An Implementation of Causal Memories using the Writing Semantic
|
|
|
- Eric Owens
- 6 years ago
- Views:
Transcription
1 An Implementation of Causal Memories using the Writing Semantic R. Baldoni, C. Spaziani and S. Tucci-Piergiovanni D. Tulone Dipartimento di Informatica e Sistemistica Bell-Laboratories Universita di Roma La Sapienza 700 Mountain Avenue Via Salaria 3, I-0098 Roma, Italy Murray Hill, NJ , USA baldoni@dis.uniroma.it tulone@research.bell-labs.com Abstract Causal consistency has been introduced to increase wait-free concurrent accesses to a shared memory. Contrarily to sequential consistency, causal consistency allows independent write operations, with respect to the causality relation, to be executed in different orders at each distinct process. This paper introduces a protocol for fully replicated settings which exploits the writing semantic and piggybacks on each update message related to a write operation an amount of control information which is O(n) where n is the number of processes. The protocol tracks causality relation by taking transitive dependencies on write operations into account. Keywords: Causal Memories, Writing Semantic, Replication, Distributed Coordination, Distributed Systems. Introduction Implementing a shared memory abstraction which preserves a given consistency criterion in an asynchronous distributed system is a real challenge due to unpredictable latencies and failures. Programmers are more comfortable to work with very strict consistency criteria like sequential consistency and atomic consistency. These criteria impose all processes implementing the shared memory abstraction agree on logical (sequential consistency [8]) or physical (atomic consistency [2]) execution order of a set of operations on the memory. Such consistency criteria are then costly to implement if processes are deployed in a partially synchronous distributed systems [5], or, even impossible (in deterministic way) in fully asynchronous distributed systems in the presence of failures due to FLP impossibility result [6]. Corresponding Author: Fax n baldoni@dis.uniroma.it.
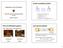
2 This is the reason why weaker consistency critera such as PRAM (also called FIFO consistency) [0] and causal consistency [] have been introduced in the past. These consistency criteria allow to get better scalability and performance with respect to more restrictive consistency criteria. In particular causal consistency ensures that values returned by a read operation are consistent with the Lamport causality relation [9]. In a setting where each process has a local copy of the shared memory locations, causal ordering ensures that readers can access their local copy concurrently (wait-free) without the risk of an invalidation of those reads due to a write operation. This enlarges the set of possible executions with respect to atomic and sequential consistency criteria. To our knowledge, two protocols have been presented in the literature in the context of fully ([]) and partially replicated memory locations ([4]). To ensure causal ordering of readings each message that notifies a write operation (update message) piggybacks a control information (i.e., actually a vector clock []) which is at least O(n) where n is the number of processes (See section 3.5 for a deeper discussion). More specifically, [] works as follows: when an update message of a write operation arrives at a process out of causal order (as w 2 (x)b at process p 3 depicted in Figure (a)), the execution of that operation is delayed till all update messages of causally preceding operations have been delivered (w (x)a update message in figure (a)). To get more efficiency causal consistency protocols, Raynal and Ahamad [4] introduce the notion of writing semantic. This notion informally states that a process p i can write a new value b in the memory location x, (e.g. w(x)b) as soon as it receives the w(x)b s update message even though p i detects, looking into the control information of w(x)b s update message, there exists a causally preceding write operation on x, (e.g. w(x)a) not yet arrived at p i. When the w(x)a s update message arrives at p i, it is discarded as it contains an obsolete value. This scenario is depicted in Figure (b). From an abstract point of view, the causality relation is actually preserved as it is like w(x)a has arrived and executed first at p i and then it has been immediately overwritten by w(x)b. P w (x)a P w (x)a P2 w 2 (x)b P2 w 2 (x)b P3 P3 DISCARDED delay delay (a) Figure : Example of writing semantic (b) The protocol of Raynal and Ahamad [4], adapted to a fully replicated setting, piggybacks on each update message a control information which is the maximum between O(n) and O(m), where m is the number of replicated objects. In this paper we provide a protocol exploiting writing semantic which guarantees causal consistency of a shared memory system by piggybacking on each update message a control information which is O(n). More specifically, the protocol piggybacks into an update message of a write operation w(x) issued by p i : (i) a vector of size n which represents to the p i s knowledge the sequence numbers of the last write operation on 2
3 x executed by each process (used for detecting obsolete values) (ii) a set of write operations which represents the causal barrier of w(x). i.e., w(x) cannot be executed at a process till all the elements in its causal barrier have been executed. The idea of causal barrier was presented for the first time in [3] in the context of guaranteeing causal message deliveries within multimedia applications. Compared to the protocol of Raynal and Ahamad [4], the one presented in this paper is well-suited to settings where the number of shared memory locations is more than n. Moreover, from a pedagogical point of view it clearly separates data structures for managing writing semantic and the ones for ensuring causal consistency. The paper is structured into 4 sections. Section 2 presents the model. Section 3 presents the protocol and the relative data structures and Section 4 introduces some discussion points. 2 Shared Memory Model We consider a finite set of sequential processes Π {p, p 2,... p n } interacting via a shared memory M composed by m locations x, x 2,... x m. The locations can be accessed through read and write operations. A write operation executed by a process p i, denoted w i (x)v, stores a new value v in location x. A read operation executed by a process p i, denoted r i (x)v, returns to p i the value v stored in location x. A local history of a process p i, denoted h i, is a set of read ad write operations. If p i issues two operations o and o 2 and o is issued first, then o precedes o 2 in process order of p i. This precedence relation is denoted by o poi o 2. Definition. A history, denoted H, is a collection of local histories h, h 2,... h n one for each process. Operations issued by distinct processes in H are related by the write-into relation. Formally write-into relation, denoted wo, is defined as follow: if o wo o 2, then there are x and v such that o = w(x)v and o 2 = r(x)v; for any operation o 2, there is at most one o such that o wo o 2 ; if o 2 = r(x)v for some x and there is no o such that o wo o 2, then v = ; that is, a read with no write must read the initial value. We denote as causal order relation (o co o 2 ) the transitive closure of the union of the local history s relations poi and the relation wo. In other words o co o 2 if and only if: o poi o 2 for some p i ; o wo o 2 ; o 3 : o co o 3 and o 3 co o 2. Whenever not necessary we omit the value v and the identifier of the process that issued the operation 3
4 If o and o 2 are two operations belonging to H, we said that o and o 2 are concurrent w.r.t. co, denoted by o o 2, if and only if (o co o 2 ) and (o 2 co o ). Let as note that Ĥ = (H, co), is a partial order. We call such a partial order execution history of H. Definition 2. A read event belonging to H, denoted r(x)v, is legal if w(x)v : w(x)v co r(x)v w(x)v : w(x)v co w(x)v co r(x)v Definition 3. An execution history, denoted Ĥ, is legal if all read operation in H are legal. Definition 4. An execution history Ĥ = (H, ) is causally consistent iff. Ĥ is legal; 2. co ; As processes are sequential the definition of causal memory allows to each process to see a specific linear extension of the partial order Ĥ. More specifically, this allows concurrent writes to be viewed in different orders by different processes. Let us finally remark that if we replace point of Definition 4 with:. there exists a linear extension of Ĥ where all read events in H are legal; we get another way to define sequential consistency [8, 5]. 3 An Implementation of Causal Memory using Message Passing This section presents an implementation of causal memory using message passing. It requires correct processes and reliable channels (a sent message is eventually received exactly once, no spurious messages can be ever delivered). Each process p i maintains a local copy M i of the abstract shared memory M and issues read and write operations. Each time p i issues a read operation, it actually reads immediately (i.e., without delay) the value accessing its own copy M i. When p i issues a write operation, it sends an update message to all the processes which are responsible to add the necessary synchronizations between update messages to respect causal consistency. 3. Causality Graph The causality graph of a distributed execution Ĥ = (H, ) is a directed acyclic graph whose vertices are all write operation in H, such that there is a direct edge from w(x) to w(y) (denoted w(x) w(y)) if. w(x) co w(y) and 2. w(z) : w(x) co w(z) and w(z) co w(y) 4
