How to Encrypt Files Containing Sensitive Data (using 7zip software or Microsoft password protection) How to Create Strong Passwords
|
|
|
- Shawn Wilson
- 6 years ago
- Views:
Transcription
1 How to Encrypt Files Containing Sensitive Data (using 7zip software or Microsoft password protection) How to Create Strong Passwords School IT Systems Support Standards and School Effectiveness Hertfordshire Development Centre SROB220, Robertson House, Six Hills Way, Stevenage, Herts, SG1 2FQ Doc Ref S1218 Published January 2012 School IT Systems Support (SITSS), Hertfordshire County Council Technical Support Centre Accredited by the Learning and Performance Institute (formerly, Institute of IT Training) RM Approved Support Partner Fully accredited by Capita SIMS for proven quality of SIMS support
2
3 CONTENTS FOREWORD... 1 DOWNLOADING THE SOFTWARE (7-ZIP)... 2 ENCRYPTING DOCUMENTS, FILES OR FOLDERS... 4 TO ACCESS THE FILE (DECRYPTION)... 6 HOW TO SECURELY ENCRYPT A WORD OR EXCEL DOCUMENT (SIMILAR METHODS EXIST IN THE OTHER MS OFFICE PRODUCTS)... 7 Using Word Using Excel Using Word Using Excel Removing Password Protection from a Word 2003 Document Removing Password Protection from an Excel 2003 Document Removing Password Protection from a Word 2007 Document Removing Password Protection from an Excel 2007 Document CREATE STRONG PASSWORDS PROTECT YOUR PASSWORDS FROM PRYING EYES TOP TIPS FOR INTERNET SAFETY AT WORK S1218
4
5 School IT Systems Support Foreword Schools may choose to use any provider other than the HCC preferred supplier of Microsoft It is therefore vital that files containing sensitive or personal data are encrypted or at least password protected (until your school has software encryption such as 7-zip) before transmitting electronically. This document offers a solution using 7-zip software and instructions on password protecting an Excel or Word document. It is recommended that such protocols are included in the school s ICT Acceptable Use Policy which should be issued to all users. For more information on Microsoft Live@Edu please click on the following link. The following extract is taken from FAQs concerning Live@Edu. Can I trust Microsoft with my school's data? Yes, Microsoft is committed to the security and privacy of your school's data. We apply enterprise-grade standards and processes that have come with 30+ years of experience. Live@edu securely stores data with multiple datacenters around the world and does not show 3rd party ads in the interface. Also, Live@edu services are engineered with essential controls for Education, such as bad word filter, anti-bullying or closed campus functionality. Check out Securing Microsoft Cloud Infrastructure ( pdf) for more information. BUT note that the transport of s to users is still vulnerable unless they use a specific secure method of accessing the . For schools not using Live@Edu it is vital that confidential or sensitive data that needs to be ed from schools is encrypted to a min of AES 128 bit level using encryption software such as 7-zip. Each workstation that will be used for sending such s will require this software installation. Your technical support supplier may be able to deploy this software as a package to the relevant workstations. All SITSS managed schools will have 7-zip software installed on CC3 and CC4 machines. If you have any issues installing this software then contact your technical support provider. Select Option 1 followed by Option 2 if you would like general help or advice regarding and internet connectivity or sitss.internet@lea.herts.sch.uk Doc Ref S of 17
6 School IT Systems Support Downloading the Software (7-zip) 1. Go to 2. Select the Download for Any Windows version ignore the blocker at this stage if it appears 3. Wait for the clock to countdown and Click on 7-Zip hyperlink 4. If a download blocker appears click on options and select Download File 5. Click on the Download box, again checking if any blocker appears as in previous step 2 of 17 Doc Ref S1218
7 School IT Systems Support 6. Select Save and choose a location to save the file to 7. When the file has been downloaded close the panel 8. Go to the location that you saved it to and double click the 7z ***.exe to initiate the installation. (The *** is the version number which you downloaded) 9. Click Run 10. Accept the default location 11. Select Install. The application will install, close the panel by the Finish button. You will now be able to encrypt files and folders that you can send by Doc Ref S of 17
8 School IT Systems Support Encrypting documents, Files or Folders 1. To encrypt your documents, files or folders run the 7Zip File Manager program 2. Select the location of the file that you wish to encrypt in the drop down box 3. Highlight the file and then select Add Browse Button Enter Password Encrypt file names The Add to Archive window will open and you will be offered a number of options. 4. Archive. This is where the encrypted document or folder will be saved. The default location is the same folder as the original document. You have the option to save to another folder by selecting the Browse button and browsing to the required folder 5. Archive Format. The default format is 7z but it is recommended that this is changed to zip format by using the dropdown option. Using the zip format means that the recipient of the will be able to use any standard zip software, including the Microsoft built-in zip compression, and therefore will have no need to install 7zip themselves 4 of 17 Doc Ref S1218
9 School IT Systems Support Change to zip 6. Enter the password that you require which should be EIGHT characters, mixing numbers and letters. Re-enter the password. The recipient of the ed document will need to know this password in order for them to open it. They should be notified of the password in a separate communication for obvious reasons 7. You can select that the file name also be encrypted if you wish. It is recommended that the file name or the subject name of the does not contain information that could identify individuals 8. All the other defaults can be left as they are 9. A file will then be created in the location that you chose. It will be the same name as the original file but with a.7z file extension (some file extension may show as.7x but behave the same) 10. Open your program, attach the encrypted document to the and then send it to the intended recipient. Please note that the recipient must also have 7- Zip installed on the PC upon which the attachment is to be opened If you have any issues installing this software then please contact your technical support provider. Doc Ref S of 17
10 School IT Systems Support To Access the File (decryption) 1. To access the file Open the and Save the encrypted document to a folder, My Documents for example Extract Enter Password 2. Open 7Zip file manager, select the document and click Extract 3. Enter the password which should have been sent in a separate communication 4. By default the decrypted document will be extracted to the same folder as where the encrypted document was saved to, now access the file using the usual application ie Microsoft Word or Excel 6 of 17 Doc Ref S1218
11 School IT Systems Support How to Securely Encrypt a Word or Excel Document (similar methods exist in the other MS Office products) Using Word Create your document 2. When finished, choose the Save As option from the File menu 3. In the Save As dialogue box, choose Tools > Security Options 4. Enter the password that you require which should be EIGHT characters, mixing numbers and letters. The recipient of the ed document will need to know this password in order for them to open it. They should be notified of the password in a separate communication for obvious reasons 5. Select the Advanced Button 6. From the dropdown in the Encryption Type Box, choose RC 4 Microsoft RSA SChannel Cryptograhic Provider 7. Click Ok Doc Ref S of 17
