Application of Equivalence Checking in a Loan Origination Process in Banking Industry
|
|
|
- Donald Colin Douglas
- 5 years ago
- Views:
Transcription
1 2013 Workshops on Enabling Technologies: Infrastructure for Collaborative Enterprises Application of Equivalence Checking in a Loan Origination Process in Banking Industry Antonella Santone Dipartimento di Ingegneria, Università degli Studi del Sannio, Italy santone@unisannio.it Valentina Intilangelo intivale@hotmail.it Domenico Raucci Dipartimento di Economia, Università degli Studi di Chieti-Pescara, Italy d.raucci@unich.it Abstract Equivalence checking is traditionally applied to computer system design. It is a promising formal technique for the improvement of software quality. However, it requires detailed specifications of systems and is therefore not very accessible, above all in certain restricted fields of application. One of this domain is business process management. In particular, we examine the applicability of equivalence checking to validation of Business Processes that are mapped through the systems of Workflow Management. The usage of formal methods in business domain, however, is still not widely used. This is due also to the state explosion problem, which says that the state space grows exponentially in the number of concurrent processes. In this paper we consider a heuristic-based methodology developed to combat the state explosion problem for checking process equivalence. Our proposal is two-fold: (i) we show how equivalence checking can be applied in the context of business modelling and analysis; (ii) we evaluate and test the heuristic-based methodology using, as a case study, a real-world banking workflow of a loan origination process. Our investigations suggest that the business community, especially in the banking field, can benefit from this efficient methodology developed in the process algebra area to prevent significant errors. We show and discuss the experimental results obtained. Index Terms Business Process Management; Formal Methods; CCS; Heuristic Search; Workflow Verification; Banking Process. I. INTRODUCTION Formal methods are powerful techniques for specifying and verifying complex systems. Several techniques for formal verification have been developed over the past three decade among them equivalence checking. Equivalence checking is the process of determining whether two systems are equivalent to each other according to some mathematically-defined notion of equivalence. Equivalence checking is typically used to verify if a system design conforms to its high-level service specification. Although equivalence checking is currently not applicable to all domains, it is useful for certain restricted fields of application. One of this domain is business process management. In particular, we examine the applicability of equivalence checking to validation of Business Processes that are mapped through the systems of Workflow Management. The usage of this formal method in the domain of business process management however, is still not widely used. This is due also to the state explosion problem, which says that the state space grows exponentially in the number of concurrent processes. In fact, the parallelism between the processes of the system leads to a number of reachable states which may become very large, in some cases on the order of millions or billions of states. When the number of states is too large to fit in a computer s main memory, verification quickly breaks down. In fact, in the business process taken into account, we came across the state explosion problem. Specifically, this problem has emerged as a result of a first modelling of the banking process, in which the excessive number of processes in parallel has made impracticable the verification using standard model checker. Several approaches have been developed to solve or reduce the state explosion problem. In this paper to combat the state explosion problem for checking process equivalence we consider an efficient procedure, based on heuristic search [1], proposed in [2]. The procedure is applied to processes defined through a specification language very compact, the Calculus of Communicating Systems (CCS)[3] defined by Milner, which is one of the most well known process algebras and it is largely used for modeling concurrent and distributed systems. The approach uses a heuristic function that suggests to expand first the states that offer the most promising way to deduce that two systems are not equivalent. This makes it possible to avoid the exhaustive exploration of the global state graph of the two systems when they are not equivalent. One of the authors of this paper has contributed to the design of Grease (GREedy Algorithm for System Equivalence), a C++ tool supporting the heuristic approach to check equivalence of CCS processes. The use of Grease on a sample of small CCS processes has shown a significant reduction of both state-space size and time, compared to traditional equivalence checking algorithms. Our proposal is two-fold: (i) we show how equivalence checking can be applied in the context of business modelling and analysis; (ii) we evaluate and test the heuristic-based methodology using, as a case study, a realworld banking workflow of a loan origination process. More precisely, in this paper we describe in CCS both the implementation of the banking process and the specifications of the expected behaviours. Our results obtained by evaluating /13 $ IEEE DOI /WETICE
2 a real-world banking process are validated by comparing them to those obtained by a state-of-the-art tool for equivalence checking, i.e., the Concurrency Workbench of New Century (CWB-NC) [4], which one of the most popular environments for verifying concurrent system. Applying our approach we can prove the correctness of the system obtaining a considerable reduction of both state space size and time with respect to CWB-NC. Actually, for the proposed case study, differently from Grease, the CWB-NC is not able to give an answer, after waiting more than half an hour. This is due to the big number of states. This confirms that our approach is more scalable than CWB-NC. Our investigations suggest that the business community, especially in the banking field, can benefit from this efficient methodology developed in the process algebra area to prevent significant errors. The remainder of the paper is organized as follows. Section II is a review of the basic concepts of equivalence checking, while Section III briefly describes the heuristic-based approach for equivalence checking and its applicability in the business process management in banking industry. In Section IV the experimental results we obtained are reported and discussed. Finally, comparisons with related work and our conclusions are presented in Section V. II. EQUIVALENCE CHECKING In this section we introduce the basic concepts of formal methods. Formal methods are mathematically based languages, techniques, and tools for specifying and verifying complex systems. Several techniques for formal verification have been developed over the past three decade among them equivalence checking. For applying equivalence checking we first need a precise notation for defining systems. Specification is the process of describing a system. As starting point, we assume that system behaviour is represented as an automaton. It basically consists of a set of nodes together with a set of labelled edges between these nodes. A node represents a system state, while a labelled edge represents a transition from one system state to the next. That is, if the automaton contains an edge s a s, then the system can evolve from state s into state s by the execution of action a. One state is selected to be the root state, i.e., the initial state of the automaton. However, for the purpose of mathematical reasoning it is often convenient to represent automaton algebraically in the form of terms. For this aim, we use Milner s Calculus of Communicating Systems (CCS)[3], one of the most well known process algebras. CCS contains basic operators to build finite processes, communication operators to express concurrency, and some notion of recursion to capture infinite behaviour. The semantics of a CCS term p is precisely defined by means of the structural operational semantics. The semantic definition is given by a set of conditional rules describing the transition relation of the automaton corresponding to the behavior expression defining p. This automaton is called standard transition system for p and is denoted by S(p). More precisely, the syntax of processes is the following: p ::= nil α.p p + p p p p\l p[f] x where α ranges over a finite set of actions A = {τ,a,a, b, b,...}. Input actions are labeled with non-barred names, e.g. a, while output actions are barred, e.g. a. The action τ Ais called internal action. The set L ranges over sets of visible actions (A {τ}), f ranges over functions from actions to actions, while x ranges over a set of constant names: each constant x is defined by a constant definition x def = p. We give the semantics for CCS by induction over the structure of processes. The process nil can perform no actions. The process α.p can perform the action α and thereby become the process p. The process p + q can behave either as p or as q. The operator expresses parallel composition: if the process p can perform α and become p, then p q can perform α and become p q, and similarly for q. Furthermore, if p can perform a visible action l and become p, and q can perform l and become q, then p q can perform τ and become p q. The operator \ expresses the restriction of actions. If p can perform α and become p, then p\l can perform α to become p \L only if α, α L. The operator [f] expresses the relabeling of actions. If p can perform α and become p, then p[f] can perform f(α) and become p [f]. Each relabeling function f has the property that f(τ) = τ. Finally, a constant x behaves as p if x def = p. Equivalence checking is the process of determining whether two systems are equivalent to each other according to some mathematically defined notion of equivalence, such as strong and weak equivalence previously defined. The CCS language, like all other process algebras, can be used to describe both implementations of processes and specifications of their expected behaviours. Therefore CCS supports the so-called single language approach to process theory, that is, the approach in which a single language is used to describe both actual processes and their specifications. One process description, say SYS, may describe an implementation, and another, say SPEC, may describe a specification of the expected behaviour. This approach to program verification is also sometimes called implementation verification. For example, if the observable behaviour of a communications protocol is identical to that of a perfect communication channel that delivers all messages in order, then it would be justifiable to deem the protocol correct. One of the most popular environments for verifying concurrent systems is the Concurrency Workbench of New Century (CWB-NC) [4], which supports several different specification languages, among which CCS. In the CWB-NC the verification can be based both on model checking [5] and on equivalence checking. III. HOW TO GREASE IN A LOAN ORIGINATION PROCESS Formal methods cannot be easily scaled due to the state explosion problem, which says that the state space grows exponentially in the number of concurrent processes. In fact, the parallelism between the processes of the system leads to a
