1 INTRODUCTION 2 PROBLEM STATEMENT
|
|
|
- Clara Burns
- 5 years ago
- Views:
Transcription
1 EVACUATION SIMULATION WITH LIMITED CAPACITY SINKS An evolutionary approach to solve the shelter allocation and capacity assignment problem in a multi-agent evacuation simulation Gunnar Flötteröd Transport and Mobility Laboratory, EPFL - Ecole Polytechnique Fédérale de Lausanne, Lausanne, Switzerland gunnar.floetteroed@epfl.ch Gregor Lämmel Transport Systems Planning and Transport Telematics, Berlin Institute of Technology, Berlin, Germany laemmel@vsp.tu-berlin.de Keywords: Abstract: evacuation, shelter allocation, shelter capacity assignment, iterative learning, Nash equilibrium, system optimum, multi-agent simulation. We heuristically solve an evacuation problem with limited capacity shelters. An evolutionary learning algorithm is developed for the combined route- and shelter-assignment problem. It is complemented with a heuristic method for the fair minimization of shelter capacities. Different behavioral assumptions fair vs. globally optimal ) are investigated. The proposed approaches are discussed in the context of a real-world tsunami evacuation problem. 1 INTRODUCTION The evacuation of whole cities or even regions is a problem of substantial practical relevance, which is demonstrated by recent events such as the evacuation of Houston because of Hurricane Rita or the evacuation of coastal cities in the case of tsunamis. Important tools for the planning of organized reactions to such events are model-based simulation systems. The general evacuation problem is to minimize the egress time of an endangered region or building by assigning a feasible escape route and destination to every evacuee. This problem is complex because of congestion effects that inevitably occur when many evacuees enter the transportation facilities (roads, hallways, stairways) at once. In some evacuation scenarios, there exist secure areas of limited capacity within the evacuation zone, such as shelter buildings in tsunami prone areas. Concrete applications of mathematical programming techniques to the evacuee shelter allocation problem can be found in (Sherali et al., 1991; Peng, 2006). This paper deploys a detailed microsimulation for the representation, analysis, and optimization of pedestrian evacuation dynamics for a tsunami situation in a large coastal metropolitan area. Building on existing routing strategies (Lämmel and Flötteröd, 2009), it provides new solutions to (i) the combined route and shelter assignment problem and (ii) the shelter capacity assignment problem, considering both fair and optimal assignment rules. The added value of the agent-based approach is its natural representation of individual travelers as software agents that interact in a simulated version of the real world (a virtual environment). This is an advantage over analytical models in that it allows (at least technically) for a much higher model resolution. However, it comes at the price of greater difficulties in the mathematical treatment of the problem. The optimization results presented in this article are therefore only of an approximate nature. 2 PROBLEM STATEMENT In a first step, we investigate different strategies to assign routes and destinations (shelters) to evacuees. In a second step, we identify optimal dimensions of the shelters. Overall, we consider two different objectives: Fairness. No evacuee will agree to take an obvious detour or to select an obviously faraway shelter instead of a nearby one. This requires to identify route and shelter assignments that are fair in that no evacuee can obviously gain by switching to a different
2 route or shelter. It corresponds to a Nash equilibrium of all evacuation strategies in the population. Efficiency. It is desirable to evacuate the system as quickly as possible. While a Nash strategy has the obvious and important advantage of general acceptance, it may be suboptimal in this regard because some evacuees may do great damage to others by blocking their ways/shelters. We therefore identify approximations of optimal evacuation strategies as benchmarks to which fair solutions can be compared. An important topic for future research is to combine both approaches into evacuation strategies that are more efficient than Nash equilibria without introducing obvious levels of unfairness. 2.1 Simulation framework We model the urban evacuation region and the population of evacuees with a multi-agent simulation, where every single person is individually represented. For this purpose, the MATSim simulation framework is adopted (MATSim, 2010). MATSim is designed for the computation of transport equilibria, and hence it can be immediately deployed for the computation of Nash evacuation strategies. Some adjustments are necessary for approximately optimal strategies. MATSim allows for adjustments in the different choice dimensions of a simulated traveler through modules, where, typically, one module is responsible for one choice dimension. In our application, this requires to specify four modules: (1) Nash route choice, (2) Nash destination (shelter) choice, (3) optimal route choice, (4) optimal shelter choice. MATSim computes approximate Nash equilibria by iterating best-response behavior: in every iteration, a fraction of the travelers recalculates a route or a destination based on what would have been best in the previous iteration, assuming that the behavior of all other agents stays unchanged. After this replanning, the resulting plans of all travelers are simultaneously executed in the mobility simulation and new performance measures are computed. This process is repeated many times. Once it stabilizes, no agent can substantially improve through a route or destination replanning, and an approximate Nash equilibrium is obtained. An alternative assignment logic is to not compute best responses in every iteration but cooperative behavior that improves the situation of the population as a whole. The more involved realization of such behavior follows essentially the same simulation logic as the Nash assignment, but with a modified cost function being presented to the agents. 2.2 Network modeling The evacuation network consists of a set of nodes that are connected by a set of directed links. Sources (origins) as well as sinks (destinations, shelters) are associated with respective node subsets. Every destination d has a capacity c d that represents the maximum number of evacuees it can shelter. Destination nodes may also be located at the boundary of the endangered area, in which case they do not provide a limited shelter but access to a safe region, which is modeled by assigning them an unlimited capacity. We consider a pedestrian simulation scenario on a road network, where the intersections correspond to nodes and the street segments connecting the intersections are modeled through links. Basic pedestrian traffic flow dynamics are captured through a limited number of link parameters: outflow capacity (maximum number of pedestrians the link can emit per time unit), space capacity (maximum number of pedestrians in the link), and maximum velocity (in uncongested conditions). Note that this formalism can be immediately transferred to vehicular evacuation problems (Cetin et al., 2003). 3 ROUTE ASSIGNMENT Given that every evacuee n = 1...N is assigned to a shelter d(n), the route assignment problem is to find a feasible and in some sense best route from that evacuee s origin s(n) to her shelter. 3.1 Nash equilibrium assignment In the given context, a Nash equilibrium describes a situation where no evacuee can gain by unilaterally deviating from her current route (Nash, 1951). Since a Nash equilibrium means that nobody has an incentive to make a change, it can be considered as a socially acceptable and hence implementable evacuation strategy. In a multi-agent (evacuation) simulation, the solution can be moved towards a Nash equilibrium through iterative learning (Gawron, 1998). As described above, such an algorithm starts with a given (routing) strategy for every agent, and then adjusts this strategy through some trial and error mechanism. In the given evacuation context, strategies are only evaluated based on their travel times. Formally, the real-valued time is discretized into K segments ( bins ), which are indexed by k = 0...K 1. The time-dependent link travel time when
3 Algorithm 1 Nash equilibrium routing 1. initialize τ a (k) with the free-flow travel time for all links a and time steps k 2. repeat for many iterations: (a) recalculate routes based on time-dependent link costs τ a (k) (b) simulate agent movements, obtain new τ a (k) for all a and k entering link a in time step k is denoted by τ a (k). Alg. 1 drafts the Nash-equilibrium routing logic. 3.2 System optimal assignment A system optimal routing solution minimizes the total travel time in the system. Classical solutions to this problem apply mathematical programming techniques, which are based on the theory of dynamic network flows. The foundations of these techniques have been laid in (Ford and Fulkerson, 1962), and dynamic flow models have been applied to evacuation problems from the early 1980s on (see, e.g., (Chalmet et al., 1982)). In the multi-agent domain, an approximate system optimum (SO) can be found through an iterative learning approach that is closely related to the simulation of a Nash equilibrium as described above (Lämmel and Flötteröd, 2009). The only difference to the Nash routing logic given in Algorithm 1 is that the travel time based on which agents evaluate their routes is replaced by the marginal travel time (Peeta and Mahmassani, 1995). The marginal travel time of a link is the amount by which the total system travel time changes if one additional traveler enters that link. It is the sum of the cost experienced by the added traveler (τ a (k)) and the cost imposed on all other travelers. The latter is denoted as the time-dependent social cost. Letting each evacuee individually minimize her marginal travel time implicitly enforces a cooperative behavior that also minimizes the total system travel time. This maximizes the number of evacuees who have reached their destinations in each time step, which in turn minimizes the egress time (Jarvis and Ratliff, 1982). 4 SHELTER ASSIGNMENT The shelter assignment problem is to identify, for each evacuee, if this evacuee should access a shelter or not and, given that a shelter is accessed, to decide which Algorithm 2 Nash shelter allocation 1. initialize routes and destinations for all agents 2. repeat many times (a) load all agents on the network (b) extract link travel times (c) for every agent n = 1...N, do with P replan : with P reroute, compute a new route from s(n) to d(n). with P move, i. randomly select a non-full shelter d ii. compute the benefit of a move: δ = c s(n)d(n) c s(n)d iii. if δ > 0, assign d as the new destination to n and re-route n with P switch, i. randomly select n from {1,...,N} ii. compute the minimum benefit of a switch: δ = min(c s(n)d(n) c s(n)d(n ),c s(n )d(n ) c s(n )d(n)) iii. if δ > 0, then switch the destinations of n and n and re-route both agents shelter. Again, both a Nash and an SO approach are possible. 4.1 Nash shelter assignment We extend the individual best-response logic to a pairwise best response, where for every agent n that replans its shelter a switching partner n in another shelter is randomly selected, and both agents switch their shelters if and only if both benefit from this switch. This decision is made based on the expected travel time of a best-response re-routing to each new destination; the resulting routes are also adopted in the case of an accomplished switch. The iterative simulation conducts a shelter switch with a certain probability P switch, and it also maintains the option of a plain route recomputation with P reroute. Algorithm 2 defines the details of this logic. The origin of agent n is denoted by s(n) and its destination by d(n). The cost c s(n)d(n) corresponds to the travel time from s(n) to d(n). Step 1., 2.(a), 2.(b) and the first step of 2.(c) are symmetric to the routing logic of Algorithm 1. An agent moves with probability P replan P move to a non-full shelter if it would benefit from that move. With probability P replan P switch, two agents switch their shelters if both of them would benefit.
