Priority Inheritance Spin Locks for Multiprocessor Real-Time Systems
|
|
|
- George Bates
- 6 years ago
- Views:
Transcription
1 Priority Inheritance Spin Locks for Multiprocessor Real-Time Systems Cai-Dong Wang, Hiroaki Takada, and Ken Sakamura Department of Information Science, Faculty of Science, University of Tokyo Hongo, Bunkyo-ku, Tokyo 113, Japan Abstract When a real-time system is realized on a shared-memory multiprocessor, priority-ordered spin locks are often required to reduce priority inversions. However, simple priority-ordered spin locks can cause uncontrolled priority inversions when they are used for nested spin locks. This paper points out the problem of uncontrolled priority inversions in the context of spin locks and proposes priority inheritance spin locks, spin lock algorithms that are enhanced with the priority inheritance scheme, to solve the problem. Two algorithms of priority inheritance spin locks are presented and their effectiveness is demonstrated through performance measurements. 1 Introduction Spin lock is one of the fundamental synchronization primitives for exclusive access to shared resources on shared-memory multiprocessors. It is usually implemented with atomic read-modify-write operations on a single word (or aligned contiguous words) of shared memory such as test and set, fetch and store (swap), or compare and swap. Various spin lock algorithms using these operations have been proposed [1, 2] and are widely used. In real-time systems, each job has some timing constraints to be met. A scheduling algorithm or a run-time scheduler translates the timing constraints into a priority, and a run-time system assigns system resources to higher priority jobs. It is often the case with a multiprocessor real-time system that a spin lock is also required to pass the lock in a priority order. In order to satisfy this requirement, some priority-ordered spin lock algorithms, in which processors acquire a lock in the order of their priorities, have been proposed [3, 4, 5]. In general, shared resources that must be accessed exclusively by a processor are divided into some lock units in order to improve concurrency. When a processor accesses some shared resources included in different lock units, it must acquire multiple locks one by one. If priorityordered spin locks are simply used for this kind of nested spin locks, uncontrolled priority inversions can occur. The uncontrolled priority inversion problem in nested spin locks is described in Section 2. In order to solve this problem, this paper proposes priority inheritance spin locks, spin lock algorithms that are routine (a) acquire lock(l 1 ); acquire lock(l 2 ); release lock(l 2 ); release lock(l 1 ); routine (b) Fig. 1: Example of nested spin locks enhanced with the priority inheritance scheme. The priority inheritance scheme is a promising approach to solve uncontrolled priority inversion problems and its applications to task scheduling algorithms are actively studied [6, 7]. Priority inheritance spin locks are also required to realize bounded and scalable nested spin locks for real-time systems [8]. After describing the necessity of priority inheritance spin locks in Section 2, we present two algorithms of priority inheritance spin locks in Section 3. In Section 4, their effectiveness is evaluated through performance measurements. 2 Priority Inversion and Priority Inheritance 2.1 The Priority Inversion Problem in Nested Spin Locks Priority inversion in the context of spin locks is the phenomenon that a higher priority processor is forced to wait for the execution of a lower priority processor. Because priority inversion cannot be avoided unless a higher priority processor can steal the lock held by a lower priority one, how to minimize its duration is a concern. When the maximum duration of a priority inversion cannot be determined, it is called uncontrolled. When priority-ordered spin locks are used for nested spin locks, uncontrolled priority inversions can occur. A typical case is described in the following example. Example 1 (uncontrolled priority inversion) We assume that P1, P2, P3, and P4 are processors arranged in descing order of priority with P1 having the highest priority, and that L1 and L2 are locks. These processors repeatedly execute one of the two routines presented in Figure 1. Suppose the case that when P1 s executing 1
2 routine (b) and tries to acquire the lock L1, P4 is holding L1 and is waiting for the other lock L2 in routine (b). If P2 and P3 repeatedly execute routine (a) in this situation, P2 and P3 can acquire L2 alternately and P4 must wait for L2 all the while. Because P1 must also wait for the executions of P2 and P3, this duration is a priority inversion. Obviously, the maximum duration of this priority inversion cannot be determined. 2.2 Spin Lock with Priority Inheritance In order to solve this problem of uncontrolled priority inversions, we introduce the priority inheritance scheme to spin locks. The fundamental concept of priority inheritance scheme is that when a processor makes some higher priority processors wait, its priority should be raised to the level of the highest priority processor among the waiting ones. In other words, the processor inherits the priority of the highest priority processor blocked by it. Also, priority inheritance must be transitive. For example, suppose that P1, P2, and P3 are three processors in descing order of priority. When P2 makes P1 wait and P3 makes P2 wait, P3 should inherit the priority of P1. With the basic priority inheritance scheme, which is the naive realization of the concept, the uncontrolled priority inversion problem illustrated in Example 1 is solved as follows. When P1 tries to acquire L1 and s waiting for it, P4, which is holding L1, inherits the priority of P1 because P1 is forced to wait by P4. Because the inherited priority is higher than the priorities of P2 and P3, P4 can acquire L2 with precedence over P2 and P3. As the result, P1 need not wait for the alternate executions of routine (a) by P2 and P3, and the maximum duration of the priority inversion can be bounded. When a processor releases one of the locks, its priority is necessary to be re-calculated in general. Specifically, its priority is changed to the highest one of its original priority and the priorities of the processors that is waiting for the locks held by the former one. When the processor releases the last lock it is holding, its priority is recovered to its original level. This re-calculation can be omitted under the following two assumptions. The first assumption is that the inherited priority is used only for spin locks, and not used for task schedulings. In more specific, the inherited priority is used only when the processor tries to acquire another lock. The second assumption is that the two-phase protocol is adopted. In other words, once a processor releases a lock, it cannot acquire another lock until it releases all the locks it is holding. Under these two assumptions, once the priority of a processor is raised, it need not be lowered until it releases all the locks. These assumptions can be removed by adding re-calculation routines to the algorithms proposed in Section 3 at the cost of some runtime overhead. The required behavior of priority inheritance spin locks can be summarized as follows. 1. Processors acquire a lock in the order of their priorities 1. 1 A strict definition of priority-ordered spin lock is appeared in [3]. // global shared variables. shared var L1, L2: Lock; // local variables (allocated for each processor). var I1, I2: Node; var my prio: integer; var my notify: boolean; // my notify is necessary only in the second algorithm. // initialize my prio. acquire first lock(&l1, &I1); acquire second lock(&l2, &I2, &L1); release lock(&l2, &I2); release lock(&l1, &I1); Fig. 2: Usage of the algorithms 2. When a processor P1 s waiting for a lock, and when its priority is higher than that of the processor P2 that is holding the lock, the priority of P2 is raised to that of P1. 3. When the priority of a processor P1 is raised while waiting for a lock, and when its new priority is higher than that of the processor P2 that is holding the lock, the priority of P2 is raised to the new priority of P1. 3 Priority Inheritance Spin Lock Algorithms In this section, we present two algorithms of priority inheritance spin locks, which are based on the priority-ordered queueing spin lock algorithm proposed by Markatos [3]. With the Markatos algorithm, processors trying to acquire a lock are linked to the waiting queue in a FIFO order 2. In releasing the lock, a processor searches the highest priority processor in the waiting queue and passes the lock to it. The first algorithm is a straightforward extension of the Markatos lock. A new variable that indicates the highest priority of the processors that is waiting for the lock is prepared for each lock. The processor holding the lock polls the variable while it is waiting for another lock. When the processor detects that the highest priority is raised, it inherits the priority. Because any processor can poll this highest priority variable for each lock, pollings on the variable are remote memory accesses and severely increase the interconnection network traffic with a multiprocessor system without coherent cache. The second algorithm is to avoid this non-local spin and is expected to have higher performance without coherent cache. In order to avoid unnecessary complexity, this paper presents the pseudo codes of the algorithms when a processor acquires at most two locks at the same time, in other words, when the nesting level of locks is less than or equal to two. With this simplification, we prepares two lock acquisition routines: acquire first lock for acquiring the outer lock and acquire second lock for acquiring the 2 Though the original Markatos algorithm adopts a double-linked queue structure, a single-linked queue structure is sufficient to implement the algorithm. Therefore, we enhance the simplified version adopting single-linked queue with the priority inheritance scheme.