3 number of reachable states which may become very large, in some cases on the order of millions or billions of states. When the number of states is too large to fit in a computer s main memory, verification quickly breaks down. Several approaches have been developed to solve or reduce the state explosion problem. We now present a methodology to combat the state explosion problem for equivalence checking. In [2] an efficient approach based on heuristic search techniques to check equivalences has been defined. In general, a heuristic search strategy [1] uses an evaluation function to determine the order in which the nodes in the search graph are selected for expansion. The evaluation function measures the distance to a goal node based on an heuristic function which gives the estimated shortest distance from the given node to a goal node. In [2] the equivalence checking has been formalized as a search problem on AND/OR graphs. Moreover, an efficient equivalence checking procedure has been proposed, defining a heuristic function that suggests to expand first the states that offer the most promising way to deduce that two systems are not equivalent. The heuristic function, which is inductively defined on the syntactic structure of the CCS process, assigns a value to each node of the graph. Roughly speaking, that value is a measure of the degree of not similarity of the two states considered in that node. This makes it possible to avoid the exhaustive exploration of the global state graph of the two systems when they are not equivalent. One of the authors of this paper has contributed to the design of Grease 1 (GREedy Algorithm for System Equivalence), a C++ tool supporting the heuristic approach to check equivalence of CCS processes. Currently Grease accepts only CCS processes but it can be easily extended to manage also other specification languages like for example CSP and LOTOS. The use of Grease on a sample of small CCS processes has shown a significant reduction of both state-space size and time, compared to traditional equivalence checking algorithms. In this paper we evaluate the methodology on a real-world banking workflow of a loan origination process. A. Banking Process Overview As stated above, the application of formal techniques consists of an algorithmic approach to verification of such systems that can be represented by a formal model. According to the mentioned outlook, these methodologies are primarily related to verification of hardware and software systems. However, formal techniques and tools have a number of features that make it possible to extend their use to specific business domains, including the formal verification of business processes that are mapped and administrated through the systems of Workflow Management. The latter are generally used by managers to automate all or part of business processes by flushing documents, information and tasks from one participant to another, according to a set of procedural rules. With specific reference to dynamic workflows, i.e. those that evolve according to the events that occur and to the ways in which tasks are handled by users, a particular problem is represented by fairness because it is necessary to ensure 1 a080224/grease/ that workflows have been defined adequately with regard to desired properties. To deal with this situation it is possible to use the formal verification techniques and the associated tools. The underlying idea consists in representing each business process, including interactions between human components, databases, and hardware/software elements of the information system as a finite state transition system [6], [7], [8]. However, the complexity of this approach ends to limit its applicability to restricted areas where its use is justified in the light of economic considerations arising from the natural tradeoff between the costs of implementation and the benefits achieved. We refer in particular to those business processes so-called business-critical or commercially-critical, where the characteristics of fairness and integrity are prerequisites for the success of a market or business transaction [9], [10], [11], [12], [13]. The above-mentioned banking process of loan origination fits into this context. The need to increase efficiency and reduce costs is pushing for a long time many banks to review internal processes, models, organizational procedures and technological applications, in order to ensure cost-effectiveness and maintain, at the same time, a high level of quality of services provided to customers. In this vein are situated very important projects including the reengineering of the process of investigation and provision of different forms of credit on mortgages and personal loans, aimed in particular to the introduction of new procedures supported by Workflow Management tools [14], [15], [16]. We introduce, at this point, the banking process in question, providing a broad overview of the same thanks to typical logic of workflow tools. The process is instantiated whenever a customer of the bank applies for a loan and it starts with the update of customer data if he/she is already present in the registry or with the insertion of a new record in the database if he/she is a new customer. Taking into account the information provided, the process proceeds with the identification of the type of customer and with its simultaneous location in the segmentation made by the bank. Then there is the need to make a series of internal and external controls in order to assign a rating to the customer, which is a synthetic judgment of reliability based on assets and income of the same, thanks to which it is possible to express the level of the loan credit-worthiness. Afterwards it is selected among the products that are part of the bank s offer, the one which corresponds to the set of features and price conditions that fits better the type of client that requested the funding. If the latter is satisfied with the proposal received, the bank proceeds to the signing of the contract and, therefore, the formalization of the agreement, reaching the end of the process. IV. EXPERIMENT RESULTS In this section we present and discuss our experience with using the Grease, implementing the heuristic-based approach, to verify the banking process previously described. The aim is to evaluate the performances of the approach and compare it against the CWB-NC. Experiments were executed on a 64 bit, 2.67 GHz Intel i5 CPU equipped with 8 GiB of RAM and running Gentoo Linux. The tool is freely available for download at the url a080224/grease/
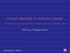
4 Customer Clerk preprocessor Clerk postprocessor Supervisor Manager Loan Request Input Customer Data and Identification Rating Request Internal and External Rating Big Amount? No Pricing Bundled Product Yes Internal Rating Verification Possible Modifications No Three Attempts? No Negative feedback Yes Verification Request Price Bundled Product Adequate? Yes Customer Signature Positive feedback Manager Signature Fig. 1: Loan origination workflow. Figure 1 shows a typical loan origination process in the banking domain, as previously described. To formally verify the banking process it is firstly required to give a formal specification of each component of the system. Each component of the banking process involves complex interactions since the component can dialogue with other components. For example, the customer dialogue with the first phase clerk, for instance to ask for a loan request. Figure 2 shows a view of all the processes (the boxes in the figure) involved in this loan origination process as well as the synchronisations between these entities. Synchronisations are denoted using lines joining the involved agents with actions and their direction (prefixed by a quote for emissions). Each process is translated in CCS and all CCS processes are then composed using the parallel operator providing that all synchronisations are defined as restricted actions. All component have been specified in CCS; in Table I we show only the CCS specification of the first phase clerk, just to give the reader the flavor of the approach followed. From a textual CCS specification it is possible to generate the corresponding labeled transition system, which can be successively used for equivalence checking. We prefer textual syntax since it is more adapted to proof-writing and formal reasoning, as well as to the description of large-scale systems. Graphical notations are anyway complementary and can be used by user-friendly front-ends. The results for the verification of our system using weak equivalence are shown in Table II. In the table the second column shows the results in terms of generating states (gen) and time, expressed in seconds, using Grease. The third column should show the number of generated states and time resulting from the CWB-NC. The CCS specification (namely p) representing the CCS banking process has states and transitions. To apply equivalence checking we have to specify in CCS also the expected behaviours. Thus, in the first experiment we represent as CCS process (namely q) the following requirement: the customer receives a copy of the contract only if the loan application was successful. The result is that p is not weak equivalent to q, since it must hold that the customer receives a copy of the contract not only if the loan application was successful but also when another condition is satisfied, i.e., when the customers he has affixed his signature. In the second experiment, we represent as CCS process (namely q) the following requirement: after a request by the customer for a loan, the procedure terminates with success. The result is that p is not weak equivalent to q, since obviously the procedure can terminate also with a failure. It is worth pointing out that, differently from Grease, the CWB-NC is not able to give an answer, after waiting more than half an hour for both the requirements. Therefore no verification can be performed. This is due to the big number of states. This confirms that our approach is more scalable than CWB-NC. Grease CWB-NC gen time gen time first requirement second requirement TABLE II: Results - weak equivalence. V. CONCLUSIONS AND RELATED WORK The work presented in this paper shows that equivalence checking can be very useful to enhance the quality in the doamin of business management. However, using traditional equivalence checkers we find some difficulties to prove the
