(12) United States Patent (10) Patent No.: US 7,673,003 B2
|
|
|
- Sharleen Walsh
- 5 years ago
- Views:
Transcription
1 USOO B2 (12) United States Patent (10) Patent No.: US 7,673,003 B2 Little, II (45) Date of Patent: Mar. 2, 2010 (54) SOCIAL NETWORK FILTERING 2006/ A1* 2/2006 Libbey et al.... TO9, / A1* 8, 2006 Kohavi TO9,226 (75) Inventor: Charles Reeves Little, II, San Jose, CA 2006/ A1* 11/2006 Pannu et al.... T26.1 (US) 2007, A1* 8, 2007 Stern et al , / A1* 11/2007 Roskind /15 (73) Assignee: Msion Corporation, Redmond, WA FOREIGN PATENT DOCUMENTS WO WO9937O66 7, 1999 (*) Notice: Subject to any disclaimer, the term of this WO WO , 2004 patent is extended or adjusted under 35 U.S.C. 154(b) by 1476 days. OTHER PUBLICATIONS Seairth et al. It Takes a Village to Stop Spam, Feb. 5, 2004, retrived (21) Appl. No.: 10/835,373 on Oct. 1, p Asami, et al; "A Taxonomy of Spam and a Protection Method for (22) Filed: Apr. 28, 2004 Enterprise Networks ; ICOIN 2002, LNCS 2344; pp Blankenhorn; " audits clean lists, imporve response rates'; 3 (65) Prior Publication Data pages; B to B; vol. 87, No. 6, Jun. 10, US 2005/O24642O A1 Nov. 3, 2005 * cited by examiner (51) Int. Cl. Primary Examiner Nathan Flynn G06F 5/16 ( ) Assistant Examiner Mohamed Wasel (52) U.S. Cl /206: 709/ /207 (74) Attorney, Agent, or Firm-Lee & Hayes, PLLC 709/224; 709/225 (58) Field of Classification Search /204, (57) ABSTRACT See application file for com E. 225 A user's address book includes a first group of pp p ry. addresses. Those addresses are used to identify address (56) References Cited books that include another group of addresses. Multiple iterations may be used to identify several groups of U.S. PATENT DOCUMENTS addresses, representing a user's Social network. When an 6,073,165 A * 6/2000 Narasimhan et al.... TO9,206 message addressed to the user is received, the message 6,161,130 A 12/2000 Horvitz et al. is trusted if the sending address is within the user's 6,266,692 B1 7/2001 Greenstein Social network. Otherwise, the message is flagged as junk 6, B1 1 1/2002 Donohue mail. Varying trust levels may be applied to messages that are 6,654,787 B1 * 1 1/2003 Aronson et al.... TO9,206 received based on a distance within a social network between 6,691,156 B1 ck Pund et al. f the sending address and the user and/or how often the of R R ck g2. E. et al sending address appears within the Social network. 2004/ A1* 12/2004 Ingerman et al , / A1* 4/2005 Appelman... T Claims, 9 Drawing Sheets 116 Friend Address Address Book Friend Address Book S 112 FrNd Address Book USER Address XY Friend NT ADDREss Book Address Book
2 U.S. Patent Mar. 2, 2010 Sheet 1 of 9 US 7,673,003 B to USER
3 U.S. Patent Mar. 2, 2010 Sheet 2 of 9 US 7,673,003 B a
4 U.S. Patent Mar. 2, 2010 Sheet 3 of 9 US 7,673,003 B2 3O2 Filter Options Please Select an Filter Level Below: e NO Filter 304 (Allow ALL Messages) Restricted Filter (Allow Messages ONLY From Specified Addresses) Customized Filter One Degree of Separation (Trust Friends) -2 Two Degrees of Separation (Trust Friends of Friends) Three Degrees of Separation (Trust Friends of Friends of Friends) 312 Customize
5 U.S. Patent Mar. 2, 2010 Sheet 4 of 9 US 7,673,003 B2 inbox New Message Delete Forward Reply From Trust Subject Received Size friend 1G)example.com 100% Dinner Plans 3/1/04 8:56am 1 KB friend2o)example.com 90% Party Saturday 2/27/042:02pm 3KB friend3gdexample.com 30% Job Leads? 2/27/04 9:34am 1KB Nao 412 -/ N-ace \-ace alo 402
6 U.S. Patent Mar. 2, 2010 Sheet 5 Of 9 US 7,673,003 B2 SERVICE DATA DATA REPOSITORY REPOSITORY USER INTERFACE GENERATOR SOCIAL NETWORK FILTER 51 TRUSTED ESLIST GENERATOR MESSAGE TRUST LEVEL IDENTIFIER
7 U.S. Patent Mar. 2, 2010 Sheet 6 of 9 US 7,673,003 B2 600 V DATA REPOSITORY SERVER SOCIAL NETWORK FILTER TRUSTED ESLIST GENERATOR MESSAGE TRUST LEVEL DENTIFIER DATA REPOSITORY 610 WEB PLUG-N 614 CLIENT COMPUTER SYSTEM 604(1) CLIENT COMPUTER SYSTEM 604(2) CLIENT CLIENT COMPUTER SYSTEM 604(N WEB CLIENT 624
8 U.S. Patent Mar. 2, 2010 Sheet 7 of 9 US 7,673,003 B2 SERVER SYSTEM PROCESSOR OPERATING SYSTEM 708 COMMUNICATION NTERFACE O6 im SERVICE O2
9 U.S. Patent Mar. 2, 2010 Sheet 8 of 9 US 7,673,003 B2 800 y TRUST LEVEL = 100% 802 POPULATE TRUSTED ESLIST WITH USER ENTRIES 804 IDENTIFY S ASSOCIATED WITH CURRENT TRUST LEVEL ENTRIES 806 REDUCE TRUST LEVEL POPULATE TRUSTED LST WITH IDENTIFIED ENTRIES 810 c 812 NO PROCESS DUPLICATES eve 8
10 U.S. Patent Mar. 2, 2010 Sheet 9 Of 9 US 7,673,003 B ? SOCIAL NETWORK FILTERING ENABLED DENTIFY FROM ASSOCIATED WITH THE MESSAGE NO OTHER FILTERING ENABLED? APPLY FILTER 914 TRUSTED2 MESSAGE PASSES FILTER2 ASSOCATE TRUST LEVEL WITH THE MESSAGE 910 REJECT THE MESSAGE ADD MESSAGE TO INBOX
11 1. SOCIAL NETWORK FILTERING TECHNICAL FIELD This invention relates to filtering, and more specifi cally to filtering based on a social network. BACKGROUND As more and more individuals are utilizing electronic mail as a tool for communication, unsolicited junk has become a problem. To enable users to reduce the amount of junk ("spam) that they receive, many filtering tools have been developed. One of the most effective filters is an exclusive filter based on entries in a user's address book. For example, an exclusive filter identifies as junk mail, any received from an address not found in the recipients address book. While this is an effective filtering technique, it is likely that many messages may be identified as junk mail when, in fact, they are that the recipient would like to receive. For example, if a user has the address of a friend in their address book, s from that friend will be received. How ever, if the friend passes on the user's address to another friend, any s received from that individual will be clas sified as junk mail until the user adds the new friend's address to their address book. Accordingly, a need exists for an filter that classifies an received from a friend of a friend as being a trusted rather than a junk . SUMMARY Techniques for filtering messages based on a social network are described. A first level of a user's social network is determined based on addresses stored in the user's address book. Those addresses are used to identify additional address books that belong to friends of the user, Additional members of the user's social network are deter mined based on addresses stored in the additional address books that belong to friends of the user. The social network may be limited to any number of such iterations. Trust levels may be assigned to addresses that are part of a user's social network. Trust levels may be based on how far a particular address is removed from the user and/or on how often a particular address appears within the social network. When an message is received that is addressed to the user, the address from which the message was sent is compared to the addresses that are part of the user's social network. If the address is found, then the trust level associated with the address is applied to the received message. On the other hand, if the address is not found, then the message is flagged as junk . BRIEF DESCRIPTION OF THE DRAWINGS FIG. 1 is a block diagram that illustrates an exemplary Social network associated with a particular user. FIG. 2 is a block diagram that illustrates an exemplary way in which trust levels may be applied to elements of the social network illustrated in FIG. 1. FIG. 3 is a display screen diagram of an exemplary user interface that enables a user to modify filtering options associated with an account. US 7,673,003 B FIG. 4 is a display screen diagram of an exemplary inbox user interface for displaying messages received through a social network filter. FIG. 5 is a block diagram that illustrates an exemplary environment in which a social network filter may be implemented as part of a web-based service. FIG. 6 is a block diagram that illustrates an exemplary environment in which a social network filter may be implemented as part of a network-based service. FIG. 7 is a block diagram that illustrates select components of an exemplary server system. FIG. 8 is a flow diagram that illustrates an exemplary method for identifying addresses that are part of a user's Social network and assigning trust levels to individual ones of the identified addresses. FIG. 9 is a flow diagram that illustrates an exemplary method for applying a Social network filter to a received message. DETAILED DESCRIPTION Overview The embodiments described below provide techniques for filtering based on a user's Social network. addresses stored in the user's address book are assumed to belong to friends of the user. Accordingly, as in an exclusive filtering system, s received from addresses stored in the user's address book are allowed, and are not flagged as junk . A users friends (as identified by addresses in the user's address book), being part of the user's Social network, are trusted to have friendly' addresses stored in their address books as well. Accordingly, in addition to explicitly trusting (i.e., not flagging as junk ) messages received from addresses stored in the user's address book, messages received from addresses stored in the users friends address books are also trusted. Social Network FIG. 1 illustrates an exemplary social network 100 associated with a particular user. A user stores addresses associated with their friends in user address book 102. Those friends (identified by addresses in the user address book 102) may also have address books. For example, user address book 102 may include address associated with five friends of the particular user. Those friends may also have address books, represented by friend address books 104,106, 108, 110, and 112. Similarly, individuals identified by addresses stored in friend address books 104,106, 108, 110, and 112 may also have address books. For example, two individuals represented by addresses stored in friend address book 104 may have address books, represented by friend address books 114 and 116. Similarly, an individual represented by an address stored in both friend address book 106 and friend address book 108 may have an address book, represented by friend address book 118. Social Network Trust Levels FIG. 2 illustrates example trust levels that may be associ ated with address found in address books that are part of a user's Social network. In an exemplary implementation, trust levels are associated with addresses that are found in the various address books belonging to the user, friends of the user, and friends of friends of the user. The trust levels are established to enable a user to determine, when he or she receives an message, how confident the user should be that the received message is not junk . For example, messages received from addresses that are stored in user address book 102 are assigned a high trust level, while
