Seqrite TERMINATOR (UTM) Unified Threat Management Solution.
|
|
|
- Jayson Craig
- 5 years ago
- Views:
Transcription
1 Unified Threat Management Solution
2 TERMINATOR Introduction Seqrite TERMINATOR is a high-performance, easy-to-use Unified Threat Management solution for small and mid-size enterprises. It is a robust solution for keeping your entire IT infrastructure stable, secure, and productive. The new collaborative platform architecture brings network security, management, backup and recovery of UTM data, and many other critical network services together under a single unified umbrella. This directly translates into better ROI, lower costs and a safer, more productive work environment. Seqrite TERMINATOR is tailored to suit the complexity of emerging threat scenarios. This fully integrated product is a simple and smart way of replacing multiple security programs with one solution. It is easy to use and install for small and mid-size enterprises. Firewall Remote users IDS/IPS (Intrusion detection/prevention) Content Filtering Internet Seqrite TERMINATOR Secured End User Anti Spam/Anti Malware VPN
3 Benefits Promotes a secure, safe and virus-free network environment that adds to the reputation of your organization. Enhances employee productivity by controlling web access. Cost- effective bundled solution with all security solutions in one appliance. Helps in optimum usage of IT resources. Provides a layer of robust anti-virus protection along with additional security and manageability tools like Firewall, IDS/IPS, VPN and bandwidth manager. Easy deployment and management. Plug-and-play solution without manual intervention and any major changes to existing network setup. Easily available customer support for timely consultation and recommendation.
4 TERMINATOR Feature List Networking ISP Load Balancing Policy Based Routing Automatic Gateway Failover VLAN Support 802.Q Integrated DNS server Dynamic DNS DHCP Server USB Internet Support 3G/4G IP and Port forwarding Fiber Optic Support (SFP) IEEE 802.D transparent bridging. Configurable LAN/WAN/DMZ Zone/ports Administration Command Line interface (CLI) Multi Lingual Support (English and Japanese) Web portal customization Backup and Restore Configurations Content Filtering Category Based Custom Web Lists HTTP & HTTPS blocking Upload / Download limit for each profile/user Time based access limit Bandwidth management Data Quota Management Application Classification and Control Multiple Administrator Support Administrator Profile Management
5 User Authentication Monitoring and Reporting Internal Database Active directory integration LDAP integration IP / MAC binding Multiple Authentication servers Guest User Support Group based access control Captive portal Internal Services Usage (CPU/RAM/etc.) Alerts ( and SMS) Scheduled Reports (Daily, Weekly and Monthly) Diagnostic Tools Log Viewer Reports In pdf,.doc and.xls format Firewall & Security Features VPN IPSec VPN Site-to-Site VPN Remote Access VPN SSL VPN Remote Access Client Software SSL VPN Compression Dead Peer Detection Stateful Inspection Firewall Intrusion Prevention Gateway Antivirus Network Address Translation (NAT) Masquerade and SNAT Automatic update for AV, IDS
6 Mail Protection Mail Antivirus and Anti-spam (SMTP, POP3 and IMAP) Attachment control Technical Specifications TS Series THROUGHPUT & CONNECTIONS T- T-2 T-3 T-0 Firewall Throughput 200 Mbps 47 Mbps 70 Mbps 90 Mbps TERMINATOR -TS Series Antivirus Throughput IPSEC VPN Throughput SSL VPN Throughput TERMINATOR Throughput Interfaces I/O Interfaces Concurrent Sessions Console Ports Model Upgradeable 4 Mbps 70 Mbps 4 Mbps 6 Mbps 22 Mbps 26 Mbps 90 Mbps 0 Mbps 7 Mbps 40 Mbps 6 Mbps 0 Mbps 4 GBE 4 GBE Mbps 360 Mbps 22 Mbps 30 Mbps NO VPN TUNNELS Branch Office VPN (IPSEC/SSL) Mobile User VPN (PPTP/SSL)
7 TM Series THROUGHPUT & CONNECTIONS T-7 T-00 T-0 TERMINATOR -TM Series Firewall Throughput Antivirus Throughput IPSEC VPN Throughput SSL VPN Throughput TERMINATOR Throughput Interfaces I/O Interfaces Concurrent Sessions Console Ports Model Upgradeable 00 Mbps 7 Mbps 400 Mbps 30 Mbps 4 Mbps Mbps 20 Mbps 460 Mbps 390 Mbps 60 Mbps Mbps 2 Mbps 60 Mbps 40 Mbps 200 Mbps NO VPN TUNNELS Branch Office VPN (IPSEC/SSL) Mobile User VPN (PPTP/SSL)
8 TE Series THROUGHPUT & CONNECTIONS T-200 T-20 T-300 T-00 TERMINATOR -TE Series Firewall Throughput Antivirus Throughput IPSEC VPN Throughput SSL VPN Throughput TERMINATOR Throughput Interfaces I/O Interfaces Concurrent Sessions Console Ports Model Upgradeable 60 Mbps 68 Mbps 800 Mbps 300 Mbps 390 Mbps 47 Mbps 80 Mbps 90 Mbps 22 Mbps 440 Mbps 460 Mbps 490 Mbps 240 Mbps 290 Mbps 320 Mbps 0 GBE 0 GBE 0 GBE Mbps 77 Mbps 400 Mbps 600 Mbps 90 Mbps 0 GBE NO VPN TUNNELS Branch Office VPN (IPSEC/SSL) Mobile User VPN (PPTP/SSL) UTM performance is measured based on HTTP traffic under standard testing conditions. Actual performance may vary depending on the real network traffic environments.
