Overview and Benefits of SEEBURGER AS2 Spokes. Trading Partner Integration Using SEEBURGER'S BIS:AS2 Spoke
|
|
|
- Blake Bradford
- 6 years ago
- Views:
Transcription
1 Overview and Benefits of SEEBURGER AS2 Spokes Trading Partner Integration Using SEEBURGER'S BIS:AS2 Spoke
2 Technical Documentation Contents 1 CLASSIC EDI AND ITS COST PROBLEM VAN (VALUE ADDED NETWORK) POINT-TO-POINT SUMMARY EDIINT TO THE RESCUE HOW DOES AS2 WORK? AS2 Message Types AS2 Message Exchange SEEBURGER BIS: AS2 STAND ALONE ADMINISTRATION TRADING PARTNER MANAGEMENT MONITORING INTEGRATION SERVICES TRANSFORMATION SERVICES SECURITY AND RELIABILITY BIS:AS2 FEATURE OVERVIEW 14 Seeburger Whitepaper Page 1/15
3 1 Classic EDI and its cost problem Most modern companies face the problem of effectively exchanging business data and documents with their trading partners. Often the volume of this business data is so high that dealing with it manually becomes very costly and therefore requires a more automated and cost efficient processing solution. A way to cope with this high volume of business data is to use an EDI (Electronic Data Interchange) system to automate the communication to all trading partners using classical EDI document standards like EDIFACT, ANSI X12, TRADACOM or others. Basically EDI utilizes two main methodologies to exchange those business documents: either by using a VAN (Value added Network) service or by a direct Point-to-Point connection. 1.1 VAN (Value added Network) VAN networks do provide a simple connectivity model and provide the routing of data from the originator to the destination partners as part of their services. VAN systems at a high level are a mailbox system where you post messages; the VAN service splits those messages and delivers them to the mailbox of the different recipients (from which the recipients can download them). As of today, there are several VAN providers which offer their services either nationally and/or internationally and are quite often only utilized within a specific branch or business type. VAN providers charge for their services in various ways: some of them are based on data volume, some on the number of transmissions (documents), and some on the number of trading partners that exchange dedicated messages. Obviously the fee structures of VAN providers can cause significant expenses and can force users to avoid usage of features due to the resulting costs (such as message acknowledgments). Also it is not unusual for more horizontal oriented businesses to support a multitude of different VAN networks in order to reach all of their trading partners. Additionally, companies may also be required to deal with trading partners which are not able (or willing) to use a VAN network. Trading Partners VAN Seeburger Whitepaper Page 2/15
4 1.2 Point-to-Point By using Point-to-Point connections, you have to provide and configure a direct dial-in connection to establish a link to every single trading partner. Although you can get rid of the VAN costs utilizing this methodology, you will have to deal with dial-in configuration and provisioning as well as (long distance) call costs. Furthermore there may be availability and reliability issues associated with the Point-to-Point dial-ins. Trading Partners 1.3 Summary As we have seen, the classic EDI transport of data via VAN or Point-to-Point is not very costefficient due to either VAN provider fees or long-distance call fees. Add to this important issues like availability, reliability and the security of the data were often handled, if they where handled at all, in a very non-standard way, and you have to conclude that there must be a better way to exchange your business data with your trading partners. Seeburger Whitepaper Page 3/15
5 2 EDIINT to the rescue To address the issues described above, the Internet Engineering Task Force (IETF) established a work group called EDIINT to develop recommendations for the secure transfer of EDI data over the Internet. This work group has produced 2 draft standards for this purpose, called AS1 and AS2. Applicability Statement 1 (AS1) is a draft specification developed by the Internet Engineering Task Force (IETF) for the secure exchange of EDI/B2B data using the Simple Mail Transfer protocol (SMTP) over the Internet. Applicability Statement 2 (AS2) is a draft specification developed by the Internet Engineering Task Force (IETF) for the secure exchange of EDI/B2B data using Secure Multipurpose Internet Mail Extensions (SMIME) to encapsulate the EDI/B2B data and the Hypertext Transfer Protocol (HTTP) to transmit the data over the Internet. The basic design goal was to define standard procedures for EDI data including confidentiality, authentication and non-repudiation of receipt as well as non-repudiation of origin. AS2, which builds on existing and established Internet technologies, can be used to transport all types of data including but not limited to: XML, EDI, text, binary and so on. By using AS2 to exchange data with your trading partners and suppliers you get the following benefits compared to VAN or Point-to-Point connections: No charges for VAN services No charge for long distance calls 24/7 availability (Internet) Designed for secure and reliable data transmission over the Internet Digital Signatures provide authentication and prevents data manipulation. Encryption ensures the security of your data at all time. Supports the handling of acknowledgments to ensure your data was safely transferred and received and accepted by the recipient Utilizing the internet-based AS2 solution for your EDI exchange, can offer a very fast ROI, if you currently have to support many partners with high transaction volumes and are currently using dial ups or VAN services. Using AS2 can help you to greatly reduce or even eliminate all costs related to dial ups and VAN services. The only requirements for you to start using AS2 to exchange data with your trading partner are a persistent Internet Connection and a Software package, like SEEBURGER s AS2 Solutions, offering EDIINT AS2 capabilities. Seeburger Whitepaper Page 4/15
6 2.1 How does AS2 work? The purpose of the EDIINT AS2 (EDI over INTernet) protocol is to allow the secure exchange of EDI data over the public Internet utilizing HTTP as the transport protocol. AS2 is designed to allow the secure transmission of any type of files (but usually EDI). As AS2 utilizes the internet to exchange data with your trading partners, all you and your partners need is a persistent connection to the Internet. Trading Partners Internet AS2 Message Types AS2 uses two different message types: the actual payload message and the Message Disposition Notification (MDN). The payload message encapsulates an EDI file so that it can be transmitted via HTTP. Additionally, the payload message may be compressed, encrypted or digitally signed by the sender. The purpose of the MDN is to acknowledge the receipt of a payload message. An MDN contains machine-readable information about the delivery status of the payload message. For example, it contains the message digest (MIC) of the payload message as calculated by the recipient. An MDN may optionally be signed, in which case the recipient can authenticate the sender of the MDN and check its integrity. A valid, signed MDN together with a valid MIC reported by the MDN can be used by the sender of the payload message to claim non-repudiation of receipt (NRR) of the payload message AS2 Message Exchange In the simplest case of an AS2 message exchange, a sender packages the EDI payload file he wishes to send into an AS2 message structure and sends this message via HTTP to the receiving trading partner. Optionally the sender may compress, sign, or encrypt the AS2 message. In this simple case, the sender has no guarantee about the status of the message on the recipient s side. If the sender wants to be sure that the message has been transferred, unmodified, and that the recipient has been able to decompress or decrypt the message, he has to request an MDN from the recipient. In this case, the sender indicates the request for an MDN together Seeburger Whitepaper Page 5/15
7 with the transmission of the payload message. Basically there are two different modes in which an MDN may be delivered: Synchronous: The MDN will be delivered together with the HTTP response to the HTTP request which carried the payload message. Asynchronous MDN: The MDN will be delivered at a later time after the transmission of the payload message. In the asynchronous mode, the sender has to indicate to which address the MDN shall be delivered. The asynchronous MDN may be delivered by a separate HTTP request to the sender s web server or via to a mailbox. In order to identify the sender of an AS2 message, the trading partners have to agree upon unique identifiers, the so-called AS2-IDs. These AS2-IDs are for the most part arbitrary. The following sequence diagram shows the steps involved in data exchange via AS2. Supplier Manufacturer ERP BIS AS2 (Sender) BIS AS2 (Receiver) ERP Get Msg fro m ERP Compress Msg S E N D I N G Calculate MIC Sign Msg Encrypt Msg Send via HTTP/S Decrypt Msg Verify Signature Route Msg to ERP R E C E I V I N G Verify MIC and handle MDN Route MDN to ERP Send via HTTP/S Calculate MIC Create M DN t t t t Seeburger Whitepaper Page 6/15
