Security in Confirmit Software - Individual User Settings
|
|
|
- Audrey Waters
- 5 years ago
- Views:
Transcription
1 Security in Confirmit Software - Individual User Settings Unclassified. Copyright 2017 Confirmit. All Rights Reserved Page 1 of 5
2 1 Using HTTPS in Confirmit Horizons SSL certificates are installed for all web facing servers in our hosted Confirmit Horizons environments, allowing all users to encrypt their sessions by using HTTPS instead of plain-text HTTP when connecting to the hosted platform. HTTPS protects your session against network eavesdropping (sometimes referred to as "packet sniffing") by ensuring the traffic between the client computer and the server is encrypted. By default, we enforce the HTTPS protocol for all login pages in Confirmit Horizons, i.e. for Professional users, Express users, Translators, Reportal users, and panelists. Exchanges of authentication credentials between the client and server are therefore always secured with SSL encryption. Users are then redirected back to regular, unencrypted HTTP once the server has successfully authenticated the login request. However, it is possible to enforce SSL encryption for the entire session when working in Confirmit Horizons. As a logged on user, you can open your settings by clicking on your user name in the top right area of the screen in Confirmit Horizons to access your user settings (you can also use the Home > User > Settings menu selection to open the same page). This will bring up an overlay screen where the setting 'Use HTTPS connection' can be found: If the checkbox is selected, Confirmit will always keep your session secured with HTTPS, even if you open windows to Confirmit Express, Reportal or Translator. Unclassified. Copyright 2017 Confirmit. All Rights Reserved Page 2 of 5
3 2 Using HTTPS in Confirmit Surveys Of course, Confirmit Horizons also supports HTTPS encryption for respondents. With the default settings, all surveys can be accessed over both HTTP and HTTPS at the same time. The perhaps easiest way to deploy your surveys over SSL, is to select the 'Enforce https access to this survey' checkbox on the Survey Settings page when launching your survey. By selecting this option, the Confirmit Horizons survey engine will ensure that every respondent that accesses the survey will be redirected to access the survey link over HTTPS. Regardless of whether you have an open or limited survey, respondents will be redirected to HTTPS even if you have sent out invitation s using the ^SLINK^ primitive in s (instead of ^SECURESLINK^, which will prefix all survey links with or have an open survey where you have linked to the survey using a regular link. If you are linking to the survey from an external page, you can also simply set up your survey link to use the prefix, this will work out of the box without having to compile the survey specifically to support HTTPS. If you are creating a respondent , you can select the 'Use HTTPS' checkbox, or use the ^SECURESLINK^ primitive in the body to have survey links automatically formatted with the prefix when s are sent out. You can even use both the ^SLINK^ and ^SECURESLINK^ primitives in the same to include both and links to the survey, providing respondents with the option to select for themselves which link they want to use. 3 HTTPS for Reportal Viewers Confirmit Horizons supports HTTPS encryption for Reportal users, and will enforce all Reportal login sessions to take place over HTTPS in order to encrypt the username and password exchange during the authentication process. This is also enforced for Reportal viewers and analysts. As a Confirmit Horizons user, you can also enforce HTTPS for entire Reportal sessions for your end users. This can be done on an individual end user list basis by enabling the 'Always use SSL' checkbox in the general settings for the end user list. All users uploaded to the particular end user list will inherit the setting. Unclassified. Copyright 2017 Confirmit. All Rights Reserved Page 3 of 5
4 4 Password / Account Security Passwords in Confirmit Horizons must comply with the minimum requirements configured on the system. As seen in the below screenshot, these settings include: Locking of accounts after 5 consecutive failed login attempts. Lock screen displayed after 60 minutes inactivity (Password required to unlock). Sessions logged off after 3 hours unless unlocked. Passwords must be changed after 90 days. Passwords cannot be reused (history of last 12 passwords stored on the system). Passwords cannot be changed more than once per day (to prevent circumvention of password history). Minimum requirements for passwords: 8 characters in length, at least one uppercase character and one numeric/symbol character. Passwords are not stored in clear text in the database, instead they are encrypted using one-way hashing technique (using the PBKDF2 key derivation function) with a unique salt value for each account, and the output hash value is stored in the database. The authentication mechanism will perform the same hash function on a password submitted from the login page and will try to match this against the hash value that is stored in the database for the user account, rather than verifying the actual password itself. A side-effect of this is that no one, not even Confirmit's Account Management Team, can retrieve the original clear-text password from the database. Instead of retrieving existing passwords, it is possible for an account administrator to reset a user's password from the admin menu (and provide the user with the new, temporary password, which must be Unclassified. Copyright 2017 Confirmit. All Rights Reserved Page 4 of 5
5 changed at the first subsequent login), or the user may request a password reset link to be sent to the registered address for the account from the login page as long as they know their Confirmit Horizons user name. 5 Other options Other security options are also available, but may depend on license specific add-ons. See the separate Additional Options document for further details. Unclassified. Copyright 2017 Confirmit. All Rights Reserved Page 5 of 5
Security in Confirmit Software - Additional Options
 Security in Confirmit Software - Additional Options Unclassified. Copyright 2017 Confirmit. All Rights Reserved Page 1 of 5 1 Encryption of data exports If you are concerned about the safety of your data
Security in Confirmit Software - Additional Options Unclassified. Copyright 2017 Confirmit. All Rights Reserved Page 1 of 5 1 Encryption of data exports If you are concerned about the safety of your data
How to Configure Guest Access with the Ticketing System
 How to Configure Guest Access with the Ticketing System Set up a login or ticketing system to temporarily grant access to guest users. Ticketing admins assign guest tickets to the users. The user credentials
How to Configure Guest Access with the Ticketing System Set up a login or ticketing system to temporarily grant access to guest users. Ticketing admins assign guest tickets to the users. The user credentials
A. Getting Started About e-access Enrolling in e-access: Authenticating your account Login... 5
 Contents A. Getting Started... 3 1. About e-access... 3 2. Enrolling in e-access:... 3 3. Authenticating your account... 5 4. Login... 5 B. Fix a Problem... 6 1. Provided the wrong email address during
Contents A. Getting Started... 3 1. About e-access... 3 2. Enrolling in e-access:... 3 3. Authenticating your account... 5 4. Login... 5 B. Fix a Problem... 6 1. Provided the wrong email address during
Configuring 802.1X Settings on the WAP351
 Article ID: 5078 Configuring 802.1X Settings on the WAP351 Objective IEEE 802.1X authentication allows the WAP device to gain access to a secured wired network. You can configure the WAP device as an 802.1X
Article ID: 5078 Configuring 802.1X Settings on the WAP351 Objective IEEE 802.1X authentication allows the WAP device to gain access to a secured wired network. You can configure the WAP device as an 802.1X
Contents Using the Primavera Cloud Service Administrator's Guide... 9 Web Browser Setup Tasks... 10
 Cloud Service Administrator's Guide 15 R2 March 2016 Contents Using the Primavera Cloud Service Administrator's Guide... 9 Web Browser Setup Tasks... 10 Configuring Settings for Microsoft Internet Explorer...
