It Might Be Valid, But It's Still Wrong Paul Maskens and Andy Kramek
|
|
|
- Alison Fitzgerald
- 5 years ago
- Views:
Transcription
1 Seite 1 von 5 Issue Date: FoxTalk July 2000 It Might Be Valid, But It's Still Wrong Paul Maskens and Andy Kramek This month, Paul Maskens and Andy Kramek discuss the problems of validating data entry. Paul: Okay, Andy, let's see what you make of this one. I have a simple data entry form for inserting a name, address, and phone number into a table. What I want to do is to make sure that the data is valid, so the question is: What sort of code should I be using, and where should I put it? Andy: Well, I'd say that it all depends on what you mean by a "Form," what you mean by a "Table," and, most importantly of all, what you mean by "Valid." Paul: That sort of cop-out won't do! This is a very real problem just how should we set about handling validation of user input. In the good old FoxPro 2.6 days, I've have simply used the VALID snippet of a control and put the code right in there. Andy: But my answer wasn't a cop-out, Paul. The issue of what sort of code, and where to place it, does depend on those three things! For example, if the "Form" is a simple data entry form running inside a VFP application directly against a local VFP table, then there's no problem just put the code into the Valid method of the controls. However, if your "Form" is actually being displayed in a Web browser, or is accessing remote data through ODBC, then you have a whole different set of problems. Paul: And that's is precisely my point where should the validation go then? In the Database Container? Andy: Well, that depends on what you mean by a "Table." Again, if we're talking a pure VFP solution, then it might be possible. But it's not going to work if you're using SQL Pass-Through to access a back-end data server you don't actually have tables in a DBC in that situation. Paul: Hmph! We don't seem to be getting very far. Maybe we should review the possibilities and see where that takes us? Andy: Sounds good to me. Let's start with the design (now there's a novel concept <g>). What are you actually trying to build, and on what sort of platform is it going to run? Paul: I don't know! Actually, on reflection, perhaps it would be more accurate to say that I can't predict how this application is going to evolve. What I can be sure of is that I can't afford to tie myself to a "pure VFP" solution. I must at least plan for the possibility that this application will have to run against a remote data source and might even require multiple user interfaces. Andy: Good, we have a starting point, then. What you're saying is that we'll need to use at least a three-tier model, and we should probably plan for a true n-tier architecture. Paul: I've never really been happy about this distinction. When does a three-tier model become n-tier? Andy: I don't think it works like that. The basis of the designs is completely different. But I agree that the terminology is certainly unclear. I think that the difference is best illustrated diagrammatically. Figure 1 is a layered three-tier model. Figure 1: Layered tree-tier architecture. Paul: Yes, that looks right. Each tier comprises a number of layers, and there are always at least three: an "upward" and a "downward" interface, and a core, which may itself be made up of a number of layers. The basic rule here is that any layer may have knowledge of only the layer immediately below itself. Andy: That's a very important rule too! In this diagram, the middle tier's UI Interface Layer doesn't need to know anything about what exists above itself, but must know how to address the Rules Layer below. Conversely all that the User Interface needs to know about is the Public Interface of the Middle Tier. Paul: Which, yet again, emphasizes the importance of programming to interface, not implementation. So for the n-tier model,
2 Seite 2 von 5 what's different? Andy: In practice, nothing. What we're really doing is dividing the tiers into separate functional components, as opposed to incorporating the functionality into layers within a single tier. An n-tier diagram might look something like Figure 2. Figure 2: N-tier architecture. Paul: Ah, I see. As we have the three-tier model drawn, the middle tier must include both the actual business rules and the necessary functionality to communicate with the data tier. So if more than one application wants to share the same data, we'd need to duplicate that code in a different middle-tier object. Andy: Exactly in the n-tier model, the task of communicating with the database is no longer part of the middle tier, but is separate in its own right. Paul: That's very clear, Andy. A picture really is worth a thousand words in this case. I agree that the n-tier model is the way we should go, though the price to pay is obviously going to be a more complex set of interfaces and an increase in messaging. But at the risk of keeping to the point, where should our validation go then? Andy: The diagram makes it pretty clear that it really has to go in either the Application Rules Tier, the Data Tier, or both. Paul: I can see why you're saying the Application Rules anything above that tier really has to be UI-specific and, since we're looking for data validation, that should be independent of the UI. I don't see why you'd have validation in both places, though. Andy: That would depend on the implementation. But in general I'd say that business rules must be implemented only in the Rules Tiers and integrity rules only in the Data Tier. Paul: I'm not sure that I follow your distinction here we're not back into "what is data" again, are we? Andy: Not quite <bg>. There's a distinction between rules that are required for enforcing the integrity of data and those that are purely business related. Paul: So what you're saying is that a rule like this: "An entry to the Orders table must reference a valid entry in the Customer table." is a data integrity rule, while "All entries in the Customer table must have a telephone number." is merely a business rule? Andy: Exactly. Violating the first would break the referential integrity of your database, and so it must be implemented in, and by, the database through whatever mechanism it provides for enforcing referential integrity. The second, however, doesn't really matter to the database one way or the other. If a customer record is missing the telephone number field, it won't change my ability to access the database in any way (other than by searching via telephone number, of course). Paul: I have no problem with the database enforcing referential integrity that seems entirely proper. But you also seem to be saying that we should not be enforcing field- and, by extension, record-level validation in the database. If that were really the case, then why would databases have field- and record-level validation rules built into them? Andy: Well, actually they don't. Built-in field/record-level validation is a feature of the Visual FoxPro DBC, but it's not a normal part of a SQL database. Such validation is enforced either through index constraints or in triggers and stored procedures. Some back-end databases will allow for default values to be specified in the table definition, but I don't know of one that permits field-level validation like Visual FoxPro does. Paul: Ah! So it's Visual FoxPro that's out of line here, not other databases. I suppose this is a consequence of the way in which the DBC has to be implemented in a file-based database like Visual FoxPro. Andy: That seems a reasonable assumption, but I wouldn't really know. So where are we now in terms of your original question? Paul: Well, I think we're agreed that I need to implement an n-tier design and that the job of maintaining the referential integrity
