Virtual Product Fair. Protect your agency data protect your business
|
|
|
- Jeffrey Adam Robinson
- 5 years ago
- Views:
Transcription
1 Virtual Product Fair Protect your agency data protect your business October 2011
2 2 Are you doing all that you can to protect your business?
3 Agenda Background Fraudulent activities Sabre actions Steps you can take 3
4 Background Forms of fraud Over $40M was stolen from small businesses in The FDIC says this has grown to $200M in the last 12 months 4
5 Phishing Phishing s can be difficult to recognize as they often include recognized graphics or logos that appear to be connected to legitimate websites Sample Links look legitimate and are designed to entice recipients to login to fraudulent systems Instead, the links take you to phony scam sites or legitimatelooking but fraudulent pop-up windows 5
6 Phishing examples Source: 6
7 Phishing examples 7 Source:
8 8 Phishing example
9 9 Phishing example
10 Phishing example An example of a phishing received from one of our customers 10
11 Phishing Sabre will never... send you an asking if you ve used our system recently send you an unsolicited notifying you to click on a link to change your password. 11
12 Phishing Steps you can take Never log on (enter user name and/or password) to a site with an ed click-through link Bookmark your trusted login sites and access them only through your bookmark, or by manually typing in the web address Manually type the website address into your Internet browser, if you re concerned about a possibly fraudulent link, Sign in through a secured method and change your password as a precaution 12
13 Phishing Steps you can take If you receive a suspicious that looks like it comes from Sabre, report the incident to the Sabre Help Desk immediately 13
14 Passwords Always keep your Sabre password private Your Sabre password is for only you to know Do not disclose or share your Sabre password with anyone, including others within your agency or branch locations Do not write your password down or store it where someone can access it 14
15 Passwords Sabre will never... ask you for your password have a 3 rd party company ask you for your password 15
16 Passwords Steps you can take Change your Sabre password regularly Make sure your password is difficult for someone else to guess If you receive a call from someone wanting your sign-on and/or password, do not provide your credentials Obtain the caller s contact information and report the incident immediately to the Sabre Help Desk Advise the Help Desk agent you are calling to report a potential invalid request for credentials Avoid using the same password for multiple accounts 16
17 Passwords Steps you can take If you receive a call from someone wanting your sign-on and/or password, do not provide your credentials 17
18 EPR Keywords and Ticket Safe Review your employee EPR keywords Employee Profile Record (EPR) keywords control your employees access to the Sabre system Your agents should have only the keywords necessary for their roles in your agency Every employee is unique and doesn t need the same keywords. Use Ticket Safe to open and/or close the ability to issue airline tickets outside of office hours 18
19 EPR keywords and Ticket Safe Sabre will never... contract with a 3 rd party to adjust your EPR keywords request private information from you regarding your clients or your bookings 19
20 EPR keywords and Ticket Safe Steps you can take Review EPR Quick Reference guide to understand keywords available to help manage your business Review your agents EPR keywords quarterly to ensure each employee has correct access for their role in the agency Increase new staff keywords over time and monitor their initial use of high risk keywords for a short period Inactivate EPRs of former employees Permanently delete 1234 EPR if it still exists. 20
21 EPR keywords and Ticket Safe Steps you can take If you use a robotic application to manage electronic ticketing while your agency is closed, work with your after-hours call center to determine who is authorized to activate and deactivate ticketing 21
22 If your ticketing has been compromised Immediately report incidents to ARC or BSP VOID any potentially fraudulent tickets at once If ticket cannot be voided, contact the air carrier to advise of potential fraud Track and document all activities from the point fraud was identified and reported and throughout the investigation Report incident immediately to the Sabre Help Desk Advise the Help Desk agent you are calling to report potential fraudulent tickets Report the incident to local law enforcement 22
23 Protection Always use designated protected fields for sensitive data like credit card numbers Position workstations so visitors can t see your screen Use a privacy filter on your monitor Use password protected screensavers when you step away from your desk Keep faxes and print copies away from visitor access 23
24 Protection Steps you can take If you receive unsolicited requests for office visits, do not allow these individuals access to your office or your Sabre records. If you receive a suspicious call requesting access to your data or Sabre records, immediately contact the Sabre Help Desk at your usual number Advise Help Desk agent you re reporting a suspicious activity Try to obtain the suspicious individual s contact information to report Report the incident to local law enforcement 24
25 Protection Sabre will never... request private information from you regarding your clients or your bookings. send anyone to your office to repair equipment or ask for you to send us your equipment 25
26 1. Bookmark your trusted login sites and access them only through your bookmark, or type in what you know to be the legitimate website address 2. Sign in through a secured method (using a legitimate link to a Sabre site) and change your password if you have logged on to the Sabre site after clicking on a link you received recently 3. Review your agents Employee Profile Records (EPRs) to ensure that all employees have the correct level of access for their roles in the agency 1. Click on links that require you to enter your login credentials. 2. Disclose login credentials to anyone claiming to be from Sabre. If someone calls your office asking for login credentials, do not provide this information. The Sabre Help Desk or others at Sabre will never ask you to reveal your login and password information. 3. Disclose or share login credentials with anyone else, including others within your agency or branch location 4. Put sensitive data, like credit card numbers, in designated protected fields in the PNR 4. Don t delay reporting fraudulent tickets 26
27 Questions? Refer to our Agency Security community for information on how to protect your agency from this type of fraudulent activity. eservices.sabre.com > Business Tools > Community > Agency Security Today s slides Top right hand corner of the home page between the words FindIt: Site Index and Search Index there is a box. Type VPF in the box and hit enter. Click on the Virtual Product Fair (VPF) presentation link on the next page and then scroll down to Virtual Product Fair 27
Agency Security. Quick Reference. Agency Security Quick Reference Page 1 I N T R O D U C T I O N
 Agency Security Quick Reference I N T R O D U C T I O N The Sabre system has developed a comprehensive security structure to provide only authorized personnel access to the Sabre system. Sabre Travel Network
Agency Security Quick Reference I N T R O D U C T I O N The Sabre system has developed a comprehensive security structure to provide only authorized personnel access to the Sabre system. Sabre Travel Network
Why was an extra step of choosing a Security Image added to the sign-in process?
