Defining Unified CCX CTI Messages
|
|
|
- Dayna Foster
- 5 years ago
- Views:
Transcription
1 This chapter includes the following topics that you need to understand in order to correctly define Unified CCX CTI Messages:, page 2 Alignment of data elements, page 6 Pack and unpack a Unified CCX CTI Message, page 6 Message classification, page 7 Message type definitions, page 8 1
2 A Unified CCX CTI message is a byte array of fields containing a Message Header and a Message Body. Figure 1: Diagram of a Unified CCX CTI Protocol Message, on page 2 shows its structure. Figure 1: Diagram of a Unified CCX CTI Protocol Message A Unified CCX CTI message is structured as follows. The numbered items refer to the numbers in Figure 1: Diagram of a Unified CCX CTI Protocol Message, on page 2: 1. Message Header The message header is a required field. It contains a 4-byte MessageTypeID field and a 4-byte BodyLength field. The message header is in what is called the Message HeaDeR (MHDR) data format, which is a common format used for message headers that precede all messages exchanged between a client and a server. Message header data format defines the MHDR format. 2. BodyLength The BodyLength field contains the length of the MessageBody in bytes. 2
3 3. MessageTypeID The MessageTypeID field identifies the type of message and has a unique numeric value used to determine the format of the remainder of the message. It also indicates if the message includes a floating part, and if so, what types of floating fields may appear within it. The MessageTypeID field name usually indicates the purpose of the message. Example message types are OPEN_REQ and HEARTBEAT_REQ. Table 1 defines all the message types in the message set with a unique MessageTypeID number that identifies each message type. To enter a message type into a message header, enter the MessageTypeID number specified for that message in Table Message Body A message body consists of either a fixed part only or a fixed part and a floating part. The maximum size of a message body is 256 bytes. 5. Fixed Part All the fields in the fixed part of a message are required and have both a fixed order and a fixed size. 6. Fixed Fields Fixed fields begin after the message header. Every field defined in the fixed part of a message is required and must be defined in the order given with the defined size for the field. That is, all the field sizes in the fixed part of a message must be the size specified by the message definition. For example, if there are 3 fields of 4 bytes in the fixed part of the message and the second field is a reserved one, you need to specify that the third field starts at byte 9, even though you are not using bytes 5 through 8. A field in the fixed part of a message is identified by its location in the fixed part of the message. Some messages have only fixed fields. 3
4 7. Fixed Field Data Fixed Fields in messages are defined using a special set of data types. These are: CHAR UCHAR SHORT USHORT INT UINT BOOL TIME For definitions of these data types, see Message field data types. All numeric data longer than one byte is transmitted in order of the most significant byte to the least significant byte. This is the canonical network byte order defined by TCP/IP standards. 8. Floating Part (Variable in length and sometimes optional) The message floating part contains floating fields that follow the fixed fields. The floating part is a required part of a message having floating fields. 9. Floating Fields The length of a floating field is variable. It can be up to or less than that maximum size specified in the message definition. Since these fields can be variable in length, the position of a floating field in a message can be said to float, depending on the length of the other floating fields in the message. Floating fields are packed together in the floating part of the message. The FieldDataID of one floating field immediately follows the data of the previous field. The message length (in the message header) indicates the end of the message. Some floating fields may be optional. In general, with one exception, floating fields may appear in any order in the floating part of a message, although, it is better to follow the order defined in the message. The exception is the situation in which a floating field can appear more than once, that is, when the field is a member of a list. In this case, a fixed field in the message indicates the number of list entries present. 4
5 10. FieldDataID A floating field begins with a one-byte FieldDataID identifying the field type. Its data type is UCHAR. Table 1 numerically lists all the available FieldDataID types. Some floating fields are reserved. In the Message Type Definitions, the square bracketed subscript number ending the Field Names for the data in the Floating Part of the message descriptions is the FieldDataID for that field. For example AgentID[194] means that 194 is the FieldDataID for the AgentID field. A field FieldDataID is a global ID not specific to a message. More than one message can use the same DataID. For example, the AGENT_STATE_EVENT and the SET_AGENT_STATE_REQ messages can both use the AGENT_ID FieldDataID. 11. FieldDataLength 12. Data Following the FieldDataID is a one-byte FieldDataLength field indicating the number of bytes, n, of data in the data subfield (excluding FieldDataID and FieldDataLength). Its data type is UCHAR. The data immediately follows the FieldLength subfield. The maximum data size listed in each message definition for each floating field is the maximum number of data bytes allowed. This size, however, does not include the FieldDataID and the FieldLength bytes. For STRING data, the maximum size includes the null termination byte. Any data type listed in Message field data types, (with the exception of the MHDR (Message Header) data type) can appear in the floating part of a message. However, the following four types of data appear only in the floating part: STRING[n] UNSPEC[n] NAMEDVAR NAMEDARRAY For the definitions of all the message data types, see Message field data types. 5
6 Alignment of data elements Alignment of data elements The messages described in this document are sent as a stream of bytes. If the client application uses data structures to represent the messages, take care that the data structures do not have padding inserted to align elements on particular boundaries, such as aligning 32-bit integers so that they are located on a 4-byte boundary. Pack and unpack a Unified CCX CTI Message You may use data structures in your choice of programming languages to represent CTI messages. For example, in C++, you may use a class to represent a message type. The process of converting this data structure to a byte array to be sent to the Unified CCX server is called packing. The reverse process is called unpacking. The following are typical steps to do packing and unpacking. Pack a CTI message Procedure Step 1 Step 2 Step 3 Step 4 Step 5 Step 6 Allocate a continuous block of memory. Add the message header to the beginning of the memory block. Reserve a 4-byte place for the BodyLength field to fill in later when you accurately know the message body length (when you have added all the Body fields). Convert the 4-byte MessageTypeID to network-byte order and add it to the memory block after the reserved BodyLength field. Convert each of the fixed message fields, one by one, to network-byte order, if needed, and add them to the memory block in the appropriate order according to the MessageTypeID. Convert the floating data fields, one by one, if needed, to the network-byte order. Add the fields in the floating part of the message into the memory block without any gap between the fields. Repeat this process to pack the rest of the floating fields until the end of the message. Remember to convert the BodyLength bytes from host-byte order to network-byte order. Then update the BodyLength field in the message header part of the memory block after all the floating fields are added to accurately reflect the message body length. 6
