Structured Systems Analysis and Design
|
|
|
- Garey Oliver
- 6 years ago
- Views:
Transcription
1 Structured Systems Analysis and Design Sogeti University February 1, 2011 Dr. Kevin P. Duffy
2 What is SSAD? A few definitions to start everybody off on the same page. System: A collection of interrelated components that function together to achieve some outcome (goal or objective) Structured Systems Analysis and Design: an organizational process used to develop and maintain computer-based information systems (both business and systems professionals participate in SSAD). 2
3 What is SSAD? Hence, a Systems Development Methodology is a standard process followed in an organization to conduct all the steps necessary to analyze, design, implement, and maintain information systems. Why use a standard process? The most common, or traditional, methodology is the Systems Development Life Cycle, or SDLC. 3
4 General Systems Theory General Systems Theory (or, Systems Theory) became popular as a discipline in the 1940s and 1950s Systems theory has proven useful in Systems Analysis and Design as a means of providing definitions and explaining system behavior(s). Systems theory notes that All Systems are composed of sub-systems, and all systems are themselves sub-systems to larger systems From this foundation, systems theory permits Decomposition, or the ability to break a large system down into its component parts. What is gained by breaking something into component [ smaller ] parts? - the ability to better grasp system functionality - easier to work with smaller components and/or systems - easier to maintain, update, and replace components 4
5 General Systems Theory Systems Theory provides us with a definition for systems Systems theory defines nine characteristics of a system: System components Interrelationships Boundary Purpose Environment System interfaces Input Output Constraints Each of these characteristics provide us with a means of checking the system 5
6 Analysis and Design Landscape 1950s: focus on efficient automation of existing processes 1960s: advent of 3GL, faster and more reliable computers 1970s: system development becomes more like an engineering discipline 1980s: major breakthrough with 4GL, CASE tools, object-oriented methods 1990s: focus on system integration, GUI applications, client/server platforms, the Internet The New Century: Web application development, wireless PDAs, component-based applications 6
7 Larger Picture Problems Systems come in late Systems come in over-budget Systems tend to be considered as failures (up to 76%) for one reason or another Technology changes, and systems don t keep up with technology (hence, the existence of so-called legacy systems) 7
8 SDLC The SDLC is the traditional methodology used to develop, maintain, and replace information systems. The activities falling throughout analysis, design, and development are categorized into phases (the number of phases will vary from one writer to another) 8
9 SDLC The Phases of the SDLC include: Planning Analysis Design Implementation Maintenance The cycle typically flows through numerous iterations 9
10 SDLC The SDLC is often referred to as the waterfall model Planning Analysis Design Implementation Maintenance 10
11 SDLC Planning: an organization s total information system needs are identified, analyzed, prioritized, and arranged Analysis: System requirements are studied and structured Design: A description of the recommended solution is converted into logical and then physical system specifications Logical design: all functional features of the system chosen for development in analysis are described independently of any computer platform Physical design: the logical specifications of the system from logical design are transformed into the technology-specific details from which all programming and system construction can be accomplished Implementation: the information system is coded, tested, installed and supported in the organization Maintenance: the system is systematically repaired and improved 11
12 Structured Systems Analysis and Design The Analyst s Role Sogeti University February 1, 2011 Dr. Kevin P. Duffy
13 Systems Analyst Role The systems analyst functions within the organization as a liaison between the business professionals and the information systems or computer science professionals In this capacity, a number of skills are required of the analyst: Working knowledge of information technology Computer programming experience and expertise General business knowledge General problem-solving skills Good interpersonal communication skills Good interpersonal relations skills Flexibility and adaptability Character and ethics 13
14 Systems Analyst Role By "Problems" that need solving, we mean: Problems, either real or anticipated, that require corrective action Opportunities to improve a situation despite the absence of complaints Directives to change a situation regardless of whether anyone has complained about the current situation 14
15 Systems Analyst Role In the role of a liaison, one of the primary roles of the systems analyst is to interact with organizational stakeholders, including the end-users of the system Why interact with end-users? To gain Buy-In for the system To calm user fears To gain the end-users understanding of the process How it operates Why it operates as it does What the process accomplishes Where a process fits into a larger process 15
16 Systems Analyst Role There are a number of reasons why a system changes Business Drivers Globalization of the Economy Electronic Commerce and Business Security and Privacy Collaboration and Partnership Knowledge Asset Management Continuous Improvement and Total Quality Management Business Process Redesign 16
17 Systems Analyst Role Technology Drivers Networks and the Internet Mobile and Wireless Technologies Object Technologies Collaborative Technologies Enterprise Applications 17
18 Systems Analyst Role Regardless of the driver of change, a systems analyst must analyze and understand the problem or opportunity identify solution requirements or expectations 18
19 Systems Analyst Role In today s Information Technology environment, there are numerous sources for software and systems acquisition Outsourcing Custom built in-house Customized off-the-shelf software (COTS) Application Service Providers (ASPs) Open source software Enterprise wide software solutions The analyst must be able to compare software against a variety of metrics cost functionality and response time flexibility ease-of-use vendor support 19
20 Structured Systems Analysis and Design Project Management Sogeti University February 1, 2011 Dr. Kevin P. Duffy
21 Project Management and Planning As you might imagine, an analysis and design project can become a huge undertaking! Because of the size of projects, and because projects are a team effort (too large, involved, and complicated to be an individual project), project management techniques are invaluable. Project Management helps to ensure that Customer expectations are met Budget and Time constraints are satisfied 21
22 Project Management Project A planned undertaking of related activities to reach an objective that has a beginning and an end Project management A controlled process of initiating, planning, executing, and closing down a project Planning a project Define clear, discrete activities and the work needed to complete each activity Tasks Define project scope, alternatives, feasibility Divide project into tasks Estimate resource requirements Develop preliminary schedule Create preliminary budget All of these activities or tasks must be re-visited, and perhaps updated, throughout the entire project 22
23 Project Management and Planning Project Scope the determination of scope will depend on the following factors: Which organizational units (business functions and divisions) might be affected by or use the proposed system or system change? With which current systems might the proposed system need to interact or be consistent, or which current systems might be changed due to a replacement system? Who inside and outside the requesting organization (or the organization as a whole) might care about the proposed system? What range of potential system capabilities is to be considered? Project scope is an iterative process, and will evolve: as more information is collected as the project proceeds. 23
24 Project Management and Planning Another task is to undertake a feasibility study of a proposed project when a request for service is received Feasibility is the measure of how beneficial or practical the development of an information system will be to an organization. There are numerous types of feasibility to be considered: Operational feasibility is a measure of how well a solution meets the identified system requirements to solve the problems and take advantage of the opportunities envisioned for the system Cultural (or political) feasibility is a measure of how people feel about a solution and how well it will be accepted in a given organization climate Technical feasibility is a measure of the practicality of a specific technical solution and the availability of technical resources and expertise to implement and maintain it Schedule feasibility is a measure of how reasonable the project timetable is Legal feasibility is a measure of how well a solution can be implemented within existing legal and contractual obligations 24
25 Project Management and Planning Project Planning may include scheduling diagrams, such as a Gantt chart (where horizontal bars represent task duration) or network charts (PERT/CPM) where activities and links represent task dependencies. Gantt Chart: 25
26 Project Management and Planning PERT/CPM chart: 26
27 Project Management and Planning Economic feasibility is a measure of the cost-effectiveness of a project or solution, and involves performing a cost-benefit analysis of an IT investment Time Value of Money: undertaking a cost-benefit analysis of an IT investment. PV n 1 Y (1 + i) = n Where PV = present value n = year (time) Y = payment; some portion of principal i = interest rate 27
28 Project Management and Planning Use a spreadsheet for calculations! 28
