744 Motooka Nishi-ku Fukuoka , Japan Phone/Fax:
|
|
|
- Nora Barber
- 6 years ago
- Views:
Transcription
1 September 12, 2009 To whom it may concern: I am Dr. Masafumi Yamashita, a professor at the Department of Informatics, Graduate School of Information Science and Electrical Engineering, Kyushu University, Japan. I would like to submit a report on the habilitation thesis of Dr. Akka Zemmari to the committee. Sincerely yours, Masafumi Yamashita Professor, Department of Informatics, Graduate School of Information Science and Electrical Engineering, Kyushu University 1
2 Review Report on the Dr. Akka Zemmari s HdR Dissertation 0. General Information Since I cannot read French well, I am writing this review report by reading an English overview of the dissertation and a set of his articles written in English, both of which were provided by Dr. Zemmari. Dr. Zemmari and I belong to the same research society known as the distributed computing, whose main concern is the theoretical aspects of distributed systems. A part of his research topics overlaps with mine, but we have not written co-authored papers. 1. Curriculum Vitae Dr. Akka Zemmari obtained his Ph.D in 2000 and started his carrier in academia. Since 2001, he is an associate professor at Universite Montesquieu Bordeaux IV. He has supervised one Ph.D. candidate and two Master course students. They have successfully received their degrees. Although the number of students that he supervised is not large, this fact witnesses his ability of supervising students. 2. Summary of Papers in Dissertation Distributed systems consist of autonomous computing entities (i.e., nodes, processes, processors, or agents) communicating each other through communication links. To collaborate with and to resolve conflicts among the entitiies, agreement problems repeatedly emerge in distributed systems. The agreement problems are thus considered to be the most fundamental problem in the distributed computing. The dissertation investigates the following agreement problems: Leader Election Problem: selecting a one from the entities of distributed system. Maximal Independent Set Problem: selecting a maximal independent set of the communication network. 2
3 Coloring Problem: deciding the colors of vertices (i.e., entities) in such a way that neighboring vertices always have distinct colors. Handshake Problem: extracting a matching from the communi- cation network. The above problems are indeed agreement problems in the sense that all the entities need to agree on (i.e., consistently choose) the leader, the maximal independent set, the colors or the matching. However, these problems are shown to be unsolvable in a deterministic way when an order among the entities is not provided a-priori, e.g., when the distributed system is anonymous (i.e., when the entities do not have unique identifiers). This motivates the introduction of probabilistic algorithms. The dissertation investigates probabilistic agreement problems on anonymous networks. It presents many agreemtns algorithms and analyzes their performances. In the following, we look at each of the four agreement problems mentioned above. 3. Leader Election Problem The leader election problem is the problem of electing an entity (called leader) from the set of entities. Angluin proposed an election algorithm for a tree, which repeatedly removes a leaf from the current tree one-by-one until a single vertex remains. The remaining vertex becomes the leader. Dr. Zemmari discussed two issues on Angluin's algorithm. First, he investigated how to control the distribution that each of the entities is elected in a distributed manner, and proposed such a method to realize it. This problem setting and the solutions are interesting and important, not only from the view of practice, but also from the view of the probability theory. This random process of election seems to have still another deep relationship with a conventional stochastic process. Second, Dr. Zemmari considered an extension of this algorithm to other classes of communication networks. He only considered polyominoids. The result is technically interesting, but the class of polyominoids is specific. I hope that he contiues to do this research direction until he obtains an election algorithm for general graphs. 3
4 In summary, the papers in this category shows that his ability of analyzing algorithms using mathematical tools is deep and impressive. 4. Maximal Independent Set and Coloring Problems: A set of vertices (i.e., entities) is called independent if they do not share an edge in the communication graph. Intuitively, two non-adjacent vertices can proceed their executions independently, so that a set of independent vertices represents a set of simultaneously executable entities. Thus a maximal (or a maximum) independent set is looked for to extract maximal (or maximum) parallelism. The essence of difficulty is in the symmetry breaking and Dr. Zemmari made use of random bits (i.e., coin flips) to break symmetry. This basic idea is a conventional one, but by elegantly implementing this idea in the algorithm, he could design an algorithm that shows better performance than the previous ones. That is, its time complexity is O(log n), its message size (number of bits) is 1, and its bit complexity (per channel) is O(log n), all of which are the best among the known algorithms, and this is the first algorithm to realize message size 1. The algorithm does not need any global information, e.g., the order or the size, on the network, which it the feature that I want to emphasize. The coloring problem is to color vertices in such a way that two end-vertices of each edge do not have the same colors. Since the set of vertices having the same color is an independent set, coloring problem is considered to be an extension of the independent set problem. The idea behind his coloring algorithm is a conventional one and using a trick (to implement it into a one-bit protocol) similar to the one in his maximal independent set algorithm, Dr. Zemmari obtained an algorithm that performs well. In summary, these papers show that the quality of his techniques to implement ideas in algorithms is high. 5. Handshake Problem: In order for two end-vertices of an edge to start communication, both of them select each other as communication parties. The problem asks a protocol to select the partners. In articles they use terms rendezvouz and hand shake, but they refer to the same concept. 4
5 We can restate the problem as the maximal matching problem to extract matching edges from a given communcation graph. I rank the papers in this category best because of thier sophisticated analysis based on the probabiliy theory. It may be interesting to consider a problem (like in the case of leader election) of controlling the probability that an edge is selected in a distributed manner. 6. Publications Dr. Akka Zemmari has 9 journal papers and 20 conference papers in his 9 years carrier, 3 papers/year. I have examined their qualities in above. As for quantity, I believe that it is sufficient. 7. Concluding Remarks I have examined Dr. Zemmari's carrier and publications. As a result, I conclude that the quantity and quality of their publications show that he is a leading researcher in distributed computing. The above as well as the fact that all of the students that he has supervised successfully obtained their degrees witness that Dr. Akka Zemmari is at the high scientific level, and has sufficient talent to supervise young researchers. 5
The University of Jordan. Accreditation & Quality Assurance Center. Curriculum for Doctorate Degree
 Accreditation & Quality Assurance Center Curriculum for Doctorate Degree 1. Faculty King Abdullah II School for Information Technology 2. Department Computer Science الدكتوراة في علم الحاسوب (Arabic).3