3 Seite 3 von 5 will be left to the database. Business rules will be enforced in their own tier, which will provide a standard interface so that different presentation tiers can access them. That leaves only the issue of "assistive validation" to be addressed, then. Andy: Assistive validation? What does that mean? Paul: I mean validation placed in the UI with the objective of assisting the user during data input. One thing that really annoys me is the kind of interface where I enter a whole lot of data, hit the Save key, and the damn thing then sneers at me and says something like "You may not leave the telephone number field blank!" Assistive validation means trapping this sort of thing immediately when it occurs, rather than waiting for the results of the submission process. Andy: Oh boy, Paul, you really must hate the Web interfaces then <g>. Very few of them have this sort of validation, but I can see where you're coming from, and you do have a good point. Paul: Of course, to implement it we should be making calls into the Application Tier rather than simply adding yet more code to the UI and duplicating functionality. Andy: Good, that sounds very reasonable. Most importantly, it also provides for situations in which different business rules may apply to the same set of data in different circumstances. Paul: Huh? How can two sets of rules apply to the same data; surely that's not very sensible. Andy: On the contrary, it can easily happen. Consider the case where you have a common table in which the addresses and phone numbers of all people with whom you deal are stored. It might be entirely reasonable to say that a "supplier" must have a telephone number, but surely an employee need not have one? If you were to enforce the "must have a telephone number" rule in the database, either you'd be unable to employ someone unless they had a telephone, or you'd need a special table for storing the addresses of employees. Paul: Or, more likely, the users will just put some dummy or meaningless information into the telephone number field. Which brings us back to the specific problem I originally wanted to address how should we validate user input fields? Andy: I suppose that there are essentially four situations with which we have to deal and each requires a different solution. Paul: I think I see where you're going; let me guess. First is "Choose a Value from a List." Andy: Absolutely! This one is easy to deal with because we can use a list or combo box and simply populate it with all the valid options, and only the valid options! If necessary, we can force a default by setting the ListIndex property to the appropriate value. Paul: I'd go further and say that a default is always necessary when using a predefined list from which an option must be chosen. Andy: I wouldn't disagree there. The second case is where there's a list of possible values, but new ones can be added by the user at runtime. You could just use a standard combo box to cover this. Paul: No, I don't like that idea at all. The combo box will allow you to enter data for only one field directly. I'm much more likely to use a lookup table that includes a primary key, code, and description. I could add only one field in the combo, so I'd much prefer to have a proper data entry form called when a new entry to the list is required. Andy: Good, we're agreed on that one too. So for both of these situations, the issue of validation has to be addressed when an item is added to the list rather than in the application at runtime. Paul: Ah, but in the second case, the addition of the item is actually going to happen at runtime. Andy: That could be true for either case don't you include pick-list maintenance screens in your application? Paul: Of course, so what we're saying is that using list-based values merely shifts the problem of validation to the point at which the item is added to the list. Andy: Yes, in reality we come down to only two situations. Either we're dealing with "formatted" or "unformatted" input. Paul: What do you mean by "formatted"? You don't just mean using the Format or InputMask properties, do you? Andy: No. Although they're useful in many circumstances, they're applicable only when we're actually using Visual FoxPro directly (either as DBC properties or as properties of native controls). I mean input where we can define a value's type, range, or both.
4 Seite 4 von 5 Paul: Specifying that a value must be a "date" would qualify it as formatted input, then? Andy: Yes, because there are standard rules for checking dates. Similarly, specifying that a value must be a number between 0 and 10 would qualify as formatted. Paul: But now you're implying that this should go into the User Interface by setting up a Visual FoxPro text box with a date value, for example. Andy: Not at all! The fact that, in the Visual FoxPro-based UI we can set up a text box to accept only date values is a bonus, but it doesn't relieve us of the necessity to ensure, in the Application Rules tier, that the value that's been supplied is actually appropriate. Paul: Ah! You're talking about ensuring that the value supplied is actually valid for the purpose for which it's been entered! For example, if we want to specify a start and an end date for a reporting period, we can use a date text box control in the UI to ensure that the user can enter only dates. However, the check that the end date is later than the start date still belongs in the Application Rules. Andy: I'd say that you need to check both that the value is really a date and that it conforms to the business rules. The same applies to any other formatted entry. Paul: This implies that there are two stages to validating formatted inputs. The first is to ensure that the input supplied is of the correct type. This might be enforced in the UI assuming it supports the necessary functionality but should still be checked in the Application Rules. The second is to ensure that the input is valid in the context of the application, which must be done in the rules tier. That seems entirely reasonable, but what about unformatted input? Andy: That's a more difficult problem. Since we're saying that the input isn't formatted, by definition we can't know what it's supposed to contain, and therefore the only approach we can take is to ensure that it is not invalid. Paul: That suggests that the first stage of validation is actually the same whether we're dealing with formatted or unformatted data, then? Andy: And so it is. The second-stage validation is what differs. Paul: So maybe first-stage validation could be implemented as a separate layer. That would help with the assistive validation too! Andy: Nice one! I hadn't thought of that. Paul: But, as always, as soon as we start saying things are the same, we should be thinking in terms of abstracting the implicit functionality. At least, that's what you keep telling me! Andy: Okay, I just hadn't thought of it in those terms. So, when we're dealing with formatted data, we can apply positive rules because we know what the data must look like. Conversely, for unformatted data, all we can apply are negative rules because all we know is what it can't look like. Paul: Coming back to my name, address, and telephone number example (which is where we started), I can see that I'm in trouble. There's no universal format for a name, for an address, or even for a telephone number! Andy: I'm afraid not. Of course you might be able to define some local rules. Addresses and phone numbers within the UK do conform to some basic standards, and so do those in the USA, although the standard is different, of course. Paul: Yes, I can see how to do that all right. A simple root class, specialized for different locations and implemented at runtime using a strategy based on locale would handle it. But the actual validation still bothers me. Andy: It will, because what you're really dealing with in this situation is unformatted data and, as we just said, all you can do is apply negative rules. Paul: So the best I can do is to say that the telephone number must be a character string containing at least nine and not more than 13 digits, can't be empty, and might (or might not) contain a "+" or a "-" or parentheses or periods. Andy: If those are the rules that you want to apply, then yes. Of course, you could include a look-up into a list of valid area codes and even apply formatting rules to the numbers if appropriate. Paul: This is my real problem. I was hoping that I could stop my users from doing things (like entering telephone numbers that don't exist) to bypass the validation and so have a greater degree of confidence that this data would be valid. But I can see
5 Seite 5 von 5 that I can't. Andy: Sorry to disagree with you there, Paul. You can always ensure that the data is valid, what you can't do is to ensure that it is right! This is the fundamental problem with all data entry. No matter how carefully you validate your data, there's no way to detect when an input is wrong if it meets the rules. After all, your software can't possibly know that the name "Paul Maskers" should really have been entered as "Paul Maskens." Paul: Of course. So the conclusion is that, while we can check that data is entered according to rules, and we can even specify those rules at various levels, there's just no software solution to the problem of data that is "valid, but wrong."