29 Project Management and Planning The goal of project management and planning is to begin to gain an understanding of the project establish realistic goals that can be met 29
30 Structured Systems Analysis and Design, Requirements Elicitation Sogeti University February 1, 2011 Dr. Kevin P. Duffy
31 Requirements Determination Traditional Methods for Determining Requirements Interviewing individuals Interviewing groups Observing workers Studying business documents 31
32 Requirements Determination One of the primary ways analysts gather information about an information systems project Interview Guide is a document for developing, planning and conducting an interview Plan the interview. Prepare interviewee: appointment, priming questions. Prepare agenda, checklist, questions. Listen carefully and take notes (tape record if permitted). Review notes within 48 hours. Be neutral. Seek diverse views. Each question in an interview guide can include both verbal and non-verbal information. Open-ended questions: questions that have no pre-specified answers Closed-ended questions: questions that ask those responding to choose from among a set of specified responses 32
33 Requirements Determination Direct Observation Watching users do their jobs Obtaining more firsthand and objective measures of employee interaction with information systems Can cause people to change their normal operating behavior Time-consuming and limited time to observe Analyzing Procedures and Other Documents Document Analysis Review of existing business documents Can give a historical and formal view of system requirements Types of information to be discovered: Problems with existing system, or Opportunity to meet new need Organizational direction and Names of key individuals Values of organization Special information processing circumstances Reasons for current system design Rules for processing data 33
34 Requirements Determination When analyzing Procedures, be aware: Formal Systems: the official way a system works as described in organizational documentation (i.e. work procedure) Informal Systems: the way a system actually works (i.e. interviews, observations) Useful document: Business form Used for all types of business functions Explicitly indicate what data flow in and out of a system and data necessary for the system to function Gives crucial information about the nature of the organization 34
35 Requirements Determination Joint Application Design (JAD) may be useful: Brings together key users, managers, and systems analysts Purpose: collect system requirements simultaneously from key people Conducted off-site But, is resource-intensive JAD Participants Session Leader: facilitates group process Users: active, speaking participants Managers: active, speaking participants Sponsor: high-level champion, limited participation Systems Analysts: should mostly listen Scribe: record session activities IS Staff: should mostly listen 35
36 Structured Systems Analysis and Design, Modeling Sogeti University February 1, 2011 Dr. Kevin P. Duffy
37 Modeling Modeling, or Diagramming, system requirements Assists by structuring requirements Graphically represent the processes that capture, manipulate, store, and distribute data between a system and its environment and among system components. A process is a systematic series of actions directed toward an end or outcome A Data Flow Diagram (DFD) is a process modeling methodology DFDs should be drawn for both the current and the proposed system DFDs are simple to draw (consist of very few symbols) Because of their simplicity, DFDs are explained easily to users DFDs are drawn for successive layers, with each layer delving further into the process and its functionality Above all, use diagrams as a communication device 37
38 Modeling Process modeling using data flow diagrams views a system: as a collection of processes processes interact with data entities processes accept inputs and produce outputs Data Flow Diagrams are constructed using only a few symbols (hence, they re easier to understand than typical flowcharts) Process Data Store Entity (Source or Sink) Data Flow 38
39 Modeling The highest level DFD is a context diagram, and consists of one and only one process, and absolutely zero data stores. It gives a very high level view of the system. A context diagram is followed by a level 0 diagram, then a level 1 diagram, and so forth. The lowest level DFD is known as a primitive data flow diagram. Context Diagram for an ATM System The diagram shows both Input(s) and Output(s) Only 1 process is shown on a Context Diagram this process represents the system in its entirety A Data Store is never shown on a Context Diagram The inputs to a process are different from the outputs (processes transform inputs into outputs 39
40 Modeling All Communication must flow through a process An entity cannot communicate directly with another entity (since an entity is external to the system) An entity cannot access a data store without going through a process (since a data store is part of the system, and an entity is external to the system). Data cannot move directly from one data store to another; data movement must occur through a process Data flows in only one direction at a time (data flow arrows are uni-directional) All entities, processes, data flows, and data stores are labeled There may be as many entities, processes, data flows, and data stores as needed. 40
41 Modeling The Level-0 diagram is followed by a Level-1 diagram One Level-1 diagram is drawn for each process appearing on the Level-0 diagram Inputs and outputs from the process should remain balanced with what is depicted on higher level diagrams When the process is fully understood, diagramming stops (this rule applies to the system as a whole, as well) The final set of data flow diagrams is referred to as primitive data flow diagrams All processes must have input; if a process is making outputs without inputs, there is a miracle taking place All processes must produce outputs; if a process is taking inputs but not producing outputs, there is a black hole (if an object only ever receives inputs without producing outputs, perhaps it should be modeled as a sink (entity) rather than as a process). Processes typically have a verb (action) name, while entities and data stores typically have a noun name A data flow leading into a data store is an update (i.e., write, modify, delete) A data flow leading out of a data store is a use (i.e., read, retrieve) 41
42 Modeling Data may not flow directly from one data store to another data store. All movement of data must occur through a process Data may not move from a source into a data store. Data must be sent from the source into a process and from the process into the data store Data may not move from a data store into a sink. Data must be sent from the data store into a process and from the process into the sink Data may not move directly between a source and a sink. All data must flow through the system. If data does not flow through a process (i.e., through the system), it is external to the system, and therefore does not appear on a data flow diagram. A data flow may be split on lower level DFDs (a composite data flow may be split into simpler data flows, where part of the data flows into one process, and part into another process) Note also that the inputs to a process must be sufficient to produce the outputs (think back to miracles happening) 42
43 Modeling There may be four different sets of DFDs drawn in total: Current Logical (representation of current system with technology references removed) Current Physical (representation of current system, including technology references data stores actually represent existing data, tables) Proposed Logical (representation of proposed system with technology references removed) Proposed Physical (representation of proposed system including technology references) Time is not represented on a DFD Several iterations of drawings will likely occur (software drawing tool use becomes a must) Consider stopping drawing when each process captures a single decision, and when each data store represents a single data entity 43
44 Modeling Data modeling captures the data fed into the system or produced by the system, and provides a structure to house (store) the data The most common data model is the relational database model In the relational database model, data are grouped into subjects of interest (i.e., customer, product, sales, etc.) The data model includes a 2-dimensional table, where a table often corresponds to a data subject of interest (i.e., customer, product, etc.) A table resembles (for example) an Excel spreadsheet, where Each column represents an attribute (or characteristic) of the data. A table column may be called a field Each row represents an instance of the data. A row may be called a record Data is stored according to its subject, i.e., client data in one table, product information in another table, and order information in another table Each row of data contains a field (or fields) which uniquely identify a record, or a single instance of the data. This is known as the primary key 44
45 Modeling Keep in mind that data is a symbolic representation of a real customer, or of a real order. Because it is symbolic, it can t be seen directly. Hence, the primary key is needed to distinguish one record from another record. Choose a primary key which: is a characteristic which all instances of the data are likely to possess is a characteristic which will be non-null across all instances of the data is a characteristic which will be stable (non-changing) over time Likely candidates or choices for primary key: Customer number Product Id or number Sales representative Employee number Fields such as employee name are not good candidates to serve as the primary key. More than one person, or employee, may have the same name; more than one person, or employee, will not have the same employee ID. 45
46 Modeling In this sample entity The name of the entity is Customer (shown in all caps) The primary key field is Customer_ID Sales_Rep_Id serves as a foreign key CUSTOMER Customer_ID Customer_Name Customer_Addr1 Customer_Addr2 Customer_City Customer_State Customer_Zip Customer_Phone Customer_POC FK Sales_Rep_Id 46
