Network Attack and Defence: State-of- Art, Challenges, and Opportunities
|
|
|
- Darcy Bradford
- 5 years ago
- Views:
Transcription
1 Network Attack and Defence: State-of- Art, Challenges, and Opportunities Dr Shui Yu ( 余水 ) School of Information Technology Deakin University, Melbourne, Australia syu@deakin.edu.au
2 About Deakin, SIT, and Melbourne Deakin University is ranked 214 worldwide by ARWU. School of IT is ranked 123 worldwide by ARWU. At SIT, we are very good at cybersecurity. Melbourne is the most liveable city in the world. We welcome outstanding students for various scholarship applications and visits.
3 Outline Introduction Cybersecurity: detection Cybersecurity: mitigation Cybersecurity: traceback Cybersecurity: privacy Q&A
4 1. Cyberspace, a not well understood space What does the cyberspace look like? What are the features of cyberspace? Many more questions than answers
5 1. Cyberspace: a heaven for intelligent criminals Cyber crime statistics ( Source of Attack Number of Attacks Russia 2,402,722 Taiwan 907,102 Germany 780,425 US Navy sees 110,000 cyber-attacks every hour, or more than 30 every single second. Top 15 Countries/Areas Where Cyber Attacks Originate in February (right table). Ukraine 566,531 Hungary 367,966 USA 355,341 Romania 350,948 Brazil 337,977 Italy 288,607 Australia 255,777 Argentina 185,720 China 168,146 Poland 162,235 Israel 143,943 Japan 133,908
6 1. Cyberspace: a heaven for intelligent criminals Why so many cyber attacks or crimes? - Extraordinary financial or political reward. - Easy to organize attacks. - Hard to be caught.
7 1. Cyberspace: a heaven for intelligent criminals Reasons for the heaven - No-security original design of the Internet. - Limited understanding of the cyberspace. - Shallow understanding of hackers.
8 1. Cybersecurity: a big deal A few recent DDoS attacks - DDoS attacks at USA before the election - DDoS attacks at Australia census night -
9 1. Cybersecurity: a big deal
10 1. Cybersecurity: a big deal
11 1. Cybersecurity, our current understanding Our understanding of the world. Englishman : What is the name of the animal? Aboriginal: Kangaroo
12 1. Cybersecurity, our current understanding Vincent Van Gogh ( ) : see the world in his own eyes.
13 1. Cybersecurity, the problems Current problems Who How Where When What Why
14 1. Cybersecurity, the problems There are three categories in cybersecurity Detection Mitigation Traceback Attack and counter-attack is an endless loop between hackers and defenders
15 2. Cybersecurity: Detection The essential issues in detection Hackers try their best to hide themselves. We need to understand our opponents Detect anomaly by unique features
16 2. Cybersecurity: Detection Malware distribution in large-scale networks - Exponential distribution at the early stage. - Power law distribution with a short exponential tail at the late stage - Power law distribution at the final stage. Shui Yu, Guofei Gu, Ahmed Barnawi, Song Guo, and Ivan Stojmenovic, "Malware Propagation in Large-Scale Networks," IEEE Transactions on Knowledge and Data Engineering, Vol. 27, Issue 1, 2015, pp
17 2. Cybersecurity: Detection We need to improve the old tools, even invent new tools, for detection. We extended the flat one layer epidemic model to two layer to better model malware propagation.
18 2. Cybersecurity: Detection Hackers are exhausting their energy to fly under the radar. - mimicking legitimate behavior to disable our detection. - e.g., DDoS attack vs Flash crowd (11.11 festival)
19 2. Cybersecurity: Detection Discriminate mimicking attack from flash crowd - It is hard to deal with mimicking attacks - The resources that hackers have usually limited - It is critical to find the features to differentiate them Shui Yu, Wanlei Zhou, Weijia Jia, Song Guo, Yong Xiang, and Feilong Tang, Discriminating DDoS Attacks from Flash Crowds Using Flow Correlation Coefficient, IEEE Transactions on Parallel and Distributed Systems, Vol. 23, Issue 6, June 2012, pp
20 2. Cybersecurity: Detection There is an essential fact - Active bots of a botnet are around 1k - Legitimate computers of a flash crowd has about 10k concurrent users We used a second order statistics method to discriminate mimicking attack from flash crowd
21 3. Cybersecurity: mitigation Mitigation is important for counter attacks. - What are the critical factors in mitigation - Is it possible? Is it affordable? - How to implement mitigation if it is possible?
22 3. Cybersecurity: mitigation The essential factors in cyber battle (e.g., in DDoS case). - It is a competition of resources - the winner is the party who has relatively more resources than the other party. Shui Yu, Song Guo, and Ivan Stojmenovic, "Fool Me If You Can: Mimicking Attacks and Anti-attacks in Cyberspace," IEEE Transactions on Computers, Vol. 64 Issue 1, 2015, pp
23 3. Cybersecurity: mitigation Following the previous finding, can we beat DDoS attacks or not? - It is very hard in the traditional Internet - But, we can in clouds. Shui Yu, Yonghong Tian, Song Guo, and Dapeng Oliver Wu, "Can We Beat DDoS Attacks in Clouds?" IEEE Transactions on Parallel and Distributed Systems, vol 25, no 9, 2014, pp
24 3. Cybersecurity: mitigation We can beat DDoS attacks in clouds in terms of resource and cost
25 4. Cybersecurity: traceback Finding the attack sources or hackers are the critical solution to remove threats. - It is hard in the non-cooperative environment of the Internet - It is hard in the heterogeneous complex systems Shui Yu, Wanlei Zhou, Robin Doss, and Weijia Jia, Traceback DDoS Attacks using Entropy Variations, IEEE Transactions on Parallel and Distributed Systems, vol. 22, No. 3, March, 2011,
26 4. Cybersecurity: traceback - The mainstream of traceback is packet marking, but it suffers a scalability problem, and therefore not feasible - We invented a flow entropy based traceback method - New methodology besides packet marking - But hard to implement in the Internet environment Shui Yu, Wanlei Zhou, Robin Doss, and Weijia Jia, Traceback DDoS Attacks using Entropy Variations, IEEE Transactions on Parallel and Distributed Systems, vol. 22, No. 3, March, 2011, pp
27 4. Cybersecurity: traceback A flow entropy based traceback method
28 4. Cybersecurity: traceback Packet marking is an effective method, but not practical due to the scalability problem. - We need to identify the problems? (How to addressed the scalability problem of packet marking?) - Study the problem deeply, and offer solutions Shui Yu, Wanlei Zhou, Song Guo, and Minyi Guo, "A Feasible IP Traceback Framework through Dynamic Deterministic Packet Marking," IEEE Transactions on Computers, Vol 65, No 5, pp
29 4. Cybersecurity: traceback We found that - Not every internet router is evolved in an attack. - Using a round-robin method to utilize the marking space resource. Shui Yu, Wanlei Zhou, Song Guo, and Minyi Guo, "A Feasible IP Traceback Framework through Dynamic Deterministic Packet Marking," IEEE Transactions on Computers, Vol 65, No 5, pp
