Digital Certificate Service (DCS) - User Guide
|
|
|
- Alicia Hicks
- 6 years ago
- Views:
Transcription
1 Digital Certificate Service (DCS) - User Guide Information Security Branch
2 Contents Using this Guide... 3 User Requirements... 3 Secure Messaging... 4 Send a Secure Message... 4 Receive a Secure Message (Verify a Digitally Signed )... 6 Receive a Secure message (Decrypt an )... 9 Secure Files in a Folder Encrypt and Digitally Sign File(s) Decrypt and Verify Digitally Secured File(s) Manual check of a digital signature Page 2 of 21
3 Using this Guide This Digital Certificate Service (DCS) guide provides a reference for individuals assigned a DCS ID. DCS account creation and management is performed by individuals assigned the role of DCS Local Registration Authority, commonly referred to as DCS LRAs. DCS LRAs follow established procedures to create, modify, deactivate or reactivate accounts as well as perform other administrative functions. DCS users should contact their LRA when additional assistance is required or check the DCS website. User Requirements An approved DCS Token, such as a SafeNet 5100 or 5110 etoken Entrust Entelligence and SafeNet software installed on their computer An active DCS Account within their Ministry or Organization Page 3 of 21
4 Secure Messaging Send a Secure Message The user completes the following steps to send a secure message: 1. Ensure the Token is inserted into a USB port. 2. From Microsoft Outlook>Home tab, in the New group, click New . An Message (HTML) window displays: 3. Type recipient addresses, Subject and message text. 4. Select Options. 5. In the Permission group, click one or both of: o Encrypt to prevent unauthorized people from reading the o Sign to digitally sign an so that other people can be sure who it came from 6. Click Send. Page 4 of 21
5 o If the Token is not inserted, the Invalid Certificate dialog box displays: Click OK to close the dialog box and return to the message. Insert the Token and click Send again. o If sending a secure message for the first time since inserting the Token, the Token Logon dialog box displays showing the Token Name: Enter the Token Password and click OK to close the dialog box and return to the Home tab. The message will appear in the Sent folder. 7. Continue to send messages as needed without logging on again. Note: After a specified period of inactivity (currently set to 12 hours), the secure session is logged off. Page 5 of 21
6 Receive a Secure Message (Verify a Digitally Signed ) The user completes the following steps to receive a secure message (Token is not required): 1. From the Microsoft Outlook tabs, select Home (selected by default). 2. In the left navigation, select Inbox (selected by default). 3. In the message list, double-click the to be verified. The Message (HTML) window displays with an icon indicating that the is digitally signed: 4. Click the Digital signature is trusted icon. Page 6 of 21
7 The Digital Signature: Valid window displays: 5. Click Details to see details of the certificate used to sign the message. Page 7 of 21
8 The Message Security Properties window displays: 6. From the Digital Signature Layer, select Signer to see the signature details. 7. Click Close to close the dialog and return to the . Page 8 of 21
9 Receive a Secure message (Decrypt an ) The user completes the following steps to decrypt an 1. Ensure the Token is inserted into a USB port. 2. From the Microsoft Outlook tabs, select Home (selected by default). 3. In the left navigation, select Inbox (selected by default). 4. In the message list, double-click the to be decrypted. o If the Token is not inserted, a Microsoft information message appears: Click OK to close the dialog box and return to the message list. Insert Token in a USB port. o If decrypting a secure message for the first time since inserting the Token, the Token Logon dialog box displays showing the Token Name: Enter the Token Password and click OK to close the dialog box and return to the Home tab. In the message list, double-click the to be decrypted. Page 9 of 21
10 The Message (HTML) window displays with an icon indicating that the is encrypted: 5. Click the icon. Page 10 of 21
11 The Message Security Properties window displays: 6. Select Encryption Layer to see the Encryption Layer details. 7. Click Close to close the window and return to the . Page 11 of 21
12 Secure Files in a Folder Encrypt and Digitally Sign File(s) The user completes the following steps to encrypt and digitally sign file(s) in a folder: 1. Ensure the Token is inserted into a USB port. 2. Navigate to the folder containing the file(s) to be secured. 3. Select the file(s) and right-click (multiple files may be selected at the same time). A menu displays: 4. Select one of the following options: o Encrypt File to prevent unauthorized people from reading the file o Digitally Sign File to digitally sign a file so that other people can be sure who it came from Page 12 of 21
13 o Encrypt and Digitally Sign File to prevent unauthorized people from reading the file and digitally sign the file so that other people can be sure who it came from An Encrypt Files Wizard specific to the selected option opens, and the Welcome page lists the selected file(s): 5. Click Next. Page 13 of 21
14 The Encryption and Digital and Signature Options page displays showing the Encryption Certificate and/or Signing Certificates: 6. Click Next. o If the Token is not inserted, select Cancel, insert the Token and return to Step 3 to start the wizard again. Page 14 of 21
15 o If securing a file for the first time since inserting the Token, the Token Logon dialog box displays showing the Token Name: Enter the Token Password and click OK. Page 15 of 21
16 The Completing the Wizard page displays with a success message and lists the secured file(s). Note: The files have a.p7m extension indicating that they are secure. 7. If shown, select the option: Delete the original files on finish, as needed. 8. Click Finish to exit the wizard. o A lock icon appears on the secure file(s). o The original file(s) are deleted only where specified in the previous step. 9. Continue to encrypt and digitally sign files as needed without logging on again. Note: After a specified period of inactivity (currently set to 12 hours), the secure session is logged off. Page 16 of 21
17 Decrypt and Verify Digitally Secured File(s) The user completes the following steps to decrypt, verify and open file(s) secured (encrypted, digitally signed or both) using the DCS service: 1. Insert Token. 2. Navigate to the folder containing the file(s). 3. Select the file(s) and right-click (one or more files may be selected at the same time). A menu displays: 4. Select one of the following options: o Decrypt, Verify and Open o Decrypt and Verify Page 17 of 21