47 Modeling Why include a foreign key? A foreign key is used to link, or relate one table to another table. By definition, a foreign key is a field which serves as a primary key in another, related, table, but is not the primary key in the current table CUSTOMER Customer_ID Customer_Name Customer_Addr1 Customer_Addr2 Customer_City Customer_State Customer_Zip Customer_Phone Customer_POC FK Sales_Rep_Id FK SALES_REP Sales_Rep_ID Sales_Rep_Name Sales_Rep_Addr1 Sales_Rep_Addr2 Sales_Rep_City Sales_Rep_State Sales_Rep_Zip Sales_Rep_Phone PK 47
48 Modeling The relational database model functions on the basis of shared data values among tables (i.e., the field value for Sales_Rep_ID is found in the SALES_REP table as well as in the CUSTOMER table) The foreign keys serve to map out the relationships among the entities in the database A conceptual data model for a relational database is referred to as an Entity-Relationship Diagram (or E-R Diagram) The ability to relate data tables to one another allows us to capture intricate relationships among the data while storing data in stable structures Stability of the structures is enhanced through the data normalization process When beginning the data modeling task, walk through processes, data flow diagrams, business forms, etc. These are invaluable sources in determining what data is important to the business and to its systems Group like data together Ask whether multiple instances can be stored in one record of a table, or are multiple instances an indication that separate tables are needed 48
49 Modeling Example: An employee may have more than one phone number Office phone Mobile phone Home phone These would likely be stored as separate fields in one record Example: A customer may place more than one order Order placed on January 21 Order placed on May 27 Order placed on August 17 These would likely be stored as separate records (separate instances of the Order entity) How can you tell? Examine the primary key for the table. Is the data functionally dependent upon the primary key? 49
50 Modeling A Use Case Model comes out of the object-oriented perspective. However, the notion of a use case has become part of the business lexicon, and is likely to be a phrase often heard during an analysis and design Use-case modeling: the process of modeling a system s functions in terms of business events, who initiated the events, and how the system responds to those events. Use-case modeling has proved to be a valuable aid in meeting the challenges of determining what a system is required to do from a user and stakeholder perspective. It is now widely recognized as a best practice for the defining, documenting, and understanding of an information system s functional requirements. The use case model consists of 2 parts: the use case diagram, and the use case narrative. The use case diagram graphically depicts the system as a collection of use cases, actors (users), and their relationships. The use narrative is a textual description of the business event and how the user will interact with the system to accomplish the task. 50
51 Modeling Example Use Case Diagram 51
52 Modeling Example Use Case Narrative Example: Library book 1. Check student status 2. Scan book 3. Assign due date 4. de-security book 5. update book status 1.a. Student status is not found. Notify customer. 1.b. Student status suspended. Refer to student account office. 52
53 Modeling To construct use cases: Identify business actors Identify business requirements use cases Construct use-case model diagram Document business requirements use-case narratives An actor typically represents a role, rather than a particular person i.e., Manager, Sales Rep, etc. Time may be an actor (some use cases are triggered by time of day) Another system may be an actor (outputs from one system may be triggering inputs to another system) 53
54 Modeling Throughout the modeling process, it becomes increasingly important to fully utilize CASE tools CASE = Computer Assisted Software Engineering CASE tools serve as a knowledge repository for the system Include completeness and consistency checking Upper-CASE tools capture early phases of the SDLC Lower-CASE tools capture later phases of the SDLC I-CASE (Integrated CASE) tools capture throughout the entire SDLC When a system is completely documented within a CASE tool, updates and changes are easy to manage Sophisticated CASE tools can create a system s data structures, applications, and interfaces from the material recorded 54
*ANSWERS * **********************************
 CS/183/17/SS07 UNIVERSITY OF SURREY BSc Programmes in Computing Level 1 Examination CS183: Systems Analysis and Design Time allowed: 2 hours Spring Semester 2007 Answer ALL questions in Section A and TWO
CS/183/17/SS07 UNIVERSITY OF SURREY BSc Programmes in Computing Level 1 Examination CS183: Systems Analysis and Design Time allowed: 2 hours Spring Semester 2007 Answer ALL questions in Section A and TWO
Chapter 6 Structuring System Requirements: Process Modeling 6.1
 Chapter 6 Structuring System Requirements: Process Modeling 6.1 Learning Objectives Explain process modeling Discuss data-flow diagramming mechanics, definitions, and rules Discuss balancing data-flow
Chapter 6 Structuring System Requirements: Process Modeling 6.1 Learning Objectives Explain process modeling Discuss data-flow diagramming mechanics, definitions, and rules Discuss balancing data-flow
Joint Application Design & Function Point Analysis the Perfect Match By Sherry Ferrell & Roger Heller
 Joint Application Design & Function Point Analysis the Perfect Match By Sherry Ferrell & Roger Heller Introduction The old adage It s not what you know but when you know it that counts is certainly true
Joint Application Design & Function Point Analysis the Perfect Match By Sherry Ferrell & Roger Heller Introduction The old adage It s not what you know but when you know it that counts is certainly true
Answer: D. Answer: B. Answer: B
 1. Management information systems (MIS) A. create and share documents that support day-today office activities C. capture and reproduce the knowledge of an expert problem solver B. process business transactions
1. Management information systems (MIS) A. create and share documents that support day-today office activities C. capture and reproduce the knowledge of an expert problem solver B. process business transactions
Abstract class Audit trail Class diagram Balancing Acceptance testing Closed-ended questions Baseline modules Action stubs Cohesion Activation
 Glossary of Terms Abstract class A class that has no direct instances but whose descendants may have direct instances. Acceptance testing The process whereby actual users test a completed information system,
Glossary of Terms Abstract class A class that has no direct instances but whose descendants may have direct instances. Acceptance testing The process whereby actual users test a completed information system,
Systems Analysis and Design in a Changing World, Fourth Edition
 Systems Analysis and Design in a Changing World, Fourth Edition Systems Analysis and Design in a Changing World, 4th Edition Learning Objectives Explain the purpose and various phases of the systems development
Systems Analysis and Design in a Changing World, Fourth Edition Systems Analysis and Design in a Changing World, 4th Edition Learning Objectives Explain the purpose and various phases of the systems development
APPENDIX M INTRODUCTION TO THE UML
 M INTRODUCTION TO THE UML This appendix, written only for those readers not familiar with the topic, provides a brief introduction, which cannot be considered as exhaustive, to the UML. The UML is a general-purpose
M INTRODUCTION TO THE UML This appendix, written only for those readers not familiar with the topic, provides a brief introduction, which cannot be considered as exhaustive, to the UML. The UML is a general-purpose
Predictive Insight, Automation and Expertise Drive Added Value for Managed Services
 Sponsored by: Cisco Services Author: Leslie Rosenberg December 2017 Predictive Insight, Automation and Expertise Drive Added Value for Managed Services IDC OPINION Competitive business leaders are challenging
Sponsored by: Cisco Services Author: Leslie Rosenberg December 2017 Predictive Insight, Automation and Expertise Drive Added Value for Managed Services IDC OPINION Competitive business leaders are challenging
Sample Exam. Advanced Test Automation - Engineer
 Sample Exam Advanced Test Automation - Engineer Questions ASTQB Created - 2018 American Software Testing Qualifications Board Copyright Notice This document may be copied in its entirety, or extracts made,
Sample Exam Advanced Test Automation - Engineer Questions ASTQB Created - 2018 American Software Testing Qualifications Board Copyright Notice This document may be copied in its entirety, or extracts made,
Requests Charges. Librarian. University affiliated patrons students, faculty, staff. Media Center Staff
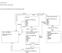 Catherine Rutan INFO 530-901 Dr. Valerie Yonker Circulation of Media Materials from University Media Center: Requests Charges Librarian Circulation Desk Attendant Inquires University ID # (Primary Key)
Catherine Rutan INFO 530-901 Dr. Valerie Yonker Circulation of Media Materials from University Media Center: Requests Charges Librarian Circulation Desk Attendant Inquires University ID # (Primary Key)
What is the Joint Application Development (JAD) Process?
 What is the Joint Application Development (JAD) Process? By Joy Matthews, Vice President, Pierson Requirements Group, Inc. jmatthews@piersonrequirementsgroup.com JAD is an Important Technique for Software
What is the Joint Application Development (JAD) Process? By Joy Matthews, Vice President, Pierson Requirements Group, Inc. jmatthews@piersonrequirementsgroup.com JAD is an Important Technique for Software
Overview. What is system analysis and design? Tools and models Methodologies
 Overview What is system analysis and design? Tools and models Methodologies Information Systems What is a system? Why do systems fail? What is systems analysis and design? How do we do systems analysis?
Overview What is system analysis and design? Tools and models Methodologies Information Systems What is a system? Why do systems fail? What is systems analysis and design? How do we do systems analysis?