5 Fig. 2: Graphic representation of the interactions among all the components involved in a loan origination process. proc FirstPhaseClerk = loanrequest. informationrequest.customerinformation.( insertcustumerdata. ratingrequest.firstphaseclerk + updatecustomerdata. ratingrequest.firstphaseclerk) TABLE I: The CCS first phase clerk specification concreteness of real-world banking. This is mainly due to the state explosion problem. To combat this problem we consider an efficient procedure, based on heuristic search, which uses a heuristic function that suggests to expand first the states that offer the most promising way to deduce that two systems are not equivalent. This makes it possible to avoid the exhaustive exploration of the global state graph of the two systems when they are not equivalent. We use Grease (GREedy Algorithm for System Equivalence), a C++ tool supporting the heuristic approach to check equivalence of CCS processes. Our investigations suggest that the business community, especially in the banking filed, can benefit from the efficient heuristic-based methodology developed in the process algebra area to prevent significant errors. A real-world banking workflow of a loan origination process was chosen as a case study to demonstrate the usefulness of Grease which reduces the state explosion problem. As shown by the above experiments, Grease obtains good results when compared with CWB-NC both in performance, i.e., the speed at which the tool returns its results, and its scalability, i.e., the extent to which the tool can manage increasingly large systems
6 Similarly to our investigation, in [17], the authors analyse the verification of the safety of a system (i.e., avoiding the undesired propagation of access rights or indirect access through some other granted resource) which is one of the goals of access control research. In particular, they consider delegation and revocation functionalities mainly focusing on organizational control principles. However, differently by our equivalence-checking approach, they propose a modelchecking based methodology using SMV tool. Moreover, our aim is also to reduce the state explosion problem arising when dealing with complex systems such as the loan origination processes in banking industry. The most challenging task when applying automated formal verification in practice is to conquer the state explosion problem. Several approaches have been developed to solve or reduce the state explosion problem for model checking. Among them, reduction techniques based on symbolic model checking techniques [18], partial order techniques [19], compositional techniques [20], [21], abstraction approaches [22], [23] and heuristic-based approaches [24], [25], [26]. Moreover, the above approaches has been successfully applied in several fields, like for example clone detection [27], [28], analysis of social networks [29], incremental construction of complex systems [30], secure information flow in concurrent programs [31]. For equivalence checking algorithms with minimal space complexity are of particular interest. Two algorithmic families can be considered to perform the equivalence checking. The first one is based on refinement principle: given an initial partition, find the coarsest partition stable with respect to the transition relation see for example the algorithm proposed by Paige and Tarjan in [32]. The other family of algorithms is based on a Cartesian product traversal from the initial state [33], [34]. These algorithms are both applied on the whole state graph, and they require an explicit enumeration of this state space. This approach leads to the well-known state explosion problem. Classical reduction algorithms already exist [35], [36], but they can be applied only when the whole state space has been computed, which limits their interest. A possible solution is to reduce the state graph before performing the check as shown in [37], where symbolic representation of the state space is used. REFERENCES [1] J. Pearl, Heuristics - intelligent search strategies for computer problem solving, Addison-Wesley series in artificial intelligence, Addison- Wesley, [2] A. Santone, Heuristic for simulation checking, in: Proceedings of the 2011 International Conference on Artificial Intelligence, ICAI 2011, Vol. 1, 2011, pp [3] R. Milner, Communication and concurrency, PHI Series in computer science, Prentice Hall, [4] R. Cleaveland, S. Sims, The ncsu concurrency workbench, in: R. Alur, T. A. Henzinger (Eds.), CAV, Vol of Lecture Notes in Computer Science, Springer, 1996, pp [5] E. M. Clarke, O. Grumberg, D. Peled, Model checking, MIT Press, [6] M. Kohlbacher, The effects of process orientation on customer satisfaction, product quality and time-based performance, 29th International Conference of the Strategic Management Society, Washington DC (2009). [7] G. Gorry, M. S. Morton, A framework for management information systems, vol. 13, n. 1, Sloan Management Review (1971). [8] R. Daft, Organization theory and design, South Western Educ Pub. (2009). [9] R. Kaplan, D. Norton, The execution premium: linking strategy to operations for competitive advantage, Harward Business School Press, Boston (2008). [10] M. Porter, Competitive advantage, Free Press, New York (1985). [11] M. Morrow, M. Hazell, Activity mapping for business process redesign, management accounting, feb. p. 36 (1992). [12] M. Hammer, J. Champy, Reengineering the corporation, Harper Business, NY (1993). [13] T. Davenport, Process innovation, Harvard Business School Press, Boston (1993). [14] S. Drew, Business re-engineering in financial services, Pitman Publishing, London (1994). [15] G. De Laurentis, (edited by), Performance measurements frontiers in banking and finance, Egea (2004). [16] P. Allen, Reengineering the bank, Probus Publishing Company (1994). [17] A. Schaad, V. Lotz, K. Sohr, A model-checking approach to analysing organisational controls in a loan origination process, in: SACMAT, 2006, pp [18] K. L. McMillan, Symbolic model checking, Kluwer, [19] P. Godefroid, Partial-Order Methods for the Verification of Concurrent Systems - An Approach to the State-Explosion Problem, Vol of Lecture Notes in Computer Science, Springer, [20] E. M. Clarke, D. E. Long, K. L. McMillan, Compositional model checking, in: LICS, IEEE Computer Society, 1989, pp [21] A. Santone, Automatic verification of concurrent systems using a formula-based compositional approach, Acta Inf. 38 (8) (2002) [22] A. Santone, G. Vaglini, Abstract reduction in directed model checking ccs processes, Acta Inf. 49 (5) (2012) [23] E. M. Clarke, O. Grumberg, D. E. Long, Model checking and abstraction, ACM Trans. Program. Lang. Syst. 16 (5) (1994) [24] A. Santone, Heuristic search + local model checking in selective mucalculus, IEEE Trans. Software Eng. 29 (6) (2003) [25] S. Gradara, A. Santone, M. L. Villani, Delfin + : An efficient deadlock detection tool for ccs processes, J. Comput. Syst. Sci. 72 (8) (2006) [26] S. Gradara, A. Santone, M. L. Villani, Using heuristic search for finding deadlocks in concurrent systems, Inf. Comput. 202 (2) (2005) [27] A. Cuomo, A. Santone, U. Villano, A novel approach based on formal methods for clone detection, in: IWSC, IEEE, 2012, pp [28] A. Santone, Clone detection through process algebras and java bytecode, in: IWSC, 2011, pp [29] A. Santone, G. Vaglini, Modelling and analysing social networks through formal methods and heuristic searches, in: ICSOFT, 2012, pp [30] A. Santone, G. Vaglini, M. Villani, Incremental construction of systems: An efficient characterization of the lacking sub-system, Science of Computer Programming. [31] N. D. Francesco, A. Santone, L. Tesei, Abstract interpretation and model checking for checking secure information flow in concurrent systems, Fundam. Inform. 54 (2-3) (2003) [32] R. Paige, R. E. Tarjan, Three partition refinement algorithms, SIAM J. Comput. 16 (6) (1987) [33] J.-C. Fernandez, L. Mounier, on the fly verification of behavioural equivalences and preorders, in: Larsen and Skou [38], pp [34] J. Godskesen, K. Larsen, M. Zeeberg, TAV - tools for automatic verification: users manual, Institute for Electronic Systems, Department of Mathematics and Computer Science, The University of Aalborg, URL [35] J.-C. Fernandez, An implementation of an efficient algorithm for bisimulation equivalence, Sci. Comput. Program. 13 (1) (1989) [36] P. C. Kanellakis, S. A. Smolka, Ccs expressions, finite state processes, and three problems of equivalence, Inf. Comput. 86 (1) (1990) [37] J.-C. Fernandez, A. Kerbrat, L. Mounier, Symbolic equivalence checking, in: C. Courcoubetis (Ed.), CAV, Vol. 697 of Lecture Notes in Computer Science, Springer, 1993, pp [38] K. G. Larsen, A. Skou (Eds.), Computer Aided Verification, 3rd International Workshop, CAV 91, Aalborg, Denmark, July, 1-4, 1991, Proceedings, Vol. 575 of Lecture Notes in Computer Science, Springer,
TIV: A Toolset for Interactive Verification of Basic LOTOS Specifications
 TIV: A Toolset for Interactive Verification of Basic LOTOS Specifications Cheoljoo Jeong Kangho Kim Youngchan Kim Yeondae Chung Systems Engineering Research Institute Taejon, 305-333, Korea {cjeong,khkim,yckim,chung}@eagles.seri.re.kr
TIV: A Toolset for Interactive Verification of Basic LOTOS Specifications Cheoljoo Jeong Kangho Kim Youngchan Kim Yeondae Chung Systems Engineering Research Institute Taejon, 305-333, Korea {cjeong,khkim,yckim,chung}@eagles.seri.re.kr
A Fair Extension of (Soft) Concurrent Constraint Languages
 A Fair Extension of (Soft) Concurrent Constraint Languages Stefano Bistarelli 1,2,3 and Paola Campli 1 1 Department of Science, University G. d Annunzio of Chieti-Pescara, Italy [bista,campli]@sci.unich.it
A Fair Extension of (Soft) Concurrent Constraint Languages Stefano Bistarelli 1,2,3 and Paola Campli 1 1 Department of Science, University G. d Annunzio of Chieti-Pescara, Italy [bista,campli]@sci.unich.it
ECDAR: An Environment for Compositional Design and Analysis of Real Time Systems
 ECDAR: An Environment for Compositional Design and Analysis of Real Time Systems AlexandreDavid 1,Kim.G.Larsen 1,AxelLegay 2, UlrikNyman 1,AndrzejWąsowski 3 1 ComputerScience,AalborgUniversity,Denmark
ECDAR: An Environment for Compositional Design and Analysis of Real Time Systems AlexandreDavid 1,Kim.G.Larsen 1,AxelLegay 2, UlrikNyman 1,AndrzejWąsowski 3 1 ComputerScience,AalborgUniversity,Denmark
Substitution in Structural Operational Semantics and value-passing process calculi
