FlexVPN HA Dual Hub Configuration Example
|
|
|
- Bernice Cameron
- 5 years ago
- Views:
Transcription
1 FlexVPN HA Dual Hub Configuration Example Document ID: Contributed by Piotr Kupisiewicz, Wen Zhang, and Frederic Detienne, Cisco TAC Engineers. Apr 08, 2015 Contents Introduction Prerequisites Requirements Components used Background Information Configure Network Diagram Regular Operational Scenario Spoke to Spoke (Shortcut) Routing Tables and Outputs for Regular Operational Scenario HUB1 Failure Scenario Configurations R1 HUB Configuration R2 HUB2 Configuration R3 SPOKE1 Configuration R4 SPOKE2 Configuration R5 AGGR1 Configuration R6 AGGR2 Configuration R7 HOST Configuration (simulation of HOST in that network) Important Configuration Notes Verify Troubleshoot Related Information Introduction This document describes how to configure a full redundancy design for Remote Offices that connect to a Data Center via IPSec based VPN over an insecure network medium, such as the Internet. Prerequisites Requirements There are no specific requirements for this document. Components used The information in this document is based on these technology components: Border Gateway Protocol (BGP) as the routing protocol within the Data Center and between spokes and hubs in the VPN overlay.
2 Bidirectional Forwarding Detection (BFD) as a mechanism that detects down links (router down) that run inside of the Data Center only (not over the overlay tunnels). Cisco IOS FlexVPN between the hubs and spokes, with spoke to spoke capabilities enabled via short cut switching. Generic Routing Encapsulation (GRE) tunneling between two hubs in order to enable spoke to spoke communication, even when the spokes are connected to different hubs. Enhanced Object Tracking and static routes tied to the tracked objects. The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command. Background Information When you design remote access solutions for the Data Center, High Availability (HA) is often a key requirement for mission critical user applications. The solution that is presented in this document allows fast detection and recovery from failure scenarios in which one of the VPN terminating hubs goes down due to a reload, upgrade, or power problems. All of the Remote Offices routers (spokes) then use the other operational hub immediately upon detection of such failure. Here are the advantages of this design: Fast network recovery from a VPN hub down scenario No complicated stateful synchronizations (such as IPSec Security Associations (SAs), Internet Security Association and Key Management Protocol (ISAKMP) SAs, and Crypto routing) between the VPN hubs No anti replay problems due to delays in the Encapsulating Security Payload (ESP) sequence number synchronization with IPSec Stateful HA VPN hubs can use different Cisco IOS/IOS XE based hardware or software Flexible load balancing implementation choices with BGP as the routing protocol that runs in the VPN overlay Clear and readable routing on all devices with no hidden mechanisms that run in the background Direct spoke to spoke connectivity All of the FlexVPN advantages, to include Authentication, Authorization, and Accounting (AAA) integration and per tunnel Quality of Service (QoS) Configure This section provides example scenarios and describes how to configure a full redundancy design for Remote Offices that connect to the Data Center via IPSec based VPN over an insecure network medium.
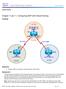
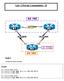
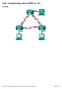
3 Note: Use the Command Lookup Tool (registered customers only) in order to obtain more information on the commands used in this section. Network Diagram This is the network topology that is used in this document: Note: All of the routers that are used in this topology run Cisco IOS Version 15.2(4)M1, and the Internet Cloud uses an address scheme of /24. Regular Operational Scenario In a normal operational scenario, when all of the routers are up and operational, all spoke routers route all of the traffic through the default hub (R1 HUB1). This routing preference is achieved when the default BGP local preference is set to 200 (refer to the sections that follow for details). This can be adjusted based on the deployment requirements, such as traffic load balancing. Spoke to Spoke (Shortcut) If R3 Spoke1 initiates a connection to R4 Spoke2, a dynamic spoke to spoke tunnel is created with the short cut switching configuration. Tip: For more details, refer to the Configuring FlexVPN Spoke to Spoke configuration guide. If R3 Spoke1 is connected only to R1 HUB1, and R4 Spoke2 is connected only to R2 HUB2, a direct spoke to spoke connection can still be achieved with the point to point GRE tunnel that runs between the hubs. In this case, the initial traffic path between R3 Spoke1 and R4 Spoke2 appears similar to this:
4 Since R1 Hub1 receives the packet on the virtual access interface, which has the same Next Hop Resolution Protocol (NHRP) network ID as that on the GRE tunnel, the Traffic Indication is sent toward the R3 Spoke1. This triggers spoke to spoke dynamic tunnel creation:
5 Routing Tables and Outputs for Regular Operational Scenario Here is the R1 HUB1 routing table in a regular operational scenario: R1 HUB1# show ip route Codes: L local, C connected, S static, R RIP, M mobile, B BGP D EIGRP, EX EIGRP external, O OSPF, IA OSPF inter area N1 OSPF NSSA external type 1, N2 OSPF NSSA external type 2 E1 OSPF external type 1, E2 OSPF external type 2 i IS IS, su IS IS summary, L1 IS IS level 1, L2 IS IS level 2 ia IS IS inter area, * candidate default, U per user static route o ODR, P periodic downloaded static route, H NHRP, l LISP a application route + replicated route, % next hop override Gateway of last resort is not set /8 is variably subnetted, 11 subnets, 3 masks S /8 is directly connected, Null0 C /24 is directly connected, Tunnel0 L /32 is directly connected, Tunnel0 C /32 is directly connected, Loopback0 S /32 is directly connected, Virtual Access1 S /32 is directly connected, Virtual Access2 B /32 [200/0] via , 00:05:40 B /32 [200/0] via , 00:05:40 B /32 [200/0] via , 00:05:40
6 B /32 [200/0] via , 00:05:40 B /32 [200/0] via , 00:05: /16 is variably subnetted, 2 subnets, 2 masks C /24 is directly connected, Ethernet0/0 L /32 is directly connected, Ethernet0/0 S /16 is directly connected, Null /24 is variably subnetted, 2 subnets, 2 masks C /24 is directly connected, Ethernet0/2 L /32 is directly connected, Ethernet0/2 B /24 [200/0] via , 00:05:40 B /24 [200/0] via , 00:05:24 B /24 [200/0] via , 00:05:33 Here is the R3 SPOKE1 routing table in a regular operational scenario after the spoke to spoke tunnel with R4 SPOKE2 is created: R3 SPOKE1# show ip route Codes: L local, C connected, S static, R RIP, M mobile, B BGP D EIGRP, EX EIGRP external, O OSPF, IA OSPF inter area N1 OSPF NSSA external type 1, N2 OSPF NSSA external type 2 E1 OSPF external type 1, E2 OSPF external type 2 i IS IS, su IS IS summary, L1 IS IS level 1, L2 IS IS level 2 ia IS IS inter area, * candidate default, U per user static route o ODR, P periodic downloaded static route, H NHRP, l LISP a application route + replicated route, % next hop override Gateway of last resort is not set /8 is variably subnetted, 8 subnets, 2 masks B /8 [200/0] via , 00:06:27 H /32 is directly connected, 00:06:38, Tunnel1 S % /32 is directly connected, Tunnel0 C /32 is directly connected, Tunnel0 H /32 is directly connected, 00:01:30, Virtual Access1 S /32 is directly connected, Tunnel1 C /32 is directly connected, Tunnel1 H /32 [250/1] via , 00:01:30, Virtual Access /16 is variably subnetted, 2 subnets, 2 masks C /24 is directly connected, Ethernet0/0 L /32 is directly connected, Ethernet0/0 B /16 [200/0] via , 00:06: /24 is variably subnetted, 2 subnets, 2 masks C /24 is directly connected, Ethernet0/1 L /32 is directly connected, Ethernet0/ /32 is subnetted, 1 subnets H [250/1] via , 00:01:30, Virtual Access1 On R3 Spoke1, the BGP table has two entries for the /16 network with different local preferences (R1 Hub1 is preferred): R3 SPOKE1#show ip bgp /16 BGP routing table entry for /16, version 8 Paths: (2 available, best #2, table default) Not advertised to any peer Refresh Epoch 1 Local from ( ) Origin incomplete, metric 0, localpref 100, valid, internal rx pathid: 0, tx pathid: 0 Refresh Epoch 1 Local from ( ) Origin incomplete, metric 0, localpref 200, valid, internal, best rx pathid: 0, tx pathid: 0x0