Systems Analysis & Design
 Systems Analysis & Design Dr. Ahmed Lawgali Ahmed.lawgali@uob.edu.ly Slide 1 Systems Analysis & Design Course Textbook: Systems Analysis and Design With UML 2.0 An Object-Oriented Approach, Second Edition
Systems Analysis & Design Dr. Ahmed Lawgali Ahmed.lawgali@uob.edu.ly Slide 1 Systems Analysis & Design Course Textbook: Systems Analysis and Design With UML 2.0 An Object-Oriented Approach, Second Edition
Alignment of Business and IT - ArchiMate. Dr. Barbara Re
 Alignment of Business and IT - ArchiMate Dr. Barbara Re What is ArchiMate? ArchiMate is a modelling technique ("language") for describing enterprise architectures. It presents a clear set of concepts within
Alignment of Business and IT - ArchiMate Dr. Barbara Re What is ArchiMate? ArchiMate is a modelling technique ("language") for describing enterprise architectures. It presents a clear set of concepts within
Lecture 8 Requirements Engineering
 Lecture 8 Requirements Engineering Software Engineering ITCS 3155 Fall 2008 Dr. Jamie Payton Department of Computer Science University of North Carolina at Charlotte September 18, 2008 Lecture Overview
Lecture 8 Requirements Engineering Software Engineering ITCS 3155 Fall 2008 Dr. Jamie Payton Department of Computer Science University of North Carolina at Charlotte September 18, 2008 Lecture Overview
Data Warehouse and Data Mining
 Data Warehouse and Data Mining Lecture No. 09 Plannning Data Warehouse Naeem Ahmed Email: naeemmahoto@gmail.com Department of Software Engineering Mehran Univeristy of Engineering and Technology Jamshoro
Data Warehouse and Data Mining Lecture No. 09 Plannning Data Warehouse Naeem Ahmed Email: naeemmahoto@gmail.com Department of Software Engineering Mehran Univeristy of Engineering and Technology Jamshoro
History of object-oriented approaches
 Prof. Dr. Nizamettin AYDIN naydin@yildiz.edu.tr http://www.yildiz.edu.tr/~naydin Object-Oriented Oriented Systems Analysis and Design with the UML Objectives: Understand the basic characteristics of object-oriented
Prof. Dr. Nizamettin AYDIN naydin@yildiz.edu.tr http://www.yildiz.edu.tr/~naydin Object-Oriented Oriented Systems Analysis and Design with the UML Objectives: Understand the basic characteristics of object-oriented
Identify the guidelines for system development. Discuss the purpose of the activities performed in the analysis phase
 Discovering Computers 2010 Living in a Digital World Objectives Overview Define system development and list the system development phases Identify the guidelines for system development Discuss the importance
Discovering Computers 2010 Living in a Digital World Objectives Overview Define system development and list the system development phases Identify the guidelines for system development Discuss the importance
Meltem Özturan
 Meltem Özturan www.mis.boun.edu.tr/ozturan/samd 1 1 The systems development life cycle (SDLC) provides an overall framework for the process of system development, but the developer relies on many more
Meltem Özturan www.mis.boun.edu.tr/ozturan/samd 1 1 The systems development life cycle (SDLC) provides an overall framework for the process of system development, but the developer relies on many more
Today s cyber threat landscape is evolving at a rate that is extremely aggressive,
 Preparing for a Bad Day The importance of public-private partnerships in keeping our institutions safe and secure Thomas J. Harrington Today s cyber threat landscape is evolving at a rate that is extremely
Preparing for a Bad Day The importance of public-private partnerships in keeping our institutions safe and secure Thomas J. Harrington Today s cyber threat landscape is evolving at a rate that is extremely
2 The IBM Data Governance Unified Process
 2 The IBM Data Governance Unified Process The benefits of a commitment to a comprehensive enterprise Data Governance initiative are many and varied, and so are the challenges to achieving strong Data Governance.
2 The IBM Data Governance Unified Process The benefits of a commitment to a comprehensive enterprise Data Governance initiative are many and varied, and so are the challenges to achieving strong Data Governance.
1. i. What are the 3 major components of a information system and show their relationship input output
 Higher National Diploma in Information Technology First Year, Second semesterexamination-2011 IT2005: System Analysis and Design Answer Script No. of pages: 11 1. i. What are the 3 major components of
Higher National Diploma in Information Technology First Year, Second semesterexamination-2011 IT2005: System Analysis and Design Answer Script No. of pages: 11 1. i. What are the 3 major components of
1. The narratives, diagrams, charts, and other written materials that explain how a system works are collectively called
 CH 3 MULTIPLE CHOICE 1. The narratives, diagrams, charts, and other written materials that explain how a system works are collectively called a) documentation. b) data flows. c) flowcharts. d) schema.
CH 3 MULTIPLE CHOICE 1. The narratives, diagrams, charts, and other written materials that explain how a system works are collectively called a) documentation. b) data flows. c) flowcharts. d) schema.
10 Steps to Building an Architecture for Space Surveillance Projects. Eric A. Barnhart, M.S.
 10 Steps to Building an Architecture for Space Surveillance Projects Eric A. Barnhart, M.S. Eric.Barnhart@harris.com Howard D. Gans, Ph.D. Howard.Gans@harris.com Harris Corporation, Space and Intelligence
10 Steps to Building an Architecture for Space Surveillance Projects Eric A. Barnhart, M.S. Eric.Barnhart@harris.com Howard D. Gans, Ph.D. Howard.Gans@harris.com Harris Corporation, Space and Intelligence
CS504-Softwere Engineering -1 Solved Objective Midterm Papers For Preparation of Midterm Exam
 CS504-Softwere Engineering -1 Solved Objective Midterm Papers For Preparation of Midterm Exam MIDTERM EXAMINATION 2010 Question No: 1 ( Marks: 1 ) - Please choose one By following modern system engineering
CS504-Softwere Engineering -1 Solved Objective Midterm Papers For Preparation of Midterm Exam MIDTERM EXAMINATION 2010 Question No: 1 ( Marks: 1 ) - Please choose one By following modern system engineering
BPS Suite and the OCEG Capability Model. Mapping the OCEG Capability Model to the BPS Suite s product capability.
 BPS Suite and the OCEG Capability Model Mapping the OCEG Capability Model to the BPS Suite s product capability. BPS Contents Introduction... 2 GRC activities... 2 BPS and the Capability Model for GRC...
BPS Suite and the OCEG Capability Model Mapping the OCEG Capability Model to the BPS Suite s product capability. BPS Contents Introduction... 2 GRC activities... 2 BPS and the Capability Model for GRC...
System Analysis & design
 Assiut University Faculty of Computers and Information System Analysis & design Year 2 Academic Year 2014/ 2015 Term (2) 5 A PICTURE IS WORTH A 1,000 WORDS A process model is a graphical way of representing
Assiut University Faculty of Computers and Information System Analysis & design Year 2 Academic Year 2014/ 2015 Term (2) 5 A PICTURE IS WORTH A 1,000 WORDS A process model is a graphical way of representing
Managing the development and purchase of information systems (Part 2)
 Managing the development and purchase of information systems (Part 2) (Week 14, Thursday 4/12/2007) BUS3500 - Abdou Illia, Spring 2007 1 LEARNING GOALS Describe alternative systems development methodologies
Managing the development and purchase of information systems (Part 2) (Week 14, Thursday 4/12/2007) BUS3500 - Abdou Illia, Spring 2007 1 LEARNING GOALS Describe alternative systems development methodologies
Implementing ITIL v3 Service Lifecycle
 Implementing ITIL v3 Lifecycle WHITE PAPER introduction GSS INFOTECH IT services have become an integral means for conducting business for all sizes of businesses, private and public organizations, educational
Implementing ITIL v3 Lifecycle WHITE PAPER introduction GSS INFOTECH IT services have become an integral means for conducting business for all sizes of businesses, private and public organizations, educational
Ans 1-j)True, these diagrams show a set of classes, interfaces and collaborations and their relationships.
 Q 1) Attempt all the following questions: (a) Define the term cohesion in the context of object oriented design of systems? (b) Do you need to develop all the views of the system? Justify your answer?
Q 1) Attempt all the following questions: (a) Define the term cohesion in the context of object oriented design of systems? (b) Do you need to develop all the views of the system? Justify your answer?