12 School IT Systems Support 8. Confirm your password remember that passwords cannot be recovered so ensure that you make a note of passwords and the corresponding documents 9. Click Ok and Save your document 10. Attach the document in the as required. Remember the subject of the should not identify individuals and the password should be sent to the recipient in a different communication Using Excel Create and finish your document 2. Select the File menu and choose the Save As option 3. In the Save As dialogue box, select Tools > General Options 4. The Save Options box will then open. Enter the password that you require which should be EIGHT characters, mixing numbers and letters. The recipient of the ed document will need to know this password in order for them to open it. They should be notified of the password in a separate communication for obvious reasons 8 of 17 Doc Ref S1218
13 School IT Systems Support 5. Click Advanced and in the dropdown on the Encryption Type box choose RC 4 Microsoft RSA SChannel Cryptograhic Provider 6. Click OK 7. Re-enter password - remember that passwords cannot be recovered so ensure that you make a note of passwords and the corresponding documents. Click Ok 8. Continue to Save the document to a location of your choice 9. Attach the document in the as required. Remember the subject of the should not identify individuals and the password should be sent to the recipient in a different communication. Using Word Click the Microsoft Office Button, point to Prepare 2. Select Encrypt Document 3. Enter the password that you require which should be EIGHT characters, mixing Doc Ref S of 17
14 School IT Systems Support numbers and letters. The recipient of the ed document will need to know this password in order for them to open it. They should be notified of the password in a separate communication for obvious reasons 4. Click Ok 5. Re-enter the password to confirm and click OK 6. Continue saving your document to a location of your choice 7. Click No if presented with this message 8. Attach the document in the as required. Remember the subject of the should not identify individuals and the password should be sent to the recipient in a different communication Using Excel Click the Microsoft Office Button, point to Prepare 2. Select Encrypt Document 3. Follow Steps 3 7 as per Word of 17 Doc Ref S1218
15 School IT Systems Support Removing Password Protection from a Word 2003 Document 1. Use the password to Open the document 2. Select the File menu and choose the Save As option 3. In the Save As dialogue box, select Tools > General Options 4. The Save Options box will then open, delete the passwords 5. Click Ok 6. Continue to Save your document to a location of your choice Removing Password Protection from an Excel 2003 Document 1. Open the file using the password 2. Select the File menu and choose the Save As option Doc Ref S of 17
16 School IT Systems Support 3. In the Save As dialogue box, select Tools > General Options 4. The Save Options box will then open, delete the passwords 5. Continue to Save your document to a location of your choice Removing Password Protection from a Word 2007 Document 1. Use the password to open the document 2. Click the Microsoft Office Button, point to Prepare, and then click Encrypt Document 3. In the Encrypt Document dialog box, in the Password box, delete the encrypted password, and then click OK 4. Save the file Removing Password Protection from an Excel 2007 Document 1. Do one or both of the following: Open the file using your open password and as read/write Open the file using your modify password and as read/write 2. Click the Microsoft Office Button, and then click Save As 3. Click Tools, and then click General Options 4. Select the password, and then press DELETE 12 of 17 Doc Ref S1218
17 School IT Systems Support 5. Click OK 6. Click Save 7. If prompted, click Yes to replace the existing file Doc Ref S of 17
18 School IT Systems Support Create Strong Passwords Strong passwords are important protections to help you have safer online transactions. Keys to password strength: length and complexity An ideal password is long and has letters, punctuation, symbols, and numbers Whenever possible, use at least 14 characters or more The greater the variety of characters in your password, the better Use the entire keyboard, not just the letters and characters you use or see most often Create a strong password you can remember There are many ways to create a long, complex password. Here is one way that may make remembering it easier: What to do Suggestion Example Start with a sentence or two (about 10 words total). Think of something meaningful to you. Long and complex passwords are safest. Turn your sentences into a row of letters. Use the first letter of each word. lacpasikms (10 characters) Add complexity. Make only the letters in the first half of the alphabet uppercase. lacpasikms (10 characters) Add length with numbers. Put two numbers that are meaningful to you between the two sentences. lacpas56ikms (12 characters) Add length with punctuation. Put a punctuation mark at the beginning.?lacpas56ikms (13 characters) Add length with symbols. Put a symbol at the end.?lacpas56ikms" (14 characters) 14 of 17 Doc Ref S1218
19 School IT Systems Support Protect your passwords from prying eyes The easiest way to "remember" passwords is to write them down. It is okay to write passwords down, but keep them secure. It is critical that you remember your password. If you forget your password and you have used Microsoft software, Microsoft cannot retrieve it. Store the passwords that you write down in a secure place away from the information that they help protect. Use strong passwords that combine uppercase and lowercase letters, numbers, and symbols. Weak passwords don't mix these elements. Strong password: Y6dh!et5. Weak password: House27. Passwords should be 8 or more characters in length. A pass phrase that uses 14 or more characters is better. For more information, see Help protect your personal information with strong passwords Cyber criminals use sophisticated tools that can rapidly decipher passwords. Avoid creating passwords using: o Dictionary words in any language o Words spelled backwards, common misspellings, and abbreviations o Sequences or repeated characters. Examples: , , abcdefg, or adjacent letters on your keyboard (qwerty) o Personal information. Your name, birthday, driver's license, passport number, or similar information Doc Ref S of 17
20 School IT Systems Support Top Tips for Internet Safety at Work 1. Defend your computer Keep all software current (including your Web browser) with automatic updates and install all security updates that your IT department recommends Use antivirus, antispam, and antispyware software and activate your firewall 2. Think before you share sensitive information Look for signs that a Web page is safe, before you enter sensitive personal or business data a Web address with https ( s for secure) and a closed padlock ( ) beside it Never give sensitive info in response to an or instant message (IM) request 3. Think before you click Pause before you open attachments or click links in or IM even if you know the sender; they could be phony. Confirm with the sender that the message is real or visit the official Web site by typing the address yourself Be wary of clicking links or buttons in pop-up windows 4. Use strong passwords Lock your online accounts, computer, phone, and other devices with passwords at least eight characters (longer is better), and include upper and lower case letters, numbers, and symbols Keep passwords and PINs secret. Don t disclose them to coworkers or businesses (like an Internet café operator), or be tricked into giving them away Don t use the same password everywhere 5. Protect yourself from scams Look out for alarmist messages, misspellings and grammatical errors, deals that sound too good to be true, requests for sensitive info like account numbers, and other signs of a scam Turn on a filter that warns you of suspicious Web sites 6. Protect your data on the go When you use public Wi-Fi, choose the most secure option, even if you have to pay for it. It could include password-protection and encryption Confirm the exact spelling of the wireless network you re connecting to Beware of clever (slightly misspelled) fakes 16 of 17 Doc Ref S1218