30 4. Cybersecurity: traceback Attack source traceback in social networks. - Reverse traceback - Effective distance Jiaojiao Jiang, Sheng Wen, Shui Yu, Yang Xiang, and Wanlei Zhou, "K-center: An Approach on the Multi-source Identification of Information Diffusion," IEEE Transactions on Information Forensics and Security, vol 10, no 12, 2015, pp
31 5. Cybersecurity: privacy in big data era Privacy is new critical issue - Big data, big problem (Science, 2014) - The end of privacy in big data era (Science, 2015 January)
32 5. Cybersecurity: privacy in big data era Six blind men and an elephant our current understanding of privacy
33 5. Cybersecurity: privacy in big data era Shui Yu, Big Privacy: Challenges and Opportunities in Privacy Study in the Age of Big Data, IEEE Access, no. 4, 2016, pp
34 5. Cybersecurity: privacy in big data era Shui Yu, Big Privacy: Challenges and Opportunities in Privacy Study in the Age of Big Data, IEEE Access, no. 4, 2016, pp
35 5. Cybersecurity: privacy in big data era First Challenge: privacy measurement. I can calculate the movement of stars, but cannot measure the madness (privacy) of men
36 5. Cybersecurity: privacy in big data era Other challenges in big data privacy - personalized privacy - theoretical tools for privacy (mathematical tools, models) - privacy for trading -
37 Thank you & Questions The mentioned papers can be downloaded from the website
IDENTIFYING MALICIOUS DATA IN SOCIAL MEDIA
 IDENTIFYING MALICIOUS DATA IN SOCIAL MEDIA M.Sai Sri Lakshmi Yellari 1, M.Manisha 2, J.Dhanesh 3,M.Srinivasa Rao 4,Dr.S.Suhasini 5 1Student, Dept. of Information Technology, Velagapudi Ramakrishna Siddhartha
IDENTIFYING MALICIOUS DATA IN SOCIAL MEDIA M.Sai Sri Lakshmi Yellari 1, M.Manisha 2, J.Dhanesh 3,M.Srinivasa Rao 4,Dr.S.Suhasini 5 1Student, Dept. of Information Technology, Velagapudi Ramakrishna Siddhartha
Fool Me If You Can: Mimicking Attacks and Anti-Attacks in Cyberspace
 IEEE TRANSACTIONS ON COMPUTERS, VOL. 64, NO. 1, JANUARY 2015 139 Fool Me If You Can: Mimicking Attacks and Anti-Attacks in Cyberspace Shui Yu, Senior Member, IEEE, Song Guo, Senior Member, IEEE, and Ivan
IEEE TRANSACTIONS ON COMPUTERS, VOL. 64, NO. 1, JANUARY 2015 139 Fool Me If You Can: Mimicking Attacks and Anti-Attacks in Cyberspace Shui Yu, Senior Member, IEEE, Song Guo, Senior Member, IEEE, and Ivan
A Feasible IP Traceback Framework through Dynamic Deterministic Packet Marking
 1 A Feasible IP Traceback Framework through Dynamic Deterministic Packet Marking Shui Yu, Senior Member, IEEE, Wanlei Zhou, Senior Member, IEEE, Song Guo, Senior Member, IEEE, and Minyi Guo, Senior Member,
1 A Feasible IP Traceback Framework through Dynamic Deterministic Packet Marking Shui Yu, Senior Member, IEEE, Wanlei Zhou, Senior Member, IEEE, Song Guo, Senior Member, IEEE, and Minyi Guo, Senior Member,
DDOS Attack Prevention Technique in Cloud
 DDOS Attack Prevention Technique in Cloud Priyanka Dembla, Chander Diwaker CSE Department, U.I.E.T Kurukshetra University Kurukshetra, Haryana, India Email: priyankadembla05@gmail.com Abstract Cloud computing
DDOS Attack Prevention Technique in Cloud Priyanka Dembla, Chander Diwaker CSE Department, U.I.E.T Kurukshetra University Kurukshetra, Haryana, India Email: priyankadembla05@gmail.com Abstract Cloud computing
Romania - Cyber Security Strategy. 6th IT STAR Workshop on Digital Security
 Romania - Cyber Security Strategy 6th IT STAR Workshop on Digital Security 30 March 2012 Bratislava, Slovakia Florin VREJOIU Horia GLIGOR Programme Manager Member of the Board Association for Information
Romania - Cyber Security Strategy 6th IT STAR Workshop on Digital Security 30 March 2012 Bratislava, Slovakia Florin VREJOIU Horia GLIGOR Programme Manager Member of the Board Association for Information
Packets Flow-Based Intrusion Detection Technique for Websites
 Packets Flow-Based Intrusion Detection Technique for Websites 1 S. Vijayanand, PG Student, Department of Computer Applications, Sathyabama University, Chennai-600 119. 2 Mrs. C. Deepa, Assistant Professor,
Packets Flow-Based Intrusion Detection Technique for Websites 1 S. Vijayanand, PG Student, Department of Computer Applications, Sathyabama University, Chennai-600 119. 2 Mrs. C. Deepa, Assistant Professor,
Discriminating DDoS Attacks from Flash Crowds in IPv6 networks using Entropy Variations and Sibson distance metric
 Discriminating DDoS Attacks from Flash Crowds in IPv6 networks using Entropy Variations and Sibson distance metric HeyShanthiniPandiyaKumari.S 1, Rajitha Nair.P 2 1 (Department of Computer Science &Engineering,
Discriminating DDoS Attacks from Flash Crowds in IPv6 networks using Entropy Variations and Sibson distance metric HeyShanthiniPandiyaKumari.S 1, Rajitha Nair.P 2 1 (Department of Computer Science &Engineering,
MITIGATION OF DENIAL OF SERVICE ATTACK USING ICMP BASED IP TRACKBACK. J. Gautam, M. Kasi Nivetha, S. Anitha Sri and P. Madasamy
 MITIGATION OF DENIAL OF SERVICE ATTACK USING ICMP BASED IP TRACKBACK J. Gautam, M. Kasi Nivetha, S. Anitha Sri and P. Madasamy Department of Information Technology, Velammal College of Engineering and
MITIGATION OF DENIAL OF SERVICE ATTACK USING ICMP BASED IP TRACKBACK J. Gautam, M. Kasi Nivetha, S. Anitha Sri and P. Madasamy Department of Information Technology, Velammal College of Engineering and
SIMULATION OF THE COMBINED METHOD
 SIMULATION OF THE COMBINED METHOD Ilya Levin 1 and Victor Yakovlev 2 1 The Department of Information Security of Systems, State University of Telecommunication, St.Petersburg, Russia lyowin@gmail.com 2
SIMULATION OF THE COMBINED METHOD Ilya Levin 1 and Victor Yakovlev 2 1 The Department of Information Security of Systems, State University of Telecommunication, St.Petersburg, Russia lyowin@gmail.com 2
Low-rate and High-rate Distributed DoS Attack Detection Using Partial Rank Correlation
 Low-rate and High-rate Distributed DoS Attack Detection Using Partial Rank Correlation Monowar H. Bhuyan and Abhishek Kalwar Dept. of Computer Science & Engg. Kaziranga University, Jorhat-785006, Assam
Low-rate and High-rate Distributed DoS Attack Detection Using Partial Rank Correlation Monowar H. Bhuyan and Abhishek Kalwar Dept. of Computer Science & Engg. Kaziranga University, Jorhat-785006, Assam
IN this paper, we present a novel flow similarity-based
 IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS, VOL. 23, NO. 6, JUNE 2012 1073 Discriminating DDoS Attacks from Flash Crowds Using Flow Correlation Coefficient Shui Yu, Member, IEEE, Wanlei Zhou,
IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS, VOL. 23, NO. 6, JUNE 2012 1073 Discriminating DDoS Attacks from Flash Crowds Using Flow Correlation Coefficient Shui Yu, Member, IEEE, Wanlei Zhou,
Israel Internet Security Threat Profile
 Israel Internet Security Threat Profile Worldwide Ranking.%.%.%.%.%.%.%.%.%.%.% Overall Average Spam Zombies Malicious Code Phishing Hosts Bots Network Attacking Countries Copyright Symantec Corporation.
