CPS352 Lecture: Distributed Database Systems last revised 4/20/2017. Materials: Projectable showing horizontal and vertical partitioning
|
|
|
- Rosa Hensley
- 5 years ago
- Views:
Transcription
1 CPS352 Lecture: Distributed Database Systems last revised 4/20/2017 Materials: Projectable showing horizontal and vertical partitioning I. What is a Distributed Database System? A. In a distributed database system, the database is stored on several computers located at multiple physical sites. 1. This distinguishes it from a centralized system, in which the database is stored at a single location. 2. This distinguishes it from a parallel/cluster system, in which the database is stored on multiple computers at the same physical site. 3. This distinguishes it from a client-server system, in which the database is only stored at one site, though it may be accessed from multiple sites. (Of course, the server in a client-server system may itself be a distributed database!) B. There are two major variants of distributed systems 1. A distributed system can be HOMOGENOUS. All sites run the same brand of DBMS software (and generally the same general kind of hardware and operating system.) 2. A distributed system can be HETEROGENOUS. Different sites run different DBMS software, perhaps on different kinds of hardware running different operating systems as well. The databases at the different sites may have different schemes, and the individual sites may not even be aware of each other. 3. Naturally, coordination of activities between sites is much easier in the homogenous case - and most actual implementations are of this type. This is the type we will focus on. 1
2 II. What are the Advantages and Disadvantages of a Distributed System? A. We will basically consider the advantages and disadvantages of a remotely distributed system as over against a large, centralized system. 1. One of the major advantages of a distributed system is sharing of data generated at the different sites, without requiring that all the data be moved to a single central site. 2. Another advantage is the possibility of LOCAL CONTROL and AUTONOMY. Within boundaries established by the need for sharing, each site can control its own data, determine what is stored how etc. 3. The possibility of mproved response times to queries. As over-against a centralized system, a distributed system that stores data at the site(s) that use it the most allows them to access the data more quickly than they would if they had to get the data from a central site via a communication link. 4. With the rise of reliance on the internet and ecommerce, a fourth motivation that has always been there have become especially prominent: Reliability and availability. In a centralized system, the failure of the main system - or some sort of disaster at the place where it is located - shuts down all processing activity until the problem is fixed. But in a distributed system, the failure of a site may reduce performance and/or make some data unavailable. But processing of most kinds of requests can continue. Indeed, if data is replicated at multiple sites, it is possible for most processing to proceed - albeit perhaps with reduced performance. We say that the system has improved availability. 5. Much of the work on distributed systems was done before the rise of ecommerce and cloud computing, but the issues that were discovered and solutions to them arose in this context are also relevant to the kinds of systems needed for these contexts as well. Some of the issues have helped motivate movement toward NoSQL database models and away from ACID transactions. But that's for 2
3 another lecture. Our focus in this lecture will be on distribured computing in the context of traditional relational databases with ACID transactions. B. Disadvantages 1. One major disadvantage of a distributed system is the cost and time required for communication between sites. a. This is not necessarily a disadvantage, if the alternatives are a centralized system where ALL queries require communication vs a distributed system where SOME queries can be processed locally at the requesting site. b. But operations requiring access to data at multiple sites will almost always involve more communication between sites than would be required if all the data involved were at one location. c. The performance impact of communication depends a great deal on what kind of communication links are used. In particular, note that the performance of a network is determined by the slowest link. If the Internet is used, this is often the "last mile" connection between a DBMS site and the ISP. d. The time cost of any given message is given by: Access delay + (message length) / (data rate) i. Access delay is the overhead time needed to set up for a message between sites. This varies greatly from system to system, but will tend to be a constant that is independent of message length. 3
4 ii. For short messages, access delay may be the dominant cost. iii. For longer messages, (message length) / (data rate) may be the dominant cost. e. Depending on the configuration, communication cost may dominate disk access cost, in which case a distributed systems might need to be optimized to minimize the number and volume of messages, rather than disk accesses. 2. A second disadvantage is increased complexity. As we shall see, choosing a query processing strategy, performing updates, dealing with crashes, and concurrency control are all much more complex in a distributed system. 3. A third disadvantage related to the second is that distributed systems are much harder to debug. In fact, the algorithms used must be bug-proof; discovering the cause of a problem that arises only under certain circumstances of operation timing is not possible using conventional debugging techniques. III. Partitioning and Replication of Data A. At the heart of the idea of a distributed system is the distribution of data over multiple sites. 1. The conceptually simplest distribution scheme is to distribute at the table level: any given table is stored in its entirety at some site. 2. However, there are situations which call for splitting a table up between sites. This is called PARTITIONING or FRAGMENTATION. (Fragmentation is the term used in the book, but partitioning seems to be the more common term now.) 4
5 3. Oftentimes, an organization will have branch offices at different physical locations, each of which is a network site. If different tuples in a table are associated with different sites, it may make sense to partition the table HORIZONTALLY - i.e. by rows. a. Example: the book used the example of a deposit relation for a bank, where each branch stores the rows pertaining to its customers. b. Example: a customer relation for a sales organization may be stored so that each customer's data is stored by the branch office that normally services him/her/it. c. When a table is partitioned horizontally, the entire table can be reconstructed by doing the UNION of the partitions. d. The impact of horizontal partitioning on performance involves both gains and losses: i. Operations by a local office on relevant rows of the table incur no communications cost. ii. Operations on the entire table (e.g. complete printouts, searches for rows meeting some criterion other than the one used for partitioning, summaries, etc) may incur massive communications cost - more than if the entire unpartitioned relation were stored at one site. 4. In other cases, it will make sense to partition a table VERTICALLY - by columns. a. One motivation for this is security. i. Most DBMS's provide mechanisms whereby certain users may be given access to some columns of a table but not others. (In a relational scheme, this is done by using views. The restricted users are given access to the view, but not directly to the underlying table.) 5
6 ii. In a distributed system, there is increased risk of a breach of the security mechanisms, since each site has some degree of autonomy. Thus, it may be decided that certain sensitive columns should only be stored at the site having primary responsibility for them. iii. For example, the salary column of a personnel relation may be stored only at the site containing the payroll department. Other sites may store personnel data contained in other columns. b. Another motivation for vertical partitioning is selective replication of a table. It may be decided that a copy of the entire table should be kept at one central site, but that other sites might store copies of the most frequently used columns. In this way, most queries on the table can be done without communication cost; but some queries (those involving the infrequently-used columns) will have to be referred to the central site.) c. A vertically-partitioned table can be reconstructed using a natural join if one of the following criteria is met: i. Each partition participating in the join includes the primary key. or ii. Each partition includes a system-generated tuple identifier that is unique for each row of the table. (In essence, this is a system-generated primary key for the table; but it is never actually seen by users.) d. Note that joining partitions to reconstruct the table is only necessary if there is NO site that has a copy of the whole table. This would be a fairly unusual situation. 5. If reasons for both kinds of partitioning pertain to a given table, then it can be partitioned both ways. PROJECT Partitioning Example 6
7 a. Note that personnel data is distributed horizontally by regional office. b. In two of the regions, salary data is partitioned off vertically and stored at corporate headquarters. This is not done in the central region - perhaps the division office there shares a system with corporate payroll. c. Job history data is partitioned off vertically but is not partitioned horizontally. Presumably, an employees past job history may encompass several regions and so cannot be associated with any one. This partition is presumably used less often than other parts of the table, and so may be stored at a central archival site (corporate headquarters). 6. A partitioning scheme can be specified by giving a relational algebra or SQL-like expression specifying exactly what goes into each partition. a. In a horizontal partitioning, each partition will be specified by a selection operation for each partition that specifies what tuples belong in it. b. In a vertical partitioning, each partition will be specified by a projection operation for each partition that specifies what columns belong in it. c. In a combined partitioning, both operations will be present. B. Two of the major motivations for distributing a database are improved availability and improved performance through making it possible for frequent queries to be processed locally at the originating site. Both of these advantages typically require that some data be REPLICATED - i.e. that the same information be stored at more than one site. 7
8 1. Replicated data may still be available in the face of the failure of one site, providing that another site has a copy. 2. Local access to a private replica of commonly-used data is more efficient than having to go to some other site to get at the only copy. 3. Replication can be combined with partitioning: often only the most commonly-used partitions of a given table is replicated widely. 4. Of course, replication is a form of redundancy, and creates its share of problems. a. Replicating data uses extra storage space. b. Updating of replicated data is a significant problem, to which there are no easy solutions. i. Whatever update strategy is used must ensure that all copies of the data agree with one another; but it is inevitable that there be a time during the update process when some copies have been updated while others have not. The update strategy must prevent transactions from producing inconsistent results through reading the wrong version of an item being updated at the same time. ii. It is always possible that a replica of data being updated exists on a site that is currently not functioning - either crashed or cut off from the rest of the network by a communication failure. The update strategy must assure that an inconsistent replica is not used in a computation. c. When data is replicated, the advantages of improved availability and access must be weighed against these disadvantages to decide whether replicating a particular portion of the database is worth it. 8