Cloud Service Administrator's Guide 15 R2 March 2016 Contents Using the Primavera Cloud Service Administrator's Guide... 9 Web Browser Setup Tasks... 10 Configuring Settings for Microsoft Internet Explorer...
Lab Guide. Barracuda NextGen Firewall F-Series Microsoft Azure - NGF0501
 Barracuda NextGen Firewall F-Series Microsoft Azure - NGF0501 Lab Guide Official training material for Barracuda certified trainings and Authorized Training Centers. Edition 2018 Revision 1.0 campus.barracuda.com
Barracuda NextGen Firewall F-Series Microsoft Azure - NGF0501 Lab Guide Official training material for Barracuda certified trainings and Authorized Training Centers. Edition 2018 Revision 1.0 campus.barracuda.com
Recommendations for Device Provisioning Security
 Internet Telephony Services Providers Association Recommendations for Device Provisioning Security Version 2 May 2017 Contact: team@itspa.org.uk Contents Summary... 3 Introduction... 3 Risks... 4 Automatic
Internet Telephony Services Providers Association Recommendations for Device Provisioning Security Version 2 May 2017 Contact: team@itspa.org.uk Contents Summary... 3 Introduction... 3 Risks... 4 Automatic
SAML-Based SSO Solution
 About SAML SSO Solution, page 1 Single Sign on Single Service Provider Agreement, page 2 SAML-Based SSO Features, page 2 Basic Elements of a SAML SSO Solution, page 3 Cisco Unified Communications Applications
About SAML SSO Solution, page 1 Single Sign on Single Service Provider Agreement, page 2 SAML-Based SSO Features, page 2 Basic Elements of a SAML SSO Solution, page 3 Cisco Unified Communications Applications
penelope case management software AUTHENTICATION GUIDE v4.4 and higher
 penelope case management software AUTHENTICATION GUIDE v4.4 and higher Last modified: August 9, 2016 TABLE OF CONTENTS Authentication: The basics... 4 About authentication... 4 SSO authentication... 4
penelope case management software AUTHENTICATION GUIDE v4.4 and higher Last modified: August 9, 2016 TABLE OF CONTENTS Authentication: The basics... 4 About authentication... 4 SSO authentication... 4
AVS Portal Security User Guide
 AVS Portal Security User Guide Oregon Department of Human Services 2018 TABLE OF CONTENTS I. ACCESS OVERVIEW...2 II. AVS PORTAL.4 2.1 AVS PORTAL LOGIN. 4 2.2 SECURITY USER PORTAL VIEW..5 2.3 SECURITY USER
AVS Portal Security User Guide Oregon Department of Human Services 2018 TABLE OF CONTENTS I. ACCESS OVERVIEW...2 II. AVS PORTAL.4 2.1 AVS PORTAL LOGIN. 4 2.2 SECURITY USER PORTAL VIEW..5 2.3 SECURITY USER
Cloud FastPath: Highly Secure Data Transfer
 Cloud FastPath: Highly Secure Data Transfer Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. Tervela has been creating high performance
Cloud FastPath: Highly Secure Data Transfer Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. Tervela has been creating high performance
User Directories. Overview, Pros and Cons
 User Directories Overview, Pros and Cons Overview Secure ISMS can operate with one or more of the following user directories. Secure ISMS Users (ISMS) Internal users local to the Secure ISMS application
User Directories Overview, Pros and Cons Overview Secure ISMS can operate with one or more of the following user directories. Secure ISMS Users (ISMS) Internal users local to the Secure ISMS application
Oracle Eloqua Legacy Authenticated Microsites and Contact Users. Configuration Guide
 Oracle Eloqua Legacy Authenticated Microsites and Contact Users Configuration Guide 2019 Oracle Corporation. All rights reserved 04-Jan-2019 Contents 1 Authenticated microsites 3 2 Creating authenticated
Oracle Eloqua Legacy Authenticated Microsites and Contact Users Configuration Guide 2019 Oracle Corporation. All rights reserved 04-Jan-2019 Contents 1 Authenticated microsites 3 2 Creating authenticated
Salesforce Mobile App Security Guide
 Salesforce Mobile App Security Guide Version 3, 0 @salesforcedocs Last updated: October 11, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com,
Salesforce Mobile App Security Guide Version 3, 0 @salesforcedocs Last updated: October 11, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com,
FAQ. General Information: Online Support:
 FAQ General Information: info@cionsystems.com Online Support: support@cionsystems.com CionSystems Inc. Mailing Address: 16625 Redmond Way, Ste M106 Redmond, WA. 98052 http://www.cionsystems.com Phone:
FAQ General Information: info@cionsystems.com Online Support: support@cionsystems.com CionSystems Inc. Mailing Address: 16625 Redmond Way, Ste M106 Redmond, WA. 98052 http://www.cionsystems.com Phone:
Specialty Contractor User Manual. Table of Contents. Specialty Contractor User Manual Version 1 11/16/15
 Specialty Contractor User Manual Welcome to the C3 Training Database for Construction Career Collaborative! This software is where you keep track of your employees' training and safety credentials, project
Specialty Contractor User Manual Welcome to the C3 Training Database for Construction Career Collaborative! This software is where you keep track of your employees' training and safety credentials, project
Grapevine web hosting user manual. 12 August 2005
 Grapevine web hosting user manual 12 August 2005 Grapevine web hosting user manual 2 Contents Contents... 2 Introduction... 4 System features... 4 How it looks... 5 Main navigation... 5 Reports... 6 Web
Grapevine web hosting user manual 12 August 2005 Grapevine web hosting user manual 2 Contents Contents... 2 Introduction... 4 System features... 4 How it looks... 5 Main navigation... 5 Reports... 6 Web
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
Kenna Platform Security. A technical overview of the comprehensive security measures Kenna uses to protect your data
 Kenna Platform Security A technical overview of the comprehensive security measures Kenna uses to protect your data V3.0, MAY 2017 Multiple Layers of Protection Overview Password Salted-Hash Thank you
Kenna Platform Security A technical overview of the comprehensive security measures Kenna uses to protect your data V3.0, MAY 2017 Multiple Layers of Protection Overview Password Salted-Hash Thank you
SAML-Based SSO Solution
 About SAML SSO Solution, page 1 SAML-Based SSO Features, page 2 Basic Elements of a SAML SSO Solution, page 2 SAML SSO Web Browsers, page 3 Cisco Unified Communications Applications that Support SAML SSO,
About SAML SSO Solution, page 1 SAML-Based SSO Features, page 2 Basic Elements of a SAML SSO Solution, page 2 SAML SSO Web Browsers, page 3 Cisco Unified Communications Applications that Support SAML SSO,
Here is a screenshot of the log in screen you will see at the above address:
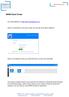 BWM Client Portal Our portal address is: https://bwm.clientspace.co.uk Here is a screenshot of the log in screen you will see at the above address: Here is an example of how your portal will look on screen
BWM Client Portal Our portal address is: https://bwm.clientspace.co.uk Here is a screenshot of the log in screen you will see at the above address: Here is an example of how your portal will look on screen
KYOCERA Net Admin User Guide
 KYOCERA Net Admin User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
KYOCERA Net Admin User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
Ekran System v.6.0 Privileged User Accounts and Sessions (PASM)
 Ekran System v.6.0 Privileged User Accounts and Sessions (PASM) Table of Contents About... 3 Using Privileged User Accounts... 4 Password Vault Configuration... 5 Defining Domain Administrator Credentials...