8 3 Seeburger BIS: AS2 stand alone SEEBURGER offers two fully compliant AS2 solutions. A purely java based AS2 solution for stand alone use or for integration in already existing B2B/EDI infrastructure as described in this whitepaper. An AS2 module for use with the SEEBURGER Business Integration Server. See BIS: AS2 Module Whitepaper for details. SEEBURGER s AS2 solutions passed the AS2 interoperability test hosted by the Drummond group ( SEEBURGER s BIS: AS2 stand alone solution is a state of the art, purely java based application which implements the full AS2 specification including, but not limited to, the following topics: Message security Signatures Encryption Non-repudiation of origin Non-repudiation of receipt Message compression Synchronous and asynchronous delivery notifications (MDN) Beside the AS2 protocol specific features, SEEBURGER s BIS: AS2 stand alone solution offers a broad set of functionality to deliver a complete and sophisticated solution. To enable you to connect and manage your data exchange with your trading partners, SEEBURGER's AS2 stand alone solution provides the following features: Trading Partner management. Sending/receiving messages using AS2 Monitoring of message exchanges and trading partners. Backend integration Services (DB, File, Batch, Script, API) Transformation Services. Possibility to transform messages from in-house formats to a partner specific format and vice versa. Almost all relevant formats are supported (EDIFACT, ANSI X12, CVS, INHOUSE (Flat files), XML Remote administration. Seeburger Whitepaper Page 7/15
9 3.1 Administration SEEBURGER s BIS: AS2 stand alone solution exposes its whole administration and monitoring interface through a modern browser-based GUI. This provides the opportunity to remotely administer and monitor your AS2 processes from any place with a Web Browser (e.g. your desktop without the need to go to the data center where the AS2 software is physically located). The administration and monitoring always uses a secure link by utilizing the HTTP/S protocol. SEEBURGER s BIS: AS2 stand alone also offers an integrated, role based user management to assign specific access roles and levels. Seeburger Whitepaper Page 8/15
10 3.2 Trading Partner Management The management of your AS2 communication relationships with your suppliers involving master data and trading partner data is fully supported by the SEEBURGER BIS: AS2 solution. Seeburger Whitepaper Page 9/15
11 3.3 Monitoring SEEBURGER s BIS: AS2 stand alone solution provides you with the ability to monitor your ongoing AS2 exchanges anyplace, anytime, anywhere. You can monitor the ongoing exchanges and see the already completed transactions. You will also be alerted of failed transactions or any communication problem with your trading partner. The ability to utilize user defined filters for your own reporting/monitoring views is also present. 3.4 Integration Services The ability to integrate your AS2 exchanges into your backend/erp system is critical to achieve a fully automated and therefore cost effective data exchange with your trading partners. SEEBURGER s BIS: AS2 stand alone solution offers the flexibility to integrate AS2 communication into already existing EDI/B2B infrastructures or to your backend or ERP applications by offering the following integration services: DB Integration Enables you to directly integrate the received messages into any JDBC supporting database. Script Integration Allows you to include your own shell scripts into the AS2 process. Batch Integration Provides the functionality to interact with SEEBURGER s BIS: AS2 stand alone solution out of your batch processes Seeburger Whitepaper Page 10/15
12 File Integration Makes it possible to integrate with SEEBURGER BIS:AS2 stand alone solution by merely dropping messages (files) in defined folders for sending and looking in other defined folders for received messages (files) API As the most advanced of the integration options, the API allows you to control and drive every aspect of SEEBURGER s BIS: AS2 solution from your own application by using a Java based API provided by SEEBURGER. It is also possible by using this API to integrate the whole functionality of SEEBURGERS BIS: AS2 stand alone or parts of it into your own applications. Seeburger Whitepaper Page 11/15
13 3.5 Transformation Services Unlike most other AS2 solutions, SEEBURGER s solution is able to handle almost all document conversions by providing a fully functional EDI/B2B converter. If you have to send a specific document format (e.g. an ANSI X12) to your trading partner, but your backend systems can only provide another specific format (e.g. Fixed record file); SEEBURGER s BIS: AS2 stand alone can handle this conversion. SEEBURGER s BIS: AS2 stand alone solution supports the conversion for, but not limited to, formats like: EDIFACT, ANSIX12, XML (all Schema or DTD based messages), CVS, and INHOUSE (flat files like SAP IDOCS ) Seeburger Whitepaper Page 12/15
14 3.6 Security and Reliability As EDI/B2B data typically contains sensitive information (e.g. inventory reports, prices, etc ), integrity and security of data is crucial. This is especially true if this data is to be transferred using the Internet. AS2 was designed from the ground up to provide this level of safety by supporting digital signature and data encryption technologies. SEEBURGER s BIS: AS2 stand alone fully supports this requirement and adds additional role based user management including role based application permissions. Seeburger Whitepaper Page 13/15
15 4 BIS: AS2 Feature Overview Technology Java Pure java based solution OO-Design Modern OO-based design Platforms Windows WIN NT/ WIN 2000/ WIN XP LINUX SOLARIS Java All platforms with JDK >1.4 are supported. Networks TCP/IP All TCP/IP based networks. Installation Administration Automated installation Automated update Automated/Preset configuration Using Java WebStart technology. Using Java WebStart Technology. No need to do update manually. Automated distribution of a preset configuration from a central point of administration. Browser based Complete access to the application by using your local Browser. No installation needed No need to install a local GUI client. Integrated User management Restrict access rights by using the integrated user management remote Administration Remote administration and access Customizable Is easy to change the look of the GUI to your Corporate design. Centralized error handling Application firewall Security Transport Security SSL. Data-encryption RSA, DSA, IDEA. Digital Signatures RSA, ElGamal,. Customizable error-reports and actions Easy restriction of application access rights. Authentication Authentication of users and roles. Data-Transport Acknowledgements Acknowledgements for sending/receiving messages Deliver Exactly Once Recognition of duplicates. Retry Configurable retry in case of connection failure. Archiving Optional archiving of send/received data in file system. Dial-In support Support for dial-in (RAS). Seeburger Whitepaper Page 14/15
16 Conversion capabilities XML All Schema/DTD based messages. INHOUSE All fixed record based messages (e.g. SAP IDOC) CSV All delimiter separated values messages (e.g.. Excel CSV) EDIFACT All messages based on EDIFACT. ANSI X12 All messages based on ANSI X12. Integration capabilities Databases All JDBC capable databases Script/Batch-Interface Possibility to execute external scripts File Observes directories for incoming data and sends them according to the configuration. WebServices/SOAP Possibility to handle SOAP messages. API A SDK is delivered to allow application integration Connection to SEEBURGER BIS Connection to Seeburger BIS for EDI/EAI. Seeburger Whitepaper Page 15/15
Whitepaper. Boomi Integration Platform v Introduction and Technical Overview
 Whitepaper Boomi Integration Platform v3.3.0 Introduction and Technical Overview `` Boomi, Inc. 801 Cassatt Road, Suite 120 Berwyn, PA 19312 ph. 610.854.0700 fx. 610.854.0708 Page 2 of 18 Table of Contents
Whitepaper Boomi Integration Platform v3.3.0 Introduction and Technical Overview `` Boomi, Inc. 801 Cassatt Road, Suite 120 Berwyn, PA 19312 ph. 610.854.0700 fx. 610.854.0708 Page 2 of 18 Table of Contents
B2B Integration Using Seeburger AS2 Adapter with PI 7.1 Ehp1
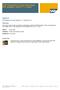 B2B Integration Using Seeburger AS2 Adapter with PI 7.1 Ehp1 Applies to: SAP NetWeaver Process Integration 7.1x, Seeburger 2.1x Summary This article is about preliminary design & configuration aspects
B2B Integration Using Seeburger AS2 Adapter with PI 7.1 Ehp1 Applies to: SAP NetWeaver Process Integration 7.1x, Seeburger 2.1x Summary This article is about preliminary design & configuration aspects
BusinessMail X AS2-Gateway
 BusinessMail X.400 - AS2-Gateway For years X.400 has been the preferred protocol for reliably transmitting EDI data. The deciding factors for this include standardized reports and tracing every mail. Using
BusinessMail X.400 - AS2-Gateway For years X.400 has been the preferred protocol for reliably transmitting EDI data. The deciding factors for this include standardized reports and tracing every mail. Using