21 School IT Systems Support Encrypt the data on your laptop (or USB flash drive) in case you lose it or it s stolen using software such as Truecrypt. Instructions available on the Grid within the document network_manager_guidance_for_schools_on_data_security_may_2010.doc at Guard your laptop, smartphone, and PDA as carefully as your wallet For further information or guidance on esafety please visit the Grid at For further information or guidance on Data Security please visit the Grid at Doc Ref S of 17
How to Encrypt Files Containing Sensitive Data (using 7zip software or Microsoft password protection) How to Create Strong Passwords
 How to Encrypt Files Containing Sensitive Data (using 7zip software or Microsoft password protection) How to Create Strong Passwords School IT Systems Support Herts for Learning Ltd SROB220, Robertson
How to Encrypt Files Containing Sensitive Data (using 7zip software or Microsoft password protection) How to Create Strong Passwords School IT Systems Support Herts for Learning Ltd SROB220, Robertson
SIMS Discover Upgrade
 SIMS Discover Upgrade For use with SIMS Autumn 2014 (version 7.160) School IT Systems Support Herts for Learning Ltd SROB220, Robertson House, Six Hills Way, Stevenage, Herts, SG1 2FQ Doc Ref Error! Unknown
SIMS Discover Upgrade For use with SIMS Autumn 2014 (version 7.160) School IT Systems Support Herts for Learning Ltd SROB220, Robertson House, Six Hills Way, Stevenage, Herts, SG1 2FQ Doc Ref Error! Unknown
How to Download and Import DfE QWS QAN Catalogue and Performance Measures XML Files into SIMS
 How to Download and Import DfE QWS QAN Catalogue and Performance Measures XML Files into SIMS School IT Systems Support Herts for Learning Ltd SROB220, Robertson House, Six Hills Way, Stevenage, Herts,
How to Download and Import DfE QWS QAN Catalogue and Performance Measures XML Files into SIMS School IT Systems Support Herts for Learning Ltd SROB220, Robertson House, Six Hills Way, Stevenage, Herts,
Create strong passwords
 Create strong passwords Passwords are the first line of defense against break-ins to your online accounts and computer, tablet, or phone. Poorly chosen passwords can render your information vulnerable
Create strong passwords Passwords are the first line of defense against break-ins to your online accounts and computer, tablet, or phone. Poorly chosen passwords can render your information vulnerable
Discover Installation For use with SIMS Autumn 2014 (version 7.160)
 Discover Installation For use with SIMS Autumn 2014 (version 7.160) Please check the Server & Workstation Requirements carefully before beginning! School IT Systems Support Herts for Learning Ltd SROB220,
Discover Installation For use with SIMS Autumn 2014 (version 7.160) Please check the Server & Workstation Requirements carefully before beginning! School IT Systems Support Herts for Learning Ltd SROB220,
FAQ: Privacy, Security, and Data Protection at Libraries
 FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
Using your Employer Account
 Effective November 1, 2013, EIT Benefit Funds ( Fund Office ) the monthly Employer Work Reports are no longer sent via mail to you and are only available to be printed directly from the EIT Benefit Funds'
Effective November 1, 2013, EIT Benefit Funds ( Fund Office ) the monthly Employer Work Reports are no longer sent via mail to you and are only available to be printed directly from the EIT Benefit Funds'
Importing Pay Scales into Personnel 2016/2017
 Importing Pay Scales into Personnel 2016/2017 Please complete Document S1527 first if you HAVE APPLIED the Salary Pay Range Patch and are USING a Salary Pay Range for Teachers. School IT Systems Support
Importing Pay Scales into Personnel 2016/2017 Please complete Document S1527 first if you HAVE APPLIED the Salary Pay Range Patch and are USING a Salary Pay Range for Teachers. School IT Systems Support
Importing ATF Files into SIMS
 Importing ATF Files into SIMS Document Reference DMS004 Published/Updated May 2018 Fully accredited by Capita SIMS for proven quality of SIMS support Contact us via the ICT Service Desk at: 01438 844777
Importing ATF Files into SIMS Document Reference DMS004 Published/Updated May 2018 Fully accredited by Capita SIMS for proven quality of SIMS support Contact us via the ICT Service Desk at: 01438 844777
System Manager 7 Quick Guide (SIMS.net onwards)
 System Manager 7 Quick Guide (SIMS.net 7.142 onwards) Published December 11 School IT Systems Support Hertfordshire Development Centre Six Hills Way Stevenage SG1 2FQ Website: http://www.thegrid.org.uk/info/traded/sitss
System Manager 7 Quick Guide (SIMS.net 7.142 onwards) Published December 11 School IT Systems Support Hertfordshire Development Centre Six Hills Way Stevenage SG1 2FQ Website: http://www.thegrid.org.uk/info/traded/sitss
Safety and Security. April 2015
 Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
General Maintenance Practices for SQL Servers (SIMS Servers and Office Masters)
 General Maintenance Practices for SQL Servers (SIMS Servers and Office Masters) ICT Services Herts for Learning Ltd SROB202, Robertson House, Six Hills Way, Stevenage, Herts, SG1 2FQ Doc Ref T051 Published
General Maintenance Practices for SQL Servers (SIMS Servers and Office Masters) ICT Services Herts for Learning Ltd SROB202, Robertson House, Six Hills Way, Stevenage, Herts, SG1 2FQ Doc Ref T051 Published
Pupil Premium in SIMS: Importing the Pupil Premium CSV File and Maintaining/Updating Pupil Premium
 Pupil Premium in SIMS: Importing the Pupil Premium CSV File and Maintaining/Updating Pupil Premium Document Reference DMS060 Published/Updated September 2018 Fully accredited by Capita SIMS for proven
Pupil Premium in SIMS: Importing the Pupil Premium CSV File and Maintaining/Updating Pupil Premium Document Reference DMS060 Published/Updated September 2018 Fully accredited by Capita SIMS for proven
Enroll a New Student
 The txsuite How To Guide Series Connect tx Web-based Access for Teachers, Parents, and Students How to: Enroll a New Student Developed by the T E XA S CO M P U T E R CO O P E R AT I V E Business and Student
The txsuite How To Guide Series Connect tx Web-based Access for Teachers, Parents, and Students How to: Enroll a New Student Developed by the T E XA S CO M P U T E R CO O P E R AT I V E Business and Student
Importing Pay Scales into Personnel 2018/2019
 Importing Pay Scales into Personnel 2018/2019 Document Reference DMS017 Published/Updated April 2018 Fully accredited by Capita SIMS for proven quality of SIMS support Contact us via the ICT Service Desk
Importing Pay Scales into Personnel 2018/2019 Document Reference DMS017 Published/Updated April 2018 Fully accredited by Capita SIMS for proven quality of SIMS support Contact us via the ICT Service Desk
BEST PRACTICES FOR PERSONAL Security
 BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