MITOCW ocw f99-lec07_300k
 MITOCW ocw-18.06-f99-lec07_300k OK, here's linear algebra lecture seven. I've been talking about vector spaces and specially the null space of a matrix and the column space of a matrix. What's in those
MITOCW ocw-18.06-f99-lec07_300k OK, here's linear algebra lecture seven. I've been talking about vector spaces and specially the null space of a matrix and the column space of a matrix. What's in those
Post Experiment Interview Questions
 Post Experiment Interview Questions Questions about the Maximum Problem 1. What is this problem statement asking? 2. What is meant by positive integers? 3. What does it mean by the user entering valid
Post Experiment Interview Questions Questions about the Maximum Problem 1. What is this problem statement asking? 2. What is meant by positive integers? 3. What does it mean by the user entering valid
Formal Methods of Software Design, Eric Hehner, segment 24 page 1 out of 5
 Formal Methods of Software Design, Eric Hehner, segment 24 page 1 out of 5 [talking head] This lecture we study theory design and implementation. Programmers have two roles to play here. In one role, they
Formal Methods of Software Design, Eric Hehner, segment 24 page 1 out of 5 [talking head] This lecture we study theory design and implementation. Programmers have two roles to play here. In one role, they
In our first lecture on sets and set theory, we introduced a bunch of new symbols and terminology.
 Guide to and Hi everybody! In our first lecture on sets and set theory, we introduced a bunch of new symbols and terminology. This guide focuses on two of those symbols: and. These symbols represent concepts
Guide to and Hi everybody! In our first lecture on sets and set theory, we introduced a bunch of new symbols and terminology. This guide focuses on two of those symbols: and. These symbols represent concepts
Instructor: Craig Duckett. Lecture 04: Thursday, April 5, Relationships
 Instructor: Craig Duckett Lecture 04: Thursday, April 5, 2018 Relationships 1 Assignment 1 is due NEXT LECTURE 5, Tuesday, April 10 th in StudentTracker by MIDNIGHT MID-TERM EXAM is LECTURE 10, Tuesday,
Instructor: Craig Duckett Lecture 04: Thursday, April 5, 2018 Relationships 1 Assignment 1 is due NEXT LECTURE 5, Tuesday, April 10 th in StudentTracker by MIDNIGHT MID-TERM EXAM is LECTURE 10, Tuesday,
Formal Methods of Software Design, Eric Hehner, segment 1 page 1 out of 5
 Formal Methods of Software Design, Eric Hehner, segment 1 page 1 out of 5 [talking head] Formal Methods of Software Engineering means the use of mathematics as an aid to writing programs. Before we can
Formal Methods of Software Design, Eric Hehner, segment 1 page 1 out of 5 [talking head] Formal Methods of Software Engineering means the use of mathematics as an aid to writing programs. Before we can
The following content is provided under a Creative Commons license. Your support
 MITOCW Lecture 9 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To make a donation
MITOCW Lecture 9 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To make a donation
Skill 1: Multiplying Polynomials
 CS103 Spring 2018 Mathematical Prerequisites Although CS103 is primarily a math class, this course does not require any higher math as a prerequisite. The most advanced level of mathematics you'll need
CS103 Spring 2018 Mathematical Prerequisites Although CS103 is primarily a math class, this course does not require any higher math as a prerequisite. The most advanced level of mathematics you'll need
So the UI needs to change when the button changes. When the button becomes submit it needs to change color and get bigger.
 Things to improve in the user interface. The bottom right button. In some screens it is continue and in other screens it is submit. The problem is that the user gets in the habit of simply always clicking
Things to improve in the user interface. The bottom right button. In some screens it is continue and in other screens it is submit. The problem is that the user gets in the habit of simply always clicking
Linked Lists. What is a Linked List?
 Linked Lists Along with arrays, linked lists form the basis for pretty much every other data stucture out there. This makes learning and understand linked lists very important. They are also usually the
Linked Lists Along with arrays, linked lists form the basis for pretty much every other data stucture out there. This makes learning and understand linked lists very important. They are also usually the
I'm Andy Glover and this is the Java Technical Series of. the developerworks podcasts. My guest is Brian Jakovich. He is the
 I'm Andy Glover and this is the Java Technical Series of the developerworks podcasts. My guest is Brian Jakovich. He is the director of Elastic Operations for Stelligent. He and I are going to talk about
I'm Andy Glover and this is the Java Technical Series of the developerworks podcasts. My guest is Brian Jakovich. He is the director of Elastic Operations for Stelligent. He and I are going to talk about
Binary Search Trees. Carlos Moreno uwaterloo.ca EIT https://ece.uwaterloo.ca/~cmoreno/ece250
 Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 https://ece.uwaterloo.ca/~cmoreno/ece250 Standard reminder to set phones to silent/vibrate mode, please! Previously, on ECE-250... We discussed trees (the
Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 https://ece.uwaterloo.ca/~cmoreno/ece250 Standard reminder to set phones to silent/vibrate mode, please! Previously, on ECE-250... We discussed trees (the
Instructor: Craig Duckett. Lecture 03: Tuesday, April 3, 2018 SQL Sorting, Aggregates and Joining Tables
 Instructor: Craig Duckett Lecture 03: Tuesday, April 3, 2018 SQL Sorting, Aggregates and Joining Tables 1 Assignment 1 is due LECTURE 5, Tuesday, April 10 th, 2018 in StudentTracker by MIDNIGHT MID-TERM
Instructor: Craig Duckett Lecture 03: Tuesday, April 3, 2018 SQL Sorting, Aggregates and Joining Tables 1 Assignment 1 is due LECTURE 5, Tuesday, April 10 th, 2018 in StudentTracker by MIDNIGHT MID-TERM
PROFESSOR: Last time, we took a look at an explicit control evaluator for Lisp, and that bridged the gap between
 MITOCW Lecture 10A [MUSIC PLAYING] PROFESSOR: Last time, we took a look at an explicit control evaluator for Lisp, and that bridged the gap between all these high-level languages like Lisp and the query
MITOCW Lecture 10A [MUSIC PLAYING] PROFESSOR: Last time, we took a look at an explicit control evaluator for Lisp, and that bridged the gap between all these high-level languages like Lisp and the query
Smart formatting for better compatibility between OpenOffice.org and Microsoft Office
 Smart formatting for better compatibility between OpenOffice.org and Microsoft Office I'm going to talk about the backbreaking labor of helping someone move and a seemingly unrelated topic, OpenOffice.org
Smart formatting for better compatibility between OpenOffice.org and Microsoft Office I'm going to talk about the backbreaking labor of helping someone move and a seemingly unrelated topic, OpenOffice.org
PROFESSOR: Well, yesterday we learned a bit about symbolic manipulation, and we wrote a rather stylized
 MITOCW Lecture 4A PROFESSOR: Well, yesterday we learned a bit about symbolic manipulation, and we wrote a rather stylized program to implement a pile of calculus rule from the calculus book. Here on the
MITOCW Lecture 4A PROFESSOR: Well, yesterday we learned a bit about symbolic manipulation, and we wrote a rather stylized program to implement a pile of calculus rule from the calculus book. Here on the
MITOCW watch?v=yarwp7tntl4
 MITOCW watch?v=yarwp7tntl4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free.
