalability 23
24 Dynamic Source Routing (DSR) Reactive Route discovery cycle used for route finding Maintenance of active routes Utilizes source routing 24
25 DSR: Route Discovery S RREQ: S A B C D 1. Node S needs a route to D 2. Broadcasts RREQ packet 1. RREQ identifies the target of the route discovery, contains a route record in which the traversed route is accumulated, contains a pair <initiator, request id> uniquely identifying the request 25
26 DSR: Route Discovery S RREQ: S A B C D 1. Node S needs a route to D 2. Broadcasts RREQ packet 3. Node A receives packet, has no route to D AND is NOT D Rebroadcasts packet after adding its address to source route 26
27 DSR: Route Discovery RREQ: S, A B S A C D 1. Node S needs a route to D 2. Broadcasts RREQ packet 3. Node A receives packet, has no route to D Rebroadcasts packet after adding its address to source route 27
28 DSR: Route Discovery S RREQ: S, A A B C D 4. Node C receives RREQ, has no route to D Rebroadcasts packet after adding its address to source route 28
29 DSR: Route Discovery B S A RREQ: S, A, C C D 4. Node C receives RREQ, has no route to D Rebroadcasts packet after adding its address to source route 29
30 DSR: Route Discovery B S A RREQ: S, A, C C D 4. Node C receives RREQ, has no route to D Rebroadcasts packet after adding its address to source route 5. Node D receives RREQ, unicasts RREP to C Puts source route accumulated in RREQ into RREP 30
31 DSR: Route Discovery B S A C RREP: S, A, C, D D 4. Node C receives RREQ, has no route to D Rebroadcasts packet after adding its address to source route 5. Node D receives RREQ, unicasts RREP to C Puts source route accumulated in RREQ into RREP 31
32 DSR: Route Discovery B S A RREP: S, A, C, D C D 6. Node C receives RREP Unicasts to A 32
33 DSR: Route Discovery RREP: S, A, C, D S 6. Node A receives RREP Unicasts to S A B C D 33
34 DSR: Route Discovery RREP: S, A, C, D S A B C D 8. Node S receives RREP Uses route for data packet transmissions 34
35 General node operation upon receiving RREQ If the pair <initiator address, request ID> has recently been seen, DISCARD If the node ID is already listed in the source route DISCARDà avoids loops If I m the destination, send a RREP Otrherwise, append my ID in the source route and rebroadcast (orange cases already seen in the previous slides) 35
36 Route maintenance The two endpoints of a failed link are transmitted to the source in a route error packet Upon a receiving a RERR packet a node invalidates all the routes going through that link If the route is invalidated and it is needed, a new route must be discovered 36
37 Optimizations (1) Extensive use of caching (caching source routes means that I already know all the route to intermediate destinations; discovery of a better route to an intermediate destination also brings me to improve the route to the final destination). Transmitting packets or sending back replies make me learn routes. A node that knows a route to a given destination (has a source route in cache) can immediately answer a RREQ Broadcast storm? Each nodes waits for a time which is C*(h-1+r), r random in (0,1), h length of the route I m advertising. Only if I haven t received other routes listen to other routes tx in the meanwhile-i transmit mine. 37
38 Optimization (2) Operation in promiscuous mode (I keep discovering new routes by transmission of routes by my neighbours) RREQ overhead minimization: first set a TTL=1, if I do not get answer I set it to infinity Path shortening: if Y receives a packet by node X but in the source route we have X, B,,C,Y, Y signals the path can be shortened (unsolicited RREP) What if the network is disconnected? Exponential back-off to decrease the quantity of RREQ sent 38
39 AODV and DSR Differences DSR uses source routing; AODV uses next hop entry DSR uses route cache; AODV uses route table DSR route cache entries do not have lifetimes; AODV route table entries do have lifetimes 39
40 Proactive Solutions: Drawbacks Updates overhead, especially in presence of high mobility Overhead for enforcing loop freedom Large routing tables Low scalability Ø Is it really necessary to maintain a consistent view of the network topology? 40
41 Reactive Protocols: Drawbacks The discovery phase introduces long delays Route discovery and maintenance is very sensitive to node mobility Route caching is memory greedy The size of the header of a data packet can become cumbersome in approaches such as DSR (no scalability) Operating in promiscuous mode is energy-consuming. Relying on flooding based route discovery is resource consuming. Ø Is the dependency on the network topology avoidable? 41
42 Geographically-Enabled Routing Outline Problems with proactive approaches Problems with reactive approaches A new way of naming\locating the destination node: geographic routing Two seminal protocols ü DREAM & LAR Geo-enable routing costs: I need to know where I am, where the destination is. 42
43 Location-Enabled Ad Hoc Routing Nodes are equipped with positioning system devices (e.g., Global Positioning System receivers) that make them aware of their position This enables directional routing Possible solutions differ on how the location information of the destination nodes is achieved 43
44 Strengths No need to update big routing tables, no need to piggyback routes to the packet Destination position must be known at the source. No need to know the nodes on the way to the destination: they can be moving while the packet travels 44
45 Drawbacks Needs extra hardware Depends on the extra hardware limitation (and resource requirements) Scalability is an issue (indeed the problem here translates to how to maintain correct estimates of the nodes positions) 45
46 Location-Aided Routing (LAR) Exploits location information to limit scope of RREQ flood Expected Zone: region that is expected to hold the current location of the destination Expected region determined based on potentially old location information, and knowledge of the destination s speed RREQs limited to a Request Zone that contains the Expected Zone and location of the sender node 46
47 LAR: Expected Zone D = last known location of node D, at time t 0 D' = location of node D at current time t 1, unknown to node S r = (t 1 t 0 ) * estimate of D s speed r D D' Expected Zone 47
48 LAR-1 The request zone is the smallest rectangle that includes the current location of the source and the expected zone Only nodes within the request zone forward route requests Node A does not forward RREQ, but node B does Request zone explicitly specified in the RREQ Each node must know its physical location to determine whether it is within the request zone 48
49 LAR, Possible Failures If route discovery using the smaller request zone fails to find a route, the sender initiates another route discovery (after a timeout) using a larger request zone The larger request zone may be the entire network Rest of route discovery protocol similar to DSR The directional flooding approach proposed in the paper is used to reach the destination with a limited overhead wrt traditional flooding Destination then answers with a route reply packets This allows the source to compute based on tradictional reactive protocols approaches the route towards the destination 49
50 LAR, the Routing The basic proposal assumes that, initially, location information for node X becomes known to Y only during a route discovery This location information is used for a future route discovery according to the paradigm explained before Updates on the node position are piggybacked in the route reply message à This allows to reduce overhead associated to route discovery process provided that the time between two route discovery is not too much Destination may also proactively distribute its location information But in this case the control traffic for geographic information updates could be high ü How to solve this issue? Later (DREAM) 50
51 LAR - 2 Each protocol relies RREQ if it is closer to the destination than the source (greedy forwarding) 51
52 DREAM Distance routing effect algorithm for mobility [Basagni+, 1998] A proactive, effective way to spread location information Directional routing 52
53 DREAM: Directional Routing Source S determines the location of destination D at time t0 based on its location table Based on the current time t1 and t0 S determines the area in which D can be found (hence, D s direction) S transmits the data packet to all its neighbors in D s direction Each neighbor does the same till D is reached 53
54 DREAM: Routing a Data Packet 54
55 Disseminating Location Information: Problems Need to periodically update the location of a moving node. Efficient broadcast of location information Determining how far each location packet should travel Determining how often a location packet should be sent 55
56 Disseminating Location Information: Solutions Distance effect Rate of updates is bound to the mobility of the node 56
57 The Distance Effect Closer nodes look like they are moving faster Need to receive more location updates from closer node Each location update packet is associated with an age that determines how far that packet must travel 57
58 DREAM: Rate of updates Triggered by the mobility of the nodes The faster the node the more updates it sends A plus: slow moving nodes impose little overhead 58
59 DREAM, Strengths First of its kind: after that, the deluge! Robustness: multiple routes to the destination directional flooding DREAM, Weaknesses It is flooding, although only directional It is not that scalable, geographic info updates have to be periodically transmitted (even if mechanisms to limit such overhead are enforced) 59