7 Unpack a CTI message Unpack a CTI message Procedure Step 1 Step 2 Step 3 Step 4 Step 5 Step 6 Step 7 Read the first 4 bytes as an unsigned integer. This value is the message BodyLength. Remember to convert the BodyLength bytes from network-byte order to host-byte order. Make sure all the BodyLength bytes are available from the network before further unpacking. Read the next 4 bytes and convert them to a host-byte-order unsigned integer. This value is the MessageTypeID. Based on the MessageTypeID, you can then use the message body definition to find out the fixed fields and their appropriate order in the fixed part of the message. Read each field, one by one, and convert it to host data-byte order, if needed. Based on the FieldDataID value and its definition, convert the floating data fields to the host-byte order, if necessary. Repeat this process to unpack the rest of floating fields until the end of the message. The end of the message is determined by the Message BodyLength. Message classification The Unified CCX CTI Protocol messages can be classified in different ways: As Solicited (initiated by the client) or Unsolicited (initiated by Unified CCX). Solicited Messages: Messages that the client initiates and for which the client expects a response (called a confirmation message) from Unified CCX. Unsolicited Messages: Messages sent by Unified CCX that the client does not initiate and that do not require a confirmation. A bridge mode client can receive all unsolicited messages. In addition to unsolicited messages, a client receives confirmation (solicited) messages only for the requests it makes. A bridge mode client does not receive confirmation messages for other clients requests. A client s request message triggers a solicited message response. In addition a client s request message may also trigger an unsolicited message. For example, the client s request could trigger an agent state event (an unsolicited message) as well as a confirmation message for the request (a solicited message). By function You can classify messages by function as: Session Management Messages Messages for managing a session (for initializing, maintaining, and closing a session) Configuration Messages Messages for sharing server configuration data (initial and updated) with the server s clients. Agent State Messages 7
8 Message type definitions Messages that allow the client to control the agent state, such as, for example, login and logout. Call Control Messages Messages that allow the client to control inbound and outbound calls. Call Events Messages Messages that describe what is happening to a call; for example, call established and call begun. Also messages that update call data in call context variables while the call is active. Miscellaneous Service and Query Status Messages Miscellaneous unsolicited event messages and solicited messages available to all clients. And, messages that query the status of an agent, a queue, or a device. Message type definitions All the message types in the Unified CCX Protocol message set are listed and defined in Message type definitions When creating a message, you must use the definition specified for the type of message you are creating. A version number next to a field name in a message type definition indicates that the field is used in the CTI protocol beginning with the specified version number. 8
Cisco Unified Contact Center Express CTI Protocol Developer Guide Release 9.0(1)
 Cisco Unified Contact Center Express CTI Protocol Developer Guide Release 9.0(1) First Published: July 06, 01 Last Modified: May 16, 013 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive
Cisco Unified Contact Center Express CTI Protocol Developer Guide Release 9.0(1) First Published: July 06, 01 Last Modified: May 16, 013 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive
CTI Server Overview. How CTI Server Works
 How CTI Server Works, page 1 Unified CCE Call Processing, page 2 CTI Server Configurations, page 4 CTI Server Message Set, page 7 How CTI Server Works The CTI Server provides an interface between Unified
How CTI Server Works, page 1 Unified CCE Call Processing, page 2 CTI Server Configurations, page 4 CTI Server Message Set, page 7 How CTI Server Works The CTI Server provides an interface between Unified
Understand Computer Storage and Data Types
 Understand Computer Storage and Data Types Lesson Overview Students will understand computer storage and data types. In this lesson, you will learn: How a computer stores programs and instructions in computer
Understand Computer Storage and Data Types Lesson Overview Students will understand computer storage and data types. In this lesson, you will learn: How a computer stores programs and instructions in computer
CSCI 2212: Intermediate Programming / C Review, Chapters 10 and 11
 ... 1/16 CSCI 2212: Intermediate Programming / C Review, Chapters 10 and 11 Alice E. Fischer February 3, 2016 ... 2/16 Outline Basic Types and Diagrams ... 3/16 Basic Types and Diagrams Types in C C has
... 1/16 CSCI 2212: Intermediate Programming / C Review, Chapters 10 and 11 Alice E. Fischer February 3, 2016 ... 2/16 Outline Basic Types and Diagrams ... 3/16 Basic Types and Diagrams Types in C C has
C How to Program, 6/e by Pearson Education, Inc. All Rights Reserved.
 C How to Program, 6/e 1992-2010 by Pearson Education, Inc. An important part of the solution to any problem is the presentation of the results. In this chapter, we discuss in depth the formatting features
C How to Program, 6/e 1992-2010 by Pearson Education, Inc. An important part of the solution to any problem is the presentation of the results. In this chapter, we discuss in depth the formatting features
Basic program The following is a basic program in C++; Basic C++ Source Code Compiler Object Code Linker (with libraries) Executable
 Basic C++ Overview C++ is a version of the older C programming language. This is a language that is used for a wide variety of applications and which has a mature base of compilers and libraries. C++ is
Basic C++ Overview C++ is a version of the older C programming language. This is a language that is used for a wide variety of applications and which has a mature base of compilers and libraries. C++ is
Inbound Reports. Cisco Unified Contact Center Express Report Description Guide, Release 11.0(1) 1
 Abandoned Call Detail Activity Report, page 2 Aborted Rejected Call Detail Report, page 3 Agent All s Report, page 6 Agent Call Summary Report, page 9 Agent Detail Report, page 12 Agent Login Logout Activity
Abandoned Call Detail Activity Report, page 2 Aborted Rejected Call Detail Report, page 3 Agent All s Report, page 6 Agent Call Summary Report, page 9 Agent Detail Report, page 12 Agent Login Logout Activity
Visual C# Instructor s Manual Table of Contents
 Visual C# 2005 2-1 Chapter 2 Using Data At a Glance Instructor s Manual Table of Contents Overview Objectives s Quick Quizzes Class Discussion Topics Additional Projects Additional Resources Key Terms
Visual C# 2005 2-1 Chapter 2 Using Data At a Glance Instructor s Manual Table of Contents Overview Objectives s Quick Quizzes Class Discussion Topics Additional Projects Additional Resources Key Terms
Arrays. Defining arrays, declaration and initialization of arrays. Designed by Parul Khurana, LIECA.