Ekran System v.6.0 Privileged User Accounts and Sessions (PASM) Table of Contents About... 3 Using Privileged User Accounts... 4 Password Vault Configuration... 5 Defining Domain Administrator Credentials...
Partner Side SMART Guide
 Partner Side SMART Guide Table of Contents 1. Introduction... 3 2. Partner Registration Process... 3 3. Additional Form... 12 4. Scorecard... 13 5. View Buyer Profile... 14 Partner Side User Manual 31
Partner Side SMART Guide Table of Contents 1. Introduction... 3 2. Partner Registration Process... 3 3. Additional Form... 12 4. Scorecard... 13 5. View Buyer Profile... 14 Partner Side User Manual 31
CLI users are not listed on the Cisco Prime Collaboration User Management page.
 Cisco Prime Collaboration supports creation of user roles. A user can be assigned the Super Administrator role. A Super Administrator can perform tasks that both system administrator and network administrator
Cisco Prime Collaboration supports creation of user roles. A user can be assigned the Super Administrator role. A Super Administrator can perform tasks that both system administrator and network administrator
Contents. Is Rumpus Secure? 2. Use Care When Creating User Accounts 2. Managing Passwords 3. Watch Out For Symbolic Links 4. Deploy A Firewall 5
 Contents Is Rumpus Secure? 2 Use Care When Creating User Accounts 2 Managing Passwords 3 Watch Out For Symbolic Links 4 Deploy A Firewall 5 Minimize Running Applications And Processes 5 Manage Physical
Contents Is Rumpus Secure? 2 Use Care When Creating User Accounts 2 Managing Passwords 3 Watch Out For Symbolic Links 4 Deploy A Firewall 5 Minimize Running Applications And Processes 5 Manage Physical
MANAGING LOCAL AUTHENTICATION IN WINDOWS
 MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
SC Common Reporting (ComRep) Portal User Manual
 SC Common Reporting (ComRep) Portal User Manual 1 Contents Page 1. Introduction 1.1 Overview of ComRep portal: brief overview and explanation on ComRep objectives, features and user roles. 3 2. Get Started
SC Common Reporting (ComRep) Portal User Manual 1 Contents Page 1. Introduction 1.1 Overview of ComRep portal: brief overview and explanation on ComRep objectives, features and user roles. 3 2. Get Started
Club admins are able to perform the following actions via the Participant Login Management screen:
 This Rugby Link self-help guide explains the process of how Club administrators can send participant logins. This will enable the participant to log into the online registration forms and also the participant
This Rugby Link self-help guide explains the process of how Club administrators can send participant logins. This will enable the participant to log into the online registration forms and also the participant
ColdFusion Application Security: The Next Step - Handout
 ColdFusion Application Security: The Next Step - Handout Jason Dean http://www.12robots.com Boston CFUG September 16 th, 2009 REQUEST FORGERIES A request forgery, also sometimes called a Cross-Site (or
ColdFusion Application Security: The Next Step - Handout Jason Dean http://www.12robots.com Boston CFUG September 16 th, 2009 REQUEST FORGERIES A request forgery, also sometimes called a Cross-Site (or
Contents About This Guide... 5 About Notifications... 5 Managing User Accounts... 6 Managing Companies Managing Password Policies...
 Cloud Services Identity Management Administration Guide Version 17 July 2017 Contents About This Guide... 5 About Notifications... 5 Managing User Accounts... 6 About the User Administration Table...
Cloud Services Identity Management Administration Guide Version 17 July 2017 Contents About This Guide... 5 About Notifications... 5 Managing User Accounts... 6 About the User Administration Table...
