>MESSAGELABS END USER IT SECURITY GUIDE >WHAT STEPS CAN YOU TAKE TO KEEP YOURSELF, YOUR COLLEAGUES AND YOUR COMPANY SAFE ONLINE?
|
|
|
- Barnard Goodwin
- 5 years ago
- Views:
Transcription
1 >MESSAGELABS END USER IT SECURITY GUIDE >WHAT STEPS CAN YOU TAKE TO KEEP YOURSELF, YOUR COLLEAGUES AND YOUR COMPANY SAFE ONLINE?
2 >CONTENTS >WHAT IS MESSAGING AND WEB SECURITY? >P1 > THREATS >P1 >VIRUSES >P1 >SPAM >P1 >PHISHING >P2 >DOS & DON TS >P3 >WEB THREATS >P4 >SPYWARE >P4 >DOS & DON TS >P4 >IM THREATS >INSTANT MESSAGING >P5 >DOS & DON TS >P5
3 >WHAT IS MESSAGING AND WEB SECURITY? AND WHY IS IT IMPORTANT? , the web and instant messaging are all important methods of communicating and exchanging vital business information. While the benefits of these technologies are great, enabling us to communicate and exchange information with practically anyone, they also present a real threat to our security, productivity and profitability. This short guide to messaging and web security outlines the main dangers and the steps you can take to make sure you and your company stay secure. > THREATS AND HOW TO PROTECT AGAINST THEM >VIRUSES Viruses are one of the most common threats from . You may also have heard the terms worm or trojan, these are essentially different types of viruses. In essence, a virus is a program or programming code that replicates itself by being copied, or initiating its own copying, to another program, document or part of your computer. >MYDOOM > WORM Most viruses spread by enticing people to open an innocent looking and/or attachment, which actually contains the virus. Viruses are particularly dangerous because they often arrive in s from people you know, sending themselves on to all of the people in your address book. >SPAM Billions of spam s are sent every day, making it a huge problem. Spam has become such a familiar, not to mention annoying, feature of the landscape that it s easy to forget the damage it does to a business. >RUSSIAN3 >SUBJECT: EVER HEARD THAT YOU RE GETTING FAT? >TEXT AND IMAGE-BASED SPAM Put simply, spam is no longer just a nuisance. It significantly affects business efficiency and productivity. Think of the amount of time you spend during the course of a year identifying and deleting spam s. These messages clog up your inbox, requiring more expense and effort to safeguard against the relentless tide of spam. ALL IMAGES ARE GENERATED USING SOURCE CODE FROM ACTUAL THEATS PAGE 1
4 >PHISHING A phishing is designed to look like a genuine from your bank or other financial institution. However, it will in fact lure you to a fraudulent website where you will be asked to enter your bank account or credit card details. Phishing s are particularly dangerous because they are a social engineering technique and will in many cases look like the real thing. Remember, no bank or financial institution will ever ask you to confirm your account number and login details in an . >PHISHING5 >SUBJECT: ACCOUNT NOTIFICATION! The design is spoofed to resemble a well known brand (in this example we have simulated a bank) Phishing s will often direct you to a false site and ask you to confirm your account information The false site is made to look like the real website The web address is actually a graphic, overlaid onto the screen to make you think it s the correct address A graphic simulates the padlock symbol ALL IMAGES ARE GENERATED USING SOURCE CODE FROM ACTUAL THEATS PAGE 2
5 >DOS & DON TS: Do make sure you download the latest security updates. Do look out for words or language used which would not actually be used by the sender. Don t open it if you think you have received a virus, don t open it or even view it using your preview pane. Do report any viruses to your IT department and/or delete them immediately. Don t open or forward a spam , delete it immediately. Don t reply to spam, or any you are unsure about, even if it s to unsubscribe this will only validate your address to the sender. Do ignore delivery failure receipts for messages you didn t send. Do consider having a secondary address this can be used when filling out registration forms, surveys, subscribing to newsletters etc. Don t open an unsolicited message unless it is from someone you know and trust. This rule applies to avoiding security breaches in general don t forget that spam can contain viruses and other malicious software. Don t post your address on your website or in newsgroups many spammers trawl the Internet for as many addresses as they can find. Don t give your address to anyone or any website you don t trust. Don t click on any of the links in a suspicious . Do delete any potential phishing immediately. Do contact your bank or financial institution if you can t be certain whether an seemingly from them is genuine. PAGE 3
6 >WEB THREATS AND HOW TO PROTECT AGAINST THEM >SPYWARE >GHOST >KEYLOGGER Spyware is a catch-all term for unwanted software that either secretly monitors your online activity to aid advertising and marketing, or in its more sinister form steals private information from your PC. This can include searching for your banking details, logging your key strokes, or even allowing outsiders to control your computer. Spyware can get onto your computer in a number of ways; downloading seemingly legitimate software or freeware on the web, clicking agree to the small print of a download form, signing up for a new tool bar, smiles or similar offer, or even just visiting a particularly unscrupulous site, can all lead to you falling victim. Spyware is a major risk because it isn t easy to detect and can do untold damage before being discovered. Some telltale signs that you have spyware on your computer include: regular pop ups appearing, your computer running slowly, or automatically being directed to a site you didn t want to visit every time you go online. Your IT department will be able to tell immediately if you have spyware on your computer. If you are in any doubt, contact them at once. >DOS & DON TS: Do comply with your company s acceptable usage policy. Do make sure your browser is up-to-date with the latest security patches. Do only visit websites you know and trust. Don t follow links to sites from or instant messages that you are not sure of. Do check the destination of links. If you hover your cursor over a link it will highlight the destination in the bottom left of your browser window. Do be careful if you use social networking sites like Facebook, LinkedIn or MySpace. Be very wary of friend requests from people you don t know. Many unsolicited friend requests are bogus and will try to lure you into downloading spyware. Do contact your IT department immediately if you think you have spyware on your computer. ALL IMAGES ARE GENERATED USING SOURCE CODE FROM ACTUAL THEATS PAGE 4