12 3 messages received from address that are stored in more distant friend address books (e.g., friend address books 114, 116, or 118) may be assigned a lower trust level. In an exemplary implementation, a user's Social network may be described in terms of degrees of separation. For example, addresses specified in the user's address book 102 are Zero degrees separated from the user. Addresses specified in address books that belong to the friends who are specified in the user's address book 102 are one degree sepa rated from the user. Address books 104, 106, 108, 110, and 112 each belong to an individual associated with an address that is found in the user's address book 102, and thus, are each one-degree removed from the user. Similarly, address books 114 and 116 are associated with individuals who are identified by addresses stored in address book 104, and address book 118 is associated with an individual who is identified by an address stored in both address book 106 and address book 108. Thus, friend address books 114, 116, and 118 are two-degrees removed from the user. Although not illustrated, any number of degrees of separation may be defined for a particular user's social network. In an exemplary implementation, each degree of separation has an associated trust level. For example, those address stored in the user address book 102 are zero-degrees removed, and are 100% trusted. Therefore, trusted addresses circle 202 includes all of the addresses stored in user address book 102. Dashed line 204 represents those address books that are one-degree removed from the user. In the illustrated example, addresses stored in the one-degree removed address books (e.g., friend address books 104,106,108,110, and 112) are assigned a 50% trust level. Similarly, dotted line 206 represents those address books that are two-degrees removed from the user. In the illustrated example, address stored in the two-degrees removed address books (e.g., friend address books 114, 116, and 118) are assigned a 30% trust level. The trust levels described herein are given only as an illus tration. It is recognized that any number of different methods may be used for determining a trust level associated with a particular address, based on how far removed it is from a particular user. In the described implementation, trust levels are assigned to addresses that are added to the trusted addresses circle 202 from the various degrees of separation. In addition, a trust level associated with a particular address may be increased if the address is found multiple times. For example, if a particular address is not stored in user address book 102, but is stored in three friend address books that are one-degree removed from the user (e.g., friend address books 108, 110, and 112), then that particular address may be assigned a trust level equal to 150% (i.e., 50%+50%+50%; one rating of 50% for each one-degree removed friend address book in which the address is stored). However, to prevent an address that is not stored in the user address book 102 from being assigned a trust level greater than 100%, each degree of separation may have an associated maximum trust level. For example, one-degree of separation may have a maximum trust level of 90% and two-degrees of separation may have a maximum trust level of 45%. Given these maximums, an address that is not stored in user address book 102 cannot be assigned a trust level greater than 90%. Similarly, an address that is not stored in user address book 102 or friend address books 104, 106, 108, 110, or 112 (but is stored in at least one of friend address books 114, 116, or 118) cannot be assigned a trust level greater than 45%. US 7,673,003 B In the described exemplary implementation, the maximum trust level allowed for a particular address is determined by the closest degree of separation in which the address is found. For example, an address that is found in friend address book 114, friend address book 116, and friend address book 118 may be assigned a trust level of 45% (30% from address book % from address book % from address book %, but the maximum for two degrees removed is 45%). On the other hand, an address that is found in friend address book 112, friend address book 114, and friend address book 118 may be assigned a trust level of 90% (50% from address book % from address book % from address book 118=110%, but the maximum for one-degree removed is 90%). In an exemplary implementation, a user can specify a degree to which messages received from friends friends are to be trusted. For example, if a user specifies a Zero-degree trust, then only messages received from addresses specified in the user address book 102 are trusted; if a user specifies a one-degree trust, then messages received from addresses specified in the user address book 102 or messages received from addresses specified address books that are one-degree removed from the user address book 102 (e.g., address books 104, 106, 108, 110, and 112) are trusted. In an alternate implementation, a user may also be allowed to specify the trust level to be applied to addresses that are separated from the user by various degrees. For example, a default setting may assign a 50% trust level to address that are one-degree removed from the user, but the user may be allowed to override that setting to assign, for example, a 70% trust level to address that are one-degree removed from the user. Similarly, in an alternate implementation, a user may be allowed to customize a maximum trust level associated with various degrees of separation. For example, a default setting may enforce a maximum trust level of 90% for addresses that are one-degree removed from a user, but the user may be allowed to override the default to assign a maximum trust level of 99% for addresses that are on-degree removed from a user. Social Network Filter Setup User Interface FIG.3 illustrates an exemplary filter setup user inter face 300. In the illustrated exemplary implementation, a user can select No Filter 302 to allow receipt of all messages. Alternatively, a user can select Restricted Filter 304 to allow receipt of messages only from addresses stored in the user's address book. To take advantage of a social network filter, a user may select one of three Customized Filter options. A one-degree of separa tion option 306 may be selected to allow receipt of messages from address specified in the user's address book or in address books belonging to individuals who are identified in the user's address book (i.e., the user and the users friends). A two-degrees of separation option 308 may be selected to allow receipt of messages from addresses found in address books belonging to the user, the users friends, and friends of the users friends. Similarly, a three-degrees of separation option 310 may be selected to allow receipt of messages from addresses found in address books belonging to the user, the users friends, friends of the users friends, and friends of those friends. In an exemplary implementation, a customize button 312 may be enabled when a user selects one of the customized options 306, 308, or 310. By selecting the customize button 312, another screen (not shown) may be displayed that enables the user to customize a trust level to be associated
13 5 with each degree of separation and/or to customize a maxi mum trust level to be associated with each degree of separa tion. User Interface Display FIG. 4 illustrates an exemplary user interface display 402 of an inbox containing messages received through a social network filter. As in typical system user interfaces, details of a received message are displayed, such as a from address 404, a subject 406, a received date and time 408, and a size 410. In the described exemplary implementation, messages received through a social network filter also have an associated a trust level 412, which may be displayed to indicate how trusted a particular message is. For example, messages received from friends of a user (e.g., based on addresses stored in the user's address book) may be 100% trusted, while messages received from friends of the user's friends may be less than 100% trusted. In the illustrated example, a numeric indicator is used to indicate a trust level associated with a received message. In alternate implementations, trust levels associated with received messages may be represented in other ways. For example, different icons or other graphical indica tors may be used to represent trust levels. Exemplary Environment FIGS. 5 and 6 illustrate two exemplary environments in which Social network filtering may be implemented. FIG. 5 illustrates an exemplary environment 500 in which a Social network filter may be implemented as part of a web-based service. Environment 500 includes service 502 and one or more client devices, such as client device 504 and client device 506. In the illustrated example, service 502 is an Internet-based service that may be accessed by client devices 504 and 506 through the Internet service 502 includes address book data repository 510, data repository 512, social network filter 514, and user interface generator service 502 may also include other components not illustrated in FIG. 5, including, but not limited to, additional types of filters. Address book data repository 510 is configured to store address books associated with multiple users of service 502. Address book data repository 510 may store addresses as well as other contact information, such as mailing address, phone numbers, and so on. Address book data repository 510 is also configured to store data that iden tifies trusted addresses for users who have enabled social network filter 514 for their account. In an exem plary implementation, trusted addresses and trust levels associated therewith may be automatically updated periodi cally, Such as once per week. Alternatively, trusted addresses based on a user's Social network may be stored in a separate data repository, for example, associated with social network filter 514. In an alternate implementation, rather than storing data that represents a user's Social net work, social network filter 514 may perform a real-time search and trust level determination for a particular address when an message is received from that address. data repository 512 is configured to store actual messages associated with accounts of multiple users. data repository 512 may store incoming and/or outgoing messages associated with users. Social network filter 514 is configured to determine, for a user account with Social network filtering enabled, from what addresses messages are to be trusted, and what trust levels are to be associated with them. That is, social filter 514 identifies address book data stored in address book data repository 510 to determine addresses at various degrees of separation from a particular user and US 7,673,003 B assigns appropriate trust levels to those addresses. Social network filter 514 is further configured to deter mine, when an message is received, whether or not the message is to be trusted, and if so, to what level. Exemplary social network filter 514 includes trusted addresses list generator 518 and message trust level identifier 520. Trusted addresses list generator 518 is configured to iden tify addresses that are to be part of a user's social network, and to determine trust values to be associated with each of those addresses. For example, trusted addresses list generator 518 may search extract addresses from data stored in address book data repository 510 that repre sents a particular user's address book. Each of the extracted addresses may be assigned a 100% trust level, indicating that each of those addresses is 100% trusted by the user. Trusted addresses list generator 518 may then search address book data repository 510 for address books associated with any of the addresses found in the user's address book. addresses may then be extracted from any identified address books, and assigned a trust level that is to be associ ated with addresses that are one-degree removed from the user. This process may be performed iteratively a pre-config ured number of times to identify the addresses that are part of the user's Social network. Any duplicate entries may then be processed, for example, to remove the duplicates and increase the trust levels for those addresses that appear multiple times within the user's social network. Message trust level identifier 520 is configured to deter mine a trust level to be associated with a received message. For example, ifa message is received from an address that is not found within the message recipient's Social network, then the message may be classified as junk (e.g. the message is assigned a 0% trust level). If a message is received from an address that is found within the mes sage recipient's Social network, then the message is assigned the trust level that is associated with the address from which the message was sent. User interface generator 516 is configured to provide one or more user interface screens to users accessing Ser vice 502. In an exemplary implementation, user interface generator 516 generates hypertext markup language (HTML) user interface Screens that provide web-based access to a user's account. One example user interface Screen may provide access to an inbox, Such as the user interface screen illustrated in FIG. 4. Another example user interface screen may provide access to filter customization, Such as the user interface screen illustrated in FIG. 3. User inter face generator 516 may also generate other user interface screens that are not illustrated or described herein. FIG. 6 illustrates an alternate exemplary environment 600 in which a social network filter may be implemented as part of an server. Environment 600 includes network server 602 and one or more client computer systems, such as client computer systems 604(1), 604(2),..., 604(N). Client computer systems 604(1), 604(2) (N) include clients 606(1), 606(2),..., 606(N). clients 606 provide an interface to server 602 to enable users to view received messages, send messages, and customize account settings, such as filter options. Communication between server 602 and clients 606 occurs over network 608. In the illustrated exemplary implementation, server 602 is implemented as a network server that includes data repository 610 and social network filter 612. Network server 602 may also include web address book plug-in 614.