 Substitution in Structural Operational Semantics and value-passing process calculi Sam Staton Computer Laboratory University of Cambridge Abstract Consider a process calculus that allows agents to communicate
Substitution in Structural Operational Semantics and value-passing process calculi Sam Staton Computer Laboratory University of Cambridge Abstract Consider a process calculus that allows agents to communicate
Rule Formats for Nominal Modal Transition Systems
 Rule Formats for Nominal Modal Transition Systems Anke Stüber Universitet Uppsala, Uppsala, Sweden anke.stuber@it.uu.se Abstract. Modal transition systems are specification languages that allow the expression
Rule Formats for Nominal Modal Transition Systems Anke Stüber Universitet Uppsala, Uppsala, Sweden anke.stuber@it.uu.se Abstract. Modal transition systems are specification languages that allow the expression
Distributed Systems Programming (F21DS1) Formal Verification
 Distributed Systems Programming (F21DS1) Formal Verification Andrew Ireland Department of Computer Science School of Mathematical and Computer Sciences Heriot-Watt University Edinburgh Overview Focus on
Distributed Systems Programming (F21DS1) Formal Verification Andrew Ireland Department of Computer Science School of Mathematical and Computer Sciences Heriot-Watt University Edinburgh Overview Focus on
An Eclipse-based Editor to Support LOTOS Newcomers
 1 An Eclipse-based Editor to Support LOTOS Newcomers Giuseppe De Ruvo, Antonella Santone Department of Engineering, University of Sannio, Benevento, Italy e-mail: {gderuvo@unisannio.it, santone@unisannio.it}
1 An Eclipse-based Editor to Support LOTOS Newcomers Giuseppe De Ruvo, Antonella Santone Department of Engineering, University of Sannio, Benevento, Italy e-mail: {gderuvo@unisannio.it, santone@unisannio.it}
40 Behaviour Compatibility
 40 Behaviour Compatibility [2] R. De Nicola, Extentional Equivalences for Transition Systems, Acta Informatica, vol. 24, pp. 21-237, 1987. [3] J. Gray, Notes on Data Base Operating Systems, in Operating
40 Behaviour Compatibility [2] R. De Nicola, Extentional Equivalences for Transition Systems, Acta Informatica, vol. 24, pp. 21-237, 1987. [3] J. Gray, Notes on Data Base Operating Systems, in Operating
COMP 763. Eugene Syriani. Ph.D. Student in the Modelling, Simulation and Design Lab School of Computer Science. McGill University
 Eugene Syriani Ph.D. Student in the Modelling, Simulation and Design Lab School of Computer Science McGill University 1 OVERVIEW In the context In Theory: Timed Automata The language: Definitions and Semantics
Eugene Syriani Ph.D. Student in the Modelling, Simulation and Design Lab School of Computer Science McGill University 1 OVERVIEW In the context In Theory: Timed Automata The language: Definitions and Semantics
Managing test suites for services
 Managing test suites for services Kathrin Kaschner Universität Rostock, Institut für Informatik, 18051 Rostock, Germany kathrin.kaschner@uni-rostock.de Abstract. When developing an existing service further,
Managing test suites for services Kathrin Kaschner Universität Rostock, Institut für Informatik, 18051 Rostock, Germany kathrin.kaschner@uni-rostock.de Abstract. When developing an existing service further,
Composability Test of BOM based models using Petri Nets
 I. Mahmood, R. Ayani, V. Vlassov and F. Moradi 7 Composability Test of BOM based models using Petri Nets Imran Mahmood 1, Rassul Ayani 1, Vladimir Vlassov 1, and Farshad Moradi 2 1 Royal Institute of Technology
I. Mahmood, R. Ayani, V. Vlassov and F. Moradi 7 Composability Test of BOM based models using Petri Nets Imran Mahmood 1, Rassul Ayani 1, Vladimir Vlassov 1, and Farshad Moradi 2 1 Royal Institute of Technology
On The Theoretical Foundation for Data Flow Analysis in Workflow Management
 Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2005 Proceedings Americas Conference on Information Systems (AMCIS) 2005 On The Theoretical Foundation for Data Flow Analysis in
Association for Information Systems AIS Electronic Library (AISeL) AMCIS 2005 Proceedings Americas Conference on Information Systems (AMCIS) 2005 On The Theoretical Foundation for Data Flow Analysis in
Liveness and Fairness Properties in Multi-Agent Systems
 Liveness and Fairness Properties in Multi-Agent Systems Hans-Dieter Burkhard FB Informatik Humboldt-University Berlin PF 1297, 1086 Berlin, Germany e-mail: hdb@informatik.hu-berlin.de Abstract Problems
Liveness and Fairness Properties in Multi-Agent Systems Hans-Dieter Burkhard FB Informatik Humboldt-University Berlin PF 1297, 1086 Berlin, Germany e-mail: hdb@informatik.hu-berlin.de Abstract Problems
The UPPAAL Model Checker. Julián Proenza Systems, Robotics and Vision Group. UIB. SPAIN
 The UPPAAL Model Checker Julián Proenza Systems, Robotics and Vision Group. UIB. SPAIN The aim of this presentation Introduce the basic concepts of model checking from a practical perspective Describe
The UPPAAL Model Checker Julián Proenza Systems, Robotics and Vision Group. UIB. SPAIN The aim of this presentation Introduce the basic concepts of model checking from a practical perspective Describe
An Approach to Software Component Specification
 Page 1 of 5 An Approach to Software Component Specification Jun Han Peninsula School of Computing and Information Technology Monash University, Melbourne, Australia Abstract. Current models for software
Page 1 of 5 An Approach to Software Component Specification Jun Han Peninsula School of Computing and Information Technology Monash University, Melbourne, Australia Abstract. Current models for software
Automatic Verification of Real-Timed Systems Using Epsilon *
 1 Automatic Verification of Real-Timed Systems Using Epsilon * Jens Chr. Godskesen t Kim G. Larsen Arne Skou + Abstract In this paper we report on an application and extension of the theory of Timed Modal
1 Automatic Verification of Real-Timed Systems Using Epsilon * Jens Chr. Godskesen t Kim G. Larsen Arne Skou + Abstract In this paper we report on an application and extension of the theory of Timed Modal
Lecture1: Symbolic Model Checking with BDDs. Edmund M. Clarke, Jr. Computer Science Department Carnegie Mellon University Pittsburgh, PA 15213
 Lecture: Symbolic Model Checking with BDDs Edmund M Clarke, Jr Computer Science Department Carnegie Mellon University Pittsburgh, PA 523 Temporal Logic Model Checking Specification Language: A propositional
Lecture: Symbolic Model Checking with BDDs Edmund M Clarke, Jr Computer Science Department Carnegie Mellon University Pittsburgh, PA 523 Temporal Logic Model Checking Specification Language: A propositional
Joint Entity Resolution
 Joint Entity Resolution Steven Euijong Whang, Hector Garcia-Molina Computer Science Department, Stanford University 353 Serra Mall, Stanford, CA 94305, USA {swhang, hector}@cs.stanford.edu No Institute
Joint Entity Resolution Steven Euijong Whang, Hector Garcia-Molina Computer Science Department, Stanford University 353 Serra Mall, Stanford, CA 94305, USA {swhang, hector}@cs.stanford.edu No Institute
Enhancing Datalog with Epistemic Operators to Reason About Systems Knowledge in
 Enhancing Datalog with Epistemic Operators to Enhancing ReasonDatalog About Knowledge with Epistemic in Distributed Operators to Reason About Systems Knowledge in Distributed (Extended abstract) Systems
Enhancing Datalog with Epistemic Operators to Enhancing ReasonDatalog About Knowledge with Epistemic in Distributed Operators to Reason About Systems Knowledge in Distributed (Extended abstract) Systems
Tutorial on Model Checking Modelling and Verification in Computer Science
 Tutorial on Model Checking Modelling and Verification in Computer Science Armin Biere Institute for Formal Models and Verification Johannes Kepler University, Linz, Austria Abstract. This paper serves
Tutorial on Model Checking Modelling and Verification in Computer Science Armin Biere Institute for Formal Models and Verification Johannes Kepler University, Linz, Austria Abstract. This paper serves
Model-based GUI testing using Uppaal at NOVO Nordisk
 Model-based GUI testing using Uppaal at NOVO Nordisk Ulrik H. Hjort 2, Jacob Illum 1, Kim G. Larsen 1, Michael A. Petersen 2, and Arne Skou 1 1 Department of Computer Science, Aalborg University, Denmark
Model-based GUI testing using Uppaal at NOVO Nordisk Ulrik H. Hjort 2, Jacob Illum 1, Kim G. Larsen 1, Michael A. Petersen 2, and Arne Skou 1 1 Department of Computer Science, Aalborg University, Denmark
Specification and Analysis of Contracts Tutorial
 Specification and Analysis of Contracts Tutorial Gerardo Schneider gerardo@ifi.uio.no http://folk.uio.no/gerardo/ Department of Informatics, University of Oslo Gerardo Schneider (UiO) Specification and
Specification and Analysis of Contracts Tutorial Gerardo Schneider gerardo@ifi.uio.no http://folk.uio.no/gerardo/ Department of Informatics, University of Oslo Gerardo Schneider (UiO) Specification and
! Use of formal notations. ! in software system descriptions. ! for a broad range of effects. ! and varying levels of use. !
 What Are Formal Methods? David S. Rosenblum ICS 221 Winter 2001! Use of formal notations! first-order logic, state machines, etc.! in software system descriptions! system models, constraints, specifications,
What Are Formal Methods? David S. Rosenblum ICS 221 Winter 2001! Use of formal notations! first-order logic, state machines, etc.! in software system descriptions! system models, constraints, specifications,
Automated Refinement Checking of Asynchronous Processes. Rajeev Alur. University of Pennsylvania
 Automated Refinement Checking of Asynchronous Processes Rajeev Alur University of Pennsylvania www.cis.upenn.edu/~alur/ Intel Formal Verification Seminar, July 2001 Problem Refinement Checking Given two
Automated Refinement Checking of Asynchronous Processes Rajeev Alur University of Pennsylvania www.cis.upenn.edu/~alur/ Intel Formal Verification Seminar, July 2001 Problem Refinement Checking Given two
A Top-Down Visual Approach to GUI development
 A Top-Down Visual Approach to GUI development ROSANNA CASSINO, GENNY TORTORA, MAURIZIO TUCCI, GIULIANA VITIELLO Dipartimento di Matematica e Informatica Università di Salerno Via Ponte don Melillo 84084
A Top-Down Visual Approach to GUI development ROSANNA CASSINO, GENNY TORTORA, MAURIZIO TUCCI, GIULIANA VITIELLO Dipartimento di Matematica e Informatica Università di Salerno Via Ponte don Melillo 84084
Scenario Graphs Applied to Security (Summary Paper)
 Book Title Book Editors IOS Press, 2003 1 Scenario Graphs Applied to Security (Summary Paper) Jeannette M. Wing Computer Science Department Carnegie Mellon University Pittsburgh, PA 15213 US Abstract.
Book Title Book Editors IOS Press, 2003 1 Scenario Graphs Applied to Security (Summary Paper) Jeannette M. Wing Computer Science Department Carnegie Mellon University Pittsburgh, PA 15213 US Abstract.