Accreditation & Quality Assurance Center Curriculum for Doctorate Degree 1. Faculty King Abdullah II School for Information Technology 2. Department Computer Science الدكتوراة في علم الحاسوب (Arabic).3
PURDUE UNIVERSITY. Exam Forms. Graduate School Web Database
 PURDUE UNIVERSITY Graduate School Web Database 9/18/2013 This document is an introduction to the Exam Form process recently implemented in the Graduate School Web Database. It provides guidance on how
PURDUE UNIVERSITY Graduate School Web Database 9/18/2013 This document is an introduction to the Exam Form process recently implemented in the Graduate School Web Database. It provides guidance on how
Master & Doctor of Philosophy Programs in Computer Science
 Master & Doctor of Philosophy Programs in Computer Science Research Fields Pattern Recognition Data Analysis Internet of Things and Network Communication Machine Learning Web Semantic and Ontology For
Master & Doctor of Philosophy Programs in Computer Science Research Fields Pattern Recognition Data Analysis Internet of Things and Network Communication Machine Learning Web Semantic and Ontology For
Master of Computer Applications
 FIRST SEMESTER EXAMINATION ID 044101 MCA 101 Fundamentals of IT 3 1 4 044103 MCA 103 Programming in C 3 1 4 044105 MCA 105 Discrete Mathematics 3 1 4 044107 MCA 107 Computer Organization 3 1 4 044109 MCA
FIRST SEMESTER EXAMINATION ID 044101 MCA 101 Fundamentals of IT 3 1 4 044103 MCA 103 Programming in C 3 1 4 044105 MCA 105 Discrete Mathematics 3 1 4 044107 MCA 107 Computer Organization 3 1 4 044109 MCA
INITIATE THE THESIS ACCEPTANCE FORM
 INITIATE THE THESIS ACCEPTANCE FORM 1) Students using the electronic form will still select an appointment time using the selfscheduling calendar on our website. a) However, students will not need to be
INITIATE THE THESIS ACCEPTANCE FORM 1) Students using the electronic form will still select an appointment time using the selfscheduling calendar on our website. a) However, students will not need to be
GUIDELINES FOR MASTER OF SCIENCE INTERNSHIP THESIS
 GUIDELINES FOR MASTER OF SCIENCE INTERNSHIP THESIS Dear Participant of the MScIS Program, If you have chosen to follow an internship, one of the requirements is to write a Thesis. This document gives you
GUIDELINES FOR MASTER OF SCIENCE INTERNSHIP THESIS Dear Participant of the MScIS Program, If you have chosen to follow an internship, one of the requirements is to write a Thesis. This document gives you
Doctoral School: József Hatvany Doctoral School for Computer Science and Engineering
 University of Miskolc Faculty of Mechanical Engineering and Doctoral School: József Hatvany Doctoral School for Computer Science and Engineering Name of the Study Program: Computer Science and Engineering
University of Miskolc Faculty of Mechanical Engineering and Doctoral School: József Hatvany Doctoral School for Computer Science and Engineering Name of the Study Program: Computer Science and Engineering
STUDIES IN DIGITAL SYSTEMS INVESTMENT ON KNOWLEDGE OF DIGITAL SYSTEMS
 STUDIES IN DIGITAL SYSTEMS INVESTMENT ON KNOWLEDGE OF DIGITAL SYSTEMS Presentation Overview Location of the Department s premises The Department in a Nutshell Studies and Education: Offered in the context
STUDIES IN DIGITAL SYSTEMS INVESTMENT ON KNOWLEDGE OF DIGITAL SYSTEMS Presentation Overview Location of the Department s premises The Department in a Nutshell Studies and Education: Offered in the context
Master's Programme, Computer Science, 120 credits Masterprogram, datalogi credits
 Programme syllabus Master's Programme, Computer Science, 120 credits Masterprogram, datalogi 120.0 credits Valid for students admitted to the education from autumn 18 (HT - Autumn term; VT - Spring term).
Programme syllabus Master's Programme, Computer Science, 120 credits Masterprogram, datalogi 120.0 credits Valid for students admitted to the education from autumn 18 (HT - Autumn term; VT - Spring term).
Welcome to Maastricht University. School of Business and Economics
 Welcome to Maastricht University School of Business and Economics MSc Business Intelligence and Smart Services (BISS) Service design and development in cyber-society Dr. Alexander Grigoriev Why should
Welcome to Maastricht University School of Business and Economics MSc Business Intelligence and Smart Services (BISS) Service design and development in cyber-society Dr. Alexander Grigoriev Why should
Master Course in Computer Science Orientation day
 Master Course in Computer Science Orientation day Info on the Department of Computer Science Ranked first (in its area) in 5-year Research Assessment by Ministry of University and Research 2013 e 2017
Master Course in Computer Science Orientation day Info on the Department of Computer Science Ranked first (in its area) in 5-year Research Assessment by Ministry of University and Research 2013 e 2017
Version studieåret 2015/2016
 2015 Curriculum for the Master of Disaster Management programme at the Faculty of Health and Medical Sciences, University of Copenhagen This curriculum comes into force on 1 September 2015 and shall apply
2015 Curriculum for the Master of Disaster Management programme at the Faculty of Health and Medical Sciences, University of Copenhagen This curriculum comes into force on 1 September 2015 and shall apply
CATALOG 2018/2019 BINUS UNIVERSITY. Computer Science. Introduction. Vision. Mission
 Computer Science Introduction In the new millennium and the global era, the role of information and automation in the various domains and activities of the business industry are becoming more important.
Computer Science Introduction In the new millennium and the global era, the role of information and automation in the various domains and activities of the business industry are becoming more important.
Sample Form Only. Albright Associate Application Form. Title * Name * Middle Initial or Name. Proposed Project Title *
 Albright Associate Application Form To apply for an AIAR Associate Fellowship, please fill in the form below. Associate Applications are considered year round. There is no deadline. You should SAVE your
Albright Associate Application Form To apply for an AIAR Associate Fellowship, please fill in the form below. Associate Applications are considered year round. There is no deadline. You should SAVE your
MASTER OF ENGINEERING PROGRAM IN INFORMATION
 MASTER OF ENGINEERING PROGRAM IN INFORMATION AND COMMUNICATION TECHNOLOGY FOR EMBEDDED SYSTEMS (INTERNATIONAL PROGRAM) Curriculum Title Master of Engineering in Information and Communication Technology
MASTER OF ENGINEERING PROGRAM IN INFORMATION AND COMMUNICATION TECHNOLOGY FOR EMBEDDED SYSTEMS (INTERNATIONAL PROGRAM) Curriculum Title Master of Engineering in Information and Communication Technology
ASSIUT UNIVERSITY. Faculty of Computers and Information Department of Information Technology. on Technology. IT PH.D. Program.
 ASSIUT UNIVERSITY Faculty of Computers and Information Department of Information Technology Informatiio on Technology PhD Program IT PH.D. Program Page 0 Assiut University Faculty of Computers & Informationn
ASSIUT UNIVERSITY Faculty of Computers and Information Department of Information Technology Informatiio on Technology PhD Program IT PH.D. Program Page 0 Assiut University Faculty of Computers & Informationn
Oral Qualifier ENGG194
 Oral Qualifier ENGG194 Committee The examination committee is constituted based upon suggestions of the advisor, in consultation with the MS-PhD director if desired. The chair is assigned by the director.
Oral Qualifier ENGG194 Committee The examination committee is constituted based upon suggestions of the advisor, in consultation with the MS-PhD director if desired. The chair is assigned by the director.