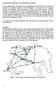
4 4.2 SO shelter assignment Technically, the SO shelter assignment does not function differently from the Nash shelter assignment, only that two agents now agree to switch their shelters if this reduces the total travel time in the system. To decide this, the expected change in marginal travel times is evaluated before and after the switch. Algorithm 2 is still applicable with the following modifications: c s(n)d(n) now represents agent n s marginal travel time, cf. Section 3.2. A switch is only performed if both agents would benefit from it. Therefore, the switching benefit δ of Step 2. (c) ii. needs to be computed as c s(n)d(n) + c s(n )d(n ) c s(n)d(n ) c s(n )d(n). 5 SHELTER CAPACITY ASSIGNMENT The shelter capacity assignment problem is to minimize the total shelter capacity subject to the constraint that no evacuee takes damage from being neither able to reach the safe area nor to enter a shelter because of lacking capacity. That is, a configuration is required where only those evacuees are assigned to shelters who would not make it to the safe region otherwise. 5.1 Shelter capacity assignment subject to Nash constraints We base our approach on the Nash simulation logic of Algorithm 2. If there is more shelter capacity than strictly needed, there are likely to be agents in the shelters that could also make it to the safe region (because it can be assumed that for many such agents the shelter still is closer than the safe area). It is not feasible to ex post remove these agents from the shelters and to constrain the shelter capacities accordingly because this would change the travel times and hence the survival chances of the needy agents. The shelter capacities therefore need to be gradually adjusted during the iterations. This effect is achieved by evaluating, in every iteration, the space occupied in every single shelter by agents that would also have made it to the safe region. If this surplus is vanishing, the shelter is urgently needed, and its capacity is increased by a relative amount (say, 5 percent). If, on the other hand, this surplus is substantial, the shelter is too large, and it is shrunk by a relative amount (say, again, 5 percent) of its surplus capacity. Algorithm 3 Heuristic Nash shelter allocation and capacity assignment 1. initialize routes and destinations for all agents 2. repeat many times (a) load all agents on the network (b) extract link travel times (c) for every agent n = 1...N, replan with P replan its route/destination; give strict preference to needy agents in shelter assignment (d) for every shelter d = 1...D, do: o(d) = c(d) N n=1 x nd + N n=1 ŷn if o(d) > 0, decrease c(d) by min(o(d),q c(d)) and re-route non-needy agents to supershelter if necessary; else increase c(d) by q c(d)) This mechanism, in combination with a strict preference for needy agents in the shelter allocation, eventually leads to a configuration where all available shelter capacity is allocated to needy agents, given otherwise fair Nash equilibrium conditions. Algorithm 3 gives an overview. The variable x nd indicates the allocation of agent n to shelter d, i.e., x nd = 1 d(n) = d. y n indicates if agent n has enough time to evacuate to the super shelter. If agent n has enough time to evacuate to the super shelter y n = 1 and y n = 0 otherwise. ŷ n is the estimated value of y n based on the experienced travel costs from previous iteration. q denotes the relative amount by which the capacity of a shelter can change at most. The super-shelter represents the entire safe area. 5.2 Shelter capacity assignment subject to SO constraints The only change when going from a shelter capacity assignment subject to Nash constraints to one subject to SO constraints is that the route choice and shelter switching behavior of all re-planning agents is conducted according to the SO logic described in Subsections 3.2 and 4.2. The conditions for shelter capacity decreases and increases in the SO case are the same as for the Nash case given in in Algorithm 3. 6 EXPERIMENTS The Indonesian city of Padang, located at the West Coast of Sumatra Island, is exposed to earth quake
5 meter with 2000 iterations takes between 05:30 h (Run 1) and 10:30 h (Run 4) on a 2.66 GHz CPU running 64 bit Java on Linux. The memory consumption is below 3 GB in all experiments. Evacuation time Run 1 Run 2 Run 3 Run avg. evacuation time in s triggered tsunamis. The evacuation street network consist of approx unidirectional links and nodes. There are in total evacuees. This corresponds to the number of persons living in the evacuation area. 42 hypothetical shelter buildings with a total capacity of roughly evacuees are placed in the network. A sketch of the network including the shelters is given in Figure 1. The grayshaded area has to be evacuated iteration 1,500 2,000 Figure 2: Average evacuation time per agent versus iteration number. At the beginning of all runs, the agents are assigned randomly to the shelters. Figure 2 shows the average evacuation time per agent over the iteration number. Run 1 shows that a Nash shelter assignment leads to considerably better evacuation times than a random shelter assignment. Adding the shelter capacity assignment reduces the average evacuation times further (Run 2). However, this comes at the cost of a drastic increase in shelter capacities, which is shown in Figure 3. Figure 1: Map of the evacuation area. Shelter utilization 8,000 Run 1 implements the Nash equilibrium routing and shelter allocation. Run 2 implements the Nash equilibrium routing and shelter allocation and the shelter capacity assignment. Run 3 implements the SO routing and shelter allocation. Run 4 implements the SO routing and shelter allocation and the shelter capacity assignment. These runs are performed with a 10% sample of the population. The shelter capacities and network flow parameters are accordingly scaled down to 10%. This procedure saves computing time while staying reasonably realistic. With this setup, a simulation number of agents in shelters We conduct four different simulations. 7,000 Run 1 Run 2 Run 3 Run 4 6,000 5,000 4,000 3,000 2, iteration 1,500 2,000 Figure 3: Change of the shelters total utilization over the learning iterations.