60 In a sensor network we seek.. For solutions which scale Which are energy saving Which are well integrated with awake/asleep schedules Which do not require to maintain routing tables Which are simple Solutions such as AODV and DSR have been proven to work well iff they exploit intensively caching and promiscuous mode operation (energy inefficientß work by L. Feeney et al, 2001) and have been shown not to scale to the volumes of nodes expected in sensor networks (work by E. Belding Royer and S.J. Lee) What can we use? communication sensors sink Info such as localization and some level of synchronization often needed by the application (if I sense an event I have to say WHERE and WHEN it occurred, otherwise the information is not very interesting) 60
61 Integrates geographic routing awake/asleep schedule MAC An example: GeRaF How do nodes alternate between awake and asleep states? According to a duty cycle (time ON/time ON+ OFF) ON OFF 61 ON OFF
62 GeRaF basic idea Geographic routing: each node needs to know its location, the destination (sink) location, and the location of whom is transmitting (communicated in the packet) Greedy approach: tries to select relays so to advance as much as possible toward the destination at each hop 62
63 GeRaF: operations Main problem to be solved: how to make a contention-based scheme/routing work in the presence of sleep modes Flat solution Integrated MAC/routing/awake-asleep but awake-asleep schedule and routing decoupled à each node does not know its neighbor and their schedules à low overhead Tightly integrated with the routing layer (no clear separation really) Without requiring routing tables/routing table updates Based on the knowledge of the nodes location and on the knowledge of the sink location 63
64 Example of GeRaF operation RTS invites all awake neighbors to become a relay Nodes in best position should win Nodes within tx range are divided in areas depending on how close they are to the final destination (the closest the better as relay) Need of location awareness 64
65 GeraF operation Node i sends RTS with the identity of the area it is polling now (starting from the closer to the sink, among the slices in which its tx range has been divided) Each node, upon receiving the RTS, decides whether it belongs to the polled area or not (based on location info) Only nodes in the polled area answer with a CTS No node answers à node i polls next area (no node available for forwarding in the area-there are no nodes or they are sleeping) One answer, CTS correctly received, send DATA Multiple answer COLLISION, sender sends a collision packet, MAC needed to solve collision (next slide) 65
66 GeraF operation (how to handle collision) 1)A node receiving a collision packet tosses a coin and with probability p transmits a CTS iff it was participating to the previous phase (it had previously sent a CTS resulting in collision) if only one node answers node i sends data If no node answers node i asks these nodes to toss a coin again.. if more nodes answer COLLISION. Collision packet is sent. GO TO 1) (only the nodes which have lead to collision survive to the next phase) 66
67 What If All areas are polled unsuccessfully? Try again after some time (exponential backoff) Can I always reach the destination in this way? 67
68 What if (answer) No. Here is An example Tx radius sink Solutions? (mechanisms have to be added to recognize the problem, do backtracking and try another route) 68
69 How to solve dead-ends A problem only at low density We can set a maximum number of attempts to find a relay. When a node fails to find a relay it starts decreasing its duty cycle/or the probability to propose itself as relay over time nodes along paths to dead-ends are less and less selected as next hop relays and other paths able to bring to the destination are instead found Still..we may have problems Tx radius sink 69
70 GeRaf performance Casari, Marcucci,Nati, Petrioli, Zorzi IEEE MILCOM 2005 square area 320m x 320m Transmission range=40m randomly deployed nodes (avg degree 5-50) Duty cycle =0.01,0.1,0.5 Comparable costs for tx/rx/idle Poisson packet arrival Channel data rate 38Kbps 70
71 GeRaf performance, d=0.1 Casari, Marcucci,Nati, Petrioli, Zorzi IEEE MILCOM
72 GeRaf performance, d=0.1 Casari, Marcucci,Nati, Petrioli, Zorzi IEEE MILCOM 2005 Backtracking in case of dead ends packet delivery ratio increases. When N= % of packets are correctly delivered. Problem is instead not solved when N=100. Solution to the problem provided by ALBA-R (or better by the R RAINBOW scheme of ALBA). 72
73 Localization in sensor networks Thanks to Prof. Mani Srivastava These slides have been derived From his tutorial on sensor networks Given at Rome Un. On July 2003
74 Localization Useful info Helps with some protocols (e.g. GeraF) Needed for being able to identify where events occur Why not just GPS (Global Positioning System) at every node? High power consumption Works only when LOS to satellites (not in indoor, heavy foliage ) Over kill often only relative position is needed (e.g. enough to know that relative to a coordinate system centered in the sink the event occurred in a position (x,y). Starting from relative info if some nodes have global coordinates global coordinates of events can be inferred. 74
75 Localization Basic step is to evaluate distance between two nodes (ranging). Different techniques depending on the available HW: AoA (e.g. directional antennas) RSS ToA Range free approaches (number of hops between nodes used to estimate the distance between them without using any extra HW) 75
76 Techniques for Location Sensing (AoA) Measure direction of landmarks Simple geometric relationships can be used to determine the location by finding the intersections of the lines-of-position e.g. Radiolocation based on angle of arrival (AoA) measurements of beacon nodes (e.g. base stations) ü can be done using directive antennas + a compass ü need at least two measurements BS φ 1 φ 2 BS MS φ 3 BS 76
77 Techniques for Location Sensing (RSS or ToA) Measure distance to landmarks, or Ranging e.g. Radiolocation using signal-strength or time-of-flight ü also done with optical and acoustic signals Distance via received signal strength ü use a mathematical model that describes the path loss attenuation with distance each measurement gives a circle on which the MS must lie ü use pre-measured signal strength contours around fixed basestation (beacon) nodes can combat shadowing location obtained by overlaying contours for each BS Distance via Time-of-arrival (ToA) ü distance measured by the propagation time distance = time * c ü each measurement gives a circle on which the MS must lie ü active vs. passive active: receiver sends a signal that is bounced back so that the receiver knows the round-trip time passive: receiver and transmitter are separate» time of signal transmission needs to be known N+1 BSs give N+1 distance measurements to locate in N dimensions 77
78 Radiolocation via ToA and RSSI x 2 BS d 2 x 1 BS But what if the circles do not intersect due to measurement errors (e.g. due to fading etc.)? à will have to identify the best guess given errors 78 d 1 MS BS x 3 d3
79 Location in 3D 79
80 Location in 3D 80
81 Location in 3D 81
82 A possible solution: Absolute Localization Unkown Location Beacon Beacon nodes Randomly Deployed Sensor Network A small fraction of the nodes is aware of their locations Rest need to collaborate to estimate their locations 82
83 Atomic Multilateration Nodes with at least three Neighbors aware of their Location can estimate their position (triangolarization) xˆ f, ˆ ˆ - initial position estimate for node u 2 2 u, i = ru, i ( xi xu ) + ( yi yu ) yˆ ( u u ) 1 2 r u,1 r u,2 Our objective function is: u r u, F( xu, yu ) = min fu, i 3 Beacon node with known location In case of errors metric is root mean square error
84 Iterative Multilateration Nodes that estimate their locations can become beacons and help other nodes discover their locations. Some observations: Can work for small networks, if ranging is accurate Energy efficient Still requires quite a lot of initial beacons Suffers from error accumulation Bad geometry yields bad results => unpredictable performance Still a useful primitive for Distributed Collaborative Multilateration First simple approach, many solutions in the literature Ref: based on slides by Andreas 84 Savvides
85 Range free localization Does not use ranging But only information available (e.g., discovered during routing protocols operation) 85
86 How does it work? Anchors know their position according to a common coordinate system X1,Y1 X2,Y2 X3,Y3 86
87 How it works All nodes compute shortest path between them and anchors Also anchors compute their rela5ve distance in hops X1,Y1 X2,Y2 X3,Y3 87
88 How it works Anchor A: I know my position, the position of the other anchors, our distance in hops à I can therefore estimate the average length of a one hop. This information is used to estimate distances D(x,y), where x is a node and y is one of the anchors. Based on such estimated distances and on the position of the anchor nodes each node computes its own position by exploiting triangolarization. Pro: No extra HW Cons: Not very accurate 88
Routing in Ad Hoc Wireless Networks PROF. MICHAEL TSAI / DR. KATE LIN 2014/05/14
 Routing in Ad Hoc Wireless Networks PROF. MICHAEL TSAI / DR. KATE LIN 2014/05/14 Routing Algorithms Link- State algorithm Each node maintains a view of the whole network topology Find the shortest path
Routing in Ad Hoc Wireless Networks PROF. MICHAEL TSAI / DR. KATE LIN 2014/05/14 Routing Algorithms Link- State algorithm Each node maintains a view of the whole network topology Find the shortest path
Kapitel 5: Mobile Ad Hoc Networks. Characteristics. Applications of Ad Hoc Networks. Wireless Communication. Wireless communication networks types
 Kapitel 5: Mobile Ad Hoc Networks Mobilkommunikation 2 WS 08/09 Wireless Communication Wireless communication networks types Infrastructure-based networks Infrastructureless networks Ad hoc networks Prof.
Kapitel 5: Mobile Ad Hoc Networks Mobilkommunikation 2 WS 08/09 Wireless Communication Wireless communication networks types Infrastructure-based networks Infrastructureless networks Ad hoc networks Prof.