9 Copyright 20 Quick Heal Technologies (P) Ltd. All Rights Reserved. No part of this publication may be reproduced, duplicated or modified in any form or incorporated into any information retrieval system, electronic or any other or transmitted in any form without prior permission of Quick Heal Technologies (P) Ltd., 603 Mayfair Towers II, Wakdewadi, Shivajinagar, Pune-4 00, India. Marketing distribution or use by anyone barring the people authorized by Quick Heal Technologies (P) Ltd. is liable to legal prosecution. Headquarters Quick Heal Technologies (P) Ltd. 603, Mayfair Tower II, Wakdewadi, Shivajinagar, Pune , India. info@seqrite.com, For more details visit: All Intellectual Property Right(s) including trademark(s), logo(s) and copyright(s) is property of their respective owners. Copyright 204 Quick Heal Technologies (P) Ltd. All rights reserved.
Future-ready security for small and mid-size enterprises
 First line of defense for your network Quick Heal Terminator (UTM) (Unified Threat Management Solution) Data Sheet Future-ready security for small and mid-size enterprises Quick Heal Terminator is a high-performance,
First line of defense for your network Quick Heal Terminator (UTM) (Unified Threat Management Solution) Data Sheet Future-ready security for small and mid-size enterprises Quick Heal Terminator is a high-performance,
Seqrite Unified Threat Management
 Seqrite Unified Threat Management 2.1 Release Notes July 2, 2018 Seqrite Unified Threat Management www.seqrite.com Copyright Information Copyright 2018 Quick Heal Technologies Ltd. All Rights Reserved.
Seqrite Unified Threat Management 2.1 Release Notes July 2, 2018 Seqrite Unified Threat Management www.seqrite.com Copyright Information Copyright 2018 Quick Heal Technologies Ltd. All Rights Reserved.
Unified Threat Management
 G H I J ECS Enter Unified Threat Management CR500ia-1F QUICK START GUIDE CR500ia-1F Appliance Document Version: PL QSG500ia-1F/96000/10.02.0.0.473/08082012 G H I J CR500ia-1F ECS Enter DEFAULTS Default
G H I J ECS Enter Unified Threat Management CR500ia-1F QUICK START GUIDE CR500ia-1F Appliance Document Version: PL QSG500ia-1F/96000/10.02.0.0.473/08082012 G H I J CR500ia-1F ECS Enter DEFAULTS Default
Unified Threat Management
 A B A C B D C E D F E F POWER CF/HDD POWER CF/HDD Unified Threat Management Console Console Future-ready CR 200iNG-XP Future-ready CR 300iNG-XP QUICK START GUIDE CR200iNG-XP Appliance CR300iNG-XP Appliance
A B A C B D C E D F E F POWER CF/HDD POWER CF/HDD Unified Threat Management Console Console Future-ready CR 200iNG-XP Future-ready CR 300iNG-XP QUICK START GUIDE CR200iNG-XP Appliance CR300iNG-XP Appliance
Security Quick Sales Guide
 Security Quick Sales Guide Security Quick Finder Product/Segment Model 200 ~ 500 PC Users USG 2000 75 ~ 200 PC Users USG 1000 50 ~ 75 PC Users USG 300 Unified Security Gateway 25 ~ 50 PC Users USG 200
Security Quick Sales Guide Security Quick Finder Product/Segment Model 200 ~ 500 PC Users USG 2000 75 ~ 200 PC Users USG 1000 50 ~ 75 PC Users USG 300 Unified Security Gateway 25 ~ 50 PC Users USG 200
Security with Passion. Endian UTM Virtual Appliance
 Security with Passion Endian UTM Virtual Appliance Endian UTM Virtual Appliance Endian UTM Virtual Appliance: Secure and Protect your Virtual Infrastructure Whether you are securing your internal virtual
Security with Passion Endian UTM Virtual Appliance Endian UTM Virtual Appliance Endian UTM Virtual Appliance: Secure and Protect your Virtual Infrastructure Whether you are securing your internal virtual
EN6200 Series Feature Sheet
 + 7500 Successful Installation EN6200 Series Feature Sheet Security Solutions Antivirus UTM AAA User Management VPN Connectivity www.tacitine.com EN 6200 Series Unified Threat Management with AAA Hotspot
+ 7500 Successful Installation EN6200 Series Feature Sheet Security Solutions Antivirus UTM AAA User Management VPN Connectivity www.tacitine.com EN 6200 Series Unified Threat Management with AAA Hotspot
Secure and Always Online Networking for Small- to Medium-sized Businesses
 Secure and Always Online Networking for Small- to Medium-sized Businesses High-performance, high-value Next Generation Firewall (NGFW) for small and medium-sized businesses Anti-malware protection with
Secure and Always Online Networking for Small- to Medium-sized Businesses High-performance, high-value Next Generation Firewall (NGFW) for small and medium-sized businesses Anti-malware protection with
Administrator s Guide Ver 2.0
 Administrator s Guide Ver 2.0 Copyright & License Information Copyright 2017 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication may be reproduced, duplicated or modified in any
Administrator s Guide Ver 2.0 Copyright & License Information Copyright 2017 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication may be reproduced, duplicated or modified in any
Unified Threat Management
 Unified Threat Management QUICK START GUIDE CR15iNG Appliance Document Version: PL QSG 15iNG/96000-10.04.5.0.007/250121014 USB DEFAULTS Default IP addresses Ethernet Port IP Address Zone A 172.16.16.16/255.255.255.0
Unified Threat Management QUICK START GUIDE CR15iNG Appliance Document Version: PL QSG 15iNG/96000-10.04.5.0.007/250121014 USB DEFAULTS Default IP addresses Ethernet Port IP Address Zone A 172.16.16.16/255.255.255.0
Check Point 1100 Appliances Frequently Asked Questions
 CHECK POINT SOFTWARE TECHNOLOGIES Check Point 1100 Appliances Frequently Asked Questions Table of Contents Overview:... 2 Ordering Information:... 3 Technology:... 4 Hardware:... 6 Performance:... 6 Updated
CHECK POINT SOFTWARE TECHNOLOGIES Check Point 1100 Appliances Frequently Asked Questions Table of Contents Overview:... 2 Ordering Information:... 3 Technology:... 4 Hardware:... 6 Performance:... 6 Updated
NSG50/100/200 Nebula Cloud Managed Security Gateway
 NSG50/100/200 The Zyxel is built with remote management and ironclad security for organizations with multiple distributed sites. With an extensive suite of security features including ICSAcertified firewall,