Liaison ECS. Architecture. Introduction
 Liaison ECS Connect every corner of your enterprise with ECS, Liaison s communications server. Fluent in a wide variety of data transfer protocols and standards, ECS moves data across your enterprise and
Liaison ECS Connect every corner of your enterprise with ECS, Liaison s communications server. Fluent in a wide variety of data transfer protocols and standards, ECS moves data across your enterprise and
Copyright and Legal Disclaimers
 1 Copyright and Legal Disclaimers User Manual for DiConnect Enterprise R11. Document Release Date: June 25, 2014. Copyright 2014 by DiCentral Corporation. All rights reserved. This document and all content
1 Copyright and Legal Disclaimers User Manual for DiConnect Enterprise R11. Document Release Date: June 25, 2014. Copyright 2014 by DiCentral Corporation. All rights reserved. This document and all content
BUSINESSMAIL X.400 WEB INTERFACE AS2 GATEWAY V2.9
 GATEWAY V2.9 User information (1) In the past it was necessary to use special forms or Excel sheets for the administration of your partners and trading relations. You had to send this information to central
GATEWAY V2.9 User information (1) In the past it was necessary to use special forms or Excel sheets for the administration of your partners and trading relations. You had to send this information to central
GS1 Finland Synkka Data Pool - AS2 Connection
 Synkka Data Pool - AS2 Connection Connectivity Guide Version 0.4, Draft/Approved, 2017.06.16. Document Summary Document Item Document Name Current Value GS1 Finland Synkka Data Pool - AS2 Connection (Connectivity
Synkka Data Pool - AS2 Connection Connectivity Guide Version 0.4, Draft/Approved, 2017.06.16. Document Summary Document Item Document Name Current Value GS1 Finland Synkka Data Pool - AS2 Connection (Connectivity
BusinessMail X.400 Web interface MessageGate V3.0
 Web interface MessageGate V3.0 User information (1) In the past you had to use special forms or Excel sheets for the administration of your partners and trading relations. You had to send this information
Web interface MessageGate V3.0 User information (1) In the past you had to use special forms or Excel sheets for the administration of your partners and trading relations. You had to send this information
BusinessMail X.400 Web interface AS2 Gateway V3.0
 Web interface AS2 Gateway V3.0 User information (1) In the past it was necessary to use special forms or Excel sheets for the administration of your partners and trading relations. You had to send this
Web interface AS2 Gateway V3.0 User information (1) In the past it was necessary to use special forms or Excel sheets for the administration of your partners and trading relations. You had to send this
Redix Product Family White Paper
 A Company Name White Paper Redix International, Inc. 265 Davidson Avenue Suite 142 Somerset, NJ 08873 Phone: (888) 850-8088 Fax: (732) 302-0828 Email: info@redix.com http://www.redix.com/ Redix Product
A Company Name White Paper Redix International, Inc. 265 Davidson Avenue Suite 142 Somerset, NJ 08873 Phone: (888) 850-8088 Fax: (732) 302-0828 Email: info@redix.com http://www.redix.com/ Redix Product
DirectLine for Business AS2 USER GUIDE
 DirectLine for Business AS2 USER GUIDE Contents BMO AS2 Service...1 Introduction... 1 Overview... 1 ICS AS2 Mailbox User... 2 AS2 Mailbox Service Setup...3 Before You Begin... 3 Connectivity Testing...
DirectLine for Business AS2 USER GUIDE Contents BMO AS2 Service...1 Introduction... 1 Overview... 1 ICS AS2 Mailbox User... 2 AS2 Mailbox Service Setup...3 Before You Begin... 3 Connectivity Testing...
APPLICATION LAYER APPLICATION LAYER : DNS, HTTP, , SMTP, Telnet, FTP, Security-PGP-SSH.
 APPLICATION LAYER : DNS, HTTP, E-mail, SMTP, Telnet, FTP, Security-PGP-SSH. To identify an entity, the Internet used the IP address, which uniquely identifies the connection of a host to the Internet.
APPLICATION LAYER : DNS, HTTP, E-mail, SMTP, Telnet, FTP, Security-PGP-SSH. To identify an entity, the Internet used the IP address, which uniquely identifies the connection of a host to the Internet.
HP Instant Support Enterprise Edition (ISEE) Security overview
 HP Instant Support Enterprise Edition (ISEE) Security overview Advanced Configuration A.03.50 Mike Brandon Interex 03 / 30, 2004 2003 Hewlett-Packard Development Company, L.P. The information contained
HP Instant Support Enterprise Edition (ISEE) Security overview Advanced Configuration A.03.50 Mike Brandon Interex 03 / 30, 2004 2003 Hewlett-Packard Development Company, L.P. The information contained
Despite a number of newer and more complex file transfer requirements, we sometimes lose track of the basic needs for managing file transfers.
 GoAnywhere Director is a managed file transfer solution that manages basic file transfers and automates data movement, translation, encryption and compression processes. Despite a number of newer and more
GoAnywhere Director is a managed file transfer solution that manages basic file transfers and automates data movement, translation, encryption and compression processes. Despite a number of newer and more
USPS USPS Provisioning Services
 May 2, 2014 Manual USPS USPS Provisioning Services USPS Provisioning Services Partner Frequently Asked Questions Version 2.1 of May 2, 2014 Status: final Axway, 2014 / Version: 2.1 / Status : Final / Ref:
May 2, 2014 Manual USPS USPS Provisioning Services USPS Provisioning Services Partner Frequently Asked Questions Version 2.1 of May 2, 2014 Status: final Axway, 2014 / Version: 2.1 / Status : Final / Ref:
To start the project, launch your Visual Studio, and then Open Project FrediAppEdifact_Solution.sln
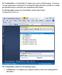 The FrediAppEdifact is a Visual Studio C# solution of an end-to-end EDI program. Its purpose is to give programmers a framework of a working EDI solution that they can build on or simply get inspiration
The FrediAppEdifact is a Visual Studio C# solution of an end-to-end EDI program. Its purpose is to give programmers a framework of a working EDI solution that they can build on or simply get inspiration
Connectivity Implementation Guide
 Version 3.0, October 2017 Document History Version Date Update Origin Written by Verified by 1.00 3/25/2011 Initial Draft Mike DeAlto Sue Merk 1.08 11/03/11 Final for customer use Sue Merk Sue Merk 2.0
Version 3.0, October 2017 Document History Version Date Update Origin Written by Verified by 1.00 3/25/2011 Initial Draft Mike DeAlto Sue Merk 1.08 11/03/11 Final for customer use Sue Merk Sue Merk 2.0
J2EE APIs and Emerging Web Services Standards
 J2EE APIs and Emerging Web Services Standards Session #4 Speaker Title Corporation 1 Agenda J2EE APIs for Web Services J2EE JAX-RPC APIs for Web Services JAX-RPC Emerging Web Services Standards Introduction
J2EE APIs and Emerging Web Services Standards Session #4 Speaker Title Corporation 1 Agenda J2EE APIs for Web Services J2EE JAX-RPC APIs for Web Services JAX-RPC Emerging Web Services Standards Introduction
Request for Comments: 5402 Category: Informational February 2010 ISSN:
 Independent Submission T. Harding, Ed. Request for Comments: 5402 Axway Category: Informational February 2010 ISSN: 2070-1721 Abstract Compressed Data within an Internet Electronic Data Interchange (EDI)
Independent Submission T. Harding, Ed. Request for Comments: 5402 Axway Category: Informational February 2010 ISSN: 2070-1721 Abstract Compressed Data within an Internet Electronic Data Interchange (EDI)
Messaging Protocols in IBM Sterling B2B Integrator - Overview and Comparison
 Messaging Protocols in IBM Sterling B2B Integrator - Overview and Comparison Aparna D Dhenge (aparna.dhenge@in.ibm.com) Kamalakannan R (rkamalakannan@in.ibm.com) Manoj Kumar Goyal (manojgoyal16@in.ibm.com)
Messaging Protocols in IBM Sterling B2B Integrator - Overview and Comparison Aparna D Dhenge (aparna.dhenge@in.ibm.com) Kamalakannan R (rkamalakannan@in.ibm.com) Manoj Kumar Goyal (manojgoyal16@in.ibm.com)
Send and Receive Exchange Use Case Test Methods
 Send and Receive Exchange Use Case Test Methods Release 1 Version 1.0 October 1, 2017 Send and Receive Exchange Test Methods Release 1 Version 1.0 Technology Sponsor [Name] [Email] [Telephone] Signature
Send and Receive Exchange Use Case Test Methods Release 1 Version 1.0 October 1, 2017 Send and Receive Exchange Test Methods Release 1 Version 1.0 Technology Sponsor [Name] [Email] [Telephone] Signature
These patterns include: The use of proprietary software
 Strategic Planning, F. Kenney, J. Thompson Research Note 7 August 2003 B2B Security Patterns: Finding the Perfect Combination Achieving business-to-business security is a combination of examining internal
Strategic Planning, F. Kenney, J. Thompson Research Note 7 August 2003 B2B Security Patterns: Finding the Perfect Combination Achieving business-to-business security is a combination of examining internal
Messenger. Installation and Configuration Guide
 Messenger Installation and Configuration Guide Manual Version 3.1 September 19, 2008 Content FURTHER INFORMATION AND SUPPORT... 4 1 INTRODUCTION... 5 1.1 ABOUT PONTON X/P... 5 1.2 ARCHITECTURE OVERVIEW...