Israel Internet Security Threat Profile Worldwide Ranking.%.%.%.%.%.%.%.%.%.%.% Overall Average Spam Zombies Malicious Code Phishing Hosts Bots Network Attacking Countries Copyright Symantec Corporation.
A Cooperative Multilayer End-Point Approach to Mitigate DDoS Attack
 A Cooperative Multilayer End-Point Approach to Mitigate DDoS Attack S RENUKA DEVI, S SARASWATHI, P YOGESH Department of Information Science and Technology, College of Engineering Guindy, Anna University,
A Cooperative Multilayer End-Point Approach to Mitigate DDoS Attack S RENUKA DEVI, S SARASWATHI, P YOGESH Department of Information Science and Technology, College of Engineering Guindy, Anna University,
Can We Beat Legitimate Cyber Behavior Mimicking Attacks from Botnets?
 The 31st Annual IEEE International Conference on Computer Communications: Mini-Conference Can We Beat Legitimate Cyber Behavior Mimicking Attacks from Botnets? Shui Yu SIT, Deakin University Victoria,
The 31st Annual IEEE International Conference on Computer Communications: Mini-Conference Can We Beat Legitimate Cyber Behavior Mimicking Attacks from Botnets? Shui Yu SIT, Deakin University Victoria,
Security in India: Enabling a New Connected Era
 White Paper Security in India: Enabling a New Connected Era India s economy is growing rapidly, and the country is expanding its network infrastructure to support digitization. India s leapfrogging mobile
White Paper Security in India: Enabling a New Connected Era India s economy is growing rapidly, and the country is expanding its network infrastructure to support digitization. India s leapfrogging mobile
RATING ASSOCIATION FOR SHORT DEGREE DDOS ATTACK RECOGNITION
 RATING ASSOCIATION FOR SHORT DEGREE DDOS ATTACK RECOGNITION 1 Prof.C.Thangamalar 2 Dr.K.Ravikumar 1 Research and Development Centre, Bharathiar University, Coimbatore 641046. 2 Assistant Professor, Dept.of.Computer
RATING ASSOCIATION FOR SHORT DEGREE DDOS ATTACK RECOGNITION 1 Prof.C.Thangamalar 2 Dr.K.Ravikumar 1 Research and Development Centre, Bharathiar University, Coimbatore 641046. 2 Assistant Professor, Dept.of.Computer
Phishing Activity Trends Report August, 2005
 Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Phishing Activity Trends Report August, 25 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial
Certified Cyber Security Analyst VS-1160
 VS-1160 Certified Cyber Security Analyst Certification Code VS-1160 Vskills certification for Cyber Security Analyst assesses the candidate as per the company s need for cyber security and forensics. The
VS-1160 Certified Cyber Security Analyst Certification Code VS-1160 Vskills certification for Cyber Security Analyst assesses the candidate as per the company s need for cyber security and forensics. The
Systemic Analyser in Network Threats
 Systemic Analyser in Network Threats www.project-saint.eu @saintprojecteu #saintprojecteu John M.A. Bothos jbothos@iit.demokritos.gr Integrated System Laboratory Institute of Informatics & Telecommunication
Systemic Analyser in Network Threats www.project-saint.eu @saintprojecteu #saintprojecteu John M.A. Bothos jbothos@iit.demokritos.gr Integrated System Laboratory Institute of Informatics & Telecommunication
DoS Cyber Attack on a Government Agency in Europe- April 2012 Constantly Changing Attack Vectors
 DoS Cyber Attack on a Government Agency in Europe- April 2012 Constantly Changing Attack Vectors 1 Table of Content Preamble...3 About Radware s DefensePro... 3 About Radware s Emergency Response Team
DoS Cyber Attack on a Government Agency in Europe- April 2012 Constantly Changing Attack Vectors 1 Table of Content Preamble...3 About Radware s DefensePro... 3 About Radware s Emergency Response Team
A WEB BASED APPROACH TO DETECT MIMICKING ATTACKS IN HOMOGENEOUS ENVIRONMENT
 A WEB BASED APPROACH TO DETECT MIMICKING ATTACKS IN HOMOGENEOUS ENVIRONMENT R. Padmapriya and S. Igni Sabasti Prabu Information technology, Sathyabama University, Chennai, India E-Mail: padmapriyacse60@gmail.com
A WEB BASED APPROACH TO DETECT MIMICKING ATTACKS IN HOMOGENEOUS ENVIRONMENT R. Padmapriya and S. Igni Sabasti Prabu Information technology, Sathyabama University, Chennai, India E-Mail: padmapriyacse60@gmail.com
Simulation of Rank Correlation Based Detection Mechanism for Distributed Denial of Services Attacks
 International Journal of Computer (IJC) ISSN 2307-4523 (Print & Online) Global Society of Scientific Research and Researchers http://ijcjournal.org/ Simulation of Rank Correlation Based Detection Mechanism
International Journal of Computer (IJC) ISSN 2307-4523 (Print & Online) Global Society of Scientific Research and Researchers http://ijcjournal.org/ Simulation of Rank Correlation Based Detection Mechanism
CyberSecurity Training and Capacity Building: A Starting Point for Collaboration and Partnerships. from the most trusted name in information security
 CyberSecurity Training and Capacity Building: A Starting Point for Collaboration and Partnerships About SANS The SANS (SysAdmin, Audit, Network, Security) Institute Established in 1989 Cooperative research
CyberSecurity Training and Capacity Building: A Starting Point for Collaboration and Partnerships About SANS The SANS (SysAdmin, Audit, Network, Security) Institute Established in 1989 Cooperative research
A Study on Preventive Methods used for Distributed Denial of Service Attacks
 ISSN UA Volume 01 Issue 01 June-2018 A Study on Preventive Methods used for Distributed Denial of Service Attacks Vaivbhav Tyagi 1 and Umakant Dwivedi 1 Available online at: www.xournals.com Received 14
ISSN UA Volume 01 Issue 01 June-2018 A Study on Preventive Methods used for Distributed Denial of Service Attacks Vaivbhav Tyagi 1 and Umakant Dwivedi 1 Available online at: www.xournals.com Received 14
Assessment for all units is ongoing and continuous consisting of tests, assignments and reports. Most units have a final two-hour examination.