9 d. In general, replication improves performance for read-only transactions, while requiring more effort (and hence potentially hurting performance) for transactions involving updating data. C. One author suggested the following broad guidelines for deciding whether to partition, replicate, or centralize a given relation: 1. If a relation used at many sites is small, then replicate it. 2. If a relation used at many sites is large, but there is a way to partition it so that most queries will only access the local part, then partition it. 3. If a relation used at many sites is large, and cannot be partitioned in such a way as to allow most queries to only access the local part, then centralize it. (In this case, a partitioned scheme would require more communications overhead since many queries would need access to data stored at two or more sites.) Example: suppose we were to take the example library database we have been using throughout the course and distribute it. (We assume that the library has several branches.) - The category relation might well be replicated at each site, since it is small and referred to frequently. - The relation tying together a book's call_number, copy_number and barcode might well be partitioned horizontally, with each branch getting the portion pertaining to the books that belong there. - The relation tying together a book and its authors might well be stored centrally, since it is large, cannot be partitioned in a site-specific way, and is likely accessed infrequently. 9
10 D. A highly desirable property of a distributed system is LOCATION TRANSPARENCY: a user should not have to know WHERE an object is stored in order to access it. 1. Location transparency makes it possible for data to be moved to another site if appropriate, without requiring users to alter their queries. 2. Location transparency makes it possible for the query strategy planner to select the most inexpensive site to get data from in the case of replicated data. 3. Location transparency allows a query to access replicated data from another site if the normal site from which it is obtained is down. E. An important property is that top-level items (databases or perhaps tables within a database) have unique names. This can be handled in a number of ways: 1. A central name server that "registers" all names - but clearly this can be become a performance bottleneck and makes the whole system vulnerable to the failure of a single site. 2. Incorporating the id of a site (e.g. its ip number) into the names of items residing on the site - but this flies in the face of location transparency. 3. Combining the above with the use of aliases at this site. For example, this is the approach db2 uses a. You have been accessing the database through one of the workstations, though in fact the database resides on the server, joshua. b. Each of the workstations actually runs a copy of db2, which accesses a client instance (not the instance in which the data is actually stored.) The client instance, however, records aliases to items residing on the server. 10
11 c. When you issue a command like connect to sample..., what actually occurs is that the dbms software you are running checks the client database and discovers that "sample" is an alias for a database on joshua, and connects to it. (It happens to the case that this database is also called sample, but that is not necessary) IV. Querying Distributed Data A. When data is distributed, we have to deal with the possibility that a given transaction will involve processing at more than one site. 1. We associate a given transaction with the site where it originates; this is the place where the results must finally be sent. 2. A transaction is said to be LOCAL if it only accesses data stored at the site if originates at. 3. A transaction is said to be GLOBAL if it must access data at a site other than its point of origin. From the standpoint of a given site doing some of the work on a global transaction, the transaction may be either: a. A transaction originating locally, but needing data from elsewhere. b. A transaction originating elsewhere, but needed local data at the current site. B. An important goal of a distributed system is FRAGMENTATION TRANSPARENCY. In the case of partitioned or replicated tables, the user should be able to formulate a query without knowing how the table is partitioned and/or replicated across multiple sites - i.e. from the user's standpoint, it should appear as if the the entire table exists at one site. (And when this is combined with location transparency, the appearance is given that this site is the user's own site.) 11
12 C. The strategy selection component of a query processor has a challenging job when dealing with a global query. Because of the time costs associated with communication of data, different plausible strategies may differ in time needed by orders of magnitude. C.J. Date gives the following illustration of this point. 1. Assume an organization has three tables, as follows: a. Schemes: Scheme S(S#, CITY) - relating suppliers to the city where they are located. (Primary key S#) Scheme P(P#, COLOR) - relating parts to their colors. (Primary key P#) Scheme SP(S#, P#) - specifying which suppliers supply which parts b. Cardinalities of the tables (number of tuples): n(s) = 10,000 n(p) = 100,000 n(sp) = 1,000,000 c. Each tuple is 200 bits long. d. Tables S and SP are stored at site A, and P at site B. 2. Suppose that the data communication system can transmit 50,000 bits per second, with an 0.1 second access delay for each message. (This is an old example. While modern networks offer much higher data rates, the basic relationships between times for various strategies we shall see still hold.) 12
13 3. Now consider the following query (originating at some site A): Give the supplier numbers of all suppliers located in London who supply red parts. In SQL: SELECT S.S# FROM S NATURAL JOIN SP NATURAL JOIN P WHERE CITY = 'LONDON' AND COLOR = 'RED'; Suppose that statistical information leads to the following estimates of sizes: a. From the given n values, we can estimate that each part is supplied by 10 suppliers (n(sp) / n(p)), and that each supplier supplies an average of 100 parts (n(sp) / n(s)) b. Suppose we also can learn that the number of red parts is 10, and the number of SP tuples pertaining to London suppliers is 100, Now consider various plausible strategies. In each case, we consider only communication time. The cost for doing the necessary joins is comparable for each strategy. a. Copy relation P to site A and do all processing there. T = (100,000 tuples * 200 bits/tuple) / (50,000 bits/second) = seconds = seconds = 6.67 minutes (The entire relation P is transmitted as a single long message) b. Copy relations S and SP to site B and do all processing there. T = (10,000 tuples * 200 bits/tuple) / (50,000 bits/second) (1,000,000 tuples * 200 bits/tuple) / (50,000 bits/second) seconds to send final answer = 40.1 seconds seconds +.1 seconds = seconds = 1.12 hours 13
14 c. Join relations S and SP at site A, then select out the London tuples. For each, query site B to see if the part involved is red. T = 2 * 0.1 * 100,000 seconds = 20,000 seconds = 5.56 hours - There are 100,000 SP tuples pertaining to London suppliers - Each gives rise to a query message and a response (2 messages). - Since the messages will presumably be small, the dominant cost will be the access delay of 0.1 second for each. (Even if the message were the full 200 bit tuple, transmission time would only be seconds.) d. Select tuples from P at site B for which the color is red, and send a message to site A requesting a list of London suppliers that supply that particular part. Then send final answer back to A. T = 10 * ( / 50,000) second = 2.05 seconds - There are 10 P tuples for red parts - Each gives rise to two messages - a query and a response. The query message time is essentially just the access delay. - The statistical data leads us to expect that each part is supplied by 10 suppliers. Since 1/10 of the suppliers are in London, the reply message will typically contain one supplier. 14
15 e. Join S and SP at site A, select tuples from the join for which the city is London, and project the result over (S# P#). Move the projection to site B and complete the processing there. Then send final answer back to A. T = (100,000*200)/50, = seconds = 6.67 minutes f. Select tuples from P at site B for which the color is red. Send these to site A and complete the processing there T = (10 * 200) / 50,000 = approx 0.1 second g. Note, then, that these strategies (all of which are plausible) have communication costs ranging from 0.1 second to the better part of a day! D. One observation that can help to narrow down the number of options to be considered is to recognize that operations on data are of two types: data reducing and data expanding. 1. A data reducing operation produces a result that is smaller in size than what it started with. a. Select and project are almost always data reducing. b. Natural join may be data reducing if the number of tuples which successfully join is a fraction of the total number of tuples in the relations involved. c. Theta join may also be data reducing if the selection condition eliminates most of the tuples produced by the join. d. Intersection and division are also data reducing. e. Union is data reducing if some tuples appear in both relations being combined. f. Summarizing functions (count, sum, average etc.) are data reducing 15
16 2. A data expanding operation produces a result that is larger in size than what it started with. a. Cartesian join is always data expanding. b. Natural join and theta join may be data expanding. 3. As a general rule, data reducing operations should be performed at the site where data is stored before sending it to another site, and data expanding operations should be performed at the site where data is needed after it has been sent there. E. One data reducing operator that can be used in some cases is the SEMIJOIN. 1. Example: a. Suppose we distribute our library database so that checkout information is stored locally, but full catalog information on a book (callno, title etc.) is stored centrally. b. Suppose we need to print out overdue notices for a group of checkouts pertaining to books that have just become overdue. We will do something like: select callno, copyno, title, borrower_id from checkout natural join bookinfo where datedue = yesterday; c. One option for accomplishing this is to copy the entire bookinfo table from the central site to the local branch, and then do the join locally. This is an obviously bad idea, since the book relation is presumably quite large, and only a few rows are relevant to our query. 16
17 d. A better approach would be to send to the local branch only those tuples of the book relation which are relevant to the query - i.e. those whose callno matches the callno of one of the overdue books. This is computed by taking the semijoin: bookinfo X checkout which is defined as project bookinfo X checkout bookinfo scheme e. The complete strategy might then be as follows: i. Compute project select checkout callno datedue = yesterday ii. Send this to the central site. iii. Compute the semijoin of bookinfo with this, project out callno and title, and send the result back to the local office. iv. Join the information returned from the central site with checkout and project the desired fields. f. It is obvious that, in this case, the semijoin is far superior to sending the entire bookinfo relation to the local site. Even though tuples flow both ways, the total volume of information transmitted is much less. g. We might also compare this semijoin-based strategy to one other option involving only regular joins: Send the relevant checkout tuples to the central site, do the join with bookinfo there, and send the result back. The semijoin-based strategy involves transmitting the same number of tuples in each direction; but 17