 General Information Why was an extra step of choosing a Security Image added to the sign-in process? Criminals can create websites that look very similar to legitimate business websites. We want to take
General Information Why was an extra step of choosing a Security Image added to the sign-in process? Criminals can create websites that look very similar to legitimate business websites. We want to take
FACTS WHAT DOES FARMERS STATE BANK DO WITH YOUR PERSONAL INFORMATION? WHY? WHAT? HOW? L QUESTIONS?
 FACTS WHAT DOES FARMERS STATE BANK DO WITH YOUR PERSONAL INFORMATION? WHY? WHAT? HOW? Financial companies choose how they share your personal information. Federal law gives consumers the right to limit
FACTS WHAT DOES FARMERS STATE BANK DO WITH YOUR PERSONAL INFORMATION? WHY? WHAT? HOW? Financial companies choose how they share your personal information. Federal law gives consumers the right to limit
IMPORTANT SECURITY INFORMATION PHISHING
 IMPORTANT SECURITY INFORMATION PHISHING Protect Yourself and Your Accounts Important Security Information At Century Savings Bank, security and privacy of your financial information is a top priority.
IMPORTANT SECURITY INFORMATION PHISHING Protect Yourself and Your Accounts Important Security Information At Century Savings Bank, security and privacy of your financial information is a top priority.
Verizon Enhanced Security Authentication
 Verizon Enhanced Security Authentication Overview Verizon introduced a new security process for Verizon s business portals to help maintain the security of your data. Over the next few months we will initiate
Verizon Enhanced Security Authentication Overview Verizon introduced a new security process for Verizon s business portals to help maintain the security of your data. Over the next few months we will initiate
Online Fraud and Identity Theft Guide. A Guide to Protecting Your Identity and Accounts
 A Guide to Protecting Your Identity and Accounts As part of SunTrust s commitment to protecting your accounts and identity, we ve created the Online Fraud & Identity Theft Guide, which provides information
A Guide to Protecting Your Identity and Accounts As part of SunTrust s commitment to protecting your accounts and identity, we ve created the Online Fraud & Identity Theft Guide, which provides information
Financial scams. What to look for and how to avoid them.
 Financial scams What to look for and how to avoid them. Keep your money secure We take the security and wellbeing of our customers very seriously. So we ve created this guide to highlight the most common
Financial scams What to look for and how to avoid them. Keep your money secure We take the security and wellbeing of our customers very seriously. So we ve created this guide to highlight the most common
CIBC FirstCaribbean Mobile App. FREQUENTLY ASKED QUESTIONS (FAQs)
 CIBC FirstCaribbean Mobile App FREQUENTLY ASKED QUESTIONS (FAQs) 1. What is the CIBC FirstCaribbean Mobile App? A: The CIBC FirstCaribbean Mobile App allows you to complete everyday banking functions on
CIBC FirstCaribbean Mobile App FREQUENTLY ASKED QUESTIONS (FAQs) 1. What is the CIBC FirstCaribbean Mobile App? A: The CIBC FirstCaribbean Mobile App allows you to complete everyday banking functions on
Best Practices Guide to Electronic Banking
 Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
ANNUAL SECURITY AWARENESS TRAINING 2012
 UMW Information Technology Security Program Annual Security Awareness Training for UMW Faculty and Staff ANNUAL SECURITY AWARENESS TRAINING 2012 NETWORK AND COMPUTER USE POLICY Users of information technology
UMW Information Technology Security Program Annual Security Awareness Training for UMW Faculty and Staff ANNUAL SECURITY AWARENESS TRAINING 2012 NETWORK AND COMPUTER USE POLICY Users of information technology
FAQ: Privacy, Security, and Data Protection at Libraries
 FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
Frequently Asked Questions (FAQ)
 Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
Safety and Security. April 2015
 Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
CIBC FirstCaribbean Mobile App. FREQUENTLY ASKED QUESTIONS (FAQs) Page 1 of 9
 CIBC FirstCaribbean Mobile App FREQUENTLY ASKED QUESTIONS (FAQs) 1. What is the CIBC FirstCaribbean Mobile App? A: The CIBC FirstCaribbean Mobile App allows you to complete everyday banking functions on
CIBC FirstCaribbean Mobile App FREQUENTLY ASKED QUESTIONS (FAQs) 1. What is the CIBC FirstCaribbean Mobile App? A: The CIBC FirstCaribbean Mobile App allows you to complete everyday banking functions on
Maria Hishikawa MSIX Technical Lead Sarah Storms MSIX Contractor Security
 Migrant Student Information Exchange (MSIX) Security, Privacy and Account Management Webinar Deloitte Consulting LLP. February 22, 2018 Maria Hishikawa MSIX Technical Lead Sarah Storms MSIX Contractor
Migrant Student Information Exchange (MSIX) Security, Privacy and Account Management Webinar Deloitte Consulting LLP. February 22, 2018 Maria Hishikawa MSIX Technical Lead Sarah Storms MSIX Contractor
Federal Deposit Insurance Corporation. National Credit Union Administration. Office of the Comptroller of the Currency. Office of Thrift Supervision
 YOU HAVE THE POWER TO STOP IDENTITY THEFT A message from the federal bank, credit union and thrift regulatory agencies Board of Governors of the Federal Reserve System Federal Deposit Insurance Corporation
YOU HAVE THE POWER TO STOP IDENTITY THEFT A message from the federal bank, credit union and thrift regulatory agencies Board of Governors of the Federal Reserve System Federal Deposit Insurance Corporation
CUSTOMER TIPS: HOW TO GUARD AGAINST FRAUD WHEN USING ONLINE BANKING OR ATM s
 CUSTOMER TIPS: HOW TO GUARD AGAINST FRAUD WHEN USING ONLINE BANKING OR ATM s ATM Fraud - Watch out for the following scams. Scam 1 - you find you are having difficulty with your card. Someone will come
CUSTOMER TIPS: HOW TO GUARD AGAINST FRAUD WHEN USING ONLINE BANKING OR ATM s ATM Fraud - Watch out for the following scams. Scam 1 - you find you are having difficulty with your card. Someone will come
FAQ. Usually appear to be sent from official address
 FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
PIN / Password Security
 PIN / Password Security www.gatewaycu.com.au INDEX PIN / Password Security 2 Protection of Information 3 Keep Informed 3 Your Protection 4 Online Banking Security 5 Visa Debit Card Security 6 Electronic
PIN / Password Security www.gatewaycu.com.au INDEX PIN / Password Security 2 Protection of Information 3 Keep Informed 3 Your Protection 4 Online Banking Security 5 Visa Debit Card Security 6 Electronic
When you provide personal information to us it will only be used in the ways described in this privacy policy.