 Diploma of Computing Course Outline (T3, 2017) Campus Intake CRICOS Course Duration Teaching Methods Assessment Course Structure Units Melbourne Burwood Campus / Jakarta Campus, Indonesia March, June,
Diploma of Computing Course Outline (T3, 2017) Campus Intake CRICOS Course Duration Teaching Methods Assessment Course Structure Units Melbourne Burwood Campus / Jakarta Campus, Indonesia March, June,
The situation of threats in cyberspace in the first half of 2018
 The situation of threats in cyberspace in the first half of 2018 1. Cyber-attacks (1) Scanning activities in cyberspace a. Overview of unexpected incoming packets to the sensors 1 The number of unexpected
The situation of threats in cyberspace in the first half of 2018 1. Cyber-attacks (1) Scanning activities in cyberspace a. Overview of unexpected incoming packets to the sensors 1 The number of unexpected
Cyber Security: Threat and Prevention
 Expand Your Horizons Webinar Series Cyber Security: Threat and Prevention February 24, 2015 1:00 1:45pm The Webinar will begin shortly. You can ask a question in the box on the right hand side. We will
Expand Your Horizons Webinar Series Cyber Security: Threat and Prevention February 24, 2015 1:00 1:45pm The Webinar will begin shortly. You can ask a question in the box on the right hand side. We will
Eight units must be completed and passed to be awarded the Diploma.
 Diploma of Computing Course Outline Campus Intake CRICOS Course Duration Teaching Methods Assessment Course Structure Units Melbourne Burwood Campus / Jakarta Campus, Indonesia March, June, October 022638B
Diploma of Computing Course Outline Campus Intake CRICOS Course Duration Teaching Methods Assessment Course Structure Units Melbourne Burwood Campus / Jakarta Campus, Indonesia March, June, October 022638B
CLASSIFICATION OF LINK BASED IDENTIFICATION RESISTANT TO DRDOS ATTACKS
 CLASSIFICATION OF LINK BASED IDENTIFICATION RESISTANT TO DRDOS ATTACKS 1 S M ZAHEER, 2 V.VENKATAIAH 1 M.Tech, Department of CSE, CMR College Of Engineering & Technology, Kandlakoya Village, Medchal Mandal,
CLASSIFICATION OF LINK BASED IDENTIFICATION RESISTANT TO DRDOS ATTACKS 1 S M ZAHEER, 2 V.VENKATAIAH 1 M.Tech, Department of CSE, CMR College Of Engineering & Technology, Kandlakoya Village, Medchal Mandal,
ITU Regional Cybersecurity Forum for Asia-Pacific
 ITU Regional Cybersecurity Forum for Asia-Pacific Incident Management Capabilities Australia Country Case Study Graham Ingram General Manager AusCERT July 2008 Copyright 2008 AusCERT Not for further distribution
ITU Regional Cybersecurity Forum for Asia-Pacific Incident Management Capabilities Australia Country Case Study Graham Ingram General Manager AusCERT July 2008 Copyright 2008 AusCERT Not for further distribution
The NextGen cyber crime battlefield. Why organizations will always lose this battle
 The NextGen cyber crime battlefield. Why organizations will always lose this battle Enforce cyber threat intelligence into your organization 10 April 2014 KPMG has been awarded with the Europe Awards as
The NextGen cyber crime battlefield. Why organizations will always lose this battle Enforce cyber threat intelligence into your organization 10 April 2014 KPMG has been awarded with the Europe Awards as
The emerging battle between Cyber Defense and Cybercrime: How Technology is changing to keep Company and HR data safe
 The emerging battle between Cyber Defense and Cybercrime: How Technology is changing to keep Company and HR data safe Copyright 2017 Protocol 46, Inc. All Rights Reserved Copyright 2017 Protocol 46, Inc.
The emerging battle between Cyber Defense and Cybercrime: How Technology is changing to keep Company and HR data safe Copyright 2017 Protocol 46, Inc. All Rights Reserved Copyright 2017 Protocol 46, Inc.
Malware Research at SMU. Tom Chen SMU
 Malware Research at SMU Tom Chen SMU tchen@engr.smu.edu www.engr.smu.edu/~tchen Outline About SMU and Me Virus Research Lab Early Worm Detection Epidemic Modeling New Research Interests TC/BT/11-5-04 SMU
Malware Research at SMU Tom Chen SMU tchen@engr.smu.edu www.engr.smu.edu/~tchen Outline About SMU and Me Virus Research Lab Early Worm Detection Epidemic Modeling New Research Interests TC/BT/11-5-04 SMU
Diploma Of Computing
 Diploma Of Computing Course Outline Campus Intake CRICOS Course Duration Teaching Methods Assessment Course Structure Units Melbourne Burwood Campus / Jakarta Campus, Indonesia March, June, October 022638B
Diploma Of Computing Course Outline Campus Intake CRICOS Course Duration Teaching Methods Assessment Course Structure Units Melbourne Burwood Campus / Jakarta Campus, Indonesia March, June, October 022638B
NETWORKING. 8. ITDNW08 Congestion Control for Web Real-Time Communication
 NETWORKING 1. ITDNW01 Wormhole: The Hidden Virus Propagation Power of a Search Engine in Social 2. ITDNW02 Congestion Control for Background Data Transfers With Minimal Delay Impact 3. ITDNW03 Transient
NETWORKING 1. ITDNW01 Wormhole: The Hidden Virus Propagation Power of a Search Engine in Social 2. ITDNW02 Congestion Control for Background Data Transfers With Minimal Delay Impact 3. ITDNW03 Transient
TRACEBACK OF DOS OVER AUTONOMOUS SYSTEMS
 TRACEBACK OF DOS OVER AUTONOMOUS SYSTEMS Mohammed Alenezi 1 and Martin J Reed 2 1 School of Computer Science and Electronic Engineering, University of Essex, UK mnmale@essex.ac.uk 2 School of Computer
TRACEBACK OF DOS OVER AUTONOMOUS SYSTEMS Mohammed Alenezi 1 and Martin J Reed 2 1 School of Computer Science and Electronic Engineering, University of Essex, UK mnmale@essex.ac.uk 2 School of Computer
ENISA EU Threat Landscape
 ENISA EU Threat Landscape 24 th February 2015 Dr Steve Purser ENISA Head of Department European Union Agency for Network and Information Security www.enisa.europa.eu Agenda ENISA Areas of Activity Key
ENISA EU Threat Landscape 24 th February 2015 Dr Steve Purser ENISA Head of Department European Union Agency for Network and Information Security www.enisa.europa.eu Agenda ENISA Areas of Activity Key
Battle between hackers and machine learning. Alexey Lukatsky Cybersecurity Business Consultant April 03, 2019
 Battle between hackers and machine learning Alexey Lukatsky Cybersecurity Business Consultant April 03, 2019 Google: facts and numbers Real Cisco Big Data for Security Training Set Why is Machine Learning
Battle between hackers and machine learning Alexey Lukatsky Cybersecurity Business Consultant April 03, 2019 Google: facts and numbers Real Cisco Big Data for Security Training Set Why is Machine Learning
Phishing Activity Trends Report August, 2006
 Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Phishing Activity Trends Report, 26 Phishing is a form of online identity theft that employs both social engineering and technical subterfuge to steal consumers' personal identity data and financial account
Computer Information Systems (CIS) CIS 105 Current Operating Systems/Security CIS 101 Introduction to Computers
 Computer Information Systems (CIS) CIS 101 Introduction to Computers This course provides an overview of the computing field and its typical applications. Key terminology and components of computer hardware,
Computer Information Systems (CIS) CIS 101 Introduction to Computers This course provides an overview of the computing field and its typical applications. Key terminology and components of computer hardware,
Top 10 Global Threat Rank by Source
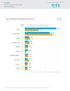 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco
 What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
What can we lose not implementing proper security in our IT environment? Aleksandar Pavlovic Security Account Manager Cisco Increasing Digital Traffic Creates a Greater Attack Surface Global IP Traffic
Think Oslo 2018 Where Technology Meets Humanity. Oslo. Felicity March Cyber Resilience - Europe
