A Metadata Management Method Base on Directory Path Code
|
|
|
- Karin Gregory
- 6 years ago
- Views:
Transcription
1 JOURNAL OF SOFTWARE, VOL. 9, NO. 9, SEPTEMBER A Metadata Management Method Base on Directory Path Code Hui Cai Logistical Engineering University of P.L.A, Chongqing, China caihui_cool@126.com Shenglin Li Logistical Engineering University of P.L.A, Chongqing, China @qq.com Zhaoxia Wang Logistical Engineering University of P.L.A, Chongqing, China weimo1234@sina.com Xingchen Li Logistical Engineering University of P.L.A, Chongqing, China since0701@163.com Lichuan Huang Ministry of Supplies & Pol Chengdu Military Region, Chengdu, China lichuan_85@aliyun.com Abstract Metadata distribution is important in mass storage system. Sub-tree partition and hash are two traditional metadata distribution algorithms used in file system. But they both have a defect in system scalability. This paper presents a new metadata management method, Directory Path Code Hash ( DPCH ). This method is to store directory and file metadata separately, and effectively solving the unbalanced metadata distribution and access hot point problems in Sub-tree partition and the excessive reading times and large metadata migration amount after directory property modification in hash algorithm. The experiment indicates that this method proposed significantly outweighs other algorithms in terms of throughput rate, metadata distribution, reading times, etc. Index Terms metadata distribution, binary code, file system, directory path code hash(dpch) I. INTRODUCTION With the rapid development of scientific computing and network application, the data size of network information is increasing constantly and PB-grade mass data storage system plays a more and more important role. As a new storage structure, object-based storage adopts the current network technology and storage technology and provides a foundation for mass data storage system. The core idea of this object-based mass data parallel storage system is to store the metadata and data of files separately and manage them in a distributed cluster mode. According to relevant studies, many operations in mass data storage systems are for metadata only. 75.4% of read operations requires the use of metadata, accounting for 49% of total time and space consumption; 82.2% of write operations requires the use of metadata, accounting for 63.5% total time and space consumption [1-2]. Therefore, the metadata management efficiency determines the performance of the whole storage system, and the realization of high performance, high reliability, load balance and expansion of metadata management are the hot topics of current study on mass data storage system. Regarding to the structure of metadata management system, exsiting researches mainly divided into two methods, they are centralized metadata servers and distributed metadata servers. The centralized metadata servers means the single decisive metadata data server node exists in the storage network, the interaction only exsits between other metadata servers and the decisive metadata server. Though the structure of this method is relatively simple, it has an obvious bottleneck. To decrease the happening rate of this bottleneck, we could optimize the processing paths requested by metadata, which could, to some extent, meet the requirements of the system scale expansion. While the distributed metadata servers indicates no single decisive server does not exsit in the storage network, and all metadata server could intercommunicate. Structurally speaking, there is no bottleneck, but it is relatively complicated which need a consistent preservation. From the metadata distribution strategy, researches are mainly include Sub-tree partition and Hash algorithm. The research findings on Sub-tree partition are LOCUS [Popek 1986], AFS [Morris 1986], CODA doi: /jsw
2 2444 JOURNAL OF SOFTWARE, VOL. 9, NO. 9, SEPTEMBER 2014 [Satyanarayanan 1990], Sprite [Ousterhout 1988], Dynamic Sub-tree partition [Weil 2004], etc. The research findings on Hash algorithm are Vesta [Corbett 1996], InterMezzo [Braam 1999], RAMA [Miller 1997], Lustre [Braam2002], Dynamic Hashing [Li2006], etc. This paper, based on previous studies, proposes a new metadata management method based on path object codes called Directory Path Code Hash. This method is to store directory and file metadata separately, perform hash distribution through binary coding of directory paths, and introduce the concepts of bucket partition, comprehensive access authority and main and secondary mapping tables, effectively solving the access hot point and large metadata migration amount after directory property modification. II. RELEVANT STUDIES Metadata distribution is an important study aspect of metadata management. Reasonable data distribution may bring forth high retrieval efficiency, balanced load and good system expansibility. Metadata is the data for data description, and is small in size. However, with the constant expansion of system size and application degree, metadata size will increase gradually. Therefore, a good metadata distribution strategy may maximize the use of the whole cluster resources, realize the uniform load distribution between different metadata servers, and improve the performance of the whole storage system [3-4]. The current study mainstreams may be classified into two types; i.e., sub-tree partition [5] and hash algorithm [6]. A. Sub-tree Partition Sub-tree partition, proposed by Popek et al [7] from Massachusetts Institute of Technology in 1986, could be classified into static sub-tree partition and dynamic subtree partition. Static sub-tree partition is to distribute all subdirectories or certain subdirectories at a lower level to different metadata servers for storage. The advantages include that the metadata distribution is simple and it could maintain a traditional hierarchical file directory structure and the disadvantages include that it could not effectively partition the load between different metadata servers. When metadata becomes a hot access point, it will become the performance bottleneck of the whole system and the computing consumption during directory traversal process is large. Dynamic sub-tree partition is to entrust different sub-trees in the hierarchical directory structure of file systems to different metadata servers. The advantages include that the partition granularity is smaller, the method is more flexible and the dynamic load balance is realized according to the load of metadata server; and the disadvantages include that the consumption of directory traversal is large, the repeat cache of prefix directory information reduces the utilization rate and hit rate of Cache, and large amount of metadata migration is required when a sub-tree is reentrusted. B. Hash Algorithm A hash algorithm is also called static hash algorithm, which was proposed by Corbett et al [8] from IBM in The basic idea of a hash algorithm to hash a certain key value in files, such as file name or path, and then uniformly distribute the files to different metadata servers according to the hash results. The best advantage of this method is the realization of load balance, avoiding the bottleneck problem that a certain directory becomes a hot access point. This algorithm also has disadvantages. First, hash algorithm destroys the original hierarchical directory structure, which is not good for the search of instructions similar to IS; actually, the system expansibility is poor in that the output range will also be determined when a certain hash function is determined, and mass data migration will be required if output range needs to be expanded and hash function needs to be changed. Second, the file rename operation is not well supported. After a file is renamed, a large amount of data between metadata servers needs to be re-distributed. C. Lazy Hybrid Algorithm The Lazy Hybrid (LH) algorithm was proposed by Brandt et al [9] from University of California, Santa Cruz in It combines two types of algorithms, i.e., tree structure and Hash algorithm, use full pathname of files to compute hash value and then define the storage position of metadata in Metadata Lookup Table (MLT) with the hash value obtained as the index. The advantage is that it integrates the directory access authority into the metadata of every file, thus reducing the consumption of directory path traversal. The disadvantage is that the recomputation of hashed value will generate the migration and upgrading of a large amount of metadata, thus not reducing the consumption of system and not realizing the goal of distributed directory renaming. III. DIRECTORY PATH CODE HASH A. Basic Idea By analyzing the studies and exiting problems of metadata management, this paper proposes a new metadata management method, Directory Path Code Hash ( DPCH ). The method differs from other traditional file system metadata management methods in that it has the following features. First, the partition granularity is different. The hash codes adopted in traditional file systems are for files, but this file hash algorithm has manage defects, which are described in Article II hereof; statistics indicates that the operation number of directory only accounts for less than 10% of the total file number. Therefore, the paper adopts the directory-based codes, which differs from traditional file systems in partition granularity, significantly reducing the complexity of operation. Second, the storage method is different. In traditional file systems, file metadata is used to store the access properties of files and the storage position of data block. From the perspective of management, data access is controlled by file property, while data property is controlled by directory path property. Therefore, this
3 JOURNAL OF SOFTWARE, VOL. 9, NO. 9, SEPTEMBER paper classifies file metadata into directory property and file property, and store and management them separately. Directory property includes the absolute directory path of files and the access control authority of directories; file property includes the access properties such as file name, file type, creation time, modification time and file size. This storage mode is the further deepening of objectbased storage structure, eliminating the metadata upgrading and migration caused by directory modification, and this separation storage mode may better reduce the directory path traversal consumption and disk I/O times. Third, the coding type is different. According to the first feature, the paper adopts the coding method based on directory path. However, the directory-based coding in existing documents and studies mostly adopts the full-path name as the main key value of hash codes, the biggest problem of which is that the directory renaming operation may require a large amount of file migration. Therefore, this paper proposes a new coding method, the basic idea of which is to perform binary transcoding of directory name according to creation time and then take it as a hash major key. That is, a mapping layer is added between directory full-path name and hash major key value, thus avoiding the metadata migration caused by directory renaming operation. Fourth, the concept of a bucket partition is introduced. For the partition granularity based on directory coding, we introduce the concept of bucket partition to overcome the metadata distribution and load balance problems caused by the uncertainty of file quantity under directory. That is, every path code could store only a certain quantity of metadata; and when the metadata quantity under a certain path code, a new path code will be created. B. System Model The DPCH system model realized in this paper is composed of the following parts: client, client file system (CFS), directory management server (DMS), metadata server (MDS) and object storage device (OSD). The working principle of this system model is similar to the tripartite transmission framework structure commonly used in object-based storage systems, but the study object is different slightly. The object-based storage studies the storage and management of files, while this paper studies the storage and index management of metadata. The structure of the system model is shown in Figure 1. OSD FileRead The operation of file Client CFS Metadate properties MDS Client operation Directory properties The operation of directory Figure 1. DPCH System Model CFS is mainly responsible for providing hierarchical directory structure and metadata management system interface for upper application, and supports the upper DMS user operation to execute complete file operations such as creation, deletion and modification. DMS stores all directory