18 since the tuples are projected down to smaller size first in each case, the semijoin-based strategy has an edge in terms of total data volume. 2. Formally, given relations r1 on scheme R1 and r2 on scheme R2, r1 X r2 is defined to be project (r1 X r2) R1 3. Observe that r2 X (r1 X r2) = r2 X r1. This is one fact we relied on in the above example. 4. Further, r1 X r2 = r1 X project r2. This is what R1 intersect R2 let us do a projection locally before sending checkout tuples to the central site to be semijoined with bookinfo there. V. Updating Distributed Data A. Most of the complexities associated with distributed databases arise in conjunction with the updating of data in the database. The two major sources of complexity are these: 1. If a transaction updates data stored at more than one site, we must ensure that either all the updates commit or none of the updates commit. We must avoid the possibility that an update at one site commits while another aborts. 2. When data is replicated, we must make sure that ALL replicas are updated consistently. Since it is impossible to ensure that all updates to replicas of an item occur at exactly the same moment of time, we must also ensure that inconsistencies do not result from a transaction reading a replica that is not yet updated. 18
19 3. In addressing each of these problems, we must bear in mind that a distributed system is vulnerable to partial failure - some sites may be up while others are down. a. An individual site may suffer a hardware failure or software crash at any time - including in the middle of an update operation in which it is one of the participating sites. b. A communication link between sites can fail at any time - including in the middle of an update operation. The consequences of link failure range from causing a site to be out of touch with the rest of the network to a partitioning of the network into two disconnected subnetworks. When link failure makes communication between certain sites impossible, we say the network has been partitioned. (We do not worry about a link failure that still leaves a site connected to the rest of the network through an alternate path. We assume that lower levels of network software handle this transparently for us.) c. In addition to the total failure of a site or link, we must also consider the possible garbling or loss of a message in transit. i. If a message is garbled, lower layers of the software will request a repeat transmission. ii. However, if a message is lost, appropriate action might need to be taken at a higher level. B. We consider first the matter of updating data stored at more than one site. 1. To ensure that either all updates commit or no updates commit, we can use a protocol called the TWO-PHASE COMMIT PROTOCOL. a. In this protocol, one site acts as the coordinator. Normally, this is the site where the transaction originated. 19
20 b. As each site completes its work on the transaction and becomes partially-committed, it sends a message to the coordinator. i. Once the coordinator receives completion messages from all participating sites, it can begin the commit protocol. ii. However, if it receives a failure message from any site, then it must instruct all sites to abort the transaction. iii. The coordinator must also abort the transaction if it fails to receive a completion message from some site within a reasonable time. This is necessary to deal with the possibility that a participating site (or its link) might fail in mid transaction. c. In phase 1 of the protocol, the following events occur: i. The coordinator adds a <prepare T> entry to its log and forces all log records to stable storage. ii. The coordinator sends a prepare-to-commit message to all participating sites. iii. Each site normally adds a <ready T> entry to its log and forces all log entries to stable storage. It then sends a ready message to the coordinator. iv. However, if some site wishes to abort the transaction, it may still do so by adding a <no T> entry to its log, forcing the log entries to stable storage, and then sending an abort message to the coordinator. v. Once a site sends a ready message to the coordinator, it gives up the right to abort the transaction. It must go ahead with the commit if the coordinator tells it to do so. 20
21 d. In phase 2 of the protocol, the coordinator waits for replies from its prepare-to-commit message to come back. i. If any comes back negative, or fails to come back in a reasonable time, then the coordinator must write an <abort T> entry in its log and send an abort message to all sites. ii. If all replies come back positive, the coordinator writes a <commit T> entry in its log and sends a commit message to all sites. iii. At this point, the decision of the coordinator is final. Whatever was decided, the protocol will now operate to ensure that it occurs - even if a site or link should now fail. iv. Each site, when it receives the message from the coordinator, either commits or aborts the transaction, makes an appropriate entry in its log, and then sends an acknowledge message to the coordinator. (The sending of an acknowledgement is not strictly necessary - some implementations require this while others do not.) v. When the coordinator receives acknowledge messages from all sites, it writes a <complete T> entry to its log. vi. Should any site fail to respond within reasonable time, the coordinator may resend the message to it. This resending can continue at regular intervals until the site response comes back. (This is not strictly necessary, however. Once the coordinator has decided the transaction's fate, the site will assume responsibility for finding it out anyway.) 2. The two-phase commit protocol deals with site or link failures (other than failure of the coordinator) as follows: 21
22 a. If a site or link fails before sending its ready message, then the transaction will abort. i. When the site comes back up or is reconnected, it may try to send a ready message, but if the coordinator has decided to abort the transaction the ready message will now be ignored. ii. The coordinator will continue sending periodic abort messages to the site until it acknowledges; thus the protocol will eventually finish in a consistent state. b. If a site or link fails after the site sends its ready message, and the failure results in the ready message being lost, then the result is the same as above. c. If a site or link fails after the coordinator receives the site's ready message but before the site receives the final decision from the coordinator, then the site's log will contain a <ready T> entry. During recovery, the site must determine the fate of T by either receiving a message from the coordinator or consulting some other site that participated in the transaction. d. If a site or link fails after it receives the coordinator's decision and records <abort T> or <commit T> in its log - but before the site sends an acknowledge message - then the site knows what to do about the transaction when it comes back up. It will send an acknowledge message in response to a resend of the coordinator's verdict. (The same situation holds if the site's acknowledge message is lost in transmission.) 3. Coordinator failure is handled as follows: a. If the coordinator fails before it sends a final decision as to the transaction's fate to at least one site, then a site that 22
23 has already sent a ready message to the coordinator must wait until the coordinator recovers or is reconnected before deciding what to do about the transaction. (But a site that has not sent a ready message can timeout and decide to abort the transaction, of course; and if another site can find out it has done so, it can abort too.) b. If the coordinator fails after sending a final decision to at least one site, other sites may be able to obtain the decision from that site so as not to have to wait. c. In any case, when the coordinator recovers or is reconnected, it will inspect its log and send some decision to each site. i. If it finds <start T> but no <prepare T>, it will presumably abort the transaction. ii. If it finds <prepare T> but no <commit T> or <abort T>, it may try again to find out the status of the participating sites, or it may just abort the transaction. iii. If it finds <abort T> or <commit T> but no <complete T>, it can start the process of sending abort/commit messages and waiting for acknowledgements over again. iv. Of course, if it finds <complete T> then nothing need be done. d. Under some circumstances, coordinator failure can result in BLOCKING. If a site has to wait for the recovery of the coordinator before it knows whether or not a given transaction committed, then certain data items may be locked for a long time. This is, of course, highly undesirable. (The book discusses some alternatives for dealing with situations like this, such as 3-phase commit.) 23
24 C. Now we consider the matter of updating replicated data. 1. Ultimately, all replicas of a given data item must be updated. However, the system should exhibit REPLICATION TRANSPARENCY; any update transaction should be able to execute without knowing how many replicas of a given item exist. (I.e. a transaction's write to one copy of an item should be converted by the DBMS into writes to all of them.) 2. One way to do this is to perform simultaneous updates at the transaction level - i.e. transform each update transaction into a set of updates at each site. a. This flies in the face of replication transparency b. This does ensure that all replicas of a given item are consistent, if each replica is locked as part of the update process. c. Moreover, it can make response time for update transactions poor. d. Finally, one or more replicas may be located at sites that are either down or out of contact due to failed links. i. If we made a transaction wait if ANY replica of an updated item is not available, then replication works against availability rather than for it. (We would be better off, from an availability for update standpoint, if data were not replicated.) ii. For this reason, some provision must be made for postponing an update to an inaccessible site. Some site must be responsible for informing it of updates that were missed once it comes back. iii. This can get complicated, because we must decide who is responsible for informing the unavailable site. What if the responsible site is offline when the other site comes back? 24
25 3. An alternate that is often used is to designate one copy of the data as the PRIMARY (or master) copy. a. Transactions that wish to read an item may read any replica, but all updates are done first to the primary copy. b. The site containing the primary copy is responsible for sending updates to sites containing replicas. i. This may be done after every update transaction. ii. This may involve resending the updates periodically if a site is down. iii. Or, if updates are infrequent and currency of data is not vital, a fresh copy of the entire file may be shipped from the primary site to secondary sites on a periodic basis. c. We accept the possibility that data at secondary sites may be a bit out of date. Thus, any transaction for which it is critical that we have the most recent data (e.g. a funds transfer) must read the primary copy. Secondary copies can be read only in cases where inconsistency could not result from stale data. d. Of course, we now must face the possibility that the site containing the primary copy of a data item should be offline or disconnected. i. In this case, we may declare the data item unavailable for update until the primary copy site comes back online. ii. Or, we may temporarily designate a secondary copy as the primary copy, and then report changes back to the primary site when it comes back online. 25
26 iii. However, designating a secondary site as the primary copy could lead to inconsistencies (requiring human intervention to straighten out) if partitioning of the network leads to two primary copies being declared - one in each partition. VI. Concurrency Control for Distributed Data A. So far, our discussion has dealt with problems that arise if just one transaction attempts to access or update a data item. We now consider how our concurrency control schemes must be modified to cope with distributed data. B. First, we consider the lock-based schemes. 1. As always, we must lock a data item before we access it. But now we face the possibility of having to lock items stored at several different sites. 2. One approach to locking is to use a CENTRALIZED LOCK MANAGER located at one of the sites. All locks are obtained by means of a message to this site. a. Compared to other schemes, this has two advantages. i. A site that needs to lock several replicas of the same item can get all the locks it needs with a single message. ii. As we shall see, this makes deadlock detection much easier. b. However, centralized lock management has the usual disadvantages of centralizing any function in a distributed system. i. Even a local transaction will now involve communication overhead if locking is needed. 26