5 We say that w(x) is an immediate predecessor of w(y). It should be noted that as each process can issue a write operation at a time, a write operation v can have at most n immediate predecessors, one from each process. In Figure 2 is shown an example of computation in which update messages, establishing causality relation among write operations, are depicted by thick line. Figure 3 shows the causality graph associated with the computation of Figure 2. Let + denote the transitive closure of. Two write operations w(x) and w(y) are said to be concurrent if neither of them is a predecessor of the other in the causality graph, i.e., (w(x) + w(y)) and (w(y) + w(x)). P w(y)a w(x)f P2 w(x)c w(y)e P3 w(x)d P4 w(y)b discard Figure 2: Example of message pattern w(y)a w(x)d w(y)b w(x)f w(x)c w(y)e Figure 3: Causality graph of the message pattern of Figure 2 5
6 3.2 Writing semantic To reduce the number of synchronizations among update messages of write operations, improving thus performance, Raynal and Ahamad observed in [4] that in a specific condition, based on writing semantic of a shared memory, a message of a write operation w can be early delivered at a process p i even though a message of a write operation w (such that w co w) has not arrived at p i yet (i.e., the execution of operation w is intentionally actually done out-of-causal order) provided that w is not executed by p i (i.e., the update message of w is discarded by p i ). In this way, from the p i s viewpoint it is like the operation w has been virtually executed immediately (and atomically) before the execution of w (i.e., no read between the execution of o and o). This guarantees causally consistent executions. From a formal point of view the writing semantic (WS) condition, introduced by Raynal-Ahamad, can be expressed as follows using the relation : (WS) if (w(x)a + w(x)b) and ( w(z) : w(x)a + w(z) and w(z) + w(x)b) then the value b can be applied at the location x of process p i as soon as the relative update message is received (no need to wait for the message related to w(x)a). In the following we refer w(x)a as the obsolete value and w(x)b as the overwrite value. Let us consider the causality graph depicted in Figure 3: the write operation w(x)f is an overwrite of the write operation w(x)d. This means that if a process p 4 (see Figure 2) receives w(x)f, it applies the overwrite value f immediately and then it will discard the w(x)d s update message that carries the obsolete value d. 3.3 Data Structure Each process p i manages a local variable #seq (initially set to zero) in which it stores the sequence number of its last write operation. A write operation w(x)a is uniquely identified by an operation timestamp t which is a triple (sender identity, sequence number, variable). As an example w(x)f issued by p in Figure 2 is identified by the timestamp (, 2, x). In the next subsections we present the data structures needed (i) to track causal dependencies among operations on the causality graph and (ii) to take into account the writing semantic Handling the Causality Graph: the IP set Figure 3 shows that the execution of w(x)f cannot occur before the execution of all the other write operations. But, due to transitive dependencies, the execution of w(x)f can depend only on its direct predecessors w(x)d and w(y)e as w(x)d can be only executed after w(y)a and w(y)b, and, w(y)e can be executed only after the execution of w(x)c. As remarked in [4], this simple observation allows us to reduce the control information 6
7 piggybacked on update messages with respect to solutions (e.g. []) that always piggyback a vector of integers of size n. We denote as immediate predecessor set (IP i ) at process p i the set of operation timestamps whose corresponding write operations would immediately precede a write operation issued at that time by p i. Each time a write operation w is executed at p i, w is added into IP i. When a process p i issues a write operation with a timestamp ts then IP i is set to ts Applying writing semantic: the DEL array If a process p i receives an update message of a write operation w(x)a issued by p j whose timestamp is say (j, 25, x), then assume p i executes w(x)a, all update messages related to write operations on variable x issued by p j with sequence number less than 25 are actually overwritten. This information has to be transferred to the receiving processes when p i issues a write operation in order that receivers can discard obsolete values (if any). At this aim, each process manages an array DEL i : array [... n;,... m] of Integers. The component DEL i [j, x] = #seq expresses the knowledge of p i on the sequence number of the last write operation on variable x executed by p j. Each element of the array is initially set to zero, each time a write operation w(x)a is issued by p i, the column of DEL i related x, denoted DEL i [, x], is piggybacked to the update message. When a process p i receives an update message with a timestamp (j, #seq, x) piggybacking DEL[, x], after executing the corresponding write operation, it updates DEL i [, x] by doing a component wise maximum between DEL i [, x] and DEL[, x] and finally sets DEL i [j, x] to #seq Guaranteeing Causal Consistency: the CB and the LCB set A write operation w(x)f should be executed at each process once all the immediate predecessors of w(x)f have been executed but the ones that are made obsolete by w(x)f due to writing semantic (e.g. w(x)d in Figure 3). On the other hand, if we do not constraint the execution of w(x)f to the one of w(x)d, w(x)f has to be executed anyway after all the immediate predecessors of w(x)d in order the execution be causally consistent (see Figure 3). All write operations that constraint the execution of a given write operation w form the causal barrier of w. To manage the causal barrier of a write operation, we introduce two data structures: CB and LCB. Intuitively, the causal barrier of a write operation w(x) is formed by a set of operation timestamps. This set includes (i) the timestamps of each operation w(y) that immediately precedes w(x) with x y and (ii) for each immediately predecessor w (x) of w(x), all timestamps of the operations belonging to the causal barrier of w (x). Let us note that from previous intuitive definition, the size of a causal barrier would have, as complexity, the number of write operations executed during the computation. However a simple observation on the program 7
8 CB w(x)f w(y)a w(x)d w(y)b w(x)f w(x)c w(y)e CB w(y)e Figure 4: Example of causal barriers of the message pattern depicted in Figure 2 order allows to reduce the size of the causal barrier to a data structure of O(n) through a filtering statement. Let us suppose two write operations w(y) and w(z) issued by the same process p i whose timestamps, denoted (i, #seq y, y) and (i, #seq z, z) with #seq y < #seq z, belong to the causal barrier of w(x). There is no point in keeping the timestamp of w(y) in the causal barrier of w(x) as the constraint on the the execution of w(x) imposed by w(z) transitively implies the one of w(y) due to the program order on p i. Following this observation, the causal barrier can be formally defined as follows: Definition 5. The causal barrier (CB w(x) ) of a write operation w(x) is a set of operation timestamps at most one for each process. This set includes the timestamp with the greatest sequence number one for each process taken from the set of timestamps formed by (i) the timestamps of each operation w(y) that immediately precedes w(x) with x y and (ii) for each immediately predecessor w (x) of w(x), all timestamps of the operations belonging to CB w (x). As an example Figure 4 shows the causal barrier of w(x)f. This data structure has therefore a complexity that only in the worst case is O(n). From an operational point of view, in order to guarantee causal consistency, each w(x)v s update message sent by p i has to piggyback as control information CB w(x)v. In this way, when a destination process p i receives an update message related to w(x)v, p i will execute w(x)v (i.e., the value v will be stored in M i [x]) as soon as the following predicate (P) becomes true: (k, d, l) CB w(x)v : (d DEL j [k, l]) (P ) When a process p i issues a w(x)v, to build CB w(x)v needs (i) IP i and (ii) the causal barriers of all the 8