Messenger Installation and Configuration Guide Manual Version 3.1 September 19, 2008 Content FURTHER INFORMATION AND SUPPORT... 4 1 INTRODUCTION... 5 1.1 ABOUT PONTON X/P... 5 1.2 ARCHITECTURE OVERVIEW...
WHITE PAPER. Good Mobile Intranet Technical Overview
 WHITE PAPER Good Mobile Intranet CONTENTS 1 Introduction 4 Security Infrastructure 6 Push 7 Transformations 8 Differential Data 8 Good Mobile Intranet Server Management Introduction Good Mobile Intranet
WHITE PAPER Good Mobile Intranet CONTENTS 1 Introduction 4 Security Infrastructure 6 Push 7 Transformations 8 Differential Data 8 Good Mobile Intranet Server Management Introduction Good Mobile Intranet
MOM MESSAGE ORIENTED MIDDLEWARE OVERVIEW OF MESSAGE ORIENTED MIDDLEWARE TECHNOLOGIES AND CONCEPTS. MOM Message Oriented Middleware
 MOM MESSAGE ORIENTED MOM Message Oriented Middleware MIDDLEWARE OVERVIEW OF MESSAGE ORIENTED MIDDLEWARE TECHNOLOGIES AND CONCEPTS Peter R. Egli 1/25 Contents 1. Synchronous versus asynchronous interaction
MOM MESSAGE ORIENTED MOM Message Oriented Middleware MIDDLEWARE OVERVIEW OF MESSAGE ORIENTED MIDDLEWARE TECHNOLOGIES AND CONCEPTS Peter R. Egli 1/25 Contents 1. Synchronous versus asynchronous interaction
The Collaboration Cornerstone
 E-Mail: The Collaboration Cornerstone On Demand Insurance Business Problems 1. We lose customers because we process new policy applications too slowly. 2. Our claims processing is time-consuming and inefficient.
E-Mail: The Collaboration Cornerstone On Demand Insurance Business Problems 1. We lose customers because we process new policy applications too slowly. 2. Our claims processing is time-consuming and inefficient.
SAMPLE Test for C : IBM Sterling B2B Integrator V5.2.6, Solution Implementation
 SAMPLE Test for C8060-217: IBM Sterling B2B Integrator V5.2.6, Solution Implementation This sample test is designed to give the candidate an idea of the content and format of the questions that will be
SAMPLE Test for C8060-217: IBM Sterling B2B Integrator V5.2.6, Solution Implementation This sample test is designed to give the candidate an idea of the content and format of the questions that will be
Technologies for Securing the Networked Supply Chain. Alex Deacon Advanced Products and Research Group VeriSign, Inc.
 Technologies for Securing the Networked Supply Chain Alex Deacon Advanced Products and Research Group VeriSign, Inc. Agenda Introduction Security challenges Security technologies in use today Applying
Technologies for Securing the Networked Supply Chain Alex Deacon Advanced Products and Research Group VeriSign, Inc. Agenda Introduction Security challenges Security technologies in use today Applying
BUSINESSMAIL X.400 WEB INTERFACE SMTP MTA V2.9
 V2.9 User information (1) In addition to X.400 MTA (P1 Connection) the MailGate service now also supports a SMTP MTA (Message- Gate SMTP) to bind an X.400 Domain to worldwide X.400 network. While using
V2.9 User information (1) In addition to X.400 MTA (P1 Connection) the MailGate service now also supports a SMTP MTA (Message- Gate SMTP) to bind an X.400 Domain to worldwide X.400 network. While using
Technical Overview. Access control lists define the users, groups, and roles that can access content as well as the operations that can be performed.
 Technical Overview Technical Overview Standards based Architecture Scalable Secure Entirely Web Based Browser Independent Document Format independent LDAP integration Distributed Architecture Multiple
Technical Overview Technical Overview Standards based Architecture Scalable Secure Entirely Web Based Browser Independent Document Format independent LDAP integration Distributed Architecture Multiple
Electronic Mail Paradigm
 Electronic Mail Paradigm E-mail uses the client-server model. E-mail was designed as an electronic extension of the old paper office memo. - A quick and easy means of low-overhead written communication.
Electronic Mail Paradigm E-mail uses the client-server model. E-mail was designed as an electronic extension of the old paper office memo. - A quick and easy means of low-overhead written communication.