LECTURE 9. Ad hoc Networks and Routing
 1 LECTURE 9 Ad hoc Networks and Routing Ad hoc Networks 2 Ad Hoc Networks consist of peer to peer communicating nodes (possibly mobile) no infrastructure. Topology of the network changes dynamically links
1 LECTURE 9 Ad hoc Networks and Routing Ad hoc Networks 2 Ad Hoc Networks consist of peer to peer communicating nodes (possibly mobile) no infrastructure. Topology of the network changes dynamically links
Content. 1. Introduction. 2. The Ad-hoc On-Demand Distance Vector Algorithm. 3. Simulation and Results. 4. Future Work. 5.
 Rahem Abri Content 1. Introduction 2. The Ad-hoc On-Demand Distance Vector Algorithm Path Discovery Reverse Path Setup Forward Path Setup Route Table Management Path Management Local Connectivity Management
Rahem Abri Content 1. Introduction 2. The Ad-hoc On-Demand Distance Vector Algorithm Path Discovery Reverse Path Setup Forward Path Setup Route Table Management Path Management Local Connectivity Management
Mobile Ad-hoc and Sensor Networks Lesson 04 Mobile Ad-hoc Network (MANET) Routing Algorithms Part 1
 Mobile Ad-hoc and Sensor Networks Lesson 04 Mobile Ad-hoc Network (MANET) Routing Algorithms Part 1 Oxford University Press 2007. All rights reserved. 1 Ad-hoc networks deployment For routing, target detection,
Mobile Ad-hoc and Sensor Networks Lesson 04 Mobile Ad-hoc Network (MANET) Routing Algorithms Part 1 Oxford University Press 2007. All rights reserved. 1 Ad-hoc networks deployment For routing, target detection,
Outline. CS5984 Mobile Computing. Taxonomy of Routing Protocols AODV 1/2. Dr. Ayman Abdel-Hamid. Routing Protocols in MANETs Part I
 CS5984 Mobile Computing Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Part I Outline Routing Protocols for Ad hoc Networks Example of a reactive routing protocol AODV: Ad hoc On-demand
CS5984 Mobile Computing Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Part I Outline Routing Protocols for Ad hoc Networks Example of a reactive routing protocol AODV: Ad hoc On-demand
Wireless Networking & Mobile Computing
 Wireless Networking & Mobile Computing CS 752/852 - Spring 2012 Network Layer: Ad Hoc Routing Tamer Nadeem Dept. of Computer Science The OSI Communication Model Page 2 Spring 2012 CS 752/852 - Wireless
Wireless Networking & Mobile Computing CS 752/852 - Spring 2012 Network Layer: Ad Hoc Routing Tamer Nadeem Dept. of Computer Science The OSI Communication Model Page 2 Spring 2012 CS 752/852 - Wireless
Ad Hoc Routing Protocols and Issues
 Ad Hoc Routing Protocols and Issues Stefano Basagni ECE Dept Northeastern University Boston, Jan 2003 Ad hoc (AD-HAHK or AD-HOKE)-Adjective a) Concerned with a particular end or purpose, and b) formed
Ad Hoc Routing Protocols and Issues Stefano Basagni ECE Dept Northeastern University Boston, Jan 2003 Ad hoc (AD-HAHK or AD-HOKE)-Adjective a) Concerned with a particular end or purpose, and b) formed
CMPE 257: Wireless and Mobile Networking
 CMPE 257: Wireless and Mobile Networking Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 6 CMPE 257 Winter'11 1 Announcements Project proposals. Student presentations. 10 students so
CMPE 257: Wireless and Mobile Networking Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 6 CMPE 257 Winter'11 1 Announcements Project proposals. Student presentations. 10 students so
Mobile & Wireless Networking. Lecture 10: Mobile Transport Layer & Ad Hoc Networks. [Schiller, Section 8.3 & Section 9] [Reader, Part 8]
![Mobile & Wireless Networking. Lecture 10: Mobile Transport Layer & Ad Hoc Networks. [Schiller, Section 8.3 & Section 9] [Reader, Part 8] Mobile & Wireless Networking. Lecture 10: Mobile Transport Layer & Ad Hoc Networks. [Schiller, Section 8.3 & Section 9] [Reader, Part 8]](/thumbs/92/110300020.jpg) 192620010 Mobile & Wireless Networking Lecture 10: Mobile Transport Layer & Ad Hoc Networks [Schiller, Section 8.3 & Section 9] [Reader, Part 8] Geert Heijenk Outline of Lecture 10 Mobile transport layer
192620010 Mobile & Wireless Networking Lecture 10: Mobile Transport Layer & Ad Hoc Networks [Schiller, Section 8.3 & Section 9] [Reader, Part 8] Geert Heijenk Outline of Lecture 10 Mobile transport layer
Routing Protocols in MANETs
 Chapter 4 Routing Protocols in MANETs 4.1 Introduction The main aim of any Ad Hoc network routing protocol is to meet the challenges of the dynamically changing topology and establish a correct and an
Chapter 4 Routing Protocols in MANETs 4.1 Introduction The main aim of any Ad Hoc network routing protocol is to meet the challenges of the dynamically changing topology and establish a correct and an
2013, IJARCSSE All Rights Reserved Page 85
 Volume 3, Issue 12, December 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Overview of
Volume 3, Issue 12, December 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Overview of
A COMPARISON OF REACTIVE ROUTING PROTOCOLS DSR, AODV AND TORA IN MANET
 ISSN: 2278 1323 All Rights Reserved 2016 IJARCET 296 A COMPARISON OF REACTIVE ROUTING PROTOCOLS DSR, AODV AND TORA IN MANET Dr. R. Shanmugavadivu 1, B. Chitra 2 1 Assistant Professor, Department of Computer
ISSN: 2278 1323 All Rights Reserved 2016 IJARCET 296 A COMPARISON OF REACTIVE ROUTING PROTOCOLS DSR, AODV AND TORA IN MANET Dr. R. Shanmugavadivu 1, B. Chitra 2 1 Assistant Professor, Department of Computer
ECS-087: Mobile Computing
 ECS-087: Mobile Computing Mobile Adhoc Networks and Routing in MANETS (most of the slides borrowed from Prof. Sridhar Iyer) Diwakar Yagyasen 1 Index Mobile Ad Hoc Networks (MANET) MAC in MANET MANET routing
ECS-087: Mobile Computing Mobile Adhoc Networks and Routing in MANETS (most of the slides borrowed from Prof. Sridhar Iyer) Diwakar Yagyasen 1 Index Mobile Ad Hoc Networks (MANET) MAC in MANET MANET routing
Redes Inalámbricas Tema 4. Mobile Ad Hoc Networks
 Redes Inalámbricas Tema 4. Mobile Ad Hoc Networks A. Specific properties B. Flooding as a basic mechanism C. Basic routing protocols DSR AODV y DYMO OLSR y OLSRv2 D. Advanced protocols and techniques Acknowledgments
Redes Inalámbricas Tema 4. Mobile Ad Hoc Networks A. Specific properties B. Flooding as a basic mechanism C. Basic routing protocols DSR AODV y DYMO OLSR y OLSRv2 D. Advanced protocols and techniques Acknowledgments
Lecture 13: Routing in multihop wireless networks. Mythili Vutukuru CS 653 Spring 2014 March 3, Monday
 Lecture 13: Routing in multihop wireless networks Mythili Vutukuru CS 653 Spring 2014 March 3, Monday Routing in multihop networks Figure out a path from source to destination. Basic techniques of routing
Lecture 13: Routing in multihop wireless networks Mythili Vutukuru CS 653 Spring 2014 March 3, Monday Routing in multihop networks Figure out a path from source to destination. Basic techniques of routing
AODV-PA: AODV with Path Accumulation
 -PA: with Path Accumulation Sumit Gwalani Elizabeth M. Belding-Royer Department of Computer Science University of California, Santa Barbara fsumitg, ebeldingg@cs.ucsb.edu Charles E. Perkins Communications
-PA: with Path Accumulation Sumit Gwalani Elizabeth M. Belding-Royer Department of Computer Science University of California, Santa Barbara fsumitg, ebeldingg@cs.ucsb.edu Charles E. Perkins Communications
Mobile Ad-Hoc Networks & Routing Algorithms
 Mobile Ad-Hoc Networks & Routing Algorithms EMMANOUIL G. SPANAKIS, PhD. spanakis@csd.uoc.gr COLLABORATING RESEARCHER, COMPUTATIONAL BIOMEDICINE LABORATORY, FORTH-ICS VISITING LECTURER, COMPUTER SCIENCE
Mobile Ad-Hoc Networks & Routing Algorithms EMMANOUIL G. SPANAKIS, PhD. spanakis@csd.uoc.gr COLLABORATING RESEARCHER, COMPUTATIONAL BIOMEDICINE LABORATORY, FORTH-ICS VISITING LECTURER, COMPUTER SCIENCE