 Website Privacy Policy Overview Welcome to this Global Payroll Management Institute website, owned and produced by the Global Payroll Management Institute, Inc. (GPMI). Our website is available to all
Website Privacy Policy Overview Welcome to this Global Payroll Management Institute website, owned and produced by the Global Payroll Management Institute, Inc. (GPMI). Our website is available to all
COMMON WAYS IDENTITY THEFT CAN HAPPEN:
 COMMON WAYS IDENTITY THEFT CAN HAPPEN: OLD FASHIONED STEALING / DUMPSTER DIVING Thieves typically steal wallets and purses. They also steal mail such as credit card and bank statements, pre-approved credit
COMMON WAYS IDENTITY THEFT CAN HAPPEN: OLD FASHIONED STEALING / DUMPSTER DIVING Thieves typically steal wallets and purses. They also steal mail such as credit card and bank statements, pre-approved credit
Regulation P & GLBA Training
 Regulation P & GLBA Training Overview Regulation P governs the treatment of nonpublic personal information about consumers by the financial institution. (Gramm-Leach-Bliley Act of 1999) The GLBA is composed
Regulation P & GLBA Training Overview Regulation P governs the treatment of nonpublic personal information about consumers by the financial institution. (Gramm-Leach-Bliley Act of 1999) The GLBA is composed
It s still very important that you take some steps to help keep up security when you re online:
 PRIVACY & SECURITY The protection and privacy of your personal information is a priority to us. Privacy & Security The protection and privacy of your personal information is a priority to us. This means
PRIVACY & SECURITY The protection and privacy of your personal information is a priority to us. Privacy & Security The protection and privacy of your personal information is a priority to us. This means
WHAT IS CORPORATE ACCOUNT TAKEOVER? HOW DOES IT HAPPEN?
 WHAT IS CORPORATE ACCOUNT TAKEOVER? Corporate Account Takeover (also referred to as CATO) is a type of fraud where criminals gain access to a business financial accounts to make unauthorized transactions.
WHAT IS CORPORATE ACCOUNT TAKEOVER? Corporate Account Takeover (also referred to as CATO) is a type of fraud where criminals gain access to a business financial accounts to make unauthorized transactions.
security FRAUD PREVENTION Business Checklist Safeguard your money, your credit and your good name.
 security FRAUD PREVENTION Business Checklist Safeguard your money, your credit and your good name. Security for Your Business Mitigating risk is a daily reality for business owners, but you don t have
security FRAUD PREVENTION Business Checklist Safeguard your money, your credit and your good name. Security for Your Business Mitigating risk is a daily reality for business owners, but you don t have
The BUSINESS of Fraud. Don t let it put you out of business. AFFILIATE LOGO
 The BUSINESS of Fraud. Don t let it put you out of business. Veenindra J. Singh, First Vice President, Treasury Management Consultant California Bank & Trust 300 Lakeside Drive, Suite 800 Oakland, Ca 94612
The BUSINESS of Fraud. Don t let it put you out of business. Veenindra J. Singh, First Vice President, Treasury Management Consultant California Bank & Trust 300 Lakeside Drive, Suite 800 Oakland, Ca 94612
Identity Theft Prevention Policy
 Identity Theft Prevention Policy Purpose of the Policy To establish an Identity Theft Prevention Program (Program) designed to detect, prevent and mitigate identity theft in connection with the opening
Identity Theft Prevention Policy Purpose of the Policy To establish an Identity Theft Prevention Program (Program) designed to detect, prevent and mitigate identity theft in connection with the opening
Why you MUST protect your customer data
 Why you MUST protect your customer data If you think you re exempt from compliance with customer data security and privacy laws because you re a small business, think again. Businesses of all sizes are
Why you MUST protect your customer data If you think you re exempt from compliance with customer data security and privacy laws because you re a small business, think again. Businesses of all sizes are
Access Control Policy
 Access Control Policy Version Control Version Date Draft 0.1 25/09/2017 1.0 01/11/2017 Related Polices Information Services Acceptable Use Policy Associate Accounts Policy IT Security for 3 rd Parties,
Access Control Policy Version Control Version Date Draft 0.1 25/09/2017 1.0 01/11/2017 Related Polices Information Services Acceptable Use Policy Associate Accounts Policy IT Security for 3 rd Parties,
CAREERBUILDER.COM - PRIVACY POLICY
 Effective Date: September 15, 2010 CareerBuilder, LLC and its subsidiaries and divisions (collectively, CareerBuilder, We or Our ) has drafted its Privacy Policy to ensure that you can use CareerBuilder
Effective Date: September 15, 2010 CareerBuilder, LLC and its subsidiaries and divisions (collectively, CareerBuilder, We or Our ) has drafted its Privacy Policy to ensure that you can use CareerBuilder
Identity Theft, Fraud & You. PrePare. Protect. Prevent.