 Arrays Defining arrays, declaration and initialization of arrays Introduction Many applications require the processing of multiple data items that have common characteristics (e.g., a set of numerical
Arrays Defining arrays, declaration and initialization of arrays Introduction Many applications require the processing of multiple data items that have common characteristics (e.g., a set of numerical
SpiNNaker Application Programming Interface (API)
 SpiNNaker Application Programming Interface (API) Version 2.0.0 10 March 2016 Application programming interface (API) Event-driven programming model The SpiNNaker API programming model is a simple, event-driven
SpiNNaker Application Programming Interface (API) Version 2.0.0 10 March 2016 Application programming interface (API) Event-driven programming model The SpiNNaker API programming model is a simple, event-driven
Chapter 2: Introduction to C++
 Chapter 2: Introduction to C++ Copyright 2010 Pearson Education, Inc. Copyright Publishing as 2010 Pearson Pearson Addison-Wesley Education, Inc. Publishing as Pearson Addison-Wesley 2.1 Parts of a C++
Chapter 2: Introduction to C++ Copyright 2010 Pearson Education, Inc. Copyright Publishing as 2010 Pearson Pearson Addison-Wesley Education, Inc. Publishing as Pearson Addison-Wesley 2.1 Parts of a C++
Chapter 2: Special Characters. Parts of a C++ Program. Introduction to C++ Displays output on the computer screen
 Chapter 2: Introduction to C++ 2.1 Parts of a C++ Program Copyright 2009 Pearson Education, Inc. Copyright 2009 Publishing Pearson as Pearson Education, Addison-Wesley Inc. Publishing as Pearson Addison-Wesley
Chapter 2: Introduction to C++ 2.1 Parts of a C++ Program Copyright 2009 Pearson Education, Inc. Copyright 2009 Publishing Pearson as Pearson Education, Addison-Wesley Inc. Publishing as Pearson Addison-Wesley
Silent Monitoring. Silent Monitoring Overview
 Overview, page 1 Prerequisites, page 2 Configure Task Flow, page 2 Interactions and Restrictions, page 8 Overview Silent call monitoring allows a supervisor to eavesdrop on a phone conversation. The most
Overview, page 1 Prerequisites, page 2 Configure Task Flow, page 2 Interactions and Restrictions, page 8 Overview Silent call monitoring allows a supervisor to eavesdrop on a phone conversation. The most
A Rendezvous-based Paradigm for Analysis of Solicited and Unsolicited Traffic
 A Rendezvous-based Paradigm for Analysis of Solicited and Unsolicited Traffic DUST 2012 May 15, 2012 David Plonka & Paul Barford {plonka,pb}@cs.wisc.edu Outline Rendezvous-based Traffic Analysis What is
A Rendezvous-based Paradigm for Analysis of Solicited and Unsolicited Traffic DUST 2012 May 15, 2012 David Plonka & Paul Barford {plonka,pb}@cs.wisc.edu Outline Rendezvous-based Traffic Analysis What is
Data Storage and Query Answering. Data Storage and Disk Structure (4)
 Data Storage and Query Answering Data Storage and Disk Structure (4) Introduction We have introduced secondary storage devices, in particular disks. Disks use blocks as basic units of transfer and storage.
Data Storage and Query Answering Data Storage and Disk Structure (4) Introduction We have introduced secondary storage devices, in particular disks. Disks use blocks as basic units of transfer and storage.
Fundamentals of Programming. Lecture 12: C Structures, Unions, Bit Manipulations and Enumerations
 Fundamentals of Programming Lecture 12: C Structures, Unions, Bit Manipulations and Enumerations Instructor: Fatemeh Zamani f_zamani@ce.sharif.edu Sharif University of Technology Computer Engineering Department
Fundamentals of Programming Lecture 12: C Structures, Unions, Bit Manipulations and Enumerations Instructor: Fatemeh Zamani f_zamani@ce.sharif.edu Sharif University of Technology Computer Engineering Department
Brief introduction about memory queue -- CUQueue and CScopeUQueue objects
 Brief introduction about memory queue -- CUQueue and CScopeUQueue objects UDAParts support@udaparts.com Updated on Nov. 22, 2016 Contents 1. Introduction 2. C++, C#/VB.NET, Java and Python samples 3. Key
Brief introduction about memory queue -- CUQueue and CScopeUQueue objects UDAParts support@udaparts.com Updated on Nov. 22, 2016 Contents 1. Introduction 2. C++, C#/VB.NET, Java and Python samples 3. Key
Chapter 2: Using Data
 Chapter 2: Using Data Declaring Variables Constant Cannot be changed after a program is compiled Variable A named location in computer memory that can hold different values at different points in time
Chapter 2: Using Data Declaring Variables Constant Cannot be changed after a program is compiled Variable A named location in computer memory that can hold different values at different points in time
int fnvgetconfig(handle h, UINT32 id, const void *cfg, size_t sz);... 4
 RP-VL-UTIL-V1 Developer s Guide [ Contents ] 1. Introduction... 1 2. Building Environment... 1 3. Operating Environment... 1 4. Function Explanation... 2 4.1. Common API for Transmitting and Receiving...
RP-VL-UTIL-V1 Developer s Guide [ Contents ] 1. Introduction... 1 2. Building Environment... 1 3. Operating Environment... 1 4. Function Explanation... 2 4.1. Common API for Transmitting and Receiving...
Application User Setup
 This chapter provides information on managing application user information. About, page 1 Add Application User, page 2 Application User Deletion, page 3 Application User Settings, page 3 Add Administrator
This chapter provides information on managing application user information. About, page 1 Add Application User, page 2 Application User Deletion, page 3 Application User Settings, page 3 Add Administrator
Variation of Pointers
 Variation of Pointers A pointer is a variable whose value is the address of another variable, i.e., direct address of the memory location. Like any variable or constant, you must declare a pointer before
Variation of Pointers A pointer is a variable whose value is the address of another variable, i.e., direct address of the memory location. Like any variable or constant, you must declare a pointer before
You can configure different reason codes with the same reason code label across various teams.
 The Reasons tab on the Cisco Finesse administration console allows you to view, add, edit, and delete Not Ready reason codes, Sign Out reason codes, and Wrap-Up reasons. The reason codes you configure
The Reasons tab on the Cisco Finesse administration console allows you to view, add, edit, and delete Not Ready reason codes, Sign Out reason codes, and Wrap-Up reasons. The reason codes you configure
CHAPTER 3 BASIC INSTRUCTION OF C++
 CHAPTER 3 BASIC INSTRUCTION OF C++ MOHD HATTA BIN HJ MOHAMED ALI Computer programming (BFC 20802) Subtopics 2 Parts of a C++ Program Classes and Objects The #include Directive Variables and Literals Identifiers
CHAPTER 3 BASIC INSTRUCTION OF C++ MOHD HATTA BIN HJ MOHAMED ALI Computer programming (BFC 20802) Subtopics 2 Parts of a C++ Program Classes and Objects The #include Directive Variables and Literals Identifiers
Cisco Unified Contact Center Express Historical Reporting Guide, Release 10.5(1)
 Cisco Unified Contact Center Express Historical Reporting Guide, Release 10.5(1) First Published: June 11, 2014 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA
Cisco Unified Contact Center Express Historical Reporting Guide, Release 10.5(1) First Published: June 11, 2014 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA
CS 405G: Introduction to Database Systems. Storage
 CS 405G: Introduction to Database Systems Storage It s all about disks! Outline That s why we always draw databases as And why the single most important metric in database processing is the number of disk
CS 405G: Introduction to Database Systems Storage It s all about disks! Outline That s why we always draw databases as And why the single most important metric in database processing is the number of disk
Transport Protocol (IEX-TP)
 Transport Protocol (IEX-TP) Please contact IEX Market Operations at 646.568.2330 or marketops@iextrading.com, or your IEX onboarding contact with any questions. Version: 1.1 Updated: December 22, 2014
Transport Protocol (IEX-TP) Please contact IEX Market Operations at 646.568.2330 or marketops@iextrading.com, or your IEX onboarding contact with any questions. Version: 1.1 Updated: December 22, 2014
Computer Programming
 Computer Programming Dr. Deepak B Phatak Dr. Supratik Chakraborty Department of Computer Science and Engineering Session: Introduction to Pointers Part 1 Dr. Deepak B. Phatak & Dr. Supratik Chakraborty,
Computer Programming Dr. Deepak B Phatak Dr. Supratik Chakraborty Department of Computer Science and Engineering Session: Introduction to Pointers Part 1 Dr. Deepak B. Phatak & Dr. Supratik Chakraborty,
The XMPI API and trace file format
 The XMPI API and trace file format Nicholas J. Nevin January 29, 1997 1 Overview This document describes the interface between the portable and system independent parts of XMPI, and the format of an XMPI
The XMPI API and trace file format Nicholas J. Nevin January 29, 1997 1 Overview This document describes the interface between the portable and system independent parts of XMPI, and the format of an XMPI
QUIZ. 1. Explain the meaning of the angle brackets in the declaration of v below:
 QUIZ 1. Explain the meaning of the angle brackets in the declaration of v below: This is a template, used for generic programming! QUIZ 2. Why is the vector class called a container? 3. Explain how the
QUIZ 1. Explain the meaning of the angle brackets in the declaration of v below: This is a template, used for generic programming! QUIZ 2. Why is the vector class called a container? 3. Explain how the
Byte Ordering. Jin-Soo Kim Computer Systems Laboratory Sungkyunkwan University
 Byte Ordering Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Memory Model Physical memory DRAM chips can read/write 4, 8, 16 bits DRAM modules
Byte Ordering Jin-Soo Kim (jinsookim@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Memory Model Physical memory DRAM chips can read/write 4, 8, 16 bits DRAM modules
First of all, it is a variable, just like other variables you studied
 Pointers: Basics What is a pointer? First of all, it is a variable, just like other variables you studied So it has type, storage etc. Difference: it can only store the address (rather than the value)
Pointers: Basics What is a pointer? First of all, it is a variable, just like other variables you studied So it has type, storage etc. Difference: it can only store the address (rather than the value)
Cisco Unified Contact Center Express Historical Reporting Guide, Release 10.6(1)
 Cisco Unified Contact Center Express Historical Reporting Guide, Release 10.6(1) First Published: December 15, 2014 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706
Cisco Unified Contact Center Express Historical Reporting Guide, Release 10.6(1) First Published: December 15, 2014 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706
Objectives. Chapter 2: Basic Elements of C++ Introduction. Objectives (cont d.) A C++ Program (cont d.) A C++ Program
 Objectives Chapter 2: Basic Elements of C++ In this chapter, you will: Become familiar with functions, special symbols, and identifiers in C++ Explore simple data types Discover how a program evaluates
Objectives Chapter 2: Basic Elements of C++ In this chapter, you will: Become familiar with functions, special symbols, and identifiers in C++ Explore simple data types Discover how a program evaluates
OpenCL Overview Benedict R. Gaster, AMD
 Copyright Khronos Group, 2011 - Page 1 OpenCL Overview Benedict R. Gaster, AMD March 2010 The BIG Idea behind OpenCL OpenCL execution model - Define N-dimensional computation domain - Execute a kernel
Copyright Khronos Group, 2011 - Page 1 OpenCL Overview Benedict R. Gaster, AMD March 2010 The BIG Idea behind OpenCL OpenCL execution model - Define N-dimensional computation domain - Execute a kernel
Chapter 2: Basic Elements of C++
 Chapter 2: Basic Elements of C++ Objectives In this chapter, you will: Become familiar with functions, special symbols, and identifiers in C++ Explore simple data types Discover how a program evaluates
Chapter 2: Basic Elements of C++ Objectives In this chapter, you will: Become familiar with functions, special symbols, and identifiers in C++ Explore simple data types Discover how a program evaluates
Chapter 2: Basic Elements of C++ Objectives. Objectives (cont d.) A C++ Program. Introduction
 Chapter 2: Basic Elements of C++ C++ Programming: From Problem Analysis to Program Design, Fifth Edition 1 Objectives In this chapter, you will: Become familiar with functions, special symbols, and identifiers
Chapter 2: Basic Elements of C++ C++ Programming: From Problem Analysis to Program Design, Fifth Edition 1 Objectives In this chapter, you will: Become familiar with functions, special symbols, and identifiers
Introduction. Following are the types of operators: Unary requires a single operand Binary requires two operands Ternary requires three operands
 Introduction Operators are the symbols which operates on value or a variable. It tells the compiler to perform certain mathematical or logical manipulations. Can be of following categories: Unary requires
Introduction Operators are the symbols which operates on value or a variable. It tells the compiler to perform certain mathematical or logical manipulations. Can be of following categories: Unary requires
Operators. Java operators are classified into three categories:
 Operators Operators are symbols that perform arithmetic and logical operations on operands and provide a meaningful result. Operands are data values (variables or constants) which are involved in operations.
Operators Operators are symbols that perform arithmetic and logical operations on operands and provide a meaningful result. Operands are data values (variables or constants) which are involved in operations.
KMC API documentation
 KMC API documentation for KMC v. 2.3.0 Contents Introduction 2 1 API 3 1.1 CKmerAPI class.............................................. 3 1.2 CKMCFile class..............................................
KMC API documentation for KMC v. 2.3.0 Contents Introduction 2 1 API 3 1.1 CKmerAPI class.............................................. 3 1.2 CKMCFile class..............................................