CYAN SECURE WEB Installing on Windows
 CYAN SECURE WEB September 2009 Applies to: 1.7 and above Table of Contents 1 Introduction... 2 2 Preparation... 2 3 Network Integration... 3 3.1 Out-of-line Deployment... 3 3.2 DMZ Deployment... 3 4 Proxy
CYAN SECURE WEB September 2009 Applies to: 1.7 and above Table of Contents 1 Introduction... 2 2 Preparation... 2 3 Network Integration... 3 3.1 Out-of-line Deployment... 3 3.2 DMZ Deployment... 3 4 Proxy
Arrow Contract Management System. Electronic Tendering Guide
 Arrow Contract Management System Electronic Tendering Guide CONTENTS 1. RECEIVING & VIEWING A TENDER INVITATION... 3 2. LOGGING INTO PROCON... 4 3. OBTAINING TENDER DOCUMENTS... 5 4. HOW TO RESPOND ELECTRONICALLY
Arrow Contract Management System Electronic Tendering Guide CONTENTS 1. RECEIVING & VIEWING A TENDER INVITATION... 3 2. LOGGING INTO PROCON... 4 3. OBTAINING TENDER DOCUMENTS... 5 4. HOW TO RESPOND ELECTRONICALLY
How-To Guide for Administrators
 Users The Users area enables you to add users, reset their passwords, manage their profile data, and access their MyTeachingStrategies account as that user. The main Users screen provides an overview of
Users The Users area enables you to add users, reset their passwords, manage their profile data, and access their MyTeachingStrategies account as that user. The main Users screen provides an overview of
SafeConsole On-Prem Install Guide
 SafeConsole On-Prem Install Guide This guide applies to SafeConsole 5.0.5 Introduction This guide describes how to install a new SafeConsole server on Windows using the SafeConsole installer. As an option,
SafeConsole On-Prem Install Guide This guide applies to SafeConsole 5.0.5 Introduction This guide describes how to install a new SafeConsole server on Windows using the SafeConsole installer. As an option,
CSU Talent Management User Guide Search Committee Member How to Log In and View Applications
 CSU Talent Management User Guide Search Committee Member How to Log In and View Applications Last Updated: 8/30/2017 my HR Working together. Search Committee Member E-mail Notification 1. The Search Committee
CSU Talent Management User Guide Search Committee Member How to Log In and View Applications Last Updated: 8/30/2017 my HR Working together. Search Committee Member E-mail Notification 1. The Search Committee
Link Gateway Initial Configuration Manual
 Link Gateway Initial Configuration Manual Copyright 2016 NetLinkz. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
Link Gateway Initial Configuration Manual Copyright 2016 NetLinkz. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
VMware AirWatch Certificate Authentication for Cisco IPSec VPN
 VMware AirWatch Certificate Authentication for Cisco IPSec VPN For VMware AirWatch Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
VMware AirWatch Certificate Authentication for Cisco IPSec VPN For VMware AirWatch Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
SSPR Registration. 1. Use your SVSU credentials to log in to
 Self-Service Password Reset (SSPR) SVSU uses a Self-Service Password Reset system to make it easy to recover your password if you ever forget it. To ensure you never lose access to your account, you must
Self-Service Password Reset (SSPR) SVSU uses a Self-Service Password Reset system to make it easy to recover your password if you ever forget it. To ensure you never lose access to your account, you must
Setting Up Resources in VMware Identity Manager (SaaS) Modified 15 SEP 2017 VMware Identity Manager
 Setting Up Resources in VMware Identity Manager (SaaS) Modified 15 SEP 2017 VMware Identity Manager Setting Up Resources in VMware Identity Manager (SaaS) You can find the most up-to-date technical documentation
Setting Up Resources in VMware Identity Manager (SaaS) Modified 15 SEP 2017 VMware Identity Manager Setting Up Resources in VMware Identity Manager (SaaS) You can find the most up-to-date technical documentation
inty CASCADE Management Portal Self Service Ticketing Guide (Trusted Advisor)
 inty CASCADE Management Portal Self Service Ticketing Guide (Trusted Advisor) Contents 1. Overview... 2 2. Accessing the Portal... 2 3. Logging In... 2 4. Forgotten Your Password?... 3 5. Creating a New
inty CASCADE Management Portal Self Service Ticketing Guide (Trusted Advisor) Contents 1. Overview... 2 2. Accessing the Portal... 2 3. Logging In... 2 4. Forgotten Your Password?... 3 5. Creating a New
Certified Secure Web Application Secure Development Checklist
 www.certifiedsecure.com info@certifiedsecure.com Tel.: +31 (0)70 310 13 40 Loire 128-A 2491 AJ The Hague The Netherlands About Certified Secure Checklist Certified Secure exists to encourage and fulfill
www.certifiedsecure.com info@certifiedsecure.com Tel.: +31 (0)70 310 13 40 Loire 128-A 2491 AJ The Hague The Netherlands About Certified Secure Checklist Certified Secure exists to encourage and fulfill
Pass, No Record: An Android Password Manager
 Pass, No Record: An Android Password Manager Alex Konradi, Samuel Yeom December 4, 2015 Abstract Pass, No Record is an Android password manager that allows users to securely retrieve passwords from a server
Pass, No Record: An Android Password Manager Alex Konradi, Samuel Yeom December 4, 2015 Abstract Pass, No Record is an Android password manager that allows users to securely retrieve passwords from a server
Welcome to ncrypted Cloud!... 4 Getting Started Register for ncrypted Cloud Getting Started Download ncrypted Cloud...
 Windows User Manual Welcome to ncrypted Cloud!... 4 Getting Started 1.1... 5 Register for ncrypted Cloud... 5 Getting Started 1.2... 7 Download ncrypted Cloud... 7 Getting Started 1.3... 9 Access ncrypted
Windows User Manual Welcome to ncrypted Cloud!... 4 Getting Started 1.1... 5 Register for ncrypted Cloud... 5 Getting Started 1.2... 7 Download ncrypted Cloud... 7 Getting Started 1.3... 9 Access ncrypted
Contents. SSL-Based Services: HTTPS and FTPS 2. Generating A Certificate 2. Creating A Self-Signed Certificate 3. Obtaining A Signed Certificate 4
 Contents SSL-Based Services: HTTPS and FTPS 2 Generating A Certificate 2 Creating A Self-Signed Certificate 3 Obtaining A Signed Certificate 4 Enabling Secure Services 5 A Note About Ports 5 Connecting
Contents SSL-Based Services: HTTPS and FTPS 2 Generating A Certificate 2 Creating A Self-Signed Certificate 3 Obtaining A Signed Certificate 4 Enabling Secure Services 5 A Note About Ports 5 Connecting
Help Document Series: Connecting to your Exchange mailbox via Outlook from off-campus
 Help Document Series: Connecting to your Exchange mailbox via Outlook from off-campus This document will take you through setting up your Clark Exchange mailbox in Outlook 2003 from off-campus. This will
Help Document Series: Connecting to your Exchange mailbox via Outlook from off-campus This document will take you through setting up your Clark Exchange mailbox in Outlook 2003 from off-campus. This will
User Administration Vaultview Security
 User Administration Vaultview Security User Administration using Vaultview Security allows Vaultview Administrators to define Roles and Permissions within Vaultview to grant users access to functions and
User Administration Vaultview Security User Administration using Vaultview Security allows Vaultview Administrators to define Roles and Permissions within Vaultview to grant users access to functions and
Deploy the ExtraHop Discover Appliance in Azure
 Deploy the ExtraHop Discover Appliance in Azure Published: 2018-04-20 The following procedures explain how to deploy an ExtraHop Discover virtual appliance in a Microsoft Azure environment. You must have
Deploy the ExtraHop Discover Appliance in Azure Published: 2018-04-20 The following procedures explain how to deploy an ExtraHop Discover virtual appliance in a Microsoft Azure environment. You must have
Emergency Routing Service (ERS) Subscriber Guide
 Emergency Routing Service (ERS) Subscriber Guide Rev B August 15, 2016 1 SUBSCRIBER PORTAL... 3 Login and Registration... 3 Subscriber Portal Home Page... 5 Changing your Location... 6 1.3.1 Recent Locations...