NSG50/100/200 The Zyxel is built with remote management and ironclad security for organizations with multiple distributed sites. With an extensive suite of security features including ICSAcertified firewall,
NSG50/100/200 Nebula Cloud Managed Security Gateway
 NSG50/100/200 Managed The Zyxel Managed is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive suite of security features
NSG50/100/200 Managed The Zyxel Managed is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive suite of security features
Quick Sales Guide. Security
 Quick Sales Guide Security Security Quick Finder Product/Segment Model Unified Security Gateway USG 100/USG 100-PLUS USG 20/20W ZyWALL 1100 VPN Firewall ZyWALL 310 ZyWALL 110 ZyWALL OTPv2/OTP-MOBI Security
Quick Sales Guide Security Security Quick Finder Product/Segment Model Unified Security Gateway USG 100/USG 100-PLUS USG 20/20W ZyWALL 1100 VPN Firewall ZyWALL 310 ZyWALL 110 ZyWALL OTPv2/OTP-MOBI Security
Q-Balancer Range FAQ The Q-Balance LB Series General Sales FAQ
 Q-Balancer Range FAQ The Q-Balance LB Series The Q-Balance Balance Series is designed for Small and medium enterprises (SMEs) to provide cost-effective solutions for link resilience and load balancing
Q-Balancer Range FAQ The Q-Balance LB Series The Q-Balance Balance Series is designed for Small and medium enterprises (SMEs) to provide cost-effective solutions for link resilience and load balancing
Systrome Next Gen Firewalls
 N E T K S Systrome Next Gen Firewalls Systrome s Next Generation Firewalls provides comprehensive security protection from layer 2 to layer 7 for the mobile Internet era. The new next generation security
N E T K S Systrome Next Gen Firewalls Systrome s Next Generation Firewalls provides comprehensive security protection from layer 2 to layer 7 for the mobile Internet era. The new next generation security
*1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2.
 PA-500 PA-220 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID, User-ID,
PA-500 PA-220 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID, User-ID,
AccessEnforcer Version 4.0 Features List
 AccessEnforcer Version 4.0 Features List AccessEnforcer UTM Firewall is the simple way to secure and manage your small business network. You can choose from six hardware models, each designed to protect
AccessEnforcer Version 4.0 Features List AccessEnforcer UTM Firewall is the simple way to secure and manage your small business network. You can choose from six hardware models, each designed to protect
HS5200 Series AAA Hotspot Solutions
 + 7500 Successful Installation Authentication Authorisation Accounting HS5200 Series AAA Solutions For Educational Segment Lorem ipsum User Management & Bandwidth Management Co-Works with Any Access Points
+ 7500 Successful Installation Authentication Authorisation Accounting HS5200 Series AAA Solutions For Educational Segment Lorem ipsum User Management & Bandwidth Management Co-Works with Any Access Points
Endian Hotspot main features
 Endian Hotspot main features Service Customization Freely configurable home page after successful login Completely customizable welcome page and printed user information through a user friendly visual
Endian Hotspot main features Service Customization Freely configurable home page after successful login Completely customizable welcome page and printed user information through a user friendly visual
UTM. (Unified Threat Manager) Support for signatures from Snort VRT and Emerging Threat.
 UTM (Unified Threat Manager) Intrusion Prevention based Snort 2.9. Support for signatures from Snort VRT and Emerging Threat. HTTP/SSL Web Proxy based on Squid 3.1.20 URL Filtering with Internet DB from
UTM (Unified Threat Manager) Intrusion Prevention based Snort 2.9. Support for signatures from Snort VRT and Emerging Threat. HTTP/SSL Web Proxy based on Squid 3.1.20 URL Filtering with Internet DB from
NSG100 Nebula Cloud Managed Security Gateway
 Managed Security Gateway The Zyxel Nebula Cloud Managed Security Gateway is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive
Managed Security Gateway The Zyxel Nebula Cloud Managed Security Gateway is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive
USG310/210/110. Benefits. Always online. Protection and optimization. Next Generation Firewall (NGFW) for small and medium-sized businesses
 Next Generation Firewall (NGFW) for small and medium-sized businesses with firewall, anti-virus, antispam, content filtering, IDP, next-generation application intelligence and SSL inspection connectivity
Next Generation Firewall (NGFW) for small and medium-sized businesses with firewall, anti-virus, antispam, content filtering, IDP, next-generation application intelligence and SSL inspection connectivity
Surat Smart City Development Ltd. Surat Municipal Corporation 1
 Surat Smart City Development Ltd. Surat Municipal Corporation 1 Surat Smart City Development Limited (SSCDL) ADDENDUM AND CORRIGENDUM-1 Name of the work: - [SSCDL-Network-01-2018] The Bidders are requested
Surat Smart City Development Ltd. Surat Municipal Corporation 1 Surat Smart City Development Limited (SSCDL) ADDENDUM AND CORRIGENDUM-1 Name of the work: - [SSCDL-Network-01-2018] The Bidders are requested
Powerful, Robust Anti-malware Protection for Medium-sized Businesses
 Powerful, Robust Anti-malware Protection for Medium-sized Businesses High-performance, high-value Next Generation Firewall (NGFW) for medium-sized businesses and campuses Anti-malware protection with firewall,
Powerful, Robust Anti-malware Protection for Medium-sized Businesses High-performance, high-value Next Generation Firewall (NGFW) for medium-sized businesses and campuses Anti-malware protection with firewall,
MX Sizing Guide. 4Gon Tel: +44 (0) Fax: +44 (0)
 MX Sizing Guide FEBRUARY 2015 This technical document provides guidelines for choosing the right Cisco Meraki security appliance based on real-world deployments, industry standard benchmarks and in-depth
MX Sizing Guide FEBRUARY 2015 This technical document provides guidelines for choosing the right Cisco Meraki security appliance based on real-world deployments, industry standard benchmarks and in-depth
*1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2.