College of Sciences. College of Sciences. Master s of Science in Computer Sciences Master s of Science in Biotechnology
 Master s of Science in Computer Sciences Master s of Science in Biotechnology Department of Computer Sciences 1. Introduction\Program Mission The Program mission is to prepare students to be fully abreast
Master s of Science in Computer Sciences Master s of Science in Biotechnology Department of Computer Sciences 1. Introduction\Program Mission The Program mission is to prepare students to be fully abreast
Algorithms for Grid Graphs in the MapReduce Model
 University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln Computer Science and Engineering: Theses, Dissertations, and Student Research Computer Science and Engineering, Department
University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln Computer Science and Engineering: Theses, Dissertations, and Student Research Computer Science and Engineering, Department
STATISTICS (STAT) Statistics (STAT) 1
 Statistics (STAT) 1 STATISTICS (STAT) STAT 2013 Elementary Statistics (A) Prerequisites: MATH 1483 or MATH 1513, each with a grade of "C" or better; or an acceptable placement score (see placement.okstate.edu).
Statistics (STAT) 1 STATISTICS (STAT) STAT 2013 Elementary Statistics (A) Prerequisites: MATH 1483 or MATH 1513, each with a grade of "C" or better; or an acceptable placement score (see placement.okstate.edu).
PROGRAMME SPECIFICATION POSTGRADUATE PROGRAMMES
 PROGRAMME SPECIFICATION POSTGRADUATE PROGRAMMES KEY FACTS Programme name Telecommunications and Networks Award MSc School School of Engineering and Mathematical Sciences Department or equivalent School
PROGRAMME SPECIFICATION POSTGRADUATE PROGRAMMES KEY FACTS Programme name Telecommunications and Networks Award MSc School School of Engineering and Mathematical Sciences Department or equivalent School
Graduate Student Orientation
 Graduate Student Orientation Department of Computer Science The Volgenau School of Engineering Professor Sanjeev Setia, Chair Fall 2018 http://cs.gmu.edu Presented by: Professor Alex Brodsky Outline CS
Graduate Student Orientation Department of Computer Science The Volgenau School of Engineering Professor Sanjeev Setia, Chair Fall 2018 http://cs.gmu.edu Presented by: Professor Alex Brodsky Outline CS
Chapter I INTRODUCTION. and potential, previous deployments and engineering issues that concern them, and the security
 Chapter I INTRODUCTION This thesis provides an introduction to wireless sensor network [47-51], their history and potential, previous deployments and engineering issues that concern them, and the security
Chapter I INTRODUCTION This thesis provides an introduction to wireless sensor network [47-51], their history and potential, previous deployments and engineering issues that concern them, and the security
Exact Algorithms Lecture 7: FPT Hardness and the ETH
 Exact Algorithms Lecture 7: FPT Hardness and the ETH February 12, 2016 Lecturer: Michael Lampis 1 Reminder: FPT algorithms Definition 1. A parameterized problem is a function from (χ, k) {0, 1} N to {0,
Exact Algorithms Lecture 7: FPT Hardness and the ETH February 12, 2016 Lecturer: Michael Lampis 1 Reminder: FPT algorithms Definition 1. A parameterized problem is a function from (χ, k) {0, 1} N to {0,
MASTER OF SCIENCE IN COMPUTER SCIENCE
 THE UNIVERSITY OF ZAMBIA SCHOOL OF NATURAL SCIENCES DEPARTMENT OF COMPUTER STUDIES MASTER OF SCIENCE IN COMPUTER SCIENCE November 2014 1) BACKGROUND From the inception of Computer Science programmes at
THE UNIVERSITY OF ZAMBIA SCHOOL OF NATURAL SCIENCES DEPARTMENT OF COMPUTER STUDIES MASTER OF SCIENCE IN COMPUTER SCIENCE November 2014 1) BACKGROUND From the inception of Computer Science programmes at
Master of Engineering Program in Mining Engineering (International Program) Program Overview. Fields of Research
 Master of Engineering Program in Mining Engineering (International Program) Name of the Degree Full Master of Engineering (Mining Engineering) Abbreviated M. Eng. (Mining Engineering) Plan A Type A 1 36
Master of Engineering Program in Mining Engineering (International Program) Name of the Degree Full Master of Engineering (Mining Engineering) Abbreviated M. Eng. (Mining Engineering) Plan A Type A 1 36
certification.setac.org Certification Contact of Environmental Risk Assessors Phone: certification.setac.
 certification.setac.org Certification Contact Phone: +32 2 772 72 81 Email: CRA@setac.org certification.setac.org of Environmental Risk Assessors The SETAC Europe Certification of Environmental Risk Assessors
certification.setac.org Certification Contact Phone: +32 2 772 72 81 Email: CRA@setac.org certification.setac.org of Environmental Risk Assessors The SETAC Europe Certification of Environmental Risk Assessors
The Structure and Properties of Clique Graphs of Regular Graphs
 The University of Southern Mississippi The Aquila Digital Community Master's Theses 1-014 The Structure and Properties of Clique Graphs of Regular Graphs Jan Burmeister University of Southern Mississippi
The University of Southern Mississippi The Aquila Digital Community Master's Theses 1-014 The Structure and Properties of Clique Graphs of Regular Graphs Jan Burmeister University of Southern Mississippi
Establishment of new Department of Informatics, UNIRI and experiences in teaching SE course
 Establishment of new Department of Informatics, UNIRI and experiences in teaching SE course Nataša Hoić-Božić, natasah@inf.uniri.hr Sanja Čandrlić, sanjac@inf.uniri.hr Odjel za informatiku, Sveučilište
Establishment of new Department of Informatics, UNIRI and experiences in teaching SE course Nataša Hoić-Božić, natasah@inf.uniri.hr Sanja Čandrlić, sanjac@inf.uniri.hr Odjel za informatiku, Sveučilište
CATALOG 2016/2017 BINUS UNIVERSITY
 Computer Science Introduction In the new millennium and the global era, the role of information and automation in the various domains and activities of the business industry are becoming more important.
Computer Science Introduction In the new millennium and the global era, the role of information and automation in the various domains and activities of the business industry are becoming more important.
CATALOG 2017/2018 BINUS UNIVERSITY. Cyber Security. Introduction. Vision. Mission
 Cyber Security Introduction Cyber attack is raising and threaten ubiquitous world on internet today. Industry and government need cyber security expert to counter and defend from this threaten. Cyber Security
Cyber Security Introduction Cyber attack is raising and threaten ubiquitous world on internet today. Industry and government need cyber security expert to counter and defend from this threaten. Cyber Security
Drawing Bipartite Graphs as Anchored Maps
 Drawing Bipartite Graphs as Anchored Maps Kazuo Misue Graduate School of Systems and Information Engineering University of Tsukuba 1-1-1 Tennoudai, Tsukuba, 305-8573 Japan misue@cs.tsukuba.ac.jp Abstract
Drawing Bipartite Graphs as Anchored Maps Kazuo Misue Graduate School of Systems and Information Engineering University of Tsukuba 1-1-1 Tennoudai, Tsukuba, 305-8573 Japan misue@cs.tsukuba.ac.jp Abstract
Note: All Electrical & Computer Engineering graduate students will be expected to read this guide before consulting academic advisors.