 PrePare. Protect. Prevent. Identity Theft, Fraud & You Fraud and identity theft incidents claimed fewer victims in 2010 than in previous years. But don t get too comfortable. Average out-of-pocket consumer
PrePare. Protect. Prevent. Identity Theft, Fraud & You Fraud and identity theft incidents claimed fewer victims in 2010 than in previous years. But don t get too comfortable. Average out-of-pocket consumer
Important Information
 Important Information Important Information Effective from 13 January 2018 1. Your information 1.1 Who we are We are Coutts & Co, of 440 Strand, London WC2R OQS. We are a member of The Royal Bank of Scotland
Important Information Important Information Effective from 13 January 2018 1. Your information 1.1 Who we are We are Coutts & Co, of 440 Strand, London WC2R OQS. We are a member of The Royal Bank of Scotland
How to Build a Culture of Security
 How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
LightGig Communications, LLC Privacy Policy
 LightGig Communications, LLC Privacy Policy Effective Date: December 06, 2018 1. Privacy Policy Overview LightGig Communications, LLC ( we, us, or our ) operates the website https://lightgig.com/ (the
LightGig Communications, LLC Privacy Policy Effective Date: December 06, 2018 1. Privacy Policy Overview LightGig Communications, LLC ( we, us, or our ) operates the website https://lightgig.com/ (the
STUDENT ACCEPTABLE USE OF IT SYSTEMS POLICY
 STUDENT ACCEPTABLE USE OF IT SYSTEMS POLICY Introduction The college offer an extensive range of IT systems across campuses and online for course related activities and drop-in purposes. This policy applies
STUDENT ACCEPTABLE USE OF IT SYSTEMS POLICY Introduction The college offer an extensive range of IT systems across campuses and online for course related activities and drop-in purposes. This policy applies
TIPS TO AVOID PHISHING SCAMS
 TIPS TO AVOID PHISHING SCAMS WHAT IS PHISHING? Phishing is the use of fraudulent email, websites, text messages and phone calls to trick people into disclosing personal financial or identity information,
TIPS TO AVOID PHISHING SCAMS WHAT IS PHISHING? Phishing is the use of fraudulent email, websites, text messages and phone calls to trick people into disclosing personal financial or identity information,
Terms and conditions of use for the Online and Mobile Banking Service
 Terms and conditions of use for the Online and Mobile Banking Service Effective from July 2016 Please read these terms and conditions carefully. They re also available on our website and our Mobile Banking
Terms and conditions of use for the Online and Mobile Banking Service Effective from July 2016 Please read these terms and conditions carefully. They re also available on our website and our Mobile Banking
Privacy Policy. How we handle your information you provide to us. Updated: 14 March 2016
 Privacy Policy How we handle your information you provide to us Updated: 14 March 2016 Overview Enteronline (Pty) Ltd and its affiliated companies and subsidiaries (collectively, Entrytime Enteronline,
Privacy Policy How we handle your information you provide to us Updated: 14 March 2016 Overview Enteronline (Pty) Ltd and its affiliated companies and subsidiaries (collectively, Entrytime Enteronline,
South Central Power Stop Scams
 Don t get tricked. People around the country have been receiving emails and phone calls from scammers. South Central Power wants to help you keep your money and prevent scams. Review the helpful tips below.
Don t get tricked. People around the country have been receiving emails and phone calls from scammers. South Central Power wants to help you keep your money and prevent scams. Review the helpful tips below.
Taking control of your finances... 5 Use these tips to manage your finances
 In focus Index In focus... 2 Safeguard your NRI account Taking control of your finances... 5 Use these tips to manage your finances NRI Expert speak... 6 Mr. S. Shanbhag - Financial Expert, answers queries
In focus Index In focus... 2 Safeguard your NRI account Taking control of your finances... 5 Use these tips to manage your finances NRI Expert speak... 6 Mr. S. Shanbhag - Financial Expert, answers queries
Guide to Getting Started. Personal Online Banking & Bill Pay
 Guide to Getting Started Personal Online Banking & Bill Pay What s Inside Welcome to National Bank of Arizona s Online Banking. Whether you re at home, at work, or on the road, our online services are
Guide to Getting Started Personal Online Banking & Bill Pay What s Inside Welcome to National Bank of Arizona s Online Banking. Whether you re at home, at work, or on the road, our online services are
We reserve the right to modify this Privacy Policy at any time without prior notice.