18 o If the Token is not inserted, the Entrust Entelligence Security Provider dialog box appears, requesting confirmation to replace the file: Select OK to close the dialog. Insert the Token and try again. o If the Token Logon dialog box displays showing the Token Name: Enter the Token Password and click OK. Note: A file that is only digitally signed will not require password authentication. Page 18 of 21
19 o If the Entrust Entelligence Security Provider dialog box displays requesting confirmation to replace the file: Click Yes. A decrypted version of the file is created. This ends the Decrypt and Verify process. Note: The remaining steps apply if the option to Decrypt, Verify and Open digitally secured file(s) (in Step 4) was chosen. 5. The Entrust Entelligence Security Provider dialog box displays requesting confirmation to open the file: 6. Click Yes. The file opens. Page 19 of 21
20 7. When closing the file (i.e. when no longer needing to use the file) the Entrust Entelligence Security Provider dialog box displays requesting confirmation to delete (and securely erase) the decrypted version of the file: Note: only the decrypted version of the file is deleted, not the secured (encrypted/digitally signed) version of the file. 8. Either: o Click Yes to close the dialog box and delete (and securely erase) the decrypted version of the file. Note: to see that the decrypted version of a file is deleted from a folder you may need to refresh right-click the folder and select Refresh. o Click No to close the dialog box and keep both the decrypted version and the secured version of the file. Page 20 of 21
21 Manual check of a digital signature The user completes the following steps to see details of the individual who digitally signed a file: 1. Open the Properties of the digitally-signed file (right-click the file and select Properties). 2. Select the Security Status tab to view Signature Information. 3. Click View Certificate or Details to see additional information contained in the digital certificate that was used in digitally signing the file. Page 21 of 21
Document Signing Certificate Getting Started Guide
 Certificate Services Document Signing Certificate Getting Started Guide Using the SafeNet Authentication Client: 8.3 Document issue: 1.0 Date of issue: March 2017 For software release 12.1 Document Signing
Certificate Services Document Signing Certificate Getting Started Guide Using the SafeNet Authentication Client: 8.3 Document issue: 1.0 Date of issue: March 2017 For software release 12.1 Document Signing
1. from the Start menu (figure 1.) or 2. from the System tray, by right-clicking on the icon (Golden key) (figure 2)
 Activation of MTnet KSN and MTnet KSN+ certificates Before activating MTnet KSN and MTnet KSN+ certificates, the user must have both the Reference number and Authorization code which the user can get from
Activation of MTnet KSN and MTnet KSN+ certificates Before activating MTnet KSN and MTnet KSN+ certificates, the user must have both the Reference number and Authorization code which the user can get from
MSEDCL e-tendering Help-Contractor. MSEDCL e-tendering Contractor s Guide
 MSEDCL e-tendering Contractor s Guide 1 Table Of Contents Getting Started... 3 Getting Started... 3 Understanding MSEDCL e-tendering System... 3 Logging in... 4 Messages... 5 Sending Reply... 5 Tenders...
MSEDCL e-tendering Contractor s Guide 1 Table Of Contents Getting Started... 3 Getting Started... 3 Understanding MSEDCL e-tendering System... 3 Logging in... 4 Messages... 5 Sending Reply... 5 Tenders...
Cisco CTL Client Setup
 This chapter provides information about Cisco CTL client setup. About, page 2 Addition of Second SAST Role in the CTL File for Recovery, page 2 Cluster Encryption Configuration Through CLI, page 3 Remove
This chapter provides information about Cisco CTL client setup. About, page 2 Addition of Second SAST Role in the CTL File for Recovery, page 2 Cluster Encryption Configuration Through CLI, page 3 Remove
Netrust Pte Ltd. Netrust Digital Signer User Guide CORENET Version 3.1
 Netrust Digital Signer User Guide CORENET Version 3. Netrust Digital Signer User Guide Version: 3. Prepared By: Alexander Kong Date Created: 5 th April 03 Revision History Date Version Description Author
Netrust Digital Signer User Guide CORENET Version 3. Netrust Digital Signer User Guide Version: 3. Prepared By: Alexander Kong Date Created: 5 th April 03 Revision History Date Version Description Author
Client Configuration Guide
 Email Client Configuration Guide Contents Prerequisites... 1 Microsoft Outlook 2007... 2 Microsoft Outlook 2002/XP and 2003... 7 Microsoft Windows Mail (available with Vista only)... 11 Microsoft Outlook
Email Client Configuration Guide Contents Prerequisites... 1 Microsoft Outlook 2007... 2 Microsoft Outlook 2002/XP and 2003... 7 Microsoft Windows Mail (available with Vista only)... 11 Microsoft Outlook
SECARDEO. certbox. Help-Manual. Secardeo GmbH Release:
 certbox Help-Manual Secardeo GmbH Release: 02.12.2014 certbox Help Manual 02.12.2014 Table of Contents 1 Search and retrieve Public Key Certificates... 1 1.1 Search by an e-mail address... 1 1.2 Download
certbox Help-Manual Secardeo GmbH Release: 02.12.2014 certbox Help Manual 02.12.2014 Table of Contents 1 Search and retrieve Public Key Certificates... 1 1.1 Search by an e-mail address... 1 1.2 Download
OUTLOOK WEB APP (OWA): MAIL
 Office 365 Navigation Pane: Navigating in Office 365 Click the App Launcher and then choose the application (i.e. Outlook, Calendar, People, etc.). To modify your personal account settings, click the Logon
Office 365 Navigation Pane: Navigating in Office 365 Click the App Launcher and then choose the application (i.e. Outlook, Calendar, People, etc.). To modify your personal account settings, click the Logon
Cisco CTL Client setup
 Cisco CTL Client setup This chapter provides information about Cisco CTL client setup. About Cisco CTL Client setup, page 2 Remove etoken Run Time Environment 3.00 for CTL Client 5.0 plug-in, page 2 Cisco
Cisco CTL Client setup This chapter provides information about Cisco CTL client setup. About Cisco CTL Client setup, page 2 Remove etoken Run Time Environment 3.00 for CTL Client 5.0 plug-in, page 2 Cisco
Guide Installation and User Guide - Mac