6 The SO in Run 3 and Run 4 is realized by adding social costs to the travel time on each link. Figure 2 reveals that the SO experiments Run 3 and Run 4 yield higher travel times than the Nash runs. However, the SO runs result in a substantially lower shelter utilization, cf. Figure 3. The higher travel times in the SO runs are likely to result from those travelers that are kept out of the shelters and hence have to take longer routes to the safe city boundaries. In theory, at least Run 3 should outperform Run 1. The fact that this is not the case is due to the approximate nature of the deployed algorithms, which clearly need further attention. 7 DISCUSSION AND SUMMARY The safest strategy for a tsunami-threatened city like Padang would arguably be to build a tsunami proof shelter for every single person. However, this would exceed any financial resources. The relevant question thus is to identify which shelters are actually needed by persons who cannot be evacuated out of the city in time. The proposed algorithms help to identify these shelters and their capacities under different behavioral assumptions. An important result of the simulation studies is that the required shelter capacity in the Nash equilibrium case is much higher than in the SO case. If one wanted to achieve the highest benefits with the least effort, one could implement the shelter configuration of Run 4 and distribute some kind of tickets to the people that are allowed to enter a shelter. Those tickets could be preferably handed out to the most vulnerable people like the elderly or pregnant women. Summarizing, a learning framework that approximately solves the shelter allocation and capacity optimization problem is presented and tested on a realworld scenario. The learning framework can be configured either to attain an approximate Nash equilibrium, where individual travel times are minimized non-cooperatively, or an approximate system optimum, where the global travel time is minimized in a cooperative manner. The experiments show that both approaches yield reasonable results and that substantial savings in shelter capacity are possible if the evacuation behavior can be influenced to deviate from a perfectly fair Nash equilibrium towards a system optimum. In future work, the proposed algorithms could be extended to also identify appropriate shelter locations. This could be realized by starting with a high number of shelter buildings, followed by a successive removal of underutilized shelters. Another interesting topic for further research would be to investigate the relative effect of capacity improvements in the transportation system when compared to investments in increased shelter capacities. ACKNOWLEDGEMENTS This project was funded in part by the German Ministry for Education and Research (BMBF) under grants 03G0666E ( last mile ) and 03NAPI4 ( Advest ). REFERENCES Cetin, N., Burri, A., and Nagel, K. (2003). A large-scale agent-based traffic microsimulation based on queue model. In Proceedings of the 3rd Swiss Transport Research Conference, Monte Verita/Ascona, Switzerland. Chalmet, L., Francis, R., and Saunders, P. (1982). Network models for building evacuation. Management Science, 28: Ford, L. and Fulkerson, D. (1962). Princeton University Press. Flows in Networks. Gawron, C. (1998). An iterative algorithm to determine the dynamic user equilibrium in a traffic simulation model. International Journal of Modern Physics C, 9(3): Jarvis, J. and Ratliff, H. (1982). Some equivalent objectives for dynamic network flow problems. Management Science, 28: Lämmel, G. and Flötteröd, G. (2009). Towards system optimum: Finding optimal routing strategies in timetependent networks for large-scale evacuation problems. volume 5803 of LNCS (LNAI), pages , Berlin Heidelberg. Springer. MATSim (accessed 2010). MATSim web site. Nash, J. (1951). Non-cooperative games. Annals of Mathematics, 54(2): Peeta, S. and Mahmassani, H. (1995). System optimal and user equilibrium time-dependent traffic assignment in congested networks. Annals of Operations Research, 60: Peng, L. (2006). A DYNAMIC NETWORK FLOW OP- TIMIZATION FOR LARGE-SCALE EMERGENCY EVACUATION. PhD thesis, City University of Hong Kong. Sherali, H., Carter, T., and Hobeika, A. (1991). A locationallocation model and algorithm for evacuation planning under hurricane/flood conditions. Transportation Research Part B: Methodological, 25(6):
Different Optimal Solutions in Shared Path Graphs
 Different Optimal Solutions in Shared Path Graphs Kira Goldner Oberlin College Oberlin, OH 44074 (610) 324-3931 ksgoldner@gmail.com ABSTRACT We examine an expansion upon the basic shortest path in graphs
Different Optimal Solutions in Shared Path Graphs Kira Goldner Oberlin College Oberlin, OH 44074 (610) 324-3931 ksgoldner@gmail.com ABSTRACT We examine an expansion upon the basic shortest path in graphs
Optimal Egress Time Calculation and Path Generation for Large. Evacuation Networks
 Optimal Egress Time Calculation and Path Generation for Large Evacuation Networks Mukesh Rungta, Gino J. Lim and M. Reza Baharnemati July 3, 2012 Abstract Finding the optimal clearance time and deciding
Optimal Egress Time Calculation and Path Generation for Large Evacuation Networks Mukesh Rungta, Gino J. Lim and M. Reza Baharnemati July 3, 2012 Abstract Finding the optimal clearance time and deciding
Nash equilibria in Voronoi Games on Graphs
 Nash equilibria in Voronoi Games on Graphs Christoph Dürr, Nguyễn Kim Thắng (Ecole Polytechnique) ESA, Eilat October 07 Plan Motivation : Study the interaction between selfish agents on Internet k players,
Nash equilibria in Voronoi Games on Graphs Christoph Dürr, Nguyễn Kim Thắng (Ecole Polytechnique) ESA, Eilat October 07 Plan Motivation : Study the interaction between selfish agents on Internet k players,
THE EFFECT OF SEGREGATION IN NON- REPEATED PRISONER'S DILEMMA
 THE EFFECT OF SEGREGATION IN NON- REPEATED PRISONER'S DILEMMA Thomas Nordli University of South-Eastern Norway, Norway ABSTRACT This article consolidates the idea that non-random pairing can promote the
THE EFFECT OF SEGREGATION IN NON- REPEATED PRISONER'S DILEMMA Thomas Nordli University of South-Eastern Norway, Norway ABSTRACT This article consolidates the idea that non-random pairing can promote the
Simple Channel-Change Games for Spectrum- Agile Wireless Networks
 1 Proceedings of Student/Faculty Research Day, CSIS, Pace University, May 5 th, 26 Simple Channel-Change Games for Spectrum- Agile Wireless Networks Roli G. Wendorf and Howard Blum Abstract The proliferation
1 Proceedings of Student/Faculty Research Day, CSIS, Pace University, May 5 th, 26 Simple Channel-Change Games for Spectrum- Agile Wireless Networks Roli G. Wendorf and Howard Blum Abstract The proliferation
The representation and implementation of time-dependent inundation in large-scale microscopic evacuation simulations
 The representation and implementation of time-dependent inundation in large-scale microscopic evacuation simulations Gregor Lämmel, Dominik Grether, Kai Nagel Transport Systems Planning and Transport Telematics,
The representation and implementation of time-dependent inundation in large-scale microscopic evacuation simulations Gregor Lämmel, Dominik Grether, Kai Nagel Transport Systems Planning and Transport Telematics,
Stability of Marriage and Vehicular Parking
 Stability of Marriage and Vehicular Parking Daniel Ayala, Ouri Wolfson, Bo Xu, Bhaskar DasGupta, and Jie Lin University of Illinois at Chicago Abstract. The proliferation of mobile devices, location-based
Stability of Marriage and Vehicular Parking Daniel Ayala, Ouri Wolfson, Bo Xu, Bhaskar DasGupta, and Jie Lin University of Illinois at Chicago Abstract. The proliferation of mobile devices, location-based
Metaheuristic Development Methodology. Fall 2009 Instructor: Dr. Masoud Yaghini
 Metaheuristic Development Methodology Fall 2009 Instructor: Dr. Masoud Yaghini Phases and Steps Phases and Steps Phase 1: Understanding Problem Step 1: State the Problem Step 2: Review of Existing Solution
Metaheuristic Development Methodology Fall 2009 Instructor: Dr. Masoud Yaghini Phases and Steps Phases and Steps Phase 1: Understanding Problem Step 1: State the Problem Step 2: Review of Existing Solution
Handling Multi Objectives of with Multi Objective Dynamic Particle Swarm Optimization
 Handling Multi Objectives of with Multi Objective Dynamic Particle Swarm Optimization Richa Agnihotri #1, Dr. Shikha Agrawal #1, Dr. Rajeev Pandey #1 # Department of Computer Science Engineering, UIT,
Handling Multi Objectives of with Multi Objective Dynamic Particle Swarm Optimization Richa Agnihotri #1, Dr. Shikha Agrawal #1, Dr. Rajeev Pandey #1 # Department of Computer Science Engineering, UIT,
Optimal Channel Selection for Cooperative Spectrum Sensing Using Coordination Game
 2012 7th International ICST Conference on Communications and Networking in China (CHINACOM) Optimal Channel Selection for Cooperative Spectrum Sensing Using Coordination Game Yuhua Xu, Zhan Gao and Wei