Which Communications Protocol Is Best for B2B Integration? Comparing AS2, FTP and other popular B2B e-commerce standards
 Which Communications Protocol Is Best for B2B Integration? Comparing AS2, FTP and other popular B2B e-commerce standards John Radko, Vice President, Enterprise Architecture, GXS Rochelle Cohen, Sr. Marketing
Which Communications Protocol Is Best for B2B Integration? Comparing AS2, FTP and other popular B2B e-commerce standards John Radko, Vice President, Enterprise Architecture, GXS Rochelle Cohen, Sr. Marketing
Web Services Security. Dr. Ingo Melzer, Prof. Mario Jeckle
 Web Services Security Dr. Ingo Melzer, Prof. Mario Jeckle What is a Web Service? Infrastructure Web Service I. Melzer -- Web Services Security 2 What is a Web Service? Directory Description UDDI/WSIL WSDL
Web Services Security Dr. Ingo Melzer, Prof. Mario Jeckle What is a Web Service? Infrastructure Web Service I. Melzer -- Web Services Security 2 What is a Web Service? Directory Description UDDI/WSIL WSDL
W408 Supply Chain Interface XML
 W408 Supply Chain Interface XML Pre-requisites: none The world of e-commerce connectivity is changing rapidly. Once upon a time, realtime supply chain information came at the touch of a button -- actually,
W408 Supply Chain Interface XML Pre-requisites: none The world of e-commerce connectivity is changing rapidly. Once upon a time, realtime supply chain information came at the touch of a button -- actually,
Agenda. What is Managed File Transfer? The shortcomings of traditional file transfer solutions. Introducing WebSphere MQ File Transfer Edition
 Session 1887: Introduction to WebSphere MQ File Transfer Edition Adrian Preston (prestona@uk.ibm.com) Agenda What is Managed File Transfer? The shortcomings of traditional file transfer solutions Introducing
Session 1887: Introduction to WebSphere MQ File Transfer Edition Adrian Preston (prestona@uk.ibm.com) Agenda What is Managed File Transfer? The shortcomings of traditional file transfer solutions Introducing
Indiana Health Coverage Programs
 Indiana Health Coverage Programs Standard Companion Guide Transaction Information Communications Guide Companion Guide Version Number: 3.2 Revision Date: April 2017 April 2017 005010 3.2 1 Preface The
Indiana Health Coverage Programs Standard Companion Guide Transaction Information Communications Guide Companion Guide Version Number: 3.2 Revision Date: April 2017 April 2017 005010 3.2 1 Preface The
Mida TerraFaxPro. Overview. Why Deploy a Fax Server
 Mida TerraFaxPro Overview TerraFaxPro is the IP Fax Server (FoIP) application offered by Mida Solutions. It is based on the world leading Dialogic Brooktrout SR140 fax software and can manage incoming
Mida TerraFaxPro Overview TerraFaxPro is the IP Fax Server (FoIP) application offered by Mida Solutions. It is based on the world leading Dialogic Brooktrout SR140 fax software and can manage incoming
Chapter 17 Web Services Additional Topics
 Prof. Dr.-Ing. Stefan Deßloch AG Heterogene Informationssysteme Geb. 36, Raum 329 Tel. 0631/205 3275 dessloch@informatik.uni-kl.de Chapter 17 Web Services Additional Topics Prof. Dr.-Ing. Stefan Deßloch
Prof. Dr.-Ing. Stefan Deßloch AG Heterogene Informationssysteme Geb. 36, Raum 329 Tel. 0631/205 3275 dessloch@informatik.uni-kl.de Chapter 17 Web Services Additional Topics Prof. Dr.-Ing. Stefan Deßloch
Saperion. Release Notes. Version: 8.0
 Saperion Release Notes Version: 8.0 Written by: Product Knowledge, R&D Date: July 2017 2017 Lexmark. All rights reserved. Lexmark is a trademark of Lexmark International Inc., registered in the U.S. and/or
Saperion Release Notes Version: 8.0 Written by: Product Knowledge, R&D Date: July 2017 2017 Lexmark. All rights reserved. Lexmark is a trademark of Lexmark International Inc., registered in the U.S. and/or
Component-based Approach to the Development of Internet EDI Software for Electronic Document Management
 Association for Information Systems AIS Electronic Library (AISeL) PACIS 2001 Proceedings Pacific Asia Conference on Information Systems (PACIS) December 2001 Component-based Approach to the Development
Association for Information Systems AIS Electronic Library (AISeL) PACIS 2001 Proceedings Pacific Asia Conference on Information Systems (PACIS) December 2001 Component-based Approach to the Development
PIDX PIP Specification. P11: Send Field Ticket. Version 1.0
 PIDX PIP Specification P11: Send Field Ticket Version 1.0 July 8, 2014 Table of Contents 1 Introduction... 4 1.1 Document Purpose... 4 1.2 Document Conventions... 4 1.3 Intended Audience... 4 1.4 References...
PIDX PIP Specification P11: Send Field Ticket Version 1.0 July 8, 2014 Table of Contents 1 Introduction... 4 1.1 Document Purpose... 4 1.2 Document Conventions... 4 1.3 Intended Audience... 4 1.4 References...
Message exchange with. Finnish Customs
 Message exchange with Finnish Customs Introduction to message exchange with Finnish Customs Finnish Customs 24.8.2018 Message Exchange Support Contents Introduction... 3 1 Electronic services of Finnish
Message exchange with Finnish Customs Introduction to message exchange with Finnish Customs Finnish Customs 24.8.2018 Message Exchange Support Contents Introduction... 3 1 Electronic services of Finnish
PIDX PIP Specification. P22: Send Invoice Response. Version 1.0
 PIDX PIP Specification P22: Send Invoice Response Version 1.0 July 9, 2014 Table of Contents Document Version History... 4 1 Introduction... 5 1.1 Document Purpose... 5 1.2 Document Conventions... 5 1.3
PIDX PIP Specification P22: Send Invoice Response Version 1.0 July 9, 2014 Table of Contents Document Version History... 4 1 Introduction... 5 1.1 Document Purpose... 5 1.2 Document Conventions... 5 1.3
AS2. By John Radko, Chief Architect for GXS. A GXS White Paper for the Active Business
 AS2 By John Radko, Chief Architect for GXS for the Active Business Table of Contents Executive Summary...3 Why AS2? The Business Case...4 How AS2 Works...5 AS2 Meeting the Challenges of B2B Commerce...7
AS2 By John Radko, Chief Architect for GXS for the Active Business Table of Contents Executive Summary...3 Why AS2? The Business Case...4 How AS2 Works...5 AS2 Meeting the Challenges of B2B Commerce...7
CUSTOMER CONTROL PANEL... 2 DASHBOARD... 3 HOSTING &
 Table of Contents CUSTOMER CONTROL PANEL... 2 LOGGING IN... 2 RESET YOUR PASSWORD... 2 DASHBOARD... 3 HOSTING & EMAIL... 4 WEB FORWARDING... 4 WEBSITE... 5 Usage... 5 Subdomains... 5 SSH Access... 6 File
Table of Contents CUSTOMER CONTROL PANEL... 2 LOGGING IN... 2 RESET YOUR PASSWORD... 2 DASHBOARD... 3 HOSTING & EMAIL... 4 WEB FORWARDING... 4 WEBSITE... 5 Usage... 5 Subdomains... 5 SSH Access... 6 File
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0. Feature and Technical Overview
 BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Feature and Technical Overview SWDT305802-524791-0331031644-001 Contents 1 Overview: BlackBerry Enterprise Server... 5 New in this release...
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Feature and Technical Overview SWDT305802-524791-0331031644-001 Contents 1 Overview: BlackBerry Enterprise Server... 5 New in this release...