Course Modelling of Concurrent Systems Summer Semester 2016 University of Duisburg-Essen
 Course Modelling of Concurrent Systems Summer Semester 2016 University of Duisburg-Essen Harsh Beohar LF 265, harsh.beohar@uni-due.de Harsh Beohar Course Modelling of Concurrent Systems 1 Course handler
Course Modelling of Concurrent Systems Summer Semester 2016 University of Duisburg-Essen Harsh Beohar LF 265, harsh.beohar@uni-due.de Harsh Beohar Course Modelling of Concurrent Systems 1 Course handler
Formal Methods in Software Design. Markus Roggenbach
 Formal Methods in Software Design Markus Roggenbach October 2001 2 Formal Methods Use of mathematics in software development main activities: writing formal specifications 2 Formal Methods Use of mathematics
Formal Methods in Software Design Markus Roggenbach October 2001 2 Formal Methods Use of mathematics in software development main activities: writing formal specifications 2 Formal Methods Use of mathematics
Formal Verification of Cognitive Models
 Formal Verification of Cognitive Models A. Macklem, F. Mili Oakland University Rochester, MI 48309-4478 macklem@oakland.edu, mili@oakland.edu Abstract Cognitive modeling has outgrown the toy problems of
Formal Verification of Cognitive Models A. Macklem, F. Mili Oakland University Rochester, MI 48309-4478 macklem@oakland.edu, mili@oakland.edu Abstract Cognitive modeling has outgrown the toy problems of
CLAN: A Tool for Contract Analysis and Conflict Discovery
 CLAN: A Tool for Contract Analysis and Conflict Discovery Stephen Fenech 1, Gordon J. Pace 1, and Gerardo Schneider 2 1 Dept. of Computer Science, University of Malta, Malta 2 Dept. of Informatics, University
CLAN: A Tool for Contract Analysis and Conflict Discovery Stephen Fenech 1, Gordon J. Pace 1, and Gerardo Schneider 2 1 Dept. of Computer Science, University of Malta, Malta 2 Dept. of Informatics, University
Course Modelling of Concurrent Systems Summer Semester 2016 University of Duisburg-Essen
 Course Modelling of Concurrent Systems Summer Semester 2016 University of Duisburg-Essen Harsh Beohar LF 265, harsh.beohar@uni-due.de Harsh Beohar Course Modelling of Concurrent Systems 1 Course handler
Course Modelling of Concurrent Systems Summer Semester 2016 University of Duisburg-Essen Harsh Beohar LF 265, harsh.beohar@uni-due.de Harsh Beohar Course Modelling of Concurrent Systems 1 Course handler
The Maude LTL Model Checker and Its Implementation
 The Maude LTL Model Checker and Its Implementation Steven Eker 1,José Meseguer 2, and Ambarish Sridharanarayanan 2 1 Computer Science Laboratory, SRI International Menlo Park, CA 94025 eker@csl.sri.com
The Maude LTL Model Checker and Its Implementation Steven Eker 1,José Meseguer 2, and Ambarish Sridharanarayanan 2 1 Computer Science Laboratory, SRI International Menlo Park, CA 94025 eker@csl.sri.com
Generic tools for verifying concurrent systems
 Science of Computer Programming 42 (2002) 39 47 www.elsevier.com/locate/scico Generic tools for verifying concurrent systems Rance Cleaveland a;, Steven T. Sims b a Department of Computer Science, SUNY
Science of Computer Programming 42 (2002) 39 47 www.elsevier.com/locate/scico Generic tools for verifying concurrent systems Rance Cleaveland a;, Steven T. Sims b a Department of Computer Science, SUNY
Modeling, Testing and Executing Reo Connectors with the. Reo, Eclipse Coordination Tools
 Replace this file with prentcsmacro.sty for your meeting, or with entcsmacro.sty for your meeting. Both can be found at the ENTCS Macro Home Page. Modeling, Testing and Executing Reo Connectors with the
Replace this file with prentcsmacro.sty for your meeting, or with entcsmacro.sty for your meeting. Both can be found at the ENTCS Macro Home Page. Modeling, Testing and Executing Reo Connectors with the
Formal Foundation of Workflow Hyperpaths and a Graph Search Algorithm for Workflow Hyperpath Generation
 Formal Foundation of Workflow Hyperpaths and a Graph Search Algorithm for Workflow Hyperpath Generation Sinnakkrishnan Perumal and Ambuj Mahanti Indian Institute of Management Calcutta, Joka, D.H. Road,
Formal Foundation of Workflow Hyperpaths and a Graph Search Algorithm for Workflow Hyperpath Generation Sinnakkrishnan Perumal and Ambuj Mahanti Indian Institute of Management Calcutta, Joka, D.H. Road,
A Modelling and Analysis Environment for LARES
 A Modelling and Analysis Environment for LARES Alexander Gouberman, Martin Riedl, Johann Schuster, and Markus Siegle Institut für Technische Informatik, Universität der Bundeswehr München, {firstname.lastname@unibw.de
A Modelling and Analysis Environment for LARES Alexander Gouberman, Martin Riedl, Johann Schuster, and Markus Siegle Institut für Technische Informatik, Universität der Bundeswehr München, {firstname.lastname@unibw.de
Sérgio Campos, Edmund Clarke
 Sérgio Campos, Edmund 1 / 23 Model checking is a technique that relies on building a finite model of a system and checking that a desired property holds in that model. The check is performed by an exhaustive
Sérgio Campos, Edmund 1 / 23 Model checking is a technique that relies on building a finite model of a system and checking that a desired property holds in that model. The check is performed by an exhaustive
3.4 Deduction and Evaluation: Tools Conditional-Equational Logic
 3.4 Deduction and Evaluation: Tools 3.4.1 Conditional-Equational Logic The general definition of a formal specification from above was based on the existence of a precisely defined semantics for the syntax
3.4 Deduction and Evaluation: Tools 3.4.1 Conditional-Equational Logic The general definition of a formal specification from above was based on the existence of a precisely defined semantics for the syntax
Flight Systems are Cyber-Physical Systems
 Flight Systems are Cyber-Physical Systems Dr. Christopher Landauer Software Systems Analysis Department The Aerospace Corporation Computer Science Division / Software Engineering Subdivision 08 November
Flight Systems are Cyber-Physical Systems Dr. Christopher Landauer Software Systems Analysis Department The Aerospace Corporation Computer Science Division / Software Engineering Subdivision 08 November
MODEL CHECKING FOR PLANNING RESOURCE-SHARING PRODUCTION
 MODEL CHECKING FOR PLANNING RESOURCE-SHARING PRODUCTION Jüri Vain, Tauno Otto, Alar Kuusik Tallinn University of Technology, vain@ioc.ee, tauno.otto@ttu.ee, kalar@va.ttu.ee Effectiveness of operation of
MODEL CHECKING FOR PLANNING RESOURCE-SHARING PRODUCTION Jüri Vain, Tauno Otto, Alar Kuusik Tallinn University of Technology, vain@ioc.ee, tauno.otto@ttu.ee, kalar@va.ttu.ee Effectiveness of operation of
SCHOOL: a Small Chorded Object-Oriented Language
 SCHOOL: a Small Chorded Object-Oriented Language S. Drossopoulou, A. Petrounias, A. Buckley, S. Eisenbach { s.drossopoulou, a.petrounias, a.buckley, s.eisenbach } @ imperial.ac.uk Department of Computing,
SCHOOL: a Small Chorded Object-Oriented Language S. Drossopoulou, A. Petrounias, A. Buckley, S. Eisenbach { s.drossopoulou, a.petrounias, a.buckley, s.eisenbach } @ imperial.ac.uk Department of Computing,
StateClock: a Tool for Timed Reactive Modules
 StateClock: a Tool for Timed Reactive Modules Jonathan S. Ostroff Department Of Computer Science, York University, Toronto, Canada, M3J 1P3. Email: jonathan@yorku.ca Abstract: We provide an overview of
StateClock: a Tool for Timed Reactive Modules Jonathan S. Ostroff Department Of Computer Science, York University, Toronto, Canada, M3J 1P3. Email: jonathan@yorku.ca Abstract: We provide an overview of
Proving the Correctness of Distributed Algorithms using TLA
 Proving the Correctness of Distributed Algorithms using TLA Khushboo Kanjani, khush@cs.tamu.edu, Texas A & M University 11 May 2007 Abstract This work is a summary of the Temporal Logic of Actions(TLA)
Proving the Correctness of Distributed Algorithms using TLA Khushboo Kanjani, khush@cs.tamu.edu, Texas A & M University 11 May 2007 Abstract This work is a summary of the Temporal Logic of Actions(TLA)
Rance Cleaveland The Concurrency Factory is an integrated toolset for specication, simulation,
 The Concurrency Factory Software Development Environment Rance Cleaveland (rance@csc.ncsu.edu) Philip M. Lewis (pml@cs.sunysb.edu) y Scott A. Smolka (sas@cs.sunysb.edu) y Oleg Sokolsky (oleg@ccc.com) y
The Concurrency Factory Software Development Environment Rance Cleaveland (rance@csc.ncsu.edu) Philip M. Lewis (pml@cs.sunysb.edu) y Scott A. Smolka (sas@cs.sunysb.edu) y Oleg Sokolsky (oleg@ccc.com) y
Lecture Notes on Program Equivalence
 Lecture Notes on Program Equivalence 15-312: Foundations of Programming Languages Frank Pfenning Lecture 24 November 30, 2004 When are two programs equal? Without much reflection one might say that two
Lecture Notes on Program Equivalence 15-312: Foundations of Programming Languages Frank Pfenning Lecture 24 November 30, 2004 When are two programs equal? Without much reflection one might say that two
XEVE, an ESTEREL Verification Environment