 Guide Installation and User Guide - Mac With Fujitsu mpollux DigiSign Client, you can use your smart card for secure access to electronic services or organization networks, as well as to digitally sign
Guide Installation and User Guide - Mac With Fujitsu mpollux DigiSign Client, you can use your smart card for secure access to electronic services or organization networks, as well as to digitally sign
Schneider Electric License Manager
 Schneider Electric License Manager EIO0000001070 11/2012 Schneider Electric License Manager User Manual 12/2012 EIO0000001070.01 www.schneider-electric.com The information provided in this documentation
Schneider Electric License Manager EIO0000001070 11/2012 Schneider Electric License Manager User Manual 12/2012 EIO0000001070.01 www.schneider-electric.com The information provided in this documentation
USER MANUAL FOR SECURE E MAIL MICROSOFT OUTLOOK (2003)
 YATANARPON TELEPORT COMPANY LTD., YATANARPON CERTIFICATION AUTHORITY USER MANUAL FOR SECURE E MAIL MICROSOFT OUTLOOK (2003) Yatanarpon Teleport Company Ltd., Hlaing Universities Campus, Hlaing Township,
YATANARPON TELEPORT COMPANY LTD., YATANARPON CERTIFICATION AUTHORITY USER MANUAL FOR SECURE E MAIL MICROSOFT OUTLOOK (2003) Yatanarpon Teleport Company Ltd., Hlaing Universities Campus, Hlaing Township,
KYOCERA Net Viewer User Guide Supplement
 KYOCERA Net Viewer User Guide Supplement Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be
KYOCERA Net Viewer User Guide Supplement Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be
Dohatec CA. Export/Import Procedure etoken Pro 72K FOR USERS OF ETOKENS [VERSION 1.0]
![Dohatec CA. Export/Import Procedure etoken Pro 72K FOR USERS OF ETOKENS [VERSION 1.0] Dohatec CA. Export/Import Procedure etoken Pro 72K FOR USERS OF ETOKENS [VERSION 1.0]](/thumbs/83/87091309.jpg) Dohatec CA Export/Import Procedure etoken Pro 72K FOR USERS OF ETOKENS [VERSION 1.0] 1 1 Digital Certificate Certificates issued by Dohatec CA are in X.509 v3 format. In Microsoft windows machines, these
Dohatec CA Export/Import Procedure etoken Pro 72K FOR USERS OF ETOKENS [VERSION 1.0] 1 1 Digital Certificate Certificates issued by Dohatec CA are in X.509 v3 format. In Microsoft windows machines, these
Exostar LDAP Proxy/Secure Setup Guide September 2017
 Exostar LDAP Proxy/Secure Email Setup Guide September 2017 Copyright 2017 Exostar, LLC All rights reserved. 1 Table of Contents Email Encryption Set-up Outlook 2003... 4 Digitally Signing an Email... 4
Exostar LDAP Proxy/Secure Email Setup Guide September 2017 Copyright 2017 Exostar, LLC All rights reserved. 1 Table of Contents Email Encryption Set-up Outlook 2003... 4 Digitally Signing an Email... 4
ModeChanger
 35020808-02 2015.11 ModeChanger ModeChanger is a software utility that can switch the drive between normal mode and encrypted mode. Operating in encrypted mode will help protect your data. While the drive
35020808-02 2015.11 ModeChanger ModeChanger is a software utility that can switch the drive between normal mode and encrypted mode. Operating in encrypted mode will help protect your data. While the drive
OPC-UA Tutorial. A Guide to Configuring the TOP Server for OPC-UA
 OPC-UA Tutorial A Guide to Configuring the TOP Server for OPC-UA Page 2 of 40 Table of Contents INTRODUCTION 4 Introduction to OPC UA 4 Introduction to TOP Server 5 Intended Audience 5 Prerequisites 6
OPC-UA Tutorial A Guide to Configuring the TOP Server for OPC-UA Page 2 of 40 Table of Contents INTRODUCTION 4 Introduction to OPC UA 4 Introduction to TOP Server 5 Intended Audience 5 Prerequisites 6
Windows Smart Card Logon Use Case
 Windows Smart Card Logon Use Case Issue Smart Card Logon versasec.com 1(13) Table of Contents Windows Smart Card Logon Use Case... 3 Step 1 Configuring a Windows Smart Card Logon Template... 3 Step 2 Configuring
Windows Smart Card Logon Use Case Issue Smart Card Logon versasec.com 1(13) Table of Contents Windows Smart Card Logon Use Case... 3 Step 1 Configuring a Windows Smart Card Logon Template... 3 Step 2 Configuring
SafeNet Authentication Manager
 SafeNet Authentication Manager Version 8.0 Rev A User s Guide Copyright 2010 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document complete and accurate.
SafeNet Authentication Manager Version 8.0 Rev A User s Guide Copyright 2010 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document complete and accurate.
Managing GSS Devices from the GUI
 CHAPTER 1 This chapter describes how to configure and manage your Global Site Selector Manager (GSSM) and Global Site Selector (GSS) devices from the primary GSSM graphical user interface. It includes
CHAPTER 1 This chapter describes how to configure and manage your Global Site Selector Manager (GSSM) and Global Site Selector (GSS) devices from the primary GSSM graphical user interface. It includes
CLIQ Web Manager. User Manual. The global leader in door opening solutions V 6.1
 CLIQ Web Manager User Manual V 6.1 The global leader in door opening solutions Program version: 6.1 Document number: ST-003478 Date published: 2016-03-31 Language: en-gb Table of contents 1 Overview...9
CLIQ Web Manager User Manual V 6.1 The global leader in door opening solutions Program version: 6.1 Document number: ST-003478 Date published: 2016-03-31 Language: en-gb Table of contents 1 Overview...9
Configure Outlook to use port 587 with authentication
 Configure Outlook 2003 email to use port 587 with authentication In order to send and receive E-mail through your website hosted with FastWebEngine, you can configure Outlook as your preferred E-mail client.
Configure Outlook 2003 email to use port 587 with authentication In order to send and receive E-mail through your website hosted with FastWebEngine, you can configure Outlook as your preferred E-mail client.
3.0. Manual and. Application note. USB Adapter
 3.0 USB Adapter Manual and Application note Index INTRODUCTION 1 CHAPTER 1 Package 2 Features 2 Bluetooth profile support 2 Drivers support 3 CHAPTER 2 Setup for Windows 98SE/ME/2000/XP 4 CHAPTER 3 Application
3.0 USB Adapter Manual and Application note Index INTRODUCTION 1 CHAPTER 1 Package 2 Features 2 Bluetooth profile support 2 Drivers support 3 CHAPTER 2 Setup for Windows 98SE/ME/2000/XP 4 CHAPTER 3 Application
Exchange Address Book Order
 Exchange Address Book Order From your Outlook Ribbon, locate the Address Book Click on Tools, Options 3 options are available, as shown below, select Custom to arrange the order of your address books.
Exchange Address Book Order From your Outlook Ribbon, locate the Address Book Click on Tools, Options 3 options are available, as shown below, select Custom to arrange the order of your address books.