Your security on click Jobs
 Your security on click Jobs At Click Jobs is a trading name of Raspberry Recruitment Limited, we're committed to helping you find the right job in a safe and secure environment. On these pages, you can
Your security on click Jobs At Click Jobs is a trading name of Raspberry Recruitment Limited, we're committed to helping you find the right job in a safe and secure environment. On these pages, you can
Quick recap on ing Security Recap on where to find things on Belvidere website & a look at the Belvidere Facebook page
 Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
STEAM Clown Production. Passwords. STEAM Clown & Productions Copyright 2016 STEAM Clown. Page 1 - Cyber Security Class
 Production Passwords Page 1 - Cyber Security Class Copyright 2016 Does It Matter? Is your email password the same as your Facebook password? Is that Good? Bad? Why? Page 2 - Cyber Security Class Copyright
Production Passwords Page 1 - Cyber Security Class Copyright 2016 Does It Matter? Is your email password the same as your Facebook password? Is that Good? Bad? Why? Page 2 - Cyber Security Class Copyright
USER MANUAL FOR SECURE E MAIL MICROSOFT OUTLOOK (2003)
 YATANARPON TELEPORT COMPANY LTD., YATANARPON CERTIFICATION AUTHORITY USER MANUAL FOR SECURE E MAIL MICROSOFT OUTLOOK (2003) Yatanarpon Teleport Company Ltd., Hlaing Universities Campus, Hlaing Township,
YATANARPON TELEPORT COMPANY LTD., YATANARPON CERTIFICATION AUTHORITY USER MANUAL FOR SECURE E MAIL MICROSOFT OUTLOOK (2003) Yatanarpon Teleport Company Ltd., Hlaing Universities Campus, Hlaing Township,
INTERNET SAFETY IS IMPORTANT
 INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
How to Build a Culture of Security
 How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
INTERNET SAFETY* GALEN GARRETSON RASCAL MARCH 2-3, * Sources include learnfree.org, PC World, wikpedia.com, techterms.com
 INTERNET SAFETY* GALEN GARRETSON RASCAL MARCH 2-3, 2016 * Sources include learnfree.org, PC World, wikpedia.com, techterms.com SOME QUESTIONS TO ASK YOURSELF. HAVE YOU.. 1. Googled yourself to see what
INTERNET SAFETY* GALEN GARRETSON RASCAL MARCH 2-3, 2016 * Sources include learnfree.org, PC World, wikpedia.com, techterms.com SOME QUESTIONS TO ASK YOURSELF. HAVE YOU.. 1. Googled yourself to see what
Signing up for My Lahey Chart
 Signing up for My Lahey Chart What is My Lahey Chart? My Lahey Chart is a helpful service that allows you to connect with your doctor and your health information online, anytime. Using your personal computer
Signing up for My Lahey Chart What is My Lahey Chart? My Lahey Chart is a helpful service that allows you to connect with your doctor and your health information online, anytime. Using your personal computer
A practical guide to IT security
 Data protection A practical guide to IT security Ideal for the small business The Data Protection Act states that appropriate technical and organisational measures shall be taken against unauthorised or
Data protection A practical guide to IT security Ideal for the small business The Data Protection Act states that appropriate technical and organisational measures shall be taken against unauthorised or
COMMON WAYS IDENTITY THEFT CAN HAPPEN:
 COMMON WAYS IDENTITY THEFT CAN HAPPEN: OLD FASHIONED STEALING / DUMPSTER DIVING Thieves typically steal wallets and purses. They also steal mail such as credit card and bank statements, pre-approved credit
COMMON WAYS IDENTITY THEFT CAN HAPPEN: OLD FASHIONED STEALING / DUMPSTER DIVING Thieves typically steal wallets and purses. They also steal mail such as credit card and bank statements, pre-approved credit
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
EVERY NATION OUTLOOK WEB ACCESS (OWA) USER S GUIDE
 EVERY NATION OUTLOOK WEB ACCESS (OWA) USER S GUIDE Exchange 2003 Version Revised September 2005 TABLE OF CONTENTS WHAT S NEW IN OWA 2003?...2 General...2 Inbox and Message Composition...2 Tasks...2 INTRODUCTION
EVERY NATION OUTLOOK WEB ACCESS (OWA) USER S GUIDE Exchange 2003 Version Revised September 2005 TABLE OF CONTENTS WHAT S NEW IN OWA 2003?...2 General...2 Inbox and Message Composition...2 Tasks...2 INTRODUCTION
Returning KS1 Phonics Screening Check Data (Year 1 Checks & Year 2 Rechecks) 2018
 Returning KS1 Phonics Screening Check Data (Year 1 Checks & Year 2 Rechecks) 2018 The FINAL deadline for submission is 5pm on Monday 25 th June 2018 The pass mark threshold for this year will be released
Returning KS1 Phonics Screening Check Data (Year 1 Checks & Year 2 Rechecks) 2018 The FINAL deadline for submission is 5pm on Monday 25 th June 2018 The pass mark threshold for this year will be released
SECURE USER GUIDE FOR EXTERNAL PARTNERS
 SECURE E-MAIL USER GUIDE FOR EXTERNAL PARTNERS A guide for using encrypted electronic mail to protect the privacy and data integrity of sensitive information. October 2016 Data Classification: Public Information
SECURE E-MAIL USER GUIDE FOR EXTERNAL PARTNERS A guide for using encrypted electronic mail to protect the privacy and data integrity of sensitive information. October 2016 Data Classification: Public Information
How Cyber-Criminals Steal and Profit from your Data
 How Cyber-Criminals Steal and Profit from your Data Presented by: Nick Podhradsky, SVP Operations SBS CyberSecurity www.sbscyber.com Consulting Network Security IT Audit Education 1 Agenda Why cybersecurity
How Cyber-Criminals Steal and Profit from your Data Presented by: Nick Podhradsky, SVP Operations SBS CyberSecurity www.sbscyber.com Consulting Network Security IT Audit Education 1 Agenda Why cybersecurity
TxEIS txconnect Training Guide August, 2012
 August, 2012 Education Service Center 3001 North Freeway Fort Worth, Texas 76106 Contents Introduction...3 How to Display a Page in another Language..4 How to Display Help 5 How to Contact the Teacher..6
August, 2012 Education Service Center 3001 North Freeway Fort Worth, Texas 76106 Contents Introduction...3 How to Display a Page in another Language..4 How to Display Help 5 How to Contact the Teacher..6
CUSTOMER TIPS: HOW TO GUARD AGAINST FRAUD WHEN USING ONLINE BANKING OR ATM s
 CUSTOMER TIPS: HOW TO GUARD AGAINST FRAUD WHEN USING ONLINE BANKING OR ATM s ATM Fraud - Watch out for the following scams. Scam 1 - you find you are having difficulty with your card. Someone will come
CUSTOMER TIPS: HOW TO GUARD AGAINST FRAUD WHEN USING ONLINE BANKING OR ATM s ATM Fraud - Watch out for the following scams. Scam 1 - you find you are having difficulty with your card. Someone will come
Registration and Login
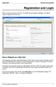 Registration and Login When a parent accesses txconnect, the following Login page is displayed. The parent needs to register as a new user. How to Register as a New User The registration process is self-administered,
Registration and Login When a parent accesses txconnect, the following Login page is displayed. The parent needs to register as a new user. How to Register as a New User The registration process is self-administered,
WHAT IS CORPORATE ACCOUNT TAKEOVER? HOW DOES IT HAPPEN?
 WHAT IS CORPORATE ACCOUNT TAKEOVER? Corporate Account Takeover (also referred to as CATO) is a type of fraud where criminals gain access to a business financial accounts to make unauthorized transactions.
WHAT IS CORPORATE ACCOUNT TAKEOVER? Corporate Account Takeover (also referred to as CATO) is a type of fraud where criminals gain access to a business financial accounts to make unauthorized transactions.
SmartJCForms User Guide
 SmartJCForms User Guide 6/18/2015 C O N T E N T S Part 1: Introduction and Getting Started... 4 Chapter 1 - Introduction SmartJCForms Overview... 5 System Requirements... 6 Installation... 6 Licensing...
