securedretail.com The Importance of Meeting Regulatory Compliance The Importance of Meeting Regulatory Compliance 1
|
|
|
- Quentin Ward
- 5 years ago
- Views:
Transcription
1 securedretail.com The Importance of Meeting Regulatory Compliance The Importance of Meeting Regulatory Compliance 1
2 The Importance of Meeting Regulatory Compliance It s hard enough to run a business without having to fret over issues which spring up but regulatory compliance is a BIG one. Many businesses are bound by regulations, depending on their specific industry and/or the types of information they handle. If any of the best practices set by these regulations are not followed, or if sufficient security measures are not put in place to protect the sensitive data governed by these regulations, the results for the offending company could be disastrous. Hence the reason for regulatory compliance. What Exactly Is Regulatory Compliance? Regulatory compliance is, simply put, the rules and regulations put forth by both credit companies and the government which are intended to ensure the information and funds handled within an organization are conducted properly. Here are a few examples of compliances business fall under: The Importance of Meeting Regulatory Compliance 2
3 Any company dealing with individual medical records in any way, shape, or fashion is bound to operate within HIPAA compliance Any company who reports their accounting or financial reports is bound by SOX compliance Any company processing or retaining credit card information must adhere to PSI DSS compliance. There are several other forms of compliance to which specific organizations must adhere, but the three listed above are the most common. While steadfast devotion to keeping your business compliant is both admirable and recommended, even the most careful organizations can suddenly find themselves under the watchful eye of the government and violations can vary from costly to catastrophic. Fred s Data is Now Much Safer Regulatory compliance is, simply put, the rules and regulations put forth by both credit companies and the government which are intended to ensure the 3 The Importance of Meeting Regulatory Compliance
4 information and funds handled within an organization are conducted properly. Here are a few examples of compliances business fall under: Any company dealing with individual medical records in any way, shape, or fashion is bound to operate within HIPAA compliance Any company who reports their accounting or financial reports is bound by SOX compliance Any company processing or retaining credit card information must adhere to PSI DSS compliance There are several other forms of compliance to which specific organizations must adhere, but the three listed above are the most common. The Importance of Meeting Regulatory Compliance 4
5 While steadfast devotion to keeping your business compliant is both admirable and recommended, even the most careful organizations can suddenly find themselves under the watchful eye of the government and violations can vary from costly to catastrophic. Examples of PCI DSS Compliance Violations Over the years especially the last decade there have been several notable PCI DSS violation cases. Here are just a few: In 2013, Genesco a retailer with 2,440 stores in the U.S., U.K., Canada, and Ireland, discovered Visa had imposed almost $13.3 million upon them in PCI DSS compliance fees. This was in response to a credit card data breach Genesco had suffered three years earlier. While Genesco was left to deal with the aftermath of their data breach including notifying their customers of the breach, dealing with fallout from the event, and attempting to re-secure public trust they were then forced to deal with enormous violation fees. had imposed almost $13.3 million upon them in PCI DSS compliance fees. 5 The Importance of Meeting Regulatory Compliance
6 Granted the hacker access to the credit card information of around 2.4 million credit and debit cards. $10,000 of a $50,000+ regulatory compliance penalty from the owners account. A grocery store chain, Schnuck s Markets, was the victim of credit card data breach in late 2012 to early A clever hacker slipped a code into their processing system which granted the hacker access to the credit card information of around 2.4 million credit and debit cards. As a result, class-action suits brought by Schnuck s customers demanded $2.1 million in damages. After those cases were settled, Schnuck s then found themselves being held in violation of PCI DSS compliance by their banks, with respective fees imposed upon them. Another case involving a Park City, Utah eatery Cisero s Ristorante and Nightclub reared its head in Visa and Mastercard believed Cisero allowed a data breach of their customers card information to occur and imposed what they felt were appropriate fees. When Cisero disputed the claims, the credit card companies responded by ordering Cisero s financial institution to draft $10,000 of a $50,000+ regulatory compliance penalty from the owners account. In response, the Cisero owners immediately closed their bank account and secured their money elsewhere to keep the credit card companies from taking more funds they felt were owed them. Eventually, the case simply went away, suggesting both parties had come to a mutual settlement. In all of these cases, the fees levied onto these organizations were so high, they were considered heavily damaging to each company s future. Some chose to fight, but more often than not, companies simply choose to pay the penalties in an attempt to put the ordeal behind them. The Importance of Meeting Regulatory Compliance 6
7 What Can You Do? Regardless of the compliances you must adhere to, there are protocols which can be put in place to help ensure consistent and reliable regulatory compliance for your organization. Speak with an IT consultant to discuss your specific compliance requirements, and ask what can be done on a technical level to keep all activities and securities on the up-and-up. SRN Can Help You with Regulatory Compliance At SRN, we know what to look for to keep businesses compliant. We are more than happy to offer customized solutions for our clients who need to stay within PCI DSS compliance at all times. Let s have a conversation about what it is you need, and we ll share with you what we can do for your organization. 7 The Importance of Meeting Regulatory Compliance
8 26000 Towne Centre Drive Suite 100 Foothill Ranch, CA securedretail.com 8 The Importance of Meeting Regulatory Compliance
Online Presentment and Payment FAQ s
 General Online Presentment and Payment FAQ s What are some of the benefits of receiving my bill electronically? It is convenient, saves time, reduces errors, allows you to receive bills anywhere at any
General Online Presentment and Payment FAQ s What are some of the benefits of receiving my bill electronically? It is convenient, saves time, reduces errors, allows you to receive bills anywhere at any
Online Presentment and Payment FAQ s
 General Online Presentment and Payment FAQ s What are some of the benefits of receiving my bill electronically? It is convenient, saves time, reduces errors, allows you to receive bills anywhere at any
General Online Presentment and Payment FAQ s What are some of the benefits of receiving my bill electronically? It is convenient, saves time, reduces errors, allows you to receive bills anywhere at any
PCI COMPLIANCE IS NO LONGER OPTIONAL
 PCI COMPLIANCE IS NO LONGER OPTIONAL YOUR PARTICIPATION IS MANDATORY To protect the data security of your business and your customers, the credit card industry introduced uniform Payment Card Industry
PCI COMPLIANCE IS NO LONGER OPTIONAL YOUR PARTICIPATION IS MANDATORY To protect the data security of your business and your customers, the credit card industry introduced uniform Payment Card Industry
Village of Wellsville Online Presentment and Payment FAQ s
 General Village of Wellsville Online Presentment and Payment FAQ s What are some of the benefits of receiving my bill electronically? It is convenient, saves time, reduces errors, allows you to receive
General Village of Wellsville Online Presentment and Payment FAQ s What are some of the benefits of receiving my bill electronically? It is convenient, saves time, reduces errors, allows you to receive
A QUICK PRIMER ON PCI DSS VERSION 3.0
 1 A QUICK PRIMER ON PCI DSS VERSION 3.0 This white paper shows you how to use the PCI 3 compliance process to help avoid costly data security breaches, using various service provider tools or on your own.