14 7 data repository 610 is configured to maintain data associated with user accounts. The data that is maintained may include, but is not limited to, incoming messages, outgoing messages, user account cus tomization data, and user address books. Social network filter 612 includes trusted addresses list generator 616 and message trust level identifier 618. User address books may be stored on server 602 (e.g., as part of data repository 610). In such an implemen tation, a user's Social network may be defined in terms of other users who also store address books on Server 602. To enable the definition of user's social networks that include addresses that are associated with individuals who may not be associated with server 602, environ ment 600 also includes a web-based address book data reposi tory 620, which may be accessed through the Internet 622. For example, client computer system 604(N) may also include a web client 624 that provides an interface through the Internet 622 to address book data repository 620. Address book data repository 620 may be implemented as a web based subscription-type service that allows users to maintain web-based electronic address books. Address book data repository 620 may be accessed by any users with Internet access, not restricted to users of server 602. To identify members of a user's social network based on data stored in address book data repository 620, server 602 may also include web address book plug-in 614 that enables server 602 to search and extract data from address book data repository 620. In this way, a social net work associated with a user of server 602 may be expanded to include addresses that are stored in web based address book data repository Server System FIG. 7 illustrates select components of an exemplary server computer system 700 configured to support social network filtering. server system 700 includes a processor 702, memory 704, and communication interface 706. An operating system 708 and service 502 are stored in memory 704 and executed on processor 702. Com munication interface 706 enables communication, for example over the Internet, between server system 700 and one or more client devices. Trusted Address List Generation Method FIG. 8 is a flow diagram that illustrates an exemplary method 800 for generating a list of trusted address from which a particular user may receive messages. The illustrated process can be implemented in any Suitable hard ware, software, firmware or combination thereof. At block 802, the system sets a trust level equal to 100%. For example, social network filter 514 may assign a trust level variable a value of 100%. At block 804, social network filter 514 populates a trusted addresses list associated with a user's account with addresses found in the user's address book. In the described exemplary implementation, the trusted address list includes a trust indicator, which, for each address found, is set to the value of the trust level variable, which, at this point, is equal to 100%. At block 806, social network filter 514 identifies other address books associated with the addresses that are found in the user's address book. For example, any other users of service 502 whose address is stored in the user's address book are identified. At block 808, social network filter 514 reduces the value of the trust level variable to the trust level value to be associated with addresses that are the next degree US 7,673,003 B removed from the user. For example, if a users friends are to be 50% trusted, the value of the trust level variable is set to 50%. At block 810, social network filter 514 adds to the list of trusted addresses, those addresses found in the address books identified as described above with reference to block 806. The current value of the trust level variable is associated with each of the added addresses. At block 812, social network filter 514 determines whether or not the next level of the social network is to be trusted. In an exemplary implementation, a default of three degrees of separation may be used for the Social network filter. Alternatively, a user may be allowed to customize the greatest degree of separation to be trusted, as illustrated and described above with reference to FIG. 3. If users that are the next degree separated from the user are to be trusted (the Yes branch from block 812), then processing continues as described above with reference to blocks Other wise, duplicate entries in the list of trusted addresses are processed, as described below with reference to block 814. At block 814, social network filter 514 processes duplicate entries in the list of trusted addresses. In an exem plary implementation, duplicate entries are consolidated to one entry and the trust levels associated with the duplicate entries are added together to indicate that the particular address is to be more trusted because it is found multiple times within the user's social network. Furthermore, as described above, each degree of separation may have an asso ciated maximum trust level. The maximums are applied to the duplicate entries to ensure that after the trust levels for dupli cate entries are added together, the value is not greater than the maximum for the degree of separation associated with the entry that is found closest to the user. For example, if a particular address is found in multiple address books, with at least one being only one degree removed from the user's address book, then the maximum trust level that may be assigned to that address is the maximum allowed for addresses that are one-degree removed. If, however, the clos est of the duplicate entries for a particular address is two-degrees removed from the user, then the maximum trust level that may be assigned for that address is the maxi mum for addresses that are two-degrees removed from the user, which is typically lower than a maximum trust level that may be assigned to an address that is only one-degree removed from the user. Social Network Filtering Method FIG. 9 is a flow diagram that illustrates an exemplary method 900 for applying a social network filter to a received message. The illustrated process can be imple mented in any suitable hardware, Software, firmware or com bination thereof. At block 902, the system receives an message. For example, service 502 receives an message addressed to a user of the service. At block 904, social network service 502 determines whether or not social network filtering is enabled for the user account to which the received message is addressed. If social network filtering is enabled (the Yes branch from block 904), then processing continues as described below with reference to block906. On the other hand, if social network filtering is not enabled (the No branch from block 904), then processing continues as described below with reference to block 914. At block 906, when it is determined that social network filtering is enabled, service 502 identifies the address from which the message was sent. For example,
15 9 social network filter 514 examines the header informa tion associated with the received message and extracts the sender's address. At block 908, social network filter 514 determines whether or not the sender's address is trusted. For example, social network filter 514 compares the sender's address to addresses identified by trusted addresses list generator (as described above with reference to FIG. 8) as being part of the message recipient's Social network. If the sender's address is not found in the message recipient s social network (the No branch from block 908), then processing continues as described below with reference to block 920. At block 910, when the sender's address is found in the message recipient s social network (the Yes branch from block 908), social network filter 514 associates a trust level with the received message. For example, message trust level identifier 520 associates with the received message, the same trust level that is associated with the sender's address within the message recipient's Social network. At block 912, the received message is added to the recipi ent's inbox. At block 914, when a message is received and it is deter mined that social network filtering is not enabled for the message recipient (the No branch from block 904), service 502 determines whether or not another type of filtering is enabled. If no other type of filtering is enabled (the No branch from block 914), then as described above with reference to block 912, the received message is added to the recipient s inbox. At block 916, if another type of filtering is enabled (the Yes branch from block 914), service 502 applies the appropriate filter to the received message. At block 918, service 502 determines whether or not the message passes the appropriate filter. If the message passes the filter (the Yes branch from block 918), then the message is added to the recipient's inbox, as described above with reference to block 912. At block 920, if the message does not pass the filter (the No branch from block 908 or block 918), service 502 rejects the message. Message rejection may implemented by flagging the received message as junk mail. Alternatively, message rejection may be implemented by deleting the mes Sage. CONCLUSION The techniques described above enable social network filtering. Although the invention has been described in language specific to structural features and/or methodologi cal steps, it is to be understood that the invention defined in the appended claims is not necessarily limited to the specific features or steps described. Rather, the specific features and steps are disclosed as preferred forms of implementing the claimed invention. The invention claimed is: 1. A method comprising: defining a social network of a user, wherein: addresses specified in an electronic address book belonging to the user are defined as being Zero degrees separated from the user, and addresses specified in an electronic address book that belongs to an owner of an address that is Zero degrees separated from the user are defined as being one degree separated from the user; identifying an address associated with an mes Sage that occurs within the user's Social network; US 7,673,003 B in response to identifying the address associated with the message, associating a trust level with the address associated with the message, the trust level being based, at least in part on a number of degrees of separation between the user and the address associated with the message; determining that the address associated with the message occurs more than once within the user's Social network; and in response to determining that the address associ ated with the message occurs more than once within the user's Social network, increasing the trust level associated with the address associated with the message to indicate that the address associated with the message is more trusted because it occurs more than once within the user's Social network. 2. The method as recited in claim 1 wherein the first trust level is represented as a numerical value. 3. The method as recited in claim 1 wherein the identifying the address comprises extracting the address from the address book belonging to the user. 4. The method as recited in claim 1 wherein the identifying the address comprises extracting the address from an address book belonging to an owner of an address that was extracted from the address book belonging to the user. 5. The method as recited in claim 1 wherein a first trust level assigned to a first address is less than a second trust level assigned to a second address, thereby indi cating that a likelihood that an message received from the first address is junk is greater than alikelihood that an message received from the second address is junk The method as recited in claim 1 wherein the increasing comprises: identifying for the address that occurs more than once within the user's Social network, a degree of sepa ration associated with an occurrence that is closest to the user, determining a maximum trust level associated with the degree of separation; and limiting the trust level associated with the address that occurs more than once to the maximum trust level. 7. The method as recited in claim 1 further comprising: receiving an message addressed to the user; determining whether an address from which the message was sent is in a social network associated with the user; and in an event that the address from which the message was sent is in the Social network associated with the user: associating a trust level with the message, the trust level being associated in terms of the Social network, with the address from which the message was sent, and displaying an indication that the message has been received, wherein the indication that the mes sage has been received comprises an indication of the trust level that has been associated with the message. 8. A memory encoded with computer-readable instructions that, when executed by a computer, cause the computer to implement the method as recited in claim An system comprising: an data repository configured to manage incoming and outgoing messages associated with a user's account; and
16 11 a social network filter configured to filter an incom ing message addressed to the user's account based on whether an address from which the incoming message is received is part of a social network associated with the user's account, wherein the social network filter comprises: a trusted addresses list generator configured to: identify addresses that are within the user's social network; and assign a trust level to each address that is within the user's social network, wherein the trust levels that are assigned are based, at least in part, on: a number of degrees of separation between a particu lar address and the user, Such that addresses having fewer degrees of separation are more trusted than addresses having more degrees of separation; and a frequency of occurrence of a particular address within the user's social network, such that a first address having a particular degree of separation from the user is assigned a first trust level and a second address having the same particular degree of separation from the user is assigned a second trust level, greater than the first trust level, based on the second address occurring more times within the user's Social net work than the first address; and a message trust level identifier configured to associate a trust level with an incoming message based on a trust level assigned to an address from which the incoming message was sent. 10. A memory encoded with computer-readable instruc tions that, when executed by a computer, cause the computer to perform a method comprising: defining a Social network associated with an account, such that: a first address stored in an address book associated with the account is identified as a first-level address; and a second address stored in an address book associ ated with the first-level address is identified as a second-level address; associating a first trust level with the first-level address; associating a second trust level with the second-level address, whereina difference between the first trust level and the second trust level indicates that the first-level address is more trusted to not send spam s than the second-level address; US 7,673,003 B receiving an message addressed to a particular account, determining a sending address from which the message Was Sent; determining whether the sending address is part of a Social network associated with the particular account, in an event that the sending address is not part of the Social network associated with the particular account, flagging the message as junk mail; and in an event that the sending address is part of the Social network associated with the particular account: determining a trust level associated with the sending address within the social network; associating the trust level with the message; and forwarding the message to an inbox associated with the particular account, whereby an indication of the message is displayable along with an indica tion of the trust level associated with the message. 11. The memory as recited in claim 10, wherein the method further comprises defining the Social network Such that: a third address stored in an address book associated with the second-level address is identified as a third-level address within the social network. 12. A memory encoded with computer-readable instruc tions which, when executed by a computer, cause the com puter to perform a method comprising: receiving an message addressed to a particular account; determining sending address from which the message was sent; determining whether the sending address is part of a Social network associated with the particular account, in an event that the sending address is not part of the Social network associated with the particular account, flagging the message as junk mail; and in an event that the sending address is part of the Social network associated with the particular account, determining a trust level associated with the sending address within the social network; associating the trust level with the message; and forwarding the message to an inbox associated with the particular account, whereby an indication of the message is displayable along with an indica tion of the trust level associated with the message. k k k k k
(12) United States Patent (10) Patent No.: US 6,199,058 B1
 USOO6199058B1 (12) United States Patent (10) Patent No.: US 6,199,058 B1 Wong et al. (45) Date of Patent: Mar. 6, 2001 (54) REPORT SERVER CACHING 5,168,444 12/1992 Cukor et al.... 705/1 5,625,818 4/1997
USOO6199058B1 (12) United States Patent (10) Patent No.: US 6,199,058 B1 Wong et al. (45) Date of Patent: Mar. 6, 2001 (54) REPORT SERVER CACHING 5,168,444 12/1992 Cukor et al.... 705/1 5,625,818 4/1997
(12) Patent Application Publication (10) Pub. No.: US 2012/ A1
 (19) United States US 20120047545A1 (12) Patent Application Publication (10) Pub. No.: US 2012/0047545 A1 SELLERS et al. (43) Pub. Date: Feb. 23, 2012 (54) TOPOGRAPHIC FRAUD DETECTION (52) U.S. Cl....
(19) United States US 20120047545A1 (12) Patent Application Publication (10) Pub. No.: US 2012/0047545 A1 SELLERS et al. (43) Pub. Date: Feb. 23, 2012 (54) TOPOGRAPHIC FRAUD DETECTION (52) U.S. Cl....
/ client computer. \ single sign-on. application program server (AP) network. server (SS0) (12) United States Patent Hsieh et a].