paths, file names under directory, father directory, existing file quantity of bucket and binary encodes of path, and is mainly responsible for the management of directory path properties such as path coding and query, creation, deletion and modification. MDS stores all metadata information and is mainly responsible for the storage and management of all metadata under directory, including the query, creation, upgrading and deletion of metadata. The cooperation of MDS and DMS provides uniform naming space and rules for the whole storage system, controls the client s access authority to the storage system, and is responsible for directory hierarchical partition and authority management as well as relevant operations on metadata. OSD is responsible for the storage of bottom data and the supply of object-based storage interface service. IV. METADATA DISTRIBUTION In the metadata management system proposed in this paper, metadata management is divided into two independent parts; i.e., directory management server and metadata server, so as to separate the directory information and the file metadata under directory. Directory information mainly comprises the authority distribution and hierarchical management of directory, and file information mainly includes the contents of file metadata. Directory management server is specifically responsible for directory coding, directory traversal and authority management tasks, minimizes the cache occupancy, applies more cache on file metadata and reduces the disc I/O consumption of metadata read and right, thus alleviating the management task of file metadata in metadata server and enabling it to focus more on the management of file data. A. Improved Metadata Distribution Algorithm Basically, metadata distribution algorithm based on path object coding adopts Hash algorithm, but has two features. First, the hash object is directory, not file; second, the hash content is binary codes after path transcoding, not directory path. We may express the improved metadata distribution algorithm with the following three formulas: pathcode=f(path) (1) result=hash ( pathcode ) 错误! 未找到引用源 (2) 错误! 未找到引用源 MDS_Location=Search (result) (3) In Formula (1), f(x) is the function used for the coding of directory path name. We specify fixed-length binary code as the directory path name, with length as N and formalization as (N figures). Therefore, the new equative directory under a certain path may be expressed respectively according to the creation time [ ], [ ], [ ], [ ], [ ], [ ], [ ], [ ]. The absolute path of directory after coding is expressed as
4 2446 JOURNAL OF SOFTWARE, VOL. 9, NO. 9, SEPTEMBER \ \...\ \..., so the only code of any directory in file system formed at creation could be obtained by this analogy. This algorithm may be expressed as: CreatCode (path) /path is a new directory under current directory/ if (PathCode_Father (path)!= null) /path s father directory exists/ { CodeID++; /under current directory, create directory code ID plus 1/ PathCode (path); /code the path according to the CodeID value/ /path's absolute path code is path s upper directory/ /code plus \Code (path) / } else /path s father directory does not exist/ { PathCode (path) = ; /path s code is N- digit full 0 binary code/ /path s absolute path code is N- digit full 0 binary code/ } In Formula (2), Hash (x) is the hash function used by this algorithm, the function value is the path code in Formula (1), and result is the result obtained after path code hash.in Formula (3), Search (x) is the distribution function from has result to MDS_Location, while MDS_Location is the distribution position of metadata under this directory in MDS cluster. Therefore, Formula (3) could also be considered as the mapping function from hash directory code value in query operation to metadata MDS cluster distribution position. B. Storage Object Distribution This paper separately stores the metadata directory and files; thus, the storage objects include directory information and file information respectively. When the Client has new write-in contents, new metadata will be written in DMS and MDS. For directory information, DMS is responsible for the management and maintenance, and the structure includes the absolute path of directory, the binary code of directory, father directory information, names of all files under this equative directory (excluding the directory name under this directory) and bucket volume information. See the following figure: Figure 2. Distribution of Directory Storage Object Dir1 contains the content such as Dir1 s absolute path, binary code , name file1 and file2 under this directory and bucket volume information. Since Dir1 has no father directory, there is no father directory information.dir2 contains the content such as Dir2 s absolute path, binary code \ , file3, file4, bucket volume information and father directory Dir1 s information. For file information, DMS and MDS are jointly responsible for the management and maintenance. To be more specific, DMS is responsible for recording the names of files under the corresponding directory, and MDS is responsible for storing the metadata of the file. The distribution of file metadata in MDS is determined by the improved metadata distribution algorithm as mentioned in Article III. First, it looks up the corresponding binary codes according to the directory of the files, hash the binary codes, then apply the hash result into the distribution function, and finally determine the actual storage position of file metadata in MDS. During the actual application process of system, we set a fixed upper volume limit for bucket. For example, we specify the upper volume limit of bucket as 50, the bucket volume information in every directory code in DMS the actual file quantity and bucket status value respectively. When there are new write-in contents in this directory, DMS will first check the bucket status value under this directory code. If the status value is not full, the file name after successful creation will be stored in this directory, and the actual file quantity will increase by 1.If the status value is full, the binary code of the directory will be created, and then the file name will be written in the new directory code. This indicates that the same directory in DMS may have several binary code records, that is, the contained file metadata exists in the different positions of MDS. This way may effectively avoid the problems of unbalanced distribution of metadata and load balance. C. Metadata Storage Metadata storage is mainly classified into directory storage and file storage. For directory, the position of directory in DMS and relevant information need to be determined. First, Client sends a request on directory creation to DMS, which will check whether this directory exists. If this directory exists,
5 JOURNAL OF SOFTWARE, VOL. 9, NO. 9, SEPTEMBER DMS will return the existence information to Client; if this directory does not exist, DMS will check whether the father directory of this directory exists. If the father directory exists, DMS will create a new directory, perform binary coding on the new directory according to Formula (1) in Article III, perform binary transcoding, set the volume information of the directory bucket, save the father directory information, and finally return the successful creation information to DMS. If DMS finds that the father directory of the new directory does not exist, will look up the maximum matching father directory of this directory, then circularly construct the directory according to the maximum matching father directory and the method of level-by-level creation, and finally return the successful creation information to Client. For file, the following two aspects need to be determined: first, directory structure of file storage, i.e., the position of file directory in DMS, since the tree structure of file directory is mainly completed and maintained by DMS; second, the position of file metadata in MDS, i.e., the specific storage position of metadata. Therefore, first, Client needs to send the file directory look-up request to DMS, which will look up in the existing directory. If DMS finds the path of the directory and the bucket volume under this directory code is not full, DMS will hash the binary codes of the path and look up the storage ID of metadata in MDS according to the hash results and metadata distribution algorithm, and then return to Client which then sends the write application to the corresponding MDS. After the write operation of metadata is completed, MDS sends the success information to DMS, which will add the file name under corresponding directory and increase the actual bucket volume under this directory code by 1. If DMS finds that the bucket volume under this directory code is ready full, it will create a new directory code record, perform the binary coding on the directory according to the algorithm in Formula (1) in Article III, reset the bucket volume information and father directory information, hash the binary code of the directory, look up the storage ID of metadata in MDS according to the hash results and metadata distribution algorithm, and then return to Client which then sends the write application to the corresponding MDS. After the write operation of metadata is completed, MDS sends the success information to DMS, which will add the file name under corresponding directory and increase the actual bucket volume under this directory code by 1. If DMS does not find the directory, it will create a new directory according to the method above and then complete the file creation operation. V. METADATA EXPRESSION A. Directory Index Entry We learn from the above introduction that the metadata management method adopted in this paper differs from traditional metadata management methods in that directory path information is independently managed and stored by DMS, the service is provided by one or several servers (constituting a server cluster) according to storage size, and the only directory binary code corresponding to MDS address is distributed to all directory paths through binary transcoding of path, thus guaranteeing the one-toone correspondence of binary code and MDS address. The directory index entries of DMS include: DirectoryPath: refers to the path name of the directory; DirectoryID: refers to the binary code of the directory; FatherDirectory: refers to the father directory path name of the directory; DircetoryAC: refers to the self access control authority property of the directory; DircetoryAC F: refers to the comprehensive access control authority property of the directory; FileName: refers to the names of all files under the directory; FileNum: refers to the quantity of files under the directory; BC: refers to whether the quantity of files under the directory is full. The directory index entry is determined only by DirectoryID, and the file metadata under this directory is distributed to different metadata servers according to the hashed value of Directory. The codes may, according to the system storage size, control the directory volume by adjusting the digits of binary codes. This way may avoid the migration and upgrading of metadata under this directory caused by directory modification. FatherDirectory refers to the upper father directory of the directory, and is used for maintaining the tree structure of directory. DirectoryAC is used for controlling user s access authority. Filename is used to express the file name under the directory code. After the introduction of bucket, a certain directory may have several codes and each code may store different files. FileNum and BC is about the information volume of bucket, with FileNum referring to the quantity of files in the bucket and BC referring to whether the bucket is full. When accessing a certain file, it will first look up the DircetoryAC of the file directory path in DMS and determine whether the user has corresponding access authority. If the user has no access authority, it will reject the access; on the contrary, it will look up the file s ID in MDS through the binary code of the directory and return it together with DircetoryAC to Client, which will store the directory cache obtained to local Cache and then obtain file metadata in corresponding MDS. The positioning of directory index in local Cache is to increase the metadata access efficiency. In default, the user will access the local Cache for the first time. This is because the possibility of the same user accessing the same directory successively is very high according to principle of locality. In the following two circumstances, Cache will expire. First, the user detects that the cache has expired; second, the directory index that the user accesses changes. The following is the comparison taking the file access process according to static sub-tree segmentation as an example and assuming the access file is /usr/src/test/hello.c.