Creating a C++ Program
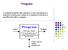 Program A computer program (also software, or just a program) is a sequence of instructions written in a sequence to perform a specified task with a computer. 1 Creating a C++ Program created using an
Program A computer program (also software, or just a program) is a sequence of instructions written in a sequence to perform a specified task with a computer. 1 Creating a C++ Program created using an
MATLAB SON Library. Malcolm Lidierth King's College London Updated October 2005 (version 2.0)
 MATLAB SON Library Malcolm Lidierth King's College London Updated October 2005 (version 2.0) This pack now contains two libraries: SON2 is a backwards-compatible update to the previous library. It provides
MATLAB SON Library Malcolm Lidierth King's College London Updated October 2005 (version 2.0) This pack now contains two libraries: SON2 is a backwards-compatible update to the previous library. It provides
Modbus ASCII Serial Device Driver Help 2009 Kepware Technologies
 Modbus ASCII Serial Device Driver Help 2009 Kepware Technologies 1 Table of Contents 1 Getting Started... 3 Help Contents... 3 Overview... 3 2 Device Setup... 3 Device Setup... 3 Cable Diagram... 4 Modem
Modbus ASCII Serial Device Driver Help 2009 Kepware Technologies 1 Table of Contents 1 Getting Started... 3 Help Contents... 3 Overview... 3 2 Device Setup... 3 Device Setup... 3 Cable Diagram... 4 Modem
Application User Configuration
 CHAPTER 87 The following topics contain information on managing application user information: Settings, page 87-1 Adding an Administrator User to Cisco Unity or Cisco Unity Connection, page 87-6 Changing
CHAPTER 87 The following topics contain information on managing application user information: Settings, page 87-1 Adding an Administrator User to Cisco Unity or Cisco Unity Connection, page 87-6 Changing
The C++ Language. Arizona State University 1
 The C++ Language CSE100 Principles of Programming with C++ (based off Chapter 2 slides by Pearson) Ryan Dougherty Arizona State University http://www.public.asu.edu/~redoughe/ Arizona State University
The C++ Language CSE100 Principles of Programming with C++ (based off Chapter 2 slides by Pearson) Ryan Dougherty Arizona State University http://www.public.asu.edu/~redoughe/ Arizona State University
Number Systems Prof. Indranil Sen Gupta Dept. of Computer Science & Engg. Indian Institute of Technology Kharagpur Number Representation
 Number Systems Prof. Indranil Sen Gupta Dept. of Computer Science & Engg. Indian Institute of Technology Kharagpur 1 Number Representation 2 1 Topics to be Discussed How are numeric data items actually
Number Systems Prof. Indranil Sen Gupta Dept. of Computer Science & Engg. Indian Institute of Technology Kharagpur 1 Number Representation 2 1 Topics to be Discussed How are numeric data items actually
Byte Ordering. Jinkyu Jeong Computer Systems Laboratory Sungkyunkwan University
 Byte Ordering Jinkyu Jeong (jinkyu@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu SSE2030: Introduction to Computer Systems, Spring 2018, Jinkyu Jeong (jinkyu@skku.edu)
Byte Ordering Jinkyu Jeong (jinkyu@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu SSE2030: Introduction to Computer Systems, Spring 2018, Jinkyu Jeong (jinkyu@skku.edu)
C++ Programming: From Problem Analysis to Program Design, Third Edition
 C++ Programming: From Problem Analysis to Program Design, Third Edition Chapter 2: Basic Elements of C++ Objectives (continued) Become familiar with the use of increment and decrement operators Examine
C++ Programming: From Problem Analysis to Program Design, Third Edition Chapter 2: Basic Elements of C++ Objectives (continued) Become familiar with the use of increment and decrement operators Examine
CS 261 Fall Mike Lam, Professor. Structs and I/O
 CS 261 Fall 2018 Mike Lam, Professor Structs and I/O Typedefs A typedef is a way to create a new type name Basically a synonym for another type Useful for shortening long types or providing more meaningful
CS 261 Fall 2018 Mike Lam, Professor Structs and I/O Typedefs A typedef is a way to create a new type name Basically a synonym for another type Useful for shortening long types or providing more meaningful
Numerical Computing in C and C++ Jamie Griffin. Semester A 2017 Lecture 2
 Numerical Computing in C and C++ Jamie Griffin Semester A 2017 Lecture 2 Visual Studio in QM PC rooms Microsoft Visual Studio Community 2015. Bancroft Building 1.15a; Queen s W207, EB7; Engineering W128.D.
Numerical Computing in C and C++ Jamie Griffin Semester A 2017 Lecture 2 Visual Studio in QM PC rooms Microsoft Visual Studio Community 2015. Bancroft Building 1.15a; Queen s W207, EB7; Engineering W128.D.
The type of all data used in a C (or C++) program must be specified
 The type of all data used in a C (or C++) program must be specified A data type is a description of the data being represented That is, a set of possible values and a set of operations on those values
The type of all data used in a C (or C++) program must be specified A data type is a description of the data being represented That is, a set of possible values and a set of operations on those values
CSC 1300 Exam 4 Comprehensive-ish and Structs
 CSC 1300 Exam 4 Comprehensive-ish and Structs December 8, 2017 Name: Read through the entire test first BEFORE starting Multiple Choice and T/F sections should be completed on the scantron Test has two
CSC 1300 Exam 4 Comprehensive-ish and Structs December 8, 2017 Name: Read through the entire test first BEFORE starting Multiple Choice and T/F sections should be completed on the scantron Test has two
Type Checking. Prof. James L. Frankel Harvard University
 Type Checking Prof. James L. Frankel Harvard University Version of 7:10 PM 27-Feb-2018 Copyright 2018, 2016, 2015 James L. Frankel. All rights reserved. C Types C Types Type Category Type Category Type
Type Checking Prof. James L. Frankel Harvard University Version of 7:10 PM 27-Feb-2018 Copyright 2018, 2016, 2015 James L. Frankel. All rights reserved. C Types C Types Type Category Type Category Type
[ DATA STRUCTURES] to Data Structures
![[ DATA STRUCTURES] to Data Structures [ DATA STRUCTURES] to Data Structures](/thumbs/95/124812037.jpg) [ DATA STRUCTURES] Chapter - 01 : Introduction to Data Structures INTRODUCTION TO DATA STRUCTURES A Data type refers to a named group of data which share similar properties or characteristics and which
[ DATA STRUCTURES] Chapter - 01 : Introduction to Data Structures INTRODUCTION TO DATA STRUCTURES A Data type refers to a named group of data which share similar properties or characteristics and which
LECTURE 02 INTRODUCTION TO C++
 PowerPoint Slides adapted from *Starting Out with C++: From Control Structures through Objects, 7/E* by *Tony Gaddis* Copyright 2012 Pearson Education Inc. COMPUTER PROGRAMMING LECTURE 02 INTRODUCTION
PowerPoint Slides adapted from *Starting Out with C++: From Control Structures through Objects, 7/E* by *Tony Gaddis* Copyright 2012 Pearson Education Inc. COMPUTER PROGRAMMING LECTURE 02 INTRODUCTION
FUNCTION POINTERS. int (*pf)(); // pf is a pointer to a function returning an int.
 Function Pointers 1 FUNCTION POINTERS Sometimes we would like to choose different behaviors at different times in the same piece of code or function. For instance in a sorting routine, we want to allow
Function Pointers 1 FUNCTION POINTERS Sometimes we would like to choose different behaviors at different times in the same piece of code or function. For instance in a sorting routine, we want to allow
Objectives. In this chapter, you will:
 Objectives In this chapter, you will: Become familiar with functions, special symbols, and identifiers in C++ Explore simple data types Discover how a program evaluates arithmetic expressions Learn about
Objectives In this chapter, you will: Become familiar with functions, special symbols, and identifiers in C++ Explore simple data types Discover how a program evaluates arithmetic expressions Learn about
Lecture 8: Other IPC Mechanisms. CSC 469H1F Fall 2006 Angela Demke Brown
 Lecture 8: Other IPC Mechanisms CSC 469H1F Fall 2006 Angela Demke Brown Topics Messages through sockets / pipes Receiving notification of activity Generalizing the event notification mechanism Kqueue Semaphores
Lecture 8: Other IPC Mechanisms CSC 469H1F Fall 2006 Angela Demke Brown Topics Messages through sockets / pipes Receiving notification of activity Generalizing the event notification mechanism Kqueue Semaphores
Time (self-scheduled): Location Schedule Your Exam: What to bring:
 ECE 120 Midterm 1B HKN Review Session Time (self-scheduled): Between Wednesday, September 27 and Friday, September 29, 2017 Location: 57 Grainger Engineering Library (in the basement on the east side)
ECE 120 Midterm 1B HKN Review Session Time (self-scheduled): Between Wednesday, September 27 and Friday, September 29, 2017 Location: 57 Grainger Engineering Library (in the basement on the east side)
Topics. Lecture 8: Other IPC Mechanisms. Socket IPC. Unix Communication
 Topics Lecture 8: Other IPC Mechanisms CSC 469H1F Fall 2006 Angela Demke Brown Messages through sockets / pipes Receiving notification of activity Generalizing the event notification mechanism Kqueue Semaphores
Topics Lecture 8: Other IPC Mechanisms CSC 469H1F Fall 2006 Angela Demke Brown Messages through sockets / pipes Receiving notification of activity Generalizing the event notification mechanism Kqueue Semaphores
! A literal represents a constant value used in a. ! Numbers: 0, 34, , -1.8e12, etc. ! Characters: 'A', 'z', '!', '5', etc.