SmartJCForms User Guide 6/18/2015 C O N T E N T S Part 1: Introduction and Getting Started... 4 Chapter 1 - Introduction SmartJCForms Overview... 5 System Requirements... 6 Installation... 6 Licensing...
*Updated for SIMS and above* How do I run a report? preview a report? delete a report?... 3
 *Updated for SIMS 7.153 and above* How do I......run a report?... 1...preview a report?... 2...delete a report?... 3...add a report to Favourites?... 3...download and import new reports?... 4...export
*Updated for SIMS 7.153 and above* How do I......run a report?... 1...preview a report?... 2...delete a report?... 3...add a report to Favourites?... 3...download and import new reports?... 4...export
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Duo Travel Guide. duo.com
 Duo Travel Guide duo.com Overview As a member of an organization protected by Duo, you already have secure access to applications and assets. This guide is designed to help you maintain that trusted access
Duo Travel Guide duo.com Overview As a member of an organization protected by Duo, you already have secure access to applications and assets. This guide is designed to help you maintain that trusted access
ATTACHMENTS, INSERTS, AND LINKS...
 Conventions used in this document: Keyboard keys that must be pressed will be shown as Enter or Ctrl. Objects to be clicked on with the mouse will be shown as Icon or. Cross Reference Links will be shown
Conventions used in this document: Keyboard keys that must be pressed will be shown as Enter or Ctrl. Objects to be clicked on with the mouse will be shown as Icon or. Cross Reference Links will be shown
Course Outline (version 2)
 Course Outline (version 2) Page. 1 CERTIFIED SECURE COMPUTER USER This course is aimed at end users in order to educate them about the main threats to their data s security. It also equips the students
Course Outline (version 2) Page. 1 CERTIFIED SECURE COMPUTER USER This course is aimed at end users in order to educate them about the main threats to their data s security. It also equips the students
Thank you for purchasing the CharJi EVO CLOUD. This CharJi EVO CLOUD brings you a high speed wireless network connection.
 Thank you for purchasing the CharJi EVO CLOUD. This CharJi EVO CLOUD brings you a high speed wireless network connection. This document will help you understand your CharJi EVO CLOUD so you can start using
Thank you for purchasing the CharJi EVO CLOUD. This CharJi EVO CLOUD brings you a high speed wireless network connection. This document will help you understand your CharJi EVO CLOUD so you can start using
Returning Early Years Foundation Stage Profile 2018
 Returning Early Years Foundation Stage Profile 2018 Deadline for submission is 5pm on Monday 25 th June 2018 Document Reference DMS006 Published/Updated June 2018 Fully accredited by Capita SIMS for proven
Returning Early Years Foundation Stage Profile 2018 Deadline for submission is 5pm on Monday 25 th June 2018 Document Reference DMS006 Published/Updated June 2018 Fully accredited by Capita SIMS for proven
Campus Solutions Self Service: Faculty Quick Reference Guide
 Campus Solutions Self Service: Faculty Table of Contents Introduction to Step Sheets... 1 The Faculty Center... 2 View Teaching Schedule... 3 Enter My Textbooks... 9 View Textbook Summary... 19 View Exam
Campus Solutions Self Service: Faculty Table of Contents Introduction to Step Sheets... 1 The Faculty Center... 2 View Teaching Schedule... 3 Enter My Textbooks... 9 View Textbook Summary... 19 View Exam
Useful Google Apps for Teaching and Learning
 Useful Google Apps for Teaching and Learning Centre for Development of Teaching and Learning (CDTL) National University of Singapore email: edtech@groups.nus.edu.sg Table of Contents About the Workshop...
Useful Google Apps for Teaching and Learning Centre for Development of Teaching and Learning (CDTL) National University of Singapore email: edtech@groups.nus.edu.sg Table of Contents About the Workshop...
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Microsoft Word Part 3 Office 2013
 Microsoft Word Part 3 Office 2013 Hyperlinks When a document is sent as an electronic copy, hyperlinks can be added to direct the reader to a web page. To add a hyperlink: Highlight the word, phrase, paragraph,
Microsoft Word Part 3 Office 2013 Hyperlinks When a document is sent as an electronic copy, hyperlinks can be added to direct the reader to a web page. To add a hyperlink: Highlight the word, phrase, paragraph,
Worksheet - Reading Guide for Keys and Passwords
 Unit 2 Lesson 15 Name(s) Period Date Worksheet - Reading Guide for Keys and Passwords Background Algorithms vs. Keys. An algorithm is how to execute the encryption and decryption and key is the secret
Unit 2 Lesson 15 Name(s) Period Date Worksheet - Reading Guide for Keys and Passwords Background Algorithms vs. Keys. An algorithm is how to execute the encryption and decryption and key is the secret
BitLocker to Go: Encryption for personal USB
 BitLocker to Go: Encryption for personal USB [Windows 10] Encryption is an effective method of protecting data stored on portable USB devices such as flash drives and external hard drives. Encryption encodes
BitLocker to Go: Encryption for personal USB [Windows 10] Encryption is an effective method of protecting data stored on portable USB devices such as flash drives and external hard drives. Encryption encodes
Secure Recipient Guide
 Secure Email Recipient Guide Contents How to open your first Encrypted Message.... 3 Step-by-Step Guide to Opening Your First Envelope... 3 Step One:... 3 Step Two:... 4 Step Three:... 4 Step Four:...
Secure Email Recipient Guide Contents How to open your first Encrypted Message.... 3 Step-by-Step Guide to Opening Your First Envelope... 3 Step One:... 3 Step Two:... 4 Step Three:... 4 Step Four:...
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Cyber Security. February 13, 2018 (webinar) February 15, 2018 (in-person)
 Cyber Security Presenters: - Brian Everest, Chief Technology Officer, Starport Managed Services - Susan Pawelek, Accountant, Compliance and Registrant Regulation February 13, 2018 (webinar) February 15,
Cyber Security Presenters: - Brian Everest, Chief Technology Officer, Starport Managed Services - Susan Pawelek, Accountant, Compliance and Registrant Regulation February 13, 2018 (webinar) February 15,
DLP GUIDE
 www.safetica.com I DLP GUIDE Content Introduction to context DLP protecting data with Safetica... 3 How does Safetica protect data?... 3 Exercise: Use-cases for most common scenarios... 4 Protecting data
www.safetica.com I DLP GUIDE Content Introduction to context DLP protecting data with Safetica... 3 How does Safetica protect data?... 3 Exercise: Use-cases for most common scenarios... 4 Protecting data
5 Tips to Fortify your Wireless Network
 Article ID: 5035 5 Tips to Fortify your Wireless Network Objective Although Wi-Fi networks are convenient for you and your employees, there may be unwanted clients using up the bandwidth you pay for. In
Article ID: 5035 5 Tips to Fortify your Wireless Network Objective Although Wi-Fi networks are convenient for you and your employees, there may be unwanted clients using up the bandwidth you pay for. In
PRACTICING SAFE COMPUTING AT HOME
 PRACTICING SAFE COMPUTING AT HOME WILLIAM (THE GONZ) FLINN M.S. INFORMATION SYSTEMS SECURITY MANAGEMENT; COMPTIA SECURITY+, I-NET+, NETWORK+; CERTIFIED PATCHLINK ENGINEER ENTERPRISE INFORMATION SYSTEMS
PRACTICING SAFE COMPUTING AT HOME WILLIAM (THE GONZ) FLINN M.S. INFORMATION SYSTEMS SECURITY MANAGEMENT; COMPTIA SECURITY+, I-NET+, NETWORK+; CERTIFIED PATCHLINK ENGINEER ENTERPRISE INFORMATION SYSTEMS
DLP GUIDE
 www.safetica.com DLP GUIDE Content Introduction to context DLP protecting data with Safetica... 3 How does Safetica protect data?... 3 Exercise: Use-cases for most common scenarios... 4 Protecting data
www.safetica.com DLP GUIDE Content Introduction to context DLP protecting data with Safetica... 3 How does Safetica protect data?... 3 Exercise: Use-cases for most common scenarios... 4 Protecting data
The Launch GDS can be updated via a wireless internet connection as well as by USB or cat5 cable.