Emergency Routing Service (ERS) Subscriber Guide Rev B August 15, 2016 1 SUBSCRIBER PORTAL... 3 Login and Registration... 3 Subscriber Portal Home Page... 5 Changing your Location... 6 1.3.1 Recent Locations...
New Password Reset for Dental Connect Provider
 New Password Reset for Dental Connect Provider 1 INDEX Access Dental Connect for Providers:... 3 1. Username verification:... 4 1.1 user name not provided:... 5 1.2 Invalid user name:... 6 1.3 Invalid
New Password Reset for Dental Connect Provider 1 INDEX Access Dental Connect for Providers:... 3 1. Username verification:... 4 1.1 user name not provided:... 5 1.2 Invalid user name:... 6 1.3 Invalid
Oracle Database Security and Audit. Authentication and authorization
 Copyright 2014, Oracle Database Security and Audit Beyond Checklists Authentication and authorization Copyright 2014, Learning objectives Understand authentication Understand authorization Understand the
Copyright 2014, Oracle Database Security and Audit Beyond Checklists Authentication and authorization Copyright 2014, Learning objectives Understand authentication Understand authorization Understand the
Participant Information Management System (PIMS)
 Participant Information Management System (PIMS) User Manual Andrew Jackson Building Third Floor For assistance contact: 502 Deaderick St., Nashville, TN 37243 PIMS@THDA.org 1. Go to https://resources.thda.org/pims
Participant Information Management System (PIMS) User Manual Andrew Jackson Building Third Floor For assistance contact: 502 Deaderick St., Nashville, TN 37243 PIMS@THDA.org 1. Go to https://resources.thda.org/pims
Using the AETA Remote Access service
 Using the AETA Remote Access service 1. Background AETA codecs can all be controlled via an IP interface, and for instance a computer can easily take control over a codec when it is connected on the same
Using the AETA Remote Access service 1. Background AETA codecs can all be controlled via an IP interface, and for instance a computer can easily take control over a codec when it is connected on the same
WebEx Integration User Guide. Cvent, Inc 1765 Greensboro Station Place McLean, VA
 WebEx Integration User Guide 2018 Cvent, Inc 1765 Greensboro Station Place McLean, VA 22102 www.cvent.com Contents WebEx Integration User Guide... 3 Enabling WebEx Integration in Your Account... 4 Setting
WebEx Integration User Guide 2018 Cvent, Inc 1765 Greensboro Station Place McLean, VA 22102 www.cvent.com Contents WebEx Integration User Guide... 3 Enabling WebEx Integration in Your Account... 4 Setting
Workspace ONE UEM Certificate Authentication for Cisco IPSec VPN. VMware Workspace ONE UEM 1810
 Workspace ONE UEM Certificate Authentication for Cisco IPSec VPN VMware Workspace ONE UEM 1810 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Workspace ONE UEM Certificate Authentication for Cisco IPSec VPN VMware Workspace ONE UEM 1810 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Vodafone Secure Device Manager Administration User Guide
 Vodafone Secure Device Manager Administration User Guide Vodafone New Zealand Limited. Correct as of June 2017. Vodafone Ready Business Contents Introduction 3 Help 4 How to find help in the Vodafone Secure
Vodafone Secure Device Manager Administration User Guide Vodafone New Zealand Limited. Correct as of June 2017. Vodafone Ready Business Contents Introduction 3 Help 4 How to find help in the Vodafone Secure
Security Guide Zoom Video Communications Inc.
 Zoom unifies cloud video conferencing, simple online meetings, group messaging, and a softwaredefined conference room solution into one easy-to-use platform. Zoom offers the best video, audio, and wireless
Zoom unifies cloud video conferencing, simple online meetings, group messaging, and a softwaredefined conference room solution into one easy-to-use platform. Zoom offers the best video, audio, and wireless
SelectSurveyASP Advanced User Manual
 SelectSurveyASP Advanced User Manual Creating Surveys 2 Designing Surveys 2 Templates 3 Libraries 4 Item Types 4 Scored Surveys 5 Page Conditions 5 Piping Answers 6 Previewing Surveys 7 Managing Surveys
SelectSurveyASP Advanced User Manual Creating Surveys 2 Designing Surveys 2 Templates 3 Libraries 4 Item Types 4 Scored Surveys 5 Page Conditions 5 Piping Answers 6 Previewing Surveys 7 Managing Surveys
Salesforce1 Mobile Security White Paper. Revised: April 2014
 Salesforce1 Mobile Security White Paper Revised: April 2014 Table of Contents Introduction Salesforce1 Architecture Overview Authorization and Permissions Communication Security Authentication OAuth Pairing
Salesforce1 Mobile Security White Paper Revised: April 2014 Table of Contents Introduction Salesforce1 Architecture Overview Authorization and Permissions Communication Security Authentication OAuth Pairing
USER MANUAL. SalesPort Salesforce Customer Portal for WordPress (Lightning Mode) TABLE OF CONTENTS. Version: 3.1.0
 USER MANUAL TABLE OF CONTENTS Introduction...1 Benefits of Customer Portal...1 Prerequisites...1 Installation...2 Salesforce App Installation... 2 Salesforce Lightning... 2 WordPress Manual Plug-in installation...
USER MANUAL TABLE OF CONTENTS Introduction...1 Benefits of Customer Portal...1 Prerequisites...1 Installation...2 Salesforce App Installation... 2 Salesforce Lightning... 2 WordPress Manual Plug-in installation...