27 ii. The lock manager is a potential bottleneck. iii. Failure of the lock manager can cripple the system. (There is a way to deal with this by using an election scheme to choose a new lock manager in such cases. The book discusses this.) 3. An alternative to centralized locking is distributed locking, with each site managing the locks on items stored there. a. The advantages are the opposites of the disadvantages of the centralized scheme. In particular, local transactions stay local. b. There are some disadvantages, though. i. The message overhead is increased significantly. For each item to be locked, at least three messages are needed, IN ADDITION TO THE MESSAGES NEEDED TO ACCESS THE DATA: - A lock request message to the site where the item is stored. - A lock granted message back to the requestor. - An unlock message to finally release the item. (Actually, this last message might be combined with the messages involved in the two-phase commit protocol.) ii. Deadlock detection now becomes much harder. No one site has all the information needed to determine whether the system is deadlocked. 27
28 Example: Transaction T1 locks item Q1 at its own site, site S1. Transaction T2 (at site S2) locks item Q3 at another site, site S3. Transaction T1 now sends a message to site S3, requesting a lock on Q3. Transaction T1 is forced to wait. Transaction T2 now sends a message to site S1, requesting a lock on Q1. Transaction T2 is forced to wait. Transactions T1 and T2 are now deadlocked, but neither site knows it! - Site S1 knows that its transaction, T1, is waiting for a lock at site S3, and that transaction T2 from S2 is waiting for a local lock held by T1. This can be represented by the graph (T2) --> (T1) - Site S2 knows that its transaction, T2, is waiting for a lock at site S1. - Site S3 knows that transaction T1 from site S1 is waiting for a local lock held by T2. This can be represented by the graph (T1) --> (T2) - No one knows about the circular wait! c. Distributed lock management can further complicate dealing with updates to replicated data 28
29 i. If the updating transaction is responsible for updating all copies of an item, then it would appear that no update can take place without first obtaining a lock on ALL the copies. This requires a great deal of message overhead (three messages per replica), and would prevent doing an update if one site were down. Furthermore, deadlock could occur if two transactions were trying to lock the same item but started with different copies. (Each would be holding locks on some copies awaiting the others.) ii. These problems can be reduced by using a MAJORITY PROTOCOL. An updating transaction is only required to obtain locks on a majority of the replicas in order to proceed with the update. This cuts message traffic in half, allows updates even if one site is down, and reduces (but does not eliminate) the chance of deadlock. Note: in order for this to work correctly, a transaction that needs to read and then update an item must obtain an exclusive lock originally, rather than obtaining a shared lock which is subsequently upgraded to exclusive. iii. It is also possible to use a BIASED PROTOCOL for updates, whereby read-only operations are only required to lock one copy of an item, while update transactions must lock all copies. d. Many of the difficulties in updated replicated items can be reduced if the primary copy method of updating is used. In this case, we need only require the updating transaction to lock the primary copy of the item. C. Another issue that must be dealt with is the management of locks in conjunction with recovery. Any locks that were held by a transaction whose fate is in doubt during recovery must be held until the fate is determined - potentially resulting in an item being tied up for a long time. (The book discusses an alternative to two phase commit called three phase commit which addresses this issue.) 29
30 D. Because of the complexity of implementing locking in a distributed system, timestamp-based methods of concurrency control become an attractive alternative. 1. Some of the key ideas involved in adapting the timestamp algorithms for distributed use are discussed in the book. 2. One important point in any distributed scheme based on timestamps is ensuring consistency and uniqueness of timestamps across the system. a. Since each site generates its own timestamps, it is quite possible for two transactions originating at different sites to be given the same timestamp locally. To prevent this, we form a timestamp by concatenating two fields: the locally-generated timestamp and a unique site id, like this: [ locally-generated timestamp ] [ site id ] Note that the site id must become the low order part of the overall timestamp, so that it is significant only when resolving a situation where two transactions from different sites have the same locally-generated portion. b. We also want to ensure that if some transaction T1 receives a timestamp TS(T1) at some moment of time, some other transaction T2 does not receive a smaller timestamp at some later moment of time. i. This could theoretically be guaranteed if we used clocks to generate timestamps at each site, and if we ensured that the clocks were always synchronized. However, it is hard to ensure this in practice. 30
31 ii. The following is sufficient: if any site receives a request from a transaction originating elsewhere whose timestamp is greater than the current reading of its own timestamp clock, it must advance its timestamp clock to be one greater than the value of the timestamp of this transaction. iii. This latter method will work even if timestamps are generated by a local counter, rather than a local clock. VII. The CAP Theorem A. We noted at the outset that one advantage of a distributed system over a centralized system is the potential for improved availability of data (by replication). B. At the same time, we also noted that when data is replicated, consistency requires preventing a site from accessing an old version of a data item that is updated. But what if the network is partitioned at the time an update occurs? 1. If the primary copy method of ensuring consistency is used - i.e. a site that needs to be sure it has the latest copy of an item gets it from the primary site - and the network is partitioned in such a way that the site containing the primary copy is not accessible, then this works against availability. 2. The same sort of thing can happen with some sort of majority protocol, if the partitioning of the network makes it impossible to reach a majority of the replicas. C. An important theorem known as the CAP theorem says that you can design protocols to achieve any two of Consistency, Availability, and Partition Tolerance - but you can't have all three! Note that CAP defines Availability in a special way: "Every request received by a non-failing node in the system must result in a response" [ Lynch and Gilbert cited by Sandalage and Fowler ]. That is, if an update request is received by a node that ordinarily could fulfill it, but cannot because a network partition has made it impossible - then the data item is said to be non-available. 31
32 1. In a distributed system that uses something like the primary copy or majority protocol, a network partition could make some data unavailable at some nodes. 2. Availability could be preserved if we were willing to relax expectations regarding consistency. D. The practical ramification of this is to explore alternative DBMS structures in which relaxation of the ACID requirements leads to trading off strong consistency in favor of better availability. We explore this next in the context of NoSQL database models. An alternative to strict ACID consistency in such systems is sometimes called BASE - Basically Available, Soft State, Eventually Consistent. 32
Database Architectures
 Database Architectures CPS352: Database Systems Simon Miner Gordon College Last Revised: 11/15/12 Agenda Check-in Centralized and Client-Server Models Parallelism Distributed Databases Homework 6 Check-in
Database Architectures CPS352: Database Systems Simon Miner Gordon College Last Revised: 11/15/12 Agenda Check-in Centralized and Client-Server Models Parallelism Distributed Databases Homework 6 Check-in
Database Architectures
 Database Architectures CPS352: Database Systems Simon Miner Gordon College Last Revised: 4/15/15 Agenda Check-in Parallelism and Distributed Databases Technology Research Project Introduction to NoSQL
Database Architectures CPS352: Database Systems Simon Miner Gordon College Last Revised: 4/15/15 Agenda Check-in Parallelism and Distributed Databases Technology Research Project Introduction to NoSQL
Chapter 19: Distributed Databases
 Chapter 19: Distributed Databases Database System Concepts, 6 th Ed. See www.db-book.com for conditions on re-use Chapter 19: Distributed Databases Heterogeneous and Homogeneous Databases Distributed Data
Chapter 19: Distributed Databases Database System Concepts, 6 th Ed. See www.db-book.com for conditions on re-use Chapter 19: Distributed Databases Heterogeneous and Homogeneous Databases Distributed Data
Distributed KIDS Labs 1
 Distributed Databases @ KIDS Labs 1 Distributed Database System A distributed database system consists of loosely coupled sites that share no physical component Appears to user as a single system Database
Distributed Databases @ KIDS Labs 1 Distributed Database System A distributed database system consists of loosely coupled sites that share no physical component Appears to user as a single system Database
Mobile and Heterogeneous databases Distributed Database System Transaction Management. A.R. Hurson Computer Science Missouri Science & Technology
 Mobile and Heterogeneous databases Distributed Database System Transaction Management A.R. Hurson Computer Science Missouri Science & Technology 1 Distributed Database System Note, this unit will be covered
Mobile and Heterogeneous databases Distributed Database System Transaction Management A.R. Hurson Computer Science Missouri Science & Technology 1 Distributed Database System Note, this unit will be covered
Distributed Transaction Management. Distributed Database System
 Distributed Transaction Management Advanced Topics in Database Management (INFSCI 2711) Some materials are from Database Management Systems, Ramakrishnan and Gehrke and Database System Concepts, Siberschatz,
Distributed Transaction Management Advanced Topics in Database Management (INFSCI 2711) Some materials are from Database Management Systems, Ramakrishnan and Gehrke and Database System Concepts, Siberschatz,
Database Management Systems
 Database Management Systems Distributed Databases Doug Shook What does it mean to be distributed? Multiple nodes connected by a network Data on the nodes is logically related The nodes do not need to be
Database Management Systems Distributed Databases Doug Shook What does it mean to be distributed? Multiple nodes connected by a network Data on the nodes is logically related The nodes do not need to be
Distributed Databases
 Distributed Databases These slides are a modified version of the slides of the book Database System Concepts (Chapter 20 and 22), 5th Ed., McGraw-Hill, by Silberschatz, Korth and Sudarshan. Original slides
Distributed Databases These slides are a modified version of the slides of the book Database System Concepts (Chapter 20 and 22), 5th Ed., McGraw-Hill, by Silberschatz, Korth and Sudarshan. Original slides
CSE 544 Principles of Database Management Systems. Alvin Cheung Fall 2015 Lecture 14 Distributed Transactions
 CSE 544 Principles of Database Management Systems Alvin Cheung Fall 2015 Lecture 14 Distributed Transactions Transactions Main issues: Concurrency control Recovery from failures 2 Distributed Transactions
CSE 544 Principles of Database Management Systems Alvin Cheung Fall 2015 Lecture 14 Distributed Transactions Transactions Main issues: Concurrency control Recovery from failures 2 Distributed Transactions
Chapter 19: Distributed Databases
 Chapter 19: Distributed Databases Chapter 19: Distributed Databases Heterogeneous and Homogeneous Databases Distributed Data Storage Distributed Transactions Commit Protocols Concurrency Control in Distributed
Chapter 19: Distributed Databases Chapter 19: Distributed Databases Heterogeneous and Homogeneous Databases Distributed Data Storage Distributed Transactions Commit Protocols Concurrency Control in Distributed