 This Privacy Policy sets out the privacy policy relating to this site accessible at www.battleevents.com and all other sites of Battle Events which are linked to this site (collectively the Site ), which
This Privacy Policy sets out the privacy policy relating to this site accessible at www.battleevents.com and all other sites of Battle Events which are linked to this site (collectively the Site ), which
HUMAN RESOURCES DEPARTMENT
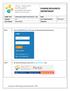 FORM TITLE MANAGING SUBSTITUTION RULES - MSS PAGE 1 Step 1 Go to the KAUST Portal link, fill in your user ID and password and click enter. Step 2 On the top of the portal, click on the Manager Self-Service
FORM TITLE MANAGING SUBSTITUTION RULES - MSS PAGE 1 Step 1 Go to the KAUST Portal link, fill in your user ID and password and click enter. Step 2 On the top of the portal, click on the Manager Self-Service
Personal Online Banking & Bill Pay. Guide to Getting Started
 Personal Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Online Banking. Whether you re at home,
Personal Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Online Banking. Whether you re at home,
SHS Annual Information Privacy and Security Training
 SHS Annual Information Privacy and Security Training Purpose for Training Samaritan Health Services has created the following training to meet the annual regulatory requirements for education related to
SHS Annual Information Privacy and Security Training Purpose for Training Samaritan Health Services has created the following training to meet the annual regulatory requirements for education related to
Fraud Awareness Campaign for the Travel industry
 Fraud Awareness Campaign for the Travel industry The Fraud Awareness Campaign for the Travel industry (FACT) is an outreach and education initiative of the International Air Transport Association (IATA)
Fraud Awareness Campaign for the Travel industry The Fraud Awareness Campaign for the Travel industry (FACT) is an outreach and education initiative of the International Air Transport Association (IATA)
Protecting your Security and Privacy on the Web. Tony Brett Head of IT Support Staff Services IT Services. 11 March 2013
 Protecting your Security and Privacy on the Web Tony Brett Head of IT Support Staff Services IT Services 11 March 2013 Agenda Why bother? Common data leaks Email security Viruses & Trojans Phishing Why
Protecting your Security and Privacy on the Web Tony Brett Head of IT Support Staff Services IT Services 11 March 2013 Agenda Why bother? Common data leaks Email security Viruses & Trojans Phishing Why
VIEWING AND/OR USE AND/OR COMMUNICATION IS CONSTRUED AS ACCEPTANCE OF THE TERMS OF THIS POLICY
 PRIVACY POLICY Last Modified: September 11, 2017 PERSONS OR PARTIES COVERED This Privacy Policy is intended to cover all visitors to this website, all subscribers to lists or newsletters associated with
PRIVACY POLICY Last Modified: September 11, 2017 PERSONS OR PARTIES COVERED This Privacy Policy is intended to cover all visitors to this website, all subscribers to lists or newsletters associated with
Data protection. 3 April 2018
 Data protection 3 April 2018 Policy prepared by: Ltd Approved by the Directors on: 3rd April 2018 Next review date: 31st March 2019 Data Protection Registration Number (ico.): Z2184271 Introduction Ltd
Data protection 3 April 2018 Policy prepared by: Ltd Approved by the Directors on: 3rd April 2018 Next review date: 31st March 2019 Data Protection Registration Number (ico.): Z2184271 Introduction Ltd
UKIP needs to gather and use certain information about individuals.
 UKIP Data Protection Policy Context and overview Key details Policy Update Prepared by: D. Dennemarck / S. Turner Update approved by Management on: November 6, 2015 Policy update became operational on:
UKIP Data Protection Policy Context and overview Key details Policy Update Prepared by: D. Dennemarck / S. Turner Update approved by Management on: November 6, 2015 Policy update became operational on:
CYBER THREATS: REAL ESTATE FRAUD ADVISORY COUNCIL
 CYBER THREATS: REAL ESTATE FRAUD ADVISORY COUNCIL RAHUL GUPTA SENIOR DEPUTY DISTRICT ATTORNEY ORANGE COUNTY DISTRICT ATTORNEYS OFFICE CELL: 714-345-7722 EMAIL: rahul.gupta@da.ocgov.com DAVE WHITE INVESTIGATOR
CYBER THREATS: REAL ESTATE FRAUD ADVISORY COUNCIL RAHUL GUPTA SENIOR DEPUTY DISTRICT ATTORNEY ORANGE COUNTY DISTRICT ATTORNEYS OFFICE CELL: 714-345-7722 EMAIL: rahul.gupta@da.ocgov.com DAVE WHITE INVESTIGATOR
PBX Fraud Information
 PBX Fraud Information Increasingly, hackers are gaining access to corporate phone and/or voice mail systems. These individuals place long distance and international calls through major telecom networks
PBX Fraud Information Increasingly, hackers are gaining access to corporate phone and/or voice mail systems. These individuals place long distance and international calls through major telecom networks
Us bank phishing letter. Us bank phishing letter
 Paieška Paieška Paieška Us bank phishing letter Us bank phishing letter > > Bank fraud is the use of potentially illegal means to obtain money, assets, or other property... "bank guarantees and standby
Paieška Paieška Paieška Us bank phishing letter Us bank phishing letter > > Bank fraud is the use of potentially illegal means to obtain money, assets, or other property... "bank guarantees and standby
Guide to credit card security
 Contents Click on a title below to jump straight to that section. What is credit card fraud? Types of credit card fraud Current scams Keeping your card and card details safe Banking and shopping securely
Contents Click on a title below to jump straight to that section. What is credit card fraud? Types of credit card fraud Current scams Keeping your card and card details safe Banking and shopping securely
Business Online Banking & Bill Pay Guide to Getting Started
 Business Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Business Online Banking. Whether you re
Business Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Business Online Banking. Whether you re
Create strong passwords
 Create strong passwords Passwords are the first line of defense against break-ins to your online accounts and computer, tablet, or phone. Poorly chosen passwords can render your information vulnerable
Create strong passwords Passwords are the first line of defense against break-ins to your online accounts and computer, tablet, or phone. Poorly chosen passwords can render your information vulnerable
University of North Texas System Administration Identity Theft Prevention Program
 University of North Texas System Administration Identity Theft Prevention Program I. Purpose of the Identity Theft Prevention Program The Federal Trade Commission ( FTC ) requires certain entities, including
University of North Texas System Administration Identity Theft Prevention Program I. Purpose of the Identity Theft Prevention Program The Federal Trade Commission ( FTC ) requires certain entities, including
This policy is a public document and has been prepared in light of the National Privacy Principle 5: Openness.