9 immediate predecessors in IP i. To realize the second point p i needs a data structure, denoted LCB i, which memorizes such causal barriers. LCB is therefore a set of causal barriers. It is initialized to, each time a write operation is executed at p i the corresponding causal barrier is added to LCB i and after p i issues a write operation w(x)v, LCB i is set to CB w(x)v. 3.4 Protocol Behavior When a process p i wants to read a location x, p i returns immediately, by using a single assignment statement, the value stored in the location x of local copy of M. The read is legal due to the fact that the execution of a single statement is atomic and then the procedure will return the last value written into the location. Write(x, v) 2 begin 3 #seq i := #seq i + ; CB (i,#seq,x) := ; 4 for each (k, d, l) IP i :: if (l = x) S 5 then CB (i,#seq,x) := CB (i,#seq,x) CB(k,d,l) LCB i ; S 6 S else CB (i,#seq,x) := CB (i,#seq,x) (k, d, l); 7 p k CB (i,#seq,x) := k=,...n (max #seq(cb (i,#seq,x) pk )); 8 send [ Write, x, v, #seq i, DEL i[, x], CB (i,#seq,x) ] to Π; 9 IP i := {(i, #seq i, x)}; LCB i := {CB (i,#seq,x) }; 0 end Figure 5: Write operation executed by a process p i When a process p i wants to a write operation w i (x)v, then it executes the procedure Write(x, v) depicted in Figure 5. In details, it first increments its sequence number and initializes the causal barrier of w(x)v to (line 3). Then p i builds CB w(x)v (lines 4-6) based on IP i and LCB i as defined in Section Line 7 actually compresses CB w(x)v obtained exiting from the for statement by leaving, according to Definition 5, into CB w(x)v at most one timestamp for each distinct process. Then the update message of w(x)v is broadcast to other processes piggybacking CB w(x)v (necessary for the causally ordered execution of w(x)v at receiver side), DEL[, x] (to propagate knowledge on obsolete write operations on variable x) as well as x, #seq and the value v. Finally IP i and LCB i are updated according to their definitions (line 9). Each time a W rite message is received by a process p i a new thread is spawned and the code of this thread is depicted in Figure 6. First at line 2 it is checked if the operation is obsolete (i.e., to the knowledge of p i the operation w(x)v has been overwritten). In the affirmative, the update message is discarded and the operation is not executed. Otherwise, the write operation wait until all operations in CB (j,#seq,x) have been executed. Then the value v is stored into the location x (line 6) and then all data structures are updated according to their definition. Lines from 6 to 0 are executed atomically. 9
10 Figure 7 shows a message pattern with (i) the data structures piggybacked by update messages of w(x)f and w(x)d and (ii) the evolution of the DEL array at process p 4. when (deliver [ Write, x, v, #seq, DEL[, x], CB (j,#seq,x) ] from p j) do 2 if ((#seq DEL i [j, x]) 3 then discard the Write message; 4 exit; 5 wait until ( (k, d, l) CB (j,#seq,x) : d DEL i[k, l]); % Synchronization to respect co % 6 M i[x] := v; S 7 LCB i := LCB i {CB(j,#seq,x) }; S 8 IP i = IP i CB (j,#seq,x) {(j, #seq, x)}; 9 DEL i [j, x] := #seq; 0 k j DEL i [k, x] := max(del i [k, x], DEL[k, x]); Figure 6: Processing of an update message by a process p i 3.5 Discussion Correctness Proof. The proof showing safety and liveness requirement is omitted due to lack of space as it uses the typical induction techniques employed in [, 2, 4]. However, it can be easily devised that: Liveness (i.e., no write operation remains blocked forever at a process) is ensured by the fact that either a write operation w is overwritten by another one, say w, at process p i. In this case w is discarded at p i ; or the write operation w waits all the operations in its causal barrier. Due to the fact that messages cannot be lost and to the update rule of the data structure internal at each process, eventually w will be executed at p i. Safety (i.e., the execution respects Definition 4) Point 2 of Definition 4 (i.e., write operations are causally ordered) is ensured by the wait condition in Figure 6 that guarantees write operations are causally ordered at each process (due to properties of transitive dependencies) and by the use of DEL array to ensure a safe discard of obsolete values. Finally Point of Definition 4 is trivially satisfied (in a wait-free way) as each process reads a value from its local copy of the memory location. Therefore, each read operation returns the last value written onto that location. Comparison to prior solutions. The only solution that exploits the writing semantic ([4]) was designed for a partially replicated setting. The simple adaptation of that protocol to a fully replicated setting would imply a control information, piggybacked to each update, composed by two vectors of size O(n) and O(m) respectively. On the other hand, the solution presented in this work piggybacks on each update message a control information composed by two vectors of size O(n). More specifically, managing the writing semantic 0
11 P w(y)a w(x)f DEL=[0,,,0] CB={(,,y), (4,,y), (2,,y)} P2 w(x)c w(y)e P3 w(x)d DEL=[0,0,0,0] CB={(,,y), (4,,y)} P4 w(y)b P P2 P3 P4 P P2 P3 P4 discard X Y X Y Figure 7: Example of the message pattern of Figure 2 with some data structures requires locally each process to be equipped with an array n m (i.e., DEL[]) and to attach to each message a column of this array. Guaranteeing that the execution of a write operation is causally consistent requires to attach a set of timestamps, the causal barrier, whose cardinality is at most n and each process has to be equipped locally with a set of causal barriers that actually stores the casual barriers of the immediate predecessors of a write operation issued by that process. Then our solution is well-suited for environments in which the number of replicated objects (or memory locations) m is greater than the number of processes n. Let us finally point out that if we do not consider the writing semantic, CB w(x)v = IP i. Therefore the predicate P of Section becomes (i) the same to the one defined in [4] in the context of causal delivery of messages; and (ii) equivalent to the predicate defined by Ahamad et al. in [] based on vector clocks. This equivalence can be easily proved as from the point of view of ensuring causality, a system of vector clock is equivalent to a causal barrier which tracks immediate predecessor of an operation [4]. 4 Conclusion In this paper we proposed a protocol to guarantee causal consistency in a shared memory implemented in a fully replicated setting. This protocol combines two interesting notions to get good performance (in terms for example of local buffer reduction): the writing semantic (defined in [4]) and the transitive dependency tracking
12 to guarantee causally consistent executions (defined in [3]). The protocol piggybacks on each update message a control information which is O(n). As it provides a clear separation of concerns among the two basic notions, it can be used as a starting point for the development of other protocols in more complex settings such as client/server and overlapping groups. References [] M. Ahamad, G. Neiger, J.E. Burns, P. Kohli, P.W. Hutto. Causal Memory: Definitions, Implementation and Programming, Distributed Computing, Vol. 9, No., 995, pp [2] R. Baldoni, A. Mostefaoui, and M.Raynal, Causal Delivery of Messages with Real-Time Data in Unreliable Networks, Journal of Real-time Systems, Vol. 0, No. 3, 996. [3] R. Baldoni, M. Raynal. Fundamentals of Distributed Computing: A Practical Tour of Vector Clocks, IEEE Distributed Systems on-line, Vol. 3, No. 2, [4] R. Baldoni, R. Prakash, M. Raynal, and M. Singhal. Efficient Delta-Causal Broadcasting. International Journal of Computer Systems Science and Engineering, Pages , September 998. [5] C. Dwork and N.A. Lynch L. Stockmeyer, Consensus in the Presence of Partial Synchrony, Journal of the ACM, 988, 35(2), [6] M. Fischer and N. Lynch and M. Patterson, Impossibility of Distributed Consensus with One Faulty Process, Journal of the ACM, 985, 32(2), [7] M. Herlihy and J. Wing. Linearizability: a Correctness Condition for concurrent Objects, ACM TOPLAS, 2(3): , 990 [8] L. Lamport, How to Make a Multiprocessor Computer that Correctly Executes Multiprocess Programs, IEEE Transactions on Computers, Vol. C-28, No. 9, 979, pp [9] Lamport L., Time, Clocks and the Ordering of Events in a Distributed System, Communications of the ACM, 2(7): , 978. [0] Lipton R. and Sandberg J, PRAM: A scalable shared memory, Tech. Rep. CS-TR-80-88, Princeton University, Sept [] Mattern F., Virtual Time and Global States of Distributed Systems, Proc. Parallel and Distributed Algorithms Conference, (Cosnard, Quinton, Raynal, Robert Eds), North-Holland, pp , 988. [2] J. Misra, Axioms for memory access in asynchronous hardware systems, ACM Transactions on Programming Languages and Systems, Vol.8, No., 986, pp [3] R. Prakash, M. Raynal, M. Singhal, An Efficient Causal Ordering Algorithm for Mobile Computing Environments, Proc. 6th IEEE International Conference on Distributed Computing Systems (996) pp [4] M. Raynal, M. Ahamad, Exploiting Write Semantics in Implementig Partially Replicated Causal Objects, Proc. of 6th Euromicro Conference on Parallel and Distributed Systems, pp.75-64, Madrid, January
13 [5] M. Raynal, A. Schiper, From Causal Consistency to Sequential Consistency in Shared Memory Systems, Proc. 5th Int. Conf. on Foundations of Software Technology & Theoretical Computer Science, Bangalore, India, Springer- Verlag LNCS 026 (P.S. Thiagarajan Ed.), 995, pp
A Suite of Formal Denitions for Consistency Criteria. in Distributed Shared Memories Rennes Cedex (France) 1015 Lausanne (Switzerland)
 A Suite of Formal Denitions for Consistency Criteria in Distributed Shared Memories Michel Raynal Andre Schiper IRISA, Campus de Beaulieu EPFL, Dept d'informatique 35042 Rennes Cedex (France) 1015 Lausanne
A Suite of Formal Denitions for Consistency Criteria in Distributed Shared Memories Michel Raynal Andre Schiper IRISA, Campus de Beaulieu EPFL, Dept d'informatique 35042 Rennes Cedex (France) 1015 Lausanne
About the efficiency of partial replication to implement Distributed Shared Memory
 About the efficiency of partial replication to implement Distributed Shared Memory Jean-Michel Hélary IRISA Campus de Beaulieu, 35042 Rennes-cedex, France helary@irisa.fr Alessia Milani DIS, Universitá
About the efficiency of partial replication to implement Distributed Shared Memory Jean-Michel Hélary IRISA Campus de Beaulieu, 35042 Rennes-cedex, France helary@irisa.fr Alessia Milani DIS, Universitá
Memory Consistency. Minsoo Ryu. Department of Computer Science and Engineering. Hanyang University. Real-Time Computing and Communications Lab.