Instructions for connecting to the FDIBA Wireless Network. (Windows XP)
 Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Outlook Desktop Application for Windows
 Access Your Email There are two common ways to access your mail: via the Outlook Desktop Application and the Outlook Web Application. This document focuses on how to use the Outlook Desktop Application
Access Your Email There are two common ways to access your mail: via the Outlook Desktop Application and the Outlook Web Application. This document focuses on how to use the Outlook Desktop Application
MyFloridaNet-2 (MFN-2) Remote Access VPN Reference Guide
 MyFloridaNet-2 (MFN-2) Remote Access VPN Reference Guide Document Control Number: 7055011 Contract Number: DMS-13/14-024 Prepared for: Florida Department of Management Services Division of Departmental
MyFloridaNet-2 (MFN-2) Remote Access VPN Reference Guide Document Control Number: 7055011 Contract Number: DMS-13/14-024 Prepared for: Florida Department of Management Services Division of Departmental
Aventail Connect Client with Smart Tunneling
 Aventail Connect Client with Smart Tunneling User s Guide Windows v8.9.0 1996-2007 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
Aventail Connect Client with Smart Tunneling User s Guide Windows v8.9.0 1996-2007 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
Guide Installation and User Guide - Windows
 Guide Installation and User Guide - Windows With Fujitsu mpollux DigiSign Client, you can use your smart card for secure access to electronic services or organization networks, as well as to digitally
Guide Installation and User Guide - Windows With Fujitsu mpollux DigiSign Client, you can use your smart card for secure access to electronic services or organization networks, as well as to digitally
Schneider Electric Floating License Manager
 Schneider Electric Floating License Manager EIO0000001078 11/2012 Schneider Electric Floating License Manager User Manual 12/2012 EIO0000001078.01 www.schneider-electric.com The information provided in
Schneider Electric Floating License Manager EIO0000001078 11/2012 Schneider Electric Floating License Manager User Manual 12/2012 EIO0000001078.01 www.schneider-electric.com The information provided in
SureClose Product Line
 SureClose Product Line Release Notes 3.7 June 21, 2013 SureClose 3.7 Release Notes June 2013 1 Table of Contents Overview... 4 Post-Installation Considerations... 4 Features and Functionality... 6 New
SureClose Product Line Release Notes 3.7 June 21, 2013 SureClose 3.7 Release Notes June 2013 1 Table of Contents Overview... 4 Post-Installation Considerations... 4 Features and Functionality... 6 New
SafeGuard Enterprise. user help. Product Version: 8.1
 SafeGuard Enterprise user help Product Version: 8.1 Contents About SafeGuard Enterprise...1 Modules... 2 Full disk encryption with BitLocker...2 Full disk encryption with SafeGuard Power-on Authentication...
SafeGuard Enterprise user help Product Version: 8.1 Contents About SafeGuard Enterprise...1 Modules... 2 Full disk encryption with BitLocker...2 Full disk encryption with SafeGuard Power-on Authentication...
Approving the Outside Interests Disclosure Form Without Conflicts. Supervisor Level. IRIS Mobile through the Web
 Approving the Outside Interests Disclosure Form Without Conflicts Supervisor Level IRIS Mobile through the Web The Outside Interests Disclosure Form is for the University of Tennessee faculty and staff
Approving the Outside Interests Disclosure Form Without Conflicts Supervisor Level IRIS Mobile through the Web The Outside Interests Disclosure Form is for the University of Tennessee faculty and staff
Step by Step - Digital IDs in Adobe Acrobat & Reader versions XI and DC
 Step by Step - Digital IDs in Adobe Acrobat & Reader versions XI and DC Create a self-signed digital ID 1. In the upper left click Edit, choose Preferences, then Signatures on the left, under Categories.
Step by Step - Digital IDs in Adobe Acrobat & Reader versions XI and DC Create a self-signed digital ID 1. In the upper left click Edit, choose Preferences, then Signatures on the left, under Categories.
PAN-OS Integration with SafeNet Luna SA HSM Tech Note PAN-OS 6.0
 PAN-OS Integration with SafeNet Luna SA HSM Tech Note PAN-OS 6.0 Revision 1 2014, Palo Alto Networks, Inc. www.paloaltonetworks.com Secure Keys with a SafeNet Luna Hardware Security Module A hardware security
PAN-OS Integration with SafeNet Luna SA HSM Tech Note PAN-OS 6.0 Revision 1 2014, Palo Alto Networks, Inc. www.paloaltonetworks.com Secure Keys with a SafeNet Luna Hardware Security Module A hardware security
Microsoft Office Outlook 2007: Intermediate Course 01 Customizing Outlook
 Microsoft Office Outlook 2007: Intermediate Course 01 Customizing Outlook Slide 1 Customizing Outlook Course objectives Create a custom toolbar and customize the menu bar; customize the Quick Access toolbar,
Microsoft Office Outlook 2007: Intermediate Course 01 Customizing Outlook Slide 1 Customizing Outlook Course objectives Create a custom toolbar and customize the menu bar; customize the Quick Access toolbar,
HOL122 Lab 1: Configuring Microsoft Windows Server 2003 RPC Proxy
 HOL122 Lab 1: Configuring Microsoft Windows Server 2003 RPC Proxy Objectives After completing this lab, you will be able to: Install remote procedure call (RPC) over Hypertext Transfer Protocol (HTTP)
HOL122 Lab 1: Configuring Microsoft Windows Server 2003 RPC Proxy Objectives After completing this lab, you will be able to: Install remote procedure call (RPC) over Hypertext Transfer Protocol (HTTP)
TIBCO Managed File Transfer Internet Server Transfer and File Share Clients User's Guide
 TIBCO Managed File Transfer Internet Server Transfer and File Share Clients User's Guide Software Release 8.1 March 2018 Two-Second Advantage 2 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES
TIBCO Managed File Transfer Internet Server Transfer and File Share Clients User's Guide Software Release 8.1 March 2018 Two-Second Advantage 2 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES
Life After Webmail Reference Guide
 Life After Webmail Reference Guide (An Introduction to Outlook Web Access 2007 Client User Interface) https://owa.wiu.k12.pa.us Westmoreland Intermediate Unit Information Technology Services 102 Equity
Life After Webmail Reference Guide (An Introduction to Outlook Web Access 2007 Client User Interface) https://owa.wiu.k12.pa.us Westmoreland Intermediate Unit Information Technology Services 102 Equity
Browser Set-Up Instructions
 Browser Set-Up Instructions Before visiting the Assessment LinkBC site for the first time, you must configure your Internet Explorer browser: o to recognize the Assessment LinkBC site as a trusted site,
Browser Set-Up Instructions Before visiting the Assessment LinkBC site for the first time, you must configure your Internet Explorer browser: o to recognize the Assessment LinkBC site as a trusted site,
USER GUIDE WWPass Security for (Thunderbird)
 USER GUIDE WWPass Security for Email (Thunderbird) TABLE OF CONTENTS Chapter 1 Welcome... 3 Introducing WWPass Security for Email (Thunderbird)... 4 Connecting Your PassKey to Your Computer... 4 Need Assistance?...