1 A QUICK PRIMER ON PCI DSS VERSION 3.0 This white paper shows you how to use the PCI 3 compliance process to help avoid costly data security breaches, using various service provider tools or on your own.
A Checklist for Compliance in the Cloud 1. A Checklist for Compliance in the Cloud
 A Checklist for Compliance in the Cloud 1 A Checklist for Compliance in the Cloud A Checklist for Compliance in the Cloud 1 With the industrialization of hacking and the enormous impact of security breaches,
A Checklist for Compliance in the Cloud 1 A Checklist for Compliance in the Cloud A Checklist for Compliance in the Cloud 1 With the industrialization of hacking and the enormous impact of security breaches,
FAQs. The Worldpay PCI Program. Help protect your business and your customers from data theft
 The Worldpay PCI Program Help protect your business and your customers from data theft What is the Payment Card Industry Data Security Standard (PCI DSS)? Do I have to comply? The PCI DSS is a set of 12
The Worldpay PCI Program Help protect your business and your customers from data theft What is the Payment Card Industry Data Security Standard (PCI DSS)? Do I have to comply? The PCI DSS is a set of 12
Have breaches declined since the massive Heartland Payments leak in 2008? What proportion of breaches are the result of hacking?
 The financial sector struggles with data leakage in part because many such organizations rely on dinosaurs - security solutions that struggle to protect data outside the corporate network. These orgs also
The financial sector struggles with data leakage in part because many such organizations rely on dinosaurs - security solutions that struggle to protect data outside the corporate network. These orgs also
Compliance in 5 Steps
 Email Compliance in 5 Steps Introduction For most businesses, email is a vital communication resource. Used to perform essential business functions, many organizations rely on email to send sensitive confidential
Email Compliance in 5 Steps Introduction For most businesses, email is a vital communication resource. Used to perform essential business functions, many organizations rely on email to send sensitive confidential
74% 2014 SIEM Efficiency Report. Hunting out IT changes with SIEM
 2014 SIEM Efficiency Report Hunting out IT changes with SIEM 74% OF USERS ADMITTED THAT DEPLOYING A SIEM SOLUTION DIDN T PREVENT SECURITY BREACHES FROM HAPPENING Contents Introduction 4 Survey Highlights
2014 SIEM Efficiency Report Hunting out IT changes with SIEM 74% OF USERS ADMITTED THAT DEPLOYING A SIEM SOLUTION DIDN T PREVENT SECURITY BREACHES FROM HAPPENING Contents Introduction 4 Survey Highlights
Merchant Guide to PCI DSS
 0800 085 3867 www.cardpayaa.com Merchant Guide to PCI DSS Contents What is PCI DSS and why was it introduced?... 3 Who needs to become PCI DSS compliant?... 3 Card Pay from the AA Simple PCI DSS - 3 step
0800 085 3867 www.cardpayaa.com Merchant Guide to PCI DSS Contents What is PCI DSS and why was it introduced?... 3 Who needs to become PCI DSS compliant?... 3 Card Pay from the AA Simple PCI DSS - 3 step
By accessing your Congressional Federal Credit Union account(s) electronically with the use of Online Banking through a personal computer or any other
 CONGRESSIONAL FEDERAL CREDIT UNION ELECTRONIC CORRESPONDENCE DISCLOSURE & AGREEMENT Please read this information carefully and print a copy and/or retain this information electronically for your records.
CONGRESSIONAL FEDERAL CREDIT UNION ELECTRONIC CORRESPONDENCE DISCLOSURE & AGREEMENT Please read this information carefully and print a copy and/or retain this information electronically for your records.
What is HIPPA/PCI? Understanding HIPAA. Understanding PCI DSS
 What is HIPPA/PCI? In this digital era, where every bit of information pertaining to individuals has gone digital and is stored in digital form somewhere or the other, there is a need protect the individuals
What is HIPPA/PCI? In this digital era, where every bit of information pertaining to individuals has gone digital and is stored in digital form somewhere or the other, there is a need protect the individuals
Global Prepaid Card Market with Focus on The United States ( ) April 2016
 Global Prepaid Card Market with Focus on The United States (2016-2020) April 2016 Global Prepaid Card Market Report Scope of the Report The report titled Global Prepaid Card Market with Focus on The United
Global Prepaid Card Market with Focus on The United States (2016-2020) April 2016 Global Prepaid Card Market Report Scope of the Report The report titled Global Prepaid Card Market with Focus on The United
CERTIFIED FINANCIAL PLANNER BOARD OF STANDARDS, INC. ANONYMOUS CASE HISTORIES NUMBER 30648
 CERTIFIED FINANCIAL PLANNER BOARD OF STANDARDS, INC. ANONYMOUS CASE HISTORIES NUMBER 30648 This is a summary of a decision issued following the October 2017 hearings of the Disciplinary and Ethics Commission
CERTIFIED FINANCIAL PLANNER BOARD OF STANDARDS, INC. ANONYMOUS CASE HISTORIES NUMBER 30648 This is a summary of a decision issued following the October 2017 hearings of the Disciplinary and Ethics Commission
PayPlug. The payment solution that increases your sales PAYPLUG EXTENSION FOR MAGENTO V1
 PAYPLUG EXTENSION FOR MAGENTO V1 TABLE OF CONTENTS 1. INTRODUCTION..3 2. CONFIGURATION 4 2.1. CONNECT... 2.2. SETTINGS..5 2.3. PAYMENT PAGE..6 2.4. DISPLAY/HIDE PAYPLUG. 3. PAYMENT PAGE.6 3.1. REDIRECT.7
PAYPLUG EXTENSION FOR MAGENTO V1 TABLE OF CONTENTS 1. INTRODUCTION..3 2. CONFIGURATION 4 2.1. CONNECT... 2.2. SETTINGS..5 2.3. PAYMENT PAGE..6 2.4. DISPLAY/HIDE PAYPLUG. 3. PAYMENT PAGE.6 3.1. REDIRECT.7
Independent Intelligence from the World of Prepaid. Market Report. iq. Market Report. Issue 55:
 iq. Market Report. Issue 55: 22.10.09 Management in the UK Ruben del Aguila, Global Prepaid Exchange Based on research by Management is a key BIN Sponsorship, Funds Holding The BIN sponsor is also role
iq. Market Report. Issue 55: 22.10.09 Management in the UK Ruben del Aguila, Global Prepaid Exchange Based on research by Management is a key BIN Sponsorship, Funds Holding The BIN sponsor is also role
VANGUARD POLICY MANAGERTM
 VANGUARD TM VANGUARD dramatically reduces security risks and improves regulatory compliance, minimizing the need for expensive remediation, while increasing staff productivity. Policy Manager provides
VANGUARD TM VANGUARD dramatically reduces security risks and improves regulatory compliance, minimizing the need for expensive remediation, while increasing staff productivity. Policy Manager provides
Security and Compliance Powered by the Cloud. Ben Friedman / Strategic Accounts Director /
 Security and Compliance Powered by the Cloud Ben Friedman / Strategic Accounts Director / bf@alertlogic.com Founded: 2002 Headquarters: Ownership: Houston, TX Privately Held Customers: 1,200 + Employees:
Security and Compliance Powered by the Cloud Ben Friedman / Strategic Accounts Director / bf@alertlogic.com Founded: 2002 Headquarters: Ownership: Houston, TX Privately Held Customers: 1,200 + Employees:
POLICY MANAGER VANGUARD POLICY MANAGER (AUDIT/COMPLIANCE)
 POLICY MANAGER VANGUARD POLICY MANAGER (AUDIT/COMPLIANCE) VANGUARD POLICY MANAGER dramatically reduces security risks and improves regulatory compliance, minimizing the need for expensive remediation,
POLICY MANAGER VANGUARD POLICY MANAGER (AUDIT/COMPLIANCE) VANGUARD POLICY MANAGER dramatically reduces security risks and improves regulatory compliance, minimizing the need for expensive remediation,
PCI DSS COMPLIANCE DATA
 PCI DSS COMPLIANCE DATA AND PROTECTION FROM RESULTS Technology CONTENTS Overview.... 2 The Basics of PCI DSS... 2 PCI DSS Compliance... 4 The Solution Provider Role (and Accountability).... 4 Concerns
PCI DSS COMPLIANCE DATA AND PROTECTION FROM RESULTS Technology CONTENTS Overview.... 2 The Basics of PCI DSS... 2 PCI DSS Compliance... 4 The Solution Provider Role (and Accountability).... 4 Concerns
To receive money, just share your enrolled address or U.S. mobile phone number with a friend and ask them to send you money with Zelle.
 Consumer FAQs 1. What is Zelle? Zelle is a fast, safe and easy way to send money directly between almost any bank accounts in the U.S., typically within minutes 1. With just an email address or U.S. mobile
Consumer FAQs 1. What is Zelle? Zelle is a fast, safe and easy way to send money directly between almost any bank accounts in the U.S., typically within minutes 1. With just an email address or U.S. mobile
How PayPal can help colleges and universities reduce PCI DSS compliance scope. Prepared by PayPal and Sikich LLP.
 How PayPal can help colleges and universities reduce PCI DSS compliance scope. Prepared by PayPal and Sikich LLP. Reduce time and resources needed for PCI DSS compliance. Campus merchants want to offer
How PayPal can help colleges and universities reduce PCI DSS compliance scope. Prepared by PayPal and Sikich LLP. Reduce time and resources needed for PCI DSS compliance. Campus merchants want to offer
How Secure Do You Feel About Your HIPAA Compliance Plan? Daniel F. Shay, Esq.
 How Secure Do You Feel About Your HIPAA Compliance Plan? Daniel F. Shay, Esq. Word Count: 2,268 Physician practices have lived with the reality of HIPAA for over twenty years. In that time, it has likely
How Secure Do You Feel About Your HIPAA Compliance Plan? Daniel F. Shay, Esq. Word Count: 2,268 Physician practices have lived with the reality of HIPAA for over twenty years. In that time, it has likely
VANGUARD Policy Manager TM
 Compliance Endures that RACF commands comply with company policy Remediation Provides proactive enforcement, corrects commands in accordance with corporate policies Auditing Provides and audit trail within
Compliance Endures that RACF commands comply with company policy Remediation Provides proactive enforcement, corrects commands in accordance with corporate policies Auditing Provides and audit trail within
Regulating Cyber: the UK s plans for the NIS Directive
 Regulating Cyber: the UK s plans for the NIS Directive September 2017 If you are a digital service provider or operate an essential service then new security and breach notification obligations may soon
Regulating Cyber: the UK s plans for the NIS Directive September 2017 If you are a digital service provider or operate an essential service then new security and breach notification obligations may soon
for the Dental Industry
 for the Dental Industry If you re practicing dentistry, you ll also need to be an expert on email encryption and patient privacy. Dental practices are among the fastest growing adopters of cloud email
for the Dental Industry If you re practicing dentistry, you ll also need to be an expert on email encryption and patient privacy. Dental practices are among the fastest growing adopters of cloud email
PAYMENT CARD INDUSTRY DATA SECURITY STANDARD (PCI DSS)
 PAYMENT CARD INDUSTRY DATA SECURITY STANDARD (PCI DSS) Table of Contents Introduction 03 Who is affected by PCI DSS? 05 Why should my organization comply 06 with PCI DSS? Email security requirements 08
PAYMENT CARD INDUSTRY DATA SECURITY STANDARD (PCI DSS) Table of Contents Introduction 03 Who is affected by PCI DSS? 05 Why should my organization comply 06 with PCI DSS? Email security requirements 08
BANK WAYS TO. Secure and convenient banking options to fit your lifestyle. Branches. Online Banking. Phoneline Banking. Mobile Banking.