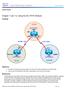
7 Here is the R5 AGGR1 routing table in a regular operational scenario: R5 LAN1#show ip route /8 is variably subnetted, 10 subnets, 3 masks B /8 [200/0] via , 00:07:22 B /24 [200/0] via , 00:07:22 B /32 [200/0] via , 00:07:22 B /32 [200/0] via , 00:07:17 B /32 [200/0] via , 00:07:16 B /32 [200/0] via , 15:44:13 B /32 [200/0] via , 15:44:13 B /32 [200/0] via , 15:44:13 C /32 is directly connected, Loopback0 B /32 [200/0] via , 00:07: /24 is subnetted, 1 subnets B [200/0] via , 00:07:22 B /16 [200/0] via , 00:07: /24 is variably subnetted, 2 subnets, 2 masks C /24 is directly connected, Ethernet0/0 L /32 is directly connected, Ethernet0/ /24 is variably subnetted, 2 subnets, 2 masks C /24 is directly connected, Ethernet0/1 L /32 is directly connected, Ethernet0/1 B /24 [200/0] via , 00:07:06 B /24 [200/0] via , 00:07:15 Here is the R7 HOST routing table in a regular operational scenario: R7 HOST#show ip route S* /0 [1/0] via /24 is variably subnetted, 2 subnets, 2 masks C /24 is directly connected, Ethernet0/0 L /32 is directly connected, Ethernet0/0 HUB1 Failure Scenario Here is an R1 HUB1 down scenario (due to actions such as power outages or an upgrade):
8 In this scenario, this sequence of events occurs: 1. The BFD on R2 HUB2 and on LAN aggregate routers R5 AGGR1 and R6 AGGR2 detect the down status of R1 HUB1. As a result, the BGP neighborship immediately goes down. 2. The track object detection for R2 HUB2 that detects the presence of the R1 HUB1 loopback goes down (Track 1 in the example configuration). 3. This downed tracked object triggers another track to go up (Logical NOT). In this example, Track 2 goes up whenever Track 1 goes down. 4. This triggers a static IP routing entry to be added to the routing table due to a value that is lower than the default administrative distance. Here is the relevant configuration: Routes added when second HUB is down ip route Null0 tag 500 track 2 ip route Null0 tag 500 track 2 Default static routes are with Tag 200 and admin distance of 150 ip route Null0 150 tag 200 ip route Null0 150 tag R2 HUB2 redistributes these static routes with a BGP local preference that is larger than the value that is set for R1 HUB1. In this example, a local preference of 500 is used in the failure scenario, instead of the 200 that is set by R1 HUB1: route map LOCALPREF permit 5 match tag 500 set local preference 500 route map LOCALPREF permit 10 match tag 200
9 6. L 7. set local preference 200 On R3 Spoke1, you can see this in the BGP outputs. Note that the entry to R1 still exists, but it is not used: R3 SPOKE1#show ip bgp /16 BGP routing table entry for /16, version 10 Paths: (2 available, best #1, table default) Not advertised to any peer Refresh Epoch 1 Local from ( ) Origin incomplete, metric 0, localpref 500, valid, internal, best rx pathid: 0, tx pathid: 0x0 Refresh Epoch 1 Local from ( ) Origin incomplete, metric 0, localpref 200, valid, internal rx pathid: 0, tx pathid: 0 At this point, both spokes (R3 Spoke1 and R4 Spoke2) begin to send traffic to R2 HUB2. All of these steps should occur within one second. Here is the routing table on Spoke 3: R3 SPOKE1#show ip route /8 is variably subnetted, 5 subnets, 2 masks B /8 [200/0] via , 00:00:01 S /32 is directly connected, Tunnel0 C /32 is directly connected, Tunnel0 S /32 is directly connected, Tunnel1 C /32 is directly connected, Tunnel /16 is variably subnetted, 2 subnets, 2 masks C /24 is directly connected, Ethernet0/0 L /32 is directly connected, Ethernet0/0 B /16 [200/0] via , 00:00: /24 is variably subnetted, 2 subnets, 2 masks C /24 is directly connected, Ethernet0/ /32 is directly connected, Ethernet0/1 Later BGP sessions between the spokes and R1 HUB1 goes down, and Dead Peer Detection (DPD) removes the IPSec tunnels that are terminated on R1 HUB1. However, this does not impact traffic forwarding, since R2 HUB2 is already used as the main tunnel terminating gateway: R3 SPOKE1#show ip bgp /16 BGP routing table entry for /16, version 10 Paths: (1 available, best #1, table default) Not advertised to any peer Refresh Epoch 1 Local from ( ) Origin incomplete, metric 0, localpref 500, valid, internal, best rx pathid: 0, tx pathid: 0x0 Configurations This section provides sample configurations for the hubs and spokes that are used in this topology. R1 HUB Configuration version 15.4 hostname R1 HUB1 aaa new model
10 aaa authorization network default local aaa session id common setting track timers to the lowest possible (the lower this value is the faster router will react track timer ip route msec 500 Monitoring of HUB2's loopback present in routing table If it is present it will mean that HUB2 is alive track 1 ip route reachability Monitoring of loopback of R5 AGGR 1 track 3 ip route reachability Monitoring of loopback of R6 AGGR 2 track 4 ip route reachability Track 2 should be UP only when HUB2 is not available and both AGGRE routers are up track 2 list boolean and object 1 not object 3 object 4 IKEv2 Config Exchange configuration (IP addresses for spokes are assigned from pool) crypto ikev2 authorization policy default pool SPOKES route set interface route accept any tag 20 IKEv2 profile for Spokes Smart Defaults used crypto ikev2 profile default match identity remote any authentication remote pre share key cisco authentication local pre share key cisco aaa authorization group psk list default default virtual template 1 interface Loopback0 ip address GRE Tunnel configured to second HUB. It is required for spoke to spoke connectivity to work in all possible circumstances no BFD echo configuration is required to avoid Traffic Indication sent by remote HUB (BFD echo is having the same source and destination IP address) interface Tunnel0 ip address ip nhrp redirect bfd interval 50 min_rx 50 multiplier 3 no bfd echo tunnel source Ethernet0/2 tunnel destination interface Ethernet0/0 ip address interface Ethernet0/2 ip address bfd interval 50 min_rx 50 multiplier 5
11 interface Virtual Template1 type tunnel ip unnumbered Loopback0 ip nhrp redirect tunnel protection ipsec profile default BGP Configuration router bgp 1 bgp log neighbor changes dynamic peer groups are used for AGGR routers and SPOKES bgp listen range /24 peer group DC bgp listen range /24 peer group SPOKES BGP timers configured timers bgp neighbor SPOKES peer group neighbor SPOKES remote as 1 neighbor DC peer group neighbor DC remote as 1 Within DC BFD is used to determine neighbour status neighbor DC fall over bfd neighbor remote as 1 BFD is used to detect HUB2 status neighbor fall over bfd address family ipv4 redistribute connected route map which determines what should be the local pref redistribute static route map LOCALPREF neighbor SPOKES activate to spokes only Aggregate/Summary routes are sent neighbor SPOKES route map AGGR out neighbor DC activate neighbor DC route reflector client neighbor activate neighbor route reflector client exit address family ip local pool SPOKES When HUB2 goes down Static Routes with Tag 500 are added and admin distance of 1 ip route Null0 tag 500 track 2 ip route Null0 tag 500 track 2 Default static routes are with Tag 200 and admin distance of 150 ip route Null0 150 tag 200 ip route Null0 150 tag 200 ip prefix list AGGR seq 5 permit /16 ip prefix list AGGR seq 10 permit /8 route map AGGR permit 10 match ip address prefix list AGGR route map LOCALPREF permit 5 match tag 500 set local preference 500 route map LOCALPREF permit 10 match tag 200 set local preference 200 route map LOCALPREF permit 15 match tag 20