The Analysis and Proposed Modifications to ISO/IEC Software Engineering Software Quality Requirements and Evaluation Quality Requirements
 Journal of Software Engineering and Applications, 2016, 9, 112-127 Published Online April 2016 in SciRes. http://www.scirp.org/journal/jsea http://dx.doi.org/10.4236/jsea.2016.94010 The Analysis and Proposed
Journal of Software Engineering and Applications, 2016, 9, 112-127 Published Online April 2016 in SciRes. http://www.scirp.org/journal/jsea http://dx.doi.org/10.4236/jsea.2016.94010 The Analysis and Proposed
Systems Analysis & Design
 Systems Analysis & Design Dr. Arif Sari Email: arif@arifsari.net Course Website: www.arifsari.net/courses/ Slide 1 Adapted from slides 2005 John Wiley & Sons, Inc. Slide 2 Course Textbook: Systems Analysis
Systems Analysis & Design Dr. Arif Sari Email: arif@arifsari.net Course Website: www.arifsari.net/courses/ Slide 1 Adapted from slides 2005 John Wiley & Sons, Inc. Slide 2 Course Textbook: Systems Analysis
Chapter 2: The Database Development Process
 : The Database Development Process Modern Database Management 7 th Edition Jeffrey A. Hoffer, Mary B. Prescott, Fred R. McFadden 1 Objectives Definition of terms Describe system development life cycle
: The Database Development Process Modern Database Management 7 th Edition Jeffrey A. Hoffer, Mary B. Prescott, Fred R. McFadden 1 Objectives Definition of terms Describe system development life cycle
The Open Group SOA Ontology Technical Standard. Clive Hatton
 The Open Group SOA Ontology Technical Standard Clive Hatton The Open Group Releases SOA Ontology Standard To Increase SOA Adoption and Success Rates Ontology Fosters Common Understanding of SOA Concepts
The Open Group SOA Ontology Technical Standard Clive Hatton The Open Group Releases SOA Ontology Standard To Increase SOA Adoption and Success Rates Ontology Fosters Common Understanding of SOA Concepts
Ch 4: Requirements Engineering. What are requirements?
 Ch 4: Engineering What are? Functional and non-functional The software document specification engineering processes elicitation and analysis validation management The descriptions of what the system should
Ch 4: Engineering What are? Functional and non-functional The software document specification engineering processes elicitation and analysis validation management The descriptions of what the system should
Professional (CBAP) version 3
 Certified Business Analysis Professional (CBAP) version 3 Amman Jordan July 29 th August 5 th, 2017 Instructor Mr. Tareq Al Nashawati Certified CBAP, PMP Table of Content 1 PROGRAM VALUE... 3 2 TARGET
Certified Business Analysis Professional (CBAP) version 3 Amman Jordan July 29 th August 5 th, 2017 Instructor Mr. Tareq Al Nashawati Certified CBAP, PMP Table of Content 1 PROGRAM VALUE... 3 2 TARGET
Lab 16: Visio Introduction
 Lab 16: Visio Introduction () CONTENTS 1 Visio- Introduction to DFD Data Flow Diagraming... 2 1.1 In-Lab... 3 1.1.1 In-Lab Materials... 3 1.1.2 In-Lab Instructions... 3 2 Getting started: Let s decompose
Lab 16: Visio Introduction () CONTENTS 1 Visio- Introduction to DFD Data Flow Diagraming... 2 1.1 In-Lab... 3 1.1.1 In-Lab Materials... 3 1.1.2 In-Lab Instructions... 3 2 Getting started: Let s decompose
Key Ideas. OO Analysis and Design Foundation. Objectives. Adapted from slides 2005 John Wiley & Sons, Inc.
 Slide 1 Information Systems Development COMM005 (CSM03) Autumn Semester 2009 Dr. Jonathan Y. Clark Email: j.y.clark@surrey.ac.uk Course Website: www.computing.surrey.ac.uk/courses/csm03/isdmain.htm Course
Slide 1 Information Systems Development COMM005 (CSM03) Autumn Semester 2009 Dr. Jonathan Y. Clark Email: j.y.clark@surrey.ac.uk Course Website: www.computing.surrey.ac.uk/courses/csm03/isdmain.htm Course
3Lesson 3: Web Project Management Fundamentals Objectives
 3Lesson 3: Web Project Management Fundamentals Objectives By the end of this lesson, you will be able to: 1.1.11: Determine site project implementation factors (includes stakeholder input, time frame,
3Lesson 3: Web Project Management Fundamentals Objectives By the end of this lesson, you will be able to: 1.1.11: Determine site project implementation factors (includes stakeholder input, time frame,
Chapter 10. Database System Development Lifecycle
 Chapter 10 Database System Development Lifecycle Chapter 10 - Objectives Main components of an information system. Main stages of database system development lifecycle. Main phases of database design:
Chapter 10 Database System Development Lifecycle Chapter 10 - Objectives Main components of an information system. Main stages of database system development lifecycle. Main phases of database design:
The Development of Information Systems
 Instructor: Kevin Robertson The Development of Information Systems Lecture Outline 12-1 Principles and Learning Objectives Understand the process used by organizations to manage the development of information
Instructor: Kevin Robertson The Development of Information Systems Lecture Outline 12-1 Principles and Learning Objectives Understand the process used by organizations to manage the development of information
Fundamental Shift: A LOOK INSIDE THE RISING ROLE OF IT IN PHYSICAL ACCESS CONTROL
 Fundamental Shift: A LOOK INSIDE THE RISING ROLE OF IT IN PHYSICAL ACCESS CONTROL Shifting budgets and responsibilities require IT and physical security teams to consider fundamental change in day-to-day
Fundamental Shift: A LOOK INSIDE THE RISING ROLE OF IT IN PHYSICAL ACCESS CONTROL Shifting budgets and responsibilities require IT and physical security teams to consider fundamental change in day-to-day
Scenario-Based Analysis. Scenario-Based Analysis (example) Form analysis
 Scenario-Based Analysis Scenario-Based Analysis (example) Provides a more user-oriented view perspective on the design and development of an interactive system. The defining property of a scenario is that
Scenario-Based Analysis Scenario-Based Analysis (example) Provides a more user-oriented view perspective on the design and development of an interactive system. The defining property of a scenario is that
How Cisco IT Improved Development Processes with a New Operating Model
 How Cisco IT Improved Development Processes with a New Operating Model New way to manage IT investments supports innovation, improved architecture, and stronger process standards for Cisco IT By Patrick
How Cisco IT Improved Development Processes with a New Operating Model New way to manage IT investments supports innovation, improved architecture, and stronger process standards for Cisco IT By Patrick
Candidate Profile for the Position of Vice President, Education and Certification
 Candidate Profile for the Position of Vice President, Education and Certification * * * * This profile provides information about the National Automatic Merchandising Association and the position requirements
Candidate Profile for the Position of Vice President, Education and Certification * * * * This profile provides information about the National Automatic Merchandising Association and the position requirements
Business Analysis for Practitioners - Requirements Elicitation and Analysis (Domain 3)
 Business Analysis for Practitioners - Requirements Elicitation and Analysis (Domain 3) COURSE STRUCTURE Introduction to Business Analysis Module 1 Needs Assessment Module 2 Business Analysis Planning Module
Business Analysis for Practitioners - Requirements Elicitation and Analysis (Domain 3) COURSE STRUCTURE Introduction to Business Analysis Module 1 Needs Assessment Module 2 Business Analysis Planning Module
Advanced Security Tester Course Outline
 Advanced Security Tester Course Outline General Description This course provides test engineers with advanced skills in security test analysis, design, and execution. In a hands-on, interactive fashion,
Advanced Security Tester Course Outline General Description This course provides test engineers with advanced skills in security test analysis, design, and execution. In a hands-on, interactive fashion,
Evolution of the ICT Field: New Requirements to Specialists
 Lumen 2/2017 ARTICLE Evolution of the ICT Field: New Requirements to Specialists Vladimir Ryabov, PhD, Principal Lecturer, School of Business and Culture, Lapland UAS Tuomo Lindholm, MBA, Senior Lecturer,
Lumen 2/2017 ARTICLE Evolution of the ICT Field: New Requirements to Specialists Vladimir Ryabov, PhD, Principal Lecturer, School of Business and Culture, Lapland UAS Tuomo Lindholm, MBA, Senior Lecturer,
Object Oriented Analysis is popular approach that sees a system from the viewpoint of the objects themselves as they function and interact
 Chapter 6 Object Oriented Analysis is popular approach that sees a system from the viewpoint of the objects themselves as they function and interact Object-oriented (O-O) analysis describes an information
Chapter 6 Object Oriented Analysis is popular approach that sees a system from the viewpoint of the objects themselves as they function and interact Object-oriented (O-O) analysis describes an information
SYMANTEC: SECURITY ADVISORY SERVICES. Symantec Security Advisory Services The World Leader in Information Security
 SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
SOFTWARE ENGINEERING. Lecture 6. By: Latifa ALrashed. Networks and Communication Department
 1 SOFTWARE ENGINEERING Networks and Communication Department Lecture 6 By: Latifa ALrashed Outline q q q q q q q q Define the concept of the software life cycle in software engineering. Identify the system
1 SOFTWARE ENGINEERING Networks and Communication Department Lecture 6 By: Latifa ALrashed Outline q q q q q q q q Define the concept of the software life cycle in software engineering. Identify the system
MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question.