 LAUNCH Wifi Setup Procedure The Launch GDS can be updated via a wireless internet connection as well as by USB or cat5 cable. If you are in a wifi hotspot or have an open network available simply choose
LAUNCH Wifi Setup Procedure The Launch GDS can be updated via a wireless internet connection as well as by USB or cat5 cable. If you are in a wifi hotspot or have an open network available simply choose
Minimum Standards for Connecting to the UCLA Network
 Minimum Standards for Connecting to the UCLA Network Last April, the CSG approved a set of minimum standards for connecting to the UCLA network that were based on a policy that had been developed by Berkeley.
Minimum Standards for Connecting to the UCLA Network Last April, the CSG approved a set of minimum standards for connecting to the UCLA network that were based on a policy that had been developed by Berkeley.
IBM Notes Client V9.0.1 Reference Guide
 IBM Notes Client V9.0.1 Reference Guide Revised 05/20/2016 1 Accessing the IBM Notes Client IBM Notes Client V9.0.1 Reference Guide From your desktop, double-click the IBM Notes icon. Logging in to the
IBM Notes Client V9.0.1 Reference Guide Revised 05/20/2016 1 Accessing the IBM Notes Client IBM Notes Client V9.0.1 Reference Guide From your desktop, double-click the IBM Notes icon. Logging in to the
Security Awareness. Presented by OSU Institute of Technology
 Security Awareness Presented by OSU Institute of Technology Information Technologies Division Security Awareness Topics Social Engineering Phishing Social Networks Displaying Sensitive Information Wireless
Security Awareness Presented by OSU Institute of Technology Information Technologies Division Security Awareness Topics Social Engineering Phishing Social Networks Displaying Sensitive Information Wireless
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
3CX Mobile Device Manager
 3CX Mobile Device Manager Manual 1 Copyright 2013, 3CX Ltd. http://www.3cx.com E-mail: info@3cx.com Information in this document is subject to change without notice. Companies names and data used in examples
3CX Mobile Device Manager Manual 1 Copyright 2013, 3CX Ltd. http://www.3cx.com E-mail: info@3cx.com Information in this document is subject to change without notice. Companies names and data used in examples
Table of Contents. User Guide
 Table of Contents Locate Laptop Laptop Tracking & Data Security 2 Feature: 2 Port Locker Stop Information & File Leaks 3 Feature 3 BitDefender Internet Security Secure Your Every Bit 3 Feature: 3 PROTEGENT
Table of Contents Locate Laptop Laptop Tracking & Data Security 2 Feature: 2 Port Locker Stop Information & File Leaks 3 Feature 3 BitDefender Internet Security Secure Your Every Bit 3 Feature: 3 PROTEGENT
Outlook Web Access (OWA) Tutorial
 Outlook Web Access (OWA) Tutorial Outlook Web Access 2010 allows you to gain access to your email messages, calendars, contact, tasks and public folders from any computer with internet access. How to access
Outlook Web Access (OWA) Tutorial Outlook Web Access 2010 allows you to gain access to your email messages, calendars, contact, tasks and public folders from any computer with internet access. How to access
VERSION 7 JUNE Union Benefits. Employer User Guide Data Collection Tool
 VERSION 7 JUNE 2018 Union Benefits Employer User Guide Data Collection Tool About this guide This document is intended to provide an overview of the main sections of the Data Collection Tool ( DCT ) for
VERSION 7 JUNE 2018 Union Benefits Employer User Guide Data Collection Tool About this guide This document is intended to provide an overview of the main sections of the Data Collection Tool ( DCT ) for
OUTLOOK WEB ACCESS UOW USER GUIDE INDEX
 OUTLOOK WEB ACCESS UOW USER GUIDE INDEX ACCESSING MAIL... 2 SETTING UP... 2 OPTIONS... 3 VIEWING... 4 ARRANGE MESSAGES... 4 CREATING/SENDING A NEW MESSAGE... 5 REPLYING TO MESSAGES... 5 FORWARDING MESSAGES...
OUTLOOK WEB ACCESS UOW USER GUIDE INDEX ACCESSING MAIL... 2 SETTING UP... 2 OPTIONS... 3 VIEWING... 4 ARRANGE MESSAGES... 4 CREATING/SENDING A NEW MESSAGE... 5 REPLYING TO MESSAGES... 5 FORWARDING MESSAGES...
Department of Technology MEDIA EXCHANGE WEB APPLICATION USER MANUAL
 Department of Technology MEDIA EXCHANGE WEB APPLICATION USER MANUAL 1 Contents: MediaShuttle Transfer Application Configuration Settings and Internet Browser Settings.... 3 Firewall Settings... 5 Username
Department of Technology MEDIA EXCHANGE WEB APPLICATION USER MANUAL 1 Contents: MediaShuttle Transfer Application Configuration Settings and Internet Browser Settings.... 3 Firewall Settings... 5 Username
KSI/KAI Cyber Security Policy / Procedures For Registered Reps
 KSI/KAI Cyber Security Policy / Procedures For Registered Reps Password Protection 1) All electronic devices used in any way for KSI/KAI business must be password protected. 2) Passwords, where applicable,
KSI/KAI Cyber Security Policy / Procedures For Registered Reps Password Protection 1) All electronic devices used in any way for KSI/KAI business must be password protected. 2) Passwords, where applicable,
On-Line Master Gardener Hours
 On-Line Master Gardener Hours 1. To Enter the Web-site log-in at http://www.four-h.purdue.edu/mg/ (This is the page to Bookmark for easy reference) a. First Name, then Last Name (not case-sensitive) b.
On-Line Master Gardener Hours 1. To Enter the Web-site log-in at http://www.four-h.purdue.edu/mg/ (This is the page to Bookmark for easy reference) a. First Name, then Last Name (not case-sensitive) b.