USER GUIDE WWPass Security for Email (Thunderbird) TABLE OF CONTENTS Chapter 1 Welcome... 3 Introducing WWPass Security for Email (Thunderbird)... 4 Connecting Your PassKey to Your Computer... 4 Need Assistance?...
Changing Settings for ViewMail for Outlook (Version 8.0 Only)
 Changing Settings for ViewMail for Outlook Note This content applies to ViewMail for Outlook version 8.0 only. For later ViewMail versions, see the Quick Start Guide for Cisco ViewMail for Microsoft Outlook
Changing Settings for ViewMail for Outlook Note This content applies to ViewMail for Outlook version 8.0 only. For later ViewMail versions, see the Quick Start Guide for Cisco ViewMail for Microsoft Outlook
Passwordstate Mobile Client Manual Click Studios (SA) Pty Ltd
 2 Table of Contents Foreword 0 Part I Introduction 3 Part II User Preferences 3 Part III System Settings 4 Part IV Mobile Client Permissions 6 Part V Mobile Client Usage 8 Introduction 1 3 Introduction
2 Table of Contents Foreword 0 Part I Introduction 3 Part II User Preferences 3 Part III System Settings 4 Part IV Mobile Client Permissions 6 Part V Mobile Client Usage 8 Introduction 1 3 Introduction
ISA 2006 and OWA 2003 Implementation Guide
 ISA 2006 and OWA 2003 Implementation Guide Copyright Copyright 2006, CRYPTOCard Corp. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
ISA 2006 and OWA 2003 Implementation Guide Copyright Copyright 2006, CRYPTOCard Corp. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
Adobe Acrobat DC Forms
 Adobe Acrobat DC Forms Course objectives: Create interactive forms Manage form fields and properties Use forms in Adobe Reader Use PDF Actions Digital Signatures This course does not cover LiveCycle. Staff
Adobe Acrobat DC Forms Course objectives: Create interactive forms Manage form fields and properties Use forms in Adobe Reader Use PDF Actions Digital Signatures This course does not cover LiveCycle. Staff
PKI Contacts PKI for Fraunhofer Contacts
 Fraunhofer Competence Center PKI PKI Contacts PKI for Fraunhofer Contacts User manual for communication partners of the Fraunhofer-Gesellschaft Author[s]: Uwe Bendisch, Maximilian Gottwald As at: 03.02.2017
Fraunhofer Competence Center PKI PKI Contacts PKI for Fraunhofer Contacts User manual for communication partners of the Fraunhofer-Gesellschaft Author[s]: Uwe Bendisch, Maximilian Gottwald As at: 03.02.2017
Online Documentation. Version 5.2
 Online Documentation Version 5.2 Table of Contents Table of Contents... 1 Introduction... 2 INDORSE CLOUD Features Overview... 3 Getting Started with INDORSE CLOUD... 3 Install and Register in Mobile App
Online Documentation Version 5.2 Table of Contents Table of Contents... 1 Introduction... 2 INDORSE CLOUD Features Overview... 3 Getting Started with INDORSE CLOUD... 3 Install and Register in Mobile App
Websense Secure Messaging User Help
 Websense Secure Messaging User Help Welcome to Websense Secure Messaging, a tool that provides a secure portal for the transmission and viewing of sensitive, personal data in email. Use the portal to view
Websense Secure Messaging User Help Welcome to Websense Secure Messaging, a tool that provides a secure portal for the transmission and viewing of sensitive, personal data in email. Use the portal to view
Jumble for Microsoft Outlook
 Jumble for Microsoft Outlook Jumble provides truly usable and secure email encryption by integrating with existing email clients. Users can easily and securely communicate from their email client simply
Jumble for Microsoft Outlook Jumble provides truly usable and secure email encryption by integrating with existing email clients. Users can easily and securely communicate from their email client simply
Identity Finder: Managing Your Results
 Updated 1/30/2012 Identity Finder: Managing Your Results The most important part of running Identity Finder is determining the most effective and secure way of managing the search results. Be sure to carefully
Updated 1/30/2012 Identity Finder: Managing Your Results The most important part of running Identity Finder is determining the most effective and secure way of managing the search results. Be sure to carefully
Set Up with Microsoft Outlook 2013 using POP3
 Page 1 of 14 Help Center Set Up E-mail with Microsoft Outlook 2013 using POP3 Learn how to configure Microsoft Outlook 2013 for use with your 1&1 e-mail account using the POP3 Protocol. Before you begin,
Page 1 of 14 Help Center Set Up E-mail with Microsoft Outlook 2013 using POP3 Learn how to configure Microsoft Outlook 2013 for use with your 1&1 e-mail account using the POP3 Protocol. Before you begin,
Office 365 Employee San Jac Outlook 2010
 Office 365 Employee Email San Jac Outlook 2010 Interface Overview 1. Quick Access Toolbar contains shortcuts for the most commonly used tools. 2. File tab (Backstage View) contains tools to manage account
Office 365 Employee Email San Jac Outlook 2010 Interface Overview 1. Quick Access Toolbar contains shortcuts for the most commonly used tools. 2. File tab (Backstage View) contains tools to manage account
Maximo Self Service Center
 Maximo Self Service Center Once you have received an email regarding your registration approval, go to the following web address: https://maximo.mysodexo.com Log in to the Self Service Center: Your User
Maximo Self Service Center Once you have received an email regarding your registration approval, go to the following web address: https://maximo.mysodexo.com Log in to the Self Service Center: Your User
Bulletproofing the Database
 Bulletproofing the Database Robert Grauer, Keith Mulbery, Maurie Wigman Lockley Copyright 2008 Pearson Prentice Hall. All rights reserved. 1 Objectives Encrypt and password protect a database Digitally
Bulletproofing the Database Robert Grauer, Keith Mulbery, Maurie Wigman Lockley Copyright 2008 Pearson Prentice Hall. All rights reserved. 1 Objectives Encrypt and password protect a database Digitally
Avaya Event Processor Release 2.2 Operations, Administration, and Maintenance Interface
 Avaya Event Processor Release 2.2 Operations, Administration, and Maintenance Interface Document ID: 13-603114 Release 2.2 July 2008 Issue No.1 2008 Avaya Inc. All Rights Reserved. Notice While reasonable
Avaya Event Processor Release 2.2 Operations, Administration, and Maintenance Interface Document ID: 13-603114 Release 2.2 July 2008 Issue No.1 2008 Avaya Inc. All Rights Reserved. Notice While reasonable
WEBppliance for Windows User Administrator's Help
 WEBppliance for Windows User Administrator's Help September 23, 2003 Contents About This Document...3 How to use this Help system...4 Getting started...6 What to do first... 6 Viewing your account settings...