 PA-3020 PA-850 PA-820 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID,
PA-3020 PA-850 PA-820 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID,
Angelo Gentili Head of Business Development, EMEA Region, PartnerNET
 Angelo Gentili Head of Business Development, EMEA Region, PartnerNET The Innovation Solution in the Business Security Field. PartnerNet introduces Seqrite Welcome To Dynamic. Scalable. Future-Ready. Why
Angelo Gentili Head of Business Development, EMEA Region, PartnerNET The Innovation Solution in the Business Security Field. PartnerNet introduces Seqrite Welcome To Dynamic. Scalable. Future-Ready. Why
*1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2.
 PA-220 PA-200 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID, User-ID,
PA-220 PA-200 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID, User-ID,
ZyWALL USG100-PLUS Unified Security Gateway. Security on a New Level. Benefits. - The Future Is Ahead. Stay Ahead with ZyXEL USG100-PLUS
 Layer 7 Application Firewall Robust security without sacrificing performance Transparent proxy (HTTP redirect) Robust hybrid VPN (IPSec/SSL/LTP) - Zero-configuration remote access with EASY VPN - Support
Layer 7 Application Firewall Robust security without sacrificing performance Transparent proxy (HTTP redirect) Robust hybrid VPN (IPSec/SSL/LTP) - Zero-configuration remote access with EASY VPN - Support
Gigabit SSL VPN Security Router
 As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is the ideal to help the SMBs increase the
As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is the ideal to help the SMBs increase the
All-in one security for large and medium-sized businesses.
 All-in one security for large and medium-sized businesses www.entensys.com sales@entensys.com Overview UserGate UTM provides firewall, intrusion detection, anti-malware, spam and content filtering, and
All-in one security for large and medium-sized businesses www.entensys.com sales@entensys.com Overview UserGate UTM provides firewall, intrusion detection, anti-malware, spam and content filtering, and
Product SuperMassive 9200 SuperMassive 9400 SuperMassive 9600 Part Numbers
 SuperMassive 9000 Series Product SuperMassive 9200 SuperMassive 9400 SuperMassive 9600 Market Positioning and Bundled Services General Features Across all SM 9000 Appliances Specifications Nodes Cores
SuperMassive 9000 Series Product SuperMassive 9200 SuperMassive 9400 SuperMassive 9600 Market Positioning and Bundled Services General Features Across all SM 9000 Appliances Specifications Nodes Cores
Endpoint web control overview guide
 Endpoint web control overview guide Sophos Web Appliance Sophos UTM (version 9.2 or later) Sophos Enterprise Console Sophos Endpoint Security and Control Contents 1 Endpoint web control...3 2 Enterprise
Endpoint web control overview guide Sophos Web Appliance Sophos UTM (version 9.2 or later) Sophos Enterprise Console Sophos Endpoint Security and Control Contents 1 Endpoint web control...3 2 Enterprise
Seqrite Antivirus for Server
 Best server security with optimum performance. Product Highlights Easy installation, optimized antivirus scanning, and minimum resource utilization. Robust and interoperable technology makes it one of
Best server security with optimum performance. Product Highlights Easy installation, optimized antivirus scanning, and minimum resource utilization. Robust and interoperable technology makes it one of
Seqrite Cloud. Integrated cloud console for Endpoint Security and UTM. Seqrite Managed Security Service Portal (MSSP)
 Managed Security Service Portal (MSSP) Enterprise Security Solutions by Quick Heal Seqrite Integrated cloud console for Endpoint Security and UTM Product Highlights A single cost-effective solution to
Managed Security Service Portal (MSSP) Enterprise Security Solutions by Quick Heal Seqrite Integrated cloud console for Endpoint Security and UTM Product Highlights A single cost-effective solution to
Security with Passion Secure your Business with Endian UTM
 Security with Passion Endian UTM Security Gateways Secure your Business with Endian UTM Unlimited : No user licensing limitations for all functionality (VPN included) Fully Loaded: Every product has all
Security with Passion Endian UTM Security Gateways Secure your Business with Endian UTM Unlimited : No user licensing limitations for all functionality (VPN included) Fully Loaded: Every product has all
Cisco Meraki MX products come in 6 models. The chart below outlines MX hardware properties for each model:
 MX Sizing Guide AUGUST 2016 This technical document provides guidelines for choosing the right Cisco Meraki security appliance based on real-world deployments, industry standard benchmarks and in-depth
MX Sizing Guide AUGUST 2016 This technical document provides guidelines for choosing the right Cisco Meraki security appliance based on real-world deployments, industry standard benchmarks and in-depth
*1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2.
 PA-3020 PA-500 PA-200 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID,
PA-3020 PA-500 PA-200 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID,
*1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2.
 PA-3060 PA-3050 PA-3020 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID,
PA-3060 PA-3050 PA-3020 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID,
WHG711 Wireless LAN Controller
 WHG711 Wireless LAN Controller Wireless INTRODUCTION The WHG711 is an enterprise-grade wireless LAN controller that provides establishments such as hotels, universities, or even complete municipalities
WHG711 Wireless LAN Controller Wireless INTRODUCTION The WHG711 is an enterprise-grade wireless LAN controller that provides establishments such as hotels, universities, or even complete municipalities
*1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2.
 PA-200 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID, User-ID, IPS,
PA-200 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID, User-ID, IPS,
Barracuda Firewall Release Notes 6.6.X
 Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
*1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2.