MITOCW watch?v=yarwp7tntl4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free.
CS103 Spring 2018 Mathematical Vocabulary
 CS103 Spring 2018 Mathematical Vocabulary You keep using that word. I do not think it means what you think it means. - Inigo Montoya, from The Princess Bride Consider the humble while loop in most programming
CS103 Spring 2018 Mathematical Vocabulary You keep using that word. I do not think it means what you think it means. - Inigo Montoya, from The Princess Bride Consider the humble while loop in most programming
PROFESSOR: Well, now that we've given you some power to make independent local state and to model objects,
 MITOCW Lecture 5B PROFESSOR: Well, now that we've given you some power to make independent local state and to model objects, I thought we'd do a bit of programming of a very complicated kind, just to illustrate
MITOCW Lecture 5B PROFESSOR: Well, now that we've given you some power to make independent local state and to model objects, I thought we'd do a bit of programming of a very complicated kind, just to illustrate
Who am I? I m a python developer who has been working on OpenStack since I currently work for Aptira, who do OpenStack, SDN, and orchestration
 Who am I? I m a python developer who has been working on OpenStack since 2011. I currently work for Aptira, who do OpenStack, SDN, and orchestration consulting. I m here today to help you learn from my
Who am I? I m a python developer who has been working on OpenStack since 2011. I currently work for Aptira, who do OpenStack, SDN, and orchestration consulting. I m here today to help you learn from my
Binary Search Trees. Carlos Moreno uwaterloo.ca EIT https://ece.uwaterloo.ca/~cmoreno/ece250
 Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 https://ece.uwaterloo.ca/~cmoreno/ece250 Previously, on ECE-250... We discussed trees (the general type) and their implementations. We looked at traversals
Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 https://ece.uwaterloo.ca/~cmoreno/ece250 Previously, on ECE-250... We discussed trees (the general type) and their implementations. We looked at traversals
The following content is provided under a Creative Commons license. Your support
 MITOCW Lecture 11 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make a
MITOCW Lecture 11 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make a
The following content is provided under a Creative Commons license. Your support
 MITOCW Lecture 23 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free. To make a
MITOCW Lecture 23 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free. To make a
MITOCW watch?v=w_-sx4vr53m
 MITOCW watch?v=w_-sx4vr53m The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
MITOCW watch?v=w_-sx4vr53m The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
MITOCW watch?v=se4p7ivcune
 MITOCW watch?v=se4p7ivcune The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=se4p7ivcune The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=4dj1oguwtem
 MITOCW watch?v=4dj1oguwtem PROFESSOR: So it's time to examine uncountable sets. And that's what we're going to do in this segment. So Cantor's question was, are all sets the same size? And he gives a definitive
MITOCW watch?v=4dj1oguwtem PROFESSOR: So it's time to examine uncountable sets. And that's what we're going to do in this segment. So Cantor's question was, are all sets the same size? And he gives a definitive
CPSC 320 Sample Solution, Playing with Graphs!
 CPSC 320 Sample Solution, Playing with Graphs! September 23, 2017 Today we practice reasoning about graphs by playing with two new terms. These terms/concepts are useful in themselves but not tremendously
CPSC 320 Sample Solution, Playing with Graphs! September 23, 2017 Today we practice reasoning about graphs by playing with two new terms. These terms/concepts are useful in themselves but not tremendously
The following content is provided under a Creative Commons license. Your support
 MITOCW Recitation 4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make
MITOCW Recitation 4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make
6 Stephanie Well. It s six, because there s six towers.
 Page: 1 of 10 1 R1 So when we divided by two all this stuff this is the row we ended up with. 2 Stephanie Um hm. 3 R1 Isn t that right? We had a row of six. Alright. Now before doing it see if you can
Page: 1 of 10 1 R1 So when we divided by two all this stuff this is the row we ended up with. 2 Stephanie Um hm. 3 R1 Isn t that right? We had a row of six. Alright. Now before doing it see if you can
Advisor Answers. January, Visual FoxPro 3.0 and 5.0
 January, 1998 Advisor Answers Visual FoxPro 3.0 and 5.0 Q: I would like to create a combo box that functions exactly like the FoxPro help index, that is, when the user types in a value, that value is automatically
January, 1998 Advisor Answers Visual FoxPro 3.0 and 5.0 Q: I would like to create a combo box that functions exactly like the FoxPro help index, that is, when the user types in a value, that value is automatically
Designing a Database -- Understanding Relational Design
 Designing a Database -- Understanding Relational Design Contents Overview The Database Design Process Steps in Designing a Database Common Design Problems Determining the Purpose Determining the Tables
Designing a Database -- Understanding Relational Design Contents Overview The Database Design Process Steps in Designing a Database Common Design Problems Determining the Purpose Determining the Tables
Q &A on Entity Relationship Diagrams. What is the Point? 1 Q&A
 1 Q&A Q &A on Entity Relationship Diagrams The objective of this lecture is to show you how to construct an Entity Relationship (ER) Diagram. We demonstrate these concepts through an example. To break
1 Q&A Q &A on Entity Relationship Diagrams The objective of this lecture is to show you how to construct an Entity Relationship (ER) Diagram. We demonstrate these concepts through an example. To break
Naming Things in Adafruit IO
 Naming Things in Adafruit IO Created by Adam Bachman Last updated on 2016-07-27 09:29:53 PM UTC Guide Contents Guide Contents Introduction The Two Feed Identifiers Name Key Aside: Naming things in MQTT
Naming Things in Adafruit IO Created by Adam Bachman Last updated on 2016-07-27 09:29:53 PM UTC Guide Contents Guide Contents Introduction The Two Feed Identifiers Name Key Aside: Naming things in MQTT
MITOCW watch?v=9h6muyzjms0
 MITOCW watch?v=9h6muyzjms0 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=9h6muyzjms0 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
mismatch between what is maybe possible today and what is going on in many of today's IDEs.