7 >IM THREATS AND HOW TO PROTECT AGAINST THEM >INSTANT MESSAGING As instant messaging (IM) becomes more popular, the risks of using it have increased dramatically. IM systems can receive attachments either containing, or linking to, malware or spyware in just the same way as . In fact IM can be even more dangerous because it is even more immediate. >DOS & DON TS: >ROGUEWARE SPYSHERIFF >FAKE ANTI-SPYWARE PROGRAM Don t follow links sent to you by IM. If you must follow a link, cut and paste it into your Internet browser. Do be wary of IM from friends or colleagues that direct you to a website. Their computer may be infected with a virus that sends out these messages. For more information on any of the web and messaging security threats detailed in this guide, and for a copy of your company s and web acceptable usage policy, please contact your IT department. ALL IMAGES ARE GENERATED USING SOURCE CODE FROM ACTUAL THEATS PAGE 5
8 > >FREEPHONE US Americas AMERICAS HEADQUARTERS 512 Seventh Avenue 6th Floor New York, NY USA T F CENTRAL REGION 7760 France Avenue South Suite 1100 Bloomington, MN USA T F Asia Pacific HONG KONG 1601 Tower II 89 Queensway Admiralty Hong Kong T F AUSTRALIA Level Arthur Street North Sydney NSW 2060 Australia T F SINGAPORE Level 14 Prudential Tower 30 Cecil Street Singapore T F Europe HEADQUARTERS 1270 Lansdowne Court Gloucester Business Park Gloucester, GL3 4AB United Kingdom T +44 (0) F +44 (0) LONDON 3rd Floor 1 Great Portland Street London, W1W 8PZ United Kingdom T +44 (0) F +44 (0) NETHERLANDS Teleport Towers Kingsfordweg GR Amsterdam Netherlands T +31 (0) F +31 (0) BELGIUM / LUXEMBOURG Culliganlaan 1B B-1831 Diegem Belgium T +32 (0) F +32 (0) DACH Feringastraße Unterföhring Munich Germany T +49 (0) F +49 (0) PAGE 6
PDF Spam: Spam Evolves, PDF becomes the Latest Threat
 PDF Spam: Spam Evolves, PDF becomes the Latest Threat A MessageLabs Whitepaper: August 2007 Nick Johnston, Anti-Spam Development at MessageLabs Table of Contents Introduction 3 The Beginning of PDF Spam
PDF Spam: Spam Evolves, PDF becomes the Latest Threat A MessageLabs Whitepaper: August 2007 Nick Johnston, Anti-Spam Development at MessageLabs Table of Contents Introduction 3 The Beginning of PDF Spam
ELECTRONIC BANKING & ONLINE AUTHENTICATION
 ELECTRONIC BANKING & ONLINE AUTHENTICATION How Internet fraudsters are trying to trick you What you can do to stop them How multi-factor authentication and other new techniques can help HELPING YOU STAY
ELECTRONIC BANKING & ONLINE AUTHENTICATION How Internet fraudsters are trying to trick you What you can do to stop them How multi-factor authentication and other new techniques can help HELPING YOU STAY
Spam Protection Guide
 Spam Email Protection Guide Version 1.0 Last Modified 5/29/2014 by Mike Copening Contents Overview of Spam at RTS... 1 Types of Spam... 1 Spam Tricks... 2 Imitation of 3 rd Party Email Template... 2 Spoofed
Spam Email Protection Guide Version 1.0 Last Modified 5/29/2014 by Mike Copening Contents Overview of Spam at RTS... 1 Types of Spam... 1 Spam Tricks... 2 Imitation of 3 rd Party Email Template... 2 Spoofed
FAQ. Usually appear to be sent from official address
 FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
>Buyer s guide to hosted security
 >Buyer s guide to hosted security >Ten questions that every IT manager should ask Now part of Symantec >CONTENTS >Introduction to hosted security >P1 1. Is hosted security right for our business? >P2 2.
>Buyer s guide to hosted security >Ten questions that every IT manager should ask Now part of Symantec >CONTENTS >Introduction to hosted security >P1 1. Is hosted security right for our business? >P2 2.
Cyber Security Guide for NHSmail
 Cyber Security Guide for NHSmail Version 3.0 February 2017 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
Cyber Security Guide for NHSmail Version 3.0 February 2017 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
INTERNET SAFETY IS IMPORTANT
 INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
Quick recap on ing Security Recap on where to find things on Belvidere website & a look at the Belvidere Facebook page
 Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
Dataprise Managed Anti-Spam Console
 Dataprise Managed Anti-Spam Console The easy-to-use solution for managing junk and virus-infected email. Use this guide to get started using your personal dashboard. # WinningWithIT What is the Personal
Dataprise Managed Anti-Spam Console The easy-to-use solution for managing junk and virus-infected email. Use this guide to get started using your personal dashboard. # WinningWithIT What is the Personal
Online Scams. Ready to get started? Click on the green button to continue.
 Online Scams Hi, I m Kate. We re here to learn how to protect ourselves from online scams. We ll follow along with Kevin to learn what types of scams are out there, how to recognize the warning signs,
Online Scams Hi, I m Kate. We re here to learn how to protect ourselves from online scams. We ll follow along with Kevin to learn what types of scams are out there, how to recognize the warning signs,
Quick Heal Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac.
 Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to
Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to
BEST PRACTICES FOR PERSONAL Security
 BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
BEST PRACTICES FOR PERSONAL Email Security Sometimes it feels that the world of email and internet communication is fraught with dangers: malware, viruses, cyber attacks and so on. There are some simple
Online Security and Safety Protect Your Computer - and Yourself!