Chapter 18: Parallel Databases
 Chapter 18: Parallel Databases Introduction Parallel machines are becoming quite common and affordable Prices of microprocessors, memory and disks have dropped sharply Recent desktop computers feature
Chapter 18: Parallel Databases Introduction Parallel machines are becoming quite common and affordable Prices of microprocessors, memory and disks have dropped sharply Recent desktop computers feature
Copyright 2007 Ramez Elmasri and Shamkant B. Navathe Slide 25-1
 Copyright 2007 Ramez Elmasri and Shamkant B. Navathe Slide 25-1 Chapter 25 Distributed Databases and Client-Server Architectures Copyright 2007 Ramez Elmasri and Shamkant B. Navathe Chapter 25 Outline
Copyright 2007 Ramez Elmasri and Shamkant B. Navathe Slide 25-1 Chapter 25 Distributed Databases and Client-Server Architectures Copyright 2007 Ramez Elmasri and Shamkant B. Navathe Chapter 25 Outline
Advanced Databases Lecture 17- Distributed Databases (continued)
 Advanced Databases Lecture 17- Distributed Databases (continued) Masood Niazi Torshiz Islamic Azad University- Mashhad Branch www.mniazi.ir Alternative Models of Transaction Processing Notion of a single
Advanced Databases Lecture 17- Distributed Databases (continued) Masood Niazi Torshiz Islamic Azad University- Mashhad Branch www.mniazi.ir Alternative Models of Transaction Processing Notion of a single
Distributed Databases
 C H A P T E R 1 9 Distributed Databases Unlike parallel systems, in which the processors are tightly coupled and constitute a single database system, a distributed database system consists of loosely coupled
C H A P T E R 1 9 Distributed Databases Unlike parallel systems, in which the processors are tightly coupled and constitute a single database system, a distributed database system consists of loosely coupled
CS352 Lecture - Concurrency
 CS352 Lecture - Concurrency Objectives: Last revised 3/21/17 1. To introduce locking as a means of preserving the serializability of concurrent schedules. 2. To briefly introduce other approaches to this
CS352 Lecture - Concurrency Objectives: Last revised 3/21/17 1. To introduce locking as a means of preserving the serializability of concurrent schedules. 2. To briefly introduce other approaches to this
Silberschatz and Galvin Chapter 18
 Silberschatz and Galvin Chapter 18 Distributed Coordination CPSC 410--Richard Furuta 4/21/99 1 Distributed Coordination Synchronization in a distributed environment Ð Event ordering Ð Mutual exclusion
Silberschatz and Galvin Chapter 18 Distributed Coordination CPSC 410--Richard Furuta 4/21/99 1 Distributed Coordination Synchronization in a distributed environment Ð Event ordering Ð Mutual exclusion
Distributed Databases
 Distributed Databases Chapter 22.6-22.14 Comp 521 Files and Databases Spring 2010 1 Final Exam When Monday, May 3, at 4pm Where, here FB007 What Open book, open notes, no computer 48-50 multiple choice
Distributed Databases Chapter 22.6-22.14 Comp 521 Files and Databases Spring 2010 1 Final Exam When Monday, May 3, at 4pm Where, here FB007 What Open book, open notes, no computer 48-50 multiple choice
CS352 Lecture - Concurrency
 CS352 Lecture - Concurrency Objectives: Last revised 11/16/06 1. To introduce locking as a means of preserving the serializability of concurrent schedules. 2. To briefly introduce other approaches to this
CS352 Lecture - Concurrency Objectives: Last revised 11/16/06 1. To introduce locking as a means of preserving the serializability of concurrent schedules. 2. To briefly introduce other approaches to this
11/7/2018. Event Ordering. Module 18: Distributed Coordination. Distributed Mutual Exclusion (DME) Implementation of. DME: Centralized Approach
 Module 18: Distributed Coordination Event Ordering Event Ordering Mutual Exclusion Atomicity Concurrency Control Deadlock Handling Election Algorithms Reaching Agreement Happened-before relation (denoted
Module 18: Distributed Coordination Event Ordering Event Ordering Mutual Exclusion Atomicity Concurrency Control Deadlock Handling Election Algorithms Reaching Agreement Happened-before relation (denoted
SCALABLE CONSISTENCY AND TRANSACTION MODELS
 Data Management in the Cloud SCALABLE CONSISTENCY AND TRANSACTION MODELS 69 Brewer s Conjecture Three properties that are desirable and expected from realworld shared-data systems C: data consistency A:
Data Management in the Cloud SCALABLE CONSISTENCY AND TRANSACTION MODELS 69 Brewer s Conjecture Three properties that are desirable and expected from realworld shared-data systems C: data consistency A:
CPS352 Lecture - The Transaction Concept
 Objectives: CPS352 Lecture - The Transaction Concept Last Revised March 3, 2017 1. To introduce the notion of a transaction and the ACID properties of a transaction 2. To introduce the notion of the state
Objectives: CPS352 Lecture - The Transaction Concept Last Revised March 3, 2017 1. To introduce the notion of a transaction and the ACID properties of a transaction 2. To introduce the notion of the state
Chapter 18: Parallel Databases Chapter 19: Distributed Databases ETC.
 Chapter 18: Parallel Databases Chapter 19: Distributed Databases ETC. Introduction Parallel machines are becoming quite common and affordable Prices of microprocessors, memory and disks have dropped sharply
Chapter 18: Parallel Databases Chapter 19: Distributed Databases ETC. Introduction Parallel machines are becoming quite common and affordable Prices of microprocessors, memory and disks have dropped sharply
Chapter 16: Distributed Synchronization
 Chapter 16: Distributed Synchronization Chapter 16 Distributed Synchronization Event Ordering Mutual Exclusion Atomicity Concurrency Control Deadlock Handling Election Algorithms Reaching Agreement 18.2
Chapter 16: Distributed Synchronization Chapter 16 Distributed Synchronization Event Ordering Mutual Exclusion Atomicity Concurrency Control Deadlock Handling Election Algorithms Reaching Agreement 18.2
Distributed Databases
 Distributed Databases Chapter 22, Part B Database Management Systems, 2 nd Edition. R. Ramakrishnan and Johannes Gehrke 1 Introduction Data is stored at several sites, each managed by a DBMS that can run
Distributed Databases Chapter 22, Part B Database Management Systems, 2 nd Edition. R. Ramakrishnan and Johannes Gehrke 1 Introduction Data is stored at several sites, each managed by a DBMS that can run
Chapter 18: Distributed
 Chapter 18: Distributed Synchronization, Silberschatz, Galvin and Gagne 2009 Chapter 18: Distributed Synchronization Event Ordering Mutual Exclusion Atomicity Concurrency Control Deadlock Handling Election
Chapter 18: Distributed Synchronization, Silberschatz, Galvin and Gagne 2009 Chapter 18: Distributed Synchronization Event Ordering Mutual Exclusion Atomicity Concurrency Control Deadlock Handling Election
Distributed Transaction Management 2003
 Distributed Transaction Management 2003 Jyrki Nummenmaa http://www.cs.uta.fi/~dtm jyrki@cs.uta.fi General information We will view this from the course web page. Motivation We will pick up some motivating
Distributed Transaction Management 2003 Jyrki Nummenmaa http://www.cs.uta.fi/~dtm jyrki@cs.uta.fi General information We will view this from the course web page. Motivation We will pick up some motivating
Databases - Transactions
 Databases - Transactions Gordon Royle School of Mathematics & Statistics University of Western Australia Gordon Royle (UWA) Transactions 1 / 34 ACID ACID is the one acronym universally associated with
Databases - Transactions Gordon Royle School of Mathematics & Statistics University of Western Australia Gordon Royle (UWA) Transactions 1 / 34 ACID ACID is the one acronym universally associated with
CS352 Lecture - The Transaction Concept
 CS352 Lecture - The Transaction Concept Last Revised 11/7/06 Objectives: 1. To introduce the notion of a transaction and the ACID properties of a transaction 2. To introduce the notion of the state of
CS352 Lecture - The Transaction Concept Last Revised 11/7/06 Objectives: 1. To introduce the notion of a transaction and the ACID properties of a transaction 2. To introduce the notion of the state of
NoSQL systems: sharding, replication and consistency. Riccardo Torlone Università Roma Tre
 NoSQL systems: sharding, replication and consistency Riccardo Torlone Università Roma Tre Data distribution NoSQL systems: data distributed over large clusters Aggregate is a natural unit to use for data
NoSQL systems: sharding, replication and consistency Riccardo Torlone Università Roma Tre Data distribution NoSQL systems: data distributed over large clusters Aggregate is a natural unit to use for data
Distributed Databases
 Distributed Databases Chapter 21, Part B Database Management Systems, 2 nd Edition. R. Ramakrishnan and Johannes Gehrke 1 Introduction Data is stored at several sites, each managed by a DBMS that can run
Distributed Databases Chapter 21, Part B Database Management Systems, 2 nd Edition. R. Ramakrishnan and Johannes Gehrke 1 Introduction Data is stored at several sites, each managed by a DBMS that can run
Incompatibility Dimensions and Integration of Atomic Commit Protocols
 The International Arab Journal of Information Technology, Vol. 5, No. 4, October 2008 381 Incompatibility Dimensions and Integration of Atomic Commit Protocols Yousef Al-Houmaily Department of Computer
The International Arab Journal of Information Technology, Vol. 5, No. 4, October 2008 381 Incompatibility Dimensions and Integration of Atomic Commit Protocols Yousef Al-Houmaily Department of Computer
Outline. Non-Standard Database Systems. Distributed Database System. Outline. Distributed Databases
 Non-Standard Database Systems Distributed Databases Nikolaus Augsten nikolaus.augsten@sbg.ac.at Department of Computer Sciences University of Salzburg http://dbresearch.uni-salzburg.at SS 2017/18 Version
Non-Standard Database Systems Distributed Databases Nikolaus Augsten nikolaus.augsten@sbg.ac.at Department of Computer Sciences University of Salzburg http://dbresearch.uni-salzburg.at SS 2017/18 Version
Distributed Databases Systems
 Distributed Databases Systems Lecture No. 01 Distributed Database Systems Naeem Ahmed Email: naeemmahoto@gmail.com Department of Software Engineering Mehran Univeristy of Engineering and Technology Jamshoro
Distributed Databases Systems Lecture No. 01 Distributed Database Systems Naeem Ahmed Email: naeemmahoto@gmail.com Department of Software Engineering Mehran Univeristy of Engineering and Technology Jamshoro
DB2 Lecture 10 Concurrency Control
 DB2 Lecture 10 Control Jacob Aae Mikkelsen November 28, 2012 1 / 71 Jacob Aae Mikkelsen DB2 Lecture 10 Control ACID Properties Properly implemented transactions are commonly said to meet the ACID test,
DB2 Lecture 10 Control Jacob Aae Mikkelsen November 28, 2012 1 / 71 Jacob Aae Mikkelsen DB2 Lecture 10 Control ACID Properties Properly implemented transactions are commonly said to meet the ACID test,
CPS352 Lecture: Database System Architectures last revised 3/27/2017
 CPS352 Lecture: Database System Architectures last revised 3/27/2017 I. Introduction - ------------ A. Most large databases require support for accesing the database by multiple users, often at multiple
CPS352 Lecture: Database System Architectures last revised 3/27/2017 I. Introduction - ------------ A. Most large databases require support for accesing the database by multiple users, often at multiple
CMU SCS CMU SCS Who: What: When: Where: Why: CMU SCS
 Carnegie Mellon Univ. Dept. of Computer Science 15-415/615 - DB s C. Faloutsos A. Pavlo Lecture#23: Distributed Database Systems (R&G ch. 22) Administrivia Final Exam Who: You What: R&G Chapters 15-22
Carnegie Mellon Univ. Dept. of Computer Science 15-415/615 - DB s C. Faloutsos A. Pavlo Lecture#23: Distributed Database Systems (R&G ch. 22) Administrivia Final Exam Who: You What: R&G Chapters 15-22
Data Modeling and Databases Ch 14: Data Replication. Gustavo Alonso, Ce Zhang Systems Group Department of Computer Science ETH Zürich
 Data Modeling and Databases Ch 14: Data Replication Gustavo Alonso, Ce Zhang Systems Group Department of Computer Science ETH Zürich Database Replication What is database replication The advantages of
Data Modeling and Databases Ch 14: Data Replication Gustavo Alonso, Ce Zhang Systems Group Department of Computer Science ETH Zürich Database Replication What is database replication The advantages of
It also performs many parallelization operations like, data loading and query processing.