06/02/ Local & Metropolitan Area Networks 0. INTRODUCTION. 1. History and Future of TCP/IP ACOE322
 1 Local & Metropolitan Area Networks ACOE322 Lecture 5 TCP/IP Protocol suite and IP addressing 1 0. INTRODUCTION We shall cover in this topic: 1. The relation of TCP/IP with internet and OSI model 2. Internet
1 Local & Metropolitan Area Networks ACOE322 Lecture 5 TCP/IP Protocol suite and IP addressing 1 0. INTRODUCTION We shall cover in this topic: 1. The relation of TCP/IP with internet and OSI model 2. Internet
Implementation Guide for Delivery Notification in Direct
 Implementation Guide for Delivery Notification in Direct Contents Change Control... 2 Status of this Guide... 3 Introduction... 3 Overview... 3 Requirements... 3 1.0 Delivery Notification Messages... 4
Implementation Guide for Delivery Notification in Direct Contents Change Control... 2 Status of this Guide... 3 Introduction... 3 Overview... 3 Requirements... 3 1.0 Delivery Notification Messages... 4
Deltek Touch Expense for Ajera. Touch 1.0 Technical Installation Guide
 Deltek Touch Expense for Ajera Touch 1.0 Technical Installation Guide June 01, 2018 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical
Deltek Touch Expense for Ajera Touch 1.0 Technical Installation Guide June 01, 2018 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical
Installation Guide for 3.1.x
 CARETEND BI Installation Guide for 3.1.x TABLE OF CONTENTS DOCUMENT PURPOSE... 2 OVERVIEW... 2 PLATFORM COMPONENTS... 3 Rock-Pond BI Server... 3 CareTend BI Client Application... 3 ABOUT INSTANCES... 3
CARETEND BI Installation Guide for 3.1.x TABLE OF CONTENTS DOCUMENT PURPOSE... 2 OVERVIEW... 2 PLATFORM COMPONENTS... 3 Rock-Pond BI Server... 3 CareTend BI Client Application... 3 ABOUT INSTANCES... 3
Enterprise SOA Experience Workshop. Module 8: Operating an enterprise SOA Landscape
 Enterprise SOA Experience Workshop Module 8: Operating an enterprise SOA Landscape Agenda 1. Authentication and Authorization 2. Web Services and Security 3. Web Services and Change Management 4. Summary
Enterprise SOA Experience Workshop Module 8: Operating an enterprise SOA Landscape Agenda 1. Authentication and Authorization 2. Web Services and Security 3. Web Services and Change Management 4. Summary
Integrating with EPiServer
 Integrating with EPiServer Abstract EPiServer is an excellent tool when integration with existing systems within an organization is a requirement. This document outlines the Web services that are shipped
Integrating with EPiServer Abstract EPiServer is an excellent tool when integration with existing systems within an organization is a requirement. This document outlines the Web services that are shipped
XML ALONE IS NOT SUFFICIENT FOR EFFECTIVE WEBEDI
 Chapter 18 XML ALONE IS NOT SUFFICIENT FOR EFFECTIVE WEBEDI Fábio Ghignatti Beckenkamp and Wolfgang Pree Abstract: Key words: WebEDI relies on the Internet infrastructure for exchanging documents among
Chapter 18 XML ALONE IS NOT SUFFICIENT FOR EFFECTIVE WEBEDI Fábio Ghignatti Beckenkamp and Wolfgang Pree Abstract: Key words: WebEDI relies on the Internet infrastructure for exchanging documents among
Exactly User Guide. Contact information. GitHub repository. Download pages for application. Version
 Exactly User Guide Version 0.1 2016 01 11 Contact information AVPreserve http://www.avpreserve.com/ GitHub repository https://github.com/avpreserve/uk exactly Download pages for application Windows https://www.avpreserve.com/wp
Exactly User Guide Version 0.1 2016 01 11 Contact information AVPreserve http://www.avpreserve.com/ GitHub repository https://github.com/avpreserve/uk exactly Download pages for application Windows https://www.avpreserve.com/wp
Category: Standards Track Drummond Group C. Shih Gartner Group September 2002
 Network Working Group Request for Comments: 3335 Category: Standards Track T. Harding Cyclone Commerce R. Drummond Drummond Group C. Shih Gartner Group September 2002 Status of this Memo MIME-based Secure
Network Working Group Request for Comments: 3335 Category: Standards Track T. Harding Cyclone Commerce R. Drummond Drummond Group C. Shih Gartner Group September 2002 Status of this Memo MIME-based Secure
Don t just manage your documents. Mobilize them!
 Don t just manage your documents Mobilize them! Don t just manage your documents Mobilize them! A simple, secure way to transform how you control your documents across the Internet and in your office.
Don t just manage your documents Mobilize them! Don t just manage your documents Mobilize them! A simple, secure way to transform how you control your documents across the Internet and in your office.
for Multi-Services Gateways
 KURA an OSGi-basedApplication Framework for Multi-Services Gateways Introduction & Technical Overview Pierre Pitiot Grenoble 19 février 2014 Multi-Service Gateway Approach ESF / Increasing Value / Minimizing
KURA an OSGi-basedApplication Framework for Multi-Services Gateways Introduction & Technical Overview Pierre Pitiot Grenoble 19 février 2014 Multi-Service Gateway Approach ESF / Increasing Value / Minimizing
BlackBerry Enterprise Server Express for Microsoft Exchange
 BlackBerry Enterprise Server Express for Microsoft Exchange Version: 5.0 Service Pack: 3 Feature and Technical Overview Published: 2011-04-11 SWDT305802-1526466-0411010819-001 Contents 1 Overview: BlackBerry
BlackBerry Enterprise Server Express for Microsoft Exchange Version: 5.0 Service Pack: 3 Feature and Technical Overview Published: 2011-04-11 SWDT305802-1526466-0411010819-001 Contents 1 Overview: BlackBerry
Mobile MOUSe EXCHANGE SERVER 2010 CONFIGURATION ONLINE COURSE OUTLINE
 Mobile MOUSe EXCHANGE SERVER 2010 CONFIGURATION ONLINE COURSE OUTLINE COURSE TITLE EXCHANGE SERVER 2010 CONFIGURATION COURSE DURATION 16 Hour(s) of Interactive Training COURSE OVERVIEW Prepare for Microsoft's
Mobile MOUSe EXCHANGE SERVER 2010 CONFIGURATION ONLINE COURSE OUTLINE COURSE TITLE EXCHANGE SERVER 2010 CONFIGURATION COURSE DURATION 16 Hour(s) of Interactive Training COURSE OVERVIEW Prepare for Microsoft's
XEP-0056: Business Data Interchange
 XEP-0056: Business Data Interchange Ulrich Staudinger mailto:chicago5@gmx.de xmpp:uls@jabber.org 2018-11-03 Version 0.3.1 Status Type Short Name Deferred Standards Track N/A This document defines a way
XEP-0056: Business Data Interchange Ulrich Staudinger mailto:chicago5@gmx.de xmpp:uls@jabber.org 2018-11-03 Version 0.3.1 Status Type Short Name Deferred Standards Track N/A This document defines a way
ebxml Transport Routing and Packaging Overview and Requirements
 ebxml Transport Routing and Packaging Overview and Requirements This paper provides an overview of the Transport Routing and Packaging It describes: an overview and description of the scope of the group's
ebxml Transport Routing and Packaging Overview and Requirements This paper provides an overview of the Transport Routing and Packaging It describes: an overview and description of the scope of the group's
BlackBerry Enterprise Server Express for IBM Lotus Domino
 BlackBerry Enterprise Server Express for IBM Lotus Domino Version: 5.0 Service Pack: 3 Feature and Technical Overview Published: 2011-04-11 SWDT305802-1526466-0411011002-001 Contents 1 Overview: BlackBerry
BlackBerry Enterprise Server Express for IBM Lotus Domino Version: 5.0 Service Pack: 3 Feature and Technical Overview Published: 2011-04-11 SWDT305802-1526466-0411011002-001 Contents 1 Overview: BlackBerry
WAM!NET Direct! SM. Service Description
 WAM!NET Direct! SM Service Description INTRODUCTION The Direct! Service is a subscription based content delivery service that provides customers with the ability to send, receive, and track digital files
WAM!NET Direct! SM Service Description INTRODUCTION The Direct! Service is a subscription based content delivery service that provides customers with the ability to send, receive, and track digital files
Final Report AS4 Interoperability Test 2018
 Final Report AS4 Interoperability Test 2018 Nov 18, 2018 Prepared & Administered By: DRUMMOND GROUP http://www.drummondgroup.com/ Copyright Drummond Group 2018 AS4-2018 Final Report page 1 Table of Contents
Final Report AS4 Interoperability Test 2018 Nov 18, 2018 Prepared & Administered By: DRUMMOND GROUP http://www.drummondgroup.com/ Copyright Drummond Group 2018 AS4-2018 Final Report page 1 Table of Contents
RESOLV EDI CONTROL. User Guide Version 9.2 for HANA PRESENTED BY ACHIEVE IT SOLUTIONS
 RESOLV EDI CONTROL User Guide Version 9.2 for HANA PRESENTED BY ACHIEVE IT SOLUTIONS Copyright 2011-2016 by Achieve IT Solutions These materials are subject to change without notice. These materials are
RESOLV EDI CONTROL User Guide Version 9.2 for HANA PRESENTED BY ACHIEVE IT SOLUTIONS Copyright 2011-2016 by Achieve IT Solutions These materials are subject to change without notice. These materials are
(2½ hours) Total Marks: 75
 (2½ hours) Total Marks: 75 N. B.: (1) All questions are compulsory. (2) Makesuitable assumptions wherever necessary and state the assumptions made. (3) Answers to the same question must be written together.