 Graduate Student Guide Department of Electrical & Computer Engineering Fall 2017 Note: All Electrical & Computer Engineering graduate students will be expected to read this guide before consulting academic
Graduate Student Guide Department of Electrical & Computer Engineering Fall 2017 Note: All Electrical & Computer Engineering graduate students will be expected to read this guide before consulting academic
CONCENTRATIONS: HIGH-PERFORMANCE COMPUTING & BIOINFORMATICS CYBER-SECURITY & NETWORKING
 MAJOR: DEGREE: COMPUTER SCIENCE MASTER OF SCIENCE (M.S.) CONCENTRATIONS: HIGH-PERFORMANCE COMPUTING & BIOINFORMATICS CYBER-SECURITY & NETWORKING The Department of Computer Science offers a Master of Science
MAJOR: DEGREE: COMPUTER SCIENCE MASTER OF SCIENCE (M.S.) CONCENTRATIONS: HIGH-PERFORMANCE COMPUTING & BIOINFORMATICS CYBER-SECURITY & NETWORKING The Department of Computer Science offers a Master of Science
Enhancing Forecasting Performance of Naïve-Bayes Classifiers with Discretization Techniques
 24 Enhancing Forecasting Performance of Naïve-Bayes Classifiers with Discretization Techniques Enhancing Forecasting Performance of Naïve-Bayes Classifiers with Discretization Techniques Ruxandra PETRE
24 Enhancing Forecasting Performance of Naïve-Bayes Classifiers with Discretization Techniques Enhancing Forecasting Performance of Naïve-Bayes Classifiers with Discretization Techniques Ruxandra PETRE
Prof.Dr. Sotiraq Dhamo Doc. Julian Naqellari The University of Tirana Accounting Department
 Prof.Dr. Sotiraq Dhamo Doc. Julian Naqellari The University of Tirana Accounting Department 1. Key stakeholders in A&A Education 2. Current Third Level Qualification: University of Tirana (as an example)
Prof.Dr. Sotiraq Dhamo Doc. Julian Naqellari The University of Tirana Accounting Department 1. Key stakeholders in A&A Education 2. Current Third Level Qualification: University of Tirana (as an example)
A Survey and Recent Results Developments of Two or More
 JAIST Reposi https://dspace.j Title A Survey and Recent Results Developments of Two or More About Co Boxes Author(s)Uehara, Ryuhei Citation Origami^6 : proceedings of the sixth international meeting on
JAIST Reposi https://dspace.j Title A Survey and Recent Results Developments of Two or More About Co Boxes Author(s)Uehara, Ryuhei Citation Origami^6 : proceedings of the sixth international meeting on
Finding Neighbor Communities in the Web using Inter-Site Graph
 Finding Neighbor Communities in the Web using Inter-Site Graph Yasuhito Asano 1, Hiroshi Imai 2, Masashi Toyoda 3, and Masaru Kitsuregawa 3 1 Graduate School of Information Sciences, Tohoku University
Finding Neighbor Communities in the Web using Inter-Site Graph Yasuhito Asano 1, Hiroshi Imai 2, Masashi Toyoda 3, and Masaru Kitsuregawa 3 1 Graduate School of Information Sciences, Tohoku University
Computer Science Curriculum for International Students
 Computer Science Curriculum for International Students 2011-2012 Language of instruction Although the lecturer is allowed to teach his course in Dutch, - the course notes, handbook and/or other information
Computer Science Curriculum for International Students 2011-2012 Language of instruction Although the lecturer is allowed to teach his course in Dutch, - the course notes, handbook and/or other information
Extremal Graph Theory: Turán s Theorem
 Bridgewater State University Virtual Commons - Bridgewater State University Honors Program Theses and Projects Undergraduate Honors Program 5-9-07 Extremal Graph Theory: Turán s Theorem Vincent Vascimini
Bridgewater State University Virtual Commons - Bridgewater State University Honors Program Theses and Projects Undergraduate Honors Program 5-9-07 Extremal Graph Theory: Turán s Theorem Vincent Vascimini
International Max Planck Research School on Neuroscience of Communication (IMPRS NeuroCom)
 Application Form International Max Planck Research School on Neuroscience of Communication (IMPRS NeuroCom) Deadline: 1 December, 2018 (24:00 - midnight Central European Time) Please note: You will have
Application Form International Max Planck Research School on Neuroscience of Communication (IMPRS NeuroCom) Deadline: 1 December, 2018 (24:00 - midnight Central European Time) Please note: You will have
Syntactic Measures of Complexity
 A thesis submitted to the University of Manchester for the degree of Doctor of Philosophy in the Faculty of Arts 1999 Bruce Edmonds Department of Philosophy Table of Contents Table of Contents - page 2
A thesis submitted to the University of Manchester for the degree of Doctor of Philosophy in the Faculty of Arts 1999 Bruce Edmonds Department of Philosophy Table of Contents Table of Contents - page 2
Imam Mohammad Ibn Saud Islamic University College of Computer and Information Sciences Department of Computer Sciences
 1121-1122 In the Name Of Allah, the Most Beneficent, the Most Merciful Imam Mohammad Ibn Saud Islamic University Department of Computer Sciences Program Description of Master of Science in Computer Sciences
1121-1122 In the Name Of Allah, the Most Beneficent, the Most Merciful Imam Mohammad Ibn Saud Islamic University Department of Computer Sciences Program Description of Master of Science in Computer Sciences
Course Curriculum for Master Degree in Network Engineering and Security
 Course Curriculum for Master Degree in Network Engineering and Security The Master Degree in Network Engineering and Security is awarded by the Faculty of Graduate Studies at Jordan University of Science
Course Curriculum for Master Degree in Network Engineering and Security The Master Degree in Network Engineering and Security is awarded by the Faculty of Graduate Studies at Jordan University of Science
System Identification Algorithms and Techniques for Systems Biology
 System Identification Algorithms and Techniques for Systems Biology by c Choujun Zhan A Thesis submitted to the School of Graduate Studies in partial fulfillment of the requirements for the degree of Doctor
System Identification Algorithms and Techniques for Systems Biology by c Choujun Zhan A Thesis submitted to the School of Graduate Studies in partial fulfillment of the requirements for the degree of Doctor
Backup and Recovery Scheme for Distributed e-learning System
 Notice for the use of this material The copyright of this material is retained by the Information Processing Society of Japan (IPSJ). This material is published on this web site with the agreement of the
Notice for the use of this material The copyright of this material is retained by the Information Processing Society of Japan (IPSJ). This material is published on this web site with the agreement of the
INSTITUTE OF INFORMATION TECHNOLOGY UNIVERSITY OF DHAKA
 INSTITUTE OF INFORMATION TECHNOLOGY UNIVERSITY OF DHAKA http://www.iit.du.ac.bd/ BACHELOR OF SCIENCE IN SOFTWARE ENGINEERING (BSSE) 1. Institute of Information Technology (IIT) Institute of Information
INSTITUTE OF INFORMATION TECHNOLOGY UNIVERSITY OF DHAKA http://www.iit.du.ac.bd/ BACHELOR OF SCIENCE IN SOFTWARE ENGINEERING (BSSE) 1. Institute of Information Technology (IIT) Institute of Information
Detecting Controversial Articles in Wikipedia
 Detecting Controversial Articles in Wikipedia Joy Lind Department of Mathematics University of Sioux Falls Sioux Falls, SD 57105 Darren A. Narayan School of Mathematical Sciences Rochester Institute of
Detecting Controversial Articles in Wikipedia Joy Lind Department of Mathematics University of Sioux Falls Sioux Falls, SD 57105 Darren A. Narayan School of Mathematical Sciences Rochester Institute of
ASSIUT UNIVERSITY. Faculty of Computers and Information Department of Information Systems. IS Ph.D. Program. Page 0
 ASSIUT UNIVERSITY Faculty of Computers and Information Department of Information Systems Informatiio on Systems PhD Program IS Ph.D. Program Page 0 Assiut University Faculty of Computers & Informationn
ASSIUT UNIVERSITY Faculty of Computers and Information Department of Information Systems Informatiio on Systems PhD Program IS Ph.D. Program Page 0 Assiut University Faculty of Computers & Informationn
PART-TIME MASTER S DEGREE PROGRAM. Information Systems. Choose from seven specializations study on campus and online.