6 2448 JOURNAL OF SOFTWARE, VOL. 9, NO. 9, SEPTEMBER 2014 The access process of static sub-tree segmentation includes: (1) GetAttr (usr); (2) LookUp (src); (3) GetAttr (src); (4) LookUp (test); (5) GetAttr (test); (6) LookUp (hello.c); (7) GetAttr (hello.c) and (8) Read (hello.c). The first seven steps is the process of obtaining metadata, Step (8) is to read the actual data of file. The access process of the method adopted in this paper includes: (1) GetAttr (/usr/src/test/); (2) LookUp(hello.c); (3) GetAttr (hello.c) and (4) Read (hello.c). The first three steps is the process of obtaining metadata, Step (4) is to read the actual data of the file. According to the above derivation, we may get the general case of the access process of the two methods. When the number of file layers to be accessed is n, it takes 2n+2 times to access the actual metadata through the way of static sub-tree segmentation. The first 2n+1 times are to obtain metadata, and the time is to read the metadata; the method adopted in this paper is irrelevant with the number of file directory layers, and it takes only four times to read the metadata, with the first three times obtaining metadata and the last time reading metadata. Clearly, when n>1, the method adopted in this paper has a significant higher file access rate over the static sub-tree segmentation. B. Directory Object In a traditional file system, the directory file content and file metadata are stored separately, and file metadata may be obtained through several times of disk I/O. The imbedding of file metadata into directory files may increase the efficiency of access [10]. The directory object referred to in this paper is classified based on the binary code of directory path and according to the number of files, and includes all metadata of files. It is similar with the directory files in traditional file systems, but differs from traditional directory file that contains only file names and index numbers and obtains index number and then reads the metadata. For the directory object adopted in this paper, when the directory object is accessed, the metadata could be obtained simultaneously. Directory objects are uniformly managed by MDS, and each object is comprised of several fixed-number entities and file metadata entries. The file quantity of directory object is determined by bucket size, while metadata entry contains all metadata of the directory object properties. The structure of the directory object is shown as follows: Figure 3. Structure of Directory Object The metadata of directory object mainly includes the followings: DirectoryID: corresponding to the DirectoryID in DMS and used for examining the binary code information of directory. EntityID: indicating the ID of entity object inside the directory object. It is the only identifier of the entity inside the directory object, expressed by integer N, and adjustable according to bucket volume. For example, 16- digit identifier may support entities. EntityFlag: indicating the current status of entity object; Entry: indicating the entrance information of file metadata in file object; Name: indicating the name of file; FileID: indicating the globally uniform file ID of file objects; FileType: indicating the type of file metadata; FileFlag: indicating the current status of file metadata; FileAC: indicating the access authority of file metadata. Other basic properties of file metadata include mode, uid, gid, size, atime, ctime, mtime, etc. On one hand, the use of directory object changes the inefficient linear method of positioning file metadata through level-by-level traversal index in traditional file systems and significantly reduce the disk I/O times required by metadata reading; on the other hand, the use of directory object increases the efficiency of MDS. In traditional file system, in order to avoid large volume problem, MDS needs to partition the directory volume [11] apart from the storage of metadata. The partition of directory volume will be handed over to DMS for management. In this way, MDS could be responsible for metadata storage in a more focusing and efficient manner. VI. METADATA ACCESS A. Setting of Access Authority The paper classifies the access authority of a file or directory as self access authority and comprehensive authority, where self access authority refers to the own access authority of the file of the directory; that is, each file or directory has its own access authority, and is recorded in the corresponding metadata of MDS. While the comprehensive access authority is only available in directory as we define. The comprehensive access authority is the intersection of the self access authority of directory and other upper directory authority and is recorded in corresponding directory index in DMS. This classification method mainly solves two problems. First, it reduces the directory traversal times when access authority is determined. In traditional directory-based access control methods, when the access authority of a certain file or directory needs to be determined, the user s access authority could finally be determined after the traversal of all directories under the directory path. With the introduction of comprehensive access authority, when a new directory is to be created, the intersection of the self access authority of new directory and the comprehensive access authority of upper directory is taken, then the comprehensive access authority of the new directory is obtained and recorded in the corresponding directory indexes (the self access authority
7 JOURNAL OF SOFTWARE, VOL. 9, NO. 9, SEPTEMBER and comprehensive access authority at the first level of directory are the same). When a new directory is to be created, this method could be used recursively. In this way, when the access authority of a certain directory needs to be determined, it only needs to access the comprehensive access authority under the directory index, without the need of the traversal of all upper directories in the directory path. Second, it avoids the upgrading of a large amount of metadata resulted from the change to the access authority of directory. In a traditional file system, the access authority is saved in file metadata and distributed in each MDS, such as Lazy Hybrid method. When the access authority of a certain directory is changed, all metadata under this directory must be changed, which will result in the upgrading operation of a large amount of metadata. If the volume of file system is large, this will be a heavy task and cause the corresponding metadata compliance problems. This paper classifies the access authority into self access authority and comprehensive access authority. The file metadata of MDS only stores the self access authority, while the comprehensive access authority is stored in DMS. Therefore, when the access authority of directory is changed, it only needs to upgrade the comprehensive access authority property in corresponding directory index in DMS, without the need of changing the metadata information in MDS. The following figure illustrates the while construction process of access authority: access authority of the new directory new D, and obtain the comprehensive access authority of directory /root/app / newd as rwxr--r--. B. Metadata Positioning The metadata positioning operation mainly adopts the method of combining hashed and mapping tables. Hash algorithm mainly includes the three algorithms in Article III, which are established in DMS. The directory binary codes and the mapping table corresponding to MDS needs to be established in DMS according to the results from hash algorithm. The mapping table is classified into main mapping table and secondary mapping table, with the first one being the mapping established with the value from hash algorithm and MDS according to directory binary code and the latter one being the mapping established directly with the directory binary code and MDS. The MDS found through main mapping table is called the main MDS of a certain directory path, while the MDS found through the secondary mapping table is called the secondary MDS of a certain directory path. In default, the first lookup of metadata positioning is to look up the MDS entrance of the secondary mapping table and then, if there is no corresponding entrance, look up the MDS entrance of the main mapping table. The establishment of the main and secondary mapping tables is shown in Table 1 and Table 2. TABLE 1. MAIN MDS MAPPING TABLE Value IP address of MDS Figure 4. Construction of Directory Comprehensive Access Authority According to Linux file system rules, the access authority of the directory is expressed with 9 characters, with the left three characters indicating the authority of the owner, the middle three characters indicating the authority of users at the same group with the owner and the right three characters indicating the authority of other users. The characters r, w and x means read, write and execute respectively. Assume a user creates a new directory /root/app /newd under /root/app: (1) First, obtain the comprehensive access authority property of directory /root/app; assume it is rwxrwxrwx, and then the user has the authority to create a new directory under this directory. (2). Second, the user sets the self access authority of the new directory newd; assume it is rwxr--r--. (3) Last, take the intersection of the comprehensive access authority of upper directory /root/app and the self TABLE 2. SECONDARY MDS MAPPING TABLE Value IP address of MDS The advantages of classifying the mapping table into main mapping table and secondary mapping table include that the MDS load is balanced and that no certain MDS will become a hot access point. The main mapping table is established when a new directory is created. It is determined according to the hashed value of the binary code of directory path. According to the characteristic that the binary code is globally unique and will not change, the main MDS of any directory is unchanged, regardless of the change to directory property. Under
8 2450 JOURNAL OF SOFTWARE, VOL. 9, NO. 9, SEPTEMBER 2014 normal load circumstances, all metadata access will be responded by the main MDS. In addition, according to the processing capacity difference of each MDS, more entrances may be allocated to the main mapping table of the MDS with strong capacity, so that it could undertake more metadata tasks. For example, the processing capacity of the IP in Table 1 is twice the capacity of , and then the mapping entrance in the main mapping table is also twice the capacity of In practical situations, unbalanced load or even more extreme cases may be unavoidable. Therefore, we balance the load through the way of establishing mapping tables. The specific method is to set a counter and timer in the directory object of MDS, while the access frequency (counter/timer) indicates the access enthusiasm of directory object, then MDS transmit through the heartbeat mechanism the directory information and access frequency to DMS, which will select the MDS with lightest load as the secondary MDS of the directory according to the set access frequency threshold after receiving the information, and insert the mapping information into the secondary mapping table. If the access frequency of a certain directory in the secondary mapping table also reaches the threshold, then MDS will continue to add directory mapping relations from the secondary mapping table. When the metadata read entrance is to be selected, it is required to select the lightest entrance. In order to guarantee the conformity of metadata, the secondary table is only responsible for the read operation of metadata, while the write operation must be treated by the main mapping table. the same directory. The experiment uses 10 clients, 3 DMS nodes, 7 MDS nodes and 7 layers of directory tree for new files, with each directory containing 7 subdirectories and 50 files. The following figures show the experiment results of the two circumstances and the performance comparison with other metadata management methods. Figure 5 shows the file creation throughput rate of balanced access load, and Figure 6 shows the file creation throughput rate of concentrated access load. Figure 5. File Creation Throughput Rate of Balanced Access Load VII. SIMULATION AND IMPLEMENTATION In order to verify the effectiveness of DPCH proposed in this paper, the paper compares this method and several typical metadata