 Online Security and Safety Protect Your Computer - and Yourself! www.scscu.com Fraud comes in many shapes and sizes, but the outcome is simple: the loss of both money and time. That s why protecting your
Online Security and Safety Protect Your Computer - and Yourself! www.scscu.com Fraud comes in many shapes and sizes, but the outcome is simple: the loss of both money and time. That s why protecting your
Quick Heal Total Security for Mac. Simple, fast and seamless protection for Mac.
 Simple, fast and seamless protection for Mac. Product Highlights Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth email
Simple, fast and seamless protection for Mac. Product Highlights Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth email
Quick Heal Total Security for Mac. Simple, fast and seamless protection for Mac.
 Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth
Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth
Using WebQuarantine for Managing Quarantined Messages
 Using WebQuarantine for Managing Quarantined Messages Logging In To start a new mail session: Open your Internet browser and to go the WebQuarantine login page, URL: http://spam.mmc.org/quarantine/login.aspx
Using WebQuarantine for Managing Quarantined Messages Logging In To start a new mail session: Open your Internet browser and to go the WebQuarantine login page, URL: http://spam.mmc.org/quarantine/login.aspx
Security Awareness. Presented by OSU Institute of Technology
 Security Awareness Presented by OSU Institute of Technology Information Technologies Division Security Awareness Topics Social Engineering Phishing Social Networks Displaying Sensitive Information Wireless
Security Awareness Presented by OSU Institute of Technology Information Technologies Division Security Awareness Topics Social Engineering Phishing Social Networks Displaying Sensitive Information Wireless
3.5 SECURITY. How can you reduce the risk of getting a virus?
 3.5 SECURITY 3.5.4 MALWARE WHAT IS MALWARE? Malware, short for malicious software, is any software used to disrupt the computer s operation, gather sensitive information without your knowledge, or gain
3.5 SECURITY 3.5.4 MALWARE WHAT IS MALWARE? Malware, short for malicious software, is any software used to disrupt the computer s operation, gather sensitive information without your knowledge, or gain
Introduction to
 Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting
Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting
I G H T T H E A G A I N S T S P A M. ww w.atmail.com. Copyright 2015 atmail pty ltd. All rights reserved. 1
 T H E F I G H T A G A I N S T S P A M ww w.atmail.com Copyright 2015 atmail pty ltd. All rights reserved. 1 EXECUTIVE SUMMARY IMPLEMENTATION OF OPENSOURCE ANTI-SPAM ENGINES IMPLEMENTATION OF OPENSOURCE
T H E F I G H T A G A I N S T S P A M ww w.atmail.com Copyright 2015 atmail pty ltd. All rights reserved. 1 EXECUTIVE SUMMARY IMPLEMENTATION OF OPENSOURCE ANTI-SPAM ENGINES IMPLEMENTATION OF OPENSOURCE
Be certain. MessageLabs Intelligence: May 2006
 Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
Be certain MessageLabs Intelligence: May 2006 Introduction Welcome to the May edition of the MessageLabs Intelligence monthly report. This report provides the latest threat trends for May 2006 to keep
Risks, Threats, Solution. Nick Johnston, Software Engineer, Symantec.cloud
 Nick Johnston, Software Engineer, Symantec.cloud White Paper: Security Contents Old Enemy, New Weapon................................................................................. 1 URLs A Key Battleground...............................................................................
Nick Johnston, Software Engineer, Symantec.cloud White Paper: Security Contents Old Enemy, New Weapon................................................................................. 1 URLs A Key Battleground...............................................................................
WHAT IS CORPORATE ACCOUNT TAKEOVER? HOW DOES IT HAPPEN?
 WHAT IS CORPORATE ACCOUNT TAKEOVER? Corporate Account Takeover (also referred to as CATO) is a type of fraud where criminals gain access to a business financial accounts to make unauthorized transactions.
WHAT IS CORPORATE ACCOUNT TAKEOVER? Corporate Account Takeover (also referred to as CATO) is a type of fraud where criminals gain access to a business financial accounts to make unauthorized transactions.
How to recognize phishing s
 Phishing email messages, websites, and phone calls are designed to steal money, steal data and/or destroy information. Cybercriminals can do this by installing malicious software on your computer or stealing
Phishing email messages, websites, and phone calls are designed to steal money, steal data and/or destroy information. Cybercriminals can do this by installing malicious software on your computer or stealing
It pays to stop and think
 It pays to stop and think Protect yourself from financial fraud Together we thrive 2 In the first six months of 2018, over 34,000 people were scammed out of 145.4m At HSBC, we work hard to keep our customers
It pays to stop and think Protect yourself from financial fraud Together we thrive 2 In the first six months of 2018, over 34,000 people were scammed out of 145.4m At HSBC, we work hard to keep our customers
Elementary Computing CSC 100. M. Cheng, Computer Science
 Elementary Computing CSC 100 1 Internet (2) TCP/IP and IP Addresses Hostnames and Domain Name System Internet Services Client/Server and Peer- 2- Peer Applications SPAMs & Phishing, Worms, Viruses & Trojans
Elementary Computing CSC 100 1 Internet (2) TCP/IP and IP Addresses Hostnames and Domain Name System Internet Services Client/Server and Peer- 2- Peer Applications SPAMs & Phishing, Worms, Viruses & Trojans
Introduction to
 Introduction to E-mail Ramsey County Library Maplewood Library 3025 Southlawn Drive Maplewood, MN 55109 651-704-2033 Mounds View Library 2576 County Hwy. 10 Mounds View, MN 55112 763-717-3272 New Brighton
Introduction to E-mail Ramsey County Library Maplewood Library 3025 Southlawn Drive Maplewood, MN 55109 651-704-2033 Mounds View Library 2576 County Hwy. 10 Mounds View, MN 55112 763-717-3272 New Brighton
The 12 scams of Christmas
 The 12 scams of Christmas November 2011: SCAMwatch is advising consumers to watch out for this year s 12 scams of Christmas. Scams occur all year round but scammers prey on people s generosity and vulnerabilities
The 12 scams of Christmas November 2011: SCAMwatch is advising consumers to watch out for this year s 12 scams of Christmas. Scams occur all year round but scammers prey on people s generosity and vulnerabilities
Online Fraud and Identity Theft Guide. A Guide to Protecting Your Identity and Accounts
 A Guide to Protecting Your Identity and Accounts As part of SunTrust s commitment to protecting your accounts and identity, we ve created the Online Fraud & Identity Theft Guide, which provides information
A Guide to Protecting Your Identity and Accounts As part of SunTrust s commitment to protecting your accounts and identity, we ve created the Online Fraud & Identity Theft Guide, which provides information
Duplication and/or selling of the i-safe copyrighted materials, or any other form of unauthorized use of this material, is against the law.