 Think Oslo 2018 Where Technology Meets Humanity Oslo Felicity March Cyber Resilience - Europe Cyber Resilience Cyber Resilience is the ability of an organisation to maintain its core purpose and integrity
Think Oslo 2018 Where Technology Meets Humanity Oslo Felicity March Cyber Resilience - Europe Cyber Resilience Cyber Resilience is the ability of an organisation to maintain its core purpose and integrity
Vincent van Kooten, EMEA North Fraud & Risk Intelligence Specialist RSA, The Security Division of EMC
 Vincent van Kooten, EMEA North Fraud & Risk Intelligence Specialist RSA, The Security Division of EMC 1 2013 2 3 in 4 3 5.900.000.000 $ 4 RSA s Top 10 List 5 RSA s top 10 phishing list Copyright 2014 EMC
Vincent van Kooten, EMEA North Fraud & Risk Intelligence Specialist RSA, The Security Division of EMC 1 2013 2 3 in 4 3 5.900.000.000 $ 4 RSA s Top 10 List 5 RSA s top 10 phishing list Copyright 2014 EMC
Driving Internet of Things (IoT) standardization to build smart sustainable cities. Cristina Bueti, Adviser, ITU
 Driving Internet of Things (IoT) standardization to build smart sustainable cities Cristina Bueti, Adviser, ITU The world is Mobile broadband penetration globally is reaching 47% in 2015, a value that
Driving Internet of Things (IoT) standardization to build smart sustainable cities Cristina Bueti, Adviser, ITU The world is Mobile broadband penetration globally is reaching 47% in 2015, a value that
Digital Forensic Science: Ideas, Gaps and the Future. Dr. Joshua I. James
 Digital Forensic Science: Ideas, Gaps and the Future Dr. Joshua I. James Joshua@cybercrimetech.com 2015-08-09 Overview Digital Forensic Science where are we now? Past Present Where are we going? Future
Digital Forensic Science: Ideas, Gaps and the Future Dr. Joshua I. James Joshua@cybercrimetech.com 2015-08-09 Overview Digital Forensic Science where are we now? Past Present Where are we going? Future
CYBERSECURITY: Scholarship and Job Opportunities
 CYBERSECURITY: Scholarship and Job Opportunities Malware Invasion in Cyberspace Blackhole Malware Exploit Kit (2012) Shamoon Virus (2012) Stuxnet Worm (2010) Operation Aurora (2009) and many others Job
CYBERSECURITY: Scholarship and Job Opportunities Malware Invasion in Cyberspace Blackhole Malware Exploit Kit (2012) Shamoon Virus (2012) Stuxnet Worm (2010) Operation Aurora (2009) and many others Job
Information Technology
 Courses - Victoria 2017 This document has been developed to assist students and parents in researching undergraduate information technology and computer science courses. It isn t an exhaustive list, and
Courses - Victoria 2017 This document has been developed to assist students and parents in researching undergraduate information technology and computer science courses. It isn t an exhaustive list, and
Using Game Theory To Solve Network Security. A brief survey by Willie Cohen
 Using Game Theory To Solve Network Security A brief survey by Willie Cohen Network Security Overview By default networks are very insecure There are a number of well known methods for securing a network
Using Game Theory To Solve Network Security A brief survey by Willie Cohen Network Security Overview By default networks are very insecure There are a number of well known methods for securing a network
Cybersecurity Risk Mitigation: Protect Your Member Data. Introduction
 Cybersecurity Risk Mitigation: Protect Your Member Data Presented by Matt Mitchell, CISSP Knowledge Consulting Group Introduction Matt Mitchell- Director Risk Assurance 17 years information security experience
Cybersecurity Risk Mitigation: Protect Your Member Data Presented by Matt Mitchell, CISSP Knowledge Consulting Group Introduction Matt Mitchell- Director Risk Assurance 17 years information security experience
A Secure Method to Deliver Access Tokens to End Hosts
 A Secure Method to Deliver Access Tokens to End Hosts Dr.V Asha 1, Ashwini M 2, Divyansh 3 1,2,3 Department of Master of Computer Applications, New Horizon College of Engineering, Abstract--IP traceback
A Secure Method to Deliver Access Tokens to End Hosts Dr.V Asha 1, Ashwini M 2, Divyansh 3 1,2,3 Department of Master of Computer Applications, New Horizon College of Engineering, Abstract--IP traceback
EU funded research is keeping up trust in digital society
 EU funded research is keeping up trust in digital society Rafael Tesoro Trust and Security Unit DG Communica5ons Networks, Content and Technology European Commission Cybersecurity Strategy of the EU: An
EU funded research is keeping up trust in digital society Rafael Tesoro Trust and Security Unit DG Communica5ons Networks, Content and Technology European Commission Cybersecurity Strategy of the EU: An
Effective Scheme for Reducing Spam in System
 Effective Scheme for Reducing Spam in Email System 1 S. Venkatesh, 2 K. Geetha, 3 P. Manju Priya, 4 N. Metha Rani 1 Assistant Professor, 2,3,4 UG Scholar Department of Computer science and engineering
Effective Scheme for Reducing Spam in Email System 1 S. Venkatesh, 2 K. Geetha, 3 P. Manju Priya, 4 N. Metha Rani 1 Assistant Professor, 2,3,4 UG Scholar Department of Computer science and engineering
Security is one of the biggest concerns today. Ever since the advent of the 21 st century, the world has been facing several challenges regarding the
 Security is one of the biggest concerns today. Ever since the advent of the 21 st century, the world has been facing several challenges regarding the security of people, economy, and infrastructure. One
Security is one of the biggest concerns today. Ever since the advent of the 21 st century, the world has been facing several challenges regarding the security of people, economy, and infrastructure. One
State of the Internet Security Q Mihnea-Costin Grigore Security Technical Project Manager
 State of the Internet Security Q2 2017 Mihnea-Costin Grigore Security Technical Project Manager Topics 1. Introduction 2. DDoS Attack Trends 3. Web Application Attack Trends 4. Spotlights 5. Resources
State of the Internet Security Q2 2017 Mihnea-Costin Grigore Security Technical Project Manager Topics 1. Introduction 2. DDoS Attack Trends 3. Web Application Attack Trends 4. Spotlights 5. Resources
ISO in the world today
 ISO 27001 in the world today 1 Agenda ISO 27001 worldwide Why ISO 27001 Framework to implement ISO 27001 2 ISO 27001 worldwide Source: ISO Annual Survey 3 ISO 27001 worldwide Number of Certificates Year
ISO 27001 in the world today 1 Agenda ISO 27001 worldwide Why ISO 27001 Framework to implement ISO 27001 2 ISO 27001 worldwide Source: ISO Annual Survey 3 ISO 27001 worldwide Number of Certificates Year
Computer Information Systems (CIS) CIS 105 Current Operating Systems/Security CIS 101 Introduction to Computers
 Computer Information Systems (CIS) CIS 101 Introduction to Computers This course provides an overview of the computing field and its typical applications. Key terminology and components of computer hardware,
Computer Information Systems (CIS) CIS 101 Introduction to Computers This course provides an overview of the computing field and its typical applications. Key terminology and components of computer hardware,
Identifying Spoofed Packets Origin using Hop Count Filtering and Defence Mechanisms against Spoofing Attacks
 Identifying Spoofed Packets Origin using Hop Count Filtering and Defence Mechanisms against Spoofing Attacks Israel Umana 1, Sornalakshmi Krishnan 2 1 M.Tech Student, Information Security and Cyber Forensic,
Identifying Spoofed Packets Origin using Hop Count Filtering and Defence Mechanisms against Spoofing Attacks Israel Umana 1, Sornalakshmi Krishnan 2 1 M.Tech Student, Information Security and Cyber Forensic,
Preempting Cyber Fraud: SWIFT Threat Indicator Sharing Tool. Cyber Security 3.0 Better Together August 18, 2017