management methods through experiment, which utilizes 10 computers with LINUX operation system (i5-3570k processor, 4GB memory and 500GB hard disk) and connected through gigabit Ethernet. The prototype system uses JAVA language and Iozine as performance testing tool. The experiment is consisted of five parts; i.e., file creation, file deletion, file reading, metadata distribution and metadata migration. A. File Creation The file creation method is to create a 0 word length file, because a 0 word length file does not requires the involvement of storage node server and could be completed by MDS independently, thus reducing the impact of other links on metadata processing capacity and enabling the test results to be more accurate. Then, the file creation efficiency will be summarized, with throughput rate as the performance evaluation index, i.e., the number of files created in a unit time. The experiment includes balanced access load and concentrated access load, with the former one referring to the file creation of Client under different directories and the latter one referring to the file creation of Client under Figure 6. File Creation Throughput Rate of Concentrated Access Load According to Figure 5, under balanced access load, the Sub-tree partition has the best throughput rate because this algorithm processes the sub-tree directories in the same MDS, thus enabling all metadata requests under this directory to be completed in the same MDS, reducing the disk I/O times of MDS and increasing the file creation rate. The FileHash algorithm has the poorest throughput rate, since this algorithm breaks the traditional directory hierarchy structure concept of file systems and distributes files through HASH evenly to each MDS, thus directly causing massive MDS access requests and causing the files under the same directory to be distributed in different MDS. This algorithm needs the traversal of several MDS, significantly increasing the disk I/O times for accessing MDS. LazyHybrid algorithm has improved throughput rate over the FileHash algorithm, but is basically a file-based hash algorithm. It only makes some improvements on file pre-treatment and Cache. The algorithm proposed in the paper has a larger partition granularity than that of the files, but is not completely the
9 JOURNAL OF SOFTWARE, VOL. 9, NO. 9, SEPTEMBER same with the Sub-tree partition. The creation process involves the directory binary coding and hash distribution function, thus the throughput rate under balanced access load is lower than that of Sub-tree partition but higher than that of FileHash algorithm and LazyHybrid algorithm. According to Figure 6, under concentrated access load, the Sub-tree partition has an obvious low throughput rate. This is because the files under the same directory will increase with the increase of client nodes, which will directly result in the load increase of MDS storing the directory, thus causing it to be the access hot point and finally the access bottleneck and reducing the file creation throughput rate. The other three algorithms adopt Hash distribution, and could still better process the access hot point problem under concentrated access load. The file creation throughput rate has only a minor difference with that under balanced access load, and the throughput curve also has only slight change with the increase of clients. It is particularly worth mentioning that the algorithm proposed in this paper takes directory code as hash unit, with partition granularity larger than that of files, but it is different from traditional directory structure. Through the bucket partition and the two mechanisms, i.e., main mapping table and secondary mapping table, this algorithm may enable the file metadata to be evenly distributed in each MDS, and the file creation throughput rate is better than that with FileHash algorithm and LazyHybrid algorithm. B. File Deletion The file deletion method is to delete the files based on the new files created above, and the file deletion throughput rate is also taken as the evaluation index. The experiment environment is the same with that of file creation operation above. The following figures show the file deletion throughput rate of the two circumstances and the performance comparison with other metadata management methods. Figure 8. File Deletion Throughput Rate of Concentrated Access Load According to Figure 7, under balanced access load, the experiment results are basically the same with that in previous description. The Sub-tree partition has the best file deletion throughput rate, followed by the algorithm adopted in this paper, LazyHybrid algorithm and FileHash algorithm in order. The reasons for the performance differences of these algorithms are the same with the previous description and will not be repeated here. The same conclusion could also be obtained from Figure 8. Under the Sub-tree partition, an access bottleneck will be formed with the increase of clients, resulting in the decrease of throughput rate. For the other algorithms adopting hash distribution, the throughput rate will be reduced significantly with the increase of clients. C. File Reading File reading mainly refers to the file reading operation from disk to memory. In file metadata operation, reading operation accounts for a considerable proportion, thus the file reading time is an important index to evaluate the performance of different algorithms. The experiment data is files randomly distributed under 1000 directories. The method adopted is to test the total reading times of each algorithm under the same file quantity and in the same reading order. The following figure shows the reading times of several algorithms. Figure 7. File Deletion Throughput Rate of Balanced Access Load Figure 9. Reading Times of Different MDS According to Figure 9, the algorithm adopted in this paper and the Sub-tree partition have the least reading time, followed by the LazyHybrid algorithm and
10 2452 JOURNAL OF SOFTWARE, VOL. 9, NO. 9, SEPTEMBER 2014 FileHash algorithm in order. The main reason for this difference is due to the different Cache hit rate. The basic idea of the algorithm adopted in this paper and the Subtree partition is to distribute metadata into different MDS according to the file location in directories. The only difference of the two algorithms is the processing mode. This partition may optimize the directory storage locality and reduce the overlapping of prefix directory in different MDS, thus increasing the Cache hit rate and reducing the reading times. Particularly, the algorithm adopted in the paper also introduces the concept of comprehensive access authority, which may further reduce the reading times enquired by directory traversal. LazyHybrid algorithm and FileHash algorithm determine the metadata distribution in MDS according to the hash value of fullpath file names, which results in the distribution of metadata under the same directory into different MDS and ignores the directory storage locality and prefix directory MDS overlapping, thus reducing the Cache hit rate and increasing the reading times. LazyHybrid algorithm also adopts the method of storing directory access authority, thus having less reading times than FileHash algorithm. D. Metadata Distribution Metadata distribution mainly refers to the distribution of metadata in each MDS. The experiment method is to store, in the same order, files in 10 MDS with same size. The figure below shows the metadata distribution in different MDS in different algorithms. Figure 10. Metadata Distribution in Different Algorithms According to Figure 10, LazyHybrid algorithm and FileHash algorithm have well balanced metadata distribution, with minor difference of metadata quantity in each MDS. This is because the two algorithms take files as the partition granularity and evenly distribute each metadata into each MDS through hash algorithm. It is followed by the algorithm proposed in the paper. Since the partition granularity is larger than files, the algorithm proposed in the paper may have less balanced metadata distribution in certain extreme circumstances compared with the previous two algorithms. The Sub-tree partition has the poorest metadata distribution, with obvious difference of metadata quantity in each MDS. E. Metadata Migration Metadata migration refers to the migration of metadata in each MDS when the user modifies directory properties (path, directory name, etc.). The experiment method is, based on the previous description, to draw 1-10% of all directories at random. The figure below shows the metadata migration after the modification of directory property in centralized algorithm. Figure 11. Metadata Migration after Modification of Directory Proportion According to the above figure, LazyHybrid algorithm and FileHash algorithm have the largest metadata migration amount. With the increase of directory modification amount, the metadata migration amount may reach 38.5%. This is because the two algorithms adopt hash distribution based on file full-path name. The modification of directory property results in the migration of a large amount of metadata in MDS. The algorithm proposed in the paper performs hash distribution after binary coding of path names. The modification of directory property will not affect the metadata distribution in MDS and has no metadata migration. The Sub-tree partition also only needs to modify a single directory property, and it involves no migration of metadata. F. Experiment Summary According to the simulation experiment results above, a comprehensive comparison on different metadata management performances is shown in the following Table 3. The evaluation adopts five rating points, with 1 as the poorest and 5 as the best. TABLE 3 PERFORMANCE COMPARISON OF DIFFERENT ALGORITHMS According to the table above, the metadata management method proposed in the paper shows good performance in all aspects, i.e., throughput rate, reading
11 JOURNAL OF SOFTWARE, VOL. 9, NO. 9, SEPTEMBER times, metadata distribution and metadata migration, and has the highest comprehensive points. VIII. CONCLUSION Based on the study on different metadata management methods, this paper proposes improvements for existing problems as well as the Directory Path Code Hash(DPCH). This method is to store directory and file metadata separately, perform hash distribution through binary coding of directory paths, and introduce the concepts of bucket partition, comprehensive access authority and main and secondary mapping tables, effectively solving the unbalanced metadata distribution and access hot point problems in Sub-tree partition and the excessive reading times and large metadata migration amount after directory property modification in LazyHybrid algorithm and FileHash algorithm. The experiment indicates that the method proposed in this paper significantly outweighs other algorithms in terms of throughput rate, metadata distribution, reading times, etc. ACKNOWLEDGMENT Fund project: the army logistics key scientific research program funded projects of PLA (BS211R099). REFERENCES [1] Roselli D, Lorch J, Anderson T. A comparison of file system workloads [C]// Proceedings of the 2000 USENIX Annual Technical Conference, San Diego. Boston: USENIX Association, 2000: [2] Grorge A, Garcia J, Kim K. Distributed parallel processing techniques for adaptive sonar beamforming[j]. Journal of Computation Acoustics, 2002, 10(1):1-23. [3] Weil s a, Pollack K T, Brandt S A, et al. Dynamic metadata management for petabyte-scale file systems[c]. ACM/IEEE Conference on Supercomputing, DC, USA, 2004:4. [4] National Information Standards Organization. Understanding Metadata. [ ]. [5] Gongye Zhou, Qiuju Lan, Jincai Chen. A dynamic metadata equipotent subtree partition policy for mass storage system //Proc of the Japan-China Joint Workshop on Frontier of Computer Science and Technology [6] Walter A, Francesco G, Marco M. Indexing and retrieval of multimedia metadata on a secure DHT. Informatica, 2009,33(1): [7] Popek G J, Rudisn G, Stoughton A, et al. Detection of mutual inconsistency in distributed system[j]. IEEE Transactions on software engineering, 1986,12(11): [8] Corbett P F, Feitelso D G. The Vesta Parallel File System[J]. Transactions on Computer Systems, 1996, 14(3): [9] Brandt S A, Lan Xue, Miller E L, et al. Efficient Metadata Management in Large Distributed File Systems[C]//Proceedings of the 20th IEEE NASA Goddard Conference on Mass Storage Systems and Technologies. [S. 1.]: IEEE Press, 2003: [10] Ganger GR, Kaashoek MF. Embedded inodes and explicit groupings: Exploiting disk bandwidth for small files. In: Proc. Of the 1997 USENIX Annual Technical Conf. Anaheim: USENIX, [11] Litwin W, Neimat MA, Schneider DA. LH A scalable, distributed data structure. ACM Trans. On Database Systems, 1996,21(4): [12] Tong Yang. Mass Data Analysis and Forecasting Based on Cloud Computing. Journal of Software, Vol. 7, No. 10, 2012: [13] Xindong You. ARAS-M: Automatic Resource Allocation Strategy based on Market Mechanism in Cloud Computing. Journal of Computers, Vol. 6, No. 7, 2011: Hui Cai, born in 1983, Ph. D. His research orientations are cloud and P2P computing. Shenlin Li, born in 1964, professor, Ph.D. His research interests include Logistic Informationization and cloud computing. Zhaoxia Wang, born in 1973, Ph.D. Her research direction includes cloud and grid computing. Xingchen Li, born in 1986, Ph.D. His main research interests are data processing and intelligent interaction of the IOT. Lichuan Huang, born in 1985, M.S. His main research interests are oil gas station management, and oil Informationization.