Location Awareness in Ad Hoc Wireless Mobile Neworks
 Location Awareness in Ad Hoc Wireless Mobile Neworks Lijuan Ai Wenyu Wang Yi Zhou 11/14/2001 Mobile Computing, Fall 2001 1 PART I INTRODUCTION TO MANET & LOCATION-AWARE COMPONENTS 11/14/2001 Mobile Computing,
Location Awareness in Ad Hoc Wireless Mobile Neworks Lijuan Ai Wenyu Wang Yi Zhou 11/14/2001 Mobile Computing, Fall 2001 1 PART I INTRODUCTION TO MANET & LOCATION-AWARE COMPONENTS 11/14/2001 Mobile Computing,
CMPE 257: Wireless and Mobile Networking
 CMPE 257: Wireless and Mobile Networking Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 5 CMPE 257 Winter'11 1 Announcements Project proposals. Student presentations. 10 students so
CMPE 257: Wireless and Mobile Networking Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 5 CMPE 257 Winter'11 1 Announcements Project proposals. Student presentations. 10 students so
1 Multipath Node-Disjoint Routing with Backup List Based on the AODV Protocol
 1 Multipath Node-Disjoint Routing with Backup List Based on the AODV Protocol Vahid Zangeneh i and Shahriar Mohammadi ii * ABSTRACT In recent years, routing has been the most focused area in ad hoc networks
1 Multipath Node-Disjoint Routing with Backup List Based on the AODV Protocol Vahid Zangeneh i and Shahriar Mohammadi ii * ABSTRACT In recent years, routing has been the most focused area in ad hoc networks
A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols. Broch et al Presented by Brian Card
 A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols Broch et al Presented by Brian Card 1 Outline Introduction NS enhancements Protocols: DSDV TORA DRS AODV Evaluation Conclusions
A Performance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols Broch et al Presented by Brian Card 1 Outline Introduction NS enhancements Protocols: DSDV TORA DRS AODV Evaluation Conclusions
Performance Evaluation of MANET through NS2 Simulation
 International Journal of Electronic and Electrical Engineering. ISSN 0974-2174, Volume 7, Number 1 (2014), pp. 25-30 International Research Publication House http://www.irphouse.com Performance Evaluation
International Journal of Electronic and Electrical Engineering. ISSN 0974-2174, Volume 7, Number 1 (2014), pp. 25-30 International Research Publication House http://www.irphouse.com Performance Evaluation
6. Node Disjoint Split Multipath Protocol for Unified. Multicasting through Announcements (NDSM-PUMA)
 103 6. Node Disjoint Split Multipath Protocol for Unified Multicasting through Announcements (NDSM-PUMA) 6.1 Introduction It has been demonstrated in chapter 3 that the performance evaluation of the PUMA
103 6. Node Disjoint Split Multipath Protocol for Unified Multicasting through Announcements (NDSM-PUMA) 6.1 Introduction It has been demonstrated in chapter 3 that the performance evaluation of the PUMA
Experiment and Evaluation of a Mobile Ad Hoc Network with AODV Routing Protocol
 Experiment and Evaluation of a Mobile Ad Hoc Network with AODV Routing Protocol Kalyan Kalepu, Shiv Mehra and Chansu Yu, Department of Electrical and Computer Engineering Cleveland State University 2121
Experiment and Evaluation of a Mobile Ad Hoc Network with AODV Routing Protocol Kalyan Kalepu, Shiv Mehra and Chansu Yu, Department of Electrical and Computer Engineering Cleveland State University 2121
Study and Comparison of Mesh and Tree- Based Multicast Routing Protocols for MANETs
 Study and Comparison of Mesh and Tree- Based Multicast Routing Protocols for MANETs Rajneesh Gujral Associate Proffesor (CSE Deptt.) Maharishi Markandeshwar University, Mullana, Ambala Sanjeev Rana Associate
Study and Comparison of Mesh and Tree- Based Multicast Routing Protocols for MANETs Rajneesh Gujral Associate Proffesor (CSE Deptt.) Maharishi Markandeshwar University, Mullana, Ambala Sanjeev Rana Associate
UCS-805 MOBILE COMPUTING Jan-May,2011 TOPIC 8. ALAK ROY. Assistant Professor Dept. of CSE NIT Agartala.
 Mobile Ad Hoc Networks: Routing TOPIC 8 UCS-805 MOBILE COMPUTING Jan-May,2011 ALAK ROY. Assistant Professor Dept. of CSE NIT Agartala Email-alakroy.nerist@gmail.com Mobile Ad Hoc Networks (MANET) Introduction
Mobile Ad Hoc Networks: Routing TOPIC 8 UCS-805 MOBILE COMPUTING Jan-May,2011 ALAK ROY. Assistant Professor Dept. of CSE NIT Agartala Email-alakroy.nerist@gmail.com Mobile Ad Hoc Networks (MANET) Introduction
Computation of Multiple Node Disjoint Paths
 Chapter 5 Computation of Multiple Node Disjoint Paths 5.1 Introduction In recent years, on demand routing protocols have attained more attention in mobile Ad Hoc networks as compared to other routing schemes
Chapter 5 Computation of Multiple Node Disjoint Paths 5.1 Introduction In recent years, on demand routing protocols have attained more attention in mobile Ad Hoc networks as compared to other routing schemes
WSN Routing Protocols
 WSN Routing Protocols 1 Routing Challenges and Design Issues in WSNs 2 Overview The design of routing protocols in WSNs is influenced by many challenging factors. These factors must be overcome before
WSN Routing Protocols 1 Routing Challenges and Design Issues in WSNs 2 Overview The design of routing protocols in WSNs is influenced by many challenging factors. These factors must be overcome before
QoS Routing By Ad-Hoc on Demand Vector Routing Protocol for MANET
 2011 International Conference on Information and Network Technology IPCSIT vol.4 (2011) (2011) IACSIT Press, Singapore QoS Routing By Ad-Hoc on Demand Vector Routing Protocol for MANET Ashwini V. Biradar
2011 International Conference on Information and Network Technology IPCSIT vol.4 (2011) (2011) IACSIT Press, Singapore QoS Routing By Ad-Hoc on Demand Vector Routing Protocol for MANET Ashwini V. Biradar
Routing Protocols in MANET: Comparative Study
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 7, July 2014, pg.119
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 7, July 2014, pg.119
Recent Researches in Communications, Information Science and Education
 AODV Based Multi-path Local Repairing Scheme for Mobile Ad Hoc Networks Eman Shaaban, PhD Computer Systems Dept. Faculty of computer and information science Ain-Shams university, Cairo, Egypt Eman.shaaban@cis.asu.edu.eg
AODV Based Multi-path Local Repairing Scheme for Mobile Ad Hoc Networks Eman Shaaban, PhD Computer Systems Dept. Faculty of computer and information science Ain-Shams university, Cairo, Egypt Eman.shaaban@cis.asu.edu.eg
A Comparative Study of Routing Protocols for Mobile Ad-Hoc Networks
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 11, November 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 11, November 2014,
ROUTING ALGORITHMS Part 2: Data centric and hierarchical protocols
 ROUTING ALGORITHMS Part 2: Data centric and hierarchical protocols 1 Negative Reinforcement Time out Explicitly degrade the path by re-sending interest with lower data rate. Source Gradient New Data Path
ROUTING ALGORITHMS Part 2: Data centric and hierarchical protocols 1 Negative Reinforcement Time out Explicitly degrade the path by re-sending interest with lower data rate. Source Gradient New Data Path
Unicast Routing in Mobile Ad Hoc Networks. Dr. Ashikur Rahman CSE 6811: Wireless Ad hoc Networks
 Unicast Routing in Mobile Ad Hoc Networks 1 Routing problem 2 Responsibility of a routing protocol Determining an optimal way to find optimal routes Determining a feasible path to a destination based on
Unicast Routing in Mobile Ad Hoc Networks 1 Routing problem 2 Responsibility of a routing protocol Determining an optimal way to find optimal routes Determining a feasible path to a destination based on
A COMPARISON OF IMPROVED AODV ROUTING PROTOCOL BASED ON IEEE AND IEEE