 Preempting Cyber Fraud: SWIFT Threat Indicator Sharing Tool Cyber Security 3.0 Better Together August 18, 2017 Research Overview Problem Statement Research Goals & Methodology Defining Insider Cashout
Preempting Cyber Fraud: SWIFT Threat Indicator Sharing Tool Cyber Security 3.0 Better Together August 18, 2017 Research Overview Problem Statement Research Goals & Methodology Defining Insider Cashout
Analysis of Detection Mechanism of Low Rate DDoS Attack Using Robust Random Early Detection Algorithm
 Analysis of Detection Mechanism of Low Rate DDoS Attack Using Robust Random Early Detection Algorithm 1 Shreeya Shah, 2 Hardik Upadhyay 1 Research Scholar, 2 Assistant Professor 1 IT Systems & Network
Analysis of Detection Mechanism of Low Rate DDoS Attack Using Robust Random Early Detection Algorithm 1 Shreeya Shah, 2 Hardik Upadhyay 1 Research Scholar, 2 Assistant Professor 1 IT Systems & Network
Flow Based DetectingDDoS Attack in Large Scale Network by Using Entropy Variation Technique
 Flow Based DetectingDDoS Attack in Large Scale Network by Using Entropy Variation Technique V.Deepa,V.Nandhini Abstract A distributed denial-of-service (DDoS) attack is an attempt to make a computer resource
Flow Based DetectingDDoS Attack in Large Scale Network by Using Entropy Variation Technique V.Deepa,V.Nandhini Abstract A distributed denial-of-service (DDoS) attack is an attempt to make a computer resource
BUILDING A NEXT-GENERATION FIREWALL
 How to Add Network Intelligence, Security, and Speed While Getting to Market Faster INNOVATORS START HERE. EXECUTIVE SUMMARY Your clients are on the front line of cyberspace and they need your help. Faced
How to Add Network Intelligence, Security, and Speed While Getting to Market Faster INNOVATORS START HERE. EXECUTIVE SUMMARY Your clients are on the front line of cyberspace and they need your help. Faced
Enhanced Multivariate Correlation Analysis (MCA) Based Denialof-Service
 International Journal of Computer Science & Mechatronics A peer reviewed International Journal Article Available online www.ijcsm.in smsamspublications.com Vol.1.Issue 2. 2015 Enhanced Multivariate Correlation
International Journal of Computer Science & Mechatronics A peer reviewed International Journal Article Available online www.ijcsm.in smsamspublications.com Vol.1.Issue 2. 2015 Enhanced Multivariate Correlation
Commonwealth Cyber Declaration
 Commonwealth Cyber Declaration Recognising that the development of cyberspace has made a powerful contribution to the economic, social, cultural and political life of the Commonwealth; Underlining that
Commonwealth Cyber Declaration Recognising that the development of cyberspace has made a powerful contribution to the economic, social, cultural and political life of the Commonwealth; Underlining that
!!!!!!!!!!!!!!!!!!!!!!!!!!!"!#$%%!&'!"(&)'*!!!!!!"#$%!&'(!)*+',+%!!
 "#$%%&'"(&)'* "#$%&'()*+',+% -&..+*/0+1*'2"#$%&'()*+',+% #,3410,$3*41(,3%&'()*+',+#,0531+67/-&..+*/0+1*' "'+3*(50+1*' For too long, service providers have been getting a free pass on addressing some of
"#$%%&'"(&)'* "#$%&'()*+',+% -&..+*/0+1*'2"#$%&'()*+',+% #,3410,$3*41(,3%&'()*+',+#,0531+67/-&..+*/0+1*' "'+3*(50+1*' For too long, service providers have been getting a free pass on addressing some of
Advanced IT Risk, Security management and Cybercrime Prevention
 Advanced IT Risk, Security management and Cybercrime Prevention Course Goal and Objectives Information technology has created a new category of criminality, as cybercrime offers hackers and other tech-savvy
Advanced IT Risk, Security management and Cybercrime Prevention Course Goal and Objectives Information technology has created a new category of criminality, as cybercrime offers hackers and other tech-savvy
THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION BREACH & ATTACK SIMULATION
 BREACH & ATTACK SIMULATION THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION Cymulate s cyber simulation platform allows you to test your security assumptions, identify possible security gaps and receive
BREACH & ATTACK SIMULATION THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION Cymulate s cyber simulation platform allows you to test your security assumptions, identify possible security gaps and receive
Global DDoS Threat Landscape
 DDOS REPORT Global DDoS Threat Landscape OVERVIEW Overview The number of network layer attacks continued to fall in, the fourth consecutive quarterly drop since peaking in Q2 2016. After reaching a record
DDOS REPORT Global DDoS Threat Landscape OVERVIEW Overview The number of network layer attacks continued to fall in, the fourth consecutive quarterly drop since peaking in Q2 2016. After reaching a record
The Global Cybercrime Industry
 Nir Kshetri The Global Cybercrime Industry Economic, Institutional and Strategic Perspectives 4y Springer 1 The Global Cybercrime Industry and Its Structure: Relevant Actors, Motivations, Threats, and
Nir Kshetri The Global Cybercrime Industry Economic, Institutional and Strategic Perspectives 4y Springer 1 The Global Cybercrime Industry and Its Structure: Relevant Actors, Motivations, Threats, and
Xiang, Yang and Zhou, Wanlei 2005, Mark-aided distributed filtering by using neural network for DDoS defense, in GLOBECOM '05 : IEEE Global
 Xiang, Yang and Zhou, Wanlei 25, Mark-aided distributed filtering by using neural network for DDoS defense, in GLOBECOM '5 : IEEE Global Telecommunications Conference, 28 November-2 December 25 St. Louis,
Xiang, Yang and Zhou, Wanlei 25, Mark-aided distributed filtering by using neural network for DDoS defense, in GLOBECOM '5 : IEEE Global Telecommunications Conference, 28 November-2 December 25 St. Louis,
PROACTIVE & DETECTION STRATEGY DESIGNING FOR DRDOS ATTACK
 PROACTIVE & DETECTION STRATEGY DESIGNING FOR DRDOS ATTACK Dipika Mahire Amruta Amune 1 Department of Computer Engineering, 2 Professor, Department of Computer Engineering, G. H. Raisoni Collage of Engineering
PROACTIVE & DETECTION STRATEGY DESIGNING FOR DRDOS ATTACK Dipika Mahire Amruta Amune 1 Department of Computer Engineering, 2 Professor, Department of Computer Engineering, G. H. Raisoni Collage of Engineering
The fast track to top skills and top jobs in cyber. Guaranteed. FREE TO TRANSITIONING VETERANS
 The fast track to top skills and top jobs in cyber. Guaranteed. FREE TO TRANSITIONING VETERANS WELCOME SANS Institute is presenting the SANS VetSuccess Immersion Academy in the DC Metro area. For transitioning
The fast track to top skills and top jobs in cyber. Guaranteed. FREE TO TRANSITIONING VETERANS WELCOME SANS Institute is presenting the SANS VetSuccess Immersion Academy in the DC Metro area. For transitioning
Trustworthy ICT. FP7-ICT Objective 1.5 WP 2013
 Trustworthy ICT FP7-ICT-2013-10 Objective 1.5 WP 2013 1 General Overview Focused in a limited number of technologies in emerging application of high economic impact in the security area, Cloud Computing
Trustworthy ICT FP7-ICT-2013-10 Objective 1.5 WP 2013 1 General Overview Focused in a limited number of technologies in emerging application of high economic impact in the security area, Cloud Computing
CSIRT capacity building Andrea Dufkova CSIRT-relations, COD1 NLO meeting Athens June 8. European Union Agency for Network and Information Security
 CSIRT capacity building Andrea Dufkova CSIRT-relations, COD1 NLO meeting Athens June 8 European Union Agency for Network and Information Security Capacity and community building for CSIRTs 2005 Start up
CSIRT capacity building Andrea Dufkova CSIRT-relations, COD1 NLO meeting Athens June 8 European Union Agency for Network and Information Security Capacity and community building for CSIRTs 2005 Start up
AN ANALYSIS OF CYBER CRIME AND INTERNET SECURITY
 WORLD JOURNAL OF PHARMACY AND PHARMACEUTICAL SCIENCES Shoba. SJIF Impact Factor 6.647 Volume 6, Issue 5, 304-308 Review Article ISSN 2278 4357 AN ANALYSIS OF CYBER CRIME AND INTERNET SECURITY *Prof. V.