Dynamic Metadata Management for Petabyte-scale File Systems
 Dynamic Metadata Management for Petabyte-scale File Systems Sage Weil Kristal T. Pollack, Scott A. Brandt, Ethan L. Miller UC Santa Cruz November 1, 2006 Presented by Jae Geuk, Kim System Overview Petabytes
Dynamic Metadata Management for Petabyte-scale File Systems Sage Weil Kristal T. Pollack, Scott A. Brandt, Ethan L. Miller UC Santa Cruz November 1, 2006 Presented by Jae Geuk, Kim System Overview Petabytes
Efficient Metadata Management in Cloud Computing
 Send Orders for Reprints to reprints@benthamscience.ae The Open Cybernetics & Systemics Journal, 2015, 9, 1485-1489 1485 Efficient Metadata Management in Cloud Computing Open Access Yu Shuchun 1,* and
Send Orders for Reprints to reprints@benthamscience.ae The Open Cybernetics & Systemics Journal, 2015, 9, 1485-1489 1485 Efficient Metadata Management in Cloud Computing Open Access Yu Shuchun 1,* and
Efficient Metadata Management in Large Distributed Storage Systems
 Efficient Management in Large Distributed Storage Systems Scott A. Brandt scott@cs.ucsc.edu Ethan L. Miller elm@cs.ucsc.edu Darrell D. E. Long darrell@cs.ucsc.edu Storage Systems Research Center University
Efficient Management in Large Distributed Storage Systems Scott A. Brandt scott@cs.ucsc.edu Ethan L. Miller elm@cs.ucsc.edu Darrell D. E. Long darrell@cs.ucsc.edu Storage Systems Research Center University
PPMS: A Peer to Peer Metadata Management Strategy for Distributed File Systems
 PPMS: A Peer to Peer Metadata Management Strategy for Distributed File Systems Di Yang, Weigang Wu, Zhansong Li, Jiongyu Yu, and Yong Li Department of Computer Science, Sun Yat-sen University Guangzhou
PPMS: A Peer to Peer Metadata Management Strategy for Distributed File Systems Di Yang, Weigang Wu, Zhansong Li, Jiongyu Yu, and Yong Li Department of Computer Science, Sun Yat-sen University Guangzhou
A Hybrid Scheme for Object Allocation in a Distributed Object-Storage System
 A Hybrid Scheme for Object Allocation in a Distributed Object-Storage System Fang Wang **, Shunda Zhang, Dan Feng, Hong Jiang, Lingfang Zeng, and Song Lv Key Laboratory of Data Storage System, Ministry
A Hybrid Scheme for Object Allocation in a Distributed Object-Storage System Fang Wang **, Shunda Zhang, Dan Feng, Hong Jiang, Lingfang Zeng, and Song Lv Key Laboratory of Data Storage System, Ministry
Research Article A Two-Level Cache for Distributed Information Retrieval in Search Engines
 The Scientific World Journal Volume 2013, Article ID 596724, 6 pages http://dx.doi.org/10.1155/2013/596724 Research Article A Two-Level Cache for Distributed Information Retrieval in Search Engines Weizhe
The Scientific World Journal Volume 2013, Article ID 596724, 6 pages http://dx.doi.org/10.1155/2013/596724 Research Article A Two-Level Cache for Distributed Information Retrieval in Search Engines Weizhe
New research on Key Technologies of unstructured data cloud storage
 2017 International Conference on Computing, Communications and Automation(I3CA 2017) New research on Key Technologies of unstructured data cloud storage Songqi Peng, Rengkui Liua, *, Futian Wang State
2017 International Conference on Computing, Communications and Automation(I3CA 2017) New research on Key Technologies of unstructured data cloud storage Songqi Peng, Rengkui Liua, *, Futian Wang State
Preliminary Research on Distributed Cluster Monitoring of G/S Model
 Available online at www.sciencedirect.com Physics Procedia 25 (2012 ) 860 867 2012 International Conference on Solid State Devices and Materials Science Preliminary Research on Distributed Cluster Monitoring
Available online at www.sciencedirect.com Physics Procedia 25 (2012 ) 860 867 2012 International Conference on Solid State Devices and Materials Science Preliminary Research on Distributed Cluster Monitoring
Ceph: A Scalable, High-Performance Distributed File System
 Ceph: A Scalable, High-Performance Distributed File System S. A. Weil, S. A. Brandt, E. L. Miller, D. D. E. Long Presented by Philip Snowberger Department of Computer Science and Engineering University
Ceph: A Scalable, High-Performance Distributed File System S. A. Weil, S. A. Brandt, E. L. Miller, D. D. E. Long Presented by Philip Snowberger Department of Computer Science and Engineering University
Design and Implementation of High-Speed Real-Time Data Acquisition and Processing System based on FPGA
 2nd International Conference on Social Science and Technology Education (ICSSTE 2016) Design and Implementation of High-Speed Real-Time Data Acquisition and Processing System based on FPGA Guojuan Zhou
2nd International Conference on Social Science and Technology Education (ICSSTE 2016) Design and Implementation of High-Speed Real-Time Data Acquisition and Processing System based on FPGA Guojuan Zhou
An Oracle White Paper September Oracle Utilities Meter Data Management Demonstrates Extreme Performance on Oracle Exadata/Exalogic
 An Oracle White Paper September 2011 Oracle Utilities Meter Data Management 2.0.1 Demonstrates Extreme Performance on Oracle Exadata/Exalogic Introduction New utilities technologies are bringing with them
An Oracle White Paper September 2011 Oracle Utilities Meter Data Management 2.0.1 Demonstrates Extreme Performance on Oracle Exadata/Exalogic Introduction New utilities technologies are bringing with them
A Hybrid Approach to CAM-Based Longest Prefix Matching for IP Route Lookup
 A Hybrid Approach to CAM-Based Longest Prefix Matching for IP Route Lookup Yan Sun and Min Sik Kim School of Electrical Engineering and Computer Science Washington State University Pullman, Washington
A Hybrid Approach to CAM-Based Longest Prefix Matching for IP Route Lookup Yan Sun and Min Sik Kim School of Electrical Engineering and Computer Science Washington State University Pullman, Washington
The Improvement and Implementation of the High Concurrency Web Server Based on Nginx Baiqi Wang1, a, Jiayue Liu2,b and Zhiyi Fang 3,*
 Computing, Performance and Communication systems (2016) 1: 1-7 Clausius Scientific Press, Canada The Improvement and Implementation of the High Concurrency Web Server Based on Nginx Baiqi Wang1, a, Jiayue
Computing, Performance and Communication systems (2016) 1: 1-7 Clausius Scientific Press, Canada The Improvement and Implementation of the High Concurrency Web Server Based on Nginx Baiqi Wang1, a, Jiayue
ZigBee Routing Algorithm Based on Energy Optimization
 Sensors & Transducers 2013 by IFSA http://www.sensorsportal.com ZigBee Routing Algorithm Based on Energy Optimization Wangang Wang, Yong Peng, Yongyu Peng Chongqing City Management College, No. 151 Daxuecheng
Sensors & Transducers 2013 by IFSA http://www.sensorsportal.com ZigBee Routing Algorithm Based on Energy Optimization Wangang Wang, Yong Peng, Yongyu Peng Chongqing City Management College, No. 151 Daxuecheng
A Data Classification Algorithm of Internet of Things Based on Neural Network
 A Data Classification Algorithm of Internet of Things Based on Neural Network https://doi.org/10.3991/ijoe.v13i09.7587 Zhenjun Li Hunan Radio and TV University, Hunan, China 278060389@qq.com Abstract To
A Data Classification Algorithm of Internet of Things Based on Neural Network https://doi.org/10.3991/ijoe.v13i09.7587 Zhenjun Li Hunan Radio and TV University, Hunan, China 278060389@qq.com Abstract To
CLIP: A Compact, Load-balancing Index Placement Function
 CLIP: A Compact, Load-balancing Index Placement Function Michael McThrow Storage Systems Research Center University of California, Santa Cruz Abstract Existing file searching tools do not have the performance
CLIP: A Compact, Load-balancing Index Placement Function Michael McThrow Storage Systems Research Center University of California, Santa Cruz Abstract Existing file searching tools do not have the performance
File Systems. Chapter 11, 13 OSPP
 File Systems Chapter 11, 13 OSPP What is a File? What is a Directory? Goals of File System Performance Controlled Sharing Convenience: naming Reliability File System Workload File sizes Are most files
File Systems Chapter 11, 13 OSPP What is a File? What is a Directory? Goals of File System Performance Controlled Sharing Convenience: naming Reliability File System Workload File sizes Are most files
A Finite State Mobile Agent Computation Model
 A Finite State Mobile Agent Computation Model Yong Liu, Congfu Xu, Zhaohui Wu, Weidong Chen, and Yunhe Pan College of Computer Science, Zhejiang University Hangzhou 310027, PR China Abstract In this paper,
A Finite State Mobile Agent Computation Model Yong Liu, Congfu Xu, Zhaohui Wu, Weidong Chen, and Yunhe Pan College of Computer Science, Zhejiang University Hangzhou 310027, PR China Abstract In this paper,
Load Balancing Algorithm over a Distributed Cloud Network
 Load Balancing Algorithm over a Distributed Cloud Network Priyank Singhal Student, Computer Department Sumiran Shah Student, Computer Department Pranit Kalantri Student, Electronics Department Abstract
Load Balancing Algorithm over a Distributed Cloud Network Priyank Singhal Student, Computer Department Sumiran Shah Student, Computer Department Pranit Kalantri Student, Electronics Department Abstract
Main Points. File layout Directory layout
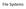 File Systems Main Points File layout Directory layout File System Design Constraints For small files: Small blocks for storage efficiency Files used together should be stored together For large files:
File Systems Main Points File layout Directory layout File System Design Constraints For small files: Small blocks for storage efficiency Files used together should be stored together For large files:
Outline. Challenges of DFS CEPH A SCALABLE HIGH PERFORMANCE DFS DATA DISTRIBUTION AND MANAGEMENT IN DISTRIBUTED FILE SYSTEM 11/16/2010
 Outline DATA DISTRIBUTION AND MANAGEMENT IN DISTRIBUTED FILE SYSTEM Erin Brady and Shantonu Hossain What are the challenges of Distributed File System (DFS) Ceph: A scalable high performance DFS Data Distribution
Outline DATA DISTRIBUTION AND MANAGEMENT IN DISTRIBUTED FILE SYSTEM Erin Brady and Shantonu Hossain What are the challenges of Distributed File System (DFS) Ceph: A scalable high performance DFS Data Distribution
Research on Approach of Equipment Status and Operation Information Acquisition Based on Equipment Control Bus
 Research on Approach of Equipment Status and Operation Information Acquisition Based on Equipment Control Bus Xu Li a, *, Chen Meng, Huixia Jiang, Cheng Wang Army Engineering University, Shijiazhuang 050003,
Research on Approach of Equipment Status and Operation Information Acquisition Based on Equipment Control Bus Xu Li a, *, Chen Meng, Huixia Jiang, Cheng Wang Army Engineering University, Shijiazhuang 050003,
Lustre A Platform for Intelligent Scale-Out Storage
 Lustre A Platform for Intelligent Scale-Out Storage Rumi Zahir, rumi. May 2003 rumi.zahir@intel.com Agenda Problem Statement Trends & Current Data Center Storage Architectures The Lustre File System Project
Lustre A Platform for Intelligent Scale-Out Storage Rumi Zahir, rumi. May 2003 rumi.zahir@intel.com Agenda Problem Statement Trends & Current Data Center Storage Architectures The Lustre File System Project
Database Design on Construction Project Cost System Nannan Zhang1,a, Wenfeng Song2,b
 3rd International Conference on Materials Engineering, Manufacturing Technology and Control (ICMEMTC 2016) Database Design on Construction Project Cost System Nannan Zhang1,a, Wenfeng Song2,b 1 School
3rd International Conference on Materials Engineering, Manufacturing Technology and Control (ICMEMTC 2016) Database Design on Construction Project Cost System Nannan Zhang1,a, Wenfeng Song2,b 1 School
Chapter 11: File System Implementation. Objectives