 Privacy Policy: Wireless Life Pty Ltd trading as ISP Connect Effective: 11 November 2015 Wireless Life Pty Ltd t/as ISP Connect ( ISP Connect ) is committed to protecting the privacy of its customer s
Privacy Policy: Wireless Life Pty Ltd trading as ISP Connect Effective: 11 November 2015 Wireless Life Pty Ltd t/as ISP Connect ( ISP Connect ) is committed to protecting the privacy of its customer s
It pays to stop and think
 It pays to stop and think Protect yourself from financial fraud Together we thrive 2 In the first six months of 2018, over 34,000 people were scammed out of 145.4m At HSBC, we work hard to keep our customers
It pays to stop and think Protect yourself from financial fraud Together we thrive 2 In the first six months of 2018, over 34,000 people were scammed out of 145.4m At HSBC, we work hard to keep our customers
Retail/Consumer Client Internet Banking Awareness and Education Program
 Retail/Consumer Client Internet Banking Table of Contents Securing Your Environment... 3 Unsolicited Client Contact... 3 Protecting Your Identity... 3 1) E-mail Risk... 3 2) Internet Risks... 4 3) Telephone
Retail/Consumer Client Internet Banking Table of Contents Securing Your Environment... 3 Unsolicited Client Contact... 3 Protecting Your Identity... 3 1) E-mail Risk... 3 2) Internet Risks... 4 3) Telephone
Target Breach Overview
 Target Breach Overview Q: Media reports are stating that Target experienced a data breach. Can you provide more specifics? A: Yes, Target has confirmed that it experienced unauthorized access to its systems
Target Breach Overview Q: Media reports are stating that Target experienced a data breach. Can you provide more specifics? A: Yes, Target has confirmed that it experienced unauthorized access to its systems
MOBILE.NET PRIVACY POLICY
 MOBILE.NET PRIVACY POLICY As the operator of the Mobile.net website (https://mobile.net.ltd/) (Website), ADX Labs, LLC. (Company, we or us) is committed to protecting and respecting your privacy. The data
MOBILE.NET PRIVACY POLICY As the operator of the Mobile.net website (https://mobile.net.ltd/) (Website), ADX Labs, LLC. (Company, we or us) is committed to protecting and respecting your privacy. The data
NMHC HIPAA Security Training Version
 NMHC HIPAA Security Training 2017 Version HIPAA Data Security HIPAA Data Security is intended to provide the technical controls to ensure electronic Protected Health Information (PHI) is kept secure and
NMHC HIPAA Security Training 2017 Version HIPAA Data Security HIPAA Data Security is intended to provide the technical controls to ensure electronic Protected Health Information (PHI) is kept secure and
Cyber Security Guide for NHSmail
 Cyber Security Guide for NHSmail Version 3.0 February 2017 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
Cyber Security Guide for NHSmail Version 3.0 February 2017 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
FREQUENTLY ASKED QUESTIONS
 FREQUENTLY ASKED QUESTIONS In order to better assist you with the transition to our new home banking service, we wanted to provide you with a list of anticipated questions and things that may need your
FREQUENTLY ASKED QUESTIONS In order to better assist you with the transition to our new home banking service, we wanted to provide you with a list of anticipated questions and things that may need your
FRAUDULENT TRAVEL SCAMS
 FINANCIAL INTELLIGENCE CENTRE (FIC) REPUBLIC OF NAMIBIA P.O.BOX 2882, Windhoek Tel: + 264 61 2835100, Fax +264 61 2835259 Web address: www.fic.na E-mail address: helpdesk@fic.na FRAUDULENT TRAVEL SCAMS
FINANCIAL INTELLIGENCE CENTRE (FIC) REPUBLIC OF NAMIBIA P.O.BOX 2882, Windhoek Tel: + 264 61 2835100, Fax +264 61 2835259 Web address: www.fic.na E-mail address: helpdesk@fic.na FRAUDULENT TRAVEL SCAMS
The Table Privacy Policy Last revised on August 22, 2012
 The Table Privacy Policy Last revised on August 22, 2012 The Table, an online venue through which your organization and its members/employees can connect to better fulfill its mission respects and is committed
The Table Privacy Policy Last revised on August 22, 2012 The Table, an online venue through which your organization and its members/employees can connect to better fulfill its mission respects and is committed
Overview Bank IT examination perspective Background information Elements of a sound plan Customer notifications
 Gramm-Leach Bliley Act Section 501(b) and Customer Notification Roger Pittman Director of Operations Risk Federal Reserve Bank of Atlanta Overview Bank IT examination perspective Background information
Gramm-Leach Bliley Act Section 501(b) and Customer Notification Roger Pittman Director of Operations Risk Federal Reserve Bank of Atlanta Overview Bank IT examination perspective Background information
Page 1 of 6 Bank card and cheque fraud
 Page 1 of 6 happens when criminals steal your cards or chequebook and gain access to funds in your account. More about bank card and cheque fraud Criminals steal your bank cards or cheque book; or they
Page 1 of 6 happens when criminals steal your cards or chequebook and gain access to funds in your account. More about bank card and cheque fraud Criminals steal your bank cards or cheque book; or they
NTS ONLINE BOOKING TOOL SABRE.RES
 NTS ONLINE BOOKING TOOL SABRE.RES National Travel Systems is pleased to present its online booking tool that offers state travelers another means to search fares and schedules that offer the best value
NTS ONLINE BOOKING TOOL SABRE.RES National Travel Systems is pleased to present its online booking tool that offers state travelers another means to search fares and schedules that offer the best value
Shaw Privacy Policy. 1- Our commitment to you
 Privacy Policy last revised on: Sept 16, 2016 Shaw Privacy Policy If you have any questions regarding Shaw s Privacy Policy please contact: privacy@shaw.ca or use the contact information shown on any of
Privacy Policy last revised on: Sept 16, 2016 Shaw Privacy Policy If you have any questions regarding Shaw s Privacy Policy please contact: privacy@shaw.ca or use the contact information shown on any of
We will ask you for certain kinds of personal information ( Personal Information ) to provide the services you request. This information includes:
 PRIVACY POLICY This Website is operated by Mergent, Inc., a member of the London Stock Exchange plc group of companies ( we/our/us/mergent ). Website means the website located at www.mergent.com, any subsequent
PRIVACY POLICY This Website is operated by Mergent, Inc., a member of the London Stock Exchange plc group of companies ( we/our/us/mergent ). Website means the website located at www.mergent.com, any subsequent