 Journal of Engineering Science and Technology Vol. 4, No. 2 (2009) 132-141 School of Engineering, Taylor s University College A COMPARISON OF IMPROVED AODV ROUTING PROTOCOL BASED ON IEEE 802.11 AND IEEE
Journal of Engineering Science and Technology Vol. 4, No. 2 (2009) 132-141 School of Engineering, Taylor s University College A COMPARISON OF IMPROVED AODV ROUTING PROTOCOL BASED ON IEEE 802.11 AND IEEE
Power aware Multi-path Routing Protocol for MANETS
 Power aware Multi-path Routing Protocol for MANETS Shruthi P Murali 1,Joby John 2 1 (ECE Dept, SNGCE, India) 2 (ECE Dept, SNGCE, India) Abstract: Mobile Adhoc Network consists of a large number of mobile
Power aware Multi-path Routing Protocol for MANETS Shruthi P Murali 1,Joby John 2 1 (ECE Dept, SNGCE, India) 2 (ECE Dept, SNGCE, India) Abstract: Mobile Adhoc Network consists of a large number of mobile
What is Multicasting? Multicasting Fundamentals. Unicast Transmission. Agenda. L70 - Multicasting Fundamentals. L70 - Multicasting Fundamentals
 What is Multicasting? Multicasting Fundamentals Unicast transmission transmitting a packet to one receiver point-to-point transmission used by most applications today Multicast transmission transmitting
What is Multicasting? Multicasting Fundamentals Unicast transmission transmitting a packet to one receiver point-to-point transmission used by most applications today Multicast transmission transmitting
Expanding Ring Search for Route Discovery in LOADng Routing Protocol
 Expanding Ring Search for Route Discovery in LOADng Routing Protocol Antonin Bas, Jiazi Yi, Thomas Clausen Laboratoire d Informatique (LIX) Ecole Polytechnique, France) antonin@antonin-bas.fr, jiazi@jiaziyi.com,
Expanding Ring Search for Route Discovery in LOADng Routing Protocol Antonin Bas, Jiazi Yi, Thomas Clausen Laboratoire d Informatique (LIX) Ecole Polytechnique, France) antonin@antonin-bas.fr, jiazi@jiaziyi.com,
A Survey - Energy Efficient Routing Protocols in MANET
 , pp. 163-168 http://dx.doi.org/10.14257/ijfgcn.2016.9.5.16 A Survey - Energy Efficient Routing Protocols in MANET Jyoti Upadhyaya and Nitin Manjhi Department of Computer Science, RGPV University Shriram
, pp. 163-168 http://dx.doi.org/10.14257/ijfgcn.2016.9.5.16 A Survey - Energy Efficient Routing Protocols in MANET Jyoti Upadhyaya and Nitin Manjhi Department of Computer Science, RGPV University Shriram
Routing protocols in WSN
 Routing protocols in WSN 1.1 WSN Routing Scheme Data collected by sensor nodes in a WSN is typically propagated toward a base station (gateway) that links the WSN with other networks where the data can
Routing protocols in WSN 1.1 WSN Routing Scheme Data collected by sensor nodes in a WSN is typically propagated toward a base station (gateway) that links the WSN with other networks where the data can
White Paper. Mobile Ad hoc Networking (MANET) with AODV. Revision 1.0
 White Paper Mobile Ad hoc Networking (MANET) with AODV Revision 1.0 This page is intentionally blank, or rather nearly blank. Table of Contents TABLE OF CONTENTS...3 TABLE OF FIGURES...4 WHAT IS MANET?...5
White Paper Mobile Ad hoc Networking (MANET) with AODV Revision 1.0 This page is intentionally blank, or rather nearly blank. Table of Contents TABLE OF CONTENTS...3 TABLE OF FIGURES...4 WHAT IS MANET?...5
Mitigating Superfluous Flooding of Control Packets MANET
 Mitigating Superfluous Flooding of Control Packets MANET B.Shanmugha Priya 1 PG Student, Department of Computer Science, Park College of Engineering and Technology, Kaniyur, Coimbatore, India 1 Abstract:
Mitigating Superfluous Flooding of Control Packets MANET B.Shanmugha Priya 1 PG Student, Department of Computer Science, Park College of Engineering and Technology, Kaniyur, Coimbatore, India 1 Abstract:
Tietokoneverkot T
 Tietokoneverkot T-110.350 Ad-hoc networking 9.2.2005 Antti Ylä-Jääski 9.2.2005 / AYJ Slide 1 Goals and topics Ad-hoc networking terminology & outline Ad-hoc networking hot topics - routing Discuss how
Tietokoneverkot T-110.350 Ad-hoc networking 9.2.2005 Antti Ylä-Jääski 9.2.2005 / AYJ Slide 1 Goals and topics Ad-hoc networking terminology & outline Ad-hoc networking hot topics - routing Discuss how
Figure 1: Ad-Hoc routing protocols.
 Performance Analysis of Routing Protocols for Wireless Ad-Hoc Networks Sukhchandan Lally and Ljiljana Trajković Simon Fraser University Vancouver, British Columbia Canada E-mail: {lally, ljilja}@sfu.ca
Performance Analysis of Routing Protocols for Wireless Ad-Hoc Networks Sukhchandan Lally and Ljiljana Trajković Simon Fraser University Vancouver, British Columbia Canada E-mail: {lally, ljilja}@sfu.ca
Wireless Sensor Networks: Clustering, Routing, Localization, Time Synchronization
 Wireless Sensor Networks: Clustering, Routing, Localization, Time Synchronization Maurizio Bocca, M.Sc. Control Engineering Research Group Automation and Systems Technology Department maurizio.bocca@tkk.fi
Wireless Sensor Networks: Clustering, Routing, Localization, Time Synchronization Maurizio Bocca, M.Sc. Control Engineering Research Group Automation and Systems Technology Department maurizio.bocca@tkk.fi
PERFORMANCE COMPARISON OF LINK, NODE AND ZONE DISJOINT MULTI-PATH ROUTING STRATEGIES AND MINIMUM HOP SINGLE PATH ROUTING FOR MOBILE AD HOC NETWORKS
 PERFORMANCE COMPARISON OF LINK, NODE AND ZONE DISJOINT MULTI-PATH ROUTING STRATEGIES AND MINIMUM HOP SINGLE PATH ROUTING FOR MOBILE AD HOC NETWORKS Natarajan Meghanathan Jackson State University, 1400
PERFORMANCE COMPARISON OF LINK, NODE AND ZONE DISJOINT MULTI-PATH ROUTING STRATEGIES AND MINIMUM HOP SINGLE PATH ROUTING FOR MOBILE AD HOC NETWORKS Natarajan Meghanathan Jackson State University, 1400
Optimizing Performance of Routing against Black Hole Attack in MANET using AODV Protocol Prerana A. Chaudhari 1 Vanaraj B.
 IJSRD - International Journal for Scientific Research & Development Vol. 3, Issue 04, 2015 ISSN (online): 2321-0613 Optimizing Performance of Routing against Black Hole Attack in MANET using AODV Protocol
IJSRD - International Journal for Scientific Research & Development Vol. 3, Issue 04, 2015 ISSN (online): 2321-0613 Optimizing Performance of Routing against Black Hole Attack in MANET using AODV Protocol
A REVERSE AND ENHANCED AODV ROUTING PROTOCOL FOR MANETS
 A REVERSE AND ENHANCED AODV ROUTING PROTOCOL FOR MANETS M. Sanabani 1, R. Alsaqour 2 and S. Kurkushi 1 1 Faculty of Computer Science and Information Systems, Thamar University, Thamar, Republic of Yemen
A REVERSE AND ENHANCED AODV ROUTING PROTOCOL FOR MANETS M. Sanabani 1, R. Alsaqour 2 and S. Kurkushi 1 1 Faculty of Computer Science and Information Systems, Thamar University, Thamar, Republic of Yemen
Simulation and Comparative Analysis of AODV, DSR, DSDV and OLSR Routing Protocol in MANET Abstract Keywords:
 Volume-9 Number-1 Jan -June 2017 pp. 16-21 available online at www.csjournalss.com Simulation and Comparative Analysis of AODV, DSR, DSDV and OLSR Routing Protocol in MANET Sachin Lalar, Arun Kumar Yadav
Volume-9 Number-1 Jan -June 2017 pp. 16-21 available online at www.csjournalss.com Simulation and Comparative Analysis of AODV, DSR, DSDV and OLSR Routing Protocol in MANET Sachin Lalar, Arun Kumar Yadav
Mobile Communications. Ad-hoc and Mesh Networks
 Ad-hoc+mesh-net 1 Mobile Communications Ad-hoc and Mesh Networks Manuel P. Ricardo Faculdade de Engenharia da Universidade do Porto Ad-hoc+mesh-net 2 What is an ad-hoc network? What are differences between
Ad-hoc+mesh-net 1 Mobile Communications Ad-hoc and Mesh Networks Manuel P. Ricardo Faculdade de Engenharia da Universidade do Porto Ad-hoc+mesh-net 2 What is an ad-hoc network? What are differences between
6367(Print), ISSN (Online) Volume 4, Issue 2, March April (2013), IAEME & TECHNOLOGY (IJCET)