 WAYS TO BANK Secure and convenient banking options to fit your lifestyle Branches Online Banking Phoneline Banking Mobile Banking Post Office Cash Machines Contents 01 What can I do in branch? What can
WAYS TO BANK Secure and convenient banking options to fit your lifestyle Branches Online Banking Phoneline Banking Mobile Banking Post Office Cash Machines Contents 01 What can I do in branch? What can
Presented by: Jason C. Gavejian Morristown Office
 Presented by: Jason C. Gavejian Morristown Office jason.gavejian@jacksonlewis.com 973.538.6890 } Unauthorized use of, or access to, records or data containing personal information Personal Information
Presented by: Jason C. Gavejian Morristown Office jason.gavejian@jacksonlewis.com 973.538.6890 } Unauthorized use of, or access to, records or data containing personal information Personal Information
Table of Contents. PCI Information Security Policy
 PCI Information Security Policy Policy Number: ECOMM-P-002 Effective Date: December, 14, 2016 Version Number: 1.0 Date Last Reviewed: December, 14, 2016 Classification: Business, Finance, and Technology
PCI Information Security Policy Policy Number: ECOMM-P-002 Effective Date: December, 14, 2016 Version Number: 1.0 Date Last Reviewed: December, 14, 2016 Classification: Business, Finance, and Technology
PCI Compliance: It's Required, and It's Good for Your Business
 PCI Compliance: It's Required, and It's Good for Your Business INTRODUCTION As a merchant who accepts payment cards, you know better than anyone that the war against data fraud is ongoing and escalating.
PCI Compliance: It's Required, and It's Good for Your Business INTRODUCTION As a merchant who accepts payment cards, you know better than anyone that the war against data fraud is ongoing and escalating.
How to Get Started Guide
 How to Get Started Guide FAST Opening Page Navigation Bar Use the navigation bar to move back and forth through the application. Paper Worksheet If you want to pre-fill out this application, download a
How to Get Started Guide FAST Opening Page Navigation Bar Use the navigation bar to move back and forth through the application. Paper Worksheet If you want to pre-fill out this application, download a
Compliance with CloudCheckr
 DATASHEET Compliance with CloudCheckr Introduction Security in the cloud is about more than just monitoring and alerts. To be truly secure in this ephemeral landscape, organizations must take an active
DATASHEET Compliance with CloudCheckr Introduction Security in the cloud is about more than just monitoring and alerts. To be truly secure in this ephemeral landscape, organizations must take an active
BFS VISA PREPAID CARDS FREQUENTLY ASKED QUESTIONS (FAQ S)
 BFS VISA PREPAID CARDS FREQUENTLY ASKED QUESTIONS (FAQ S) 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 What is a BFS Visa Prepaid
BFS VISA PREPAID CARDS FREQUENTLY ASKED QUESTIONS (FAQ S) 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 What is a BFS Visa Prepaid
Data Processing Agreement
 Data Processing Agreement Merchant (the "Data Controller") and Nets (the "Data Processor") (separately referred to as a Party and collectively the Parties ) have concluded this DATA PROCESSING AGREEMENT
Data Processing Agreement Merchant (the "Data Controller") and Nets (the "Data Processor") (separately referred to as a Party and collectively the Parties ) have concluded this DATA PROCESSING AGREEMENT
PRIVACY AND ONLINE DATA: CAN WE HAVE BOTH?
 PAPER PRIVACY AND ONLINE DATA: CAN WE HAVE BOTH? By Peter Varhol www.actian.com ignificant change has arrived in how computing and storage consumes data concerning individuals. Merchants, data collection
PAPER PRIVACY AND ONLINE DATA: CAN WE HAVE BOTH? By Peter Varhol www.actian.com ignificant change has arrived in how computing and storage consumes data concerning individuals. Merchants, data collection
June 2012 First Data PCI RAPID COMPLY SM Solution
 June 2012 First Data PCI RAPID COMPLY SM Solution You don t have to be a security expert to be compliant. Developer: 06 Rev: 05/03/2012 V: 1.0 Agenda Research Background Product Overview Steps to becoming
June 2012 First Data PCI RAPID COMPLY SM Solution You don t have to be a security expert to be compliant. Developer: 06 Rev: 05/03/2012 V: 1.0 Agenda Research Background Product Overview Steps to becoming
Application of Key UCC 4A Concepts and Terms to the Real-Time Payment System
 Application of Key UCC 4A Concepts and Terms to the Real-Time Payment System Note: Capitalized terms have the same meaning as provided in the RTP Rules, unless otherwise noted. UCC 4A Concept or Term Scope
Application of Key UCC 4A Concepts and Terms to the Real-Time Payment System Note: Capitalized terms have the same meaning as provided in the RTP Rules, unless otherwise noted. UCC 4A Concept or Term Scope
Section 3.9 PCI DSS Information Security Policy Issued: November 2017 Replaces: June 2016
 Section 3.9 PCI DSS Information Security Policy Issued: vember 2017 Replaces: June 2016 I. PURPOSE The purpose of this policy is to establish guidelines for processing charges on Payment Cards to protect
Section 3.9 PCI DSS Information Security Policy Issued: vember 2017 Replaces: June 2016 I. PURPOSE The purpose of this policy is to establish guidelines for processing charges on Payment Cards to protect
NEXT GENERATION ENCRYPTION AND KEY MANAGEMENT MEDIA OVERVIEW
 NEXT GENERATION ENCRYPTION AND KEY MANAGEMENT MEDIA OVERVIEW MEDIA OVERVIEW PKWARE is a global leader in business data security, providing encryption and compression solutions to more than 35,000 enterprise
NEXT GENERATION ENCRYPTION AND KEY MANAGEMENT MEDIA OVERVIEW MEDIA OVERVIEW PKWARE is a global leader in business data security, providing encryption and compression solutions to more than 35,000 enterprise
Comodo HackerGuardian PCI Approved Scanning Vendor
 Creating Trust Online TM E N T E R P R I S E Enterprise Security Solutions TM Comodo HackerGuardian PCI Approved Scanning Vendor Compliancy drives commerce: A reseller's Case Study - Merchant-Accounts.ca
Creating Trust Online TM E N T E R P R I S E Enterprise Security Solutions TM Comodo HackerGuardian PCI Approved Scanning Vendor Compliancy drives commerce: A reseller's Case Study - Merchant-Accounts.ca
Credit Card Frauds Sept.08, 2016
 Credit Card Frauds Sept.08, 2016 Definitions Credit Card A card allowing the holder to purchasing goods or services on credit Debit Card A card allowing transfer of money from a bank a/c electronically
Credit Card Frauds Sept.08, 2016 Definitions Credit Card A card allowing the holder to purchasing goods or services on credit Debit Card A card allowing transfer of money from a bank a/c electronically
Automate and simplify PCI DSS compliance using FileAudit Plus
 PCI-DSS Compliance Automate and simplify PCI DSS compliance using FileAudit Plus Automate and simplify PCI DSS compliance using FileAudit Plus Payment Card Industry Data Security Standard (PCI DSS) compliance
PCI-DSS Compliance Automate and simplify PCI DSS compliance using FileAudit Plus Automate and simplify PCI DSS compliance using FileAudit Plus Payment Card Industry Data Security Standard (PCI DSS) compliance
DATA PROTECTION BY DESIGN
 DATA PROTECTION BY DESIGN Preparing for Europe s New Security Regulations Summary In 2018, the European Union will begin to enforce the provisions of the General Data Protection Regulation (GDPR), a new
DATA PROTECTION BY DESIGN Preparing for Europe s New Security Regulations Summary In 2018, the European Union will begin to enforce the provisions of the General Data Protection Regulation (GDPR), a new
marketing: With your permission, we may send you s about new products or services and other updates.