12 R2 HUB2 Configuration hostname R2 HUB2 aaa new model aaa authorization network default local track timer ip route msec 500 track 1 ip route reachability track 2 list boolean and object 1 not object 3 object 4 track 3 ip route reachability track 4 ip route reachability crypto ikev2 authorization policy default pool SPOKES route set interface route accept any tag 20 crypto ikev2 profile default match identity remote any authentication remote pre share key cisco authentication local pre share key cisco aaa authorization group psk list default default virtual template 1 interface Loopback0 ip address interface Tunnel0 ip address ip nhrp redirect bfd interval 50 min_rx 50 multiplier 3 no bfd echo tunnel source Ethernet0/2 tunnel destination interface Ethernet0/0 ip address interface Ethernet0/2 ip address bfd interval 50 min_rx 50 multiplier 5 interface Virtual Template1 type tunnel ip unnumbered Loopback0 ip nhrp redirect tunnel protection ipsec profile default router bgp 1 bgp log neighbor changes bgp listen range /24 peer group DC bgp listen range /24 peer group SPOKES timers bgp 15 30
13 neighbor SPOKES peer group neighbor SPOKES remote as 1 neighbor DC peer group neighbor DC remote as 1 neighbor DC fall over bfd neighbor remote as 1 neighbor fall over bfd address family ipv4 redistribute connected redistribute static route map LOCALPREF neighbor SPOKES activate neighbor SPOKES route map AGGR out neighbor DC activate neighbor DC route reflector client neighbor activate neighbor route reflector client exit address family ip local pool SPOKES ip forward protocol nd ip route Null0 tag 500 track 2 ip route Null0 tag 500 track 2 ip route Null0 150 tag 200 ip route Null0 150 tag 200 ip prefix list AGGR seq 5 permit /16 ip prefix list AGGR seq 10 permit /8 route map AGGR permit 10 match ip address prefix list AGGR route map LOCALPREF permit 5 match tag 500 set local preference 500 route map LOCALPREF permit 10 match tag 200 set local preference 100 route map LOCALPREF permit 15 match tag 20 R3 SPOKE1 Configuration hostname R3 SPOKE1 aaa new model aaa authorization network default local crypto ikev2 authorization policy default route set interface crypto ikev2 profile default match identity remote any authentication remote pre share key cisco authentication local pre share key cisco dpd 10 2 on demand aaa authorization group psk list default default
14 Tunnel to the HUB1 interface Tunnel0 ip address negotiated ip nhrp shortcut virtual template 2 tunnel source Ethernet0/0 tunnel destination tunnel protection ipsec profile default Tunnel to the HUB2 interface Tunnel1 ip address negotiated ip nhrp shortcut virtual template 2 tunnel source Ethernet0/0 tunnel destination tunnel protection ipsec profile default interface Ethernet0/0 description INTERNET CLOUD ip address interface Ethernet0/1 description LAN ip address interface Virtual Template2 type tunnel ip unnumbered Ethernet0/1 ip nhrp shortcut virtual template 2 tunnel protection ipsec profile default router bgp 1 bgp log neighbor changes timers bgp neighbor remote as 1 neighbor remote as 1 address family ipv4 network neighbor activate neighbor activate exit address family R4 SPOKE2 Configuration hostname R4 SPOKE2 aaa new model aaa authorization network default local crypto ikev2 authorization policy default route set interface crypto ikev2 profile default match identity remote any authentication remote pre share key cisco authentication local pre share key cisco dpd 10 2 on demand aaa authorization group psk list default default interface Tunnel0
15 ip address negotiated ip nhrp shortcut virtual template 2 tunnel source Ethernet0/0 tunnel destination tunnel protection ipsec profile default interface Tunnel1 ip address negotiated ip nhrp shortcut virtual template 2 tunnel source Ethernet0/0 tunnel destination tunnel protection ipsec profile default interface Ethernet0/0 ip address interface Ethernet0/1 ip address interface Virtual Template2 type tunnel ip unnumbered Ethernet0/1 ip nhrp shortcut virtual template 2 tunnel protection ipsec profile default router bgp 1 bgp log neighbor changes timers bgp neighbor remote as 1 neighbor remote as 1 address family ipv4 network neighbor activate neighbor activate exit address family R5 AGGR1 Configuration hostname R5 LAN1 no aaa new model interface Loopback0 ip address interface Ethernet0/0 ip address bfd interval 50 min_rx 50 multiplier 5 HSRP configuration on the LAN side interface Ethernet0/1 ip address standby 1 ip router bgp 1 bgp log neighbor changes neighbor remote as 1 neighbor fall over bfd neighbor remote as 1 neighbor fall over bfd
16 address family ipv4 redistribute connected redistribute static neighbor activate neighbor activate exit address family R6 AGGR2 Configuration hostname R6 LAN2 interface Loopback0 ip address interface Ethernet0/0 ip address bfd interval 50 min_rx 50 multiplier 5 interface Ethernet0/1 ip address standby 1 ip standby 1 priority 200 router bgp 1 bgp log neighbor changes neighbor remote as 1 neighbor fall over bfd neighbor remote as 1 neighbor fall over bfd address family ipv4 redistribute connected redistribute static neighbor activate neighbor activate exit address family R7 HOST Configuration (simulation of HOST in that network) hostname R7 HOST no aaa new model interface Ethernet0/0 ip address ip route Important Configuration Notes Here are some important notes about the configurations that are described in the previous sections: The point to point GRE tunnel between the two hubs is required for spoke to spoke connectivity to work in all scenarios, specifically to include those scenarios in which some of the spokes are connected only to one of the hubs and others to another hub. The no bfd echo configuration in the GRE tunnel interface between the two hubs is required in order to avoid the Traffic Indication that is sent out from another hub. The BFD Echo has the same source and destination IP address, which is equal to the IP address of the router that sends the BFD Echo. Since these packets are routed back by the router that responds, the NHRP Traffic Indications are
17 generated. In the BGP configuration, route map filtering that advertises the networks towards spokes is not required, but it makes the configurations more optimal since only aggregate/summary routes are advertised: neighbor SPOKES route map AGGR out On the hubs, the route map LOCALPREF configuration is required in order to set up the proper BGP local preference, and it filters the redistributed static routes to only the summary and IKEv2 configuration mode routes. This design does not address redundancy at Remote Office locations (spoke). If the WAN link on the spoke goes down, VPN also does not work. Add a second link to the spoke router or add a second spoke router within the same location in order to address this issue. In summary, the redundancy design that is presented in this document can be treated as a modern alternative to the Stateful Switchover (SSO)/Stateful feature. It is highly flexible and can be fine tuned in order to meet your specific deployment requirements. Verify There is currently no verification procedure available for this configuration. Troubleshoot There is currently no specific troubleshooting information available for this configuration. Related Information Cisco IOS FlexVPN Data Sheet Configuring FlexVPN Spoke to Spoke Technical Support & Documentation Cisco Systems Updated: Apr 08, 2015 Document ID:
Configuring FlexVPN Spoke to Spoke
 Last Published Date: March 28, 2014 The FlexVPN Spoke to Spoke feature enables a FlexVPN client to establish a direct crypto tunnel with another FlexVPN client leveraging virtual tunnel interfaces (VTI),
Last Published Date: March 28, 2014 The FlexVPN Spoke to Spoke feature enables a FlexVPN client to establish a direct crypto tunnel with another FlexVPN client leveraging virtual tunnel interfaces (VTI),
BGP Best External. Finding Feature Information
 The feature provides the network with a backup external route to avoid loss of connectivity of the primary external route. The feature advertises the most preferred route among those received from external