 PA-5050 PA-5020 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID, User-ID,
PA-5050 PA-5020 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID, User-ID,
ZyWALL VPN2S VPN Firewall
 ZyWALL 2S Firewall The ZyWALL 2S is designed for small businesses, branch offices and home/remote workers. it provides you Internet connections with high reliability, high performance and high security
ZyWALL 2S Firewall The ZyWALL 2S is designed for small businesses, branch offices and home/remote workers. it provides you Internet connections with high reliability, high performance and high security
QUICKSTART GUIDE FOR BRANCH SRX SERIES SERVICES GATEWAYS
 APPLICATION NOTE QUICKSTART GUIDE FOR BRANCH SRX SERIES SERVICES GATEWAYS Configuring Basic Security and Connectivity on Branch SRX Series Services Gateways Copyright 2009, Juniper Networks, Inc. Table
APPLICATION NOTE QUICKSTART GUIDE FOR BRANCH SRX SERIES SERVICES GATEWAYS Configuring Basic Security and Connectivity on Branch SRX Series Services Gateways Copyright 2009, Juniper Networks, Inc. Table
JURUMANI MERAKI CLOUD MANAGED SECURITY & SD-WAN
 JURUMANI CLOUD MANAGED SECURITY & SD-WAN SECURITY BY DESIGN OVERVIEW Cisco Meraki MX Security Appliances are ideal for organizations considering a Unified Threat Managment (UTM) solution, for distributed
JURUMANI CLOUD MANAGED SECURITY & SD-WAN SECURITY BY DESIGN OVERVIEW Cisco Meraki MX Security Appliances are ideal for organizations considering a Unified Threat Managment (UTM) solution, for distributed
Deploy and Manage a Highly Scalable, Worry-Free WLAN
 Deploy and Manage a Highly Scalable, Worry-Free WLAN Centralized WLAN management and auto provisioning Manages up to 512 APs with granular access control ZyMESH simplifies complex, inconvenient cabling
Deploy and Manage a Highly Scalable, Worry-Free WLAN Centralized WLAN management and auto provisioning Manages up to 512 APs with granular access control ZyMESH simplifies complex, inconvenient cabling
Sophos Migration Assistant. migration guide
 Sophos Migration Assistant migration guide Contents Preface... 1 Prerequisites... 2 Convert SG/UTM configuration to Sophos XG Firewall-compatible configuration... 3 Reimaging and applying configuration...8
Sophos Migration Assistant migration guide Contents Preface... 1 Prerequisites... 2 Convert SG/UTM configuration to Sophos XG Firewall-compatible configuration... 3 Reimaging and applying configuration...8
Unified Threat Management
 Datasheet EN6200 Q 15 Unified Threat Management USB Port 3G/4G VGA Power Input Combo LAN/WAN LAN Modern Day UTM For Every Office In today s world, Cyber threats are same for all types of modern business.
Datasheet EN6200 Q 15 Unified Threat Management USB Port 3G/4G VGA Power Input Combo LAN/WAN LAN Modern Day UTM For Every Office In today s world, Cyber threats are same for all types of modern business.
GPZ Next Generation UTM Appliances
 GPZ 1000 - Next Generation UTM Appliances The gateprotect GPZ 1000 next generation fi rewall appliance has been designed as an entry-level product for the redundant Enterprise series for larger networks.
GPZ 1000 - Next Generation UTM Appliances The gateprotect GPZ 1000 next generation fi rewall appliance has been designed as an entry-level product for the redundant Enterprise series for larger networks.
Secure and Always Online Networking for Small- to Medium-sized Businesses
 Secure and Always Online Networking for Small- to Medium-sized Businesses High-performance, high-value Next Generation Firewall (NGFW) for small and medium-sized businesses Anti-malware protection with
Secure and Always Online Networking for Small- to Medium-sized Businesses High-performance, high-value Next Generation Firewall (NGFW) for small and medium-sized businesses Anti-malware protection with
*1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2.
 PA-3020 PA-500 PA-200 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID,
PA-3020 PA-500 PA-200 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID,
Minutes of Meeting of the Designated Technical Bid Evaluation Committee in regard to e-tender for Procurement of UTM at STPI Noida.
 SOFTWARE TECHNOLOGY PARKS OF INDIA NOIDA 29 th Sept 2015 Minutes of Meeting of the Designated Technical Bid Evaluation Committee in regard to e-tender for Procurement of UTM at STPI Noida. File Ref No:
SOFTWARE TECHNOLOGY PARKS OF INDIA NOIDA 29 th Sept 2015 Minutes of Meeting of the Designated Technical Bid Evaluation Committee in regard to e-tender for Procurement of UTM at STPI Noida. File Ref No:
VPN- Next-Generation Firewall (NGFW) 1/46
 VPN- Next-Generation Firewall (NGFW) 1/46 AR AR7xx Next-Generation Firewall (NGFW) VPN Firewall 2/46 3/46 AR AR7xx VPN AT-AR415S 1 x PIC WAN 1 x 10/100TX WAN 4 x 10/100TX LAN 1 x RS232 50 VPN 95 Mbps 3DES
VPN- Next-Generation Firewall (NGFW) 1/46 AR AR7xx Next-Generation Firewall (NGFW) VPN Firewall 2/46 3/46 AR AR7xx VPN AT-AR415S 1 x PIC WAN 1 x 10/100TX WAN 4 x 10/100TX LAN 1 x RS232 50 VPN 95 Mbps 3DES
Next-Generation Firewall Series Datasheet
 RUIJIE NETWORKS COMPANY LIMITED www.ruijienetworks.com Ruijie 1600 Next-Generation Firewall Series Datasheet Ruijie 1600 Firewall Series is a collection of nextgeneration firewall offering security, routing
RUIJIE NETWORKS COMPANY LIMITED www.ruijienetworks.com Ruijie 1600 Next-Generation Firewall Series Datasheet Ruijie 1600 Firewall Series is a collection of nextgeneration firewall offering security, routing
Quick Heal Mobile Device Management. Available on
 Available on Infinite Devices. One Unified Solution. Quick Heal A simple yet powerful solution, Quick Heal is a unified platform for managing and monitoring multiple mobile devices within your enterprise
Available on Infinite Devices. One Unified Solution. Quick Heal A simple yet powerful solution, Quick Heal is a unified platform for managing and monitoring multiple mobile devices within your enterprise
N-Dimension n-platform 340S Unified Threat Management System
 N-Dimension n-platform 340S Unified Threat Management System Firewall Router Site-to-Site VPN Remote-Access VPN Serial SCADA VPN Proxy Anti-virus SCADA IDS Port Scanner Vulnerability Scanner System & Service
N-Dimension n-platform 340S Unified Threat Management System Firewall Router Site-to-Site VPN Remote-Access VPN Serial SCADA VPN Proxy Anti-virus SCADA IDS Port Scanner Vulnerability Scanner System & Service
McAfee NGFW Installation Guide for Firewall/VPN Role 5.7. NGFW Engine in the Firewall/VPN Role
 McAfee NGFW Installation Guide for Firewall/VPN Role 5.7 NGFW Engine in the Firewall/VPN Role Legal Information The use of the products described in these materials is subject to the then current end-user
McAfee NGFW Installation Guide for Firewall/VPN Role 5.7 NGFW Engine in the Firewall/VPN Role Legal Information The use of the products described in these materials is subject to the then current end-user
Next Generation Firewalls For Your Network Security
 Our On-Premises Managed Firewall services go beyond perimeter protection; providing a new Web and Unified Threat Management (UTM) security feature. The solution combines the best-of-breed technologies.