3 type Node = record next: pointer to Node; locked: (Released, Locked); prio: integer type Lock = record last: pointer to Node; maxprio: integer; notifyp: pointer to boolean // notifyp is necessary only in the second algorithm. // last and notifyp fields should be initialized to NULL. // maxprio field should be initialized to MIN PRIO. type NodePtr = pointer to Node; type LockPtr = pointer to Lock; Fig. 3: Data structures inner lock. A typical usage of the routines is illustrated in Figure 2. The third argument of acquire second lock is the pointer to the lock that the processor is holding. In Figure 2, the keyword shared indicates that only one instance of the variable is allocated in the system and shared by all processors. The other local variables are allocated for each processor. With a multiprocessor without coherent cache, the local variables should be placed on the processor s locally accessible shared memory. The my prio variable is to store the current priority of the processor, and must be initialized before the processor tries to acquire the outermost lock. 3.1 The First Algorithm Figure 3 presents the common data structures for both algorithms (one of the fields is necessary only in the second algorithm). The Lock record should be prepared for each lock in the system. Its maxprio field is the highest priority variable for the lock. When the lock is empty (in other words, no processor holds the lock), the last field of its Lock record is NULL and its maxprio field is MIN PRIO, which designates the minimum priority value. A Node record is necessary for each nested lock for each processor. Figure 8 and Figure 9 present the pseudo codes of the first algorithm. In these figures, we assume that a larger value represents a higher priority. The fetch and store operation reads the memory addressed by the first parameter, returns the contents of the memory as its value, and atomically writes the second parameter to the memory. The CAS operation, the abbreviation of compare and swap, first reads the memory pointed to by the first parameter and compares its contents with the second parameter. If they are equal, the function writes the third parameter to the memory atomically and returns true. Otherwise, it returns false. Compared to the Markatos algorithm, two invocations of the raise priority procedure, which is to update the maxprio field of lock when it is lower than the newprio parameter, are added to the acquire first lock procedure and the acquire second lock procedure in Figure 8. The first invocation (marked with 31 ) is to raise maxprio for priority inheritance, when the processor s waiting for the lock. The second one (marked with 32 ) is to set maxprio, when the processor succeeds to acquire the lock without waiting. In the acquire second lock procedure, the processor must check the maxprio field of lock1, which is the lock being held by the processor, while waiting for lock. When maxprio becomes higher than the priority of the processor (the if statement marked with 33 ), it inherits maxprio of lock1 and updates maxprio of lock for transitive priority inheritance. The only difference of the release lock procedure in Figure 9 with that of the Markatos algorithm is the necessity of updating the maxprio field (two lines marked with 34 and 35 ). Assigning MIN PRIO to the maxprio field at first is necessary to avoid some racing conditions. This algorithm can be easily generalized to the case that a processor acquires more than two locks at the same time with the following method. The list of locks held by a processor should be maintained using an array or a linked list. In the generalized version of the acquire lock procedure, the maxprio fields of all the locks in the list should be checked while waiting for another lock. If some of them are higher than the priority of the processor, it inherits the highest priority among them. 3.2 Avoiding Non-Local Spins While a processor is waiting for a lock in the acquire second lock procedure of the first algorithm, the maxprio field of the holding lock is accessed repeatedly (marked with 33 ). This accesses cause a heavy traffic on the interconnection network without coherent cache. With the second algorithm presented in Figure 10 and Figure 11, this problem is solved by introducing a flag to notify that the maxprio field is modified. This notification flag (the my notify variable in Figure 2) is prepared for each processor on its locally accessible shared memory. A processor waiting for a lock in the acquire second lock procedure in Figure 10 reads the maxprio field only when the notification flag of the processor is set (the if statement marked with 36 ). Thus the non-local spin can be avoided. It also checks the maxprio field when it s waiting for a lock (by assigning TRUE to my notify). Introducing the notification flag is also advantageous when a processor acquires more than two locks at the same time, because only one memory location (i.e. the notification flag) is necessary to be checked in the waiting loop. Maintaining the list of locks held by a processor is still necessary in this case. Also, the raise priority notify procedure is used instead of raise priority (three lines marked with 37 ) in Figure 10. After updating the maxprio field of lock, the raise priority notify procedure sets the notification flag of the processor holding the lock. In order to locate the notification flag of the lock holder, a new field notifyp which points to the notification flag is introduced in the Lock record. The notifyp field of a lock is set when a processor succeeds to acquire the lock (two lines marked with 38 ). The field is also necessary to be cleared to NULL at the top of the release lock procedure in Figure 11 (marked with
4 Processor 1 Processor 8 GMICRO GMICRO GMICRO GMICRO GMICRO /200 GMICRO GMICRO GMICRO /200 /200 /200 /200 /200 /200 /200 Local Local Local Local Memory Local Memory Local Local Memory Memory Local Memory Memory Memory Memory Local Memory GMICRO /200 Master Processor Fig. 4: Evaluation environment VMEbus 39 ). There is a slight chance that the notification flag of a wrong processor is set. Specifically, suppose the case that the processor holding a lock passes the lock to another one and its notifyp field is changed, after yet another processor reads the notifyp field of the lock in the raise priority notify procedure and before it writes TRUE on 3notifyp. In this case, the notification flag of the processor that has already passed the lock to another is set. Although this difficulty can increase the interconnection network traffic a little, it does not cause wrong behavior. 4 Performance Evaluation In this section, the effectiveness of the priority inheritance spin lock algorithms proposed in the previous section is examined through performance evaluation. Their performance is compared with the simple priority-ordered spin locks without supporting priority inheritance scheme. We have used the single-linked queue version of the Markatos spin lock algorithm for this purpose. 4.1 Evaluation Environment A shared-bus multiprocessor system without coherent cache is used for the evaluation. The shared bus is based on the VMEbus specification, and each processor node consists of agmicro/200microprocessor, which is rated approximately at 10 MIPS, and 1 MB of local memory. The local memory can be accessed from other processors through the shared bus. No coherent cache is equipped. All the program code and the data area for each processor are placed on the local memory of the processor. Global shared variables are placed on the local memory of the master processor, which does not execute spin locks (Figure 4). Since thegmicro/200microprocessor supports compare and swap instruction but not fetch and store, the latter operation is emulated with a compare and swap instruction and a retry loop. As the VMEbus has only four pairs of bus request/grant lines, processors are classified into four groups by the bus request line they use. The round-robin arbitration scheme is adopted among groups and the static priority scheme is applied among processors belonging to a same group. routine (a) acquire lock(l 0 1); release lock(l 0 1); routine (c) Fig. 5: Evaluation routines acquire lock(l 1); release lock(l 1); routine (b) acquire lock(l 00 1 ); release lock(l 00 1 ); routine (d) 4.2 Evaluation Method We have used one to eight processors for the evaluation. The original (or assigned) priority of a processor is fixed to its ID numbers. Each processor repeatedly executes one of the four routines presented in Figure 5 in random order. Routines (c) and (d) are introduced in order to expose the problem of non-local spins with the first algorithm 3. The execution time of each routine is measured for each execution, and their distributions are obtained. Inside the critical section, a processor accesses the shared bus several number of times and waits for a while using empty loops. In case of routines (b), (c), and (d), shared bus accesses and an empty loop are also inserted between acquire first lock and acquire second lock. Without spin locks, the execution time of each routine is about 30 s, including the overhead for measuring execution times. Each processor also waits for a random time after each execution of the routines. Because our evaluation system has no coherent cache, the simple implementation of the first algorithm causes heavy shared-bus traffic. In order to avoid shared-bus saturation, the frequency to read the maxprio field in the acquire second lock routine is reduced. In more concrete, maxprio is checked only once for every four checkings of me!locked. In real-time systems, because the worst-case behavior of the system has primary importance, the effectiveness of the algorithms should be evaluated with their maximum execution times. Because maximum execution times cannot be obtained through experiments due to unavoidable non-determinism in multiprocessor systems, however, a p-reliable time, the time within which a processor finishes execution with probability p, is adopted as the performance metric instead of a maximum execution time. In this section, we show the evaluation results when p is (i.e %). 4.3 Evaluation Results Figure 6 presents the 99.99%-reliable execution times that the highest priority processor executes routine (b). 3 With routines (a) and (b) only, the effect of shared-bus traffic is not revealed, because at most one processor spins on non-local memory at the same time.