(2½ hours) Total Marks: 75 N. B.: (1) All questions are compulsory. (2) Makesuitable assumptions wherever necessary and state the assumptions made. (3) Answers to the same question must be written together.
CSCE 813 Internet Security Secure Services I
 CSCE 813 Internet Security Secure E-Mail Services I Professor Lisa Luo Fall 2017 Previous Class Why do we need cloud computing? Three models of cloud service Software as a service (SaaS) Platform as a
CSCE 813 Internet Security Secure E-Mail Services I Professor Lisa Luo Fall 2017 Previous Class Why do we need cloud computing? Three models of cloud service Software as a service (SaaS) Platform as a
Fusion Registry 9 SDMX Data and Metadata Management System
 Registry 9 Data and Management System Registry 9 is a complete and fully integrated statistical data and metadata management system using. Whether you require a metadata repository supporting a highperformance
Registry 9 Data and Management System Registry 9 is a complete and fully integrated statistical data and metadata management system using. Whether you require a metadata repository supporting a highperformance
B2B STRATEGIES FOR COMPETITIVE ADVANTAGE. ebxml TRP.
 B2B STRATEGIES FOR COMPETITIVE ADVANTAGE ebxml TRP Goal The ebxml goal: To accomplish cross-industry XML-based business process integration. Business events are building blocks that must be understood.
B2B STRATEGIES FOR COMPETITIVE ADVANTAGE ebxml TRP Goal The ebxml goal: To accomplish cross-industry XML-based business process integration. Business events are building blocks that must be understood.
Contents. Microsoft is a registered trademark of Microsoft Corporation. TRAVERSE is a registered trademark of Open Systems Holdings Corp.
 TPLWPT Contents Summary... 1 General Information... 1 Technology... 2 Server Technology... 2 Business Layer... 4 Client Technology... 4 Structure... 4 Ultra-Thin Client Considerations... 7 Internet and
TPLWPT Contents Summary... 1 General Information... 1 Technology... 2 Server Technology... 2 Business Layer... 4 Client Technology... 4 Structure... 4 Ultra-Thin Client Considerations... 7 Internet and
CLEO VLTrader Made Simple Guide
 CLEO VLTrader Made Simple Guide Table of Contents Quick Reference... 3 Miscellaneous Technical Notes... 3 CLEO VLTrader at a Glance... 3 Introduction... 5 Application Page Layout... 5 Preconfigured Hosts...
CLEO VLTrader Made Simple Guide Table of Contents Quick Reference... 3 Miscellaneous Technical Notes... 3 CLEO VLTrader at a Glance... 3 Introduction... 5 Application Page Layout... 5 Preconfigured Hosts...
Preface. + Purpose of this Document. + Who Should Read this Document? + Organization of this Document. + Position of this Document.
 Preface + Purpose of this Document This document has been prepared for Interstage CollaborationRing Process Manager (hereafter, referred to as CollaborationRing PM). This product is designed to achieve
Preface + Purpose of this Document This document has been prepared for Interstage CollaborationRing Process Manager (hereafter, referred to as CollaborationRing PM). This product is designed to achieve
New Features Summary. SAP Sybase Event Stream Processor 5.1 SP02
 Summary SAP Sybase Event Stream Processor 5.1 SP02 DOCUMENT ID: DC01616-01-0512-01 LAST REVISED: April 2013 Copyright 2013 by Sybase, Inc. All rights reserved. This publication pertains to Sybase software
Summary SAP Sybase Event Stream Processor 5.1 SP02 DOCUMENT ID: DC01616-01-0512-01 LAST REVISED: April 2013 Copyright 2013 by Sybase, Inc. All rights reserved. This publication pertains to Sybase software
Electronic Transcript Processing Made Easy
 Electronic Transcript Processing Made Easy With Innovative Solutions From the Clearinghouse Joe Roof, Regional Director 10/8/2012 1 Agenda Introductions and Background Clearinghouse Transcript Options
Electronic Transcript Processing Made Easy With Innovative Solutions From the Clearinghouse Joe Roof, Regional Director 10/8/2012 1 Agenda Introductions and Background Clearinghouse Transcript Options
BlackBerry 101: An Introduction to the BlackBerry Wireless Solution
 BlackBerry 101: An Introduction to the BlackBerry Wireless Solution BlackBerry 101 Agenda What is the BlackBerry Enterprise Solution? Tracing a Message Security, Security, Security Enabling the User Extensibility:
BlackBerry 101: An Introduction to the BlackBerry Wireless Solution BlackBerry 101 Agenda What is the BlackBerry Enterprise Solution? Tracing a Message Security, Security, Security Enabling the User Extensibility:
A Signing Proxy for Web Services Security
 A Signing Proxy for Web Services Security Dr. Ingo Melzer Prof. Mario Jeckle What is a Web Service? Web Service Directory Description UDDI/WSIL WSDL Transport Content Infrastructure SOAP XML Web Service
A Signing Proxy for Web Services Security Dr. Ingo Melzer Prof. Mario Jeckle What is a Web Service? Web Service Directory Description UDDI/WSIL WSDL Transport Content Infrastructure SOAP XML Web Service
GoToMyPC Corporate Product Guide
 GoToMyPC Corporate Product Guide 072402 Contents Product Overview...1 How It Works...1 Target Audiences/Product Uses...2 Primary Selling Points...3 Software Features and Benefits...4 Administration Center
GoToMyPC Corporate Product Guide 072402 Contents Product Overview...1 How It Works...1 Target Audiences/Product Uses...2 Primary Selling Points...3 Software Features and Benefits...4 Administration Center
Revised (10/17) Overview Transmission Toolkit
 Revised (10/17) Overview Transmission Toolkit Copyright 2017 by KeyBank, N.A. Overview Transmission Toolkit All rights reserved. Reproduction of any part of this work beyond that permitted by Section 107
Revised (10/17) Overview Transmission Toolkit Copyright 2017 by KeyBank, N.A. Overview Transmission Toolkit All rights reserved. Reproduction of any part of this work beyond that permitted by Section 107
Implementing a Ground Service- Oriented Architecture (SOA) March 28, 2006
 Implementing a Ground Service- Oriented Architecture (SOA) March 28, 2006 John Hohwald Slide 1 Definitions and Terminology What is SOA? SOA is an architectural style whose goal is to achieve loose coupling
Implementing a Ground Service- Oriented Architecture (SOA) March 28, 2006 John Hohwald Slide 1 Definitions and Terminology What is SOA? SOA is an architectural style whose goal is to achieve loose coupling
The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to
 1 The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to compromises of various sorts, with a range of threats
1 The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to compromises of various sorts, with a range of threats
Final Report ebms Interoperability Test Fourth Quarter 2018 (4Q18)
 Final Report ebms Interoperability Test Fourth Quarter 2018 (4Q18) Feb 4, 2019 Prepared & Administered By: DRUMMOND GROUP, LLC http://www.drummondgroup.com/ Copyright Drummond Group, LLC 2018 ebms 4Q18
Final Report ebms Interoperability Test Fourth Quarter 2018 (4Q18) Feb 4, 2019 Prepared & Administered By: DRUMMOND GROUP, LLC http://www.drummondgroup.com/ Copyright Drummond Group, LLC 2018 ebms 4Q18
Sentinet for Microsoft Azure SENTINET
 Sentinet for Microsoft Azure SENTINET Sentinet for Microsoft Azure 1 Contents Introduction... 2 Customer Benefits... 2 Deployment Topologies... 3 Cloud Deployment Model... 3 Hybrid Deployment Model...
Sentinet for Microsoft Azure SENTINET Sentinet for Microsoft Azure 1 Contents Introduction... 2 Customer Benefits... 2 Deployment Topologies... 3 Cloud Deployment Model... 3 Hybrid Deployment Model...