 Week 1: Introduction to C++ Gaddis: Chapter 2 (excluding 2.1, 2.11, 2.14) CS 1428 Fall 2014 Jill Seaman Literals A literal represents a constant value used in a program statement. Numbers: 0, 34, 3.14159,
Week 1: Introduction to C++ Gaddis: Chapter 2 (excluding 2.1, 2.11, 2.14) CS 1428 Fall 2014 Jill Seaman Literals A literal represents a constant value used in a program statement. Numbers: 0, 34, 3.14159,
Cisco Unified CCX reason codes
 This appendix describes the events that cause an agent to go to the Logout state or Not Ready state. The built-in agent Not Ready reason codes are generated by the Unified CCX server. The Agent State Detail
This appendix describes the events that cause an agent to go to the Logout state or Not Ready state. The built-in agent Not Ready reason codes are generated by the Unified CCX server. The Agent State Detail
UNIT- 3 Introduction to C++
 UNIT- 3 Introduction to C++ C++ Character Sets: Letters A-Z, a-z Digits 0-9 Special Symbols Space + - * / ^ \ ( ) [ ] =!= . $, ; : %! &? _ # = @ White Spaces Blank spaces, horizontal tab, carriage
UNIT- 3 Introduction to C++ C++ Character Sets: Letters A-Z, a-z Digits 0-9 Special Symbols Space + - * / ^ \ ( ) [ ] =!= . $, ; : %! &? _ # = @ White Spaces Blank spaces, horizontal tab, carriage
[0569] p 0318 garbage
![[0569] p 0318 garbage [0569] p 0318 garbage](/thumbs/74/69959549.jpg) A Pointer is a variable which contains the address of another variable. Declaration syntax: Pointer_type *pointer_name; This declaration will create a pointer of the pointer_name which will point to the
A Pointer is a variable which contains the address of another variable. Declaration syntax: Pointer_type *pointer_name; This declaration will create a pointer of the pointer_name which will point to the
Vive Input Utility Developer Guide
 Vive Input Utility Developer Guide vivesoftware@htc.com Abstract Vive Input Utility is a tool based on the SteamVR plugin that allows developers to access Vive device status in handy way. We also introduce
Vive Input Utility Developer Guide vivesoftware@htc.com Abstract Vive Input Utility is a tool based on the SteamVR plugin that allows developers to access Vive device status in handy way. We also introduce
C++ Basic Elements of COMPUTER PROGRAMMING. Special symbols include: Word symbols. Objectives. Programming. Symbols. Symbols.
 EEE-117 COMPUTER PROGRAMMING Basic Elements of C++ Objectives General Questions Become familiar with the basic components of a C++ program functions, special symbols, and identifiers Data types Arithmetic
EEE-117 COMPUTER PROGRAMMING Basic Elements of C++ Objectives General Questions Become familiar with the basic components of a C++ program functions, special symbols, and identifiers Data types Arithmetic
Agent Administration
 This chapter explains the tasks you must be familiar with when setting up agents for your Unified CCE contact center. Administering Agents, page 1 Configure Not Ready Reason Codes, page 4 Agent Feature
This chapter explains the tasks you must be familiar with when setting up agents for your Unified CCE contact center. Administering Agents, page 1 Configure Not Ready Reason Codes, page 4 Agent Feature
C Programming. Course Outline. C Programming. Code: MBD101. Duration: 10 Hours. Prerequisites:
 C Programming Code: MBD101 Duration: 10 Hours Prerequisites: You are a computer science Professional/ graduate student You can execute Linux/UNIX commands You know how to use a text-editing tool You should
C Programming Code: MBD101 Duration: 10 Hours Prerequisites: You are a computer science Professional/ graduate student You can execute Linux/UNIX commands You know how to use a text-editing tool You should
Configuration of Campaigns and Imports
 Outbound Option Configuration Process Overview, on page 1 Configuration Process Task Maps, on page 2 Preliminary Configuration Requirements, on page 3 Contact and Do Not Call List Imports, on page 6 Outbound
Outbound Option Configuration Process Overview, on page 1 Configuration Process Task Maps, on page 2 Preliminary Configuration Requirements, on page 3 Contact and Do Not Call List Imports, on page 6 Outbound
Data structures and libraries
 Data structures and libraries Bjarki Ágúst Guðmundsson Tómas Ken Magnússon Árangursrík forritun og lausn verkefna School of Computer Science Reykjavík University Today we re going to cover Basic data types
Data structures and libraries Bjarki Ágúst Guðmundsson Tómas Ken Magnússon Árangursrík forritun og lausn verkefna School of Computer Science Reykjavík University Today we re going to cover Basic data types
Data Storage. August 9, Indiana University. Geoffrey Brown, Bryce Himebaugh 2015 August 9, / 19
 Data Storage Geoffrey Brown Bryce Himebaugh Indiana University August 9, 2016 Geoffrey Brown, Bryce Himebaugh 2015 August 9, 2016 1 / 19 Outline Bits, Bytes, Words Word Size Byte Addressable Memory Byte
Data Storage Geoffrey Brown Bryce Himebaugh Indiana University August 9, 2016 Geoffrey Brown, Bryce Himebaugh 2015 August 9, 2016 1 / 19 Outline Bits, Bytes, Words Word Size Byte Addressable Memory Byte
Data Types and Variables in C language
 Data Types and Variables in C language Disclaimer The slides are prepared from various sources. The purpose of the slides is for academic use only Operators in C C supports a rich set of operators. Operators
Data Types and Variables in C language Disclaimer The slides are prepared from various sources. The purpose of the slides is for academic use only Operators in C C supports a rich set of operators. Operators
Programming for Engineers Arrays
 Programming for Engineers Arrays ICEN 200 Spring 2018 Prof. Dola Saha 1 Array Ø Arrays are data structures consisting of related data items of the same type. Ø A group of contiguous memory locations that
Programming for Engineers Arrays ICEN 200 Spring 2018 Prof. Dola Saha 1 Array Ø Arrays are data structures consisting of related data items of the same type. Ø A group of contiguous memory locations that
Configuring QoS CHAPTER
 CHAPTER 34 This chapter describes how to use different methods to configure quality of service (QoS) on the Catalyst 3750 Metro switch. With QoS, you can provide preferential treatment to certain types
CHAPTER 34 This chapter describes how to use different methods to configure quality of service (QoS) on the Catalyst 3750 Metro switch. With QoS, you can provide preferential treatment to certain types
Allen-Bradley ControlLogix Slave Ethernet Driver Help Kepware Technologies
 Allen-Bradley ControlLogix Slave Ethernet Driver Help 2012 Kepware Technologies 2 Table of Contents Table of Contents 2 4 Overview 4 Channel Setup 4 Device Setup 6 Master Device Configuration 6 Controller
Allen-Bradley ControlLogix Slave Ethernet Driver Help 2012 Kepware Technologies 2 Table of Contents Table of Contents 2 4 Overview 4 Channel Setup 4 Device Setup 6 Master Device Configuration 6 Controller
EXAMINATION FOR THE BSC (HONS) INFORMATION SYSTEMS; BSC (HONS) INFORMATION TECHNOLOGY & BSC (HONS) COMPUTER SCIENCE; YEAR 1
 FACULTY OF SCIENCE AND TECHNOLOGY EXAMINATION FOR THE BSC (HONS) INFORMATION SYSTEMS; BSC (HONS) INFORMATION TECHNOLOGY & BSC (HONS) COMPUTER SCIENCE; YEAR 1 ACADEMIC SESSION 2014; SEMESTER 1 & 2 FINAL
FACULTY OF SCIENCE AND TECHNOLOGY EXAMINATION FOR THE BSC (HONS) INFORMATION SYSTEMS; BSC (HONS) INFORMATION TECHNOLOGY & BSC (HONS) COMPUTER SCIENCE; YEAR 1 ACADEMIC SESSION 2014; SEMESTER 1 & 2 FINAL
IPV6 SIMPLE SECURITY CAPABILITIES.