WEBppliance for Windows User Administrator's Help September 23, 2003 Contents About This Document...3 How to use this Help system...4 Getting started...6 What to do first... 6 Viewing your account settings...
Navigation Bar Icons
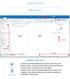 Outlook 2016 Main Screen Navigation Bar Icons Mail Calendar Contains mail-related folders like your Inbox, Sent Items and Search Folders. Use the Favorite Folders at the top of the pane for easy access
Outlook 2016 Main Screen Navigation Bar Icons Mail Calendar Contains mail-related folders like your Inbox, Sent Items and Search Folders. Use the Favorite Folders at the top of the pane for easy access
ProSigner. Quick User Guide. Frontier Technologies Corporation
 ProSigner Quick User Guide Frontier Technologies Corporation Table of Contents Chapter Page No. 1. Create your digital credential ----------------------------- 3 2. Configuring Prosigner -----------------------------
ProSigner Quick User Guide Frontier Technologies Corporation Table of Contents Chapter Page No. 1. Create your digital credential ----------------------------- 3 2. Configuring Prosigner -----------------------------
KG-TOWER Software Download and Installation Instructions
 KG-TOWER Software Download and Installation Instructions Procedures are provided for three options to download and install KG-TOWER software version 5.1. Download to a temporary folder and install immediately.
KG-TOWER Software Download and Installation Instructions Procedures are provided for three options to download and install KG-TOWER software version 5.1. Download to a temporary folder and install immediately.
Web and e-registration Vendor Help Manual
 Web and e-registration Vendor Help Manual Table of Contents Contact Us... 2 Web Registration Process... 2 DSC Serial No. Updation Process... 4 Empanelment (E REGISTRATION) Process... 9 Contact Us: For
Web and e-registration Vendor Help Manual Table of Contents Contact Us... 2 Web Registration Process... 2 DSC Serial No. Updation Process... 4 Empanelment (E REGISTRATION) Process... 9 Contact Us: For
ISL01: Transparently Authenticating Tablets, Smartphones and Laptops with Symantec Managed PKI Service
 ISL01: Transparently Authenticating Tablets, Smartphones and Laptops with Symantec Managed PKI Service Hands-On Lab Description In this session, you will take a free test drive of Symantec Managed PKI
ISL01: Transparently Authenticating Tablets, Smartphones and Laptops with Symantec Managed PKI Service Hands-On Lab Description In this session, you will take a free test drive of Symantec Managed PKI
Along the top of the Inbox is a toolbar with icons for commonly used functions within .
 Outlook Inbox Once you log on to Outlook on the Web, the default page is your Outlook Inbox. For detailed information about logging into your account see: Getting Started - Logging On. The Inbox Viewer
Outlook Inbox Once you log on to Outlook on the Web, the default page is your Outlook Inbox. For detailed information about logging into your account see: Getting Started - Logging On. The Inbox Viewer
Taxpayer Enhancements:
 Taxpayer Enhancements: 1. Authentication for Business Returns and K-1 Distribution: To enhance security for business returns and K-1 distribution, we have removed the need for the recipients to enter the
Taxpayer Enhancements: 1. Authentication for Business Returns and K-1 Distribution: To enhance security for business returns and K-1 distribution, we have removed the need for the recipients to enter the
Secure Recipient Guide
 Secure Email Recipient Guide Contents How to open your first Encrypted Message.... 3 Step-by-Step Guide to Opening Your First Envelope... 3 Step One:... 3 Step Two:... 4 Step Three:... 4 Step Four:...
Secure Email Recipient Guide Contents How to open your first Encrypted Message.... 3 Step-by-Step Guide to Opening Your First Envelope... 3 Step One:... 3 Step Two:... 4 Step Three:... 4 Step Four:...
Setup Guide. Page 0
 Email Setup Guide Page 0 Table of Contents Mailbox Setup Guide... 2 Before you Start... 2 Desktop Mail Clients... 3 Outlook 2016 setup... 3 Outlook 2013 setup... 7 Outlook 2010 setup... 12 Windows 10 Mail
Email Setup Guide Page 0 Table of Contents Mailbox Setup Guide... 2 Before you Start... 2 Desktop Mail Clients... 3 Outlook 2016 setup... 3 Outlook 2013 setup... 7 Outlook 2010 setup... 12 Windows 10 Mail
NoSpamProxy 12.2 Outlook Add-In User Manual. Protection Encryption Large Files
 NoSpamProxy 12.2 Outlook Add-In User Manual Protection Encryption Large Files Imprint All rights reserved. This manual and the depicted applications are copyrighted products of Net at Work GmbH, Paderborn,
NoSpamProxy 12.2 Outlook Add-In User Manual Protection Encryption Large Files Imprint All rights reserved. This manual and the depicted applications are copyrighted products of Net at Work GmbH, Paderborn,
Automated Court Reporter Application. Digital Signatures
 Automated Court Reporter Application Digital Signatures Doc Version 1.5 December 1, 2010 Administrative Office of the U.S. Courts Revision History Date Version Description of Revision 2/10/2009 1.0 Initial
Automated Court Reporter Application Digital Signatures Doc Version 1.5 December 1, 2010 Administrative Office of the U.S. Courts Revision History Date Version Description of Revision 2/10/2009 1.0 Initial
Ekran System v.6.0 Privileged User Accounts and Sessions (PASM)
 Ekran System v.6.0 Privileged User Accounts and Sessions (PASM) Table of Contents About... 3 Using Privileged User Accounts... 4 Password Vault Configuration... 5 Defining Domain Administrator Credentials...
Ekran System v.6.0 Privileged User Accounts and Sessions (PASM) Table of Contents About... 3 Using Privileged User Accounts... 4 Password Vault Configuration... 5 Defining Domain Administrator Credentials...