 Memory Consistency Minsoo Ryu Department of Computer Science and Engineering 2 Distributed Shared Memory Two types of memory organization in parallel and distributed systems Shared memory (shared address
Memory Consistency Minsoo Ryu Department of Computer Science and Engineering 2 Distributed Shared Memory Two types of memory organization in parallel and distributed systems Shared memory (shared address
Specifying and Proving Broadcast Properties with TLA
 Specifying and Proving Broadcast Properties with TLA William Hipschman Department of Computer Science The University of North Carolina at Chapel Hill Abstract Although group communication is vitally important
Specifying and Proving Broadcast Properties with TLA William Hipschman Department of Computer Science The University of North Carolina at Chapel Hill Abstract Although group communication is vitally important
A Parametrized Algorithm that Implements Sequential, Causal, and Cache Memory Consistencies
 A Parametrized Algorithm that Implements Sequential, Causal, and Cache Memory Consistencies Ernesto Jiménez b, Antonio Fernández a, Vicent Cholvi c, a Universidad Rey Juan Carlos, 28933 Móstoles, Spain
A Parametrized Algorithm that Implements Sequential, Causal, and Cache Memory Consistencies Ernesto Jiménez b, Antonio Fernández a, Vicent Cholvi c, a Universidad Rey Juan Carlos, 28933 Móstoles, Spain
Time and distributed systems. Just use time stamps? Correct consistency model? Replication and Consistency
 Correct consistency model? Replication and Consistency B COS 58: dvanced Computer Systems Lecture 3 Let s say and B send an op. ll readers see B? ll readers see B? Michael Freedman Some see B and others
Correct consistency model? Replication and Consistency B COS 58: dvanced Computer Systems Lecture 3 Let s say and B send an op. ll readers see B? ll readers see B? Michael Freedman Some see B and others
Causal Consistency Algorithms for Partially Replicated and Fully Replicated Systems
 Causal Consistency Algorithms for Partially Replicated and Fully Replicated Systems TaYuan Hsu, Ajay D. Kshemkalyani, Min Shen University of Illinois at Chicago TaYuan Hsu, Ajay D. Kshemkalyani, MinCausal
Causal Consistency Algorithms for Partially Replicated and Fully Replicated Systems TaYuan Hsu, Ajay D. Kshemkalyani, Min Shen University of Illinois at Chicago TaYuan Hsu, Ajay D. Kshemkalyani, MinCausal
A Methodological Construction of an Efficient Sequential Consistency Protocol Λ
 A Methodological Construction of an Efficient Sequential Consistency Protocol Λ Vicent CHOLVI ffi Antonio FERNÁNDEZ y Ernesto JIMÉNEZ z Michel RAYNAL? ffi Universidad Jaume I, Castellón, Spain y Laboratorio
A Methodological Construction of an Efficient Sequential Consistency Protocol Λ Vicent CHOLVI ffi Antonio FERNÁNDEZ y Ernesto JIMÉNEZ z Michel RAYNAL? ffi Universidad Jaume I, Castellón, Spain y Laboratorio
Low Cost Coherence Protocol for DSM Systems with Processor Consistency 1
 Low Cost Coherence Protocol for DSM Systems with Processor Consistency Jerzy Brzeziński Michał Szychowiak Institute of Computing Science Poznań University of Technology Piotrowo 3a, 6-965 Poznań, POLAND
Low Cost Coherence Protocol for DSM Systems with Processor Consistency Jerzy Brzeziński Michał Szychowiak Institute of Computing Science Poznań University of Technology Piotrowo 3a, 6-965 Poznań, POLAND
Deadline-Constrained Causal Order
 Deadline-Constrained Causal Order L. Rodrigues Universidade de Lisboa FCUL, Campo Grande, 1749-016 Lisboa, Portugal ler@di.fc.ul.pt R. Baldoni University of Rome via Salaria 113 I-00198 Rome, Italy. baldoni@dis.uniroma1.it
Deadline-Constrained Causal Order L. Rodrigues Universidade de Lisboa FCUL, Campo Grande, 1749-016 Lisboa, Portugal ler@di.fc.ul.pt R. Baldoni University of Rome via Salaria 113 I-00198 Rome, Italy. baldoni@dis.uniroma1.it
A Case Study of Agreement Problems in Distributed Systems : Non-Blocking Atomic Commitment
 A Case Study of Agreement Problems in Distributed Systems : Non-Blocking Atomic Commitment Michel RAYNAL IRISA, Campus de Beaulieu 35042 Rennes Cedex (France) raynal @irisa.fr Abstract This paper considers
A Case Study of Agreement Problems in Distributed Systems : Non-Blocking Atomic Commitment Michel RAYNAL IRISA, Campus de Beaulieu 35042 Rennes Cedex (France) raynal @irisa.fr Abstract This paper considers
Fork Sequential Consistency is Blocking
 Fork Sequential Consistency is Blocking Christian Cachin Idit Keidar Alexander Shraer May 14, 2008 Abstract We consider an untrusted server storing shared data on behalf of clients. We show that no storage
Fork Sequential Consistency is Blocking Christian Cachin Idit Keidar Alexander Shraer May 14, 2008 Abstract We consider an untrusted server storing shared data on behalf of clients. We show that no storage
Applying Sequential Consistency to Web Caching
 Applying Sequential Consistency to Web Caching Francisco J. Torres-Rojas and Esteban Meneses Abstract Web caches have several advantages for reducing the server load, minimizing the network traffic and
Applying Sequential Consistency to Web Caching Francisco J. Torres-Rojas and Esteban Meneses Abstract Web caches have several advantages for reducing the server load, minimizing the network traffic and
On the interconnection of message passing systems
 Information Processing Letters 105 (2008) 249 254 www.elsevier.com/locate/ipl On the interconnection of message passing systems A. Álvarez a,s.arévalo b, V. Cholvi c,, A. Fernández b,e.jiménez a a Polytechnic
Information Processing Letters 105 (2008) 249 254 www.elsevier.com/locate/ipl On the interconnection of message passing systems A. Álvarez a,s.arévalo b, V. Cholvi c,, A. Fernández b,e.jiménez a a Polytechnic
Timed Consistency for Shared Distributed Objects
 Timed Consistency for Shared Distributed Objects Francisco J. Torres-Rojas College of Computing Georgia Institute of Technology U.S.A. torres@cc.gatech.edu Mustaque Ahamad College of Computing Georgia
Timed Consistency for Shared Distributed Objects Francisco J. Torres-Rojas College of Computing Georgia Institute of Technology U.S.A. torres@cc.gatech.edu Mustaque Ahamad College of Computing Georgia
Fork Sequential Consistency is Blocking
 Fork Sequential Consistency is Blocking Christian Cachin Idit Keidar Alexander Shraer Novembe4, 008 Abstract We consider an untrusted server storing shared data on behalf of clients. We show that no storage
Fork Sequential Consistency is Blocking Christian Cachin Idit Keidar Alexander Shraer Novembe4, 008 Abstract We consider an untrusted server storing shared data on behalf of clients. We show that no storage
Replication and Consistency
 Replication and Consistency Today l Replication l Consistency models l Consistency protocols The value of replication For reliability and availability Avoid problems with disconnection, data corruption,
Replication and Consistency Today l Replication l Consistency models l Consistency protocols The value of replication For reliability and availability Avoid problems with disconnection, data corruption,
Consensus in Byzantine Asynchronous Systems
 Consensus in Byzantine Asynchronous Systems R. BALDONI Universitá La Sapienza, Roma, Italy J.-M. HÉLARY IRISA, Université de Rennes 1, France M. RAYNAL IRISA, Université de Rennes 1, France L. TANGUY IRISA,
Consensus in Byzantine Asynchronous Systems R. BALDONI Universitá La Sapienza, Roma, Italy J.-M. HÉLARY IRISA, Université de Rennes 1, France M. RAYNAL IRISA, Université de Rennes 1, France L. TANGUY IRISA,
Chapter 4: Distributed Systems: Replication and Consistency. Fall 2013 Jussi Kangasharju
 Chapter 4: Distributed Systems: Replication and Consistency Fall 2013 Jussi Kangasharju Chapter Outline n Replication n Consistency models n Distribution protocols n Consistency protocols 2 Data Replication
Chapter 4: Distributed Systems: Replication and Consistency Fall 2013 Jussi Kangasharju Chapter Outline n Replication n Consistency models n Distribution protocols n Consistency protocols 2 Data Replication
Consistency examples. COS 418: Distributed Systems Precept 5. Themis Melissaris
 Consistency examples COS 418: Distributed Systems Precept 5 Themis Melissaris Plan Midterm poll Consistency examples 2 Fill out this poll: http://tinyurl.com/zdeq4lr 3 Linearizability 4 Once read returns
Consistency examples COS 418: Distributed Systems Precept 5 Themis Melissaris Plan Midterm poll Consistency examples 2 Fill out this poll: http://tinyurl.com/zdeq4lr 3 Linearizability 4 Once read returns
Replication and Consistency. Fall 2010 Jussi Kangasharju
 Replication and Consistency Fall 2010 Jussi Kangasharju Chapter Outline Replication Consistency models Distribution protocols Consistency protocols 2 Data Replication user B user C user A object object