 IPV6 SIMPLE SECURITY CAPABILITIES. 50 issues from RFC 6092 edited by J. Woodyatt, Apple Presentation by Olle E. Johansson, Edvina AB. ABSTRACT The RFC which this presentation is based upon is focused on
IPV6 SIMPLE SECURITY CAPABILITIES. 50 issues from RFC 6092 edited by J. Woodyatt, Apple Presentation by Olle E. Johansson, Edvina AB. ABSTRACT The RFC which this presentation is based upon is focused on
3. Except for strings, double quotes, identifiers, and keywords, C++ ignores all white space.
 Chapter 2: Problem Solving Using C++ TRUE/FALSE 1. Modular programs are easier to develop, correct, and modify than programs constructed in some other manner. ANS: T PTS: 1 REF: 45 2. One important requirement
Chapter 2: Problem Solving Using C++ TRUE/FALSE 1. Modular programs are easier to develop, correct, and modify than programs constructed in some other manner. ANS: T PTS: 1 REF: 45 2. One important requirement
Bandwidth, Latency, and QoS for Core Components
 Bandwidth, Latency, and QoS for Core Components, on page 1 Bandwidth, Latency, and QoS for Optional Cisco Components, on page 18 Bandwidth, Latency, and QoS for Optional Third-Party Components, on page
Bandwidth, Latency, and QoS for Core Components, on page 1 Bandwidth, Latency, and QoS for Optional Cisco Components, on page 18 Bandwidth, Latency, and QoS for Optional Third-Party Components, on page
Arrays in C. Rab Nawaz Jadoon DCS. Assistant Professor. Department of Computer Science. COMSATS IIT, Abbottabad Pakistan
 Arrays in C DCS COMSATS Institute of Information Technology Rab Nawaz Jadoon Assistant Professor COMSATS IIT, Abbottabad Pakistan Introduction to Computer Programming (ICP) Array C language provides a
Arrays in C DCS COMSATS Institute of Information Technology Rab Nawaz Jadoon Assistant Professor COMSATS IIT, Abbottabad Pakistan Introduction to Computer Programming (ICP) Array C language provides a
ASPRS LiDAR SPRS Data Exchan LiDAR Data Exchange Format Standard LAS ge Format Standard LAS IIT Kanp IIT Kan ur
 ASPRS LiDAR Data Exchange Format Standard LAS IIT Kanpur 1 Definition: Files conforming to the ASPRS LIDAR data exchange format standard are named with a LAS extension. The LAS file is intended to contain
ASPRS LiDAR Data Exchange Format Standard LAS IIT Kanpur 1 Definition: Files conforming to the ASPRS LIDAR data exchange format standard are named with a LAS extension. The LAS file is intended to contain
Chi-X Japan CHIXOE Interface Specification
 Chi-X Japan Trading System Document ID: JPCX-L3-D-022 9-Nov-2017 Version 1.8 CONTENTS 1 Introduction... 1 1.1 Relevant documents... 1 1.2 Revision History... 1 2 Data Types... 2 2.1 Integer... 2 2.2 Alpha...
Chi-X Japan Trading System Document ID: JPCX-L3-D-022 9-Nov-2017 Version 1.8 CONTENTS 1 Introduction... 1 1.1 Relevant documents... 1 1.2 Revision History... 1 2 Data Types... 2 2.1 Integer... 2 2.2 Alpha...
eprosima Dynamic Fast Buffers User Manual Version 0.2.0
 eprosima Dynamic Fast Buffers User Manual Version 0.2.0 The Middleware Experts eprosima 2013 1 eprosima Proyectos y Sistemas de Mantenimiento SL Ronda del poniente 2 1ºG 28760 Tres Cantos Madrid Tel: +
eprosima Dynamic Fast Buffers User Manual Version 0.2.0 The Middleware Experts eprosima 2013 1 eprosima Proyectos y Sistemas de Mantenimiento SL Ronda del poniente 2 1ºG 28760 Tres Cantos Madrid Tel: +
Programming in C++ 5. Integral data types
 Programming in C++ 5. Integral data types! Introduction! Type int! Integer multiplication & division! Increment & decrement operators! Associativity & precedence of operators! Some common operators! Long
Programming in C++ 5. Integral data types! Introduction! Type int! Integer multiplication & division! Increment & decrement operators! Associativity & precedence of operators! Some common operators! Long
Introduction to C# Applications
 1 2 3 Introduction to C# Applications OBJECTIVES To write simple C# applications To write statements that input and output data to the screen. To declare and use data of various types. To write decision-making
1 2 3 Introduction to C# Applications OBJECTIVES To write simple C# applications To write statements that input and output data to the screen. To declare and use data of various types. To write decision-making
Modbus Plus Driver Kepware, Inc.
 2015 Kepware, Inc. 2 Table of Contents Table of Contents 2 4 Overview 4 External Dependencies 4 Device Setup 5 Device ID (PLC Network Address) 5 Block Sizes 9 Settings 9 Variable Import Settings 12 Automatic
2015 Kepware, Inc. 2 Table of Contents Table of Contents 2 4 Overview 4 External Dependencies 4 Device Setup 5 Device ID (PLC Network Address) 5 Block Sizes 9 Settings 9 Variable Import Settings 12 Automatic
Primitive Types. Four integer types: Two floating-point types: One character type: One boolean type: byte short int (most common) long
 Primitive Types Four integer types: byte short int (most common) long Two floating-point types: float double (most common) One character type: char One boolean type: boolean 1 2 Primitive Types, cont.
Primitive Types Four integer types: byte short int (most common) long Two floating-point types: float double (most common) One character type: char One boolean type: boolean 1 2 Primitive Types, cont.