Comodo LoginPro Software Version 1.0
 Comodo LoginPro Software Version 1.0 User Guide Guide Version 1.0.102512 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo LoginPro... 3 1.1.System
Comodo LoginPro Software Version 1.0 User Guide Guide Version 1.0.102512 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo LoginPro... 3 1.1.System
Wireless for Windows 7
 Wireless for Windows 7 The new CWSL wireless network consists of three different wireless networks CWSL Faculty-Staff - This network is for faculty and staff only. (uses WPA2-Enterprise encryption) CWSL
Wireless for Windows 7 The new CWSL wireless network consists of three different wireless networks CWSL Faculty-Staff - This network is for faculty and staff only. (uses WPA2-Enterprise encryption) CWSL
Jumble Encryption for Microsoft Outlook
 Jumble Email Encryption for Microsoft Outlook Jumble provides truly usable and secure email encryption by integrating with existing email clients. Users can easily and securely communicate from their email
Jumble Email Encryption for Microsoft Outlook Jumble provides truly usable and secure email encryption by integrating with existing email clients. Users can easily and securely communicate from their email
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE. 31 January 2017
 BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
Server Manager User and Permissions Setup
 Login and Security Once you successfully create your company databases, the next step is to define the groups and users that can access the TRAVERSE data and the functionality they will have within the
Login and Security Once you successfully create your company databases, the next step is to define the groups and users that can access the TRAVERSE data and the functionality they will have within the
METADATA FRAMEWORK 6.3. and High Availability
 METADATA FRAMEWORK 6.3 and High Availability Publishing Information Software version 6.3.160 Document version 4 Publication date May 22, 2017 Copyright (c) 2005-2017 Varonis Systems Inc. All rights reserved.
METADATA FRAMEWORK 6.3 and High Availability Publishing Information Software version 6.3.160 Document version 4 Publication date May 22, 2017 Copyright (c) 2005-2017 Varonis Systems Inc. All rights reserved.
Business ebanking Quick Reference Guide. Merchant Capture. bankwithunited.com
 Business ebanking Quick Reference Guide Merchant Capture bankwithunited.com Table of Contents Getting Started System Requirements......................................1-1 Client PC Installation.......................................1-3
Business ebanking Quick Reference Guide Merchant Capture bankwithunited.com Table of Contents Getting Started System Requirements......................................1-1 Client PC Installation.......................................1-3
Equitrac Integrated for Konica Minolta. Setup Guide Equitrac Corporation
 Equitrac Integrated for Konica Minolta 1.2 Setup Guide 2012 Equitrac Corporation Equitrac Integrated for Konica Minolta Setup Guide Document Revision History Revision Date Revision List November 1, 2012
Equitrac Integrated for Konica Minolta 1.2 Setup Guide 2012 Equitrac Corporation Equitrac Integrated for Konica Minolta Setup Guide Document Revision History Revision Date Revision List November 1, 2012
Configuring the VPN Client
 Configuring the VPN Client This chapter explains how to configure the VPN Client. To configure the VPN Client, you enter values for a set of parameters known as a connection entry. The VPN Client uses
Configuring the VPN Client This chapter explains how to configure the VPN Client. To configure the VPN Client, you enter values for a set of parameters known as a connection entry. The VPN Client uses
VRABE Outlook Web Access (OWA)Basics
 VRABE Outlook Web Access (OWA)Basics Logging On 1. Open Internet Explorer. 2. If you are at RHS, you MUST type http://rockmail/exchange. 3. Outside Rockville High (e.g. home, work) type http://mail.vernonct.org/exchange
VRABE Outlook Web Access (OWA)Basics Logging On 1. Open Internet Explorer. 2. If you are at RHS, you MUST type http://rockmail/exchange. 3. Outside Rockville High (e.g. home, work) type http://mail.vernonct.org/exchange
Verizon MDM UEM Unified Endpoint Management
 Verizon MDM UEM Unified Endpoint Management Version: 1.0 Last Updated: 3/29/18 Table of Contents Unified Endpoint Management (UEM) Overview... 4 Account Dashboard... 4 Unified Endpoint Management (UEM)
Verizon MDM UEM Unified Endpoint Management Version: 1.0 Last Updated: 3/29/18 Table of Contents Unified Endpoint Management (UEM) Overview... 4 Account Dashboard... 4 Unified Endpoint Management (UEM)
Web Access to with Office 365
 Web Access to Email with Office 365 Web Access to email allows you to access your LSE mailbox from any computer or mobile device connected to the internet. Be aware, however, that Outlook 365 looks and
Web Access to Email with Office 365 Web Access to email allows you to access your LSE mailbox from any computer or mobile device connected to the internet. Be aware, however, that Outlook 365 looks and
Idaho Form Simplicity Course Outline
 Idaho Form Simplicity Course Outline Optimizing Your Workflow with Form Simplicity Leveraging Form Simplicity s Management Tools for the Broker Optimizing Your Workflow with Form Simplicity Setting Up
Idaho Form Simplicity Course Outline Optimizing Your Workflow with Form Simplicity Leveraging Form Simplicity s Management Tools for the Broker Optimizing Your Workflow with Form Simplicity Setting Up
AgentWorks Administrator and Manager User Guide - Release 12.5
 AgentWorks Administrator and Manager User Guide - Release 12.5 March 21, 2013 2012 MoneyGram InternationalAll rights reserved. Table of Contents Registration Overview... 2 1. Initial Log In AgentWorks
AgentWorks Administrator and Manager User Guide - Release 12.5 March 21, 2013 2012 MoneyGram InternationalAll rights reserved. Table of Contents Registration Overview... 2 1. Initial Log In AgentWorks
Affiliation Set-up User Guide
 DUKE MEDICINE CoreResearch@Duke Affiliation Set-up User Guide 11/29/16 Version 1.1 1 Table of Contents Target Audiences... 3 Affiliation Set-up Overview... 3 Core Set-up... 3 Recognizing Affiliations...
DUKE MEDICINE CoreResearch@Duke Affiliation Set-up User Guide 11/29/16 Version 1.1 1 Table of Contents Target Audiences... 3 Affiliation Set-up Overview... 3 Core Set-up... 3 Recognizing Affiliations...