![/ client computer. \ single sign-on. application program server (AP) network. server (SS0) (12) United States Patent Hsieh et a]. / client computer. \ single sign-on. application program server (AP) network. server (SS0) (12) United States Patent Hsieh et a].](/thumbs/90/103929709.jpg) US007278155B2 (12) United States Patent Hsieh et a]. (10) Patent N0.: (45) Date of Patent: US 7,278,155 B2 Oct. 2, 2007 (54) (75) (73) (*) (21) (22) (65) (30) Foreign Application Priority Data Oct. 22,
US007278155B2 (12) United States Patent Hsieh et a]. (10) Patent N0.: (45) Date of Patent: US 7,278,155 B2 Oct. 2, 2007 (54) (75) (73) (*) (21) (22) (65) (30) Foreign Application Priority Data Oct. 22,
(12) United States Patent (10) Patent No.: US 7,640,289 B2
 USOO7640289B2 (12) United States Patent (10) Patent No.: Chen (45) Date of Patent: *Dec. 29, 2009 (54) INTELLIGENT COMPUTER SWITCH 6,388,658 B1 5/2002 Ahern et al. 6,567,869 B2 5/2003 Shirley (75) Inventor:
USOO7640289B2 (12) United States Patent (10) Patent No.: Chen (45) Date of Patent: *Dec. 29, 2009 (54) INTELLIGENT COMPUTER SWITCH 6,388,658 B1 5/2002 Ahern et al. 6,567,869 B2 5/2003 Shirley (75) Inventor:
(12) United States Patent (10) Patent No.: US 6,467,088 B1
 USOO6467088B1 (12) United States Patent (10) Patent No.: US 6,467,088 B1 alsafadi et al. (45) Date of Patent: Oct. 15, 2002 (54) RECONFIGURATION MANAGER FOR WO WO9015394 6/1990... GO6F/15/46 CONTROLLING
USOO6467088B1 (12) United States Patent (10) Patent No.: US 6,467,088 B1 alsafadi et al. (45) Date of Patent: Oct. 15, 2002 (54) RECONFIGURATION MANAGER FOR WO WO9015394 6/1990... GO6F/15/46 CONTROLLING
(12) Patent Application Publication (10) Pub. No.: US 2015/ A1
 US 20150358424A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2015/0358424 A1 BRAUN et al. (43) Pub. Date: Dec. 10, 2015 (54) SYSTEMAND METHOD FOR PROVIDING (52) U.S. Cl. DATABASE
US 20150358424A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2015/0358424 A1 BRAUN et al. (43) Pub. Date: Dec. 10, 2015 (54) SYSTEMAND METHOD FOR PROVIDING (52) U.S. Cl. DATABASE
(12) United States Patent (10) Patent No.: US 6,657,548 B2. Dai (45) Date of Patent: Dec. 2, 2003
 USOO6657548B2 (12) United States Patent (10) Patent No.: US 6,657,548 B2 Dai (45) Date of Patent: Dec. 2, 2003 (54) SYSTEMSTATUS LIGHT INDICATOR 6,501,897 B1 * 12/2002 German et al.... 385/134 DEVICE EMBEDDED
USOO6657548B2 (12) United States Patent (10) Patent No.: US 6,657,548 B2 Dai (45) Date of Patent: Dec. 2, 2003 (54) SYSTEMSTATUS LIGHT INDICATOR 6,501,897 B1 * 12/2002 German et al.... 385/134 DEVICE EMBEDDED
(12) Patent Application Publication (10) Pub. No.: US 2014/ A1
 (19) United States US 20140282538A1 (12) Patent Application Publication (10) Pub. No.: US 2014/0282538A1 ConoVer et al. ( 43) Pub. Date: Sep. 18, 2014 (54) (71) (72) (73) (21) (22) (60) MINIMIZING SCSI
(19) United States US 20140282538A1 (12) Patent Application Publication (10) Pub. No.: US 2014/0282538A1 ConoVer et al. ( 43) Pub. Date: Sep. 18, 2014 (54) (71) (72) (73) (21) (22) (60) MINIMIZING SCSI
(12) United States Patent Cunningham et al.
 US007765264B2 (12) United States Patent Cunningham et al. (10) Patent N0.: (45) Date of Patent: Jul. 27, 2010 (54) SELECTION OF MODE ACCORDING TO MESSAGE CHARACTERISTICS (75) Inventors: Ivy F. Cunningham,
US007765264B2 (12) United States Patent Cunningham et al. (10) Patent N0.: (45) Date of Patent: Jul. 27, 2010 (54) SELECTION OF MODE ACCORDING TO MESSAGE CHARACTERISTICS (75) Inventors: Ivy F. Cunningham,
(12) Patent Application Publication (10) Pub. No.: US 2005/ A1
 (19) United States US 20050281269A1 (12) Patent Application Publication (10) Pub. No.: US 2005/0281269 A1 Choi (43) Pub. Date: (54) MOBILE TELECOMMUNICATION SYSTEM (30) Foreign Application Priority Data
(19) United States US 20050281269A1 (12) Patent Application Publication (10) Pub. No.: US 2005/0281269 A1 Choi (43) Pub. Date: (54) MOBILE TELECOMMUNICATION SYSTEM (30) Foreign Application Priority Data
(12) Patent Application Publication (10) Pub. No.: US 2011/ A1
 (19) United States US 2011 0231.630A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0231630 A1 Dannowski et al. (43) Pub. Date: Sep. 22, 2011 (54) ADDRESS MAPPING IN VIRTUALIZED (52) U.S.
(19) United States US 2011 0231.630A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0231630 A1 Dannowski et al. (43) Pub. Date: Sep. 22, 2011 (54) ADDRESS MAPPING IN VIRTUALIZED (52) U.S.
(12) United States Patent (10) Patent No.: US 8,385,897 B1
 US0083.85897 B1 (12) United States Patent (10) Patent No.: Yadav-Ranjan (45) Date of Patent: Feb. 26, 2013 (54) GLOBAL TEXT MESSAGING SYSTEMAND (56) References Cited METHOD U.S. PATENT DOCUMENTS (75) Inventor:
US0083.85897 B1 (12) United States Patent (10) Patent No.: Yadav-Ranjan (45) Date of Patent: Feb. 26, 2013 (54) GLOBAL TEXT MESSAGING SYSTEMAND (56) References Cited METHOD U.S. PATENT DOCUMENTS (75) Inventor:
(12) United States Patent (10) Patent No.: US 8, B2. Cha et al. (45) Date of Patent: Oct. 8, 2013
 US008554.937B2 (12) United States Patent (10) Patent No.: US 8,554.937 B2 Cha et al. (45) Date of Patent: Oct. 8, 2013 (54) METHOD AND SYSTEM FOR 6,259,701 B1* 7/2001 Shur et al.... 370/401 6,836,806 B1*
US008554.937B2 (12) United States Patent (10) Patent No.: US 8,554.937 B2 Cha et al. (45) Date of Patent: Oct. 8, 2013 (54) METHOD AND SYSTEM FOR 6,259,701 B1* 7/2001 Shur et al.... 370/401 6,836,806 B1*
(12) United States Patent (10) Patent No.: US 6,611,682 B1
 USOO661 1682B1 (12) United States Patent (10) Patent No.: Pröjtz (45) Date of Patent: Aug. 26, 2003 (54) MOBILE TELEPHONE APPARATUS AND 6,188.888 B1 * 2/2001 Bartle et al.... 455/417 METHOD FOR CALL DIVERT
USOO661 1682B1 (12) United States Patent (10) Patent No.: Pröjtz (45) Date of Patent: Aug. 26, 2003 (54) MOBILE TELEPHONE APPARATUS AND 6,188.888 B1 * 2/2001 Bartle et al.... 455/417 METHOD FOR CALL DIVERT
(12) United States Patent (10) Patent No.: US 6,418,453 B1
 USOO6418453B1 (12) United States Patent (10) Patent No.: Kraft et al. (45) Date of Patent: Jul. 9, 2002 (54) NETWORK REPOSITORY SERVICE FOR 6.295,529 B1 * 9/2001 Corston-Oliver et al.... 707/3 EFFICIENT
USOO6418453B1 (12) United States Patent (10) Patent No.: Kraft et al. (45) Date of Patent: Jul. 9, 2002 (54) NETWORK REPOSITORY SERVICE FOR 6.295,529 B1 * 9/2001 Corston-Oliver et al.... 707/3 EFFICIENT
(12) United States Patent (10) Patent No.: US 8.131,217 B2
 US008131217B2 (12) United States Patent (10) Patent No.: US 8.131,217 B2 Srinivasa et al. (45) Date of Patent: Mar. 6, 2012 (54) IDENTIFICATION OF MAKE AND MODEL 2004/0266347 A1* 12/2004 Palin et al....
US008131217B2 (12) United States Patent (10) Patent No.: US 8.131,217 B2 Srinivasa et al. (45) Date of Patent: Mar. 6, 2012 (54) IDENTIFICATION OF MAKE AND MODEL 2004/0266347 A1* 12/2004 Palin et al....
(12) Patent Application Publication (10) Pub. No.: US 2007/ A1
 US 20070116246A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0116246A1 Walker et al. (43) Pub. Date: May 24, 2007 (54) CATEGORIZATION OF TELEPHONE CALLS Publication Classification
US 20070116246A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0116246A1 Walker et al. (43) Pub. Date: May 24, 2007 (54) CATEGORIZATION OF TELEPHONE CALLS Publication Classification
(12) Patent Application Publication (10) Pub. No.: US 2012/ A1
 (19) United States US 20120033670A1 (12) Patent Application Publication (10) Pub. No.: US 2012/0033670 A1 Olakangil (43) Pub. Date: Feb. 9, 2012 (54) EGRESS PROCESSING OF INGRESS VLAN (52) U.S. Cl....
(19) United States US 20120033670A1 (12) Patent Application Publication (10) Pub. No.: US 2012/0033670 A1 Olakangil (43) Pub. Date: Feb. 9, 2012 (54) EGRESS PROCESSING OF INGRESS VLAN (52) U.S. Cl....
(12) United States Patent (10) Patent No.: US 6,208,340 B1. Amin et al. (45) Date of Patent: Mar. 27, 2001
 USOO620834OB1 (12) United States Patent (10) Patent No.: US 6,208,340 B1 Amin et al. (45) Date of Patent: Mar. 27, 2001 (54) GRAPHICAL USER INTERFACE 5,317,687 5/1994 Torres... 395/159 INCLUDING A DROP-DOWN
USOO620834OB1 (12) United States Patent (10) Patent No.: US 6,208,340 B1 Amin et al. (45) Date of Patent: Mar. 27, 2001 (54) GRAPHICAL USER INTERFACE 5,317,687 5/1994 Torres... 395/159 INCLUDING A DROP-DOWN
(12) (10) Patent No.: US 7,103,736 B2. Sachs (45) Date of Patent: Sep. 5, 2006
 United States Patent US007103736B2 (12) (10) Patent No.: Sachs (45) Date of Patent: Sep. 5, 2006 (54) SYSTEM FOR REPAIR OF ROM 5.325,504 A * 6/1994 Tipley et al.... T11/128 PROGRAMMING ERRORS ORDEFECTS
United States Patent US007103736B2 (12) (10) Patent No.: Sachs (45) Date of Patent: Sep. 5, 2006 (54) SYSTEM FOR REPAIR OF ROM 5.325,504 A * 6/1994 Tipley et al.... T11/128 PROGRAMMING ERRORS ORDEFECTS
United States Patent (19) Pinard et al.
 United States Patent (19) Pinard et al. US005454032A 11 Patent Number: 45) Date of Patent: Sep. 26, 1995 54 METHOD OF ESTABLISHING COMMUNICATION LINK TO ONE OF MULTIPLE DEVICES ASSOCIATED WITH SINGLETELEPHONE
United States Patent (19) Pinard et al. US005454032A 11 Patent Number: 45) Date of Patent: Sep. 26, 1995 54 METHOD OF ESTABLISHING COMMUNICATION LINK TO ONE OF MULTIPLE DEVICES ASSOCIATED WITH SINGLETELEPHONE
(12) United States Patent
 US0088.12887B2 (12) United States Patent Liu et al. (54) ELECTRONIC DISPLAY DEVICE AUTOMATICALLY TURNS ON OR OFF ACCORDING TO WHETHER AUSERN FRONT OF THE DISPLAY (75) Inventors: Xu Liu, Shanghai (CN);
US0088.12887B2 (12) United States Patent Liu et al. (54) ELECTRONIC DISPLAY DEVICE AUTOMATICALLY TURNS ON OR OFF ACCORDING TO WHETHER AUSERN FRONT OF THE DISPLAY (75) Inventors: Xu Liu, Shanghai (CN);
(12) Patent Application Publication (10) Pub. No.: US 2015/ A1. (51) Int. Cl. (52) U.S. Cl COMMUNICATIONS
 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2015/0036568 A1 HWANG US 2015.0036568A1 (43) Pub. Date: Feb. 5, 2015 (54) (71) (72) (73) (21) (22) (30) WIRELESS COMMUNICATIONSTERMINAL
(19) United States (12) Patent Application Publication (10) Pub. No.: US 2015/0036568 A1 HWANG US 2015.0036568A1 (43) Pub. Date: Feb. 5, 2015 (54) (71) (72) (73) (21) (22) (30) WIRELESS COMMUNICATIONSTERMINAL
(12) Patent Application Publication (10) Pub. No.: US 2011/ A1
 (19) United States US 2011 0004845A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0004845 A1 Ciabarra (43) Pub. Date: Jan. 6, 2011 (54) METHOD AND SYSTEM FOR NOTIFYINGA USER OF AN EVENT OR
(19) United States US 2011 0004845A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0004845 A1 Ciabarra (43) Pub. Date: Jan. 6, 2011 (54) METHOD AND SYSTEM FOR NOTIFYINGA USER OF AN EVENT OR
(12) United States Patent
 (12) United States Patent Ramaswamy USOO6480717B1 (10) Patent No.: (45) Date of Patent: Nov. 12, 2002 (54) (75) (73) (*) (21) (22) (51) (52) (58) (56) TUNNELING OF NON-GSM SIGNALNG MESSAGES IN A GSM BASED
(12) United States Patent Ramaswamy USOO6480717B1 (10) Patent No.: (45) Date of Patent: Nov. 12, 2002 (54) (75) (73) (*) (21) (22) (51) (52) (58) (56) TUNNELING OF NON-GSM SIGNALNG MESSAGES IN A GSM BASED
(12) United States Patent (10) Patent No.: US 7,739,050 B2
 USOO773905OB2 (12) United States Patent (10) Patent No.: US 7,739,050 B2 Tatro (45) Date of Patent: Jun. 15, 2010 (54) SOFTWARE-BASED QUALITY CONTROL (56) References Cited ANALYSIS OF WELL LOG DATA U.S.