 What will happen if we do very, very small and lightweight tools instead of heavyweight, integrated big IDEs? Lecturer: Martin Lippert, VMware and Eclispe tooling expert LIPPERT: Welcome, everybody, to
What will happen if we do very, very small and lightweight tools instead of heavyweight, integrated big IDEs? Lecturer: Martin Lippert, VMware and Eclispe tooling expert LIPPERT: Welcome, everybody, to
(Refer Slide Time: 01:25)
 Computer Architecture Prof. Anshul Kumar Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture - 32 Memory Hierarchy: Virtual Memory (contd.) We have discussed virtual
Computer Architecture Prof. Anshul Kumar Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture - 32 Memory Hierarchy: Virtual Memory (contd.) We have discussed virtual
Contents. What's New. Version released. Newsletter #31 (May 24, 2008) What's New New version released, version 4.3.3
 Campground Master Newsletter #31 (May 24, 2008) 1 Newsletter #31 (May 24, 2008) Contents What's New New version released, version 4.3.3 Q & A Retrieving credit card information Guarantee Info missing the
Campground Master Newsletter #31 (May 24, 2008) 1 Newsletter #31 (May 24, 2008) Contents What's New New version released, version 4.3.3 Q & A Retrieving credit card information Guarantee Info missing the
MITOCW watch?v=hverxup4cfg
 MITOCW watch?v=hverxup4cfg PROFESSOR: We've briefly looked at graph isomorphism in the context of digraphs. And it comes up in even more fundamental way really for simple graphs where the definition is
MITOCW watch?v=hverxup4cfg PROFESSOR: We've briefly looked at graph isomorphism in the context of digraphs. And it comes up in even more fundamental way really for simple graphs where the definition is
MITOCW watch?v=v3omvlzi0we
 MITOCW watch?v=v3omvlzi0we The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=v3omvlzi0we The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
The Stack, Free Store, and Global Namespace
 Pointers This tutorial is my attempt at clarifying pointers for anyone still confused about them. Pointers are notoriously hard to grasp, so I thought I'd take a shot at explaining them. The more information
Pointers This tutorial is my attempt at clarifying pointers for anyone still confused about them. Pointers are notoriously hard to grasp, so I thought I'd take a shot at explaining them. The more information
How to Improve Your Campaign Conversion Rates
 How to Improve Your Email Campaign Conversion Rates Chris Williams Author of 7 Figure Business Models How to Exponentially Increase Conversion Rates I'm going to teach you my system for optimizing an email
How to Improve Your Email Campaign Conversion Rates Chris Williams Author of 7 Figure Business Models How to Exponentially Increase Conversion Rates I'm going to teach you my system for optimizing an email
BBC LEARNING ENGLISH 6 Minute English Wireless furniture for phones
 BBC LEARNING ENGLISH 6 Minute English Wireless furniture for phones NB: This is not a word-for-word transcript Hello and welcome to 6 Minute English. I'm and I'm. Hello. Hello,! Now,, could I borrow your
BBC LEARNING ENGLISH 6 Minute English Wireless furniture for phones NB: This is not a word-for-word transcript Hello and welcome to 6 Minute English. I'm and I'm. Hello. Hello,! Now,, could I borrow your
Lab 4. Recall, from last lab the commands Table[], ListPlot[], DiscretePlot[], and Limit[]. Go ahead and review them now you'll be using them soon.
![Lab 4. Recall, from last lab the commands Table[], ListPlot[], DiscretePlot[], and Limit[]. Go ahead and review them now you'll be using them soon. Lab 4. Recall, from last lab the commands Table[], ListPlot[], DiscretePlot[], and Limit[]. Go ahead and review them now you'll be using them soon.](/thumbs/95/122797207.jpg) Calc II Page 1 Lab 4 Wednesday, February 19, 2014 5:01 PM Recall, from last lab the commands Table[], ListPlot[], DiscretePlot[], and Limit[]. Go ahead and review them now you'll be using them soon. Use
Calc II Page 1 Lab 4 Wednesday, February 19, 2014 5:01 PM Recall, from last lab the commands Table[], ListPlot[], DiscretePlot[], and Limit[]. Go ahead and review them now you'll be using them soon. Use
Definition: A data structure is a way of organizing data in a computer so that it can be used efficiently.
 The Science of Computing I Lesson 4: Introduction to Data Structures Living with Cyber Pillar: Data Structures The need for data structures The algorithms we design to solve problems rarely do so without
The Science of Computing I Lesson 4: Introduction to Data Structures Living with Cyber Pillar: Data Structures The need for data structures The algorithms we design to solve problems rarely do so without
Slick The Split:
 Email Slick The Split: Let's just keep this simple. I have no use for fancy graphics or anything. I am so bogged down in work right now, I really have no business taking time out of my schedule to craft
Email Slick The Split: Let's just keep this simple. I have no use for fancy graphics or anything. I am so bogged down in work right now, I really have no business taking time out of my schedule to craft
In today s video I'm going show you how you can set up your own online business using marketing and affiliate marketing.
 Hey guys, Diggy here with a summary of part two of the four part free video series. If you haven't watched the first video yet, please do so (https://sixfigureinc.com/intro), before continuing with this
Hey guys, Diggy here with a summary of part two of the four part free video series. If you haven't watched the first video yet, please do so (https://sixfigureinc.com/intro), before continuing with this
The following content is provided under a Creative Commons license. Your support
 MITOCW Lecture 10 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To make a
MITOCW Lecture 10 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To make a
9 R1 Get another piece of paper. We re going to have fun keeping track of (inaudible). Um How much time do you have? Are you getting tired?
 Page: 1 of 14 1 R1 And this is tell me what this is? 2 Stephanie x times y plus x times y or hm? 3 R1 What are you thinking? 4 Stephanie I don t know. 5 R1 Tell me what you re thinking. 6 Stephanie Well.
Page: 1 of 14 1 R1 And this is tell me what this is? 2 Stephanie x times y plus x times y or hm? 3 R1 What are you thinking? 4 Stephanie I don t know. 5 R1 Tell me what you re thinking. 6 Stephanie Well.
I always recommend diversifying and testing more than one source, but make sure it is as targeted as possible.