 Introduction to Parallel Databases Companies need to handle huge amount of data with high data transfer rate. The client server and centralized system is not much efficient. The need to improve the efficiency
Introduction to Parallel Databases Companies need to handle huge amount of data with high data transfer rate. The client server and centralized system is not much efficient. The need to improve the efficiency
Control. CS432: Distributed Systems Spring 2017
 Transactions and Concurrency Control Reading Chapter 16, 17 (17.2,17.4,17.5 ) [Coulouris 11] Chapter 12 [Ozsu 10] 2 Objectives Learn about the following: Transactions in distributed systems Techniques
Transactions and Concurrency Control Reading Chapter 16, 17 (17.2,17.4,17.5 ) [Coulouris 11] Chapter 12 [Ozsu 10] 2 Objectives Learn about the following: Transactions in distributed systems Techniques
Distributed Consensus Protocols
 Distributed Consensus Protocols ABSTRACT In this paper, I compare Paxos, the most popular and influential of distributed consensus protocols, and Raft, a fairly new protocol that is considered to be a
Distributed Consensus Protocols ABSTRACT In this paper, I compare Paxos, the most popular and influential of distributed consensus protocols, and Raft, a fairly new protocol that is considered to be a
Chapter 11 - Data Replication Middleware
 Prof. Dr.-Ing. Stefan Deßloch AG Heterogene Informationssysteme Geb. 36, Raum 329 Tel. 0631/205 3275 dessloch@informatik.uni-kl.de Chapter 11 - Data Replication Middleware Motivation Replication: controlled
Prof. Dr.-Ing. Stefan Deßloch AG Heterogene Informationssysteme Geb. 36, Raum 329 Tel. 0631/205 3275 dessloch@informatik.uni-kl.de Chapter 11 - Data Replication Middleware Motivation Replication: controlled
Chapter 2. DB2 concepts
 4960ch02qxd 10/6/2000 7:20 AM Page 37 DB2 concepts Chapter 2 Structured query language 38 DB2 data structures 40 Enforcing business rules 49 DB2 system structures 52 Application processes and transactions
4960ch02qxd 10/6/2000 7:20 AM Page 37 DB2 concepts Chapter 2 Structured query language 38 DB2 data structures 40 Enforcing business rules 49 DB2 system structures 52 Application processes and transactions
CISC 7610 Lecture 5 Distributed multimedia databases. Topics: Scaling up vs out Replication Partitioning CAP Theorem NoSQL NewSQL
 CISC 7610 Lecture 5 Distributed multimedia databases Topics: Scaling up vs out Replication Partitioning CAP Theorem NoSQL NewSQL Motivation YouTube receives 400 hours of video per minute That is 200M hours
CISC 7610 Lecture 5 Distributed multimedia databases Topics: Scaling up vs out Replication Partitioning CAP Theorem NoSQL NewSQL Motivation YouTube receives 400 hours of video per minute That is 200M hours
 A can be implemented as a separate process to which transactions send lock and unlock requests The lock manager replies to a lock request by sending a lock grant messages (or a message asking the transaction
A can be implemented as a separate process to which transactions send lock and unlock requests The lock manager replies to a lock request by sending a lock grant messages (or a message asking the transaction
Integrity in Distributed Databases
 Integrity in Distributed Databases Andreas Farella Free University of Bozen-Bolzano Table of Contents 1 Introduction................................................... 3 2 Different aspects of integrity.....................................
Integrity in Distributed Databases Andreas Farella Free University of Bozen-Bolzano Table of Contents 1 Introduction................................................... 3 2 Different aspects of integrity.....................................
DHANALAKSHMI COLLEGE OF ENGINEERING, CHENNAI
 DHANALAKSHMI COLLEGE OF ENGINEERING, CHENNAI Department of Computer Science and Engineering CS6302- DATABASE MANAGEMENT SYSTEMS Anna University 2 & 16 Mark Questions & Answers Year / Semester: II / III
DHANALAKSHMI COLLEGE OF ENGINEERING, CHENNAI Department of Computer Science and Engineering CS6302- DATABASE MANAGEMENT SYSTEMS Anna University 2 & 16 Mark Questions & Answers Year / Semester: II / III
Distributed Commit in Asynchronous Systems
 Distributed Commit in Asynchronous Systems Minsoo Ryu Department of Computer Science and Engineering 2 Distributed Commit Problem - Either everybody commits a transaction, or nobody - This means consensus!
Distributed Commit in Asynchronous Systems Minsoo Ryu Department of Computer Science and Engineering 2 Distributed Commit Problem - Either everybody commits a transaction, or nobody - This means consensus!
A transaction is a sequence of one or more processing steps. It refers to database objects such as tables, views, joins and so forth.
 1 2 A transaction is a sequence of one or more processing steps. It refers to database objects such as tables, views, joins and so forth. Here, the following properties must be fulfilled: Indivisibility
1 2 A transaction is a sequence of one or more processing steps. It refers to database objects such as tables, views, joins and so forth. Here, the following properties must be fulfilled: Indivisibility
Fault Tolerance. Distributed Systems IT332
 Fault Tolerance Distributed Systems IT332 2 Outline Introduction to fault tolerance Reliable Client Server Communication Distributed commit Failure recovery 3 Failures, Due to What? A system is said to
Fault Tolerance Distributed Systems IT332 2 Outline Introduction to fault tolerance Reliable Client Server Communication Distributed commit Failure recovery 3 Failures, Due to What? A system is said to
Advances in Data Management - NoSQL, NewSQL and Big Data A.Poulovassilis
 Advances in Data Management - NoSQL, NewSQL and Big Data A.Poulovassilis 1 NoSQL So-called NoSQL systems offer reduced functionalities compared to traditional Relational DBMSs, with the aim of achieving
Advances in Data Management - NoSQL, NewSQL and Big Data A.Poulovassilis 1 NoSQL So-called NoSQL systems offer reduced functionalities compared to traditional Relational DBMSs, with the aim of achieving
Report to Brewer s original presentation of his CAP Theorem at the Symposium on Principles of Distributed Computing (PODC) 2000
 Brewer s CAP Theorem Report to Brewer s original presentation of his CAP Theorem at the Symposium on Principles of Distributed Computing (PODC) 2000 Written by Table of Contents Introduction... 2 The CAP-Theorem...
Brewer s CAP Theorem Report to Brewer s original presentation of his CAP Theorem at the Symposium on Principles of Distributed Computing (PODC) 2000 Written by Table of Contents Introduction... 2 The CAP-Theorem...
CS October 2017
 Atomic Transactions Transaction An operation composed of a number of discrete steps. Distributed Systems 11. Distributed Commit Protocols All the steps must be completed for the transaction to be committed.
Atomic Transactions Transaction An operation composed of a number of discrete steps. Distributed Systems 11. Distributed Commit Protocols All the steps must be completed for the transaction to be committed.
DISTRIBUTED DATABASES CS561-SPRING 2012 WPI, MOHAMED ELTABAKH
 DISTRIBUTED DATABASES CS561-SPRING 2012 WPI, MOHAMED ELTABAKH 1 RECAP: PARALLEL DATABASES Three possible architectures Shared-memory Shared-disk Shared-nothing (the most common one) Parallel algorithms
DISTRIBUTED DATABASES CS561-SPRING 2012 WPI, MOHAMED ELTABAKH 1 RECAP: PARALLEL DATABASES Three possible architectures Shared-memory Shared-disk Shared-nothing (the most common one) Parallel algorithms
Introduces the RULES AND PRINCIPLES of DBMS operation.