USOO773905OB2 (12) United States Patent (10) Patent No.: US 7,739,050 B2 Tatro (45) Date of Patent: Jun. 15, 2010 (54) SOFTWARE-BASED QUALITY CONTROL (56) References Cited ANALYSIS OF WELL LOG DATA U.S.
(12) (10) Patent No.: US 7, B2. Peng (45) Date of Patent: Mar. 20, 2007
 United States Patent US007194291B2 (12) (10) Patent No.: US 7,194.291 B2 Peng (45) Date of Patent: Mar. 20, 2007 (54) PROTECTIVE MASK OF MOBILE PHONE 6,591,088 B1* 7/2003 Watanabe... 455/90.3 6,594,472
United States Patent US007194291B2 (12) (10) Patent No.: US 7,194.291 B2 Peng (45) Date of Patent: Mar. 20, 2007 (54) PROTECTIVE MASK OF MOBILE PHONE 6,591,088 B1* 7/2003 Watanabe... 455/90.3 6,594,472
(12) United States Patent
 USOO7370164B1 (12) United States Patent Nagarkar et al. (54) BACKUP OF VIRTUAL MACHINES FROM THE BASE MACHINE (75) Inventors: Kuldeep Sureshrao Nagarkar, Pune (IN); Sinh Dang Nguyen, Eden Prairie, MN (US);
USOO7370164B1 (12) United States Patent Nagarkar et al. (54) BACKUP OF VIRTUAL MACHINES FROM THE BASE MACHINE (75) Inventors: Kuldeep Sureshrao Nagarkar, Pune (IN); Sinh Dang Nguyen, Eden Prairie, MN (US);
(12) (10) Patent No.: US 7,330,395 B2. Ichijo (45) Date of Patent: Feb. 12, 2008
 United States Patent USOO7330395 B2 (12) (10) Patent No.: US 7,330,395 B2 Ichijo (45) Date of Patent: Feb. 12, 2008 (54) METHOD AND SYSTEM FOR 2002fOO67835 A1 6/2002 Vatter... 381.58 AUTOMATICALLY CALIBRATING
United States Patent USOO7330395 B2 (12) (10) Patent No.: US 7,330,395 B2 Ichijo (45) Date of Patent: Feb. 12, 2008 (54) METHOD AND SYSTEM FOR 2002fOO67835 A1 6/2002 Vatter... 381.58 AUTOMATICALLY CALIBRATING
(12) (10) Patent No.: US 8,548,906 B1. Pelican (45) Date of Patent: Oct. 1, 2013
 United States Patent USOO8548906B1 (12) () Patent No.: Pelican (45) Date of Patent: Oct. 1, 2013 (54) METHOD AND APPARATUS FOR 6,272.472 B1* 8/2001 Danneels et al.... 705/27 AUTOMATC SAVINGS UPON EVENT
United States Patent USOO8548906B1 (12) () Patent No.: Pelican (45) Date of Patent: Oct. 1, 2013 (54) METHOD AND APPARATUS FOR 6,272.472 B1* 8/2001 Danneels et al.... 705/27 AUTOMATC SAVINGS UPON EVENT
(12) United States Patent
 (12) United States Patent USOO7506087B2 (10) Patent No.: US 7,506,087 B2 H0 et al. (45) Date of Patent: Mar. 17, 2009 (54) METHOD FOR CONFIGURING A (56) References Cited PERPHERAL COMPONENT INTERCONNECT
(12) United States Patent USOO7506087B2 (10) Patent No.: US 7,506,087 B2 H0 et al. (45) Date of Patent: Mar. 17, 2009 (54) METHOD FOR CONFIGURING A (56) References Cited PERPHERAL COMPONENT INTERCONNECT
(12) Patent Application Publication (10) Pub. No.: US 2008/ A1
 (19) United States US 2008.0068375A1 (12) Patent Application Publication (10) Pub. No.: US 2008/0068375 A1 Min et al. (43) Pub. Date: Mar. 20, 2008 (54) METHOD AND SYSTEM FOR EARLY Z (30) Foreign Application
(19) United States US 2008.0068375A1 (12) Patent Application Publication (10) Pub. No.: US 2008/0068375 A1 Min et al. (43) Pub. Date: Mar. 20, 2008 (54) METHOD AND SYSTEM FOR EARLY Z (30) Foreign Application
(12) United States Patent
 (12) United States Patent USOO6941277B2 (10) Patent No.: Imag0 (45) Date of Patent: Sep. 6, 2005 (54) METHODS AND SYSTEMS FOR PROVIDING (56) References Cited ONLINE INFORMATION FOR NETWORKED DEVICES U.S.
(12) United States Patent USOO6941277B2 (10) Patent No.: Imag0 (45) Date of Patent: Sep. 6, 2005 (54) METHODS AND SYSTEMS FOR PROVIDING (56) References Cited ONLINE INFORMATION FOR NETWORKED DEVICES U.S.
(12) United States Patent (10) Patent No.: US 6,922,791 B2
 USOO6922791 B2 (12) United States Patent (10) Patent No.: Mashayekhi et al. (45) Date of Patent: Jul. 26, 2005 (54) FAILOVER SYSTEM AND METHOD FOR 6,115,830 A 9/2000 Zabarsky et al.... 714/15 CLUSTER ENVIRONMENT
USOO6922791 B2 (12) United States Patent (10) Patent No.: Mashayekhi et al. (45) Date of Patent: Jul. 26, 2005 (54) FAILOVER SYSTEM AND METHOD FOR 6,115,830 A 9/2000 Zabarsky et al.... 714/15 CLUSTER ENVIRONMENT
(12) United States Patent
 (12) United States Patent Beck et al. USOO6842611B2 (10) Patent No.: (45) Date of Patent: Jan. 11, 2005 (54) RECEIVED DATA PROCESSING METHOD IN COMMUNICATION DEVICE FOR SUPPORTING WIRELESS COMMUNICATION
(12) United States Patent Beck et al. USOO6842611B2 (10) Patent No.: (45) Date of Patent: Jan. 11, 2005 (54) RECEIVED DATA PROCESSING METHOD IN COMMUNICATION DEVICE FOR SUPPORTING WIRELESS COMMUNICATION
SCSI routing table (90) and a SCSI to Fibre Channel routing table (92). The system receives a cross bus transfer of data
 US00604.1381A United States Patent (19) 11 Patent Number: 6,041,381 Hoese (45) Date of Patent: Mar. 21, 2000 54 FIBRE CHANNEL TO SCSI ADDRESSING OTHER PUBLICATIONS METHOD AND SYSTEM Hoese, Geoffrey B.,
US00604.1381A United States Patent (19) 11 Patent Number: 6,041,381 Hoese (45) Date of Patent: Mar. 21, 2000 54 FIBRE CHANNEL TO SCSI ADDRESSING OTHER PUBLICATIONS METHOD AND SYSTEM Hoese, Geoffrey B.,
Selecting init r. Associating. Authenticating Unit Master Key. (12) Patent Application Publication (10) Pub. No.: US 2007/ A1.
 (19) United States US 20070153732A1 (12) Patent Application Publication (10) Pub. No.: US 2007/0153732 A1 Yao (43) Pub. Date: Jul. 5, 2007 (54) METHOD FOR AWIRELESS LOCAL AREA NETWORK TERMINAL TO ACCESS
(19) United States US 20070153732A1 (12) Patent Application Publication (10) Pub. No.: US 2007/0153732 A1 Yao (43) Pub. Date: Jul. 5, 2007 (54) METHOD FOR AWIRELESS LOCAL AREA NETWORK TERMINAL TO ACCESS
Is more than one finger placed on touchpad surface?
 USOO776O189B2 (12) United States Patent (10) Patent No.: Cheston et al. (45) Date of Patent: Jul. 20, 2010 (54) TOUCHPAD DIAGONAL SCROLLING 6,043,809 A 3/2000 Holehan 6,707.449 B2 3/2004 Hinckley et al.
USOO776O189B2 (12) United States Patent (10) Patent No.: Cheston et al. (45) Date of Patent: Jul. 20, 2010 (54) TOUCHPAD DIAGONAL SCROLLING 6,043,809 A 3/2000 Holehan 6,707.449 B2 3/2004 Hinckley et al.