Our On-Premises Managed Firewall services go beyond perimeter protection; providing a new Web and Unified Threat Management (UTM) security feature. The solution combines the best-of-breed technologies.
Meraki MX Family Cloud Managed Security Appliances
 DATASHEET Meraki MX Family Cloud Managed Security Appliances Overview The Meraki MX is a complete next generation firewall and branch gateway solution, designed to make distributed networks fast, secure,
DATASHEET Meraki MX Family Cloud Managed Security Appliances Overview The Meraki MX is a complete next generation firewall and branch gateway solution, designed to make distributed networks fast, secure,
SuperMassive 9000 Series
 SuperMassive 9 Series Product SuperMassive 92 SuperMassive 94 SuperMassive 96 SuperMassive 98 Part Numbers Market Positioning and Bundled Services General Features Across all SM 9 Appliances Specifications
SuperMassive 9 Series Product SuperMassive 92 SuperMassive 94 SuperMassive 96 SuperMassive 98 Part Numbers Market Positioning and Bundled Services General Features Across all SM 9 Appliances Specifications
USG 50/20/20W Sales Kits
 USG 50/20/20W Sales Kits Why do more than 400,000 small and mediumsized businesses (SMB) choose ZyWALL in Europe? ZyWALL understand SMBs need "I was impressed with the ZyWALL's high performance while handling
USG 50/20/20W Sales Kits Why do more than 400,000 small and mediumsized businesses (SMB) choose ZyWALL in Europe? ZyWALL understand SMBs need "I was impressed with the ZyWALL's high performance while handling
*1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2.
 Feature PA-7000-20G-NPC PA-5060 Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID,
Feature PA-7000-20G-NPC PA-5060 Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID,
Security Assessment Checklist
 Security Assessment Checklist Westcon Security Checklist - Instructions The first step to protecting your business includes a careful and complete assessment of your security posture. Our Security Assessment
Security Assessment Checklist Westcon Security Checklist - Instructions The first step to protecting your business includes a careful and complete assessment of your security posture. Our Security Assessment
Release Notes. Seqrite Endpoint Security Cloud
 Seqrite Endpoint Security Cloud 1.1.1 Release Notes Seqrite Endpoint Security Cloud www.seqrite.com Copyright Information Copyright 2018 Quick Heal Technologies Ltd. All Rights Reserved. No part of this
Seqrite Endpoint Security Cloud 1.1.1 Release Notes Seqrite Endpoint Security Cloud www.seqrite.com Copyright Information Copyright 2018 Quick Heal Technologies Ltd. All Rights Reserved. No part of this
Training UNIFIED SECURITY. Signature based packet analysis
 Training UNIFIED SECURITY Signature based packet analysis At the core of its scanning technology, Kerio Control integrates a packet analyzer based on Snort. Snort is an open source IDS/IPS system that
Training UNIFIED SECURITY Signature based packet analysis At the core of its scanning technology, Kerio Control integrates a packet analyzer based on Snort. Snort is an open source IDS/IPS system that
High Availability Configuration Guide. Version 10
 Version 10 Document version 1.0 10.6.6.042-24/11/2017 Important Notice Cyberoam Technologies Pvt. Ltd. has supplied this Information believing it to be accurate and reliable at the time of printing, but
Version 10 Document version 1.0 10.6.6.042-24/11/2017 Important Notice Cyberoam Technologies Pvt. Ltd. has supplied this Information believing it to be accurate and reliable at the time of printing, but
Deployment Scenarios Microsoft TMG Standard, TMG Enterprise, TMG Branch Office series Appliances
 Deployment Scenarios Microsoft TMG Standard, TMG Enterprise, TMG Branch Office series Appliances TMG Server 2010 Appliance (ntmg or ntmge Series) provides value to IT managers, network administrators,
Deployment Scenarios Microsoft TMG Standard, TMG Enterprise, TMG Branch Office series Appliances TMG Server 2010 Appliance (ntmg or ntmge Series) provides value to IT managers, network administrators,
UTM Content Security Gateway CS-2001
 UTM Content Security Gateway CS-2001 Quick Installation Guide Table of Contents 1. Package Contents... 3 2. Setup the UTM Content Security Gateway... 4 3. Hardware Installation... 5 4. Basic System Configuration...
UTM Content Security Gateway CS-2001 Quick Installation Guide Table of Contents 1. Package Contents... 3 2. Setup the UTM Content Security Gateway... 4 3. Hardware Installation... 5 4. Basic System Configuration...