The feature provides the network with a backup external route to avoid loss of connectivity of the primary external route. The feature advertises the most preferred route among those received from external
Easy Virtual Network Configuration Example
 Easy Virtual Network Configuration Example Document ID: 117974 Contributed by Fabrice Ducomble, Cisco TAC Engineer. Aug 04, 2014 Contents Introduction Prerequisites Requirements Components Used Background
Easy Virtual Network Configuration Example Document ID: 117974 Contributed by Fabrice Ducomble, Cisco TAC Engineer. Aug 04, 2014 Contents Introduction Prerequisites Requirements Components Used Background
Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT
 Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT The Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT feature supports the forwarding of packets from a standby
Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT The Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT feature supports the forwarding of packets from a standby
Shortcut Switching Enhancements for NHRP in DMVPN Networks
 Shortcut Switching Enhancements for NHRP in DMVPN Networks Routers in a Dynamic Multipoint VPN (DMVPN) Phase 3 network use Next Hop Resolution Protocol (NHRP) Shortcut Switching to discover shorter paths
Shortcut Switching Enhancements for NHRP in DMVPN Networks Routers in a Dynamic Multipoint VPN (DMVPN) Phase 3 network use Next Hop Resolution Protocol (NHRP) Shortcut Switching to discover shorter paths
DMVPN Topology. Page1
 DMVPN DMVPN Topology Page1 LAB 2: Configure EIGRP over DMVPN: Task 1: Configure EIGRP over DMVPN Process Step 1 In the configuration mode of router configure EIGRP over DMVPN by following command: R1:
DMVPN DMVPN Topology Page1 LAB 2: Configure EIGRP over DMVPN: Task 1: Configure EIGRP over DMVPN Process Step 1 In the configuration mode of router configure EIGRP over DMVPN by following command: R1:
RR> RR> RR>en RR# RR# RR# RR# *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 RR#
 RR> RR> RR>en *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 term len 0 show run Building configuration... Current configuration : 2568 bytes version 15.4 service timestamps debug
RR> RR> RR>en *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 term len 0 show run Building configuration... Current configuration : 2568 bytes version 15.4 service timestamps debug
LAB1: BGP IPv4. BGP: Initial Config. Disclaimer
 Page1 LAB1: BGP IPv4 Disclaimer This Configuration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 LAB1: BGP IPv4 Disclaimer This Configuration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Configuring Redundant Routing on the VPN 3000 Concentrator
 Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
LAB11: EIGRP IPv4. EIGRP: Stub. Disclaimer
 Page1 AB11: EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 AB11: EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Chapter 7 Lab 7-1, Configuring BGP with Default Routing
 Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
LAB8: Named EIGRP IPv4
 Page1 AB8: Named EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 AB8: Named EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Adjust Administrative Distance for Route Selection in Cisco IOS Routers Configuration Example
 Adjust Administrative Distance for Route Selection in Cisco IOS Routers Configuration Example Document ID: 113153 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
Adjust Administrative Distance for Route Selection in Cisco IOS Routers Configuration Example Document ID: 113153 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
Chapter 3 Lab 3-2, Multi-Area OSPFv2 and OSPFv3 with Stub Area
 Chapter 3 Topology Objectives Configure multi-area OSPFv2 for IPv4. Configure multi-area OSPFv3 for IPv6 Verify multi-area behavior. Configure stub and totally stubby areas for OSPFv2. Configure stub and
Chapter 3 Topology Objectives Configure multi-area OSPFv2 for IPv4. Configure multi-area OSPFv3 for IPv6 Verify multi-area behavior. Configure stub and totally stubby areas for OSPFv2. Configure stub and
The information in this document is based on Cisco IOS Software Release 15.4 version.
 Contents Introduction Prerequisites Requirements Components Used Background Information Configure Network Diagram Relevant Configuration Verify Test case 1 Test case 2 Test case 3 Troubleshoot Introduction
Contents Introduction Prerequisites Requirements Components Used Background Information Configure Network Diagram Relevant Configuration Verify Test case 1 Test case 2 Test case 3 Troubleshoot Introduction
GRE Tunnel with VRF Configuration Example
 GRE Tunnel with VRF Configuration Example Document ID: 46252 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Caveats
GRE Tunnel with VRF Configuration Example Document ID: 46252 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Caveats
Configuring Easy Virtual Network Shared Services
 Configuring Easy Virtual Network Shared Services This chapter describes how to use route replication and redistribution to share services in an Easy Virtual Network (EVN). Finding Feature Information,
Configuring Easy Virtual Network Shared Services This chapter describes how to use route replication and redistribution to share services in an Easy Virtual Network (EVN). Finding Feature Information,
IPsec Virtual Tunnel Interfaces
 IPsec virtual tunnel interfaces (VTIs) provide a routable interface type for terminating IPsec tunnels and an easy way to define protection between sites to form an overlay network IPsec VTIs simplify
IPsec virtual tunnel interfaces (VTIs) provide a routable interface type for terminating IPsec tunnels and an easy way to define protection between sites to form an overlay network IPsec VTIs simplify
Chapter 6 Lab 6-4, BGP Route Reflectors and Route Filters
 Chapter 6 Lab 6-4, BGP Route Reflectors and Route Filters Topology Objectives Background Configure IBGP routers to use a route reflector and a simple route filter. The International Travel Agency maintains
Chapter 6 Lab 6-4, BGP Route Reflectors and Route Filters Topology Objectives Background Configure IBGP routers to use a route reflector and a simple route filter. The International Travel Agency maintains
EIGRP on SVTI, DVTI, and IKEv2 FlexVPN with the "IP[v6] Unnumbered" Command Configuration Example
![EIGRP on SVTI, DVTI, and IKEv2 FlexVPN with the IP[v6] Unnumbered Command Configuration Example EIGRP on SVTI, DVTI, and IKEv2 FlexVPN with the IP[v6] Unnumbered Command Configuration Example](/thumbs/92/108645128.jpg) EIGRP on SVTI, DVTI, and IKEv2 FlexVPN with the "IP[v6] Unnumbered" Command Configuration Example Document ID: 116346 Contributed by Michal Garcarz and Olivier Pelerin, Cisco TAC Engineers. Sep 18, 2013
EIGRP on SVTI, DVTI, and IKEv2 FlexVPN with the "IP[v6] Unnumbered" Command Configuration Example Document ID: 116346 Contributed by Michal Garcarz and Olivier Pelerin, Cisco TAC Engineers. Sep 18, 2013
Contents. Introduction. Prerequisites. Requirements
 Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations Verify Inheritence with EIGRP Named mode Route Replication with EIGRP name mode Routing Context
Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations Verify Inheritence with EIGRP Named mode Route Replication with EIGRP name mode Routing Context
MPLS VPN Half-Duplex VRF
 The feature provides scalable hub-and-spoke connectivity for subscribers of an Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service. This feature addresses the limitations of hub-and-spoke
The feature provides scalable hub-and-spoke connectivity for subscribers of an Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service. This feature addresses the limitations of hub-and-spoke
Segment Routing On Demand Next Hop for L3/L3VPN
 Segment Routing On Demand Next Hop for L3/L3VPN When redistributing routing information across domains, provisioning of multi-domain services (L2VPN & L3VPN) has its own complexity and scalability issues.