Replication and Consistency Fall 2010 Jussi Kangasharju Chapter Outline Replication Consistency models Distribution protocols Consistency protocols 2 Data Replication user B user C user A object object
Consensus Problem. Pradipta De
 Consensus Problem Slides are based on the book chapter from Distributed Computing: Principles, Paradigms and Algorithms (Chapter 14) by Kshemkalyani and Singhal Pradipta De pradipta.de@sunykorea.ac.kr
Consensus Problem Slides are based on the book chapter from Distributed Computing: Principles, Paradigms and Algorithms (Chapter 14) by Kshemkalyani and Singhal Pradipta De pradipta.de@sunykorea.ac.kr
CS6450: Distributed Systems Lecture 11. Ryan Stutsman
 Strong Consistency CS6450: Distributed Systems Lecture 11 Ryan Stutsman Material taken/derived from Princeton COS-418 materials created by Michael Freedman and Kyle Jamieson at Princeton University. Licensed
Strong Consistency CS6450: Distributed Systems Lecture 11 Ryan Stutsman Material taken/derived from Princeton COS-418 materials created by Michael Freedman and Kyle Jamieson at Princeton University. Licensed
Important Lessons. A Distributed Algorithm (2) Today's Lecture - Replication
 Important Lessons Lamport & vector clocks both give a logical timestamps Total ordering vs. causal ordering Other issues in coordinating node activities Exclusive access to resources/data Choosing a single
Important Lessons Lamport & vector clocks both give a logical timestamps Total ordering vs. causal ordering Other issues in coordinating node activities Exclusive access to resources/data Choosing a single
Multi-writer Regular Registers in Dynamic Distributed Systems with Byzantine Failures
 Multi-writer Regular Registers in Dynamic Distributed Systems with Byzantine Failures Silvia Bonomi, Amir Soltani Nezhad Università degli Studi di Roma La Sapienza, Via Ariosto 25, 00185 Roma, Italy bonomi@dis.uniroma1.it
Multi-writer Regular Registers in Dynamic Distributed Systems with Byzantine Failures Silvia Bonomi, Amir Soltani Nezhad Università degli Studi di Roma La Sapienza, Via Ariosto 25, 00185 Roma, Italy bonomi@dis.uniroma1.it
A Methodological Construction of an Efficient Sequentially Consistent Distributed Shared Memory 1
 The Computer Journal Advance Access published November 3, 2009 The Author 2009. Published by Oxford University Press on behalf of The British Computer Society. All rights reserved. For Permissions, please
The Computer Journal Advance Access published November 3, 2009 The Author 2009. Published by Oxford University Press on behalf of The British Computer Society. All rights reserved. For Permissions, please
An algorithm for Performance Analysis of Single-Source Acyclic graphs
 An algorithm for Performance Analysis of Single-Source Acyclic graphs Gabriele Mencagli September 26, 2011 In this document we face with the problem of exploiting the performance analysis of acyclic graphs
An algorithm for Performance Analysis of Single-Source Acyclic graphs Gabriele Mencagli September 26, 2011 In this document we face with the problem of exploiting the performance analysis of acyclic graphs
Distributed Systems. Lec 12: Consistency Models Sequential, Causal, and Eventual Consistency. Slide acks: Jinyang Li
 Distributed Systems Lec 12: Consistency Models Sequential, Causal, and Eventual Consistency Slide acks: Jinyang Li (http://www.news.cs.nyu.edu/~jinyang/fa10/notes/ds-eventual.ppt) 1 Consistency (Reminder)
Distributed Systems Lec 12: Consistency Models Sequential, Causal, and Eventual Consistency Slide acks: Jinyang Li (http://www.news.cs.nyu.edu/~jinyang/fa10/notes/ds-eventual.ppt) 1 Consistency (Reminder)
Checkpointing and Rollback Recovery in Distributed Systems: Existing Solutions, Open Issues and Proposed Solutions
 Checkpointing and Rollback Recovery in Distributed Systems: Existing Solutions, Open Issues and Proposed Solutions D. Manivannan Department of Computer Science University of Kentucky Lexington, KY 40506
Checkpointing and Rollback Recovery in Distributed Systems: Existing Solutions, Open Issues and Proposed Solutions D. Manivannan Department of Computer Science University of Kentucky Lexington, KY 40506
Coordination and Agreement
 Coordination and Agreement Nicola Dragoni Embedded Systems Engineering DTU Informatics 1. Introduction 2. Distributed Mutual Exclusion 3. Elections 4. Multicast Communication 5. Consensus and related problems
Coordination and Agreement Nicola Dragoni Embedded Systems Engineering DTU Informatics 1. Introduction 2. Distributed Mutual Exclusion 3. Elections 4. Multicast Communication 5. Consensus and related problems
Replication in Distributed Systems
 Replication in Distributed Systems Replication Basics Multiple copies of data kept in different nodes A set of replicas holding copies of a data Nodes can be physically very close or distributed all over
Replication in Distributed Systems Replication Basics Multiple copies of data kept in different nodes A set of replicas holding copies of a data Nodes can be physically very close or distributed all over
Causal Consistency and Two-Phase Commit
 Causal Consistency and Two-Phase Commit CS 240: Computing Systems and Concurrency Lecture 16 Marco Canini Credits: Michael Freedman and Kyle Jamieson developed much of the original material. Consistency
Causal Consistency and Two-Phase Commit CS 240: Computing Systems and Concurrency Lecture 16 Marco Canini Credits: Michael Freedman and Kyle Jamieson developed much of the original material. Consistency
Distributed Algorithms Reliable Broadcast
 Distributed Algorithms Reliable Broadcast Alberto Montresor University of Trento, Italy 2016/04/26 This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. Contents
Distributed Algorithms Reliable Broadcast Alberto Montresor University of Trento, Italy 2016/04/26 This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. Contents
A Wait-free Multi-word Atomic (1,N) Register for Large-scale Data Sharing on Multi-core Machines
 A Wait-free Multi-word Atomic (1,N) Register for Large-scale Data Sharing on Multi-core Machines Mauro Ianni, Alessandro Pellegrini DIAG Sapienza Università di Roma, Italy Email: {mianni,pellegrini}@dis.uniroma1.it
A Wait-free Multi-word Atomic (1,N) Register for Large-scale Data Sharing on Multi-core Machines Mauro Ianni, Alessandro Pellegrini DIAG Sapienza Università di Roma, Italy Email: {mianni,pellegrini}@dis.uniroma1.it
Byzantine Consensus in Directed Graphs
 Byzantine Consensus in Directed Graphs Lewis Tseng 1,3, and Nitin Vaidya 2,3 1 Department of Computer Science, 2 Department of Electrical and Computer Engineering, and 3 Coordinated Science Laboratory
Byzantine Consensus in Directed Graphs Lewis Tseng 1,3, and Nitin Vaidya 2,3 1 Department of Computer Science, 2 Department of Electrical and Computer Engineering, and 3 Coordinated Science Laboratory
A Graph-Theoretic Model of Shared-Memory Legality
 A Graph-Theoretic Model of Shared-Memory Legality Ayru L Oliveira Filho Valmir C Barbosa Centro de Pesquisas de Energia Elétrica CEPEL Caixa Postal 68007 21944-970 Rio de Janeiro - RJ, Brazil ayru@cepelbr
A Graph-Theoretic Model of Shared-Memory Legality Ayru L Oliveira Filho Valmir C Barbosa Centro de Pesquisas de Energia Elétrica CEPEL Caixa Postal 68007 21944-970 Rio de Janeiro - RJ, Brazil ayru@cepelbr
Coordination and Agreement
 Coordination and Agreement 12.1 Introduction 12.2 Distributed Mutual Exclusion 12.4 Multicast Communication 12.3 Elections 12.5 Consensus and Related Problems AIM: Coordination and/or Agreement Collection
Coordination and Agreement 12.1 Introduction 12.2 Distributed Mutual Exclusion 12.4 Multicast Communication 12.3 Elections 12.5 Consensus and Related Problems AIM: Coordination and/or Agreement Collection
Clock Synchronization. Synchronization. Clock Synchronization Algorithms. Physical Clock Synchronization. Tanenbaum Chapter 6 plus additional papers
 Clock Synchronization Synchronization Tanenbaum Chapter 6 plus additional papers Fig 6-1. In a distributed system, each machine has its own clock. When this is the case, an event that occurred after another
Clock Synchronization Synchronization Tanenbaum Chapter 6 plus additional papers Fig 6-1. In a distributed system, each machine has its own clock. When this is the case, an event that occurred after another
Consistent Checkpointing in Distributed Computations: Theoretical Results and Protocols
 Università degli Studi di Roma La Sapienza Dottorato di Ricerca in Ingegneria Informatica XI Ciclo 1999 Consistent Checkpointing in Distributed Computations: Theoretical Results and Protocols Francesco
Università degli Studi di Roma La Sapienza Dottorato di Ricerca in Ingegneria Informatica XI Ciclo 1999 Consistent Checkpointing in Distributed Computations: Theoretical Results and Protocols Francesco
Accepted Manuscript. On the Interconnection of Message Passing Systems. A. Álvarez, S. Arévalo, V. Cholvi, A. Fernández, E.