 Thank you for your interest in e-safety, and for teaching safe and responsible Internet use to your students. Educators are invited to access and download i-safe curriculum AT NO CHARGE under the following
Thank you for your interest in e-safety, and for teaching safe and responsible Internet use to your students. Educators are invited to access and download i-safe curriculum AT NO CHARGE under the following
PROTECTING YOUR BUSINESS ASSETS
 PROTECTING YOUR BUSINESS ASSETS How to Spot Danger Before Your Computer Gets Infected, Your Site Hosts Malware, and Your Credit Card Number Gets Stolen A MyNAMS Presentation by Regina Smola @2012 Regina
PROTECTING YOUR BUSINESS ASSETS How to Spot Danger Before Your Computer Gets Infected, Your Site Hosts Malware, and Your Credit Card Number Gets Stolen A MyNAMS Presentation by Regina Smola @2012 Regina
Malicious s. How to Identify Them and How to Protect Yourself
 Malicious Emails How to Identify Them and How to Protect Yourself 1.Identify the Sender This is the first thing you should do whenever you receive an email, especially if: It is requesting sensitive information
Malicious Emails How to Identify Them and How to Protect Yourself 1.Identify the Sender This is the first thing you should do whenever you receive an email, especially if: It is requesting sensitive information
SUMMARIES OF INTERACTIVE MULTIMEDIA
 SUMMARIES OF INTERACTIVE MULTIMEDIA GRADE 10-12 INTERNET TECHNOLOGIES 1. Introduction to Electronic Communications Use this lesson to: Understand the differences between the various e-communications modes
SUMMARIES OF INTERACTIVE MULTIMEDIA GRADE 10-12 INTERNET TECHNOLOGIES 1. Introduction to Electronic Communications Use this lesson to: Understand the differences between the various e-communications modes
Paid-for antivirus software
 Paid-for antivirus software Many people keep their computer safe by paying for a security suite (almost half of Which? members, according to our recent survey), which will usually include antivirus software,
Paid-for antivirus software Many people keep their computer safe by paying for a security suite (almost half of Which? members, according to our recent survey), which will usually include antivirus software,
Phishing. What do phishing s do?
 Phishing We have become all too familiar with phishing emails but if that s the case, why do we as a community still fall victim? In this newsletter our goal is to provide you with some basic information
Phishing We have become all too familiar with phishing emails but if that s the case, why do we as a community still fall victim? In this newsletter our goal is to provide you with some basic information
TIPS TO AVOID PHISHING SCAMS
 TIPS TO AVOID PHISHING SCAMS WHAT IS PHISHING? Phishing is the use of fraudulent email, websites, text messages and phone calls to trick people into disclosing personal financial or identity information,
TIPS TO AVOID PHISHING SCAMS WHAT IS PHISHING? Phishing is the use of fraudulent email, websites, text messages and phone calls to trick people into disclosing personal financial or identity information,
Financial scams. What to look for and how to avoid them.
 Financial scams What to look for and how to avoid them. Keep your money secure We take the security and wellbeing of our customers very seriously. So we ve created this guide to highlight the most common
Financial scams What to look for and how to avoid them. Keep your money secure We take the security and wellbeing of our customers very seriously. So we ve created this guide to highlight the most common
Your security on click Jobs
 Your security on click Jobs At Click Jobs is a trading name of Raspberry Recruitment Limited, we're committed to helping you find the right job in a safe and secure environment. On these pages, you can
Your security on click Jobs At Click Jobs is a trading name of Raspberry Recruitment Limited, we're committed to helping you find the right job in a safe and secure environment. On these pages, you can
Cyber Security Guide. For Politicians and Political Parties
 Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
Protecting your Security and Privacy on the Web. Tony Brett Head of IT Support Staff Services IT Services. 11 March 2013
 Protecting your Security and Privacy on the Web Tony Brett Head of IT Support Staff Services IT Services 11 March 2013 Agenda Why bother? Common data leaks Email security Viruses & Trojans Phishing Why
Protecting your Security and Privacy on the Web Tony Brett Head of IT Support Staff Services IT Services 11 March 2013 Agenda Why bother? Common data leaks Email security Viruses & Trojans Phishing Why
Octopus Online Service Safety Guide
 Octopus Online Service Safety Guide This Octopus Online Service Safety Guide is to provide you with security tips and reminders that you should be aware of when using online and mobile services provided
Octopus Online Service Safety Guide This Octopus Online Service Safety Guide is to provide you with security tips and reminders that you should be aware of when using online and mobile services provided
Cyber Security Practice Questions. Varying Difficulty
 Cyber Security Practice Questions Varying Difficulty 1 : This is a class of programs that searches your hard drive and floppy disks for any known or potential viruses. A. intrusion detection B. security
Cyber Security Practice Questions Varying Difficulty 1 : This is a class of programs that searches your hard drive and floppy disks for any known or potential viruses. A. intrusion detection B. security
Barracuda Security Service User Guide
 The Barracuda Email Security Service is a cloud-based email security service that protects both inbound and outbound email against the latest spam, viruses, worms, phishing, and denial of service attacks.