Registration and account management. NPDA User Guide: How to register to use the NPDA data capture system
 NPDA User Guide: How to register to use the NPDA data capture system Register an account on the system PLEASE NOTE: If you have already registered to submit data to the NPDA in 2017, your login details
NPDA User Guide: How to register to use the NPDA data capture system Register an account on the system PLEASE NOTE: If you have already registered to submit data to the NPDA in 2017, your login details
ENROLLING FOR YOUR SYKES HOME TRAINING
 ENROLLING FOR YOUR SYKES HOME TRAINING Upon the completion of ALL your preemployment requirements, your employee profile will be finalized and you will be pushed into WebCenter and allowed to enroll for
ENROLLING FOR YOUR SYKES HOME TRAINING Upon the completion of ALL your preemployment requirements, your employee profile will be finalized and you will be pushed into WebCenter and allowed to enroll for
Monitise. RSA Adaptive Authentication On-Premise Implementation Guide. Partner Information. Monitise Mobile Banking Solution
 RSA Adaptive Authentication On-Premise Implementation Guide Partner Information Last Modified: June 12, 2013 Product Information Partner Name Web Site www.monitise.com Product Name Version & Platform 5.0
RSA Adaptive Authentication On-Premise Implementation Guide Partner Information Last Modified: June 12, 2013 Product Information Partner Name Web Site www.monitise.com Product Name Version & Platform 5.0
Salesforce Mobile App Security Guide
 Salesforce Mobile App Security Guide Version 2, 2 @salesforcedocs Last updated: November 2, 2017 Copyright 2000 2017 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com,
Salesforce Mobile App Security Guide Version 2, 2 @salesforcedocs Last updated: November 2, 2017 Copyright 2000 2017 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com,
Vendor: Microsoft. Exam Code: Exam Name: MTA Security Fundamentals Practice Test. Version: Demo
 Vendor: Microsoft Exam Code: 98-367 Exam Name: MTA Security Fundamentals Practice Test Version: Demo DEMO QUESTION 1 To prevent users from copying data to removable media, you should: A. Lock the computer
Vendor: Microsoft Exam Code: 98-367 Exam Name: MTA Security Fundamentals Practice Test Version: Demo DEMO QUESTION 1 To prevent users from copying data to removable media, you should: A. Lock the computer
AN IPSWITCH WHITEPAPER. The Definitive Guide to Secure FTP
 AN IPSWITCH WHITEPAPER The Definitive Guide to Secure FTP The Importance of File Transfer Are you concerned with the security of file transfer processes in your company? According to a survey of IT pros
AN IPSWITCH WHITEPAPER The Definitive Guide to Secure FTP The Importance of File Transfer Are you concerned with the security of file transfer processes in your company? According to a survey of IT pros
Add/Manage Business Users
 Primary and Secondary Administrators are created by First Interstate Bank and have full access to functionality; these Administrators set up other employees as Business Banking users via the Entitlements
Primary and Secondary Administrators are created by First Interstate Bank and have full access to functionality; these Administrators set up other employees as Business Banking users via the Entitlements
Secure Internet File Transfer (SIFT) HTTPS User Guide. How to send and receive files via HTTPS using SIFT
 Secure Internet File Transfer (SIFT) HTTPS User Guide How to send and receive files via HTTPS using SIFT Document History Version Date Reason For Change 0.1 22/02/2012 Initial Version 0.2 06/06/2016 Updated
Secure Internet File Transfer (SIFT) HTTPS User Guide How to send and receive files via HTTPS using SIFT Document History Version Date Reason For Change 0.1 22/02/2012 Initial Version 0.2 06/06/2016 Updated
Configuring Your Mail Server, Time Zone, and Locale
 Configuring Your Mail Server, Time Zone, and Locale Configuring an Email (SMTP) Server, page 1 Setting the Time Zone, Language, and Locale, page 7 Creating Administrator Accounts, page 7 About System Testing,
Configuring Your Mail Server, Time Zone, and Locale Configuring an Email (SMTP) Server, page 1 Setting the Time Zone, Language, and Locale, page 7 Creating Administrator Accounts, page 7 About System Testing,
System Setup. Accessing the Administration Interface CHAPTER
 CHAPTER 3 The system can be configured through the web interface to provide the networking configuration for the appliance and other system settings that are important such as time and SSL certificate.
CHAPTER 3 The system can be configured through the web interface to provide the networking configuration for the appliance and other system settings that are important such as time and SSL certificate.
Tenable.io for Thycotic
 How-To Guide Tenable.io for Thycotic Introduction This document describes how to deploy Tenable.io for integration with Thycotic Secret Server. Please email any comments and suggestions to support@tenable.com.
How-To Guide Tenable.io for Thycotic Introduction This document describes how to deploy Tenable.io for integration with Thycotic Secret Server. Please email any comments and suggestions to support@tenable.com.
System Administrator s Guide Login. Updated: May 2018 Version: 2.4
 System Administrator s Guide Login Updated: May 2018 Version: 2.4 Contents CONTENTS... 2 WHAT S NEW IN THIS VERSION 2018R1 RELEASE... 4 Password Retrieval via Email (GDPR Alignment)... 4 Self-Registration
System Administrator s Guide Login Updated: May 2018 Version: 2.4 Contents CONTENTS... 2 WHAT S NEW IN THIS VERSION 2018R1 RELEASE... 4 Password Retrieval via Email (GDPR Alignment)... 4 Self-Registration
USER GUIDELINES. Q 2. Is it necessary to configure password retrieval question and answer? How can I do that? Q 3. How can I change password?
 USER GUIDELINES Revision 1.8 20 August, 2015 Q 1. How can I log into my webmail? Q 2. Is it necessary to configure password retrieval question and answer? How can I do that? Q 3. How can I change password?
USER GUIDELINES Revision 1.8 20 August, 2015 Q 1. How can I log into my webmail? Q 2. Is it necessary to configure password retrieval question and answer? How can I do that? Q 3. How can I change password?