CURTIS BANKS LIMITED. Privacy Information Notice. curtisbanks.co.uk
 CURTIS BANKS LIMITED Privacy Information Notice curtisbanks.co.uk Contents Section Page 1 Who we are 3 2 Why we need to collect, use and process personal information 3 3 The information we may collect,
CURTIS BANKS LIMITED Privacy Information Notice curtisbanks.co.uk Contents Section Page 1 Who we are 3 2 Why we need to collect, use and process personal information 3 3 The information we may collect,
Prevention of Identity Theft in Student Financial Transactions AP 5800
 Reference: Fair and Accurate Credit Transactions Act (Pub. L. 108-159) The Board recognizes that some activities of the Shasta-Tehama-Trinity Joint Community College District, "District," are subject to
Reference: Fair and Accurate Credit Transactions Act (Pub. L. 108-159) The Board recognizes that some activities of the Shasta-Tehama-Trinity Joint Community College District, "District," are subject to
Enviro Technology Services Ltd Data Protection Policy
 Enviro Technology Services Ltd Data Protection Policy 1. CONTEXT AND OVERVIEW 1.1 Key details Rev 1.0 Policy prepared by: Duncan Mounsor. Approved by board on: 23/03/2016 Policy became operational on:
Enviro Technology Services Ltd Data Protection Policy 1. CONTEXT AND OVERVIEW 1.1 Key details Rev 1.0 Policy prepared by: Duncan Mounsor. Approved by board on: 23/03/2016 Policy became operational on:
VAX VacationAccess Booking Engine
 Amadeus Tours - VAX VacationAccess VAX VacationAccess Booking Engine Frequently Asked Questions Intentionally left blank January 2013 VAX VacationAccess Page 2 Version Date: January 29, 2013 Table of Contents
Amadeus Tours - VAX VacationAccess VAX VacationAccess Booking Engine Frequently Asked Questions Intentionally left blank January 2013 VAX VacationAccess Page 2 Version Date: January 29, 2013 Table of Contents
Employee Security Awareness Training
 Employee Security Awareness Training September 2016 Purpose Employees have access to sensitive data through the work they perform for York. Examples of sensitive data include social security numbers, medical
Employee Security Awareness Training September 2016 Purpose Employees have access to sensitive data through the work they perform for York. Examples of sensitive data include social security numbers, medical
Client Resources. participant guide
 Guidebook Client Resources Client resources participant guide Welcome The TD Ameritrade Institutional client resources participant guide can help you: Establish an account with an advisor Gain online access
Guidebook Client Resources Client resources participant guide Welcome The TD Ameritrade Institutional client resources participant guide can help you: Establish an account with an advisor Gain online access
( Utility Name ) Identity Theft Prevention Program
 ***DRAFT*** ( Utility Name ) Identity Theft Prevention Program Implemented as of, 2008 *** This document is intended to give guidance to municipal utilities in their understanding of the FTC Red Flag Rule.
***DRAFT*** ( Utility Name ) Identity Theft Prevention Program Implemented as of, 2008 *** This document is intended to give guidance to municipal utilities in their understanding of the FTC Red Flag Rule.
Business Services Centre itrent Employee Self Service
 Business Services Centre itrent Employee Self Service Author Leanne Ireland Date Created 09 th February 2017 Date Modified Version 1. 1. Overview This guide is designed to help you understand the design
Business Services Centre itrent Employee Self Service Author Leanne Ireland Date Created 09 th February 2017 Date Modified Version 1. 1. Overview This guide is designed to help you understand the design
ANZ FASTPAY NEXT GENERATION MERCHANT OPERATING GUIDE ANZ FASTPAY PORTAL
 ANZ FASTPAY NEXT GENERATION MERCHANT OPERATING GUIDE ANZ FASTPAY PORTAL ANZ FastPay Next Generation. A handy way to get paid. ANZ FastPay Next Generation lets you take EFTPOS, credit or debit card payments
ANZ FASTPAY NEXT GENERATION MERCHANT OPERATING GUIDE ANZ FASTPAY PORTAL ANZ FastPay Next Generation. A handy way to get paid. ANZ FastPay Next Generation lets you take EFTPOS, credit or debit card payments
Technology Safety Quick Tips
 Technology Safety Quick Tips Spyware: Computer & Phone Monitoring Software It enables a person to secretly monitor someone else s entire computer activity. It can be installed remotely by sending an email,
Technology Safety Quick Tips Spyware: Computer & Phone Monitoring Software It enables a person to secretly monitor someone else s entire computer activity. It can be installed remotely by sending an email,
Privacy and cookie policy
 Privacy and cookie policy http://www.ferrybookings.com/ (Website) and the Burger Ferry Agencies BV App (APP) is brought to you by Burger Ferry Agencies BV, a company incorporated and registered in Rotterdam,
Privacy and cookie policy http://www.ferrybookings.com/ (Website) and the Burger Ferry Agencies BV App (APP) is brought to you by Burger Ferry Agencies BV, a company incorporated and registered in Rotterdam,
Red Flags/Identity Theft Prevention Policy: Purpose
 Red Flags/Identity Theft Prevention Policy: 200.3 Purpose Employees and students depend on Morehouse College ( Morehouse ) to properly protect their personal non-public information, which is gathered and
Red Flags/Identity Theft Prevention Policy: 200.3 Purpose Employees and students depend on Morehouse College ( Morehouse ) to properly protect their personal non-public information, which is gathered and
Security Awareness & Best Practices Best Practices for Maintaining Data Security in Your Business Environment
 Security Awareness & Best Practices Best Practices for Maintaining Data Security in Your Business Environment Ray Colado, Information Security Analyst Raise awareness around information security to help
Security Awareness & Best Practices Best Practices for Maintaining Data Security in Your Business Environment Ray Colado, Information Security Analyst Raise awareness around information security to help
Cyber Security Guide. For Politicians and Political Parties
 Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
Security Awareness. Chapter 2 Personal Security
 Security Awareness Chapter 2 Personal Security Objectives After completing this chapter, you should be able to do the following: Define what makes a weak password Describe the attacks against passwords
Security Awareness Chapter 2 Personal Security Objectives After completing this chapter, you should be able to do the following: Define what makes a weak password Describe the attacks against passwords
Phishing. What do phishing s do?