5 execution time of routine (b) (micro sec.) execution time of routine (a) (micro sec.) Markatos The first algorithm The second algorithm number of processors Fig. 6: 99.99%-reliable execution times of routine (b) Markatos The first algorithm The second algorithm number of processors Fig. 7: 99.99%-reliable execution times of routine (a) When the number of processors is large, the execution time with Markatos locks is much slower than those with our algorithms due to uncontrolled priority inversions. When the number of processors is small, our algorithms are slower because of the overhead for maintaining the maxprio field of each lock. Our second algorithm is a bit faster than the first one when the number of processors is more than six, but the difference is very small. Though it is not measured in our experiments, the shared-bus traffic is expected to be much larger with the first algorithm. Figure 7 presents the 99.99%-reliable execution times that the highest priority processor executes routine (a). As easily imagined, there are little difference in the behavior of routine (a) with three algorithms. This graph confirms the conjecture. Finally, in order to examine the average performance of the algorithms, we present the average execution times of routine (b) in Figure 12. From this graph, our algorithms are slower than Markatos lock in average performance. We can say that priority inheritance spin locks are not appropriate in case that improving average performance is the primary concern. 5 Conclusion and Future Work When a real-time system is realized on a shared-memory multiprocessor, priority-ordered spin locks are often required to reduce priority inversions. But, simple application of a priority-ordered spin lock algorithm to nested spin locks causes uncontrolled priority inversions, which are very harmful for satisfying the timing constraints imposed on real-time jobs. In order to solve the problem, we have proposed priority inheritance spin locks. Two algorithms of priority inheritance spin locks are presented: one for coherent cache multiprocessors and the other for multiprocessor systems without coherent cache. Performance evaluations to demonstrate their effectiveness have been conducted, and some affirmative results have been obtained. In this paper, we have proposed the algorithms based on the Markatos spin lock algorithm. We also plan to ext other priority-based spin lock algorithms, especially the PR-lock [5] and the bubble lock [9], to support the priority inheritance scheme. Our motivation of this study is the application to a scalable real-time operating system kernel for functiondistributed multiprocessors [10]. It also remains as a future work to implement a real-time kernel with the algorithms and to evaluate them in more realistic conditions. References [1] T. E. Anderson, The performance of spin lock alternatives for shared-memory multiprocessors, IEEE Trans. Parallel and Distributed Systems, vol. 1, pp. 6 16, Jan [2] J. M. Mellor-Crummey and M. L. Scott, Algorithms for scalable synchronization on shared-memory multiprocessors, ACM Trans. Computer Systems, vol. 9, pp , Feb [3] E. P. Markatos, Multiprocessor synchronization primitives with priorities, in Proc. 8th IEEE Workshop on Real-Time Operating Systems and Software, May [4] T. S. Craig, Queuing spin lock algorithms to support timing predictability, in Proc. Real-Time Systems Symposium, pp , Dec [5] T. Johnson and K. Harathi, A prioritized multiprocessor spin lock, Tech. Rep. TR , Department of Computer Science, University of Florida, [6] L. Sha, R. Rajkumar, and J. P. Lehoczky, Priority inheritance protocols: An approach to real-time synchronization, IEEE Trans. Computers, vol. 39, pp , Sept [7] R. Rajkumar, Synchronization in Real-Time Systems: A Priority Inheritance Approach. Kluwer Academic Publishers, [8] H. Takada and K. Sakamura, Real-time scalability of nested spin locks, in Proc. 2nd Real-Time Computing Systems and Applications, pp , Oct [9] N. Sakiyama, H. Takada, and K. Sakamura, Bubble lock: Another priority-orderd spin lock algorithm, in Collection of Position Papers for the 2nd Youth Forum in Computer Science and Engineering (YUFORIC), Oct [10] H. Takada and K. Sakamura, Towards a scalable real-time kernel for function-distributed multiprocessors, in Proc. of 20th IFAC/IFIP Workshop on Real Time Programming, Nov
6 procedure raise priority(lock: LockPtr, newprio: integer): boolean; var prio: integer; retry: prio := lock!maxprio; if newprio > prio then if CAS(&(lock!maxprio), prio, newprio) then return TRUE goto retry return FALSE procedure acquire first lock(lock: LockPtr, me: NodePtr); // enqueue myself. // when the queue is not empty 31 raise priority(lock, my prio); repeat until me!locked = Released // succeed to acquire the lock without waiting. 32 raise priority(lock, my prio) procedure acquire second lock(lock: LockPtr, me: NodePtr, lock1: LockPtr); // enqueue myself. // when the queue is not empty 31 raise priority(lock, my prio); repeat 33 if lock1!maxprio > my prio then // lock1!maxprio is non-local access. my prio := lock1!maxprio; raise priority(lock, my prio) until me!locked = Released // succeed to acquire the lock without waiting. 32 raise priority(lock, my prio) // move entry to the top of the waiting queue of lock. // pred is the predecessor of entry. // oldtop is the top of the queue before the move. procedure move to top(lock: LockPtr, entry, pred, oldtop: NodePtr); var succ: NodePtr; succ := entry!next; if succ = NULL then pred!next := NULL; if CAS(&(lock!last), entry, pred) then entry!next := oldtop; return repeat succ := entry!next until succ 6= NULL pred!next := succ; enry!next := oldtop procedure release lock(lock: LockPtr, me: NodePtr); var top, entry, pred: NodePtr; var hentry, hpred: NodePtr; 34 lock!maxprio = MIN PRIO; top := me!next; if top = NULL then if CAS(&(lock!last), me, NULL) then // the queue becomes empty. return repeat top := me!next until top 6= NULL // search the higest priority processor hentry := top; hpred := NULL; pred := top; entry := pred!next; while entry 6= NULL do if (entry!prio > hentry!prio) then hentry := entry; hpred := pred; pred := entry; entry := pred!next // now, hentry is the higest priority processor. if hentry 6= top then move to top(lock, hentry, hpred, top) 35 raise priority(lock, hentry!prio); hentry!locked = Released Fig. 9: The first algorithm (cont.) Fig. 8: The first algorithm
7 procedure raise priority notify(lock: LockPtr, newprio: integer); var notifyp: pointer to boolean; if raise priority(lock, newprio) then notifyp := lock!notifyp; if notifyp 6= NULL then // set the notification flag. 3notifyp := TRUE procedure acquire first lock(lock: LockPtr, me: NodePtr); // enqueue myself. // when the queue is not empty 37 raise priority notify(lock, my prio); repeat until me!locked = Released // succeed to acquire the lock without waiting. raise priority(lock, my prio) 38 lock!notifyp := &my notify procedure acquire second lock(lock: LockPtr, me: NodePtr, lock1: LockPtr); 37 raise priority notify(lock, my prio); my notify := TRUE; repeat // check if a priority inheritance is notified. 36 if my notify then my notify := FALSE; if lock1!maxprio > my prio then my prio := lock1!maxprio; 37 raise priority notify(lock, my prio) until me!locked = Released raise priority(lock, my prio) 38 lock!notifyp := &my notify procedure release lock(lock: LockPtr, me: NodePtr); var top, entry, pred: NodePtr; var hentry, hpred: NodePtr; lock!maxprio := MIN PRIO; 39 lock!notifyp := NULL; top := me!next; if top = NULL then if CAS(&(lock!last), me, NULL) then // the queue becomes empty. return repeat top := me!next until top 6= NULL // search the higest priority processor hentry := top; hpred := NULL; pred := top; entry := pred!next; while entry 6= NULL do if (entry!prio > hentry!prio) then hentry := entry; hpred := pred pred := entry; entry := pred!next // now, hentry is the higest priority processor. if hentry 6= top then move to top(lock, hentry, hpred, top) raise priority(lock, hentry!prio); hentry!locked := Released execution time of routine (b) (micro sec.) Fig. 11: The second algorithm (cont.) Markatos The first algorithm The second algorithm number of processors Fig. 12: Average execution times of routine (b) Fig. 10: The second algorithm
Real-Time Scalability of Nested Spin Locks. Hiroaki Takada and Ken Sakamura. Faculty of Science, University of Tokyo
 Real-Time Scalability of Nested Spin Locks Hiroaki Takada and Ken Sakamura Department of Information Science, Faculty of Science, University of Tokyo 7-3-1, Hongo, Bunkyo-ku, Tokyo 113, Japan Abstract
Real-Time Scalability of Nested Spin Locks Hiroaki Takada and Ken Sakamura Department of Information Science, Faculty of Science, University of Tokyo 7-3-1, Hongo, Bunkyo-ku, Tokyo 113, Japan Abstract
Reducing Priority Inversion in Interprocessor Synchronization on a Fixed-Priority Bus
 Reducing Priority Inversion in Interprocessor Synchronization on a Fixed-Priority Bus Chi-Sing Chen (cschen@cs.fsu.edu) Pratit Santiprabhob (pratit@cs.fsu.edu) T.P. Baker (baker@cs.fsu.edu) Department
Reducing Priority Inversion in Interprocessor Synchronization on a Fixed-Priority Bus Chi-Sing Chen (cschen@cs.fsu.edu) Pratit Santiprabhob (pratit@cs.fsu.edu) T.P. Baker (baker@cs.fsu.edu) Department
A simple correctness proof of the MCS contention-free lock. Theodore Johnson. Krishna Harathi. University of Florida. Abstract
 A simple correctness proof of the MCS contention-free lock Theodore Johnson Krishna Harathi Computer and Information Sciences Department University of Florida Abstract Mellor-Crummey and Scott present