Version: 4.1 Date: 02/09/2017
 User manual Version: 4.1 Date: 02/09/2017 Microsoft, Windows, Windows Vista, Outlook and Microsoft.NET are either registered trademarks or trademarks of the Microsoft Corporation in the USA and / or other
User manual Version: 4.1 Date: 02/09/2017 Microsoft, Windows, Windows Vista, Outlook and Microsoft.NET are either registered trademarks or trademarks of the Microsoft Corporation in the USA and / or other
INSTRUCTION FOR INSTALLATION OF PBZ USB PKI DEVICE
 This document provides the description of how to install software on computers of users of PBZCOM@NET internet banking, how to change a PIN and how to unlock the PBZ PKI USB device. This Instruction consist
This document provides the description of how to install software on computers of users of PBZCOM@NET internet banking, how to change a PIN and how to unlock the PBZ PKI USB device. This Instruction consist
The SSID to use and the credentials required to be used are listed below for each type of account: SSID TO CREDENTIALS TO BE USED:
 Installation Guides - Information required for connection to the Central Regional TAFE Kalgoorlie Campus Wireless Network Wireless Network Names and Credentials There are two wireless networks operating
Installation Guides - Information required for connection to the Central Regional TAFE Kalgoorlie Campus Wireless Network Wireless Network Names and Credentials There are two wireless networks operating
Guide Installation and User Guide - Linux
 Guide Installation and User Guide - Linux With Fujitsu mpollux DigiSign Client, you can use your smart card for secure access to electronic services or organization networks, as well as to digitally sign
Guide Installation and User Guide - Linux With Fujitsu mpollux DigiSign Client, you can use your smart card for secure access to electronic services or organization networks, as well as to digitally sign
Using a Digital Certificate in Microsoft Outlook 2010 or Later to Digitally Sign and Encrypt s
 Using a Digital Certificate in Microsoft Outlook 2010 or Later to Digitally Sign and Encrypt Emails If you have a digital certificate, you can use it to digitally sign and encrypt emails. IdenTrust digital
Using a Digital Certificate in Microsoft Outlook 2010 or Later to Digitally Sign and Encrypt Emails If you have a digital certificate, you can use it to digitally sign and encrypt emails. IdenTrust digital
Verify that your operating environment meets all hardware and software requirements. For detailed requirements
 Troubleshooting E-mail Router issues This section provides guidelines for troubleshooting issues that you might encounter as you deploy and configure the E-mail Router. E-mail Router installation issues
Troubleshooting E-mail Router issues This section provides guidelines for troubleshooting issues that you might encounter as you deploy and configure the E-mail Router. E-mail Router installation issues
WESTAT REMOTE ACCESS (WRA)
 WESTAT REMOTE ACCESS (WRA) SET UP INSTRUCTIONS The following instructions will allow you to access Westat s Citrix XenApp Web Interface (WXA). This document will teach you how to access Westat s At Home
WESTAT REMOTE ACCESS (WRA) SET UP INSTRUCTIONS The following instructions will allow you to access Westat s Citrix XenApp Web Interface (WXA). This document will teach you how to access Westat s At Home
SoftBank Wireless Assistant Desktop Assistant Client User's Guide
 SoftBank Wireless Assistant Desktop Assistant Client User's Guide Ver.5.5 Rev.1.1 3 Contents Preface Introduction... 4 1 The Personal Edition Desktop Assistant... 4 2 Requirements... 4 Chapter 1 Checking
SoftBank Wireless Assistant Desktop Assistant Client User's Guide Ver.5.5 Rev.1.1 3 Contents Preface Introduction... 4 1 The Personal Edition Desktop Assistant... 4 2 Requirements... 4 Chapter 1 Checking
Securewireless Windows 7 Setup Guide
 Securewireless Windows 7 Setup Guide 1. Click on the wireless icon in the lower right-hand corner of the taskbar and then click on Open Network and Sharing Center. 2. From the Network and Sharing Center
Securewireless Windows 7 Setup Guide 1. Click on the wireless icon in the lower right-hand corner of the taskbar and then click on Open Network and Sharing Center. 2. From the Network and Sharing Center
Adobe Acrobat Pro DC for Windows
 Adobe Acrobat Pro DC for Windows Creating Interactive PDF Forms University Information Technology Services Learning Technologies, Training & Audiovisual Outreach Copyright 2017 KSU Division of University
Adobe Acrobat Pro DC for Windows Creating Interactive PDF Forms University Information Technology Services Learning Technologies, Training & Audiovisual Outreach Copyright 2017 KSU Division of University
1) Installing Bluetooth software for Windows (A) Place installation CD into PC and setup should launch automatically.
 1) Installing Bluetooth software for Windows (A) Place installation CD into PC and setup should launch automatically. If setup does not launch, use Windows Explorer to navigate to the appropriate CD- ROM
1) Installing Bluetooth software for Windows (A) Place installation CD into PC and setup should launch automatically. If setup does not launch, use Windows Explorer to navigate to the appropriate CD- ROM
Outlook 2010 Common Tasks
 Outlook 2010 Common Tasks January 6, 2015 Table of Contents Creating a New Message... 2 Addressing the Message... 2 Using the Address Book... 2 Using the Check Names Icon... 5 Using AutoComplete... 7 Spell
Outlook 2010 Common Tasks January 6, 2015 Table of Contents Creating a New Message... 2 Addressing the Message... 2 Using the Address Book... 2 Using the Check Names Icon... 5 Using AutoComplete... 7 Spell
SafeGuard Enterprise user help. Product version: 8.0
 SafeGuard Enterprise user help Product version: 8.0 Contents 1 About SafeGuard Enterprise...4 2 SafeGuard Enterprise modules...5 3 Security recommendations...7 4 Full disk encryption...9 4.1 Encryption
SafeGuard Enterprise user help Product version: 8.0 Contents 1 About SafeGuard Enterprise...4 2 SafeGuard Enterprise modules...5 3 Security recommendations...7 4 Full disk encryption...9 4.1 Encryption
IT Quick Reference Guides Connecting to SU-Secure using Windows 8
 IT Quick Reference Guides Connecting to SU-Secure using Windows 8 Windows Guides CONNECTING TO SU-SECURE WI-FI This document will give you instructions on how to connect your Windows 8 Computer to our
IT Quick Reference Guides Connecting to SU-Secure using Windows 8 Windows Guides CONNECTING TO SU-SECURE WI-FI This document will give you instructions on how to connect your Windows 8 Computer to our
Appendix A: Use an Outlook Rule to Manage Recruiting Solutions to Approver
 Appendix A: Use an Outlook Rule to Manage Recruiting Solutions E-mail to Approver Discussion Per Microsoft Help, a rule is an action that Microsoft Office Outlook takes automatically on an arriving or
Appendix A: Use an Outlook Rule to Manage Recruiting Solutions E-mail to Approver Discussion Per Microsoft Help, a rule is an action that Microsoft Office Outlook takes automatically on an arriving or
Reference Card: How to connect Windows 7 to UniWireless
 Reference Card: How to connect Windows 7 to UniWireless Important Information Windows 7 is not supported by ITS. These instructions provided are only a guide and do not provide any troubleshooting assistance.
Reference Card: How to connect Windows 7 to UniWireless Important Information Windows 7 is not supported by ITS. These instructions provided are only a guide and do not provide any troubleshooting assistance.
About the To-Do Bar in Outlook 2007
 Tasks in the Microsoft Office system are similar to a to-do list. Tasks make it easy to use Microsoft Office Outlook 007 to organize your time and your work. Tasks are integrated across Outlook 007, Microsoft
Tasks in the Microsoft Office system are similar to a to-do list. Tasks make it easy to use Microsoft Office Outlook 007 to organize your time and your work. Tasks are integrated across Outlook 007, Microsoft