VMware AirWatch Integration with F5 Guide Enabling secure connections between mobile applications and your backend resources
 VMware AirWatch Integration with F5 Guide Enabling secure connections between mobile applications and your backend resources Workspace ONE UEM v9.6 Have documentation feedback? Submit a Documentation Feedback
VMware AirWatch Integration with F5 Guide Enabling secure connections between mobile applications and your backend resources Workspace ONE UEM v9.6 Have documentation feedback? Submit a Documentation Feedback
imaconnect: Guide to the system
 imaconnect: Guide to the system This Guide is intended to assist you navigate through the imaconnect System. You may refer to the links provided in the next slide, to navigate quickly to your area of Guidance
imaconnect: Guide to the system This Guide is intended to assist you navigate through the imaconnect System. You may refer to the links provided in the next slide, to navigate quickly to your area of Guidance
GoToMyPC Corporate Administrator Guide
 GoToMyPC Corporate Administrator Guide Contents Getting Started... 6 Administration Center Overview... 6 Log in to the Administration Center... 6 Notes on Installation and Feature Access... 8 Mac Features...
GoToMyPC Corporate Administrator Guide Contents Getting Started... 6 Administration Center Overview... 6 Log in to the Administration Center... 6 Notes on Installation and Feature Access... 8 Mac Features...
Contents. SSL-Based Services: HTTPS and FTPS 2. Generating A Certificate 2. Creating A Self-Signed Certificate 3. Obtaining A Signed Certificate 4
 Contents SSL-Based Services: HTTPS and FTPS 2 Generating A Certificate 2 Creating A Self-Signed Certificate 3 Obtaining A Signed Certificate 4 Enabling Secure Services 5 SSL/TLS Security Level 5 A Note
Contents SSL-Based Services: HTTPS and FTPS 2 Generating A Certificate 2 Creating A Self-Signed Certificate 3 Obtaining A Signed Certificate 4 Enabling Secure Services 5 SSL/TLS Security Level 5 A Note
Indian Standards on DVDs
 Indian Standards on DVDs User Manual Version 1.0 Prepared by Everonn Education Ltd Table of Contents 1. Introduction...3 1.1 Document Objective... 3 1.2 Who will read this manual... 3 2. Overview...3 3.
Indian Standards on DVDs User Manual Version 1.0 Prepared by Everonn Education Ltd Table of Contents 1. Introduction...3 1.1 Document Objective... 3 1.2 Who will read this manual... 3 2. Overview...3 3.
Web and MAC Authentication
 3 Web and MAC Authentication Contents Overview..................................................... 3-2 Client Options.............................................. 3-3 General Features............................................
3 Web and MAC Authentication Contents Overview..................................................... 3-2 Client Options.............................................. 3-3 General Features............................................
ESS Security Enhancements
 ESS Security Enhancements payentry.com Employee Self Service Enhancements 1 Table of Contents INTRODUCTION 3 EXISTING EMPLOYEES 3 Existing Employee -Email Address 4 Existing Employee - Username 4 Existing
ESS Security Enhancements payentry.com Employee Self Service Enhancements 1 Table of Contents INTRODUCTION 3 EXISTING EMPLOYEES 3 Existing Employee -Email Address 4 Existing Employee - Username 4 Existing
SaaS Security for Confirmit Horizons Arnt Feruglio Chief Operating Officer
 SaaS Security for Confirmit Horizons Arnt Feruglio Chief Operating Officer April 2017 Confirmit Horizons v22 About this document This document describes the Confirmit Horizons SaaS environments and security
SaaS Security for Confirmit Horizons Arnt Feruglio Chief Operating Officer April 2017 Confirmit Horizons v22 About this document This document describes the Confirmit Horizons SaaS environments and security
3) Click the Screen Sharing option and click connect to establish the session
 Preliminary steps before starting the experiment: 1) Click the Launch button to start the experiment. 2) Click OK to create a new session 3) Click the Screen Sharing option and click connect to establish
Preliminary steps before starting the experiment: 1) Click the Launch button to start the experiment. 2) Click OK to create a new session 3) Click the Screen Sharing option and click connect to establish
Configuring the Cisco APIC-EM Settings
 Logging into the Cisco APIC-EM, page 1 Quick Tour of the APIC-EM Graphical User Interface (GUI), page 2 Configuring the Prime Infrastructure Settings, page 3 Discovery Credentials, page 4 Security, page
Logging into the Cisco APIC-EM, page 1 Quick Tour of the APIC-EM Graphical User Interface (GUI), page 2 Configuring the Prime Infrastructure Settings, page 3 Discovery Credentials, page 4 Security, page
Customer Care Portal User Guide
 Customer Care Portal User Guide Table of Contents Logging In...3 Live Chat... 3 Viewing your Cases...4 Logging a Case for Customer Support...4 Projects...6 Knowledge Base....6 Content.....7 Forms...7 Event
Customer Care Portal User Guide Table of Contents Logging In...3 Live Chat... 3 Viewing your Cases...4 Logging a Case for Customer Support...4 Projects...6 Knowledge Base....6 Content.....7 Forms...7 Event
MULTI-FACTOR AUTHENTICATION SET-UP
 MULTI-FACTOR AUTHENTICATION SET-UP DepositPartner Web Application FIRST TIME ENROLLMENT 1. Enter your User ID and click Login. 2. Click Begin Setup to continue or Sign Off to cancel this process and exit
MULTI-FACTOR AUTHENTICATION SET-UP DepositPartner Web Application FIRST TIME ENROLLMENT 1. Enter your User ID and click Login. 2. Click Begin Setup to continue or Sign Off to cancel this process and exit
Office 365 and Azure Active Directory Identities In-depth
 Office 365 and Azure Active Directory Identities In-depth Jethro Seghers Program Director SkySync #ITDEVCONNECTIONS ITDEVCONNECTIONS.COM Agenda Introduction Identities Different forms of authentication
Office 365 and Azure Active Directory Identities In-depth Jethro Seghers Program Director SkySync #ITDEVCONNECTIONS ITDEVCONNECTIONS.COM Agenda Introduction Identities Different forms of authentication
SUPPLIERS - SMARTSOURCE QUICK REFERENCE GUIDE
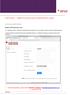 SUPPLIERS - SMARTSOURCE QUICK REFERENCE GUIDE ACCESSING SMARTSOURCE Supplier Self Registration steps As a supplier there will be a link within the advertisement for Tenders/EOI s etc. will redirect you
SUPPLIERS - SMARTSOURCE QUICK REFERENCE GUIDE ACCESSING SMARTSOURCE Supplier Self Registration steps As a supplier there will be a link within the advertisement for Tenders/EOI s etc. will redirect you
MyPatientVisit Patient Portal User Guide
 Table of Contents Patient Setup and Login to the Patient Portal...2 Patient Registration... 2 Security Questions... 3 Patient Portal Dashboard...4 Patient s Dashboard... 4 Patient Documents in mydocuments
Table of Contents Patient Setup and Login to the Patient Portal...2 Patient Registration... 2 Security Questions... 3 Patient Portal Dashboard...4 Patient s Dashboard... 4 Patient Documents in mydocuments
Configure Settings and Customize Notifications on FindIT Network Probe
 Configure Email Settings and Customize Email Notifications on FindIT Network Probe Objective Cisco FindIT Network Probe equips a network administrator with indispensable tools that help securely monitor
Configure Email Settings and Customize Email Notifications on FindIT Network Probe Objective Cisco FindIT Network Probe equips a network administrator with indispensable tools that help securely monitor
Step 1: Adding Darwin to your computer
 Step 1: Adding Darwin to your computer You MUST be on GoucherWIFI. If you receive any network connection problems at any point, double-check your WIFI connection. Remove/Move GoucherGuest and GoucherMultimedia
Step 1: Adding Darwin to your computer You MUST be on GoucherWIFI. If you receive any network connection problems at any point, double-check your WIFI connection. Remove/Move GoucherGuest and GoucherMultimedia
Platform Compatibility... 1 Enhancements... 2 Known Issues... 3 Upgrading SonicOS Enhanced Image Procedures... 3 Related Technical Documentation...