Best Practices Guide to Electronic Banking
 Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Identity Finder: Managing Your Results
 Updated 1/30/2012 Identity Finder: Managing Your Results The most important part of running Identity Finder is determining the most effective and secure way of managing the search results. Be sure to carefully
Updated 1/30/2012 Identity Finder: Managing Your Results The most important part of running Identity Finder is determining the most effective and secure way of managing the search results. Be sure to carefully
Edith Cowan University Information Technology Services Centre
 Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
SUMMARIES OF INTERACTIVE MULTIMEDIA
 SUMMARIES OF INTERACTIVE MULTIMEDIA GRADE 10-12 INTERNET TECHNOLOGIES 1. Introduction to Electronic Communications Use this lesson to: Understand the differences between the various e-communications modes
SUMMARIES OF INTERACTIVE MULTIMEDIA GRADE 10-12 INTERNET TECHNOLOGIES 1. Introduction to Electronic Communications Use this lesson to: Understand the differences between the various e-communications modes
Main area: Security Additional areas: Digital Access, Information Literacy, Privacy and Reputation
 Public Wi Fi Created: March 2016 Last Updated: July 2018 Estimated time: Group or individual activity: Ages: 60 minutes [10 minutes] Activity #1 [15 minutes] Activity #2 [10 minutes] Activity #3 [10 minutes]
Public Wi Fi Created: March 2016 Last Updated: July 2018 Estimated time: Group or individual activity: Ages: 60 minutes [10 minutes] Activity #1 [15 minutes] Activity #2 [10 minutes] Activity #3 [10 minutes]
IT User accounts. IT resources for McGill students. McGill ID ( a 9 digit number) Minerva PIN - (yymmdd) First time login to Minerva
 IT resources for McGill students IT User accounts First time login to Minerva McGill ID - 260123456 ( a 9 digit number) Minerva PIN - (yymmdd) Will be prompted to change the initial Minerva PIN 1 IT User
IT resources for McGill students IT User accounts First time login to Minerva McGill ID - 260123456 ( a 9 digit number) Minerva PIN - (yymmdd) Will be prompted to change the initial Minerva PIN 1 IT User
SECURITY ON PUBLIC WI-FI New Zealand. A guide to help you stay safe online while using public Wi-Fi
 SECURITY ON PUBLIC WI-FI New Zealand A guide to help you stay safe online while using public Wi-Fi WHAT S YOUR WI-FI PASSWORD? Enter password for the COFFEE_TIME Wi-Fi network An all too common question
SECURITY ON PUBLIC WI-FI New Zealand A guide to help you stay safe online while using public Wi-Fi WHAT S YOUR WI-FI PASSWORD? Enter password for the COFFEE_TIME Wi-Fi network An all too common question
Backup everything to cloud / local storage. CloudBacko Home. Essential steps to get started
 CloudBacko Home Essential steps to get started Last update: December 2, 2016 Index Step 1). Installation Step 2). Configure a new backup set, trigger a backup manually Step 3). Configure other backup set
CloudBacko Home Essential steps to get started Last update: December 2, 2016 Index Step 1). Installation Step 2). Configure a new backup set, trigger a backup manually Step 3). Configure other backup set
COMPUTER PASSWORDS POLICY
 COMPUTER PASSWORDS POLICY 1.0 PURPOSE This policy describes the requirements for acceptable password selection and maintenance to maximize security of the password and minimize its misuse or theft. Passwords
COMPUTER PASSWORDS POLICY 1.0 PURPOSE This policy describes the requirements for acceptable password selection and maintenance to maximize security of the password and minimize its misuse or theft. Passwords
Online Scams. Ready to get started? Click on the green button to continue.
 Online Scams Hi, I m Kate. We re here to learn how to protect ourselves from online scams. We ll follow along with Kevin to learn what types of scams are out there, how to recognize the warning signs,
Online Scams Hi, I m Kate. We re here to learn how to protect ourselves from online scams. We ll follow along with Kevin to learn what types of scams are out there, how to recognize the warning signs,
Table of Contents. 1. Background Logging In Account Setup Requests Submissions Discussions...
 Trust Safety: PwC Connect Tool Upload Release: Final Updated November 2018 Table of Contents 1. Background... 3 2. Logging In... 4 3. Account Setup... 8 3. Requests... 9 4. Submissions... 10 5. Discussions...
Trust Safety: PwC Connect Tool Upload Release: Final Updated November 2018 Table of Contents 1. Background... 3 2. Logging In... 4 3. Account Setup... 8 3. Requests... 9 4. Submissions... 10 5. Discussions...
2 User Guide. Contents
 E-mail User Guide 2 E-mail User Guide Contents Logging in to your web mail... 3 Changing your password... 5 Editing your signature... 6 Adding an e-mail account to Outlook 2010/2013/2016... 7 Adding an
E-mail User Guide 2 E-mail User Guide Contents Logging in to your web mail... 3 Changing your password... 5 Editing your signature... 6 Adding an e-mail account to Outlook 2010/2013/2016... 7 Adding an
OUTLOOK ATTACHMENT EXTRACTOR 3
 OUTLOOK ATTACHMENT EXTRACTOR 3 PROGRAM HELP GILLMEISTER SOFTWARE WWW.GILLMEISTER-SOFTWARE.COM 1 TABLE OF CONTENTS 1 Table of contents... 1 2 Start... 4 3 Main menu... 4 3.1 Menu entries of the group Menu...
OUTLOOK ATTACHMENT EXTRACTOR 3 PROGRAM HELP GILLMEISTER SOFTWARE WWW.GILLMEISTER-SOFTWARE.COM 1 TABLE OF CONTENTS 1 Table of contents... 1 2 Start... 4 3 Main menu... 4 3.1 Menu entries of the group Menu...
Office 365. Contents. Features, screen shots, and instructions are subject to change at any time Page 1
 Office 365 Contents Office 365..1 Accessing Your Email...3 First Time Set-Up...4 Changing Your Password. 6 The Email Environment...8 Reading Pane View...9 Reading Your Emails.10 Reading Attachments...11
Office 365 Contents Office 365..1 Accessing Your Email...3 First Time Set-Up...4 Changing Your Password. 6 The Email Environment...8 Reading Pane View...9 Reading Your Emails.10 Reading Attachments...11
Online Fraud and Identity Theft Guide. A Guide to Protecting Your Identity and Accounts
 A Guide to Protecting Your Identity and Accounts As part of SunTrust s commitment to protecting your accounts and identity, we ve created the Online Fraud & Identity Theft Guide, which provides information
A Guide to Protecting Your Identity and Accounts As part of SunTrust s commitment to protecting your accounts and identity, we ve created the Online Fraud & Identity Theft Guide, which provides information
CERTIFIED SECURE COMPUTER USER COURSE OUTLINE
 CERTIFIED SECURE COMPUTER USER COURSE OUTLINE Page 1 TABLE OF CONTENT 1 COURSE DESCRIPTION... 3 2 MODULE-1: INTRODUCTION TO DATA SECURITY... 4 3 MODULE-2: SECURING OPERATING SYSTEMS... 6 4 MODULE-3: MALWARE
CERTIFIED SECURE COMPUTER USER COURSE OUTLINE Page 1 TABLE OF CONTENT 1 COURSE DESCRIPTION... 3 2 MODULE-1: INTRODUCTION TO DATA SECURITY... 4 3 MODULE-2: SECURING OPERATING SYSTEMS... 6 4 MODULE-3: MALWARE
Quick Heal AntiVirus Pro Advanced. Protects your computer from viruses, malware, and Internet threats.