 With traffic there are two real kinds - free and paid. I always recommend diversifying and testing more than one source, but make sure it is as targeted as possible. More often than not, I've had people
With traffic there are two real kinds - free and paid. I always recommend diversifying and testing more than one source, but make sure it is as targeted as possible. More often than not, I've had people
CPSC W2 Midterm #2 Sample Solutions
 CPSC 320 2014W2 Midterm #2 Sample Solutions March 13, 2015 1 Canopticon [8 marks] Classify each of the following recurrences (assumed to have base cases of T (1) = T (0) = 1) into one of the three cases
CPSC 320 2014W2 Midterm #2 Sample Solutions March 13, 2015 1 Canopticon [8 marks] Classify each of the following recurrences (assumed to have base cases of T (1) = T (0) = 1) into one of the three cases
MITOCW watch?v=kz7jjltq9r4
 MITOCW watch?v=kz7jjltq9r4 PROFESSOR: We're going to look at the most fundamental of all mathematical data types, namely sets, and let's begin with the definitions. So informally, a set is a collection
MITOCW watch?v=kz7jjltq9r4 PROFESSOR: We're going to look at the most fundamental of all mathematical data types, namely sets, and let's begin with the definitions. So informally, a set is a collection
6.001 Notes: Section 8.1
 6.001 Notes: Section 8.1 Slide 8.1.1 In this lecture we are going to introduce a new data type, specifically to deal with symbols. This may sound a bit odd, but if you step back, you may realize that everything
6.001 Notes: Section 8.1 Slide 8.1.1 In this lecture we are going to introduce a new data type, specifically to deal with symbols. This may sound a bit odd, but if you step back, you may realize that everything
Show notes for today's conversation are available at the podcast website.
 Title: Managing Security Vulnerabilities Based on What Matters Most Transcript Part 1: The Challenges in Defining a Security Vulnerability Julia Allen: Welcome to CERT's Podcast Series: Security for Business
Title: Managing Security Vulnerabilities Based on What Matters Most Transcript Part 1: The Challenges in Defining a Security Vulnerability Julia Allen: Welcome to CERT's Podcast Series: Security for Business
Autodesk University Step Up Your Game AutoCAD P&ID and SQL: Making Data Work for You Skill Level: All Levels
 Autodesk University Step Up Your Game AutoCAD P&ID and SQL: Making Data Work for You Skill Level: All Levels JULIAN CHAVEZ: Good afternoon, ladies and gentlemen. Last class of the last day and everybody's
Autodesk University Step Up Your Game AutoCAD P&ID and SQL: Making Data Work for You Skill Level: All Levels JULIAN CHAVEZ: Good afternoon, ladies and gentlemen. Last class of the last day and everybody's
Understanding Business Objects, Part 1
 Understanding Business Objects, Part 1 A well-designed set of business objects forms the engine for your application, but learning to create and use business objects has been a struggle for this author.
Understanding Business Objects, Part 1 A well-designed set of business objects forms the engine for your application, but learning to create and use business objects has been a struggle for this author.
Intro. Scheme Basics. scm> 5 5. scm>
 Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
MITOCW watch?v=0jljzrnhwoi
 MITOCW watch?v=0jljzrnhwoi The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=0jljzrnhwoi The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
2: Functions, Equations, and Graphs
 2: Functions, Equations, and Graphs 2-1: Relations and Functions Relations A relation is a set of coordinate pairs some matching between two variables (say, x and y). One of the variables must be labeled
2: Functions, Equations, and Graphs 2-1: Relations and Functions Relations A relation is a set of coordinate pairs some matching between two variables (say, x and y). One of the variables must be labeled
How To Make 3-50 Times The Profits From Your Traffic
 1 How To Make 3-50 Times The Profits From Your Traffic by Chris Munch of Munchweb.com Copyright Munchweb.com. All Right Reserved. This work cannot be copied, re-published, or re-distributed. No re-sell
1 How To Make 3-50 Times The Profits From Your Traffic by Chris Munch of Munchweb.com Copyright Munchweb.com. All Right Reserved. This work cannot be copied, re-published, or re-distributed. No re-sell
PROFESSOR: So far in this course we've been talking a lot about data abstraction. And remember the idea is that
 MITOCW Lecture 4B [MUSIC-- "JESU, JOY OF MAN'S DESIRING" BY JOHANN SEBASTIAN BACH] PROFESSOR: So far in this course we've been talking a lot about data abstraction. And remember the idea is that we build
MITOCW Lecture 4B [MUSIC-- "JESU, JOY OF MAN'S DESIRING" BY JOHANN SEBASTIAN BACH] PROFESSOR: So far in this course we've been talking a lot about data abstraction. And remember the idea is that we build
MITOCW watch?v=zm5mw5nkzjg
 MITOCW watch?v=zm5mw5nkzjg The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=zm5mw5nkzjg The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
A lot of people make repeated mistakes of not calling their functions and getting errors. Make sure you're calling your functions.
 Handout 2 Functions, Lists, For Loops and Tuples [ ] Functions -- parameters/arguments, "calling" functions, return values, etc. Please make sure you understand this example: def square(x): return x *
Handout 2 Functions, Lists, For Loops and Tuples [ ] Functions -- parameters/arguments, "calling" functions, return values, etc. Please make sure you understand this example: def square(x): return x *
Introduction to Programming
 CHAPTER 1 Introduction to Programming Begin at the beginning, and go on till you come to the end: then stop. This method of telling a story is as good today as it was when the King of Hearts prescribed
CHAPTER 1 Introduction to Programming Begin at the beginning, and go on till you come to the end: then stop. This method of telling a story is as good today as it was when the King of Hearts prescribed
MITOCW watch?v=ninwepprkdq
 MITOCW watch?v=ninwepprkdq The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=ninwepprkdq The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
P1_L3 Operating Systems Security Page 1
 P1_L3 Operating Systems Security Page 1 that is done by the operating system. systems. The operating system plays a really critical role in protecting resources in a computer system. Resources such as
P1_L3 Operating Systems Security Page 1 that is done by the operating system. systems. The operating system plays a really critical role in protecting resources in a computer system. Resources such as
CS144 Final Review. Dec 4th, 2009 Tom Wiltzius
 CS144 Final Review Dec 4th, 2009 Tom Wiltzius Topics Topics In narrative format! Let's follow Packy as he traverses the Internet! Packy comes into being to help Compy the Computer load a web page Compy
CS144 Final Review Dec 4th, 2009 Tom Wiltzius Topics Topics In narrative format! Let's follow Packy as he traverses the Internet! Packy comes into being to help Compy the Computer load a web page Compy
Understandable manual? Posted by Max Besser - 02 Feb :10
 Understandable manual? Posted by Besser - 02 Feb 2011 17:10 www.lightworksbeta.com/index.php?option=com_kunena&func=view&catid=6&id=5100& amp;limit=6&limitstart=6&itemid=202#5167 Forum Admin wrote: @ Besser
Understandable manual? Posted by Besser - 02 Feb 2011 17:10 www.lightworksbeta.com/index.php?option=com_kunena&func=view&catid=6&id=5100& amp;limit=6&limitstart=6&itemid=202#5167 Forum Admin wrote: @ Besser
BBC Learning English 6 Minute English Work s
 BBC Learning English 6 Minute English Work Emails NB: This is not a word for word transcript Hello and welcome to 6 Minute English from BBC Learning English. I'm Michelle. And I'm Neil. Thanks for joining
BBC Learning English 6 Minute English Work Emails NB: This is not a word for word transcript Hello and welcome to 6 Minute English from BBC Learning English. I'm Michelle. And I'm Neil. Thanks for joining
Instructor (Mehran Sahami):
 Programming Methodology-Lecture26 Instructor (Mehran Sahami): All right. Welcome back to what kind of day is it going to be in 106a? Anyone want to fun-filled and exciting. It always is. Thanks for playing
Programming Methodology-Lecture26 Instructor (Mehran Sahami): All right. Welcome back to what kind of day is it going to be in 106a? Anyone want to fun-filled and exciting. It always is. Thanks for playing
Well, Hal just told us how you build robust systems. The key idea was-- I'm sure that many of
 MITOCW Lecture 3B [MUSIC PLAYING] Well, Hal just told us how you build robust systems. The key idea was-- I'm sure that many of you don't really assimilate that yet-- but the key idea is that in order
MITOCW Lecture 3B [MUSIC PLAYING] Well, Hal just told us how you build robust systems. The key idea was-- I'm sure that many of you don't really assimilate that yet-- but the key idea is that in order
This lesson is part 5 of 5 in a series. You can go to Invoice, Part 1: Free Shipping if you'd like to start from the beginning.