 XEVE, an ESTEREL Verification Environment Amar Bouali INRIA, B.P. 93, F-06902 Sophia-Antipolis cedex amar@sophia, inria, fr Abstract. We describe the verification methods and tools we are currently developing
XEVE, an ESTEREL Verification Environment Amar Bouali INRIA, B.P. 93, F-06902 Sophia-Antipolis cedex amar@sophia, inria, fr Abstract. We describe the verification methods and tools we are currently developing
Automatic synthesis of switching controllers for linear hybrid systems: Reachability control
 Automatic synthesis of switching controllers for linear hybrid systems: Reachability control Massimo Benerecetti and Marco Faella Università di Napoli Federico II, Italy Abstract. We consider the problem
Automatic synthesis of switching controllers for linear hybrid systems: Reachability control Massimo Benerecetti and Marco Faella Università di Napoli Federico II, Italy Abstract. We consider the problem
Part 1.3 Modal I/O Transition Systems as Semantics of UML4SOA
 IMT 2013 Lucca, Italy September 2013 Part 1.3 Modal I/O Transition Systems as Semantics of UML4SOA Martin Wirsing LMU München in co-operation with Sebastian Bauer, Rolf Hennicker, Philip Mayer M. Wirsing
IMT 2013 Lucca, Italy September 2013 Part 1.3 Modal I/O Transition Systems as Semantics of UML4SOA Martin Wirsing LMU München in co-operation with Sebastian Bauer, Rolf Hennicker, Philip Mayer M. Wirsing
An Algebraic Framework for Optimizing Parallel Programs
 An Algebraic Framework for Optimizing Parallel Programs Ichiro Satoh Department of Information Sciences, Ochanomizu University 2-1-1 Otsuka Bunkyo-ku Tokyo 112, Japan ichiro@is.ocha.ac.jp Abstract This
An Algebraic Framework for Optimizing Parallel Programs Ichiro Satoh Department of Information Sciences, Ochanomizu University 2-1-1 Otsuka Bunkyo-ku Tokyo 112, Japan ichiro@is.ocha.ac.jp Abstract This
On the Verification of Coordination
 On the Verification of Coordination Paul Dechering 1 and Izak van Langevelde 2 1 Hollandse Signaalapparaten B.V. P.O. Box 42, 7550 GD Hengelo, The Netherlands paul@dechering.net 2 Centrum voor Wiskunde
On the Verification of Coordination Paul Dechering 1 and Izak van Langevelde 2 1 Hollandse Signaalapparaten B.V. P.O. Box 42, 7550 GD Hengelo, The Netherlands paul@dechering.net 2 Centrum voor Wiskunde
Resource-bound process algebras for Schedulability and Performance Analysis of Real-Time and Embedded Systems
 Resource-bound process algebras for Schedulability and Performance Analysis of Real-Time and Embedded Systems Insup Lee 1, Oleg Sokolsky 1, Anna Philippou 2 1 RTG (Real-Time Systems Group) Department of
Resource-bound process algebras for Schedulability and Performance Analysis of Real-Time and Embedded Systems Insup Lee 1, Oleg Sokolsky 1, Anna Philippou 2 1 RTG (Real-Time Systems Group) Department of
when a process of the form if be then p else q is executed and also when an output action is performed. 1. Unnecessary substitution: Let p = c!25 c?x:
 URL: http://www.elsevier.nl/locate/entcs/volume27.html 7 pages Towards Veried Lazy Implementation of Concurrent Value-Passing Languages (Abstract) Anna Ingolfsdottir (annai@cs.auc.dk) BRICS, Dept. of Computer
URL: http://www.elsevier.nl/locate/entcs/volume27.html 7 pages Towards Veried Lazy Implementation of Concurrent Value-Passing Languages (Abstract) Anna Ingolfsdottir (annai@cs.auc.dk) BRICS, Dept. of Computer
Security for Multithreaded Programs under Cooperative Scheduling
 Security for Multithreaded Programs under Cooperative Scheduling Alejandro Russo and Andrei Sabelfeld Dept. of Computer Science and Engineering, Chalmers University of Technology 412 96 Göteborg, Sweden,
Security for Multithreaded Programs under Cooperative Scheduling Alejandro Russo and Andrei Sabelfeld Dept. of Computer Science and Engineering, Chalmers University of Technology 412 96 Göteborg, Sweden,
Experiences with OWL-S, Directions for Service Composition:
 Experiences with OWL-S, Directions for Service Composition: The Cashew Position Barry Norton 1 Knowledge Media Institute, Open University, Milton Keynes, UK b.j.norton@open.ac.uk Abstract. Having used
Experiences with OWL-S, Directions for Service Composition: The Cashew Position Barry Norton 1 Knowledge Media Institute, Open University, Milton Keynes, UK b.j.norton@open.ac.uk Abstract. Having used
EXTENDED DISTRIBUTED UML-BASED PROTOCOL SYNTHESIS METHOD
 EXTENDED DISTRIBUTED UML-BASED PROTOCOL SYNTHESIS METHOD Jehad Al Dallal Department of Information Science, Kuwait University, Kuwait ABSTRACT Synthesizing specifications for real time applications that
EXTENDED DISTRIBUTED UML-BASED PROTOCOL SYNTHESIS METHOD Jehad Al Dallal Department of Information Science, Kuwait University, Kuwait ABSTRACT Synthesizing specifications for real time applications that
Truth A verification platform for concurrent systems
 Truth A verification platform for concurrent systems Martin Lange, Martin Leucker, Thomas Noll, Stephan Tobies Abstract. We briefly explain the design and implementation of the newly developed tool Truth
Truth A verification platform for concurrent systems Martin Lange, Martin Leucker, Thomas Noll, Stephan Tobies Abstract. We briefly explain the design and implementation of the newly developed tool Truth
Learning Probabilistic Ontologies with Distributed Parameter Learning
 Learning Probabilistic Ontologies with Distributed Parameter Learning Giuseppe Cota 1, Riccardo Zese 1, Elena Bellodi 1, Fabrizio Riguzzi 2, and Evelina Lamma 1 1 Dipartimento di Ingegneria University
Learning Probabilistic Ontologies with Distributed Parameter Learning Giuseppe Cota 1, Riccardo Zese 1, Elena Bellodi 1, Fabrizio Riguzzi 2, and Evelina Lamma 1 1 Dipartimento di Ingegneria University
Modelling and Verifying Web Service Orchestration by means of the Concurrency Workbench p.1/19
 Modelling and Verifying Web Service Orchestration by means of the Concurrency Workbench Mariya Koshkina / Franck van Breugel IBM, Toronto / York University, Toronto Modelling and Verifying Web Service
Modelling and Verifying Web Service Orchestration by means of the Concurrency Workbench Mariya Koshkina / Franck van Breugel IBM, Toronto / York University, Toronto Modelling and Verifying Web Service
State Identification In The Hybrid Automata Description Of Dynamical Systems
 State Identification In The Hybrid Automata Description Of Dynamical Systems ISABELLA KOTINI, GEORGE HASSAPIS Dept. of Electrical and Computer Engineering Aristotle University of Thessaloniki 54006, Thessaloniki
State Identification In The Hybrid Automata Description Of Dynamical Systems ISABELLA KOTINI, GEORGE HASSAPIS Dept. of Electrical and Computer Engineering Aristotle University of Thessaloniki 54006, Thessaloniki
Verification of Bakery algorithm variants for two processes
 Verification of Bakery algorithm variants for two processes David Dedi 1, Robert Meolic 2 1 Nova Vizija d.o.o., Vreerjeva ulica 8, SI-3310 Žalec 2 Faculty of Electrical Engineering and Computer Science,
Verification of Bakery algorithm variants for two processes David Dedi 1, Robert Meolic 2 1 Nova Vizija d.o.o., Vreerjeva ulica 8, SI-3310 Žalec 2 Faculty of Electrical Engineering and Computer Science,
A Semantics to Generate the Context-sensitive Synchronized Control-Flow Graph (extended)
 A Semantics to Generate the Context-sensitive Synchronized Control-Flow Graph (extended) Marisa Llorens, Javier Oliver, Josep Silva, and Salvador Tamarit Universidad Politécnica de Valencia, Camino de
A Semantics to Generate the Context-sensitive Synchronized Control-Flow Graph (extended) Marisa Llorens, Javier Oliver, Josep Silva, and Salvador Tamarit Universidad Politécnica de Valencia, Camino de
Lecture 1: Model Checking. Edmund Clarke School of Computer Science Carnegie Mellon University
 Lecture 1: Model Checking Edmund Clarke School of Computer Science Carnegie Mellon University 1 Cost of Software Errors June 2002 Software bugs, or errors, are so prevalent and so detrimental that they
Lecture 1: Model Checking Edmund Clarke School of Computer Science Carnegie Mellon University 1 Cost of Software Errors June 2002 Software bugs, or errors, are so prevalent and so detrimental that they
1 Executive Overview The Benefits and Objectives of BPDM
 1 Executive Overview The Benefits and Objectives of BPDM This is an excerpt from the Final Submission BPDM document posted to OMG members on November 13 th 2006. The full version of the specification will
1 Executive Overview The Benefits and Objectives of BPDM This is an excerpt from the Final Submission BPDM document posted to OMG members on November 13 th 2006. The full version of the specification will
An Approach to the Generation of High-Assurance Java Card Applets
 An Approach to the Generation of High-Assurance Java Card Applets Alessandro Coglio Kestrel Institute 3260 Hillview Avenue, Palo Alto, CA 94304, USA Ph. +1-650-493-6871 Fax +1-650-424-1807 http://www.kestrel.edu/