Segment Routing On Demand Next Hop for L3/L3VPN When redistributing routing information across domains, provisioning of multi-domain services (L2VPN & L3VPN) has its own complexity and scalability issues.
GRE and DM VPNs. Understanding the GRE Modes Page CHAPTER
 CHAPTER 23 You can configure Generic Routing Encapsulation (GRE) and Dynamic Multipoint (DM) VPNs that include GRE mode configurations. You can configure IPsec GRE VPNs for hub-and-spoke, point-to-point,
CHAPTER 23 You can configure Generic Routing Encapsulation (GRE) and Dynamic Multipoint (DM) VPNs that include GRE mode configurations. You can configure IPsec GRE VPNs for hub-and-spoke, point-to-point,
Basic Router Configuration
 This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
LAB5: OSPF IPv4. OSPF: Stub. Disclaimer
 Page1 LAB5: SPF IPv4 Disclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 LAB5: SPF IPv4 Disclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
LAB12: OSPF IPv6. OSPF: Redistribution. Disclaimer
 Page1 LAB12: OSPF IPv6 Disclaimer This Configuration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 LAB12: OSPF IPv6 Disclaimer This Configuration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
LAB15: EIGRP IPv4. LAB 15: Diagram. Disclaimer
 AB15: EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material is as
AB15: EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material is as
CCIE R&S LAB CFG H2/A5 (Jacob s & Jameson s)
 Contents Section 1 Layer 2 Technologies... 2 1.1 Jameson s Datacenter: Access port... 2 1.2 Jameson s Datacenter: Trunk ports... 4 1.3 Jameson s Datacenter: Link bundling... 5 1.4 Jameson s Branch Offices...
Contents Section 1 Layer 2 Technologies... 2 1.1 Jameson s Datacenter: Access port... 2 1.2 Jameson s Datacenter: Trunk ports... 4 1.3 Jameson s Datacenter: Link bundling... 5 1.4 Jameson s Branch Offices...
Intelligent WAN Multiple VRFs Deployment Guide
 Cisco Validated design Intelligent WAN Multiple VRFs Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deploying the Cisco IWAN Multiple VRFs...
Cisco Validated design Intelligent WAN Multiple VRFs Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deploying the Cisco IWAN Multiple VRFs...
Contents. Introduction. Prerequisites. Configure. Requirements. Components Used
 Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations CE1 CE2 PE1 PE2 Verify Case 1: Accepting and exchanging customer routes over MP-BGP Case 2: Leaking
Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations CE1 CE2 PE1 PE2 Verify Case 1: Accepting and exchanging customer routes over MP-BGP Case 2: Leaking
Cisco Virtual Office High-Scalability Design
 Solution Overview Cisco Virtual Office High-Scalability Design Contents Scope of Document... 2 Introduction... 2 Platforms and Images... 2 Design A... 3 1. Configure the ACE Module... 3 2. Configure the
Solution Overview Cisco Virtual Office High-Scalability Design Contents Scope of Document... 2 Introduction... 2 Platforms and Images... 2 Design A... 3 1. Configure the ACE Module... 3 2. Configure the
Border Gateway Protocol (BGP) Optimal Route Reflection
 Border Gateway Protocol (BGP) Optimal Route Reflection Contents Introduction Background Information Network Diagram Theory IOS-XR Implementation Configure Configuration Example MPLS Traffic-Engineering
Border Gateway Protocol (BGP) Optimal Route Reflection Contents Introduction Background Information Network Diagram Theory IOS-XR Implementation Configure Configuration Example MPLS Traffic-Engineering
Configuring Scalable Hub-and-Spoke MPLS VPNs
 Configuring Scalable Hub-and-Spoke MPLS VPNs Last Updated: December 15, 2011 This module explains how to ensure that virtual private network (VPN) clients that connect to the same provider edge (PE) router
Configuring Scalable Hub-and-Spoke MPLS VPNs Last Updated: December 15, 2011 This module explains how to ensure that virtual private network (VPN) clients that connect to the same provider edge (PE) router
Configuring Dynamic Addressing on the GGSN
 CHAPTER 13 This chapter describes how to configure dynamic IP addressing on the gateway GRPS support node (GGSN). Note Dynamic IP addressing is not supported for IPv6 and PPP PDP types. Therefore, the
CHAPTER 13 This chapter describes how to configure dynamic IP addressing on the gateway GRPS support node (GGSN). Note Dynamic IP addressing is not supported for IPv6 and PPP PDP types. Therefore, the
Reverse Route Injection
 Reverse Route Injection Last Updated: October 15, 2012 Reverse route injection (RRI) is the ability to automatically insert static routes in the routing process for those networks and hosts protected by
Reverse Route Injection Last Updated: October 15, 2012 Reverse route injection (RRI) is the ability to automatically insert static routes in the routing process for those networks and hosts protected by
Add Path Support in EIGRP
 The feature enables hubs in a single Dynamic Multipoint VPN (DMVPN) domain to advertise multiple best paths to connected spokes when the Enhanced Interior Gateway Routing Protocol (EIGRP) is the routing
The feature enables hubs in a single Dynamic Multipoint VPN (DMVPN) domain to advertise multiple best paths to connected spokes when the Enhanced Interior Gateway Routing Protocol (EIGRP) is the routing
Chapter 7 Lab 7-2, Using the AS_PATH Attribute
 Chapter 7 Topology Objectives Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter BGP routes based on their source AS numbers.
Chapter 7 Topology Objectives Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter BGP routes based on their source AS numbers.
Initial Configurations for OSPF over a Point to Point Link
 Initial onfigurations for OSPF over a Point to Point Link Document ID: 13687 ontents Introduction Prerequisites Requirements omponents Used onventions OSPF over a Point to Point Link with IP Addresses
Initial onfigurations for OSPF over a Point to Point Link Document ID: 13687 ontents Introduction Prerequisites Requirements omponents Used onventions OSPF over a Point to Point Link with IP Addresses
Routing Configuration Guide, Cisco IOS XE Everest a (Catalyst 9300 Switches)
 Routing Configuration Guide, Cisco IOS XE Everest 16.5.1a (Catalyst 9300 Switches) First Published: 2017-06-20 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA
Routing Configuration Guide, Cisco IOS XE Everest 16.5.1a (Catalyst 9300 Switches) First Published: 2017-06-20 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA
IPv6 Switching: Provider Edge Router over MPLS
 Multiprotocol Label Switching (MPLS) is deployed by many service providers in their IPv4 networks. Service providers want to introduce IPv6 services to their customers, but changes to their existing IPv4
Multiprotocol Label Switching (MPLS) is deployed by many service providers in their IPv4 networks. Service providers want to introduce IPv6 services to their customers, but changes to their existing IPv4
Cisco Group Encrypted Transport VPN
 Cisco Group Encrypted Transport VPN Q. What is Cisco Group Encrypted Transport VPN? A. Cisco Group Encrypted Transport is a next-generation WAN VPN solution that defines a new category of VPN, one that
Cisco Group Encrypted Transport VPN Q. What is Cisco Group Encrypted Transport VPN? A. Cisco Group Encrypted Transport is a next-generation WAN VPN solution that defines a new category of VPN, one that
IPv6 over DMVPN. Finding Feature Information
 This document describes how to implement the Dynamic Multipoint VPN for IPv6 feature, which allows users to better scale large and small IPsec Virtual Private Networks (VPNs) by combining generic routing
This document describes how to implement the Dynamic Multipoint VPN for IPv6 feature, which allows users to better scale large and small IPsec Virtual Private Networks (VPNs) by combining generic routing
Configuring WAN Backhaul Redundancy
 CHAPTER 7 This chapter describes how to configure WAN backhaul redundancy for cellular and WiMAX interfaces on the Cisco 1000 Series Connected Grid Routers (hereafter referred to as the Cisco CG-OS router).