 PRIVACY STATEMENT SECTION 1 WHAT DO WE DO WITH YOUR INFORMATION? When you submit your email address and/or sign up for our service, we collect the personal information you give us such as your name, address
PRIVACY STATEMENT SECTION 1 WHAT DO WE DO WITH YOUR INFORMATION? When you submit your email address and/or sign up for our service, we collect the personal information you give us such as your name, address
You are signing up to use the Middlesex Savings Bank Person to Person Service powered by Acculynk that allows you to send funds to another person.
 Middlesex Bank Person to Person Service You are signing up to use the Middlesex Savings Bank Person to Person Service powered by Acculynk that allows you to send funds to another person. This Agreement
Middlesex Bank Person to Person Service You are signing up to use the Middlesex Savings Bank Person to Person Service powered by Acculynk that allows you to send funds to another person. This Agreement
City of Portland Audit: Follow-Up on Compliance with Payment Card Industry Data Security Standard BY ALEXANDRA FERCAK SENIOR MANAGEMENT AUDITOR
 City of Portland Audit: Follow-Up on Compliance with Payment Card Industry Data Security Standard BY ALEXANDRA FERCAK SENIOR MANAGEMENT AUDITOR Examples of Government data breaches in 2016, listing number
City of Portland Audit: Follow-Up on Compliance with Payment Card Industry Data Security Standard BY ALEXANDRA FERCAK SENIOR MANAGEMENT AUDITOR Examples of Government data breaches in 2016, listing number
You can use your PIN to complete your purchases at point-of-sale and for ATM transactions.
 Westpac Business Prepaid MasterCard FAQs General Questions Is the Business Prepaid card a credit card? No. The Business Prepaid card has funds loaded on it by your employer. You can use the Business Prepaid
Westpac Business Prepaid MasterCard FAQs General Questions Is the Business Prepaid card a credit card? No. The Business Prepaid card has funds loaded on it by your employer. You can use the Business Prepaid
With certain types of prepaid account, you can do just about everything a traditional bank account allows you to do, including using your prepaid
 With certain types of prepaid account, you can do just about everything a traditional bank account allows you to do, including using your prepaid card to shop in store and online. But the key is you cannot
With certain types of prepaid account, you can do just about everything a traditional bank account allows you to do, including using your prepaid card to shop in store and online. But the key is you cannot
Baptist Financial Services
 Baptist Financial Services BFS Visa Prepaid PayCard FREQUENTLY ASKED QUESTIONS (FAQ S) Questions for Employers 1 What is a BFS Visa Prepaid PayCard? 2 How do I get a BFS Visa Prepaid PayCard? 3 How does
Baptist Financial Services BFS Visa Prepaid PayCard FREQUENTLY ASKED QUESTIONS (FAQ S) Questions for Employers 1 What is a BFS Visa Prepaid PayCard? 2 How do I get a BFS Visa Prepaid PayCard? 3 How does
PEOPLES COMMUNITY BANK IT S AS EASY AS 1,2,3!
 Switch To A True Community Bank. PEOPLES COMMUNITY BANK IT S AS EASY AS 1,2,3! Here s All You Need To Do. 1. Complete the New Account Application and other applicable information sheets. If you don t want
Switch To A True Community Bank. PEOPLES COMMUNITY BANK IT S AS EASY AS 1,2,3! Here s All You Need To Do. 1. Complete the New Account Application and other applicable information sheets. If you don t want
GDPR Workflow White Paper
 White Paper The European Union is implementing new legislation with the objective of protecting personal data of citizens within the EU and giving them more control over how their data is used. Hefty fines
White Paper The European Union is implementing new legislation with the objective of protecting personal data of citizens within the EU and giving them more control over how their data is used. Hefty fines
YourStore A GUIDE TO
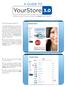 A GUIDE TO YourStore 3.0 Selling contact lenses online has never been easier! This is the homepage of YourStore 3.0. 1. The header displays just your company name as its default. The rectangular space
A GUIDE TO YourStore 3.0 Selling contact lenses online has never been easier! This is the homepage of YourStore 3.0. 1. The header displays just your company name as its default. The rectangular space
SIP Trunks. PCI compliance paired with agile and cost-effective telephony
 SIP Trunks PCI compliance paired with agile and cost-effective telephony What is PCI DSS compliance? What does this mean for you? The Payment Card Industry Data Security Standard (PCI DSS) is the proprietary
SIP Trunks PCI compliance paired with agile and cost-effective telephony What is PCI DSS compliance? What does this mean for you? The Payment Card Industry Data Security Standard (PCI DSS) is the proprietary
Cloud Communications for Healthcare
 Cloud Communications for Healthcare Today, many powerful business communication challenges face everyone in the healthcare chain including clinics, hospitals, insurance providers and any other organization
Cloud Communications for Healthcare Today, many powerful business communication challenges face everyone in the healthcare chain including clinics, hospitals, insurance providers and any other organization
Risk Outlook Anti money Laundering and Cybercrime. Steve Wilmott and George Hawkins
 Risk Outlook Anti money Laundering and Cybercrime Steve Wilmott and George Hawkins Introductions Steve Wilmott, Director of Intelligence and Investigations George Hawkins, Senior Technical Advisor, Risk
Risk Outlook Anti money Laundering and Cybercrime Steve Wilmott and George Hawkins Introductions Steve Wilmott, Director of Intelligence and Investigations George Hawkins, Senior Technical Advisor, Risk
Five Key Considerations for Selecting Cloud Recovery Services
 Five Key Considerations for Selecting Cloud Recovery Services Looking for a cloud-based solution for backup and recovery? Here are some important things to keep in mind when interviewing providers. By
Five Key Considerations for Selecting Cloud Recovery Services Looking for a cloud-based solution for backup and recovery? Here are some important things to keep in mind when interviewing providers. By
Jordan Morell, AAP, NCP Tim Thorson, AAP, CTP
 April 11, 2017 Presented by: Jordan Morell, AAP, NCP Associate Director of Education Services, UMACHA Tim Thorson, AAP, CTP SVP & Manager, ACH Operations, Regions Financial Corporation Overview Lessons
April 11, 2017 Presented by: Jordan Morell, AAP, NCP Associate Director of Education Services, UMACHA Tim Thorson, AAP, CTP SVP & Manager, ACH Operations, Regions Financial Corporation Overview Lessons
EXECUTIVE REPORT. 4 Critical Steps Financial Firms Must Take for IT Uptime, Security, and Connectivity
 EXECUTIVE REPORT 4 Critical Steps Financial Firms Must Take for IT Uptime, Security, and Connectivity When Millions of Dollars of Financial Transactions are On the Line, Downtime is Not an Option The many
EXECUTIVE REPORT 4 Critical Steps Financial Firms Must Take for IT Uptime, Security, and Connectivity When Millions of Dollars of Financial Transactions are On the Line, Downtime is Not an Option The many
New learner registration form - RQF
 New learner registration form - RQF Please read the following notes carefully before completing this form: This form is for new ABE learners. If you think you might have registered in the past, contact
New learner registration form - RQF Please read the following notes carefully before completing this form: This form is for new ABE learners. If you think you might have registered in the past, contact
PCI DATA SECURITY STANDARDS VERSION 3.2. What's Next?