Check Point Virtual Systems & Identity Awareness
 Check Point Virtual Systems & Identity Awareness Jason Card, Senior Security Consultant, CISSP card@avantec.ch Agenda Check Point Virtual Systems Private Cloud Simplify Security Overview Identity Awareness
Check Point Virtual Systems & Identity Awareness Jason Card, Senior Security Consultant, CISSP card@avantec.ch Agenda Check Point Virtual Systems Private Cloud Simplify Security Overview Identity Awareness
Unified Threat Management Systems
 Unified Threat Management Systems 500 POWER HDD Another Product by Open Kod TO SOLVE AND TO SECURE www.openkod.com MALAYSIA CYBER SECURITY INNOVATION OF THE YEAR AWARD 2016 WINNER - OPENKOD SDN BHD Unified
Unified Threat Management Systems 500 POWER HDD Another Product by Open Kod TO SOLVE AND TO SECURE www.openkod.com MALAYSIA CYBER SECURITY INNOVATION OF THE YEAR AWARD 2016 WINNER - OPENKOD SDN BHD Unified
*1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2.
 Feature PA-7080 PA-7050 PA-7000-20GQXM-NPC Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured
Feature PA-7080 PA-7050 PA-7000-20GQXM-NPC Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured
VPN Routers DSR-150/250/500/1000AC. Product Highlights. Features. Overview. Comprehensive Management Capabilities. Web Authentication Capabilities
 Product Highlights Comprehensive Management Solution Advanced features such as WAN failover, load balancing, and integrated firewall help make this a reliable, secure, and flexible way to manage your network.
Product Highlights Comprehensive Management Solution Advanced features such as WAN failover, load balancing, and integrated firewall help make this a reliable, secure, and flexible way to manage your network.
Product NSA E5500 NSA E6500 NSA E8500 NSA E8510 Part Numbers. 01-SSC SSC-7028 TotalSecure
 E-Class NSA Series Product NSA E5500 NSA E6500 NSA E8500 NSA E8510 Positioning and Bundled Services General Features Across all NSA Appliances Specifications Nodes Interfaces Stateful Firewall Performance
E-Class NSA Series Product NSA E5500 NSA E6500 NSA E8500 NSA E8510 Positioning and Bundled Services General Features Across all NSA Appliances Specifications Nodes Interfaces Stateful Firewall Performance
Copyright Huawei Technologies Co., Ltd All rights reserved. Trademark Notice General Disclaimer
 Copyright Huawei Technologies Co., Ltd. 2011. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of Huawei Technologies
Copyright Huawei Technologies Co., Ltd. 2011. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of Huawei Technologies
Feature. *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2.
 Performance Feature *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID, User-ID, IPS, antivirus
Performance Feature *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID, User-ID, IPS, antivirus
Wireless Controller DWC-1000
 Network Architecture Manage up to 6 wireless APs, upgradable to 24 APs 1 per controller Control up to 24 wireless APs, maximum 96 APs 1 per cluster Robust Network Security Wireless Instruction Detection
Network Architecture Manage up to 6 wireless APs, upgradable to 24 APs 1 per controller Control up to 24 wireless APs, maximum 96 APs 1 per cluster Robust Network Security Wireless Instruction Detection
Wireless Controller DWC Product Highlights. Features. Robust and Optimised Network. Comprehensive Security
 Product Highlights Reliable, Secure Network Self-healing and self-optimising technology combined with 4 + 4 wireless controller redundancy and RF scanning ensures reliability and performance Easy Guest
Product Highlights Reliable, Secure Network Self-healing and self-optimising technology combined with 4 + 4 wireless controller redundancy and RF scanning ensures reliability and performance Easy Guest
Appliance Comparison Chart
 Security Gateway Appliances 300 300 500 500 5400 5600 5800 5900 Branch Office Small Enterprise Mid-Size Enterprise Real-World Production Conditions Security 60 50 340 45 600 950 750 400 Firewall (Gbps)..
Security Gateway Appliances 300 300 500 500 5400 5600 5800 5900 Branch Office Small Enterprise Mid-Size Enterprise Real-World Production Conditions Security 60 50 340 45 600 950 750 400 Firewall (Gbps)..
DATASHEET. Advanced 6-Port Gigabit VPN Network Router. Model: ER-6. Sophisticated Routing Features. Advanced Security, Monitoring, and Management
 Data Center & Cloud Computing DATASHEET Advanced 6-Port Gigabit VPN Network Router Model: ER-6 Sophisticated Routing Features Advanced Security, Monitoring, and Management High-Performance Gigabit Ports
Data Center & Cloud Computing DATASHEET Advanced 6-Port Gigabit VPN Network Router Model: ER-6 Sophisticated Routing Features Advanced Security, Monitoring, and Management High-Performance Gigabit Ports
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Meraki MX Family Cloud Managed Security Appliances
 DATASHEET Meraki MX Family Cloud Managed Security Appliances Overview The Meraki MX is a complete next generation firewall and branch gateway solution, designed to make distributed networks fast, secure,
DATASHEET Meraki MX Family Cloud Managed Security Appliances Overview The Meraki MX is a complete next generation firewall and branch gateway solution, designed to make distributed networks fast, secure,
*1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2.