2.1. Chapter 2: Parts of a C++ Program. Parts of a C++ Program. Introduction to C++ Parts of a C++ Program
 Chapter 2: Introduction to C++ 2.1 Parts of a C++ Program Copyright 2009 Pearson Education, Inc. Publishing as Pearson Addison-Wesley 2-1 Parts of a C++ Program Parts of a C++ Program // sample C++ program
Chapter 2: Introduction to C++ 2.1 Parts of a C++ Program Copyright 2009 Pearson Education, Inc. Publishing as Pearson Addison-Wesley 2-1 Parts of a C++ Program Parts of a C++ Program // sample C++ program
ArcaTrade Specification for Bonds
 Specification for Bonds For the New York Stock Exchange April 24, 2007 Version 1.07 Copyright 2006 Archipelago Holdings, Inc. All Rights Reserved. Copyright 2006 Archipelago Holdings, Inc. All rights reserved.
Specification for Bonds For the New York Stock Exchange April 24, 2007 Version 1.07 Copyright 2006 Archipelago Holdings, Inc. All Rights Reserved. Copyright 2006 Archipelago Holdings, Inc. All rights reserved.
PROGRAMMAZIONE I A.A. 2017/2018
 PROGRAMMAZIONE I A.A. 2017/2018 A pointer is a variable whose value is the address of another variable, i.e., direct address of the memory location. DECLARING POINTERS POINTERS A pointer represents both
PROGRAMMAZIONE I A.A. 2017/2018 A pointer is a variable whose value is the address of another variable, i.e., direct address of the memory location. DECLARING POINTERS POINTERS A pointer represents both
Input File Syntax The parser expects the input file to be divided into objects. Each object must start with the declaration:
 TCC Low Level Parser Purpose The TCC low level parser is designed to convert the low level ASCII based configuration files into a binary format which can then be downloaded to the Alpha processor boards.
TCC Low Level Parser Purpose The TCC low level parser is designed to convert the low level ASCII based configuration files into a binary format which can then be downloaded to the Alpha processor boards.
µtasker Document µtasker MQTT/MQTTS
 Embedding it better... µtasker Document /MQTTS utasker_mqtt.doc/v1.00 Copyright 2018 M.J.Butcher Consulting Table of Contents 1. Introduction...3 2. Enabling MQTT...4 3. MQTT Operation and Interface...5
Embedding it better... µtasker Document /MQTTS utasker_mqtt.doc/v1.00 Copyright 2018 M.J.Butcher Consulting Table of Contents 1. Introduction...3 2. Enabling MQTT...4 3. MQTT Operation and Interface...5
Modbus Plus Driver Help Kepware Technologies
 2010 Kepware Technologies 1 Table of Contents 1 Getting Started... 3 Help Contents Overview... 3... 3 2 Device Setup... 3 Device Setup Device ID Block Sizes Settings... 3... 4... 7... 8 Variable Import...
2010 Kepware Technologies 1 Table of Contents 1 Getting Started... 3 Help Contents Overview... 3... 3 2 Device Setup... 3 Device Setup Device ID Block Sizes Settings... 3... 4... 7... 8 Variable Import...
A First Book of ANSI C Fourth Edition. Chapter 8 Arrays
 A First Book of ANSI C Fourth Edition Chapter 8 Arrays Objectives One-Dimensional Arrays Array Initialization Arrays as Function Arguments Case Study: Computing Averages and Standard Deviations Two-Dimensional
A First Book of ANSI C Fourth Edition Chapter 8 Arrays Objectives One-Dimensional Arrays Array Initialization Arrays as Function Arguments Case Study: Computing Averages and Standard Deviations Two-Dimensional
Chapter 2: Using Data
 Chapter 2: Using Data TRUE/FALSE 1. A variable can hold more than one value at a time. F PTS: 1 REF: 52 2. The legal integer values are -2 31 through 2 31-1. These are the highest and lowest values that
Chapter 2: Using Data TRUE/FALSE 1. A variable can hold more than one value at a time. F PTS: 1 REF: 52 2. The legal integer values are -2 31 through 2 31-1. These are the highest and lowest values that
Overview. Arrays and their properties Creating arrays Accessing array elements Modifying array elements Loops and arrays. Initialization Searching
 Arrays Overview Arrays and their properties Creating arrays Accessing array elements Modifying array elements Loops and arrays Initialization Searching Arrays and Their Properties Hold several values of
Arrays Overview Arrays and their properties Creating arrays Accessing array elements Modifying array elements Loops and arrays Initialization Searching Arrays and Their Properties Hold several values of
Fundamentals of Programming Session 15
 Fundamentals of Programming Session 15 Instructor: Reza Entezari-Maleki Email: entezari@ce.sharif.edu 1 Fall 2013 These slides have been created using Deitel s slides Sharif University of Technology Outlines
Fundamentals of Programming Session 15 Instructor: Reza Entezari-Maleki Email: entezari@ce.sharif.edu 1 Fall 2013 These slides have been created using Deitel s slides Sharif University of Technology Outlines
Advanced Computer Programming
 Hazırlayan Yard. Doç. Dr. Mehmet Fidan VARIABLE TYPES Integral Types: In C#, an integral is a category of types. For anyone confused because the word Integral sounds like a mathematical term, from the
Hazırlayan Yard. Doç. Dr. Mehmet Fidan VARIABLE TYPES Integral Types: In C#, an integral is a category of types. For anyone confused because the word Integral sounds like a mathematical term, from the
Computer System and programming in C
 1 Basic Data Types Integral Types Integers are stored in various sizes. They can be signed or unsigned. Example Suppose an integer is represented by a byte (8 bits). Leftmost bit is sign bit. If the sign
1 Basic Data Types Integral Types Integers are stored in various sizes. They can be signed or unsigned. Example Suppose an integer is represented by a byte (8 bits). Leftmost bit is sign bit. If the sign
Time: 8:30-10:00 pm (Arrive at 8:15 pm) Location What to bring:
 ECE 120 Midterm 1 HKN Review Session Time: 8:30-10:00 pm (Arrive at 8:15 pm) Location: Your Room on Compass What to bring: icard, pens/pencils, Cheat sheet (Handwritten) Overview of Review Binary IEEE
ECE 120 Midterm 1 HKN Review Session Time: 8:30-10:00 pm (Arrive at 8:15 pm) Location: Your Room on Compass What to bring: icard, pens/pencils, Cheat sheet (Handwritten) Overview of Review Binary IEEE
Allen-Bradley ControlLogix Unsolicited Driver PTC Inc. All Rights Reserved.
 Allen-Bradley ControlLogix Unsolicited Driver 2016 PTC Inc. All Rights Reserved. 2 Table of Contents 1 Table of Contents 2 4 Overview 5 Setup 6 Channel Setup 6 Channel Properties - General 6 Channel Properties
Allen-Bradley ControlLogix Unsolicited Driver 2016 PTC Inc. All Rights Reserved. 2 Table of Contents 1 Table of Contents 2 4 Overview 5 Setup 6 Channel Setup 6 Channel Properties - General 6 Channel Properties