 PCI DATA SECURITY STANDARDS VERSION 3.2 What's Next? Presenters Alan Gutierrez Arana Director National PCI Leader RSM US LLP Gus Orologas, QSA Manager RSM US LLP Travis Wendling, QSA Supervisor RSM US
PCI DATA SECURITY STANDARDS VERSION 3.2 What's Next? Presenters Alan Gutierrez Arana Director National PCI Leader RSM US LLP Gus Orologas, QSA Manager RSM US LLP Travis Wendling, QSA Supervisor RSM US
Cybersecurity and Hospitals: A Board Perspective
 Cybersecurity and Hospitals: A Board Perspective Cybersecurity is an important issue for both the public and private sector. At a time when so many of our activities depend on information systems and technology,
Cybersecurity and Hospitals: A Board Perspective Cybersecurity is an important issue for both the public and private sector. At a time when so many of our activities depend on information systems and technology,
Cybowall Solution Overview
 Cybowall Solution Overview 1 EVOLVING SECURITY CHALLENGES 2 EXAMPLES OF CYBER BREACHES INCLUDING CARD DATA 2013: Adobe Systems Hackers raided an Adobe back-up server on which they found and published a
Cybowall Solution Overview 1 EVOLVING SECURITY CHALLENGES 2 EXAMPLES OF CYBER BREACHES INCLUDING CARD DATA 2013: Adobe Systems Hackers raided an Adobe back-up server on which they found and published a
Managing Privacy Risk & Compliance in Financial Services. Brett Hamilton Advisory Solutions Consultant ServiceNow
 Managing Privacy Risk & Compliance in Financial Services Brett Hamilton Advisory Solutions Consultant ServiceNow 1 Speaker Introduction INSERT PHOTO Name: Brett Hamilton Title: Advisory Solutions Consultant
Managing Privacy Risk & Compliance in Financial Services Brett Hamilton Advisory Solutions Consultant ServiceNow 1 Speaker Introduction INSERT PHOTO Name: Brett Hamilton Title: Advisory Solutions Consultant
UTAH VALLEY UNIVERSITY Policies and Procedures
 Page 1 of 5 POLICY TITLE Section Subsection Responsible Office Private Sensitive Information Facilities, Operations, and Information Technology Information Technology Office of the Vice President of Information
Page 1 of 5 POLICY TITLE Section Subsection Responsible Office Private Sensitive Information Facilities, Operations, and Information Technology Information Technology Office of the Vice President of Information
Comodo HackerGuardian. PCI Security Compliance The Facts. What PCI security means for your business
 Comodo HackerGuardian PCI Security Compliance The Facts What PCI security means for your business Overview The Payment Card Industry Data Security Standard (PCI DSS) is a set of 12 requirements intended
Comodo HackerGuardian PCI Security Compliance The Facts What PCI security means for your business Overview The Payment Card Industry Data Security Standard (PCI DSS) is a set of 12 requirements intended
New learner registration form - RQF
 New learner registration form - RQF Please read the following notes carefully before completing this form: This form is for new ABE learners. If you think you might have registered in the past, contact
New learner registration form - RQF Please read the following notes carefully before completing this form: This form is for new ABE learners. If you think you might have registered in the past, contact
Don t Be the Next Headline! PHI and Cyber Security in Outsourced Services.
 Don t Be the Next Headline! PHI and Cyber Security in Outsourced Services. June 2017 Melanie Duerr Fazzi Associates Partner, Director of Coding Operations Jami Fisher Fazzi Associates Chief Information
Don t Be the Next Headline! PHI and Cyber Security in Outsourced Services. June 2017 Melanie Duerr Fazzi Associates Partner, Director of Coding Operations Jami Fisher Fazzi Associates Chief Information
Pay as you go Terms and Charges
 Pay as you go Terms and Charges Would you prefer this information in large print, on disk, or in Braille? Call our specialist accessibility team on 03333 043 222 or email disability.access@vodafone.co.uk
Pay as you go Terms and Charges Would you prefer this information in large print, on disk, or in Braille? Call our specialist accessibility team on 03333 043 222 or email disability.access@vodafone.co.uk
Customer Breach Support A Deloitte managed service. Notifying, supporting and protecting your customers through a data breach
 Customer Breach Support A Deloitte managed service Notifying, supporting and protecting your customers through a data breach Customer Breach Support Client challenges Protecting your customers, your brand
Customer Breach Support A Deloitte managed service Notifying, supporting and protecting your customers through a data breach Customer Breach Support Client challenges Protecting your customers, your brand
Think big, think Brazil
 Think big, think Brazil Expand in Brazil and around the world confidently, with Worldpay GLOBAL ACQUIRING - BRAZIL Brazil an exciting emerging ecommerce market With a population of 209.5 million1 and a
Think big, think Brazil Expand in Brazil and around the world confidently, with Worldpay GLOBAL ACQUIRING - BRAZIL Brazil an exciting emerging ecommerce market With a population of 209.5 million1 and a
Employee Security Awareness Training Program
 Employee Security Awareness Training Program Date: September 15, 2015 Version: 2015 1. Scope This Employee Security Awareness Training Program is designed to educate any InComm employee, independent contractor,
Employee Security Awareness Training Program Date: September 15, 2015 Version: 2015 1. Scope This Employee Security Awareness Training Program is designed to educate any InComm employee, independent contractor,
Preparing for a Breach October 14, 2016
 Preparing for a Breach October 14, 2016 Jeremy Gilbert, GCFE, GASF, EnCE, CPA Manager, DHG Forensics forensics 1 Agenda Medical data breaches Why? Types? Frequency? Impact of a data breach How to prepare
Preparing for a Breach October 14, 2016 Jeremy Gilbert, GCFE, GASF, EnCE, CPA Manager, DHG Forensics forensics 1 Agenda Medical data breaches Why? Types? Frequency? Impact of a data breach How to prepare
SECTION 1 - WHAT DO WE DO WITH YOUR INFORMATION?
