SQL Server Database Provisioning Report. Survey on database provisioning requirements among SQL Server Professionals
|
|
|
- Ezra James
- 6 years ago
- Views:
Transcription
1 SQL Server Database Provisioning Report Survey on database provisioning requirements among SQL Server Professionals
2 Foreword Waiting until the point of release to see how our software behaves is a key cause of chaotic or even catastrophic software releases. Establishing production-like environments with realistic load and data sets for use in development and testing has long been a challenge for organizations. The need to bake quality in, by ensuring realistic configurations and data sets are shifted left, has never been higher, and the DevOps movement recognizes that. Our goal is to ensure that Development and QA are routinely integrating the code with production-like environments at increasingly frequent intervals " In other words, we will only accept development work as done when it can be successfully built, deployed and confirmed that it runs as expected in a production-like environment DevOps Handbook Kim et al. Database provisioning carries its own challenges, with its own characteristics which have not commonly been addressed by provisioning toolsets. Some of these include concerns around data security, regulatory compliance, and internal infrastructure such as storage space. This report seeks to identify how organizations currently provision databases, and to assess the importance of provisioning requirements.
3 Key Findings Over 460 SQL Server professionals that showed interest in Redgate's new provisioning tool SQL Clone participated in the survey. Respondents represented a wide range of job roles from a variety of industries. Among the key findings are: 72% of respondents provision a copy of production that is used in a non-production environment (i.e. Dev / Test / QA). Only 28% of respondents always modify the data in some way before it reaches a non-production environment. 63% of organizations have provisioning controlled by the DBA. Only 29% allow individuals to self-serve. 54% of organizations provision weekly or more often with 28% provisioning daily. 83% of respondents agreed or strongly agreed that it is desirable to use production data in development and testing. The main factors restricting use of production data in non-production environments are data security, regulatory compliance, and storage concerns.
4 1 For databases in your day-to-day development environment (excluding QA, staging, etc.) do you? (multiple choice) 53% 89% Have a database that only you make use of Use a database shared with other developers As expected, more respondents work with databases in shared environments. However, many respondents also have databases that only they make use of. This varies slightly depending on job role. 59% of Application Developers have databases that only they use as opposed to DBAs (51%) or BI Developers (45%). Likewise DBAs and BI developers use shared databases more frequently (91% and 93%) than Application Developers 82%. 4
5 2 Where does the data in your development/test/qa environment come from? (multiple choice) A copy of production A modified copy of production (masked, subsetted, etc.) Synthesized Manually created 72% 50% 13% 28% Surprisingly, 72% of respondents work on data that comes directly from production in some instances in non-production environments. Astonishingly, 3 of respondents always use production data in non-production environments. This is most common for those that work in the media (50%), consulting (44%), and insurance (44%) industries. Surprisingly, 30% of healthcare organizations and 30% of government organizations that responded also always use data from production for development/test/qa purposes. Only 28% of respondents never use a direct copy of production. This was most common in healthcare organizations (44%), followed by finance (29%) and insurance (2). 5
6 3 Who controls the provisioning of databases? 63% DBAs 29% Self serve 8% Other The DBA controls the provisioning of databases in 63% of organizations, yet 29% of organizations allow teams to self-serve. We suspect that all those who can allow self-service do. Removing the need for ticketing, and thereby friction and dead time at the start of a development cycle, is self-evidently desirable. On the other hand, the specifics of database provisioning (file moves, swapping permission sets, managing disk space) may mean that the barriers to enabling self-service are high. For those that selected other, the provisioning was often owned by the DBA and a senior developer. 6
7 4 What is the highest frequency at which non-production databases are refreshed? Daily 28% Weekly 2 Monthly 19% Quarterly 12% Other 15% A lot of provisioning of non-production databases is done as requested or on demand, however 28% of respondents provision as frequently as daily while 54% provision weekly or more. Surprisingly, those who self-serve provision at a similar frequency to those who have provisioning managed by a DBA. Among those who provision daily, 28% provision databases 1TB of larger. 7
8 5 Do you agree or disagree with the following? It is desirable to use Production data in Dev and Test I am restricted from using Production data in dev and test Disagree Somewhat Disagree Somewhat Agree Strongly Agree Disagree Somewhat Disagree Somewhat Agree Strongly Agree 8% 9% 31% 52% 37% 22% 23% 17% 83% of respondents agree or strongly agree that it is desirable to use production data in development and testing. 7 of DBAs that responded agree with this as do 87% of Application Developers. This suggests Application Developers find having production data in development and test more desirable than DBAs. 40% of respondents are restricted from using production data in dev and test. 4 of those restricted do not use data in development/test/qa environments that has come directly from production. 8
9 6 If you're restricted from using production data, why is that? (multiple choice) Storage concerns Not enough hardware or licenses Data sensitivity Regulatory requirements We can't access the data as it's on clients' systems We don't have permission to use the data as it belongs to clients The environment is too complex to copy the databases Other 30% 10% 4 27% 14% Unsurprisingly, the main reason for restricting use of production data is due to data sensitivity and regulatory requirements. This reasoning was most frequent among finance (63%), government (62%), and healthcare (61%) organizations. With the GDPR, HIPAA, and other industry regulations, organizations are having to take more caution with how data is used and who has access to it. 9
10 7 What size is the biggest database in your dev or test environments? 39% 24% 9% 13% 12% 2% 1% <1GB 1-10GB GB 100GB - 1TB 1-2TB 2TB+ Don t know Storage concerns were also a key reason that use of production data is restricted. There are multiple reasons why this may be, including the cost of storage, the time it takes to manage storage, processes around requisitions, or not having enough storage. As expected, the majority of organizations have databases in development or test between 100GB and 1TB. Only 2 have databases 1TB or larger in development or test. Among those restricted from using production data due to storage concerns only, 41% have databases in development or test 1TB or larger and 3 of those provision daily. 10
11 8 What are your plans for Azure SQL Database in the next 12 months? What s Azure SQL Database? 1% No plans at all 53% Going to try it 2 Currently trying it 8% Have concrete plans to use it 4% Already using it 8% The adoption of Azure SQL Database is relatively low with only 8% of respondents using it and 4% with concrete plans to use it in the next 12 months. A large proportion are still looking at trying it. However, over 52% have no plans for Azure in the next 12 months. Of those organizations with storage concerns, 39% of respondents are currently using or trying Azure or have concrete plans to use it in the next 12 months. For those whose only concern was storage, 5 still had no plans to try out Azure SQL Database. 11
12 9 How important are the following? I can quickly refresh databases in non-production environments The data is up-to-date in non-production environments Sensitive data is masked or removed from Production copies 2% 5% 21% 15% 34% 20% 60% 47% 23% 23% 14% 3 Permissions are replaced in the Production copy Operational features (e.g. replication) are removed in copies Developers (and others) can self-serve copies of Production databases 1 24% 19% 22% 31% 29% 39% 30% 37% 24% 15% 15% Production databases can be copied on a schedule Access to provision and refresh databases copies is controlled 5% 24% 22% 47% 41% 23% 32% The most important provisioning operation to respondents was the ability to quickly refresh databases in non-production environments, with 83% rating this as very important or critical. Although the speed at which databases can be refreshed came out on top, surprisingly the ability for developers to self-serve is much lower with only 52% rating this as very important or critical. 19% felt this was not important at all. This indicates many organizations want some control over who can provision databases. This is reinforced by 73% of respondents rating controlling access to provision and refresh databases as very important or critical. 12
13 Survey Demographics Job title Application Developer BI Developer DBA Other 32% 9% 4 13% Industry Technology Finance Consulting Healthcare Insurance Government Media Other 21% 15% 13% 3% 30% To learn more about how Redgate can help your organization overcome some of the challenges of provisioning SQL Server databases visit
Faster Provisioning with SQL Clone
 Faster Provisioning with SQL Clone Redgate Software Grant Fritchey, Product Evangelist, Redgate Software Richard Macaskill, Product Manager, Redgate Software Get in touch Grant Fritchey scarydba.com grant@scarydba.com
Faster Provisioning with SQL Clone Redgate Software Grant Fritchey, Product Evangelist, Redgate Software Richard Macaskill, Product Manager, Redgate Software Get in touch Grant Fritchey scarydba.com grant@scarydba.com
Tripwire State of Container Security Report
 RESEARCH Tripwire State of Container Security Report January 2019 FOUNDATIONAL CONTROLS FOR SECURITY, COMPLIANCE & IT OPERATIONS As DevOps continues to drive increased use of containers, security teams
RESEARCH Tripwire State of Container Security Report January 2019 FOUNDATIONAL CONTROLS FOR SECURITY, COMPLIANCE & IT OPERATIONS As DevOps continues to drive increased use of containers, security teams
2018 Database DevOps Survey DBmaestro 1
 2018 Database DevOps Survey 2017 DBmaestro 1 Table of Contents Executive Summary... 3 What Percentage of IT Projects in Your Company Use a DevOps Approach?... 4 Integration of DBAs with DevOps Teams...