A simple correctness proof of the MCS contention-free lock Theodore Johnson Krishna Harathi Computer and Information Sciences Department University of Florida Abstract Mellor-Crummey and Scott present
Advance Operating Systems (CS202) Locks Discussion
 Advance Operating Systems (CS202) Locks Discussion Threads Locks Spin Locks Array-based Locks MCS Locks Sequential Locks Road Map Threads Global variables and static objects are shared Stored in the static
Advance Operating Systems (CS202) Locks Discussion Threads Locks Spin Locks Array-based Locks MCS Locks Sequential Locks Road Map Threads Global variables and static objects are shared Stored in the static
A Transaction Processing Technique in Real-Time Object- Oriented Databases
 122 IJCSNS International Journal of Computer Science and Network Security, VOL.8 No.1, January 2008 A Transaction Processing Technique in Real-Time Object- Oriented Databases Woochun Jun Dept. of Computer
122 IJCSNS International Journal of Computer Science and Network Security, VOL.8 No.1, January 2008 A Transaction Processing Technique in Real-Time Object- Oriented Databases Woochun Jun Dept. of Computer
Adaptive Lock. Madhav Iyengar < >, Nathaniel Jeffries < >
 Adaptive Lock Madhav Iyengar < miyengar@andrew.cmu.edu >, Nathaniel Jeffries < njeffrie@andrew.cmu.edu > ABSTRACT Busy wait synchronization, the spinlock, is the primitive at the core of all other synchronization
Adaptive Lock Madhav Iyengar < miyengar@andrew.cmu.edu >, Nathaniel Jeffries < njeffrie@andrew.cmu.edu > ABSTRACT Busy wait synchronization, the spinlock, is the primitive at the core of all other synchronization
Midterm Exam Amy Murphy 6 March 2002
 University of Rochester Midterm Exam Amy Murphy 6 March 2002 Computer Systems (CSC2/456) Read before beginning: Please write clearly. Illegible answers cannot be graded. Be sure to identify all of your
University of Rochester Midterm Exam Amy Murphy 6 March 2002 Computer Systems (CSC2/456) Read before beginning: Please write clearly. Illegible answers cannot be graded. Be sure to identify all of your
Lecture 18: Coherence and Synchronization. Topics: directory-based coherence protocols, synchronization primitives (Sections
 Lecture 18: Coherence and Synchronization Topics: directory-based coherence protocols, synchronization primitives (Sections 5.1-5.5) 1 Cache Coherence Protocols Directory-based: A single location (directory)
Lecture 18: Coherence and Synchronization Topics: directory-based coherence protocols, synchronization primitives (Sections 5.1-5.5) 1 Cache Coherence Protocols Directory-based: A single location (directory)
Multiprocessor Systems. Chapter 8, 8.1
 Multiprocessor Systems Chapter 8, 8.1 1 Learning Outcomes An understanding of the structure and limits of multiprocessor hardware. An appreciation of approaches to operating system support for multiprocessor
Multiprocessor Systems Chapter 8, 8.1 1 Learning Outcomes An understanding of the structure and limits of multiprocessor hardware. An appreciation of approaches to operating system support for multiprocessor
Algorithms for Scalable Synchronization on Shared Memory Multiprocessors by John M. Mellor Crummey Michael L. Scott
 Algorithms for Scalable Synchronization on Shared Memory Multiprocessors by John M. Mellor Crummey Michael L. Scott Presentation by Joe Izraelevitz Tim Kopp Synchronization Primitives Spin Locks Used for
Algorithms for Scalable Synchronization on Shared Memory Multiprocessors by John M. Mellor Crummey Michael L. Scott Presentation by Joe Izraelevitz Tim Kopp Synchronization Primitives Spin Locks Used for
CPSC/ECE 3220 Summer 2017 Exam 2
 CPSC/ECE 3220 Summer 2017 Exam 2 Name: Part 1: Word Bank Write one of the words or terms from the following list into the blank appearing to the left of the appropriate definition. Note that there are
CPSC/ECE 3220 Summer 2017 Exam 2 Name: Part 1: Word Bank Write one of the words or terms from the following list into the blank appearing to the left of the appropriate definition. Note that there are
GLocks: Efficient Support for Highly- Contended Locks in Many-Core CMPs
 GLocks: Efficient Support for Highly- Contended Locks in Many-Core CMPs Authors: Jos e L. Abell an, Juan Fern andez and Manuel E. Acacio Presenter: Guoliang Liu Outline Introduction Motivation Background
GLocks: Efficient Support for Highly- Contended Locks in Many-Core CMPs Authors: Jos e L. Abell an, Juan Fern andez and Manuel E. Acacio Presenter: Guoliang Liu Outline Introduction Motivation Background
Lecture 9: Multiprocessor OSs & Synchronization. CSC 469H1F Fall 2006 Angela Demke Brown
 Lecture 9: Multiprocessor OSs & Synchronization CSC 469H1F Fall 2006 Angela Demke Brown The Problem Coordinated management of shared resources Resources may be accessed by multiple threads Need to control
Lecture 9: Multiprocessor OSs & Synchronization CSC 469H1F Fall 2006 Angela Demke Brown The Problem Coordinated management of shared resources Resources may be accessed by multiple threads Need to control
Spin Locks and Contention Management
 Chapter 7 Spin Locks and Contention Management 7.1 Introduction We now turn our attention to the performance of mutual exclusion protocols on realistic architectures. Any mutual exclusion protocol poses
Chapter 7 Spin Locks and Contention Management 7.1 Introduction We now turn our attention to the performance of mutual exclusion protocols on realistic architectures. Any mutual exclusion protocol poses
Deadlock. Lecture 4: Synchronization & Communication - Part 2. Necessary conditions. Deadlock handling. Hierarchical resource allocation
 Lecture 4: Synchronization & ommunication - Part 2 [RTS h 4] Deadlock Priority Inversion & Inheritance Mailbox ommunication ommunication with Objects Deadlock Improper allocation of common resources may
Lecture 4: Synchronization & ommunication - Part 2 [RTS h 4] Deadlock Priority Inversion & Inheritance Mailbox ommunication ommunication with Objects Deadlock Improper allocation of common resources may
250P: Computer Systems Architecture. Lecture 14: Synchronization. Anton Burtsev March, 2019
 250P: Computer Systems Architecture Lecture 14: Synchronization Anton Burtsev March, 2019 Coherence and Synchronization Topics: synchronization primitives (Sections 5.4-5.5) 2 Constructing Locks Applications
250P: Computer Systems Architecture Lecture 14: Synchronization Anton Burtsev March, 2019 Coherence and Synchronization Topics: synchronization primitives (Sections 5.4-5.5) 2 Constructing Locks Applications
Relative Performance of Preemption-Safe Locking and Non-Blocking Synchronization on Multiprogrammed Shared Memory Multiprocessors
 Relative Performance of Preemption-Safe Locking and Non-Blocking Synchronization on Multiprogrammed Shared Memory Multiprocessors Maged M. Michael Michael L. Scott University of Rochester Department of
Relative Performance of Preemption-Safe Locking and Non-Blocking Synchronization on Multiprogrammed Shared Memory Multiprocessors Maged M. Michael Michael L. Scott University of Rochester Department of
CSC2/458 Parallel and Distributed Systems Scalable Synchronization
 CSC2/458 Parallel and Distributed Systems Scalable Synchronization Sreepathi Pai February 20, 2018 URCS Outline Scalable Locking Barriers Outline Scalable Locking Barriers An alternative lock ticket lock
CSC2/458 Parallel and Distributed Systems Scalable Synchronization Sreepathi Pai February 20, 2018 URCS Outline Scalable Locking Barriers Outline Scalable Locking Barriers An alternative lock ticket lock
Agenda. Lecture. Next discussion papers. Bottom-up motivation Shared memory primitives Shared memory synchronization Barriers and locks
 Agenda Lecture Bottom-up motivation Shared memory primitives Shared memory synchronization Barriers and locks Next discussion papers Selecting Locking Primitives for Parallel Programming Selecting Locking
Agenda Lecture Bottom-up motivation Shared memory primitives Shared memory synchronization Barriers and locks Next discussion papers Selecting Locking Primitives for Parallel Programming Selecting Locking
AST: scalable synchronization Supervisors guide 2002
 AST: scalable synchronization Supervisors guide 00 tim.harris@cl.cam.ac.uk These are some notes about the topics that I intended the questions to draw on. Do let me know if you find the questions unclear
AST: scalable synchronization Supervisors guide 00 tim.harris@cl.cam.ac.uk These are some notes about the topics that I intended the questions to draw on. Do let me know if you find the questions unclear
SMP T-Kernel Specification
 SMP T-Kernel Specification Ver. 1.00.00 TEF021-S002-01.00.00/en February 2009 SMP T-Kernel Specification (Ver.1.00.00) TEF021-S002-01.00.00/en February 2009 Copyright 2006-2009 T-Engine Forum. All Rights
SMP T-Kernel Specification Ver. 1.00.00 TEF021-S002-01.00.00/en February 2009 SMP T-Kernel Specification (Ver.1.00.00) TEF021-S002-01.00.00/en February 2009 Copyright 2006-2009 T-Engine Forum. All Rights
Verification of Real-Time Systems Resource Sharing
 Verification of Real-Time Systems Resource Sharing Jan Reineke Advanced Lecture, Summer 2015 Resource Sharing So far, we have assumed sets of independent tasks. However, tasks may share resources to communicate
Verification of Real-Time Systems Resource Sharing Jan Reineke Advanced Lecture, Summer 2015 Resource Sharing So far, we have assumed sets of independent tasks. However, tasks may share resources to communicate
CPSC/ECE 3220 Summer 2018 Exam 2 No Electronics.