 PART-TIME MASTER S DEGREE PROGRAM Information Systems Choose from seven specializations study on campus and online. The IT program for leaders MASTER OF SCIENCE IN INFORMATION SYSTEMS The part-time MSIS
PART-TIME MASTER S DEGREE PROGRAM Information Systems Choose from seven specializations study on campus and online. The IT program for leaders MASTER OF SCIENCE IN INFORMATION SYSTEMS The part-time MSIS
GRAPH THEORY: AN INTRODUCTION
 GRAPH THEORY: AN INTRODUCTION BEGINNERS 3/4/2018 1. GRAPHS AND THEIR PROPERTIES A graph G consists of two sets: a set of vertices V, and a set of edges E. A vertex is simply a labeled point. An edge is
GRAPH THEORY: AN INTRODUCTION BEGINNERS 3/4/2018 1. GRAPHS AND THEIR PROPERTIES A graph G consists of two sets: a set of vertices V, and a set of edges E. A vertex is simply a labeled point. An edge is
WALL, NICOLE TURPIN, M.A. On the Reconstruction Conjecture. (2008) Directed by Dr. Paul Duvall. 56 pp.
 WALL, NICOLE TURPIN, M.A. On the Reconstruction Conjecture. (2008) Directed by Dr. Paul Duvall. 56 pp. Every graph of order three or more is reconstructible. Frank Harary restated one of the most famous
WALL, NICOLE TURPIN, M.A. On the Reconstruction Conjecture. (2008) Directed by Dr. Paul Duvall. 56 pp. Every graph of order three or more is reconstructible. Frank Harary restated one of the most famous
Before you start filling the forms online, you will be asked the following two preliminary questions:
 United States-India Educational Foundation 2015 FULBRIGHT FLTA PROGRAM Instructions for Completing the Fulbright Online FLTA Program Application Read all instructions carefully before completing the application
United States-India Educational Foundation 2015 FULBRIGHT FLTA PROGRAM Instructions for Completing the Fulbright Online FLTA Program Application Read all instructions carefully before completing the application
USER GUIDE FOR THE PLAGIARISM SERVICE TURNITIN BASIC FUNCTIONALITIES PhD CANDIDATES Section
 USER GUIDE FOR THE PLAGIARISM SERVICE TURNITIN BASIC FUNCTIONALITIES PhD CANDIDATES Section 14 th November 2017 Contents A) ACCOUNT ACTIVATION... 2 B) UPLOAD AN ASSIGNMENT... 6 C) VISUALISATION OF THE
USER GUIDE FOR THE PLAGIARISM SERVICE TURNITIN BASIC FUNCTIONALITIES PhD CANDIDATES Section 14 th November 2017 Contents A) ACCOUNT ACTIVATION... 2 B) UPLOAD AN ASSIGNMENT... 6 C) VISUALISATION OF THE
Bachelor of Information Technology (Network Security)
 Course information for Bachelor of Information Technology (Network Security) Course Number HE20524 Location Meadowbank Course Design The Bachelor of Information Technology (Network Security) is a three-year
Course information for Bachelor of Information Technology (Network Security) Course Number HE20524 Location Meadowbank Course Design The Bachelor of Information Technology (Network Security) is a three-year
Michigan Technological University - Graduate School Review of a Dissertation, Thesis, or Report
 TDR-Review Michigan Technological University - Graduate School Review of a Dissertation, Thesis, or Report The Graduate School completes this form for all students who submit a dissertation, thesis, or
TDR-Review Michigan Technological University - Graduate School Review of a Dissertation, Thesis, or Report The Graduate School completes this form for all students who submit a dissertation, thesis, or
Department of Computer Science
 College of Science and Mathematics Department of Computer Science Dr. Vasil Hnatyshin Department Head Advising brochures also available online at: https://rucsm.org/cs/advising/brochures/ Fall 2017 Computer
College of Science and Mathematics Department of Computer Science Dr. Vasil Hnatyshin Department Head Advising brochures also available online at: https://rucsm.org/cs/advising/brochures/ Fall 2017 Computer
PROGRAMME SYLLABUS Information Architecture and Innovation (Two Years), 120
 PROGRAMME SYLLABUS Information Architecture and Innovation (Two Years), 120 credits Programmestart: Autumn 2018 Jönköping International Business School, Box 1026, SE-551 11 Jönköping VISIT Gjuterigatan
PROGRAMME SYLLABUS Information Architecture and Innovation (Two Years), 120 credits Programmestart: Autumn 2018 Jönköping International Business School, Box 1026, SE-551 11 Jönköping VISIT Gjuterigatan
Curriculum Vitae. Research interests, honors and other things (a brief description)
 Curriculum Vitae Nader Jafari Rad, (Associate Professor) Department of Mathematics, Shahrood University of Technology Shahrood, Iran P.O. Box: 3619995161, Phone: (98) 2733392012 Email: n.jafarirad@{gmail.com,
Curriculum Vitae Nader Jafari Rad, (Associate Professor) Department of Mathematics, Shahrood University of Technology Shahrood, Iran P.O. Box: 3619995161, Phone: (98) 2733392012 Email: n.jafarirad@{gmail.com,
Curriculum for the main subject at Master s level in. IT and Cognition, The 2015 curriculum. Adjusted 2017 and 2018
 Curriculum for the main subject at Master s level in IT and Cognition, The 2015 curriculum Adjusted 2017 and 2018 Department of Nordic Research Faculty of Humanities U i it f C h Contents Part 1. Authority,
Curriculum for the main subject at Master s level in IT and Cognition, The 2015 curriculum Adjusted 2017 and 2018 Department of Nordic Research Faculty of Humanities U i it f C h Contents Part 1. Authority,
HYBRID PETRI NET MODEL BASED DECISION SUPPORT SYSTEM. Janetta Culita, Simona Caramihai, Calin Munteanu
 HYBRID PETRI NET MODEL BASED DECISION SUPPORT SYSTEM Janetta Culita, Simona Caramihai, Calin Munteanu Politehnica University of Bucharest Dept. of Automatic Control and Computer Science E-mail: jculita@yahoo.com,
HYBRID PETRI NET MODEL BASED DECISION SUPPORT SYSTEM Janetta Culita, Simona Caramihai, Calin Munteanu Politehnica University of Bucharest Dept. of Automatic Control and Computer Science E-mail: jculita@yahoo.com,
GLS UNIVERSITY. Faculty of Computer Technology Master of Computer Applications (MCA) Programme
 GLS UNIVERSITY Faculty of Computer Technology Master of Computer Applications (MCA) Programme 1. GLS University s Master of Computer Applications programme is a three-year full-time postgraduate programme