2018 Database DevOps Survey 2017 DBmaestro 1 Table of Contents Executive Summary... 3 What Percentage of IT Projects in Your Company Use a DevOps Approach?... 4 Integration of DBAs with DevOps Teams...
Create, protect, and manage databases for compliant DevOps
 Create, protect, and manage databases for compliant DevOps 26 years SQL Server data experience DBA, developer, manager, writer, speaker in a variety of companies and industries Founder, SQLServerCentral
Create, protect, and manage databases for compliant DevOps 26 years SQL Server data experience DBA, developer, manager, writer, speaker in a variety of companies and industries Founder, SQLServerCentral
The state of SQL Server monitoring
 The state of SQL Server monitoring Foreword What are the three biggest challenges facing teams who are responsible for monitoring and maintaining the performance of SQL Server? It s not the question we
The state of SQL Server monitoring Foreword What are the three biggest challenges facing teams who are responsible for monitoring and maintaining the performance of SQL Server? It s not the question we
CASE STUDY INSURANCE. Innovation at Moody's Analytics: A new approach to database provisioning using SQL Clone
 CASE STUDY INSURANCE Innovation at Moody's Analytics: A new approach to database provisioning using SQL Clone We already had a one-click process for database provisioning, but it was still taking too much
CASE STUDY INSURANCE Innovation at Moody's Analytics: A new approach to database provisioning using SQL Clone We already had a one-click process for database provisioning, but it was still taking too much
270 Total Nodes. 15 Nodes Down 2018 CONTAINER ADOPTION SURVEY. Clusters Running. AWS: us-east-1a 23 nodes. AWS: us-west-1a 62 nodes
 AWS: us-east-1a 23 nodes AWS: us-west-1a 62 nodes 20 Clusters Running 2018 CONTAINER ADOPTION SURVEY 6 lumes 270 Total Nodes 15 Nodes Down EXECUTIVE SUMMARY It s clear to most industry watchers that containers
AWS: us-east-1a 23 nodes AWS: us-west-1a 62 nodes 20 Clusters Running 2018 CONTAINER ADOPTION SURVEY 6 lumes 270 Total Nodes 15 Nodes Down EXECUTIVE SUMMARY It s clear to most industry watchers that containers
Trends in Next Generation Data Center Infrastructure. Summary Results January 2018
 Trends in Next Generation Data Center Infrastructure Survey Summary Between October 2017 and January 2018 Gatepoint Research invited selected executives to participate in a survey themed Trends in Next
Trends in Next Generation Data Center Infrastructure Survey Summary Between October 2017 and January 2018 Gatepoint Research invited selected executives to participate in a survey themed Trends in Next
Welcome. #sqlclone.
 Welcome #sqlclone sqlclonefeedback@red-gate.com What problems do we face when provisioning databases? Grant Fritchey Problem: Realistic Data Matching production volumes Mirroring data distribution of
Welcome #sqlclone sqlclonefeedback@red-gate.com What problems do we face when provisioning databases? Grant Fritchey Problem: Realistic Data Matching production volumes Mirroring data distribution of
CASE STUDY FINANCE. Republic Bank Streamlining database deployments with SQL Compare
 CASE STUDY FINANCE Republic Bank Streamlining database deployments with SQL Compare In a previous life, SQL Server database comparisons and deployments were run using manually compiled scripts. Headquartered
CASE STUDY FINANCE Republic Bank Streamlining database deployments with SQL Compare In a previous life, SQL Server database comparisons and deployments were run using manually compiled scripts. Headquartered
SD-WAN. Enabling the Enterprise to Overcome Barriers to Digital Transformation. An IDC InfoBrief Sponsored by Comcast
 SD-WAN Enabling the Enterprise to Overcome Barriers to Digital Transformation An IDC InfoBrief Sponsored by Comcast SD-WAN Is Emerging as an Important Driver of Business Results The increasing need for
SD-WAN Enabling the Enterprise to Overcome Barriers to Digital Transformation An IDC InfoBrief Sponsored by Comcast SD-WAN Is Emerging as an Important Driver of Business Results The increasing need for
Actifio Test Data Management
 Actifio Test Data Management Oracle MS SQL Faster Time To Market Start Release Time To Market (TTM) Finish Faster App Releases Faster Application Releases Faster TTM Increases Revenue Market Share Competitive
Actifio Test Data Management Oracle MS SQL Faster Time To Market Start Release Time To Market (TTM) Finish Faster App Releases Faster Application Releases Faster TTM Increases Revenue Market Share Competitive
Nicman Group Test Data Management 2.0 Leveraging Copy Data Virtualization Technology in QA for SQuAD. November 2016
 Nicman Group Test Data Management 2.0 Leveraging Copy Data Virtualization Technology in QA for SQuAD November 2016 Agenda Test Data Management 2.0 Leveraging Copy Data Virtualization Technology in QA Copy
Nicman Group Test Data Management 2.0 Leveraging Copy Data Virtualization Technology in QA for SQuAD November 2016 Agenda Test Data Management 2.0 Leveraging Copy Data Virtualization Technology in QA Copy
Good Technology State of BYOD Report
 Good Technology State of BYOD Report New data finds Finance and Healthcare industries dominate BYOD picture and that users are willing to pay device and service plan costs if they can use their own devices
Good Technology State of BYOD Report New data finds Finance and Healthcare industries dominate BYOD picture and that users are willing to pay device and service plan costs if they can use their own devices
THALES DATA THREAT REPORT
 2018 THALES DATA THREAT REPORT Trends in Encryption and Data Security INDIA EDITION EXECUTIVE SUMMARY #2018DataThreat THE TOPLINE Rising risks for sensitive data in India In India, as in the rest of the
2018 THALES DATA THREAT REPORT Trends in Encryption and Data Security INDIA EDITION EXECUTIVE SUMMARY #2018DataThreat THE TOPLINE Rising risks for sensitive data in India In India, as in the rest of the
WHO-ITU National ehealth Strategy Toolkit
 WHO-ITU National ehealth Strategy Toolkit Context and need for a National Strategy A landscape of isolated islands of small scale applications unable to effectively communicate and to share information
WHO-ITU National ehealth Strategy Toolkit Context and need for a National Strategy A landscape of isolated islands of small scale applications unable to effectively communicate and to share information
WHITE PAPER- Managed Services Security Practices
 WHITE PAPER- Managed Services Security Practices The information security practices outlined below provide standards expected of each staff member, consultant, or customer staff member granted access to
WHITE PAPER- Managed Services Security Practices The information security practices outlined below provide standards expected of each staff member, consultant, or customer staff member granted access to
` 2017 CloudEndure 1
 ` 2017 CloudEndure 1 Table of Contents Executive Summary... 3 Production Machines in the Organization... 4 Production Machines Using Disaster Recovery... 5 Workloads Primarily Covered by Disaster Recovery...