 CPSC/ECE 3220 Summer 2018 Exam 2 No Electronics. Name: Write one of the words or terms from the following list into the blank appearing to the left of the appropriate definition. Note that there are more
CPSC/ECE 3220 Summer 2018 Exam 2 No Electronics. Name: Write one of the words or terms from the following list into the blank appearing to the left of the appropriate definition. Note that there are more
Distributed Computing Group
 Distributed Computing Group HS 2009 Prof. Dr. Roger Wattenhofer, Thomas Locher, Remo Meier, Benjamin Sigg Assigned: December 11, 2009 Discussion: none Distributed Systems Theory exercise 6 1 ALock2 Have
Distributed Computing Group HS 2009 Prof. Dr. Roger Wattenhofer, Thomas Locher, Remo Meier, Benjamin Sigg Assigned: December 11, 2009 Discussion: none Distributed Systems Theory exercise 6 1 ALock2 Have
Lecture 2: Snooping and Directory Protocols. Topics: Snooping wrap-up and directory implementations
 Lecture 2: Snooping and Directory Protocols Topics: Snooping wrap-up and directory implementations 1 Split Transaction Bus So far, we have assumed that a coherence operation (request, snoops, responses,
Lecture 2: Snooping and Directory Protocols Topics: Snooping wrap-up and directory implementations 1 Split Transaction Bus So far, we have assumed that a coherence operation (request, snoops, responses,
Module 14: "Directory-based Cache Coherence" Lecture 31: "Managing Directory Overhead" Directory-based Cache Coherence: Replacement of S blocks
 Directory-based Cache Coherence: Replacement of S blocks Serialization VN deadlock Starvation Overflow schemes Sparse directory Remote access cache COMA Latency tolerance Page migration Queue lock in hardware
Directory-based Cache Coherence: Replacement of S blocks Serialization VN deadlock Starvation Overflow schemes Sparse directory Remote access cache COMA Latency tolerance Page migration Queue lock in hardware
Single-Path Programming on a Chip-Multiprocessor System
 Single-Path Programming on a Chip-Multiprocessor System Martin Schoeberl, Peter Puschner, and Raimund Kirner Vienna University of Technology, Austria mschoebe@mail.tuwien.ac.at, {peter,raimund}@vmars.tuwien.ac.at
Single-Path Programming on a Chip-Multiprocessor System Martin Schoeberl, Peter Puschner, and Raimund Kirner Vienna University of Technology, Austria mschoebe@mail.tuwien.ac.at, {peter,raimund}@vmars.tuwien.ac.at
Hardware: BBN Butterfly
 Algorithms for Scalable Synchronization on Shared-Memory Multiprocessors John M. Mellor-Crummey and Michael L. Scott Presented by Charles Lehner and Matt Graichen Hardware: BBN Butterfly shared-memory
Algorithms for Scalable Synchronization on Shared-Memory Multiprocessors John M. Mellor-Crummey and Michael L. Scott Presented by Charles Lehner and Matt Graichen Hardware: BBN Butterfly shared-memory
Interprocess Communication By: Kaushik Vaghani
 Interprocess Communication By: Kaushik Vaghani Background Race Condition: A situation where several processes access and manipulate the same data concurrently and the outcome of execution depends on the
Interprocess Communication By: Kaushik Vaghani Background Race Condition: A situation where several processes access and manipulate the same data concurrently and the outcome of execution depends on the
Multiprocessor Synchronization
 Multiprocessor Synchronization Material in this lecture in Henessey and Patterson, Chapter 8 pgs. 694-708 Some material from David Patterson s slides for CS 252 at Berkeley 1 Multiprogramming and Multiprocessing
Multiprocessor Synchronization Material in this lecture in Henessey and Patterson, Chapter 8 pgs. 694-708 Some material from David Patterson s slides for CS 252 at Berkeley 1 Multiprogramming and Multiprocessing
(b) External fragmentation can happen in a virtual memory paging system.
 Alexandria University Faculty of Engineering Electrical Engineering - Communications Spring 2015 Final Exam CS333: Operating Systems Wednesday, June 17, 2015 Allowed Time: 3 Hours Maximum: 75 points Note:
Alexandria University Faculty of Engineering Electrical Engineering - Communications Spring 2015 Final Exam CS333: Operating Systems Wednesday, June 17, 2015 Allowed Time: 3 Hours Maximum: 75 points Note:
CS377P Programming for Performance Multicore Performance Synchronization
 CS377P Programming for Performance Multicore Performance Synchronization Sreepathi Pai UTCS October 21, 2015 Outline 1 Synchronization Primitives 2 Blocking, Lock-free and Wait-free Algorithms 3 Transactional
CS377P Programming for Performance Multicore Performance Synchronization Sreepathi Pai UTCS October 21, 2015 Outline 1 Synchronization Primitives 2 Blocking, Lock-free and Wait-free Algorithms 3 Transactional
Operating System Performance and Large Servers 1
 Operating System Performance and Large Servers 1 Hyuck Yoo and Keng-Tai Ko Sun Microsystems, Inc. Mountain View, CA 94043 Abstract Servers are an essential part of today's computing environments. High
Operating System Performance and Large Servers 1 Hyuck Yoo and Keng-Tai Ko Sun Microsystems, Inc. Mountain View, CA 94043 Abstract Servers are an essential part of today's computing environments. High
The complete license text can be found at
 SMP & Locking These slides are made distributed under the Creative Commons Attribution 3.0 License, unless otherwise noted on individual slides. You are free: to Share to copy, distribute and transmit
SMP & Locking These slides are made distributed under the Creative Commons Attribution 3.0 License, unless otherwise noted on individual slides. You are free: to Share to copy, distribute and transmit
Dr. D. M. Akbar Hussain DE5 Department of Electronic Systems
 Concurrency 1 Concurrency Execution of multiple processes. Multi-programming: Management of multiple processes within a uni- processor system, every system has this support, whether big, small or complex.
Concurrency 1 Concurrency Execution of multiple processes. Multi-programming: Management of multiple processes within a uni- processor system, every system has this support, whether big, small or complex.
CS604 - Operating System Solved Subjective Midterm Papers For Midterm Exam Preparation
 CS604 - Operating System Solved Subjective Midterm Papers For Midterm Exam Preparation The given code is as following; boolean flag[2]; int turn; do { flag[i]=true; turn=j; while(flag[j] && turn==j); critical
CS604 - Operating System Solved Subjective Midterm Papers For Midterm Exam Preparation The given code is as following; boolean flag[2]; int turn; do { flag[i]=true; turn=j; while(flag[j] && turn==j); critical
Transactional Memory: Architectural Support for Lock-Free Data Structures Maurice Herlihy and J. Eliot B. Moss ISCA 93
 Transactional Memory: Architectural Support for Lock-Free Data Structures Maurice Herlihy and J. Eliot B. Moss ISCA 93 What are lock-free data structures A shared data structure is lock-free if its operations
Transactional Memory: Architectural Support for Lock-Free Data Structures Maurice Herlihy and J. Eliot B. Moss ISCA 93 What are lock-free data structures A shared data structure is lock-free if its operations
Advanced Operating Systems (CS 202) Memory Consistency, Cache Coherence and Synchronization
 Advanced Operating Systems (CS 202) Memory Consistency, Cache Coherence and Synchronization (some cache coherence slides adapted from Ian Watson; some memory consistency slides from Sarita Adve) Classic
Advanced Operating Systems (CS 202) Memory Consistency, Cache Coherence and Synchronization (some cache coherence slides adapted from Ian Watson; some memory consistency slides from Sarita Adve) Classic
Multiprocessor System. Multiprocessor Systems. Bus Based UMA. Types of Multiprocessors (MPs) Cache Consistency. Bus Based UMA. Chapter 8, 8.