 Exam Name MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. 1) A process has a: 1) A) pronoun label B) noun phrase label C) verb phrase label D) adjective
Exam Name MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. 1) A process has a: 1) A) pronoun label B) noun phrase label C) verb phrase label D) adjective
Slide 1 Welcome to Fundamentals of Health Workflow Process Analysis and Redesign: Process Mapping: Gane-Sarson Notation. This is Lecture d.
 WORKFLOW ANALYSIS Audio Transcript Component 10 Unit 3 Lecture D Fundamentals of Health Workflow Process Analysis & Redesign Interpreting and Creating Process Diagrams Process Mapping Gane-Sarson Notation
WORKFLOW ANALYSIS Audio Transcript Component 10 Unit 3 Lecture D Fundamentals of Health Workflow Process Analysis & Redesign Interpreting and Creating Process Diagrams Process Mapping Gane-Sarson Notation
The Information Technology Program (ITS) Contents What is Information Technology?... 2
 The Information Technology Program (ITS) Contents What is Information Technology?... 2 Program Objectives... 2 ITS Program Major... 3 Web Design & Development Sequence... 3 The Senior Sequence... 3 ITS
The Information Technology Program (ITS) Contents What is Information Technology?... 2 Program Objectives... 2 ITS Program Major... 3 Web Design & Development Sequence... 3 The Senior Sequence... 3 ITS
Full file at https://fratstock.eu
 TEACHING TIPS Chapter 2 SYSTEMS TECHNIQUES AND DOCUMENTATION I normally introduce flowcharting symbols with simple examples on the board. I first introduce a very simple manual flowchart involving only
TEACHING TIPS Chapter 2 SYSTEMS TECHNIQUES AND DOCUMENTATION I normally introduce flowcharting symbols with simple examples on the board. I first introduce a very simple manual flowchart involving only
Requirement Analysis
 Requirement Analysis Requirements Analysis & Specification Objective: determine what the system must do to solve the problem (without describing how) Done by Analyst (also called Requirements Analyst)
Requirement Analysis Requirements Analysis & Specification Objective: determine what the system must do to solve the problem (without describing how) Done by Analyst (also called Requirements Analyst)
Principles of Information Security, Fourth Edition. Chapter 1 Introduction to Information Security
 Principles of Information Security, Fourth Edition Chapter 1 Introduction to Information Security Introduction Information security: a well-informed sense of assurance that the information risks and controls
Principles of Information Security, Fourth Edition Chapter 1 Introduction to Information Security Introduction Information security: a well-informed sense of assurance that the information risks and controls
Certified Manager Certification
 Certified Manager Certification Get Trained Get Certified Get Recognized www.hr-pulse.org In Partnership With HR Pulse has the Learning Solutions to Empower Your People & Grow Your Business About ICPM
Certified Manager Certification Get Trained Get Certified Get Recognized www.hr-pulse.org In Partnership With HR Pulse has the Learning Solutions to Empower Your People & Grow Your Business About ICPM
INTRODUCTORY INFORMATION TECHNOLOGY CREATING ENTERPRISE APPLICATIONS. Faramarz Hendessi
 INTRODUCTORY INFORMATION TECHNOLOGY CREATING ENTERPRISE APPLICATIONS Faramarz Hendessi INTRODUCTORY INFORMATION TECHNOLOGY Lecture 10 Fall 2010 Isfahan University of technology Dr. Faramarz Hendessi 2
INTRODUCTORY INFORMATION TECHNOLOGY CREATING ENTERPRISE APPLICATIONS Faramarz Hendessi INTRODUCTORY INFORMATION TECHNOLOGY Lecture 10 Fall 2010 Isfahan University of technology Dr. Faramarz Hendessi 2
The Secret Sauce of ILM
 The Secret Sauce of ILM the ILM Assessment Core LeRoy Budnik, Knowledge Transfer Abstract The Secret Sauce of ILM Assessment Professional Services and internal consulting figure prominently in the success
The Secret Sauce of ILM the ILM Assessment Core LeRoy Budnik, Knowledge Transfer Abstract The Secret Sauce of ILM Assessment Professional Services and internal consulting figure prominently in the success
How to choose the right Data Governance resources. by First San Francisco Partners
 How to choose the right Data Governance resources by First San Francisco Partners 2 Your organization is unique. It has its own strengths, opportunities, products, services and customer base. Your culture
How to choose the right Data Governance resources by First San Francisco Partners 2 Your organization is unique. It has its own strengths, opportunities, products, services and customer base. Your culture
Introduction to Software Engineering
 Introduction to Software Engineering Gérald Monard Ecole GDR CORREL - April 16, 2013 www.monard.info Bibliography Software Engineering, 9th ed. (I. Sommerville, 2010, Pearson) Conduite de projets informatiques,
Introduction to Software Engineering Gérald Monard Ecole GDR CORREL - April 16, 2013 www.monard.info Bibliography Software Engineering, 9th ed. (I. Sommerville, 2010, Pearson) Conduite de projets informatiques,
Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS
 Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Continual disclosed and reported
Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Continual disclosed and reported
What s New in Spotfire DXP 1.1. Spotfire Product Management January 2007
 What s New in Spotfire DXP 1.1 Spotfire Product Management January 2007 Spotfire DXP Version 1.1 This document highlights the new capabilities planned for release in version 1.1 of Spotfire DXP. In this
What s New in Spotfire DXP 1.1 Spotfire Product Management January 2007 Spotfire DXP Version 1.1 This document highlights the new capabilities planned for release in version 1.1 of Spotfire DXP. In this
Modelling as a Communication Tool: Introduction to Process Modelling. Modelling. Simplification in modelling. Representation in modelling
 CSE104 - Information Systems 1 Modelling as a Communication Tool: Introduction to Process Modelling The requirements specification document Must be communicated to key stakeholders Should contain: Functions
CSE104 - Information Systems 1 Modelling as a Communication Tool: Introduction to Process Modelling The requirements specification document Must be communicated to key stakeholders Should contain: Functions
DOMAIN ENGINEERING OF COMPONENTS
 4-02-55 INFORMATION MANAGEMENT: STRATEGY, SYSTEMS, AND TECHNOLOGIES DOMAIN ENGINEERING OF COMPONENTS Carma McClure INSIDE Definition of Components; Component-Based Development; Reuse Processes; Domain
4-02-55 INFORMATION MANAGEMENT: STRATEGY, SYSTEMS, AND TECHNOLOGIES DOMAIN ENGINEERING OF COMPONENTS Carma McClure INSIDE Definition of Components; Component-Based Development; Reuse Processes; Domain
PROFESSIONAL DEVELOPMENT COURSES. May - December Institute for Professional Excellence
 PROFESSIONAL DEVELOPMENT COURSES May - December 2018 Institute for Professional Excellence INSTITUTE FOR PROFESSIONAL EXCELLENCE (IPEx) Training to Advance Your Career Davenport University s IPEx offers
PROFESSIONAL DEVELOPMENT COURSES May - December 2018 Institute for Professional Excellence INSTITUTE FOR PROFESSIONAL EXCELLENCE (IPEx) Training to Advance Your Career Davenport University s IPEx offers
Choosing the Right Usability Tool (the right technique for the right problem)
 Choosing the Right Usability Tool (the right technique for the right problem) User Friendly 2005 December 18, Shanghai Whitney Quesenbery Whitney Interactive Design www.wqusability.com Daniel Szuc Apogee
Choosing the Right Usability Tool (the right technique for the right problem) User Friendly 2005 December 18, Shanghai Whitney Quesenbery Whitney Interactive Design www.wqusability.com Daniel Szuc Apogee
Sample Exam Syllabus
 ISTQB Foundation Level 2011 Syllabus Version 2.9 Release Date: December 16th, 2017. Version.2.9 Page 1 of 46 Dec 16th, 2017 Copyright 2017 (hereinafter called ISTQB ). All rights reserved. The authors
ISTQB Foundation Level 2011 Syllabus Version 2.9 Release Date: December 16th, 2017. Version.2.9 Page 1 of 46 Dec 16th, 2017 Copyright 2017 (hereinafter called ISTQB ). All rights reserved. The authors
Working with Health IT Systems is available under a Creative Commons Attribution-NonCommercial- ShareAlike 3.0 Unported license.