(12) United States Patent
 USOO97296.58B2 (12) United States Patent Trahan et al. (10) Patent No.: (45) Date of Patent: Aug. 8, 2017 (54) SYSTEM FOR MANAGING WEB-BASED CONTENT DATA AND APPLICATIONS (76) Inventors: Chris Trahan,
USOO97296.58B2 (12) United States Patent Trahan et al. (10) Patent No.: (45) Date of Patent: Aug. 8, 2017 (54) SYSTEM FOR MANAGING WEB-BASED CONTENT DATA AND APPLICATIONS (76) Inventors: Chris Trahan,
(12) Patent Application Publication (10) Pub. No.: US 2017/ A1
 (19) United States US 2017009 1001A1 (12) Patent Application Publication (10) Pub. No.: US 2017/0091001 A1 PANDEY et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR MANAGING (52) U.S. Cl. AND LINKING SOFTWARE
(19) United States US 2017009 1001A1 (12) Patent Application Publication (10) Pub. No.: US 2017/0091001 A1 PANDEY et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR MANAGING (52) U.S. Cl. AND LINKING SOFTWARE
(12) United States Patent
 USOO9660456B2 (12) United States Patent Dwelley et al. (10) Patent No.: (45) Date of Patent: May 23, 2017 (54) (71) (72) (73) (*) (21) (22) (65) (60) (51) (52) (58) SWITCHING OF CONDUCTOR PAIR IN POWER
USOO9660456B2 (12) United States Patent Dwelley et al. (10) Patent No.: (45) Date of Patent: May 23, 2017 (54) (71) (72) (73) (*) (21) (22) (65) (60) (51) (52) (58) SWITCHING OF CONDUCTOR PAIR IN POWER
(12) Patent Application Publication (10) Pub. No.: US 2007/ A1
 (19) United States US 20070073878A1 (12) Patent Application Publication (10) Pub. No.: US 2007/0073878A1 Issa (43) Pub. Date: Mar. 29, 2007 (54) SYSTEM AND METHOD FOR LOWERING (52) U.S. Cl.... 709/225
(19) United States US 20070073878A1 (12) Patent Application Publication (10) Pub. No.: US 2007/0073878A1 Issa (43) Pub. Date: Mar. 29, 2007 (54) SYSTEM AND METHOD FOR LOWERING (52) U.S. Cl.... 709/225
(12) United States Patent
 US008176558B2 (12) United States Patent Ku Wamura (54) ANTI-VIRUS METHOD, COMPUTER, AND RECORDING MEDIUM (75) Inventor: Shinya Kuwamura, Kawasaki (JP) (73) Assignee: Fujitsu Limited, Kawasaki (JP) (*)
US008176558B2 (12) United States Patent Ku Wamura (54) ANTI-VIRUS METHOD, COMPUTER, AND RECORDING MEDIUM (75) Inventor: Shinya Kuwamura, Kawasaki (JP) (73) Assignee: Fujitsu Limited, Kawasaki (JP) (*)
Wireless devices supports in a simple environment
 USOO8868690B2 (12) United States Patent (10) Patent No.: US 8,868,690 B2 Tsao (45) Date of Patent: *Oct. 21, 2014 (54) SYSTEMAND METHOD FOR SUPPORT (52) U.S. Cl. (71) (72) (73) (*) (21) (22) (65) (63)
USOO8868690B2 (12) United States Patent (10) Patent No.: US 8,868,690 B2 Tsao (45) Date of Patent: *Oct. 21, 2014 (54) SYSTEMAND METHOD FOR SUPPORT (52) U.S. Cl. (71) (72) (73) (*) (21) (22) (65) (63)
(12) Patent Application Publication (10) Pub. No.: US 2010/ A1. Breiner et al. (43) Pub. Date: Mar. 4, 2010
 US 20100057686A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2010/0057686 A1 Breiner et al. (43) Pub. Date: Mar. 4, 2010 - (54) DEEP WEB SEARCH Publication Classification (76)
US 20100057686A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2010/0057686 A1 Breiner et al. (43) Pub. Date: Mar. 4, 2010 - (54) DEEP WEB SEARCH Publication Classification (76)
(12) Patent Application Publication (10) Pub. No.: US 2011/ A1
 US 2011 O270691A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0270691 A1 Park (43) Pub. Date: Nov. 3, 2011 (54) METHOD AND SYSTEM FOR PROVIDING Publication Classification
US 2011 O270691A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0270691 A1 Park (43) Pub. Date: Nov. 3, 2011 (54) METHOD AND SYSTEM FOR PROVIDING Publication Classification
Xying. GoD-12 ACL 1-1. (12) Patent Application Publication (10) Pub. No.: US 2009/ A1. (19) United States SUPPLIER POLICY DRIVER/-108 PLATFORM
 (19) United States US 20090172797A1 (12) Patent Application Publication (10) Pub. No.: US 2009/0172797 A1 Yao et al. (43) Pub. Date: Jul. 2, 2009 (54) METHOD AND SYSTEM FOR SECURING APPLICATION PROGRAMINTERFACES
(19) United States US 20090172797A1 (12) Patent Application Publication (10) Pub. No.: US 2009/0172797 A1 Yao et al. (43) Pub. Date: Jul. 2, 2009 (54) METHOD AND SYSTEM FOR SECURING APPLICATION PROGRAMINTERFACES
231 age sins N3 : as a. (12) United States Patent US 8,194,335 B2. Jun. 5, (45) Date of Patent: (10) Patent No.
 USOO8194,335B2 (12) United States Patent Hsueh (10) Patent No.: (45) Date of Patent: US 8,194,335 B2 Jun. 5, 2012 (54) (75) (73) (*) (21) (22) (65) (51) (52) (58) OPTICAL LENS ON WAFER LEVEL AND RELATED
USOO8194,335B2 (12) United States Patent Hsueh (10) Patent No.: (45) Date of Patent: US 8,194,335 B2 Jun. 5, 2012 (54) (75) (73) (*) (21) (22) (65) (51) (52) (58) OPTICAL LENS ON WAFER LEVEL AND RELATED
(12) United States Patent (10) Patent No.: US 7, B2
 USOO7941.543B2 (12) United States Patent (10) Patent No.: US 7,941.543 B2 Moussallam et al. (45) Date of Patent: May 10, 2011 (54) SYSTEMAND METHOD FOR MIGRATING 2002/0169781 A1* 11/2002 Poole et al....
USOO7941.543B2 (12) United States Patent (10) Patent No.: US 7,941.543 B2 Moussallam et al. (45) Date of Patent: May 10, 2011 (54) SYSTEMAND METHOD FOR MIGRATING 2002/0169781 A1* 11/2002 Poole et al....
(12) United States Patent (10) Patent No.: US 7, B2
 USOO7561411 B2 (12) United States Patent (10) Patent No.: US 7,561.411 B2 Johnson, Jr. (45) Date of Patent: Jul. 14, 2009 (54) UNINTERRUPTIBLE POWER DISTRIBUTION 7,400,066 B2 * 7/2008 Tassitino et al....
USOO7561411 B2 (12) United States Patent (10) Patent No.: US 7,561.411 B2 Johnson, Jr. (45) Date of Patent: Jul. 14, 2009 (54) UNINTERRUPTIBLE POWER DISTRIBUTION 7,400,066 B2 * 7/2008 Tassitino et al....
(12) Patent Application Publication (10) Pub. No.: US 2016/ A1
 (19) United States US 2016037 1322A1 (12) Patent Application Publication (10) Pub. No.: US 2016/0371322 A1 GUNTI et al. (43) Pub. Date: Dec. 22, 2016 (54) EFFICIENT MANAGEMENT OF LARGE (52) U.S. Cl. NUMBER
(19) United States US 2016037 1322A1 (12) Patent Application Publication (10) Pub. No.: US 2016/0371322 A1 GUNTI et al. (43) Pub. Date: Dec. 22, 2016 (54) EFFICIENT MANAGEMENT OF LARGE (52) U.S. Cl. NUMBER
(12) United States Patent (10) Patent No.: US 6,711,172 B1
 USOO6711 172B1 (12) United States Patent (10) Patent No.: US 6,711,172 B1 Li (45) Date of Patent: Mar. 23, 2004 (54) NETWORK PACKET ROUTING 6,275,492 B1 * 8/2001 Zhang... 370/392 6,331,983 B1 * 12/2001
USOO6711 172B1 (12) United States Patent (10) Patent No.: US 6,711,172 B1 Li (45) Date of Patent: Mar. 23, 2004 (54) NETWORK PACKET ROUTING 6,275,492 B1 * 8/2001 Zhang... 370/392 6,331,983 B1 * 12/2001
Medina (45) Date of Patent: Aug. 18, (54) FOOT CONTROLLED COMPUTER MOUSE 2004/ A1* 11/2004 Koda et al , 183
 (12) United States Patent US007576729B2 (10) Patent No.: Medina (45) Date of Patent: Aug. 18, 2009 (54) FOOT CONTROLLED COMPUTER MOUSE 2004/022.7741 A1* 11/2004 Koda et al.... 345, 183 WITH FINGER CLICKERS
(12) United States Patent US007576729B2 (10) Patent No.: Medina (45) Date of Patent: Aug. 18, 2009 (54) FOOT CONTROLLED COMPUTER MOUSE 2004/022.7741 A1* 11/2004 Koda et al.... 345, 183 WITH FINGER CLICKERS
(12) Patent Application Publication (10) Pub. No.: US 2005/ A1
 (19) United States US 2005O125217A1 (12) Patent Application Publication (10) Pub. No.: US 2005/0125217 A1 MaZOr (43) Pub. Date: Jun. 9, 2005 (54) SERVER-BASED SPELL CHECK ENGINE (52) U.S. Cl.... 704/1
(19) United States US 2005O125217A1 (12) Patent Application Publication (10) Pub. No.: US 2005/0125217 A1 MaZOr (43) Pub. Date: Jun. 9, 2005 (54) SERVER-BASED SPELL CHECK ENGINE (52) U.S. Cl.... 704/1
(12) Patent Application Publication (10) Pub. No.: US 2003/ A1
 (19) United States US 2003.0109252A1 (12) Patent Application Publication (10) Pub. No.: US 2003/0109252 A1 Prentice et al. (43) Pub. Date: Jun. 12, 2003 (54) SYSTEM AND METHOD OF CODEC EMPLOYMENT INA CELLULAR
(19) United States US 2003.0109252A1 (12) Patent Application Publication (10) Pub. No.: US 2003/0109252 A1 Prentice et al. (43) Pub. Date: Jun. 12, 2003 (54) SYSTEM AND METHOD OF CODEC EMPLOYMENT INA CELLULAR
(12) Patent Application Publication (10) Pub. No.: US 2014/ A1
 US 20140O82324A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0082324 A1 Elhamias et al. (43) Pub. Date: Mar. 20, 2014 (54) METHOD AND STORAGE DEVICE FOR (52) U.S. Cl.
US 20140O82324A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0082324 A1 Elhamias et al. (43) Pub. Date: Mar. 20, 2014 (54) METHOD AND STORAGE DEVICE FOR (52) U.S. Cl.