 Multiprocessor System Multiprocessor Systems Chapter 8, 8.1 We will look at shared-memory multiprocessors More than one processor sharing the same memory A single CPU can only go so fast Use more than
Multiprocessor System Multiprocessor Systems Chapter 8, 8.1 We will look at shared-memory multiprocessors More than one processor sharing the same memory A single CPU can only go so fast Use more than
Queuing Spin Lock Algorithms to Support Timing Predictability
 Queuing Spin Lock Algorithms to Support Timing Predictability Travis S. Craig Department of Computer Science and Engineering, FR-35 University of Washington Seattle, WA 98195 Abstract We introduce practical
Queuing Spin Lock Algorithms to Support Timing Predictability Travis S. Craig Department of Computer Science and Engineering, FR-35 University of Washington Seattle, WA 98195 Abstract We introduce practical
Multiprocessor Systems. COMP s1
 Multiprocessor Systems 1 Multiprocessor System We will look at shared-memory multiprocessors More than one processor sharing the same memory A single CPU can only go so fast Use more than one CPU to improve
Multiprocessor Systems 1 Multiprocessor System We will look at shared-memory multiprocessors More than one processor sharing the same memory A single CPU can only go so fast Use more than one CPU to improve
Remaining Contemplation Questions
 Process Synchronisation Remaining Contemplation Questions 1. The first known correct software solution to the critical-section problem for two processes was developed by Dekker. The two processes, P0 and
Process Synchronisation Remaining Contemplation Questions 1. The first known correct software solution to the critical-section problem for two processes was developed by Dekker. The two processes, P0 and
Mutual Exclusion Algorithms with Constant RMR Complexity and Wait-Free Exit Code
 Mutual Exclusion Algorithms with Constant RMR Complexity and Wait-Free Exit Code Rotem Dvir 1 and Gadi Taubenfeld 2 1 The Interdisciplinary Center, P.O.Box 167, Herzliya 46150, Israel rotem.dvir@gmail.com
Mutual Exclusion Algorithms with Constant RMR Complexity and Wait-Free Exit Code Rotem Dvir 1 and Gadi Taubenfeld 2 1 The Interdisciplinary Center, P.O.Box 167, Herzliya 46150, Israel rotem.dvir@gmail.com
Cache-Aware Lock-Free Queues for Multiple Producers/Consumers and Weak Memory Consistency
 Cache-Aware Lock-Free Queues for Multiple Producers/Consumers and Weak Memory Consistency Anders Gidenstam Håkan Sundell Philippas Tsigas School of business and informatics University of Borås Distributed
Cache-Aware Lock-Free Queues for Multiple Producers/Consumers and Weak Memory Consistency Anders Gidenstam Håkan Sundell Philippas Tsigas School of business and informatics University of Borås Distributed
Operating Systems. Lecture 4 - Concurrency and Synchronization. Master of Computer Science PUF - Hồ Chí Minh 2016/2017
 Operating Systems Lecture 4 - Concurrency and Synchronization Adrien Krähenbühl Master of Computer Science PUF - Hồ Chí Minh 2016/2017 Mutual exclusion Hardware solutions Semaphores IPC: Message passing
Operating Systems Lecture 4 - Concurrency and Synchronization Adrien Krähenbühl Master of Computer Science PUF - Hồ Chí Minh 2016/2017 Mutual exclusion Hardware solutions Semaphores IPC: Message passing
Dr. Rafiq Zakaria Campus. Maulana Azad College of Arts, Science & Commerce, Aurangabad. Department of Computer Science. Academic Year
 Dr. Rafiq Zakaria Campus Maulana Azad College of Arts, Science & Commerce, Aurangabad Department of Computer Science Academic Year 2015-16 MCQs on Operating System Sem.-II 1.What is operating system? a)
Dr. Rafiq Zakaria Campus Maulana Azad College of Arts, Science & Commerce, Aurangabad Department of Computer Science Academic Year 2015-16 MCQs on Operating System Sem.-II 1.What is operating system? a)
Reactive Synchronization Algorithms for Multiprocessors
 Synchronization Algorithms for Multiprocessors Beng-Hong Lim and Anant Agarwal Laboratory for Computer Science Massachusetts Institute of Technology Cambridge, MA 039 Abstract Synchronization algorithms
Synchronization Algorithms for Multiprocessors Beng-Hong Lim and Anant Agarwal Laboratory for Computer Science Massachusetts Institute of Technology Cambridge, MA 039 Abstract Synchronization algorithms
EC 513 Computer Architecture
 EC 513 Computer Architecture Cache Coherence - Directory Cache Coherence Prof. Michel A. Kinsy Shared Memory Multiprocessor Processor Cores Local Memories Memory Bus P 1 Snoopy Cache Physical Memory P
EC 513 Computer Architecture Cache Coherence - Directory Cache Coherence Prof. Michel A. Kinsy Shared Memory Multiprocessor Processor Cores Local Memories Memory Bus P 1 Snoopy Cache Physical Memory P
SYNCHRONIZATION M O D E R N O P E R A T I N G S Y S T E M S R E A D 2. 3 E X C E P T A N D S P R I N G 2018
 SYNCHRONIZATION M O D E R N O P E R A T I N G S Y S T E M S R E A D 2. 3 E X C E P T 2. 3. 8 A N D 2. 3. 1 0 S P R I N G 2018 INTER-PROCESS COMMUNICATION 1. How a process pass information to another process
SYNCHRONIZATION M O D E R N O P E R A T I N G S Y S T E M S R E A D 2. 3 E X C E P T 2. 3. 8 A N D 2. 3. 1 0 S P R I N G 2018 INTER-PROCESS COMMUNICATION 1. How a process pass information to another process
Scalable Spin Locks for Multiprogrammed Systems
 Scalable Spin Locks for Multiprogrammed Systems Robert W. Wisniewski, Leonidas Kontothanassis, and Michael L. Scott bob, kthanasi, and scott@cs.rochester.edu Department of Computer Science University of
Scalable Spin Locks for Multiprogrammed Systems Robert W. Wisniewski, Leonidas Kontothanassis, and Michael L. Scott bob, kthanasi, and scott@cs.rochester.edu Department of Computer Science University of
Marwan Burelle. Parallel and Concurrent Programming
 marwan.burelle@lse.epita.fr http://wiki-prog.infoprepa.epita.fr Outline 1 2 Solutions Overview 1 Sharing Data First, always try to apply the following mantra: Don t share data! When non-scalar data are
marwan.burelle@lse.epita.fr http://wiki-prog.infoprepa.epita.fr Outline 1 2 Solutions Overview 1 Sharing Data First, always try to apply the following mantra: Don t share data! When non-scalar data are
MULTIPROCESSORS AND THREAD LEVEL PARALLELISM
 UNIT III MULTIPROCESSORS AND THREAD LEVEL PARALLELISM 1. Symmetric Shared Memory Architectures: The Symmetric Shared Memory Architecture consists of several processors with a single physical memory shared
UNIT III MULTIPROCESSORS AND THREAD LEVEL PARALLELISM 1. Symmetric Shared Memory Architectures: The Symmetric Shared Memory Architecture consists of several processors with a single physical memory shared
Marwan Burelle. Parallel and Concurrent Programming
 marwan.burelle@lse.epita.fr http://wiki-prog.infoprepa.epita.fr Outline 1 2 3 OpenMP Tell Me More (Go, OpenCL,... ) Overview 1 Sharing Data First, always try to apply the following mantra: Don t share
marwan.burelle@lse.epita.fr http://wiki-prog.infoprepa.epita.fr Outline 1 2 3 OpenMP Tell Me More (Go, OpenCL,... ) Overview 1 Sharing Data First, always try to apply the following mantra: Don t share
Multiprocessors II: CC-NUMA DSM. CC-NUMA for Large Systems
 Multiprocessors II: CC-NUMA DSM DSM cache coherence the hardware stuff Today s topics: what happens when we lose snooping new issues: global vs. local cache line state enter the directory issues of increasing
Multiprocessors II: CC-NUMA DSM DSM cache coherence the hardware stuff Today s topics: what happens when we lose snooping new issues: global vs. local cache line state enter the directory issues of increasing
6.852: Distributed Algorithms Fall, Class 15
 6.852: Distributed Algorithms Fall, 2009 Class 15 Today s plan z z z z z Pragmatic issues for shared-memory multiprocessors Practical mutual exclusion algorithms Test-and-set locks Ticket locks Queue locks
6.852: Distributed Algorithms Fall, 2009 Class 15 Today s plan z z z z z Pragmatic issues for shared-memory multiprocessors Practical mutual exclusion algorithms Test-and-set locks Ticket locks Queue locks
1. Memory technology & Hierarchy
 1. Memory technology & Hierarchy Back to caching... Advances in Computer Architecture Andy D. Pimentel Caches in a multi-processor context Dealing with concurrent updates Multiprocessor architecture In
1. Memory technology & Hierarchy Back to caching... Advances in Computer Architecture Andy D. Pimentel Caches in a multi-processor context Dealing with concurrent updates Multiprocessor architecture In
Wait-Free Multi-Word Compare-And-Swap using Greedy Helping and Grabbing
 Wait-Free Multi-Word Compare-And-Swap using Greedy Helping and Grabbing H. Sundell 1 1 School of Business and Informatics, University of Borås, Borås, Sweden Abstract We present a new algorithm for implementing
Wait-Free Multi-Word Compare-And-Swap using Greedy Helping and Grabbing H. Sundell 1 1 School of Business and Informatics, University of Borås, Borås, Sweden Abstract We present a new algorithm for implementing
Lecture 6: Lazy Transactional Memory. Topics: TM semantics and implementation details of lazy TM
 Lecture 6: Lazy Transactional Memory Topics: TM semantics and implementation details of lazy TM 1 Transactions Access to shared variables is encapsulated within transactions the system gives the illusion
Lecture 6: Lazy Transactional Memory Topics: TM semantics and implementation details of lazy TM 1 Transactions Access to shared variables is encapsulated within transactions the system gives the illusion
Symmetric Multiprocessors: Synchronization and Sequential Consistency
 Constructive Computer Architecture Symmetric Multiprocessors: Synchronization and Sequential Consistency Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology November
Constructive Computer Architecture Symmetric Multiprocessors: Synchronization and Sequential Consistency Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology November
Tasks. Task Implementation and management