 INTERNATIONAL International Journal of Computer JOURNAL Engineering OF COMPUTER and Technology ENGINEERING (IJCET), ISSN 0976- & TECHNOLOGY (IJCET) ISSN 0976 6367(Print) ISSN 0976 6375(Online) Volume 4,
INTERNATIONAL International Journal of Computer JOURNAL Engineering OF COMPUTER and Technology ENGINEERING (IJCET), ISSN 0976- & TECHNOLOGY (IJCET) ISSN 0976 6367(Print) ISSN 0976 6375(Online) Volume 4,
Arvind Krishnamurthy Fall 2003
 Ad-hoc Routing Arvind Krishnamurthy Fall 2003 Ad Hoc Routing Create multi-hop connectivity among set of wireless, possibly moving, nodes Mobile, wireless hosts act as forwarding nodes as well as end systems
Ad-hoc Routing Arvind Krishnamurthy Fall 2003 Ad Hoc Routing Create multi-hop connectivity among set of wireless, possibly moving, nodes Mobile, wireless hosts act as forwarding nodes as well as end systems
LOCATION-AIDED ROUTING PROTOCOL IN HYBRID WIRED-WIRELESS NETWORKS. WU MINTAO (B.Eng.(Hons.), NTU)
 LOCATION-AIDED ROUTING PROTOCOL IN HYBRID WIRED-WIRELESS NETWORKS WU MINTAO (B.Eng.(Hons.), NTU) A THESIS SUBMITTED FOR THE DEGREE OF MASTER OF ENGINEERING DEPARTMENT OF ELECTRICAL AND COMPUTER ENGINEERING
LOCATION-AIDED ROUTING PROTOCOL IN HYBRID WIRED-WIRELESS NETWORKS WU MINTAO (B.Eng.(Hons.), NTU) A THESIS SUBMITTED FOR THE DEGREE OF MASTER OF ENGINEERING DEPARTMENT OF ELECTRICAL AND COMPUTER ENGINEERING
Wireless Mesh Networks
 Wireless Mesh Networks COS 463: Wireless Networks Lecture 6 Kyle Jamieson [Parts adapted from I. F. Akyildiz, B. Karp] Wireless Mesh Networks Describes wireless networks in which each node can communicate
Wireless Mesh Networks COS 463: Wireless Networks Lecture 6 Kyle Jamieson [Parts adapted from I. F. Akyildiz, B. Karp] Wireless Mesh Networks Describes wireless networks in which each node can communicate
3. Evaluation of Selected Tree and Mesh based Routing Protocols
 33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY
 INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK COMPARISON OF MANET REACTIVE ROUTING PROTOCOLS USING OPNET SIMULATOR SANGEETA MONGA
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK COMPARISON OF MANET REACTIVE ROUTING PROTOCOLS USING OPNET SIMULATOR SANGEETA MONGA
Politecnico di Milano Facoltà di Ingegneria dell Informazione. WI-7 Ad hoc networks. Wireless Internet Prof. Antonio Capone
 Politecnico di Milano Facoltà di Ingegneria dell Informazione WI-7 Ad hoc networks Wireless Internet Prof. Antonio Capone Acknowlegments o This class notes are mostly based on the teaching material of:
Politecnico di Milano Facoltà di Ingegneria dell Informazione WI-7 Ad hoc networks Wireless Internet Prof. Antonio Capone Acknowlegments o This class notes are mostly based on the teaching material of:
Lecture 6: Vehicular Computing and Networking. Cristian Borcea Department of Computer Science NJIT
 Lecture 6: Vehicular Computing and Networking Cristian Borcea Department of Computer Science NJIT GPS & navigation system On-Board Diagnostic (OBD) systems DVD player Satellite communication 2 Internet
Lecture 6: Vehicular Computing and Networking Cristian Borcea Department of Computer Science NJIT GPS & navigation system On-Board Diagnostic (OBD) systems DVD player Satellite communication 2 Internet
CHAPTER 2 LITERATURE REVIEW
 39 CHAPTER 2 LITERATURE REVIEW This chapter gives a brief summary of the MANET routing protocol types and their details. 2.1 ROUTING IN AD-HOC NETWORKS Routing is the act of moving information from source
39 CHAPTER 2 LITERATURE REVIEW This chapter gives a brief summary of the MANET routing protocol types and their details. 2.1 ROUTING IN AD-HOC NETWORKS Routing is the act of moving information from source
INTERNATIONAL JOURNAL FOR ADVANCE RESEARCH IN ENGINEERING AND TECHNOLOGY WINGS TO YOUR THOUGHTS..
 INTERNATIONAL JOURNAL FOR ADVANCE RESEARCH An Overview of Mobile Ad-Hoc Networks: Architecture, Routing and Challenges Avadhesh Kumar 1 Sonali Yadav 2 Kamalesh Chandra Maurya 3 1 Assistant Professor, avadhesh@iul.ac.in
INTERNATIONAL JOURNAL FOR ADVANCE RESEARCH An Overview of Mobile Ad-Hoc Networks: Architecture, Routing and Challenges Avadhesh Kumar 1 Sonali Yadav 2 Kamalesh Chandra Maurya 3 1 Assistant Professor, avadhesh@iul.ac.in
Routing Protocols in Mobile Ad-Hoc Network
 International Journal of Computer Science & Management Studies, Vol. 12, Issue 02, April 2012 Protocols in Mobile Ad-Hoc Network Sachin Minocha M. Tech Student, Vaish College of Engineering, Rohtak, Haryana
International Journal of Computer Science & Management Studies, Vol. 12, Issue 02, April 2012 Protocols in Mobile Ad-Hoc Network Sachin Minocha M. Tech Student, Vaish College of Engineering, Rohtak, Haryana
Ad Hoc Networks: Issues and Routing
 Ad Hoc Networks: Issues and Routing Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse574-08/
Ad Hoc Networks: Issues and Routing Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse574-08/
Mobile and Sensor Systems. Lecture 3: Infrastructure, Ad-hoc and Delay Tolerant Mobile Networks Dr Cecilia Mascolo
 Mobile and Sensor Systems Lecture 3: Infrastructure, Ad-hoc and Delay Tolerant Mobile Networks Dr Cecilia Mascolo In this lecture In this lecture we will describe the difference in infrastructure and ad
Mobile and Sensor Systems Lecture 3: Infrastructure, Ad-hoc and Delay Tolerant Mobile Networks Dr Cecilia Mascolo In this lecture In this lecture we will describe the difference in infrastructure and ad
A Comparative study of On-Demand Data Delivery with Tables Driven and On-Demand Protocols for Mobile Ad-Hoc Network
 A Comparative study of On-Demand Data Delivery with Tables Driven and On-Demand Protocols for Mobile Ad-Hoc Network Humayun Bakht Research Fellow, London School of Commerce, United Kingdom humayunbakht@yahoo.co.uk
A Comparative study of On-Demand Data Delivery with Tables Driven and On-Demand Protocols for Mobile Ad-Hoc Network Humayun Bakht Research Fellow, London School of Commerce, United Kingdom humayunbakht@yahoo.co.uk
Comparative Study of Routing Protocols in MANET
 Comparative Study of Routing Protocols in MANET First Author-PrernaYadav 1 Student,Second Author-ShubhraSaxena 2 Professor Abstract-An ad hoc network is basically a collection of wireless nodes not having
Comparative Study of Routing Protocols in MANET First Author-PrernaYadav 1 Student,Second Author-ShubhraSaxena 2 Professor Abstract-An ad hoc network is basically a collection of wireless nodes not having
A Review of Reactive, Proactive & Hybrid Routing Protocols for Mobile Ad Hoc Network
 ShriRam College of Engineering & Management 1 A Review of Reactive, Proactive & Hybrid Routing Protocols for Mobile Ad Hoc Network M.Ramaiya Rohit Gupta Rachit Jain Head,Dept. Computer Science Dept. Computer
ShriRam College of Engineering & Management 1 A Review of Reactive, Proactive & Hybrid Routing Protocols for Mobile Ad Hoc Network M.Ramaiya Rohit Gupta Rachit Jain Head,Dept. Computer Science Dept. Computer
CS5984 Mobile Computing
 CS5984 Mobile Computing Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Part II 1 Outline Routing Protocols for Ad hoc Networks DSDV: Highly Dynamic Destination-Sequenced Distance- Vector
CS5984 Mobile Computing Dr. Ayman Abdel-Hamid Computer Science Department Virginia Tech Part II 1 Outline Routing Protocols for Ad hoc Networks DSDV: Highly Dynamic Destination-Sequenced Distance- Vector
DYNAMIC DATA ROUTING IN MANET USING POSITION BASED OPPORTUNISTIC ROUTING PROTOCOL
 INTERNATIONAL JOURNAL OF RESEARCH IN COMPUTER APPLICATIONS AND ROBOTICS ISSN 2320-7345 DYNAMIC DATA ROUTING IN MANET USING POSITION BASED OPPORTUNISTIC ROUTING PROTOCOL P. Kalaivani 1, G. Sathya 2, N.