 SECTION 1 - WHAT DO WE DO WITH YOUR INFORMATION? When you purchase something from our store, as part of the buying and selling process, we collect the personal information you give us such as your name,
SECTION 1 - WHAT DO WE DO WITH YOUR INFORMATION? When you purchase something from our store, as part of the buying and selling process, we collect the personal information you give us such as your name,
M&A Cyber Security Due Diligence
 M&A Cyber Security Due Diligence Prepared by: Robert Horton, Ollie Whitehouse & Sherief Hammad Contents Page 1 Introduction 3 2 Technical due diligence goals 3 3 Enabling the business through cyber security
M&A Cyber Security Due Diligence Prepared by: Robert Horton, Ollie Whitehouse & Sherief Hammad Contents Page 1 Introduction 3 2 Technical due diligence goals 3 3 Enabling the business through cyber security
Bye Bye Paper! Getting to 100% Electronic Payroll. Presenter: John Laudani
 Bye Bye Paper! Getting to 100% Electronic Payroll Presenter: John Laudani Agenda Market Update Electronic Payroll and Paycards Employer and Employee Benefits Questions and Comments PlanSource & rapid!
Bye Bye Paper! Getting to 100% Electronic Payroll Presenter: John Laudani Agenda Market Update Electronic Payroll and Paycards Employer and Employee Benefits Questions and Comments PlanSource & rapid!
Webinar Tokenization 101
 Webinar Tokenization 101 René M. Pelegero Retail Payments Global Consulting Group L.L.C December 15 th, 2014 Webinar Overview A description of tokenization and how the technology is being employed in the
Webinar Tokenization 101 René M. Pelegero Retail Payments Global Consulting Group L.L.C December 15 th, 2014 Webinar Overview A description of tokenization and how the technology is being employed in the
SECTION 1 WHAT DO WE DO W ITH YOUR INFORMATION?
 Hasslefreerepartnership.com is serious about protecting your online privacy. This Privacy Statement explains our views and practices concerning privacy, and how they may pertain to you as a user of our
Hasslefreerepartnership.com is serious about protecting your online privacy. This Privacy Statement explains our views and practices concerning privacy, and how they may pertain to you as a user of our
8 COMMON HIPAA COMPLIANCE ERRORS TO AVOID
 Billing & Reimbursement Revenue Cycle Management 8 COMMON HIPAA COMPLIANCE ERRORS TO AVOID Billing and Reimbursement for Physician Offices, Ambulatory Surgery Centers and Hospitals Billings & Reimbursements
Billing & Reimbursement Revenue Cycle Management 8 COMMON HIPAA COMPLIANCE ERRORS TO AVOID Billing and Reimbursement for Physician Offices, Ambulatory Surgery Centers and Hospitals Billings & Reimbursements
USER CORPORATE RULES. These User Corporate Rules are available to Users at any time via a link accessible in the applicable Service Privacy Policy.
 These User Corporate Rules are available to Users at any time via a link accessible in the applicable Service Privacy Policy. I. OBJECTIVE ebay s goal is to apply uniform, adequate and global data protection
These User Corporate Rules are available to Users at any time via a link accessible in the applicable Service Privacy Policy. I. OBJECTIVE ebay s goal is to apply uniform, adequate and global data protection
Hot Topics in Privacy
 Hot Topics in Privacy Gretchen S. Herault Monster Worldwide SCCE Conference April 12, 2013 Agenda Privacy Landscape current state of regulatory coverage > Global > Industry Sector > Technology Hot Topics
Hot Topics in Privacy Gretchen S. Herault Monster Worldwide SCCE Conference April 12, 2013 Agenda Privacy Landscape current state of regulatory coverage > Global > Industry Sector > Technology Hot Topics
Hot Topics in Privacy
 Hot Topics in Privacy Gretchen S. Herault Monster Worldwide SCCE Conference April 12, 2013 Agenda Privacy Landscape current state of regulatory coverage > Global > Industry Sector > Technology Hot Topics
Hot Topics in Privacy Gretchen S. Herault Monster Worldwide SCCE Conference April 12, 2013 Agenda Privacy Landscape current state of regulatory coverage > Global > Industry Sector > Technology Hot Topics
Security Breach Notification Reflections on the U.S. Experience
 Compliance & Regulatory Matters Data Privacy Security Breach Notification Reflections on the U.S. Experience Bojana Bellamy Director of Data Privacy Accenture Brief History of Breach Notification Laws
Compliance & Regulatory Matters Data Privacy Security Breach Notification Reflections on the U.S. Experience Bojana Bellamy Director of Data Privacy Accenture Brief History of Breach Notification Laws
Group means any company within the STB Leasing Limited s group of companies and/or the ThinkSmart group of companies.