DupScout DUPLICATE FILES FINDER
 DupScout DUPLICATE FILES FINDER User Manual Version 10.3 Dec 2017 www.dupscout.com info@flexense.com 1 1 Product Overview...3 2 DupScout Product Versions...7 3 Using Desktop Product Versions...8 3.1 Product
DupScout DUPLICATE FILES FINDER User Manual Version 10.3 Dec 2017 www.dupscout.com info@flexense.com 1 1 Product Overview...3 2 DupScout Product Versions...7 3 Using Desktop Product Versions...8 3.1 Product
FileDirector. Decreased costs, increased efficiency and secure access to your business documents. The New FileDirector Version 2.
 FileDirector enterprise The New FileDirector Version 2 Decreased costs, increased efficiency and secure access to your business documents The Solution that tailors itself to your Your needs Requirements
FileDirector enterprise The New FileDirector Version 2 Decreased costs, increased efficiency and secure access to your business documents The Solution that tailors itself to your Your needs Requirements
XenApp 5 Security Standards and Deployment Scenarios
 XenApp 5 Security Standards and Deployment Scenarios 2015-03-04 20:22:07 UTC 2015 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents XenApp 5 Security Standards
XenApp 5 Security Standards and Deployment Scenarios 2015-03-04 20:22:07 UTC 2015 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents XenApp 5 Security Standards
User Documentation for the Media-Saturn WebEDI-Portal from SEEBURGER (Supplier View)
 User Documentation for the Media-Saturn WebEDI-Portal from SEEBURGER (Supplier View) Version 1.1, 2016 June 24th Copyright (c) 2015 SEEBURGER AG (http://www.seeburger.com). All rights reserved. For trade
User Documentation for the Media-Saturn WebEDI-Portal from SEEBURGER (Supplier View) Version 1.1, 2016 June 24th Copyright (c) 2015 SEEBURGER AG (http://www.seeburger.com). All rights reserved. For trade
Microsoft PRO- Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010
 http://www.ipass4sure.com Microsoft PRO- Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 http://www.ipass4sure.com/exams.asp?examcode= The practice exam is written and formatted
http://www.ipass4sure.com Microsoft PRO- Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 http://www.ipass4sure.com/exams.asp?examcode= The practice exam is written and formatted
Actual4Test. Actual4test - actual test exam dumps-pass for IT exams
 Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : 000-378 Title : IBM WebSphere DataPower SOA Appliances, Firmware V3.7.3 Vendors : IBM Version : DEMO
Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : 000-378 Title : IBM WebSphere DataPower SOA Appliances, Firmware V3.7.3 Vendors : IBM Version : DEMO
Oracle B2B 11g Technical Note. Technical Note: 11g_006 Security. Table of Contents
 Oracle B2B 11g Technical Note Technical Note: 11g_006 Security This technical note lists the security options available in Oracle B2B Table of Contents Users... 2 Roles... 2 Step 1: Create the user in
Oracle B2B 11g Technical Note Technical Note: 11g_006 Security This technical note lists the security options available in Oracle B2B Table of Contents Users... 2 Roles... 2 Step 1: Create the user in
ERDAS Image Web Server Datasheet
 ERDAS Image Web Server Datasheet age 1 of 10 ERDAS Image Web Server Image serving protocols Multi-protocol support Expose images with different protocols. ERDAS Compressed Wavelet Protocol (ECWP) image
ERDAS Image Web Server Datasheet age 1 of 10 ERDAS Image Web Server Image serving protocols Multi-protocol support Expose images with different protocols. ERDAS Compressed Wavelet Protocol (ECWP) image
Application Note. Providing Secure Remote Access to Industrial Control Systems Using McAfee Firewall Enterprise (Sidewinder )
 Application Note Providing Secure Remote Access to Industrial Control Systems Using McAfee Firewall Enterprise (Sidewinder ) This document describes how to configure McAfee Firewall Enterprise to provide
Application Note Providing Secure Remote Access to Industrial Control Systems Using McAfee Firewall Enterprise (Sidewinder ) This document describes how to configure McAfee Firewall Enterprise to provide
Cisco Encryption
 This chapter contains the following sections: Overview of, page 1 How to Encrypt Messages with a Local Key Server, page 2 Encrypting Messages using the Email Security Appliance, page 3 Determining Which
This chapter contains the following sections: Overview of, page 1 How to Encrypt Messages with a Local Key Server, page 2 Encrypting Messages using the Email Security Appliance, page 3 Determining Which
User Manual. Admin Report Kit for Exchange Server
 User Manual Admin Report Kit for Exchange Server Table of Contents 1 About ARKES-Admin Report Kit for Exchange Server 1 1.1 System requirements 2 1.2 How to activate the software? 3 1.3 ARKES Reports Primer
User Manual Admin Report Kit for Exchange Server Table of Contents 1 About ARKES-Admin Report Kit for Exchange Server 1 1.1 System requirements 2 1.2 How to activate the software? 3 1.3 ARKES Reports Primer
Installing and Configuring VMware vcenter Orchestrator
 Installing and Configuring VMware vcenter Orchestrator vcenter Orchestrator 4.2.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
Installing and Configuring VMware vcenter Orchestrator vcenter Orchestrator 4.2.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
Web Mechanisms. Draft: 2/23/13 6:54 PM 2013 Christopher Vickery
 Web Mechanisms Draft: 2/23/13 6:54 PM 2013 Christopher Vickery Introduction While it is perfectly possible to create web sites that work without knowing any of their underlying mechanisms, web developers
Web Mechanisms Draft: 2/23/13 6:54 PM 2013 Christopher Vickery Introduction While it is perfectly possible to create web sites that work without knowing any of their underlying mechanisms, web developers
Managing Different Interfaces in Electronic Commerce
 Managing Different s in Electronic Commerce Christian Huemer Institute of Applied Computer Science and Information Systems, University of Vienna, Austria, e-mail: ch@ifs.univie.ac.at Abstract During the
Managing Different s in Electronic Commerce Christian Huemer Institute of Applied Computer Science and Information Systems, University of Vienna, Austria, e-mail: ch@ifs.univie.ac.at Abstract During the
Legacy Integrator for SAP NetWeaver. I n t e g r a t i o n o f S A P N e t W e a v e r w i t h b a c k - o f f i c e a p p l i c a t i o n s
 Technical Brief Legacy Integrator for NetWeaver I n t e g r a t i o n o f S A P N e t W e a v e r w i t h b a c k - o f f i c e a p p l i c a t i o n s CONTENTS Executive Summary 2 Overview: architecture
Technical Brief Legacy Integrator for NetWeaver I n t e g r a t i o n o f S A P N e t W e a v e r w i t h b a c k - o f f i c e a p p l i c a t i o n s CONTENTS Executive Summary 2 Overview: architecture
Enabling Embedded Systems to access Internet Resources
 Enabling Embedded Systems to access Internet Resources Embedded Internet Book www.embeddedinternet.org 2 Agenda : RATIONALE Web Services: INTRODUCTION HTTP Protocol: REVIEW HTTP Protocol Bindings Testing
Enabling Embedded Systems to access Internet Resources Embedded Internet Book www.embeddedinternet.org 2 Agenda : RATIONALE Web Services: INTRODUCTION HTTP Protocol: REVIEW HTTP Protocol Bindings Testing
Provide Real-Time Data To Financial Applications
 Provide Real-Time Data To Financial Applications DATA SHEET Introduction Companies typically build numerous internal applications and complex APIs for enterprise data access. These APIs are often engineered
Provide Real-Time Data To Financial Applications DATA SHEET Introduction Companies typically build numerous internal applications and complex APIs for enterprise data access. These APIs are often engineered
Identity & security CLOUDCARD+ When security meets convenience
 Identity & security CLOUDCARD+ When security meets convenience CLOUDCARD+ When security meets convenience We live in an ever connected world. Digital technology is leading the way to greater mobility and
Identity & security CLOUDCARD+ When security meets convenience CLOUDCARD+ When security meets convenience We live in an ever connected world. Digital technology is leading the way to greater mobility and