(12) Patent Application Publication (10) Pub. No.: US 2005/ A1
 (19) United States US 20050289474A1 (12) Patent Application Publication (10) Pub. No.: Master et al. (43) Pub. Date: Dec. 29, 2005 (54) PRESENTATION OF INFORMATION BASED (52) U.S. Cl.... 715/765; 715/744;
(19) United States US 20050289474A1 (12) Patent Application Publication (10) Pub. No.: Master et al. (43) Pub. Date: Dec. 29, 2005 (54) PRESENTATION OF INFORMATION BASED (52) U.S. Cl.... 715/765; 715/744;
(12) United States Patent
 US007617236B2 (12) United States Patent Gaurav et al. (10) Patent No.: (45) Date of Patent: Nov. 10, 2009 (54) METHOD AND SYSTEM FOR DISPLAYING RESULTS OF A DYNAMIC SEARCH (75) Inventors: Vishal Gaurav,
US007617236B2 (12) United States Patent Gaurav et al. (10) Patent No.: (45) Date of Patent: Nov. 10, 2009 (54) METHOD AND SYSTEM FOR DISPLAYING RESULTS OF A DYNAMIC SEARCH (75) Inventors: Vishal Gaurav,
(12) Patent Application Publication (10) Pub. No.: US 2012/ A1. Menezes et al. (43) Pub. Date: Jun. 28, 2012
 US 20120167185A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0167185 A1 Menezes et al. (43) Pub. Date: Jun. 28, 2012 (54) REGISTRATION AND NETWORKACCESS Publication Classification
US 20120167185A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0167185 A1 Menezes et al. (43) Pub. Date: Jun. 28, 2012 (54) REGISTRATION AND NETWORKACCESS Publication Classification
Core Wireless Licensing S.a.r.l. v. Apple, Inc. Doc. 1 Att. 3 EXHIBIT 2. Dockets.Justia.com
 Core Wireless Licensing S.a.r.l. v. Apple, Inc. Doc. 1 Att. 3 EXHIBIT 2 Dockets.Justia.com 111111 1111111111111111111111111111111111111111111111111111111111111 US007606910B2 (12) United States Patent Bajko
Core Wireless Licensing S.a.r.l. v. Apple, Inc. Doc. 1 Att. 3 EXHIBIT 2 Dockets.Justia.com 111111 1111111111111111111111111111111111111111111111111111111111111 US007606910B2 (12) United States Patent Bajko
(12) Patent Application Publication (10) Pub. No.: US 2012/ A1
 (19) United States US 2012O100868A1 (12) Patent Application Publication (10) Pub. No.: US 2012/0100868 A1 KM et al. (43) Pub. Date: Apr. 26, 2012 (54) METHOD AND APPARATUS FOR Publication Classification
(19) United States US 2012O100868A1 (12) Patent Application Publication (10) Pub. No.: US 2012/0100868 A1 KM et al. (43) Pub. Date: Apr. 26, 2012 (54) METHOD AND APPARATUS FOR Publication Classification
(12) Patent Application Publication (10) Pub. No.: US 2005/ A1
 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0192794A1 Ertemalp et al. US 2005O192794A1 (43) Pub. Date: Sep. 1, 2005 (54) (75) (73) (21) (22) (63) SYSTEMAND METHOD FOR
(19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0192794A1 Ertemalp et al. US 2005O192794A1 (43) Pub. Date: Sep. 1, 2005 (54) (75) (73) (21) (22) (63) SYSTEMAND METHOD FOR
(12) United States Patent (10) Patent No.: US 7,917,832 B2
 US007.917832B2 (12) United States Patent (10) Patent No.: US 7,917,832 B2 Hsieh et al. (45) Date of Patent: Mar. 29, 2011 (54) APPARATUS FOR IMPROVING DATA 6,725,321 B1 4/2004 Sinclair et al.... T11 103
US007.917832B2 (12) United States Patent (10) Patent No.: US 7,917,832 B2 Hsieh et al. (45) Date of Patent: Mar. 29, 2011 (54) APPARATUS FOR IMPROVING DATA 6,725,321 B1 4/2004 Sinclair et al.... T11 103
(12) (10) Patent No.: US 9,588,741 B2. Liberant (45) Date of Patent: Mar. 7, 2017
 United States Patent USOO9588.741B2 (12) () Patent No.: Liberant (45) Date of Patent: Mar. 7, 2017 (54) METHODS, APPARATUSES AND 2006/0059464 A1 3/2006 Jameson... 717/120 COMPUTER PROGRAMI PRODUCTS FOR
United States Patent USOO9588.741B2 (12) () Patent No.: Liberant (45) Date of Patent: Mar. 7, 2017 (54) METHODS, APPARATUSES AND 2006/0059464 A1 3/2006 Jameson... 717/120 COMPUTER PROGRAMI PRODUCTS FOR
US 7.663,338 B2. Feb. 16, (45) Date of Patent: (10) Patent No.: Guthrie et al. used to receive a USB bus voltage from the USB interface and (51)
 USOO7663338B2 (12) United States Patent Guthrie et al. (10) Patent No.: (45) Date of Patent: US 7.663,338 B2 Feb. 16, 2010 (54) (75) (73) (*) (21) (22) (65) (60) (51) (52) (58) (56) METHOD AND APPARATUS
USOO7663338B2 (12) United States Patent Guthrie et al. (10) Patent No.: (45) Date of Patent: US 7.663,338 B2 Feb. 16, 2010 (54) (75) (73) (*) (21) (22) (65) (60) (51) (52) (58) (56) METHOD AND APPARATUS
(12) United States Patent
 US007107617B2 (12) United States Patent Hursey et al. (10) Patent No.: (45) Date of Patent: Sep. 12, 2006 (54) MALWARE SCANNING OF COMPRESSED COMPUTER S (75) Inventors: Nell John Hursey, Hertfordshire
US007107617B2 (12) United States Patent Hursey et al. (10) Patent No.: (45) Date of Patent: Sep. 12, 2006 (54) MALWARE SCANNING OF COMPRESSED COMPUTER S (75) Inventors: Nell John Hursey, Hertfordshire
(12) United States Patent
 USOO7600.040B1 (12) United States Patent Henry et al. (54) BUFFERING PACKETS DESTINED FORA MOBILE DEVICE WHILE THE MOBILE DEVICE MOVES FROM ONE NETWORK TO ANOTHER NETWORK TO PREVENT HANDOFF PACKET LOSS
USOO7600.040B1 (12) United States Patent Henry et al. (54) BUFFERING PACKETS DESTINED FORA MOBILE DEVICE WHILE THE MOBILE DEVICE MOVES FROM ONE NETWORK TO ANOTHER NETWORK TO PREVENT HANDOFF PACKET LOSS
(12) United States Patent
 USOO9729447B2 (12) United States Patent Wang et al. (10) Patent No.: (45) Date of Patent: US 9,729.447 B2 *Aug. 8, 2017 (54) APPARATUS AND METHOD FOR (71) (72) (73) (*) (21) (22) (65) (63) (60) (51) (52)
USOO9729447B2 (12) United States Patent Wang et al. (10) Patent No.: (45) Date of Patent: US 9,729.447 B2 *Aug. 8, 2017 (54) APPARATUS AND METHOD FOR (71) (72) (73) (*) (21) (22) (65) (63) (60) (51) (52)
(12) Patent Application Publication (10) Pub. No.: US 2016/ A1
 US 20160261583A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2016/0261583 A1 ZHANG (43) Pub. Date: Sep. 8, 2016 (54) METHOD AND APPARATUS FOR USER Publication Classification
US 20160261583A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2016/0261583 A1 ZHANG (43) Pub. Date: Sep. 8, 2016 (54) METHOD AND APPARATUS FOR USER Publication Classification
(12) United States Patent
 (12) United States Patent US007 140922B2 (10) Patent No.: US 7,140,922 B2 Lulu et al. (45) Date of Patent: Nov. 28, 2006 (54) MULTI-OUTLET AC/DC ADAPTER (56) References Cited (75) Inventors: Daniel V.
(12) United States Patent US007 140922B2 (10) Patent No.: US 7,140,922 B2 Lulu et al. (45) Date of Patent: Nov. 28, 2006 (54) MULTI-OUTLET AC/DC ADAPTER (56) References Cited (75) Inventors: Daniel V.
(12) Patent Application Publication (10) Pub. No.: US 2011/ A1. LYRA et al. (43) Pub. Date: Mar. 24, 2011
 (19) United States US 2011 0072284A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0072284 A1 LYRA et al. (43) Pub. Date: Mar. 24, 2011 (54) METHODS OF PREPARING A POWER (52) U.S. Cl.... 713/320,710/32;
(19) United States US 2011 0072284A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0072284 A1 LYRA et al. (43) Pub. Date: Mar. 24, 2011 (54) METHODS OF PREPARING A POWER (52) U.S. Cl.... 713/320,710/32;
(12) United States Patent (10) Patent No.: US 7,679,316 B2
 USOO7679.316B2 (12) United States Patent (10) Patent No.: US 7,679,316 B2 Guthrie et al. (45) Date of Patent: Mar. 16, 2010 (54) METHOD AND APPARATUS FOR 6,21 1,649 B1 4/2001 Matsuda... 320,115 CONTROLLING
USOO7679.316B2 (12) United States Patent (10) Patent No.: US 7,679,316 B2 Guthrie et al. (45) Date of Patent: Mar. 16, 2010 (54) METHOD AND APPARATUS FOR 6,21 1,649 B1 4/2001 Matsuda... 320,115 CONTROLLING
(12) Patent Application Publication (10) Pub. No.: US 2008/ A1
 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2008/0317029 A1 TASAK et al. US 20080317029A1 (43) Pub. Date: Dec. 25, 2008 (54) (75) (73) (21) (22) (60) UNICAST/MULTICAST SYSTEM
(19) United States (12) Patent Application Publication (10) Pub. No.: US 2008/0317029 A1 TASAK et al. US 20080317029A1 (43) Pub. Date: Dec. 25, 2008 (54) (75) (73) (21) (22) (60) UNICAST/MULTICAST SYSTEM
United States Patent (19) Boltz et al.
 United States Patent (19) Boltz et al. 54 SYSTEM AND METHOD FOR TIME DEFINED DELIVERY OF SHORT MESSAGE SERVICE MESSAGES 75 Inventors: David Boltz; David B. Westbrook, both of Garland, TeX. 73 Assignee:
United States Patent (19) Boltz et al. 54 SYSTEM AND METHOD FOR TIME DEFINED DELIVERY OF SHORT MESSAGE SERVICE MESSAGES 75 Inventors: David Boltz; David B. Westbrook, both of Garland, TeX. 73 Assignee:
INSTANTTEXT REPLY SAVED MESSAGES NEW MESSAGE SETTINGS. (12) Patent Application Publication (10) Pub. No.: US 2007/ A1. (19) United States
 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0238474 A1 Ballas et al. US 20070238474A1 (43) Pub. Date: Oct. 11, 2007 (54) INSTANT TEXT REPLY FOR MOBILE TELEPHONY DEVICES
(19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0238474 A1 Ballas et al. US 20070238474A1 (43) Pub. Date: Oct. 11, 2007 (54) INSTANT TEXT REPLY FOR MOBILE TELEPHONY DEVICES
(12) United States Patent
 US00788.5654B2 (12) United States Patent Fade () Patent No.: () Date of Patent: Feb. 8, 2011 (54) DYNAMICCARRIER SELECTION (75) Inventor: Tony Fadell, Portola Valley, CA (US) (73) Assignee: Apple Inc.,
US00788.5654B2 (12) United States Patent Fade () Patent No.: () Date of Patent: Feb. 8, 2011 (54) DYNAMICCARRIER SELECTION (75) Inventor: Tony Fadell, Portola Valley, CA (US) (73) Assignee: Apple Inc.,
(12) United States Patent
 USOO7490248B1 (12) United States Patent Valfridsson et al. (10) Patent No.: (45) Date of Patent: US 7.490,248 B1 Feb. 10, 2009 (54) METHOD FOR REENCRYPTION OF A DATABASE (75) Inventors: Thomas Valfridsson,
USOO7490248B1 (12) United States Patent Valfridsson et al. (10) Patent No.: (45) Date of Patent: US 7.490,248 B1 Feb. 10, 2009 (54) METHOD FOR REENCRYPTION OF A DATABASE (75) Inventors: Thomas Valfridsson,
(12) United States Patent (10) Patent No.: US 6,446,087 B1. Lai (45) Date of Patent: Sep. 3, 2002
 USOO6446087B1 (12) United States Patent (10) Patent No.: Lai (45) Date of Patent: Sep. 3, 2002 (54) SYSTEM FOR MAINTAINING THE (74) Attorney, Agent, or Firm-Patton Boggs, LLP INTEGRITY OF APPLICATION DATA
USOO6446087B1 (12) United States Patent (10) Patent No.: Lai (45) Date of Patent: Sep. 3, 2002 (54) SYSTEM FOR MAINTAINING THE (74) Attorney, Agent, or Firm-Patton Boggs, LLP INTEGRITY OF APPLICATION DATA
(12) United States Patent (10) Patent No.: US 6,237,112 B1
 USOO62371.12B1 (12) United States Patent (10) Patent No.: Yo0 et al. (45) Date of Patent: May 22, 2001 (54) SCSI DEVICE AVAILABLE FOR BREAKDOWN PREDICTION AND 5,966,510 * 10/1999 Carbonneau et al.... 714/44
USOO62371.12B1 (12) United States Patent (10) Patent No.: Yo0 et al. (45) Date of Patent: May 22, 2001 (54) SCSI DEVICE AVAILABLE FOR BREAKDOWN PREDICTION AND 5,966,510 * 10/1999 Carbonneau et al.... 714/44
(12) Patent Application Publication (10) Pub. No.: US 2006/ A1
 (19) United States US 20060041739A1 (12) Patent Application Publication (10) Pub. No.: US 2006/0041739 A1 Iwakura et al. (43) Pub. Date: Feb. 23, 2006 (54) MEMORY DUMP GENERATION WITH (52) U.S. Cl....
(19) United States US 20060041739A1 (12) Patent Application Publication (10) Pub. No.: US 2006/0041739 A1 Iwakura et al. (43) Pub. Date: Feb. 23, 2006 (54) MEMORY DUMP GENERATION WITH (52) U.S. Cl....
(12) Patent Application Publication (10) Pub. No.: US 2013/ A1. Large et al. (43) Pub. Date: Aug. 8, 2013
 (19) United States US 201302011 12A1 (12) Patent Application Publication (10) Pub. No.: US 2013/0201112 A1 Large et al. (43) Pub. Date: Aug. 8, 2013 (54) LOW-LATENCY TOUCH-INPUT DEVICE (52) U.S. Cl. USPC...