CHAPTER 7 This chapter describes how to configure WAN backhaul redundancy for cellular and WiMAX interfaces on the Cisco 1000 Series Connected Grid Routers (hereafter referred to as the Cisco CG-OS router).
MPLS VPN C H A P T E R S U P P L E M E N T. BGP Advertising IPv4 Prefixes with a Label
 7 C H A P T E R S U P P L E M E N T This online supplement of Chapter 7 focuses on two important developments. The first one is Inter-Autonomous. Inter-Autonomous is a concept whereby two service provider
7 C H A P T E R S U P P L E M E N T This online supplement of Chapter 7 focuses on two important developments. The first one is Inter-Autonomous. Inter-Autonomous is a concept whereby two service provider
Chapter 3 Lab 3-4, OSPF over Frame Relay
 Chapter 3 Lab 3-4, OSPF over Frame Relay Topology Objectives Background Configure OSPF over Frame Relay. Use non-broadcast and point-to-multipoint OSPF network types. Modify default OSPF timers. You are
Chapter 3 Lab 3-4, OSPF over Frame Relay Topology Objectives Background Configure OSPF over Frame Relay. Use non-broadcast and point-to-multipoint OSPF network types. Modify default OSPF timers. You are
Connecting to a Service Provider Using External BGP
 Connecting to a Service Provider Using External BGP First Published: May 2, 2005 Last Updated: August 21, 2007 This module describes configuration tasks that will enable your Border Gateway Protocol (BGP)
Connecting to a Service Provider Using External BGP First Published: May 2, 2005 Last Updated: August 21, 2007 This module describes configuration tasks that will enable your Border Gateway Protocol (BGP)
OSPF Commands. Cisco IOS IP Command Reference, Volume 2 of 3: Routing Protocols IP2R-61
 OSPF Commands Use the commands in this chapter to configure and monitor the Open Shortest Path First (OSPF) routing protocol. For OSPF configuration information and examples, refer to the Configuring OSPF
OSPF Commands Use the commands in this chapter to configure and monitor the Open Shortest Path First (OSPF) routing protocol. For OSPF configuration information and examples, refer to the Configuring OSPF
Lab- Configuring Basic Single-Area OSPFv2
 Lab- onfiguring Basic Single-Area OSPFv2 Topology G0/0 G0/0 2013 isco and/or its affiliates. All rights reserved. This document is isco Public. Page 1 of 29 Addressing Table Objectives Device Interface
Lab- onfiguring Basic Single-Area OSPFv2 Topology G0/0 G0/0 2013 isco and/or its affiliates. All rights reserved. This document is isco Public. Page 1 of 29 Addressing Table Objectives Device Interface
LARGE SCALE DYNAMIC MULTIPOINT VPN
 LARGE SCALE DYNAMIC MULTIPOINT VPN NOVEMBER 2004 1 INTRODUCTION Presentation_ID 2004, Cisco Systems, Inc. All rights reserved. 2 Dynamic Multipoint VPN Facts Dynamic Multipoint VPN (DMVPN) can work with
LARGE SCALE DYNAMIC MULTIPOINT VPN NOVEMBER 2004 1 INTRODUCTION Presentation_ID 2004, Cisco Systems, Inc. All rights reserved. 2 Dynamic Multipoint VPN Facts Dynamic Multipoint VPN (DMVPN) can work with
Cisco Multicloud Portfolio: Cloud Connect
 Deployment Guide Cisco Multicloud Portfolio: Cloud Connect Private Network to Azure Transit Virtual Network October 2018 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public
Deployment Guide Cisco Multicloud Portfolio: Cloud Connect Private Network to Azure Transit Virtual Network October 2018 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public
MPLS VPN--Inter-AS Option AB
 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service provider
The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service provider
Flexible Dynamic Mesh VPN draft-detienne-dmvpn-00
 Flexible Dynamic Mesh VPN draft-detienne-dmvpn-00 Fred Detienne, Cisco Systems Manish Kumar, Cisco Systems Mike Sullenberger, Cisco Systems What is Dynamic Mesh VPN? DMVPN is a solution for building VPNs
Flexible Dynamic Mesh VPN draft-detienne-dmvpn-00 Fred Detienne, Cisco Systems Manish Kumar, Cisco Systems Mike Sullenberger, Cisco Systems What is Dynamic Mesh VPN? DMVPN is a solution for building VPNs
LAB24: EIGRP IPv6. EIGRP: Load Balancing. Disclaimer
 Page1 LAB24: EIGRP IPv6 Disclaimer This Configuration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 LAB24: EIGRP IPv6 Disclaimer This Configuration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
DMVPN for R&S CCIE Candidates Johnny Bass CCIE #6458
 DMVPN for R&S CCIE Candidates Johnny Bass CCIE #6458 BRKCCIE-3003 @CCIE6458 2015 Cisco and/or its affiliates. All rights reserved. Cisco Public About the Presenter Johnny Bass Networking industry since
DMVPN for R&S CCIE Candidates Johnny Bass CCIE #6458 BRKCCIE-3003 @CCIE6458 2015 Cisco and/or its affiliates. All rights reserved. Cisco Public About the Presenter Johnny Bass Networking industry since
LAB20: EIGRP IPv6. EIGRP: Summarization. Disclaimer
 Page1 LAB20: EIGRP IPv6 Disclaimer This Configuration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 LAB20: EIGRP IPv6 Disclaimer This Configuration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
ASA Has High CPU Usage Due to a Traffic Loop When VPN Clients Disconnect
 ASA Has High CPU Usage Due to a Traffic Loop When VPN Clients Disconnect Contents Introduction Prerequisites Requirements Components Used Background Information Problem: Packets Destined for a Disconnected
ASA Has High CPU Usage Due to a Traffic Loop When VPN Clients Disconnect Contents Introduction Prerequisites Requirements Components Used Background Information Problem: Packets Destined for a Disconnected
ARCHIVED DOCUMENT. - The topics in the document are now covered by more recent content.
 ARCHIVED DOCUMENT This document is archived and should only be used as a historical reference and should not be used for new deployments for one of the following reasons: - The topics in the document are
ARCHIVED DOCUMENT This document is archived and should only be used as a historical reference and should not be used for new deployments for one of the following reasons: - The topics in the document are
Information About Routing
 19 CHAPTER This chapter describes underlying concepts of how routing behaves within the adaptive security appliance, and the routing protocols that are supported. The chapter includes the following sections:,
19 CHAPTER This chapter describes underlying concepts of how routing behaves within the adaptive security appliance, and the routing protocols that are supported. The chapter includes the following sections:,
Routing Overview. Information About Routing CHAPTER
 21 CHAPTER This chapter describes underlying concepts of how routing behaves within the ASA, and the routing protocols that are supported. This chapter includes the following sections: Information About
21 CHAPTER This chapter describes underlying concepts of how routing behaves within the ASA, and the routing protocols that are supported. This chapter includes the following sections: Information About
Building the Routing Table. Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles
 Building the Routing Table Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles Introducing the Routing Table R1# show ip route Codes: C - connected,
Building the Routing Table Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles Introducing the Routing Table R1# show ip route Codes: C - connected,
The Radio Aware Routing feature offers the following benefits: Provides faster network convergence through immediate recognition of changes.