 AntiVirus Pro Advanced Protects your computer from viruses, malware, and Internet threats. Features List Ransomware Protection anti-ransomware feature is more effective and advanced than other anti-ransomware
AntiVirus Pro Advanced Protects your computer from viruses, malware, and Internet threats. Features List Ransomware Protection anti-ransomware feature is more effective and advanced than other anti-ransomware
Encrypted containers for secure file transport
 Encrypted containers for secure file transport Use Zed! encrypted containers to protect your file transports regardless of the method used (email attachment, USB stick, removable device, file transfer,
Encrypted containers for secure file transport Use Zed! encrypted containers to protect your file transports regardless of the method used (email attachment, USB stick, removable device, file transfer,
CONTENTS... 1 OVERVIEW OF SIMNET...
 CONTENTS CONTENTS... 1 OVERVIEW OF SIMNET... 3 COMPUTER REQUIREMENTS... 3 OPTIMIZING YOUR COMPUTER TO RUN SIMNET ONLINE... 3 Changing Pop-Up Blocker Setting... 3 Changing Screen Resolution Settings...
CONTENTS CONTENTS... 1 OVERVIEW OF SIMNET... 3 COMPUTER REQUIREMENTS... 3 OPTIMIZING YOUR COMPUTER TO RUN SIMNET ONLINE... 3 Changing Pop-Up Blocker Setting... 3 Changing Screen Resolution Settings...
VPN4ALL Mobile for Android 4.X Guide
 VPN4ALL Mobile for Android 4.X Guide How to setup VPN4ALL Mobile on your Android 4.X device - SmartPhone or Tablet - with an English language interface. In your Android 4.x device, go to 'Settings': Click
VPN4ALL Mobile for Android 4.X Guide How to setup VPN4ALL Mobile on your Android 4.X device - SmartPhone or Tablet - with an English language interface. In your Android 4.x device, go to 'Settings': Click
Datasheet - Sitekit CMS Secure Forms
 Datasheet - Sitekit CMS Secure Forms Registered Office Business Unit Role Document Type Document Author Document Checked by Sitekit Ltd Sitekit House Broom Place Portree Isle of Skye IV51 9HL Sitekit.Solutions
Datasheet - Sitekit CMS Secure Forms Registered Office Business Unit Role Document Type Document Author Document Checked by Sitekit Ltd Sitekit House Broom Place Portree Isle of Skye IV51 9HL Sitekit.Solutions
Installation Guide Web Browser Method
 Installation Guide Web Browser Method Table of Contents (click on the links below) Overview... 4 First Time Installation on a Windows PC... 5 First Time Installation on a Mac using FireFox (recommended)...
Installation Guide Web Browser Method Table of Contents (click on the links below) Overview... 4 First Time Installation on a Windows PC... 5 First Time Installation on a Mac using FireFox (recommended)...
FASTT Math Installation Guide
 FASTT Math Installation Guide For use with FASTT Math Enterprise Edition version 2.4 or later and Student Achievement Manager version 2.4 or later PDF0885 (PDF) Houghton Mifflin Harcourt Publishing Company
FASTT Math Installation Guide For use with FASTT Math Enterprise Edition version 2.4 or later and Student Achievement Manager version 2.4 or later PDF0885 (PDF) Houghton Mifflin Harcourt Publishing Company
Salesforce Classic Guide for iphone
 Salesforce Classic Guide for iphone Version 35.0, Winter 16 @salesforcedocs Last updated: October 27, 2015 Copyright 2000 2015 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
Salesforce Classic Guide for iphone Version 35.0, Winter 16 @salesforcedocs Last updated: October 27, 2015 Copyright 2000 2015 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
Returning Key Stage 1 Teacher Assessments 2018
 Returning Key Stage 1 Teacher Assessments 2018 The FINAL deadline for submission is 5pm on Monday 25 h June 2018 Document Reference DMS007 Published/Updated June 2018 Fully accredited by Capita SIMS for
Returning Key Stage 1 Teacher Assessments 2018 The FINAL deadline for submission is 5pm on Monday 25 h June 2018 Document Reference DMS007 Published/Updated June 2018 Fully accredited by Capita SIMS for
How to: Enroll a New Student in the District
 The txsuite How To Guide Series txconnect Parent Web-based Access for Teachers, Parents, and Students How to: Enroll a New Student in the District Developed by the T E XA S CO M P U T E R CO O P E R AT
The txsuite How To Guide Series txconnect Parent Web-based Access for Teachers, Parents, and Students How to: Enroll a New Student in the District Developed by the T E XA S CO M P U T E R CO O P E R AT
ipassconnect for Symbian User s Guide
 ipassconnect 1.50.0 for Symbian User s Guide Version: 1.0, April 07 Corporate Headquarters ipass Inc. 3800 Bridge Parkway Redwood Shores, CA 94065 USA www.ipass.com +1 650-232-4100 +1 650-232-0227 F TABLE
ipassconnect 1.50.0 for Symbian User s Guide Version: 1.0, April 07 Corporate Headquarters ipass Inc. 3800 Bridge Parkway Redwood Shores, CA 94065 USA www.ipass.com +1 650-232-4100 +1 650-232-0227 F TABLE
GHz g. Wireless A+G. User Guide. Notebook Adapter. Dual-Band. Dual-Band WPC55AG a. A Division of Cisco Systems, Inc.
 A Division of Cisco Systems, Inc. Dual-Band 5 GHz 802.11a + GHz 2.4 802.11g WIRELESS Dual-Band Wireless A+G Notebook Adapter User Guide Model No. WPC55AG Copyright and Trademarks Specifications are subject
A Division of Cisco Systems, Inc. Dual-Band 5 GHz 802.11a + GHz 2.4 802.11g WIRELESS Dual-Band Wireless A+G Notebook Adapter User Guide Model No. WPC55AG Copyright and Trademarks Specifications are subject
Getting started with Hot Potatoes by Deborah Healey
 Getting started with Hot Potatoes by Deborah Healey Hot Potatoes lets you create interactive exercises that students can do on the web or from a diskette. It has five options: JBC lets you create multiple
Getting started with Hot Potatoes by Deborah Healey Hot Potatoes lets you create interactive exercises that students can do on the web or from a diskette. It has five options: JBC lets you create multiple
K Hinds
 www.smsbarbados.wordpress.com 1 www.smsbarbados.wordpress.com 2 Editing Features Over Type Mode/Type Over mode You may engage overtype mode by hitting the INSET button on the keyboard within a word processor.
www.smsbarbados.wordpress.com 1 www.smsbarbados.wordpress.com 2 Editing Features Over Type Mode/Type Over mode You may engage overtype mode by hitting the INSET button on the keyboard within a word processor.
Guide Installation and User Guide - Mac
 Guide Installation and User Guide - Mac With Fujitsu mpollux DigiSign Client, you can use your smart card for secure access to electronic services or organization networks, as well as to digitally sign
Guide Installation and User Guide - Mac With Fujitsu mpollux DigiSign Client, you can use your smart card for secure access to electronic services or organization networks, as well as to digitally sign