An Approach to the Generation of High-Assurance Java Card Applets Alessandro Coglio Kestrel Institute 3260 Hillview Avenue, Palo Alto, CA 94304, USA Ph. +1-650-493-6871 Fax +1-650-424-1807 http://www.kestrel.edu/
Agent-Oriented Software Engineering
 Agent-Oriented Software Engineering Lin Zuoquan Information Science Department Peking University lz@is.pku.edu.cn http://www.is.pku.edu.cn/~lz/teaching/stm/saswws.html Outline Introduction AOSE Agent-oriented
Agent-Oriented Software Engineering Lin Zuoquan Information Science Department Peking University lz@is.pku.edu.cn http://www.is.pku.edu.cn/~lz/teaching/stm/saswws.html Outline Introduction AOSE Agent-oriented
Modeling Interactions of Web Software
 Modeling Interactions of Web Software Tevfik Bultan Department of Computer Science University of California Santa Barbara, CA 9106 bultan@cs.ucsb.edu Abstract Modeling interactions among software components
Modeling Interactions of Web Software Tevfik Bultan Department of Computer Science University of California Santa Barbara, CA 9106 bultan@cs.ucsb.edu Abstract Modeling interactions among software components
Safety Property Analysis Techniques for Cooperating Embedded Systems using LTS
 Safety Property Analysis Techniques for Cooperating Embedded Systems using LTS Woo Jin Lee 1, HoJun Kim 1, Heung Seok Chae 2 1 EECS, Kyungpook National University, Sangyeokdong, Bukgu, Daegu, South Korea
Safety Property Analysis Techniques for Cooperating Embedded Systems using LTS Woo Jin Lee 1, HoJun Kim 1, Heung Seok Chae 2 1 EECS, Kyungpook National University, Sangyeokdong, Bukgu, Daegu, South Korea
A modified and fast Perceptron learning rule and its use for Tag Recommendations in Social Bookmarking Systems
 A modified and fast Perceptron learning rule and its use for Tag Recommendations in Social Bookmarking Systems Anestis Gkanogiannis and Theodore Kalamboukis Department of Informatics Athens University
A modified and fast Perceptron learning rule and its use for Tag Recommendations in Social Bookmarking Systems Anestis Gkanogiannis and Theodore Kalamboukis Department of Informatics Athens University
Cover Page. The handle holds various files of this Leiden University dissertation
 Cover Page The handle http://hdl.handle.net/1887/22891 holds various files of this Leiden University dissertation Author: Gouw, Stijn de Title: Combining monitoring with run-time assertion checking Issue
Cover Page The handle http://hdl.handle.net/1887/22891 holds various files of this Leiden University dissertation Author: Gouw, Stijn de Title: Combining monitoring with run-time assertion checking Issue
Aalborg Universitet. Published in: Lecture Notes in Computer Science. DOI (link to publication from Publisher): / _29
 Aalborg Universitet ECDAR: An Environment for Compositional Design and Analysis of Real Time Systems David, Alexandre; Larsen, Kim Guldstrand; Nyman, Ulrik Mathias; Legay, Axel; Wasowski, Andrzej Published
Aalborg Universitet ECDAR: An Environment for Compositional Design and Analysis of Real Time Systems David, Alexandre; Larsen, Kim Guldstrand; Nyman, Ulrik Mathias; Legay, Axel; Wasowski, Andrzej Published
Investigating F# as a development tool for distributed multi-agent systems
 PROCEEDINGS OF THE WORKSHOP ON APPLICATIONS OF SOFTWARE AGENTS ISBN 978-86-7031-188-6, pp. 32-36, 2011 Investigating F# as a development tool for distributed multi-agent systems Extended abstract Alex
PROCEEDINGS OF THE WORKSHOP ON APPLICATIONS OF SOFTWARE AGENTS ISBN 978-86-7031-188-6, pp. 32-36, 2011 Investigating F# as a development tool for distributed multi-agent systems Extended abstract Alex
Handout 9: Imperative Programs and State
 06-02552 Princ. of Progr. Languages (and Extended ) The University of Birmingham Spring Semester 2016-17 School of Computer Science c Uday Reddy2016-17 Handout 9: Imperative Programs and State Imperative
06-02552 Princ. of Progr. Languages (and Extended ) The University of Birmingham Spring Semester 2016-17 School of Computer Science c Uday Reddy2016-17 Handout 9: Imperative Programs and State Imperative
A Framework for Enforcing Constrained RBAC Policies
 A Framework for Enforcing Constrained RBAC Policies Jason Crampton Information Security Group Royal Holloway, University of London jason.crampton@rhul.ac.uk Hemanth Khambhammettu Information Security Group
A Framework for Enforcing Constrained RBAC Policies Jason Crampton Information Security Group Royal Holloway, University of London jason.crampton@rhul.ac.uk Hemanth Khambhammettu Information Security Group
PROJECT PERIODIC REPORT
 PROJECT PERIODIC REPORT Grant Agreement number: 257403 Project acronym: CUBIST Project title: Combining and Uniting Business Intelligence and Semantic Technologies Funding Scheme: STREP Date of latest
PROJECT PERIODIC REPORT Grant Agreement number: 257403 Project acronym: CUBIST Project title: Combining and Uniting Business Intelligence and Semantic Technologies Funding Scheme: STREP Date of latest
JOURNAL OF OBJECT TECHNOLOGY
 JOURNAL OF OBJECT TECHNOLOGY Online at www.jot.fm. Published by ETH Zurich, Chair of Software Engineering JOT, 2002 Vol. 1, No. 2, July-August 2002 The Theory of Classification Part 2: The Scratch-Built
JOURNAL OF OBJECT TECHNOLOGY Online at www.jot.fm. Published by ETH Zurich, Chair of Software Engineering JOT, 2002 Vol. 1, No. 2, July-August 2002 The Theory of Classification Part 2: The Scratch-Built
Proof Pearl: The Termination Analysis of Terminator
 Proof Pearl: The Termination Analysis of Terminator Joe Hurd Computing Laboratory Oxford University joe.hurd@comlab.ox.ac.uk Abstract. Terminator is a static analysis tool developed by Microsoft Research
Proof Pearl: The Termination Analysis of Terminator Joe Hurd Computing Laboratory Oxford University joe.hurd@comlab.ox.ac.uk Abstract. Terminator is a static analysis tool developed by Microsoft Research
Mining with Eve - Process Discovery and Event Structures
 Mining with Eve - Process Discovery and Event Structures Robin Bergenthum, Benjamin Meis Department of Software Engineering, FernUniversität in Hagen {firstname.lastname}@fernuni-hagen.de Abstract. This
Mining with Eve - Process Discovery and Event Structures Robin Bergenthum, Benjamin Meis Department of Software Engineering, FernUniversität in Hagen {firstname.lastname}@fernuni-hagen.de Abstract. This
PROPAGATION-BASED CONSTRAINT SOLVER IN IMS Igor Ol. Blynov Kherson State University
 Інформаційні технології в освіті UDC 0044:37 PROPAGATION-BASED CONSTRAINT SOLVER IN IMS Igor Ol Blynov Kherson State University Abstracts Article compiling the main ideas of creating propagation-based
Інформаційні технології в освіті UDC 0044:37 PROPAGATION-BASED CONSTRAINT SOLVER IN IMS Igor Ol Blynov Kherson State University Abstracts Article compiling the main ideas of creating propagation-based
Constructing Control Flow Graph for Java by Decoupling Exception Flow from Normal Flow
 Constructing Control Flow Graph for Java by Decoupling Exception Flow from Normal Flow Jang-Wu Jo 1 and Byeong-Mo Chang 2 1 Department of Computer Engineering Pusan University of Foreign Studies Pusan
Constructing Control Flow Graph for Java by Decoupling Exception Flow from Normal Flow Jang-Wu Jo 1 and Byeong-Mo Chang 2 1 Department of Computer Engineering Pusan University of Foreign Studies Pusan
Negations in Refinement Type Systems
 Negations in Refinement Type Systems T. Tsukada (U. Tokyo) 14th March 2016 Shonan, JAPAN This Talk About refinement intersection type systems that refute judgements of other type systems. Background Refinement
Negations in Refinement Type Systems T. Tsukada (U. Tokyo) 14th March 2016 Shonan, JAPAN This Talk About refinement intersection type systems that refute judgements of other type systems. Background Refinement
Decoupled Software Pipelining in LLVM
 Decoupled Software Pipelining in LLVM 15-745 Final Project Fuyao Zhao, Mark Hahnenberg fuyaoz@cs.cmu.edu, mhahnenb@andrew.cmu.edu 1 Introduction 1.1 Problem Decoupled software pipelining [5] presents an
Decoupled Software Pipelining in LLVM 15-745 Final Project Fuyao Zhao, Mark Hahnenberg fuyaoz@cs.cmu.edu, mhahnenb@andrew.cmu.edu 1 Introduction 1.1 Problem Decoupled software pipelining [5] presents an
UML-Based Conceptual Modeling of Pattern-Bases
 UML-Based Conceptual Modeling of Pattern-Bases Stefano Rizzi DEIS - University of Bologna Viale Risorgimento, 2 40136 Bologna - Italy srizzi@deis.unibo.it Abstract. The concept of pattern, meant as an
UML-Based Conceptual Modeling of Pattern-Bases Stefano Rizzi DEIS - University of Bologna Viale Risorgimento, 2 40136 Bologna - Italy srizzi@deis.unibo.it Abstract. The concept of pattern, meant as an
2 after reception of a message from the sender, do one of two things: either the message is delivered to the receiver, or it is lost. The loss of a me
 Protocol Verification using UPPAAL: Exercises? Lab assistant: Alexandre David Department of Computer Systems (room 1237, mailbox 26), Uppsala University, Box 325, S751 05, Uppsala. Phone: 018-18 73 41.