` 2017 CloudEndure 1 Table of Contents Executive Summary... 3 Production Machines in the Organization... 4 Production Machines Using Disaster Recovery... 5 Workloads Primarily Covered by Disaster Recovery...
How the GDPR will impact your software delivery processes
 How the GDPR will impact your software delivery processes About Redgate 230 17 202,000 2m Redgaters and counting years old customers SQL Server Central and Simple Talk users 91% of the Fortune 100 use
How the GDPR will impact your software delivery processes About Redgate 230 17 202,000 2m Redgaters and counting years old customers SQL Server Central and Simple Talk users 91% of the Fortune 100 use
KNOWLEDGE GAPS: AI AND MACHINE LEARNING IN CYBERSECURITY. Perspectives from U.S. and Japanese IT Professionals
 KNOWLEDGE GAPS: AI AND MACHINE LEARNING IN CYBERSECURITY Perspectives from U.S. and ese IT Professionals Executive Summary The use of artificial intelligence (AI) and machine learning (ML) in cybersecurity
KNOWLEDGE GAPS: AI AND MACHINE LEARNING IN CYBERSECURITY Perspectives from U.S. and ese IT Professionals Executive Summary The use of artificial intelligence (AI) and machine learning (ML) in cybersecurity
Healthcare Information and Management Systems Society HIMSS. U.S. Healthcare Industry Quarterly HIPAA Compliance Survey Results: Summer 2002
 Healthcare Information and Management Systems Society HIMSS U.S. Healthcare Industry Quarterly HIPAA Compliance Survey Results: Summer 2002 HIMSS / Phoenix Health Systems Healthcare Industry Quarterly
Healthcare Information and Management Systems Society HIMSS U.S. Healthcare Industry Quarterly HIPAA Compliance Survey Results: Summer 2002 HIMSS / Phoenix Health Systems Healthcare Industry Quarterly
Epicor ERP Cloud Services Specification Multi-Tenant and Dedicated Tenant Cloud Services (Updated July 31, 2017)
 Epicor ERP Cloud Services Specification Multi-Tenant and Dedicated Tenant Cloud Services (Updated July 31, 2017) GENERAL TERMS & INFORMATION A. GENERAL TERMS & DEFINITIONS 1. This Services Specification
Epicor ERP Cloud Services Specification Multi-Tenant and Dedicated Tenant Cloud Services (Updated July 31, 2017) GENERAL TERMS & INFORMATION A. GENERAL TERMS & DEFINITIONS 1. This Services Specification
Windocks Technical Backgrounder
 Windocks Technical Backgrounder Windocks is a port of Docker s open source to Windows used to modernize SQL Server workflows. Windocks is also an open, modern, data delivery solution that sources data
Windocks Technical Backgrounder Windocks is a port of Docker s open source to Windows used to modernize SQL Server workflows. Windocks is also an open, modern, data delivery solution that sources data
CASE STUDY RETAIL. Getting a complete view of SQL Server estates using SQL Monitor and Slack
 CASE STUDY RETAIL Getting a complete view of SQL Server estates using SQL Monitor and Slack We were administering our monitoring tools as much as we were our SQL Server estate. Mamas & Papas (M&P) is a
CASE STUDY RETAIL Getting a complete view of SQL Server estates using SQL Monitor and Slack We were administering our monitoring tools as much as we were our SQL Server estate. Mamas & Papas (M&P) is a
Ensuring Compliance with Data Privacy Directives using Virtual Databases
 Ensuring Compliance with Data Privacy Directives using Virtual Databases June 2017 Steve Karam, Director of Customer Education and Experience at Delphix Agenda 1 2 3 Ensure compliance to disparate data
Ensuring Compliance with Data Privacy Directives using Virtual Databases June 2017 Steve Karam, Director of Customer Education and Experience at Delphix Agenda 1 2 3 Ensure compliance to disparate data
COPYRIGHT 2018 NETSCOUT SYSTEMS, INC. 1
 COPYRIGHT 2018 NETSCOUT SYSTEMS, INC. 1 Worldwide Infrastructure Security Report Highlights Volume XIII C F Chui, Principal Security Technologist COPYRIGHT 2018 NETSCOUT SYSTEMS, INC. 2 Overview This presentation
COPYRIGHT 2018 NETSCOUT SYSTEMS, INC. 1 Worldwide Infrastructure Security Report Highlights Volume XIII C F Chui, Principal Security Technologist COPYRIGHT 2018 NETSCOUT SYSTEMS, INC. 2 Overview This presentation
2017 Trends in Security Metrics and Security Assurance Measurement Report A Survey of IT Security Professionals
 2017 Trends in Security Metrics and Security Assurance Measurement Report A Survey of IT Security Professionals Sponsored by Contents Introduction....3 Key Takeaways from the 2017 Report:....3 Security
2017 Trends in Security Metrics and Security Assurance Measurement Report A Survey of IT Security Professionals Sponsored by Contents Introduction....3 Key Takeaways from the 2017 Report:....3 Security
Village Software. Security Assessment Report
 Village Software Security Assessment Report Version 1.0 January 25, 2019 Prepared by Manuel Acevedo Helpful Village Security Assessment Report! 1 of! 11 Version 1.0 Table of Contents Executive Summary
Village Software Security Assessment Report Version 1.0 January 25, 2019 Prepared by Manuel Acevedo Helpful Village Security Assessment Report! 1 of! 11 Version 1.0 Table of Contents Executive Summary
IBM Resilient Incident Response Platform On Cloud
 Service Description IBM Resilient Incident Response Platform On Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized
Service Description IBM Resilient Incident Response Platform On Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized
Survey Results: Virtual Insecurity