GLS UNIVERSITY Faculty of Computer Technology Master of Computer Applications (MCA) Programme 1. GLS University s Master of Computer Applications programme is a three-year full-time postgraduate programme
Multi-label classification using rule-based classifier systems
 Multi-label classification using rule-based classifier systems Shabnam Nazmi (PhD candidate) Department of electrical and computer engineering North Carolina A&T state university Advisor: Dr. A. Homaifar
Multi-label classification using rule-based classifier systems Shabnam Nazmi (PhD candidate) Department of electrical and computer engineering North Carolina A&T state university Advisor: Dr. A. Homaifar
A new MAC protocol for reducing effect of needless transmission deferment induced by missed RTS/CTS handshake
 Mobile Information Systems 5 (009) 3 DOI 0.333/MIS-009-0070 IOS Press A new MAC protocol for reducing effect of needless transmission deferment induced by missed / handshake Tetsuya Shigeyasu a, Daishi
Mobile Information Systems 5 (009) 3 DOI 0.333/MIS-009-0070 IOS Press A new MAC protocol for reducing effect of needless transmission deferment induced by missed / handshake Tetsuya Shigeyasu a, Daishi
Deterministic Leader Election in O(D + log n) Rounds with Messages of size O(1)
 Deterministic Leader Election in O(D + log n) Rounds with Messages of size O(1) A. Casteigts, Y. Métivier, J.M. Robson, A. Zemmari LaBRI - University of Bordeaux DISC 2016, Paris A. Casteigts, Y. Métivier,
Deterministic Leader Election in O(D + log n) Rounds with Messages of size O(1) A. Casteigts, Y. Métivier, J.M. Robson, A. Zemmari LaBRI - University of Bordeaux DISC 2016, Paris A. Casteigts, Y. Métivier,
Problem Solving, Presenting, and Programming: A Matter of Giving and Taking
 Olympiads in Informatics, 2016, Vol. 10, 231 235 2016 IOI, Vilnius University DOI: 10.15388/ioi.2016.15 231 Problem Solving, Presenting, and Programming: A Matter of Giving and Taking Tom VERHOEFF Dept.
Olympiads in Informatics, 2016, Vol. 10, 231 235 2016 IOI, Vilnius University DOI: 10.15388/ioi.2016.15 231 Problem Solving, Presenting, and Programming: A Matter of Giving and Taking Tom VERHOEFF Dept.
Capstone eportfolio Guidelines (2015) School of Information Sciences, The University of Tennessee Knoxville
 Capstone eportfolio Guidelines (2015) School of Information Sciences, The University of Tennessee Knoxville The University of Tennessee, Knoxville, requires a final examination to measure the candidate
Capstone eportfolio Guidelines (2015) School of Information Sciences, The University of Tennessee Knoxville The University of Tennessee, Knoxville, requires a final examination to measure the candidate
Saint Petersburg Electrotechnical University "LETI" (SPb ETU "LETI") , Saint Petersburg, Russian Federation Professora Popova str.
 Saint Petersburg Electrotechnical University "LETI" (SPb ETU "LETI") 197376, Saint Petersburg, Russian Federation Professora Popova str., 5 Professor Mikhail Kupriyanov Saint Petersburg Electrotechnical
Saint Petersburg Electrotechnical University "LETI" (SPb ETU "LETI") 197376, Saint Petersburg, Russian Federation Professora Popova str., 5 Professor Mikhail Kupriyanov Saint Petersburg Electrotechnical
Tiling Problem of Convex Pentagon
 Original Paper Forma, 15, 75 79, 2000 Tiling Problem of Convex Pentagon Teruhisa SUGIMOTO 1 and Tohru OGAWA 2 1 Department of Statistical Science, The Graduate University for Advanced Studies, 4-6-7 Minami-Azabu,
Original Paper Forma, 15, 75 79, 2000 Tiling Problem of Convex Pentagon Teruhisa SUGIMOTO 1 and Tohru OGAWA 2 1 Department of Statistical Science, The Graduate University for Advanced Studies, 4-6-7 Minami-Azabu,
Discover Viterbi: Computer Science, Cyber Security & Informatics Programs. Viterbi School of Engineering University of Southern California Fall 2017
 Discover Viterbi: Computer Science, Cyber Security & Informatics Programs Viterbi School of Engineering University of Southern California Fall 2017 WebEx Quick Facts Will I be able to get a copy of the
Discover Viterbi: Computer Science, Cyber Security & Informatics Programs Viterbi School of Engineering University of Southern California Fall 2017 WebEx Quick Facts Will I be able to get a copy of the
High Ppeed Circuit Techniques for Network Intrusion Detection Systems (NIDS)
 The University of Akron IdeaExchange@UAkron Mechanical Engineering Faculty Research Mechanical Engineering Department 2008 High Ppeed Circuit Techniques for Network Intrusion Detection Systems (NIDS) Ajay
The University of Akron IdeaExchange@UAkron Mechanical Engineering Faculty Research Mechanical Engineering Department 2008 High Ppeed Circuit Techniques for Network Intrusion Detection Systems (NIDS) Ajay
USER EXPERIENCE DESIGN (UXD)
 Kent State University Catalog 2018-2019 1 USER EXPERIENCE DESIGN (UXD) UXD 20001 INTRODUCTION TO USER EXPERIENCE DESIGN 3 Credit Students explore the context within which User Experience Design exists
Kent State University Catalog 2018-2019 1 USER EXPERIENCE DESIGN (UXD) UXD 20001 INTRODUCTION TO USER EXPERIENCE DESIGN 3 Credit Students explore the context within which User Experience Design exists
COMP3121/3821/9101/ s1 Assignment 1
 Sample solutions to assignment 1 1. (a) Describe an O(n log n) algorithm (in the sense of the worst case performance) that, given an array S of n integers and another integer x, determines whether or not
Sample solutions to assignment 1 1. (a) Describe an O(n log n) algorithm (in the sense of the worst case performance) that, given an array S of n integers and another integer x, determines whether or not
Bachelor of Science (B.Sc.) in Computer Science
 General description of the degree program Name Qualification awarded: Computer Science Bachelor of Science (B.Sc.) in Computer Science Level of qualification Qualification requirements and regulations
General description of the degree program Name Qualification awarded: Computer Science Bachelor of Science (B.Sc.) in Computer Science Level of qualification Qualification requirements and regulations
AI Technology for Quickly Solving Urban Security Positioning Problems