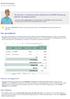 Excel Formulas Invoice, Part 5: Data Validation "Oh, hey. Um we noticed an issue with that new VLOOKUP function you added for the shipping options. If we don't type the exact name of the shipping option,
Excel Formulas Invoice, Part 5: Data Validation "Oh, hey. Um we noticed an issue with that new VLOOKUP function you added for the shipping options. If we don't type the exact name of the shipping option,
MITOCW watch?v=sdw8_0rdzuw
 MITOCW watch?v=sdw8_0rdzuw PROFESSOR: Directed acyclic graphs are a special class of graphs that really have and warrant a theory of their own. Of course, "directed acyclic graphs" is lot of syllables,
MITOCW watch?v=sdw8_0rdzuw PROFESSOR: Directed acyclic graphs are a special class of graphs that really have and warrant a theory of their own. Of course, "directed acyclic graphs" is lot of syllables,
MITOCW watch?v=flgjisf3l78
 MITOCW watch?v=flgjisf3l78 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
MITOCW watch?v=flgjisf3l78 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
MITOCW watch?v=zlohv4xq_ti
 MITOCW watch?v=zlohv4xq_ti The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
MITOCW watch?v=zlohv4xq_ti The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
3.7. Vertex and tangent
 3.7. Vertex and tangent Example 1. At the right we have drawn the graph of the cubic polynomial f(x) = x 2 (3 x). Notice how the structure of the graph matches the form of the algebraic expression. The
3.7. Vertex and tangent Example 1. At the right we have drawn the graph of the cubic polynomial f(x) = x 2 (3 x). Notice how the structure of the graph matches the form of the algebraic expression. The
 1 of 10 5/11/2006 12:10 AM CS 61A Spring 2006 Midterm 3 solutions 1. Box and pointer. > (let ((x (list 1 2 3))) (set-car! (cdr x) (cddr x)) x) (1 (3) 3) +-------------+ V --------- -- ------ ---------
1 of 10 5/11/2006 12:10 AM CS 61A Spring 2006 Midterm 3 solutions 1. Box and pointer. > (let ((x (list 1 2 3))) (set-car! (cdr x) (cddr x)) x) (1 (3) 3) +-------------+ V --------- -- ------ ---------
MITOCW watch?v=rvrkt-jxvko
 MITOCW watch?v=rvrkt-jxvko The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=rvrkt-jxvko The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=qota76ga_fy
 MITOCW watch?v=qota76ga_fy The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=qota76ga_fy The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
The following content is provided under a Creative Commons license. Your support
 MITOCW Recitation 2 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To make
MITOCW Recitation 2 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To make
============================================================================
 Linux, Cinnamon: cannot create panel icon Posted by JN_Mint - 2019/01/05 21:28 In Cinnamon (on Mint 19.3), with 'show tray icon' enabled in Rainlendar, there is no icon in any panel on my system and Cinnamon
Linux, Cinnamon: cannot create panel icon Posted by JN_Mint - 2019/01/05 21:28 In Cinnamon (on Mint 19.3), with 'show tray icon' enabled in Rainlendar, there is no icon in any panel on my system and Cinnamon
BBC Learning English Face up to Phrasals Mark's Mistake
 BBC Learning English Face up to Phrasals Mark's Email Mistake Episode 1: Email Fun? Mark: Hey Ali, did you check out that email I sent you the one about stupid Peter, saying how stupid he is? Oh dear.
BBC Learning English Face up to Phrasals Mark's Email Mistake Episode 1: Email Fun? Mark: Hey Ali, did you check out that email I sent you the one about stupid Peter, saying how stupid he is? Oh dear.