 Best Practices SURVEY Survey Results: Virtual Insecurity May 2013 Executive Summary: Virtual Assets Could Bring Real Risk Virtualization technologies have reshaped how IT offers and delivers their services
Best Practices SURVEY Survey Results: Virtual Insecurity May 2013 Executive Summary: Virtual Assets Could Bring Real Risk Virtualization technologies have reshaped how IT offers and delivers their services
Building your Castle in the Cloud for Flash Memory
 Building your Castle in the Cloud for Flash Memory Effectively using flash in the cloud Steve Knipple Principal Consultant CloudShift Advisors Santa Clara, CA 1 Agenda Speaker Perspective State of Cloud
Building your Castle in the Cloud for Flash Memory Effectively using flash in the cloud Steve Knipple Principal Consultant CloudShift Advisors Santa Clara, CA 1 Agenda Speaker Perspective State of Cloud
October 2018 ISPA CYBER SECURITY SURVEY 2018
 ISPA CYBER SECURITY SURVEY 2018 October 2018 1 1 Executive summary... 3 1.1 Key findings... 3 1.2 Recommendations to Government... 5 2 Introduction... 5 3 Survey findings and analysis... 6 3.1 Investment
ISPA CYBER SECURITY SURVEY 2018 October 2018 1 1 Executive summary... 3 1.1 Key findings... 3 1.2 Recommendations to Government... 5 2 Introduction... 5 3 Survey findings and analysis... 6 3.1 Investment
Mid-Market Data Center Purchasing Drivers, Priorities and Barriers
 Mid-Market Data Center Purchasing Drivers, Priorities and Barriers Featuring Sophia Vargas, Forrester Research Inc. 30 May 2014 Introducing today s presenters: Matt Miszewski Senior Vice President of Sales
Mid-Market Data Center Purchasing Drivers, Priorities and Barriers Featuring Sophia Vargas, Forrester Research Inc. 30 May 2014 Introducing today s presenters: Matt Miszewski Senior Vice President of Sales
ACHIEVING FIFTH GENERATION CYBER SECURITY
 ACHIEVING FIFTH GENERATION CYBER SECURITY A Survey Research Report of IT and Security Professionals MARCH 2018 INTRODUCTION The pursuit of the highest level of cyber security is a top priority for IT and
ACHIEVING FIFTH GENERATION CYBER SECURITY A Survey Research Report of IT and Security Professionals MARCH 2018 INTRODUCTION The pursuit of the highest level of cyber security is a top priority for IT and
How Security Policy Orchestration Extends to Hybrid Cloud Platforms
 How Security Policy Orchestration Extends to Hybrid Cloud Platforms Reducing complexity also improves visibility when managing multi vendor, multi technology heterogeneous IT environments www.tufin.com
How Security Policy Orchestration Extends to Hybrid Cloud Platforms Reducing complexity also improves visibility when managing multi vendor, multi technology heterogeneous IT environments www.tufin.com
Balancing the pressures of a healthcare SQL Server DBA
 Balancing the pressures of a healthcare SQL Server DBA More than security, compliance and auditing? Working with SQL Server in the healthcare industry presents many unique challenges. The majority of these
Balancing the pressures of a healthcare SQL Server DBA More than security, compliance and auditing? Working with SQL Server in the healthcare industry presents many unique challenges. The majority of these
"SQL Monitor now makes the team look more professional."
 PRUDENTIAL CASE STUDY "SQL Monitor now makes the team look more professional." How Redgate s SQL Monitor makes monitoring a host of production servers easier, faster, and more professional 91% of Fortune
PRUDENTIAL CASE STUDY "SQL Monitor now makes the team look more professional." How Redgate s SQL Monitor makes monitoring a host of production servers easier, faster, and more professional 91% of Fortune
Cloud Computing. January 2012 CONTENT COMMUNITY CONVERSATION CONVERSION
 Cloud Computing January 2012 CONTENT COMMUNITY CONVERSATION CONVERSION Purpose and Methodology Survey Sample Field Work December 20, 2011 January 9, 2012 Total Respondents 554 Margin of Error +/- 4.2%
Cloud Computing January 2012 CONTENT COMMUNITY CONVERSATION CONVERSION Purpose and Methodology Survey Sample Field Work December 20, 2011 January 9, 2012 Total Respondents 554 Margin of Error +/- 4.2%
HITRUST ON THE CLOUD. Navigating Healthcare Compliance
 HITRUST ON THE CLOUD Navigating Healthcare Compliance As the demand for digital health solutions increases, the IT regulatory landscape continues to evolve. Staying ahead of new cybersecurity rules and
HITRUST ON THE CLOUD Navigating Healthcare Compliance As the demand for digital health solutions increases, the IT regulatory landscape continues to evolve. Staying ahead of new cybersecurity rules and
UBC - Advanced Research Computing Version 0.9 REDCap Terms of Use
 UBC - Advanced Research Computing 2018-11-05 Version 0.9 REDCap Terms of Use Version 0.9.0 REDCap Terms of Use 1. Introduction 1.1 Purpose This document explains the terms of use for the REDCap instance
UBC - Advanced Research Computing 2018-11-05 Version 0.9 REDCap Terms of Use Version 0.9.0 REDCap Terms of Use 1. Introduction 1.1 Purpose This document explains the terms of use for the REDCap instance
Database Continuous Delivery & Your Salvation!
 Database Continuous Delivery & Your Salvation! John Morehouse Database Architect Farm Credit Mid-America, Louisville, Kentucky john@jmorehouse.com @SqlRUs http://linkedin.com/in/sqlrus http://www.sqlrus.com
Database Continuous Delivery & Your Salvation! John Morehouse Database Architect Farm Credit Mid-America, Louisville, Kentucky john@jmorehouse.com @SqlRUs http://linkedin.com/in/sqlrus http://www.sqlrus.com
CORPORATE PERFORMANCE IMPROVEMENT DOES CLOUD MEAN THE PRIVATE DATA CENTER IS DEAD?
 CORPORATE PERFORMANCE IMPROVEMENT DOES CLOUD MEAN THE PRIVATE DATA CENTER IS DEAD? DOES CLOUD MEAN THE PRIVATE DATA CENTER IS DEAD? MASS MIGRATION: SHOULD ALL COMPANIES MOVE TO THE CLOUD? Achieving digital
CORPORATE PERFORMANCE IMPROVEMENT DOES CLOUD MEAN THE PRIVATE DATA CENTER IS DEAD? DOES CLOUD MEAN THE PRIVATE DATA CENTER IS DEAD? MASS MIGRATION: SHOULD ALL COMPANIES MOVE TO THE CLOUD? Achieving digital
CA Test Data Manager Key Scenarios
 WHITE PAPER APRIL 2016 CA Test Data Manager Key Scenarios Generate and secure all the data needed for rigorous testing, and provision it to highly distributed teams on demand. Muhammad Arif Application
WHITE PAPER APRIL 2016 CA Test Data Manager Key Scenarios Generate and secure all the data needed for rigorous testing, and provision it to highly distributed teams on demand. Muhammad Arif Application
Minimum Wage Survey Results Phase 2. Medicine Hat & District Statistical Breakout Of the Alberta Chamber of Commerce s Dataset
 Minimum Wage Survey Results Phase Medicine Hat & District Statistical Breakout Of the Alberta Chamber of Commerce s Dataset General Information A total of 9 businesses from the Medicine Hat & District
Minimum Wage Survey Results Phase Medicine Hat & District Statistical Breakout Of the Alberta Chamber of Commerce s Dataset General Information A total of 9 businesses from the Medicine Hat & District
Disaster Recovery and Mitigation: Is your business prepared when disaster hits?
 1 Disaster Recovery and Mitigation: Is your business prepared when disaster hits? 2 Our speaker today: Catherine Roy, Director of PMO at Hosting 15 years Project Management experience At HOSTING since
1 Disaster Recovery and Mitigation: Is your business prepared when disaster hits? 2 Our speaker today: Catherine Roy, Director of PMO at Hosting 15 years Project Management experience At HOSTING since
IT Optimization Trends. Summary Results January 2018
 IT Optimization Trends Survey Summary Between October 2017 and January 2018, Gatepoint Research invited selected executives to participate in a survey themed IT Optimization Trends. Candidates were invited
IT Optimization Trends Survey Summary Between October 2017 and January 2018, Gatepoint Research invited selected executives to participate in a survey themed IT Optimization Trends. Candidates were invited
Best Practices in Securing a Multicloud World
 Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
Consideration of Issues and Directives Federal Energy Regulatory Commission Order No. 791 June 2, 2014
 Federal Energy Regulatory Commission Order No. 791 June 2, 2014 67 and 76 67. For the reasons discussed below, the Commission concludes that the identify, assess, and correct language, as currently proposed
Federal Energy Regulatory Commission Order No. 791 June 2, 2014 67 and 76 67. For the reasons discussed below, the Commission concludes that the identify, assess, and correct language, as currently proposed
Top Trends in DBMS & DW
 Oracle Top Trends in DBMS & DW Noel Yuhanna Principal Analyst Forrester Research Trend #1: Proliferation of data Data doubles every 18-24 months for critical Apps, for some its every 6 months Terabyte
Oracle Top Trends in DBMS & DW Noel Yuhanna Principal Analyst Forrester Research Trend #1: Proliferation of data Data doubles every 18-24 months for critical Apps, for some its every 6 months Terabyte
Digital Analytics & Data Governance REPORT
 2018 Digital Analytics & Data Governance REPORT INTRODUCTION In this digital era, data analysis and governance should be a top priority fixed at the forefront of the data-driven professional s mind. But
2018 Digital Analytics & Data Governance REPORT INTRODUCTION In this digital era, data analysis and governance should be a top priority fixed at the forefront of the data-driven professional s mind. But
Chapter 3 `How a Storage Policy Works
 Chapter 3 `How a Storage Policy Works 32 - How a Storage Policy Works A Storage Policy defines the lifecycle management rules for all protected data. In its most basic form, a storage policy can be thought
Chapter 3 `How a Storage Policy Works 32 - How a Storage Policy Works A Storage Policy defines the lifecycle management rules for all protected data. In its most basic form, a storage policy can be thought
Daily, Weekly or Monthly Partitions? A discussion of several factors for this important decision
 Daily, Weekly or Monthly Partitions? A discussion of several factors for this important decision Copyright 2006 Mercury Consulting Published in July 2006 Conventions The following typographical conventions
Daily, Weekly or Monthly Partitions? A discussion of several factors for this important decision Copyright 2006 Mercury Consulting Published in July 2006 Conventions The following typographical conventions
Best Practices & Lesson Learned from 100+ ITGRC Implementations
 Best Practices & Lesson Learned from 100+ ITGRC Implementations Presenter: Vivek Shivananda CEO of Rsam Dec 3, 2010 ISACA -NY Chapter Copyright 2002 2010 Relational Security Corp. (dba Rsam) Agenda Overview
Best Practices & Lesson Learned from 100+ ITGRC Implementations Presenter: Vivek Shivananda CEO of Rsam Dec 3, 2010 ISACA -NY Chapter Copyright 2002 2010 Relational Security Corp. (dba Rsam) Agenda Overview
Skybox Security Vulnerability Management Survey 2012
 Skybox Security Vulnerability Management Survey 2012 Notice: This document contains a summary of the responses to a June 2012 survey of 100 medium to large enterprise organizations about their Vulnerability
Skybox Security Vulnerability Management Survey 2012 Notice: This document contains a summary of the responses to a June 2012 survey of 100 medium to large enterprise organizations about their Vulnerability
Automating Security Practices for the DevOps Revolution
 Automating Security Practices for the DevOps Revolution Hari Srinivasan Director Product Management, Cloud and Virtualization Security Qualys Inc. 1 Qualys, Inc. 2018 Agenda Transformation of today s IT
Automating Security Practices for the DevOps Revolution Hari Srinivasan Director Product Management, Cloud and Virtualization Security Qualys Inc. 1 Qualys, Inc. 2018 Agenda Transformation of today s IT
The Role of the Data Protection Officer
 The Role of the Data Protection Officer Adrian Ross LLB (Hons), MBA GRC Consultant IT Governance Ltd 28 July 2016 www.itgovernance.co.uk Introduction Adrian Ross GRC consultant Infrastructure services
The Role of the Data Protection Officer Adrian Ross LLB (Hons), MBA GRC Consultant IT Governance Ltd 28 July 2016 www.itgovernance.co.uk Introduction Adrian Ross GRC consultant Infrastructure services
Application Networking Trends
 HIGHLIGHTS OF ASN SURVEY RESULTS n The Futuriom Applications Specific Networking (ASN) Survey collected detailed feedback from 2 enterprise technology end users on the topic of networking cloud applications.
HIGHLIGHTS OF ASN SURVEY RESULTS n The Futuriom Applications Specific Networking (ASN) Survey collected detailed feedback from 2 enterprise technology end users on the topic of networking cloud applications.
Managed Security Services - Endpoint Managed Security on Cloud
 Services Description Managed Security Services - Endpoint Managed Security on Cloud The services described herein are governed by the terms and conditions of the agreement specified in the Order Document
Services Description Managed Security Services - Endpoint Managed Security on Cloud The services described herein are governed by the terms and conditions of the agreement specified in the Order Document
Please give me your feedback
 #HPEDiscover Please give me your feedback Session ID: B4385 Speaker: Aaron Spurlock Use the mobile app to complete a session survey 1. Access My schedule 2. Click on the session detail page 3. Scroll down
#HPEDiscover Please give me your feedback Session ID: B4385 Speaker: Aaron Spurlock Use the mobile app to complete a session survey 1. Access My schedule 2. Click on the session detail page 3. Scroll down
Cyber Risk Program Maturity Assessment UNDERSTAND AND MANAGE YOUR ORGANIZATION S CYBER RISK.
 Cyber Risk Program Maturity Assessment UNDERSTAND AND MANAGE YOUR ORGANIZATION S CYBER RISK. In today s escalating cyber risk environment, you need to make sure you re focused on the right priorities by
Cyber Risk Program Maturity Assessment UNDERSTAND AND MANAGE YOUR ORGANIZATION S CYBER RISK. In today s escalating cyber risk environment, you need to make sure you re focused on the right priorities by
INTRODUCTION. We would like to thank HelpSystems for supporting this unique research. We hope you will enjoy the report.
 2019 SIEM REPORT INTRODUCTION Security Information and Event Management (SIEM) is a powerful technology that allows security operations teams to collect, correlate and analyze log data from a variety of
2019 SIEM REPORT INTRODUCTION Security Information and Event Management (SIEM) is a powerful technology that allows security operations teams to collect, correlate and analyze log data from a variety of
Swedish bank overcomes regulatory hurdles and embraces the cloud to foster innovation
 Think Cloud Compliance Case Study Swedish bank overcomes regulatory hurdles and embraces the cloud to foster innovation Customer details : Collector Bank - Sweden 329 employees www.collector.se/en Banking
Think Cloud Compliance Case Study Swedish bank overcomes regulatory hurdles and embraces the cloud to foster innovation Customer details : Collector Bank - Sweden 329 employees www.collector.se/en Banking
Lafayette College Technology Clinic An Analysis of Communications at Lafayette College
 Lafayette College Technology Clinic An Analysis of Communications at Lafayette College -Midyear Report Spring 2018- 2 3 4 1. Meet The Team. 5 2. Charge........ 7 3. Clients...... 9 4. Project Significance..
Lafayette College Technology Clinic An Analysis of Communications at Lafayette College -Midyear Report Spring 2018- 2 3 4 1. Meet The Team. 5 2. Charge........ 7 3. Clients...... 9 4. Project Significance..
SANS 2017 SOC Survey. A Mile of Numbers and a Ton of Stats. Christopher Crowley All Rights Reserved All Wrongs Reversed
 SANS 2017 SOC Survey A Mile of Numbers and a Ton of Stats Christopher Crowley twitter: @CCrowMontance All Rights Reserved All Wrongs Reversed Two Webcasts There are two webcasts covering additional aspects
SANS 2017 SOC Survey A Mile of Numbers and a Ton of Stats Christopher Crowley twitter: @CCrowMontance All Rights Reserved All Wrongs Reversed Two Webcasts There are two webcasts covering additional aspects
Kanban-The Building Blocks. Ashish Chandra Senior Manager-SunGard
 Kanban-The Building Blocks Ashish Chandra Senior Manager-SunGard 1 Ashish Chandra BE-Computer Science & Engineering, MBA (Marketing & Finance) AKT, SPC, PMP, CSM, CSP, CSQA, ITIL V 1.3 Foundation Experienced
Kanban-The Building Blocks Ashish Chandra Senior Manager-SunGard 1 Ashish Chandra BE-Computer Science & Engineering, MBA (Marketing & Finance) AKT, SPC, PMP, CSM, CSP, CSQA, ITIL V 1.3 Foundation Experienced
REGULATED DOMESTIC ROAMING RESEARCH REPORT 2017
 REGULATED DOMESTIC ROAMING RESEARCH REPORT 2017 Researching the attitudes and perceptions of regional and remote Australians towards mobile providers and domestic roaming Vodafone Regional Roaming Research
REGULATED DOMESTIC ROAMING RESEARCH REPORT 2017 Researching the attitudes and perceptions of regional and remote Australians towards mobile providers and domestic roaming Vodafone Regional Roaming Research
Service Level Management and Service Level Agreements
 N e t w o r k I n d u s t r y S u r v e y Service Level Management and Service Level Agreements By Rick Blum, Senior Research Programs Manager The knowledge behind the network. H IGHLIGHTS Six out of ten
N e t w o r k I n d u s t r y S u r v e y Service Level Management and Service Level Agreements By Rick Blum, Senior Research Programs Manager The knowledge behind the network. H IGHLIGHTS Six out of ten
HOW IT INVESTMENT STRATEGIES HELP AND HINDER GOVERNMENT S ADOPTION OF CLOUD & AI
 HOW IT INVESTMENT STRATEGIES HELP AND HINDER GOVERNMENT S ADOPTION OF CLOUD & AI Federal agencies have made significant strides in adopting cloud technologies. But a new survey of government IT leaders
HOW IT INVESTMENT STRATEGIES HELP AND HINDER GOVERNMENT S ADOPTION OF CLOUD & AI Federal agencies have made significant strides in adopting cloud technologies. But a new survey of government IT leaders
General Data Protection Regulation
 & General Data Protection Regulation As of May 25th 2018, the EU General Data Protection Regulation (GDPR) will become applicable with the purpose to regulate the processing of personal data of the EU
& General Data Protection Regulation As of May 25th 2018, the EU General Data Protection Regulation (GDPR) will become applicable with the purpose to regulate the processing of personal data of the EU
Enterprise Permission Reporter
 Enterprise Permission Reporter Version 3.5.0.2 Manual NETsec 14 August2012 NETsec GmbH & Co.KG Schillingsstrasse 117 DE - 52355 Düren What is EPR?... 4 Installation... 5 Where do I install EPR?... 5 Store
Enterprise Permission Reporter Version 3.5.0.2 Manual NETsec 14 August2012 NETsec GmbH & Co.KG Schillingsstrasse 117 DE - 52355 Düren What is EPR?... 4 Installation... 5 Where do I install EPR?... 5 Store
CASE STUDY IT. Albumprinter Adopting Redgate DLM
 CASE STUDY IT Albumprinter Adopting Redgate DLM "Once the team saw they could deploy all their database changes error-free at the click of a button, with no more manual scripts, it spread by word of mouth.
CASE STUDY IT Albumprinter Adopting Redgate DLM "Once the team saw they could deploy all their database changes error-free at the click of a button, with no more manual scripts, it spread by word of mouth.
BACKUP AND RECOVERY OF A HIGHLY VIRTUALIZED ENVIRONMENT
 BACKUP AND RECOVERY OF A HIGHLY VIRTUALIZED ENVIRONMENT Featuring Industry Perspectives from The Enterprise Strategy Group (ESG) 24 January 2013 Jason Buffington (@Jbuff), ESG Senior Analyst, Data Protection
BACKUP AND RECOVERY OF A HIGHLY VIRTUALIZED ENVIRONMENT Featuring Industry Perspectives from The Enterprise Strategy Group (ESG) 24 January 2013 Jason Buffington (@Jbuff), ESG Senior Analyst, Data Protection
STREAMLINED CERTIFICATION PATHS
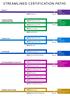 STREAMLINED CERTIFICATION PATHS MOBILITY 10 Mobility CLOUD PLATFORM & INFRASTRUCTURE Server 2016 Cloud Platform & Infrastructure Linux on Azure Cloud Platform PRODUCTIVITY Server 2016 Productivity Office
STREAMLINED CERTIFICATION PATHS MOBILITY 10 Mobility CLOUD PLATFORM & INFRASTRUCTURE Server 2016 Cloud Platform & Infrastructure Linux on Azure Cloud Platform PRODUCTIVITY Server 2016 Productivity Office
CLOUD TRENDS AND BEST PRACTICES
 2011 CLOUD TRENDS AND BEST PRACTICES Executive Summary Overview The 2011 Cloud Computing Trends and Best Practices Report was designed to identify both best practices and trends in cloud computing and
2011 CLOUD TRENDS AND BEST PRACTICES Executive Summary Overview The 2011 Cloud Computing Trends and Best Practices Report was designed to identify both best practices and trends in cloud computing and
MOBILE SECURITY 2017 SPOTLIGHT REPORT. Information Security PRESENTED BY. Group Partner
 MOBILE SECURITY 2017 SPOTLIGHT REPORT Group Partner Information Security PRESENTED BY OVERVIEW Security and privacy risks are on the rise with the proliferation of mobile devices and their increasing use
MOBILE SECURITY 2017 SPOTLIGHT REPORT Group Partner Information Security PRESENTED BY OVERVIEW Security and privacy risks are on the rise with the proliferation of mobile devices and their increasing use
Multicloud is the New Normal Cloud enables Digital Transformation (DX), but more clouds bring more challenges
 Multicloud is the New Normal Cloud enables Digital Transformation (DX), but more clouds bring more challenges An IDC InfoBrief, Sponsored by Cisco March 2018 EXECUTIVE SUMMARY Cloud is a key enabler of
Multicloud is the New Normal Cloud enables Digital Transformation (DX), but more clouds bring more challenges An IDC InfoBrief, Sponsored by Cisco March 2018 EXECUTIVE SUMMARY Cloud is a key enabler of
Gaps in Resources, Risk and Visibility Weaken Cybersecurity Posture
 February 2019 Challenging State of Vulnerability Management Today: Gaps in Resources, Risk and Visibility Weaken Cybersecurity Posture In the last two years, businesses and governments have seen data breaches
February 2019 Challenging State of Vulnerability Management Today: Gaps in Resources, Risk and Visibility Weaken Cybersecurity Posture In the last two years, businesses and governments have seen data breaches
Code of Ethics Certification 2018 CHECKLIST
 Code of Ethics Certification 2018 CHECKLIST Medical technology companies (both AdvaMed members and non-members) may participate in this certification program. The certification affirms that the company
Code of Ethics Certification 2018 CHECKLIST Medical technology companies (both AdvaMed members and non-members) may participate in this certification program. The certification affirms that the company
Application Information Lifecycle Management Control Both the Size of Your Data and the Cost of Managing It
 Application Information Lifecycle Management Control Both the Size of Your Data and the Cost of Managing It Data volume isn t just growing it s exploding. The amount of data housed in large data warehouses
Application Information Lifecycle Management Control Both the Size of Your Data and the Cost of Managing It Data volume isn t just growing it s exploding. The amount of data housed in large data warehouses
Microsoft Partner FAQ
 Microsoft Partner FAQ Topic: New role-based certifications and competencies Q. What is the new certification model? A. The model is based on three tiers of expertise: Fundamentals, Associate and Expert.
Microsoft Partner FAQ Topic: New role-based certifications and competencies Q. What is the new certification model? A. The model is based on three tiers of expertise: Fundamentals, Associate and Expert.
Research Report: Voice over Internet Protocol (VoIP)
 Research Report: Voice over Internet Protocol (VoIP) Statement Publication date: 26 July 2007 Contents Section Page 1 Executive Summary 1 2 Background and research objectives 3 3 Awareness of VoIP 5 4
Research Report: Voice over Internet Protocol (VoIP) Statement Publication date: 26 July 2007 Contents Section Page 1 Executive Summary 1 2 Background and research objectives 3 3 Awareness of VoIP 5 4
IT TRENDS REPORT 2016:
 IT TRENDS REPORT 2016: THE HYBRID IT EVOLUTION SINGAPORE WHAT WE COVER IN THE REPORT IT TRENDS REPORT 2016: THE HYBRID IT EVOLUTION Introduction Key Findings Recommendations Full Survey Results INTRODUCTION
IT TRENDS REPORT 2016: THE HYBRID IT EVOLUTION SINGAPORE WHAT WE COVER IN THE REPORT IT TRENDS REPORT 2016: THE HYBRID IT EVOLUTION Introduction Key Findings Recommendations Full Survey Results INTRODUCTION
Best Practices for Alert Tuning. This white paper will provide best practices for alert tuning to ensure two related outcomes:
 This white paper will provide best practices for alert tuning to ensure two related outcomes: 1. Monitoring is in place to catch critical conditions and alert the right people 2. Noise is reduced and people
This white paper will provide best practices for alert tuning to ensure two related outcomes: 1. Monitoring is in place to catch critical conditions and alert the right people 2. Noise is reduced and people
Windows 7 Done Right: From Migration to Implementation
 I D C E X E C U T I V E B R I E F Windows 7 Done Right: From Migration to Implementation Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com July 2010
I D C E X E C U T I V E B R I E F Windows 7 Done Right: From Migration to Implementation Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com July 2010
CASE STUDY FINANCE. Enhancing software development with SQL Monitor
 CASE STUDY FINANCE Enhancing software development with SQL Monitor We were using another SQL monitoring tool, but it wasn t providing us with the flexibility and features we needed. Founded in 2006, Xero
CASE STUDY FINANCE Enhancing software development with SQL Monitor We were using another SQL monitoring tool, but it wasn t providing us with the flexibility and features we needed. Founded in 2006, Xero
the steps that IS Services should take to ensure that this document is aligned with the SNH s KIMS and SNH s Change Requirement;
 Shaping the Future of IS and ICT in SNH: 2014-2019 SNH s IS/ICT Vision We will develop the ICT infrastructure to support the business needs of our customers. Our ICT infrastructure and IS/GIS solutions