 Radio-Aware Routing (RAR) is a mechanism that uses radios to interact with the routing protocol OSPFv3 to signal the appearance, disappearance, and link conditions of one-hop routing neighbors. In a large
Radio-Aware Routing (RAR) is a mechanism that uses radios to interact with the routing protocol OSPFv3 to signal the appearance, disappearance, and link conditions of one-hop routing neighbors. In a large
Layer3 VPN with OSPF Protocol between CE-PE
 MPLS Layer3 VPN with OSPF Protocol between CE-PE Disclaimer This Configuration Guide is designed to assist members to enhance their skills in particular technology area. While every effort has been made
MPLS Layer3 VPN with OSPF Protocol between CE-PE Disclaimer This Configuration Guide is designed to assist members to enhance their skills in particular technology area. While every effort has been made
LAB16: Named EIGRP IPv4
 AB16: Named EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
AB16: Named EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Implementing Cisco IP Routing (ROUTE)
 Implementing Cisco IP Routing (ROUTE) Foundation Learning Guide Foundation learning for the ROUTE 642-902 Exam Diane Teare Cisco Press 800 East 96th Street Indianapolis, IN 46240 Implementing Cisco IP
Implementing Cisco IP Routing (ROUTE) Foundation Learning Guide Foundation learning for the ROUTE 642-902 Exam Diane Teare Cisco Press 800 East 96th Street Indianapolis, IN 46240 Implementing Cisco IP
Migrating from Dynamic Multipoint VPN Phase 2 to Phase 3: Why and How to Migrate to the Next Phase
 Migration Guide Migrating from Dynamic Multipoint VPN Phase 2 to Phase 3: Why and How to Migrate to the Next Phase This guide shows how a Dynamic Multipoint VPN (DMVPN) deployment can be migrated to make
Migration Guide Migrating from Dynamic Multipoint VPN Phase 2 to Phase 3: Why and How to Migrate to the Next Phase This guide shows how a Dynamic Multipoint VPN (DMVPN) deployment can be migrated to make
LAB8: OSPF IPv4. OSPF: Virtual Link. Disclaimer
 Page1 AB8: OSPF IPv4 Disclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 AB8: OSPF IPv4 Disclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED
 Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED Topology Objectives Background For IBGP peers to correctly exchange routing information, use the next-hop-self command with
Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED Topology Objectives Background For IBGP peers to correctly exchange routing information, use the next-hop-self command with
IPv6 Switching: Provider Edge Router over MPLS
 Multiprotocol Label Switching (MPLS) is deployed by many service providers in their IPv4 networks. Service providers want to introduce IPv6 services to their customers, but changes to their existing IPv4
Multiprotocol Label Switching (MPLS) is deployed by many service providers in their IPv4 networks. Service providers want to introduce IPv6 services to their customers, but changes to their existing IPv4
Configure SR-TE Policies
 This module provides information about segment routing for traffic engineering (SR-TE) policies, how to configure SR-TE policies, and how to steer traffic into an SR-TE policy. About SR-TE Policies, page
This module provides information about segment routing for traffic engineering (SR-TE) policies, how to configure SR-TE policies, and how to steer traffic into an SR-TE policy. About SR-TE Policies, page
DMVPN for R&S CCIE Candidates
 DMVPN for R&S CCIE Candidates Johnny Bass CCIE #6458 BRKCCIE-3003 @CCIE6458 2014 Cisco and/or its affiliates. All rights reserved. Cisco Public About the Presenter Johnny Bass Networking industry since
DMVPN for R&S CCIE Candidates Johnny Bass CCIE #6458 BRKCCIE-3003 @CCIE6458 2014 Cisco and/or its affiliates. All rights reserved. Cisco Public About the Presenter Johnny Bass Networking industry since
RIP. Table of Contents. General Information. Summary. Specifications
 RIP Document revision 1 (Wed Mar 24 12:32:12 GMT 2004) This document applies to V2.8 Table of Contents Table of Contents General Information Summary Specifications Related Documents Additional Documents
RIP Document revision 1 (Wed Mar 24 12:32:12 GMT 2004) This document applies to V2.8 Table of Contents Table of Contents General Information Summary Specifications Related Documents Additional Documents
CertifyMe. CertifyMe
 CertifyMe Number: 642-661 Passing Score: 800 Time Limit: 120 min File Version: 7.6 http://www.gratisexam.com/ CertifyMe-642-661 Exam A QUESTION 1 Exhibit: Certkiller router#show ip route Codes: C - connected,
CertifyMe Number: 642-661 Passing Score: 800 Time Limit: 120 min File Version: 7.6 http://www.gratisexam.com/ CertifyMe-642-661 Exam A QUESTION 1 Exhibit: Certkiller router#show ip route Codes: C - connected,
AS 100 AS 300. Lab -1 Private Communities - II .1 S1/2. Task 1. On R1: / / /24. Configure the above topology.
 Lab -1 Private Communities - II AS 100.1 R1 S1/2 12.1.1.0/24 S1/1.2 R2 S1/3 S1/3 13.1.1.0/24 23.1.1.0/24 S1/1.3 R3 S1/2 Lo0 6.6.6.0/24 Lo1 7.7.7.0/24 AS 300 Task 1 Configure the above topology. On R1:
Lab -1 Private Communities - II AS 100.1 R1 S1/2 12.1.1.0/24 S1/1.2 R2 S1/3 S1/3 13.1.1.0/24 23.1.1.0/24 S1/1.3 R3 S1/2 Lo0 6.6.6.0/24 Lo1 7.7.7.0/24 AS 300 Task 1 Configure the above topology. On R1:
Lab Configuring IPv4 Static and Default Routes (Solution)
 (Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
(Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
OSPF. About OSPF. CLI Book 1: Cisco ASA Series General Operations CLI Configuration Guide, 9.4 1
 This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Open Shortest Path First () routing protocol. About, page 1 Guidelines
This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Open Shortest Path First () routing protocol. About, page 1 Guidelines
Intelligent WAN Deployment Guide
 Cisco Validated design Intelligent WAN Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deployment Details...1 Configuring DMVPN Hub Router...2
Cisco Validated design Intelligent WAN Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deployment Details...1 Configuring DMVPN Hub Router...2
MPLS VPN Inter-AS Option AB
 First Published: December 17, 2007 Last Updated: September 21, 2011 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol
First Published: December 17, 2007 Last Updated: September 21, 2011 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol
Bidirectional Forwarding Detection
 Bidirectional Forwarding Detection This document describes how to enable the Bidirectional Forwarding Detection (BFD) protocol. BFD is a detection protocol designed to provide fast forwarding path failure
Bidirectional Forwarding Detection This document describes how to enable the Bidirectional Forwarding Detection (BFD) protocol. BFD is a detection protocol designed to provide fast forwarding path failure
MPLS VPN Carrier Supporting Carrier Using LDP and an IGP
 MPLS VPN Carrier Supporting Carrier Using LDP and an IGP Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) Carrier Supporting Carrier (CSC) enables one MPLS VPN-based service provider
MPLS VPN Carrier Supporting Carrier Using LDP and an IGP Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) Carrier Supporting Carrier (CSC) enables one MPLS VPN-based service provider
Lab- Troubleshooting Basic EIGRP for 1Pv4
 Lab- Troubleshooting Basic EIGRP for 1Pv4 Topology G0/0 G0/0 PC-A PC-C 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 27 Addressing Table efault Gateway
Lab- Troubleshooting Basic EIGRP for 1Pv4 Topology G0/0 G0/0 PC-A PC-C 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 27 Addressing Table efault Gateway
Advanced IPv6 Training Course. Lab Manual. v1.3 Page 1
 Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
How to Configure an IKEv1 IPsec VPN to an AWS VPN Gateway with BGP
 How to Configure an IKEv1 IPsec VPN to an AWS VPN Gateway with BGP If you are using the Amazon Virtual Private Cloud, you can transparently extend your local network to the cloud by connecting both networks
How to Configure an IKEv1 IPsec VPN to an AWS VPN Gateway with BGP If you are using the Amazon Virtual Private Cloud, you can transparently extend your local network to the cloud by connecting both networks
Dynamic Multipoint VPN between CradlePoint and Cisco Router Example
 Dynamic Multipoint VPN between CradlePoint and Cisco Router Example Summary This article describes how to setup a Dynamic GRE over IPSec VPN tunnel with NHRP (more commonly referred to as Dynamic Multipoint
Dynamic Multipoint VPN between CradlePoint and Cisco Router Example Summary This article describes how to setup a Dynamic GRE over IPSec VPN tunnel with NHRP (more commonly referred to as Dynamic Multipoint
LAB2: Named EIGRP IPv4
 Page1 AB2: Named EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 AB2: Named EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
EIGRP. About EIGRP. CLI Book 1: Cisco ASA Series General Operations CLI Configuration Guide, 9.7 1
 This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Enhanced Interior Gateway Routing Protocol (). About, page 1
This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Enhanced Interior Gateway Routing Protocol (). About, page 1
DMVPN to Group Encrypted Transport VPN Migration
 DMVPN to Group Encrypted Transport VPN Migration This document provides the steps for Dynamic Multipoint VPN (DMVPN) to Group Encrypted Transport VPN migration. DMVPN to Group Encrypted Transport VPN Migration
DMVPN to Group Encrypted Transport VPN Migration This document provides the steps for Dynamic Multipoint VPN (DMVPN) to Group Encrypted Transport VPN migration. DMVPN to Group Encrypted Transport VPN Migration
Adapted from the Synchronization example in g/case/studies/icsbgp4.html
 Adapted from the Synchronization example in http://www.cisco.com/en/us/docs/internetworkin g/case/studies/icsbgp4.html When an AS provides transit service to other ASs when there are non-bgp routers in
Adapted from the Synchronization example in http://www.cisco.com/en/us/docs/internetworkin g/case/studies/icsbgp4.html When an AS provides transit service to other ASs when there are non-bgp routers in
Chapter 4 Lab 4-2, Redistribution Between EIGRP and OSPF
 Chapter 4 Lab 4-2, Redistribution Between EIGRP and OSPF Topology Objectives Review EIGRP and OSPF configuration. Redistribute into EIGRP. Redistribute into OSPF. Summarize routes in EIGRP. Filter routes
Chapter 4 Lab 4-2, Redistribution Between EIGRP and OSPF Topology Objectives Review EIGRP and OSPF configuration. Redistribute into EIGRP. Redistribute into OSPF. Summarize routes in EIGRP. Filter routes
Configuring Stateful Interchassis Redundancy
 The Stateful Interchassis Redundancy feature enables you to configure pairs of devices to act as backups for each other. This module describes conceptual information about and tasks for configuring stateful
The Stateful Interchassis Redundancy feature enables you to configure pairs of devices to act as backups for each other. This module describes conceptual information about and tasks for configuring stateful
Cisco Service Advertisement Framework Deployment Guide
 Cisco Service Advertisement Framework Deployment Guide What You Will Learn Cisco Service Advertisement Framework (SAF) is a network-based, scalable, bandwidth-efficient approach to service advertisement
Cisco Service Advertisement Framework Deployment Guide What You Will Learn Cisco Service Advertisement Framework (SAF) is a network-based, scalable, bandwidth-efficient approach to service advertisement
Implementing Cisco Secure Mobility Solutions
 Implementing Cisco Secure Mobility Solutions Dumps Available Here at: /cisco-exam/300-209-dumps.html Enrolling now you will get access to 269 questions in a unique set of 300-209 dumps Question 1 Which
Implementing Cisco Secure Mobility Solutions Dumps Available Here at: /cisco-exam/300-209-dumps.html Enrolling now you will get access to 269 questions in a unique set of 300-209 dumps Question 1 Which
Real4Test. Real IT Certification Exam Study materials/braindumps
 Real4Test http://www.real4test.com Real IT Certification Exam Study materials/braindumps Exam : 400-101 Title : CCIE Routing and Switching Written Exam v5.1 Vendor : Cisco Version : DEMO Get Latest & Valid
Real4Test http://www.real4test.com Real IT Certification Exam Study materials/braindumps Exam : 400-101 Title : CCIE Routing and Switching Written Exam v5.1 Vendor : Cisco Version : DEMO Get Latest & Valid
DYNAMIC MULTIPOINT VPN SPOKE TO SPOKE DIRECT TUNNELING
 DYNAMIC MULTIPOINT VPN SPOKE TO SPOKE DIRECT TUNNELING NOVEMBER 2004 1 Direct Spoke To Spoke Tunnels Initially, spoke to spoke traffic can only travel via the hub In DMVPN, spokes can send packets directly
DYNAMIC MULTIPOINT VPN SPOKE TO SPOKE DIRECT TUNNELING NOVEMBER 2004 1 Direct Spoke To Spoke Tunnels Initially, spoke to spoke traffic can only travel via the hub In DMVPN, spokes can send packets directly
Network Layer Week 5. Module : Computer Networks Lecturer: Lucy White Office : 324
 Network Layer Week 5 Module : Computer Networks Lecturer: Lucy White lbwhite@wit.ie Office : 324 1 Network Layer Network Layer Protocols Common Network Layer Protocols Internet Protocol version 4 (IPv4)
Network Layer Week 5 Module : Computer Networks Lecturer: Lucy White lbwhite@wit.ie Office : 324 1 Network Layer Network Layer Protocols Common Network Layer Protocols Internet Protocol version 4 (IPv4)
How to Configure an IKEv1 IPsec VPN to an AWS VPN Gateway with BGP
 How to Configure an IKEv1 IPsec VPN to an AWS VPN Gateway with BGP If you are using the Amazon Virtual Private Cloud, you can transparently extend your local network to the cloud by connecting both networks
How to Configure an IKEv1 IPsec VPN to an AWS VPN Gateway with BGP If you are using the Amazon Virtual Private Cloud, you can transparently extend your local network to the cloud by connecting both networks
Chapter 4 Lab 4-2, Controlling Routing Updates. Topology. Objectives. CCNPv7 ROUTE
 Chapter 4 Lab 4-2, Controlling Routing Updates Topology Objectives Filter routes using a distribute list and ACL. Filter routes using a distribute list and prefix list. Filter redistributed routes using
Chapter 4 Lab 4-2, Controlling Routing Updates Topology Objectives Filter routes using a distribute list and ACL. Filter routes using a distribute list and prefix list. Filter redistributed routes using
Lab Configuring Per-Interface Inter-VLAN Routing (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
Troubleshooting LSP Failure in MPLS VPN
 Troubleshooting LSP Failure in MPLS VPN Document ID: 23565 Contents Introduction Prerequisites Requirements Components Used Conventions Network Diagram Router Configurations Problem Cause of the LSP Failure
Troubleshooting LSP Failure in MPLS VPN Document ID: 23565 Contents Introduction Prerequisites Requirements Components Used Conventions Network Diagram Router Configurations Problem Cause of the LSP Failure
Advanced DMVPN Designs
 Advanced DMVPN Designs Alex HONORÉ Cisco TAC ahonore@cisco.com Session Agenda DMVPN refresher Review of Phase 3 logic Per-Tunnel Quality of Service DMVPN virtualization MPLS over DMVPN Multicast over DMVPN
Advanced DMVPN Designs Alex HONORÉ Cisco TAC ahonore@cisco.com Session Agenda DMVPN refresher Review of Phase 3 logic Per-Tunnel Quality of Service DMVPN virtualization MPLS over DMVPN Multicast over DMVPN