Protocol Verification using UPPAAL: Exercises? Lab assistant: Alexandre David Department of Computer Systems (room 1237, mailbox 26), Uppsala University, Box 325, S751 05, Uppsala. Phone: 018-18 73 41.
Timed Automata: Semantics, Algorithms and Tools
 Timed Automata: Semantics, Algorithms and Tools Johan Bengtsson and Wang Yi Uppsala University Email: {johanb,yi}@it.uu.se Abstract. This chapter is to provide a tutorial and pointers to results and related
Timed Automata: Semantics, Algorithms and Tools Johan Bengtsson and Wang Yi Uppsala University Email: {johanb,yi}@it.uu.se Abstract. This chapter is to provide a tutorial and pointers to results and related
Łabiak G., Miczulski P. (IIE, UZ, Zielona Góra, Poland)
 UML STATECHARTS AND PETRI NETS MODEL COMPARIS FOR SYSTEM LEVEL MODELLING Łabiak G., Miczulski P. (IIE, UZ, Zielona Góra, Poland) The system level modelling can be carried out with using some miscellaneous
UML STATECHARTS AND PETRI NETS MODEL COMPARIS FOR SYSTEM LEVEL MODELLING Łabiak G., Miczulski P. (IIE, UZ, Zielona Góra, Poland) The system level modelling can be carried out with using some miscellaneous
Petri-net-based Workflow Management Software
 Petri-net-based Workflow Management Software W.M.P. van der Aalst Department of Mathematics and Computing Science, Eindhoven University of Technology, P.O. Box 513, NL-5600 MB, Eindhoven, The Netherlands,
Petri-net-based Workflow Management Software W.M.P. van der Aalst Department of Mathematics and Computing Science, Eindhoven University of Technology, P.O. Box 513, NL-5600 MB, Eindhoven, The Netherlands,
Q Body of techniques supported by. R precise mathematics. R powerful analysis tools. Q Rigorous, effective mechanisms for system.
 Introduction to Formal Methods 1 Introduction to Formal Methods 2 Formal Specification Requirements specification R notational statement of system services Software specification R formal abstract depiction
Introduction to Formal Methods 1 Introduction to Formal Methods 2 Formal Specification Requirements specification R notational statement of system services Software specification R formal abstract depiction
A Rough Set Approach for Generation and Validation of Rules for Missing Attribute Values of a Data Set
 A Rough Set Approach for Generation and Validation of Rules for Missing Attribute Values of a Data Set Renu Vashist School of Computer Science and Engineering Shri Mata Vaishno Devi University, Katra,
A Rough Set Approach for Generation and Validation of Rules for Missing Attribute Values of a Data Set Renu Vashist School of Computer Science and Engineering Shri Mata Vaishno Devi University, Katra,
TESTING MULTI-AGENT SYSTEMS FOR DEADLOCK DETECTION BASED ON UML MODELS
 TESTING MULTI-AGENT SYSTEMS FOR DEADLOCK DETECTION BASED ON UML MODELS Nariman Mani Vahid Garousi Behrouz H. Far Department of Electrical and Computer Engineering Schulich School of Engineering, University
TESTING MULTI-AGENT SYSTEMS FOR DEADLOCK DETECTION BASED ON UML MODELS Nariman Mani Vahid Garousi Behrouz H. Far Department of Electrical and Computer Engineering Schulich School of Engineering, University
Distributed Objects with Sense of Direction
 Distributed Objects with Sense of Direction G. V. BOCHMANN University of Ottawa P. FLOCCHINI Université de Montréal D. RAMAZANI Université de Montréal Introduction An object system consists of a collection
Distributed Objects with Sense of Direction G. V. BOCHMANN University of Ottawa P. FLOCCHINI Université de Montréal D. RAMAZANI Université de Montréal Introduction An object system consists of a collection
Continuous auditing certification
 State of the Art in cloud service certification Cloud computing has emerged as the de-facto-standard when it comes to IT delivery. It comes with many benefits, such as flexibility, cost-efficiency and
State of the Art in cloud service certification Cloud computing has emerged as the de-facto-standard when it comes to IT delivery. It comes with many benefits, such as flexibility, cost-efficiency and
To be or not programmable Dimitri Papadimitriou, Bernard Sales Alcatel-Lucent April 2013 COPYRIGHT 2011 ALCATEL-LUCENT. ALL RIGHTS RESERVED.
 To be or not programmable Dimitri Papadimitriou, Bernard Sales Alcatel-Lucent April 2013 Introduction SDN research directions as outlined in IRTF RG outlines i) need for more flexibility and programmability
To be or not programmable Dimitri Papadimitriou, Bernard Sales Alcatel-Lucent April 2013 Introduction SDN research directions as outlined in IRTF RG outlines i) need for more flexibility and programmability
Studying Graph Connectivity
 Studying Graph Connectivity Freeman Yufei Huang July 1, 2002 Submitted for CISC-871 Instructor: Dr. Robin Dawes Studying Graph Connectivity Freeman Yufei Huang Submitted July 1, 2002 for CISC-871 In some
Studying Graph Connectivity Freeman Yufei Huang July 1, 2002 Submitted for CISC-871 Instructor: Dr. Robin Dawes Studying Graph Connectivity Freeman Yufei Huang Submitted July 1, 2002 for CISC-871 In some
tempo2hsal: Converting Tempo Models into HybridSal Tool Description
 tempo2hsal: Converting Tempo Models into HybridSal Tool Description Ashish Tiwari Bruno Dutertre Computer Science Laboratory SRI International Menlo Park CA 94025 USA Report submitted under Honeywell subcontract
tempo2hsal: Converting Tempo Models into HybridSal Tool Description Ashish Tiwari Bruno Dutertre Computer Science Laboratory SRI International Menlo Park CA 94025 USA Report submitted under Honeywell subcontract
2 Discrete Dynamic Systems
 2 Discrete Dynamic Systems This chapter introduces discrete dynamic systems by first looking at models for dynamic and static aspects of systems, before covering continuous and discrete systems. Transition
2 Discrete Dynamic Systems This chapter introduces discrete dynamic systems by first looking at models for dynamic and static aspects of systems, before covering continuous and discrete systems. Transition
F-Soft: Software Verification Platform
 F-Soft: Software Verification Platform F. Ivančić, Z. Yang, M.K. Ganai, A. Gupta, I. Shlyakhter, and P. Ashar NEC Laboratories America, 4 Independence Way, Suite 200, Princeton, NJ 08540 fsoft@nec-labs.com
F-Soft: Software Verification Platform F. Ivančić, Z. Yang, M.K. Ganai, A. Gupta, I. Shlyakhter, and P. Ashar NEC Laboratories America, 4 Independence Way, Suite 200, Princeton, NJ 08540 fsoft@nec-labs.com
Towards Formalization of ARD+ Conceptual Design and Refinement Method
 Proceedings of the Twenty-First International FLAIRS Conference (2008) Towards Formalization of ARD+ Conceptual Design and Refinement Method Grzegorz J. Nalepa and Igor Wojnicki Institute of Automatics,
Proceedings of the Twenty-First International FLAIRS Conference (2008) Towards Formalization of ARD+ Conceptual Design and Refinement Method Grzegorz J. Nalepa and Igor Wojnicki Institute of Automatics,
Modeling and Verification of Marine Equipment Systems Using a Model Checker
 Modeling and Verification of Marine Equipment Systems Using a Model Checker Shunsuke YAO Hiroaki AWANO Yasushi HIRAOKA Kazuko TAKAHASHI Abstract We discuss the modeling and verification of marine equipment
Modeling and Verification of Marine Equipment Systems Using a Model Checker Shunsuke YAO Hiroaki AWANO Yasushi HIRAOKA Kazuko TAKAHASHI Abstract We discuss the modeling and verification of marine equipment
Formal Methods and their role in Software and System Development. Riccardo Sisto, Politecnico di Torino
 Formal Methods and their role in Software and System Development Riccardo Sisto, Politecnico di Torino What are Formal Methods? Rigorous (mathematical) methods for modelling and analysing (computer-based)
Formal Methods and their role in Software and System Development Riccardo Sisto, Politecnico di Torino What are Formal Methods? Rigorous (mathematical) methods for modelling and analysing (computer-based)
Symbolic Evaluation of Sums for Parallelising Compilers
 Symbolic Evaluation of Sums for Parallelising Compilers Rizos Sakellariou Department of Computer Science University of Manchester Oxford Road Manchester M13 9PL United Kingdom e-mail: rizos@csmanacuk Keywords:
Symbolic Evaluation of Sums for Parallelising Compilers Rizos Sakellariou Department of Computer Science University of Manchester Oxford Road Manchester M13 9PL United Kingdom e-mail: rizos@csmanacuk Keywords:
