PVS Subscription Registration Process
|
|
|
- Merilyn Terry
- 6 years ago
- Views:
Transcription
1 PVS Subscription Registration Process Create Your Tenable Support Portal Account 1. Click on the provided link to create your account. If the link does not work, please cut and paste the entire URL into your browser. 2. The End User will need to click Click Here to Start. Continuous View, Passive Vulnerability Scanner, and Log Correlation Engine are trademarks of Tenable Network Security, Inc. All other products or services are trademarks of their
2 3. If you do not already have a Tenable Support Portal account (this is not the same as a Tenable Store account, which is for purchasing only and not providing support services), click on New Customer. 4. Fill in the requested information with a valid corporate address that will be used for the login to the Tenable Support Portal. 2
3 5. If you already have an account on the Tenable Support Portal, you still need to click on the URL to merge the new Activation Code with your existing account by selecting Existing Customer. 6. Provide your Customer ID, Registered Address, and Tenable Support Portal account password, then click Search. 7. From the drop-down list, select the contact you would like to assign the product to, and then click Submit. 3
4 8. After verifying your account information, you will receive a product activation confirmation page that includes your Activation Code, Expiration Date, and directions to download your product. Download PVS 1. If you need to download PVS, go to the Downloads link in the Tenable Support Portal. 4
5 2. Click Passive Vulnerability Scanner. Install Activation Code 1. To obtain your Activation Code, select Activation Codes from the main page of your Tenable Support Portal account. 5
6 2. Click + next to PVS Subscription. The Activation Code is listed under the Activation Code column. 3. Install the Activation Code for your PVS subscription according to the following directions: For More Information PVS documentation can be found here: More information about Tenable Support Portal features can be found here: If you experience any problems with the registration process, please contact licenses@tenable.com. Please direct all support related questions to support@tenable.com and provide your Customer ID. You may also log in to the Tenable Support Portal and open a ticket. About Tenable Network Security Tenable Network Security transforms security technology for the business needs of tomorrow through comprehensive solutions that provide continuous visibility and critical context, enabling decisive actions to protect your organization. Tenable eliminates blind spots, prioritizes threats, and reduces exposure and loss. With more than one million users and more than 20,000 enterprise customers worldwide, organizations trust Tenable for proven security innovation. Tenable's customers range from Fortune Global 500 companies, to the U.S. Department of Defense, to mid-sized and small businesses in all sectors, including finance, government, healthcare, higher education, retail, and energy. Transform security with Tenable, the creators of Nessus and leaders in continuous monitoring, by visiting tenable.com. 6
Nessus Manager Registration Process
 Nessus Manager Registration Process These instructions are provided to help managers of Nessus Manager to get started in using the software. You will need to retrieve the Activation Code from your Tenable
Nessus Manager Registration Process These instructions are provided to help managers of Nessus Manager to get started in using the software. You will need to retrieve the Activation Code from your Tenable
How to Register for Training
 How to Register for Training We have created a Training Console to help you manage your Tenable training from the Tenable Support Portal. You will be able to enroll in On Demand Training Course(s) or Certification
How to Register for Training We have created a Training Console to help you manage your Tenable training from the Tenable Support Portal. You will be able to enroll in On Demand Training Course(s) or Certification
How to Add, Deactivate, or Edit a Contact
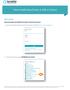 How to Add, Deactivate, or Edit a Contact Add Contact (Add account option only available to the Primary Contact for the account) 1. Log in to the Tenable Support Portal with authorized credentials: https://support.tenable.com/
How to Add, Deactivate, or Edit a Contact Add Contact (Add account option only available to the Primary Contact for the account) 1. Log in to the Tenable Support Portal with authorized credentials: https://support.tenable.com/
How-to Guide: Tenable.io for Lieberman. Last Revised: August 14, 2018
 How-to Guide: Tenable.io for Lieberman RED Last Revised: August 14, 2018 Table of Contents Introduction 3 Integrations 4 Windows Integration 5 SSH Integration 11 Database Integration 17 Additional Information
How-to Guide: Tenable.io for Lieberman RED Last Revised: August 14, 2018 Table of Contents Introduction 3 Integrations 4 Windows Integration 5 SSH Integration 11 Database Integration 17 Additional Information
How-to Guide: Tenable Nessus for BeyondTrust. Last Revised: November 13, 2018
 How-to Guide: Tenable Nessus for BeyondTrust Last Revised: November 13, 2018 Table of Contents Welcome to Nessus for BeyondTrust 3 Integrations 4 Windows Integration 5 SSH Integration 10 API Configuration
How-to Guide: Tenable Nessus for BeyondTrust Last Revised: November 13, 2018 Table of Contents Welcome to Nessus for BeyondTrust 3 Integrations 4 Windows Integration 5 SSH Integration 10 API Configuration
How-to Guide: Tenable Core Web Application Scanner for Microsoft Azure. Last Updated: May 16, 2018
 How-to Guide: Tenable Core Web Application Scanner for Microsoft Azure Last Updated: May 16, 2018 Table of Contents How-to Guide: Tenable Core Web Application Scanner for Microsoft Azure 1 Introduction
How-to Guide: Tenable Core Web Application Scanner for Microsoft Azure Last Updated: May 16, 2018 Table of Contents How-to Guide: Tenable Core Web Application Scanner for Microsoft Azure 1 Introduction
Tenable.io for Thycotic
 How-To Guide Tenable.io for Thycotic Introduction This document describes how to deploy Tenable.io for integration with Thycotic Secret Server. Please email any comments and suggestions to support@tenable.com.
How-To Guide Tenable.io for Thycotic Introduction This document describes how to deploy Tenable.io for integration with Thycotic Secret Server. Please email any comments and suggestions to support@tenable.com.
How-to Guide: Tenable.io for Microsoft Azure. Last Updated: November 16, 2018
 How-to Guide: Tenable.io for Microsoft Azure Last Updated: November 16, 2018 Table of Contents How-to Guide: Tenable.io for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
How-to Guide: Tenable.io for Microsoft Azure Last Updated: November 16, 2018 Table of Contents How-to Guide: Tenable.io for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
Tenable for McAfee epolicy Orchestrator
 HOW-TO GUIDE Tenable for McAfee epolicy Orchestrator Introduction This document describes how to deploy Tenable SecurityCenter for integration with McAfee epolicy Orchestrator (epo). Please email any comments
HOW-TO GUIDE Tenable for McAfee epolicy Orchestrator Introduction This document describes how to deploy Tenable SecurityCenter for integration with McAfee epolicy Orchestrator (epo). Please email any comments
How-to Guide: Tenable Nessus for Microsoft Azure. Last Updated: April 03, 2018
 How-to Guide: Tenable Nessus for Microsoft Azure Last Updated: April 03, 2018 Table of Contents How-to Guide: Tenable Nessus for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
How-to Guide: Tenable Nessus for Microsoft Azure Last Updated: April 03, 2018 Table of Contents How-to Guide: Tenable Nessus for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
How to Transition from Nessus to SecurityCenter Reports
 HOW-TO GUIDE How to Transition from Nessus to SecurityCenter Reports Using SecurityCenter for continuous network monitoring and vulnerability assessment will give you a greatly expanded set of features
HOW-TO GUIDE How to Transition from Nessus to SecurityCenter Reports Using SecurityCenter for continuous network monitoring and vulnerability assessment will give you a greatly expanded set of features
Tenable for McAfee epolicy Orchestrator
 How-To Guide Tenable for McAfee epolicy Orchestrator Introduction This document describes how to deploy Tenable SecurityCenter for integration with McAfee epolicy Orchestrator (epo). Please email any comments
How-To Guide Tenable for McAfee epolicy Orchestrator Introduction This document describes how to deploy Tenable SecurityCenter for integration with McAfee epolicy Orchestrator (epo). Please email any comments
How-to Guide: Tenable for McAfee epolicy Orchestrator. Last Updated: April 03, 2018
 How-to Guide: Tenable for McAfee epolicy Orchestrator Last Updated: April 03, 2018 Table of Contents How-to Guide: Tenable for McAfee epolicy Orchestrator 1 Introduction 3 Integration Requirements 4 Tenable
How-to Guide: Tenable for McAfee epolicy Orchestrator Last Updated: April 03, 2018 Table of Contents How-to Guide: Tenable for McAfee epolicy Orchestrator 1 Introduction 3 Integration Requirements 4 Tenable
Tenable for Google Cloud Platform
 How-To Guide Tenable for Google Cloud Platform Introduction This document describes how to deploy Tenable SecurityCenter Continuous View (Security Center CV ) for integration with Google Cloud Platform.
How-To Guide Tenable for Google Cloud Platform Introduction This document describes how to deploy Tenable SecurityCenter Continuous View (Security Center CV ) for integration with Google Cloud Platform.
Tenable for Palo Alto Networks
 How-To Guide Tenable for Palo Alto Networks Introduction This document describes how to deploy Tenable SecurityCenter and Nessus for integration with Palo Alto Networks next-generation firewalls (NGFW).
How-To Guide Tenable for Palo Alto Networks Introduction This document describes how to deploy Tenable SecurityCenter and Nessus for integration with Palo Alto Networks next-generation firewalls (NGFW).
Tenable Nessus Customer Loyalty Program to Purchase PVS Subscription
 Tenable Nessus Customer Loyalty Program to Purchase PVS Subscription Tenable is providing an opportunity for current Nessus customers to purchase a subscription to Tenable s Passive Vulnerability Scanner
Tenable Nessus Customer Loyalty Program to Purchase PVS Subscription Tenable is providing an opportunity for current Nessus customers to purchase a subscription to Tenable s Passive Vulnerability Scanner
Services. This document. describes how comments and. it is in. Tenable.io and. Tenable.io
 Tenable.io for Amazon Web Services Introduction This document describes how to deploy Tenable.io for integration with Amazon Web Services (AWS). Please email any comments and suggestions to support@tenable.com.
Tenable.io for Amazon Web Services Introduction This document describes how to deploy Tenable.io for integration with Amazon Web Services (AWS). Please email any comments and suggestions to support@tenable.com.
A Government Health Agency Trusts Tenable to Protect Patient Data and Manage Expanding Attack Surface
 A Government Health Agency Trusts Tenable to Protect Patient Data and Manage Expanding Attack Surface ORGANIZATION SNAPSHOT The level of visibility Tenable.io provides is phenomenal, something we just
A Government Health Agency Trusts Tenable to Protect Patient Data and Manage Expanding Attack Surface ORGANIZATION SNAPSHOT The level of visibility Tenable.io provides is phenomenal, something we just
Tenable for ServiceNow. Last Updated: March 19, 2018
 Tenable for ServiceNow Last Updated: March 19, 2018 Table of Contents Tenable for ServiceNow 1 Introduction 3 Integration Requirements 4 Integration Configuration 5 Set up a Query in SecurityCenter 5 Configure
Tenable for ServiceNow Last Updated: March 19, 2018 Table of Contents Tenable for ServiceNow 1 Introduction 3 Integration Requirements 4 Integration Configuration 5 Set up a Query in SecurityCenter 5 Configure
Tenable Network Security Support Portal. November 9, 2010 (Revision 8)
 Tenable Network Security Support Portal November 9, 2010 (Revision 8) Table of Contents TABLE OF CONTENTS... 2 INTRODUCTION... 3 OBTAINING ACCESS TO THE TENABLE SUPPORT PORTAL... 3 MANAGING YOUR NESSUS
Tenable Network Security Support Portal November 9, 2010 (Revision 8) Table of Contents TABLE OF CONTENTS... 2 INTRODUCTION... 3 OBTAINING ACCESS TO THE TENABLE SUPPORT PORTAL... 3 MANAGING YOUR NESSUS
2017 Trends in Security Metrics and Security Assurance Measurement Report A Survey of IT Security Professionals
 2017 Trends in Security Metrics and Security Assurance Measurement Report A Survey of IT Security Professionals Sponsored by Contents Introduction....3 Key Takeaways from the 2017 Report:....3 Security
2017 Trends in Security Metrics and Security Assurance Measurement Report A Survey of IT Security Professionals Sponsored by Contents Introduction....3 Key Takeaways from the 2017 Report:....3 Security
Transforming Security from Defense in Depth to Comprehensive Security Assurance
 Transforming Security from Defense in Depth to Comprehensive Security Assurance February 28, 2016 Revision #3 Table of Contents Introduction... 3 The problem: defense in depth is not working... 3 The new
Transforming Security from Defense in Depth to Comprehensive Security Assurance February 28, 2016 Revision #3 Table of Contents Introduction... 3 The problem: defense in depth is not working... 3 The new
Protecting Critical Infrastructure. SCADA Network Security Monitoring
 Protecting Critical Infrastructure SCADA Network Security Monitoring March 20, 2015 Table of Contents I. Introduction... 4 SCADA Systems... 4 In This Paper... 4 SCADA Security... 4 Assessing the Security
Protecting Critical Infrastructure SCADA Network Security Monitoring March 20, 2015 Table of Contents I. Introduction... 4 SCADA Systems... 4 In This Paper... 4 SCADA Security... 4 Assessing the Security
PATRON PORTAL LOG-IN GUIDE
 PATRON PORTAL LOG-IN GUIDE BASIC LOG-IN...2 RETRIEVING PATRON PORTAL USERNAME...6 RETRIEVING PATRON PORTAL PASSWORD...9 ACCESSING SUBSCRIBER PRE-SALE TICKETS...12 FOR ADDITIONAL QUESTIONS OR ASSISTANCE:
PATRON PORTAL LOG-IN GUIDE BASIC LOG-IN...2 RETRIEVING PATRON PORTAL USERNAME...6 RETRIEVING PATRON PORTAL PASSWORD...9 ACCESSING SUBSCRIBER PRE-SALE TICKETS...12 FOR ADDITIONAL QUESTIONS OR ASSISTANCE:
SecurityCenter 4.8.x Upgrade Guide. December 16, 2014 (Revision 1)
 SecurityCenter 4.8.x Upgrade Guide December 16, 2014 (Revision 1) Table of Contents Introduction... 3 Standards and Conventions... 3 Software Requirements... 4 Supported Operating Systems... 4 Dependencies...
SecurityCenter 4.8.x Upgrade Guide December 16, 2014 (Revision 1) Table of Contents Introduction... 3 Standards and Conventions... 3 Software Requirements... 4 Supported Operating Systems... 4 Dependencies...
UTM Firewall Registration & Activation Manual DFL-260/ 860. Ver 1.00 Network Security Solution
 UTM Firewall Registration & Activation Manual DFL-260/ 860 Ver 1.00 curitycu Network Security Solution http://security.dlink.com.tw 1.Introduction...02 2.Apply for a D-Link Membership...03 3.D-Link NetDefend
UTM Firewall Registration & Activation Manual DFL-260/ 860 Ver 1.00 curitycu Network Security Solution http://security.dlink.com.tw 1.Introduction...02 2.Apply for a D-Link Membership...03 3.D-Link NetDefend
Speed Up Incident Response with Actionable Forensic Analytics
 WHITEPAPER DATA SHEET Speed Up Incident Response with Actionable Forensic Analytics Close the Gap between Threat Detection and Effective Response with Continuous Monitoring January 15, 2015 Table of Contents
WHITEPAPER DATA SHEET Speed Up Incident Response with Actionable Forensic Analytics Close the Gap between Threat Detection and Effective Response with Continuous Monitoring January 15, 2015 Table of Contents
Tenable SCAP Standards Declarations. June 4, 2015 (Revision 11)
 Tenable SCAP Standards Declarations June 4, 2015 (Revision 11) Table of Contents Center for Internet Security (CIS)... 3 Common Criteria (NIAP)... 3 Common Vulnerability Enumeration (CVE)... 3 Common Configuration
Tenable SCAP Standards Declarations June 4, 2015 (Revision 11) Table of Contents Center for Internet Security (CIS)... 3 Common Criteria (NIAP)... 3 Common Vulnerability Enumeration (CVE)... 3 Common Configuration
rat ITarian Service Desk End-User Guide Software version 4.16 Guide version ITarian 1255 Broad Street Clifton, NJ 07013
 rat ITarian Service Desk End-User Guide Software version 4.16 Guide version 4.16.110618 ITarian 1255 Broad Street Clifton, NJ 07013 Introduction to Service Desk Module ITarian Service Desk is a web based
rat ITarian Service Desk End-User Guide Software version 4.16 Guide version 4.16.110618 ITarian 1255 Broad Street Clifton, NJ 07013 Introduction to Service Desk Module ITarian Service Desk is a web based
Reinvent Your 2013 Security Management Strategy
 Reinvent Your 2013 Security Management Strategy Laurent Boutet 18 septembre 2013 Phone:+33 6 25 34 12 01 Email:laurent.boutet@skyboxsecurity.com www.skyboxsecurity.com What are Your Key Objectives for
Reinvent Your 2013 Security Management Strategy Laurent Boutet 18 septembre 2013 Phone:+33 6 25 34 12 01 Email:laurent.boutet@skyboxsecurity.com www.skyboxsecurity.com What are Your Key Objectives for
Comodo cwatch Web Security Software Version 1.0
 rat Comodo cwatch Web Security Software Version 1.0 Webhost Reseller Guide Guide Version 1.0.121916 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
rat Comodo cwatch Web Security Software Version 1.0 Webhost Reseller Guide Guide Version 1.0.121916 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
See What You ve Been Missing
 Distribuidor autorizado See What You ve Been Missing Gain unprecedented visibility and intelligence of your attack surface SOLUTIONS OVERVIEW Vulnerability and Threat Management Security Policy Management
Distribuidor autorizado See What You ve Been Missing Gain unprecedented visibility and intelligence of your attack surface SOLUTIONS OVERVIEW Vulnerability and Threat Management Security Policy Management
Tenable Hardware Appliance Upgrade Guide
 Tenable Hardware Appliance Upgrade Guide June 4, 2012 (Revision 3) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/tenable_hardware_appliance_upgrade.pdf
Tenable Hardware Appliance Upgrade Guide June 4, 2012 (Revision 3) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/tenable_hardware_appliance_upgrade.pdf
Comodo Certificate Manager
 Comodo Certificate Manager Simple, Automated & Robust SSL Management from the #1 Provider of Digital Certificates 1 Datasheet Table of Contents Introduction 3 CCM Overview 4 Certificate Discovery Certificate
Comodo Certificate Manager Simple, Automated & Robust SSL Management from the #1 Provider of Digital Certificates 1 Datasheet Table of Contents Introduction 3 CCM Overview 4 Certificate Discovery Certificate
July 18, (Revision 3)
 3D Tool 2.0 User Guide July 18, 2011 (Revision 3) Copyright 2011. Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of Tenable Network Security,
3D Tool 2.0 User Guide July 18, 2011 (Revision 3) Copyright 2011. Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of Tenable Network Security,
SOLUTION BRIEF. RiskSense Platform. RiskSense Platform the industry s most comprehensive, intelligent platform for managing cyber risk.
 RiskSense Platform RiskSense Platform the industry s most comprehensive, intelligent platform for managing cyber risk. 27 RiskSense, Inc. Executive Summary The RiskSense Platform is a Software-as-a-Service
RiskSense Platform RiskSense Platform the industry s most comprehensive, intelligent platform for managing cyber risk. 27 RiskSense, Inc. Executive Summary The RiskSense Platform is a Software-as-a-Service
Skybox Product Tour. Installation and Starting Your Product Tour Tour Login Credentials: User Name: skyboxview Password: skyboxview
 Skybox Product Tour Installation and Starting Your Product Tour Tour Login Credentials: User Name: skyboxview Password: skyboxview The tour uses the same User Name / Password for each module This Product
Skybox Product Tour Installation and Starting Your Product Tour Tour Login Credentials: User Name: skyboxview Password: skyboxview The tour uses the same User Name / Password for each module This Product
Microsoft Office 365 Integration. Administrator Guide
 Administrator Guide Contents Contents DOCUMENT CHANGE HISTORY...3 ABOUT MICROSOFT OFFICE 365 INTEGRATION WITH BRIGHTSPACE LEARNING ENVIRONMENT...4 MICROSOFT OFFICE 365 PERMISSIONS...4 BROWSER CONSIDERATION
Administrator Guide Contents Contents DOCUMENT CHANGE HISTORY...3 ABOUT MICROSOFT OFFICE 365 INTEGRATION WITH BRIGHTSPACE LEARNING ENVIRONMENT...4 MICROSOFT OFFICE 365 PERMISSIONS...4 BROWSER CONSIDERATION
Threat Centric Vulnerability Management
 Threat Centric Vulnerability Management Solution Brief When it comes to vulnerability management, security leaders continue struggle to identify which of the thousands even millions of vulnerabilities
Threat Centric Vulnerability Management Solution Brief When it comes to vulnerability management, security leaders continue struggle to identify which of the thousands even millions of vulnerabilities
Instructions on accessing your journal s content on your new app
 Instructions on accessing your journal s content on your new app There are three main methods to access content on your journal app depending on how you normally view your journal online. 1. Do you normally
Instructions on accessing your journal s content on your new app There are three main methods to access content on your journal app depending on how you normally view your journal online. 1. Do you normally
SecOps : Security Operations. Saurav Sinha Head of Presales India
 SecOps : Security Operations Saurav Sinha Head of Presales India 1 The World s Best and Most Innovative Companies Trust BMC #1 Ranked ITOM Vendor by Gartner for 3 consecutive years 300+ Patents $8B Investment
SecOps : Security Operations Saurav Sinha Head of Presales India 1 The World s Best and Most Innovative Companies Trust BMC #1 Ranked ITOM Vendor by Gartner for 3 consecutive years 300+ Patents $8B Investment
Comodo cwatch Web Security Software Version 1.1
 rat Comodo cwatch Web Security Software Version 1.1 Quick Start Guide Guide Version 1.1.092117 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo cwatch Web Security Quick Start Guide
rat Comodo cwatch Web Security Software Version 1.1 Quick Start Guide Guide Version 1.1.092117 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo cwatch Web Security Quick Start Guide
Vulnerability Management
 Vulnerability Management Modern Vulnerability Management The IT landscape today is changing and because of that, vulnerability management needs to change too. IT environments today are filled with both
Vulnerability Management Modern Vulnerability Management The IT landscape today is changing and because of that, vulnerability management needs to change too. IT environments today are filled with both
Step 1 - Go to Step 2 - Login to your account. Step 3 - Click Register for a Test. Step 4 - Read the Requirements
 Step 1 - Go to www.texes.ets.org Go to www.texes.ets.org Click the register link found in the top navigation. Step 2 - Login to your account Enter your username and password and click login. If you do
Step 1 - Go to www.texes.ets.org Go to www.texes.ets.org Click the register link found in the top navigation. Step 2 - Login to your account Enter your username and password and click login. If you do
WorldRisk. Travel Guard Assistance Website User Guide
 WorldRisk Travel Guard Assistance Website User Guide WorldRisk Through WorldRisk, you can access AIG s Travel Guard Assistance services through an exclusive, members-only website. Read below for instructions
WorldRisk Travel Guard Assistance Website User Guide WorldRisk Through WorldRisk, you can access AIG s Travel Guard Assistance services through an exclusive, members-only website. Read below for instructions
Log Correlation Engine 4.4 Statistics Daemon Guide. February 26, 2015 (Revision 1)
 Log Correlation Engine 4.4 Statistics Daemon Guide February 26, 2015 (Revision 1) Table of Contents Introduction... Standards and Conventions... Basic Operation... Configuring the Statistics Daemon...
Log Correlation Engine 4.4 Statistics Daemon Guide February 26, 2015 (Revision 1) Table of Contents Introduction... Standards and Conventions... Basic Operation... Configuring the Statistics Daemon...
SecurityCenter Upgrade Guide. July 21, 2015 (Revision 1)
 SecurityCenter 5.0.1 Upgrade Guide July 21, 2015 (Revision 1) Table of Contents Introduction... 3 Standards and Conventions... 3 Software Requirements... 4 Supported Operating Systems... 4 Dependencies...
SecurityCenter 5.0.1 Upgrade Guide July 21, 2015 (Revision 1) Table of Contents Introduction... 3 Standards and Conventions... 3 Software Requirements... 4 Supported Operating Systems... 4 Dependencies...
Installation of RHEL 5 for Tenable SecurityCenter Evaluation
 Installation of RHEL 5 for Tenable SecurityCenter Evaluation These instructions are for the installation of Red Hat Enterprise Linux (RHEL) 5 in preparation for installing Tenable SecurityCenter 4.4 for
Installation of RHEL 5 for Tenable SecurityCenter Evaluation These instructions are for the installation of Red Hat Enterprise Linux (RHEL) 5 in preparation for installing Tenable SecurityCenter 4.4 for
Tenable.sc-Tenable.io Upgrade Assistant Guide, Version 2.0. Last Revised: January 16, 2019
 Tenable.sc-Tenable.io Upgrade Assistant Guide, Version 2.0 Last Revised: January 16, 2019 Table of Contents Welcome to the Tenable.sc-Tenable.io Upgrade Assistant 3 Get Started 4 Environment Requirements
Tenable.sc-Tenable.io Upgrade Assistant Guide, Version 2.0 Last Revised: January 16, 2019 Table of Contents Welcome to the Tenable.sc-Tenable.io Upgrade Assistant 3 Get Started 4 Environment Requirements
SecurityCenter 5.1 Upgrade Guide. November 12, 2015 (Revision 2)
 SecurityCenter 5.1 Upgrade Guide November 12, 2015 (Revision 2) Table of Contents Introduction... 3 Standards and Conventions... 3 Software Requirements... 4 Supported Operating Systems... 4 Dependencies...
SecurityCenter 5.1 Upgrade Guide November 12, 2015 (Revision 2) Table of Contents Introduction... 3 Standards and Conventions... 3 Software Requirements... 4 Supported Operating Systems... 4 Dependencies...
Brightspace Binder for ios. Learner Guide
 Learner Guide Contents Contents DOCUMENT CHANGE HISTORY... 3 BINDER BASICS... 3 About Brightspace Binder... 3 Supported devices and platform versions... 4 How Brightspace Binder works... 4 About document
Learner Guide Contents Contents DOCUMENT CHANGE HISTORY... 3 BINDER BASICS... 3 About Brightspace Binder... 3 Supported devices and platform versions... 4 How Brightspace Binder works... 4 About document
Brightspace Binder for ios. Learner Guide
 Learner Guide Contents Contents DOCUMENT CHANGE HISTORY...3 BINDER BASICS...3 About Brightspace Binder...3 Supported devices and platform versions...4 How Brightspace Binder works...4 About document storage
Learner Guide Contents Contents DOCUMENT CHANGE HISTORY...3 BINDER BASICS...3 About Brightspace Binder...3 Supported devices and platform versions...4 How Brightspace Binder works...4 About document storage
How to log a Sitefinity Support case
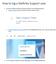 How to log a Sitefinity Support case 1. Access the Progress SupportLink portal via either of the following options: Sitefinity Support Center and click on Open a Support Ticket: Progress Support and Learning
How to log a Sitefinity Support case 1. Access the Progress SupportLink portal via either of the following options: Sitefinity Support Center and click on Open a Support Ticket: Progress Support and Learning
Verizon Enterprise Center Registration/Login User Guide
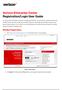 Registration/Login User Guide It is best to have an invitation code prior to beginning enrollment. You can find your invitation code on your monthly invoice. If you do not have your monthly invoice, you
Registration/Login User Guide It is best to have an invitation code prior to beginning enrollment. You can find your invitation code on your monthly invoice. If you do not have your monthly invoice, you
IBM Internet Security Systems Proventia Management SiteProtector
 Supporting compliance and mitigating risk through centralized management of enterprise security devices IBM Internet Security Systems Proventia Management SiteProtector Highlights Reduces the costs and
Supporting compliance and mitigating risk through centralized management of enterprise security devices IBM Internet Security Systems Proventia Management SiteProtector Highlights Reduces the costs and
Web Application Firewall Subscription on Cyberoam UTM appliances
 On-Appliance Reporting Web Application Firewall Subscription on Cyberoam UTM appliances Protecting Web Applications from hackers Application Visibility and Control Bandwidth Management Firewall Web Application
On-Appliance Reporting Web Application Firewall Subscription on Cyberoam UTM appliances Protecting Web Applications from hackers Application Visibility and Control Bandwidth Management Firewall Web Application
Milestone Systems. Quick guide: Register software license codes on Milestone Customer Dashboard. Milestone Customer Dashboard
 Milestone Systems Quick guide: Register software license codes on Milestone Customer Dashboard Milestone Customer Dashboard Introduction to this guide This quick guide introduces Milestone partners how
Milestone Systems Quick guide: Register software license codes on Milestone Customer Dashboard Milestone Customer Dashboard Introduction to this guide This quick guide introduces Milestone partners how
2018 GLOBAL CHANNEL PARTNER SURVEY THYCOTIC CHANNEL PARTNER SURVEY REPORT
 2018 GLOBAL CHANNEL PARTNER SURVEY THYCOTIC CHANNEL PARTNER SURVEY REPORT THYCOTIC 2018 GLOBAL CHANNEL PARTNER SURVEY Channel Partner survey highlights client cybersecurity concerns and opportunities for
2018 GLOBAL CHANNEL PARTNER SURVEY THYCOTIC CHANNEL PARTNER SURVEY REPORT THYCOTIC 2018 GLOBAL CHANNEL PARTNER SURVEY Channel Partner survey highlights client cybersecurity concerns and opportunities for
Chapter 5: Vulnerability Analysis
 Chapter 5: Vulnerability Analysis Technology Brief Vulnerability analysis is a part of the scanning phase. In the Hacking cycle, vulnerability analysis is a major and important part. In this chapter, we
Chapter 5: Vulnerability Analysis Technology Brief Vulnerability analysis is a part of the scanning phase. In the Hacking cycle, vulnerability analysis is a major and important part. In this chapter, we
Brightspace Binder for Web. Learner Guide
 Learner Guide Contents Contents DOCUMENT CHANGE HISTORY... 3 BINDER BASICS... 3 About Brightspace Binder... 3 Supported devices and platform versions... 4 How Brightspace Binder works... 4 About document
Learner Guide Contents Contents DOCUMENT CHANGE HISTORY... 3 BINDER BASICS... 3 About Brightspace Binder... 3 Supported devices and platform versions... 4 How Brightspace Binder works... 4 About document
The SANS Institute Top 20 Critical Security Controls. Compliance Guide
 The SANS Institute Top 20 Critical Security Controls Compliance Guide February 2014 The Need for a Risk-Based Approach A common factor across many recent security breaches is that the targeted enterprise
The SANS Institute Top 20 Critical Security Controls Compliance Guide February 2014 The Need for a Risk-Based Approach A common factor across many recent security breaches is that the targeted enterprise
SVPN 5.0 SSL Service User Guide
 SVPN 5.0 SSL Service User Guide First Published: May 21, 2017 Last Updated: May 21, 2017 The SVPN 5.0 SSL Service User Guide is intended to provide users with the information needed to connect to their
SVPN 5.0 SSL Service User Guide First Published: May 21, 2017 Last Updated: May 21, 2017 The SVPN 5.0 SSL Service User Guide is intended to provide users with the information needed to connect to their
1. Entering subscription information
 1. Entering subscription information 1.1 1.2 Go to the page below: http://www.cognibox.com/en/install-cognibox/open-an-account/ or http://www.cognibox.com 1.1 Fill in the three (3) required fields (Full
1. Entering subscription information 1.1 1.2 Go to the page below: http://www.cognibox.com/en/install-cognibox/open-an-account/ or http://www.cognibox.com 1.1 Fill in the three (3) required fields (Full
VMware License Registration Guide
 VMware License Registration Guide Thank you for purchasing VMware pre-installed on your NEC server. NEC has created this guide to walk you through the process of obtaining license key(s) for your VMware
VMware License Registration Guide Thank you for purchasing VMware pre-installed on your NEC server. NEC has created this guide to walk you through the process of obtaining license key(s) for your VMware
Dell Management Portal. Apple Device Enrollment Program
 Dell Management Portal Contents 3 Setting up the 3 DMP Device Deployment Program Prerequisites 4 Configure Apple VPP Token in DMP 5 Download Apple VPP Token 5 Assign VPP App Licenses 7 Configure Virtual
Dell Management Portal Contents 3 Setting up the 3 DMP Device Deployment Program Prerequisites 4 Configure Apple VPP Token in DMP 5 Download Apple VPP Token 5 Assign VPP App Licenses 7 Configure Virtual
ADP Security Management Service
 ADP Security Management Service Securing Administrator Accounts Updated March 2017 Welcome! Your administrators complete the security registration process to access the ADP services your organization has
ADP Security Management Service Securing Administrator Accounts Updated March 2017 Welcome! Your administrators complete the security registration process to access the ADP services your organization has
Network Online Services How to Register Guide
 Network Online Services How to Register Guide June 2016 How to Register... 2 Subscription... 5 Update My Profile... 7 Update Registration Details... 7 Contact Details / Postal Address... 15 How To Register
Network Online Services How to Register Guide June 2016 How to Register... 2 Subscription... 5 Update My Profile... 7 Update Registration Details... 7 Contact Details / Postal Address... 15 How To Register
Comodo One Software Version 3.26
 rat Comodo One Software Version 3.26 Service Desk End-User Guide Guide Version 4.16.1130118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Introduction to Service Desk Module Comodo Service
rat Comodo One Software Version 3.26 Service Desk End-User Guide Guide Version 4.16.1130118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Introduction to Service Desk Module Comodo Service
TROUBLE TICKET REPORTING TOOL. User Guide v1
 TROUBLE TICKET REPORTING TOOL User Guide v1 OVERVIEW & ACCOUNT SET UP Document Sections Overview and Account Set Up Dashboard Help Desk Account Settings Frequently Asked Questions 2018 Comcast. All rights
TROUBLE TICKET REPORTING TOOL User Guide v1 OVERVIEW & ACCOUNT SET UP Document Sections Overview and Account Set Up Dashboard Help Desk Account Settings Frequently Asked Questions 2018 Comcast. All rights
Virtual Classroom and Video Assignments by YouSeeU - Learner Guide. Learner Guide
 Virtual Classroom and Video Assignments by YouSeeU - Learner Guide Learner Guide Contents Contents DOCUMENT CHANGE HISTORY...3 ATTEND A VIRTUAL CLASSROOM SESSION...4 COMPLETING A VIDEO ASSIGNMENT...4 Submit
Virtual Classroom and Video Assignments by YouSeeU - Learner Guide Learner Guide Contents Contents DOCUMENT CHANGE HISTORY...3 ATTEND A VIRTUAL CLASSROOM SESSION...4 COMPLETING A VIDEO ASSIGNMENT...4 Submit
Vendor Portal Frequently Asked Questions
 Vendor Portal Frequently Asked Questions What website should I use for the Finance and Data Management Portals?... 2 What is the DPI Vendor Shipment Portal?... 2 Who should I contact for questions about
Vendor Portal Frequently Asked Questions What website should I use for the Finance and Data Management Portals?... 2 What is the DPI Vendor Shipment Portal?... 2 Who should I contact for questions about
D2L Binder for Android. Learner Guide
 Learner Guide Contents Contents DOCUMENT CHANGE HISTORY... 3 BINDER BASICS... 3 About Brightspace Binder... 3 Supported devices and platform versions... 4 How Brightspace Binder works... 4 About document
Learner Guide Contents Contents DOCUMENT CHANGE HISTORY... 3 BINDER BASICS... 3 About Brightspace Binder... 3 Supported devices and platform versions... 4 How Brightspace Binder works... 4 About document
How to Secure Your Cloud with...a Cloud?
 A New Era of Thinking How to Secure Your Cloud with...a Cloud? Eitan Worcel Offering Manager - Application Security on Cloud IBM Security 1 2016 IBM Corporation 1 A New Era of Thinking Agenda IBM Cloud
A New Era of Thinking How to Secure Your Cloud with...a Cloud? Eitan Worcel Offering Manager - Application Security on Cloud IBM Security 1 2016 IBM Corporation 1 A New Era of Thinking Agenda IBM Cloud
Access auto, commercial, home and life solutions from a single entry point.
 User Guide LexisNexis Insurance Solutions Interactive/Online Order Processing Access auto, commercial, home and life solutions from a single entry point. INS0157 -- 19 April 2017 Insurance Solutions Support
User Guide LexisNexis Insurance Solutions Interactive/Online Order Processing Access auto, commercial, home and life solutions from a single entry point. INS0157 -- 19 April 2017 Insurance Solutions Support
Creating a Parent Portal Account
 Creating a Parent Portal Account Step 1: Go to https://focus.bayschools.net/focus/auth Step 2: Click on I DO NOT have an Account Registered on the Parent Portal but my child is Actively Enrolled Welcome
Creating a Parent Portal Account Step 1: Go to https://focus.bayschools.net/focus/auth Step 2: Click on I DO NOT have an Account Registered on the Parent Portal but my child is Actively Enrolled Welcome
Brightspace Platform Release Notes
 Brightspace Platform 10.7.11 Release Notes 10. Select Delete Topic from the drop-down menu beside the /shared/ path topic item, and select Permanently delete both the topic from Content and the associated
Brightspace Platform 10.7.11 Release Notes 10. Select Delete Topic from the drop-down menu beside the /shared/ path topic item, and select Permanently delete both the topic from Content and the associated
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE
 DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
Software Support Registration
 Software Support Registration Purpose This document is to show the multiple workflows for registering for online access to the Software Support site for Schlumberger. Contents Purpose... 1 Quick Guide...
Software Support Registration Purpose This document is to show the multiple workflows for registering for online access to the Software Support site for Schlumberger. Contents Purpose... 1 Quick Guide...
OWA Security & Enhancements
 END-POINT SECURITY Messageware is a world leader in Microsoft Exchange and Outlook Web App security and productivity solutions. Our software is used by over 5 million users worldwide and has been recognized
END-POINT SECURITY Messageware is a world leader in Microsoft Exchange and Outlook Web App security and productivity solutions. Our software is used by over 5 million users worldwide and has been recognized
So You Want To Throw A Party? How to create ticket links in NeonCRM for CSPC Events
 So You Want To Throw A Party? How to create ticket links in NeonCRM for CSPC Events Background: We use our Neon CRM software to create ticket links for our events Using NeonCRM to create our ticket links
So You Want To Throw A Party? How to create ticket links in NeonCRM for CSPC Events Background: We use our Neon CRM software to create ticket links for our events Using NeonCRM to create our ticket links
Rat. Service Desk. Quick Start Guide. Software version 4.16 Guide version ITarian 1255 Broad Street Clifton, NJ 07013
 Rat Service Desk Quick Start Guide Software version 4.16 Guide version 4.16.110618 ITarian 1255 Broad Street Clifton, NJ 07013 Itarian Service Desk - Quick Start Guide This tutorial explains how ITarian
Rat Service Desk Quick Start Guide Software version 4.16 Guide version 4.16.110618 ITarian 1255 Broad Street Clifton, NJ 07013 Itarian Service Desk - Quick Start Guide This tutorial explains how ITarian
IBM Managed Security Services for X-Force Hosted Threat Analysis Service
 IBM Managed Security Services for X-Force Hosted Threat Analysis Service Z125-8483-00 05-2010 Page 1 of 5 Table of Contents 1. Scope of Services... 3 1.1 Licensing... 3 1.1.1 Individual... 3 1.1.2 Distribution...
IBM Managed Security Services for X-Force Hosted Threat Analysis Service Z125-8483-00 05-2010 Page 1 of 5 Table of Contents 1. Scope of Services... 3 1.1 Licensing... 3 1.1.1 Individual... 3 1.1.2 Distribution...
Tenable Common Criteria Evaluated Configuration Guide. October 29, 2009 (Revision 4)
 Tenable Common Criteria Evaluated Configuration Guide October 29, 2009 (Revision 4) Table of Contents TABLE OF CONTENTS... 2 OVERVIEW... 3 SECURITY CENTER COMPONENTS... 3 NESSUS VULNERABILITY SCANNER...
Tenable Common Criteria Evaluated Configuration Guide October 29, 2009 (Revision 4) Table of Contents TABLE OF CONTENTS... 2 OVERVIEW... 3 SECURITY CENTER COMPONENTS... 3 NESSUS VULNERABILITY SCANNER...
Make Wi-Fi Simple and Secure for Google Apps, BYOD, and More. 21 April 2016
 Make Wi-Fi Simple and Secure for Google Apps, BYOD, and More 21 April 2016 Today s Speaker Bruce Miller VP Product Marketing Xirrus, Inc. bruce.miller@xirrus.com @bmiller715 2 Agenda 1 2 3 4 5 6 7 Introduction
Make Wi-Fi Simple and Secure for Google Apps, BYOD, and More 21 April 2016 Today s Speaker Bruce Miller VP Product Marketing Xirrus, Inc. bruce.miller@xirrus.com @bmiller715 2 Agenda 1 2 3 4 5 6 7 Introduction
Tenable.io User Guide. Last Revised: November 03, 2017
 Tenable.io User Guide Last Revised: November 03, 2017 Table of Contents Tenable.io User Guide 1 Getting Started with Tenable.io 10 Tenable.io Workflow 12 System Requirements 15 Scanners and Agents 16 Link
Tenable.io User Guide Last Revised: November 03, 2017 Table of Contents Tenable.io User Guide 1 Getting Started with Tenable.io 10 Tenable.io Workflow 12 System Requirements 15 Scanners and Agents 16 Link
Supplier Module Supplier Registration
 Vendor Management System Supplier Module December 4, 2009 Supplier Module Vendor Management System Proprietary Information: Not for use or disclosure outside Flowserve, except under written agreement.
Vendor Management System Supplier Module December 4, 2009 Supplier Module Vendor Management System Proprietary Information: Not for use or disclosure outside Flowserve, except under written agreement.
VNC Connect security whitepaper. VNC Connect. Instant support FAQs
 VNC Connect security whitepaper VNC Connect Instant support FAQs September 2017 Contents General FAQs... 3 Technician and end user FAQs... 5 Administration and audit FAQs... 7 General FAQs Note: For more
VNC Connect security whitepaper VNC Connect Instant support FAQs September 2017 Contents General FAQs... 3 Technician and end user FAQs... 5 Administration and audit FAQs... 7 General FAQs Note: For more
Brightspace Platform Release Notes
 Brightspace Platform 10.7.5 Release Notes 1 5. Enroll a learner to this course. 6. Impersonate the learner you enrolled and navigate to the Org home page. 7. Under the My Courses widget, click View All
Brightspace Platform 10.7.5 Release Notes 1 5. Enroll a learner to this course. 6. Impersonate the learner you enrolled and navigate to the Org home page. 7. Under the My Courses widget, click View All
NSTIP Portal Registration Manual NSTIP Portal Registration Manual
 NSTIP Portal Registration Manual Jan 2013 1 Contents 1. Introduction to NSTIP Portal... 3 2. Steps... 4 2.1. Registration... 4 2.2. Login... 6 2.3. Update Profile... 8 2 1. Introduction to NSTIP Portal
NSTIP Portal Registration Manual Jan 2013 1 Contents 1. Introduction to NSTIP Portal... 3 2. Steps... 4 2.1. Registration... 4 2.2. Login... 6 2.3. Update Profile... 8 2 1. Introduction to NSTIP Portal
Compliance Audit Readiness. Bob Kral Tenable Network Security
 Compliance Audit Readiness Bob Kral Tenable Network Security Agenda State of the Market Drifting Out of Compliance Continuous Compliance Top 5 Hardest To Sustain PCI DSS Requirements Procedural support
Compliance Audit Readiness Bob Kral Tenable Network Security Agenda State of the Market Drifting Out of Compliance Continuous Compliance Top 5 Hardest To Sustain PCI DSS Requirements Procedural support
SelfService Portal. Step By Step Documentation. This document will show you how to enroll your user account to the SelfService Portal
 SelfService Portal Step By Step Documentation This document will show you how to enroll your user account to the SelfService Portal There are three types of Authentication 1. Security Questions 2. Verification
SelfService Portal Step By Step Documentation This document will show you how to enroll your user account to the SelfService Portal There are three types of Authentication 1. Security Questions 2. Verification
User Communication Citrix SecureAuth
 Prerequisites 1 *Non-Newmont PC ONLY* If you are using any PC except your Newmont issued system, you must follow this step if you are using your Newmont issued system you can move to First Time Enrollment
Prerequisites 1 *Non-Newmont PC ONLY* If you are using any PC except your Newmont issued system, you must follow this step if you are using your Newmont issued system you can move to First Time Enrollment
ForeScout Extended Module for Qualys VM
 ForeScout Extended Module for Qualys VM Version 1.2.1 Table of Contents About the Qualys VM Integration... 3 Additional Qualys VM Documentation... 3 About This Module... 3 Components... 4 Considerations...
ForeScout Extended Module for Qualys VM Version 1.2.1 Table of Contents About the Qualys VM Integration... 3 Additional Qualys VM Documentation... 3 About This Module... 3 Components... 4 Considerations...
Comodo cwatch Web Security Software Version 1.6
 rat Comodo cwatch Web Security Software Version 1.6 Quick Start Guide Guide Version 1.6.010918 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo cwatch Web Security - Quick Start Guide
rat Comodo cwatch Web Security Software Version 1.6 Quick Start Guide Guide Version 1.6.010918 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo cwatch Web Security - Quick Start Guide
USER MANUAL. SuiteCRM / SugarCRM Customer Portal for Joomla TABLE OF CONTENTS. Version: 1.1
 USER MANUAL TABLE OF CONTENTS Introduction...1 Benefits of Customer Portal...1 Installation...2 Joomla Manual Plug-in installation...2 Plug-in Configuration...4 Joomla Configuration Settings...4 CRM Fields
USER MANUAL TABLE OF CONTENTS Introduction...1 Benefits of Customer Portal...1 Installation...2 Joomla Manual Plug-in installation...2 Plug-in Configuration...4 Joomla Configuration Settings...4 CRM Fields
SYMANTEC: SECURITY ADVISORY SERVICES. Symantec Security Advisory Services The World Leader in Information Security
 SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
Microsoft DirectAccess
 Microsoft DirectAccess The New Choice of Enterprises Over Traditional VPN Whitepaper August 2017 Microsoft DirectAccess The New Choice of Enterprises Over Traditional VPN Microsoft DirectAccess is a unique
Microsoft DirectAccess The New Choice of Enterprises Over Traditional VPN Whitepaper August 2017 Microsoft DirectAccess The New Choice of Enterprises Over Traditional VPN Microsoft DirectAccess is a unique
Automating the Top 20 CIS Critical Security Controls
 20 Automating the Top 20 CIS Critical Security Controls SUMMARY It s not easy being today s CISO or CIO. With the advent of cloud computing, Shadow IT, and mobility, the risk surface area for enterprises
20 Automating the Top 20 CIS Critical Security Controls SUMMARY It s not easy being today s CISO or CIO. With the advent of cloud computing, Shadow IT, and mobility, the risk surface area for enterprises
Comodo SiteInspector Software Version 3.3
 Comodo SiteInspector Software Version 3.3 Administrator Guide Guide Version 3.3.032812 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo SiteInspector...
Comodo SiteInspector Software Version 3.3 Administrator Guide Guide Version 3.3.032812 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo SiteInspector...
Ask OMAFRA ONe-key Enrolment Guide. Including steps to create your ONe-key User ID and Password
 Ask OMAFRA ONe-key Enrolment Guide Including steps to create your ONe-key User ID and Password Contents Ask OMAFRA ONe-key Enrolment Guide... 1 Introduction... 3 Purpose of this Guide... 3 What is ONe-key
Ask OMAFRA ONe-key Enrolment Guide Including steps to create your ONe-key User ID and Password Contents Ask OMAFRA ONe-key Enrolment Guide... 1 Introduction... 3 Purpose of this Guide... 3 What is ONe-key