 Tasks Task Implementation and management Tasks Vocab Absolute time - real world time Relative time - time referenced to some event Interval - any slice of time characterized by start & end times Duration
Tasks Task Implementation and management Tasks Vocab Absolute time - real world time Relative time - time referenced to some event Interval - any slice of time characterized by start & end times Duration
The Art and Science of Memory Allocation
 Logical Diagram The Art and Science of Memory Allocation Don Porter CSE 506 Binary Formats RCU Memory Management Memory Allocators CPU Scheduler User System Calls Kernel Today s Lecture File System Networking
Logical Diagram The Art and Science of Memory Allocation Don Porter CSE 506 Binary Formats RCU Memory Management Memory Allocators CPU Scheduler User System Calls Kernel Today s Lecture File System Networking
Advanced Operating Systems (CS 202) Memory Consistency, Cache Coherence and Synchronization
 Advanced Operating Systems (CS 202) Memory Consistency, Cache Coherence and Synchronization Jan, 27, 2017 (some cache coherence slides adapted from Ian Watson; some memory consistency slides from Sarita
Advanced Operating Systems (CS 202) Memory Consistency, Cache Coherence and Synchronization Jan, 27, 2017 (some cache coherence slides adapted from Ian Watson; some memory consistency slides from Sarita
Operating Systems (1DT020 & 1TT802)
 Uppsala University Department of Information Technology Name: Perso. no: Operating Systems (1DT020 & 1TT802) 2009-05-27 This is a closed book exam. Calculators are not allowed. Answers should be written
Uppsala University Department of Information Technology Name: Perso. no: Operating Systems (1DT020 & 1TT802) 2009-05-27 This is a closed book exam. Calculators are not allowed. Answers should be written
Processes and Threads. Processes: Review
 Processes and Threads Processes and their scheduling Threads and scheduling Multiprocessor scheduling Distributed Scheduling/migration Lecture 3, page 1 Processes: Review Multiprogramming versus multiprocessing
Processes and Threads Processes and their scheduling Threads and scheduling Multiprocessor scheduling Distributed Scheduling/migration Lecture 3, page 1 Processes: Review Multiprogramming versus multiprocessing
Concurrency, Mutual Exclusion and Synchronization C H A P T E R 5
 Concurrency, Mutual Exclusion and Synchronization C H A P T E R 5 Multiple Processes OS design is concerned with the management of processes and threads: Multiprogramming Multiprocessing Distributed processing
Concurrency, Mutual Exclusion and Synchronization C H A P T E R 5 Multiple Processes OS design is concerned with the management of processes and threads: Multiprogramming Multiprocessing Distributed processing
Chapter 5. Thread-Level Parallelism
 Chapter 5 Thread-Level Parallelism Instructor: Josep Torrellas CS433 Copyright Josep Torrellas 1999, 2001, 2002, 2013 1 Progress Towards Multiprocessors + Rate of speed growth in uniprocessors saturated
Chapter 5 Thread-Level Parallelism Instructor: Josep Torrellas CS433 Copyright Josep Torrellas 1999, 2001, 2002, 2013 1 Progress Towards Multiprocessors + Rate of speed growth in uniprocessors saturated
Algorithms for Scalable Lock Synchronization on Shared-memory Multiprocessors
 Algorithms for Scalable Lock Synchronization on Shared-memory Multiprocessors John Mellor-Crummey Department of Computer Science Rice University johnmc@rice.edu COMP 422/534 Lecture 21 30 March 2017 Summary
Algorithms for Scalable Lock Synchronization on Shared-memory Multiprocessors John Mellor-Crummey Department of Computer Science Rice University johnmc@rice.edu COMP 422/534 Lecture 21 30 March 2017 Summary
Scalable Locking. Adam Belay
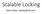 Scalable Locking Adam Belay Problem: Locks can ruin performance 12 finds/sec 9 6 Locking overhead dominates 3 0 0 6 12 18 24 30 36 42 48 Cores Problem: Locks can ruin performance the locks
Scalable Locking Adam Belay Problem: Locks can ruin performance 12 finds/sec 9 6 Locking overhead dominates 3 0 0 6 12 18 24 30 36 42 48 Cores Problem: Locks can ruin performance the locks
CPU Scheduling. The scheduling problem: When do we make decision? - Have K jobs ready to run - Have N 1 CPUs - Which jobs to assign to which CPU(s)
 CPU Scheduling The scheduling problem: - Have K jobs ready to run - Have N 1 CPUs - Which jobs to assign to which CPU(s) When do we make decision? 1 / 31 CPU Scheduling new admitted interrupt exit terminated
CPU Scheduling The scheduling problem: - Have K jobs ready to run - Have N 1 CPUs - Which jobs to assign to which CPU(s) When do we make decision? 1 / 31 CPU Scheduling new admitted interrupt exit terminated
Algorithms for Scalable Lock Synchronization on Shared-memory Multiprocessors
 Algorithms for Scalable Lock Synchronization on Shared-memory Multiprocessors John Mellor-Crummey Department of Computer Science Rice University johnmc@cs.rice.edu COMP 422 Lecture 18 17 March 2009 Summary
Algorithms for Scalable Lock Synchronization on Shared-memory Multiprocessors John Mellor-Crummey Department of Computer Science Rice University johnmc@cs.rice.edu COMP 422 Lecture 18 17 March 2009 Summary
Module 7: Synchronization Lecture 13: Introduction to Atomic Primitives. The Lecture Contains: Synchronization. Waiting Algorithms.
 The Lecture Contains: Synchronization Waiting Algorithms Implementation Hardwired Locks Software Locks Hardware Support Atomic Exchange Test & Set Fetch & op Compare & Swap Traffic of Test & Set Backoff
The Lecture Contains: Synchronization Waiting Algorithms Implementation Hardwired Locks Software Locks Hardware Support Atomic Exchange Test & Set Fetch & op Compare & Swap Traffic of Test & Set Backoff
Distributed Operating Systems
 Distributed Operating Systems Synchronization in Parallel Systems Marcus Völp 2009 1 Topics Synchronization Locking Analysis / Comparison Distributed Operating Systems 2009 Marcus Völp 2 Overview Introduction
Distributed Operating Systems Synchronization in Parallel Systems Marcus Völp 2009 1 Topics Synchronization Locking Analysis / Comparison Distributed Operating Systems 2009 Marcus Völp 2 Overview Introduction
What is the Race Condition? And what is its solution? What is a critical section? And what is the critical section problem?
 What is the Race Condition? And what is its solution? Race Condition: Where several processes access and manipulate the same data concurrently and the outcome of the execution depends on the particular
What is the Race Condition? And what is its solution? Race Condition: Where several processes access and manipulate the same data concurrently and the outcome of the execution depends on the particular
Synchronization. Jinkyu Jeong Computer Systems Laboratory Sungkyunkwan University
 Synchronization Jinkyu Jeong (jinkyu@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Types of Synchronization Mutual Exclusion Locks Event Synchronization Global or group-based
Synchronization Jinkyu Jeong (jinkyu@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Types of Synchronization Mutual Exclusion Locks Event Synchronization Global or group-based
Synchronization. Jinkyu Jeong Computer Systems Laboratory Sungkyunkwan University
 Synchronization Jinkyu Jeong (jinkyu@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu SSE3054: Multicore Systems, Spring 2017, Jinkyu Jeong (jinkyu@skku.edu) Types of Synchronization
Synchronization Jinkyu Jeong (jinkyu@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu SSE3054: Multicore Systems, Spring 2017, Jinkyu Jeong (jinkyu@skku.edu) Types of Synchronization
Computer Architecture
 Jens Teubner Computer Architecture Summer 2016 1 Computer Architecture Jens Teubner, TU Dortmund jens.teubner@cs.tu-dortmund.de Summer 2016 Jens Teubner Computer Architecture Summer 2016 83 Part III Multi-Core
Jens Teubner Computer Architecture Summer 2016 1 Computer Architecture Jens Teubner, TU Dortmund jens.teubner@cs.tu-dortmund.de Summer 2016 Jens Teubner Computer Architecture Summer 2016 83 Part III Multi-Core
Chapter 5: Process Synchronization. Operating System Concepts Essentials 2 nd Edition
 Chapter 5: Process Synchronization Silberschatz, Galvin and Gagne 2013 Chapter 5: Process Synchronization Background The Critical-Section Problem Peterson s Solution Synchronization Hardware Mutex Locks
Chapter 5: Process Synchronization Silberschatz, Galvin and Gagne 2013 Chapter 5: Process Synchronization Background The Critical-Section Problem Peterson s Solution Synchronization Hardware Mutex Locks
Lecture 4: Directory Protocols and TM. Topics: corner cases in directory protocols, lazy TM
 Lecture 4: Directory Protocols and TM Topics: corner cases in directory protocols, lazy TM 1 Handling Reads When the home receives a read request, it looks up memory (speculative read) and directory in
Lecture 4: Directory Protocols and TM Topics: corner cases in directory protocols, lazy TM 1 Handling Reads When the home receives a read request, it looks up memory (speculative read) and directory in
Synchronization. Heechul Yun
 Synchronization Heechul Yun 1 Recap: Semaphore High-level synchronization primitive Designed by Dijkstra in 1960 Definition Semaphore is an integer variable Only two operations are possible: P() or wait()
Synchronization Heechul Yun 1 Recap: Semaphore High-level synchronization primitive Designed by Dijkstra in 1960 Definition Semaphore is an integer variable Only two operations are possible: P() or wait()
Lecture 8: Directory-Based Cache Coherence. Topics: scalable multiprocessor organizations, directory protocol design issues
 Lecture 8: Directory-Based Cache Coherence Topics: scalable multiprocessor organizations, directory protocol design issues 1 Scalable Multiprocessors P1 P2 Pn C1 C2 Cn 1 CA1 2 CA2 n CAn Scalable interconnection