 3 rd September 2015 Unit 1 Objective Introduces the RULES AND PRINCIPLES of DBMS operation. Learning outcome Students will be able to apply the rules governing the use of DBMS in their day-to-day interaction
3 rd September 2015 Unit 1 Objective Introduces the RULES AND PRINCIPLES of DBMS operation. Learning outcome Students will be able to apply the rules governing the use of DBMS in their day-to-day interaction
CSC 261/461 Database Systems Lecture 24
 CSC 261/461 Database Systems Lecture 24 Fall 2017 TRANSACTIONS Announcement Poster: You should have sent us the poster by yesterday. If you have not done so, please send us asap. Make sure to send it for
CSC 261/461 Database Systems Lecture 24 Fall 2017 TRANSACTIONS Announcement Poster: You should have sent us the poster by yesterday. If you have not done so, please send us asap. Make sure to send it for
Distributed Database Management System UNIT-2. Concurrency Control. Transaction ACID rules. MCA 325, Distributed DBMS And Object Oriented Databases
 Distributed Database Management System UNIT-2 Bharati Vidyapeeth s Institute of Computer Applications and Management, New Delhi-63,By Shivendra Goel. U2.1 Concurrency Control Concurrency control is a method
Distributed Database Management System UNIT-2 Bharati Vidyapeeth s Institute of Computer Applications and Management, New Delhi-63,By Shivendra Goel. U2.1 Concurrency Control Concurrency control is a method
The Replication Technology in E-learning Systems
 Available online at www.sciencedirect.com Procedia - Social and Behavioral Sciences 28 (2011) 231 235 WCETR 2011 The Replication Technology in E-learning Systems Iacob (Ciobanu) Nicoleta Magdalena a *
Available online at www.sciencedirect.com Procedia - Social and Behavioral Sciences 28 (2011) 231 235 WCETR 2011 The Replication Technology in E-learning Systems Iacob (Ciobanu) Nicoleta Magdalena a *
Commit Protocols and their Issues in Distributed Databases
 Proceedings of the 4 th National Conference; INDIACom-2010 Computing For Nation Development, February 25 26, 2010 Bharati Vidyapeeth s Institute of Computer Applications and Management, New Delhi Commit
Proceedings of the 4 th National Conference; INDIACom-2010 Computing For Nation Development, February 25 26, 2010 Bharati Vidyapeeth s Institute of Computer Applications and Management, New Delhi Commit
Intro to Transactions
 Reading Material CompSci 516 Database Systems Lecture 14 Intro to Transactions [RG] Chapter 16.1-16.3, 16.4.1 17.1-17.4 17.5.1, 17.5.3 Instructor: Sudeepa Roy Acknowledgement: The following slides have
Reading Material CompSci 516 Database Systems Lecture 14 Intro to Transactions [RG] Chapter 16.1-16.3, 16.4.1 17.1-17.4 17.5.1, 17.5.3 Instructor: Sudeepa Roy Acknowledgement: The following slides have
DATABASE TRANSACTIONS. CS121: Relational Databases Fall 2017 Lecture 25
 DATABASE TRANSACTIONS CS121: Relational Databases Fall 2017 Lecture 25 Database Transactions 2 Many situations where a sequence of database operations must be treated as a single unit A combination of
DATABASE TRANSACTIONS CS121: Relational Databases Fall 2017 Lecture 25 Database Transactions 2 Many situations where a sequence of database operations must be treated as a single unit A combination of
CS5412: TRANSACTIONS (I)
 1 CS5412: TRANSACTIONS (I) Lecture XVII Ken Birman Transactions 2 A widely used reliability technology, despite the BASE methodology we use in the first tier Goal for this week: in-depth examination of
1 CS5412: TRANSACTIONS (I) Lecture XVII Ken Birman Transactions 2 A widely used reliability technology, despite the BASE methodology we use in the first tier Goal for this week: in-depth examination of
CS352 Lecture: Database System Architectures last revised 11/22/06
 CS352 Lecture: Database System Architectures last revised 11/22/06 I. Introduction - ------------ A. Most large databases require support for accesing the database by multiple users, often at multiple
CS352 Lecture: Database System Architectures last revised 11/22/06 I. Introduction - ------------ A. Most large databases require support for accesing the database by multiple users, often at multiple
CISC 7610 Lecture 2b The beginnings of NoSQL
 CISC 7610 Lecture 2b The beginnings of NoSQL Topics: Big Data Google s infrastructure Hadoop: open google infrastructure Scaling through sharding CAP theorem Amazon s Dynamo 5 V s of big data Everyone
CISC 7610 Lecture 2b The beginnings of NoSQL Topics: Big Data Google s infrastructure Hadoop: open google infrastructure Scaling through sharding CAP theorem Amazon s Dynamo 5 V s of big data Everyone
ATOMIC COMMITMENT Or: How to Implement Distributed Transactions in Sharded Databases
 ATOMIC COMMITMENT Or: How to Implement Distributed Transactions in Sharded Databases We talked about transactions and how to implement them in a single-node database. We ll now start looking into how to
ATOMIC COMMITMENT Or: How to Implement Distributed Transactions in Sharded Databases We talked about transactions and how to implement them in a single-node database. We ll now start looking into how to
Fundamental Research of Distributed Database
 International Journal of Computer Science and Management Studies, Vol. 11, Issue 02, Aug 2011 138 Fundamental Research of Distributed Database Swati Gupta 1, Kuntal Saroha 2, Bhawna 3 1 Lecturer, RIMT,
International Journal of Computer Science and Management Studies, Vol. 11, Issue 02, Aug 2011 138 Fundamental Research of Distributed Database Swati Gupta 1, Kuntal Saroha 2, Bhawna 3 1 Lecturer, RIMT,
Unit 9 Transaction Processing: Recovery Zvi M. Kedem 1
 Unit 9 Transaction Processing: Recovery 2013 Zvi M. Kedem 1 Recovery in Context User%Level (View%Level) Community%Level (Base%Level) Physical%Level DBMS%OS%Level Centralized Or Distributed Derived%Tables
Unit 9 Transaction Processing: Recovery 2013 Zvi M. Kedem 1 Recovery in Context User%Level (View%Level) Community%Level (Base%Level) Physical%Level DBMS%OS%Level Centralized Or Distributed Derived%Tables
Essay Question: Explain 4 different means by which constrains are represented in the Conceptual Data Model (CDM).
 Question 1 Essay Question: Explain 4 different means by which constrains are represented in the Conceptual Data Model (CDM). By specifying participation conditions By specifying the degree of relationship
Question 1 Essay Question: Explain 4 different means by which constrains are represented in the Conceptual Data Model (CDM). By specifying participation conditions By specifying the degree of relationship
Incompatibility Dimensions and Integration of Atomic Commit Protocols
 Preprint Incompatibility Dimensions and Integration of Atomic Protocols, Yousef J. Al-Houmaily, International Arab Journal of Information Technology, Vol. 5, No. 4, pp. 381-392, October 2008. Incompatibility
Preprint Incompatibility Dimensions and Integration of Atomic Protocols, Yousef J. Al-Houmaily, International Arab Journal of Information Technology, Vol. 5, No. 4, pp. 381-392, October 2008. Incompatibility
Consistency in Distributed Systems
 Consistency in Distributed Systems Recall the fundamental DS properties DS may be large in scale and widely distributed 1. concurrent execution of components 2. independent failure modes 3. transmission
Consistency in Distributed Systems Recall the fundamental DS properties DS may be large in scale and widely distributed 1. concurrent execution of components 2. independent failure modes 3. transmission
Distributed systems. Lecture 6: distributed transactions, elections, consensus and replication. Malte Schwarzkopf
 Distributed systems Lecture 6: distributed transactions, elections, consensus and replication Malte Schwarzkopf Last time Saw how we can build ordered multicast Messages between processes in a group Need
Distributed systems Lecture 6: distributed transactions, elections, consensus and replication Malte Schwarzkopf Last time Saw how we can build ordered multicast Messages between processes in a group Need
Synchronization. Chapter 5
 Synchronization Chapter 5 Clock Synchronization In a centralized system time is unambiguous. (each computer has its own clock) In a distributed system achieving agreement on time is not trivial. (it is
Synchronization Chapter 5 Clock Synchronization In a centralized system time is unambiguous. (each computer has its own clock) In a distributed system achieving agreement on time is not trivial. (it is
Topics in Reliable Distributed Systems
 Topics in Reliable Distributed Systems 049017 1 T R A N S A C T I O N S Y S T E M S What is A Database? Organized collection of data typically persistent organization models: relational, object-based,
Topics in Reliable Distributed Systems 049017 1 T R A N S A C T I O N S Y S T E M S What is A Database? Organized collection of data typically persistent organization models: relational, object-based,
Relational Database Management Systems Oct/Nov I. Section-A: 5 X 4 =20 Marks
 Relational Database Management Systems Oct/Nov 2013 1 I. Section-A: 5 X 4 =20 Marks 1. Database Development DDLC (Database Development Life Cycle): It is a process for designing, implementing and maintaining
Relational Database Management Systems Oct/Nov 2013 1 I. Section-A: 5 X 4 =20 Marks 1. Database Development DDLC (Database Development Life Cycle): It is a process for designing, implementing and maintaining
Chapter 18: Database System Architectures.! Centralized Systems! Client--Server Systems! Parallel Systems! Distributed Systems!
 Chapter 18: Database System Architectures! Centralized Systems! Client--Server Systems! Parallel Systems! Distributed Systems! Network Types 18.1 Centralized Systems! Run on a single computer system and
Chapter 18: Database System Architectures! Centralized Systems! Client--Server Systems! Parallel Systems! Distributed Systems! Network Types 18.1 Centralized Systems! Run on a single computer system and
Database Management System Prof. D. Janakiram Department of Computer Science & Engineering Indian Institute of Technology, Madras Lecture No.
 Database Management System Prof. D. Janakiram Department of Computer Science & Engineering Indian Institute of Technology, Madras Lecture No. # 20 Concurrency Control Part -1 Foundations for concurrency
Database Management System Prof. D. Janakiram Department of Computer Science & Engineering Indian Institute of Technology, Madras Lecture No. # 20 Concurrency Control Part -1 Foundations for concurrency
CAP Theorem. March 26, Thanks to Arvind K., Dong W., and Mihir N. for slides.
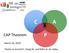 C A CAP Theorem P March 26, 2018 Thanks to Arvind K., Dong W., and Mihir N. for slides. CAP Theorem It is impossible for a web service to provide these three guarantees at the same time (pick 2 of 3):
C A CAP Theorem P March 26, 2018 Thanks to Arvind K., Dong W., and Mihir N. for slides. CAP Theorem It is impossible for a web service to provide these three guarantees at the same time (pick 2 of 3):
Final Exam Review 2. Kathleen Durant CS 3200 Northeastern University Lecture 23
 Final Exam Review 2 Kathleen Durant CS 3200 Northeastern University Lecture 23 QUERY EVALUATION PLAN Representation of a SQL Command SELECT {DISTINCT} FROM {WHERE
Final Exam Review 2 Kathleen Durant CS 3200 Northeastern University Lecture 23 QUERY EVALUATION PLAN Representation of a SQL Command SELECT {DISTINCT} FROM {WHERE
Chapter 17: Recovery System
 Chapter 17: Recovery System Database System Concepts See www.db-book.com for conditions on re-use Chapter 17: Recovery System Failure Classification Storage Structure Recovery and Atomicity Log-Based Recovery
Chapter 17: Recovery System Database System Concepts See www.db-book.com for conditions on re-use Chapter 17: Recovery System Failure Classification Storage Structure Recovery and Atomicity Log-Based Recovery
CSC 261/461 Database Systems Lecture 21 and 22. Spring 2017 MW 3:25 pm 4:40 pm January 18 May 3 Dewey 1101
 CSC 261/461 Database Systems Lecture 21 and 22 Spring 2017 MW 3:25 pm 4:40 pm January 18 May 3 Dewey 1101 Announcements Project 3 (MongoDB): Due on: 04/12 Work on Term Project and Project 1 The last (mini)
CSC 261/461 Database Systems Lecture 21 and 22 Spring 2017 MW 3:25 pm 4:40 pm January 18 May 3 Dewey 1101 Announcements Project 3 (MongoDB): Due on: 04/12 Work on Term Project and Project 1 The last (mini)
Chapter 17: Recovery System
 Chapter 17: Recovery System! Failure Classification! Storage Structure! Recovery and Atomicity! Log-Based Recovery! Shadow Paging! Recovery With Concurrent Transactions! Buffer Management! Failure with
Chapter 17: Recovery System! Failure Classification! Storage Structure! Recovery and Atomicity! Log-Based Recovery! Shadow Paging! Recovery With Concurrent Transactions! Buffer Management! Failure with
Failure Classification. Chapter 17: Recovery System. Recovery Algorithms. Storage Structure
 Chapter 17: Recovery System Failure Classification! Failure Classification! Storage Structure! Recovery and Atomicity! Log-Based Recovery! Shadow Paging! Recovery With Concurrent Transactions! Buffer Management!