 Accepted Manuscript On the Interconnection of Message Passing Systems A. Álvarez, S. Arévalo, V. Cholvi, A. Fernández, E. Jiménez PII: S0020-0190(07)00270-0 DOI: 10.1016/j.ipl.2007.09.006 Reference: IPL
Accepted Manuscript On the Interconnection of Message Passing Systems A. Álvarez, S. Arévalo, V. Cholvi, A. Fernández, E. Jiménez PII: S0020-0190(07)00270-0 DOI: 10.1016/j.ipl.2007.09.006 Reference: IPL
Consensus in Distributed Systems. Jeff Chase Duke University
 Consensus in Distributed Systems Jeff Chase Duke University Consensus P 1 P 1 v 1 d 1 Unreliable multicast P 2 P 3 Consensus algorithm P 2 P 3 v 2 Step 1 Propose. v 3 d 2 Step 2 Decide. d 3 Generalizes
Consensus in Distributed Systems Jeff Chase Duke University Consensus P 1 P 1 v 1 d 1 Unreliable multicast P 2 P 3 Consensus algorithm P 2 P 3 v 2 Step 1 Propose. v 3 d 2 Step 2 Decide. d 3 Generalizes
A Mechanism for Sequential Consistency in a Distributed Objects System
 A Mechanism for Sequential Consistency in a Distributed Objects System Cristian Ţăpuş, Aleksey Nogin, Jason Hickey, and Jerome White California Institute of Technology Computer Science Department MC 256-80,
A Mechanism for Sequential Consistency in a Distributed Objects System Cristian Ţăpuş, Aleksey Nogin, Jason Hickey, and Jerome White California Institute of Technology Computer Science Department MC 256-80,
Failures, Elections, and Raft
 Failures, Elections, and Raft CS 8 XI Copyright 06 Thomas W. Doeppner, Rodrigo Fonseca. All rights reserved. Distributed Banking SFO add interest based on current balance PVD deposit $000 CS 8 XI Copyright
Failures, Elections, and Raft CS 8 XI Copyright 06 Thomas W. Doeppner, Rodrigo Fonseca. All rights reserved. Distributed Banking SFO add interest based on current balance PVD deposit $000 CS 8 XI Copyright
A Correctness Proof for a Practical Byzantine-Fault-Tolerant Replication Algorithm
 Appears as Technical Memo MIT/LCS/TM-590, MIT Laboratory for Computer Science, June 1999 A Correctness Proof for a Practical Byzantine-Fault-Tolerant Replication Algorithm Miguel Castro and Barbara Liskov
Appears as Technical Memo MIT/LCS/TM-590, MIT Laboratory for Computer Science, June 1999 A Correctness Proof for a Practical Byzantine-Fault-Tolerant Replication Algorithm Miguel Castro and Barbara Liskov
2. Time and Global States Page 1. University of Freiburg, Germany Department of Computer Science. Distributed Systems
 2. Time and Global States Page 1 University of Freiburg, Germany Department of Computer Science Distributed Systems Chapter 3 Time and Global States Christian Schindelhauer 12. May 2014 2. Time and Global
2. Time and Global States Page 1 University of Freiburg, Germany Department of Computer Science Distributed Systems Chapter 3 Time and Global States Christian Schindelhauer 12. May 2014 2. Time and Global
global checkpoint and recovery line interchangeably). When processes take local checkpoint independently, a rollback might force the computation to it
 Checkpointing Protocols in Distributed Systems with Mobile Hosts: a Performance Analysis F. Quaglia, B. Ciciani, R. Baldoni Dipartimento di Informatica e Sistemistica Universita di Roma "La Sapienza" Via
Checkpointing Protocols in Distributed Systems with Mobile Hosts: a Performance Analysis F. Quaglia, B. Ciciani, R. Baldoni Dipartimento di Informatica e Sistemistica Universita di Roma "La Sapienza" Via
The Wait-Free Hierarchy
 Jennifer L. Welch References 1 M. Herlihy, Wait-Free Synchronization, ACM TOPLAS, 13(1):124-149 (1991) M. Fischer, N. Lynch, and M. Paterson, Impossibility of Distributed Consensus with One Faulty Process,
Jennifer L. Welch References 1 M. Herlihy, Wait-Free Synchronization, ACM TOPLAS, 13(1):124-149 (1991) M. Fischer, N. Lynch, and M. Paterson, Impossibility of Distributed Consensus with One Faulty Process,
Consensus in the Presence of Partial Synchrony
 Consensus in the Presence of Partial Synchrony CYNTHIA DWORK AND NANCY LYNCH.Massachusetts Institute of Technology, Cambridge, Massachusetts AND LARRY STOCKMEYER IBM Almaden Research Center, San Jose,
Consensus in the Presence of Partial Synchrony CYNTHIA DWORK AND NANCY LYNCH.Massachusetts Institute of Technology, Cambridge, Massachusetts AND LARRY STOCKMEYER IBM Almaden Research Center, San Jose,
Lecture 7: Logical Time
 Lecture 7: Logical Time 1. Question from reviews a. In protocol, is in- order delivery assumption reasonable? i. TCP provides it b. In protocol, need all participants to be present i. Is this a reasonable
Lecture 7: Logical Time 1. Question from reviews a. In protocol, is in- order delivery assumption reasonable? i. TCP provides it b. In protocol, need all participants to be present i. Is this a reasonable
Distributed Systems: Consistency and Replication
 Distributed Systems: Consistency and Replication Alessandro Sivieri Dipartimento di Elettronica, Informazione e Bioingegneria Politecnico, Italy alessandro.sivieri@polimi.it http://corsi.dei.polimi.it/distsys
Distributed Systems: Consistency and Replication Alessandro Sivieri Dipartimento di Elettronica, Informazione e Bioingegneria Politecnico, Italy alessandro.sivieri@polimi.it http://corsi.dei.polimi.it/distsys
Automatic synthesis of switching controllers for linear hybrid systems: Reachability control
 Automatic synthesis of switching controllers for linear hybrid systems: Reachability control Massimo Benerecetti and Marco Faella Università di Napoli Federico II, Italy Abstract. We consider the problem
Automatic synthesis of switching controllers for linear hybrid systems: Reachability control Massimo Benerecetti and Marco Faella Università di Napoli Federico II, Italy Abstract. We consider the problem
PAGE-BASED DISTRIBUTED SHARED MEMORY FOR OSF/DCE
 PAGE-BASED DISTRIBUTED SHARED MEMORY FOR OSF/DCE Jerzy Brzeziński Michał Szychowiak Dariusz Wawrzyniak Institute of Computing Science Poznań University of Technology ul. Piotrowo 3a 60-965 Poznań, Poland
PAGE-BASED DISTRIBUTED SHARED MEMORY FOR OSF/DCE Jerzy Brzeziński Michał Szychowiak Dariusz Wawrzyniak Institute of Computing Science Poznań University of Technology ul. Piotrowo 3a 60-965 Poznań, Poland
DISTRIBUTED COMPUTER SYSTEMS
 DISTRIBUTED COMPUTER SYSTEMS CONSISTENCY AND REPLICATION CONSISTENCY MODELS Dr. Jack Lange Computer Science Department University of Pittsburgh Fall 2015 Consistency Models Background Replication Motivation
DISTRIBUTED COMPUTER SYSTEMS CONSISTENCY AND REPLICATION CONSISTENCY MODELS Dr. Jack Lange Computer Science Department University of Pittsburgh Fall 2015 Consistency Models Background Replication Motivation
Consensus. Chapter Two Friends. 2.3 Impossibility of Consensus. 2.2 Consensus 16 CHAPTER 2. CONSENSUS
 16 CHAPTER 2. CONSENSUS Agreement All correct nodes decide for the same value. Termination All correct nodes terminate in finite time. Validity The decision value must be the input value of a node. Chapter
16 CHAPTER 2. CONSENSUS Agreement All correct nodes decide for the same value. Termination All correct nodes terminate in finite time. Validity The decision value must be the input value of a node. Chapter
Strong Consistency & CAP Theorem
 Strong Consistency & CAP Theorem CS 240: Computing Systems and Concurrency Lecture 15 Marco Canini Credits: Michael Freedman and Kyle Jamieson developed much of the original material. Consistency models
Strong Consistency & CAP Theorem CS 240: Computing Systems and Concurrency Lecture 15 Marco Canini Credits: Michael Freedman and Kyle Jamieson developed much of the original material. Consistency models
A parametrized algorithm that implements sequential, causal, and cache memory consistencies
 The Journal of Systems and Software xxx (2007) xxx xxx www.elsevier.com/locate/jss A parametrized algorithm that implements sequential, causal, and cache memory consistencies Ernesto Jiménez b, Antonio
The Journal of Systems and Software xxx (2007) xxx xxx www.elsevier.com/locate/jss A parametrized algorithm that implements sequential, causal, and cache memory consistencies Ernesto Jiménez b, Antonio
Consistency: Relaxed. SWE 622, Spring 2017 Distributed Software Engineering
 Consistency: Relaxed SWE 622, Spring 2017 Distributed Software Engineering Review: HW2 What did we do? Cache->Redis Locks->Lock Server Post-mortem feedback: http://b.socrative.com/ click on student login,
Consistency: Relaxed SWE 622, Spring 2017 Distributed Software Engineering Review: HW2 What did we do? Cache->Redis Locks->Lock Server Post-mortem feedback: http://b.socrative.com/ click on student login,
CS6450: Distributed Systems Lecture 15. Ryan Stutsman
 Strong Consistency CS6450: Distributed Systems Lecture 15 Ryan Stutsman Material taken/derived from Princeton COS-418 materials created by Michael Freedman and Kyle Jamieson at Princeton University. Licensed
Strong Consistency CS6450: Distributed Systems Lecture 15 Ryan Stutsman Material taken/derived from Princeton COS-418 materials created by Michael Freedman and Kyle Jamieson at Princeton University. Licensed
Consensus, impossibility results and Paxos. Ken Birman
 Consensus, impossibility results and Paxos Ken Birman Consensus a classic problem Consensus abstraction underlies many distributed systems and protocols N processes They start execution with inputs {0,1}
Consensus, impossibility results and Paxos Ken Birman Consensus a classic problem Consensus abstraction underlies many distributed systems and protocols N processes They start execution with inputs {0,1}
Replication. Consistency models. Replica placement Distribution protocols
 Replication Motivation Consistency models Data/Client-centric consistency models Replica placement Distribution protocols Invalidate versus updates Push versus Pull Cooperation between replicas Client-centric
Replication Motivation Consistency models Data/Client-centric consistency models Replica placement Distribution protocols Invalidate versus updates Push versus Pull Cooperation between replicas Client-centric
Lecture 6: Logical Time
 Lecture 6: Logical Time 1. Question from reviews a. 2. Key problem: how do you keep track of the order of events. a. Examples: did a file get deleted before or after I ran that program? b. Did this computers
Lecture 6: Logical Time 1. Question from reviews a. 2. Key problem: how do you keep track of the order of events. a. Examples: did a file get deleted before or after I ran that program? b. Did this computers
The Relative Power of Synchronization Methods
 Chapter 5 The Relative Power of Synchronization Methods So far, we have been addressing questions of the form: Given objects X and Y, is there a wait-free implementation of X from one or more instances
Chapter 5 The Relative Power of Synchronization Methods So far, we have been addressing questions of the form: Given objects X and Y, is there a wait-free implementation of X from one or more instances
Consensus a classic problem. Consensus, impossibility results and Paxos. Distributed Consensus. Asynchronous networks.