 Chapter 11: File System Implementation Objectives To describe the details of implementing local file systems and directory structures To describe the implementation of remote file systems To discuss block
Chapter 11: File System Implementation Objectives To describe the details of implementing local file systems and directory structures To describe the implementation of remote file systems To discuss block
Ceph: A Scalable, High-Performance Distributed File System PRESENTED BY, NITHIN NAGARAJ KASHYAP
 Ceph: A Scalable, High-Performance Distributed File System PRESENTED BY, NITHIN NAGARAJ KASHYAP Outline Introduction. System Overview. Distributed Object Storage. Problem Statements. What is Ceph? Unified
Ceph: A Scalable, High-Performance Distributed File System PRESENTED BY, NITHIN NAGARAJ KASHYAP Outline Introduction. System Overview. Distributed Object Storage. Problem Statements. What is Ceph? Unified
EARM: An Efficient and Adaptive File Replication with Consistency Maintenance in P2P Systems.
 : An Efficient and Adaptive File Replication with Consistency Maintenance in P2P Systems. 1 K.V.K.Chaitanya, 2 Smt. S.Vasundra, M,Tech., (Ph.D), 1 M.Tech (Computer Science), 2 Associate Professor, Department
: An Efficient and Adaptive File Replication with Consistency Maintenance in P2P Systems. 1 K.V.K.Chaitanya, 2 Smt. S.Vasundra, M,Tech., (Ph.D), 1 M.Tech (Computer Science), 2 Associate Professor, Department
The Construction of Open Source Cloud Storage System for Digital Resources
 2017 3rd International Conference on Electronic Information Technology and Intellectualization (ICEITI 2017) ISBN: 978-1-60595-512-4 The Construction of Open Source Cloud Storage System for Digital Resources
2017 3rd International Conference on Electronic Information Technology and Intellectualization (ICEITI 2017) ISBN: 978-1-60595-512-4 The Construction of Open Source Cloud Storage System for Digital Resources
The Design of Distributed File System Based on HDFS Yannan Wang 1, a, Shudong Zhang 2, b, Hui Liu 3, c
 Applied Mechanics and Materials Online: 2013-09-27 ISSN: 1662-7482, Vols. 423-426, pp 2733-2736 doi:10.4028/www.scientific.net/amm.423-426.2733 2013 Trans Tech Publications, Switzerland The Design of Distributed
Applied Mechanics and Materials Online: 2013-09-27 ISSN: 1662-7482, Vols. 423-426, pp 2733-2736 doi:10.4028/www.scientific.net/amm.423-426.2733 2013 Trans Tech Publications, Switzerland The Design of Distributed
Pantheon: Exascale File System Search for Scientific Computing
 : Exascale File System Search for Scientific Computing Joseph L. Naps, Mohamed F. Mokbel, David H. C. Du Department of Computer Science and Engineering, University of Minnesota, Minneapolis, MN, USA {naps,
: Exascale File System Search for Scientific Computing Joseph L. Naps, Mohamed F. Mokbel, David H. C. Du Department of Computer Science and Engineering, University of Minnesota, Minneapolis, MN, USA {naps,
File System Internals. Jin-Soo Kim Computer Systems Laboratory Sungkyunkwan University
 File System Internals Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics File system implementation File descriptor table, File table
File System Internals Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics File system implementation File descriptor table, File table
Research and Implementation of Server Load Balancing Strategy in Service System
 Journal of Electronics and Information Science (2018) 3: 16-21 Clausius Scientific Press, Canada Research and Implementation of Server Load Balancing Strategy in Service System Yunpeng Zhang a, Liwei Liu
Journal of Electronics and Information Science (2018) 3: 16-21 Clausius Scientific Press, Canada Research and Implementation of Server Load Balancing Strategy in Service System Yunpeng Zhang a, Liwei Liu
CLOUD-SCALE FILE SYSTEMS
 Data Management in the Cloud CLOUD-SCALE FILE SYSTEMS 92 Google File System (GFS) Designing a file system for the Cloud design assumptions design choices Architecture GFS Master GFS Chunkservers GFS Clients
Data Management in the Cloud CLOUD-SCALE FILE SYSTEMS 92 Google File System (GFS) Designing a file system for the Cloud design assumptions design choices Architecture GFS Master GFS Chunkservers GFS Clients
File System Internals. Jin-Soo Kim Computer Systems Laboratory Sungkyunkwan University
 File System Internals Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics File system implementation File descriptor table, File table
File System Internals Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics File system implementation File descriptor table, File table
Baoping Wang School of software, Nanyang Normal University, Nanyang , Henan, China
 doi:10.21311/001.39.7.41 Implementation of Cache Schedule Strategy in Solid-state Disk Baoping Wang School of software, Nanyang Normal University, Nanyang 473061, Henan, China Chao Yin* School of Information
doi:10.21311/001.39.7.41 Implementation of Cache Schedule Strategy in Solid-state Disk Baoping Wang School of software, Nanyang Normal University, Nanyang 473061, Henan, China Chao Yin* School of Information
FDDI-M: A SCHEME TO DOUBLE FDDI S ABILITY OF SUPPORTING SYNCHRONOUS TRAFFIC
 FDDI-M: A SCHEME TO DOUBLE FDDI S ABILITY OF SUPPORTING SYNCHRONOUS TRAFFIC Kang G. Shin Real-time Computing Laboratory EECS Department The University of Michigan Ann Arbor, Michigan 48109 &in Zheng Mitsubishi
FDDI-M: A SCHEME TO DOUBLE FDDI S ABILITY OF SUPPORTING SYNCHRONOUS TRAFFIC Kang G. Shin Real-time Computing Laboratory EECS Department The University of Michigan Ann Arbor, Michigan 48109 &in Zheng Mitsubishi
Design and Implementation of a Random Access File System for NVRAM
 This article has been accepted and published on J-STAGE in advance of copyediting. Content is final as presented. IEICE Electronics Express, Vol.* No.*,*-* Design and Implementation of a Random Access
This article has been accepted and published on J-STAGE in advance of copyediting. Content is final as presented. IEICE Electronics Express, Vol.* No.*,*-* Design and Implementation of a Random Access
The Load Balancing Research of SDN based on Ant Colony Algorithm with Job Classification Wucai Lin1,a, Lichen Zhang2,b
 2nd Workshop on Advanced Research and Technology in Industry Applications (WARTIA 2016) The Load Balancing Research of SDN based on Ant Colony Algorithm with Job Classification Wucai Lin1,a, Lichen Zhang2,b
2nd Workshop on Advanced Research and Technology in Industry Applications (WARTIA 2016) The Load Balancing Research of SDN based on Ant Colony Algorithm with Job Classification Wucai Lin1,a, Lichen Zhang2,b
File System Case Studies. Jin-Soo Kim Computer Systems Laboratory Sungkyunkwan University
 File System Case Studies Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics The Original UNIX File System FFS Ext2 FAT 2 UNIX FS (1)
File System Case Studies Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics The Original UNIX File System FFS Ext2 FAT 2 UNIX FS (1)
Spyglass: Fast, Scalable Metadata Search for Large-Scale Storage Systems
 Spyglass: Fast, Scalable Metadata Search for Large-Scale Storage Systems Andrew W Leung Ethan L Miller University of California, Santa Cruz Minglong Shao Timothy Bisson Shankar Pasupathy NetApp 7th USENIX
Spyglass: Fast, Scalable Metadata Search for Large-Scale Storage Systems Andrew W Leung Ethan L Miller University of California, Santa Cruz Minglong Shao Timothy Bisson Shankar Pasupathy NetApp 7th USENIX
Computer Systems Laboratory Sungkyunkwan University
 File System Internals Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics File system implementation File descriptor table, File table
File System Internals Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics File system implementation File descriptor table, File table
Storage Hierarchy Management for Scientific Computing
 Storage Hierarchy Management for Scientific Computing by Ethan Leo Miller Sc. B. (Brown University) 1987 M.S. (University of California at Berkeley) 1990 A dissertation submitted in partial satisfaction
Storage Hierarchy Management for Scientific Computing by Ethan Leo Miller Sc. B. (Brown University) 1987 M.S. (University of California at Berkeley) 1990 A dissertation submitted in partial satisfaction
Database System Concepts, 6 th Ed. Silberschatz, Korth and Sudarshan See for conditions on re-use
 Chapter 11: Indexing and Hashing Database System Concepts, 6 th Ed. See www.db-book.com for conditions on re-use Chapter 12: Indexing and Hashing Basic Concepts Ordered Indices B + -Tree Index Files Static
Chapter 11: Indexing and Hashing Database System Concepts, 6 th Ed. See www.db-book.com for conditions on re-use Chapter 12: Indexing and Hashing Basic Concepts Ordered Indices B + -Tree Index Files Static
Chapter 6 Storage Management File-System Interface 11.1
 Chapter 6 Storage Management File-System Interface 11.1 Chapter 6: File-System Interface File Concept Access Methods Disk and Directory Structure File-System Mounting File Sharing Protection 11.2 Objectives
Chapter 6 Storage Management File-System Interface 11.1 Chapter 6: File-System Interface File Concept Access Methods Disk and Directory Structure File-System Mounting File Sharing Protection 11.2 Objectives
A Study on Load Balancing Techniques for Task Allocation in Big Data Processing* Jin Xiaohong1,a, Li Hui1, b, Liu Yanjun1, c, Fan Yanfang1, d
 International Forum on Mechanical, Control and Automation IFMCA 2016 A Study on Load Balancing Techniques for Task Allocation in Big Data Processing* Jin Xiaohong1,a, Li Hui1, b, Liu Yanjun1, c, Fan Yanfang1,
International Forum on Mechanical, Control and Automation IFMCA 2016 A Study on Load Balancing Techniques for Task Allocation in Big Data Processing* Jin Xiaohong1,a, Li Hui1, b, Liu Yanjun1, c, Fan Yanfang1,
RETRACTED ARTICLE. Web-Based Data Mining in System Design and Implementation. Open Access. Jianhu Gong 1* and Jianzhi Gong 2
 Send Orders for Reprints to reprints@benthamscience.ae The Open Automation and Control Systems Journal, 2014, 6, 1907-1911 1907 Web-Based Data Mining in System Design and Implementation Open Access Jianhu
Send Orders for Reprints to reprints@benthamscience.ae The Open Automation and Control Systems Journal, 2014, 6, 1907-1911 1907 Web-Based Data Mining in System Design and Implementation Open Access Jianhu
Location Database Clustering to Achieve Location Management Time Cost Reduction in A Mobile Computing System
 Location Database Clustering to Achieve Location Management Time Cost Reduction in A Mobile Computing ystem Chen Jixiong, Li Guohui, Xu Huajie, Cai Xia*, Yang Bing chool of Computer cience & Technology,
Location Database Clustering to Achieve Location Management Time Cost Reduction in A Mobile Computing ystem Chen Jixiong, Li Guohui, Xu Huajie, Cai Xia*, Yang Bing chool of Computer cience & Technology,
Chapter 12: Indexing and Hashing. Basic Concepts
 Chapter 12: Indexing and Hashing! Basic Concepts! Ordered Indices! B+-Tree Index Files! B-Tree Index Files! Static Hashing! Dynamic Hashing! Comparison of Ordered Indexing and Hashing! Index Definition
Chapter 12: Indexing and Hashing! Basic Concepts! Ordered Indices! B+-Tree Index Files! B-Tree Index Files! Static Hashing! Dynamic Hashing! Comparison of Ordered Indexing and Hashing! Index Definition
Chapter 11: Indexing and Hashing" Chapter 11: Indexing and Hashing"
 Chapter 11: Indexing and Hashing" Database System Concepts, 6 th Ed.! Silberschatz, Korth and Sudarshan See www.db-book.com for conditions on re-use " Chapter 11: Indexing and Hashing" Basic Concepts!
Chapter 11: Indexing and Hashing" Database System Concepts, 6 th Ed.! Silberschatz, Korth and Sudarshan See www.db-book.com for conditions on re-use " Chapter 11: Indexing and Hashing" Basic Concepts!
Case study: ext2 FS 1
 Case study: ext2 FS 1 The ext2 file system Second Extended Filesystem The main Linux FS before ext3 Evolved from Minix filesystem (via Extended Filesystem ) Features Block size (1024, 2048, and 4096) configured
Case study: ext2 FS 1 The ext2 file system Second Extended Filesystem The main Linux FS before ext3 Evolved from Minix filesystem (via Extended Filesystem ) Features Block size (1024, 2048, and 4096) configured
A Low-Overhead Hybrid Routing Algorithm for ZigBee Networks. Zhi Ren, Lihua Tian, Jianling Cao, Jibi Li, Zilong Zhang
 A Low-Overhead Hybrid Routing Algorithm for ZigBee Networks Zhi Ren, Lihua Tian, Jianling Cao, Jibi Li, Zilong Zhang Chongqing Key Lab of Mobile Communications Technology, Chongqing University of Posts
A Low-Overhead Hybrid Routing Algorithm for ZigBee Networks Zhi Ren, Lihua Tian, Jianling Cao, Jibi Li, Zilong Zhang Chongqing Key Lab of Mobile Communications Technology, Chongqing University of Posts
Mobile Cloud Multimedia Services Using Enhance Blind Online Scheduling Algorithm