 Phishing We have become all too familiar with phishing emails but if that s the case, why do we as a community still fall victim? In this newsletter our goal is to provide you with some basic information
Phishing We have become all too familiar with phishing emails but if that s the case, why do we as a community still fall victim? In this newsletter our goal is to provide you with some basic information
GREATER ESSEX COUNTY DISTRICT SCHOOL BOARD
 GREATER ESSEX COUNTY DISTRICT SCHOOL BOARD REGULATION: NETWORK SECURITY AND ACCESS 1. NETWORK SECURITY AND ACCESS The purpose of this section of the Regulation is to define the standards, procedures and
GREATER ESSEX COUNTY DISTRICT SCHOOL BOARD REGULATION: NETWORK SECURITY AND ACCESS 1. NETWORK SECURITY AND ACCESS The purpose of this section of the Regulation is to define the standards, procedures and
9/11/ FALL CONFERENCE & TRAINING SEMINAR 2014 FALL CONFERENCE & TRAINING SEMINAR
 1 2 1 Agenda: Types of Fraud Things you can do internally Things that companies can do Services Provided by the Bank 3 Because that is where the money is. 4 2 Checks Credit Cards ACH (Debits / Credits)
1 2 1 Agenda: Types of Fraud Things you can do internally Things that companies can do Services Provided by the Bank 3 Because that is where the money is. 4 2 Checks Credit Cards ACH (Debits / Credits)
Multi-Factor Authentication FAQs
 General FAQs What is Multi-factor Authentication (MFA)? Multi-factor authentication (MFA) seeks to decrease the likelihood that others can access your data. Specifically, it enhances the security of your
General FAQs What is Multi-factor Authentication (MFA)? Multi-factor authentication (MFA) seeks to decrease the likelihood that others can access your data. Specifically, it enhances the security of your
Quick recap on ing Security Recap on where to find things on Belvidere website & a look at the Belvidere Facebook page
 Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
ETSY.COM - PRIVACY POLICY
 At Etsy, we value our community. You trust us with your information, and we re serious about that responsibility. We believe in transparency, and we re committed to being upfront about our privacy practices,
At Etsy, we value our community. You trust us with your information, and we re serious about that responsibility. We believe in transparency, and we re committed to being upfront about our privacy practices,
The Insider Threat Center: Thwarting the Evil Insider
 The Insider Threat Center: Thwarting the Evil Insider The CERT Top 10 List for Winning the Battle Against Insider Threats Randy Trzeciak 14 June 2012 2007-2012 Carnegie Mellon University Notices 2011 Carnegie
The Insider Threat Center: Thwarting the Evil Insider The CERT Top 10 List for Winning the Battle Against Insider Threats Randy Trzeciak 14 June 2012 2007-2012 Carnegie Mellon University Notices 2011 Carnegie
EDENRED COMMUTER BENEFITS SOLUTIONS, LLC PRIVACY POLICY. Updated: April 2017
 This Privacy Policy (this Privacy Policy ) applies to Edenred Commuter Benefits Solutions, LLC, (the Company ) online interface (i.e., website or mobile application) and any Edenred Commuter Benefit Solutions,
This Privacy Policy (this Privacy Policy ) applies to Edenred Commuter Benefits Solutions, LLC, (the Company ) online interface (i.e., website or mobile application) and any Edenred Commuter Benefit Solutions,
Website Privacy Policy
 Website Privacy Policy Last updated: May 12, 2016 This privacy policy (the Privacy Policy ) applies to this website and all services provided through this website, including any games or sweepstakes (collectively,
Website Privacy Policy Last updated: May 12, 2016 This privacy policy (the Privacy Policy ) applies to this website and all services provided through this website, including any games or sweepstakes (collectively,
What kind of information do you collect, when and how?
 Associated Telecom Solutions Privacy Policy Action- Tec Services Ltd T/A Associated Telecom Solutions collects business data in order to provide our services to our business customers. During the relationship
Associated Telecom Solutions Privacy Policy Action- Tec Services Ltd T/A Associated Telecom Solutions collects business data in order to provide our services to our business customers. During the relationship
We may change the privacy notice from time to time by amending this page. What type of information will we collect from you?
 This privacy notice sets out how we will process personal data we collect from or about you, or which you provide to us. Please read this notice carefully to understand why data is being collected and
This privacy notice sets out how we will process personal data we collect from or about you, or which you provide to us. Please read this notice carefully to understand why data is being collected and
Your security on click Jobs
 Your security on click Jobs At Click Jobs is a trading name of Raspberry Recruitment Limited, we're committed to helping you find the right job in a safe and secure environment. On these pages, you can
Your security on click Jobs At Click Jobs is a trading name of Raspberry Recruitment Limited, we're committed to helping you find the right job in a safe and secure environment. On these pages, you can
Cyber Hygiene Guide. Politicians and Political Parties
 Cyber Hygiene Guide Politicians and Political Parties Canadian Election Integrity Initiative Design by ccm.design Cover Image by Songquan Deng Helping to Safeguard the Integrity of the Electoral Process
Cyber Hygiene Guide Politicians and Political Parties Canadian Election Integrity Initiative Design by ccm.design Cover Image by Songquan Deng Helping to Safeguard the Integrity of the Electoral Process