The Barracuda Email Security Service is a cloud-based email security service that protects both inbound and outbound email against the latest spam, viruses, worms, phishing, and denial of service attacks.
Course Outline (version 2)
 Course Outline (version 2) Page. 1 CERTIFIED SECURE COMPUTER USER This course is aimed at end users in order to educate them about the main threats to their data s security. It also equips the students
Course Outline (version 2) Page. 1 CERTIFIED SECURE COMPUTER USER This course is aimed at end users in order to educate them about the main threats to their data s security. It also equips the students
INTERNET SECURITY STAYING SAFE ONLINE
 INTERNET SECURITY STAYING SAFE ONLINE 1 2 Internet security staying safe online This guide provides general advice for people using the internet. It is intended to make you aware of the various things
INTERNET SECURITY STAYING SAFE ONLINE 1 2 Internet security staying safe online This guide provides general advice for people using the internet. It is intended to make you aware of the various things
Page 1 of 6 Bank card and cheque fraud
 Page 1 of 6 happens when criminals steal your cards or chequebook and gain access to funds in your account. More about bank card and cheque fraud Criminals steal your bank cards or cheque book; or they
Page 1 of 6 happens when criminals steal your cards or chequebook and gain access to funds in your account. More about bank card and cheque fraud Criminals steal your bank cards or cheque book; or they
Introduction. Logging in. WebQuarantine User Guide
 Introduction modusgate s WebQuarantine is a web application that allows you to access and manage your email quarantine. This user guide walks you through the tasks of managing your emails using the WebQuarantine
Introduction modusgate s WebQuarantine is a web application that allows you to access and manage your email quarantine. This user guide walks you through the tasks of managing your emails using the WebQuarantine
Cyber Hygiene Guide. Politicians and Political Parties
 Cyber Hygiene Guide Politicians and Political Parties Canadian Election Integrity Initiative Design by ccm.design Cover Image by Songquan Deng Helping to Safeguard the Integrity of the Electoral Process
Cyber Hygiene Guide Politicians and Political Parties Canadian Election Integrity Initiative Design by ccm.design Cover Image by Songquan Deng Helping to Safeguard the Integrity of the Electoral Process
Protecting from Attack in Office 365
 A hacker only needs one person to click on their fraudulent link to access credit card, debit card and Social Security numbers, names, addresses, proprietary information and other sensitive data. Protecting
A hacker only needs one person to click on their fraudulent link to access credit card, debit card and Social Security numbers, names, addresses, proprietary information and other sensitive data. Protecting
Junk mail, aka Spam. Unsolicited messages that are sent in huge numbers and clog your box.
 Gmail Basics, Part 1 Read, Respond, Write and Print What is E-mail? Electronic mail a message sent from one computer to another. Message typically contains text, but can also contain files, images, or
Gmail Basics, Part 1 Read, Respond, Write and Print What is E-mail? Electronic mail a message sent from one computer to another. Message typically contains text, but can also contain files, images, or
CERTIFIED SECURE COMPUTER USER COURSE OUTLINE
 CERTIFIED SECURE COMPUTER USER COURSE OUTLINE Page 1 TABLE OF CONTENT 1 COURSE DESCRIPTION... 3 2 MODULE-1: INTRODUCTION TO DATA SECURITY... 4 3 MODULE-2: SECURING OPERATING SYSTEMS... 6 4 MODULE-3: MALWARE
CERTIFIED SECURE COMPUTER USER COURSE OUTLINE Page 1 TABLE OF CONTENT 1 COURSE DESCRIPTION... 3 2 MODULE-1: INTRODUCTION TO DATA SECURITY... 4 3 MODULE-2: SECURING OPERATING SYSTEMS... 6 4 MODULE-3: MALWARE
South Central Power Stop Scams
 Don t get tricked. People around the country have been receiving emails and phone calls from scammers. South Central Power wants to help you keep your money and prevent scams. Review the helpful tips below.
Don t get tricked. People around the country have been receiving emails and phone calls from scammers. South Central Power wants to help you keep your money and prevent scams. Review the helpful tips below.
NHS South Commissioning Support Unit
 NHS South Commissioning Support Unit ICT Anti-virus Policy This document can be made available in a range of languages and formats on request to the policy author. Version: Ratified by: V.2.1 Alliance
NHS South Commissioning Support Unit ICT Anti-virus Policy This document can be made available in a range of languages and formats on request to the policy author. Version: Ratified by: V.2.1 Alliance
Protection Against Malware. Alan German Ottawa PC Users Group
 Protection Against Malware Alan German Ottawa PC Users Group Minimum Requirements (1) Up-to-date anti-virus and anti-spyware software (2) Software firewall (3) Fully-patched operating system (Windows Update)
Protection Against Malware Alan German Ottawa PC Users Group Minimum Requirements (1) Up-to-date anti-virus and anti-spyware software (2) Software firewall (3) Fully-patched operating system (Windows Update)
Review Kaspersky Internet Security - multi-device 2015 online software downloader ]
![Review Kaspersky Internet Security - multi-device 2015 online software downloader ] Review Kaspersky Internet Security - multi-device 2015 online software downloader ]](/thumbs/72/67088147.jpg) Review Kaspersky Internet Security - multi-device 2015 online software downloader ] Description: Benefits Protecting all your connected devices the one-licence, easy-touse solution Kaspersky Internet Security
Review Kaspersky Internet Security - multi-device 2015 online software downloader ] Description: Benefits Protecting all your connected devices the one-licence, easy-touse solution Kaspersky Internet Security
Why isn t your chapter on Facebook?