2012 7th International ICST Conference on Communications and Networking in China (CHINACOM) Optimal Channel Selection for Cooperative Spectrum Sensing Using Coordination Game Yuhua Xu, Zhan Gao and Wei
COOPERATION-AWARE TOPOLOGY CONTROL
 COOPERATION-AWARE TOPOLOGY CONTROL Vivek Srivastava Arlington, VA. USA. Ramakant Komali Blacksburg, VA. USA. Allen B. MacKenzie Blacksburg, VA. USA. Luiz A. DaSilva Arlington, VA. USA. ABSTRACT In ad hoc
COOPERATION-AWARE TOPOLOGY CONTROL Vivek Srivastava Arlington, VA. USA. Ramakant Komali Blacksburg, VA. USA. Allen B. MacKenzie Blacksburg, VA. USA. Luiz A. DaSilva Arlington, VA. USA. ABSTRACT In ad hoc
Re-routing Agents in an Abstract Traffic Scenario
 Re-routing Agents in an Abstract Traffic Scenario Ana L.C. Bazzan and Franziska Klügl 1 Instituto do Informatica, UFRGS Porto Alegre, Brazil bazzan@inf.ufrgs.br 2 Dep. of Artificial Intelligence, University
Re-routing Agents in an Abstract Traffic Scenario Ana L.C. Bazzan and Franziska Klügl 1 Instituto do Informatica, UFRGS Porto Alegre, Brazil bazzan@inf.ufrgs.br 2 Dep. of Artificial Intelligence, University
Optimal Detector Locations for OD Matrix Estimation
 Optimal Detector Locations for OD Matrix Estimation Ying Liu 1, Xiaorong Lai, Gang-len Chang 3 Abstract This paper has investigated critical issues associated with Optimal Detector Locations for OD matrix
Optimal Detector Locations for OD Matrix Estimation Ying Liu 1, Xiaorong Lai, Gang-len Chang 3 Abstract This paper has investigated critical issues associated with Optimal Detector Locations for OD matrix
Principles of Network Economics
 Hagen Bobzin Principles of Network Economics SPIN Springer s internal project number, if known unknown Monograph August 12, 2005 Springer Berlin Heidelberg New York Hong Kong London Milan Paris Tokyo Contents
Hagen Bobzin Principles of Network Economics SPIN Springer s internal project number, if known unknown Monograph August 12, 2005 Springer Berlin Heidelberg New York Hong Kong London Milan Paris Tokyo Contents
Network Improvement for Equilibrium Routing
 Network Improvement for Equilibrium Routing UMANG BHASKAR University of Waterloo and KATRINA LIGETT California Institute of Technology Routing games are frequently used to model the behavior of traffic
Network Improvement for Equilibrium Routing UMANG BHASKAR University of Waterloo and KATRINA LIGETT California Institute of Technology Routing games are frequently used to model the behavior of traffic
Column Generation Method for an Agent Scheduling Problem
 Column Generation Method for an Agent Scheduling Problem Balázs Dezső Alpár Jüttner Péter Kovács Dept. of Algorithms and Their Applications, and Dept. of Operations Research Eötvös Loránd University, Budapest,
Column Generation Method for an Agent Scheduling Problem Balázs Dezső Alpár Jüttner Péter Kovács Dept. of Algorithms and Their Applications, and Dept. of Operations Research Eötvös Loránd University, Budapest,
Three-Dimensional Off-Line Path Planning for Unmanned Aerial Vehicle Using Modified Particle Swarm Optimization
 Three-Dimensional Off-Line Path Planning for Unmanned Aerial Vehicle Using Modified Particle Swarm Optimization Lana Dalawr Jalal Abstract This paper addresses the problem of offline path planning for
Three-Dimensional Off-Line Path Planning for Unmanned Aerial Vehicle Using Modified Particle Swarm Optimization Lana Dalawr Jalal Abstract This paper addresses the problem of offline path planning for
THE ADJACENT VEHICLES QUERY ALGORITHM OF MICROSCOPIC TRAFFIC SIMULATION
 Association for Information Systems AIS Electronic Library (AISeL) PACIS 2014 Proceedings Pacific Asia Conference on Information Systems (PACIS) 2014 THE ADJACENT VEHICLES QUERY ALGORITHM OF MICROSCOPIC
Association for Information Systems AIS Electronic Library (AISeL) PACIS 2014 Proceedings Pacific Asia Conference on Information Systems (PACIS) 2014 THE ADJACENT VEHICLES QUERY ALGORITHM OF MICROSCOPIC
Optimal traffic control via smartphone app users
 Optimal traffic control via smartphone app users A model for actuator and departure optimisation Daphne van Leeuwen 1, Rob van der Mei 2, Frank Ottenhof 3 1. CWI, Science Park 123, 1098XG Amsterdam, e-mail:
Optimal traffic control via smartphone app users A model for actuator and departure optimisation Daphne van Leeuwen 1, Rob van der Mei 2, Frank Ottenhof 3 1. CWI, Science Park 123, 1098XG Amsterdam, e-mail:
Modelling competition in demand-based optimization models
 Modelling competition in demand-based optimization models Stefano Bortolomiol Virginie Lurkin Michel Bierlaire Transport and Mobility Laboratory (TRANSP-OR) École Polytechnique Fédérale de Lausanne Workshop
Modelling competition in demand-based optimization models Stefano Bortolomiol Virginie Lurkin Michel Bierlaire Transport and Mobility Laboratory (TRANSP-OR) École Polytechnique Fédérale de Lausanne Workshop
Topics in Artificial Intelligence: Multiagent Systems Selfish Routing in Computer Networks
 Topics in Artificial Intelligence: Multiagent Systems Selfish Routing in Computer Networks Sebastian Streg December 10, 2005 1 Introduction Efficiency in networks with lots of traffic is a serious problem
Topics in Artificial Intelligence: Multiagent Systems Selfish Routing in Computer Networks Sebastian Streg December 10, 2005 1 Introduction Efficiency in networks with lots of traffic is a serious problem
Prioritizing the Links on the Homepage: Evidence from a University Website Lian-lian SONG 1,a* and Geoffrey TSO 2,b
 2017 3rd International Conference on E-commerce and Contemporary Economic Development (ECED 2017) ISBN: 978-1-60595-446-2 Prioritizing the Links on the Homepage: Evidence from a University Website Lian-lian
2017 3rd International Conference on E-commerce and Contemporary Economic Development (ECED 2017) ISBN: 978-1-60595-446-2 Prioritizing the Links on the Homepage: Evidence from a University Website Lian-lian
Chapter 15 Introduction to Linear Programming
 Chapter 15 Introduction to Linear Programming An Introduction to Optimization Spring, 2015 Wei-Ta Chu 1 Brief History of Linear Programming The goal of linear programming is to determine the values of
Chapter 15 Introduction to Linear Programming An Introduction to Optimization Spring, 2015 Wei-Ta Chu 1 Brief History of Linear Programming The goal of linear programming is to determine the values of
CHAPTER 6 ORTHOGONAL PARTICLE SWARM OPTIMIZATION
 131 CHAPTER 6 ORTHOGONAL PARTICLE SWARM OPTIMIZATION 6.1 INTRODUCTION The Orthogonal arrays are helpful in guiding the heuristic algorithms to obtain a good solution when applied to NP-hard problems. This
131 CHAPTER 6 ORTHOGONAL PARTICLE SWARM OPTIMIZATION 6.1 INTRODUCTION The Orthogonal arrays are helpful in guiding the heuristic algorithms to obtain a good solution when applied to NP-hard problems. This
Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Algorithms and Game Theory Date: 12/3/15
 600.363 Introduction to Algorithms / 600.463 Algorithms I Lecturer: Michael Dinitz Topic: Algorithms and Game Theory Date: 12/3/15 25.1 Introduction Today we re going to spend some time discussing game
600.363 Introduction to Algorithms / 600.463 Algorithms I Lecturer: Michael Dinitz Topic: Algorithms and Game Theory Date: 12/3/15 25.1 Introduction Today we re going to spend some time discussing game
THE REFERENCE POINT METHOD APPLIED TO DECISION SELECTION IN THE PROCESS OF BILATERAL NEGOTIATIONS
 QUANTITATIVE METHODS IN ECONOMICS Vol. XV, No. 2, 24, pp. 44 56 THE REFERENCE POINT METHOD APPLIED TO DECISION SELECTION IN THE PROCESS OF BILATERAL NEGOTIATIONS Andrzej Łodziński Department of Econometrics
QUANTITATIVE METHODS IN ECONOMICS Vol. XV, No. 2, 24, pp. 44 56 THE REFERENCE POINT METHOD APPLIED TO DECISION SELECTION IN THE PROCESS OF BILATERAL NEGOTIATIONS Andrzej Łodziński Department of Econometrics
Title: Increasing the stability and robustness of simulation-based network assignment models for largescale
 Title: Increasing the stability and robustness of simulation-based network assignment models for largescale applications Author: Michael Mahut, INRO Consultants Inc. Larger-scale dynamic network models
Title: Increasing the stability and robustness of simulation-based network assignment models for largescale applications Author: Michael Mahut, INRO Consultants Inc. Larger-scale dynamic network models
Network Capacity, Traffic Instability, and Adaptive Driving: Findings from Simulated Network Experiments
 Network Capacity, Traffic Instability, and Adaptive Driving: Findings from Simulated Network Experiments Meead Saberi Transportation Center Northwestern University 600 Foster Street Evanston, IL, USA 60208-4055
Network Capacity, Traffic Instability, and Adaptive Driving: Findings from Simulated Network Experiments Meead Saberi Transportation Center Northwestern University 600 Foster Street Evanston, IL, USA 60208-4055
Optimal Routing Control: Repeated Game Approach
 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 47, NO. 3, MARCH 2002 437 Optimal Routing Control: Repeated Game Approach Richard J. La and Venkat Anantharam, Fellow, IEEE Abstract Communication networks
IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 47, NO. 3, MARCH 2002 437 Optimal Routing Control: Repeated Game Approach Richard J. La and Venkat Anantharam, Fellow, IEEE Abstract Communication networks
Lecture Notes on Congestion Games
 Lecture Notes on Department of Computer Science RWTH Aachen SS 2005 Definition and Classification Description of n agents share a set of resources E strategy space of player i is S i 2 E latency for resource
Lecture Notes on Department of Computer Science RWTH Aachen SS 2005 Definition and Classification Description of n agents share a set of resources E strategy space of player i is S i 2 E latency for resource
A CSP Search Algorithm with Reduced Branching Factor
 A CSP Search Algorithm with Reduced Branching Factor Igor Razgon and Amnon Meisels Department of Computer Science, Ben-Gurion University of the Negev, Beer-Sheva, 84-105, Israel {irazgon,am}@cs.bgu.ac.il
A CSP Search Algorithm with Reduced Branching Factor Igor Razgon and Amnon Meisels Department of Computer Science, Ben-Gurion University of the Negev, Beer-Sheva, 84-105, Israel {irazgon,am}@cs.bgu.ac.il
Variable Neighborhood Search for Solving the Balanced Location Problem
 TECHNISCHE UNIVERSITÄT WIEN Institut für Computergraphik und Algorithmen Variable Neighborhood Search for Solving the Balanced Location Problem Jozef Kratica, Markus Leitner, Ivana Ljubić Forschungsbericht
TECHNISCHE UNIVERSITÄT WIEN Institut für Computergraphik und Algorithmen Variable Neighborhood Search for Solving the Balanced Location Problem Jozef Kratica, Markus Leitner, Ivana Ljubić Forschungsbericht
Chapter 5 Graph Algorithms Algorithm Theory WS 2012/13 Fabian Kuhn
 Chapter 5 Graph Algorithms Algorithm Theory WS 2012/13 Fabian Kuhn Graphs Extremely important concept in computer science Graph, : node (or vertex) set : edge set Simple graph: no self loops, no multiple
Chapter 5 Graph Algorithms Algorithm Theory WS 2012/13 Fabian Kuhn Graphs Extremely important concept in computer science Graph, : node (or vertex) set : edge set Simple graph: no self loops, no multiple
Reinforcement Learning for Adaptive Routing of Autonomous Vehicles in Congested Networks
 Reinforcement Learning for Adaptive Routing of Autonomous Vehicles in Congested Networks Jonathan Cox Aeronautics & Astronautics Brandon Jennings Mechanical Engineering Steven Krukowski Aeronautics & Astronautics
Reinforcement Learning for Adaptive Routing of Autonomous Vehicles in Congested Networks Jonathan Cox Aeronautics & Astronautics Brandon Jennings Mechanical Engineering Steven Krukowski Aeronautics & Astronautics
An Effective Upperbound on Treewidth Using Partial Fill-in of Separators
 An Effective Upperbound on Treewidth Using Partial Fill-in of Separators Boi Faltings Martin Charles Golumbic June 28, 2009 Abstract Partitioning a graph using graph separators, and particularly clique
An Effective Upperbound on Treewidth Using Partial Fill-in of Separators Boi Faltings Martin Charles Golumbic June 28, 2009 Abstract Partitioning a graph using graph separators, and particularly clique
DYNAMIC SITE LAYOUT PLANNING USING MTPE PRINCIPLE FROM PHYSICS
 DYNAMIC SITE LAYOUT PLANNING USING MTPE PRINCIPLE FROM PHYSICS Mohsen Andayesh* and Farnaz Sadeghpour Department of Civil Engineering, University of Calgary, Calgary, Canada * Corresponding author (m.andayesh@ucalgary.ca)
DYNAMIC SITE LAYOUT PLANNING USING MTPE PRINCIPLE FROM PHYSICS Mohsen Andayesh* and Farnaz Sadeghpour Department of Civil Engineering, University of Calgary, Calgary, Canada * Corresponding author (m.andayesh@ucalgary.ca)
Samuel Coolidge, Dan Simon, Dennis Shasha, Technical Report NYU/CIMS/TR
 Detecting Missing and Spurious Edges in Large, Dense Networks Using Parallel Computing Samuel Coolidge, sam.r.coolidge@gmail.com Dan Simon, des480@nyu.edu Dennis Shasha, shasha@cims.nyu.edu Technical Report
Detecting Missing and Spurious Edges in Large, Dense Networks Using Parallel Computing Samuel Coolidge, sam.r.coolidge@gmail.com Dan Simon, des480@nyu.edu Dennis Shasha, shasha@cims.nyu.edu Technical Report
CHAPTER 5 ANT-FUZZY META HEURISTIC GENETIC SENSOR NETWORK SYSTEM FOR MULTI - SINK AGGREGATED DATA TRANSMISSION
 CHAPTER 5 ANT-FUZZY META HEURISTIC GENETIC SENSOR NETWORK SYSTEM FOR MULTI - SINK AGGREGATED DATA TRANSMISSION 5.1 INTRODUCTION Generally, deployment of Wireless Sensor Network (WSN) is based on a many
CHAPTER 5 ANT-FUZZY META HEURISTIC GENETIC SENSOR NETWORK SYSTEM FOR MULTI - SINK AGGREGATED DATA TRANSMISSION 5.1 INTRODUCTION Generally, deployment of Wireless Sensor Network (WSN) is based on a many
Dynamic Resource Allocation in Heterogeneous Wireless Networks
 Dynamic Resource Allocation in Heterogeneous Wireless Networks Jayant Thatte [jayantt@stanford.edu] 1 Introduction As the wireless technology and standards continue to evolve, wireless communication systems
Dynamic Resource Allocation in Heterogeneous Wireless Networks Jayant Thatte [jayantt@stanford.edu] 1 Introduction As the wireless technology and standards continue to evolve, wireless communication systems
Graph Coloring via Constraint Programming-based Column Generation
 Graph Coloring via Constraint Programming-based Column Generation Stefano Gualandi Federico Malucelli Dipartimento di Elettronica e Informatica, Politecnico di Milano Viale Ponzio 24/A, 20133, Milan, Italy
Graph Coloring via Constraint Programming-based Column Generation Stefano Gualandi Federico Malucelli Dipartimento di Elettronica e Informatica, Politecnico di Milano Viale Ponzio 24/A, 20133, Milan, Italy
A Framework for A Graph- and Queuing System-Based Pedestrian Simulation
 A Framework for A Graph- and Queuing System-Based Pedestrian Simulation Srihari Narasimhan IPVS Universität Stuttgart Stuttgart, Germany Hans-Joachim Bungartz Institut für Informatik Technische Universität
A Framework for A Graph- and Queuing System-Based Pedestrian Simulation Srihari Narasimhan IPVS Universität Stuttgart Stuttgart, Germany Hans-Joachim Bungartz Institut für Informatik Technische Universität
SIMULATION ISSUES OF OPTICAL PACKET SWITCHING RING NETWORKS
 SIMULATION ISSUES OF OPTICAL PACKET SWITCHING RING NETWORKS Marko Lackovic and Cristian Bungarzeanu EPFL-STI-ITOP-TCOM CH-1015 Lausanne, Switzerland {marko.lackovic;cristian.bungarzeanu}@epfl.ch KEYWORDS
SIMULATION ISSUES OF OPTICAL PACKET SWITCHING RING NETWORKS Marko Lackovic and Cristian Bungarzeanu EPFL-STI-ITOP-TCOM CH-1015 Lausanne, Switzerland {marko.lackovic;cristian.bungarzeanu}@epfl.ch KEYWORDS
L Modeling and Simulating Social Systems with MATLAB
 851-0585-04L Modeling and Simulating Social Systems with MATLAB Lecture 4 Cellular Automata Karsten Donnay and Stefano Balietti Chair of Sociology, in particular of Modeling and Simulation ETH Zürich 2011-03-14
851-0585-04L Modeling and Simulating Social Systems with MATLAB Lecture 4 Cellular Automata Karsten Donnay and Stefano Balietti Chair of Sociology, in particular of Modeling and Simulation ETH Zürich 2011-03-14
Segmented Arrival Graph based Evacuation Plan Assessment Algorithm Using Linear Programming
 Segmented Arrival Graph based Evacuation Plan Assessment Algorithm Using Linear Programming Manki Min Dept. of Electrical Engineering and Computer Science South Dakota State University Brookings, SD 577
Segmented Arrival Graph based Evacuation Plan Assessment Algorithm Using Linear Programming Manki Min Dept. of Electrical Engineering and Computer Science South Dakota State University Brookings, SD 577
On the Computational Complexity of Nash Equilibria for (0, 1) Bimatrix Games
 On the Computational Complexity of Nash Equilibria for (0, 1) Bimatrix Games Bruno Codenotti Daniel Štefankovič Abstract The computational complexity of finding a Nash equilibrium in a nonzero sum bimatrix
On the Computational Complexity of Nash Equilibria for (0, 1) Bimatrix Games Bruno Codenotti Daniel Štefankovič Abstract The computational complexity of finding a Nash equilibrium in a nonzero sum bimatrix
Improving Computing Performance for Algorithm Finding Maximal Flows on Extended Mixed Networks
 ISSN 1746-7659, England, UK Journal of Information and Computing Science Vol. 10, No. 1, 2015, pp. 075-080 Improving Computing Performance for Algorithm Finding Maximal Flows on Extended Mixed Networks
ISSN 1746-7659, England, UK Journal of Information and Computing Science Vol. 10, No. 1, 2015, pp. 075-080 Improving Computing Performance for Algorithm Finding Maximal Flows on Extended Mixed Networks
ON THE PROBABILITY OF K-CONNECTIVITY IN WIRELESS AD HOC NETWORKS UNDER DIFFERENT MOBILITY MODELS
 ON THE PROBABILITY OF K-CONNECTIVITY IN WIRELESS AD HOC NETWORKS UNDER DIFFERENT MOBILITY MODELS Natarajan Meghanathan 1 and Sireesha Gorla 1, Jackson State University, 1400 Lynch St, Jackson, MS, USA
ON THE PROBABILITY OF K-CONNECTIVITY IN WIRELESS AD HOC NETWORKS UNDER DIFFERENT MOBILITY MODELS Natarajan Meghanathan 1 and Sireesha Gorla 1, Jackson State University, 1400 Lynch St, Jackson, MS, USA