 Mobile Cloud Multimedia Services Using Enhance Blind Online Scheduling Algorithm Saiyad Sharik Kaji Prof.M.B.Chandak WCOEM, Nagpur RBCOE. Nagpur Department of Computer Science, Nagpur University, Nagpur-441111
Mobile Cloud Multimedia Services Using Enhance Blind Online Scheduling Algorithm Saiyad Sharik Kaji Prof.M.B.Chandak WCOEM, Nagpur RBCOE. Nagpur Department of Computer Science, Nagpur University, Nagpur-441111
Study on A Recommendation Algorithm of Crossing Ranking in E- commerce
 International Journal of u-and e-service, Science and Technology, pp.53-62 http://dx.doi.org/10.14257/ijunnesst2014.7.4.6 Study on A Recommendation Algorithm of Crossing Ranking in E- commerce Duan Xueying
International Journal of u-and e-service, Science and Technology, pp.53-62 http://dx.doi.org/10.14257/ijunnesst2014.7.4.6 Study on A Recommendation Algorithm of Crossing Ranking in E- commerce Duan Xueying
Efficient Algorithm for Frequent Itemset Generation in Big Data
 Efficient Algorithm for Frequent Itemset Generation in Big Data Anbumalar Smilin V, Siddique Ibrahim S.P, Dr.M.Sivabalakrishnan P.G. Student, Department of Computer Science and Engineering, Kumaraguru
Efficient Algorithm for Frequent Itemset Generation in Big Data Anbumalar Smilin V, Siddique Ibrahim S.P, Dr.M.Sivabalakrishnan P.G. Student, Department of Computer Science and Engineering, Kumaraguru
Caching for NASD. Department of Computer Science University of Wisconsin-Madison Madison, WI 53706
 Caching for NASD Chen Zhou Wanli Yang {chenzhou, wanli}@cs.wisc.edu Department of Computer Science University of Wisconsin-Madison Madison, WI 53706 Abstract NASD is a totally new storage system architecture,
Caching for NASD Chen Zhou Wanli Yang {chenzhou, wanli}@cs.wisc.edu Department of Computer Science University of Wisconsin-Madison Madison, WI 53706 Abstract NASD is a totally new storage system architecture,
Construction Scheme for Cloud Platform of NSFC Information System
 , pp.200-204 http://dx.doi.org/10.14257/astl.2016.138.40 Construction Scheme for Cloud Platform of NSFC Information System Jianjun Li 1, Jin Wang 1, Yuhui Zheng 2 1 Information Center, National Natural
, pp.200-204 http://dx.doi.org/10.14257/astl.2016.138.40 Construction Scheme for Cloud Platform of NSFC Information System Jianjun Li 1, Jin Wang 1, Yuhui Zheng 2 1 Information Center, National Natural
Directory Structure and File Allocation Methods
 ISSN:0975-9646 Mandeep Kaur et al, / (IJCSIT) International Journal of Computer Science and Information Technologies, Vol. 7 (2), 2016, 577-582 Directory Structure and ile Allocation Methods Mandeep Kaur,
ISSN:0975-9646 Mandeep Kaur et al, / (IJCSIT) International Journal of Computer Science and Information Technologies, Vol. 7 (2), 2016, 577-582 Directory Structure and ile Allocation Methods Mandeep Kaur,
CS-580K/480K Advanced Topics in Cloud Computing. Object Storage
 CS-580K/480K Advanced Topics in Cloud Computing Object Storage 1 When we use object storage When we check Facebook, twitter Gmail Docs on DropBox Check share point Take pictures with Instagram 2 Object
CS-580K/480K Advanced Topics in Cloud Computing Object Storage 1 When we use object storage When we check Facebook, twitter Gmail Docs on DropBox Check share point Take pictures with Instagram 2 Object
Chapter 12: Indexing and Hashing
 Chapter 12: Indexing and Hashing Basic Concepts Ordered Indices B+-Tree Index Files B-Tree Index Files Static Hashing Dynamic Hashing Comparison of Ordered Indexing and Hashing Index Definition in SQL
Chapter 12: Indexing and Hashing Basic Concepts Ordered Indices B+-Tree Index Files B-Tree Index Files Static Hashing Dynamic Hashing Comparison of Ordered Indexing and Hashing Index Definition in SQL
Enhancing Downloading Time By Using Content Distribution Algorithm
 RESEARCH ARTICLE OPEN ACCESS Enhancing Downloading Time By Using Content Distribution Algorithm VILSA V S Department of Computer Science and Technology TKM Institute of Technology, Kollam, Kerala Mailid-vilsavijay@gmail.com
RESEARCH ARTICLE OPEN ACCESS Enhancing Downloading Time By Using Content Distribution Algorithm VILSA V S Department of Computer Science and Technology TKM Institute of Technology, Kollam, Kerala Mailid-vilsavijay@gmail.com
B.H.GARDI COLLEGE OF ENGINEERING & TECHNOLOGY (MCA Dept.) Parallel Database Database Management System - 2
 Introduction :- Today single CPU based architecture is not capable enough for the modern database that are required to handle more demanding and complex requirements of the users, for example, high performance,
Introduction :- Today single CPU based architecture is not capable enough for the modern database that are required to handle more demanding and complex requirements of the users, for example, high performance,
File System Case Studies. Jin-Soo Kim Computer Systems Laboratory Sungkyunkwan University
 File System Case Studies Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics The Original UNIX File System FFS Ext2 FAT 2 UNIX FS (1)
File System Case Studies Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Today s Topics The Original UNIX File System FFS Ext2 FAT 2 UNIX FS (1)
A New Logging-based IP Traceback Approach using Data Mining Techniques
 using Data Mining Techniques Internet & Multimedia Engineering, Konkuk University, Seoul, Republic of Korea hsriverv@gmail.com, kimsr@konuk.ac.kr Abstract IP Traceback is a way to search for sources of
using Data Mining Techniques Internet & Multimedia Engineering, Konkuk University, Seoul, Republic of Korea hsriverv@gmail.com, kimsr@konuk.ac.kr Abstract IP Traceback is a way to search for sources of
A priority based dynamic bandwidth scheduling in SDN networks 1
 Acta Technica 62 No. 2A/2017, 445 454 c 2017 Institute of Thermomechanics CAS, v.v.i. A priority based dynamic bandwidth scheduling in SDN networks 1 Zun Wang 2 Abstract. In order to solve the problems
Acta Technica 62 No. 2A/2017, 445 454 c 2017 Institute of Thermomechanics CAS, v.v.i. A priority based dynamic bandwidth scheduling in SDN networks 1 Zun Wang 2 Abstract. In order to solve the problems
Australian Journal of Basic and Applied Sciences. Comparative Investigation On Mygrant Wlan Performance Analysis With And Without Load Balancer
 AENSI Journals Australian Journal of Basic and Applied Sciences ISSN:1991-8178 Journal home page: www.ajbasweb.com Comparative Investigation On Mygrant Wlan Performance Analysis With And Without Load Balancer
AENSI Journals Australian Journal of Basic and Applied Sciences ISSN:1991-8178 Journal home page: www.ajbasweb.com Comparative Investigation On Mygrant Wlan Performance Analysis With And Without Load Balancer
Systems Infrastructure for Data Science. Web Science Group Uni Freiburg WS 2014/15
 Systems Infrastructure for Data Science Web Science Group Uni Freiburg WS 2014/15 Lecture II: Indexing Part I of this course Indexing 3 Database File Organization and Indexing Remember: Database tables
Systems Infrastructure for Data Science Web Science Group Uni Freiburg WS 2014/15 Lecture II: Indexing Part I of this course Indexing 3 Database File Organization and Indexing Remember: Database tables
The Design and Implementation of Disaster Recovery in Dual-active Cloud Center
 International Conference on Information Sciences, Machinery, Materials and Energy (ICISMME 2015) The Design and Implementation of Disaster Recovery in Dual-active Cloud Center Xiao Chen 1, a, Longjun Zhang
International Conference on Information Sciences, Machinery, Materials and Energy (ICISMME 2015) The Design and Implementation of Disaster Recovery in Dual-active Cloud Center Xiao Chen 1, a, Longjun Zhang
Chapter 11: Indexing and Hashing
 Chapter 11: Indexing and Hashing Database System Concepts, 6 th Ed. See www.db-book.com for conditions on re-use Chapter 11: Indexing and Hashing Basic Concepts Ordered Indices B + -Tree Index Files B-Tree
Chapter 11: Indexing and Hashing Database System Concepts, 6 th Ed. See www.db-book.com for conditions on re-use Chapter 11: Indexing and Hashing Basic Concepts Ordered Indices B + -Tree Index Files B-Tree
A paralleled algorithm based on multimedia retrieval
 A paralleled algorithm based on multimedia retrieval Changhong Guo Teaching and Researching Department of Basic Course, Jilin Institute of Physical Education, Changchun 130022, Jilin, China Abstract With
A paralleled algorithm based on multimedia retrieval Changhong Guo Teaching and Researching Department of Basic Course, Jilin Institute of Physical Education, Changchun 130022, Jilin, China Abstract With
Distributed File Systems II
 Distributed File Systems II To do q Very-large scale: Google FS, Hadoop FS, BigTable q Next time: Naming things GFS A radically new environment NFS, etc. Independence Small Scale Variety of workloads Cooperation
Distributed File Systems II To do q Very-large scale: Google FS, Hadoop FS, BigTable q Next time: Naming things GFS A radically new environment NFS, etc. Independence Small Scale Variety of workloads Cooperation
Case study: ext2 FS 1
 Case study: ext2 FS 1 The ext2 file system Second Extended Filesystem The main Linux FS before ext3 Evolved from Minix filesystem (via Extended Filesystem ) Features Block size (1024, 2048, and 4096) configured
Case study: ext2 FS 1 The ext2 file system Second Extended Filesystem The main Linux FS before ext3 Evolved from Minix filesystem (via Extended Filesystem ) Features Block size (1024, 2048, and 4096) configured
Performing MapReduce on Data Centers with Hierarchical Structures
 INT J COMPUT COMMUN, ISSN 1841-9836 Vol.7 (212), No. 3 (September), pp. 432-449 Performing MapReduce on Data Centers with Hierarchical Structures Z. Ding, D. Guo, X. Chen, X. Luo Zeliu Ding, Deke Guo,
INT J COMPUT COMMUN, ISSN 1841-9836 Vol.7 (212), No. 3 (September), pp. 432-449 Performing MapReduce on Data Centers with Hierarchical Structures Z. Ding, D. Guo, X. Chen, X. Luo Zeliu Ding, Deke Guo,
4th National Conference on Electrical, Electronics and Computer Engineering (NCEECE 2015)
 4th National Conference on Electrical, Electronics and Computer Engineering (NCEECE 2015) Benchmark Testing for Transwarp Inceptor A big data analysis system based on in-memory computing Mingang Chen1,2,a,
4th National Conference on Electrical, Electronics and Computer Engineering (NCEECE 2015) Benchmark Testing for Transwarp Inceptor A big data analysis system based on in-memory computing Mingang Chen1,2,a,
Chapter 11: Indexing and Hashing
 Chapter 11: Indexing and Hashing Basic Concepts Ordered Indices B + -Tree Index Files B-Tree Index Files Static Hashing Dynamic Hashing Comparison of Ordered Indexing and Hashing Index Definition in SQL
Chapter 11: Indexing and Hashing Basic Concepts Ordered Indices B + -Tree Index Files B-Tree Index Files Static Hashing Dynamic Hashing Comparison of Ordered Indexing and Hashing Index Definition in SQL
VFS Interceptor: Dynamically Tracing File System Operations in real. environments
 VFS Interceptor: Dynamically Tracing File System Operations in real environments Yang Wang, Jiwu Shu, Wei Xue, Mao Xue Department of Computer Science and Technology, Tsinghua University iodine01@mails.tsinghua.edu.cn,
VFS Interceptor: Dynamically Tracing File System Operations in real environments Yang Wang, Jiwu Shu, Wei Xue, Mao Xue Department of Computer Science and Technology, Tsinghua University iodine01@mails.tsinghua.edu.cn,
SOLVING LOAD REBALANCING FOR DISTRIBUTED FILE SYSTEM IN CLOUD
 1 SHAIK SHAHEENA, 2 SD. AFZAL AHMAD, 3 DR.PRAVEEN SHAM 1 PG SCHOLAR,CSE(CN), QUBA ENGINEERING COLLEGE & TECHNOLOGY, NELLORE 2 ASSOCIATE PROFESSOR, CSE, QUBA ENGINEERING COLLEGE & TECHNOLOGY, NELLORE 3
1 SHAIK SHAHEENA, 2 SD. AFZAL AHMAD, 3 DR.PRAVEEN SHAM 1 PG SCHOLAR,CSE(CN), QUBA ENGINEERING COLLEGE & TECHNOLOGY, NELLORE 2 ASSOCIATE PROFESSOR, CSE, QUBA ENGINEERING COLLEGE & TECHNOLOGY, NELLORE 3
Organization and Retrieval Method of Multimodal Point of Interest Data Based on Geo-ontology
 , pp.49-54 http://dx.doi.org/10.14257/astl.2014.45.10 Organization and Retrieval Method of Multimodal Point of Interest Data Based on Geo-ontology Ying Xia, Shiyan Luo, Xu Zhang, Hae Yong Bae Research
, pp.49-54 http://dx.doi.org/10.14257/astl.2014.45.10 Organization and Retrieval Method of Multimodal Point of Interest Data Based on Geo-ontology Ying Xia, Shiyan Luo, Xu Zhang, Hae Yong Bae Research
Design of Labour Agency Platform Based on Agent Technology of JADE *
 Design of Labour Agency Platform Based on Agent Technology of JADE * Xiaobin Qiu **, Nan Zhou, and Xin Wang Network Center, China Agriculture University, Beijing 100083, P.R. China qxb@cau.edu.cn Abstract.
Design of Labour Agency Platform Based on Agent Technology of JADE * Xiaobin Qiu **, Nan Zhou, and Xin Wang Network Center, China Agriculture University, Beijing 100083, P.R. China qxb@cau.edu.cn Abstract.