 Why isn t your chapter on Facebook? Last Updated February 2011 Why Facebook? Interact with other Women of Today members Recruit members for your chapter Connect with younger generation Facebook is the
Why isn t your chapter on Facebook? Last Updated February 2011 Why Facebook? Interact with other Women of Today members Recruit members for your chapter Connect with younger generation Facebook is the
IT & DATA SECURITY BREACH PREVENTION
 IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
Phishing: When is the Enemy
 Phishing: When E-mail is the Enemy Phishing, once only a consumer worry, is creating headaches for e-mail administrators as businesses become the next target. CONTENTS Understanding the Enemy 2 Three Things
Phishing: When E-mail is the Enemy Phishing, once only a consumer worry, is creating headaches for e-mail administrators as businesses become the next target. CONTENTS Understanding the Enemy 2 Three Things
User s Guide. SingNet Desktop Security Copyright 2010 F-Secure Corporation. All rights reserved.
 User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
Identity Theft, Fraud & You. PrePare. Protect. Prevent.
 PrePare. Protect. Prevent. Identity Theft, Fraud & You Fraud and identity theft incidents claimed fewer victims in 2010 than in previous years. But don t get too comfortable. Average out-of-pocket consumer
PrePare. Protect. Prevent. Identity Theft, Fraud & You Fraud and identity theft incidents claimed fewer victims in 2010 than in previous years. But don t get too comfortable. Average out-of-pocket consumer
Internet Safety Utilize the Internet without Fear
 Internet Safety Utilize the Internet without Fear Khou Yang Noah Fish Eliza Summerlin 1 One-to-One Computer Help Labs Mondays 12-2pm (White Bear Lake) 3-5 (Maplewood) Wednesdays 5-7 (Roseville) Thursdays
Internet Safety Utilize the Internet without Fear Khou Yang Noah Fish Eliza Summerlin 1 One-to-One Computer Help Labs Mondays 12-2pm (White Bear Lake) 3-5 (Maplewood) Wednesdays 5-7 (Roseville) Thursdays
The Challenge of Spam An Internet Society Public Policy Briefing
 The Challenge of Spam An Internet Society Public Policy Briefing 30 October 2015 Introduction Spam email, those unsolicited email messages we find cluttering our inboxes, are a challenge for Internet users,
The Challenge of Spam An Internet Society Public Policy Briefing 30 October 2015 Introduction Spam email, those unsolicited email messages we find cluttering our inboxes, are a challenge for Internet users,
Quick Heal AntiVirus Pro Advanced. Protects your computer from viruses, malware, and Internet threats.
 AntiVirus Pro Advanced Protects your computer from viruses, malware, and Internet threats. Features List Ransomware Protection anti-ransomware feature is more effective and advanced than other anti-ransomware
AntiVirus Pro Advanced Protects your computer from viruses, malware, and Internet threats. Features List Ransomware Protection anti-ransomware feature is more effective and advanced than other anti-ransomware
The Dilemma: Junk, Spam, or Phishing? How to Classify Unwanted s and Respond Accordingly
 The Email Dilemma: Junk, Spam, or Phishing? How to Classify Unwanted Emails and Respond Accordingly Anyone who has used email has experienced this: You open up an email and immediately recognize it s not
The Email Dilemma: Junk, Spam, or Phishing? How to Classify Unwanted Emails and Respond Accordingly Anyone who has used email has experienced this: You open up an email and immediately recognize it s not
PIN / Password Security
 PIN / Password Security www.gatewaycu.com.au INDEX PIN / Password Security 2 Protection of Information 3 Keep Informed 3 Your Protection 4 Online Banking Security 5 Visa Debit Card Security 6 Electronic
PIN / Password Security www.gatewaycu.com.au INDEX PIN / Password Security 2 Protection of Information 3 Keep Informed 3 Your Protection 4 Online Banking Security 5 Visa Debit Card Security 6 Electronic
November 2009 Report #35
 November 2009 Report #35 In October 2009, spam volumes made up 87 percent of all email messages. The most notable highlight this month is the growth of spam originating from APJ (23 percent) and South
November 2009 Report #35 In October 2009, spam volumes made up 87 percent of all email messages. The most notable highlight this month is the growth of spam originating from APJ (23 percent) and South
Create strong passwords
 Create strong passwords Passwords are the first line of defense against break-ins to your online accounts and computer, tablet, or phone. Poorly chosen passwords can render your information vulnerable
Create strong passwords Passwords are the first line of defense against break-ins to your online accounts and computer, tablet, or phone. Poorly chosen passwords can render your information vulnerable
Creating and Using an Account
 Creating and Using an Email Account How to get on the Internet Click two times very quickly (double click) on any of the following icons: These are called browsers. They are what you use to search the
Creating and Using an Email Account How to get on the Internet Click two times very quickly (double click) on any of the following icons: These are called browsers. They are what you use to search the
CUSTOMER TIPS: HOW TO GUARD AGAINST FRAUD WHEN USING ONLINE BANKING OR ATM s
 CUSTOMER TIPS: HOW TO GUARD AGAINST FRAUD WHEN USING ONLINE BANKING OR ATM s ATM Fraud - Watch out for the following scams. Scam 1 - you find you are having difficulty with your card. Someone will come
CUSTOMER TIPS: HOW TO GUARD AGAINST FRAUD WHEN USING ONLINE BANKING OR ATM s ATM Fraud - Watch out for the following scams. Scam 1 - you find you are having difficulty with your card. Someone will come
Layer by Layer: Protecting from Attack in Office 365
 Layer by Layer: Protecting Email from Attack in Office 365 Office 365 is the world s most popular office productivity suite, with user numbers expected to surpass 100 million in 2017. With the vast amount
Layer by Layer: Protecting Email from Attack in Office 365 Office 365 is the world s most popular office productivity suite, with user numbers expected to surpass 100 million in 2017. With the vast amount
Train employees to avoid inadvertent cyber security breaches
 Train employees to avoid inadvertent cyber security breaches TRAIN EMPLOYEES TO AVOID INADVERTENT CYBER SECURITY BREACHES PAGE 2 How much do you know about cyber security? Small business owners often lack
Train employees to avoid inadvertent cyber security breaches TRAIN EMPLOYEES TO AVOID INADVERTENT CYBER SECURITY BREACHES PAGE 2 How much do you know about cyber security? Small business owners often lack
Augmenting existing security infrastructure to mitigate information borne risks
 Augmenting existing security infrastructure to mitigate information borne risks Copyright Clearswift 2017 V1.0 www.clearswift.com Contents Introduction 3 Advanced Information Borne Threats 3 Deep Content
Augmenting existing security infrastructure to mitigate information borne risks Copyright Clearswift 2017 V1.0 www.clearswift.com Contents Introduction 3 Advanced Information Borne Threats 3 Deep Content
Staying Safe on the Internet. Mark Schulman
 Staying Safe on the Internet Mark Schulman 1 Your Presenter Mark Schulman IT professional for almost 40 years No affiliation with any product 2 What We ll Talk About Passwords Email Safety Staying Safe
Staying Safe on the Internet Mark Schulman 1 Your Presenter Mark Schulman IT professional for almost 40 years No affiliation with any product 2 What We ll Talk About Passwords Email Safety Staying Safe
Quick Heal Total Security for Android. Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping.
 Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Botnets: major players in the shadows. Author Sébastien GOUTAL Chief Science Officer
 Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
Botnets: major players in the shadows Author Sébastien GOUTAL Chief Science Officer Table of contents Introduction... 3 Birth of a botnet... 4 Life of a botnet... 5 Death of a botnet... 8 Introduction
KASPERSKY SECURITY FOR MICROSOFT OFFICE s are sent every second. It only takes one to bring down your business.
 Kaspersky KASPERSKY SECURITY for Business FOR MICROSOFT OFFICE 365 emails are sent every second. It only takes one to bring down your business. 2 When Oice 365 meets cyberthreat 24/7 Most businesses have
Kaspersky KASPERSKY SECURITY for Business FOR MICROSOFT OFFICE 365 emails are sent every second. It only takes one to bring down your business. 2 When Oice 365 meets cyberthreat 24/7 Most businesses have
Safety and Security. April 2015
 Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
Web Mail and e-scout Instructions
 Web Mail and e-scout Instructions To log into e-scout: visit our home page at www.greenhills.net, click on web mail at the top of the page OR click on the customer center tab and then the webmail button,
Web Mail and e-scout Instructions To log into e-scout: visit our home page at www.greenhills.net, click on web mail at the top of the page OR click on the customer center tab and then the webmail button,
How to Build a Culture of Security
 How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
Best Practices Guide to Electronic Banking
 Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Unit 2 Assignment 2. Software Utilities?
 1 Unit 2 Assignment 2 Software Utilities? OBJECTIVES Identify software utility types and examples of common software Why are software utilities used? Identify and describe the various networking threats.
1 Unit 2 Assignment 2 Software Utilities? OBJECTIVES Identify software utility types and examples of common software Why are software utilities used? Identify and describe the various networking threats.
to Stay Out of the Spam Folder
 Tips and Tricks to Stay Out of the Spam Folder At SendGrid we are very serious about email deliverability. We live and breathe it each day. Similar to how Google keeps adjusting its search algorithm to
Tips and Tricks to Stay Out of the Spam Folder At SendGrid we are very serious about email deliverability. We live and breathe it each day. Similar to how Google keeps adjusting its search algorithm to
Choic Anti-Spam Quick Start Guide
 ChoiceMail Anti-Spam Quick Start Guide 2005 Version 3.x Welcome to ChoiceMail Welcome to ChoiceMail Enterprise, the most effective anti-spam protection available. This guide will show you how to set up
ChoiceMail Anti-Spam Quick Start Guide 2005 Version 3.x Welcome to ChoiceMail Welcome to ChoiceMail Enterprise, the most effective anti-spam protection available. This guide will show you how to set up
Security Gap Analysis: Aggregrated Results
 Email Security Gap Analysis: Aggregrated Results Average rates at which enterprise email security systems miss spam, phishing and malware attachments November 2017 www.cyren.com 1 Email Security Gap Analysis:
Email Security Gap Analysis: Aggregrated Results Average rates at which enterprise email security systems miss spam, phishing and malware attachments November 2017 www.cyren.com 1 Email Security Gap Analysis:
WITH INTEGRITY
 EMAIL WITH INTEGRITY Reaching for inboxes in a world of spam a white paper by: www.oprius.com Table of Contents... Introduction 1 Defining Spam 2 How Spam Affects Your Earnings 3 Double Opt-In Versus Single
EMAIL WITH INTEGRITY Reaching for inboxes in a world of spam a white paper by: www.oprius.com Table of Contents... Introduction 1 Defining Spam 2 How Spam Affects Your Earnings 3 Double Opt-In Versus Single
Bank of america report phishing
 Search Search pages & people Search Search Search pages & people Search Bank of america report phishing email We recently discovered a new phishing scam from a Bank of America spam email some reports that
Search Search pages & people Search Search Search pages & people Search Bank of america report phishing email We recently discovered a new phishing scam from a Bank of America spam email some reports that
It is my great pleasure to inform that you have won the latest model of Ferrari Car and 4 Bed Room Villa in Palm Jumeirah for attending this Seminar
 You Won!!! It is my great pleasure to inform that you have won the latest model of Ferrari Car and 4 Bed Room Villa in Palm Jumeirah for attending this Seminar To Process and deliver your Car and Villa
You Won!!! It is my great pleasure to inform that you have won the latest model of Ferrari Car and 4 Bed Room Villa in Palm Jumeirah for attending this Seminar To Process and deliver your Car and Villa
Top 10 Global Threat Rank by Source
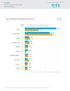 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Security Protection
 Email Security Protection Loay Alayadhi Abstract: Email is the most important business communication tool. Security has been an issue in mail from ancient times. Therefore, email security protection has