1.1 What is Microeconomics?
 1.1 What is Microeconomics? Economics is the study of allocating limited resources to satisfy unlimited wants. Such a tension implies tradeoffs among competing goals. The analysis can be carried out at
1.1 What is Microeconomics? Economics is the study of allocating limited resources to satisfy unlimited wants. Such a tension implies tradeoffs among competing goals. The analysis can be carried out at
MLR Institute of Technology
 Course Name : Engineering Optimization Course Code : 56021 Class : III Year Branch : Aeronautical Engineering Year : 2014-15 Course Faculty : Mr Vamsi Krishna Chowduru, Assistant Professor Course Objective
Course Name : Engineering Optimization Course Code : 56021 Class : III Year Branch : Aeronautical Engineering Year : 2014-15 Course Faculty : Mr Vamsi Krishna Chowduru, Assistant Professor Course Objective
DYN-OPT Users Manual. Cenk Caliskan Randolph W. Hall. California PATH Working Paper UCB-ITS-PWP-97-6
 CALIFORNIA PATH PROGRAM INSTITUTE OF TRANSPORTATION STUDIES UNIVERSITY OF CALIFORNIA, BERKELEY DYN-OPT Users Manual Cenk Caliskan Randolph W Hall California PATH Working Paper UCB-ITS-PWP-97-6 This work
CALIFORNIA PATH PROGRAM INSTITUTE OF TRANSPORTATION STUDIES UNIVERSITY OF CALIFORNIA, BERKELEY DYN-OPT Users Manual Cenk Caliskan Randolph W Hall California PATH Working Paper UCB-ITS-PWP-97-6 This work
Urban Road Traffic Simulation Techniques
 ANALELE UNIVERSITĂłII EFTIMIE MURGU REŞIłA ANUL XVIII, NR. 2, 2011, ISSN 1453-7397 Ana Maria Nicoleta Mocofan Urban Road Traffic Simulation Techniques For achieving a reliable traffic control system it
ANALELE UNIVERSITĂłII EFTIMIE MURGU REŞIłA ANUL XVIII, NR. 2, 2011, ISSN 1453-7397 Ana Maria Nicoleta Mocofan Urban Road Traffic Simulation Techniques For achieving a reliable traffic control system it
Game-theoretic Robustness of Many-to-one Networks
 Game-theoretic Robustness of Many-to-one Networks Aron Laszka, Dávid Szeszlér 2, and Levente Buttyán Budapest University of Technology and Economics, Department of Telecommunications, Laboratory of Cryptography
Game-theoretic Robustness of Many-to-one Networks Aron Laszka, Dávid Szeszlér 2, and Levente Buttyán Budapest University of Technology and Economics, Department of Telecommunications, Laboratory of Cryptography
Joint Server Selection and Routing for Geo-Replicated Services
 Joint Server Selection and Routing for Geo-Replicated Services Srinivas Narayana Joe Wenjie Jiang, Jennifer Rexford and Mung Chiang Princeton University 1 Large-scale online services Search, shopping,
Joint Server Selection and Routing for Geo-Replicated Services Srinivas Narayana Joe Wenjie Jiang, Jennifer Rexford and Mung Chiang Princeton University 1 Large-scale online services Search, shopping,
TRANSPORT PLANNING AND
 Tutorial TRANSPORT PLANNING AND MODELING Using TFTP (Teacher Friendly Transportation Program) WHAT IS MODEL? Ortusar and Willumsen, 1994, A simplified representation of a part of the real world the system
Tutorial TRANSPORT PLANNING AND MODELING Using TFTP (Teacher Friendly Transportation Program) WHAT IS MODEL? Ortusar and Willumsen, 1994, A simplified representation of a part of the real world the system
Deploying Multiple Service Chain (SC) Instances per Service Chain BY ABHISHEK GUPTA FRIDAY GROUP MEETING APRIL 21, 2017
 Deploying Multiple Service Chain (SC) Instances per Service Chain BY ABHISHEK GUPTA FRIDAY GROUP MEETING APRIL 21, 2017 Virtual Network Function (VNF) Service Chain (SC) 2 Multiple VNF SC Placement and
Deploying Multiple Service Chain (SC) Instances per Service Chain BY ABHISHEK GUPTA FRIDAY GROUP MEETING APRIL 21, 2017 Virtual Network Function (VNF) Service Chain (SC) 2 Multiple VNF SC Placement and
CONTRIBUTION TO THE INVESTIGATION OF STOPPING SIGHT DISTANCE IN THREE-DIMENSIONAL SPACE
 National Technical University of Athens School of Civil Engineering Department of Transportation Planning and Engineering Doctoral Dissertation CONTRIBUTION TO THE INVESTIGATION OF STOPPING SIGHT DISTANCE
National Technical University of Athens School of Civil Engineering Department of Transportation Planning and Engineering Doctoral Dissertation CONTRIBUTION TO THE INVESTIGATION OF STOPPING SIGHT DISTANCE
Genetic Algorithm Performance with Different Selection Methods in Solving Multi-Objective Network Design Problem
 etic Algorithm Performance with Different Selection Methods in Solving Multi-Objective Network Design Problem R. O. Oladele Department of Computer Science University of Ilorin P.M.B. 1515, Ilorin, NIGERIA
etic Algorithm Performance with Different Selection Methods in Solving Multi-Objective Network Design Problem R. O. Oladele Department of Computer Science University of Ilorin P.M.B. 1515, Ilorin, NIGERIA
Combining static and dynamic models for traffic signal optimization
 Available online at www.sciencedirect.com Procedia - Social and Behavioral Sciences 54 ( 2012 ) 1125 1134 EWGT 2012 15th meeting of the EURO Working Group on Transportation Combining static and dynamic
Available online at www.sciencedirect.com Procedia - Social and Behavioral Sciences 54 ( 2012 ) 1125 1134 EWGT 2012 15th meeting of the EURO Working Group on Transportation Combining static and dynamic
Optimal Routing-Conscious Dynamic Placement for Reconfigurable Devices
 Optimal Routing-Conscious Dynamic Placement for Reconfigurable Devices Ali Ahmadinia 1, Christophe Bobda 1,Sándor P. Fekete 2, Jürgen Teich 1, and Jan C. van der Veen 2 1 Department of Computer Science
Optimal Routing-Conscious Dynamic Placement for Reconfigurable Devices Ali Ahmadinia 1, Christophe Bobda 1,Sándor P. Fekete 2, Jürgen Teich 1, and Jan C. van der Veen 2 1 Department of Computer Science
Online k-taxi Problem
 Distributed Computing Online k-taxi Problem Theoretical Patrick Stäuble patricst@ethz.ch Distributed Computing Group Computer Engineering and Networks Laboratory ETH Zürich Supervisors: Georg Bachmeier,
Distributed Computing Online k-taxi Problem Theoretical Patrick Stäuble patricst@ethz.ch Distributed Computing Group Computer Engineering and Networks Laboratory ETH Zürich Supervisors: Georg Bachmeier,
Copyright 2007 Pearson Addison-Wesley. All rights reserved. A. Levitin Introduction to the Design & Analysis of Algorithms, 2 nd ed., Ch.
 Iterative Improvement Algorithm design technique for solving optimization problems Start with a feasible solution Repeat the following step until no improvement can be found: change the current feasible
Iterative Improvement Algorithm design technique for solving optimization problems Start with a feasible solution Repeat the following step until no improvement can be found: change the current feasible
Controlling user groups in traffic
 Controlling user groups in traffic Jaap Vreeswijk 1, Luc Wismans 2, Bas Tutert 3 1. Imtech Traffic & Infra, Basicweg 16, 3821 BR Amersfoort, The Netherlands, Phone: +31 33 454 1724, Mail: jaap.vreeswijk@imtech.com
Controlling user groups in traffic Jaap Vreeswijk 1, Luc Wismans 2, Bas Tutert 3 1. Imtech Traffic & Infra, Basicweg 16, 3821 BR Amersfoort, The Netherlands, Phone: +31 33 454 1724, Mail: jaap.vreeswijk@imtech.com
Lecture 4 Wide Area Networks - Routing
 DATA AND COMPUTER COMMUNICATIONS Lecture 4 Wide Area Networks - Routing Mei Yang Based on Lecture slides by William Stallings 1 ROUTING IN PACKET SWITCHED NETWORK key design issue for (packet) switched
DATA AND COMPUTER COMMUNICATIONS Lecture 4 Wide Area Networks - Routing Mei Yang Based on Lecture slides by William Stallings 1 ROUTING IN PACKET SWITCHED NETWORK key design issue for (packet) switched
DriveFaster: Optimizing a Traffic Light Grid System
 DriveFaster: Optimizing a Traffic Light Grid System Abstract CS221 Fall 2016: Final Report Team Members: Xiaofan Li, Ahmed Jaffery Traffic lights are the central point of control of traffic for cities
DriveFaster: Optimizing a Traffic Light Grid System Abstract CS221 Fall 2016: Final Report Team Members: Xiaofan Li, Ahmed Jaffery Traffic lights are the central point of control of traffic for cities
Neuro-fuzzy admission control in mobile communications systems
 University of Wollongong Thesis Collections University of Wollongong Thesis Collection University of Wollongong Year 2005 Neuro-fuzzy admission control in mobile communications systems Raad Raad University
University of Wollongong Thesis Collections University of Wollongong Thesis Collection University of Wollongong Year 2005 Neuro-fuzzy admission control in mobile communications systems Raad Raad University
Interactive Design and Visualization of Urban Spaces using Geometrical and Behavioral Modeling
 Interactive Design and Visualization of Urban Spaces using Geometrical and Behavioral Modeling Carlos Vanegas 1,4,5 Daniel Aliaga 1 Bedřich Beneš 2 Paul Waddell 3 1 Computer Science, Purdue University,
Interactive Design and Visualization of Urban Spaces using Geometrical and Behavioral Modeling Carlos Vanegas 1,4,5 Daniel Aliaga 1 Bedřich Beneš 2 Paul Waddell 3 1 Computer Science, Purdue University,