INTERNATIONAL JOURNAL OF RESEARCH IN COMPUTER APPLICATIONS AND ROBOTICS ISSN 2320-7345 DYNAMIC DATA ROUTING IN MANET USING POSITION BASED OPPORTUNISTIC ROUTING PROTOCOL P. Kalaivani 1, G. Sathya 2, N.
International Journal of Scientific & Engineering Research, Volume 6, Issue 3, March ISSN
 International Journal of Scientific & Engineering Research, Volume 6, Issue 3, March-2015 1464 Performance Evaluation of AODV and DSDV Routing Protocols through Clustering in MANETS Prof. A Rama Rao, M
International Journal of Scientific & Engineering Research, Volume 6, Issue 3, March-2015 1464 Performance Evaluation of AODV and DSDV Routing Protocols through Clustering in MANETS Prof. A Rama Rao, M
Realization of Fault Tolerant Routing Protocol for Zigbee
 Journal of Computer Science 8 (5): 761-766, 2012 ISSN 1549-3636 2012 Science Publications Realization of Fault Tolerant Routing Protocol for Zigbee 1 Sharmila Sankar and 2 Sankaranarayanan Department of
Journal of Computer Science 8 (5): 761-766, 2012 ISSN 1549-3636 2012 Science Publications Realization of Fault Tolerant Routing Protocol for Zigbee 1 Sharmila Sankar and 2 Sankaranarayanan Department of
Issues of Long-Hop and Short-Hop Routing in Mobile Ad Hoc Networks: A Comprehensive Study
 Issues of Long-Hop and Short-Hop Routing in Mobile Ad Hoc Networks: A Comprehensive Study M. Tarique, A. Hossain, R. Islam and C. Akram Hossain Dept. of Electrical and Electronic Engineering, American
Issues of Long-Hop and Short-Hop Routing in Mobile Ad Hoc Networks: A Comprehensive Study M. Tarique, A. Hossain, R. Islam and C. Akram Hossain Dept. of Electrical and Electronic Engineering, American
Mobile Ad Hoc Networks: Routing, MAC and Transport Issues
 Mobile Ad Hoc Networks: Routing, MAC and Transport Issues Nitin H. Vaidya University of Illinois at Urbana-Champaign nhv@uiuc.edu http://www.crhc.uiuc.edu/~nhv 2004 Nitin Vaidya 1 Notes Names in brackets,
Mobile Ad Hoc Networks: Routing, MAC and Transport Issues Nitin H. Vaidya University of Illinois at Urbana-Champaign nhv@uiuc.edu http://www.crhc.uiuc.edu/~nhv 2004 Nitin Vaidya 1 Notes Names in brackets,
Performance Analysis of Aodv Protocol under Black Hole Attack
 International Journal of Scientific & Engineering Research Volume 2, Issue 8,August-2011 1 Performance Analysis of Aodv Protocol under Black Hole Attack Monika Roopak, Dr. Bvr Reddy ABSTRACT- Mobile Ad-hoc
International Journal of Scientific & Engineering Research Volume 2, Issue 8,August-2011 1 Performance Analysis of Aodv Protocol under Black Hole Attack Monika Roopak, Dr. Bvr Reddy ABSTRACT- Mobile Ad-hoc
Performance Comparison of AODV, DSR, DSDV and OLSR MANET Routing Protocols
 Performance Comparison of AODV, DSR, DSDV and OLSR MANET Routing Protocols Akshay Shankar, Lavanya Chelle Information Science Engineering RNS Institute of Technology Bangalore, India Abstract- A Mobile
Performance Comparison of AODV, DSR, DSDV and OLSR MANET Routing Protocols Akshay Shankar, Lavanya Chelle Information Science Engineering RNS Institute of Technology Bangalore, India Abstract- A Mobile
Information Brokerage
 Information Brokerage Sensing Networking Leonidas Guibas Stanford University Computation CS321 Information Brokerage Services in Dynamic Environments Information Brokerage Information providers (sources,
Information Brokerage Sensing Networking Leonidas Guibas Stanford University Computation CS321 Information Brokerage Services in Dynamic Environments Information Brokerage Information providers (sources,
A Location-based Directional Route Discovery (LDRD) Protocol in Mobile Ad-hoc Networks
 A Location-based Directional Route Discovery (LDRD) Protocol in Mobile Ad-hoc Networks Stephen S. Yau, Wei Gao, and Dazhi Huang Dept. of Computer Science and Engineering Arizona State University Tempe,
A Location-based Directional Route Discovery (LDRD) Protocol in Mobile Ad-hoc Networks Stephen S. Yau, Wei Gao, and Dazhi Huang Dept. of Computer Science and Engineering Arizona State University Tempe,
Performance Analysis of Various Routing Protocols for Motorway Surveillance System Cameras Network
 www.ijcsi.org 7 Performance Analysis of Various Routing Protocols for Motorway Surveillance System Cameras Network L. A. Hassnawi 1, R.B Ahmad 2, Abid Yahya 3, S. A. Aljunid 4, M. Elshaikh 5 School of
www.ijcsi.org 7 Performance Analysis of Various Routing Protocols for Motorway Surveillance System Cameras Network L. A. Hassnawi 1, R.B Ahmad 2, Abid Yahya 3, S. A. Aljunid 4, M. Elshaikh 5 School of
Routing in Variable Topology Networks
 Routing in Variable Topology Networks Dr. Alhussein Abouzeid Electrical, Computer and Systems Engineering (ECSE) Rensselaer Polytechnic Institute Variable Topology Networks P2P networks for distributed
Routing in Variable Topology Networks Dr. Alhussein Abouzeid Electrical, Computer and Systems Engineering (ECSE) Rensselaer Polytechnic Institute Variable Topology Networks P2P networks for distributed
Routing for IoT and Sensor Systems
 Facoltà di Ingegneria dell Informazione, Informatica e Statistica Internet of Things A.Y. 2017/18 Routing for IoT and Sensor Systems Federico Ceccarelli PhD Student 1 The Collection Tree Protocol (CTP)
Facoltà di Ingegneria dell Informazione, Informatica e Statistica Internet of Things A.Y. 2017/18 Routing for IoT and Sensor Systems Federico Ceccarelli PhD Student 1 The Collection Tree Protocol (CTP)
An Efficient Routing Approach and Improvement Of AODV Protocol In Mobile Ad-Hoc Networks
 An Efficient Routing Approach and Improvement Of AODV Protocol In Mobile Ad-Hoc Networks Tejomayee Nath #1 & Suneeta Mohanty *2 # School of Computer Engineering, KIIT University Bhubaneswar,, India Abstract
An Efficient Routing Approach and Improvement Of AODV Protocol In Mobile Ad-Hoc Networks Tejomayee Nath #1 & Suneeta Mohanty *2 # School of Computer Engineering, KIIT University Bhubaneswar,, India Abstract
Simulation & Performance Analysis of Mobile Ad-Hoc Network Routing Protocol
 Simulation & Performance Analysis of Mobile Ad-Hoc Network Routing Protocol V.S.Chaudhari 1, Prof.P.N.Matte 2, Prof. V.P.Bhope 3 Department of E&TC, Raisoni College of Engineering, Ahmednagar Abstract:-
Simulation & Performance Analysis of Mobile Ad-Hoc Network Routing Protocol V.S.Chaudhari 1, Prof.P.N.Matte 2, Prof. V.P.Bhope 3 Department of E&TC, Raisoni College of Engineering, Ahmednagar Abstract:-
EZR: Enhanced Zone Based Routing In Manet
 EZR: Enhanced Zone Based Routing In Manet Bency Wilson 1, Geethu Bastian 2, Vinitha Ann Regi 3, Arun Soman 4 Department of Information Technology, Rajagiri School of Engineering and Technology, Rajagiri
EZR: Enhanced Zone Based Routing In Manet Bency Wilson 1, Geethu Bastian 2, Vinitha Ann Regi 3, Arun Soman 4 Department of Information Technology, Rajagiri School of Engineering and Technology, Rajagiri
IN a mobile ad hoc network, nodes move arbitrarily.