Email Security Protection Loay Alayadhi Abstract: Email is the most important business communication tool. Security has been an issue in mail from ancient times. Therefore, email security protection has
SECURING INFORMATION SYSTEMS
 SECURING INFORMATION SYSTEMS (November 7, 2016) BUS3500 - Abdou Illia - Fall 2016 1 LEARNING GOALS Understand security attacks preps Discuss the major threats to information systems. Discuss protection
SECURING INFORMATION SYSTEMS (November 7, 2016) BUS3500 - Abdou Illia - Fall 2016 1 LEARNING GOALS Understand security attacks preps Discuss the major threats to information systems. Discuss protection
WHITEPAPER: Remote workers and mobility. Remote workers and mobility
 A Symantec Connect Document WHITEPAPER: Remote workers and mobility Remote workers and mobility Remote working, outsourcing and telecommuting are realities that bring big benefits to companies and employees
A Symantec Connect Document WHITEPAPER: Remote workers and mobility Remote workers and mobility Remote working, outsourcing and telecommuting are realities that bring big benefits to companies and employees
Conveying Emotion. Chapter 12: Computers In Polite Society: Social Implications of IT. Improving the Effectiveness of . Problems with
 Chapter 12: Computers In Polite Society: Social Implications of IT Fluency with Information Technology Third Edition by Lawrence Snyder Improving the Effectiveness of Email Problems with email: Conveying
Chapter 12: Computers In Polite Society: Social Implications of IT Fluency with Information Technology Third Edition by Lawrence Snyder Improving the Effectiveness of Email Problems with email: Conveying
Student E-Safety Induction
 Central College Nottingham Student E-Safety Induction Academic Year 2015-16 Training & Learning Technologies September 2015 E-Safety It is important to the College that all students know how to stay safe
Central College Nottingham Student E-Safety Induction Academic Year 2015-16 Training & Learning Technologies September 2015 E-Safety It is important to the College that all students know how to stay safe
Symantec Protection Suite Add-On for Hosted Security
 Symantec Protection Suite Add-On for Hosted Email Security Overview Malware and spam pose enormous risk to the health and viability of IT networks. Cyber criminal attacks are focused on stealing money
Symantec Protection Suite Add-On for Hosted Email Security Overview Malware and spam pose enormous risk to the health and viability of IT networks. Cyber criminal attacks are focused on stealing money
Download firefox with virus protection
 P ford residence southampton, ny Download firefox with virus protection 3-11-2015 Protect your devices with the best free antivirus on the market. Download Avast antivirus and anti-spyware protection for
P ford residence southampton, ny Download firefox with virus protection 3-11-2015 Protect your devices with the best free antivirus on the market. Download Avast antivirus and anti-spyware protection for
Symantec Hosted Mail Security Console and Spam Quarantine User s Guide
 Symantec Hosted Mail Security Console and Spam Quarantine User s Guide Copyright 2005 Symantec Corporation and/or its thirdparty licensors. All Rights Reserved. Document Version: RESTRICTION ON USE, PUBLICATION,
Symantec Hosted Mail Security Console and Spam Quarantine User s Guide Copyright 2005 Symantec Corporation and/or its thirdparty licensors. All Rights Reserved. Document Version: RESTRICTION ON USE, PUBLICATION,
How to Stay Compliant with SMS Marketing
 How to Stay Compliant with SMS Marketing Ensure your text campaigns deliver value to customers and keep your business secure GREAT TIPS INSIDE Even legitimate marketers can fall foul of mobile spamming,
How to Stay Compliant with SMS Marketing Ensure your text campaigns deliver value to customers and keep your business secure GREAT TIPS INSIDE Even legitimate marketers can fall foul of mobile spamming,
ONLINE SAFETY. Messaging, , Vlogging and Sexting
 ONLINE SAFETY Messaging, email, Vlogging and Sexting www.eitts.co.uk Contents WhatsApp & Messaging Email Vlogging Sexting THE RISKS People online are not necessarily who they say they are or seem to be.
ONLINE SAFETY Messaging, email, Vlogging and Sexting www.eitts.co.uk Contents WhatsApp & Messaging Email Vlogging Sexting THE RISKS People online are not necessarily who they say they are or seem to be.
FACTS WHAT DOES FARMERS STATE BANK DO WITH YOUR PERSONAL INFORMATION? WHY? WHAT? HOW? L QUESTIONS?
 FACTS WHAT DOES FARMERS STATE BANK DO WITH YOUR PERSONAL INFORMATION? WHY? WHAT? HOW? Financial companies choose how they share your personal information. Federal law gives consumers the right to limit
FACTS WHAT DOES FARMERS STATE BANK DO WITH YOUR PERSONAL INFORMATION? WHY? WHAT? HOW? Financial companies choose how they share your personal information. Federal law gives consumers the right to limit
Best Practice Guide. Encryption and Secure File Transfer
 Best Practice Guide Email Encryption and Secure File Transfer Email Encryption and Secure File Transfer Table of Contents Introduction Encryption Transport Layer Security (TLS) Message Encryption (S/MIME,
Best Practice Guide Email Encryption and Secure File Transfer Email Encryption and Secure File Transfer Table of Contents Introduction Encryption Transport Layer Security (TLS) Message Encryption (S/MIME,