Chapter 17: Recovery System Failure Classification! Failure Classification! Storage Structure! Recovery and Atomicity! Log-Based Recovery! Shadow Paging! Recovery With Concurrent Transactions! Buffer Management!
Exam 2 Review. October 29, Paul Krzyzanowski 1
 Exam 2 Review October 29, 2015 2013 Paul Krzyzanowski 1 Question 1 Why did Dropbox add notification servers to their architecture? To avoid the overhead of clients polling the servers periodically to check
Exam 2 Review October 29, 2015 2013 Paul Krzyzanowski 1 Question 1 Why did Dropbox add notification servers to their architecture? To avoid the overhead of clients polling the servers periodically to check
Distributed DBMS. Concepts. Concepts. Distributed DBMS. Concepts. Concepts 9/8/2014
 Distributed DBMS Advantages and disadvantages of distributed databases. Functions of DDBMS. Distributed database design. Distributed Database A logically interrelated collection of shared data (and a description
Distributed DBMS Advantages and disadvantages of distributed databases. Functions of DDBMS. Distributed database design. Distributed Database A logically interrelated collection of shared data (and a description
Database management system Prof. D. Janakiram Department of Computer Science and Engineering Indian Institute of Technology, Madras
 Database management system Prof. D. Janakiram Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 25 Basic 2-phase & 3-phase Commit protocol In the last lecture,
Database management system Prof. D. Janakiram Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 25 Basic 2-phase & 3-phase Commit protocol In the last lecture,
Consistency and Scalability
 COMP 150-IDS: Internet Scale Distributed Systems (Spring 2015) Consistency and Scalability Noah Mendelsohn Tufts University Email: noah@cs.tufts.edu Web: http://www.cs.tufts.edu/~noah Copyright 2015 Noah
COMP 150-IDS: Internet Scale Distributed Systems (Spring 2015) Consistency and Scalability Noah Mendelsohn Tufts University Email: noah@cs.tufts.edu Web: http://www.cs.tufts.edu/~noah Copyright 2015 Noah
Last time. Distributed systems Lecture 6: Elections, distributed transactions, and replication. DrRobert N. M. Watson
 Distributed systems Lecture 6: Elections, distributed transactions, and replication DrRobert N. M. Watson 1 Last time Saw how we can build ordered multicast Messages between processes in a group Need to
Distributed systems Lecture 6: Elections, distributed transactions, and replication DrRobert N. M. Watson 1 Last time Saw how we can build ordered multicast Messages between processes in a group Need to
Introduction Aggregate data model Distribution Models Consistency Map-Reduce Types of NoSQL Databases
 Introduction Aggregate data model Distribution Models Consistency Map-Reduce Types of NoSQL Databases Key-Value Document Column Family Graph John Edgar 2 Relational databases are the prevalent solution
Introduction Aggregate data model Distribution Models Consistency Map-Reduce Types of NoSQL Databases Key-Value Document Column Family Graph John Edgar 2 Relational databases are the prevalent solution
Scaling Database Systems. COSC 404 Database System Implementation Scaling Databases Distribution, Parallelism, Virtualization
 COSC 404 Database System Implementation Scaling Databases Distribution, Parallelism, Virtualization Dr. Ramon Lawrence University of British Columbia Okanagan ramon.lawrence@ubc.ca Scaling Database Systems
COSC 404 Database System Implementation Scaling Databases Distribution, Parallelism, Virtualization Dr. Ramon Lawrence University of British Columbia Okanagan ramon.lawrence@ubc.ca Scaling Database Systems
Lectures 8 & 9. Lectures 7 & 8: Transactions
 Lectures 8 & 9 Lectures 7 & 8: Transactions Lectures 7 & 8 Goals for this pair of lectures Transactions are a programming abstraction that enables the DBMS to handle recoveryand concurrency for users.
Lectures 8 & 9 Lectures 7 & 8: Transactions Lectures 7 & 8 Goals for this pair of lectures Transactions are a programming abstraction that enables the DBMS to handle recoveryand concurrency for users.
Transactions and Concurrency Control
 Transactions and Concurrency Control Transaction: a unit of program execution that accesses and possibly updates some data items. A transaction is a collection of operations that logically form a single
Transactions and Concurrency Control Transaction: a unit of program execution that accesses and possibly updates some data items. A transaction is a collection of operations that logically form a single
System Models. 2.1 Introduction 2.2 Architectural Models 2.3 Fundamental Models. Nicola Dragoni Embedded Systems Engineering DTU Informatics
 System Models Nicola Dragoni Embedded Systems Engineering DTU Informatics 2.1 Introduction 2.2 Architectural Models 2.3 Fundamental Models Architectural vs Fundamental Models Systems that are intended
System Models Nicola Dragoni Embedded Systems Engineering DTU Informatics 2.1 Introduction 2.2 Architectural Models 2.3 Fundamental Models Architectural vs Fundamental Models Systems that are intended
Database Management System Prof. D. Janakiram Department of Computer Science & Engineering Indian Institute of Technology, Madras Lecture No.
 Database Management System Prof. D. Janakiram Department of Computer Science & Engineering Indian Institute of Technology, Madras Lecture No. # 18 Transaction Processing and Database Manager In the previous
Database Management System Prof. D. Janakiram Department of Computer Science & Engineering Indian Institute of Technology, Madras Lecture No. # 18 Transaction Processing and Database Manager In the previous
Introduction to Databases, Fall 2005 IT University of Copenhagen. Lecture 10: Transaction processing. November 14, Lecturer: Rasmus Pagh
 Introduction to Databases, Fall 2005 IT University of Copenhagen Lecture 10: Transaction processing November 14, 2005 Lecturer: Rasmus Pagh Today s lecture Part I: Transaction processing Serializability
Introduction to Databases, Fall 2005 IT University of Copenhagen Lecture 10: Transaction processing November 14, 2005 Lecturer: Rasmus Pagh Today s lecture Part I: Transaction processing Serializability
Synchronization. Clock Synchronization
 Synchronization Clock Synchronization Logical clocks Global state Election algorithms Mutual exclusion Distributed transactions 1 Clock Synchronization Time is counted based on tick Time judged by query
Synchronization Clock Synchronization Logical clocks Global state Election algorithms Mutual exclusion Distributed transactions 1 Clock Synchronization Time is counted based on tick Time judged by query
Global atomicity. Such distributed atomicity is called global atomicity A protocol designed to enforce global atomicity is called commit protocol
 Global atomicity In distributed systems a set of processes may be taking part in executing a task Their actions may have to be atomic with respect to processes outside of the set example: in a distributed
Global atomicity In distributed systems a set of processes may be taking part in executing a task Their actions may have to be atomic with respect to processes outside of the set example: in a distributed
Dynamo: Key-Value Cloud Storage
 Dynamo: Key-Value Cloud Storage Brad Karp UCL Computer Science CS M038 / GZ06 22 nd February 2016 Context: P2P vs. Data Center (key, value) Storage Chord and DHash intended for wide-area peer-to-peer systems
Dynamo: Key-Value Cloud Storage Brad Karp UCL Computer Science CS M038 / GZ06 22 nd February 2016 Context: P2P vs. Data Center (key, value) Storage Chord and DHash intended for wide-area peer-to-peer systems
Security Mechanisms I. Key Slide. Key Slide. Security Mechanisms III. Security Mechanisms II
 Database Facilities One of the main benefits from centralising the implementation data model of a DBMS is that a number of critical facilities can be programmed once against this model and thus be available
Database Facilities One of the main benefits from centralising the implementation data model of a DBMS is that a number of critical facilities can be programmed once against this model and thus be available
DHCP Failover: An Improved Approach to DHCP Redundancy
 Overview The DHCP Failover protocol specification and ISC s implementation of the protocol have problems that can cause issues in production environments, primarily in those environments where configurations
Overview The DHCP Failover protocol specification and ISC s implementation of the protocol have problems that can cause issues in production environments, primarily in those environments where configurations
Course Content. Parallel & Distributed Databases. Objectives of Lecture 12 Parallel and Distributed Databases
 Database Management Systems Winter 2003 CMPUT 391: Dr. Osmar R. Zaïane University of Alberta Chapter 22 of Textbook Course Content Introduction Database Design Theory Query Processing and Optimisation
Database Management Systems Winter 2003 CMPUT 391: Dr. Osmar R. Zaïane University of Alberta Chapter 22 of Textbook Course Content Introduction Database Design Theory Query Processing and Optimisation
Distributed Systems. Characteristics of Distributed Systems. Lecture Notes 1 Basic Concepts. Operating Systems. Anand Tripathi
 1 Lecture Notes 1 Basic Concepts Anand Tripathi CSci 8980 Operating Systems Anand Tripathi CSci 8980 1 Distributed Systems A set of computers (hosts or nodes) connected through a communication network.
1 Lecture Notes 1 Basic Concepts Anand Tripathi CSci 8980 Operating Systems Anand Tripathi CSci 8980 1 Distributed Systems A set of computers (hosts or nodes) connected through a communication network.