A PRIMAL-DUAL EXTERIOR POINT ALGORITHM FOR LINEAR PROGRAMMING PROBLEMS
 Yugoslav Journal of Operations Research Vol 19 (2009), Number 1, 123-132 DOI:10.2298/YUJOR0901123S A PRIMAL-DUAL EXTERIOR POINT ALGORITHM FOR LINEAR PROGRAMMING PROBLEMS Nikolaos SAMARAS Angelo SIFELARAS
Yugoslav Journal of Operations Research Vol 19 (2009), Number 1, 123-132 DOI:10.2298/YUJOR0901123S A PRIMAL-DUAL EXTERIOR POINT ALGORITHM FOR LINEAR PROGRAMMING PROBLEMS Nikolaos SAMARAS Angelo SIFELARAS
A+B. Approaches Get Mature. How to evaluate? Self-*, Autonomic Communication. Virtualization f 3. f 4 f 1 f 2 CCN. Loc/ID Split Functional Composition
 How FIT is Your Network? Towards a Future Internet Tournament Tanja Zseby, Jens Tiemann Competence Center Network Research Fraunhofer Institute FOKUS 1/16 2010 Approaches Get Mature CCN Virtualization
How FIT is Your Network? Towards a Future Internet Tournament Tanja Zseby, Jens Tiemann Competence Center Network Research Fraunhofer Institute FOKUS 1/16 2010 Approaches Get Mature CCN Virtualization
Solving Large Aircraft Landing Problems on Multiple Runways by Applying a Constraint Programming Approach
 Solving Large Aircraft Landing Problems on Multiple Runways by Applying a Constraint Programming Approach Amir Salehipour School of Mathematical and Physical Sciences, The University of Newcastle, Australia
Solving Large Aircraft Landing Problems on Multiple Runways by Applying a Constraint Programming Approach Amir Salehipour School of Mathematical and Physical Sciences, The University of Newcastle, Australia
A Signaling Game Approach to Databases Querying
 A Signaling Game Approach to Databases Querying Ben McCamish 1, Arash Termehchy 1, Behrouz Touri 2, and Eduardo Cotilla-Sanchez 1 1 School of Electrical Engineering and Computer Science, Oregon State University
A Signaling Game Approach to Databases Querying Ben McCamish 1, Arash Termehchy 1, Behrouz Touri 2, and Eduardo Cotilla-Sanchez 1 1 School of Electrical Engineering and Computer Science, Oregon State University
Online Dial-A-Ride Problem with Time Windows: an exact algorithm using status vectors
 Online Dial-A-Ride Problem with Time Windows: an exact algorithm using status vectors A. Fabri 1 and P. Recht 2 1 Universität Dortmund a.fabri@wiso.uni-dortmund.de 2 Universität Dortmund p.recht@wiso.uni-dortmund.de
Online Dial-A-Ride Problem with Time Windows: an exact algorithm using status vectors A. Fabri 1 and P. Recht 2 1 Universität Dortmund a.fabri@wiso.uni-dortmund.de 2 Universität Dortmund p.recht@wiso.uni-dortmund.de
Location Traceability of Users in Location-based Services
 Location Traceability of Users in Location-based Services Yutaka Yanagisawa Hidetoshi Kido Tetsuji Satoh, NTT Communication Science Laboratories, NTT Corporation Graduate School of Information Science
Location Traceability of Users in Location-based Services Yutaka Yanagisawa Hidetoshi Kido Tetsuji Satoh, NTT Communication Science Laboratories, NTT Corporation Graduate School of Information Science
Automatically Balancing Intersection Volumes in A Highway Network
 Automatically Balancing Intersection Volumes in A Highway Network Jin Ren and Aziz Rahman HDR Engineering, Inc. 500 108 th Avenue NE, Suite 1200 Bellevue, WA 98004-5549 Jin.ren@hdrinc.com and 425-468-1548
Automatically Balancing Intersection Volumes in A Highway Network Jin Ren and Aziz Rahman HDR Engineering, Inc. 500 108 th Avenue NE, Suite 1200 Bellevue, WA 98004-5549 Jin.ren@hdrinc.com and 425-468-1548
A Cluster-Based Energy Balancing Scheme in Heterogeneous Wireless Sensor Networks
 A Cluster-Based Energy Balancing Scheme in Heterogeneous Wireless Sensor Networks Jing Ai, Damla Turgut, and Ladislau Bölöni Networking and Mobile Computing Research Laboratory (NetMoC) Department of Electrical
A Cluster-Based Energy Balancing Scheme in Heterogeneous Wireless Sensor Networks Jing Ai, Damla Turgut, and Ladislau Bölöni Networking and Mobile Computing Research Laboratory (NetMoC) Department of Electrical
ScienceDirect. Studying the accuracy of demand generation from mobile phone trajectories with synthetic data
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 32 ( 2014 ) 802 807 The 3rd International Workshop on Agent-based Mobility, Traffic and Transportation Models, Methodologies
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 32 ( 2014 ) 802 807 The 3rd International Workshop on Agent-based Mobility, Traffic and Transportation Models, Methodologies
Solving Travelling Salesman Problem and Mapping to Solve Robot Motion Planning through Genetic Algorithm Principle
 Indian Journal of Science and Technology, Vol 8(35), DOI: 10.17485/ijst/2015/v8i35/86809, December 2015 ISSN (Print) : 0974-6846 ISSN (Online) : 0974-5645 Solving Travelling Salesman Problem and Mapping
Indian Journal of Science and Technology, Vol 8(35), DOI: 10.17485/ijst/2015/v8i35/86809, December 2015 ISSN (Print) : 0974-6846 ISSN (Online) : 0974-5645 Solving Travelling Salesman Problem and Mapping
Net Neutrality and Inflation of Traffic
 Introduction Net Neutrality and Inflation of Traffic Martin Peitz (MaCCI, University of Mannheim and CERRE) Florian Schuett (TILEC, CentER, Tilburg University) Symposium in Honor of Jean Tirole The Hague,
Introduction Net Neutrality and Inflation of Traffic Martin Peitz (MaCCI, University of Mannheim and CERRE) Florian Schuett (TILEC, CentER, Tilburg University) Symposium in Honor of Jean Tirole The Hague,
Intelligent Reduction of Tire Noise
 Intelligent Reduction of Tire Noise Matthias Becker and Helena Szczerbicka University Hannover Welfengarten 3067 Hannover, Germany xmb@sim.uni-hannover.de Abstract. In this paper we report about deployment
Intelligent Reduction of Tire Noise Matthias Becker and Helena Szczerbicka University Hannover Welfengarten 3067 Hannover, Germany xmb@sim.uni-hannover.de Abstract. In this paper we report about deployment
Grid Scheduling Strategy using GA (GSSGA)
 F Kurus Malai Selvi et al,int.j.computer Technology & Applications,Vol 3 (5), 8-86 ISSN:2229-693 Grid Scheduling Strategy using GA () Dr.D.I.George Amalarethinam Director-MCA & Associate Professor of Computer
F Kurus Malai Selvi et al,int.j.computer Technology & Applications,Vol 3 (5), 8-86 ISSN:2229-693 Grid Scheduling Strategy using GA () Dr.D.I.George Amalarethinam Director-MCA & Associate Professor of Computer
Transportation Planning: The maximum flow problem
 Transportation lanning: The maximum flow problem In many applications, and especially in the planning of Transportation and Logistics of materials, one important problem is that of finding how much material
Transportation lanning: The maximum flow problem In many applications, and especially in the planning of Transportation and Logistics of materials, one important problem is that of finding how much material
EXPANDED ACCOMMODATION ANALYSIS AND RAPID PROTOTYPING TECHNIQUE FOR THE DESIGN OF A CREW STATION COCKPIT
 ICAS 2002 CONGRESS EXPANDED ACCOMMODATION ANALYSIS AND RAPID PROTOTYPING TECHNIQUE FOR THE DESIGN OF A CREW STATION COCKPIT Edward Winkler 1, Landon Onyebueke 2, and Olusesan Ameye 2. 1 The Boeing Company
ICAS 2002 CONGRESS EXPANDED ACCOMMODATION ANALYSIS AND RAPID PROTOTYPING TECHNIQUE FOR THE DESIGN OF A CREW STATION COCKPIT Edward Winkler 1, Landon Onyebueke 2, and Olusesan Ameye 2. 1 The Boeing Company
Progress Towards the Total Domination Game 3 4 -Conjecture
 Progress Towards the Total Domination Game 3 4 -Conjecture 1 Michael A. Henning and 2 Douglas F. Rall 1 Department of Pure and Applied Mathematics University of Johannesburg Auckland Park, 2006 South Africa
Progress Towards the Total Domination Game 3 4 -Conjecture 1 Michael A. Henning and 2 Douglas F. Rall 1 Department of Pure and Applied Mathematics University of Johannesburg Auckland Park, 2006 South Africa
Cadyts calibration of dynamic traffic simulations Version manual
 Cadyts calibration of dynamic traffic simulations Version 1.1.0 manual Gunnar Flötteröd November 4, 2010 1 Introduction Iterated microsimulations have become prominent solution procedures for the dynamic
Cadyts calibration of dynamic traffic simulations Version 1.1.0 manual Gunnar Flötteröd November 4, 2010 1 Introduction Iterated microsimulations have become prominent solution procedures for the dynamic
A Capacity Planning Methodology for Distributed E-Commerce Applications
 A Capacity Planning Methodology for Distributed E-Commerce Applications I. Introduction Most of today s e-commerce environments are based on distributed, multi-tiered, component-based architectures. The
A Capacity Planning Methodology for Distributed E-Commerce Applications I. Introduction Most of today s e-commerce environments are based on distributed, multi-tiered, component-based architectures. The
Random Neural Networks for the Adaptive Control of Packet Networks
 Random Neural Networks for the Adaptive Control of Packet Networks Michael Gellman and Peixiang Liu Dept. of Electrical & Electronic Eng., Imperial College London {m.gellman,p.liu}@imperial.ac.uk Abstract.
Random Neural Networks for the Adaptive Control of Packet Networks Michael Gellman and Peixiang Liu Dept. of Electrical & Electronic Eng., Imperial College London {m.gellman,p.liu}@imperial.ac.uk Abstract.
Interval Algorithms for Coin Flipping
 IJCSNS International Journal of Computer Science and Network Security, VOL.10 No.2, February 2010 55 Interval Algorithms for Coin Flipping Sung-il Pae, Hongik University, Seoul, Korea Summary We discuss
IJCSNS International Journal of Computer Science and Network Security, VOL.10 No.2, February 2010 55 Interval Algorithms for Coin Flipping Sung-il Pae, Hongik University, Seoul, Korea Summary We discuss
H. W. Kuhn. Bryn Mawr College
 VARIANTS OF THE HUNGARIAN METHOD FOR ASSIGNMENT PROBLEMS' H. W. Kuhn Bryn Mawr College The author presents a geometrical modelwhich illuminates variants of the Hungarian method for the solution of the
VARIANTS OF THE HUNGARIAN METHOD FOR ASSIGNMENT PROBLEMS' H. W. Kuhn Bryn Mawr College The author presents a geometrical modelwhich illuminates variants of the Hungarian method for the solution of the
Network Fundamental Diagrams and their Dependence on Network Topology
 Network Fundamental Diagrams and their Dependence on Network Topology Victor L. Knoop 1 David de Jong 1 and Serge P. Hoogendoorn 1 Abstract Recent studies have shown that aggregated over a whole network
Network Fundamental Diagrams and their Dependence on Network Topology Victor L. Knoop 1 David de Jong 1 and Serge P. Hoogendoorn 1 Abstract Recent studies have shown that aggregated over a whole network
ECEN 5032 Data Networks Medium Access Control Sublayer
 ECEN 5032 Data Networks Medium Access Control Sublayer Peter Mathys mathys@colorado.edu University of Colorado, Boulder c 1996 2005, P. Mathys p.1/35 Overview (Sub)networks can be divided into two categories:
ECEN 5032 Data Networks Medium Access Control Sublayer Peter Mathys mathys@colorado.edu University of Colorado, Boulder c 1996 2005, P. Mathys p.1/35 Overview (Sub)networks can be divided into two categories:
Evaluation of Information Dissemination Characteristics in a PTS VANET
 Evaluation of Information Dissemination Characteristics in a PTS VANET Holger Kuprian 1, Marek Meyer 2, Miguel Rios 3 1) Technische Universität Darmstadt, Multimedia Communications Lab Holger.Kuprian@KOM.tu-darmstadt.de
Evaluation of Information Dissemination Characteristics in a PTS VANET Holger Kuprian 1, Marek Meyer 2, Miguel Rios 3 1) Technische Universität Darmstadt, Multimedia Communications Lab Holger.Kuprian@KOM.tu-darmstadt.de
Box-Cox Transformation for Simple Linear Regression
 Chapter 192 Box-Cox Transformation for Simple Linear Regression Introduction This procedure finds the appropriate Box-Cox power transformation (1964) for a dataset containing a pair of variables that are
Chapter 192 Box-Cox Transformation for Simple Linear Regression Introduction This procedure finds the appropriate Box-Cox power transformation (1964) for a dataset containing a pair of variables that are
Data and Computer Communications. Chapter 12 Routing in Switched Networks
 Data and Computer Communications Chapter 1 Routing in Switched Networks Routing in Packet Switched Network Select route between end nodes Characteristics required: Correctness Simplicity Robustness Stability
Data and Computer Communications Chapter 1 Routing in Switched Networks Routing in Packet Switched Network Select route between end nodes Characteristics required: Correctness Simplicity Robustness Stability
BookAidee: Managing Evacuees from Natural Disaster by RFID Tagged Library Books
 BookAidee: Managing Evacuees from Natural Disaster by RFID Tagged Library Books Markus Liuska 1,EmmiMakkonen 1,andItiroSiio 2 1 Centria University of Applied Sciences, RF-Media Laboratory Vierimaantie
BookAidee: Managing Evacuees from Natural Disaster by RFID Tagged Library Books Markus Liuska 1,EmmiMakkonen 1,andItiroSiio 2 1 Centria University of Applied Sciences, RF-Media Laboratory Vierimaantie
The Control Effect of Traffic Information on Traffic Assignment. Junqiang Guo,Bingzhong Ren
 The Control Effect of Traffic Information on Traffic Assignment Junqiang Guo,Bingzhong Ren Department of Information and Electrical Engineering, Shandong University of Science and Technology, Jinan 250031,
The Control Effect of Traffic Information on Traffic Assignment Junqiang Guo,Bingzhong Ren Department of Information and Electrical Engineering, Shandong University of Science and Technology, Jinan 250031,
IMPLEMENTATION OF A FIXING STRATEGY AND PARALLELIZATION IN A RECENT GLOBAL OPTIMIZATION METHOD
 IMPLEMENTATION OF A FIXING STRATEGY AND PARALLELIZATION IN A RECENT GLOBAL OPTIMIZATION METHOD Figen Öztoprak, Ş.İlker Birbil Sabancı University Istanbul, Turkey figen@su.sabanciuniv.edu, sibirbil@sabanciuniv.edu
IMPLEMENTATION OF A FIXING STRATEGY AND PARALLELIZATION IN A RECENT GLOBAL OPTIMIZATION METHOD Figen Öztoprak, Ş.İlker Birbil Sabancı University Istanbul, Turkey figen@su.sabanciuniv.edu, sibirbil@sabanciuniv.edu
Triadic Formal Concept Analysis within Multi Agent Systems
 Triadic Formal Concept Analysis within Multi Agent Systems Petr Gajdoš, Pavel Děrgel Department of Computer Science, VŠB - Technical University of Ostrava, tř. 17. listopadu 15, 708 33 Ostrava-Poruba Czech
Triadic Formal Concept Analysis within Multi Agent Systems Petr Gajdoš, Pavel Děrgel Department of Computer Science, VŠB - Technical University of Ostrava, tř. 17. listopadu 15, 708 33 Ostrava-Poruba Czech
Solving dynamic memory allocation problems in embedded systems with parallel variable neighborhood search strategies
 Available online at www.sciencedirect.com Electronic Notes in Discrete Mathematics 47 (2015) 85 92 www.elsevier.com/locate/endm Solving dynamic memory allocation problems in embedded systems with parallel
Available online at www.sciencedirect.com Electronic Notes in Discrete Mathematics 47 (2015) 85 92 www.elsevier.com/locate/endm Solving dynamic memory allocation problems in embedded systems with parallel
Complexity. Congestion Games. Algorithmic Game Theory. Alexander Skopalik Algorithmic Game Theory 2013 Congestion Games
 Algorithmic Game Theory Complexity of pure Nash equilibria We investigate the complexity of finding Nash equilibria in different kinds of congestion games. Our study is restricted to congestion games with
Algorithmic Game Theory Complexity of pure Nash equilibria We investigate the complexity of finding Nash equilibria in different kinds of congestion games. Our study is restricted to congestion games with
Exploration vs. Exploitation in Differential Evolution
 Exploration vs. Exploitation in Differential Evolution Ângela A. R. Sá 1, Adriano O. Andrade 1, Alcimar B. Soares 1 and Slawomir J. Nasuto 2 Abstract. Differential Evolution (DE) is a tool for efficient
Exploration vs. Exploitation in Differential Evolution Ângela A. R. Sá 1, Adriano O. Andrade 1, Alcimar B. Soares 1 and Slawomir J. Nasuto 2 Abstract. Differential Evolution (DE) is a tool for efficient
* Hyun Suk Park. Korea Institute of Civil Engineering and Building, 283 Goyangdae-Ro Goyang-Si, Korea. Corresponding Author: Hyun Suk Park
 International Journal Of Engineering Research And Development e-issn: 2278-067X, p-issn: 2278-800X, www.ijerd.com Volume 13, Issue 11 (November 2017), PP.47-59 Determination of The optimal Aggregation
International Journal Of Engineering Research And Development e-issn: 2278-067X, p-issn: 2278-800X, www.ijerd.com Volume 13, Issue 11 (November 2017), PP.47-59 Determination of The optimal Aggregation