Lecture 8: Directory-Based Cache Coherence Topics: scalable multiprocessor organizations, directory protocol design issues 1 Scalable Multiprocessors P1 P2 Pn C1 C2 Cn 1 CA1 2 CA2 n CAn Scalable interconnection
UNIX Input/Output Buffering
 UNIX Input/Output Buffering When a C/C++ program begins execution, the operating system environment is responsible for opening three files and providing file pointers to them: stdout standard output stderr
UNIX Input/Output Buffering When a C/C++ program begins execution, the operating system environment is responsible for opening three files and providing file pointers to them: stdout standard output stderr
CPU Scheduling. The scheduling problem: When do we make decision? - Have K jobs ready to run - Have N 1 CPUs - Which jobs to assign to which CPU(s)
 1/32 CPU Scheduling The scheduling problem: - Have K jobs ready to run - Have N 1 CPUs - Which jobs to assign to which CPU(s) When do we make decision? 2/32 CPU Scheduling Scheduling decisions may take
1/32 CPU Scheduling The scheduling problem: - Have K jobs ready to run - Have N 1 CPUs - Which jobs to assign to which CPU(s) When do we make decision? 2/32 CPU Scheduling Scheduling decisions may take
Page 1. Cache Coherence
 Page 1 Cache Coherence 1 Page 2 Memory Consistency in SMPs CPU-1 CPU-2 A 100 cache-1 A 100 cache-2 CPU-Memory bus A 100 memory Suppose CPU-1 updates A to 200. write-back: memory and cache-2 have stale
Page 1 Cache Coherence 1 Page 2 Memory Consistency in SMPs CPU-1 CPU-2 A 100 cache-1 A 100 cache-2 CPU-Memory bus A 100 memory Suppose CPU-1 updates A to 200. write-back: memory and cache-2 have stale
Suggested Solutions (Midterm Exam October 27, 2005)
 Suggested Solutions (Midterm Exam October 27, 2005) 1 Short Questions (4 points) Answer the following questions (True or False). Use exactly one sentence to describe why you choose your answer. Without
Suggested Solutions (Midterm Exam October 27, 2005) 1 Short Questions (4 points) Answer the following questions (True or False). Use exactly one sentence to describe why you choose your answer. Without
Multiprocessor Real-Time Locking Protocols: from Homogeneous to Heterogeneous
 Multiprocessor Real-Time Locking Protocols: from Homogeneous to Heterogeneous Kecheng Yang Department of Computer Science, University of North Carolina at Chapel Hill Abstract In this project, we focus
Multiprocessor Real-Time Locking Protocols: from Homogeneous to Heterogeneous Kecheng Yang Department of Computer Science, University of North Carolina at Chapel Hill Abstract In this project, we focus
Operating Systems Comprehensive Exam. There are five questions on this exam. Please answer any four questions total
 Operating Systems Comprehensive Exam There are five questions on this exam. Please answer any four questions. ID 1 2 3 4 5 total 1) The following questions pertain to McKusick et al's A Fast File System
Operating Systems Comprehensive Exam There are five questions on this exam. Please answer any four questions. ID 1 2 3 4 5 total 1) The following questions pertain to McKusick et al's A Fast File System
Panu Silvasti Page 1
 Multicore support in databases Panu Silvasti Page 1 Outline Building blocks of a storage manager How do existing storage managers scale? Optimizing Shore database for multicore processors Page 2 Building
Multicore support in databases Panu Silvasti Page 1 Outline Building blocks of a storage manager How do existing storage managers scale? Optimizing Shore database for multicore processors Page 2 Building
Chapter 5: Process Synchronization. Operating System Concepts 9 th Edition
 Chapter 5: Process Synchronization Silberschatz, Galvin and Gagne 2013 Chapter 5: Process Synchronization Background The Critical-Section Problem Peterson s Solution Synchronization Hardware Mutex Locks
Chapter 5: Process Synchronization Silberschatz, Galvin and Gagne 2013 Chapter 5: Process Synchronization Background The Critical-Section Problem Peterson s Solution Synchronization Hardware Mutex Locks
Main Points of the Computer Organization and System Software Module
 Main Points of the Computer Organization and System Software Module You can find below the topics we have covered during the COSS module. Reading the relevant parts of the textbooks is essential for a
Main Points of the Computer Organization and System Software Module You can find below the topics we have covered during the COSS module. Reading the relevant parts of the textbooks is essential for a
Nested Multiprocessor Real-Time Locking with Improved Blocking
 Nested Multiprocessor Real-Time Locking with Improved Blocking Bryan C. Ward and James H. Anderson Department of Computer Science, University of North Carolina at Chapel Hill Abstract Existing multiprocessor
Nested Multiprocessor Real-Time Locking with Improved Blocking Bryan C. Ward and James H. Anderson Department of Computer Science, University of North Carolina at Chapel Hill Abstract Existing multiprocessor
10/17/2011. Cooperating Processes. Synchronization 1. Example: Producer Consumer (3) Example
 Cooperating Processes Synchronization 1 Chapter 6.1 4 processes share something (devices such as terminal, keyboard, mouse, etc., or data structures) and can affect each other non deterministic Not exactly
Cooperating Processes Synchronization 1 Chapter 6.1 4 processes share something (devices such as terminal, keyboard, mouse, etc., or data structures) and can affect each other non deterministic Not exactly
AUTOSAR Extensions for Predictable Task Synchronization in Multi- Core ECUs
 11AE-0089 AUTOSAR Extensions for Predictable Task Synchronization in Multi- Core ECUs Copyright 2011 SAE International Karthik Lakshmanan, Gaurav Bhatia, Ragunathan (Raj) Rajkumar Carnegie Mellon University
11AE-0089 AUTOSAR Extensions for Predictable Task Synchronization in Multi- Core ECUs Copyright 2011 SAE International Karthik Lakshmanan, Gaurav Bhatia, Ragunathan (Raj) Rajkumar Carnegie Mellon University
General Objectives: To understand the process management in operating system. Specific Objectives: At the end of the unit you should be able to:
 F2007/Unit5/1 UNIT 5 OBJECTIVES General Objectives: To understand the process management in operating system Specific Objectives: At the end of the unit you should be able to: define program, process and
F2007/Unit5/1 UNIT 5 OBJECTIVES General Objectives: To understand the process management in operating system Specific Objectives: At the end of the unit you should be able to: define program, process and
Operating Systems: Quiz2 December 15, Class: No. Name:
 Operating Systems: Quiz2 December 15, 2006 Class: No. Name: Part I (30%) Multiple Choice Each of the following questions has only one correct answer. Fill the correct one in the blank in front of each
Operating Systems: Quiz2 December 15, 2006 Class: No. Name: Part I (30%) Multiple Choice Each of the following questions has only one correct answer. Fill the correct one in the blank in front of each
1 Multiprocessors. 1.1 Kinds of Processes. COMP 242 Class Notes Section 9: Multiprocessor Operating Systems
 COMP 242 Class Notes Section 9: Multiprocessor Operating Systems 1 Multiprocessors As we saw earlier, a multiprocessor consists of several processors sharing a common memory. The memory is typically divided
COMP 242 Class Notes Section 9: Multiprocessor Operating Systems 1 Multiprocessors As we saw earlier, a multiprocessor consists of several processors sharing a common memory. The memory is typically divided
COMP 3361: Operating Systems 1 Final Exam Winter 2009
 COMP 3361: Operating Systems 1 Final Exam Winter 2009 Name: Instructions This is an open book exam. The exam is worth 100 points, and each question indicates how many points it is worth. Read the exam
COMP 3361: Operating Systems 1 Final Exam Winter 2009 Name: Instructions This is an open book exam. The exam is worth 100 points, and each question indicates how many points it is worth. Read the exam
Lecture 18: Coherence Protocols. Topics: coherence protocols for symmetric and distributed shared-memory multiprocessors (Sections
 Lecture 18: Coherence Protocols Topics: coherence protocols for symmetric and distributed shared-memory multiprocessors (Sections 4.2-4.4) 1 SMP/UMA/Centralized Memory Multiprocessor Main Memory I/O System
Lecture 18: Coherence Protocols Topics: coherence protocols for symmetric and distributed shared-memory multiprocessors (Sections 4.2-4.4) 1 SMP/UMA/Centralized Memory Multiprocessor Main Memory I/O System
Introduction to OS Synchronization MOS 2.3
 Introduction to OS Synchronization MOS 2.3 Mahmoud El-Gayyar elgayyar@ci.suez.edu.eg Mahmoud El-Gayyar / Introduction to OS 1 Challenge How can we help processes synchronize with each other? E.g., how
Introduction to OS Synchronization MOS 2.3 Mahmoud El-Gayyar elgayyar@ci.suez.edu.eg Mahmoud El-Gayyar / Introduction to OS 1 Challenge How can we help processes synchronize with each other? E.g., how
more complex. Since there are many avors of PI, I'll begin by making a precise denition of simple priority inheritance (SPI) and then consider enhance
 The dangers of priority inheritance cvictor Yodaiken Department of Computer Science New Mexico Institute of Technology yodaiken@cs.nmt.edu DRAFT (corrections and comments appreciated) The recent use of
The dangers of priority inheritance cvictor Yodaiken Department of Computer Science New Mexico Institute of Technology yodaiken@cs.nmt.edu DRAFT (corrections and comments appreciated) The recent use of
CPS 310 second midterm exam, 11/14/2014
 CPS 310 second midterm exam, 11/14/2014 Your name please: Part 1. Sticking points Consider the Java code snippet below. Is it a legal use of Java synchronization? What happens if two threads A and B call
CPS 310 second midterm exam, 11/14/2014 Your name please: Part 1. Sticking points Consider the Java code snippet below. Is it a legal use of Java synchronization? What happens if two threads A and B call