 AI Technology for Quickly Solving Urban Security Positioning Problems Hiroaki Iwashita Kotaro Ohori Hirokazu Anai Security games are used for mathematically optimizing security measures aimed at minimizing
AI Technology for Quickly Solving Urban Security Positioning Problems Hiroaki Iwashita Kotaro Ohori Hirokazu Anai Security games are used for mathematically optimizing security measures aimed at minimizing
KIBABII UNIVERSITY COLLEGE
 KIBABII UNIVERSITY COLLEGE (Constituent college of Masinde Muliro University and Technology) School of Computing and Informatics Department of Computer Science INTERNAL MEMO To: Deputy Principal (ARE)
KIBABII UNIVERSITY COLLEGE (Constituent college of Masinde Muliro University and Technology) School of Computing and Informatics Department of Computer Science INTERNAL MEMO To: Deputy Principal (ARE)
GEORGE J. ANDERS, Ph.D., P.Eng., Fellow IEEE
 GEORGE J. ANDERS, Ph.D., P.Eng., Fellow IEEE George Anders is a president of Anders Consulting. Between 1975 and 2012 he has been employed by Ontario Hydro and its successor companies in Toronto, Canada.
GEORGE J. ANDERS, Ph.D., P.Eng., Fellow IEEE George Anders is a president of Anders Consulting. Between 1975 and 2012 he has been employed by Ontario Hydro and its successor companies in Toronto, Canada.
Skip Lists S 3 S 2 S 1. Skip Lists Goodrich, Tamassia
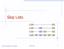 Skip Lists S 3 15 15 23 10 15 23 36 Skip Lists 1 What is a Skip List A skip list for a set S of distinct (key, element) items is a series of lists,,, S h such that Each list S i contains the special keys
Skip Lists S 3 15 15 23 10 15 23 36 Skip Lists 1 What is a Skip List A skip list for a set S of distinct (key, element) items is a series of lists,,, S h such that Each list S i contains the special keys
Research on Computer Network Virtual Laboratory based on ASP.NET. JIA Xuebin 1, a
 International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 2015) Research on Computer Network Virtual Laboratory based on ASP.NET JIA Xuebin 1, a 1 Department of Computer,
International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 2015) Research on Computer Network Virtual Laboratory based on ASP.NET JIA Xuebin 1, a 1 Department of Computer,
SDP TOOLKIT FOR EFFECTIVE DATA USE
 AN INTRODUCTION TO THE SDP TOOLKIT FOR EFFECTIVE DATA USE A GUIDE FOR CONDUCTING DATA ANALYSIS IN EDUCATION AGENCIES www.gse.harvard.edu/sdp/toolkit Toolkit Documents An Introduction to the SDP Toolkit
AN INTRODUCTION TO THE SDP TOOLKIT FOR EFFECTIVE DATA USE A GUIDE FOR CONDUCTING DATA ANALYSIS IN EDUCATION AGENCIES www.gse.harvard.edu/sdp/toolkit Toolkit Documents An Introduction to the SDP Toolkit
Comparing Two Program Contents with Computing Curricula 2005 Knowledge Areas
 Comparing Two Program Contents with Computing Curricula 2005 Knowledge Areas Azad Ali, Indiana University of Pennsylvania azad.ali@iup.edu Frederick G. Kohun, Robert Morris University kohun@rmu.edu David
Comparing Two Program Contents with Computing Curricula 2005 Knowledge Areas Azad Ali, Indiana University of Pennsylvania azad.ali@iup.edu Frederick G. Kohun, Robert Morris University kohun@rmu.edu David
Pervasive Computing. OpenLab Jan 14 04pm L Institute of Networked and Embedded Systems
 Pervasive Computing Institute of Networked and Embedded Systems OpenLab 2010 Jan 14 04pm L4.1.01 MISSION STATEMENT Founded in 2007, the Pervasive Computing Group at Klagenfurt University is part of the
Pervasive Computing Institute of Networked and Embedded Systems OpenLab 2010 Jan 14 04pm L4.1.01 MISSION STATEMENT Founded in 2007, the Pervasive Computing Group at Klagenfurt University is part of the
Thesis & Dissertation Formatting Checklist
 Thesis & Dissertation Formatting Checklist Thank you for submitting your document to the Graduate College. Please review the checklists below. Items that are not checked need to be revised, please check
Thesis & Dissertation Formatting Checklist Thank you for submitting your document to the Graduate College. Please review the checklists below. Items that are not checked need to be revised, please check
MS in Computer Sciences & MS in Software Engineering
 SUKKUR INSTITUTE OF BUSINESS ADMINISTRATION Merit-Quality-Excellence Schema of Studies for MS in Computer Sciences & MS in Software Engineering (2016-2017) DEPARTMENT OF COMPUTER SCIENCE Schema of Studies
SUKKUR INSTITUTE OF BUSINESS ADMINISTRATION Merit-Quality-Excellence Schema of Studies for MS in Computer Sciences & MS in Software Engineering (2016-2017) DEPARTMENT OF COMPUTER SCIENCE Schema of Studies
The Mashup Atelier. Cesare Pautasso, Monica Frisoni. Faculty of Informatics University of Lugano (USI), Switzerland
 The Mashup Atelier Cesare Pautasso, Monica Frisoni Faculty of Informatics University of Lugano (USI), Switzerland http://www.pautasso.info 1 University of Lugano, Switzerland Faculty of Informatics (Opened
The Mashup Atelier Cesare Pautasso, Monica Frisoni Faculty of Informatics University of Lugano (USI), Switzerland http://www.pautasso.info 1 University of Lugano, Switzerland Faculty of Informatics (Opened
A Composite Graph Model for Web Document and the MCS Technique
 A Composite Graph Model for Web Document and the MCS Technique Kaushik K. Phukon Department of Computer Science, Gauhati University, Guwahati-14,Assam, India kaushikphukon@gmail.com Abstract It has been
A Composite Graph Model for Web Document and the MCS Technique Kaushik K. Phukon Department of Computer Science, Gauhati University, Guwahati-14,Assam, India kaushikphukon@gmail.com Abstract It has been
Solutions of Stochastic Coalitional Games
 Applied Mathematical Sciences, Vol. 8, 2014, no. 169, 8443-8450 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/10.12988/ams.2014.410881 Solutions of Stochastic Coalitional Games Xeniya Grigorieva St.Petersburg
Applied Mathematical Sciences, Vol. 8, 2014, no. 169, 8443-8450 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/10.12988/ams.2014.410881 Solutions of Stochastic Coalitional Games Xeniya Grigorieva St.Petersburg
Iterative methods for solving large and sparse linear system of equations Professor Mahmoud Mohseni Moghadam