 IEEE TRANSACTIONS ON MOBILE COMPUTING, VOL. 5, NO. 6, JUNE 2006 609 Distributed Cache Updating for the Dynamic Source Routing Protocol Xin Yu Abstract On-demand routing protocols use route caches to make
IEEE TRANSACTIONS ON MOBILE COMPUTING, VOL. 5, NO. 6, JUNE 2006 609 Distributed Cache Updating for the Dynamic Source Routing Protocol Xin Yu Abstract On-demand routing protocols use route caches to make
Low Overhead Geometric On-demand Routing Protocol for Mobile Ad Hoc Networks
 Low Overhead Geometric On-demand Routing Protocol for Mobile Ad Hoc Networks Chang Su, Lili Zheng, Xiaohai Si, Fengjun Shang Institute of Computer Science & Technology Chongqing University of Posts and
Low Overhead Geometric On-demand Routing Protocol for Mobile Ad Hoc Networks Chang Su, Lili Zheng, Xiaohai Si, Fengjun Shang Institute of Computer Science & Technology Chongqing University of Posts and
Performance Evaluation of Route Failure Detection in Mobile Ad Hoc Networks
 Performance Evaluation of Route Failure Detection in Mobile Ad Hoc Networks Dimitri Marandin 4. Würzburger Workshop "IP Netzmanagement, IP Netzplanung und Optimierung" 27.-28. July 2004 www.ifn.et.tu-dresden.de/tk/
Performance Evaluation of Route Failure Detection in Mobile Ad Hoc Networks Dimitri Marandin 4. Würzburger Workshop "IP Netzmanagement, IP Netzplanung und Optimierung" 27.-28. July 2004 www.ifn.et.tu-dresden.de/tk/
Outline. Wireless Ad Hoc & Sensor Networks (Wireless Sensor Networks III) Localisation and Positioning. Localisation and Positioning properties
 Wireless Ad Hoc & Sensor Networks (Wireless Sensor Networks III) Outline Localisation and Positioning Topology Control Routing Summary WS 2009/2010 Prof. Dr. Dieter Hogrefe/Prof. Dr. Xiaoming Fu Dr. Omar
Wireless Ad Hoc & Sensor Networks (Wireless Sensor Networks III) Outline Localisation and Positioning Topology Control Routing Summary WS 2009/2010 Prof. Dr. Dieter Hogrefe/Prof. Dr. Xiaoming Fu Dr. Omar
Performance Evaluation of Two Reactive and Proactive Mobile Ad Hoc Routing Protocols
 www.ijcsi.org 551 Performance Evaluation of Two Reactive and Proactive Mobile Ad Hoc Routing Protocols Kashif Ibrahim Qazi Javed Ahmed Abdul Qudoos Mirza Aamir Mehmood Department of Computer Science, Balochistan
www.ijcsi.org 551 Performance Evaluation of Two Reactive and Proactive Mobile Ad Hoc Routing Protocols Kashif Ibrahim Qazi Javed Ahmed Abdul Qudoos Mirza Aamir Mehmood Department of Computer Science, Balochistan
CS551 Ad-hoc Routing
 CS551 Ad-hoc Routing Bill Cheng http://merlot.usc.edu/cs551-f12 1 Mobile Routing Alternatives Why not just assume a base station? good for many cases, but not some (military, disaster recovery, sensor
CS551 Ad-hoc Routing Bill Cheng http://merlot.usc.edu/cs551-f12 1 Mobile Routing Alternatives Why not just assume a base station? good for many cases, but not some (military, disaster recovery, sensor
Example of TORA operations. From last time, this was the DAG that was built. A was the source and X was the destination.
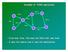 Example of TORA operations A Link 2 D Link 6 Y Link 1 Link 3 C Link 4 Link 8 B Link 5 E Link 7 X From last time, this was the DAG that was built. A was the source and X was the destination. Link 1 A B
Example of TORA operations A Link 2 D Link 6 Y Link 1 Link 3 C Link 4 Link 8 B Link 5 E Link 7 X From last time, this was the DAG that was built. A was the source and X was the destination. Link 1 A B
Link Estimation and Tree Routing
 Network Embedded Systems Sensor Networks Link Estimation and Tree Routing 1 Marcus Chang, mchang@cs.jhu.edu Slides: Andreas Terzis Outline Link quality estimation Examples of link metrics Four-Bit Wireless
Network Embedded Systems Sensor Networks Link Estimation and Tree Routing 1 Marcus Chang, mchang@cs.jhu.edu Slides: Andreas Terzis Outline Link quality estimation Examples of link metrics Four-Bit Wireless
References. Forwarding. Introduction...
 References Routing Protocols H. Karl and A. Willing. Protocols and Architectures for Wireless Sensor Networks. John Wiley & Sons, 005. (Chapter 11) K. Sohraby, D. Minoli, and T. Znati. Wireless Sensor
References Routing Protocols H. Karl and A. Willing. Protocols and Architectures for Wireless Sensor Networks. John Wiley & Sons, 005. (Chapter 11) K. Sohraby, D. Minoli, and T. Znati. Wireless Sensor
Chapter 11 Chapter 6
 Routing Protocols References H. Karl and A. Willing. Protocols and Architectures for Wireless Sensor Networks. John Wiley & Sons, 2005. (Chapter 11) K. Sohraby, D. Minoli, and T. Znati. Wireless Sensor
Routing Protocols References H. Karl and A. Willing. Protocols and Architectures for Wireless Sensor Networks. John Wiley & Sons, 2005. (Chapter 11) K. Sohraby, D. Minoli, and T. Znati. Wireless Sensor
Performance Evaluation of Various Routing Protocols in MANET
 208 Performance Evaluation of Various Routing Protocols in MANET Jaya Jacob 1,V.Seethalakshmi 2 1 II MECS,Sri Shakthi Institute of Science and Technology, Coimbatore, India 2 Associate Professor-ECE, Sri
208 Performance Evaluation of Various Routing Protocols in MANET Jaya Jacob 1,V.Seethalakshmi 2 1 II MECS,Sri Shakthi Institute of Science and Technology, Coimbatore, India 2 Associate Professor-ECE, Sri
Unicast Routing in Mobile Ad-Hoc Networks
 Unicast Routing in Mobile Ad-Hoc Networks Overview Introduction MaNet Protocols Proactive & Hybrid Protocols WRP/GSR/FSR/LAR ZRP Reactive Protocols DSR/DSDV/AODV Challenges in Ad-Hoc Networks References
Unicast Routing in Mobile Ad-Hoc Networks Overview Introduction MaNet Protocols Proactive & Hybrid Protocols WRP/GSR/FSR/LAR ZRP Reactive Protocols DSR/DSDV/AODV Challenges in Ad-Hoc Networks References
Performance analysis of aodv, dsdv and aomdv using wimax in NS-2
 Performance analysis of aodv, dsdv and aomdv using wimax in NS-2 Madhusrhee B Department Computer Science, L.J Institute of Technology, Ahmedabad, India Abstract WiMAX (IEEE 802.16) technology empowers
Performance analysis of aodv, dsdv and aomdv using wimax in NS-2 Madhusrhee B Department Computer Science, L.J Institute of Technology, Ahmedabad, India Abstract WiMAX (IEEE 802.16) technology empowers
MANET TECHNOLOGY. Keywords: MANET, Wireless Nodes, Ad-Hoc Network, Mobile Nodes, Routes Protocols.
 MANET TECHNOLOGY Dharna 1, Varsha Saroha 2, R. B. Dubey 3 1,2,3 Department of Electronics and Communication Engineering, Hindu College of Engineering, Sonepat, Haryana,(India) ABSTRACT Wireless technology
MANET TECHNOLOGY Dharna 1, Varsha Saroha 2, R. B. Dubey 3 1,2,3 Department of Electronics and Communication Engineering, Hindu College of Engineering, Sonepat, Haryana,(India) ABSTRACT Wireless technology
A Survey on Wireless Routing Protocols (AODV, DSR, DSDV)
 RESEARCH ARTICLE International Journal of Computer Techniques - Volume 2 Issue 1, 2015 OPEN ACCESS A Survey on Wireless Routing Protocols (AODV, DSR, DSDV) Sejal D Mello 1, Priyanka B. Patil 2, Tarannum
RESEARCH ARTICLE International Journal of Computer Techniques - Volume 2 Issue 1, 2015 OPEN ACCESS A Survey on Wireless Routing Protocols (AODV, DSR, DSDV) Sejal D Mello 1, Priyanka B. Patil 2, Tarannum
ENERGY EFFICIENT MULTIPATH ROUTING FOR MOBILE AD HOC NETWORKS
 ENERGY EFFICIENT MULTIPATH ROUTING FOR MOBILE AD HOC NETWORKS May Cho Aye and Aye Moe Aung Faculty of Information and Communication Technology, University of Technology (Yatanarpon Cyber City), Pyin Oo
ENERGY EFFICIENT MULTIPATH ROUTING FOR MOBILE AD HOC NETWORKS May Cho Aye and Aye Moe Aung Faculty of Information and Communication Technology, University of Technology (Yatanarpon Cyber City), Pyin Oo
Performance Evaluation of AODV and DSR routing protocols in MANET
 Performance Evaluation of AODV and DSR routing protocols in MANET Naresh Dobhal Diwakar Mourya ABSTRACT MANETs are wireless temporary adhoc networks that are being setup with no prior infrastructure and
Performance Evaluation of AODV and DSR routing protocols in MANET Naresh Dobhal Diwakar Mourya ABSTRACT MANETs are wireless temporary adhoc networks that are being setup with no prior infrastructure and