 Working with Health IT Systems is available under a Creative Commons Attribution-NonCommercial- ShareAlike 3.0 Unported license. Johns Hopkins University. Welcome to the Fundamentals of Health Workflow
Working with Health IT Systems is available under a Creative Commons Attribution-NonCommercial- ShareAlike 3.0 Unported license. Johns Hopkins University. Welcome to the Fundamentals of Health Workflow
SOFTWARE ENGINEERING : A MCQ BOOK CODE : RBMCQ0602. Second Edition
 SOFTWARE ENGINEERING : A MCQ BOOK CODE : RBMCQ0602 Second Edition S/W Engg. Fundamental 1) Which phase of the SDLC are information needs identified? A. preliminary investigation B. system analysis C. system
SOFTWARE ENGINEERING : A MCQ BOOK CODE : RBMCQ0602 Second Edition S/W Engg. Fundamental 1) Which phase of the SDLC are information needs identified? A. preliminary investigation B. system analysis C. system
Meaning & Concepts of Databases
 27 th August 2015 Unit 1 Objective Meaning & Concepts of Databases Learning outcome Students will appreciate conceptual development of Databases Section 1: What is a Database & Applications Section 2:
27 th August 2015 Unit 1 Objective Meaning & Concepts of Databases Learning outcome Students will appreciate conceptual development of Databases Section 1: What is a Database & Applications Section 2:
Article II - Standards Section V - Continuing Education Requirements
 Article II - Standards Section V - Continuing Education Requirements 2.5.1 CONTINUING PROFESSIONAL EDUCATION Internal auditors are responsible for maintaining their knowledge and skills. They should update
Article II - Standards Section V - Continuing Education Requirements 2.5.1 CONTINUING PROFESSIONAL EDUCATION Internal auditors are responsible for maintaining their knowledge and skills. They should update
Process Modeling. Wei-Tsong Wang 1 IIM, NCKU
 Process Modeling Based on Chapter 9 of Whitten, Bentley, and Dittman: Systems Analysis and Design for the Global Enterprise (7th Ed). McGraw Hill. 2007 Wei-Tsong Wang 1 IIM, NCKU 2 Models: Logical and
Process Modeling Based on Chapter 9 of Whitten, Bentley, and Dittman: Systems Analysis and Design for the Global Enterprise (7th Ed). McGraw Hill. 2007 Wei-Tsong Wang 1 IIM, NCKU 2 Models: Logical and
Project Management Professional (PMP) Certificate
 Project Management Professional (PMP) Certificate www.hr-pulse.org What is PMP Certificate HR Pulse has the Learning Solutions to Empower Your People & Grow Your Business Project Management is a professional
Project Management Professional (PMP) Certificate www.hr-pulse.org What is PMP Certificate HR Pulse has the Learning Solutions to Empower Your People & Grow Your Business Project Management is a professional
ICT-U CAMEROON, P.O. Box 526 Yaounde, Cameroon. Schools and Programs DETAILED ICT-U PROGRAMS AND CORRESPONDING CREDIT HOURS
 Website: http:// ICT-U CAMEROON, P.O. Box 526 Yaounde, Cameroon Schools and Programs DETAILED ICT-U PROGRAMS AND CORRESPONDING CREDIT HOURS Important note on English as a Second Language (ESL) and International
Website: http:// ICT-U CAMEROON, P.O. Box 526 Yaounde, Cameroon Schools and Programs DETAILED ICT-U PROGRAMS AND CORRESPONDING CREDIT HOURS Important note on English as a Second Language (ESL) and International
QM Chapter 1 Database Fundamentals Version 10 th Ed. Prepared by Dr Kamel Rouibah / Dept QM & IS
 QM 433 - Chapter 1 Database Fundamentals Version 10 th Ed Prepared by Dr Kamel Rouibah / Dept QM & IS www.cba.edu.kw/krouibah Dr K. Rouibah / dept QM & IS Chapter 1 (433) Database fundamentals 1 Objectives
QM 433 - Chapter 1 Database Fundamentals Version 10 th Ed Prepared by Dr Kamel Rouibah / Dept QM & IS www.cba.edu.kw/krouibah Dr K. Rouibah / dept QM & IS Chapter 1 (433) Database fundamentals 1 Objectives
Losing Control: Controls, Risks, Governance, and Stewardship of Enterprise Data
 Losing Control: Controls, Risks, Governance, and Stewardship of Enterprise Data an eprentise white paper tel: 407.591.4950 toll-free: 1.888.943.5363 web: www.eprentise.com Author: Helene Abrams www.eprentise.com
Losing Control: Controls, Risks, Governance, and Stewardship of Enterprise Data an eprentise white paper tel: 407.591.4950 toll-free: 1.888.943.5363 web: www.eprentise.com Author: Helene Abrams www.eprentise.com
High School Course Guide Business Management & Administration
 88610 Business Computer Information Management I (R) 1 credit Gr: 9-12 Prerequisite: Touch Systems Data Entry Keyboarding Recommended Description: Students will gain the necessary skills to make a successful
88610 Business Computer Information Management I (R) 1 credit Gr: 9-12 Prerequisite: Touch Systems Data Entry Keyboarding Recommended Description: Students will gain the necessary skills to make a successful
SE 2730 Final Review
 SE 2730 Final Review 1. Introduction 1) What is software: programs, associated documentations and data 2) Three types of software products: generic, custom, semi-custom Why is semi-custom product more
SE 2730 Final Review 1. Introduction 1) What is software: programs, associated documentations and data 2) Three types of software products: generic, custom, semi-custom Why is semi-custom product more
Certified Business Analysis Professional (CBAP )
 Certified Business Analysis Professional (CBAP ) 3 Days Classroom Training PHILIPPINES :: MALAYSIA :: VIETNAM :: SINGAPORE :: INDIA Content Certified Business Analysis Professional - (CBAP ) Introduction
Certified Business Analysis Professional (CBAP ) 3 Days Classroom Training PHILIPPINES :: MALAYSIA :: VIETNAM :: SINGAPORE :: INDIA Content Certified Business Analysis Professional - (CBAP ) Introduction
System Development Life Cycle Methods/Approaches/Models
 Week 11 System Development Life Cycle Methods/Approaches/Models Approaches to System Development System Development Life Cycle Methods/Approaches/Models Waterfall Model Prototype Model Spiral Model Extreme
Week 11 System Development Life Cycle Methods/Approaches/Models Approaches to System Development System Development Life Cycle Methods/Approaches/Models Waterfall Model Prototype Model Spiral Model Extreme
BCS THE CHARTERED INSTITUTE FOR IT. BCS HIGHER EDUCATION QUALIFICATIONS BCS Level 4 Certificate in IT INFORMATION SYSTEMS
 BCS THE CHARTERED INSTITUTE FOR IT BCS HIGHER EDUCATION QUALIFICATIONS BCS Level 4 Certificate in IT INFORMATION SYSTEMS Tuesday 27 th September 2016 - Afternoon Time: TWO hours Section A and Section B
BCS THE CHARTERED INSTITUTE FOR IT BCS HIGHER EDUCATION QUALIFICATIONS BCS Level 4 Certificate in IT INFORMATION SYSTEMS Tuesday 27 th September 2016 - Afternoon Time: TWO hours Section A and Section B
Progress Report. Object-Oriented Software Development: Requirements elicitation (ch. 4) and analysis (ch. 5) Object-oriented software development
 Progress Report Object-Oriented Software Development: Requirements elicitation (ch. 4) and analysis (ch. 5) CS 4354 Summer II 2014 Jill Seaman So far we have learned about the tools used in object-oriented
Progress Report Object-Oriented Software Development: Requirements elicitation (ch. 4) and analysis (ch. 5) CS 4354 Summer II 2014 Jill Seaman So far we have learned about the tools used in object-oriented