============================================================================
 [Solved] Title effects in v11 free? Posted by Driftwood Productions - 08 Jul 2012 15:24 I'm running LWKS v11 free edition, and am trying to figure out how to add title effects to my project, however, I
[Solved] Title effects in v11 free? Posted by Driftwood Productions - 08 Jul 2012 15:24 I'm running LWKS v11 free edition, and am trying to figure out how to add title effects to my project, however, I
MITOCW ocw f99-lec12_300k
 MITOCW ocw-18.06-f99-lec12_300k This is lecture twelve. OK. We've reached twelve lectures. And this one is more than the others about applications of linear algebra. And I'll confess. When I'm giving you
MITOCW ocw-18.06-f99-lec12_300k This is lecture twelve. OK. We've reached twelve lectures. And this one is more than the others about applications of linear algebra. And I'll confess. When I'm giving you
Blog post on updates yesterday and today:
 Beta Bug Prioritization meeting IRC Transcript 12 November 2013 Meeting was held in IRC, on the #devmo channel. Meetings are weekly, every Tuesday at 17:00 UTC (10am PST) ok, everyone, we're ready to start
Beta Bug Prioritization meeting IRC Transcript 12 November 2013 Meeting was held in IRC, on the #devmo channel. Meetings are weekly, every Tuesday at 17:00 UTC (10am PST) ok, everyone, we're ready to start
Foundations, Reasoning About Algorithms, and Design By Contract CMPSC 122
 Foundations, Reasoning About Algorithms, and Design By Contract CMPSC 122 I. Logic 101 In logic, a statement or proposition is a sentence that can either be true or false. A predicate is a sentence in
Foundations, Reasoning About Algorithms, and Design By Contract CMPSC 122 I. Logic 101 In logic, a statement or proposition is a sentence that can either be true or false. A predicate is a sentence in
Sample Online Survey Report: Complex Software Application
 Sample Online Survey Report: Complex Software Application www.sage-research.com shannon@sage-research.com 720-221-7003 Example Overview In this research project, the goal was to survey current users of
Sample Online Survey Report: Complex Software Application www.sage-research.com shannon@sage-research.com 720-221-7003 Example Overview In this research project, the goal was to survey current users of
Problem One: A Quick Algebra Review
 CS103A Winter 2019 Solutions for Week One Handout 01S Problem One: A Quick Algebra Review In the first week of CS103, we'll be doing a few proofs that will require some algebraic manipulations and reasoning
CS103A Winter 2019 Solutions for Week One Handout 01S Problem One: A Quick Algebra Review In the first week of CS103, we'll be doing a few proofs that will require some algebraic manipulations and reasoning
CFMG Training Modules Classified Ad Strategy Module
 CFMG Training Modules Classified Ad Strategy Module In This Module: 1. Introduction 2. Preliminary Set Up Create the Sequential Letterset for our Ad Strategy Set Up Your Vanity Responder Create Your Stealth
CFMG Training Modules Classified Ad Strategy Module In This Module: 1. Introduction 2. Preliminary Set Up Create the Sequential Letterset for our Ad Strategy Set Up Your Vanity Responder Create Your Stealth
WINDOWS NT FILE SYSTEM INTERNALS : OSR CLASSIC REPRINTS BY RAJEEV NAGAR
 WINDOWS NT FILE SYSTEM INTERNALS : OSR CLASSIC REPRINTS BY RAJEEV NAGAR DOWNLOAD EBOOK : WINDOWS NT FILE SYSTEM INTERNALS : OSR CLASSIC REPRINTS BY RAJEEV NAGAR PDF Click link bellow and free register
WINDOWS NT FILE SYSTEM INTERNALS : OSR CLASSIC REPRINTS BY RAJEEV NAGAR DOWNLOAD EBOOK : WINDOWS NT FILE SYSTEM INTERNALS : OSR CLASSIC REPRINTS BY RAJEEV NAGAR PDF Click link bellow and free register
Problem Solving through Programming In C Prof. Anupam Basu Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur
 Problem Solving through Programming In C Prof. Anupam Basu Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur Lecture 17 Switch Statement (Refer Slide Time: 00:23) In
Problem Solving through Programming In C Prof. Anupam Basu Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur Lecture 17 Switch Statement (Refer Slide Time: 00:23) In
Setting up ODBC, Part 2 Robert Abram
 Seite 1 von 7 Issue Date: FoxTalk October 2000 Setting up ODBC, Part 2 Robert Abram rob_abram@smartfella.com In this second article of a series about setting up ODBC connections programmaticly through
Seite 1 von 7 Issue Date: FoxTalk October 2000 Setting up ODBC, Part 2 Robert Abram rob_abram@smartfella.com In this second article of a series about setting up ODBC connections programmaticly through
Ruby on Rails Welcome. Using the exercise files
 Ruby on Rails Welcome Welcome to Ruby on Rails Essential Training. In this course, we're going to learn the popular open source web development framework. We will walk through each part of the framework,
Ruby on Rails Welcome Welcome to Ruby on Rails Essential Training. In this course, we're going to learn the popular open source web development framework. We will walk through each part of the framework,
Using icloud's Mail rules to delete a message before you see it.
 Page 1 of 9 How to block spam calls, You know how to use messaging and emails, and you use them to get things done, but far too many just want to sell you things or annoy you with them. Here's how to get
Page 1 of 9 How to block spam calls, You know how to use messaging and emails, and you use them to get things done, but far too many just want to sell you things or annoy you with them. Here's how to get
6.001 Notes: Section 6.1
 6.001 Notes: Section 6.1 Slide 6.1.1 When we first starting talking about Scheme expressions, you may recall we said that (almost) every Scheme expression had three components, a syntax (legal ways of
6.001 Notes: Section 6.1 Slide 6.1.1 When we first starting talking about Scheme expressions, you may recall we said that (almost) every Scheme expression had three components, a syntax (legal ways of
The following content is provided under a Creative Commons license. Your support
 MITOCW Lecture 8 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make a donation
MITOCW Lecture 8 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To make a donation
Database management system Prof. D. Janakiram Department of Computer Science and Engineering Indian Institute of Technology, Madras
 Database management system Prof. D. Janakiram Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 25 Basic 2-phase & 3-phase Commit protocol In the last lecture,
Database management system Prof. D. Janakiram Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 25 Basic 2-phase & 3-phase Commit protocol In the last lecture,
Database Management System Dr. S. Srinath Department of Computer Science & Engineering Indian Institute of Technology, Madras Lecture No.
 Database Management System Dr. S. Srinath Department of Computer Science & Engineering Indian Institute of Technology, Madras Lecture No. # 3 Relational Model Hello everyone, we have been looking into
Database Management System Dr. S. Srinath Department of Computer Science & Engineering Indian Institute of Technology, Madras Lecture No. # 3 Relational Model Hello everyone, we have been looking into
Detecting and correcting mistakes
 Chapter 6 Detecting and correcting mistakes 6.1 Errors and the law! In chapter 4 we saw that random noise will tend to reduce the amount of information transmitted or collected by making us uncertain that
Chapter 6 Detecting and correcting mistakes 6.1 Errors and the law! In chapter 4 we saw that random noise will tend to reduce the amount of information transmitted or collected by making us uncertain that
6.001 Notes: Section 1.1
 6.001 Notes: Section 1.1 Slide 1.1.1 This first thing we need to do is discuss the focus of 6.001. What is this course all about? This seems quite obvious -- this is a course about computer science. But
6.001 Notes: Section 1.1 Slide 1.1.1 This first thing we need to do is discuss the focus of 6.001. What is this course all about? This seems quite obvious -- this is a course about computer science. But
Outline for Today. Euler Tour Trees Revisited. The Key Idea. Dynamic Graphs. Implementation Details. Dynamic connectivity in forests.
 Dynamic Graphs Outline for Today Euler Tour Trees Revisited Dynamic connectivity in forests. The Key Idea Maintaining dynamic connectivity in general graphs Dynamic Graphs A data structure for dynamic
Dynamic Graphs Outline for Today Euler Tour Trees Revisited Dynamic connectivity in forests. The Key Idea Maintaining dynamic connectivity in general graphs Dynamic Graphs A data structure for dynamic