Shaping the Future of IS and ICT in SNH: 2014-2019 SNH s IS/ICT Vision We will develop the ICT infrastructure to support the business needs of our customers. Our ICT infrastructure and IS/GIS solutions
EBOOK. NetApp ONTAP Cloud FOR MICROSOFT AZURE ENTERPRISE DATA MANAGEMENT IN THE CLOUD
 EBOOK NetApp ONTAP Cloud FOR MICROSOFT AZURE ENTERPRISE DATA MANAGEMENT IN THE CLOUD NetApp ONTAP Cloud for Microsoft Azure The ONTAP Cloud Advantage 3 Enterprise-Class Data Management 5 How ONTAP Cloud
EBOOK NetApp ONTAP Cloud FOR MICROSOFT AZURE ENTERPRISE DATA MANAGEMENT IN THE CLOUD NetApp ONTAP Cloud for Microsoft Azure The ONTAP Cloud Advantage 3 Enterprise-Class Data Management 5 How ONTAP Cloud
Cybersecurity 2016 Survey Summary Report of Survey Results
 Introduction In 2016, the International City/County Management Association (ICMA), in partnership with the University of Maryland, Baltimore County (UMBC), conducted a survey to better understand local
Introduction In 2016, the International City/County Management Association (ICMA), in partnership with the University of Maryland, Baltimore County (UMBC), conducted a survey to better understand local
University Information Technology Data Backup and Recovery Policy
 University Information Technology Data Backup and Recovery Policy I. Purpose and Scope A. The purpose of this policy is to document the University of Utah Information Technology (UIT) data backup and recovery
University Information Technology Data Backup and Recovery Policy I. Purpose and Scope A. The purpose of this policy is to document the University of Utah Information Technology (UIT) data backup and recovery
Disaster Recovery Planning Blackout. Katrina
 Disaster Recovery 2003 Blackout Before: After: Katrina 1 Sandy Mentor, Ohio Flood Disaster Map 2 It is believed that some of the companies spend up to 25% of their budgets on disaster recovery planning;
Disaster Recovery 2003 Blackout Before: After: Katrina 1 Sandy Mentor, Ohio Flood Disaster Map 2 It is believed that some of the companies spend up to 25% of their budgets on disaster recovery planning;
CASE STUDY FINANCE Digital Outsource Services
 CASE STUDY FINANCE Digital Outsource Services How the team catch database deployment problems with Redgate SQL Monitor "...we connect to all the servers from the one interface. It lets us see everything
CASE STUDY FINANCE Digital Outsource Services How the team catch database deployment problems with Redgate SQL Monitor "...we connect to all the servers from the one interface. It lets us see everything
Mail Findings. Australia Post Consumer Survey. Research into consumer preferences of transactional communications
 Australia Post Consumer Survey Mail Findings August 2013 Australia Post Consumer Survey Mail Findings Research into consumer preferences of transactional communications Methodology The Australia Post Consumer
Australia Post Consumer Survey Mail Findings August 2013 Australia Post Consumer Survey Mail Findings Research into consumer preferences of transactional communications Methodology The Australia Post Consumer
Solution Pack. Managed Services Virtual Private Cloud Managed Database Service Selections and Prerequisites
 Solution Pack Managed Services Virtual Private Cloud Managed Database Service Selections and Prerequisites Subject Governing Agreement Term DXC Services Requirements Agreement between DXC and Customer
Solution Pack Managed Services Virtual Private Cloud Managed Database Service Selections and Prerequisites Subject Governing Agreement Term DXC Services Requirements Agreement between DXC and Customer
LEADING WITH GRC. Approaching Integrated GRC. Knute Ohman, VP, GRC Program Manager. GRC Summit 2017 All Rights Reserved
 LEADING WITH GRC Approaching Integrated GRC Knute Ohman, VP, GRC Program Manager Agenda 1. Organization Overview: Vision, Key Facts and Needs 2. GRC Program Governance, Challenges and Community 3. Implementation
LEADING WITH GRC Approaching Integrated GRC Knute Ohman, VP, GRC Program Manager Agenda 1. Organization Overview: Vision, Key Facts and Needs 2. GRC Program Governance, Challenges and Community 3. Implementation
6/4/2018 Request for Proposal. Upgrade and Consolidation Storage Backup Network Shares Virtual Infrastructure Disaster Recovery
 6/4/2018 Request for Proposal Upgrade and Consolidation Storage Backup Network Shares Virtual Infrastructure Disaster Recovery Network Infrastructure Services - Server Team DC WATER & SEWER AUTHORITY (DC
6/4/2018 Request for Proposal Upgrade and Consolidation Storage Backup Network Shares Virtual Infrastructure Disaster Recovery Network Infrastructure Services - Server Team DC WATER & SEWER AUTHORITY (DC
IBM s Integrated Data Management Solutions for the DBA
 Information Management IBM s Integrated Data Management Solutions for the DBA Stop Stressing and Start Automating! Agenda Daily Woes: Trials and tribulations of the DBA Business Challenges: Beyond the
Information Management IBM s Integrated Data Management Solutions for the DBA Stop Stressing and Start Automating! Agenda Daily Woes: Trials and tribulations of the DBA Business Challenges: Beyond the
PetaLibrary Storage Service MOU
 University of Colorado Boulder Research Computing PetaLibrary Storage Service MOU 1. INTRODUCTION This is the memorandum of understanding (MOU) for the Research Computing (RC) PetaLibrary Storage Service.
University of Colorado Boulder Research Computing PetaLibrary Storage Service MOU 1. INTRODUCTION This is the memorandum of understanding (MOU) for the Research Computing (RC) PetaLibrary Storage Service.
IT TRENDS REPORT 2016:
 IT TRENDS REPORT 2016: THE HYBRID IT EVOLUTION NORTH AMERICA WHAT WE COVER IN THE REPORT IT TRENDS REPORT 2016: THE HYBRID IT EVOLUTION Introduction Key Findings Recommendations Full Survey Results INTRODUCTION
IT TRENDS REPORT 2016: THE HYBRID IT EVOLUTION NORTH AMERICA WHAT WE COVER IN THE REPORT IT TRENDS REPORT 2016: THE HYBRID IT EVOLUTION Introduction Key Findings Recommendations Full Survey Results INTRODUCTION
How to Enable Risk-Free Database Experiments. OakTable World: Sept 23 & 24, San Francisco
 How to Enable Risk-Free Database Experiments Thank you for joining us, the webinar will start at: 08:00 Pacific / 11:00 Central / 12:00 East / 16:00 UK Time OakTable World: Sept 23 & 24, San Francisco
How to Enable Risk-Free Database Experiments Thank you for joining us, the webinar will start at: 08:00 Pacific / 11:00 Central / 12:00 East / 16:00 UK Time OakTable World: Sept 23 & 24, San Francisco
Key Findings from the Global State of Information Security Survey 2017 Indonesian Insights
 www.pwc.com/id Key Findings from the State of Information Security Survey 2017 n Insights Key Findings from the State of Information Security Survey 2017 n Insights By now, the numbers have become numbing.
www.pwc.com/id Key Findings from the State of Information Security Survey 2017 n Insights Key Findings from the State of Information Security Survey 2017 n Insights By now, the numbers have become numbing.