 VM-300 VM-200 VM-100 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID,
VM-300 VM-200 VM-100 Feature Performance *1. Firewall throughput measured with App-ID and User-ID features enabled utilizing 64KB HTTP transactions. 2. Threat prevention throughput measured with App-ID,
Unified Services Routers
 Product Highlights Comprehensive Management Solution Active-Active WAN port features such as auto WAN failover and load balancing, ICSA-certified firewall, and D-Link Green Technology make this a reliable,
Product Highlights Comprehensive Management Solution Active-Active WAN port features such as auto WAN failover and load balancing, ICSA-certified firewall, and D-Link Green Technology make this a reliable,
"Charting the Course... MOC A Planning, Deploying and Managing Microsoft Forefront TMG Course Summary
 Description Course Summary The goal of this three-day instructor-led course is to provide students with the knowledge and skills necessary to effectively plan, deploy and manage Microsoft Forefront Threat
Description Course Summary The goal of this three-day instructor-led course is to provide students with the knowledge and skills necessary to effectively plan, deploy and manage Microsoft Forefront Threat
ISG-600 Cloud Gateway
 ISG-600 Cloud Gateway Cumilon ISG Integrated Security Gateway Integrated Security Gateway Cumilon ISG-600C cloud gateway is the security product developed by Systrome for the distributed access network
ISG-600 Cloud Gateway Cumilon ISG Integrated Security Gateway Integrated Security Gateway Cumilon ISG-600C cloud gateway is the security product developed by Systrome for the distributed access network
WHITE PAPER: BEST PRACTICES. Sizing and Scalability Recommendations for Symantec Endpoint Protection. Symantec Enterprise Security Solutions Group
 WHITE PAPER: BEST PRACTICES Sizing and Scalability Recommendations for Symantec Rev 2.2 Symantec Enterprise Security Solutions Group White Paper: Symantec Best Practices Contents Introduction... 4 The
WHITE PAPER: BEST PRACTICES Sizing and Scalability Recommendations for Symantec Rev 2.2 Symantec Enterprise Security Solutions Group White Paper: Symantec Best Practices Contents Introduction... 4 The
DrayTek Vigor Technical Specifications. PPPoE, PPTP, DHCP client, static IP, L2TP*, Ipv6. Redundancy. By WAN interfaces traffic volume
 DrayTek Vigor 3900 Technical Specifications WAN Protocol Ethernet PPPoE, PPTP, DHCP client, static IP, L2TP*, Ipv6 Multi WAN Outbound policy based load balance Allow your local network to access Internet
DrayTek Vigor 3900 Technical Specifications WAN Protocol Ethernet PPPoE, PPTP, DHCP client, static IP, L2TP*, Ipv6 Multi WAN Outbound policy based load balance Allow your local network to access Internet
McAfee Security Management Center
 Data Sheet McAfee Security Management Center Unified management for next-generation devices Key advantages: Single pane of glass across the management lifecycle for McAfee next generation devices. Scalability
Data Sheet McAfee Security Management Center Unified management for next-generation devices Key advantages: Single pane of glass across the management lifecycle for McAfee next generation devices. Scalability
Hillstone E-Series Next-Generation Firewall
 TM Hillstone Next-Generation Firewall Hillstone next generation firewalls provide visibility and control of web applications regardless of port, protocol, or evasive action. It can identify and prevent
TM Hillstone Next-Generation Firewall Hillstone next generation firewalls provide visibility and control of web applications regardless of port, protocol, or evasive action. It can identify and prevent
SRX als NGFW. Michel Tepper Consultant
 SRX als NGFW Michel Tepper Consultant Firewall Security Challenges Organizations are looking for ways to protect their assets amidst today s ever-increasing threat landscape. The latest generation of web-based
SRX als NGFW Michel Tepper Consultant Firewall Security Challenges Organizations are looking for ways to protect their assets amidst today s ever-increasing threat landscape. The latest generation of web-based
NSG50/100 Nebula Cloud Managed Security Gateway
 /100 The Zyxel is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive suite of security features that includes ICSAcertified
/100 The Zyxel is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive suite of security features that includes ICSAcertified
Seqrite Endpoint Security
 Enterprise Security Solutions by Quick Heal Integrated enterprise security and unified endpoint management console Enterprise Suite Edition Product Highlights Innovative endpoint security that prevents
Enterprise Security Solutions by Quick Heal Integrated enterprise security and unified endpoint management console Enterprise Suite Edition Product Highlights Innovative endpoint security that prevents
vshield Administration Guide
 vshield Manager 5.1 vshield App 5.1 vshield Edge 5.1 vshield Endpoint 5.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
vshield Manager 5.1 vshield App 5.1 vshield Edge 5.1 vshield Endpoint 5.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
Powerful, Robust Anti-malware Protection for Medium- to Large-sized Businesses
 Powerful, Robust Anti-malware Protection for Medium- to Large-sized Businesses High-performance, high-value Next Generation Firewall (NGFW) for medium and large-sized businesses and campuses Anti-malware
Powerful, Robust Anti-malware Protection for Medium- to Large-sized Businesses High-performance, high-value Next Generation Firewall (NGFW) for medium and large-sized businesses and campuses Anti-malware
Security on a New Level -The Future Is Ahead. Stay Ahead with ZyXEL USGs.
 Security on a New Level -The Future Is Ahead. Stay Ahead with ZyXEL USGs. Robust security without sacrificing performance Comprehensive support to IPv6 Robust hybrid VPN (IPSec/SSL/TP) Zero-configuration
Security on a New Level -The Future Is Ahead. Stay Ahead with ZyXEL USGs. Robust security without sacrificing performance Comprehensive support to IPv6 Robust hybrid VPN (IPSec/SSL/TP) Zero-configuration
Barracuda Networks Portfolio. Bartłomiej Moczulski Sales Engineer CEE
 Barracuda Networks Portfolio Bartłomiej Moczulski Sales Engineer CEE Overview Filtering Networks Data Storage Barracuda Spam & Virus Firewall Barracuda Load Balancer Barracuda Message Archiver Barracuda
Barracuda Networks Portfolio Bartłomiej Moczulski Sales Engineer CEE Overview Filtering Networks Data Storage Barracuda Spam & Virus Firewall Barracuda Load Balancer Barracuda Message Archiver Barracuda
Appliance Comparison Chart
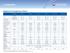 Appliance Comparison Chart Edge 0 70 570 070 070 070 Models Edge X, Edge W, Edge X ADSL, Edge W ADSL 6 7 76 57 576 07 076 07 076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65, R70 R65, R70
Appliance Comparison Chart Edge 0 70 570 070 070 070 Models Edge X, Edge W, Edge X ADSL, Edge W ADSL 6 7 76 57 576 07 076 07 076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65, R70 R65, R70
Microsoft Internet Security & Acceleration Server Overview
 Microsoft Internet Security & Acceleration Server 2006 Overview 1 What is ISA Server 2006? Three Deployment Scenarios Making Exchange, SharePoint and Web application servers available for secure remote
Microsoft Internet Security & Acceleration Server 2006 Overview 1 What is ISA Server 2006? Three Deployment Scenarios Making Exchange, SharePoint and Web application servers available for secure remote