WORLD JOURNAL OF PHARMACY AND PHARMACEUTICAL SCIENCES Shoba. SJIF Impact Factor 6.647 Volume 6, Issue 5, 304-308 Review Article ISSN 2278 4357 AN ANALYSIS OF CYBER CRIME AND INTERNET SECURITY *Prof. V.
COMPUTER FORENSICS (CFRS)
 Computer Forensics (CFRS) 1 COMPUTER FORENSICS (CFRS) 500 Level Courses CFRS 500: Introduction to Forensic Technology and Analysis. 3 credits. Presents an overview of technologies of interest to forensics
Computer Forensics (CFRS) 1 COMPUTER FORENSICS (CFRS) 500 Level Courses CFRS 500: Introduction to Forensic Technology and Analysis. 3 credits. Presents an overview of technologies of interest to forensics
Cyber Security: What s the Big Deal?
 Cyber Security: What s the Big Deal? (and why it matters to you!) Debasis Bhattacharya, UHMC Jodi Ito, CISO, UH ITS maui.hawaii.edu/cybersecurity What is Cybersecurity? cy ber: adjective of, relating to,
Cyber Security: What s the Big Deal? (and why it matters to you!) Debasis Bhattacharya, UHMC Jodi Ito, CISO, UH ITS maui.hawaii.edu/cybersecurity What is Cybersecurity? cy ber: adjective of, relating to,
Behavioral Analysis for Intrusion Resilience. Ahmed Fawaz Dec 6, 2016
 Behavioral Analysis for Intrusion Resilience Ahmed Fawaz Dec 6, 2016 1 Recent Cyber Attacks on Private and Public Entities 2 Design for Resiliency Diverse Monitoring Secure Monitoring Monitoring Fusion
Behavioral Analysis for Intrusion Resilience Ahmed Fawaz Dec 6, 2016 1 Recent Cyber Attacks on Private and Public Entities 2 Design for Resiliency Diverse Monitoring Secure Monitoring Monitoring Fusion
A SYSTEM FOR DETECTION AND PRVENTION OF PATH BASED DENIAL OF SERVICE ATTACK
 A SYSTEM FOR DETECTION AND PRVENTION OF PATH BASED DENIAL OF SERVICE ATTACK P.Priya 1, S.Tamilvanan 2 1 M.E-Computer Science and Engineering Student, Bharathidasan Engineering College, Nattrampalli. 2
A SYSTEM FOR DETECTION AND PRVENTION OF PATH BASED DENIAL OF SERVICE ATTACK P.Priya 1, S.Tamilvanan 2 1 M.E-Computer Science and Engineering Student, Bharathidasan Engineering College, Nattrampalli. 2
Cyber Security Strategy
 Cyber Security Strategy Committee for Home Affairs Introduction Cyber security describes the technology, processes and safeguards that are used to protect our networks, computers, programs and data from
Cyber Security Strategy Committee for Home Affairs Introduction Cyber security describes the technology, processes and safeguards that are used to protect our networks, computers, programs and data from
MARKET NEWSLETTER No 69 February 2013
 Standing at 543 600 t, Spanish olive oil production in the first four months of 2012/13 was 62 pc down on the previous season, according to Spain s Olive Oil Agency. Although there are still some months
Standing at 543 600 t, Spanish olive oil production in the first four months of 2012/13 was 62 pc down on the previous season, according to Spain s Olive Oil Agency. Although there are still some months
National Cyber Security Operations Center (N-CSOC) Stakeholders' Conference
 National Cyber Security Operations Center (N-CSOC) Stakeholders' Conference Benefits to the Stakeholders A Collaborative and Win-Win Strategy Lal Dias Chief Executive Officer Sri Lanka CERT CC Cyber attacks
National Cyber Security Operations Center (N-CSOC) Stakeholders' Conference Benefits to the Stakeholders A Collaborative and Win-Win Strategy Lal Dias Chief Executive Officer Sri Lanka CERT CC Cyber attacks
COST OF CYBER CRIME STUDY INSIGHTS ON THE SECURITY INVESTMENTS THAT MAKE A DIFFERENCE
 2017 COST OF CYBER CRIME STUDY INSIGHTS ON THE SECURITY INVESTMENTS THAT MAKE A DIFFERENCE NUMBER OF SECURITY BREACHES IS RISING AND SO IS SPEND Average number of security breaches each year 130 Average
2017 COST OF CYBER CRIME STUDY INSIGHTS ON THE SECURITY INVESTMENTS THAT MAKE A DIFFERENCE NUMBER OF SECURITY BREACHES IS RISING AND SO IS SPEND Average number of security breaches each year 130 Average
StreamWorks A System for Real-Time Graph Pattern Matching on Network Traffic
 StreamWorks A System for Real-Time Graph Pattern Matching on Network Traffic GEORGE CHIN, SUTANAY CHOUDHURY AND KHUSHBU AGARWAL Pacific Northwest National Laboratory 1 Emerging Graph Patterns Goal: Detect
StreamWorks A System for Real-Time Graph Pattern Matching on Network Traffic GEORGE CHIN, SUTANAY CHOUDHURY AND KHUSHBU AGARWAL Pacific Northwest National Laboratory 1 Emerging Graph Patterns Goal: Detect
International Journal of Intellectual Advancements and Research in Engineering Computations
 ISSN:2348-2079 Volume-6 Issue-2 International Journal of Intellectual Advancements and Research in Engineering Computations Local flow packet marking for network coding in manets P. Vasanthakumar, Mrs.
ISSN:2348-2079 Volume-6 Issue-2 International Journal of Intellectual Advancements and Research in Engineering Computations Local flow packet marking for network coding in manets P. Vasanthakumar, Mrs.