Lustre Clustered Meta-Data (CMD) Huang Hua Andreas Dilger Lustre Group, Sun Microsystems
 Lustre Clustered Meta-Data (CMD) Huang Hua H.Huang@Sun.Com Andreas Dilger adilger@sun.com Lustre Group, Sun Microsystems 1 Agenda What is CMD? How does it work? What are FIDs? CMD features CMD tricks Upcoming
Lustre Clustered Meta-Data (CMD) Huang Hua H.Huang@Sun.Com Andreas Dilger adilger@sun.com Lustre Group, Sun Microsystems 1 Agenda What is CMD? How does it work? What are FIDs? CMD features CMD tricks Upcoming
A Chord-Based Novel Mobile Peer-to-Peer File Sharing Protocol
 A Chord-Based Novel Mobile Peer-to-Peer File Sharing Protocol Min Li 1, Enhong Chen 1, and Phillip C-y Sheu 2 1 Department of Computer Science and Technology, University of Science and Technology of China,
A Chord-Based Novel Mobile Peer-to-Peer File Sharing Protocol Min Li 1, Enhong Chen 1, and Phillip C-y Sheu 2 1 Department of Computer Science and Technology, University of Science and Technology of China,
A Capacity Planning Methodology for Distributed E-Commerce Applications
 A Capacity Planning Methodology for Distributed E-Commerce Applications I. Introduction Most of today s e-commerce environments are based on distributed, multi-tiered, component-based architectures. The
A Capacity Planning Methodology for Distributed E-Commerce Applications I. Introduction Most of today s e-commerce environments are based on distributed, multi-tiered, component-based architectures. The
The Study of Genetic Algorithm-based Task Scheduling for Cloud Computing
 The Study of Genetic Algorithm-based Task Scheduling for Cloud Computing Sung Ho Jang, Tae Young Kim, Jae Kwon Kim and Jong Sik Lee School of Information Engineering Inha University #253, YongHyun-Dong,
The Study of Genetic Algorithm-based Task Scheduling for Cloud Computing Sung Ho Jang, Tae Young Kim, Jae Kwon Kim and Jong Sik Lee School of Information Engineering Inha University #253, YongHyun-Dong,
Chapter 12. File Management
 Operating System Chapter 12. File Management Lynn Choi School of Electrical Engineering Files In most applications, files are key elements For most systems except some real-time systems, files are used
Operating System Chapter 12. File Management Lynn Choi School of Electrical Engineering Files In most applications, files are key elements For most systems except some real-time systems, files are used
QUANTIZER DESIGN FOR EXPLOITING COMMON INFORMATION IN LAYERED CODING. Mehdi Salehifar, Tejaswi Nanjundaswamy, and Kenneth Rose
 QUANTIZER DESIGN FOR EXPLOITING COMMON INFORMATION IN LAYERED CODING Mehdi Salehifar, Tejaswi Nanjundaswamy, and Kenneth Rose Department of Electrical and Computer Engineering University of California,
QUANTIZER DESIGN FOR EXPLOITING COMMON INFORMATION IN LAYERED CODING Mehdi Salehifar, Tejaswi Nanjundaswamy, and Kenneth Rose Department of Electrical and Computer Engineering University of California,
A Miniature-Based Image Retrieval System
 A Miniature-Based Image Retrieval System Md. Saiful Islam 1 and Md. Haider Ali 2 Institute of Information Technology 1, Dept. of Computer Science and Engineering 2, University of Dhaka 1, 2, Dhaka-1000,
A Miniature-Based Image Retrieval System Md. Saiful Islam 1 and Md. Haider Ali 2 Institute of Information Technology 1, Dept. of Computer Science and Engineering 2, University of Dhaka 1, 2, Dhaka-1000,
Analyzing and Improving Load Balancing Algorithm of MooseFS
 , pp. 169-176 http://dx.doi.org/10.14257/ijgdc.2014.7.4.16 Analyzing and Improving Load Balancing Algorithm of MooseFS Zhang Baojun 1, Pan Ruifang 1 and Ye Fujun 2 1. New Media Institute, Zhejiang University
, pp. 169-176 http://dx.doi.org/10.14257/ijgdc.2014.7.4.16 Analyzing and Improving Load Balancing Algorithm of MooseFS Zhang Baojun 1, Pan Ruifang 1 and Ye Fujun 2 1. New Media Institute, Zhejiang University
The Establishment of Large Data Mining Platform Based on Cloud Computing. Wei CAI
 2017 International Conference on Electronic, Control, Automation and Mechanical Engineering (ECAME 2017) ISBN: 978-1-60595-523-0 The Establishment of Large Data Mining Platform Based on Cloud Computing
2017 International Conference on Electronic, Control, Automation and Mechanical Engineering (ECAME 2017) ISBN: 978-1-60595-523-0 The Establishment of Large Data Mining Platform Based on Cloud Computing
File System Interface and Implementation
 Unit 8 Structure 8.1 Introduction Objectives 8.2 Concept of a File Attributes of a File Operations on Files Types of Files Structure of File 8.3 File Access Methods Sequential Access Direct Access Indexed
Unit 8 Structure 8.1 Introduction Objectives 8.2 Concept of a File Attributes of a File Operations on Files Types of Files Structure of File 8.3 File Access Methods Sequential Access Direct Access Indexed
Parallel Geospatial Data Management for Multi-Scale Environmental Data Analysis on GPUs DOE Visiting Faculty Program Project Report
 Parallel Geospatial Data Management for Multi-Scale Environmental Data Analysis on GPUs 2013 DOE Visiting Faculty Program Project Report By Jianting Zhang (Visiting Faculty) (Department of Computer Science,
Parallel Geospatial Data Management for Multi-Scale Environmental Data Analysis on GPUs 2013 DOE Visiting Faculty Program Project Report By Jianting Zhang (Visiting Faculty) (Department of Computer Science,
Striped Grid Files: An Alternative for Highdimensional
 Striped Grid Files: An Alternative for Highdimensional Indexing Thanet Praneenararat 1, Vorapong Suppakitpaisarn 2, Sunchai Pitakchonlasap 1, and Jaruloj Chongstitvatana 1 Department of Mathematics 1,
Striped Grid Files: An Alternative for Highdimensional Indexing Thanet Praneenararat 1, Vorapong Suppakitpaisarn 2, Sunchai Pitakchonlasap 1, and Jaruloj Chongstitvatana 1 Department of Mathematics 1,
Finding Optimal Tour Length of Mobile Agent in Wireless Sensor Network
 Conference on Advances in Communication and Control Systems 2013 (CAC2S 2013) Finding Optimal Tour Length of Mobile Agent in Wireless Sensor Network Anil Kumar Mahto anil.fiem16@gmail.com Ajay Prasad Department
Conference on Advances in Communication and Control Systems 2013 (CAC2S 2013) Finding Optimal Tour Length of Mobile Agent in Wireless Sensor Network Anil Kumar Mahto anil.fiem16@gmail.com Ajay Prasad Department
Page Mapping Scheme to Support Secure File Deletion for NANDbased Block Devices
 Page Mapping Scheme to Support Secure File Deletion for NANDbased Block Devices Ilhoon Shin Seoul National University of Science & Technology ilhoon.shin@snut.ac.kr Abstract As the amount of digitized
Page Mapping Scheme to Support Secure File Deletion for NANDbased Block Devices Ilhoon Shin Seoul National University of Science & Technology ilhoon.shin@snut.ac.kr Abstract As the amount of digitized
The Design and Optimization of Database
 Journal of Physics: Conference Series PAPER OPEN ACCESS The Design and Optimization of Database To cite this article: Guo Feng 2018 J. Phys.: Conf. Ser. 1087 032006 View the article online for updates
Journal of Physics: Conference Series PAPER OPEN ACCESS The Design and Optimization of Database To cite this article: Guo Feng 2018 J. Phys.: Conf. Ser. 1087 032006 View the article online for updates
Key words: Wireless Sensor Networks, Clustering Routing Algorithm, Hierarchical Multi-hop Clustering Routing Algorithm
 doi:10.21311/001.39.11.34 An Improved Clustering Routing Algorithm Based on Energy Balance Li Cai and Jianying Su Chongqing City Management College, Chongqing 401331,China Abstract: For network distribution
doi:10.21311/001.39.11.34 An Improved Clustering Routing Algorithm Based on Energy Balance Li Cai and Jianying Su Chongqing City Management College, Chongqing 401331,China Abstract: For network distribution
Parallelizing Inline Data Reduction Operations for Primary Storage Systems
 Parallelizing Inline Data Reduction Operations for Primary Storage Systems Jeonghyeon Ma ( ) and Chanik Park Department of Computer Science and Engineering, POSTECH, Pohang, South Korea {doitnow0415,cipark}@postech.ac.kr
Parallelizing Inline Data Reduction Operations for Primary Storage Systems Jeonghyeon Ma ( ) and Chanik Park Department of Computer Science and Engineering, POSTECH, Pohang, South Korea {doitnow0415,cipark}@postech.ac.kr
Improving Suffix Tree Clustering Algorithm for Web Documents
 International Conference on Logistics Engineering, Management and Computer Science (LEMCS 2015) Improving Suffix Tree Clustering Algorithm for Web Documents Yan Zhuang Computer Center East China Normal
International Conference on Logistics Engineering, Management and Computer Science (LEMCS 2015) Improving Suffix Tree Clustering Algorithm for Web Documents Yan Zhuang Computer Center East China Normal
IN recent years, the amount of traffic has rapidly increased
 , March 15-17, 2017, Hong Kong Content Download Method with Distributed Cache Management Masamitsu Iio, Kouji Hirata, and Miki Yamamoto Abstract This paper proposes a content download method with distributed
, March 15-17, 2017, Hong Kong Content Download Method with Distributed Cache Management Masamitsu Iio, Kouji Hirata, and Miki Yamamoto Abstract This paper proposes a content download method with distributed
A Two-Tier Distributed Full-Text Indexing System
 Appl. Math. Inf. Sci. 8, No. 1, 321-326 (2014) 321 Applied Mathematics & Information Sciences An International Journal http://dx.doi.org/10.12785/amis/080139 A Two-Tier Distributed Full-Text Indexing System
Appl. Math. Inf. Sci. 8, No. 1, 321-326 (2014) 321 Applied Mathematics & Information Sciences An International Journal http://dx.doi.org/10.12785/amis/080139 A Two-Tier Distributed Full-Text Indexing System
A Scheme of Multi-path Adaptive Load Balancing in MANETs
 4th International Conference on Machinery, Materials and Computing Technology (ICMMCT 2016) A Scheme of Multi-path Adaptive Load Balancing in MANETs Yang Tao1,a, Guochi Lin2,b * 1,2 School of Communication
4th International Conference on Machinery, Materials and Computing Technology (ICMMCT 2016) A Scheme of Multi-path Adaptive Load Balancing in MANETs Yang Tao1,a, Guochi Lin2,b * 1,2 School of Communication
1. Introduction. Traditionally, a high bandwidth file system comprises a supercomputer with disks connected
 1. Introduction Traditionally, a high bandwidth file system comprises a supercomputer with disks connected by a high speed backplane bus such as SCSI [3][4] or Fibre Channel [2][67][71]. These systems
1. Introduction Traditionally, a high bandwidth file system comprises a supercomputer with disks connected by a high speed backplane bus such as SCSI [3][4] or Fibre Channel [2][67][71]. These systems