TASKS IN THE SYSTEMS DEVELOPMENT LIFE CYCLE
 SUMMARY AND REFERENCE ACTG 313 TASKS IN THE SYSTEMS DEVELOPMENT LIFE CYCLE PREPARATION PHASE 1. Identification of the Need for a new Information System 2. Initial Feasibility Study (always flawed because
SUMMARY AND REFERENCE ACTG 313 TASKS IN THE SYSTEMS DEVELOPMENT LIFE CYCLE PREPARATION PHASE 1. Identification of the Need for a new Information System 2. Initial Feasibility Study (always flawed because
C H A P T E R SYSTEM DESIGN
 C H A P T E R SYSTEM DESIGN Chapter Twelve Systems Design Describe the design phase in terms of your information building blocks. Identify and differentiate between several systems design strategies. Describe
C H A P T E R SYSTEM DESIGN Chapter Twelve Systems Design Describe the design phase in terms of your information building blocks. Identify and differentiate between several systems design strategies. Describe
Database Environment. Pearson Education 2009
 Chapter 2 Database Environment 1 Chapter 2 - Objectives Purpose of three-level database architecture. Contents of external, conceptual, and internal levels. Purpose of external/conceptual and conceptual/internal
Chapter 2 Database Environment 1 Chapter 2 - Objectives Purpose of three-level database architecture. Contents of external, conceptual, and internal levels. Purpose of external/conceptual and conceptual/internal
Data Process Modeling: Context Diagrams & Data Flow Diagrams (DFDs)
 Introduction Data Process Modeling: Context Diagrams & Data Flow Diagrams (DFDs) MIS 374 When designing/building an information system for an organization, you should consider the following questions regarding
Introduction Data Process Modeling: Context Diagrams & Data Flow Diagrams (DFDs) MIS 374 When designing/building an information system for an organization, you should consider the following questions regarding
Chapter : Analysis Modeling
 Chapter : Analysis Modeling Requirements Analysis Requirements analysis Specifies software s operational characteristics Indicates software's interface with other system elements Establishes constraints
Chapter : Analysis Modeling Requirements Analysis Requirements analysis Specifies software s operational characteristics Indicates software's interface with other system elements Establishes constraints
Survey of Research Data Management Practices at the University of Pretoria
 Survey of Research Data Management Practices at the University of Pretoria Undertaken by the Department of Library Services in order to improve research practices at the University Unisa Library Open Access
Survey of Research Data Management Practices at the University of Pretoria Undertaken by the Department of Library Services in order to improve research practices at the University Unisa Library Open Access
EXAM PREPARATION GUIDE
 EXAM PREPARATION GUIDE PECB Certified ISO 21500 Lead Project Manager The objective of the PECB Certified ISO 21500 Lead Project Manager examination is to ensure that the candidate has the knowledge and
EXAM PREPARATION GUIDE PECB Certified ISO 21500 Lead Project Manager The objective of the PECB Certified ISO 21500 Lead Project Manager examination is to ensure that the candidate has the knowledge and
FAQ: Database Development and Management
 Question 1: Are normalization rules followed exclusively in the real world? Answer 1: Unfortunately, the answer to this question is no. Database design and development do not have hard and fast rules,
Question 1: Are normalization rules followed exclusively in the real world? Answer 1: Unfortunately, the answer to this question is no. Database design and development do not have hard and fast rules,
The Web Service Sample
 The Web Service Sample Catapulse Pacitic Bank The Rational Unified Process is a roadmap for engineering a piece of software. It is flexible and scalable enough to be applied to projects of varying sizes.
The Web Service Sample Catapulse Pacitic Bank The Rational Unified Process is a roadmap for engineering a piece of software. It is flexible and scalable enough to be applied to projects of varying sizes.
Design Engineering. Dr. Marouane Kessentini Department of Computer Science
 Design Engineering Dr. Marouane Kessentini Department of Computer Science 1 Design Starts mostly from/with requirements (evolving mostly from functionalities and other non functional characteristics) How
Design Engineering Dr. Marouane Kessentini Department of Computer Science 1 Design Starts mostly from/with requirements (evolving mostly from functionalities and other non functional characteristics) How
Systems Analysis & Design
 Systems Analysis & Design Dr. Ahmed Lawgali Ahmed.lawgali@uob.edu.ly Slide 1 Systems Analysis & Design Course Textbook: Systems Analysis and Design With UML 2.0 An Object-Oriented Approach, Second Edition
Systems Analysis & Design Dr. Ahmed Lawgali Ahmed.lawgali@uob.edu.ly Slide 1 Systems Analysis & Design Course Textbook: Systems Analysis and Design With UML 2.0 An Object-Oriented Approach, Second Edition
CHAPTER 6 DATABASE MANAGEMENT SYSTEMS
 CHAPTER 6 DATABASE MANAGEMENT SYSTEMS Management Information Systems, 10 th edition, By Raymond McLeod, Jr. and George P. Schell 2007, Prentice Hall, Inc. 1 Learning Objectives Understand the hierarchy
CHAPTER 6 DATABASE MANAGEMENT SYSTEMS Management Information Systems, 10 th edition, By Raymond McLeod, Jr. and George P. Schell 2007, Prentice Hall, Inc. 1 Learning Objectives Understand the hierarchy
Bachelor of Design (Interior Design)
 Course information for Bachelor of Design (Interior Design) Course Number HE20501 - Bachelor of Design (Interior Design) Locations Design Centre, Enmore Course Design The Bachelor of Design (Interior Design)
Course information for Bachelor of Design (Interior Design) Course Number HE20501 - Bachelor of Design (Interior Design) Locations Design Centre, Enmore Course Design The Bachelor of Design (Interior Design)
Langara College Spring archived
 1 of 7 10/23/07 2:09 PM COMPUTING SCIENCE AND INFORMATION SYSTEMS DEPARTMENT COMPUTING SCIENCE AND INFORMATION SYSTEMS 1300 Systems Analysis & Design (3.0 credits) COURSE OUTLINE Spring 2008 Section 088
1 of 7 10/23/07 2:09 PM COMPUTING SCIENCE AND INFORMATION SYSTEMS DEPARTMENT COMPUTING SCIENCE AND INFORMATION SYSTEMS 1300 Systems Analysis & Design (3.0 credits) COURSE OUTLINE Spring 2008 Section 088
Enterprise Architecture Method
 OIO Enterprise Introduction to the OIO Enterprise Method (OIO ) Version 1.0 and X1. X2. A1. -related challenges A3. Method Foundation A5. Vision, Goals and Strategies B1. Objects B3. Services B5. UseCases
OIO Enterprise Introduction to the OIO Enterprise Method (OIO ) Version 1.0 and X1. X2. A1. -related challenges A3. Method Foundation A5. Vision, Goals and Strategies B1. Objects B3. Services B5. UseCases
ERP/CRM System Implementation Methodology
 ERP/CRM System Implementation Methodology Prepared by Admiral Consulting Group Date Submitted May 27, 2016 TABLE OF CONTENTS Implementation Methodology... 3 1.1. Analysis (Solution Envisioning) Phase...
ERP/CRM System Implementation Methodology Prepared by Admiral Consulting Group Date Submitted May 27, 2016 TABLE OF CONTENTS Implementation Methodology... 3 1.1. Analysis (Solution Envisioning) Phase...