 Consensus, impossibility results and Paxos Ken Birman Consensus a classic problem Consensus abstraction underlies many distributed systems and protocols N processes They start execution with inputs {0,1}
Consensus, impossibility results and Paxos Ken Birman Consensus a classic problem Consensus abstraction underlies many distributed systems and protocols N processes They start execution with inputs {0,1}
Distributed Systems. Fundamentals Shared Store. Fabienne Boyer Reprise du cours d Olivier Gruber. Université Joseph Fourier. Projet ERODS (LIG)
 Distributed Systems Fundamentals Shared Store Fabienne Boyer Reprise du cours d Olivier Gruber Université Joseph Fourier Projet ERODS (LIG) Message Fundamentals λ Today's Lecture λ The problem: - Sharing
Distributed Systems Fundamentals Shared Store Fabienne Boyer Reprise du cours d Olivier Gruber Université Joseph Fourier Projet ERODS (LIG) Message Fundamentals λ Today's Lecture λ The problem: - Sharing
Fault Tolerance Part II. CS403/534 Distributed Systems Erkay Savas Sabanci University
 Fault Tolerance Part II CS403/534 Distributed Systems Erkay Savas Sabanci University 1 Reliable Group Communication Reliable multicasting: A message that is sent to a process group should be delivered
Fault Tolerance Part II CS403/534 Distributed Systems Erkay Savas Sabanci University 1 Reliable Group Communication Reliable multicasting: A message that is sent to a process group should be delivered
Two-Phase Atomic Commitment Protocol in Asynchronous Distributed Systems with Crash Failure
 Two-Phase Atomic Commitment Protocol in Asynchronous Distributed Systems with Crash Failure Yong-Hwan Cho, Sung-Hoon Park and Seon-Hyong Lee School of Electrical and Computer Engineering, Chungbuk National
Two-Phase Atomic Commitment Protocol in Asynchronous Distributed Systems with Crash Failure Yong-Hwan Cho, Sung-Hoon Park and Seon-Hyong Lee School of Electrical and Computer Engineering, Chungbuk National
Distributed Algorithms Benoît Garbinato
 Distributed Algorithms Benoît Garbinato 1 Distributed systems networks distributed As long as there were no machines, programming was no problem networks distributed at all; when we had a few weak computers,
Distributed Algorithms Benoît Garbinato 1 Distributed systems networks distributed As long as there were no machines, programming was no problem networks distributed at all; when we had a few weak computers,
Distributed Systems (5DV147)
 Distributed Systems (5DV147) Replication and consistency Fall 2013 1 Replication 2 What is replication? Introduction Make different copies of data ensuring that all copies are identical Immutable data
Distributed Systems (5DV147) Replication and consistency Fall 2013 1 Replication 2 What is replication? Introduction Make different copies of data ensuring that all copies are identical Immutable data
A Timing Assumption and a t-resilient Protocol for Implementing an Eventual Leader Service in Asynchronous Shared Memory Systems
 A Timing Assumption and a t-resilient Protocol for Implementing an Eventual Leader Service in Asynchronous Shared Memory Systems Antonio FERNÁNDEZ y Ernesto JIMÉNEZ z Michel RAYNAL? Gilles TRÉDAN? y LADyR,
A Timing Assumption and a t-resilient Protocol for Implementing an Eventual Leader Service in Asynchronous Shared Memory Systems Antonio FERNÁNDEZ y Ernesto JIMÉNEZ z Michel RAYNAL? Gilles TRÉDAN? y LADyR,
Replication of Data. Data-Centric Consistency Models. Reliability vs. Availability
 CIS 505: Software Systems Lecture Note on Consistency and Replication Instructor: Insup Lee Department of Computer and Information Science University of Pennsylvania CIS 505, Spring 2007 Replication of
CIS 505: Software Systems Lecture Note on Consistency and Replication Instructor: Insup Lee Department of Computer and Information Science University of Pennsylvania CIS 505, Spring 2007 Replication of
Distributed Systems Fault Tolerance
 Distributed Systems Fault Tolerance [] Fault Tolerance. Basic concepts - terminology. Process resilience groups and failure masking 3. Reliable communication reliable client-server communication reliable
Distributed Systems Fault Tolerance [] Fault Tolerance. Basic concepts - terminology. Process resilience groups and failure masking 3. Reliable communication reliable client-server communication reliable
Relaxed Memory-Consistency Models
 Relaxed Memory-Consistency Models [ 9.1] In small multiprocessors, sequential consistency can be implemented relatively easily. However, this is not true for large multiprocessors. Why? This is not the
Relaxed Memory-Consistency Models [ 9.1] In small multiprocessors, sequential consistency can be implemented relatively easily. However, this is not true for large multiprocessors. Why? This is not the
Distributed Mutual Exclusion Algorithms
 Chapter 9 Distributed Mutual Exclusion Algorithms 9.1 Introduction Mutual exclusion is a fundamental problem in distributed computing systems. Mutual exclusion ensures that concurrent access of processes
Chapter 9 Distributed Mutual Exclusion Algorithms 9.1 Introduction Mutual exclusion is a fundamental problem in distributed computing systems. Mutual exclusion ensures that concurrent access of processes
Consistency and Replication. Why replicate?
 Consistency and Replication Today: Introduction Consistency models Data-centric consistency models Client-centric consistency models Thoughts for the mid-term Lecture 14, page 1 Why replicate? Data replication:
Consistency and Replication Today: Introduction Consistency models Data-centric consistency models Client-centric consistency models Thoughts for the mid-term Lecture 14, page 1 Why replicate? Data replication:
殷亚凤. Consistency and Replication. Distributed Systems [7]
![殷亚凤. Consistency and Replication. Distributed Systems [7] 殷亚凤. Consistency and Replication. Distributed Systems [7]](/thumbs/93/113815133.jpg) Consistency and Replication Distributed Systems [7] 殷亚凤 Email: yafeng@nju.edu.cn Homepage: http://cs.nju.edu.cn/yafeng/ Room 301, Building of Computer Science and Technology Review Clock synchronization
Consistency and Replication Distributed Systems [7] 殷亚凤 Email: yafeng@nju.edu.cn Homepage: http://cs.nju.edu.cn/yafeng/ Room 301, Building of Computer Science and Technology Review Clock synchronization
Hardware Memory Models: x86-tso
 Hardware Memory Models: x86-tso John Mellor-Crummey Department of Computer Science Rice University johnmc@rice.edu COMP 522 Lecture 9 20 September 2016 Agenda So far hardware organization multithreading
Hardware Memory Models: x86-tso John Mellor-Crummey Department of Computer Science Rice University johnmc@rice.edu COMP 522 Lecture 9 20 September 2016 Agenda So far hardware organization multithreading
Mobile Agent Model for Transaction Processing in Distributed Database Systems
 Mobile gent Model for Transaction Processing in Distributed Database Systems Takao Komiya, Hiroyuki Ohshida, and Makoto Takizawa Tokyo Denki University E-mail {komi,ohsida,taki}@takilab.k.dendai.ac.jp
Mobile gent Model for Transaction Processing in Distributed Database Systems Takao Komiya, Hiroyuki Ohshida, and Makoto Takizawa Tokyo Denki University E-mail {komi,ohsida,taki}@takilab.k.dendai.ac.jp
Coordination and Agreement
 Coordination and Agreement 1 Introduction 2 Distributed Mutual Exclusion 3 Multicast Communication 4 Elections 5 Consensus and Related Problems AIM: Coordination and/or Agreement Collection of algorithms
Coordination and Agreement 1 Introduction 2 Distributed Mutual Exclusion 3 Multicast Communication 4 Elections 5 Consensus and Related Problems AIM: Coordination and/or Agreement Collection of algorithms
Consistency and Replication. Why replicate?