 SonicOS Contents Platform Compatibility... 1 Enhancements... 2 Known Issues... 3 Upgrading SonicOS Enhanced Image Procedures... 3 Related Technical Documentation...7 Platform Compatibility The SonicOS
SonicOS Contents Platform Compatibility... 1 Enhancements... 2 Known Issues... 3 Upgrading SonicOS Enhanced Image Procedures... 3 Related Technical Documentation...7 Platform Compatibility The SonicOS
ncrypted Cloud works on desktops and laptop computers, mobile devices, and the web.
 OS X User Manual Welcome to ncrypted Cloud! ncrypted Cloud is a Security Collaboration application that uses Industry Standard Encryption Technology (AES-256 bit encryption) to secure files stored in the
OS X User Manual Welcome to ncrypted Cloud! ncrypted Cloud is a Security Collaboration application that uses Industry Standard Encryption Technology (AES-256 bit encryption) to secure files stored in the
Hearing Care Dashboard
 Hearing Care Dashboard Registration & Management Hearing Care Dashboard: Register and Manage Your Organization Hearing Care Anywhere is Starkey s remote programming system. The Hearing Care Dashboard is
Hearing Care Dashboard Registration & Management Hearing Care Dashboard: Register and Manage Your Organization Hearing Care Anywhere is Starkey s remote programming system. The Hearing Care Dashboard is
WAM!NET Submission Icons. Help Guide. March 2015
 WAM!NET Submission Icons Help Guide March 2015 Document Contents 1 Introduction...2 1.1 Submission Option Resource...2 1.2 Submission Icon Type...3 1.2.1 Authenticated Submission Icons...3 1.2.2 Anonymous
WAM!NET Submission Icons Help Guide March 2015 Document Contents 1 Introduction...2 1.1 Submission Option Resource...2 1.2 Submission Icon Type...3 1.2.1 Authenticated Submission Icons...3 1.2.2 Anonymous
Using the Terminal Services Gateway Lesson 10
 Using the Terminal Services Gateway Lesson 10 Skills Matrix Technology Skill Objective Domain Objective # Deploying a TS Gateway Server Configure Terminal Services Gateway 2.2 Terminal Services (TS) Web
Using the Terminal Services Gateway Lesson 10 Skills Matrix Technology Skill Objective Domain Objective # Deploying a TS Gateway Server Configure Terminal Services Gateway 2.2 Terminal Services (TS) Web
Quicklaw Client Administration Guide
 Quicklaw Client Administration Guide A how-to guide for administrative users of Canada s leading online legal research service. www.lexisnexis.com/ca/legal Client Administration The Client Administration
Quicklaw Client Administration Guide A how-to guide for administrative users of Canada s leading online legal research service. www.lexisnexis.com/ca/legal Client Administration The Client Administration
ISS INDIA Active Directory Self Password Management Solution ISS Facility Services India PVT.LTD.
 ISS INDIA Active Directory Self Password Management Solution ISS Facility Services India PVT.LTD. Page 1 of 14 Contents 1. OVERVIEW... 3 2. USER REGISTRATION PROCESS... 3 STEP 1: USER LOGIN... 3 STEP 2:
ISS INDIA Active Directory Self Password Management Solution ISS Facility Services India PVT.LTD. Page 1 of 14 Contents 1. OVERVIEW... 3 2. USER REGISTRATION PROCESS... 3 STEP 1: USER LOGIN... 3 STEP 2:
docalpha Monitoring Station
 ARTSYL DOCALPHA MONITORING STATION MANUAL 1. docalpha Architecture Overview... 3 1.1. Monitoring Station Overview... 4 2. What's New in docalpha Monitoring Station 4.5... 4 3. Working with Monitoring Station...
ARTSYL DOCALPHA MONITORING STATION MANUAL 1. docalpha Architecture Overview... 3 1.1. Monitoring Station Overview... 4 2. What's New in docalpha Monitoring Station 4.5... 4 3. Working with Monitoring Station...
RSA SecurID Ready Implementation Guide. Last Modified: December 13, 2013
 Ping Identity RSA SecurID Ready Implementation Guide Partner Information Last Modified: December 13, 2013 Product Information Partner Name Ping Identity Web Site www.pingidentity.com Product Name PingFederate
Ping Identity RSA SecurID Ready Implementation Guide Partner Information Last Modified: December 13, 2013 Product Information Partner Name Ping Identity Web Site www.pingidentity.com Product Name PingFederate
Louisiana Medicaid Management Information System (LMMIS)
 Louisiana Medicaid Management Information System (LMMIS) LAMedicaid Provider Login (Admin Manage Users) User Manual Date Created: 09/17/2018 Prepared By Technical Communications Group Molina Medicaid Solutions
Louisiana Medicaid Management Information System (LMMIS) LAMedicaid Provider Login (Admin Manage Users) User Manual Date Created: 09/17/2018 Prepared By Technical Communications Group Molina Medicaid Solutions