 PRIVACY DECLARATION In this Privacy Declaration, unless the context otherwise requires: We, us, our means STB Leasing Limited, and/or RentSmart Limited trading as ThinkSmart ( ThinkSmart / we / us ), and
PRIVACY DECLARATION In this Privacy Declaration, unless the context otherwise requires: We, us, our means STB Leasing Limited, and/or RentSmart Limited trading as ThinkSmart ( ThinkSmart / we / us ), and
ACCOUNT SWITCH KIT. The Honesdale National Bank
 ACCOUNT SWITCH KIT Move your accounts to quickly and easily. To get started, follow the steps below and submit the form online or through your local HNB Office. Step 1 Complete our New Account Information
ACCOUNT SWITCH KIT Move your accounts to quickly and easily. To get started, follow the steps below and submit the form online or through your local HNB Office. Step 1 Complete our New Account Information
Professional Certificate in Complex Financial Instruments in International Financial Services
 International Financial Services MEMBERSHIP In order to register to an Institute of Banking (IoB) programme you must be a current member of the Institute. The membership fee of 40 is applicable upon joining
International Financial Services MEMBERSHIP In order to register to an Institute of Banking (IoB) programme you must be a current member of the Institute. The membership fee of 40 is applicable upon joining
PRODUCT DISCLOSURE SHEET
 PRODUCT DISCLOSURE SHEET KINDLY READ THIS PRODUCT DISCLOSURE SHEET BEFORE YOU DECIDE TO TAKE UP ANY TUNE MONEY SDN BHD ( TUNE MONEY ) PREPAID CARD. PLEASE MAKE SURE YOU ALSO READ THE TERMS AND CONDITIONS
PRODUCT DISCLOSURE SHEET KINDLY READ THIS PRODUCT DISCLOSURE SHEET BEFORE YOU DECIDE TO TAKE UP ANY TUNE MONEY SDN BHD ( TUNE MONEY ) PREPAID CARD. PLEASE MAKE SURE YOU ALSO READ THE TERMS AND CONDITIONS
SELF ASSESSMENT OF SEPA COMPLIANCE November, 2013
 SELF ASSESSMENT OF SEPA COMPLIANCE November, 2013 Bucharest, November 2013 This document constitutes the self-assessment of TRANSFOND`s system SENT against the Eurosystem s SEPA-compliance criteria. The
SELF ASSESSMENT OF SEPA COMPLIANCE November, 2013 Bucharest, November 2013 This document constitutes the self-assessment of TRANSFOND`s system SENT against the Eurosystem s SEPA-compliance criteria. The
UCOP ITS Systemwide CISO Office Systemwide IT Policy
 UCOP ITS Systemwide CISO Office Systemwide IT Policy Revision History Date: By: Contact Information: Description: 08/16/17 Robert Smith robert.smith@ucop.edu Initial version, CISO approved Classification
UCOP ITS Systemwide CISO Office Systemwide IT Policy Revision History Date: By: Contact Information: Description: 08/16/17 Robert Smith robert.smith@ucop.edu Initial version, CISO approved Classification
Step 1: Create your Government of Canada online account
 Step 1: Create your Government of Canada online account Visit this link to start: https://www.canada.ca/en/immigration refugees citizenship/services/application/account.html Click Continue to GC Key button
Step 1: Create your Government of Canada online account Visit this link to start: https://www.canada.ca/en/immigration refugees citizenship/services/application/account.html Click Continue to GC Key button
South Central Power Stop Scams
 Don t get tricked. People around the country have been receiving emails and phone calls from scammers. South Central Power wants to help you keep your money and prevent scams. Review the helpful tips below.
Don t get tricked. People around the country have been receiving emails and phone calls from scammers. South Central Power wants to help you keep your money and prevent scams. Review the helpful tips below.
DIGITAL CASHLESS BANKING STATE BANK OF INDIA STATE BANK LEARNING CENTRE
 DIGITAL CASHLESS BANKING STATE BANK OF INDIA STATE BANK LEARNING CENTRE CASHLESS INDIA The Digital India programme is a flagship programme of the Government of India with a vision to transform India into
DIGITAL CASHLESS BANKING STATE BANK OF INDIA STATE BANK LEARNING CENTRE CASHLESS INDIA The Digital India programme is a flagship programme of the Government of India with a vision to transform India into
eguide: Designing a Continuous Response Architecture 5 Steps to Reduce the Complexity of PCI Security Assessments
 eguide: Designing a Continuous Response Architecture 5 Steps to Reduce the Complexity of PCI Security Assessments Today s PCI compliance landscape is one of continuing change and scrutiny. Given the number
eguide: Designing a Continuous Response Architecture 5 Steps to Reduce the Complexity of PCI Security Assessments Today s PCI compliance landscape is one of continuing change and scrutiny. Given the number
Keeping of the roll Completing the restoration to the roll application
 Keeping of the roll Completing the restoration to the roll application Contents 1. Getting Started - logging in to mysra 3 2. Before starting the application 3 3. Accessing and completing the application
Keeping of the roll Completing the restoration to the roll application Contents 1. Getting Started - logging in to mysra 3 2. Before starting the application 3 3. Accessing and completing the application
BCU Pay Anyone Terms and Conditions Credit Union Pay Anyone Service Agreement and Terms of Use ("Terms of Use") 1. Description of Service and Consent
 BCU Pay Anyone Terms and Conditions Credit Union Pay Anyone Service Agreement and Terms of Use ("Terms of Use") 1. Description of Service and Consent You may use your debit card information to send funds
BCU Pay Anyone Terms and Conditions Credit Union Pay Anyone Service Agreement and Terms of Use ("Terms of Use") 1. Description of Service and Consent You may use your debit card information to send funds
MYOB PayDirect Mobile app user guide
 MYOB PayDirect Mobile app user guide Welcome to the MYOB PayDirect Mobile app 1 The new MYOB PayDirect Mobile app lets you take care of business while you re on the go We ve taken some of the great features
MYOB PayDirect Mobile app user guide Welcome to the MYOB PayDirect Mobile app 1 The new MYOB PayDirect Mobile app lets you take care of business while you re on the go We ve taken some of the great features
The Recovery and Monitoring Program of New Jersey (Keep this sheet for your files)
 Welsh Commons, 1364 Welsh Road, Suite C-2, North Wales, PA 19454-1913, USA 800-732-DRUG (3784) Fax: 215371-1126 Internet: http://www.firstlab.com E-mail: mail@firstlab.com The Recovery and Monitoring Program
Welsh Commons, 1364 Welsh Road, Suite C-2, North Wales, PA 19454-1913, USA 800-732-DRUG (3784) Fax: 215371-1126 Internet: http://www.firstlab.com E-mail: mail@firstlab.com The Recovery and Monitoring Program
AND FINANCIAL CYBER FRAUD INSTITUTIONS FROM. Solution Brief PROTECTING BANKING
 PROTECTING BANKING AND FINANCIAL INSTITUTIONS FROM CYBER FRAUD Enabling the financial industry to become proactively secure and compliant Overview In order to keep up with the changing digital payment
PROTECTING BANKING AND FINANCIAL INSTITUTIONS FROM CYBER FRAUD Enabling the financial industry to become proactively secure and compliant Overview In order to keep up with the changing digital payment
Incident Policy Version 01, April 2, 2008 Provided by: CSRSI
 This is a sample policy from the PCI TOOLKIT. The PCI TOOLKIT is a web based program which leads the merchant through PCI compliance in an easy, understandable manner. The PCI TOOLKIT is sold through various
This is a sample policy from the PCI TOOLKIT. The PCI TOOLKIT is a web based program which leads the merchant through PCI compliance in an easy, understandable manner. The PCI TOOLKIT is sold through various