 Consistency and Replication Today: Consistency models Data-centric consistency models Client-centric consistency models Lecture 15, page 1 Why replicate? Data replication versus compute replication Data
Consistency and Replication Today: Consistency models Data-centric consistency models Client-centric consistency models Lecture 15, page 1 Why replicate? Data replication versus compute replication Data
Pet: An Interactive Software Testing Tool
 Pet: An Interactive Software Testing Tool Elsa Gunter, Robert Kurshan, and Doron Peled Bell Laboratories 600 Mountain Ave. Murray Hill, NJ 07974 Abstract. We describe here the Pet (standing for path exploration
Pet: An Interactive Software Testing Tool Elsa Gunter, Robert Kurshan, and Doron Peled Bell Laboratories 600 Mountain Ave. Murray Hill, NJ 07974 Abstract. We describe here the Pet (standing for path exploration
Distributed Systems. 09. State Machine Replication & Virtual Synchrony. Paul Krzyzanowski. Rutgers University. Fall Paul Krzyzanowski
 Distributed Systems 09. State Machine Replication & Virtual Synchrony Paul Krzyzanowski Rutgers University Fall 2016 1 State machine replication 2 State machine replication We want high scalability and
Distributed Systems 09. State Machine Replication & Virtual Synchrony Paul Krzyzanowski Rutgers University Fall 2016 1 State machine replication 2 State machine replication We want high scalability and
Implementing Isolation
 CMPUT 391 Database Management Systems Implementing Isolation Textbook: 20 & 21.1 (first edition: 23 & 24.1) University of Alberta 1 Isolation Serial execution: Since each transaction is consistent and
CMPUT 391 Database Management Systems Implementing Isolation Textbook: 20 & 21.1 (first edition: 23 & 24.1) University of Alberta 1 Isolation Serial execution: Since each transaction is consistent and
Making Consistency More Consistent: A Unified Model for Coherence, Consistency and Isolation
 Making Consistency More Consistent: A Unified Model for Coherence, Consistency and Isolation ABSTRACT Adriana Szekeres University of Washington aaasz@cs.washington.edu Ordering guarantees are often defined
Making Consistency More Consistent: A Unified Model for Coherence, Consistency and Isolation ABSTRACT Adriana Szekeres University of Washington aaasz@cs.washington.edu Ordering guarantees are often defined
arxiv: v1 [cs.dc] 8 May 2017
![arxiv: v1 [cs.dc] 8 May 2017 arxiv: v1 [cs.dc] 8 May 2017](/thumbs/81/82817673.jpg) Towards Reduced Instruction Sets for Synchronization arxiv:1705.02808v1 [cs.dc] 8 May 2017 Rati Gelashvili MIT gelash@mit.edu Alexander Spiegelman Technion sashas@tx.technion.ac.il Idit Keidar Technion
Towards Reduced Instruction Sets for Synchronization arxiv:1705.02808v1 [cs.dc] 8 May 2017 Rati Gelashvili MIT gelash@mit.edu Alexander Spiegelman Technion sashas@tx.technion.ac.il Idit Keidar Technion
Self Stabilization. CS553 Distributed Algorithms Prof. Ajay Kshemkalyani. by Islam Ismailov & Mohamed M. Ali
 Self Stabilization CS553 Distributed Algorithms Prof. Ajay Kshemkalyani by Islam Ismailov & Mohamed M. Ali Introduction There is a possibility for a distributed system to go into an illegitimate state,
Self Stabilization CS553 Distributed Algorithms Prof. Ajay Kshemkalyani by Islam Ismailov & Mohamed M. Ali Introduction There is a possibility for a distributed system to go into an illegitimate state,
EECS 144/244: Fundamental Algorithms for System Modeling, Analysis, and Optimization
 EECS 144/244: Fundamental Algorithms for System Modeling, Analysis, and Optimization Dataflow Lecture: SDF, Kahn Process Networks Stavros Tripakis University of California, Berkeley Stavros Tripakis: EECS
EECS 144/244: Fundamental Algorithms for System Modeling, Analysis, and Optimization Dataflow Lecture: SDF, Kahn Process Networks Stavros Tripakis University of California, Berkeley Stavros Tripakis: EECS
Monitoring Stable Properties in Dynamic Peer-to-Peer Distributed Systems
 Monitoring Stable Properties in Dynamic Peer-to-Peer Distributed Systems Sathya Peri and Neeraj Mittal Department of Computer Science, The University of Texas at Dallas, Richardson, TX 75083, USA sathya.p@student.utdallas.edu
Monitoring Stable Properties in Dynamic Peer-to-Peer Distributed Systems Sathya Peri and Neeraj Mittal Department of Computer Science, The University of Texas at Dallas, Richardson, TX 75083, USA sathya.p@student.utdallas.edu
Local Coteries and a Distributed Resource Allocation Algorithm
 Vol. 37 No. 8 Transactions of Information Processing Society of Japan Aug. 1996 Regular Paper Local Coteries and a Distributed Resource Allocation Algorithm Hirotsugu Kakugawa and Masafumi Yamashita In
Vol. 37 No. 8 Transactions of Information Processing Society of Japan Aug. 1996 Regular Paper Local Coteries and a Distributed Resource Allocation Algorithm Hirotsugu Kakugawa and Masafumi Yamashita In
Section 4 Concurrent Objects Correctness, Progress and Efficiency
 Section 4 Concurrent Objects Correctness, Progress and Efficiency CS586 - Panagiota Fatourou 1 Concurrent Objects A concurrent object is a data object shared by concurrently executing processes. Each object
Section 4 Concurrent Objects Correctness, Progress and Efficiency CS586 - Panagiota Fatourou 1 Concurrent Objects A concurrent object is a data object shared by concurrently executing processes. Each object
arxiv: v2 [cs.dc] 27 Jul 2016
![arxiv: v2 [cs.dc] 27 Jul 2016 arxiv: v2 [cs.dc] 27 Jul 2016](/thumbs/93/113814906.jpg) On Composition and Implementation of Sequential Consistency Matthieu Perrin, Matoula Petrolia, Achour Mostéfaoui, and Claude Jard arxiv:1607.06258v2 [cs.dc] 27 Jul 2016 LINA University of Nantes, France
On Composition and Implementation of Sequential Consistency Matthieu Perrin, Matoula Petrolia, Achour Mostéfaoui, and Claude Jard arxiv:1607.06258v2 [cs.dc] 27 Jul 2016 LINA University of Nantes, France
Coordination 2. Today. How can processes agree on an action or a value? l Group communication l Basic, reliable and l ordered multicast
 Coordination 2 Today l Group communication l Basic, reliable and l ordered multicast How can processes agree on an action or a value? Modes of communication Unicast 1ç è 1 Point to point Anycast 1è
Coordination 2 Today l Group communication l Basic, reliable and l ordered multicast How can processes agree on an action or a value? Modes of communication Unicast 1ç è 1 Point to point Anycast 1è
CSE 5306 Distributed Systems
 CSE 5306 Distributed Systems Fault Tolerance Jia Rao http://ranger.uta.edu/~jrao/ 1 Failure in Distributed Systems Partial failure Happens when one component of a distributed system fails Often leaves
CSE 5306 Distributed Systems Fault Tolerance Jia Rao http://ranger.uta.edu/~jrao/ 1 Failure in Distributed Systems Partial failure Happens when one component of a distributed system fails Often leaves
Shared Memory Seif Haridi
 Shared Memory Seif Haridi haridi@kth.se Real Shared Memory Formal model of shared memory No message passing (No channels, no sends, no delivers of messages) Instead processes access a shared memory Models
Shared Memory Seif Haridi haridi@kth.se Real Shared Memory Formal model of shared memory No message passing (No channels, no sends, no delivers of messages) Instead processes access a shared memory Models
Self-Stabilizing Distributed Queuing
 Self-Stabilizing Distributed Queuing Srikanta Tirthapura Dept. of Electrical and Computer Engg. Iowa State University Ames, IA, USA, 50011 snt@iastate.edu Maurice Herlihy Computer Science Department Brown
Self-Stabilizing Distributed Queuing Srikanta Tirthapura Dept. of Electrical and Computer Engg. Iowa State University Ames, IA, USA, 50011 snt@iastate.edu Maurice Herlihy Computer Science Department Brown
Petri Nets ~------~ R-ES-O---N-A-N-C-E-I--se-p-te-m--be-r Applications.
 Petri Nets 2. Applications Y Narahari Y Narahari is currently an Associate Professor of Computer Science and Automation at the Indian Institute of Science, Bangalore. His research interests are broadly
Petri Nets 2. Applications Y Narahari Y Narahari is currently an Associate Professor of Computer Science and Automation at the Indian Institute of Science, Bangalore. His research interests are broadly
Implementing a Register in a Dynamic Distributed System
 Implementing a Register in a Dynamic Distributed System Roberto Baldoni, Silvia Bonomi, Anne-Marie Kermarrec, Michel Raynal Sapienza Università di Roma, Via Ariosto 25, 85 Roma, Italy INRIA, Univeristé
Implementing a Register in a Dynamic Distributed System Roberto Baldoni, Silvia Bonomi, Anne-Marie Kermarrec, Michel Raynal Sapienza Università di Roma, Via Ariosto 25, 85 Roma, Italy INRIA, Univeristé
CSE 5306 Distributed Systems. Fault Tolerance
 CSE 5306 Distributed Systems Fault Tolerance 1 Failure in Distributed Systems Partial failure happens when one component of a distributed system fails often leaves other components unaffected A failure
CSE 5306 Distributed Systems Fault Tolerance 1 Failure in Distributed Systems Partial failure happens when one component of a distributed system fails often leaves other components unaffected A failure
Consensus. Chapter Two Friends. 8.3 Impossibility of Consensus. 8.2 Consensus 8.3. IMPOSSIBILITY OF CONSENSUS 55
 8.3. IMPOSSIBILITY OF CONSENSUS 55 Agreement All correct nodes decide for the same value. Termination All correct nodes terminate in finite time. Validity The decision value must be the input value of
8.3. IMPOSSIBILITY OF CONSENSUS 55 Agreement All correct nodes decide for the same value. Termination All correct nodes terminate in finite time. Validity The decision value must be the input value of
To do. Consensus and related problems. q Failure. q Raft
 Consensus and related problems To do q Failure q Consensus and related problems q Raft Consensus We have seen protocols tailored for individual types of consensus/agreements Which process can enter the
Consensus and related problems To do q Failure q Consensus and related problems q Raft Consensus We have seen protocols tailored for individual types of consensus/agreements Which process can enter the
June Gerd Liefländer System Architecture Group Universität Karlsruhe, System Architecture Group
 Distributed Systems 14 Consistency June-29-2009 Gerd Liefländer System Architecture Group 2009 Universität Karlsruhe, System Architecture Group 1 Overview Outline Motivation & Introduction Consistency
Distributed Systems 14 Consistency June-29-2009 Gerd Liefländer System Architecture Group 2009 Universität Karlsruhe, System Architecture Group 1 Overview Outline Motivation & Introduction Consistency