Challenges and Opportunities in Cyber Physical System Research
 Homeland Security Advanced Research Projects Agency Challenges and Opportunities in Cyber Physical System Research Dec 11, 2013 ACSAC Panel Dr. Dan Massey Program Manager Cyber Security Program Areas Trustworthy
Homeland Security Advanced Research Projects Agency Challenges and Opportunities in Cyber Physical System Research Dec 11, 2013 ACSAC Panel Dr. Dan Massey Program Manager Cyber Security Program Areas Trustworthy
Cyber Security Technologies
 1 / Cyber Security Technologies International Seminar on Cyber Security: An Action to Establish the National Cyber Security Center Lisbon, 12 th September 2013 23 / Key highlights - Thales Group Thales
1 / Cyber Security Technologies International Seminar on Cyber Security: An Action to Establish the National Cyber Security Center Lisbon, 12 th September 2013 23 / Key highlights - Thales Group Thales
OVERVIEW OF SUBJECT REQUIREMENTS
 Course Bachelor of Information Technology (Network Security) Course Number HE20524 Location Meadowbank OVERVIEW OF SUBJECT REQUIREMENTS Note: This document is intended as a guide only. Enrolling students
Course Bachelor of Information Technology (Network Security) Course Number HE20524 Location Meadowbank OVERVIEW OF SUBJECT REQUIREMENTS Note: This document is intended as a guide only. Enrolling students
Digital Opportunity Index. Michael Minges Telecommunications Management Group, Inc.
 Digital Opportunity Index Michael Minges Telecommunications Management Group, Inc. Digital Opportunity Index (DOI) Why How Preliminary results Conclusions WSIS Plan of Action E. Follow-up and evaluation
Digital Opportunity Index Michael Minges Telecommunications Management Group, Inc. Digital Opportunity Index (DOI) Why How Preliminary results Conclusions WSIS Plan of Action E. Follow-up and evaluation
The fast track to top skills and top jobs in cyber. Guaranteed. FREE TO TRANSITIONING VETERANS
 The fast track to top skills and top jobs in cyber. Guaranteed. FREE TO TRANSITIONING VETERANS WELCOME SANS Institute, in collaboration with Augusta Warrior Project and Augusta University, is presenting
The fast track to top skills and top jobs in cyber. Guaranteed. FREE TO TRANSITIONING VETERANS WELCOME SANS Institute, in collaboration with Augusta Warrior Project and Augusta University, is presenting
RETRIEVAL OF DATA IN DDoS ATTACKS BY TRACKING ATTACKERS USING NODE OPTIMIZATION TECHNIQUE
 RETRIEVAL OF DATA IN DDoS ATTACKS BY TRACKING ATTACKERS USING NODE OPTIMIZATION TECHNIQUE G.Sindhu AP/CSE Kalaivanicollege of technology *Mail-id:sindhugnsn24@gmail.com ABSTRACT: attempt derives from a
RETRIEVAL OF DATA IN DDoS ATTACKS BY TRACKING ATTACKERS USING NODE OPTIMIZATION TECHNIQUE G.Sindhu AP/CSE Kalaivanicollege of technology *Mail-id:sindhugnsn24@gmail.com ABSTRACT: attempt derives from a
Master of Cyber Security, Strategy and Risk Management. CECS PG Information Session April 17, 2018
 Master of Cyber Security, Strategy and Risk Management CECS PG Information Session April 17, 2018 2 Program Purpose Provide a working understanding of information, network and software security, across
Master of Cyber Security, Strategy and Risk Management CECS PG Information Session April 17, 2018 2 Program Purpose Provide a working understanding of information, network and software security, across
DHS Cybersecurity. Election Infrastructure as Critical Infrastructure. June 2017
 DHS Cybersecurity Election Infrastructure as Critical Infrastructure June 2017 Department of Homeland Security Safeguard the American People, Our Homeland, and Our Values Homeland Security Missions 1.
DHS Cybersecurity Election Infrastructure as Critical Infrastructure June 2017 Department of Homeland Security Safeguard the American People, Our Homeland, and Our Values Homeland Security Missions 1.
Towards a Theoretical Framework for Trustworthy Cyber Sensing
 Towards a Theoretical Framework for Trustworthy Cyber Sensing Shouhuai Xu Department of Computer Science University of Texas at San Antonio shxu@cs.utsa.edu ABSTRACT Cyberspace is an indispensable part
Towards a Theoretical Framework for Trustworthy Cyber Sensing Shouhuai Xu Department of Computer Science University of Texas at San Antonio shxu@cs.utsa.edu ABSTRACT Cyberspace is an indispensable part
CYBERTECH MIDWEST Indianapolis, Indiana
 MIDWEST KICK-OFF EVENT October 23, 2018 CYBERTECH MIDWEST Indianapolis, Indiana KICK-OFF EVENT: Oct. 23, 2018 JW Marriott Indianapolis CONFERENCE & EXHIBITION: June 2019 MIDWEST KICK-OFF EVENT October
MIDWEST KICK-OFF EVENT October 23, 2018 CYBERTECH MIDWEST Indianapolis, Indiana KICK-OFF EVENT: Oct. 23, 2018 JW Marriott Indianapolis CONFERENCE & EXHIBITION: June 2019 MIDWEST KICK-OFF EVENT October
Supercharge Your SIEM: How Domain Intelligence Enhances Situational Awareness
 Supercharge Your SIEM: How Domain Intelligence Enhances Situational Awareness Introduction Drowning in data but starving for information. It s a sentiment that resonates with most security analysts. For
Supercharge Your SIEM: How Domain Intelligence Enhances Situational Awareness Introduction Drowning in data but starving for information. It s a sentiment that resonates with most security analysts. For
Security activities in Japan towards the future standardization. Cybersecurity
 Security activities in Japan towards the future standardization Side Event Cybersecurity Koji NAKAO KDDI, Japan Content Current threats - Internet User in Japan - However, observation of many scans (by
Security activities in Japan towards the future standardization Side Event Cybersecurity Koji NAKAO KDDI, Japan Content Current threats - Internet User in Japan - However, observation of many scans (by
NEW JERSEY INSTITUTE OF TECHNOLOGY. Initiation of Cyber Defense Option. for the Master of Science in
 NEW JERSEY INSTITUTE OF TECHNOLOGY Initiation of Cyber Defense Option for the Master of Science in Cyber Security and Privacy (MS CSP) Degree Program With the approval of the Faculty Senate (and its Committee
NEW JERSEY INSTITUTE OF TECHNOLOGY Initiation of Cyber Defense Option for the Master of Science in Cyber Security and Privacy (MS CSP) Degree Program With the approval of the Faculty Senate (and its Committee
Cyber Attack: Is Your Business at Risk?
 15 July 2017 Cyber Attack: Is Your Business at Risk? Stanley Wong Regional Head of Financial Lines, Asia Pacific Agenda Some common misconceptions by SMEs around cyber protection Cyber Claims and Industry
15 July 2017 Cyber Attack: Is Your Business at Risk? Stanley Wong Regional Head of Financial Lines, Asia Pacific Agenda Some common misconceptions by SMEs around cyber protection Cyber Claims and Industry
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
Phishing Activity Trends Report for the Month of, 27 Summarization of Report Findings The number of phishing reports received rose to 24,853 in, an increase of over 1, from February but still more than