 Fatemeh P. A. Beik Curriculum Vitae Personal Information Full name: Fatemeh Panjeh Ali Beik (Beik, F. P. A) Academic rank: Associate professor. Marital status: Married with one child. Date of birth: December
Fatemeh P. A. Beik Curriculum Vitae Personal Information Full name: Fatemeh Panjeh Ali Beik (Beik, F. P. A) Academic rank: Associate professor. Marital status: Married with one child. Date of birth: December
THE CHINESE UNIVERSITY OF HONG KONG Department of Information Engineering
 THE CHINESE UNIVERSITY OF HONG KONG Department of Information Engineering I. Suggested Study Plan for MIEG (entrants via ENGG Faculty in 08) University Core Requirements English 9 Chinese 6 Foundation
THE CHINESE UNIVERSITY OF HONG KONG Department of Information Engineering I. Suggested Study Plan for MIEG (entrants via ENGG Faculty in 08) University Core Requirements English 9 Chinese 6 Foundation
Study Programme Description
 Study Programme Description Title of the study Software Engineering Official name of the institution, faculty (s) Vilnius University, Faculty of Mathematics and Informatics, Department of Software Engineering
Study Programme Description Title of the study Software Engineering Official name of the institution, faculty (s) Vilnius University, Faculty of Mathematics and Informatics, Department of Software Engineering
Welcome to VUB-CSC PhD Scholarship Programme
 Welcome to VUB-CSC PhD Scholarship Programme Instructions for online application at VUB For incoming students in September 2017 Steps: Search for a CSC PhD vacancy Fill in the online application form Create
Welcome to VUB-CSC PhD Scholarship Programme Instructions for online application at VUB For incoming students in September 2017 Steps: Search for a CSC PhD vacancy Fill in the online application form Create
United States India Educational Foundation
 Completing the Embark Online Application Instructions for Indian Fulbright Nehru Doctoral Research Fellowship (FNDR) Applicants For pre doctoral level research in the United States during the 2019 2020
Completing the Embark Online Application Instructions for Indian Fulbright Nehru Doctoral Research Fellowship (FNDR) Applicants For pre doctoral level research in the United States during the 2019 2020
Call for Papers for Communication QoS, Reliability and Modeling Symposium
 Call for Papers for Communication QoS, Reliability and Modeling Symposium Scope and Motivation: In modern communication networks, different technologies need to cooperate with each other for end-to-end
Call for Papers for Communication QoS, Reliability and Modeling Symposium Scope and Motivation: In modern communication networks, different technologies need to cooperate with each other for end-to-end
The K-Ring: a versatile model for the design of MIMD computer topology
 The K-Ring: a versatile model for the design of MIMD computer topology P. Kuonen Computer Science Department Swiss Federal Institute of Technology CH-115 Lausanne, Switzerland E-mail: Pierre.Kuonen@epfl.ch
The K-Ring: a versatile model for the design of MIMD computer topology P. Kuonen Computer Science Department Swiss Federal Institute of Technology CH-115 Lausanne, Switzerland E-mail: Pierre.Kuonen@epfl.ch
Master of Science in Software Engineering Student Guide
 King Fahd University of Petroleum & Minerals College of Computer Sciences and Engineering Information and Computer Science Department Master of Science in Software Engineering Student Guide http://www.ccse.kfupm.edu.sa/swe/
King Fahd University of Petroleum & Minerals College of Computer Sciences and Engineering Information and Computer Science Department Master of Science in Software Engineering Student Guide http://www.ccse.kfupm.edu.sa/swe/
FOUNDATIONS OF COMPUTER SCIENCE BY BEHROUZ A. FOROUZAN DOWNLOAD EBOOK : FOUNDATIONS OF COMPUTER SCIENCE BY BEHROUZ A. FOROUZAN PDF
 Read Online and Download Ebook FOUNDATIONS OF COMPUTER SCIENCE BY BEHROUZ A. FOROUZAN DOWNLOAD EBOOK : FOUNDATIONS OF COMPUTER SCIENCE BY BEHROUZ A. Click link bellow and free register to download ebook:
Read Online and Download Ebook FOUNDATIONS OF COMPUTER SCIENCE BY BEHROUZ A. FOROUZAN DOWNLOAD EBOOK : FOUNDATIONS OF COMPUTER SCIENCE BY BEHROUZ A. Click link bellow and free register to download ebook:
Ranking of nodes of networks taking into account the power function of its weight of connections
 Ranking of nodes of networks taking into account the power function of its weight of connections Soboliev A.M. 1, Lande D.V. 2 1 Post-graduate student of the Institute for Special Communications and Information
Ranking of nodes of networks taking into account the power function of its weight of connections Soboliev A.M. 1, Lande D.V. 2 1 Post-graduate student of the Institute for Special Communications and Information
1 Leaffix Scan, Rootfix Scan, Tree Size, and Depth
 Lecture 17 Graph Contraction I: Tree Contraction Parallel and Sequential Data Structures and Algorithms, 15-210 (Spring 2012) Lectured by Kanat Tangwongsan March 20, 2012 In this lecture, we will explore
Lecture 17 Graph Contraction I: Tree Contraction Parallel and Sequential Data Structures and Algorithms, 15-210 (Spring 2012) Lectured by Kanat Tangwongsan March 20, 2012 In this lecture, we will explore
Distributed minimum spanning tree problem
 Distributed minimum spanning tree problem Juho-Kustaa Kangas 24th November 2012 Abstract Given a connected weighted undirected graph, the minimum spanning tree problem asks for a spanning subtree with
Distributed minimum spanning tree problem Juho-Kustaa Kangas 24th November 2012 Abstract Given a connected weighted undirected graph, the minimum spanning tree problem asks for a spanning subtree with
Preface MOTIVATION ORGANIZATION OF THE BOOK. Section 1: Basic Concepts of Graph Theory
 xv Preface MOTIVATION Graph Theory as a well-known topic in discrete mathematics, has become increasingly under interest within recent decades. This is principally due to its applicability in a wide range
xv Preface MOTIVATION Graph Theory as a well-known topic in discrete mathematics, has become increasingly under interest within recent decades. This is principally due to its applicability in a wide range