(19) United States US 201302011 12A1 (12) Patent Application Publication (10) Pub. No.: US 2013/0201112 A1 Large et al. (43) Pub. Date: Aug. 8, 2013 (54) LOW-LATENCY TOUCH-INPUT DEVICE (52) U.S. Cl. USPC...
(12) Patent Application Publication (10) Pub. No.: US 2006/ A1
 (19) United States US 2006003.1337A1 (12) Patent Application Publication (10) Pub. No.: US 2006/0031337 A1 Kim (43) Pub. Date: Feb. 9, 2006 (54) METHODS AND SYSTEMS FOR BROADCASTING OFFERS OVER ELECTRONIC
(19) United States US 2006003.1337A1 (12) Patent Application Publication (10) Pub. No.: US 2006/0031337 A1 Kim (43) Pub. Date: Feb. 9, 2006 (54) METHODS AND SYSTEMS FOR BROADCASTING OFFERS OVER ELECTRONIC
(12) United States Patent (10) Patent No.: US 6,526,272 B1
 USOO6526272B1 (12) United States Patent (10) Patent No.: Bansal et al. (45) Date of Patent: Feb. 25, 2003 (54) REDUCING CALLING COSTS FOR 6,167,250 A * 12/2000 Rahman et al... 455/408 WIRELESS PHONES USING
USOO6526272B1 (12) United States Patent (10) Patent No.: Bansal et al. (45) Date of Patent: Feb. 25, 2003 (54) REDUCING CALLING COSTS FOR 6,167,250 A * 12/2000 Rahman et al... 455/408 WIRELESS PHONES USING
(12) Ulllted States Patent (10) Patent N0.: US 7,596,216 B2 Pearson et al. (45) Date of Patent: *Sep. 29, 2009
 US007596216B2 (12) Ulllted States Patent (10) Patent N0.: US 7,596,216 B2 Pearson et al. (45) Date of Patent: *Sep. 29, 2009 (54) SYSTEM AND METHOD FOR IDENTIFYING (51) Int. Cl. REDIRECTED CALLS H04M 3/42
US007596216B2 (12) Ulllted States Patent (10) Patent N0.: US 7,596,216 B2 Pearson et al. (45) Date of Patent: *Sep. 29, 2009 (54) SYSTEM AND METHOD FOR IDENTIFYING (51) Int. Cl. REDIRECTED CALLS H04M 3/42
(12) Patent Application Publication (10) Pub. No.: US 2010/ A1
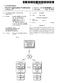 US 20100050092A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2010/0050092 A1 Williams et al. (43) Pub. Date: Feb. 25, 2010 (54) CONTENT SHARING AND INSTANT (21) Appl. No.:
US 20100050092A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2010/0050092 A1 Williams et al. (43) Pub. Date: Feb. 25, 2010 (54) CONTENT SHARING AND INSTANT (21) Appl. No.:
United States Patent (19) O Brien
 United States Patent (19) O Brien 54) HOLOGRAPHIC DIRECT MANIPULATION INTERFACE 76 Inventor: Wayne P. O'Brien, 507 N. Roosevelt Blvd., C 315, Falls Church, Va. 22044 21 Appl. No.: 09/001,101 22 Filed:
United States Patent (19) O Brien 54) HOLOGRAPHIC DIRECT MANIPULATION INTERFACE 76 Inventor: Wayne P. O'Brien, 507 N. Roosevelt Blvd., C 315, Falls Church, Va. 22044 21 Appl. No.: 09/001,101 22 Filed:
(12) (10) Patent No.: US 7, B1. Liu (45) Date of Patent: Aug. 22, 2006 (54) INTERNET FILE SAFETY INFORMATION OTHER PUBLICATIONS
 United States Patent US007096493B1 (12) (10) Patent No.: US 7,096.493 B1 Liu (45) Date of Patent: Aug. 22, 2006 (54) INTERNET FILE SAFETY INFORMATION OTHER PUBLICATIONS CENTER A software infrastructure
United States Patent US007096493B1 (12) (10) Patent No.: US 7,096.493 B1 Liu (45) Date of Patent: Aug. 22, 2006 (54) INTERNET FILE SAFETY INFORMATION OTHER PUBLICATIONS CENTER A software infrastructure
wo W /1997 * cited by examiner
 111111 1111111111111111111111111111111111111111111111111111111111111 US006963980Bl (12) United States Patent Matts son (10) Patent No.: US 6,963,980 Bl (45) Date of Patent: Nov. 8, 2005 (54) COMBINED HARDWARE
111111 1111111111111111111111111111111111111111111111111111111111111 US006963980Bl (12) United States Patent Matts son (10) Patent No.: US 6,963,980 Bl (45) Date of Patent: Nov. 8, 2005 (54) COMBINED HARDWARE
(12) United States Patent (10) Patent No.: US 7,991,882 B1. Parkhill (45) Date of Patent: Aug. 2, 2011
 US007991882B1 (12) United States Patent (10) Patent No.: US 7,991,882 B1 Parkhill (45) Date of Patent: Aug. 2, 2011 (54) COMMUNICATIONS NETWORK WITH OTHER PUBLICATIONS FLOW CONTROL (75) Inventor: Robert
US007991882B1 (12) United States Patent (10) Patent No.: US 7,991,882 B1 Parkhill (45) Date of Patent: Aug. 2, 2011 (54) COMMUNICATIONS NETWORK WITH OTHER PUBLICATIONS FLOW CONTROL (75) Inventor: Robert
(12) Patent Application Publication (10) Pub. No.: US 2016/ A1
 US 2016O156189A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2016/0156189 A1 Ci (43) Pub. Date: Jun. 2, 2016 (54) CLOUD BASED ENERGY SYSTEM (52) U.S. Cl. CPC. H02J 3/32 (2013.01);
US 2016O156189A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2016/0156189 A1 Ci (43) Pub. Date: Jun. 2, 2016 (54) CLOUD BASED ENERGY SYSTEM (52) U.S. Cl. CPC. H02J 3/32 (2013.01);
(12) Patent Application Publication (10) Pub. No.: US 2002/ A1
 (19) United States US 20020077080A1 (12) Patent Application Publication (10) Pub. No.: US 2002/0077080A1 Greene (43) Pub. Date: (54) INSTANT MESSAGE USER LOCATION TRACKING SYSTEM (76) Inventor: Kenneth
(19) United States US 20020077080A1 (12) Patent Application Publication (10) Pub. No.: US 2002/0077080A1 Greene (43) Pub. Date: (54) INSTANT MESSAGE USER LOCATION TRACKING SYSTEM (76) Inventor: Kenneth
United States Patent 19
 United States Patent 19 O'Kelly 54. SYSTEM FOR AND ED S I75 Inventor: Cathal P. O'Kelly, Maidenhead, United Kingdom 73 Assignee: Northern Telecom Limited, Montreal, Canada 21 22 Appl. No.: 539,30 Filed:
United States Patent 19 O'Kelly 54. SYSTEM FOR AND ED S I75 Inventor: Cathal P. O'Kelly, Maidenhead, United Kingdom 73 Assignee: Northern Telecom Limited, Montreal, Canada 21 22 Appl. No.: 539,30 Filed:
(12) United States Patent (10) Patent No.: US 6,993,573 B2
 USOO6993573B2 (12) United States Patent (10) Patent No.: US 6,993,573 B2 Hunter (45) Date of Patent: Jan. 31, 2006 (54) AUTOMATIC ACCESS OF INTERNET 5,640,193 A 6/1997 Wellner CONTENT WITH A CAMERA-ENABLED
USOO6993573B2 (12) United States Patent (10) Patent No.: US 6,993,573 B2 Hunter (45) Date of Patent: Jan. 31, 2006 (54) AUTOMATIC ACCESS OF INTERNET 5,640,193 A 6/1997 Wellner CONTENT WITH A CAMERA-ENABLED
(12) Patent Application Publication (10) Pub. No.: US 2007/ A1
 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0290787 A1 Fiata et al. US 20070290787A1 (43) Pub. Date: (54) (76) (21) (22) (60) SYSTEMIS AND METHODS FOR GROUP MESSAGING
(19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0290787 A1 Fiata et al. US 20070290787A1 (43) Pub. Date: (54) (76) (21) (22) (60) SYSTEMIS AND METHODS FOR GROUP MESSAGING
(12) Patent Application Publication (10) Pub. No.: US 2005/ A1
 US 2005O114452A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0114452 A1 Prakash (43) Pub. Date: May 26, 2005 (54) METHOD AND APPARATUS TO BLOCK (22) Filed: Nov. 3, 2003
US 2005O114452A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0114452 A1 Prakash (43) Pub. Date: May 26, 2005 (54) METHOD AND APPARATUS TO BLOCK (22) Filed: Nov. 3, 2003
(12) United States Patent (10) Patent No.: US 7,158,627 B1
 US007 158627 B1 (12) United States Patent () Patent No.: Lu (45) Date of Patent: Jan. 2, 2007 (54) METHOD AND SYSTEM FOR INHIBITING (56) References Cited SOFTSWITCH OVERLOAD U.S. PATENT DOCUMENTS (75)
US007 158627 B1 (12) United States Patent () Patent No.: Lu (45) Date of Patent: Jan. 2, 2007 (54) METHOD AND SYSTEM FOR INHIBITING (56) References Cited SOFTSWITCH OVERLOAD U.S. PATENT DOCUMENTS (75)
(12) Patent Application Publication (10) Pub. No.: US 2010/ A1. LOW et al. (43) Pub. Date: Jul. 15, 2010
 US 20100178904A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2010/0178904 A1 LOW et al. (43) Pub. Date: Jul. 15, 2010 (54) MESSAGING SERVICE SUBSCRIPTION (30) Foreign Application
US 20100178904A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2010/0178904 A1 LOW et al. (43) Pub. Date: Jul. 15, 2010 (54) MESSAGING SERVICE SUBSCRIPTION (30) Foreign Application
(12) Patent Application Publication (10) Pub. No.: US 2016/ A1
 US 20160364902A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2016/0364902 A1 Hong et al. (43) Pub. Date: (54) HIGH QUALITY EMBEDDED GRAPHICS (52) U.S. Cl. FOR REMOTE VISUALIZATION
US 20160364902A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2016/0364902 A1 Hong et al. (43) Pub. Date: (54) HIGH QUALITY EMBEDDED GRAPHICS (52) U.S. Cl. FOR REMOTE VISUALIZATION
(12) Patent Application Publication (10) Pub. No.: US 2002/ A1
 (19) United States US 2002009 1840A1 (12) Patent Application Publication (10) Pub. No.: US 2002/0091840 A1 Pulier et al. (43) Pub. Date: Jul. 11, 2002 (54) REAL-TIME OPTIMIZATION OF STREAMING MEDIA FROM
(19) United States US 2002009 1840A1 (12) Patent Application Publication (10) Pub. No.: US 2002/0091840 A1 Pulier et al. (43) Pub. Date: Jul. 11, 2002 (54) REAL-TIME OPTIMIZATION OF STREAMING MEDIA FROM
(12) Patent Application Publication (10) Pub. No.: US 2004/ A1
 (19) United States US 2004O231004A1 (12) Patent Application Publication (10) Pub. No.: US 2004/0231004 A1 Seo (43) Pub. Date: (54) HTTP BASED VIDEO STREAMING APPARATUS AND METHOD IN MOBILE COMMUNICATION
(19) United States US 2004O231004A1 (12) Patent Application Publication (10) Pub. No.: US 2004/0231004 A1 Seo (43) Pub. Date: (54) HTTP BASED VIDEO STREAMING APPARATUS AND METHOD IN MOBILE COMMUNICATION
